-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ d78dcc29:aa242350
2024-04-13 06:42:03
@ d78dcc29:aa242350
2024-04-13 06:42:03Opinion about ZBD: Bitcoin, Games, Rewards (iphone)
zbd is a centralised platfom. they have power over users wallets and can deactivate them even with balances, hence making your account pretty much useless. in the times that we are heading , this is definetely not the way. since zbd is A Play to Earn platform, such kind of activity is robbing from users who invested their time to stack sats. just to be kicked out . it's a 0 out of 10 for zbd
WalletScrutiny #nostrOpinion
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 3c984938:2ec11289
2024-04-25 07:23:55
@ 3c984938:2ec11289
2024-04-25 07:23:55https://image.nostr.build/bd90349f0d27124b0932e55baaa298d94ea9a7b655334092c11728f321914059.jpg
Hafa Adai Bitcoiners, Nostr is really amazing. Have you ever ate so much food at a buffet? Did you try all the different types of cake, how could you settle on just one? when there's so many. Each with different favors, frosting and textures. Ugh, now I want cake.
Habla Pac-Man
After departing from the OS green forest where Flycat lives, I must have taken a wrong turn because the forest instantly got darker with each and every step. After some time has passed my eyes started to adjust and now it started to glow. I saw the most yellow fellow. He was being hunted! He ate some kinda fruit, and you can see the ghost 👻 starting to running away.
https://image.nostr.build/cdcce1dcb2da7c4bc4bcc4ff26b45ad7afc76300c59f66bc55e005c035aab94e.jpg
what was it that powered him up? Stories and Content! It was dark and hard to see, as I venture deeper. I almost wanted to turn back. It turns out fiat thugs were hunting him! Thanks to users that voice their stories Habla Pac-Man is empowered. Feel free to report on important issues that matter - have your voice be heard even in the shadows. Habla Pac-man is on your side in the darkest part of the Publishing Forest to be your guiding light!
https://image.nostr.build/ea9625c2279c7a02fd1d42a218594de0d79fcd258ab35b6665e43a02b53cf7e4.jpg
Habla.news is wonderfully open source, so write on! Beware, ICANN still lurks in these shadowed woods. FYI, his original color is white, he just appears yellow at night because of the woods. Blue for meal time. 😂 This hamster is very happy to see mainstream media content getting eaten by users like you and me. As long as we write, Habla will be well fed.
Highlighter
Ever stumble on something by accident? I spotted something emitting light in the distance, as I continue to dive deeper into the Publishing Forest. Oh Look, an almighty highlighter! So any text I want to stand out, I can save it like a digital note on the side and publish it as a note on Nostr. Highlighter.com is content central! Some content creators have significant insight into certain topics and create alpha content. Instead of using third party services like Medium, Substack, and WordPress etc where you're not getting much credit for your content, they now can use this new powerful tool. Will you use this tool dear user? Whatever will you create?
https://image.nostr.build/b70011965aa3c6bfdbfaca404005d5522081c5f0390d324a1f1e1a9b2be69943.jpg
I held onto the highlighter, and I begin to feel powered! With this tool, Content creators can monetize their content! What a wonderful tool! Prehaps, I should start utilizing this? Whatcha think? Would you support a writer like me for 1,000 sats/quarterly?
https://image.nostr.build/4386899dc0fd455b340f0fd433d5a2bf2c865e6030c55dfbba53cbd192bb133d.jpg
It should be noted that highlighter.com is still new, and in development at the time of this publishing. I can't wait until it unveils all it's features. It does work and is usable but it's still in development. I'll wait.
https://image.nostr.build/04f92b7847fc6c5d7dce6a1152a1a4e5fe8613a0a6995801e1b942f1fe1ba97e.jpg
I'm taking this with me! I'm so happy that I can easily use "Identity by encryption" via Nostr. Just stupendous! It makes me wonder, how could this have not existed for so long? This is freedom, owning your content and not being forced to agree to share its revenue to evil corporate thugs because of "Terms and Conditions" that only care about their platform and not a user like me. I'm taking back my power, will you?
https://image.nostr.build/d3450fcf2eb9998d1150f5b7d1d261b9eb7547e9504a18f66f9dd4efe5107f57.png
The Blogstack.io curse on me
Some words about blogstack.io, the entire reason I joined Nostr was when I watched a tutorial video about Nostr as I was trying to learn. The youtuber was explaining it and used blogstack.io as an examples. I was sold within those 3 seconds of seeing blogstack.io and lost interest about blah blah Nostr is this and that. Those 3 seconds motivated me more to use Nostr then the whole 7min tutorial. So, I excitedly downloaded the app(Amethyst), made an account only to be disappointed or cursed that still plagues me today-- to not be able to use blogstack.io for some reason. I've always wanted to start my own blog but hated the idea of medium. I could go to blogstack.io, but I couldn't interact with it. This was my first experience. So the app sat on my phone for like 2 weeks. A friend of mine got a nostr account and told me to follow him, that's when it pique my interest again. One thing led to another, then another. Before I knew it, I had fallen into the rabbit hole. It is a wonderland of its own. I wish for you dear user to have a better first time experience then I did. And I hope you enjoy this content. If blogstack.io works for you- go for it, but I can't judge it's platform because 404 eludes me.
The Shipyard Pub
My journey is at it's end in the Publishing Forest and into a shipyard of sailboats. ⛵ So, I guess it's time for me to sail away! Get it? Time? The sailboats have a schedule for when they head in and out of port. So if you want to schedule a note for example, now, 4 hours, or a day+ out you can do so by using Shipyard. There's no need to feel a constant need to log on to keep publishing a note(or reposting) to stay relevant. Simply, write a note, and put a time when you want your note to be seen so you can capitalize on all time zones. Quite useful tool. If you've visit my profile page, I launched a time series of hamsters recently. I used shipyard to schedule them. Very nice feature.
https://image.nostr.build/6c0ce64194cb48c17cca219018d67fb1c5b852518fb6b72ce2087c05e6d181ce.jpg
Okay, Time for this #Hamstr to Sail away to the next adventure. Wherever will I go, is yet to be seen. Follow as I journey to find Knights of Nostr.
https://image.nostr.build/b841250eec60d41872fd61faadc027da38b32b63c5fe5c08f1b8a07ddb1342a3.jpg
I know in my heart they're out there, so let's find them! Often unseen, unappreciated and not loved for their code/software that sets us free. Together, we can change hearts, and minds but we need privacy of Identity or we'll all be punished for having a mind. ICANN Plagues the internet. Recently, Samurai Wallet was taken down because of mixing services. The Need for Identity by encryption and websites to move off ICANN's jurisdictional websites to IPFS is evermore important to adopt freedom. Yes, that means we need a Github Nostr style. So developers are never criminalized for restoring financial privacy, and speech to users. All of these platforms are Psyphers to be used against anti-reconnaissance. So speak freely!
Send some love to these specular devs that are helping to shape Nostr.
👉💋💋Kisu for OpenSource
💋💋Pablof7z💋 @npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
💋💋 Verbiricha💋 @npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
Get your NIP-23 (Long-Form-Content) Here, or get it over there, you're bound to get it from somewhere. Until Next time! Wish me smooth sailing? I'll be adopting njump.me style as of this article.
with 🧡 Onigirl
-
 @ ef1a1108:d2bb31da
2024-01-26 16:36:21
@ ef1a1108:d2bb31da
2024-01-26 16:36:211 000 000 satoshis
2 days before the Grand finale, we can proudly annouce we hit the first milestone - 1 million satoshis!
Huge warm thank you to all supportes of The Great Orchestra of Christmas Charity!

Join #orchestrathon on the Grand Finale day
We'd like to invite you to a special type of event we are organising on Nostr - #orchestrathon!
Rules are simple:
``` 1. This Sunday at 18.00 - 19.00 we all connect to nostr relays to join the #orchestrathon
-
For the whole hour - we zap this profile, posts or comments as crazy!
-
At 19.00 it's culmination of both #orchestrathon and Grand Finale ```
We're planning to stream some of The Great Orchestra concerts on zap.stream on that day.
Join the stream, where you can also zap!
Hopefully we can engage a bit Nostr community to support the cause with having fun and zapping during the last hour of Grand Finale
Every Nostr zap to our profile, comment or post will be counted as a contribution and displayed on our Geyser page.
Those contributions will be also rewarded with Nostr badges :)

Rewards
We added several rewards to the project! They look absolutely fabulous with the new Geyser update.

The rarer the badge is, the more expensive it is, but also the more real Proof of Work in computation it took to mine. Epic badge took several hours to be mined...
You can purchase beautiful and unique Nostr badges or choose a physical item, like merchandise or ticket to European Halving Party.
This is a great occasion to buy a very cool t-shirt, hat or ticket to a great event with supporting supply of state-of-the-art, saving lives medical equipment children and adults.

-
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ ef1a1108:d2bb31da
2024-01-23 15:34:05
@ ef1a1108:d2bb31da
2024-01-23 15:34:05Nostr for The Great Orchestra of Christmas Charity

This Sunday, 28.01.2024 at 18:00 - 19:00 UTC we're inviting you to take pare in a very unique #zapathon
Nostrians taking part in this special zapathon that will play in tune with thousands of people playing together with The Great Orchestra of Christmas Charity on their 32nd Grand Finale! Hence the name #orchestrathon
The goal of #orchestrathon is to support the goal of this years Grand Finale, which is: funding equipment for diagnosing, monitoring and rehabilitating lung diseases of patients in pulmonology wards for children and adults in Poland
That means all bitcoin from zaps will be converted to PLN and donated to The Great of Christmas Charity foundation.
What's The Great Orchestra of Christmas Charity? What is the 32nd Grand Finale?! You'll find all of those answers on Geyser project story, or a few paragraphs below 👇 Now coming back to #orchestrathon...
What Is #Orchesthrathon
This Nostr account is a was generated on Geyser and is tied to Geyser project: Bitcoiners support The Great Orchestra of Christmas Charity
That means all zaps sent to this account are at the same time funding Geyser campaing.
So not only you will contribute to the goal in the project, also all the zap comments will be visable there.
Ain't that crazy? We can use this campaign as one giant #orchestrathon client!

Rules are simple:
- On Sunday at 18.00 - 19.00 we all connect to our relays to join the #orchestrathon
- For the whole hour - you can zap this profile, our posts or comments as crazy!
- At 19.00 it's culmination of both #orchestrathon and Grand Finale
All Nostrians who zap will receive special badges, depending on the zapped amount (in total):

On Sunday there will be lot's of concerts and events happening all day, culminating with Grand Finale closing at 19.00. We will try to launch a stream on zap.stream, so we can enjoy Grand Finale and concerts together!
This #orchestrathon and Geyser fundraise is organised by Dwadzieścia Jeden, a community of polish Bitcoiners. More about us and Proof of Work in the project story 👇
We're not only Bitcoiners, are also Nostrians, follow us: Dwadzieścia Jeden account: @npub1cpmvpsqtzxl4px44dp4544xwgu0ryv2lscl3qexq42dfakuza02s4fsapc Saunter: @npub1m0sxqk5uwvtjhtt4yw3j0v3k6402fd35aq8832gp8kmer78atvkq9vgcru Fmar: @npub1xpuz4qerklyck9evtg40wgrthq5rce2mumwuuygnxcg6q02lz9ms275ams JesterHodl: @npub18s59mqct7se3xkhxr3epkagvuydwtvhpsacj67shrta8eknynegqttz5c3 Tomek K: @npub14wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqvagcye Tom Chojnacki: @npub1m0sxqk5uwvtjhtt4yw3j0v3k6402fd35aq8832gp8kmer78atvkq9vgcru Gracjan Pietras: @npub1trkudtnp7jg3tmy4sz8mepmgs5wdxk9x2esgts25mgkyecrse7js6ptss5 Tomek Waszczyk @npub1ah8phwmfyl2lakr23kt95kea3yavpt4m3cvppawuwkatllnrm4eqtuwdmk
Original Geyser project story
Saving Lives and Preserving Health

Dwadzieścia Jeden a polish node in decentralised bitcoin communities network Twenty One, is proud to facilitate bitcoin fundraising for the biggest, non-governmental, non-profit, charity in Poland — The Great Orchestra of Christmas Charity.
For the past 31 years, GOCC continuously fundraises money for pediatric and elderly care in Poland. Each year, a culmination of the raise occurs during the last Sunday of January in the shape of The Grand Finale — a joyful day that when tens of thousands volunteers worldwide, especially kids and teenagers, go on the streets to gather money for the cause, giving donors hear-shaped stickers with logo of the foundation. If you're in Poland on that day, basically every person you'll meet on the street will proudly wear GOCC heart.

The same hear-shaped stickers can be seen in every hospital in Poland on thousands of high quality medical equipment bought by The Great Orchestra. There is not a single polish family that hasn't benefited in some way from this equipment, and it saved thousands of lives, especially the little ones.


32nd Grand Finale Goal
This year, 32rd Grand Finale will take place on 28th of January. The aim of the 32nd Grand Finale is post-pandemic lung diseases — the raised funds will be used to purchase equipment for children's and adults' respiratory units.
The Foundation plans to purchase:
-
equipment for diagnostic imaging, i.a. MRI and ultrasound equipment,
-
equipment for functional diagnosis, i.a. polysomnographs and portable spirometers,
-
equipment for endoscopic diagnosis, i.a. navigational bronchoscopy systems and bronchoscopes
-
equipment for rehabilitation - equipment for pulmonary rehabilitation used in the treatment of patients after lung transplantation
-
equipment for thoracic surgery, e.g. electrocoagulation systems and cryoprobes.
The Great Orchestra of Proof of Work
-
31 years of non-stop fundraising for state-of-the-art saving life equipment, running medical and educational programmes and humanitarian aid
-
2 billion PLN or ~11,781 BTC raised in total
-
Areas of help: children's cardiac surgery, oncology, geriatrics, neonatology, children's nephrology, children's and young people's mental health services, ambulances for children's hospitals, volunteer firefighters & search & rescue units
-
Last year Grand Finale raised over PLN 240 million (1,410 BTC) for a goal to fight sepsis
-
You can check how money from 2022 report (224 376 706 PLN or ~1,321.69 BTC) raise were spent here (although it's in polish)
-
In addition to work focused on Poland, GOCC fundraised money for hospitals in Ukraine and provided substantial humanitarian aid for Ukrainian refugees, Polish-Belarusian border crisis, Turkey earthquake victims and more
-
GOCC is the most-trusted Polish organization and is at the top of the list as the most trusted public entities in Poland

What We'll Do With Gathered Funds
Gathered bitcoin will be converted to PLN by a polish exchange Quark and donated to The Great Orchestra of Christmas Charity after The Grand Finale which takes place on January 28th.

Dwadzieścia Jeden Proof of Work
We're a group of polish pleb Bitcoiners that started organising ourselves about 2 years ago.
Our activities include:
-
organising regular bitcoin meetups in several cities in Poland, also Nostr meetup in Warsaw
-
organising Bitcoin FilmFest and European Halving Party in Warsaw
-
orangepilling and maintaining map of polish bitcoin merchants in Poland on btcmap.org
-
giving talks on bitcoin
-
volounteering for helping with bitcoin payments and running bitcoin workshops on non-conferences (eg. Weekend of Capitalism)
-
working in human rights centered NGOs and promoting bitcoin as a tool for protecting human rights
-
...and we're just starting!
Find Out More
Gallery











-
 @ 5df413d4:2add4f5b
2024-02-18 18:26:57
@ 5df413d4:2add4f5b
2024-02-18 18:26:57You Are Not A Gadget by Jaron Lanier
Reading Jaron Lanier’s 2010 You Are Not A Gadget in 2023 is an interesting experience—equal parts withering, prophetic, and heretical clarion call warning from a high priest of the Technocracy and rambling, musing, cognitive jam session from a technofied musician-philosopher.
Yet, in ways that I think the author would be simultaneously pleased, amused, saddened, and disturbed by, the 13 yeas since the book’s publishing have, in places, proven him right with stunning foresight and precision, and in others, made his ideas appear laughable, bizarre, even naive. The book is written in five parts, yet I would suggest viewing it as two discrete elements—Part One (around the first half of the book) and…everything else.
For context, Lanier, is a computer scientist and early technologist from the area of Jobs, Wozniak, and Gates, and is considered to be a founding father of virtual reality. He is also a consummate contrarian, a player of rare and obscure musical instruments, a deep interdisciplinary thinker…and a white man with dreadlocks named Jaron.
PART ONE
Part One of the book “What is a Person?” reads like a scathing and clear-eye manifesto—where Lanier is batting 1000, merciless in his rightness. Were one to pull a passage that speaks to the soul of this portion of the book, it might be the following: “The net does not design itself. We design it.”
Lanier terms the prevailing technocratic ideology—the particular winning tech-nerd subculture that has now come to capture our society—as “the cybernetic totalist” or “digital Maoists.” Essentially a materialist and stealth collectivist movement in new-age technocratic dress, that through its successes, and now excesses, represents much the same of religion that it’s founders would have claimed to be “evolving past.”
Lanier points out that in this, we are simply trading the pursuit of finding God in spirituality or the afterlife, for a notion of digital immortality—seeking, or, if possible, becoming, God in the cloud. He aptly identifies that this worldview requires that society, and all human interactions really, be savagely bent into adherence to this new religion of aggregation that demands deification of data, gross diminishment of the individual, and belief in some objective (but never defined) "meaning" that exists beyond and apart from the human observer.
With skill and simple wit, he raises strong, rational counterpoint to the digital Maoists’ obsession with quantity, data in aggregate and at-scale, as society's prime directive “A fashionable idea in technical circles is that quantity […] turns into quality at some extreme scale […] I disagree. A trope in the early days or computer science comes to mind: garbage in, garbage out.”
Lanier is able to envision the digital cages that likes of Facebook, Youtube, social-media dating apps would become for the internet native generations. Of whom he writes “The most effective young Facebook users […] are the ones who create successful online fictions about themselves,” and “If you start out by being fake, you’ll eventually have to put in twice the effort to undo the illusion if anything good is to come of it.”
Lanier’s 2010 criticism of Wikipedia-ism is now double or triply apropos in our current hype cycle of “AI magic” and Everything-GPT, “Wikipedia, for instance, works on what I can the Oracle Illusion, in which knowledge of human authorship of a text is suppressed in order to give the text superhuman validity. Traditional holy books work in precisely the same way and present many of the same problems.” This same deep truth now sits at the heart of every “new” creation churned out by the flavor-of-the-week, plagiarism-at-scale, generative AI tool.
More darkly, he is also able to foresee the spectre of a return to collectivism lurking both at the core and on the margins of our new digital age—“The recipe that led to social catastrophe in the past was economic humiliation combined with collectivist ideology. We already have the ideology in its new digital packaging, and it’s entirely possible we could face dangerously traumatic economic shock in the coming decades.”—“No Shit” said everyone who lived through 2020-2022…
This brings us, eerily, to the world of today. Where aggregate insights are upheld as more valuable than discrete insights. Where crowds are are assumed to have more wisdom than individuals. Where truth is twisted into a might-is-right numbers game. A world ruled by the idea that if we can just centralize enough information and sufficiently pulverize authorship, the result will, necessarily, be something super-intelligent, "alive," and perhaps even divine.
In short, the cybernetic totalists and digital Maoists, having killed reason, now sit on its corpse like a thrown, smearing its blood on the walls in the name of art and reading its still-steaming entrails for prophecy.
If I were to infer some ideological takeaway from Part One of the book, it might be that Lanier seems to axiomatically reject any affirmative implication of the Turing Test. Simply put, he believes that bits are not and cannot ever be alive independent of the human-as-oracle. Further, there is no objective meaning beyond the human observer—in fact, that observer fundamentally creates any meaning there is to be had. This is best illustrated by one of the most powerful passages in the book:
“But the Turing Test cuts both ways. You can’t tell if a machine has gotten smarter or if you’ve just lowered your own standard of intelligence to such a degree that the machine seems smart. If you can have a conversation with a simulated person presented by an AI program, can you tell how far you’ve let your sense of personhood degrade in order to make the illusion work for you?”
Ponder this well, Anon.
EVERYTHING ELSE
With all of the great stuff above out of the way, we must turn to…the rest of the book. Parts Two through Five breakdown into something more like a stream of consciousness. And while there are certainly many nuggets to insight and beauty to be found, the book becomes largely dis-coherent and very difficult to read. That said, the remainder of the book does contain three particularly compelling threads that I find to be worth pulling on.
Internet Attribution First, are Lanier’s musing about money and attribution in our authorless “information wants to be free” world. He laments the infinite elevation of advertising and offers harsh critique to the concept of attention as the new currency—as this tends to overwhelmingly reward the aggregator and a piddling few soulless super-influencers at the expense of all other users and creators.
Interestingly, under the guise of “what could have been” he imagines a world where attribution is tracked across the web (though how this achieved is left unanswered) and royalty payments can flow back to the author seamlessly over the internet. I find his vision to be intriguing because in 2010, we lacked the technology to either track attribution across the web or facilitate seamless micropayment royalties based on access / usage.
While we still don't have the ability to achieve the type of fully-tracked, always-on attribution Lanier imagines, we do now have the ability to stream payments across the internet with bitcoin and the lightning network. While Lanier can be excused for not mentioning the then uber-nascent bitcoin in 2010, bitcoin’s development since only goes to underscore the prescience of Lanier’s imagination.
The bigger question that now remains, especially in the face of the advent of “AI,” is whether such a system to manage and therefore enforce attribution globally on the internet would even be a good thing. Where obscured attribution enables mashed-up plagiarism-at-scale, centrally enforced attribution can just as easily enable idea, content, discovery, and innovation suppression-at-scale.
Music in the New Age Second, much of the book, particularly in the second half, is filtered through the lens and language of music. Music is essential to Lanier’s inner life and it is clear that he views music as an emergent mystery force attributable to something unknowable, if not divine, and entirely unique to the human experience.
He bemoans the music of the 2000s as lacking in any distinct chronological era sound—everything is either a rehashed mashup or digitally lofi-ed emulation of sounds from previous begone eras—it is music that is impossible to place. To him, it is as though musical evolution stopped right around the time of the advent of the internet…and then folded back in on itself, creating an endless kaleidoscoping of what came before but rarely, if ever, the creation anything truly new.
In response, Lanier goes so far as to imagine the ridiculous (my take, not his) world of “Songles”—songs on dongles—essentially physical music NFTs. In Songleland, listening to the hottest tracks at a party hinges on the guy or gal with the dankest songles swinging through and plugging them into the Songle player. And songles, being scarce, even become speculative investments. On this, Lanier manages to be both right and wrong in only the most spectacularly absurd of ways.
But what Lanier really laments is the passing of popular music as a shared cultural experience at national or even global scale. During Lanier’s coming of age through the 1960-80s—with only a few consolidated channels for music distribution, it was truly impossible to escape the sounds and influence of the Beatles or Prince or Micheal Jackson—everyone heard it and even the deaf still felt it.
In the end, Lanier could image Songles but he couldn’t envision what Spotify would become—a conduit to shatter music distribution into a myriad of tiny longtails—providing infinitely fragmented and individually fine-tuned music experiences rather than large and cohesive cultural moments. However, even in this miss, Lanier is largely able to project what Spotify-ed music would resolve to—music designed as much or more to please the self-referential selection algorithm than any real, human listeners. A dangerously foretelling insight that goes well beyond music as AI tools are posed to become the "googling" of the next technological cycle—what happens to information, to human thought, when the majority of "generative AI" outputs are just the machine referencing itself?
Digital Neoteny The final thread to pull is that of "digital neoteny," the retention of juvenile behaviors in adult form, in this case, a neoteny of the mind if you will. Lanier sees the internet as specifically primed to propagate three kinds of neoteny in digital-native humans— a blissful and curious Bachelardian neoteny (as in Gaston Bachelard’s Poetics of Reverie); a cruel and mob-like Goldingesque neoteny (as in William Golding’s Lord of the Flies); and a general and deeply pervasive, infantile neoteny.
Neoteny of the Bachelardian variety, which Lanier likens to “the sense of wonder and weirdness that a teen can find in the unfolding world,” is what he feels the internet has provided in a few brief and magical moments generally aligned with the “early days” of successive internet technologies, movements, and companies—through this generally degrades into Goldingesque neoteny as novelty gives way to ossification.
Lanier’s missives on Bachelardian neoteny feel especially pertinent to the present state of Nostr (where I am publishing this writing). Nostr is in a moment where winner-take all dynamics and corporatization have yet to take hold. Child-like revelry abounds with each new discovery or novel Nostr client development so much so that the likes of Jack Dorsey compare it to the excitement of the early internet.
But with time, if and as the Nostr protocol wins, to what extent will technical lock-in take hold here? To what extent will calcification of seemingly trivial or even comical decisions being made by client devs today have dramatic implications on the feasibility of other development in the future? And will we early Nostr users, at some point put down welcoming inclusivesness for insular tribalism—and in what ways might we be doing this already?
Finally, to the third kind of neoteny, Infantile neoteny—which perhaps incapsulates the internet even more so than either of the other two types—Lanier sees the net driving an evermore prolonged deferral of maturity, resulting ultimately in some centrally-managed permanent arresting of society in a stupefied and juvenile mental state:
“Some of the greatest speculative investments in human history continue to converge on Silicon Valley schemes that seemed to have been named by Dr. Seuss. On any given day, one might hear of tens or hundreds of millions of dollars flowing to a start-up company named Ublibudly or MeTickly. These are names I just made up, but they would make great venture capital bait if they existed. At these companies one finds rooms full of MIT PhD engineers not seeking cancer cures or sources of safe drinking water for the underdeveloped world but schemes to send little digital pictures of teddy bears and dragons between adult members of social networks. At the end of the road of the pursuit of technological sophistication appears to lie a playhouse in which humankind regresses to nursery school.”
The popular culture of the early 2020s—with it’s NFT Monke JPEGs, silent and masked TikTok dancing in the drab aisles of crumbling department stores, and rampant peer-pressured social-media virtue-signaling and paternalism—could scarcely be described in any more stark and specific detail. That such could be seen so vividly in 2010 is as masterful as it is dishearteningly dark.
CONCLUSION
You Are Not A Gadget is a special thing, a strange beast—as lucid in its first half as it is jumbled, meandering, and even nonsensical in its second half. And while the discerning reader might judge the book harshly for these structural failings, I doubt the author would care, he might even welcome it. Lanier’s apparent purpose in writing is to share his mind rather than please the reader in any particular regard. The sufficiently curious reader, one who is willing to engage with the book’s content, for whatever the book’s faults may be, finds a king’s randoms of wisdom, insight, and uncanny foresight.
In closing, it seems fitting to recall one of Lanier’s earliest warnings in the book, “Maybe if people pretend they are not conscious or do not have free will […] then perhaps we have the power to make it so. We might be able to collectively achieve antimagic.” 13 years on, this feels more pressing and urgent and true than ever. (Rating: 4/5🐙)
-
 @ cb8f3c8e:c10ec329
2024-01-13 09:25:01
@ cb8f3c8e:c10ec329
2024-01-13 09:25:01Written by ALEX MREMA @npub1w4zrulscqraej2570gkazt0e7j0q3xq4437hnxjqfvcs59hq86fs9vnn4x
From the 13th of January 2024 the football world’s eyes will all converge on the Ivory Coast as 24 of Africa’s best football nations look to take each other on for the title of Africa’s best come 11th February. Though there is only going to be one winner, that doesn’t mean we aren’t promised exceptional football, shocks and players showcasing their razzle dazzle throughout the next 29 days. This article will focus on the players from each of the 24 competing nations who don’t get the spotlight they deserve but are certain to cause trouble.

IVORY COAST Name: Simon Adingra Age: 21 Club: Brighton and Hove Albion(England) Position: Winger The bright orange Ivorian jerseys are not the only thing that will catch your eye from this squad as the youthful, electrifying and pacey Brighton winger Simon Adingra is certainly bound to catch the interest of some during the tournament. His eye for goal and his turbo speed is bound to give trouble to any defender.

EQUATORIAL GUINEA Name: Saúl Coco Age: 24 Club: UD Las Palmas(Spain) Position: Center-Back Equatorial Guinea are not newcomers to the competition and are not going to be a pushover in a group that contains hosts Ivory Coast and the star-studded Nigeria. A player one must recognize from the Central African country is none other than Saul Coco. 6-foot-2 and a menace at the back, he will catch the eye of many particularly in his match up with the towering Bissau-Guinean players and of course Nigeria’s Victor Osimhen.

GUINEA-BISSAU Name: Fali Candé Age: 24 Club: FC Metz(France) Position: Centre-Back Like Equatorial Guinea, Guinea- Bissau come to the tournament with a familiar idea of what is expected. This is a nation known for putting up a challenge no matter what and are able to even pull a shock or two. If they are going to attract any wins in the tournament they will need a solid defense in their attack-heavy group, luckily for Guinea Bissau, they have Fali Cande who is one of the rocks at the back that Africa should have an eye on as he is aggressive and committed to keeping a clean sheet.

NIGERIA Name: Moses Simon Age: 28 Club: FC Nantes(France) Position: Winger Nigeria come in as one of the favourites to win it all and with a squad that has the African player of the year (Victor Osimhen) it’s hard to disagree that they are capable of delivering the cup back to Nigeria for the first time since 2013. A player that is sure to electrify the tournament is FC Nantes winger Moses Simon who shone in the last edition but had his time cut short after the Super Eagles shock defeat to Tunisia in the Round of 16. Now with their other attacking star (Victor Boniface) officially out of the tournament, will the Simon-Osimhen-Boniface attacking duo bear fruit for Nigeria?

CAPE VERDE Name: Jamiro Monteiro Age: 30 Club: San Jose Earthquakes(USA) Position: Center Midfield A man of experience and flair, Jamiro Monteiro is going to be a man lighting up the highlight reels throughout his time in the Ivory Coast. With a flair like Alex de Souza and an awareness equal to that of David Silva, Monteiro instantly sets himself as a man to watch in Cape Verde’s conquest to spice up the tournament.
 EGYPT
Name: Ahmed Fatouh
Age: 25
Club: Zamalek(Egypt)
Position: Left Back
Fatouh has been described as the “Egyptian Marcelo” for his ability to excel in the attacking third of the pitch despite being a left back. His skill and drive towards making an impact upfront shall not blindside viewers that he can also do it defensively. This man is pivotal for the Egyptians in their quest for glory.
EGYPT
Name: Ahmed Fatouh
Age: 25
Club: Zamalek(Egypt)
Position: Left Back
Fatouh has been described as the “Egyptian Marcelo” for his ability to excel in the attacking third of the pitch despite being a left back. His skill and drive towards making an impact upfront shall not blindside viewers that he can also do it defensively. This man is pivotal for the Egyptians in their quest for glory.

GHANA Name: Salis Abdul Samed Age: 23 Club: RC Lens(France) Position: Central Defensive Midfielder Entering AFCON 2023, the Black Stars of Ghana are a nation booming with talent mixed with just the right amount of experience. Looking to put away the demons of their last AFCON appearance and deliver their first trophy since 1980, Ghana are likely to turn to their midfield to take them all the way. Yes, Mohammed Kudus is in that midfield but a player that goes unnoticed in that midfield is Salis Abdul Samed. He is magnificent at stealing the ball from opponents in a clean manner, further, he is able to put Ghana in promising positions when he moves the ball up. He truly is the new generation player that Ghana needed to make their midfield a threat to opponents.

MOZAMBIQUE Name: Geny Catamo Age: 22 Club: Sporting CP (Portugal) Position: Winger The scouts should keep an eye out for this young talent. He manages to wriggle through spaces with his dribbling and also leave defenders in the dust when going one on one with them. Catamo carries forward the game easily and with purpose and a lucid hunger. Head coach Chiquinho Conde should put his trust in this young man to make Mozambique a threat in the tournament.
 CAMEROON
Name: François-Régis Mughe
Age: 19
Club: Olympique de Marseille(France)
Position: Winger
The youngest player on this list is a special prospect. His strength and pace is bound to make any defender have a difficult time when going up against him. He can create something out of nothing when given playing time, Cameroon coach Rigobert Song should make him have a taste of the competition and he will be wowed by the talent he has in his hands.
CAMEROON
Name: François-Régis Mughe
Age: 19
Club: Olympique de Marseille(France)
Position: Winger
The youngest player on this list is a special prospect. His strength and pace is bound to make any defender have a difficult time when going up against him. He can create something out of nothing when given playing time, Cameroon coach Rigobert Song should make him have a taste of the competition and he will be wowed by the talent he has in his hands.
 THE GAMBIA
Name: Ablie Jallow
Age: 25
Club: FC Metz(France)
Position: Winger
Classy, calm and collected. These are the three words that can best be used to describe Gambia’s top scorer during qualifiers. He carries an aura that is simply impossible to ignore and he comes at defenders like a high speed train. He will look to be the main influence in The Gambia’s drive towards making another quarter final run like in the last edition of the tournament. Oh, don’t give him time and space to shoot because he will punish the keeper.
THE GAMBIA
Name: Ablie Jallow
Age: 25
Club: FC Metz(France)
Position: Winger
Classy, calm and collected. These are the three words that can best be used to describe Gambia’s top scorer during qualifiers. He carries an aura that is simply impossible to ignore and he comes at defenders like a high speed train. He will look to be the main influence in The Gambia’s drive towards making another quarter final run like in the last edition of the tournament. Oh, don’t give him time and space to shoot because he will punish the keeper.

GUINEA Name: Amadou Diawara Age: 26 Club: RSC Anderlecht(Belgium) Position: Defensive Midfielder Composure must be this man's middle name. Once he has the ball it is not getting lost with him, he keeps the ball until he releases a pass -which on occasion are mighty sensational- despite being a defensive midfielder,he is capable of bringing up the ball to threatening positions; when Guinea are in trouble at the back he is there to clean up the mess. He is the real deal. He is Amadou Diawara.

SENEGAL Name: Ismail Jakobs Age: 26 Club: AS Monaco(France) Position: Left Back Senegal will look to make it to their third final in as many tournaments and at the same time retain their crown. A new feature to the Lions of Teranga side is left back Ismail Jakobs who is very quick and tends to join the attack. He does have a left foot capable of finding the back of the net but it’s his defensive recovery and ethic that magnifies him above some of the other modern day defenders. He is one the Senegal camp must protect from any injuries or suspensions as he is key for their progression in the Ivory Coast.

ALGERIA Name: Ramiz Zerrouki Age: 25 Club: Feyenoord(Netherlands) Position: Defensive Midfielder Africa should be proud to have this man playing in the upcoming AFCON tournament as he is the epitome of athleticism and command on the pitch. Based in the Netherlands, Zerrouki will stop at nothing to get the ball back on his feet and once he has the ball he is at peace again and can run the Algerian midfield operations with ease. He will look to make the Algerian midfield gel and spearhead The Desert Foxes into the knockout rounds after a disappointing run in the 2021 edition of the tournament.

ANGOLA Name: Gelson Dala Age: 27 Club: Al Wakrah(Qatar) Position: Center Forward This man ended qualifiers as Angola’s top scorer and is an electrifying center forward. He hustles for the ball every time one of his wingers has the ball on their feet or alternatively when the ball is in the box he will make use of it no matter what. He is Angola’s main man and should be on every manager’s list of the most dangerous players in the tournament.

BURKINA FASO Name: Stephane Aziz Ki Age: 27 Club: Young Africans(Tanzania) Position: Attacking Midfielder The Stallions are a nation capable of causing havoc in Ivory Coast with the snap of a finger, they have an impressive defensive foundation and contain plenty of attacking threats. A diamond within this attack is none other than Young Africans midfielder; Aziz Ki. He is strong on the ball, influential on the pitch and when given time and space to unleash a shot,he will make the opposing team pay. He hopes to get some playing time while at Ivory Coast and light up the tournament for his country.

MAURITANIA ** Name: Khadim Diaw Age: 25 Club: Horoya(Guinea) Position:** Left Back Khadim Diaw is more than your typical left back that is able to do it all on defense, he is a joy for attackers to use for the link up play. He has an excellent passing ability that can pick out any of the Mauritanian strikers in the box. He is certainly bound to be on coach Amir Abdou’s starting eleven.

MALI Name: Kamory Doumbia Age: 20 Club: Stade Brestois 29(France Position: Attacking Midfielder Fresh off scoring four goals(yes you read that right) four goals against FC Lorient in France, it looks impossible for young starlet Kamory Doumbia to not feature in the tournament. He is pacey, attentive and has an eye for goal which only adds to Mali’s firepower. Many should watch out for this Mali squad as they might go all the way due to their attacking firepower.

NAMIBIA Name: Peter Shalulile Age: 30 Club: Mamelodi Sundowns(South Africa) Position: Centre Forward One of Africa’s most dangerous strikers in recent years is Namibia’s very own.Shalulile stands at only five-foot-seven but he can leave a defense in shambles in little to no time as he is best friends with the net. He carries a variety of methods to make the net rifle and has done so a staggering 110 times in the Premier Soccer League in South Africa. Watch out for this man Africa.

SOUTH AFRICA Name: Teboho Mokoena Age: 26 Club: Mamelodi Sundowns(South Africa) Position: Center Midfielder A long-range specialist and a maestro in the midfield, Teboho Mokoena can impact the state of a game at any point he decides to do so. He has the game at the palm of his hands at all times and dictates it with his calm demeanour. In the dying seconds of the match, every opponent should make sure the ball doesn’t find him because if it does, it will probably be in the back of the net within the blink of an eye.

TUNISIA Name: Elias Achouri Age: 24 Club: FC Kobenhavn(Denmark) Position: Winger A confident winger who is capable of taking two to three defenders with him and will still come out of that situation with the ball still on his feet. Taking into account that he is 24, it appears to be the perfect time for Achouri to make a name for himself and the Eagles of Carthage in the Ivory Coast.

DR CONGO Name: Fiston Kalala Mayele Age: 29 Club: Pyramids FC(Egypt) Position: Center Forward The DR Congo attack line is heavily loaded with players hungry to make a name for themselves. One of them is Fiston Mayele who is based in Egypt. He spells trouble for defenders as he charges at them with nothing else in his mind but hitting the back of the net, he tends to catch others out with his ability to head the ball in a way that troubles the keeper greatly. If he manages to link correctly with the other strikers that Les Leopards have in their squad, then they will certainly be a team to watch in the tournament.

MOROCCO Name: Ismael Saibari Age: 22 Club: PSV Eindhoven(Netherlands) Position: Central Midfielder Part of the undefeated PSV squad that is yet to drop a point, Ismael Saibari has made his name known on the squad. His flair carries him through as a standout amongst the crowd. In this Moroccan team that is looking to build off their historic World Cup run, head coach Walid Regragui’s decision to grant this young prospect some time in the tournament is simply genius.

ZAMBIA Name: Clatous Chama Age: 32 Club: Simba Sports Club(Tanzania) Position: Central Midfielder The Chipolopolo look to run back their miracle of 2012 in this edition of the competition and will mostly play through their midfield. One of their key midfielders is Clatous Chama who is nicknamed “Mwamba wa Lusaka” which is Swahili for Rock of Lusaka. He is a machine in the frontline for his club and carries a great work ethic towards creating goals every time he plays. Beyond his goal scoring ability, Chama is very technically gifted and makes every situation count when he has the ball. Zambia are blessed to have him on their side.

TANZANIA Name: Tarryn Allarakhia Age: 26 Club: Wealdstone(England) Position: Central Midfielder The Taifa Stars look to shock the African continent in their AFCON 2023 campaign after disappointing campaigns in 1980 and 2019. Tanzania aims to use their hidden gem of a midfielder to the best of his ability to work on progressing the ball up the pitch. Though the Tanzanian stands at five-foot-seven, he is capable of keeping his balance every time he makes a darting run and more importantly,he is able to progress the ball up the field and win fouls in promising positions.In addition, he has sensational flair in his arsenal plus a great shot power and accuracy to his name. Keep your eyes out for this gem Africa!
-
 @ cb8f3c8e:c10ec329
2024-01-10 21:35:26
@ cb8f3c8e:c10ec329
2024-01-10 21:35:26WRITTEN BY: ALEX MREMA @npub1w4zrulscqraej2570gkazt0e7j0q3xq4437hnxjqfvcs59hq86fs9vnn4x
The whole of Africa anxiously waits for the continent’s headline tournament to kick off at the Olympic Stadium Ebimpé. This edition of AFCON features teams with talent, flair and a bottled-up hunger ready to fight for their nation to the very end. Like my most recent article that served as “part one” of the must watch games from groups A through C, this essay will look through groups D through F and what juicy encounters these groups have in store for Africa!
GROUP D
GAME: ALGERIA VS ANGOLA DATE: 15th January 2024 TIME: 20:00 BST Group D kicks off with an exciting encounter in which both sides are not entirely familiar with each other. With that, Les Fennecs are looking to put in a firm statement to show the whole of Africa that they are not the same lacklustre team that showed up to Cameroon in 2021.While Angola are looking to make it known that they are not a pushover in this tournament.
GAME: ALGERIA VS BURKINA FASO DATE: 20th January 2024 TIME: 14:00 BST The standout game of this group is one that can go both ways. Burkina Faso have a squad that is capable of going all the way to the finals, they’ve sent out the message several times in previous editions of the tournament that they are not underdogs and nothing close to that, rather they are confident and fearless squad ready to snatch a win from you with ease. Algeria on the other hand are looking to stop Les Étalons attacking threat from harming them while they also do what they do best- attack, attack, attack. Exciting encounter!
GROUP E
GAME: MALI VS SOUTH AFRICA DATE: 16th January 2024 TIME: 20:00 BST Mali have one of the most underrated squads coming to the Ivory Coast. They have a strong attacking unit and a solid midfield led by Tottenham Hotspurs star; Yves Bissouma, they are going to give the South African defence some trouble in this encounter. However, Bafana Bafana are also able to be a nuisance to the Mali defence as their no-joke attacking unit is designed to catch defences lacking especially with Percy Tau on the pitch.
GAME: TUNISIA VS MALI DATE: 20th January 2024 TIME: 20:00 BST A mouth-watering encounter that has some history after a blunder from the Zambian referee in their last AFCON encounter in Cameroon saw Janny Sikazwe blow the whistle for full time in the 86th minute! Nevermind that, Mali managed to collect the win and top their group. Tunisia are looking to set the record straight against the Malians in their quest to match their successes of AFCON 2004, which they won on home soil. If the Tunisians are looking to go all the way then this game is a must win for them to prove that they can take on the continent’ big dogs.
GAME: SOUTH AFRICA VS TUNISIA DATE: 24th January 2024 TIME: 17:00 BST Considering that this is the last game of the group stage, the Tunisians are bound to attack as much as they can against the Bafana Bafana defence that can be leaky at times. Though it must be said Tunisia’s attacking unit is an ageing one but has some sprinkles of youth here and there with the likes of Elias Achouri and Sayfallah Ltaief. With this, if South Africa do manage to stop the Tunisian attack, they are more than likely able to steal the game from them. And so this makes the clash a pretty unpredictable game on who’s going to take the three points .
GROUP F
GAME: D.R.C VS ZAMBIA DATE: 17th January 2024 TIME: 20:00 BST Zambia look to repeat their miracle of 2012 and go all the way. The Chipolopolo have a midfield unit that is able to keep the ball safely and also have an attacking unit that can score goals from nowhere, having put 3 past the Ivory Coast during qualifiers, this team is heavily underrated.Their first hurdle is none other than the Democratic Republic of Congo that carries a heavy loaded attacking unit ready to make defences regret for even trying to cope against them, Les Léopards are definitely a team to watch throughout the tournament because of their confident and exciting attacking element in their gameplay.
GAME: ZAMBIA VS TANZANIA DATE: 21st January 2024 TIME: 17:00 BST There is nothing better than a clash between two neighbours in the group stage. Stade de San Pedro is bound to cook up something sensational. The Taifa Stars squad frustrated opponents in the qualifiers with their concentrated defence plus having an attacking unit that would score and immediately join the defence in squeezing in narrow victories which eventually made them one of Africa’s 24 competing nations in the tournament. I mean, they only scored three goals during the qualifiers but are somehow in the tournament…Remarkable! But, Zambia’s attacking force during qualifiers was on fire raking 12 goals in their favour and having Leicester City star Patson Daka to lead the line, he already has 4 goals and 2 assists in 7 appearances all season and will look to carry this form to the Ivory Coast. This is a classic game of attack versus defence, keep your eye out for this game Africa!
GAME: MOROCCO VS D.R.C DATE: 21st January 2024 TIME: 14:00 BST The game of the group promises back and forth attacking football throughout. The history-making Morocco are tipped as one of the top sides to win the tournament come February 11th all due to being a well oiled machine with power in all sectors on the pitch and even on the bench! Star attackers like En-Nesyri, Ezzalzouli and Boufal aim to show the Congolese who is boss when they clash. However, Les Léopards are an established side and are not a side to mess with as their attacking options are there to make Hakimi and the rest of the Moroccan backline feel their wrath.
-
 @ 154ee9a3:14840b27
2024-01-10 17:46:26
@ 154ee9a3:14840b27
2024-01-10 17:46:26Hello NOSTR Community!
We are thrilled to introduce ourselves – The Learning Orchard, based in the vibrant city of Arusha, Tanzania. Our mission is clear: to become a center of excellence in supporting children with learning differences and to be a leading advocate for specialized education in Tanzania.
Our Journey Begins: The GEYSER Page Launch and NOSTR
Exciting news! We've officially launched our GEYSER page and NOSTR, and we're thrilled to be part of the dynamic Bitcoin and NOSTR space. This marks the beginning of a journey where we aim to make a meaningful impact in the lives of children in Tanzania with unique learning needs.
A Glimpse into Our Vision
At The Learning Orchard, we envision a future where every child, regardless of their learning differences, receives the support they need to thrive. Our commitment to excellence and advocacy drives us to create a positive change in the landscape of education in Tanzania.
Stay Tuned for More Updates!
We can't wait to share more about our initiatives, progress, and the incredible stories that unfold on this journey. Your support means the world to us, and we're grateful to be a part of the NOSTR community.
Thank you for joining us on this exciting adventure!
Warm regards,
The Learning Orchard Team
-
 @ d6dc9554:d0593a0c
2023-09-21 18:37:14
@ d6dc9554:d0593a0c
2023-09-21 18:37:14Nas blockchains PoW o consenso é alcançado por meio de prova de trabalho computacional e o objetivo principal é evitar que atores mal intencionados consumam ou ataquem a rede de forma perigosa. Este método de consenso requer um grande poder computacional para criar novos blocos, mas é muito simples, por parte de outros, verificar esse trabalho. Por isso se diz que PoW é uma estratégia assimétrica.
Nas blockchains PoS o objetivo é o mesmo, criar blocos e chegar a um consenso, mas nas PoS não é necessário um poder de processamento tão grande como nas PoW. Em média as PoS gastam menos de 1% da energia das PoW. Nas PoS os mineradores são chamados de validadores. Enquanto que nas PoW quem fica com a recompensa é quem resolve primeiro a charada matemática, nas PoS o validador que vai ganhar a recompensa é escolhido de forma aleatória, mas dando maior probabilidade aos que respeitem determinados critérios. A comunidade bitcoin é muito relutante em relação a PoS porque é mais fácil conseguir uma grande quantidade da moeda em causa do que mais que 51% de poder processamento. Logo as PoS são mais vulneráveis no que toca a segurança. Mas aqui cada caso é um caso e é preciso fazer essa análise para cada moeda.
As blockchains PoW tendem a ser mais descentralizadas enquanto as PoS mais centralizadas, não só em acesso, mas também em operação. Mais de metade dos validadores de ethereum estão na cloud da amazon. As blockchains PoW apresentam grandes desafios na escalabilidade de operação, muitas vezes exigindo soluções de segunda camada (L2), enquanto que as PoS possuem mecanismos de escalabilidade muito mais flexíveis. Os algoritmos PoW são muito mais simples de implementar do que os PoS e, portanto, menos suscetíveis a erros. Um bom exemplo é o PoS da ethereum que estava a ser implementado desde 2018.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ cb8f3c8e:c10ec329
2024-01-07 00:18:20
@ cb8f3c8e:c10ec329
2024-01-07 00:18:20WRITTEN BY: ALEX MREMA NOSTR @npub1w4zrulscqraej2570gkazt0e7j0q3xq4437hnxjqfvcs59hq86fs9vnn4x

AFCON 2023 kicks off in a couple days with 24 of Africa’s best taking each other on for the coveted prize. The journey will be long for some while others will have to cancel some of their hotel reservations in the Ivory Coast as their journey will end earlier than expected. Looking at the participating nations, we are assured of great games throughout the competition and even looking at the group stage itself, they’re games that are simply a must-watch. This article will deep dive into the games in the first three groups that promise to provide entertainment.
GROUP A

GAME: NIGERIA VS EQUATORIAL GUINEA DATE: 14th January 2024 TIME: 14:00 BST Equatorial Guinea are a side that carries no fear within their hearts and are always ready for a challenge. They are not newcomers at punishing a team for poor play and will look to catch the loaded Super Eagles squad lacking in order to pull off an early tournament surprise.

GAME: IVORY COAST VS NIGERIA DATE: 18th January 2024 TIME: 17:00 BST A clash of the heavyweights comes early on in the tournament with the Super Eagles taking on Les Éléphants at the Olympic Stadium of Ebimpé. The hosts have to be in tip top shape to not disappoint their home fans against their West African rivals. Nigeria on the other hand are expected to go all the way in the tournament and will use this as a test for what to expect in the knockout rounds should they progress.

GAME: EQUATORIAL GUINEA VS IVORY COAST DATE: 22nd January 2024 TIME: 17:00 BST The last round of group games doesn’t get more important than this. Depending on the situation in the group, this could be a win or go home situation for both nations involved. Expect hard, back-and-forth, old school fearless African football as each country will aim to send a message to the rest of the continent that their football is one not to mess with!
GROUP B

GAME: GHANA VS CAPE VERDE DATE: 14th January 2024 TIME: 20:00 BST This will be Ghana’s first AFCON game since their shambolic campaign in Cameroon. They will look to express themselves as a new and reformed nation with a fresh style capable of taking them deep into the tournament. Cape Verde on the other hand are not going to make it easy for the Ghanaians as they are capable of creating a mountain load of chances to trouble the Ghanaian defence and keeper.

GAME: EGYPT VS GHANA DATE: 18th January 2024 TIME: 20:00 BST The Pharaohs are a red hot squad who are capable of taking on any of the other 23 nations involved in the competition and Ghana is no exception to this. Egypt’s defensive excellence will be a task that is capable of frustrating the Ghanaians but will be able to provide a great game of high tactical brilliance. Tune in to this one!

GROUP C

GAME: SENEGAL VS GAMBIA DATE: 15th January 2024 TIME: 14:00 BST The Group of Death consists of nations that are capable of providing games that will leave us on the edge of our seats by the final whistle and this clash of West African neighbours is no exception. The Gambians were one of the surprise packages of the 2021 edition of the last tournament making it all the way to the quarter-finals. However, this is one huge hurdle The Scorpions have to overcome in their first game as they take on the defending champions in their first game. Senegal will be looking to make it to their third final in as many tournaments. This match is simply a must watch!

GAME: CAMEROON VS GUINEA DATE: 15th January 2024 TIME: 17:00 BST Cameroon look to get to the finals after falling short on home soil in the last edition,which they hosted. They start off their campaign against a Guinea side that plays with purpose and pride. Guinea don’t hold anything back when they step on the AFCON stage- no matter the circumstances against them they will show up and show out against any opponent. This confidence coupled with Cameroon’s determination to take the trophy home makes the perfect potion for a juicy first round encounter in Group C.

GAME: SENEGAL VS CAMEROON DATE: 19th January 2024 TIME: 17:00 BST The clash of the lions is undoubtedly the game of the group stage. The Lions of Teranga take on The Indomitable Lions looking to take revenge for their heartbreaking semi-final exit from the last edition via penalty shootouts that left the whole nation in tears. This game will have the Cameroonians carrying extra motivation in their hearts to take down the Senegalese with their blistering attack led by their skipper, the goal scoring machine: Vincent Aboubakar.

GAME: GUINEA VS GAMBIA DATE: 19th January 2024 TIME: 20:00 BST
This will likely be a must-win game for both of the nations in order to secure comfortability in matchday 3 which is essential for a group of this magnitude. Both nations have a desire for scoring goals and attacking fearlessly, almost making it a given that this game will be a back and forth encounter that will see each country put their blood, sweat and tears for the three points.

GAME: GAMBIA VS CAMEROON DATE: 23rd January 2024 TIME: 17:00 This clash can possibly determine both nations' fate in the tournament. The Scorpions of Gambia carry an attacking sting that can leave the Cameroonian defence in conflict once they get going, they really can take on Cameroon and even leave with all three points here. But, this is Cameroon we are talking about, they will be determined to give their all to assure fans that they are not going to slip up even once in their quest to the trophy.

GAME: GUINEA VS SENEGAL DATE: 23rd January 2024 TIME: 17:00 BST Like the Gambia v Cameroon encounter, this game will be the determining factor for both these nations in their chase for the trophy. Senegal’s chase to retain the trophy has to go through the resilient Guineans. This sets up for a mouth-watering tie that will make both camps play with their hearts on their sleeves.
-
 @ cb8f3c8e:c10ec329
2024-01-05 18:33:59
@ cb8f3c8e:c10ec329
2024-01-05 18:33:59SPORTSTR IS HERE...
Since my earliest days, sports has been my lifeblood. At just six years old, my mother introduced me to the world of swimming—a decision that set the course for an incredible journey. By the age of eleven, I proudly held the title of a national champion in the UK. That achievement ignited a fire within me—a passion for sports that has burned ever brighter as the years passed.
Throughout my career in sports, I've been blessed with experiences that have shaped me profoundly. But now, my focus is turning towards nurturing the talents of the next generation.
As my journey in Bitcoin continues to evolve, I've eagerly awaited the perfect opportunity to unite it with my love for Africa, sports and the next generation. That moment has arrived.
I see an incredible prospect—an opportunity to empower grassroots, amateur, and professional athletes from around the world, particularly those hailing from East Africa. With the fusion of #NOSTR and #Bitcoin, I envision SPORTSTR as a place where these remarkable talents can showcase their abilities and connect with a global audience.
One individual who embodies this passion for sports and the transformative power of Bitcoin is my nephew, Alex Mrema (⚡️alexmrema@blink.sv). He's not just a talented athlete; he's a writer whose passion for sports knows no bounds. He's witnessed my journey through the world of sports and seen how Bitcoin has seamlessly woven its way into my life. We have partnered to launch SPORTSTR as a place for him and I to create content about sport on NOSTR and receive value in the form of Bitcoin.
Today marks the launch of SPORTSTR—an initiative aimed at sharing compelling articles by young writers, sporting news, and exclusive interviews with athletes. Our ultimate goal? To introduce them and our audience to the world of Bitcoin and NOSTR, seamlessly integrating these innovative technologies into the realm of sports.
This, however, is just the beginning—a starting point for something truly orange, purple and remarkable.
MAN LIKE WHO?
MAN LIKE KWEKS!
🇹🇿⚡️💜🏔
sportstr #sports #bitcoin #nostr
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 0e9491aa:ef2adadf
2023-08-23 13:35:04
@ 0e9491aa:ef2adadf
2023-08-23 13:35:04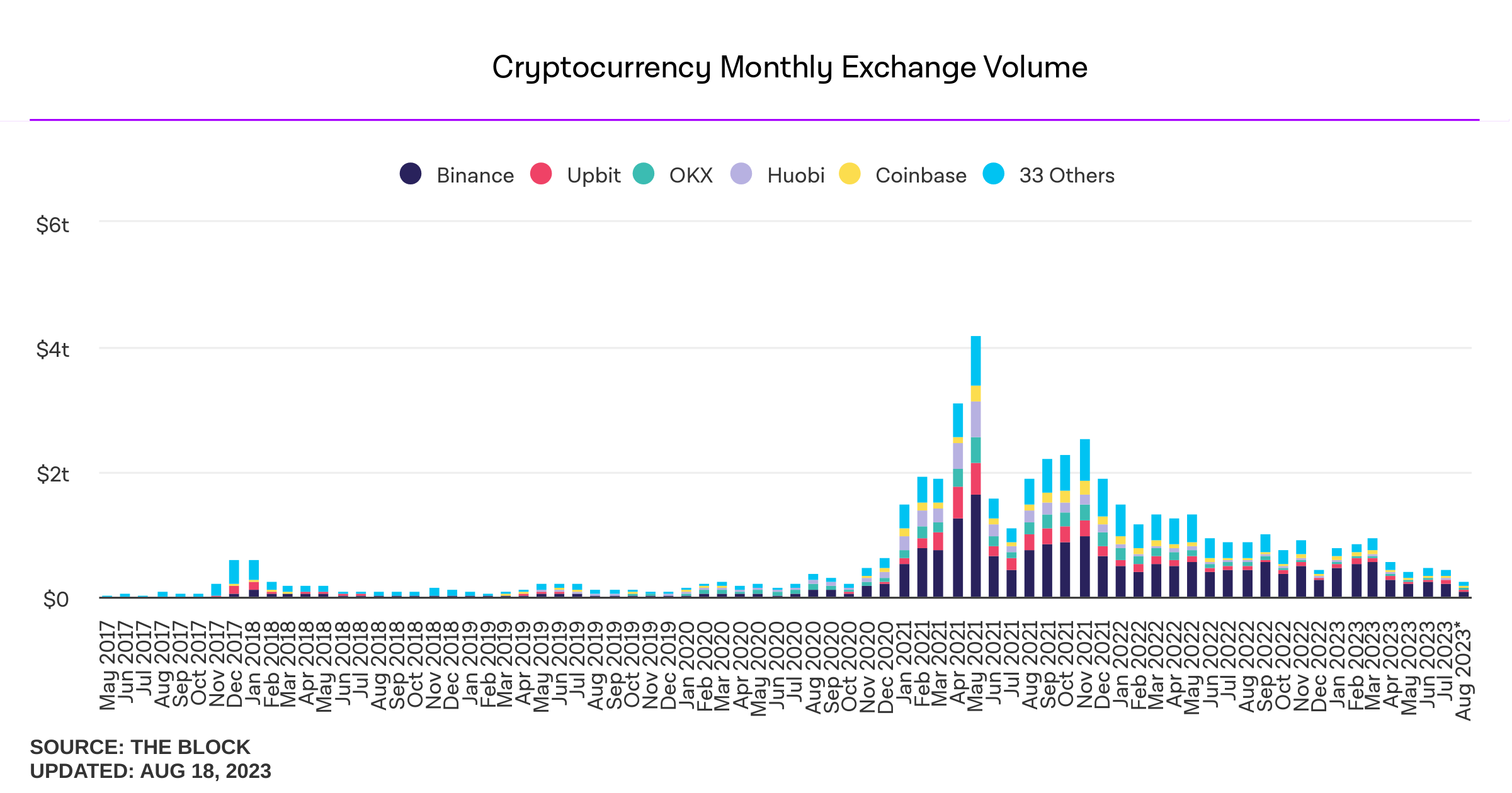
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
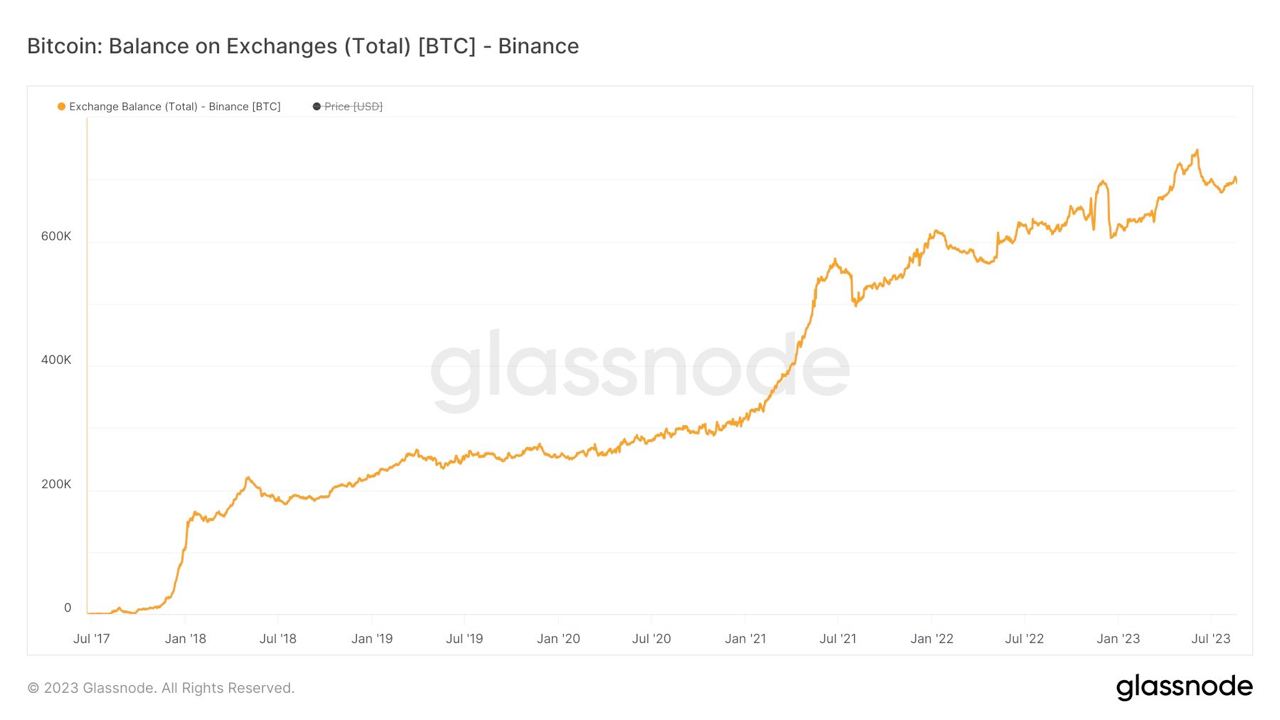
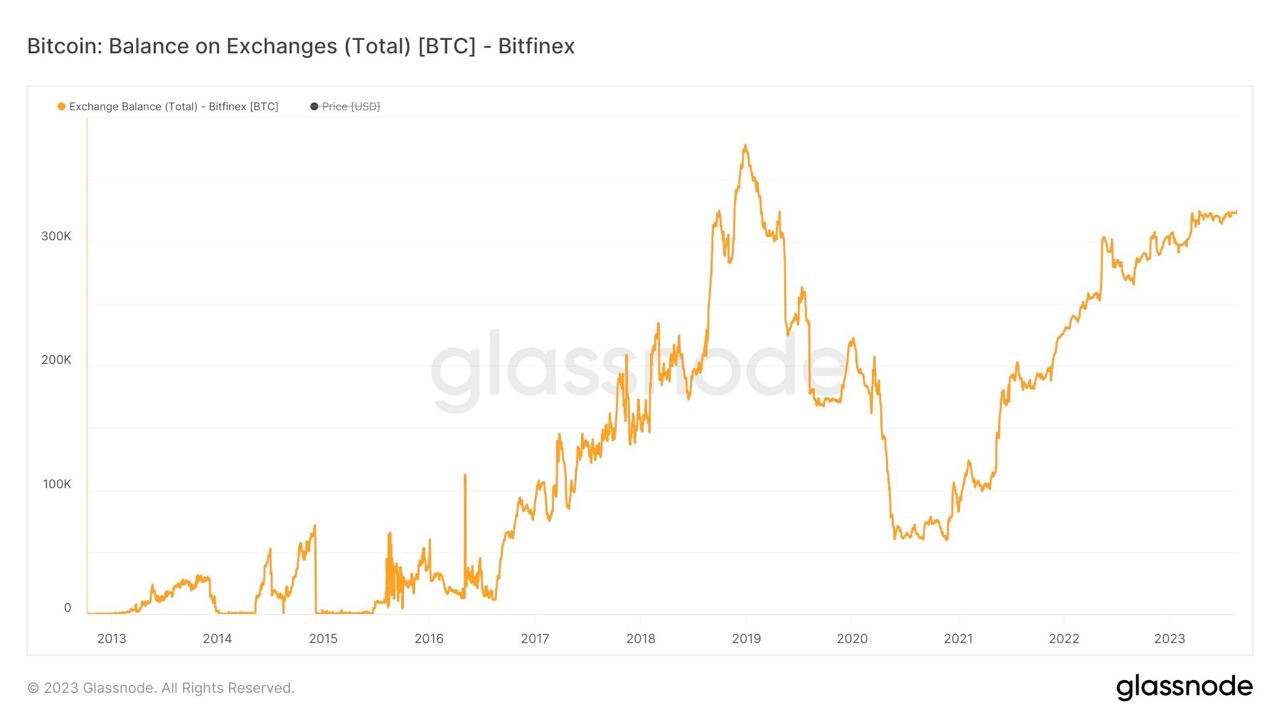
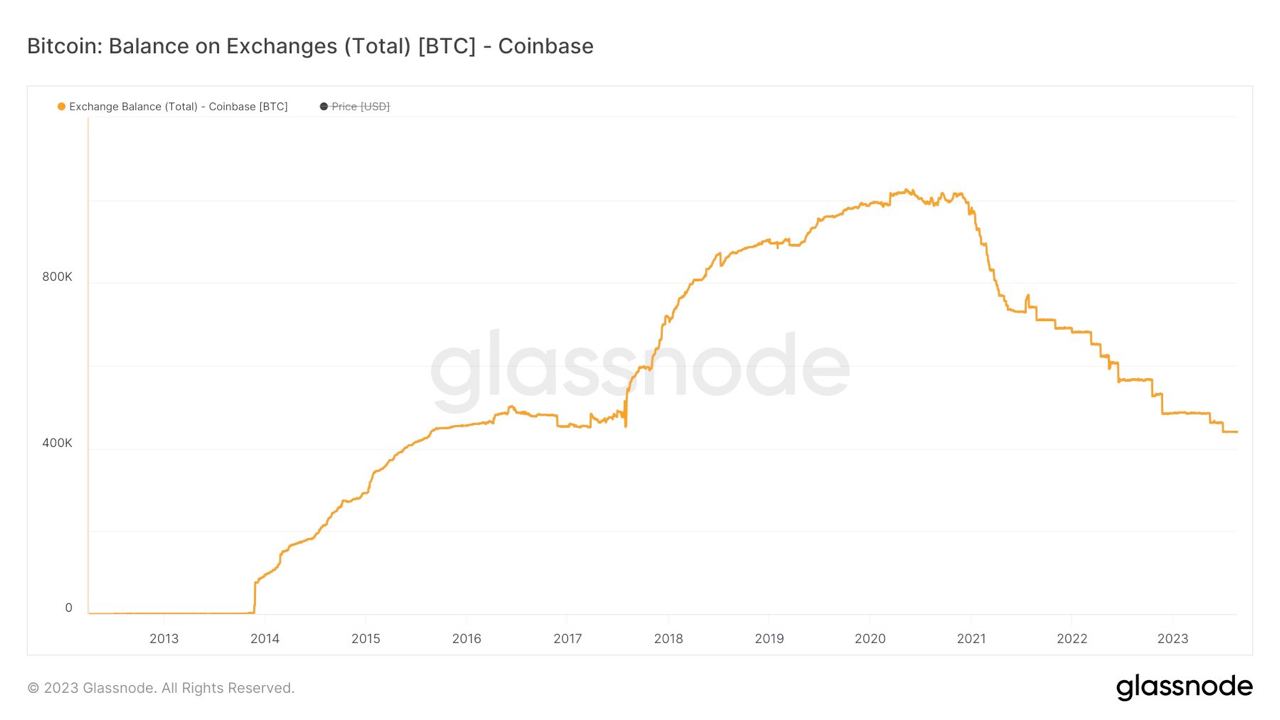
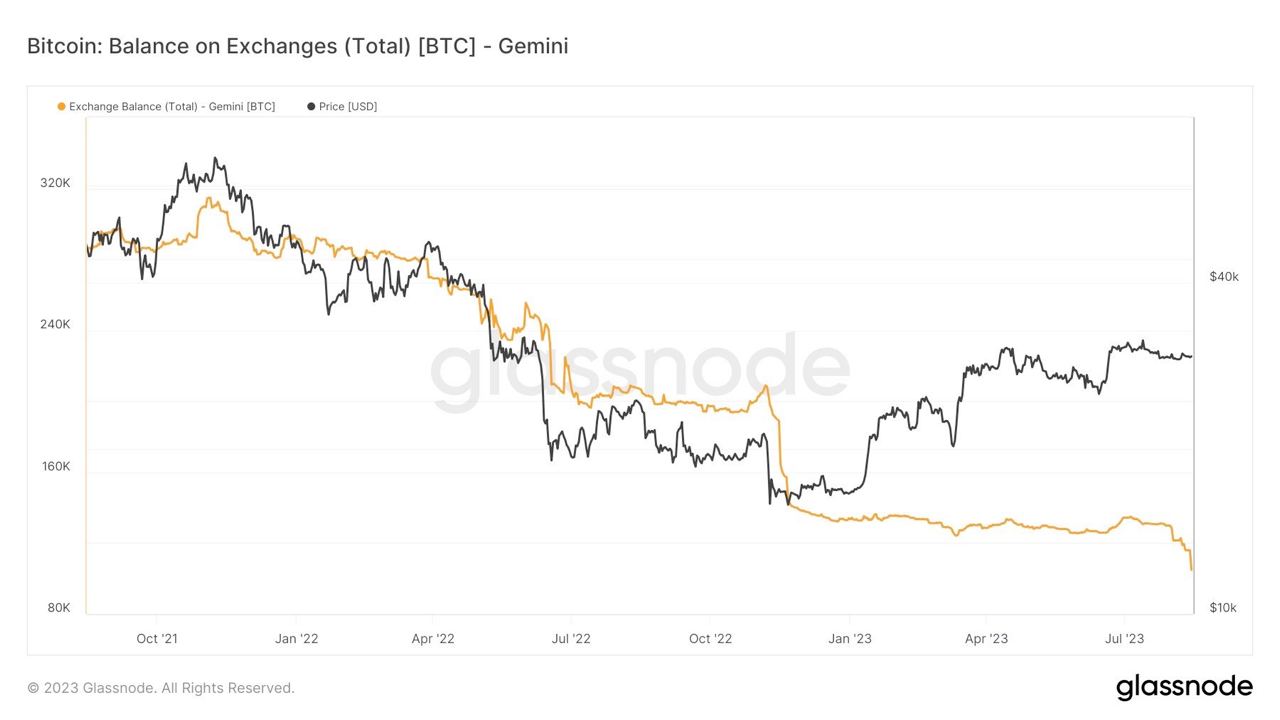
If you found this post helpful support my work with bitcoin.

-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ c23b8728:55b2d0fb
2024-06-01 17:14:24
@ c23b8728:55b2d0fb
2024-06-01 17:14:24โจทย์คือเราจะจัดการเงินบนหน้าตักของเรายังไง ให้สามารถใช้จ่ายได้ลื่นไหลและยังมีเงินเหลือออมได้ทุกเดือนโดยที่ไม่ตึงเครียดเกินไป
เริ่มแรกผมจะทำงบประมาณรายจ่ายของตัวเองออกมาก่อนว่าใช้ไปกับอะไรบ้างในแต่ละเดือน โดยจะอิงกับรายได้ของเรา เช่นตามรูปตัวอย่าง สมมติว่ารายได้รวมผม 35,000 บาท ผมก็จะกระจายไปแต่ละบัญชีให้ครบ 35,000 บาทครับ ซึ่งผมจะแบ่งเป็น 3 บัญชี 1. บัญชีออม (ช่องสีเขียว) รวม 10,000 บาท 2. บัญชีสำรองจ่าย (ช่องสีส้ม) รวม 14,000 บาท 3. บัญชีใช้จ่ายส่วนตัว (ช่องสีเหลือง) รวม 11,000 บาท

บัญชี 1 : เก็บออม
เป็นเงินที่จะแบ่งมาเก็บออมสำรองฉุกเฉินซึ่งสำคัญมาก ทุกคนจำเป็นต้องมีบัญชีนี้ ควบคู่ไปกับการลงทุนอื่นๆตามชอบ จากในรูปตัวอย่าง ผมจะเอาบัญชีนี้ไว้บนสุดของตารางเลยเพื่อย้ำเตือนว่าให้ “เก็บก่อนใช้” เสมอ ซึ่งตัวเลขของการออมนี้จะมาจากการประเมินแล้วว่า เราใช้จ่ายกับส่วนอื่นเพียงพอแล้วจึงสามารถมีเก็บส่วนนี้ได้
เป้าหมายของการออมเงินสำรองฉุกเฉินคือ ไว้ใช้จ่ายเมื่อมีเหตุการณ์ที่ไม่คาดคิด เช่น อุบัติเหตุ, ตกงาน, สูญเสียรายได้ โดยเราจะต้องประเมินความเสี่ยงตัวเองคร่าวๆให้ได้ว่า เมื่อเกิดเหตุร้ายแรงขึ้นมา จะต้องใช้เงินเท่าไหร่ ซึ่งโดยส่วนใหญ่ก็จะให้เป็นตัวเลขง่ายๆคือ 3-6 เดือนของรายจ่ายต่อเดือน ถ้าจากตัวอย่างในรูป เราจะมีรายจ่ายต่อเดือน(ช่องสีส้มและสีเหลือง)อยู่ที่ 14,000+11,000 = 25,000 บาท แปลว่าเราต้องมีเงินสำรองฉุกเฉินอย่างน้อย 75,000-150,000 บาท เพื่อเป็นหลักประกันว่า ชีวิตเราจะยังเดินต่อไปได้ไม่สะดุด หากตกงานก็มีเวลาให้หางานหาแหล่งรายได้ใหม่อีก 3-6 เดือน มันเป็นเวลาที่น่าจะเพียงพอให้คิด วางแผนทำอะไรได้ บัญชีนี้จะต้องนำไปเก็บในที่ที่สามารถถอนออกมาใช้ได้ทันทีหรือไม่เกิน 1-2 วัน เพราะ ชื่อมันก็บอกอยู่ว่า สำรองฉุกเฉิน ต้องถอนมาใช้ได้ทันที
เทคนิคส่วนตัวที่ผมใช้กับบัญชีนี้คือ ผมจะแบ่งมันเป็นชั้นเหมือนเก็บเงินในโอ่ง โดยชั้นบนจะเก็บเป็นเงินสดในบัญชีเงินฝากที่ให้ดอกเบี้ยสูง พร้อมถอนทันที เงินต้นไม่หาย เวลามีเหตุฉุกเฉินก็ดึงเงินชั้นนี้มาใช้ก่อน ส่วนตัวผมตั้งเป้าหมายเก็บไว้สัก 6 เดือน หากมีเหตุให้ต้องใช้เงินที่เกินจากชั้นนี้ก็ค่อยไปดึงจากชั้นล่าง ซึ่งชั้นล่างจะเก็บเป็นทองคำ โดยที่ผมเริ่มจากการเก็บออมทองกับร้านทอง ซึ่งสามารถทำผ่านแอปได้เลย ลองหาข้อมูลดูครับ มีหลายเจ้าให้บริการนี้อยู่ เริ่มต้นออมได้ตั้งแต่ 1,000 บาท เมื่อสะสมครบตามน้ำหนักขั้นต่ำก็สามารถถอนออกมาเป็นทองคำแท่งได้ หรือจะสั่งขายทองออกมาเป็นเงินโอนเข้าบัญชีก็ได้ บัญชีนี้ผมไม่มีเป้าหมายชัดเจนครับ กะว่าเก็บไว้เรื่อยๆ แต่ถ้าหากมีการลงทุนอะไรที่สนใจก็อาจจะดึงส่วนนี้ไปลงครับ เช่น ปัจจุบันผมสนใจบิตคอยน์ ก็จะแบ่งเงินจากส่วนนี้ไปลงครับ การเก็บเงินออมเป็นทองคำ มีข้อดีคือ ทองคำสามารถรักษามูลค่าได้ในระยะยาว มีสภาพคล่องไม่สูงเท่าเงินฝากในบัญชีแต่สูงเพียงพอที่จะแปลงเป็นเงินมาใช้จ่ายได้ไม่เกิน 1-2 วัน และ การขายทองไม่เสียภาษีครับ
บัญชี 2 : สำรองจ่าย
บัญชีนี้เป็นเงินที่ตั้งให้โอนมาอัตโนมัติไว้เลยทุกต้นเดือน เพื่อไว้สำรองจ่ายค่าใช้จ่ายคงที่แต่ละเดือน เช่น สาธารณูปโภค, ผ่อน/เช่า, ครอบครัว จุดประสงค์ที่ต้องกันมาไว้ต่างหากแยกกับบัญชีใช้จ่ายส่วนตัวคือ เพื่อให้เราไม่ต้องมาคอยกังวลว่าแต่ละเดือนจะมีเงินพอสำหรับค่าใช้จ่ายเหล่านี้รึเปล่า มันทำให้เราใช้จ่ายส่วนตัวได้สบายใจมากขึ้นครับ ในกรณีที่เรามีค่าใช้จ่ายรายปีด้วย เช่น ประกัน, ภาษี ก็สามารถนำมารวมอยู่กับบัญชีนี้ด้วยก็ได้ หรือจะแยกบัญชีไปเลยเพื่อให้ไม่งง และค่อยๆสะสมเป็นยอดเล็กๆแต่ละเดือนเข้าไปในบัญชีให้ครบตามจำนวน เช่น มีค่าประกันรายปี 12,000 บาท ก็ทยอยแบ่งเก็บไปเดือนละ 1,000 บาทหรือมากกว่านั้น ถ้ากลัวว่าจะมีไม่พอจ่ายในงวดถัดไป ในช่วงแรกที่เพิ่งเริ่มเก็บอาจจะมีเงินสำรองไม่พอสำหรับค่าใช้จ่ายรายปี ก็ให้ดึงจากบัญชีสำรองฉุกเฉินมาจ่ายไปก่อนครับ เมื่อทำตามระบบนี้ไปเรื่อยๆ เราจะมีเงินเพียงพอสำหรับทุกค่าใช้จ่ายเองครับ อาจใช้เวลาเป็นปีหรือหลายปี แค่ต้องอดทนหน่อย ผมเองก็ยังทำไม่ได้ตามระบบที่ผมวางไว้เป๊ะๆ เพราะระหว่างทางมันจะมีเรื่องที่ไม่คาดคิดเกิดขึ้นเสมอ ทำให้เงินเก็บลดลงและเป้าหมายที่วางไว้ยืดออกไปอีกครับ สำคัญที่สุดคือ อย่าหยุดเก็บเงินครับ
บัญชี 3 : ใช้จ่ายส่วนตัว
บัญชีนี้ผมก็จะตั้งให้โอนเข้ามาอัตโนมัติทุกต้นเดือนเช่นกัน โดยกำหนดจำนวนเงินเป็นรายจ่ายส่วนตัวซึ่งแบ่งเป็น 3 หมวดใหญ่ๆคือ กิน(อาหารมื้อหลักและมื้อพิเศษ), ใช้(เดินทาง/ของใช้ส่วนตัว), ช็อปปิ้ง(ของที่อยากได้) กำหนดเป็นตัวเลขที่เราคิดว่าไม่ตึงและไม่หย่อนเกินไป ถ้าตามตัวอย่างก็คือ 11,000 บาทต่อเดือน โดยหลักคิดของการใช้งานบัญชีนี้คือ ไม่ว่าเราจะมีรายได้มากแค่ไหน เราจะจำกัดตัวเองให้ใช้จ่ายส่วนตัวในแบบที่ประเมินแล้วว่ากำลังพอดี อยู่ที่ 11,000 บาทต่อเดือน โดยที่ในระหว่างเดือนเราจะคอยเช็คว่าได้ใช้เงินไปเท่าไหร่แล้วและเหลือเงินให้ใช้อีกเท่าไหร่ ซึ่งอาจจะแบ่งจุด checkpoint เป็นรายสัปดาห์หรือครึ่งเดือนก็ได้ เช่น ถ้าแบ่งเป็นครึ่งเดือนหรือง่ายๆก็วันหวยออกมาเช็คเงินในบัญชี ถ้ามีเงินเหลือเกินครึ่งหรือ 5,500 บาท แสดงว่าครึ่งเดือนที่ผ่านมาเราใช้จ่ายอยู่ในงบ ไม่ใช้เงินเกินตัว และเมื่อถึงวันสิ้นเดือนแล้ว ถ้ายังมีเงินเหลืออยู่ในบัญชีนี้ ให้คิดว่า มันคือรางวัลของการอดออมของเรา เป็นเหมือนโบนัสส่วนตัวของเราเอง เราจะใช้จ่ายอะไรกับมันก็ได้ จะแบ่งเก็บออมหรือจะสมทบไว้ใช้ในเดือนถัดไปก็ได้ เมื่อเราสามารถอดออมจนมีเงินเหลือได้ทุกเดือน มันจะทำให้เรารู้สึกเห็นคุณค่าของการเก็บออมมากขึ้น และเวลาจะซื้อของอะไรที่ไม่จำเป็นก็จะคิดมากขึ้นครับ แต่ในกรณีที่รู้สึกว่าใช้จ่ายพอดีแล้วเงินยังเหลืออยู่ทุกเดือนโดยที่ไม่ได้รู้สึกตึงมาก ก็ค่อยปรับลดจากงบประมาณในเดือนถัดไปและเอาเงินไปลงกับบัญชีออมแทนครับ
ไม่ว่าคุณจะเป็นมนุษย์เงินเดือนมีรายได้ประจำหรือมนุษย์ฟรีแลนซ์ พ่อค้าแม่ค้า ที่รายได้ไม่แน่นอน ก็สามารถประยุกต์ใช้วิธีบริหารสภาพคล่องแบบนี้ได้ โดยที่เมื่อเงินเข้ามาในบัญชีรายรับจะเป็นเงินเดือน,รายได้,ค่าจ้าง ให้แยกไว้ต่างหาก ไม่ต้องดึงออกมาใช้เอง และให้เปิดบัญชีใหม่อีก 3 บัญชีตามที่กล่าวมาคือ ออม, สำรองจ่าย, ใช้ส่วนตัว แล้วให้ตั้งโอนเงินออกจากบัญชีรายรับอัตโนมัติทุกต้นเดือน
ในช่วงแรกที่เริ่มทำตามระบบอาจจะ มีติดๆขัดๆหน่อย รายจ่ายบางหมวดหมู่มากกว่าที่ประเมินก็ค่อยๆปรับไปเดือนต่อเดือน สุดท้ายเราจะเจอจุดที่สมดุลเอง เมื่อเราจัดการรายจ่ายทุกอย่างเป็นที่เป็นทางแล้ว เราจะไม่ต้องไปปวดหัวกับมันอีก และเราจะสามารถสร้างวินัยการใช้จ่ายและเก็บออมได้ง่ายขึ้นครับ
-
 @ 0271e1b9:ad8cff90
2024-05-31 05:54:12
@ 0271e1b9:ad8cff90
2024-05-31 05:54:12Separating money from state is the single most effective way to stop all wars from happening, everywhere, and that is something we can all actively participate in, right now.
Yelling at a problem won’t make it go away.
Some lessons and notable quotes from history:
 Source: "Hyperinflation in the Weimar Republic" Britannica article
Source: "Hyperinflation in the Weimar Republic" Britannica article“It is no coincidence that the century of total war coincided with the century of central banking.”
― Ron Paul
“It is the ability of governments to acquire money without direct taxation that makes modern warfare possible, and a central bank has become the preferred method of accomplishing that.”
― G. Edward Griffin
“The government created the national banking system during the Civil War.”
― Michael D. Bordo ("A Brief History of Central Banks," published on the Federal Reserve Bank of Cleveland website, 2007)
“Why did nations start central banks? To finance the materiel needs of the nation-state in time of war.”
― Brian Domitrovic (“Central Banking's Connection To Warfare Is Intimate,” published on Forbes, 2018)
“War... is harmful, not only to the conquered but to the conqueror.”
― Ludwig von Mises
“War is a profitable venture for the banking elite, as it allows them to finance both sides and profit from increased debt.”
― G. Edward Griffin (“The Creature From Jekyll Island,” 1994)
“Again, coinage saw its greatest debasement during times of war and uncertainty.”
― “Roman currency” Wikipedia article
“Nobody should have money but I, so that I may bestow it upon the soldiers."
― Caracalla (the Roman Emperor from 198 to 217 A.D., who raised his soldiers' pay by 50%, doubled the inheritance tax, admitted almost every inhabitant of the empire to Roman citizenship (for tax collection purposes, of course) and subsequently resorted to debasing both the silver and gold coins). Sources: Jeff Desjardins (“Currency and the Collapse of the Roman Empire,” The Money Project), “Caracalla” Wikipedia article
“To defeat the aggressors is not enough to make peace durable. The main thing is to discard the ideology that generates war.”
― Ludwig von Mises
“It’s a great business to be in - central banking. We print money and people believe it.”
― Adrian Orr (Governor of the Reserve Bank of New Zealand, February 2024)
“Politics can affect things temporarily and locally, but technology is what drives things forward globally and permanently.” ― Lyn Alden (“Broken Money,” 2023)
 Source: New York Tribune, December 4, 1921
Source: New York Tribune, December 4, 1921“The essential evil of gold in its relation to war is the fact that it can be controlled. Break the control and you stop war."
― Henry Ford
Study the history of money. Study Bitcoin.
Also, don’t buy government bonds, t-bills, t-notes or any other type of government debt, no matter what your financial advisor or favorite macroeconomics guru is telling you. It’s just another way of feeding the same beast.
And what we need to do is starve the beast.
This is just one of the many reasons why “separation of money and state” is such a critical issue at this point in history.
Stay safe and stay sane, my friends. Don’t succumb to the hate. ☮️ & ❤️, Kontext
///
May 29, 2024, published at block height 845,667
Edited May 31, 2024: added the New York Tribune headline + Henry Ford quote
-
 @ 0861144c:e68a1caf
2024-05-30 13:22:39
@ 0861144c:e68a1caf
2024-05-30 13:22:39This is my lecture of the day and learned something. I made a draw in order to understand it better.
Recently I learned about the Finney Attack which was very interesting in theory but today it's a little hard to do it. So, let's say there's a guy (named Troll Finney) who has the best decentralized protocol, the internet of money named FinCoin (FIC), so let's go buy stuff with Troll who has bad intentions.
Finney Attack explained
So, in this example, we have: two shops, two transactions, two miners and one coin[^1]. Let's go shopping and make an attack to the network.
- Let's say you want to buy...a coffee. You get there and your payment method is FIC.
- But at the same time, you're selling a bag of tea to someone. This fren will pay you also in FIC.
- Here's come the tricky part. Previous to pay the coffee Mr. Troll made a copy of the same coin he received. So now he has one FIC and a copy of tha same coin.
- Troll send the coin to shop 1 and shop 2 at the same exact time.
- The first bitcoin to broadcast the transaction will be the winner. Since both shops have the same coin, one shop won't have nothing.
So, as a result, SHOP X or SHOP Y will win? Even if Troll told you he made the transaction, someone won't get the coin. Yes, the miner with lower hashrate will lose obviously but it's not that simple to perform since most exchanges (in case you want to trade) requires a 2 or 3 confirmations before make the deposit in their platforms.
[^1]: One coin to rule them all!
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 502ab02a:a2860397
2024-05-29 05:37:23
@ 502ab02a:a2860397
2024-05-29 05:37:23อาหารธรรมชาติ คือ สิ่งที่ทุกคนโหยหา แต่ในความเป็นจริงแล้ว ธรรมชาติของเราอาจไม่เท่ากัน ธรรมชาติสำหรับหลายๆคนคือ not chemฯ (ไม่เคมี) ธรรมชาติสำหรับอีกหลายๆคนคือ ธรรมชาติ อ่ะ ธรรมชาตตตตตตตตติ
ถ้าให้นึกภาพนะครับ เราจะคุ้นหูกับเพลงโฆษณาว่า “อายิโนโมะโต๊ะ ผลิตจากวัตถุดิบธรรมชาติ ตึ๊ง” เริ่มนึกออกใช่ไหมครับ คำที่ใช้ในงานโฆษณา
โฆษณาชวนเชื่อ ภาษาไทยมันก็ตรงๆแล้วครับ คำว่าว่า โฆษณา เป็นคำที่มาจากภาษาบาลีว่า โฆสณา (อ่านว่า โค-สะ-นา) แปลว่า ป่าวร้อง แจ้งให้ทราบ ดังนั้น โฆษณาชวนเชื่อ ก็คือ การป่าวร้อง ป่าวประกาศ ชวนให้เราเชื่อ นั่นเอง
ดังนั้นการรับสารจากโฆษณาชวนเชื่อ ยิ่งต้องใช้หลักกาลามสูตร ในการไตร่ตรอง เพราะฝั่งที่สื่อสารออกมา มีเป้าหมายที่จะให้เราเชื่อให้ได้ เพื่อที่จะไปซื้อสินค้าหรือบริการ มันเป็นเกมส์แห่งการรู้ทันกันครับ เราจึงได้เห็นสารพัดกลยุทธ์ในการชวนเชื่อ ไมว่าจะ แก้ painpoint, การทำเหมือนพวกเดียวกันเข้าอกเข้าใจกัน, การสื่อในด้านที่สวยงาม หรือแม้แต่ การขู่ให้กลัว ก็ยังมี เราจะเลือกเป็นสมันให้เขาเคี้ยวหรือจะเป็นเสือที่อยู่คนละฝูงแต่เขี้ยวเล็บพอๆกัน เลือกเองครับ
ส่วนธรรมชาติ ที่ผมหมายถึงนั่นคือ natural ครับ ดื้อๆดุ้นๆเลย จากผล จากต้น จากตัว ตัดมาทำอะไรก็ว่ากันไป เราเรียกแบบโง่ๆง่ายๆว่า less processed หรือ ผ่านกระบวนการให้น้อยที่สุดเท่าที่จะทำได้ เช่น เด็ดมากิน เฉือนมาย่าง ตากให้แห้งเอาเกล็ด(เช่นเกลือทะเล) เราอาจงงกับคำว่า อาหารผ่านกระบวนการหรือ processed food ซึ่งจริงๆในรายละเอียดมันมีแยกย่อยครับ ตั้งแต่ cooking ไปจนถึง ultra processed food มันมีลำดับขั้นของมันตามความหนักหน่วงในกระบวนการ จุดนี้คนที่เคยเถียงกันว่า การปรุงอาหารก็คือการผ่านกระบวนการไม่ใช่เหรอ แล้วเราควรกินอาหารปรุงเหรอ ทำไมไม่กินเนื้อดิบไปเลย ถึงจุดนี้พอจะได้คำตอบนะครับ ว่าเราไม่ได้เถรตรงขนาดคอมพิวเตอร์ 0 1 0 1 1 0 0 0 1 1 อะไรแบบนั้น เราอยู่บนพื้นฐานชีวะ จึงใช้คำว่า less processed ที่สุดเท่าที่จะทำได้ เพราะต้องอย่าลืมว่า ในอีกมุมหนึ่งความสุกของหลายๆอย่าง มันช่วยให้เราดูดซึมแร่ธาตุได้ดีกว่า แต่ขณะเดียวกันความร้อนก็ทำลายวิตามินไปมากเช่นกัน balance the force LUKE
ดังนั้นที่เราต้องพึงระวัง และ สังวรณ์เอาไว้คือ พวกที่ processed หนักๆ เช่น นมพืชต่างๆ เช่นโอ้ต เขาไม่ได้แค่แช่น้ำปั่นแบบบ้านๆ แต่มีกระบวนการทางเอนไซม์(เอนไซม์เคมี) ในการย่อย ปรุง และเติมวิตามินผง ซึ่งวิตามินผง ก็ inception เข้าไปอีกชั้น เพราะการได้แร่ธาตุวิตามินผงๆ มันก็ต้อง ultra processed หรือบางทีก็ต้องใช้เคมีผลิตขึ้นมา ทำให้เรา บริโภคสิ่งนั้นๆมากขึ้นไป เอาตามตรงเรากินโอ๊ตแห้งๆได้ไม่เท่าไร แต่พอมันทำเป็นนมแก้วนึง มันมาจากโอ้ตแห่งปริมาณมากกว่าที่เรากินแห้งๆเยอะมาก และการ more consume นี่แหละตัวหายนะในการกินอาหารเกินใช้งาน จนสะสมและเกิดโรค NCD ในที่สุด (หนึ่งในหลายปัจจัย)
เอาแบบชัดกว่านั้น ชาวคีโต ก็คือ แป้งอัลมอนด์ อันนี้ processed กลางไปค่อนหนัก คือการ meal หรือ ground หมายถึงการบดให้ละเอียดเป็นผงเล็กๆ ดังนั้นเค้กคีโต เค้กที่ทำจากผงอัลมอนด์ มันสามารถทำให้เรากินอัลมอนด์ได้มากกว่าปกติเยอะเลย อย่างถ้าเป็นเม็ดๆเราอาจเคี้ยวสัก 10 20 เม็ดก็เมื่อยปาก เพราะธรรมชาติมันปกป้องตัวเองมาแบบนั้น แต่พอเราไป processed มันหนักๆเข้า พอมันกลายเป็นเค้ก เป็นขนม จะยิ่งกินอร่อย กินมาก แล้วโพรไฟล์ของอัลมอนด์คือ คาร์บ9ต่อ100กรัม ก็จะทำให้เราคาร์บเกินไปได้ง่ายๆ รวมถึงอัลมอนด์มีโอเมก้า 6 สูงพอสมควร ก็ก่อการอักเสบได้ง่ายๆ
หรืออย่างสายคลีน สายปั่น จะพบกว่า การปั่นพืชนั้น ไฟเบอร์สายยาวได้กระจุยไปพร้อมกับใบมีดเรียบร้อยแล้ว เราก็จะเหลือได้แค่ แร่ธาตุ วิตามิน จากพืช จากผลไม้ (ที่การดูดซึมเข้าร่างจริงๆเท่าไหร่นี่ อีกเรื่องแล้วไม่พูดในโพสนี้) ที่เรารู้กันแน่ๆคือ ถ้าหวังไฟเบอร์จากการกินผักผลไม้ปั่น มันคือไม่ได้ตามนั้นแน่ๆแล้วกลับมาเข้าเรื่องของเราครับ เทคนิคง่ายๆในการ “เอ๊ะ” ก่อนเลยคือคีย์เวิร์ด (keyword) ที่มักมีการใช้กัน มักจะไม่พ้นคำว่า ผลิตจากธรรมชาติ สกัดจากธรรมชาติ มีส่วนผสมของ ได้ xxx จาก ในหมวดนี้จะค่อนข้างชัดเจนครับ จากนิยามของธรรมชาติที่เราตั้งไว้ ผลิตจาก สกัดจาก มีส่วนของ ได้จาก มันหลุดโผของเราไปเรียบร้อย คำว่า “จาก” ในทีนี้ถ้าเราจะเห็นภาพขึ้นให้เปลี่ยนเป็นคำว่า “ออกจาก” เราจะมองชัดขึ้นเลยว่า ทำไมผมถึงบอกว่ามันไม่ธรรมชาติ
ผลิตออกจากธรรมชาติ, สกัดออกจากธรรมชาติ, ได้ xx ออกมาจากธรรมชาติ ถ้าศัพท์อาชัยคือ เต็มฟอร์ม ก็ต้องบอกว่า ธรรมชาติที่เต็มฟอร์ม คือธรรมชาติ ไปแยกออกมาบางส่วนมันก็ไม่ธรรมชาติ แล้วสิ่งที่ธรรมชาติสร้างมาปกป้องเรามันก็สลายออกไป กระบวนการข้างบนนี้เลยไม่ได้เป็นธรรมชาติแท้ๆสักทีเดียว
ยกตัวอย่าง วุ้นเส้น ที่เราเพิ่งคุยกันไป วุ้นเส้นใช้คำว่า วุ้นเส้นถั่วเขียว ดูดีๆนะครับ วุ้นเส้น ถั่วเขียว คือ วุ้นที่เป็นเส้นๆ ส่วนคำว่าถั่วเขียว หมายถึงต้นตอ เขาไม่ได้บอกเราว่า ผลิตจากถั่วเขียว แต่บอกว่าใช้ถั่วเขียว เรากันเองที่บอกต่อๆกันว่า วุ้นเส้นทำจากถั่วเขียว ให้นึกถึง คำว่าน้ำมันถั่วเหลือง จะเข้าใจได้ชัดขึ้น ดังนั้นการที่วุ้นเส้น ทำมาจาก starch ล้วนๆ โดยการนำถั่วเขียวมาทำ starch หรือการสกัดคาร์โบไฮเดรตออกมาจากถั่วเขียว มันจะช่วยให้เราเห็นภาพชึ้นว่า ทำไมวุ้นเส้นไม่ใช่อาหารธรรมชาติ แต่เป็นการซัดคาร์บเพียวๆ เผลอๆหนักกว่าขนมปังสไลด์ โพรไฟล์ของโปรตีน แร่ธาตุ วิตามิน จึงหดหายไปจนเกือบจะไม่มีเหลือเลย ได้เป็นคาร์บล้วนๆ
หรือชัดๆในยุคนี้ก็ต้อง น้ำตาลหล่อฮั้งก้วย อันนี้ชัดมากทับซ้อนกันเป็นหอไอเฟล เริ่มจาก หล่อฮั้งก้วย เขาจะบอกว่า “สกัดจากผลหล่อฮั้งก้วย ได้สุขภาพ เป็นยาอายุวัฒนะ” อืมมมมมม หล่อฮั้งก้วยมีคุณสมบัติเป็นสมุนไพรเย็นชนิดนึง กินด้วยการต้มผล แต่ “การสกัดความหวานออกจากธรรมชาติหล่อฮั้งก้วย” คือ การดึงเอาแค่โมโกรไซด์ ซึ่งเป็นสารก่อเกิดความหวานยิ่งยวด ตระกูลเดียวกับที่มีในหญ้าหวาน เอามาแค่ความหวานของหล่อฮั้งก้วย แล้วจะเอาอะไรไปยาอายุวัฒนะ นี่คือการสกัดออกจากธรรมชาติ
อีกทั้งในห่อนั้นๆ มันมีสารโมโกรไซด์อยู่แค่นิดเดียว ที่เหลือเป็น อิริททริทอล รวมๆ 95-97% แล้วแต่ยี่ห้อ ไม่ต้องมาแข่งกันน้อย เพราะสูตรใช้เทียบเคียงน้ำตาล 1:1 มันประมาณนี้ ใครบอกว่าตัวเองมีอิริทแค่ 50% การันตีได้ว่าที่เหลือไม่ใช่ โมโกรไซด์ 50% เพราะมันใช้เทียบเคียงน้ำตาลแท้ 1:1 ไม่ได้ครับ หวานเหี้ยๆ นึกภาพออกใช่ไหมครับ ว่าทำไมเราย้อนสูตรหาโมโกรไซด์ได้ง่ายๆเลย เพราะมันมีอัตราส่วนการใช้งานที่ต้องสะดวกเป็นตัวค้ำคอ ที่บอกว่าน้ำตาลหล่อฮั้งก้วย มีความทับซ้อนคือ ฉลาก ใช้เทคนิคเทียบเคียงเพื่ออ้างอิงคุณสมบัติคุณประโยชน์ หมายถึง ที่ห่อจะชูประโยชน์ของหล่อฮั้งก้วย ว่าเป็นยา ลดความอ้วน ลดความดัน ลดเบาหวาน ดีต่อสุขภาพ เป็นสมุนไพรจีนหลายร้อยปี บลา บลา บลา เหมือนเล่านิทานว่าหล่อฮั้งก้วยดียังไง แต่ที่ใส่ในห่อมันไม่ใช่ตัวยาที่มีคุณสมบัตินั้นๆที่กล่าวมา มีแค่ความหวาน ที่โอเค ไม่กระชากอินซุลินให้สูงนานๆ เพราะมันไม่ใช่ กลูโคส ซูโครส นั่นเอง
นอกจากนั้น ตัวอิริททริทอลเอง ก็ไม่ใช่เล่นๆครับ ตามในเนทหรือตามคำอธิบาย เขาจะบอกว่า อิริททริทอลเป็นน้ำตาลแอลกอฮอล์เกิดจากธรรมชาติการหมักผลไม้ต่างๆ แต่ผงๆในโรงงานที่ใส่ในห่อในกระสอบนั้น ผลิตจากคาร์โบไฮเดรตที่สกัดออกมาจากข้าวโพด (corn starch) แล้วผ่านกระบวนการทางเคมิคอลเอนไซม์เพื่อให้เกิดน้ำตาลแอลกอฮอล์ เพื่อให้ได้โมเลกุลเดียวกับ อิริททริทอล ซึ่งบางคนอาจบอกว่ามันก็โมเลกุลเดียวกัน อันนี้ผมก็คงได้แต่บอกว่า เอาที่สบายใจครับ ผมไม่ได้ห้ามกิน ผมแค่บอกวิธีการผลิต เพราะมันไม่ใช่ natural มันเรียกว่า synthetic
น้ำตาลหล่อฮั้งก้วย จึงไม่ใช่ natural ตามที่เราเข้าใจ มันเป็น “synthetic อิริททริทอล + โมโกรไซด์” ในสัดส่วนอิริททริทอลมากกว่า 95% ทำให้คุณสมบัติทางยา ทางธรรมชาติ ที่หีบห่อนั้นไม่ได้หมายถึงตัวสินค้า แต่หมายถึงที่มาของสินค้า ในส่วนของการไม่กระชากอินซุลินให้สูงค้างนาน อันนั้นถูกต้อง เพราะของมันไม่ได้มีคุณสมบัตินั้น ส่วนการบรรเทาอาการเบาหวาน มันก็มีโอกาสเป้นไปได้เพราะเป็นผลสืบเนื่องจากการที่ไม่มีน้ำตาลสะสม ดังนั้นจึงไม่แปลกอะไรที่สามารถเป็นเช่นนั้นได้
สิ่งที่เราคุยกันวันนี้ไม่ได้บอกว่าอะไรดีหรือแย่ เพียงแค่ให้เราตระหนักและรู้เท่าทันฉลาก ว่าภาษาที่ใช้อาจทำให้เราเข้าใจไปเองได้ในบางอย่าง ดังนั้น ในส่วนของผู้ที่ต้องการหาความเป็นธรรมชาติ ก็จะได้เข้าใจมากขึ้นว่า สิ่งที่เคยสัมผัสมาอะไรบ้างที่เป็นธรรมชาติ อะไรที่เข้าใจไปเองว่าเป็นธรรมชาติ ส่วนอะไรดีหรือไม่ดีต่อสุขภาพ ก็ต้องไปพิจารณากันเองต่อไป เพราะยังมีอีกหลายปัจจัยโดยเฉพาะเรื่อง ultra processed food และการ over consume
pirateketo
siamstr
-
 @ 7bdef7be:784a5805
2024-05-28 13:47:50
@ 7bdef7be:784a5805
2024-05-28 13:47:50I wrote Oracolo (see the announcement below) because I was brainstorming about Nostr "long format" and thinking about how to promote it. There seems to be little love for this format, why?
Long posts should have interesting value because the author usually put effort into them, and are produced for a long-term fruition. In the end, blogging was one of the most productive strands on the web, and still holds considerable importance.But in standard (kind-1) social clients they are rather hidden. I think many people don't even know they exist, they probably intuit something just because they see a particular formatting. This is quite evident if you compare the responses/zaps/reactions of the short notes with the long ones, the latter have far fewer interactions, a fact that I read as less exposure to readers.
Interlude: don't know what this "long format" stuff is?
Check https://habla.news or https://highlighter.comI think the situation can be largely improved with some adjustments in kind-1 clients:
- Add a tab/section to the user's profile, next to the usual posts/responses, that lists only the long format notes;
- Highlight/pinning recent long notes in the user's profile to give them visibility; the user picture could also have a special mark that alerts about fresh content available;
- In the feed show the preview of long notes with a special design, and allow the user to read them in a separate/immersive view (or just link to njump.me);
- In an appropriate context (es. at the footer of a long note) invite the user to discover long format and post his own content;
- Offer a filtered feed that display only long format notes;
Finally, we should probably also evaluate and agree on a new labeling in clients, because “long notes” is self-explanatory but also a bit confusing next to "plain notes”. Perhaps “articles” might be a better term.
If clients bring more interaction on articles, content creators are naturally incentivized to invest their time in this area, thus increasing the production of in-depth content that may be of interest even to those who are not as involved in social media dynamics.
Memo for kind-1 clients: interoperability is our superpower and currently your are the main entrance to Nostr, so don't be fearful or lazy, please embrace it.
nostr:nevent1qqsrrcl7sfaxd505lyezj7u54tpdg93x0swpcpe0xj5adax5l6xz3yspzamhxue69uhky6t5vdhkjmn9wgh8xmmrd9skctcpr3mhxue69uhkxmm4de68y6t9wvhxv6tpw34xze3wvdhk6tcppemhxue69uhkummn9ekx7mp0aagyzp
nostrdesign
-
 @ 5d9ba2c5:7188ec8e
2024-05-27 22:35:06
@ 5d9ba2c5:7188ec8e
2024-05-27 22:35:06In the world of Bitcoin, the cornerstone of your privacy lies in labels and coin control.
While techniques like CoinJoins and Layer 2 (L2) can enhance your privacy, without a comprehensive understanding of your coins, also known as Unspent Transaction Outputs (UTXOs), you may not have a complete picture of your Bitcoin holdings and financial activities.
Labels: Labels empower you to affix descriptions or tags to your Bitcoin addresses, transactions, inputs, and outputs within your wallet and/or by using Labelbase. Meticulously labeling your transactions serves as a vital tool for tracking your financial activities and discerning the origins or purposes of your bitcoin. It provides context to your transactions, simplifying wallet management and facilitating audits.
Coin Control: Coin control stands as a feature present in certain Bitcoin wallets, granting users the autonomy to manually select which UTXOs to use when crafting a new transaction. This capability is of paramount importance for privacy, as it grants you the ability to pick UTXOs not associated with your identity or those with a favorable transaction history for your specific transaction needs. For instance, you can pick UTXOs with no transaction history or those that have traversed CoinJoin mixing services, thereby fortifying your privacy.
Freezing Coins: Here is where the BIP-329 spendable label takes center stage. This label attribute facilitates the freezing of UTXOs to prevent unintended spending, providing a valuable tool for ensuring that specific UTXOs remain untouched until you explicitly choose to spend them. In my opinion, every wallet should support this feature.
CoinJoins: CoinJoins, as a privacy technique, entail amalgamating multiple users' Bitcoin transactions into a singular transaction, thereby rendering it arduous to trace individual transactions. This amalgamation obscures the origins and destinations of funds, thus enhancing privacy. CoinJoins can be executed through services like Wasabi Wallet, Samourai Whirlpool or JoinMarket. As of today (May 28th, 2024), the Samourai coordinator is no longer available, and the Wasabi zkSNACKs coordinator will be shutting down its service on June 1st, 2024. Please ensure compliance with local laws when accessing these resources or running these apps and services.
Layer 2 (L2): Layer 2 solutions, exemplified by the Lightning Network (LN), are engineered to expedite and economize Bitcoin transactions by conducting the majority of transactions off-chain. In addition to scalability benefits, these solutions offer heightened privacy by shielding transaction details from the public Bitcoin timechain.
In summary, understanding the concept of UTXOs, labeling your transactions, and using coin control features can help you manage and enhance the privacy of your Bitcoin holdings. Techniques like CoinJoins and Layer 2 solutions can further improve your privacy by obfuscating transaction details and reducing the traceability of your financial activities on the Bitcoin timechain.
However, it's essential to stay informed about the latest developments and best practices in Bitcoin privacy, as the landscape is continually evolving.
Don't miss out on important updates! Subscribe to our newsletter for the latest insights, tips on labeling, BIP-329 adoption, and more to keep your Bitcoin transactions private and secure.
-
 @ eaba7a49:97790a4d
2024-05-27 11:07:50
@ eaba7a49:97790a4d
2024-05-27 11:07:50There is a lot going on now on the menopause health world, with the reinterpretation of the WHI (Women Health Initiative) study, from 2002 and now in 2024, it's gone from HRT increases risk of breast cancer to the other polarity: all women should have access to menopause therapy, its safe, and all women should be able to have. this conversation about risks and benefits with their provider.
And with that comes a lot of narratives about women's bodies that are important to deconstruct.
First, the idea that a magic pill can replenish our needs and take care of all our symptoms. The symptoms of menopause are symptoms of a systemic depletion of women's bodies. It's something that has happened over time, and there is no magic pill that can fix that. You can replenish biochemistry, but the toll that it has taken on your body, your emotions and mental health, that is something else. And yes, many women report feeling better: they are able to sleep, go to work, but still the narrative is that “my body is broken, and I can fix it with this magic pill” and that's where I see the disconnect.
Second, menopause is not about aging. Dr. Lara Briden speaks about this, and refers to the work of endocrinologist Jerilynn Prior, and I think is very important to take this into consideration. Menopause is not a failure of the body, it's not the failure of the ovaries, as a lot of the narrative goes. It is a neuroendocrine transition that is completely detached from aging.
Menopause is a brain overhaul, it's a brain reshaping so that it can be more efficient to tend to our physiological needs in the second part of our lives.
So, it's not about the failure of our bodies because we are aging, it is about our body’s ability to transform and to tend to our physiological needs. From now on, the focus is not going to be the energy intensive process of reproduction, it is going to be brain, bone, cardiovascular and metabolic health.
Neuroscientist Dr. Lisa Mosconi, who is studying women's brain in menopause explains that the menopausal brain is smaller and less energy demanding, because it doesn't need to tend to this energy intensive process of cyclicity for reproduction. So, we get to focus on our other body systems: our nervous system, brain, cardio health and that's why menopause is a window of opportunity. And that is why many women fall off the cliff in menopause. It's not because of aging, it's because they have been stressed, undernourished and overstretched for the whole reproductive period, so now when they come to menopause, that depletion makes her more vulnerable to symptoms.
Is like when you are rebuilding your house, but you didn't tend to your house for 30 years, and when you start remodeling, you find that the electric cables were damaged, the water piping breaks, it's not because of the remodeling. It's because it wasn’t maintained for 30 years.
Would love to hear your reflections and if this resonates or if I'm completely alone in this train of thought.
-
 @ 3bf0c63f:aefa459d
2024-05-26 22:16:05
@ 3bf0c63f:aefa459d
2024-05-26 22:16:05Danilo acordou cedo
Danilo acordou cedo e saiu para pegar o metrô, trajava aquelas vestes que seus amigos chamavam de "roupa de comunista", uma calça velha de brim, bege, uma blusa branca com uma logomarca vermelha - que não tinha nada a ver com comunismo - velha sob um paletó azul surrado e chinelo de dedo. Suas roupas eram todas parecidas entre si e, combinadas com sua barba malfeita castanha e seu olhar fundo típico de pessoas alcoolizadas, davam-lhe, realmente, um aspecto notório de comunista.
Quando o metrô parou na estação, Danilo entrou com sua mochila. Não havia assentos livres, mas ele já estava acostumado, aliás, até gostava de ficar em pé, para sentir melhor no rosto o vento que só vinha das janelas superiores do veículo. Colocou a mochila no chão e se segurou em uma das barras de ferro do veículo. Seus cabelos, apesar de curtos, balançavam em intrépidos estandartizados movimentos, como se dançassem o som de "One of These Days".
-
 @ 48a13ee3:2b39074c
2024-05-24 15:42:40
@ 48a13ee3:2b39074c
2024-05-24 15:42:40Friends are not easy to come across. They are made, just like good wine, after many years of ageing. At a certain point they cease to be just friends and become family. They give you the best advise, uncompromisingly, unabashedly, unreservedly. They praise your virtues and take pride on them, but are quick to call out the stupid things you are bound to do. They are patient, they forgive, they forget. They listen, and they are always available.
John was my dear friend for eighteen years. John was family.
I was part of the group that interviewed John when he applied to work at the College of Business. His knowledge and calm demeanour make him the perfect choice for our environment. During his years at UCF he was very hard working, thorough, and almost fastidious with his work. But I have not come here to talk about his work ethics, though they were exceptional.
The old man, as I used to call him every once in a while, quickly became the older brother to whom I would go to for advise, the moderator of my often too outspoken mind. We always had good topics of conversation, and he was the only person I could talk to about religion, and politics without breaking a sweat, or raising my voice. We talked about anything, and everything.
When time came for Kent---my child---to learn how to swim, it was John the one who taught him on his swimming pool. Through the years, John and Ann’s house became instruction grounds for my son Kent and cousin Alyssa, which not only shared the swimming lessons and a fun time at the pool, but also enjoyed petting the cats and dogs, and consuming high quality hot-dogs, and hamburgers.
Years passed by and when Kent needed driving lessons, uncle John offered himself, once again, as an instructor. Who better than him, right? After all, John had my utmost trust, and it was patient, yet firm. Exactly the kind of teacher a fifteen years old needed! Kent today drives, and does it very well, thanks to John.
John had my back, and I had his. After I convinced him to leave his flip phone behind and join the smart-phone generation, we shared locations with each other as a way to provide backup protection, and often used our phones to share news and stories of all kinds, commenting on them.
When John got sick I tried to spend as much time as I could with him. I understood that because of his illness, the time I could spend with him was limited, but I made myself available to him for as much as he could have me. Although I was very sad to see him dying, I put up my best face, and held back my tears as he did.
I am here to offer my contribution to John’s life celebration. I am glad that I was part of his life, and that he was part of mine. The impact he made, and the many memories we shared, will live with me for as long as I do (and he knew that, way before he even got sick). I am profoundly thankful for everything John did for me, and I celebrate his life.
-
 @ 48a13ee3:2b39074c
2024-05-24 14:08:51
@ 48a13ee3:2b39074c
2024-05-24 14:08:51This is another test for a long form post (kind:30023), using a CLI client.
From somewhere on the Internet: "kind:30023 properly defines the note as an editable one, with specific "blog-like" metadata (title, summary, banner, content as markdown) (see https://github.com/nostr-protocol/nips/blob/master/23.md)". Will it interpret returns, or should I use HTML, or...? As you can see I am a bit lost, but I will eventually find the way. I think. Maybe.
OK, I believe this is long enough. Let's try posting it.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 7308f407:94057dcf
2024-05-22 18:12:02
@ 7308f407:94057dcf
2024-05-22 18:12:02Details
- ⏲️ Prep time: Prep Time for Birria Beans
- 🍳 Cook time: Initial Boiling: 10 minutes Simmering: 2 to 3 hours (depending on the desired softness of the beans) In total, the estimated cooking time is approximately 2 hours and 10 minutes to 3 hours and 10 minutes.
- 🍽️ Servings: The serving size for the Birria Beans recipe depends on the quantity of beans and broth used. Given the ingredients listed, this recipe typically serves approximately 8-10 people+.
Ingredients
- 12 cups broth from birria (previous recipe)
- 1/2 onion
- 4 jalapeños or serrano peppers
- Water
- Salt to taste
- Beef from birria (optional)
Directions
- Wash the beans and let them soak for 30 minutes.
- In a large pot, add all the ingredients above.
- Set the heat to high and allow the mixture to come to a boil. Let it boil for 10 minutes.
- Reduce the heat to medium-low and cook for about 2 to 3 hours until the beans become soft.
- -To check the consistency of the beans, remove one from the pot to a plate. Using a fork, poke through to cut it in half. This method will help you easily tell if they are soft. You can also taste the beans.
- -If they are not soft yet, continue to cook for another 30 minutes.
- Every 30 minutes to 1 hour, check the beans to ensure they have enough water to cover them. They will dry out if the water level drops below the beans.
- You can also add beef from birria into the beans for added flavor.
- Enjoy the savory and slightly spicy flavor of the pinto beans cooked in red birria broth, topped off with cilantro, onion, and lime.
-
 @ 7308f407:94057dcf
2024-05-22 17:28:51
@ 7308f407:94057dcf
2024-05-22 17:28:51Chef's notes
This recipe is from a YouTube video that my mom sent to me because she wanted to try it. I made the recipe for my family once, and it was a success. We made Birria bowls, Birria nachos, Quesatacos (crispy tacos filled with cheese, birria, cilantro, onion and Salsa Macha.) I have been using this recipe for the last three years.
The YouTube title is "BIRRIA ESTILO TIJUANA en la birriería 'EL HOMMIE'". https://youtu.be/zAn8iM8dR14?si=gdYKBPyqyX13bwyo
Details
- ⏲️ Prep time: The prep time for the recipe involves several steps, including preparing the vegetables, roasting and preparing the chiles, blending the ingredients, and straining the sauce. Here's a rough estimate of the prep time: Preparing vegetables and chiles (cutting, roasting, and removing seeds): 15 minutes Blending and straining the sauce: 10 minutes Mixing ingredients and initial setup for cooking the meat: 10-15 minutes Overall, the estimated prep time is now approximately 35-40 minutes.
- 🍳 Cook time: The cooking time for the recipe involves several steps: Boiling the sauce: 20 minutes Cooking the meat in the broth: 4-8 hours (The cooking time for the meat in the broth depends on how small or big you cut the meat before cooking.) Additional steps such as cooking down the fat (if using for Quesatacos): 20 minutes Overall, the estimated cooking time is approximately 4 hours and 40 minutes to 8 hours and 40 minutes.
- 🍽️ Servings: This recipe typically serves approximately 8-10 people +, depending on how much meat each person eats or how many tacos you make.
Ingredients
- 24 Guajillo chiles
- 17 Pasilla chiles
- 1 large onion
- Water (to boil dry chiles)
- 5 cloves
- 2 bay leaves
- 3 tablespoons salt
- 5 garlic cloves
- Salt to taste
- Ingredients for Cooking Birria:
- 1/2 bunch cilantro
- 10 tablespoons dried oregano
- 2 teaspoons dried thyme
- 1 + 1/2 tablespoons ground black pepper
- 2 tablespoons ground cumin
- 6 cups water
- Adobo sauce (from dry chiles listed above)
Directions
- Adobo Sauce Preparation:
- To prepare the vegetables for the Adobo sauce, cut the tomatoes into halves. Next, cut the white onion into quarters.
- Remove the stem and seeds from the dried peppers. Roast the ancho and guajillo chiles for a couple of seconds on each side.
- In a medium/large pot, turn the heat to medium. Add water, chiles, onion, tomatoes, five garlic cloves, five cloves, and two bay leaves along with three tablespoons of salt.
- As some of the vegetables and spices boil, blend the ingredients from the pot. Once combined, add them back to the pot and merge the next batch.
- Remove the bay leaves to prevent them from blending into the sauce.
- Once all ingredients are blended, boil the sauce for 20 minutes, removing the foam that rises to the surface. Cooking the sauce down allows the tomatoes to break down and develop a great taste with the spices.
- After the sauce is finished cooking, use a large bowl and metal strainer to strain the sauce, removing the pepper seeds and any remnants of the tomato.
- Meat Preparation:
- In a large pot, add the meat along with 1/2 bunch of cilantro, ten tablespoons of dried oregano, two teaspoons of dried thyme, 1 1/2 teaspoons of ground black pepper, two tablespoons of ground cumin, six cups of water, and the Adobo sauce you previously made.
- Mix all ingredients in the pot to ensure the Adobo sauce is evenly dispersed.
- Cook on high heat until it begins to boil. Once boiling, stir the ingredients, cover with a lid, and set to the lowest heat setting on the stove. Cook for about 4-8 hours with the lid on.
- After the cooking time, verify that the meat is tender by using a fork to cut through. If the meat is not tender enough, add more time to cook on low.
- If the meat is to your desired consistency, remove it to another bowl. Allow the meat to cool down if you are shredding it by hand. If not, keep it aside to add back to the pot once the broth is strained. You can also chop the meat using a knife to break it down into smaller pieces.
- Remove the cilantro and discard it along with any other unwanted parts from the broth.
- Remove the fat from the broth into a bowl and keep it aside if you would like to use it for Quesatacos.
- If using the fat from the broth, cook it down on medium heat for about 20 minutes. This breaks down the fat from a solid to a liquid. After cooking, strain the fat to separate the solids from the liquid.
- Strain all sauce using a metal strainer.
- Leave some sauce on the side if you are making beans with the broth (about 12 cups).
- Once the broth is strained, add the meat back into the pot.
- Ready to serve with meat in its broth, as Quesatacos, or however you would like to enjoy the Birria.
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ d34e832d:383f78d0
2024-05-20 23:06:18
@ d34e832d:383f78d0
2024-05-20 23:06:18The blockchain ecosystem is built upon multiple layers, each serving a unique purpose to ensure the robustness, scalability, and functionality of decentralized networks. This article aims to break down these layers—Layer 1, Layer 2, and Layer 3—highlighting their roles and notable implementations such as Mainnet, Test Net, SigNet for Layer 1, Bisq, Liquid, and Lightning for Layer 2, and Nostr for Layer 3.
Layer 1 Networks
Layer 1 networks form the foundational layer of the blockchain protocol and are responsible for the core functionalities of the network, including consensus mechanisms, transaction validation, and maintaining the blockchain ledger.
Mainnet
Mainnet is the primary network where real transactions occur, and actual value is transferred. Transactions on Mainnet are irreversible and recorded on the blockchain ledger, providing a permanent audit trail. Examples of Mainnet networks include Bitcoin Mainnet and Ethereum Mainnet.
- Usage: Real-world transactions, dApps, and smart contracts.
- Security: High, with strong incentive mechanisms to ensure the integrity of transactions.
- Consensus: Proof of Work (PoW) for Bitcoin, Proof of Stake (PoS) for Ethereum 2.0.
Test Net
Test Net is an alternative network identical to Mainnet but used for testing purposes. Developers use Test Net to experiment with new features, smart contracts, and dApps without risking real assets.
- Usage: Testing and experimentation.
- Risk: Low, as Test Net transactions do not involve real value.
- Utility: Identifying bugs and issues before deploying on Mainnet.
SigNet
SigNet is a specialized Test Net that focuses on experimenting with signature schemes, particularly Schnorr signatures and Taproot, which aim to enhance privacy and scalability.
- Usage: Testing signature-related features and improvements.
- Focus: Advancements in cryptographic techniques and transaction efficiency.
- Participants: Developers and researchers focused on cryptographic enhancements.
Layer 2 Networks
Layer 2 networks are built on top of Layer 1 to enhance scalability, speed, and efficiency. These networks address the limitations of Layer 1 by handling transactions off the main blockchain while still leveraging its security features.
Bisq
Bisq is a decentralized Bitcoin exchange that allows users to trade cryptocurrencies without relying on a central authority. Bisq ensures privacy and security by conducting transactions directly between peers.
- Usage: Decentralized trading and exchange.
- Benefits: Privacy, security, and decentralization.
- Tech: Peer-to-peer network without central servers.
Liquid
Liquid is a sidechain developed by Blockstream that allows fast and confidential Bitcoin transactions. It enables quicker settlement times and privacy through confidential transactions.
- Usage: Fast and private Bitcoin transactions, trading, and issuance of digital assets.
- Features: Enhanced privacy, faster settlement, sidechain pegged to Bitcoin Mainnet.
- Participants: Exchanges, traders, and financial institutions.
Lightning Network
Lightning Network is designed to facilitate instant, low-cost micropayments by creating off-chain payment channels. Transactions are aggregated and settled on the Layer 1 network, reducing congestion and transaction fees.
- Usage: Instant micropayments and fast transactions.
- Benefits: Scalability, low fees, speed.
- Mechanism: Payment channels that operate off-chain, only settling on-chain when channels are closed.
Layer 3 Networks
Layer 3 networks build upon the functionalities of Layer 1 and Layer 2 to offer more sophisticated services and applications, often related to data management, communication, and additional privacy features.
Nostr
Nostr (Notes and Other Stuff Transmitted by Relays) is a protocol for decentralized, censorship-resistant messaging and social networking. Nostr leverages the underlying security and decentralization characteristics of the blockchain ecosystem.
- Usage: Secure, decentralized social media and communication.
- Benefits: Censorship resistance, privacy, and decentralization.
- Implementation: Uses public-private key cryptography for secure messaging and relay-based data transmission.
Closing
The blockchain ecosystem's multilayer architecture enables robust, scalable, and secure decentralized applications. Layer 1 networks like Mainnet, Test Net, and SigNet provide foundational support, while Layer 2 networks like Bisq, Liquid, and Lightning offer enhanced performance and efficiency. Layer 3 networks like Nostr further extend capabilities into decentralized communication and advanced applications.
Understanding these layers and their specific applications is crucial for anyone looking to navigate the blockchain space effectively, develop new solutions, or leverage the benefits of decentralized networks for a variety of uses. As the ecosystem continues to evolve
-
 @ deab79da:88579e68
2024-05-20 20:03:17
@ deab79da:88579e68
2024-05-20 20:03:17Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: ~20 min
Ingredients
- 4 boneless skinless chicken breast
- 1 small onion
- 1-3 jalapeno pepper, to taste
- 1/2 cup soy sauce
- 1/2 cup pineapple juice
- 1/4 cup olive oil
- 1/4 cup apple cider vinegar
- Juice of 1 lime
- 1 tsp honey
- 2 cloves garlic, minced
- 1/2 tsp ground nutmeg
- 1/2 tsp ground ginger
- 1/2 tsp allspice
- 1/2 tsp red pepper flakes
- small bunch of fresh cilantro
- Salt & Pepper
Directions
- Put all of the ingredients, except the chicken breast, in a blender and blend until smooth
- Let the chicken marinate ine the mixture for several hours, or overnight
- Best cooked on a charcoal or gas grill. In a pinch, medium heat in a saute pan will do.
- Remove the chicken from the marinade and grill or saute until cooked through. While the chicken is cooking, place the remaining marinade in a small saucepan and bring to a boil. Simmer for 5 minutes.
- When the chicken is cooked, allow to rest for 5 minutes. Before serving brush the chicken with the remaining glaze. Serve with your favorite seasonal vegetables.
-
 @ 63b027f6:2c043172
2024-05-20 13:08:33
@ 63b027f6:2c043172
2024-05-20 13:08:33In a clearing in the forest there lived a group of pigs. They had built a thriving town out of sticks, in which they attended to their own tasks and lived prosperously. Every pig had stacks of sticks outside her dwelling, and while these structures ranged from the big and extravagant to the small and humble, each was serviceable, sturdy, and adequate for the needs of its inhabitants. Anything a pig needed, he merely traded for sticks. In return for his own special work, a pig elsewhere in the town would exchange as many sticks as needed. Sticks were wonderfully useful: a fire to keep a pig warm, a tool to save a pig time, even an inheritance to secure a pig’s future–everyone was happy to trade for them.
It came about that hungry wolf descended on the town one day. Atop the wooden gate, bristling with pointy sticks, a number of pigs noticed his approach and barred his path.
He called to them, “Little pigs, little pigs, let me come in.”
“Never,” replied the pigs, who could see his violent greed, “not by the hair on our chinny-chin-chins!”
The wolf said, “Then I’ll huff, and I’ll puff,” and he began to contort grotesquely as he alternated inflating and deflating, ratcheting ever more air into his lungs. At last he reached the point of bursting, whereupon he let loose a violent gale of thunderous power against the pigs and their town. The pigs, however, had engineered the walls out of strongest sticks they could find; each stake was securely anchored and the wolf’s attack was rebuffed.
Panting, the wolf dragged himself away from the walls, burning with shame at the jeers of the pigs. He retreated to the forest and observed the pigs while contemplating his next move.
The wolf prowled the forest, and whenever a pig came to harvest sticks for the town, the wolf chased her off and kept the sticks for himself. Now at first this nuisance did not concern the pigs in the town, because they had plenty of sticks to trade amongst themselves, and many reserves and savings from so many years of plenty before the arrival of the wolf.
But sure enough, over time the sticks were steadily depleted. Homes needed heat, repairs needed to be made, tools broke down. While some pigs noticed what the wolf was doing and started hoarding their sticks and stuffing their houses full with them, other pigs were running out of sticks to trade, and grew hungry and afraid. One night, long after the town had drifted off to slumber, some of these struggling pigs took a few sticks out of the wall surrounding the town. They quietly took their prizes back to their homes and were able to trade the next day for some food.
Gradually, the strong walls that protected the pigs weakened. The wolf noticed that many points along the wall seemed to sway in the wind, and the pigs, whom he had previously observed to be tranquil and cooperative, fought with each other frequently and argued over whose responsibility it was to keep the walls strong. Each day sticks would disappear from the wall as more and more pigs grew desperate in the town. One day the wolf returned to the gate and demanded, “Little pigs, little pigs, let me in!” There were only a handful of guards now, and the once-mighty gate they stood on looked rickety and poor. One pig’s small voice quavered, “N–nn–never, not by the h-hair on my ch-ch-chinny-chin-ch-chin.”
The wolf huffed, and puffed, and blew the gate in. This time he splintered the whole structure, sending hapless pigs and broken sticks everywhere in a tremendous cloud of dust and debris. The wolf’s silent frame–a black shadow of terror–stalked through the haze and entered the defenceless city. The wolf rampaged in a frenzy of destruction. When he had eaten his fill, the wolf departed and for many years was not seen. What remained of the city struggled, and suffered, and vowed to never let this happen again.
After many years of wandering the world, the wolf became hungry again. He thought back to the great feast at the stick town and decided to return. When he emerged from the forest to behold the wreckage still pungent in his memory, he was taken aback by the colossus that confronted him.
The pigs had built an enormous, intricate city of paper. It stretched as far as the wolf could see into the horizon and at its centre he beheld a tower of dizzying height. The city was far bigger and seemed to move faster than the stick one he remembered, with thousands of pigs bustling in every direction. Pigs in the tower printed small pieces of paper with their faces on them, other pigs traded these papers for everything else, pigs standing on corners sold bundled papers that other pigs would take to benches and stare at, pigs presented papers to other pigs when they arrived at their destinations, pigs in paper uniforms handed paper tickets to pigs breaking the rules, pigs ate at paper tables, laboured to push paper wagons, wore paper clothing, and all over the city were busied with constructing paper structures. Though many sections of the paper city seemed to the wolf to be in ruins, many more pigs were employed in building new paper districts than repairing the old.
The wolf was cautious from his humiliation at the gates last time and resolved to observe the paper metropolis before attacking. He noticed the great mass of pigs on the streets of the city looked bedraggled, shabby, and desperate, while the fattest, juiciest ones lived indolently atop the tower. He could see no defences and understood no order in the way this behemoth functioned, but the sheer size of it intimidated him and made him hesitant.
Beneath the tower was a maze-like structure that spiralled out in all directions. The Labyrinth seemed to give the pigs atop the tower no end of pleasure and pride–the paper maze contained thousands of beaten-down pigs at any given time, all waiting for their chance to get to the middle and have their concerns heard at the tower. A pastime among the ruling pigs was to look down on the great line of peons snaking its way through the maze and delight in the despair with which some proportion of the pilgrims would inevitably quit, slouching back to the beginning with shoulders bowed. “Another satisfied customer,” went the joke.
Mad with hunger and past the point of caution, the wolf stormed into the unguarded city and made his way to the Labyrinth. He stepped brazenly into the maze, where he saw an endless line of huddled bodies whimpering against the support of the wall–a pathetic papier-mâché which was sagging and splitting under their weight. A smile of perfect disgust grimaced the wolf’s face and he stifled a rich laugh from deep within, then bellowed so that the pigs on the tower could hear, “Little pigs, let me in!” He walked up to the quivering forms of a nearby family who scattered to either side and once again puffed up his chest to a dizzying capacity, then expelled a vicious deflation that tore a great schism in the Labyrinth. The blast rippled through the maze in a straight line to the central tower. There was now a direct path from the wolf to the centre–a smoking corridor of whirling paper and small flames spreading from the edges. The pigs looked at each other, dumbfounded, and, stumbling over one another with increasing urgency, scrambled through the hole in the maze towards the great spire at the centre.
Pandemonium broke out in the tower as they watched swarms of pigs escaping the wolf surge through the holes in the labyrinth. The pigs scrambled up the walls of the spire and clogged its stairwells. The whole structure began to list and buckle under its own weight, until its supports gave out and it crashed into the maze, where the hungry wolf was waiting to devour them all. The paper city was a smouldering ruin, and the wolf feasted.
After many years of wandering the world, the wolf became hungry again. He thought back to the painfully proud pigs in the spire and chuckled as he remembered them falling into his jaws. He emerged from the forest a third time. The wolf beheld a wall of encrypted energy. He laughed, recalling his triumph over the paper Labyrinth, and pushed on the gate. To his surprise, he could not move the structure in the slightest. He snarled, and breathed in a great mass of air which he expelled forcefully against the shimmering, translucent wall, but to no avail. The wolf raged against the wall with breath, claw, and fury… but his power could not penetrate the defence. Spent, the wolf retired to a nearby embankment where he studied these pigs and their wall. He focused his attention on the top of the wall, where he noticed the bricklayers building it ever higher one block at a time. He could discern no pattern in it. For almost ten minutes nothing would happen, then suddenly a pig would have a block in her hands, her fellows nearby would raise a cheer and pat her on the back, and then she would add it to the wall. The wolf stared and perked up his ears; he noticed the pigs were all mumbling to themselves as they worked–mumbling an endless stream of numbers and gibberish. He looked closer at the pig who created the block; she kept a small amount of the energy for herself, which clearly was valuable by the way she protected it in her pocket, patting it and stealing glances at it when given a free moment.
Feeling hot with the embarrassment of failure, the wolf waited for nightfall and approached the wall. In a whisper no pig could hear, he started mumbling numbers himself, and to his amazement, a partial blob of flickering energy appeared in his hand, too. As he kept whispering, the block became more solid and real and took on weight, until suddenly it snapped out of existence completely and he heard the familiar cheer at the top of the wall.
He tried again, and this time concentrated all his attention on the stream of values. As the block formed in his hand, he realised he could shape it; he could imagine it and the energy would start to take on the form of a ladder that could hold his weight. He began building a ladder out of the energy, but before long it would wink out of existence and the wall would become a bit higher. Puzzled by this, he tried several more times, growing increasingly irritated when each taste of success evaporated into nothingness without warning.
The next morning the wolf went out into the forest and recruited. A mixture of greed, threat, and coercion was needed, but eventually he rounded up a number of lesser forest predators to join him at the base of the wall. They all started mumbling numbers, despite feeling a bit ridiculous, but they grew in intensity and excitement as they witnessed the shimmering ladder take shape before their eyes. They started dreaming of the feast that lay in wait for them on the other side of the wall, and their mumbling became a buzzing hum of anticipation.
The pigs at the top of the wall took notice that their construction had slowed down significantly, and called up more from inside the city to join. The wolf’s ladder was growing, and more pigs appeared at the top to speed up the construction of the wall. The ladder and the wall both grew rapidly–the wolf would inch closer and the pigs would build higher. But after about a fortnight, and despite the frenzy of the life-and-death struggle, the pace of new energy had slowed down to only a few bursts every hour, the way it had been before. The wolf’s ladder was still far too short, and the pigs always seemed to be able to get a few more of themselves on top of the wall to keep guessing numbers and stay out of reach.
After a month of competing with the pigs and making little progress, enthusiasm on the wolf’s side slackened. Each morning he found fewer creatures at the base of the wall, and he was using more and more of his time to menace those that remained and keep them in line. Many among his unwilling ranks had noticed that they got to keep a small amount of the energy when they were lucky enough to add to the ladder, and the clever among them had started surreptitiously trading with the pigs when the wolf was preoccupied. When one morning the wolf saw his own creatures on top of the wall, building it higher and trading blocks with the pigs for food, water, and supplies, he let out the most terrifying tempest he had yet achieved, swirling up monstrous clouds of dust and debris at the gate of the energy city, tearing trees from their roots, obliterating his own camp and sending the ragtag remnants of his forces into a hurricane of destruction. But, when his effort subsided and he looked at the devastation he had wrought, the energy gate remained pristine and invincible, and the pigs carried on building within its safety.
Many years passed and the wolf became mangy and emaciated. He could barely summon breath anymore and commanded no respect among the pigs, who passed him freely without a care on their way in and out of the forest. He was a historical relic, a curiosity, a class trip for children: irrelevant.
-
 @ deab79da:88579e68
2024-05-20 03:44:25
@ deab79da:88579e68
2024-05-20 03:44:25Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 6
Ingredients
- 4 large eggs
- 3/4 cup granulated sugar
- 3 cups milk
- 1 cup heavy whipping cream
- 2 teaspoons vanilla extract
- 1 1/2 teaspoons ground cinnamon
- 3 cups cooked rice , cooled
- 1 cup raisins
Directions
- Preheat oven to 350 degrees F.
- Beat the eggs and sugar together. Slowly pour in the milk and cream and mix well.
- Add the vanilla and cinnamon and mix well. Add the rice and raisins and stir to combine.
- Pour mixture into a greased casserole dish. Any oven-safe dish will work--you can use one pan to bake at least 9x9'' or bigger, or smaller individualized serving dishes.
- Place the filled casserole dish inside a larger, oven-proof dish. Add about 2 inches of water to the larger pan (or enough to fill about halfway up the side of the rice pudding dish). This method will help the pudding to have a custard texture.
- If using a 9x9'' or slightly larger pan, bake for 40-50 minutes or until the top has set (It's okay if it jiggles just slightly). Serve warm.
- Leftovers store well in the refrigerator for up to 5 days.
-
 @ 3c984938:2ec11289
2024-05-19 12:55:47
@ 3c984938:2ec11289
2024-05-19 12:55:47👉play the audio to listen to the article.
This article contain several links hidden within the text. If you dare to understand the meaning behind the last image. Click on "daily" for an image, read it. Then click on "muchness" to watch a video(about 1h) link. After you've done that, revisit here and look at my last image. You might have missed something.

Excusez-moi, s’il vous plaît. That tasted purple🍵🌺
🤤😮Are you still thirsty from the previous article? Are you amazed by the different flavors of web3 enabled sites, clients, and apps? Did you try out using NIP-07, "Signer extension?" Nos2x or NostrConnect are pretty spiffy, eh! Did it bring a similar reaction like when you first learned how to drive? When I started to explore Nostr I had that “whoa, that a lot easier than Facebook,” moment. 💡⚡A light bulb started to flicker on.

🎉🎈Are you having fun yet? Would you like another cup of tea? 💸HODL (Hold On for Dear Life) as we sip our way to purple. Things here in Nostr wonderland are curiouser and curiouser every day. One day it's 🍕pizza 🥧pie? And then the next day it's Danny, Dan, Dan. Hold on to your petticoat, because you're about to get swept away, by the tools to get the most out of Nostr.

But first, would you like a purple crumpet?💜🥞
🍵🍰🎉This wouldn't be much of a tea party without a bit of finger food. If you are following me, I'm just a little hors d'oeuvre among the many here on Nostr. So let's try some other flavors. You can start with some influencers from twitter that have fallen into the rabbit hole here at this link.
I follow Jack and Edward Snowden, but there are several others.
jack @npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Snowden @npub1sn0wdenkukak0d9dfczzeacvhkrgz92ak56egt7vdgzn8pv2wfqqhrjdv9
💡🎮🏈🎲🏹What are some topics, hobbies, and interests that are important to you? You can search for hashtags and follow those on your client. For example, #onigirl, #privacy, and even #cats in your search bar on your client. Remember, there are no algorithms here. If wish to have a vibrant feed or be fed random stuff(which is kinda cool sometimes), follow curators that you like.
👉🚦💤Don't sleep on "stacker.news", 🎩🔐📎They're entirely bonkers! But I'll tell you a secret. All the best people are. Here are just a few.
📝@Lux drops “sovereignty pills"💊 daily in “Stacker Saloon,” 🏋️♀️@grayruby does 100 push-ups and squats until 100k Bitcoin, 🔏@sethforprivacy podcast host of "Opt Out," 🎼@MusicTrappa Former Tv Contestant of NBC the voice. 💣@nerd2ninja posts invigorating and provocative links and content, 🐝@Alby for bee news, @TNstacker, @0xbitcoiner, @undisciplined and dozens more! Plus a new territory just started by @AtlantisPleb called ~openagents revolving around NIP-90 Data Vending Machine, it is hilarious to play with. Try Trolly McPirate, tis quite fun.

Are you turning purple?💜
👉🍄🦋"Who are you?” said the Caterpillar Now, that you've drank and ate, are you changing color yet? Let's explore this wonderland that Nostr has given us! It starts with changing your profile and banner image to anything you like. Since, we're not robots.

👉🌻🌹"Do you suppose she's a wildflower?" asked the Daisy. 🌼🌷 ⭐NIP-05 identity DNS ⭐ Similarly to Twitter, a check mark is to show that you are from the same garden “like a human,” and not an outlier like a weed or, "bot." But not in the nefarious way that Big Tech handles this. In Nostr wonderland this allows you to map your silver key, "npub" to a DNS identifier. Once verified, eat a mushroom and shout out to announce your new Nostr residency to share. Just remember, one quick little thing. Break a small piece of the other side of the mushroom after, don't bite.
✨There are a plenty of options but if you've followed the steps in my previous article, "First time (N)ostrich start here!" guide following my advice to get a SN, "stacker.news" then this gets extremely easier.
👉✅Click your "Profile," then click "Settings," scroll to the bottom and paste your Silver key, "npub!" and click "save" and there you go! Use your Stacker.news lightning wallet address as your ⭐NIP-05.⭐ Congratulations!!! You are now verified! Give it a few hours and when you use your "main" client you should see a checkmark!
Beware of card soldiers 2-10

👉⚔🍎👑☠Oh No! The "Queen of Apples" has released a jabberwocky that threatens some Nostriches wallets! As long as you remain using her wares within Nostr Wonderland you may need to comply to her draconian ways! 👛👾👺🐭
❗It has come to my attention that Apple users cannot utilize Chrome webstore; thus are not able to take advantage of using "Signer extension." Whatever, shall we do? Shall we paint all the roses red?🌹

👉🎠🦄'Well, now that we have seen each other,’ said the Unicorn, ‘if you’ll believe in me, I’ll believe in you. Is that a bargain?🦁🤝
For 🍏Apple users, you can still use "stacker.news" by registering with your email to help you get a starter Bitcoin lightning wallet. Another option is Primal, please note both wallets have Satoshi limits. Primal, may not be in your interest if you're concerned with privacy.
👉🎠🌼🐝🌻 A unicorn sent a friend, to help thee.🐝🌷🌹 A solution for 🍏Apple users would be to get an invitational code from Alby. You are able to use Alby via Safari on your Mac Os, and as a signer extension. Then connect 💎Damus with Alby. The good news is you can find @Alby on stacker.news and ask! Or check them out on your client. Just search "hello@getalby.com" Once you get an account, you could use your Alby lighting address as your ⭐NIP-05⭐ address as an option. The bee whispered to me, “I also support android, Safari on Mac and things,” and flew high to lead us out.
Alby the bee, silver key @npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm

Quickly! Follow me out of this maze!
✨With the help from 🐝Albee, we escaped the 👑queen's jabberwocky. The key to decentralization is to shred all thing bounding you by unseen 🔗chains and "things". To abandon all things 🏫learned, and go back to thinking about 😲six impossible things. You should try it-- It certainly is such great practice. 💡For example, what if I told you that you were all ⚰dead? How 🤡preposterous and silly! But whose, 🤝who, to say it isn't? This is your adventure, dear user. I'm merely here to help guide you in all its marvels, and to safely navigate you through its treacherous terrains. How much 🦁muchness' do you have? Oh, blind me, do I see a clearing?

Ohh! Look here, my friends must have 🦺built a safe passage.
A ♨ steaming river is set before us. We must be very careful. Unless, you want to end up in the boiling sea. There are some boulders and pebbles over there. My 😊friends, must have laboriously put these here for Nostriches like us. I'll take you to the 🐸frogstr and 🐰hare, but then that will be the end of it.

I think I see him, He's right there. Ever since 🐸Frogstr converted to freedom, he's been spreading memes to others. Take a peek!
Memestr, Pinstr, Badges, If you've received badges, put them on by visiting here., Swarmstr cute interface to view hashtags, My favorite food client with optional OnionSauce, noStrudel tastes like 🤖Reddit, Gossip My favorite Desktop Client, Extensive List of all things Nostr., and Alice in Wonderland story.
My friend the 🐇white rabbit Yakihonne now supports 🍎iOs and 🤖Android. This app supports NIP-23 in all of its entirety. Feel free to soak up the information there. When NIP-65? 🎯I don't know. Let's 🐜bug them to do that.

You can easily find all my content on 🐇Yakihonne.com or on the app. My only grief I have with the 🐰hare is that it's not Open Source. Annoy the 🐇white rabbit to go Open Source if you can catch him! He's always going off about "⏰Time⌚" which brings me to the end of my guide.

We're lucky to escape the Bloody Shrewd 👑Knave, but he will send his 🃏card ⚔soldiers yet again.
📢Lastly, dear user. What better time then now to make your life more ⛓decentralized, if not now then when? Take back your ⚖digital sovereignty, and it starts here in Nostr 🐹Wonderland. Use the 🛠tools here, and share your knowledge, experiences, or whatever and 💰monetize it. Join the 🎉Freedom Party! Learn about the Knights of Nostr that are fighting for Freedom Tech and the projects that are contributing to make it happen. FOSS for all!
👉Have you tried the 🍊Orange 🍵Tea, Dear User? It's quite divine. Would you like me to write a 💰Bitcoin guide? Let me know in the comments! I appreciate all feedback.
👉You can read my 🧵first article here. Alternatively, you can click/tap "here" if you're logged into app client.
🙇♀️🙏It would be the highest honor for me if you 🔖bookmarked my article and 🔁shared it with future (N)ostriches.
"Imagination is the only weapon in the war against reality." -Lewis Carroll
🧧⚡Zapping⚡ is always appreciated, but is not required.
💜🧡Thank you💖💋
📢🥂Special Shout-outs
🐶Uno - Spreading Nostr love @npub14q8uffuxxnhzd24u4j23kn8a0dt2ux96h5eutt7u76lddhyqa0gs97ct2x
🥂Derek Ross - welcoming committee to Nostr; I'm jumping on this. @npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
👏Nos Social - Introducing me to the Nos App community @npub1pu3vqm4vzqpxsnhuc684dp2qaq6z69sf65yte4p39spcucv5lzmqswtfch
🐇Yakihonne - For supporting all things Nip-23 @npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🐱💻Semisol - working hard to keep TOR relays up @npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
📝James - Introducing me to use my obsidian tool or earring. (I've converted at least seven Nostr since then) @npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw
-
 @ 2521f791:0cf90b37
2024-05-19 09:18:40
@ 2521f791:0cf90b37
2024-05-19 09:18:40
เราจะปกป้องความเป็นส่วนตัวของเรา ในยุคคอมพิวเตอร์ได้อย่างไร?
ในปัจจุบัน ชีวิตของเราถูกเฝ้าสังเกตในหลากหลายรูปแบบ: ทุกธุรกรรมจากบัตรเครดิตจะถูกบันทึกลงในฐานข้อมูล การโทรถูกบันทึกโดยบริษัทผู้ให้บริการโทรศัพท์และนำไปใช้เพื่อทำการตลาดให้กับตัวเอง ธนาคารถ่ายสำเนาเช็คและเก็บรวบรวมเอาไว้ และ ด้วยเทคนิคการ "จับคู่" ใหม่ๆ ก็ทำให้การรวบรวมข้อมูลจากหลายฐานข้อมูลนั้นสามารถเปิดเผยรายละเอียดเกี่ยวข้องกับชีวิตของเราได้มากขึ้น เมื่อฐานข้อมูลคอมพิวเตอร์ขยายใหญ่ขึ้น เมื่อมีการทำธุรกรรมทางอิเล็กทรอนิกส์ผ่านระบบโทรศัพท์และเครือข่ายคอมพิวเตอร์มากขึ้น การเฝ้าสังเกตและติดตามก็เพิ่มขึ้นตามไปด้วย
โดยส่วนใหญ่แล้ว ทางแก้ปัญหาที่ถูกนำเสนอขึ้นมา มักจะเกี่ยวข้องกับการมีบทบาทที่มากขึ้นของรัฐบาล หนึ่งในข้อเสนอนั้นคือ การผ่านกฎหมายที่ออกแบบมาเพื่อจำกัดการใช้ข้อมูล: "ข้อมูลจะไม่สามารถนำไปใช้ในวัตถุประสงค์อื่น นอกเหนือจากวัตถุประสงค์เดิมที่เก็บรวบรวมมา" ดังนั้น ข้อมูลรายได้ที่ธนาคารเก็บรวบรวมจากการติดตามกิจกรรมบัญชีเงินฝาก จะไม่สามารถเปิดเผยให้กับบริษัทที่รวบรวมรายชื่อผู้ติดต่อ(Mailing list companies) ข้อมูลทางโทรศัพท์จะไม่สามารถขายให้กับบริษัทการตลาดทางโทรศัพท์ได้ ฯลฯ
นี่เป็นวิธีการแก้ปัญหาที่ไม่ดีนัก ด้วยหลายๆสาเหตุ รัฐบาลมักจะไม่มีประสิทธิภาพในการบังคับใช้กฎหมาย ความง่ายในการเก็บรวบรวมและใช้ข้อมูล ทำให้เกือบจะเป็นไปไม่ได้ที่จะบังคับใช้กฎหมายลักษณะนี้ อีกทั้งรัฐบาลเองก็มีแนวโน้ม ที่จะยกเว้นตัวเองจากกฎหมายที่ร่างขึ้น เช่น แทบจะเป็นไปไม่ได้ที่ กรมสรรพากรจะยินยอมสละสิทธิ์ การใช้เทคนิคการจับคู่ฐานข้อมูล ซึ่งใช้สำหรับติดตามผู้หลีกเลี่ยงภาษี แน่นอนว่า แนวคิดในการพยายามจำกัด การใช้ข้อมูลจำเป็นต้องมีข้อจำกัดที่เข้มงวด สำหรับการกระทำการส่วนตัวของบุคคล ซึ่งผู้สนับสนุนแนวคิด Extropians นั้นยอมรับไม่ได้ หนึ่งในชุมชนออนไลน์เก่าแก่ คล้ายกับ Cypherpunks
แต่ก็มีทางเลือกอีกวิธีหนึ่ง ซึ่งได้รับการสนับสนุนโดยนักวิทยาศาสตร์คอมพิวเตอร์ชื่อ David Chaum จากศูนย์คณิตศาสตร์และวิทยาศาสตร์คอมพิวเตอร์ ประเทศเนเธอร์แลนด์ ในขณะที่ผู้คนส่วนใหญ่ ที่กังวลกับปัญหานี้ มองหาทางแก้ไขแบบพ่อปกครองลูกจากรัฐบาล แต่ Chaum กลับค่อยๆ วางรากฐานด้านเทคนิค สำหรับวิธีการจัดระเบียบข้อมูลทางการเงินและข้อมูลส่วนบุคคลของเราในรูปแบบใหม่ แทนที่จะพึ่งพากฎหมายใหม่และรัฐบาลมากขึ้น Chaum มองหาทางออกทางด้านเทคนิค และทางออกเหล่านี้ต้องพึ่งพาศาสตร์โบราณที่ทุ่มเทให้กับการรักษาความลับของข้อมูลนั่นคือ ศาสตร์การเข้ารหัส หรือ Cryptography
ศาสตร์การเข้ารหัส (Cryptography) ศิลปะแห่งการเขียนความลับ นั้นได้รับการปฏิวัติในช่วงสองทศวรรษที่ผ่านมา ซึ่งเป็นการปฏิวัติที่จุดประกายโดย การประดิษฐ์ศาสตร์การเข้ารหัส "Public-key" นักวิทยาศาสตร์คอมพิวเตอร์ ได้ต่อยอดออกไปในทิศทางต่างๆมากมาย โดยอาศัยเทคโนโลยีนี้ เพื่อผลักดันขอบเขตของความลับและความเป็นส่วนตัวไปสู่พื้นที่ใหม่ๆ การประยุกต์ใช้ศาสตร์การเข้ารหัสในรูปแบบใหม่นั้น ให้ความหวังว่ามันจะสามารถหลีกเลี่ยงอันตรายที่กล่าวถึงข้างต้นได้
แนวทางของ Chaum ในการคุ้มครองความเป็นส่วนตัว สามารถแบ่งออกเป็น 3 Layers Layers แรกคือ Public-key cryptography ซึ่งจะปกป้องความเป็นส่วนตัวของข้อความ แต่ละรายการ Layers ที่สองคือ Anonymous messaging ซึ่งช่วยให้ผู้คนสามารถสื่อสารผ่านจดหมายอิเล็กทรอนิกส์ได้โดยไม่ต้องเปิดเผยตัวตนที่แท้จริง และ Layers ที่สามคือ Electronic money ซึ่งจะทำให้ผู้คนสามารถไม่เพียงแค่สื่อสารระหว่างกันได้เท่านั้น แต่ยังสามารถทำธุรกรรมผ่านเครือข่ายคอมพิวเตอร์ด้วยความเป็นส่วนตัวได้ในระดับเดียวกันกับการใช้เงินสด
หากคุณเข้าไปในร้านค้าและซื้อสินค้าด้วยเงินสด จะไม่เหลือบันทึกใด ๆ ที่ผูกมัดคุณกับการทำธุรกรรม เมื่อไม่มีบันทึก ก็ไม่มีอะไรที่จะต้องนำเข้าไปในระบบฐานข้อมูลคอมพิวเตอร์ เป้าหมายของ Electronic money คือการอนุญาตให้ธุรกรรมส่วนตัวประเภทเดียวกันนี้ (การทำธุรกรรมคล้ายการใช้เงินสด) เกิดขึ้นได้บนระบบอิเล็กทรอนิกส์
(ยังมีข้อเสนออื่นๆ สำหรับ "เงินอิเล็กทรอนิกส์" ที่ไม่ได้ให้การคุ้มครองความเป็นส่วนตัวของบุคคลมากนัก ข้อเสนอของ Chaum มีเจตนาที่จะรักษาคุณสมบัติด้านความเป็นส่วนตัวของเงินสด ดังนั้นจึงเหมาะสมที่จะเรียกว่า "เงินสดดิจิทัล" แต่ตัวเลือกอื่นๆของเงินอิเล็กทรอนิกส์นั้น ไม่เพียงขาดความเป็นส่วนตัว แต่เอื้อต่อการเฝ้าติดตามทางคอมพิวเตอร์ โดยการนำข้อมูลที่ละเอียดมากขึ้นไปบันทึกในฐานข้อมูล และหันเหผู้คนไปจากการใช้เงินสด หากคุณได้พบเจอเงินอิเล็กทรอนิกส์อื่นๆ ให้ตรวจสอบดูว่า ระบบมีความสามารถในการรักษาความเป็นส่วนตัวของธุรกรรมทางการเงินแบบเดียวกับที่เงินสดทำได้อยู่หรือไม่ หากไม่เป็นเช่นนั้น ข้อเสนอดังกล่าวได้รับการออกแบบมาเพื่อทำลายความเป็นส่วนตัว ไม่ใช่เพื่อเพิ่มความเป็นส่วนตัวของแต่ละบุคคล)
จากบทความต้นฉบับ Protecting Privacy with Electronic cash by Hal Finney แปลและเรียบเรียงโดย Siamstr Update ตีพิมพ์ในนิตยสาร Extropy Magazine ปี 1993
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ d830ee7b:4e61cd62
2024-05-17 13:16:38
@ d830ee7b:4e61cd62
2024-05-17 13:16:38รัฐบาลโกงยังไง? หนังสือเล่มนี้แฉหมด!
เชื่อไหมว่า.. พวกเราโดนรัฐบาลหลอกมาตลอดชีวิต?
เออ.. ผมไม่ได้หมายถึงเรื่องลึกลับ Aliens หรือ Illuminati อะไรนั่นนะ ผมหมายถึงเรื่องใกล้ตัว เรื่องเศรษฐกิจนี่แหละ!
เคยรู้สึกไหมว่า.. นโยบายรัฐบาลแม่งออกมายังไงก็ไม่เห็นจะดีขึ้น ว่างงานก็ยังเยอะ ของก็แพง แต่ภาษีแม่งก็ขึ้นทุกปี แล้วไอ้พวกนักเศรษฐศาสตร์ที่ออกมาพูด ๆ ก็เหมือนจะเข้าข้างรัฐบาลตลอด พูดแต่เรื่อง GDP เงินเฟ้อ ดอกเบี้ย แต่ไม่เคยพูดถึงความจริงที่ว่าชีวิตชาวบ้านอย่างเรามันยากลำบากขึ้นทุกวันๆ สรุปคือเรา "รากหญ้า" นี่แหละที่ต้องแบกรับมันทุกอย่าง
ผมเอง.. นอกจากจะสนใจเรื่อง Bitcoin ผมยังแอบสนใจในเศรษฐศาสตร์แนว Austrian School มานานละ เพราะรู้สึกว่ามันค่อนข้าง "Real" ดี มันไม่ใช่แค่ทฤษฎีเลื่อนลอยหรือสูตรคำนวณเว่อร์ ๆ แบบที่พวก Keynesian ชอบใช้ Austrian Economics มันมองคน มองความเป็นจริง มองผลกระทบระยะยาว ไม่ใช่แค่แก้ปัญหาเฉพาะหน้าเหมือนที่รัฐบาลชอบทำ
ผมได้อ่านพรีวิวเนื้อหาในหนังสือชื่อว่า "Economics in One Lesson" เขียนโดย เฮนรี แฮซลิตต์ (Henry แฮซลิตต์) ตอนแรกเห็นชื่อก็คิดว่าคงเป็นตำราเศรษฐศาสตร์น่าเบื่อๆ อีกล่ะ แต่พอเปิดอ่านเท่านั้นแหละ.. เหมือนโดนแฮซลิตต์ตบหน้า (ในเชิงความคิด) ทุกบท ทุกตัวอย่าง มันทำให้ผมตาสว่าง และเข้าใจว่าสิ่งที่รัฐบาลชอบทำเนี่ย มันไม่ได้ช่วยเศรษฐกิจจริง ๆ หรอก แต่เป็นการซุกปัญหาไว้ใต้พรมแล้วโยนบาปให้ประชาชนอย่างเรา ๆ
แฮซลิตต์ไม่ได้แค่ด่ารัฐบาลลอยๆ นะครับ เขายังได้อธิบายอย่างเป็นเหตุเป็นผล ยกตัวอย่างชัดเจน เขาแฉหมดไม่ว่าจะเป็นเรื่องภาษี เรื่องการควบคุมราคา นโยบายงานสาธารณะ สวัสดิการสังคม การพิมพ์เงิน การอุ้มธุรกิจ ฯลฯ อ่านแล้วเราจะรู้เลยว่ารัฐบาลมันเล่นกลหลอกลวงประชาชนยังไง และ Austrian Economics มองเรื่องพวกนี้ต่างจาก Keynesian ยังไง
ผมนี่อยากจะตะโกนดัง ๆ ว่า "พวกมึง (รัฐบาล) แม่งโกงว่ะ!"
แต่ก็ทำได้แค่เห็นดีเห็นงามให้ อ.ขิง ไปแปลมันซะ อยากให้เพื่อนๆ ได้อ่านหนังสือดีๆ แล้วตัวเองก็มานั่งเขียนบทความรีวิวนี้แหละครับ (ฮา)

แฮซลิตต์ตบหน้าเคนส์ด้วย "One Lesson"
ความรู้สึกแรกที่อ่าน Economics in One Lesson เนี่ย...
ผมเหมือนโดน แฮซลิตต์ ตบหน้าชา ๆ เลยครับ (แต่เป็นการตบหน้าเชิงความคิดนะ ไม่ใช่ตบจริง ๆ ) เพราะตลอดชีวิต ผม (และเชื่อว่าอีกหลาย ๆ คน) น่าจะถูกทำให้เข้าใจมาแบบ Keynesian ตลอด คือ รัฐบาลต้องเข้ามาแทรกแซงเศรษฐกิจ ต้องกระตุ้นการใช้จ่าย ต้องพิมพ์เงิน ต้องมีสวัสดิการ เพื่อให้เศรษฐกิจมันเดินหน้าต่อไปได้
แต่พอมาเจอหนังสือของแฮซลิตต์และแนวคิด Austrian Economics เท่านั้นแหละ เหมือนโลกทัศน์ทางเศรษฐกิจของเราถูกพลิกกลับด้าน แฮซลิตต์เขาตบหน้าความเชื่อแบบ Keynesian ด้วยหลักการง่าย ๆ แค่ข้อเดียวที่เขาเรียกว่า "One Lesson" ซึ่งเป็นหลักการที่โคตรจะ "Common Sense" แต่กลับถูกมองข้ามไปอย่างหน้าตาเฉย นั่นคือ.. เวลาเรามองนโยบายเศรษฐกิจอะไรก็ตามเราต้องมองให้ครบ อย่ามองแค่ผลกระทบระยะสั้น หรือผลกระทบต่อคนกลุ่มใดกลุ่มหนึ่ง แต่ต้องมอง "ผลกระทบระยะยาว" และ "ผลกระทบต่อทุกกลุ่ม" ซึ่ง แฮซลิตต์เรียกผลกระทบที่เรามองไม่เห็นหรือมองข้ามไปว่า "ผลกระทบรอง"
ยกตัวอย่างง่าย ๆ แบบที่แฮซลิตต์เขาชอบยก คือ เรื่อง "หน้าต่างแตก"
ลองนึกภาพตามนะครับ.. สมมติมีเด็กเกเรปาหินใส่หน้าต่างร้านค้าแตก คนทั่วไปก็จะเห็นว่า เออ.. อย่างน้อยช่างกระจกก็ได้งาน เศรษฐกิจก็หมุนเวียน แต่แฮซลิตต์เขาชี้ให้เห็นว่า.. นั่นเป็นการมองแบบผิวเผิน เพราะสิ่งที่เรามองไม่เห็น คือ เจ้าของร้านต้องเสียเงินซ่อมหน้าต่าง ซึ่งเงินจำนวนนั้นเขาอาจจะเอาไปซื้อของอย่างอื่น เช่น อาจจะซื้อจักรยานใหม่ ซึ่งการซื้อจักรยานมันอาจจะสร้างประโยชน์ต่อเศรษฐกิจมากกว่าการซ่อมหน้าต่างก็ได้ ใครจะรู้?
เห็นภาพไหมครับ? Keynesian นั้นมองแค่ปลายจมูก เห็นแค่ว่าช่างกระจกจะได้งาน แต่แฮซลิตต์เขามองภาพรวม มองเห็นผลกระทบระยะยาว มองเห็นว่าเจ้าของร้านเสียโอกาสที่จะได้ใช้จ่ายเงินไปกับสิ่งที่อาจจะสร้างประโยชน์มากกว่า
และด้วยหลักการ "One Lesson" นี้แหละ ที่แฮซลิตต์เขาเอาไปวิพากษ์วิจารณ์นโยบายรัฐบาลแทบทุกอย่าง ไม่ว่าจะเป็นนโยบายงานสาธารณะที่รัฐบาลมักจะบอกว่าสร้างขึ้นมาเพื่อสร้างงาน กระตุ้นเศรษฐกิจ แต่แฮซลิตต์ก็แฉว่า จริง ๆ แล้ว เงินที่เอามาสร้าง มันมาจากภาษี ซึ่งแปลว่าภาคเอกชนมีเงินลงทุนน้อยลง สุดท้ายก็ไม่ได้สร้างงานเพิ่ม แค่ย้ายงานจากที่นึงไปอีกที่นึงเท่านั้น
หรือจะเป็นเรื่องการควบคุมราคา ที่รัฐบาลมักจะบอกว่าทำไปเพื่อช่วยเหลือผู้บริโภค แฮซลิตต์ ก็ออกมาแฉว่าการกำหนดเพดานราคามันไม่ได้แก้ปัญหา แต่กลับทำให้สินค้าขาดตลาด เกิดตลาดมืด และเราภาพสินค้าแย่ลง ที่สำคัญคือมันเป็นการทำลายกลไกตลาดที่ควรจะปรับตัวได้เองโดยธรรมชาติ
แฮซลิตต์ยังวิจารณ์นโยบายภาษีที่รัฐบาลบอกว่าเก็บไปเพื่อพัฒนาประเทศ แต่แฮซลิตต์ชี้ให้เห็นว่า “ภาษีที่สูง” มันเป็นการลงโทษคนขยัน ทำลายแรงจูงใจในการทำงานและทำให้เศรษฐกิจเติบโตช้าลง รวมถึงเรื่องสวัสดิการ ที่รัฐบาลชอบบอกว่าต้องมีเพื่อช่วยเหลือคนยากจน แฮซลิตต์ก็แฉว่า สวัสดิการที่มากเกินไป ทำให้คนไม่อยากทำงาน กลายเป็นภาระของรัฐบาล และสุดท้ายก็ล้มละลาย
นี่ยังไม่หมดนะครับ.. แฮซลิตต์เขายังวิจารณ์อีกหลายเรื่อง ไม่ว่าจะเป็นการพิมพ์เงิน การอุ้มธุรกิจ การกีดกันทางการค้า ฯลฯ
แม้ว่า แฮซลิตต์ จะเขียน “Economics in One Lesson” ตั้งแต่ปี 1946 แต่เนื้อหามันก็ยัง Relevant กับโลกทุกวันนี้ เพราะรัฐบาลทั่วโลกก็ยังคงใช้นโยบายแบบเดิม ๆ หลอกลวงประชาชนแบบเดิม ๆ ผมอ่านแล้วอยากจะเอาหนังสือ Economics in One Lesson ไปปายัดหน้าคนพวกนี้สักสิบรอบ เผื่อจะตาสว่างขึ้นมาบ้าง

อาวุธลับ Austrian Economics ปี 2024
ทีนี้พอพูดถึง Austrian Economics หลายคนอาจจะงงๆ ว่ามันคืออะไร เกี่ยวอะไรกับ Bitcoin เกี่ยวอะไรกับแฮซลิตต์ และเกี่ยวอะไรกับเราในปี 2024 (และปีต่อๆ ไป) ผมจะเล่าแบบง่ายๆ ให้ฟังละกันนะครับ
”Austrian Economics” มันเป็นสำนักคิดทางเศรษฐศาสตร์ที่เน้น "Logic" เป็นหลัก คือ ใช้ตรรกะ เหตุผลในการวิเคราะห์ ไม่ใช่ใช้สูตรคำนวณ ไม่ใช้แบบจำลองหรือสถิติอย่างที่ที่ Keynesian ชอบใช้
Austrian Economics มองว่าเศรษฐกิจมันซับซ้อนเกินกว่าที่จะยัดลงในสมการ และสิ่งสำคัญคือการเข้าใจ "Human Action" หรือ พฤติกรรมของมนุษย์ เพราะมนุษย์แต่ละคนจะมีแรงจูงใจ ความต้องการ และความรู้ ที่แตกต่างกัน ซึ่งส่งผลต่อการตัดสินใจทางเศรษฐกิจของพวกเขา
นอกจากนี้ Austrian Economics ยังเน้น "Individualism" หรือ ความสำคัญของปัจเจกชน มองว่าเศรษฐกิจมันขับเคลื่อนด้วยการตัดสินใจของปัจเจกชน ไม่ใช่การควบคุมจากส่วนกลางหรือรัฐบาล ซึ่งตรงนี้แหละที่ทำให้ Austrian Economics เชื่อมโยงกับ Bitcoin อย่างมาก
เพราะ Bitcoin มันคือ "Sound Money" ที่ไม่มีใครควบคุม มันเป็น Decentralized คือ กระจายอำนาจ ไม่มีใครสามารถพิมพ์เงินเพิ่มได้ตามใจชอบเหมือนเงิน Fiat ที่รัฐบาลควบคุม และสิ่งนี้มันสอดคล้องกับปรัชญาของ Austrian Economics ที่เชื่อใน ”Free Market” หรือ ”ตลาดเสรี” ที่ปัจเจกชนมีอิสระในการตัดสินใจ โดยไม่ต้องถูกแทรกแซงจากรัฐบาล
ถ้าจะเปรียบเทียบ Keynesian กับ Austrian Economics แบบเห็นภาพ Keynesian มันเหมือนหมอที่พยายามควบคุมร่างกายของเราด้วยการให้ยา ผ่าตัด หรือบังคับให้เราทำตามคำสั่ง ส่วน Austrian Economics มันเหมือน "ภูมิคุ้มกัน" ของร่างกาย ที่ปล่อยให้ร่างกายจัดการตัวเอง ซ่อมแซมตัวเอง โดยไม่ต้องพึ่งหมอมากนัก
และหนังสือของแฮซลิตต์นี่แหละ ที่เป็นเหมือน "วัคซีน" ฉีดภูมิคุ้มกันความรู้แบบ Austrian Economics ให้กับเรา ทำให้เราเข้าใจหลักการพื้นฐานและวิธีมองเศรษฐกิจแบบ Austrian
ตัวอย่างเช่น เรื่องเงินเฟ้อที่ Keynesian มองว่าเป็นสิ่งจำเป็นเพื่อกระตุ้นเศรษฐกิจ แต่ Austrian Economics มองว่าเงินเฟ้อเป็น "ขโมย" ที่ขโมยอำนาจซื้อของเรา ทำให้เราจนลงโดยที่เราไม่รู้ตัว
หรือเรื่องการว่างงานที่ Keynesian มองว่ารัฐบาลต้องเข้ามาแก้ไข ด้วยการสร้างงานสาธารณะ หรือ แจกเงิน แต่ Austrian Economics มองว่าการว่างงานเกิดจาก "Wage Rigidity" หรือ ”ค่าจ้างที่ไม่ยืดหยุ่น” ส่วนใหญ่เป็นเพราะสหภาพแรงงานหรือกฎหมายค่าแรงขั้นต่ำที่ทำให้ค่าจ้างสูงเกินไป จนผู้ประกอบการไม่สามารถจ้างงานได้
จะเห็นได้ว่า Austrian Economics มันมองต่างจาก Keynesian ในหลาย ๆ เรื่อง และหนังสือของแฮซลิตต์ มันเป็นจุดเริ่มต้นที่ดีที่จะทำให้เราเข้าใจ Austrian Economics ได้มากขึ้น
ผมอยากแนะนำให้ทุกคนที่สนใจ Bitcoin เศรษฐศาสตร์ หรือ การเมือง ลองศึกษา Austrian Economics กันดูครับ เพราะมันจะทำให้เราเข้าใจโลก เข้าใจเศรษฐกิจ และเข้าใจตัวเองมากยิ่งขึ้น และที่สำคัญมันจะทำให้เรารู้ทัน และไม่โดนรัฐบาลหลอกเอาง่ายๆ

อ่านแล้วได้อะไร? ทำไมต้องอ่าน?
เอาล่ะ มาถึงตรงนี้ หลายคนอาจจะคิดว่า "แล้วหนังสือเล่มนี้มันจะให้อะไรกับเราวะ?"
"ทำไมเราต้องอ่าน?" "มันจะช่วยให้ชีวิตเราง่ายขึ้น รวยขึ้น หรือหล่อขึ้นไหม?" (ฮา)
ผมบอกเลยว่าหนังสือเล่มนี้ มันไม่ใช่แค่ตำราเศรษฐศาสตร์น่าเบื่อ ๆ ที่สอนแต่ทฤษฎี ตัวเลข หรือสมการที่ทำให้เราหลับคาหนังสือ แต่แฮซลิตต์เขาเขียนแบบเข้าใจง่าย ยกตัวอย่างใกล้ตัวเหมือนกำลังนั่งคุยกับเรา เล่าเรื่องเศรษฐกิจแบบ "Common Sense" ให้เราฟัง
สิ่งแรกที่เราจะได้จากหนังสือเล่มนี้ คือ "ความรู้" ทางเศรษฐศาสตร์ที่ถูกต้อง แม่นยำ และ "ใช้ได้จริง" ไม่ใช่ความรู้แบบท่องจำหรือแค่ทฤษฎีเลื่อนลอย แฮซลิตต์จะพาเราดำดิ่งสู่โลกของ Austrian Economics ซึ่งจะทำให้เราเข้าใจ "Human Action" ที่เป็นตัวขับเคลื่อนเศรษฐกิจ ไม่เหมือน Keynesian ที่มองเศรษฐกิจแบบ "Top-down" คือ รัฐบาลต้องเข้ามาควบคุม แทรกแซง แต่ Austrian Economics นั้นมองแบบ "Bottom-up" คือ เศรษฐกิจมันขับเคลื่อนด้วยการตัดสินใจของปัจเจกชน
และแฮซลิตต์ก็สอนให้เรามอง "ผลกระทบระยะยาว" ของนโยบายซึ่งเป็นสิ่งที่รัฐบาลมักจะมองข้ามหรือจงใจไม่พูดถึง รัฐบาลชอบโฆษณาชวนเชื่อ พูดถึงแต่ผลประโยชน์ระยะสั้นแต่ไม่เคยพูดถึงผลเสียระยะยาว แฮซลิตต์จะสอนให้เรา "มองทะลุ" มายาคติและเห็น "ความจริง" ที่รัฐบาลพยายามปกปิด
นอกจากความรู้แล้ว หนังสือเล่มนี้ยังเป็น "เครื่องมือ" วิเคราะห์นโยบายเศรษฐกิจ ทำให้เรามองทะลุกลโกงของรัฐบาล รู้ทันว่านโยบายแต่ละอย่างมันมีผลกระทบที่แท้จริงอย่างไร อย่างการพิมพ์เงิน ที่รัฐบาลชอบทำเวลาเศรษฐกิจแย่โดยอ้างว่าเป็นการกระตุ้นเศรษฐกิจ แต่แฮซลิตต์จะทำให้เราเห็นว่า การพิมพ์เงินมันไม่ได้สร้างความมั่งคั่ง แต่เป็นการ "ขโมย" อำนาจซื้อจากประชาชน ทำให้เงินเฟ้อ ของแพง และชีวิตความเป็นอยู่ยากลำบากขึ้น
ที่สำคัญที่สุด หนังสือเล่มนี้จะ "เปลี่ยนวิธีมองโลก" ของเรา ทำให้เรามองเห็นความเชื่อมโยง มองเห็น "Big Picture" ของระบบเศรษฐกิจ ทำให้เราเข้าใจว่าการแทรกแซงของรัฐบาลมักจะนำไปสู่ผลลัพธ์ที่ "เลวร้าย" ยิ่งกว่าเดิม และ "ตลาดเสรี" ต่างหากที่เป็นกลไก "ธรรมชาติ" ที่สมดุลและช่วยสร้างความเจริญรุ่งเรืองได้อย่างยั่งยืน
ถ้าเราเป็นคนที่สนใจ Bitcoin เศรษฐศาสตร์ หรือ การเมือง ผมบอกเลยว่า Economics in One Lesson เป็นหนังสือที่เรา "ต้องอ่าน" เพราะมันจะทำให้เรา "ฉลาด" ขึ้น ไม่ใช่แค่ฉลาดแบบท่องจำ แต่ฉลาดแบบ "เข้าใจ" "คิดเป็น" "วิเคราะห์เป็น" และ "ตัดสินใจได้อย่างชาญฉลาด"
มันเหมือนแฮซลิตต์กำลังยื่น "อาวุธลับ" ให้กับเรา เพื่อต่อสู้กับ "ความโง่เขลา" ของรัฐบาลและ "ความไม่รู้" ของตัวเราเอง
เพราะ "ความรู้" ก็คือ อำนาจ และ Economics in One Lesson คือ หนังสือที่จะมอบ "อำนาจ" นั้นให้กับเรา
ลองถามตัวเองดูครับว่าเราอยากเป็น "เหยื่อ" ที่ถูกหลอกโดยรัฐบาล หรือ อยากเป็น "ผู้รู้" ที่มองทะลุกลโกงและสามารถตัดสินใจเลือกทางเดินชีวิตได้อย่างชาญฉลาด
ถ้าอยากเป็น "ผู้รู้" แฮซลิตต์และหนังสือเล่มนี้รอเราอยู่ครับ (รอ อ.ขิง แปลให้เสร็จก่อนด้วย)

ส่งท้าย
เฮ้อ... เขียนมาซะยาวเลย เหนื่อยเหมือนกันนะครับเนี่ย (ทำไมต้องเขียนยาวตลอดด้วย)
ใครที่สนใจเรื่องเศรษฐศาสตร์ การเมือง Bitcoin หรือ Austrian Economics ลองหาต้นฉบับหนังสือ Economics in One Lesson มาอ่านกันดูนะครับ หรือจะรอฉบับแปลไทยของ อ.ขิง ของเราก็ได้ รับรองว่าไม่ผิดหวังแน่นอน
ถ้าอยากติดตามบทความ Long-form อื่นๆ ของผม ก็สามารถติดตามได้ที่ รวมบทความ Long-form ของ Jakk และถ้าชอบผลงานของผม อยากสนับสนุน ก็สามารถ Zap กันได้เลยตามอัธยาศัยครับ (ไม่เคยพูดอะไรแบบนี้มาก่อนเลยนะเนี่ย)
ผมเชื่อในปรัชญา ”Value for Value” คือ ถ้าเราได้รับเราค่าจากงานของผม เราก็สามารถตอบแทนได้ด้วยมูลค่าที่เราเห็นสมควร
เอาล่ะ.. ส่งท้ายละ..
หลายคนอาจสงสัยว่า ไอ้ที่แฮซลิตต์เขาเขียนวิจารณ์รัฐบาลเนี่ย มันเกี่ยวกับ Keynesian ยังไง?
เอาจริงๆ คือ แฮซลิตต์ เขาไม่ได้ใช้คำว่า "โกง" ตรงๆ หรอกนะครับ แต่วิธีที่เขาอธิบาย วิเคราะห์ และยกตัวอย่างผลกระทบของนโยบายรัฐบาล มันทำให้เห็นชัดเลยว่า นโยบายแบบ Keynesian เนี่ย มันไม่ได้ช่วยเศรษฐกิจจริง ๆ แถมยังสร้างความเสียหายระยะยาวอีกต่างหาก
แฮซลิตต์ เขาเชื่อว่ารัฐบาลไม่ควรยุ่งกับเศรษฐกิจมาก ควรแค่สร้างกฎกติกาให้เป็นธรรม แล้วปล่อยให้ตลาดมันทำงานของมันไป (Leissez faire)
แต่แน่นอน.. นี่เป็นมุมมองของแฮซลิตต์ซึ่งเป็น Austrian School ที่วิจารณ์ Keynesian มันก็มีนักเศรษฐศาสตร์อีกหลายคนที่เห็นต่างและเชื่อว่า Keynesian เป็นทางออกของเศรษฐกิจ (เราได้ยินได้เห็นกันบ่อยแล้ว)
สุดท้าย ใครจะถูก ใครจะผิด ก็อยู่ที่มุมมองและการตีความของแต่ละคนครับ
ปล.
- ใครที่อ่าน Economics in One Lesson จบแล้ว อยากต่อยอดความรู้ แนะนำให้อ่าน “Human Action” ของ Ludwig von Mises ครับ เป็น "ตำราแม่" ของ Austrian Economics เลย
- ส่วนตัวผมมองว่า Economics in One Lesson เป็นหนังสือที่ "เปลี่ยนมุมมอง" ผมเลย มันทำให้ผมมองโลก มองเศรษฐกิจ มองการเมือง ต่างไปจากเดิม และทำให้ผม "เข้าใจ" และ "คิดเป็น"
- สุดท้ายอยากฝากไว้ว่า การศึกษา การเรียนรู้ เป็นสิ่งสำคัญ อย่าหยุดที่จะ "ตั้งคำถาม" "ค้นคว้า" และ "พัฒนาตัวเอง" นะครับ เพราะ "ความรู้" คือ อำนาจ และ "อำนาจ" นั้น จะทำให้เราเป็น ”อิสระ”
เจอกันใหม่ บทความหน้าครับ! ✌️

ประโยคเด็ดจาก Economics in One Lesson ฉบับ Jakk Goodday 🔥
ในฉบับแปลของ อ.ขิง จะไม่เดือดขนาดนี้นะครับ เพราะภาษาต้นฉบับออกจะสุภาพ (อันนี้ผมแปลเอามันส์)
“The art of economics consists in looking not merely at the immediate but at the longer effects of any act or policy; it consists in tracing the consequences of that policy not merely for one group but for all groups.”
“แฮซลิตต์เขาสอนให้มองการณ์ไกล ไม่ใช่แค่ผล immediate แต่ต้องดู long-term impact ไม่ใช่แค่กลุ่มใดกลุ่มหนึ่ง แต่ต้องมองภาพรวม ทุกกลุ่ม ทุกคนแม่งโดนผลกระทบหมด!”
“The bad economist sees only what immediately strikes the eye; the good economist also looks beyond. The bad economist sees only the direct consequences of a proposed course; the good economist looks also at the longer and indirect consequences.”
“นักเศรษฐศาสตร์ห่วย ๆ แม่งเห็นแค่ "สิ่งที่ตาเห็น" แต่แฮซลิตต์สอนให้มอง "ทะลุปรุโปร่ง" เห็น "ผลกระทบรอง" ที่ซ่อนอยู่ ซึ่งแม่งสำคัญกว่าที่คิดเยอะ!”
“Everything we get, outside of the free gifts of nature, must in some way be paid for.”
“ไม่มีอะไรได้มาฟรี ๆ โว้ย! (ยกเว้นอากาศบริสุทธิ์ กับ ความรักจากแม่) ทุกอย่างมันมีต้นทุน แม้แต่ "ของฟรี" จากรัฐบาล สุดท้ายก็ต้องจ่ายด้วยภาษีอยู่ดี”
“Government “encouragement” to business is sometimes as much to be feared as government hostility.”
“รัฐบาลชอบ "อุ้ม" ธุรกิจ ซึ่งน่ากลัวกว่ารัฐบาล "ตี" ธุรกิจอีก เพราะ "อุ้ม" เนี่ย.. มันบิดเบือนตลาด ทำให้ธุรกิจอ่อนแอ และประชาชน "เสียหาย" ในระยะยาว”
“The belief that machines on net balance create unemployment … is the basis of many labor union practices. The public tolerates these practices because it either believes at bottom that the unions are right, or is too confused to see just why they are wrong.”
“สหภาพแรงงานชอบโทษ "เครื่องจักร" ว่าทำให้คนตกงาน ซึ่งแม่งโคตรไม่จริง เครื่องจักรมันช่วยเพิ่มผลผลิต ลดต้นทุน และสร้างงานใหม่ด้วยซ้ำ แต่คนส่วนใหญ่แม่งไม่รู้ หรือไม่ก็ "งง" จนไม่รู้จะเถียงยังไง”
“The drive for exports is exceeded only by the pathological dread of imports.”
“รัฐบาลชอบ "บ้าส่งออก" จริงๆ แล้ว การนำเข้ามันสำคัญกว่า เพราะมันทำให้เรามีของใช้ มีทางเลือก และมีชีวิตที่ดีขึ้น การส่งออกมันแค่ "จ่ายค่า" การนำเข้าเท่านั้น”
“Inflation is the autosuggestion, the hypnotism, the anesthetic, that has dulled the pain of the operation for him. Inflation is the opium of the people.”
“เงินเฟ้อแม่งเหมือน "ฝิ่น" หลอกให้เราเคลิ้ม ว่าเศรษฐกิจดี ทั้งที่จริงๆ แล้ว มันกำลัง "ขโมย" อำนาจซื้อของเรา ทำให้เราจนลงโดยไม่รู้ตัว”
“There is no more certain way to deter employment than to harass and penalize employers. There is no more certain way to keep wages low than to destroy every incentive to investment in new and more efficient machines and equipment."
“อยากให้คนตกงาน? ก็ไป "รังแก" นายจ้างสิ! อยากให้ค่าแรงต่ำ? ก็ไป "ทำลาย" แรงจูงใจในการลงทุนสิ!”
“The idea that an expanding economy implies that all industries must be simultaneously expanding is a profound error. In order that new industries may grow fast enough it is usually necessary that some old industries should be allowed to shrink or die.”
“เศรษฐกิจโต ไม่ใช่ว่าทุกอุตสาหกรรมต้องโต บางอุตสาหกรรมมันต้อง "ตาย" ไป เพื่อให้ "อุตสาหกรรมใหม่" มันเกิด แฮซลิตต์สอนให้ "ทำลายอย่างสร้างสรรค์" ”
“The whole argument for [the government] entering the lending business, in fact, is that it will make loans to people who could not get them from private lenders. This is only another way of saying that the government will take risks with other people’s money (the taxpayers’) that private lenders will not take with their own money.”
“รัฐบาลชอบ "แจกเงินกู้" แฮซลิตต์บอกว่า แม่งเอาเงินภาษีของเราไปแจก โดยที่ธนาคารเขายังไม่กล้าปล่อยกู้เลย เสี่ยง "เจ๊ง" สูง!”
“It is impossible, moreover, to control the value of money under inflation. For, as we have seen, the causation is never a merely mechanical one … Each person’s valuation of money is affected not only by what he thinks its value is but by what he thinks is going to be everybody else’s valuation of money.”
“เงินเฟ้อแม่งควบคุมยาก มันไม่ใช่แค่ "กลไก" แต่เป็น "จิตวิทยา" ล้วน ๆ คนกลัวเงินเฟ้อ เงินเฟ้อก็ยิ่งมา แม่งวนลูป!”
* “ In a free economy, in which wages, costs and prices are left to the free play of the competitive market, the prospect of profits decides what articles will be made, and in what quantities—and what articles will not be made at all.”*
“ตลาดเสรี กำไรคือ "ตัวกำหนด" ว่าจะผลิตอะไร เท่าไหร่ รัฐบาลอย่าเสือก! ปล่อยให้ตลาดมันจัดการตัวเอง”
“The first groups to receive the additional money will benefit the most. … The gains of the first groups of producers to benefit by higher prices or wages from the inflation are necessarily at the expense of the losses suffered by the last groups of producers that are able to raise their prices or wages.
“เงินเฟ้อ ไม่ได้กระทบทุกคนเท่ากัน กลุ่มแรกที่ได้เงินแม่ง "รวย" กลุ่มสุดท้าย "จน" แม่งโคตรไม่แฟร์!”
“The real causes of depression are … maladjustments within the wage-cost-price structure: maladjustments between wages and prices, between prices of raw materials and prices of finished goods, or between one price and another or one wage and another. … Not until these maladjustments are corrected can full production and employment be resumed.”
“เศรษฐกิจพัง เพราะ "ราคา" กับ "ต้นทุน" มันเพี้ยน! ต้องแก้ที่ต้นเหตุโว้ย ไม่ใช่ "พิมพ์เงิน”
-
 @ d830ee7b:4e61cd62
2024-05-16 13:04:49
@ d830ee7b:4e61cd62
2024-05-16 13:04:49P.S. This article is translated from my original Thai article, which you can read here: My original Thai article
Have you ever felt like you're running on a treadmill that's constantly tilting upward?
No matter how much you run, you never seem to get anywhere, and eventually, you just end up exhausted... That's exactly how many people feel in the traditional economic system.
Inflation eats away at the value of your money every day. Governments impose regulations on capital, ban this and that, force you to spend your money in ways they see fit, and then tax you heavily, as if they see citizens as "cash cows" to milk endlessly.
The money you work so hard for loses value every single day. You have to work harder to earn the same amount, and the government constantly monitors and controls our spending, erecting tax barriers that exacerbate inequality.
This is the world we're familiar with... a world where power is centralized in the hands of the government and financial institutions. They set the rules that control our money and determine our destiny.
If you're one of the people who are fed up with this system... then you've come to the right place!

From a Sinking Ship to a New World of Freedom
Back in 1997, two forward-thinking writers, James Dale Davidson and Lord William Rees-Mogg, wrote a book called "The Sovereign Individual." They saw the future and dared to tell us that the world was about to transition into the information age, an era where technology would disrupt everything... even "nation-states"!
It's a world where power will be decentralized, governments will weaken, and anyone can become "free" both financially and in how they live their lives. They called these individuals "Sovereign Individuals."
Sounds like science fiction from the early days of the internet, right? But in 2024... the world Davidson and Rees-Mogg envisioned is no longer a fantasy!
Think about it... every day we live more and more of our lives online. We work, shop, invest, and communicate across borders without intermediaries, without relying on the government. The internet has become like a new "borderless world", opening up opportunities for us to access information, connect with people, and generate income from all corners of the globe without being restricted by government rules or regulations.
As the book states, "The internet" will give rise to new businesses, new forms of work, and online communities that connect people worldwide. This aligns with their vision of "individuals" gaining more power in the information age.
Today, we see that the internet has created numerous opportunities for those who dare to be different and refuse to succumb to the system. People are working remotely, able to work from anywhere in the world (like the Right Shift team). Digital nomads travel the globe while working. E-commerce businesses thrive without physical storefronts.
The internet frees us from geographical limitations and allows us to connect with the world in ways never before possible. Isn't this the beginning of the "Sovereign Individual era"?
And Bitcoin is the crucial "weapon" for the Sovereign Individual in this age. It unlocks the shackles of the old financial system. You can send money to anyone in the world without going through banks, without worrying about exorbitant fees, and all while remaining safe from government interference.
It's like we have a "submarine" that helps us escape from a sinking ship!
But wait! Can a book written in the early days of the internet truly provide answers for the decentralized and technologically advanced world of Bitcoin?
The answer is... yes!
This book is still packed with sharp insights and powerful ideas that remain applicable in today's world.
Want to know what those insights are and how they can help you achieve financial freedom in the world of Bitcoin? Read the review in this article and look forward to the Thai translation by Piriya and his team in the near future!
Before we move on... some of you might be wondering, "What exactly is a Sovereign Individual?" It sounds grand and impressive, but is it really something attainable?
Literally translated, "Sovereign" means "supreme ruler," while "Individual" refers to a "single person."
Combining these two words, "Sovereign Individual" can be literally translated as "supreme individual ruler," which I'll simply refer to as "The Great Individual." It sounds like they're kings or emperors, right?
But hold on... the meaning of "Sovereign Individual" within the context of this book doesn't refer to ruling over others. It means having the "power" to shape one's own life.
Think of kings in ancient times... they held supreme power in their lands, free to enact laws, collect taxes, and control resources as they pleased. But the "Sovereign Individual" of this era doesn't desire that kind of power. What they seek is freedom and the power to control their own lives without being subject to any government or system.
They are the "kings" of their own kingdoms!
Davidson and Rees-Mogg believe that "technology" is the key to empowering "individuals." It helps us transcend geographical limitations, access information, and connect with people worldwide directly, without intermediaries.
For instance, Bitcoin allows us to conduct financial transactions without banks. The internet allows us to work, learn, and generate income from anywhere in the world. As individuals gain more power, the power of governments diminishes. This is what Davidson and Rees-Mogg predicted in their book, and it's becoming a reality today.
Therefore, a "Sovereign Individual" is someone who can control their own finances without relying on banks or government-issued currencies. They can generate income globally without being restricted by borders or government regulations. They can shape their own lives, choosing where to live, work, and how to spend their time.
They are "free individuals" who refuse to be "slaves" to the system!
Hopefully, you're starting to understand the meaning of "Sovereign Individual."
Now, are you starting to feel the desire to become one yourself?

27 Years On, the Predictions Still Hold True (Especially Regarding Bitcoin!)
When I revisited this book in 2024, I was once again amazed by the foresight of Davidson and Rees-Mogg, who accurately predicted major changes far in advance. First published in 1997, this book predicted the transition from the industrial age to the information age, which would revolutionize social and economic structures.
Comparing the world in 1997, when the internet was just emerging, to the world in 2024, where the internet has permeated every corner of the globe, we can see that many predictions in this book are coming true.
The most striking example is the exponential growth of digital technologies. Smartphones, high-speed internet, and AI have become part of our daily lives, transforming the way we live, work, and communicate worldwide.
The small smartphone in your hand has more processing power than the computer NASA used to send humans to the moon! You can access information, connect with people worldwide, work, learn, shop, and conduct financial transactions anytime, anywhere. Many people may not recall where we were before this book was published...
In 1997, the internet in Thailand was in its infancy and not as widespread as it is today. Average internet speeds were quite slow, typically using dial-up modem connections over telephone lines, with a maximum speed of around 56 kbps (kilobits per second). Downloading large files or streaming videos was difficult and time-consuming (back then, just downloading a jpeg image was cause for celebration).
As I write this article... I'm using a 1,000 MB (1,000,000 kbps) internet connection. That's about 17,857 times faster than the average internet speed in 1997, or a whopping 1,785,614%!
Back then, popular internet usage in Thailand revolved around BBS (Bulletin Board System), online forums where users could exchange information, chat, and download files. Email was also gaining popularity as a means of electronic communication. Websites were starting to emerge, though their numbers were limited, mainly belonging to government agencies, universities, and large companies.
Communication in those days was still predominantly traditional, relying on landline phones, letters, fax machines, and pagers (anyone remember those? They were small devices for receiving short messages, popular among teenagers and businesspeople at the time).
So there you have it... Davidson and Rees-Mogg foresaw that these technologies would be crucial tools for liberating "individuals" from the grip of the state and the traditional economic system. No longer would they need to rely on or be controlled by governments or large corporations.
The book explained that in the information age, power would flow into the hands of those who could effectively control and leverage information, which are the "individuals." And "artificial intelligence" (AI) is one of the technologies that will play a critical role in enabling these non-conformists to control and utilize vast amounts of information with ever-increasing efficiency.
In their book, Davidson and Rees-Mogg recognized the potential of AI in work, decision-making, and innovation. They believed that AI would become a vital tool for pioneers to work smarter, make accurate decisions, and innovate rapidly.
Today, we see AI increasingly integrated into our daily lives, such as using ChatGPT and Gemini for writing, translating, and content creation, using AI trading for data analysis and stock trading decisions, or employing AI-powered tools in various tasks like design, video editing, and music composition.
AI is the "artificial brain" that will help us transcend human limitations and another essential "weapon" that self-reliant individuals in the information age must possess.
One of the most notable predictions in this book is the emergence of "digital currencies," and in 2024, Bitcoin stands as a clear testament to this prediction. Bitcoin is a decentralized currency, free from the control of governments and central banks, enabling us to conduct financial transactions without intermediaries, without worrying about expensive fees...
and most importantly... it's safe from government interference or confiscation (at least for now). Bitcoin utilizes encryption technology, ensuring highly secure transactions that are difficult for governments to hack or trace.
Davidson and Rees-Mogg saw encryption as a vital "shield" for those seeking to escape the shackles of the information age, where governments and organizations constantly attempt to spy on and control our data.
They used examples like data encryption to protect personal information and financial transactions from government surveillance, providing us with "private space" in the digital realm. In today's world, data protection is even more crucial as our information is scattered across the internet, vulnerable to theft or misuse.
We see the use of data shields in various forms, like VPNs to encrypt data while browsing the internet, privacy coins like Monero and Zcash that prioritize transaction anonymity, and end-to-end encryption in messaging apps like WhatsApp and Signal.
Encryption is the "secret weapon" that helps us maintain privacy and security in the digital world, and another essential tool for those who defy the system.
Imagine living in a country with a highly controlling government that restricts freedoms and confiscates citizens' assets. How secure would you feel keeping your money in a bank? The emergence of Bitcoin provides an alternative. It allows anyone to truly own and control their own "money." Davidson and Rees-Mogg called this "financial secession," a crucial step in becoming self-determining individuals.
Beyond Bitcoin, the efforts to develop and utilize platforms like DeFi (Decentralized Finance) further exemplify Davidson and Rees-Mogg's vision. DeFi is poised to disrupt the traditional financial system with its intermediary-free financial platforms. Today, DeFi enables us to borrow, lend, exchange currencies, and invest in digital assets conveniently, quickly, and securely, bypassing the complex procedures and high fees of traditional banks or financial institutions (although DeFi, while intriguing, still has much to prove in the eyes of Bitcoin enthusiasts).
Davidson and Rees-Mogg didn't just focus on technology; they envisioned the impact on "people" and how lifestyles would change in the information age. Knowledge, skills, and adaptability would become more valuable assets than physical possessions.
Today, we see a growing number of young people choosing to become freelancers. They work online, generate income globally, and don't want to be tied down to any company or location. They have the freedom to choose their work, their working hours, and their workplaces. The book refers to these individuals as the "Nomad Class," a group of people who can live and work anywhere in the world.
Moreover, we see a migration of wealthy individuals and investors relocating to countries with more favorable laws and lower tax burdens. They no longer want to be "cash cows" for governments to exploit. They want to be "free individuals" who can control their assets and determine their own destinies. Examples include the significant number of wealthy individuals and entrepreneurs relocating to Singapore, Hong Kong, or Dubai, which offer business-friendly tax systems and robust economies.
All of this reflects the world Davidson and Rees-Mogg imagined, a world where the power of nation-states is being challenged and "Great Individuals" are rising to prominence. The world in 2024 proves that "The Sovereign Individual" is not just a science fiction novel, but a "blueprint" for the future that we must prepare for.

Why Bitcoin Is the "Weapon" of Those Who Seek to Shape Their Own Futures
In a world where technology is rewriting all the rules and borders are fading in the digital realm, the question arises: Is the power of nation-states still as strong as before?
The book suggests that in the information age, power will decentralize, governments will weaken, and "individuals" will play a larger role. They will have greater freedom to control their lives and assets. Bitcoin is a prime example of this shift. It's the "weapon" of those seeking liberation, unlocking the chains of the old financial system and paving the way to true financial freedom.
Even though the book was written in 1997, before Bitcoin's inception, its ideas surprisingly resonate with the philosophy of Bitcoin. Both emphasize "breaking free from government control" and "achieving financial independence." Davidson and Rees-Mogg foresaw that technology would lead to "decentralization" and empower "individuals" to have greater control over their lives.
The book explained that in the past, governments and financial institutions held control over the world's economic and financial systems. People had to rely on and accept the rules they set.
But in the digital age, technologies like "Bitcoin" have brought about a significant change. It allows anyone to own and control their "money" without intermediaries. Imagine a world where you don't have to rely on banks, where you don't have to worry about the government seizing your assets or controlling your finances... that's the world Bitcoin is slowly building.
Bitcoin operates on blockchain technology, a public ledger that records all transactions. This blockchain is distributed across a network of computers worldwide, making it impossible for anyone to control or alter the information.
There are three main characteristics of Bitcoin that align with the book's ideas:
Firstly, Bitcoin is a decentralized system with no central authority. No one can control, command, or seize your Bitcoin, whether it's a government, bank, or even Satoshi Nakamoto, the creator of Bitcoin. The Bitcoin network is spread globally, making it difficult to block or control, mirroring the book's mention of the decline of nation-states and the rise of "microstates." Bitcoin could be part of this transformation by becoming the "currency" of microstates or independent communities.
Secondly, Bitcoin offers privacy. Although Bitcoin transactions are recorded on the blockchain, a public ledger accessible to everyone, your personal information remains undisclosed. You can conduct transactions anonymously, echoing the book's emphasis on "privacy" in the information age. Bitcoin empowers you to control your personal data and conduct financial transactions without revealing your identity.
Lastly, Bitcoin is secure. Bitcoin utilizes cryptography to ensure security, making it difficult to forge or hack data. Just as the book highlights the importance of "asset protection," Bitcoin's security and resistance to hacking make it a trustworthy "asset" for freedom seekers.
These three characteristics make Bitcoin more than just "money." It's a tool that empowers you to be a sovereign individual in the digital world. Let's look at real-world examples of Bitcoin usage that reflect the "Sovereign Individual" concept.
In Venezuela, which faced hyperinflation, people turned to Bitcoin as a store of value to protect their assets. This echoes the book's warnings about the dangers of inflation and government control over currency. Migrant workers use Bitcoin to send money back home without paying exorbitant fees to Western Union, cutting out intermediaries and reducing costs, aligning with the book's concept of "cost reduction."
(Read more about Venezuela's story here > Why are Venezuelans seeking refuge in crypto-currencies? )
Furthermore, NGOs (Non-Governmental Organizations) and activist groups use Bitcoin to raise funds globally without being blocked or censored by governments. Therefore, Bitcoin is not just a "currency" but a symbol of "freedom." It's a tool that empowers you to shape your own financial destiny and truly be your own boss.
Take, for example, WikiLeaks, the media organization founded by Julian Assange, which publishes leaked government documents. Traditional banks and financial institutions blocked WikiLeaks from receiving donations. Consequently, WikiLeaks turned to Bitcoin as a means to accept donations, allowing the organization to survive and continue its work despite government pressure.
Or consider #EndSARS, the protest movement in Nigeria against the Special Anti-Robbery Squad (SARS) for its abuse of power. The Nigerian government froze the bank accounts of protesters, prompting them to use Bitcoin as a means to receive donations to support the movement and assist affected protesters.
Human rights groups like the Human Rights Foundation use Bitcoin as a channel to receive donations from supporters worldwide for their work in countries where freedoms are restricted. Humanitarian aid organizations operating in conflict zones or countries with unstable financial systems find Bitcoin to be a convenient, fast, and secure way to send aid.
For instance, in Syria, Bitcoin was used to deliver financial assistance to war victims. Similarly, during the 2019-2020 Hong Kong pro-democracy protests, numerous protesters and activists turned to Bitcoin to raise funds and evade tracking by the Chinese government.
In an era where Bitcoin is thriving and blockchain technology is reshaping the world, the ideas of Davidson and Rees-Mogg are becoming increasingly relevant. It serves as a reminder that true power is returning to the hands of "individuals."

Freedom... Doesn't Come with a Bonus
Of course, the path to becoming a "Sovereign Individual" or "Great Individual" is not paved with roses. Davidson and Rees-Mogg didn't just tell us about the good times; they also pointed out the obstacles and challenges that lie ahead.
It's like embarking on an adventure in a new land filled with treasures but also fraught with dangers at every turn. You must be prepared to face uncertainty and unseen enemies. One of the most significant challenges is the increased "responsibility" that comes with stepping away from the familiar and sometimes stifling traditional systems. We must be ready to truly become our own "bosses."
Imagine this... you might currently be an employee at a company where, despite a nagging boss and numerous rules, there's a system, benefits, and a steady paycheck every month. But if you choose to become a "free individual," you have to throw away those "crutches"!
There's no boss, no benefits, no regular salary. Everything depends solely on "you."
You have to make decisions, plan, and take responsibility for every action, from small things like time management to big things like investment, tax planning, and protecting yourself from various dangers. In this fast-paced world, continuous learning and self-development are indispensable. Pioneers must be like "explorers" who never stop learning and are always ready to adapt to change.
Because "knowledge" is the most powerful weapon in this new world.
Apart from the increased responsibility, the digital world, while full of opportunities, is also filled with "risks."
While blockchain technology and Bitcoin are known for their security and resistance to hacking, if you lose your private keys or accidentally click on a fake link, you could wave goodbye to your Bitcoin forever. Unlike being cheated by a bank where you might have a chance to recover your funds or file complaints with authorities, in the decentralized world... no one, not even the government, can help you!
You bear full responsibility for all losses.
Therefore, becoming a "self-determining individual" is not just about declaring independence and enjoying a carefree life. It demands "discipline" in managing your life, "knowledge" for making decisions, and "caution" in protecting yourself. It's like a mountain climber who must train rigorously, prepare equipment, and plan meticulously before ascending to the summit, because a single misstep could be fatal!
But the good news is... once you overcome these challenges, the rewards waiting for you are equally immense.
Financial freedom, control over your own life, and becoming the "king" of your own kingdom are the dreams envisioned in the book.
And the world in 2024 has proven that these are not mere fantasies!
Just look at Jack Dorsey, the former CEO of Twitter, who dared to resign from his company to pursue blockchain and Bitcoin full-time. He chose to leave his comfortable "golden cage" with its hefty salary to chase his dreams and build the world he believes in. This is the true spirit of a "self-determining individual."
This example demonstrates that...
Individual sovereignty is not just about "money" or "power," but about "belief," "vision," and "taking action."
And in 2024... this book still offers invaluable lessons we can apply.
First and foremost, we must be "forward-thinking." The world is changing rapidly, and free individuals cannot cling to old frameworks. They must be willing to constantly learn and adapt to change. Furthermore, taking control of your own finances is crucial. Don't let governments or financial institutions control your life. Instead, learn to manage your money and invest wisely. Remember that relying on a single income stream is risky.
Therefore... it's essential to explore new opportunities and create multiple income sources from around the world. Technology is a tool that empowers you to be free, so learn and utilize it to its fullest potential. And finally, dare to be different, dare to challenge yourself, dare to step out of your comfort zone, and carve your own path.
This is not just a book; it's an idea that sparks hope and inspiration for "free individuals" worldwide. It's a "blueprint" for the future, and you can choose to be a part of it.
Are you ready to step into the world of the "Sovereign Individual"?

A Final Call to Action...
"The Sovereign Individual" is a book that serves as a compass, offering a fresh perspective to guide us in this rapidly changing world.
Even after 27 years, the lessons and vision conveyed by Davidson and Rees-Mogg are even more powerful and relevant. It reflects the reality that the world is not static, power and systems are subject to the laws of change, and only those who adapt, learn, and control their own destinies can overcome volatility and seize opportunities in the future.
They didn't just highlight the "problems"; they also offered "solutions" by presenting "ideas" and "strategies" for becoming "freed from the shackles."
Their language isn't overly academic or heavy; it's a blend of storytelling, situational analysis, and future forecasting with an engaging, insightful, and often humorous style.
They compared governments to "mafia gangs" that extort taxes from citizens, likened the education system to a "human factory" that brainwashes people into obedience, and portrayed technology as a powerful "weapon" for liberating individuals from government control.
They didn't speak of these things in a vacuum but drew upon historical events, from Roman times, the Middle Ages, to the present day, analyzing them sharply and connecting them to future trends.
Powerful quotes in the book reflect their vision of technology challenging state power. Governments will not be able to control, dominate, or even touch the digital economy as they once did.
For example:
"The good news is that politicians will no more be able to dominate, suppress, and regulate the greater part of commerce in this new realm than the legislators of the ancient Greek city-states could have trimmed the beard of Zeus."
Or the line:
"Soon, the cows will have wings."
This is another example of their sharp and humorous writing style. It signifies the end of an era where governments could easily collect taxes from citizens. In the digital world, wealth will move freely and borderlessly.
And the line that serves as a "declaration" of a new age where beliefs, knowledge, and systems we once held dear are being challenged and crumbling:
"The future is disorder. A door like this has cracked open five or six times since we got up on our hind legs. It is the best possible time to be alive, when almost everything you thought you knew is wrong."
This book is packed with content that is both "provocative," "thought-provoking," and "inspiring." If you want to understand the world in ways that "the powers that be" don't want you to see and desire to become a "free individual" who can truly shape their own destiny...
"The Sovereign Individual" is a book you can't miss!
-
 @ 50c940b8:647e7d0b
2024-05-15 23:25:08
@ 50c940b8:647e7d0b
2024-05-15 23:25:08Hey there, it's The Million Bitcoin Wife your friendly relationship expert with some game-changing insights today🧡💊. Ever felt lost in the dating maze, unsure of your path to happiness? Fear not, I'm here to break you free from the Fiat dating matrix.
Let's talk rules – not the boring kind from a Fiat school, but ones that make your love life way better. Imagine a blueprint to romance and confidence.
Well, buckle up, because we're diving into the five rules of love and relationships💖
Rule 1: No Settling Allowed Picture this: your relationship is like a thriving Bitcoin wallet, constantly evolving and growing. Just like you wouldn't settle for mediocrity in your financial portfolio, why settle for anything less than extraordinary in your love life? 📈 🧡Don't let your relationship plateau; keep adding value, excitement, and intimacy like you're stacking sats. Because remember, stagnation is the enemy of true love.
Rule 2: Embrace the Masculine and Feminine Perspectives Understanding the masculine and feminine mindsets isn't just a skill; it's a superpower. Dive deep into the testosterone-fueled world of your man or the nurturing realm of womanhood, and watch as empathy becomes your secret weapon. When you can anticipate each other's needs and desires, you become each other's ultimate allies in the battle of love. 💑 Embrace the dance of polarity, where yin meets yang, and together, create a harmonious symphony of mutual understanding and unconditional love. https://cdn.satellite.earth/811ae1a36900334fe685ecdace4229a90874f55d775a289ce24887776355ef7c.jpg
Rule 3: Shed Your Insecurities Like a Bad Altcoin In the world of Bitcoin, "volatility is the price you pay for the performance". But just as you wouldn't invest in a shaky shipcoin, don't invest your emotional currency in insecurity. 💎 Let go of the masks you wear to fit in and rediscover the raw, unfiltered version of yourself. Your authenticity is your greatest asset in love.
Rule 4: Fill Your Cup First In the realm of Bitcoin, self-sovereign isn't just encouraged; it's essential. Treat yourself like the individual you are, indulging in acts of self-love 🧡 that replenish your spirit and nourish your soul. Remember, you can't pour from an empty cup, so make sure yours is overflowing with love, joy, and confidence.
Rule 5: Decisions Fueled by Faith, Not Fear When it comes to matters of the heart, fear is the ultimate buzzkill. 💔 Instead of letting fear dictate your decisions, lean into faith and trust that the universe has your back. Just as you'd HODL onto your Bitcoin through market dips, HODL onto your faith in love, knowing that every decision made from a place of love brings you one step closer to your moonshot moment. 🌙 https://cdn.satellite.earth/b345c93c3335a0d6a8d56bdd1ad8646f424f3303ad1ac3424366ba9a80c4f4b8.jpg
So there you have it, my fellow Bitcoin babes and relationship revolutionaries. 🚀💕 Armed with these five rules, you're not just navigating the dating world; you're dominating it with a fierce combination of wisdom, grace, and unyielding confidence.
Let's flip the script on the Fiat dating matrix and usher in a new era of love, one sat at a time. HODL onto your hearts, because the best is yet to come. 💖✨
With love, Anastasia - The Million Bitcoin Wife 🧡👰💜
-
 @ 0461fcbe:35a474dd
2024-05-15 21:06:49
@ 0461fcbe:35a474dd
2024-05-15 21:06:49nak is an awesome command-line tool written in Rust (jk, written in Go) for doing Nostr stuff. I use it on a daily basis to talk to relays and gather events.
Using nak, you can sync your data between one relay and another like this:
sh nak req -a <pubkey> <relay-1> | nak event <relay-2>For example:
sh nak req -a 0461fcbecc4c3374439932d6b8f11269ccdb7cc973ad7a50ae362db135a474dd wss://gleasonator.dev/relay | nak event wss://slime.church/relayThis downloads all data by the author (
-a) from relay 1, and pipes it into relay 2.Most relays only return about 100 events at a time, though. To sync everything you will need to implement some sort of pagination with
sinceanduntilfilters.Most commonly I just need to sync my profile data to a new relay, which can be done with the
-k(kind) flag. You can pass multiple-kflags, eg:sh nak req -k 0 -k 3 -k 10000 -k 10001 -k 10002 -k 10003 -a 0461fcbecc4c3374439932d6b8f11269ccdb7cc973ad7a50ae362db135a474dd wss://gleasonator.dev/relay | nak event wss://slime.church/relayThis will migrate your profile, your follow list, your relay list, your mute list, pinned posts, and your bookmarks to the new relay.
If you find yourself doing this often, you can drop a little alias in your bashrc/zshrc:
sh alias nsync="nak req -k 0 -k 3 -k 10000 -k 10001 -k 10002 -k 10003 -a 0461fcbecc4c3374439932d6b8f11269ccdb7cc973ad7a50ae362db135a474dd wss://gleasonator.dev/relay | nak event"Then you'll just
nsync <relay>to copy data from your main relay to another relay! -
 @ 955e5a04:c03b3cc3
2024-05-15 05:56:38
@ 955e5a04:c03b3cc3
2024-05-15 05:56:38"In what follows and in accordance with Nature, one should not complain against the gods, because neither voluntarily nor involuntarily do they lack anything, nor against men, because they do not err spontaneously in anything, so no one should be blamed." -Marco Aurelio
In a world driven by the frenzy of cryptocurrencies, where the market's volatility can send emotions on a rollercoaster ride, perhaps there's wisdom to be found in the ancient philosophy of Stoicism. Marcus Aurelius, the Stoic emperor, left us with profound insights in his "Meditations," urging us to embrace acceptance and eschew complaint, even in the face of adversity. Let's explore how these Stoic principles resonate in the realm of Bitcoin.
-
Accepting the Nature of Bitcoin: Just as Marcus Aurelius emphasized accepting events as they unfold according to nature, so too must we accept the nature of Bitcoi
-
Resilience Amidst Market Fluctuations: Stoicism teaches us to find tranquility amidst chaos. Similarly, in the volatile world of cryptocurrencies, maintaining a stoic mindset can help investors weather the storms of market fluctuations. Rather than being swayed by euphoria during bull markets or despair during bear markets, embracing stoic principles allows for a more resilient approach to investing in Bitcoin.
-
No Blame in Bitcoin: Marcus Aurelius reminds us not to blame the gods or humans for events beyond our control. Similarly, in the realm of Bitcoin, assigning blame for market movements or technological developments is futile. Whether it's regulatory crackdowns, technological glitches, or speculative frenzy, understanding that these are natural occurrences within the Bitcoin ecosystem can alleviate frustration and resentment.
-
The Virtue of HODLing: HODLing, a term derived from a misspelling of "hold" in a Bitcoin forum post, embodies the stoic virtue of endurance. Instead of succumbing to the temptation of short-term gains or panicking during market downturns, HODLers maintain a steadfast resolve, trusting in the long-term viability of Bitcoin.
-
Finding Freedom in Decentralization: Stoicism extols the virtue of inner freedom, unaffected by external circumstances. Similarly, Bitcoin's decentralized nature offers a form of financial sovereignty, free from the control of central authorities. Embracing Bitcoin means embracing this ethos of independence and self-reliance, echoing the stoic pursuit of inner tranquility.
In conclusion, the philosophy of Stoicism provides a powerful framework for navigating the unpredictable terrain of Bitcoin. By embracing acceptance, resilience, and inner freedom, investors can find serenity amidst the volatility and uncertainty of the cryptocurrency market. As Marcus Aurelius reminds us, in the grand scheme of things, there is no one to blame, and true wisdom lies in embracing events as they unfold, in harmony with nature.
-
-
 @ 4cd9c154:37287981
2024-05-15 02:30:11
@ 4cd9c154:37287981
2024-05-15 02:30:11
An initiative by architects in the city of Pomerode (SC) is mobilizing to start rebuilding the thousands of homes destroyed by the floods in Rio Grande do Sul. Called "ReconstruSUL", the campaign aims to collect building materials and furniture to be donated to the people of Rio Grande do Sul.
The initiative originated in the state of São Paulo, on the part of an architect from that state. And in Pomerode, professionals in this field decided to join in with the idea, to contribute their knowledge and contacts.

In an interview with Jornal de Pomerode, Petra Selke Volkmann, who is responsible for the campaign in Pomerode, and who has the support of the Pomerode Association of Engineers and Architects (Asseapo), said that she found out about the "ReconstruSUL" campaign while researching how she could help people who have lost everything.
"The idea arose from a feeling of helplessness, seeing the magnitude of the tragedy, with so many towns affected, and seeing people help, but it still seems to be too little, given everything that has happened in Rio Grande do Sul. So we started thinking about what it will be like when the water recedes, what the people who lost their homes will do. As an architect, I thought about how, in my profession, I could contribute"

According to Petra, the idea is to unite architects in each city, so that each one can set up a collection point and, with their partners, suppliers and clients, obtain new building materials that are surplus to requirements.

To help the campaign, those interested can donate, for example, bags of cement, valves, pipes, i.e. things that are not returned as building materials but are in good condition. Other materials that can be donated to the "ReconstruSUL" campaign are: window frames, pieces of wood for ceilings, roof timbers, demolition bricks, cement, coverings of all kinds, as well as plumbing and electrical equipment, paint, water tanks, circuit breakers, wiring, socket mirrors, switches, finishes, light bulbs, pipes, scyphons, toilets, taps, tubs, and furniture.
"Remember that everything needs to be in good condition, because people who have lost everything don't deserve to receive something damaged. Whoever receives it also deserves some comfort, some welcome, with things that we would use in our work"
-
 @ 32e18276:5c68e245
2024-05-14 16:46:28
@ 32e18276:5c68e245
2024-05-14 16:46:28Hey Damus enjoyers,
v1.8 has been tagged! Today we submitted v1.8 to the App Store, Here's a quick preview of what's in this release!
New Emoji Selector
It's now easier than ever to select emoji reactions! Just long press the reaction button to pop-up the new emoji selector. Thanks Terry for implementing this!

Quote Reposts
Quote reposts are now listed on posts, just like on the birdsite (x site ?)

New fullscreen video player
Our video controls were pretty bad before, this has been improved in this version! You can now seek videos, view them fullscreen, and airplay them to your tv. Thanks Daniel for this feature!

Improved longform style
Longform posts now show the image and related tags. Thanks Eric!

Account recovery, bug fixes
Thread loading is greatly improved, we now support the latest nip10 specification for improved compatibility between clients. We also added an account recovery feature called First Aid. You can use this to create a new contact list if for whatever reason you don't have one anymore. If you are running into issues following people, you can use this to recover your account:

Testflight
v1.9 dev is underway, with an up and coming highlighter feature where you can clip highlights from the web and other posts and share them to your feed. If you want to test out the latest up and coming features, make sure to grab a damus purple membership to get access!
https://damus.io/purple/login
That's all for now, here's the full changelog if you want to see what else is new!
Full Changelog
Added
- Added nip10 marker replies (William Casarin)
- Add marker nip10 support when reading notes (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Relay fees metadata (ericholguin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Show list of quoted reposts in threads (William Casarin)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Add ability to mute words, add new mutelist interface (Charlie)
- Add ability to mute hashtag from SearchView (Charlie Fish)
Changed
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Errors with an NWC will show as an alert (ericholguin)
- Relay config view user interface (ericholguin)
- Always strip GPS data from images (kernelkind)
Fixed
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Fix emoji reactions being cut off (ericholguin)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
-
 @ 20986fb8:cdac21b3
2024-05-14 04:27:58
@ 20986fb8:cdac21b3
2024-05-14 04:27:58Relay is the soul of the decentralized Nostr network. In previous articles, we discussed who would bear the ongoing operational costs of Relay. To ensure a thriving storage network, Relay needs to be incentivized. In order to achieve better decentralization of media, YakiHonne has launched the Relay's early incentive plan to support the development of 50 Relays for a period of 6 months.

The details of the grant program are as follows:
- Grant amount: A total of $50,000, with each grant ideally being $1000.
- Application period: From May 15, 2024, to December 31, 2024.
- Applicants: Existing Relay node hosts or new hosters, with a funding ratio of 20 existing Relay nodes and 30 new Relay nodes.
Relay operational requirements:
-
The minimum requirements for Relay deployment are according to [1]:
-
1.1. High performance Intel
- 1.2. 1 vCPU
- 1.3. 2048 MB Ram
- 1.4. 50 GB NVMe SSD
-
1.5. OS Ubuntu 22.04 LTS
-
There are no restrictions on storage service providers, and you can choose any stable provider.
-
There are no restrictions on the location of Relays, but it is recommended to have geographical diversity to maintain a balanced distribution of Relays.
- Relays need to operate continuously for the next 6 months with downtime not exceeding 30 minutes.
- You can choose from the already existed relays implementations: nostr-rs-relay based on Rust, nostr-ts-relay akk nostream using Typescript, or strfry using C++.
- Relay models can be of any type: thematic Relays relying on keyword filtering for specific topics, invitation-only Relays that restrict publishing permissions through public keys, or paid and free public Relays corresponding to paid publishing and fully open modes, respectively. However, to maintain a balanced incentive, the proportion of paid and invitation-only Relays will not exceed 20%.
- Monthly reports on Relay stability and availability need to be shared to maintain good operational status.
Application process:
You need to submit a proposal including whether you are already hosting a Relay, the name of the existing Relay, specifications of the Relay hosting service, possible service provider choices, Relay development environment, Relay model, and more details to help you secure funding.
Submission: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Grant Evaluation and Disbursement:
Within one week of receiving the application, we will provide feedback on the grant decision. The grant amount will be disbursed in two installments, with 50% being provided initially and the remaining 50% being disbursed after 3 months.
Rewards:
In the early incentive program, nodes that contribute consistently to improving Relay performance, expanding functionality, and ensuring stability will receive special rewards and have the opportunity to earn more income.
The goal of this incentive program is to further decentralize Nostr, enhance its performance, and promote the development of Relay functionality. Through the early incentive program, we aim to explore sustainable incentive models for Relays and lay the foundation for their sustainable development.
-
 @ df67f9a7:2d4fc200
2024-05-13 21:43:50
@ df67f9a7:2d4fc200
2024-05-13 21:43:50What I’m Building
Meet Me On Nostr is an app for sharing Nostr with friends. More than ‘just’ an onboarding client, this project will bring the power of “Social Onboarding” to Nostr. The project’s measurable objectives are to grow the number of new users, to increase the retention of active users, and to strengthen the interconnected webs of trusted users. All this can be accomplished “simply” by supporting Nostr advocates in sharing Nostr with their friends.
This project can be broken into two distinct efforts.
-
Web Client for “socially onboarding” new accounts (with customizable invite QR codes for advocates, low friction profile creation for friends, built in direct messaging with advocates, and WoT powered discovery of new friends, clients, relays, and other stuff recommended by the advocate and their web of trusted friends)
-
Advocate Support & Metrics to build community and incentivize users around onboarding and retaining their trusted friends on Nostr.
Why Social Onboarding?
Social Onboarding is Nostr’s superpower. Friends sharing Nostr with friends is not only easy and natural, but also happens to be a great way to strengthen Nostr’s webs of trusted users. While it’s not a given that Nostr’s growth will be sustainable, developing tools to support “networks of trusted friends” can only help.
Because Nostr is owned by nobody, anybody is able to benefit (monetarily or socially) from its success. Everybody wins when Nostr grows, but also, everybody wants something different. With Nostr, the superpower comes when everybody gets what they want. Harnessing #grownostr to support “networks of trusted friends” may be as simple as giving advocates the tools and incentives to “curate” their own corner of the broader social network.
Invite your trusted friends, and help them to stay a while.
Because there is no “sherif of Nostr”, traditional approaches to content moderation have no power. To overcome the growing influence of bots and bad actors, Webs of Trust is still the best (and only?) form of decentralized moderation. The challenge for onboarding, in this context, is to “rapidly on-ramp” new users into trusted networks, BEFORE the spambots ruin their vibe. Social Onboarding by Nostr advocates solves this problem, while being “relatively” straightforward to tool up and incentivize.
Development Timeline & Milestones
As of this writing, I have an “almost MVP complete” web client (alpha-0.4) running live at nostrmeet.me. MVP could be completed by the time of BTC Prague (3 weeks). Target Release may have an early release as soon as Nostriga, but will likely be feature complete by mid autumn (6 months)
Minimum Viable Product
When complete, the Minimum Viable Product will allow advocates to invite their friends to a direct message chat on Nostr with minimal “onboarding” friction. What’s live today, is the invite and profile creation, but lacking DM integration.
[+] Invite QR codes [+] Invite accept screen with “low friction” profile creation. [+] Automatic Nip05 addresses for new profiles. [+] Private “cloud encrypted” key storage using NIP46 (password not stored) providing key management for new profiles. [+] Receipt logging of accepted invites (allows tracking of account creation by web client through encrypted receipts) [+] Optional “do not store” encrypted key and “keep me anonymous” receipt logging. [+] Login to web client with “cloud encrypted” key using only username and password. Retrieve nsec (unencrypted key) anytime. [ ] Direct message integration for new accounts and their advocates.
Target Release
The Target Release (maybe as soon as Nostriga), will push forward on both efforts of this project (web client and advocate support) to solidify a “baseline” toolset to measure and implement Social Onboarding for Nostr.
[ ] Customizable Invites for Advocates (allowing for private invites, limited use invites, private group invites, follow a list from invite, join relays from invite, zap to ecash after invite, and other extendable options) [ ] WoT Network Explorer for new users to find new follows and trusted friends (and view their timelines) directly from the web client. [ ] WoT Recomendations for new users to discover (and launch or subscribe to) clients and relays (and other stuff?) right from the web client. [ ] Metrics and data collection to quantify the success of “social onboarding”, and what accounts are involved. [ ] Top Advocates Awards (using these data) to incentivize onboarding of new, active, and trusted users. [ ] Advocate Training and support (in the form of chat groups, hangouts, meetups, wikis, etc) to share best practices and tips for growing one’s own web of trusted friends.
Funding and Moving Forward …
So far, this is a passion project. Born from many hours conversation with and observation of Nostr advocates and new users.
In January 2024, I managed to secure a $10k seed sponsorship for MVP development from Blockhenge. I hope to continue funding this project through sponsorships from Nostr adjacent businesses.
Everybody wins when more trusted friends join Nostr.
I am currently looking for a dev assistant and funding to last us both through fall 2024. Please contact me directly if your business might be interested.
-
-
 @ 1bc70a01:24f6a411
2024-05-13 09:49:18
@ 1bc70a01:24f6a411
2024-05-13 09:49:18Thought 1: Content Creation, Discovery & Remixing
Recently I’ve been thinking about ways we could highlight nostr’s unique properties while at the same time attracting creators to the platform.
There’s been a lot of discussion about what might spark nostr’s next wave of growth. I pointed out that people come for either other people, or for content. But, I also failed to realize that people also seek ways to express themselves via new tools that enable easy or unique ways of expressing yourself.
One thing we can say with certainty is that people are not coming to nostr for other people. While generally following influencers is a proven growth strategy - after all, many of us followed Jack, we still have a catch 22 problem of lacking audience and incentives for those creators to come here. Even if we managed to convince some large influencers to try the platform, it is not likely that they would stay. They’d need to be really passionate about nostr’s principles and vision to buckle in for the long term.
Problem: creators and influencers won’t come to nostr unless they can grow their audience, and nostr lacks the audience. We’ve seen this play out with Matt Taibi. He joined nostr but was reluctant to stay because there’s little incentive to share with a small audience when Twitter/X can bring in many more eyeballs.
Possible Solution: Instead of brining creators to the platform, enable some of the current passionate user base to become decent creators themselves. We don’t need influencers with giant audiences, we just need good content that keeps people around. If we apply the 80/20 rule (Pareto’s principle), it turns out we don’t need that many creators to have a great flow of content. Enabling just a handful of people to create great content might just do the trick.
How to get there: focus on creating tools that enable expression of creativity. One such tool is Pinstr, but its value is largely untapped. On its own, pinstr is nothing interesting, it’s practically a clone of Pinterest. But, given the interoperable nature of nostr, it would be interesting to see pinned boards / content surfaced within kind 1 clients. People could then explore the board or that user’s other boards further by making their way to Pinstr.
How do we encourage more people to curate interesting pins? How about a pin extension that makes it easy to do so?
How do we enable people remixing other pins? Allow them to re-pin the content to their own boards. These are all mechanics that made Pinterest interesting, but lack in pinstr (as far as I’m aware).
Other ways that we might encourage content creation:
- Multi-account support. Can we make it SUPER easy to switch between identities when posting some curated content? Yes we can. (Select a different identity when posting)
- Surfacing “Other stuff” with a call to action to do that thing. For example, if someone shares a list, a kind 1 client should be able to render that list in a way that’s easy to browse, share and encourages to create your own list. If someone shares a music playlist (hopefully via native nostr kind), a person should be able to see the playlist and be encouraged to create their own. Watch stream? > prompt to start your own
- Gif / meme discovery with a call to action to create your own. (Plebhy, Memester)
- Styling tools (more complex) to style media, add soundtracks etc (perhaps via integration with Wavlake or other nost-native music events).
-
Content scheduling - help existing users become power users. Instead of posting everything at once, allow users to schedule it out for even distribution. Tools like Shipyard enable this already, but having this ability in-client might make it more accessible and useful.
-
Content pinning extensions - bring the outside world to Nostr. How can people 1-click pin content to nostr without having to switch tabs constantly?
-
App discovery - I think this is already in the works, but being able to surface other apps within kind 1 clients would be super interesting.
- Enable surfacing of highlighted content and paid content - with highlights, nudge people to read more of the content if it comes from within one of the nostr clients. With paid content, indicate that it is premium content and encourage creation of premium content “Become a creator” or “Join creator studio”.
- Encourage people to write long-form opinion content. When reading a long form article, perhaps have a call to action to start your own nostr publication. “Publish on Nostr and earn”
- Surface and encourage audio creation - we don’t have a nostr podcast client yet, but if there was one, kind 1 clients could surface that content automatically and encourage people to start their own podcasts, audio diaries, audio chats (nostr nests) or audio stories. Kind 1 clients could surface audio clips with waveforms and subtitles built in, or create a framework by which other developers could create this type of interaction with your kind 1 client. Can users create their own clip playlists from audio content fetched from the nostr podcast app? Why not?
The common objection to all of this might be that “you can already do all of this just by copying links”. Yes, and no. Copying links does share content - albeit in a boring preview way. It does not enable interactivity, nor prompt people to create that type of content. I think this is where nostr could shine.
Thought 2: Interoperability
One of the greatest strengths of nostr is the ability to display events across clients. I think of kind 1 clients as the glue that holds together the “other stuff”. The other stuff apps can be used to create the stuff, and kind 1 can enable discovery of said stuff, while encouraging to visit those tools to create their own.
Traditional social media platforms are encourage to put up walls and discourage leaking of users to other places. The more time a user spends on a website or app, the better for that company. But, with nostr, there’s a virtuous positive loop that does not punish leaking of attention, but instead, rewards it. The more content people create, the more interesting your kind 1 discovery client becomes.
How to get there: It’s going to take a lot of work to integrate the other stuff, but it’s already under way. As a client developer, partner up with other stuff clients to figure out how to best support them. Open up nostrapps.com to see what exists, and how your client can accommodate the surfacing of that stuff with minimal effort (since our resources are so scarce). Tap into product designers to help conceptualize and visualize interactions and growth loops. #nostrdesign is ready to help with this.


Type of content kind 1 clients could surface and create loops for:
- Playlists
- Pin boards (pinstr)
- Audio chats (nost nests, corny chat)
- Highlights (highlighter)
- Payments
- Fundraisers (Heya, Geyser)
- Communities
- Events (Flockstr)
- Streams (zapstream)
- Long form content
- Job posts / boards
- Recipes (zap cooking)
- Lists
- Torrents (Stan)
- News feeds
- Calling functionality
- DMVs
- Podcast clips, playlists
- Audio clips
- Marketplace items (Shopstr, Creatstr, Plebeian Market)
- Paid content (highlighter)
Recap
- Build tools to aid content creation
- Surface “other stuff” in kind 1 clients
- Prompt people to create their own stuff
I’m probably missing a ton, or not thinking of unique experiences that are just under the nose. What am I missing? What other cool interactions could be enabled by nostr’s interoperabilit
-
 @ b12e2899:ed9d9c8b
2024-05-12 23:36:25
@ b12e2899:ed9d9c8b
2024-05-12 23:36:25There’s a paradoxical phenomenon. On the one hand, a high entry threshold to Nostr assumes you’re ready to take responsibility for your data, on the other hand, some nostriches still seems to have irrational behavior when it comes to anything related to personal responsibility for their own data. Most nostriches attend to leave default values in their list of relays and forget to backup important data is also a fairly common. Therefore, I’ve decided to share few tools to try and make your experience bit better.
The contact-list-backup tool is incredibly simple, yet very powerful. Unfortunately, there’s still no documentation, so let’s figure it out.
First, you’ll need to choose a relay and type a hex-32 of your npub you want to backup contacts for. In my case it looks like this:

If you don’t know how to get a hex of your npub, there’s a tool for that called Bech32-for-Nostr and it’s purpose is to convert Nostr things like nsec, npub, note, naddr, nrelay, nevent, nprofile to hex32 and vice versa.
If you have hex-32 of your npub and you know exactly which relay stores the event with your contacts, then press the PULL CONTACTS button.
 As a result, you’ll get a list of contacts.
As a result, you’ll get a list of contacts.That’s it! You have it! This is the backup of your contacts! Simple as that.
Next, let’s say you want to retranslate this backup to some relay, you’ll need to connect with Nostr by providing it with a user@provider or bunker protocol link. In my case, I use nos2x browser extension that stores my private key and helps me to sign events:
 When I press the NIP-07 EVENT button, automatically it signs the event for me.
When I press the NIP-07 EVENT button, automatically it signs the event for me.Last but not the least, press the PUSH CONTACTS button which will send your signed event to a relay of your choise.
That’s it! Now you know how to backup your contact list and restore it! Congrats!
If you find this article helpful, please share with your friends and follow me.
-
 @ 03612b0e:afd71216
2024-05-12 14:14:47
@ 03612b0e:afd71216
2024-05-12 14:14:47c-lightning-REST with Tailscale on Start9
This guide gives you commands to run additional containers on Start9. This is not officially supported and will break on reboot. You can always run the containers again to restore the setup. The containers are used to provide access, via Tailscale, to Core Lightning's c-lightning-REST plugin
Start9 setup
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
- Services > Core Lightning > Config > Advanced > Plugins > C-Lightning-REST
- SSH to your Start9, see documentation for help: https://docs.start9.com/0.3.5.x/user-manual/ssh
- Access the root account:
sudo -i - Run tailscaled and alpine/socat containers:
podman run -d \ --name=tailscaled.embassy \ -v /dev/net/tun:/dev/net/tun \ -v /var/lib:/var/lib \ -e TS_HOSTNAME=tailscaled \ --network=host \ --cap-add=NET_ADMIN \ --cap-add=NET_RAW \ docker.io/tailscale/tailscale:stablepodman run -d \ --name=socat.embassy \ --publish 4321:1234 \ --network=start9 \ docker.io/alpine/socat \ tcp-listen:1234,fork,reuseaddr tcp:c-lightning.embassy:3001-
Note, if you see errors related to
/root/.docker/config.jsonorUnexpected end of JSON, runecho '{}' > /root/.docker/config.json -
Check the status of tailscaled and log in
``` podman exec tailscaled.embassy tailscale --socket /tmp/tailscaled.sock status
example output
Logged out. Log in at: https://login.tailscale.com/a/1fa8e293dfd108
```
Zeus wallet setup
- On your phone, connect to Tailscale
- On your Start9, copy your REST Macaroon (Hex) for Zeus wallet setup
- Services > Core Lightning > Properties > REST Properties > REST Macaroon (Hex)
- In Zeus wallet, add a new node
- Settings > (tap the active node) > +
Setting | Value ---|--- Node interface | Core Lightning (c-lightning-Rest) Host | tailscaled.YOUR_TAILNET_DOMAIN Macaroon (Hex format) | see last step REST Port | 4321 Certificate Verification | disabled
SAVE NODE CONFIG
- Note, you can find YOUR_TAILNET_DOMAN at https://login.tailscale.com/admin/dns
Enjoy!
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ 6b9da920:7841cc6e
2024-05-10 23:07:42
@ 6b9da920:7841cc6e
2024-05-10 23:07:42Here is a simple chart for developers to understand when to "Nostr Native" and when to "Nostr Integrated"
Definition:
Nostr Native: Uses relays as the only network layer and storage layer and business logic is 99%+ client side.
Nostr Integrated: Has in-house solutions and only connects partially to Nostr.
Both categories could be open sourced or close sourced.
| Features | Benefit From Network Effect | Don't benefit from Network Effect | | --- | --- | --- | | Contribute To Network Effect | All in Nostr Native | Recommend Writing to Nostr | | Harm Network Effect| Don't Write to Nostr and could read from Nostr | Should be in-house solution and not write to Nostr |
Category 1
If we think we should be all-in Nostr Native no matter what (like 99%+), we are limiting ourselves to only features that both benefit from Nostr and contribute to Nostr. This is a totally valid proposition as long as developers are consciously aware that they are indeed making a product within this category.
Pretty much all public facing social features fall into this category.
But, there are many products that need features that fall into other 3 categories.
Category 2
For features that benefit from Nostr but harms it, you are basically stealing data from Nostr without contributing back. My advice to is not write to Nostr at all and only read from Nostr if you have to do it, but you should minimize this product design in general.
Pretty much any massivly bot/batch job/pipeline generated data fall into this category. Machine generated data do not necessarily mean spam data. In the data engineering & machine learning world, it's very common to generate intermediate data in data pipelines for downstream analytics. This kind of data is huge and can also be purely textual. Don't write to Nostr relays.
Category 3
Is it even possible to have features that don't benefit from the network effect of Nostr and can contribute to it?
I can't think of any. But if it exists, consider writing to Nostr even if you don't use relays as the primary storage.
Category 4
These are features that don't benefit from Nostr and also harm Nostr if writing to it.
Slack style internal organization communication falls into this category. In fact, we want to actively prevent these features from having network effects because having these data in an open network might reduce their security.
Writing them to Nostr also harms the network because these data, encrypted or not, only have semantic meaning within the organization. Posting them to Nostr reduces the overall signal(value) density of the network.
Outtro
It is very common and almost inevitable for a single product to have both lots of category 1 and lots of category 4 and some % of category 2 & 3.
Using this chart, you will know how to make wise engineering decisions that help your product design instead of harming it and help the network at the same time.
-
 @ 97c70a44:ad98e322
2024-05-09 17:25:22
@ 97c70a44:ad98e322
2024-05-09 17:25:22#lastword
A few weeks ago, Mike proposed the addition of a feature to nostr. The content of the proposal itself isn't important, but the resulting conversation illustrated something important about nostr development that I wanted to draw attention to.
If you're interested, you can find the issue here. The idea was basically a tag that disabled comments to a reply, for when you wanted to gracefully exit a conversation that had outlived its usefulness.
While I definitely sympathize with the experience of getting stuck in an unproductive argument and being unable to leave because you have to have the last word, I do think it's better to take responsibility for leaving the conversation, rather than make other people do it for you. You can either outlast your opponent, let them have the last word, or tell them "I don't want to talk about this any more, I'm not going to reply".
This is just my opinion, and it's really not important whether I'm right or not. What was interesting was how Vitor responded:
I am not sure if the NIP review process should consider "what's good for the user" in the discussion. That kind of nanny state thinking is what went wrong with regular social media in the first place.
Permaculture and Ethics
What it sounds like (although I have a hard time believing this is actually his position), is that Vitor is dismissing the relevance of an ethical framework in designing a protocol, preferring to stick to the mechanics of what is being suggested. As Vitor says, "Clients can do whatever they want, of course." This is true, but ignores the question of why a client developer might want to do any particular thing.
In a recent Thank God for Nostr episode, I interviewed Scott Mann of the Permaculture Podcast. When I asked him his opinion on how to manage decentralized protocol design and build effective consensus, here's what he had to say:
[You] don't need to frame it as a software development project, or even a protocol. I would look at it as a distributed community-based and community-supported project, whatever that is. Because permaculture is such a large umbrella, I like to go up to that 50,000 foot view and pull away from what the details are. Because the details are what we're going to build our solutions from.
And that's one of the things I didn't mention earlier — there's kind of a hierarchy within permaculture that goes, at the top are the ethics of permaculture: earth care, people care, fair share. Beneath that are the principles, then usually we have strategies and techniques.
But there's a dividing line between ethics and principles and the strategies and techniques, that we start at that top, and use the ethics to decide whether or not we're even going to launch a project.
He goes on to say:
I'm going to use the principles and see how can I apply those principles to my research and original design. To make sure that whatever I'm creating creates some kind of a surplus, to have a refinement process in place before I even launch, like what is that going to look like, even if I have to change it later, just having some of these building blocks in place.
And then once I've done that and have gone deep into my research into what this might look like, how I might launch it, that's where I would start going into strategies and going ok, how do I want to market this? How do I want to get this out to the people who are going to use it, how do I want to maintain this, how do I want to do distributed decision making, and then as I start to think about distributed decision making, looking at what is the form that I want to use for that?
Scott's thesis is that ethics and principles should be in the front of your mind both as you're considering a project, and as you continue to build it out. This not only makes sense as something to do if you want to succeed, it's categorically true. Action can't happen without agency, and it is your agency that informs what you choose to do, and how you plan to go about it.
The word "ethics" comes from the Greek ēthos, meaning "moral character". In other words, your ethic is who you are. Your values, hopes, preferences, faults all factor in to your actions.
This is not always clear, because in fiat-world, many people suspend their values in order to "get something done". If you want to protect your savings, you invest it in index funds, propping up the stock price of companies that hate you. If you want to make money, you go work at a job where you're berated quarterly for being racist. People think that they can exercise their own values in their private life, while actively undermining those values with the majority of their time and purchasing power.
But this is not how people with integrity act. And I think if you can say one thing about nostr — both its developers and the community at large — is that they have a very high level of integrity. In other words, their actions are clearly informed by their ēthos.
This is a very good thing. What is the point of building an entirely new internet if we're not going to impose our values upon it? What an absolute waste of effort.
A Nostr Manifesto
This is not to say that any one developer has the right to imposing his own vision on the protocol because of his own personal values and reasons for contributing, which is what I think Vitor was being cautious about. But there are lines I think we can draw as a community that can't really be crossed without excluding yourself from what I might call the "nostr group ethic".
So what are those boundaries? What is a nostrich? Here are some values I've observed to be generally shared among nostr developers and users. Not everyone would full agree with these (including myself), but I think they're a fair characterization of the community.
- Free speech absolutism. No central entity should be able to globally censor any content. This comes with the trade-off of objectively evil content continuing to exist. This trade-off is acceptable, both because of the value of free speech, but also because evil will continue to exist regardless of attempts to suppress it.
- Empower individuals over institutions. No centralized entity can be trusted to safeguard the interests of the individual. Institutional incentives are asymmetric and easily corrupted. Better to have many subjective views of the world, than a single, centrally managed view of the world.
- Advertising-based business models should be viewed with great skepticism and caution. Advertising is a system of incentives that is central to the institutional corruption we see around us. Broadly, this includes paid ads, monetization of engagement, public/private partnerships, and "crypto".
There are others that are shared by many within nostr, although not as widely agreed upon. Two I can think of are:
- Economic activity should be voluntary. Software and content should be free, and creators should be amply rewarded via zaps or other value-for-value models.
- Social media should support real life community and relationships, not detract from them. We should all take time to touch grass.
I'm personally skeptical of the first of these, and strongly in support of the second. Much of my energy as a nostr developer has gone into attempting to subvert and reform traditional patterns of social media to not only support, but also resemble relationships that exist in the analog world God made, and placed us in.
This particular principle is the one at play in the conversation I linked to at the top of this post. My comments weren't an accusation that anyone was acting "unethically" in a universal sense, only that the proposed feature was incompatible with my vision for what nostr should be.
But of course, my vision is not shared by everyone, and the principle of "support real life" is clearly subservient to core ethic #2, which admits the value of a diverse set of opinions about the world. I have no right (or ability) to invalidate anyone else's core principles. But by the same token I'm free to express my own, and attempt to convince other people to share them. This is the basic value proposition of freedom of speech itself.
Ethical Cohesion
I would go further, and say that not only is it permissible to talk about ethical reasons for building one thing or another on nostr, it's essential. By having these conversations we fuse our individual ethics into a shared ethic. By calibrating our moral compasses to point in (roughly) the same direction, we also decrease the friction involved in getting something done.
I think this was a significant part of the idea behind Sovereign Engineering — get a bunch of people in a room together sharing meals and going on hikes, and the work will accelerate! This is also the way a church works. By meeting weekly together we strengthen our shared identity and build one another up through our activity. In fact, this is the basic definition of a community as Scott Mann puts it. In his words, a community can provide:
a series of connections, and a knowledge base, and a skillset that we can't fulfill as an individual, while having a social relationship with people in such a way that we can call on them for help.
So maybe, as I've said before, the real protocol is the friends we made along the way. Disagreement and discussion is a healthy thing for a community to have, and we should never stop asking "why?"
-
 @ d34e832d:383f78d0
2024-05-09 06:25:16
@ d34e832d:383f78d0
2024-05-09 06:25:16Bitcoin's potential extends far beyond the realms of digital currency and investment. As a P2P, secure, and borderless payment system, Bitcoin presents novel solutions to longstanding pains and challenges in the traditional fiat monetary system. This article explores how social cues, community attitudes, and unique problem-solving approaches using Bitcoin can catalyze broader adoption and adaptability.
Social Cues Enhancing Bitcoin Adoption
The path to widespread Bitcoin adoption can significantly benefit from understanding and leveraging social cues:
Community Support and Education
Bitcoin enthusiasts are often eager to assist newcomers but may find their time limited. Structured mentorship programs, educational content, and accessible support channels can help compensate for these limitations. Ensuring that no one feels "left out of the tribe" is crucial in fostering a welcoming and inclusive Bitcoin community.
Inclusivity and Accessibility
Many individuals fear exclusion not just from monetary gains but from participating in what might be a pivotal financial revolution. Emphasizing Bitcoin's role as a tool for financial inclusion can attract wider demographics. Illustrating how Bitcoin can empower the unbanked or underbanked populations by providing access to a global financial network can be a compelling journey.
Problem-Solving with Bitcoin
Bitcoin offers distinct advantages in addressing issues endemic to the fiat system, such as inflation, accessibility, and transaction inefficiencies. Here’s how Bitcoin can uniquely tackle these challenges:
Fiat System Challenges
- Hyperinflation: In countries experiencing hyperinflation, Bitcoin presents a viable alternative that holds its value and provides financial sovereignty to individuals.
- Cross-border Payments: Bitcoin simplifies transactions across borders without the need for currency exchange or high fees, making it ideal for global trade and remittances.
Innovative Use Cases
Leveraging Bitcoin to solve specific problems can demonstrate its utility and encourage broader adoption:
- Microtransactions: Bitcoin can facilitate small transactions economically, which are not feasible with traditional payment systems due to high fees.
- Smart Contracts: Although primarily associated with other blockchain technologies, the development of platforms like RSK (Rootstock) allows Bitcoin to support smart contracts, enabling automated, trustless agreements.
Building Bitcoin Rails
To move the Bitcoin adoption process forward, significant investment in infrastructure—the "Bitcoin rails"—is necessary:
- Robust Wallets and Services: Developing user-friendly wallets and services that address the needs of diverse users can lower the entry barrier for new adopters.
- Merchant Integration: Encouraging businesses to accept Bitcoin as a form of payment can normalize its use in everyday transactions.
Readiness for Change
While the momentum behind Bitcoin grows, it's crucial to recognize that many are still apprehensive about transitioning from traditional financial systems to a digital currency-based model.
- Educational Initiatives: Continuous education on how Bitcoin works and its benefits can alleviate fears and misconceptions.
- Gradual Transition Strategies: Offering hybrid financial products that incorporate both fiat and Bitcoin can help ease the transition for hesitant individuals.
Conclusion
Bitcoin stands out not just as a financial asset but as a catalyst for solving complex monetary problems in innovative ways. As the Bitcoin community continues to build supportive rails and fosters inclusiveness, it's essential to meet people where they are, respect their pace of adaptation, and continually demonstrate how Bitcoin can positively impact their financial health and autonomy. By aligning social strategies with technological advancements, Bitcoin can transcend its current boundaries, inviting a future where financial empowerment and inclusion are accessible to all.
-
 @ d34e832d:383f78d0
2024-05-09 05:02:06
@ d34e832d:383f78d0
2024-05-09 05:02:06In the discourse surrounding Bitcoin and its underpinning technology, distinguishing between reality provides the value proposition of PoW. Here's how these distinctions apply to the conversation about Bitcoin achieving technological affinity with or surpassing conventional financial systems:
What You Can Depend On
Based on observable facts without embedding any opinions or prescriptions for action. In the context of Bitcoin: "Bitcoin's blockchain technology allows for a P2P ledger that records transactions across multiple computers." "The cryptographic security protocols used by Bitcoin provide a level of security against fraud and theft without the need for a central authority." "As of now, Bitcoin transaction processing times can vary significantly, influenced by network congestion and the transaction fees set by the sender."
What To Expect
"Bitcoin's underlying technology should be adopted by conventional financial systems to reduce reliance on centralized authorities and enhance transactional transparency." "The efficiency and security of Bitcoin's blockchain technology make it superior to traditional financial systems, which are vulnerable to fraud and operational inefficiencies." "Financial regulators ought to create frameworks that accommodate Energy like Bitcoin, recognizing their potential to innovate payments and remittances globally."
Applying These Distinctions:
When discussing Bitcoin reaching technological affinity with or surpassing that of conventional financial systems, it's essential to differentiate between what is (Expected) and what should be (achievable).
For example, I note that Bitcoin's blockchain technology has achieved certain benchmarks in transaction processing speed or security measures, comparing these achievements to those of existing financial infrastructures. This could include specific metrics or studies demonstrating how Bitcoin's P2P nature reduces certain risks inherent in centralized financial systems.
Conversely, npubs might argue that because of these technological advancements, society should shift towards a broader acceptance and integration of Bitcoin within mainstream financial operations. It could further suggest that Bitcoin's approach to security and decentralization presents a model that conventional financial systems ought to emulate for the benefit of global economic stability and inclusivity.
In debates and analyses, distinguishing between these types of statements helps in understanding the empirical basis of discussions and the value-driven visions propelling the discourse on Bitcoin's role in the future of finance.
Sources
Embracing OpenBSD for Enhanced Security: Advantages and Implementation
In a digital world increasingly threatened by security breaches and privacy invasions, OpenBSD stands out as a powerful operating system famed for its security, simplicity, and robustness. For individuals and organizations looking to enhance their digital security posture, embracing OpenBSD could be a transformative step. This article will explore why OpenBSD is a preferred choice for security-focused users and how it can be effectively utilized along with virtual machines (VMs), Chaumian e-cash systems, and tools like Firecracker.
Why Choose OpenBSD for Security?
OpenBSD is part of the Unix-like family, alongside its siblings FreeBSD and NetBSD, but it places an especially strong emphasis on security and code correctness. Here are some advantages that make OpenBSD particularly appealing for security and privacy:
Proactive Security
OpenBSD comes with a variety of built-in security features that are enabled by default. This includes randomization techniques, memory protection enhancements, and stringent cryptographic practices that significantly mitigate the risks of buffer overflows, memory leaks, and other vulnerabilities.
Minimalist Design
OpenBSD follows a minimalist design philosophy. Only essential components are included in the base system, reducing the attack surface drastically. Every feature, service, or protocol added to the system undergoes rigorous security audits, ensuring that they do not compromise the system’s integrity.
Frequent Security Patches and Updates
The OpenBSD team frequently releases patches and security updates, often responding swiftly to vulnerabilities. The project’s focus on security makes it one of the first to address flaws that could potentially affect a wide range of Unix-like systems.
Dedicated Cryptography
OpenBSD integrates robust cryptographic libraries and tools directly into its base system, providing users with powerful mechanisms for secure communications and data handling.
Implementing OpenBSD with Virtual Machines
For users seeking to combine the robust security features of OpenBSD with the flexibility of virtual environments, deploying OpenBSD on virtual machines is an excellent strategy. Using VMs allows for:
- Isolation: Running applications or services in separate VMs isolates them from the main system, containing any potential breaches within the virtualized environment and preventing them from affecting the host OS.
- Testing and Sandboxing: VMs offer an ideal environment for safely testing new applications, system updates, and configurations without risking the stability or security of the primary system.
Chaumian E-Cash in VMs on OpenBSD
Implementing Chaumian e-cash, a form of digital cash based on cryptographic algorithms proposed by David Chaum, within VMs on OpenBSD can provide an additional layer of security for financial transactions. This setup not only benefits from the inherent security features of OpenBSD but also leverages the isolation provided by VMs to protect financial data from external threats.
Using Firecracker for Secure VM Integration
Firecracker, an open-source virtualization technology created by AWS, is designed for creating and managing secure, multi-tenant container and function-based services. Integrating Firecracker with OpenBSD provides advantages such as:
- Reduced Overhead: Firecracker is designed to launch lightweight micro Virtual Machines (microVMs) in non-virtualized environments, ensuring a minimal performance overhead.
- Enhanced Security: Firecracker's model, which uses the processor's built-in virtualization support for security boundaries, complements OpenBSD’s security model, especially when running multiple isolated VMs.
Case In Closing
For users and organizations aiming to enhance their security and privacy capabilities, OpenBSD offers a proven, robust platform with an emphasis on minimalism and proactive security features. When combined with technologies like VMs and Firecracker, and concepts like Chaumian e-cash, OpenBSD becomes an even more powerful tool in the arsenal against cyber threats. Embracing OpenBSD might require an investment in learning and skill development, but the security dividends it pays can be substantial, making it a worthwhile endeavor for those serious about protecting their digital environments.
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ d34e832d:383f78d0
2024-05-09 02:37:25
@ d34e832d:383f78d0
2024-05-09 02:37:25Achieving goals and causing the shift to P2P sovereignty on your development journey on Nostr requires a solid understanding of its foundations, suitable tools, and the right environment. These sentiments will help you traverse the landscape of Nostr development, from setting up your environment to creating your first Nostr account.
Understanding the Basics of Nostr
Nostr operates atop the Lightning Network, utilizing it as the backbone for transactions on the Bitcoin blockchain. It leverages a peer-to-peer network for content distribution, eliminating any central authority's control over information flow.
Choose Your Programming Language
Nostr supports several programming languages, each with libraries and tools tailored for Nostr development: - Python: Popular for its simplicity and readability. - JavaScript: Widely used for web applications. - Rust: Known for its performance and safety features.
Choose a language that you are comfortable with and that offers robust support for developing on Nostr.
Setting Up a Nostr Development Environment
To commence development, you'll need a comprehensive setup that includes various components:
- Nostr Desktop Client: The interface for your Nostr operations.
- Lightning Network Node: Essential for handling transactions.
- Relay: Facilitates communication within the Nostr network.
- Database: For storing data locally.
Tools to assist in setting up your development environment include:
- Nostr CLI: A command-line tool for managing your Nostr configurations.
- Nostr Docker Image: Provides an easy-to-deploy Nostr relay server.
Connecting to the Nostr Network
With your development environment ready, connect to the Nostr network by executing the Nostr CLI. This connection links your Nostr node to the wider network, allowing engagement with other nodes and clients.
Creating a Nostr Account
Creating a Nostr account involves generating a new public/private key pair. Use the Nostr CLI or a hardware wallet for key generation:
- Generate Key Pair: Securely create your public and private keys.
- Register Account: Use your public key to register your Nostr account.
Funding Your Nostr Account
To activate and use your Nostr account, you'll need to fund it with Bitcoin:
- Obtain Bitcoin Address: Retrieve your Nostr account's public key lightning address.
- Transfer Funds: Using a Bitcoin wallet or exchange, transfer Bitcoin to the obtained address.
Start Developing
With your account set up and funded, you're now ready to start developing on Nostr. Begin by exploring simple projects to familiarize yourself with the network’s capabilities and gradually transition to more complex applications.
Consider Your Services, Stand Up
Developing on Nostr opens up vast opportunities in P2P applications leveraging the Bitcoin blockchain. By following these sentiments, setting up your environment, and connecting to the network, you’re well on your way to becoming an adept Nostr developer. Embrace the journey, and leverage the power of open, decentralized networks to build innovative solutions.
Remember, the path to mastering Nostr development is continuous learning and experimentation. Engage with the community, search out new pubkeys, contribute to open-source projects, and stay updated on the latest Nostr developments for a fruitful development experience.
-
 @ 97c70a44:ad98e322
2024-05-08 16:52:50
@ 97c70a44:ad98e322
2024-05-08 16:52:50I think there's been an inflection point recently in NIPs that are being proposed. Some examples:
- Products with pubkeys: https://github.com/nostr-protocol/nips/pull/1225
- Shared-ownership events: https://github.com/nostr-protocol/nips/pull/1192 and https://github.com/nostr-protocol/nips/pull/1015
- Spreadsheets: https://github.com/nostr-protocol/nips/pull/1189
- Relational databases: https://github.com/nostr-protocol/nips/pull/1168
- Relay-specific notes: https://github.com/nostr-protocol/nips/pull/1146
- Editable notes: https://github.com/nostr-protocol/nips/pull/1090
- Restricted events: https://github.com/nostr-protocol/nips/pull/1083
- Relay-based access control: https://github.com/nostr-protocol/nips/pull/1030
- Protected events: https://github.com/nostr-protocol/nips/pull/1029
- Closed groups: https://github.com/nostr-protocol/nips/pull/875
Some of these I like, some I don't. But most of them go beyond adding new features to nostr (for example audio, video, speedruns, resumes, etc), and begin to change how nostr actually works.
Nostr can be an everything app, but I think that means something very specific. Nostr can represent data types from pretty much any domain, but it can't actually support all the semantics needed to build any arbitrary system.
I would suggest conservatism in what we build on nostr, but of course anyone can build whatever they want. But I do think it's possible to identify things that nostr is good at, and things it's bad at, and play to nostr's strengths.
Nostr's strengths:
- Being able to model any data type orthogonally to the rest
- Single-owner, self-authenticating, atomic data types
- Potential for robust content dispersal and retrieval if we can flesh out NIP 65 etc.
Nostr's weaknesses:
- Mutable state, non-atomic state
- Shared ownership, key delegation/rotation
- Privacy — metadata will always leak, lack of consistency makes key rotation harder
- Consistency — not everyone has the same view of the world
- Transactionality — nostr isn't good for updating multiple pieces of data in lockstep
It happens that the original use case of nostr — public broadcast social media — benefits greatly from nostr's strengths, and isn't bothered by any of nostr's weaknesses. Blob storage like what blossom is building also works well in this paradigm. A lot of the use cases @PABLOF7z has identified work beautifully well because of the single-owner public-read nature of nostr, which makes forks easy to model.
But things like access control, relational data, collaborative document creation, heavier datasets, or anything that requires a solution to the double-spend problem become very awkward (or impossible) to model on pure nostr. A simple example of this is lists. Not only is it common for a single user to mess up his follow lists because of a lack of consistency between clients or devices, but commonly requested features like shared ownership lists immediately result in a huge increase of complexity, either on the key management side or on the data structure side. Both of these problems are difficult to solve on nostr due to lack of consistency — keys can't always be reliably or safely shared, and linked data structures spanning multiple events by different authors can be hard to assemble reliably.
I think the danger here is that if we as a developer community fail to realize the limitations of nostr and try to adapt the protocol to fit every possible use case, on an ad-hoc basis, we're going to end up with a tragedy of the commons, where no developer can comprehend what must be done to get his work done, and all kinds of weird artifacts appear for end users that no one can explain.
Here are some suggestions I have for preventing this from happening. I realize no one is going to follow them. But maybe they can be helpful for avoidance of wasted time.
- Don't overload event kinds. Many people (including myself) have tried to extend kind 0 with attributes for forms, products, and groups, but that leads to madness. Instead, create a new metadata event signifying a different kind of agent.
- Don't model things as replaceable events if you can avoid it. This creates the problem of shared mutable state, which nostr doesn't have a good story for resolving. They also have a hard limit on how big they can be.
- Use different keys for different things. For domains where some kind of access control needs to be implemented, not tying everything to your main pubkey makes it possible to create and burn keys as needed. Incidentally, this can help users maintain better privacy. An example of this is private groups, which have a dedicated key separate from the group creator's own key.
- Event ownership should always be (is) single-key. If you need shared ownership, figure out a way to share keys. More work needs to go into key invalidation and rotation for this to really work.
- Explore the fork model — this is "my" version of the same thing, and coexists with rather than supersedes the original. This has potential not just for groups or wiki entries.
- Distinguish between different ways to use relays. Relays may be used as indexers (holding specific event types or supporting different features like search/count), repositories (holding many diverse events, to be used with filters), or curated feeds (to be used without filters, or with only a few filters).
These are just suggestions, and many of them may be wrong. Nostr development is hard, and getting harder. Keep it simple.
-
 @ 7ca66d41:0a388ca3
2024-05-08 12:58:30
@ 7ca66d41:0a388ca3
2024-05-08 12:58:30Plenty who understand DIDs have already commented on the tech issues with this solution, I wanted to explain the business and market reasons this is DOA.
First of all, what problem are they trying to solve?
Email security is the first usecase they’re rolling out. Specifically addressing spoofing which is a real problem for Enterprises. Other usecases are mentioned for futures but clearly MSTR and Saylor believe - as he’s said many times - that verifiable identities will solve this business problem.
So what is spoofing? A form of social engineering which attempts to deceive a message recipient (typically email but increasingly Slack/Teams/Zoom are targeted) that a message was sent from a known or trusted source; usually by manipulating email headers or using lookalike domains.
Typically it is used by scammers for simple frauds by instructing people to act. Either by directing them to send money or gift cards, change banking details, or to get additional information they can use for downstream attacks.
MicroStrategy Orange seeks to help Enterprise avoid spoofing by authenticating a signature for a User’s email which is anchored to the Bitcoin blockchain.
As they reference in the keynote - signatures for email are not new. SMIME has been around forever and it isn’t widely used because it introduces its own set of complexities.
What enterprises ++have++ done for years is rely on Secure Email Gateways (SEGs) to reduce the volume of malicious emails reaching Users. This is a software layer inserted in the mail flow which inspects email for things like malware or malicious URLs by checking them against known bad.
This worked well enough for a long time and multibillion dollar companies such as ProofPoint and Mimecast were built around it. The method is not foolproof, but their success is why scammers had to adapt and start using more social engineering attacks because these are less likely to be picked up by a SEG which tends to look for malware hashes, low reputation domains etc.
Next Generation email security is already here and being adopted by Enterprises.
Abnormal Security is the leader in this new category. They intercept traffic and feed it into a cloud “AI engine” which analyses hundreds of data points per email - like Crowdstrike for email. It builds a baseline of what “normal” email behaviour looks like for each User in an Enterprise and then use these signals to look for abnormalities.
This starts with things like the IP address of the sender (ie they always send from an office and now suddenly are sending from Russia), and relationships (ie the CEO who supposedly sent this has never emailed this lowly employee in Accounts Payable), but goes much deeper.
They use language analysis to parse emails for things like urgency, calls to action, financial requests, as well as if the email matches the writing style of the person being spoofed (“please do the needful” won’t fly in 2024).
This is very powerful because it’s not reliant on a static list of known bad which the vendors need maintain, but rather is analysing signals in real time to pickup these modern threats where SEGs are weak and because it’s done in Abnormal’s cloud, they can cross-pollinate for their expanding customer base which constantly improves the tech for all.
If the email doesn’t meet a threshold score it simply won’t be delivered to the end user, the same as a SEG blocks emails with malicious attachments. ++This is what Security teams actually want++, as it reduces the reliance on the weakest link - the End User - acting correctly (ie verifying an Orange signature) and simply takes the bad email out of their flow altogether.
Abnormal have taken the lead in this space with ProofPoint and Mimecast playing catchup, and others will likely emerge. But these are the tools that large Enterprises are already adopting to address this challenge.
No Cybersecurity professional is going to look at this Orange Check solution and see it as useful.
Their first point will be that which nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z pointed out - bad actors will be able to get their own DID so relying on them is futile.
Secondly, unless they are ubiquitous to the point company’s would refuse non-DID signed email, then they have to leave non-Orange Checked emails to User discretion which is exactly what they don’t want to do.
Finally if this approach was going to be feasible, Microsoft (MSTR’s biggest competitor) would have already made it work - they dominate enterprise email and would have baked this in to their offering - they’re not going to allow a competitor to come in and monetise a product in that space, that’s simply not how big business works.
So what is the one chance that MicroStrategy has for this to be successful?
They will need to get the US Government onboard as a large customer and lobby to have Cybersecurity compliance frameworks require it - ie Gov entities won’t accept incoming mail without it.
Compliance tends to create its own industry; in consulting, certification, and technology solutions.
The only way this gets broad adoption is if some US Government Institution sees an ability to price out Bitcoin transactions by pushing this non-monetary usecase and forcing others to join in by mandating DIDs, and Big 4 consultancies see an ability to create an industry around it.
I don’t know how they could justify that. Certainly for email they couldn’t, possibly for codesigning or internet access or something I guess they could try as part of “secure digital supply chains”.
So if these Orange Checks somehow do gain traction you can be certain, ++100% certain++, it’s not because the free market thought they were a good solution and actually solve a problem but rather because powerful entities want to kneecap Bitcoin.
Of all the things Michael Saylor could do with 1% of the only absolutely scarce asset in the world, deciding to go this route for his company’s first project on Bitcoin is incredibly strange.
It’s as if he hasn’t actually spoken to any customers about how they’re doing email security today and instead just rolled with an idea that sounded good on paper but is in practice, useless.
I’m doubtful it will go anywhere and will be far more sceptical if it actually does.
-
 @ d34e832d:383f78d0
2024-05-07 19:09:12
@ d34e832d:383f78d0
2024-05-07 19:09:12The Societal Impact of Bitcoin: Decentralization, Power Dynamics, and Human Power
Bitcoin represents more than just a digital currency; it signifies a paradigm shift in the way society understands and utilizes money. This transformation is rooted in Bitcoin's decentralized nature, which poses a challenge to traditional financial systems and their centralized control over monetary transactions.
Decentralization and Democratization of Finance
One of the central attributes of Bitcoin is its ability to decentralize financial transactions. By eliminating the need for central authorities such as banks and governments, Bitcoin paves the way for a more democratized financial system. Individuals gain unprecedented control over their assets, fostering an environment where financial inclusivity and autonomy are enhanced. The concept reflects the internet's architecture discussed in this source, which is inherently democratic and decentralized, featuring no single point of failure. Such a structure could radically transform sectors reliant on fiduciary trust, like accounting, commercial law, and insurance, making them more efficient and less dependent on centralized entities.
Addressing Global Inequalities
Beyond its technical capabilities, Bitcoin holds the potential to address broader societal issues such as globalization and capitalism-related inequalities (source). While not a panacea, Bitcoin can undermine the power of states and central banks, potentially reducing social inequalities and political oppression. This aspect underscores Bitcoin’s role not only as a technological innovation but also as a socio-political tool that could reshape global structures.
The Future of Bitcoin and Its Societal Role
As Bitcoin continues to evolve, its impact on society extends beyond fintech. It questions long-standing power hierarchies, proposes new models for financial interactions, and stimulates discussions on sustainability and innovation. The ongoing debate and research are vital as they shape public perception and policy regarding Bitcoin and its integration into daily life.
Bitcoin is at the forefront of redefining the future of money. It challenges existing structures, advocates for a more equitable financial landscape, and provokes critical discussions on environmental sustainability. The journey of Bitcoin is not merely about technological advancement but about paving a new path for societal development and human interaction.
Further Reading and Exploration
For those keen on exploring more about Bitcoin’s implications and technological underpinnings, consider delving into discussions and research papers available in various forums and academic circles. These resources provide deeper insights and broader perspectives on the potential and challenges of Bitcoin in reshaping societal norms.
Note: This article integrates perspectives and data from discussions and sources within the Bitcoin community, reflecting a collective understanding of Bitcoin's impact on society. For a more detailed exploration of the topics discussed, readers are encouraged to review the cited sources for comprehensive insights.
Bitcoin: Transforming Society's Financial Fabric

In our journey through technological revolutions, few innovations have sparked as much debate and potential as Bitcoin. At its core, Bitcoin challenges existing paradigms and redefines our understanding of monetary transactions. Its decentralized nature not only offers a new approach to managing finances but also reshapes societal structures and power dynamics.
Decentralizing Power and Control
Bitcoin's architecture inherently promotes a decentralized and democratic system, reminiscent of the internet's original ethos—with no single point of failure (source). This feature holds the potential to revolutionize various sectors including fiduciary trust, accounting, legal frameworks, and insurance. By mitigating the reliance on centralized authorities such as banks and governments, Bitcoin encourages a more equitable financial environment.

A Shift Towards Democratic Finance
The potential of Bitcoin extends beyond mere financial transactions. It offers a novel paradigm where individuals exert greater control over their assets, leading to a more democratized financial landscape. This shift profoundly impacts how power is distributed and exercised within society, suggesting a future where financial equity is tangible.
Addressing Global Disparities
Discussions around Bitcoin often touch upon its capacity to addresses issues intrinsic to globalization and capitalism. While Bitcoin is not a cure-all for deep-seated social issues, it provides a tool that can diminish the influence of central banks and state powers, potentially reducing social inequalities and political oppression (source).

A Tool for Social Change
By circumventing traditional financial pathways, Bitcoin presents an alternative that could redistribute economic leverage, offering a counterbalance to entrenched systemic inequities.
The Road Ahead: Bitcoin's Societal Hard Involvement
As Bitcoin continues to mature, its societal hardening become more pronounced. It challenges traditional power structures, proposes innovative models for financial interactions, and stimulates discussions on technological advancements. The ongoing dialogue surrounding Bitcoin is not merely about its viability as a currency but its broader role in shaping future societal norms and human power

Bitcoin stands at the vanguard of a potential financial revolution. Its impact stretches beyond economics, touching on aspects of governance, social equity, and environmental stewardship. As we navigate these transformative waters, Bitcoin remains a key topic of discourse, emblematic of the broader search for more democratic and equitable systems.
Further Reading and Resources:
For those looking to dive deeper into the intricacies of Bitcoin and its impact, consider exploring the comprehensive discussions and analyses available through the links provided in this article. Engage with the community, participate in ongoing debates, and contribute to the shaping of this evolving technological landscape.
Sources:
- BitcoinTalk
- Linux Foundation Bitcoin Dev Mailing List July 2022
- Bitcoin Stack Exchange Discussion on Bitcoin's Societal Impact
Bitcoin's Role as a Treasury Reserve Asset: Navigating Threats and Opportunities
Bitcoin, a pioneering Reserve Asset, has gradually evolved from a speculative investment to a potential treasury reserve asset for various entities. This significant shift in perception underscores Bitcoin's growing influence and maturity within the financial domain. As we explore Bitcoin's integration into financial assets and reserves, it's crucial to understand the inherent risks, its adaptive environment, and how it shapes the domain in which it operates.
The Threats to Entities Holding Bitcoin
Entities that hold Bitcoin as a treasury reserve asset are navigating uncharted territories, where both opportunities and threats abound. The primary concern revolves around price volatility, potential regulatory shifts, and security risks associated with the digital nature of Bitcoin. Moreover, geopolitical risks come into play—if one state decides to take punitive or restrictive measures against Bitcoin, it could trigger a ripple effect, prompting other states to assess their stance, either as a protective measure or to capitalize on an open digital currency platform.
A Thriving Environment Amidst Challenges
Despite these potential threats, Bitcoin continues to find a thriving environment fostered by certain key factors:
- Technological Advancements: Continuous improvements in blockchain technology and transaction security bolster Bitcoin's attractiveness and its perception as a resilient asset.
- Decentralized Nature: A core advantage of Bitcoin is its decentralized framework. Even in the face of state-level attacks or policies, Bitcoin can operate and be maintained from anywhere in the world, ensuring its survival and functionality.
- Global Participation: As more nations and corporations explore Bitcoin, it gains diverse footholds, which can mitigate the impact of any single nation’s negative stance.
The Evolving Domain of Bitcoin
Bitcoin's current trajectory is redefining its operational domain. No longer just a currency or investment, Bitcoin is increasingly viewed through the lens of a reserve asset—a store of value that could potentially backstop private and public treasuries.
- Market Maturity: Bitcoin is becoming more integrated with traditional financial systems, with futures trading, ETFs, and other financial instruments that use Bitcoin as the underlying asset.
- Regulatory Landscape: Regulation will define Bitcoin's future use as a reserve asset. Positive regulatory frameworks can enhance its legitimacy, while restrictive policies might limit its potential.
Incentivizing Network and Cryptographic Contributions
One of Bitcoin's revolutionary impacts lies in how it incentivizes contributions to its network and underlying cryptographic security. By rewarding miners for processing transactions and securing the network, Bitcoin ensures that its ecosystem remains robust and efficient. This incentive mechanism also drives continual technological and security enhancements, as participants invest resources to maintain and improve system integrity.
- Rewards System: Mining rewards, which compensate network participants with Bitcoin, ensure that there is always a motivation to contribute to network activities.
- Enhanced Security Investments: As the value and use of Bitcoin grow, so does the incentive for improving its cryptographic foundations, promoting a cycle of continuous enhancement.
Closing
As Bitcoin matures into a potential treasury reserve asset, it navigates complex landscapes of threats and opportunities. Its capacity to adapt to a thriving environment, even under potential attacks or challenges, highlights its resilience. Furthermore, its ability to incentivize contributions ensures that the network remains robust and continues to evolve.
Entities considering Bitcoin in their asset strategies must weigh these factors carefully, balancing potential risks against the revolutionary prospects that Bitcoin offers. As the domain of Bitcoin expands, its impact on global finance, network security, and economic structures promises to be profound, warranting close attention and thoughtful engagement from all stakeholders in the financial ecosystem.
In this evolving narrative, Bitcoin is not merely a digital phenomenon but a potential cornerstone in the future architecture of global finance.
I can run my own node: With keys I Take ownership Of , Shifting to any trustee or Myself
Navigating the New Frontier of Treasury Reserve Assets
As Bitcoin continues to carve its niche in the global financial landscape, organizations and sovereign entities embracing it as a treasury reserve asset are navigating a complex matrix of opportunities and threats. This digital currency, known for its decentralized nature and potential to disrupt traditional financial systems, is moving towards a future where its influence on economic strategies cannot be ignored.
The Dual-Edged Sword of Adoption
For those who have integrated Bitcoin into their treasury reserves, the decision comes with inherent risks. The volatile nature of cryptocurrency markets means that entities must remain vigilant against the fluctuations that could affect the valuation of their reserves. Moreover, regulatory uncertainties loom large, as governments around the world grapple with how to accommodate or control this new form of asset. Yet, despite these challenges, the allure of Bitcoin's potential rewards—such as protection against inflation and currency devaluation—continues to attract a growing number of adopters.
Thriving in Adaptability
Bitcoin's resilience lies in its ability to thrive in adaptable and supportive environments. As jurisdictions compete to become the next crypto hubs, they create ecosystems where Bitcoin can grow unencumbered by restrictive regulations. These thriving environments not only benefit from the innovation and investment attracted by being crypto-friendly but also contribute to the global narrative that Bitcoin and other cryptocurrencies are here to stay.
The Evolving Domain of Bitcoin
The domain in which Bitcoin operates is continually evolving, shaped by technological advancements, market dynamics, and changing regulatory landscapes. From its inception as a peer-to-peer electronic cash system to its current role as a speculative investment and potential reserve asset, Bitcoin is exploring new realms. Innovations in blockchain technology and increased institutional interest are paving the way for Bitcoin to expand its use cases and further integrate into mainstream financial systems.
A United Front Against Adversity
The decentralized nature of Bitcoin means that an attack on it by one state highlights its importance to all others. Such actions underscore Bitcoin's role as a geopolitical tool and a hedge against state-level risks. In essence, attempts to undermine Bitcoin can inadvertently increase its visibility and credibility, uniting its global community of users, developers, and investors against perceived threats. This solidarity enhances Bitcoin's resilience and underscores its potential as a non-sovereign safe-haven asset.
Incentivizing Contributions Through Cryptography
At the heart of Bitcoin's success is its incentive mechanism, which rewards contributions to the network and advancements in cryptography. Miners secure the network by validating transactions and are rewarded with newly minted bitcoins, while developers are motivated to enhance Bitcoin's protocol, ensuring its security, efficiency, and scalability. This model of incentivization has led to a vibrant ecosystem where innovation flourishes, and continuous improvements are made to the underlying technology.
In conclusion, as Bitcoin matures and expands its domain, the complexities it faces will undoubtedly evolve. However, its foundational principles—decentralization, transparency, and incentivization—equip it to navigate these challenges and solidify its status in the financial world. For entities holding Bitcoin as a treasury reserve asset, the journey may be fraught with uncertainty, but the potential for unprecedented rewards makes it a path worth exploring.
Sources
[0] Satoshi Nakamoto. (2012, April 17). Bitcoin P2P e-cash paper. Bitcointalk Forum. https://bitcointalk.org/index.php?topic=157130.msg1665557#msg1665557
[1] Maxwell, G. (2022, July 5). [bitcoin-dev] SIGHASH_NOINPUT and forward security. Bitcoin-dev Mailing List. https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2022-July/020685.html
[2] Back, A. (2015, August 17). Re: [bitcoin-dev] Block size, technical merit, and trade-offs. Bitcoin-dev Mailing List. https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2015-August/010473.html
[3] Andrychowicz, M. (2013, April 1). How Bitcoin will change society. Oleganza Blog. https://blog.oleganza.com/post/46894057432/how-bitcoin-will-change-society
[4] eMansipater. (2013, May 23). Re: A Guide to Bitcoin Transaction Priority. Bitcoin Stack Exchange. https://bitcoin.stackexchange.com/questions/15490#16572
[5] Meni Rosenfeld. (2013, May 22). Re: A Guide to Bitcoin Transaction Priority. Bitcoin Stack Exchange. https://bitcoin.stackexchange.com/questions/65948#65950
[6] Antonopoulos, A. (2015, March 7). Internet of Value. BTC Transcripts. https://btctranscripts.com/mit-bitcoin-expo/mit-bitcoin-expo-2015/internet-of-value
[7] Gideon Greenspan. (2013, May 23). Re: A Guide to Bitcoin Transaction Priority. Bitcoin Stack Exchange. https://bitcoin.stackexchange.com/questions/21002#21004
[8] Maxwell, G. (2022, February 3). Re: [bitcoin-dev] Payjoin BIP draft. Bitcoin-dev Mailing List. https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2022-February/020022.html
-
 @ d34e832d:383f78d0
2024-05-07 09:00:13
@ d34e832d:383f78d0
2024-05-07 09:00:13Imagine the Bitcoin blockchain as a bustling metropolitan area. Transactions on the blockchain are like commuters traveling to work during rush hour; the process can be slow, and there’s a high cost associated with getting where you need to go efficiently due to congestion. Now, imagine the Lightning Network as an extensive network of express highways that supplement this bustling urban infrastructure.
When you make a traditional Bitcoin transaction, it's akin to taking local roads during peak traffic times. You'll eventually reach your destination, but it may take some time and the journey can be costly in terms of transaction fees, similar to spending extra money on fuel.
However, by using the Lightning Network, it’s like accessing a less congested express highway. Here’s how it works:
Onboarding and Offboarding Ramps: Just as highways have specific entry and exit points, Lightning Network users must open a payment channel (entry ramp) with another user. This involves making a transaction on the Bitcoin blockchain to fund the channel. Once this channel is open, users can transact freely without needing to use the main blockchain, similar to driving on an express highway where you don’t encounter stoplights or traffic.
High-Speed Transactions: Transactions on the Lightning Network can be equated to driving at high speeds on an express lane because they're not impeded by the congestion of the main Bitcoin network. This results in nearly instantaneous transactions with very low fees, just as highways allow for faster travel between points.
Network of Highways: The Lightning Network isn’t just a single highway; it's an entire system of interconnected highways. Even if you don't have a direct payment channel open with someone, your payment can be routed through the network using multiple channels, just as a highway system connects various roads to allow you to reach a destination even if it is not directly connected to the highway you started on.
Exit Points: When you’re done transacting, or if you need your funds back in the main Bitcoin blockchain (perhaps analogous to exiting the highway to reach a specific neighborhood), you close your channel. This action settles your final transaction state back on the Bitcoin blockchain.
Like a modern highway system that alleviates traffic burden from city streets, the Lightning Network decongests the Bitcoin network, making transactions faster and cheaper, while still ensuring they can securely and effectively reach their final destinations when needed. Thus, the Lightning Network not only enhances the efficiency of Bitcoin transactions but also greatly expands its scalability, much like highways enhance urban mobility and connectivity.
Beginner's Guide to Bitcoin and Lightning Network Apps
Welcome to the NEWBIES category, your dedicated space for embarking on a journey into the world of Bitcoin (BTC) and the Lightning Network (LN). Whether you're a complete beginner, a small merchant, or just curious about Bitcoin, this guide is designed to help you navigate through your initial steps into Bitcoin without the complexities of self-custody or high-level technical requirements.
Why Start Here?
This category is specially curated for users who:
- Are new to Bitcoin and the Lightning Network.
- Prefer simple applications with user-friendly processes.
- May not be technically inclined or prefer an easy introduction to cryptocurrency.
- Want to use Bitcoin in small amounts for everyday transactions or just to get a feel of the technology.
Characteristics of Beginner-Friendly Bitcoin Apps
Custodial Services
The apps recommended here are primarily custodial. This means the service provider manages the wallet's private keys on your behalf. Here’s what you need to know:
- Dependence: These wallets rely on a connection to the provider’s server, which you do not control.
- Ease of use: Custodial wallets are generally easier to set up and use, making them ideal for newcomers.
- Security: While the risk level is low with small amounts, remember that your funds are technically under someone else’s control.
KYC and Privacy
- KYC Requirements: Many services require Know Your Customer (KYC) verification to comply with regulatory standards. However, there are options available without KYC for those prioritizing privacy.
- Privacy: While custodial solutions may not offer the same level of privacy as non-custodial wallets, they are suitable for new users experimenting with small amounts.
Wallet Backup and Restore
- Provider Dependent: The backup and restoration of your wallet are entirely dependent on the service provider. Ensure you understand their process for recovering your wallet should you lose access to your device.
Recommended Wallets for Beginners
Windows Desktop Wallets
- Green Wallet: A user-friendly wallet for Windows users starting with Bitcoin.
- Sparrow Wallet: Offers a simple interface with robust security features.
- Specter Desktop: Ideal for users interested in experimenting with multi-signature setups.
Android Wallet
- Electrum for Android: A popular choice that balances ease of use with comprehensive features.
iOS Wallet
- ZeusLN: A Lightning Network-focused wallet that’s great for iOS users taking their first steps into using LN.
Web and Telegram
- Mutiny Wallet: A self-custodial lightning wallet that's straightforward and secure, making it accessible for everyone.
- SatsMobiBot on Telegram: Chat with this bot to instantly create a wallet and start transacting with Bitcoin Lightning.
Learning Resources
- RoboSats: Learn how to use this peer-to-peer Bitcoin exchange that prioritizes privacy and speed.
Consider
Starting your journey into Bitcoin doesn’t have to be complicated. By choosing the right tools and platforms, you can gradually learn about Bitcoin in a controlled and low-risk environment. Remember to transition to non-custodial options as you become more comfortable and look to involve larger amounts, to have complete control over your crypto assets. Explore, learn, and enjoy your journey into the world of Bitcoin and the Lightning Network.
Leveraging the Power of Lightning Network
For individuals with a foundational understanding of Bitcoin (BTC) and the Lightning Network (LN), advancing to an intermediate level involves embracing greater privacy, security, and autonomy over your transactions. This guide delves into the realm of running a private LN node, using non-custodial wallets, and managing an own Bitcoin Core node for a more robust crypto experience. It is ideal for users and small merchants seeking enhanced control over their digital assets.
Understanding Your Options: Private LN Nodes and Non-Custodial Wallets
At this intermediate stage, users often opt to run their own Bitcoin Core node and connect various applications to validate and broadcast on-chain transactions. A private LN node is another popular choice, providing increased privacy for lightning channel management that isn't publicly announced on the LN network.
Key Use Cases:
- Personal Bitcoin Core Node: Users run their node at home, connecting mobile and desktop apps for on-chain and LN transactions.
- Private Lightning Network Node: This setup allows managing LN channels privately, ideal for users who utilize LN for regular payments without the need to route others' transactions through their node.
- Advanced Fund Management: Intermediate users might engage in coin control, swaps, and using ramps for buying and converting BTC, managing and spending funds efficiently.
Recommended Apps for Intermediate Users
Blixt
- Description: A mobile LN node wallet with rich features that can operate as a private LN node in various scenarios. A desktop version is planned, which will expand its capabilities.
- Use Case: Perfect for those who need a mobile solution with the capabilities of a full LN node.
- Blixt Wallet
Zeus
- Description: A powerful mobile node wallet that supports multi-account and multi LN implementations such as LNDhub and LN address.
- Use Case: Best for users looking for a versatile and feature-rich mobile lightning experience.
- Zeus Wallet
Breez
- Description: This is a mobile LN node wallet integrated with a Point of Sale (PoS) system and podcasting capabilities.
- Use Case: Ideal for merchants who want to accept BTC/LN payments seamlessly and content creators.
- Breez Wallet
BlueWallet
- Description: A multi-platform (Mobile/Desktop) BTC/LN wallet that includes functionalities like multisig, advanced features, and the ability to fund LN wallets from on-chain sources.
- Use Case: Suitable for users who transition frequently between on-chain and off-chain Bitcoin management.
- BlueWallet
Electrum
- Description: An old yet powerful desktop and mobile wallet that supports on-chain and LN transactions, using trampoline channels or private channels, and integrated with swaps.
- Use Case: Great for users who need a reliable and robust platform for managing on-chain and off-chain funds.
- Electrum Wallet
Best Practices for Intermediate LN Users
- Security First: Always ensure that your wallet and node software are up to date to defend against vulnerabilities.
- Back Up Regularly: Maintain regular backups of your wallet and channel states to prevent loss of funds.
- Monitor Channel Liquidity: Keep an eye on your LN channels' liquidity to ensure efficient transaction processing.
- Privacy Enhancements: Utilize features like Tor integration for network-level privacy and consider coin control features for enhanced transaction privacy.
Case In Consideration
Progressing to an intermediate level in managing BTC and LN involves a deeper dive into non-custodial services, running personal nodes, and exploring advanced wallet features. The tools and practices highlighted in are designed to provide users and small businesses with the necessary foundation to achieve greater autonomy, security, and efficiency in their Bitcoin transactions.
Stay informed and proactive in managing your digital assets, and continue exploring the vast potentials of the Bitcoin network and the Lightning Network technology.
Mastering the Lightning Network
The Lightning Network (LN) represents a significant evolution in the scalability and utility of Bitcoin, but fully leveraging its capabilities requires a deep understanding of its mechanics and a significant commitment in terms of resources. . It covers the prerequisites for effectively operating a high-capacity routing node, including technical knowledge, financial backing, and strategic management of liquidity and routing operations.
Understanding the Requirements
Profound Knowledge Base
The role of an expert in the LN ecosystem demands more than just a cursory understanding of Bitcoin; it requires proficiency in various complex topics:
- Bitcoin Protocol: Deep knowledge of how transactions are processed on the blockchain.
- Lightning Network: Detailed understanding of LN mechanics, channel states, and network topology.
- Economic Strategies: Insights into liquidity management, fee structures, and channel balancing.
- Technological Proficiency: Skills in Linux, and potentially, the hardware used for running a node.
- Security Measures: Best practices in securing digital assets and protecting node infrastructure.
Financial Commitment
Running a high-capacity LN node isn't just technically demanding—it also requires significant financial investments:
- Channel Funding: A substantial amount of bitcoin is needed to fund channels, with the aim of facilitating effective routing.
- Liquidity Management: The ability to allocate and rebalance liquidity strategically across channels to optimize transaction throughput and fee revenue.
Best Practices for Advanced LN Users
Continuous Education and Research
Keeping abreast of the latest developments in the LN space is crucial. Regularly consulting high-quality resources can enhance your understanding and operational efficiency:
- LN Documentation: Such as those provided by Lightning Engineering and other community-curated resources like CLN Documentation.
- Research Articles: Insights from thought leaders, such as the overview by Fulgur Ventures, provide context on different LN implementations and updates.
Strategic Liquidity Management
To ensure your node serves as an effective routing hub, consider the following:
- Balanced Channels: Maintain a balanced channel state where neither side is too depleted of funds.
- Dynamic Fee Strategies: Adjust routing fees based on network congestion, channel capacity, and competitive rates.
- Risk Assessment: Continuously evaluate channel counterparts to mitigate potential losses from channel closures or uncooperative peers.
Community Engagement and Contribution
Active participation in LN and Bitcoin forums, discussions, and development channels can provide valuable insights and also contribute to the collective knowledge and improvement of network protocols and practices.
Automation and Monitoring
Utilize tools and scripts to automate routine node operations such as:
- Channel Rebalancing: Tools that can dynamically balance channels in response to network conditions to optimize fees and liquidity.
- Uptime and Performance Monitoring: Regular checks to ensure the node is operational and performing transactions as expected.
Security Best Practices
Given the financial and operational stakes involved, securing your node is paramount:
- Regular Updates: Keep the node software and its dependencies up to date to protect against vulnerabilities.
- Backup Solutions: Implement robust data backup solutions to recover from hardware failures or cyber-attacks.
- Multi-Factor Authentication and Encryption: For all node access, ensure that data is encrypted at rest and in transit.
Moving Unto A Purpose
For those at the advanced level, running a LN node is a challenging yet rewarding endeavor that requires a blend of technical skill, economic savvy, and strategic foresight. It's not merely about supporting the network; it's about actively shaping the future of Bitcoin's scalability and utility. As you embark on this journey, remember that your growth and the network's health are interlinked: invest in your knowledge, contribute to community discussions, and operate your node with the diligence it requires. The portal to mastering Lightning is through persistent learning, vigilant operation, and proactive community engagement.
Mastering the Lightning Network: Diverse Use Cases and Best Practices
The Lightning Network (LN) has opened up new frontiers for Bitcoin usage, enabling faster, cheaper, and more scalable transactions. It's not just revolutionary technology—it's a thriving ecosystem for various stakeholders. From those functioning as Liquidity Service Providers (LSPs) to small businesses and family nodes, the LN is a dynamic field with rich opportunities. In this detailed guide, we explore the different roles within the LN and the best practices and tools tailored for each.
Key Use Cases in the Lightning Network
1. Routing Nodes and LSP Operators
For users equipped with the necessary knowledge and resources, running a routing node or acting as an LSP can be highly rewarding. This role involves managing the flow of transactions across the network, akin to controlling the flow in pipelines, adjusting where and how 'liquid'—in this case, satoshis—flows.
- Best Practices:
- Maintain a robust and well-funded node with diverse, high-capacity channels.
- Use tools like ThunderHub and LNBits for effective channel management and liquidity analysis.
2. Medium/Big Merchants
Merchants with significant transaction volumes can benefit greatly from LN by adopting a self-custody payment solution. This setup enhances both the security of their funds and the efficiency of transaction handling.
- Best Practices:
- Implement user-friendly LN-compatible POS systems.
- Educate the staff and customers about LN transactions for smoother operations.
3. Wallet Providers/Developers
These users offer more than wallets; they provide essential liquidity and connective services that enhance the overall utility of the LN.
- Best Practices:
- Ensure robust security measures are in place to protect users’ funds.
- Maintain high standards of privacy and transparency in service operations.
4. Advanced LN Users: Family Node Operators
Running a family node involves managing LN channels for personal use or a small community, like close friends or family. This setup emphasizes privacy and control over transactions and channel management.
- Best Practices:
- Regularly monitor and rebalance your channels to ensure optimal liquidity.
- Provide reliable support and guidance for your network of users.
5. Developers and Testers
These users are essential for the ongoing improvement and resilience of the LN. They run full nodes for testing new features or debug existing systems.
- Best Practices:
- Stay updated with the latest LN developments and community research.
- Contribute to projects and discussions on platforms like GitHub to improve LN tools and documentation.
Tools for Effective LN Management
To manage their LN nodes and liquidity effectively, users can leverage a variety of applications and platforms: - Fully Noded: Helps manage Bitcoin and LN nodes through a comprehensive mobile interface. - Phoenix: A user-friendly mobile LN wallet that simplifies channel management and transactions. - Sparrow Wallet: For onchain management with advanced features like coin control and privacy techniques.
Concluding Thoughts
The Lightning Network isn’t just transforming how transactions are done; it’s reshaping the economic landscape of digital currencies. Each user, whether a merchant, developer, or private node operator, plays a crucial role in this ecosystem. By understanding and implementing best practices tailored to their specific roles, participants can not only optimize their operations but also contribute significantly to the LN’s growth and efficiency.
This ecosystem thrives on continuous learning and adaptation. Whether you are just transitioning from intermediate know-how or honing your expertise, remember that every contribution matters in building a more connected and efficient network. Enjoy exploring, learning, and growing in the ever-evolving landscape of the Lightning Network.
-
 @ d34e832d:383f78d0
2024-05-07 04:09:40
@ d34e832d:383f78d0
2024-05-07 04:09:40In the evolving landscape of digital payments and cryptocurrency, facilitating a seamless connection between applications and wallets is crucial. Nostr Wallet Connect (NWC) emerges as a robust solution, offering developers an effortless way to link their applications with various bitcoin wallets. So how to get started with NWC, its benefits, features, and how to obtain and handle connection strings effectively.
What is Nostr Wallet Connect (NWC)?
Nostr Wallet Connect is a protocol designed to simplify the integration between client applications and wallet services. It streamlines operations such as sending and receiving payments, displaying wallet balances, and handling transactions without the need for manual QR code scans or confirmations.
Benefits of Using NWC
NWC brings several advantages to the table that can significantly enhance user experience and developer convenience:
- Convenience: Automates payment confirmations, removing the necessity for manual entry or QR code scans.
- Flexibility: Developers can either build a complete wallet interface or incorporate individual payment features according to their needs.
- Interoperability: NWC provides a universal interface that supports integration with any bitcoin wallet.
- Risk Management: Shifts apps from having to custody funds to merely orchestrating payments, enhancing security.
- Platform Independence: Compatible across various platforms including mobile, backend, CLI tools, and desktop applications.
Core Features of Nostr Wallet Connect
- Real-time Payment Receipt: Allows instant acknowledgment of incoming payments.
- Versatile Payment Initiations: Supports sending single or multiple payments, and can automate recurring transactions.
- Wallet Balance Display: Enables apps to show current wallet balances.
- Payment Listing and Verification: Offers functionalities to list and check the status of payments.
Obtaining a Connection String
To establish a connection between a client app and a wallet service using NWC, a connection string is essential. Here’s how to acquire it:
- Discovery: The client app can discover a wallet service either by scanning a QR code, following a deep link, or entering a URI.
- Generation: The wallet service generates a connection URI using the
nostr+walletconnect:protocol. This includes a hex-encoded public key and required query parameters such as relay URLs and a secret key.
Example Connection String
nostr+walletconnect:b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis string contains all the necessary information for the client app to initiate and maintain a secure connection with the wallet service.
Practical Implementation
Once the connection string is obtained, the client app should store this configuration for ongoing use. It's important to choose relays that maintain connections even during inactivity to prevent any loss of data or events.
For developers looking to automate the construction and management of these connection strings, exploring documentation and tools provided with NWC will be highly beneficial. More insights into this can be found on the official Nostr Wallet Connect page.
To Consider
Nostr Wallet Connect offers a streamlined, secure, and efficient way for applications to interact with bitcoin wallets. By implementing this protocol, developers not only enhance the functionality of their applications but also contribute to a more interoperable and user-friendly Bitcoin ecosystem. Whether you are developing a new financial app or looking to upgrade an existing system, integrating NWC provides a clear path to improving your application's connectivity and functionality in the crypto space.

Integrating Nostr Wallet Connect (NWC): SDKs, Tools, and Best Practices for Developers
The advent of Nostr Wallet Connect (NWC) has made integrating Bitcoin payments into apps and websites significantly more accessible and efficient. As a developer looking to harness the power of NWC, understanding the available SDKs, tools, and best practices for implementation is crucial. This article provides a comprehensive guide to getting started with NWC, highlighting key resources and strategies to optimize the integration process.
SDKs and Libraries for NWC Integration
NWC supports a variety of SDKs and libraries that cater to different programming environments, ensuring compatibility and ease of integration across multiple platforms.
JavaScript SDK
For developers utilizing JavaScript, the JavaScript SDK provided by NWC offers extensive documentation and integration guides. It facilitates the connection between your application and users' wallets, streamlining the process of requesting and processing payments.
Rust SDK
If your application’s backend is built with Rust, the Rust SDK for NWC is designed to provide robust support for wallet interactions. Rust’s performance and safety features make it an excellent choice for handling cryptocurrency transactions.
Bitcoin Connect Library
For applications that need to interact with Bitcoin Lightning-powered websites, the Bitcoin Connect Library is an invaluable resource. Supporting all web frameworks, it provides code examples for HTML, JavaScript, React, and Next JS/SSR, making it a versatile option for web developers.
Best Practices for Implementing NWC
When integrating NWC into your application, consider the following best practices to ensure a smooth and secure user experience:
Permission Requests
Only request the necessary permissions, and limit the scope and duration of these permissions to what is needed for each specific action. This minimizes security risks and respects user privacy.
Connection Setup
When setting up a connection, always pass the application name to provide clarity to the user. This transparency helps build trust and improves user comprehension of what the application will access.
Handling Connection Strings
For user-generated connection strings:
- Input Security: Use password-type input fields when users need to paste a connection string. This prevents passive data leaks from screen recordings or shoulder-surfing.
- User Control: Always provide users with the option to manually add a connection string from their NWC wallet application.
Wallet Agnosticism
Do not presume the use of a specific wallet service by the user. Maintain language neutral about the wallet provider to accommodate any user from any service. For instance, use generic terms like "Pay" instead of "Pay with X."
Running or Connecting to a Relay
Understanding how to interact with relays is crucial as they facilitate communication between apps and wallets:
- Event Handling: Learn to handle different types of events (NIP-47 info, request, and response) that are used to transmit commands and responses.
- Encryption: Ensure the content of requests and responses complies with NIP04 encryption to protect data integrity and privacy.
- Dedicated Relay Usage: Consider using a dedicated relay to enhance privacy and reliability. This can help avoid metadata leaks and improve connection stability.
Starting with NWC
To get started with NWC, developers can explore the comprehensive guide and resources available on the NWC website. Here, you can find detailed documentation, code snippets, and examples to help you integrate NWC smoothly into your applications.
Considerations
Integrating Nostr Wallet Connect into your applications opens up a realm of possibilities for incorporating Bitcoin payments efficiently and safely. By utilizing the appropriate SDKs, adhering to best practices, and properly handling connections and relays, developers can provide users with a seamless and secure financial interaction experience. Whether you are developing a mobile app, a web service, or a backend system, NWC provides the tools and guidelines necessary to enhance your application's functionality with robust Bitcoin support.
-
 @ d34e832d:383f78d0
2024-05-07 02:26:06
@ d34e832d:383f78d0
2024-05-07 02:26:06Harnessing AI with Bitcoin: Introducing PayPerQ
In the realm of artificial intelligence, accessibility and affordability often determine who gets to utilize these advanced technologies. PayPerQ, developed by Matt Ahlborg, aims to democratize access to premium AI by integrating OpenAI's API with Bitcoin payments, specifically using the Bitcoin Lightning network. This innovative approach allows users from around the world to engage with a pay-per-query Chatbot, providing a scalable and cost-effective solution for leveraging AI. Here's a deeper dive into PayPerQ and how it's changing the landscape of AI interactions.
What is PayPerQ?
PayPerQ is a groundbreaking service that merges AI chat capabilities with the flexibility and security of Bitcoin transactions. It enables users to interact with a ChatGPT model, where charges accrue per interaction, calculated based on the length of the input and output text. This model not only ensures users pay only for what they use but also enhances accessibility to cutting-edge AI for users across different economic backgrounds.
How Does PayPerQ Work?
Pricing Mechanics
The cost of each query on PayPerQ is straightforwardly determined by:
- Input Words: The number of words you type into the chat.
- Output Words: The number of words ChatGPT uses to respond.
The pricing model is designed to encourage efficiency in interactions—longer conversations have higher costs, suggesting that starting new chats could be more economical for lengthy discussions.
User-Friendly Controls
To prevent unintended expenses, PayPerQ has set a default maximum context of 2048 tokens. Users have the flexibility to adjust this setting based on their specific needs—a feature that showcases the platform's commitment to user control and customization.
Features and Benefits
Bitcoin Integration
By utilizing the Bitcoin Lightning network, PayPerQ taps into a fast, low-cost payment method that is perfect for microtransactions like those in AI interactions. This integration also signifies a step towards broader financial inclusion, as Bitcoin is increasingly accessible worldwide.
Transparency and Data Privacy
Transparency is central to PayPerQ’s operation. Users can readily access information on how their data is handled, ensuring that they remain informed and in control of their privacy.
Flexible Interaction and Prompt Personalization
PayPerQ supports custom prompts, allowing users to tailor their AI interactions for more personalized and relevant responses. This feature maximizes the utility and flexibility of the ChatGPT model, adapting it to specific user needs or inquiries.
Earning Bitcoin Lightning with AddSlice
For those new to Bitcoin Lightning, PayPerQ recommends using AddSlice, a browser extension that rewards users with Bitcoin Lightning in exchange for viewing ads. This setup not only facilitates easy entry into using PayPerQ but also promotes user engagement through a reward system.
Vision and Invitation for Feedback
Matt Ahlborg's vision for PayPerQ is to make it the go-to AI interface for Bitcoin developers and professionals globally. To achieve this, user feedback is invaluable. PayPerQ encourages users to share their experiences and suggestions, shaping the service to better meet community needs.
For Your Cosideration
PayPerQ represents a significant innovation in making AI interactions more accessible and affordable through the power of Bitcoin. Whether you are a developer, researcher, educator, or enthusiast, PayPerQ provides a flexible and cost-effective platform to explore the capabilities of AI while managing expenses transparently and efficiently.
Experience the future of AI interaction by visiting PayPerQ today, and see how easy and effective it is to integrate cutting-edge technology into your projects and workflows.
PayPerq on Nostr:
npub18kzz4lkdtc5n729kvfunxuz287uvu9f64ywhjz43ra482t2y5sks0mx5sz -
 @ d34e832d:383f78d0
2024-05-07 00:21:54
@ d34e832d:383f78d0
2024-05-07 00:21:54In the ever-evolving world of Finance, Bitcoin ATMs have emerged as a pivotal player in expanding access to digital currency. For entrepreneurs and enthusiasts alike, the idea of running a Bitcoin ATM is an exciting prospect, not only as a business opportunity but also as a way to promote the adoption of Bitcoin. Thanks to innovations in technology and accessibility, setting up your own Bitcoin ATM has become more feasible than ever before. This article provides a step-by-step guide on how to assemble and operate a Bitcoin ATM, featuring a comprehensive kit available from LNbits.
What You Need to Know About Bitcoin ATMs
Bitcoin ATMs offer a straightforward way for individuals to buy Bitcoin using traditional currency, such as banknotes and coins. Unlike conventional ATMs, which connect to a bank account, Bitcoin ATMs link directly to a Bitcoin exchange through the internet and provide an intuitive and secure interface for users to purchase Bitcoin with fiat currency.
The LNbits Bitcoin ATM Kit
The LNbits Bitcoin ATM provides all the necessary components to set up a fully functional Bitcoin ATM. This kit is designed for those who wish to leverage their own LNbits instance to facilitate transactions. Here’s what’s included in the kit:
- ESP32 WT32-SC01: A powerful controller with a built-in touchscreen that serves as the user interface for the ATM.
- DG600F(S) Multi Coin Acceptor: This device allows the ATM to accept multiple types of coins, enhancing its functionality across various regions and currencies.
- NV10USB+ Bill Acceptor: A reliable bill acceptor that enables the machine to take banknotes, a fundamental feature for any ATM.
- Screw Terminal Block: For secure and organized connections between the various components.
- 12v Power Supply and Converter: Ensures that all components receive the correct voltage for safe and efficient operation.
- Male/Female GPIO Jumpers: For easy and flexible connections within the hardware setup.
Setting Up Your Bitcoin ATM
Step 1: Assemble the Hardware
Start by assembling the physical components of the ATM. Connect the ESP32 WT32-SC01 to the inputs from the bill and coin acceptors. Use the GPIO jumpers for connections that might require flexibility or additional length. Secure everything in place using the screw terminal block for a neat and safe setup.
Step 2: Configure the Software
Install and configure the software on the ESP32 WT32-SC01. This will involve setting up your LNbits instance to manage the transactions processed by the ATM. Ensure the software is properly connected and configured to communicate with both the coin acceptor and bill acceptor.
Step 3: Power and Testing
Connect your ATM to the power supply. Carefully test each component to ensure that coins and bills are accepted accurately and that the touchscreen interface is responsive and user-friendly.
Step 4: Location and Security
Choosing the right location is crucial for the success of your Bitcoin ATM. High foot traffic areas such as shopping malls, universities, and coffee shops are ideal. Consider the security of the location; ensuring that your ATM is in a safe, well-lit area can prevent tampering and theft.
Step 5: Marketing and Maintenance
Once your ATM is up and running, focus on marketing your machine to potential users. Regular maintenance checks are vital to ensure that the machine continues to operate smoothly and securely.
For Your Consideration
Running your own Bitcoin ATM can be a rewarding venture that not only profits but also promotes the broader adoption of Bitcoin. With the LNbits Bitcoin ATM kit, assembly and operation are simplified, allowing you to focus on providing value and convenience to users eager to engage with Bitcoin. Get started today by visiting LNbits Bitcoin ATM and take your first step towards becoming a part of the global Bitcoin network.
-
 @ d34e832d:383f78d0
2024-05-06 17:42:42
@ d34e832d:383f78d0
2024-05-06 17:42:42The Open Source Movement has transformed the landscape of software development and beyond, democratizing access to information and fostering a global collaborative environment. This movement, characterized by freely accessible, modifiable, and sharable software code, has become a powerful catalyst for innovation, reshaping how technologies are developed, distributed, and improved.
Democratizing Software Development
Open source software (OSS) offers a progressive model where knowledge, tools, and code are openly shared. This approach allows both individuals and organizations worldwide to contribute to and benefit from collective wisdom without barriers. Projects like Bitcoin, detailed through numerous GitHub discussions and contributions, underscore the significant impact of open source methodologies in complex fields such as cryptography and blockchain technology.
Key Benefits of Open Source:
- Collaboration: Open source projects harness the collective intelligence of developers worldwide, accelerating problem-solving and innovation.
- Transparency: With open access to code, users and developers can examine the functionality and security of the software, fostering trust and reliability.
- Flexibility: Users can modify software to meet their specific needs, which promotes a personalized approach to software utilization and improvement.
Meritocracy in Action
One of the most compelling aspects of the open source model is its emphasis on meritocracy where the value of ideas supersedes the stature of their contributors. This ethos is evident in platforms like GitHub, where a diverse group of developers can propose, refine, and implement enhancements in a collaborative manner. For instance, Bitcoin’s evolution on GitHub illustrates dynamic discussions that lead to continuous enhancements, guided by the collective expertise of the community.
```
"The open source model thrives on collaboration and meritocracy, ensuring that the best ideas prevail in the development lifecycle." ```
Broader Implications for Innovation
While open source began as a movement within software development, its principles have permeated other areas:
- Hardware: Open source hardware projects allow for physical products to be developed collaboratively and transparently.
- Education: Free access to educational resources broadens learning opportunities, empowering students globally.
- Research: Open research promotes a faster exchange of knowledge and cooperative advancements in science.
These examples highlight the versatility and expansive potential of open source principles, influencing sectors beyond traditional software development and contributing to a global culture of shared innovation.
Challenges and Considerations
Despite its many advantages, the open source model presents challenges such as ensuring sustainable project funding, managing varying quality contributions, and protecting intellectual property without stifling collaboration. Effective community management, clear licensing agreements, and robust governance models are essential for addressing these challenges.
Closing
The Open Source Movement continues to be a significant force in shaping the modern technological landscape. By fostering an environment where information is free and accessible, where innovation thrives on collaboration, and where education is uninhibited by access barriers, open source principles champion a future of inclusive growth and continuous innovation.
For developers, businesses, and academics, engaging in open source projects offers a pathway to participate in cutting-edge developments and contribute to collective advancements. It represents not just a technical methodology, but a philosophy that promotes openness, inclusivity, and the endless pursuit of knowledge.
Further exploration and contributions can be made through platforms like GitHub, where many open source projects, including Bitcoin, continue to evolve.
Sources
For further insights into the discussions and developments within these open source projects, refer to: - Bitcoin Pull Request Comment #17901 - Bitcoin Issue Discussion #18580 - Bitcoin Pull Request Review #21778
-
 @ d34e832d:383f78d0
2024-05-06 16:25:48
@ d34e832d:383f78d0
2024-05-06 16:25:48In the world of software development, GitHub stands out as a central hub for collaboration and version control. Utilizing Git, an open-source version control system, GitHub provides a powerful platform for managing projects, tracking changes, and fostering collaboration among developers. Whether you are a seasoned coder or just starting out, understanding how to effectively use GitHub can greatly enhance your coding projects and collaborations.
About GitHub
GitHub is essentially a cloud-based service that hosts Git repositories, or "repos," where you can store, manage, and track your coding projects. It offers a plethora of functionalities including:
- Project Showcasing: Display your work for public view, which is particularly beneficial for portfolio building or open-source projects.
- Change Management: Keep a detailed record of modifications in your project over time, making rollback and error identification simpler.
- Code Review: Allow others to scrutinize your code and suggest improvements.
- Collaborative Projects: Work with other developers without the risk of immediately altering the main project.
GitHub’s environment supports these activities by providing tools for reviewing code, managing projects, and building software alongside millions of other developers.
About Git
Git, the backbone of GitHub, is a version control system that manages and stores revisions of projects. Git is indispensable for managing complex projects that require many developers working on the same files simultaneously. Here’s how Git typically works within a project:
- Branching: Create independent branches from the main project to work without affecting the core project.
- Commits: Save changes to your branch, creating a transparent history of your modifications.
- Merging: Combine changes from your branch back to the main project, allowing Git to intelligently merge without losing track of parallel updates.
How Do Git and GitHub Interact?
When you use GitHub, you operate within repositories that utilize Git's version control capabilities. You can perform several Git operations directly on GitHub, such as:
- Creating and managing repositories.
- Making branches.
- Committing changes online.
For local development, common practice is:
- Sync Local and Remote Repositories: Use tools like GitHub Desktop or command-line instructions to keep your local projects aligned with GitHub.
- Collaborate Seamlessly: Pull the latest updates from GitHub, make changes locally, and push back to GitHub for integrated updates.
Getting Started on GitHub
For newcomers, the journey begins by understanding and using GitHub’s web functionalities:
- Create a GitHub Account: Start by setting up your account on GitHub.
- Learn GitHub Flow: Understand the principles of branches, commits, pull requests (PR), and merges.
- Personalize Your Profile: Enhance your profile to showcase your projects and skills.
- Explore and Connect: Find projects that inspire you and connect with other developers.
First Steps:
- Navigating GitHub: Familiarize yourself with the user interface and various functionalities.
- Creating Your First Repository: Learn how to create and manage your coding projects on GitHub.
- Making Your First Commit: Understand how to make changes and commit them to your repository.
Next Steps
Once you have the basics handled: - Explore further by Creating an account on GitHub. - Dive into more detailed functionalities such as branch management and PRs.
To Consider
GitHub, paired with the powerful Git version control system, provides a robust framework for managing development projects. By facilitating collaboration, enhancing code transparency, and supporting effective project management, GitHub empowers developers to achieve more and collaborate effectively, regardless of geographical boundaries.
Get started on your journey into GitHub and discover the vast potential of this essential tool in modern development. Happy coding!
Establishing Trust in GitHub Contributions: The Importance of Verifying Keys and Creating a Web of Trust Protocol
In the vast, collaborative arena of software development on GitHub, where countless contributors merge their efforts to forge innovative projects, ensuring the integrity and authenticity of contributions is paramount. The verification of contributors' keys and the establishment of a robust Web of Trust protocol are critical practices for securing open-source projects. This article explores the importance of these security measures and how they can be implemented effectively within the GitHub ecosystem.
Why Key Verification Matters
Key verification is the process of ensuring that commits and tags are actually made by the entity they claim to originate from. In the context of GitHub and Git, keys refer primarily to GPG (GNU Privacy Guard) or SSH (Secure Shell) keys that are used to sign data digitally. This practice is essential because it:
- Prevents Spoofing: Ensures that contributions cannot be falsely attributed to someone else, which is crucial in preventing malicious code submissions.
- Reinforces Integrity: Helps maintain the integrity of the project’s codebase by verifying that commits and merges are from trusted and verifiable sources.
- Builds Credibility: Increases the credibility of a project by showing that the maintainers are committed to security and diligent in their governance practices.
Creating a Web of Trust
A Web of Trust is a decentralized security model for verifying digital keys. In this model, trust is established through a network of individual users who verify and sign each other’s keys. This creates a framework where the verification of one’s identity is crowd-sourced among trusted parties rather than relying on a central authority. Implementing a Web of Trust in the GitHub community can:
- Enhance Collaborative Trust: In large projects with numerous contributors, a Web of Trust helps in verifying that all participants are who they say they are.
- Facilitate Scaling Security: As projects grow and attract more contributors, a Web of Trust scales the security measures by distributing the responsibility of trust verification across multiple, credible parties.
- Improve Response to Security Incidents: A robust network of trusted contributors can respond more effectively to security breaches or vulnerabilities.
Implementing Key Verification and Web of Trust on GitHub
Step 1: Integrating GPG Key Verification
- Generate or Import a GPG Key: Contributors should start by generating their own GPG keys or importing existing ones into their development environment.
- Add GPG Keys to GitHub Account: Users must add their public GPG key to their GitHub account settings which allows GitHub to verify their signed commits.
- Sign Commits and Tags: Contributors should configure their Git tools to sign commits and tags with their GPG key, ensuring that their cryptographic signature accompanies every change.
shell git config --global commit.gpgsign true git config --global user.signingkey YOUR_GPG_KEY_IDStep 2: Establishing a Web of Trust
- Community Key Signing: Organize or participate in key signing parties or events where GitHub contributors can meet (either virtually or in person) to verify identities and sign each other's keys.
- Publish and Share Trust Signatures: Contributors should publish their signed keys and trust signatures in a publicly accessible venue or directly on their GitHub profiles.
- Verify and Rely on Trusted Keys: When cloning or forking repositories, developers should verify the signatures against the Web of Trust to ensure all contributions are from trusted sources.
Case in closing
In an era of heightened cybersecurity risks, the importance of verifying keys and establishing a Web of Trust cannot be overstated in the context of GitHub contributions. These practices bolster the security of projects, protect the integrity of code, and build a foundation of trust within the developer community. As contributors and maintainers of open-source projects, embracing these protocols is a step towards a more secure and reliable software development ecosystem.
By fostering an environment where trust and security are paramount, the GitHub community can continue to thrive and drive forward the innovation that has cemented its place at the forefront of software development.
-
 @ d34e832d:383f78d0
2024-05-06 15:06:21
@ d34e832d:383f78d0
2024-05-06 15:06:21Revolutionizing Node Management with Core Lightning (CLN)
In the evolving landscape of cryptocurrency, running a Lightning node has become more accessible and efficient thanks to innovations by Core Lightning (CLN). Whether you’re a business aiming to streamline your operations or an individual enthusiast looking to take control of your financial activity, CLN stands out as a powerful solution. Here's why you should consider exploring Greenlight by CLN, along with its myriad of groundbreaking features and benefits.
Key Features of Running a Core Lightning Node
Fast Setup and Customization
- Quick Compilation: CLN is engineered for speed, allowing users a swift setup process.
- Tailored for Businesses: The infrastructure of CLN can be customized to meet enterprise needs, making it a versatile option for different scales of operations.
Innovative Channel Management
- Dual-Funded Channels: CLN is the pioneer in supporting decentralized dual-funded channels, enhancing the flexibility and efficiency of operations.
- Cost and Time Efficiency: Setting up and running your node is made cost-effective through balanced channels, ensuring monetary and temporal efficiency.
- Dynamic Rebalancing: With features like PeerSwap, you can rebalance your channels using on-chain assets, enabling immediate routing and receipt of payments.
Enhanced Privacy Features
- Blinded Payment Paths: This experimental feature enhances the privacy of CLN nodes by masking sensitive information when receiving payments.
- Advanced Payment Techniques: Multi-part payments are automated, and the path selection is randomized, increasing the anonymity of transactions.
- Channel Diversity: Users can select a diverse set of channels, bolstering defenses against de-anonymization techniques.
Extensibility through Plugins
CLN’s architecture is uniquely designed to be fully modular, supporting a wide range of plugins that can be written in any popular programming language. This offers unmatched flexibility and the ability to tailor functionality to specific needs.
- Plugin Support: Users can power-up their CLN node with custom plugins, extending the functionality and integrating with existing systems seamlessly.
- Research-Backed Development: All development is spec-driven, maintained by the skilled research team at Blockstream, ensuring reliability and forward compatibility.
Feature Comparison Between Lightning Implementations
When compared to other implementations like LND and Eclair, CLN offers distinct advantages:
- Fully Modular vs. Monolithic: Unlike the monolithic architectures of LND and Eclair, CLN’s fully modular design provides better customization and easier maintenance.
- Privacy and Automation: Features like Multi-Part Payments and route randomization are default in CLN, providing superior privacy. Full automation is achievable with the CLBOSS plugin, surpassing the automation capabilities of its peers.
| Feature | Core Lightning (CLN) | LND | Eclair | |--------------------|-----------------------|-------------------|--------------------| | Architecture | Fully Modular | Monolithic | Monolithic | | Privacy | Advanced (default) | Optional | Optional | | Automation | Full with CLBOSS | Limited | None | | API | GRPC, JSON-RPC | GRPC, REST-API | JSON-API | | Liquidity Management| P2P with ads | Centralized | Manual |
Navigating the Future with CLN
By utilizing Core Lightning (CLN), users can not only enhance their operational efficiency but also significantly boost privacy and control over their transactions and liquidity management. The innovative features of CLN, combined with its user-friendly approach, make it a top choice for anyone serious about maximizing the potential of their Bitcoin and Lightning operations.
Explore More
- Liquidity Ads: Tap into a peer-to-peer network for discovering and managing liquidity efficiently.
- BOLT12 Invoices: Implement sophisticated invoicing systems with native support for recurring payments and authorization of spontaneous transactions.
CLN stands at the forefront of Lightning technology, providing a robust, versatile, and user-centric platform for managing Bitcoin transactions efficiently and privately. Whether you’re integrating into a business environment or managing personal finances, Core Lightning offers the tools and features necessary for a superior transactional experience.
For more detailed insights and to get started with your own CLN node, visit Core Lightning Documentation Portal. Embrace the future of decentralized finance with confidence and sophistication.
-
 @ d34e832d:383f78d0
2024-05-06 02:14:02
@ d34e832d:383f78d0
2024-05-06 02:14:02In the realm of Bitcoin, the process of reaching consensus on the validity of transactions forms the backbone of network stability and security. This consensus mechanism is integral not only for confirming transactions but also for adding new blocks to the blockchain. Understanding the intricate workings of this process clarifies how Bitcoin maintains its reliability and integrity in a decentralized manner. Here’s a comprehensive breakdown of how consensus is achieved within the Bitcoin network.
1. Transaction Broadcasting
Each Bitcoin transaction begins when a user initiates a transfer. This transaction is then broadcast to the entire network.
- Mempool Storage: Upon reception, nodes store these transactions in a temporary waiting area called the "mempool" (memory pool), where they await confirmation.
2. Mining and Proof-of-Work
The role of miners comes into play as they begin the process of creating a new block:
-
Solving Proof-of-Work: Miners select transactions from the mempool and attempt to solve a complex mathematical problem—known as Proof-of-Work (PoW). This task requires substantial computational effort and serves as the first line of defense against potential network abuse.
-
Block Creation: The first miner to solve the PoW problem gets the privilege to create a new block. This block contains the validated transactions along with the miner’s solution (nonce).
3. Block Verification and Addition
Once a new block is created, it isn't immediately added to the blockchain. Rather, it goes through a validation process:
-
Network Confirmation: Other nodes on the network independently verify the proposed block’s PoW and the legitimacy of the transactions within.
-
Chain Addition: If a block passes these verifications, it is appended to the blockchain. This step finalizes the transactions contained in the block.
4. Reaching Consensus
The addition of a block is the point where consensus is realized on the network:
- Blockchain Length and Security: Nodes naturally choose the longest available version of the blockchain, which represents the most cumulative PoW effort and hence, the majority consensus. This selection mechanism helps safeguard against alterations and potential network splits.
5. Recursive and Continuous Consensus
Bitcoin’s consensus process is ongoing:
-
Continued Verification: Each new block not only adds transactions but also serves as a check on all previous blocks, reinforcing the blockchain’s integrity through cumulative consensus.
-
Incentivization through Mining Rewards: Miners are rewarded for their efforts in maintaining and securing the network with block rewards, which include new Bitcoin and transaction fees. This reward system incentivizes miners to continue operating honestly.
6. Utilization of Cryptographic Techniques
Each transaction involves stringent cryptographic procedures:
- Digital Signatures: Transactions are signed digitally using the sender’s private key. This signature ensures that transactions are secure and cannot be altered. Only the sender's public key can verify the authenticity of this signature.
To Conclude
Bitcoin's consensus mechanism is a finely orchestrated process involving multiple steps of verification, problem-solving, and network-wide agreements. This sophisticated approach allows Bitcoin to operate securely and effectively without a central governing authority, relying instead on systematic, decentralized consensus protocols.
Bitcoin's infrastructure and innovation in achieving consensus have set precedents in the cryptographic and digital currency realms, illustrating robust solutions to digital trust and security.
For more in-depth technical insights into Bitcoin’s mechanism, consider exploring contributions and discussions within the Bitcoin developer community, such as those found on GitHub.
-
 @ d34e832d:383f78d0
2024-05-06 00:13:14
@ d34e832d:383f78d0
2024-05-06 00:13:14In the decentralized realm of Nostr, maintaining anonymity and safeguarding privacy are paramount, especially given the platform's open and unregulated nature. Using tools like Tor and Whonix in conjunction with the Nostr signer, Gossip, users can significantly enhance their security and privacy while using Nostr applications. This guide provides a comprehensive breakdown for both newbies and tech-savvy users on setting up a secure Nostr environment.
Using Tor with Nostr Applications
Tor, which stands for The Onion Router, is renowned for facilitating anonymous communication across the internet. Here’s how you can integrate Tor with your Nostr applications:
Step-by-step Guide to Using Tor:
- Download and Install Tor Browser: Begin by downloading the Tor Browser from the official Tor Project website.
```
"The Tor Browser is your gateway to using the internet with enhanced anonymity." ```
-
Connect to the Tor Network: Open the Tor Browser, which automatically routes your traffic through the Tor network, masking your real IP address and location.
-
Configure Your Nostr Client: Instruct your Nostr client to connect through Tor by routing connections through your relays and s, commonly .
- Example:
wss://nos.lol
Using Whonix with Nostr Applications(Gossip Signer)
For those seeking an additional layer of security, Whonix offers a potent solution by running on top of Tor, providing comprehensive privacy features.
How to Integrate Whonix:
-
Download and Install Whonix: Download Whonix from its official page.
-
Start Whonix and Connect to Tor: Boot into the Whonix system, which automatically employs Tor, providing an added security layer.
-
Install Nostr Client in Whonix:(Gossip Signer) Set up your Nostr client inside the Whonix environment, or access Nostr services through a secure (Gossip Signer) within Whonix.
-
Engage with Nostr Network: Once set up, your interactions on the Nostr network are securely routed through Tor via Whonix, ensuring maximum privacy.
Nostr Signer: Gossip
Integrating Gossip, a Nostr client and signer, further enhances your Nostr setup. Gossip can be configured to operate with the security settings of Tor and Whonix, making it a seamless addition to your secure Nostr configuration.
Access Gossip on GitHub: - Gossip GitHub Repository
Coupling Security Frameworks
The combination of Tor, Whonix, and Gossip provides a robust framework for engaging with Nostr. This setup not only enhances your security by obfuscating your digital footprint but also maintains the integrity of your communications across the Nostr network.
By taking these steps, users can enjoy the decentralized features of Nostr without trading off their privacy. Remember, the strength of privacy and security measures largely depends on proper setup and usage. Always stay updated with the latest security practices and updates from the developers of these tools.
Join the Nostr community with confidence, backed by a fortified setup that respects and protects your digital privacy.
A Step-by-Step Guide to Setting Up Whonix for Enhanced Internet Privacy
In the digital age, safeguarding online privacy has become a fundamental concern for many internet users. Whonix, a security-focused operating system that utilizes the Tor network, provides a robust solution for maintaining anonymity and securing online activities. This step-by-step guide will walk you through setting up Whonix on your device, ensuring you can enjoy enhanced internet privacy with ease.
Prerequisites
Before you start, ensure your system meets these requirements:
- Virtualization Support: Your computer must support Intel VT-x/AMD-V.
- Memory: At least 4GB of RAM is required; 8GB or more is recommended for optimal performance.
- Disk Space: Make sure you have at least 30GB of free disk space.
- Internet Access: Consistent internet access is necessary for downloading necessary files and updates.
Step 1: Install VirtualBox
VirtualBox is the software that will run your Whonix virtual machines. To install it:
- Visit the official VirtualBox website and download the latest version compatible with your operating system.
- Run the installer and follow the on-screen instructions to complete the installation.
Step 2: Download Whonix
Next, you will need to download the Whonix virtual machine images:
- Go to the official Whonix website and navigate to the "Download" section.
- Download the Whonix Gateway and Whonix Workstation virtual machine images (OVAs).
Step 3: Import Whonix into VirtualBox
Once you have the OVA files, you need to import them into VirtualBox:
- Open VirtualBox and select "File" > "Import Appliance."
- Choose the Whonix Gateway OVA file you downloaded, click "Next," review the import settings, and click "Import."
- Repeat this process for the Whonix Workstation OVA file.
Step 4: Configure Whonix Gateway
To set up the Whonix Gateway:
- Select the Whonix Gateway VM in VirtualBox.
- Click on "Settings" > "Network":
- For "Adapter 1", select "NAT."
- For "Adapter 2", select "Internal Network," and name it (e.g., "whonix-intnet").
Step 5: Configure Whonix Workstation
Setting up the Whonix Workstation involves a similar process:
- Choose the Whonix Workstation VM.
- Click on "Settings" > "Network":
- Ensure "Adapter 1" is set to "Internal Network" and uses the same name as in the Gateway settings.
Step 6: Start Whonix
Begin by starting the virtual machines:
- Launch the Whonix Gateway VM first.
- Once it's running, start the Whonix Workstation VM.
Step 7: Configure Network Settings in Whonix Workstation
To finalize the configurations:
- In the Whonix Workstation, navigate to "Applications" > "Settings" > "Networking".
- Ensure "sys-whonix" is selected as the NetVM for network routing.
After confirming the network settings, you're ready to start browsing anonymously.
Step 8: Start Browsing Anonymously
To browse the web anonymously using Whonix:
- Launch the Tor Browser within the Whonix Workstation.
- Enjoy enhanced privacy as your online activities are routed through the Tor network.
Step 9: Test Your Anonymity
Verify anonymity by visiting: - Tor Project's Check Page: Confirms if you're connected via Tor. - WhatsMyIP.org: Ensures your IP address is anonymized.
Additional Tips for Enhanced Privacy
- Regularly Update Whonix: Run
sudo apt-get updateandsudo apt-get dist-upgradein the terminal. - Exercise Caution with Downloads: Be wary of downloaded files or attachments.
- Use Secure Transfer Methods: For file transfers between the host and VM, utilize encrypted drives or encrypted cloud storage.
Closing Case
Setting up Whonix provides a powerful means to shield your internet presence, leveraging the anonymity of the Tor network integrated within a virtual environment. By following these steps, you can ensure robust privacy and security in your online endeavors. Always remember to stay informed about the latest security practices to safeguard your digital footprint effectively. Stay secure and maintain your privacy with confidence!
-
 @ d34e832d:383f78d0
2024-05-05 21:17:45
@ d34e832d:383f78d0
2024-05-05 21:17:45The decentralized nature of Nostr facilitates a network that is robust, user-driven, and significantly less prone to central points of failure, which plague conventional social platforms. Choosing the right relay server is critical to your experience on Nostr. Here, we explore how to select a Nostr relay server, delve into the public and paid relay dynamics, and offer insights on setting up your relay server.
Key Considerations When Choosing a Nostr Relay Server
The choice of a Nostr relay server should be guided by several important factors:
- Reliability: Opt for servers known for consistent uptime to ensure uninterrupted connectivity.
- Privacy: Select servers that prioritize privacy with strong encryption and policies against logging user data.
- Performance: Consider servers that provide low latency and high responsiveness.
- Community and Support: Choosing a relay server with a strong community and active developer presence can enhance the user experience due to regular updates and feature additions.
- Network Size: Servers with a broader network can facilitate better content discovery and user interaction.
- Cost: Analyze whether the relay server is free or requires a subscription, and align this with your budget.
- Compatibility: Ensure the relay server is compatible with your Nostr client application.
Understanding the Public Relay Challenge
While over 100 public relay servers are currently operational, such as those listed on Nostr relay finder, there's a notable challenge concerning spam due to the free nature of these servers:
"Public relays, while excellent for onboarding, face challenges with spam because there is no cost to post, making them targets for bots and spammers." -
Relay owners often employ reactive measures like blacklisting offending accounts, yet the efficacy can vary, requiring continuous vigilance.
The Benefits of Paid Relays
Paid relays offer a structured approach to using Nostr, potentially reducing spam due to the cost barrier:
- Enhanced Quality and Speed: Relays that charge a fee generally provide better performance and user experience.
- Reduced Spam: The entry cost dissuades most spammers, as their operations rely on high-volume, low-cost activities.
Where to Find Paid Relays
For those seeking a more controlled environment, several paid relays are available. These include:
Exploring Nostriches: A Dive into Paid Relays
In the expansive realm of decentralized networks like Nostr, the efficiency and reliability of relays are crucial for seamless communication and transaction processing. Paid relays serve as vital components in ensuring the smooth operation of these networks, offering enhanced performance and reliability compared to their free counterparts. Let's take a closer look at some prominent paid relays in the Nostr ecosystem:
1. Relay.nostriches.org
- Price: 421
- NPub Key: npub1vnmhd287pvxxk5w9mcycf23av24nscwk0da7rrfaa5wq4l8hsehs90ftlv
- Description: This relay provides a reliable and efficient connection for Nostr transactions, ensuring fast and secure communication between network participants.
2. Nostr.milou.lol
- Price: 1000
- NPub Key: npub1rvg76s0gz535txd9ypg2dfqv0x7a80ar6e096j3v343xdxyrt4ksmkxrck
- Description: Offering high-speed connectivity and robust performance, this relay is ideal for applications requiring low-latency communication and real-time transaction processing.
3. Bitcoiner.social
- Price: 1000
- NPub Key: npub1dxs2pygtfxsah77yuncsmu3ttqr274qr5g5zva3c7t5s3jtgy2xszsn4st
- Description: This relay specializes in facilitating transactions related to Bitcoin and other digital assets, providing a secure and reliable communication channel for Bitcoin enthusiasts.
4. Relay.nostr.nu
- Price: 2000
- NPub Key: npub1vvqnak4hz0u7vkv0vs5jp4ha0dt359cgvz4jj4y2ku85z0dtt6zq9pv3s8
- Description: With enhanced capacity and scalability, this relay is capable of handling a high volume of transactions, making it suitable for large-scale applications and platforms.
5. Relay.nostrati.com
- Price: 2000
- NPub Key: npub1qqqqqqqut3z3jeuxu70c85slaqq4f87unr3vymukmnhsdzjahntsfmctgs
- Description: This relay offers advanced security features and robust performance, making it an ideal choice for mission-critical applications and financial transactions.
6. Relay.nostrich.land
- Price: 2100
- NPub Key: npub1vj0wlergmkcs0sz7hfks2ywj555c2s87f40squ4sqcmqpr7897fqn6mfew
- Description: Providing a combination of speed, reliability, and security, this relay ensures smooth communication and transaction processing in the Nostr ecosystem.
7. Relay.orangepill.dev
- Price: 4500
- NPub Key: npub16jzr7npgp2a684pasnkhjf9j2e7hc9n0teefskulqmf42cqmt4uqwszk52
- Description: This high-performance relay offers enhanced security features and seamless integration capabilities, making it well-suited for demanding applications and enterprise use cases.
8. Eden.nostr.land
- Price: 5000
- NPub Key: npub16k7j4mwsqm8hakjl8x5ycrqmhx89lxkfwz2xxxcw75eav7sd8ztqy2rwdn
- Description: With its robust infrastructure and high availability, this relay ensures uninterrupted communication and transaction processing for applications operating in the Nostr ecosystem.
9. Nostr.inosta.cc
- Price: 5000
- NPub Key: npub1r34nhc6nqswancymk452f2frgn3ypvu77h4njr67n6ppyuls4ehs44gv0h
- Description: This relay offers reliable connectivity and comprehensive security features, making it a trusted choice for businesses and developers building applications on the Nostr platform.
10. Relay.nostr.com.au
- Price: 6969
- NPub Key: npub1qqqqqrre3jxkuyj3s4m59usdyvm0umgm0lpy6cqjtwpt649sdews5q3hw7
- Description: Providing exceptional performance and scalability, this relay is capable of handling the diverse needs of applications and platforms operating in the Nostr ecosystem.
Closing Thoughts
Paid relays play a crucial role in ensuring the reliability, security, and scalability of decentralized networks like Nostr. By offering enhanced performance and robust security features, these relays empower developers, businesses, and users to build and interact with applications with confidence. Explore the diverse range of paid relays available in the Nostr ecosystem and unlock the full potential of decentralized communication and transaction processing.
These relays often require contacting the relay operator directly to get access, where your public key will be whitelisted post-payment.
Setting Up Your Own Paid Relay
For those interested in contributing more actively to Nostr, setting up a paid relay can be both a community service and a potential business opportunity, especially when combined with a Lightning routing node. A comprehensive guide on starting your relay can be accessed from reputable sources like Guide for Strfry Setup.
Closing Thoughts
Choosing the right Nostr relay server is more than a technical decision—it’s about aligning with your communication needs and how you want your social media experiences to be shaped. Whether opting for public, paid, or setting up your relay, each choice offers different advantages and challenges. As the ecosystem grows, so too will the options and innovations in relay services, continuously enhancing the way we connect and interact in the decentralized social media landscape.
Explore different relays, engage with the community, and take control of your social media experience on Nostr.
-
 @ d34e832d:383f78d0
2024-05-05 20:05:58
@ d34e832d:383f78d0
2024-05-05 20:05:58In an era where questions about data privacy, censorship, and central control are more pressing than ever, the future seems bright for decentralized social media platforms, with Nostr leading the charge. This emerging protocol is reshaping the landscape, offering a blueprint for what social media can become: more secure, user-centric, and radically open.
Overview of Nostr's Decentralized Features
Nostr stands out by empowering users and developers through several key features:
- Decentralization: Unlike traditional platforms, Nostr doesn't have a central control point. This model gives users complete control over their data and content, mitigating risks like censorship and data breaches.
"Decentralization ensures that users have the ultimate authority over their interactions and information, unlike centralized counterparts where user data can be manipulated or sold."
-
Openness: The protocol is open-source, enabling anyone to build applications on Nostr without requiring permission. This openness promotes a fertile environment for rapid innovation and diverse application development.
-
Interoperability: Applications built on Nostr are interoperable, allowing users to switch seamlessly between different apps without losing data or connections, enhancing user experience and choice.
-
Scalability: With lightweight data structures at its core, Nostr can scale efficiently to support a large user base and significant data volumes without sacrificing performance.
-
Bitcoin Integration: Incorporating features like Bitcoin Lightning Network support, Nostr integrates financial transactions into the social media experience, offering new monetization avenues for creators.
Advanced Features Enhancing User Agency in Nostr Clients
To further enhance user experience, developers can integrate sophisticated features into Nostr clients:
-
Customizable Filters: Users can set filters based on keywords, authors, or content types, making content discovery more tailored and efficient.
-
Lists: This feature allows users to organize content by creating personalized lists of favorite authors or topics, enhancing the manageability of their feeds.
-
Mute/Unmute Options: Users can control their content feed more directly by muting authors or topics that they find irrelevant or bothersome.
-
Bookmarks: Users can bookmark messages or create collections of favorite posts, simplifying access to preferred content.
-
Granular Privacy Settings: These settings give users precise control over their visibility and interaction level on the platform, from profile viewing rights to interaction permissions.
-
Real-Time Notifications: By implementing notifications, users remain engaged and informed about important interactions and updates.
-
Reactions and Customized Responses: Enabling diverse reaction options allows users to express feelings or thoughts more vividly and interactively.
-
Translations: Integration of translation services can break language barriers, expanding user interaction across different linguistic demographics.
-
Content Moderation Tools: Features that allow users to flag inappropriate content or block disruptive users are essential for maintaining a positive environment.
-
Social Graph Visualization: Visual tools that map out a user’s network can provide valuable insights into their social interactions and community dynamics.
Nostr Clients and Resources
For those looking to explore Nostr through practical applications, both desktop and mobile clients are available:
- DeskTop:
- Damus for macOS: A feature-rich desktop client designed to streamline user experience on macOS.
-
Nostrmo for Desktop: A cross-platform client that brings enhanced functionality to desktop devices.
-
Mobile:
- Damus for iOS: Seamlessly integrate Nostr on your iPhone with this robust iOS client.
- Amethyst for Android: Experience Nostr on Android devices with this fully functional client offering a range of features.
Closing Case
As Nostr continues to evolve and gain traction, we anticipate seeing a significant shift in how social media platforms operate. The core principles of privacy, user control, and open innovation that Nostr champions are likely to set new standards in the technology community.
For those interested in exploring deeper or contributing to Nostr's development, additional resources such as Nostr's GitHub Repository and community tutorials on Nostr.how provide excellent starting points.
Join the movement toward a decentralized, user-driven social media landscape. Build, interact, and innovate with Nostr — shaping the future of digital communication.
Introducing NostrSigningDevice: Revolutionizing Secure Transactions
In the rapidly evolving landscape of digital transactions, security and reliability are paramount. Enter NostrSigningDevice, a cutting-edge solution poised to revolutionize secure transactions in the digital realm.
Secure Transactions Made Simple
NostrSigningDevice offers a seamless and secure platform for signing transactions, ensuring the authenticity and integrity of each digital interaction. Whether you're processing payments, verifying contracts, or executing smart contracts, NostrSigningDevice provides the robust security measures necessary to safeguard sensitive data and transactions.
Key Features:
1. Hardware Security Module (HSM) Integration
NostrSigningDevice leverages Hardware Security Modules (HSMs), specialized hardware devices designed to securely store cryptographic keys and perform cryptographic operations. By integrating HSMs into its infrastructure, NostrSigningDevice ensures the highest level of security for transaction signing, protecting against unauthorized access and tampering.
2. Multi-Factor Authentication (MFA)
With multi-factor authentication (MFA) capabilities, NostrSigningDevice enhances the security of transactions by requiring multiple forms of verification before authorizing a transaction. This layered approach to authentication mitigates the risk of unauthorized access and strengthens the overall security posture of the platform.
3. Seamless Integration with Nostr Ecosystem
NostrSigningDevice seamlessly integrates with the broader Nostr ecosystem, providing a unified platform for secure digital transactions. Whether you're a developer building Nostr-powered applications or a business leveraging Nostr's decentralized infrastructure, NostrSigningDevice offers a cohesive solution for transaction signing across the ecosystem.
4. Developer-Friendly APIs
Developers can easily integrate NostrSigningDevice into their applications using intuitive APIs and SDKs. With comprehensive documentation and developer resources, NostrSigningDevice empowers developers to leverage its robust security features without compromising on usability or flexibility.
5. Compliance and Regulatory Support
NostrSigningDevice is designed with compliance and regulatory requirements in mind, offering features and functionalities to support adherence to industry standards and regulations. Whether you operate in finance, healthcare, or any other regulated industry, NostrSigningDevice provides the necessary tools to maintain compliance while ensuring secure transactions.
Unlock the Power of Secure Transactions with NostrSigningDevice
Whether you're a financial institution, enterprise, or individual user, NostrSigningDevice offers a trusted solution for secure transaction signing in the digital age. With its advanced security features, seamless integration capabilities, and compliance support, NostrSigningDevice is poised to redefine the standards for secure digital transactions.
Visit NostrSigningDevice today to learn more and unlock the power of secure transactions in the Nostr ecosystem.
-
 @ d34e832d:383f78d0
2024-05-05 16:49:58
@ d34e832d:383f78d0
2024-05-05 16:49:58Creating your first Nostr client application is an exciting journey into the world of decentralized communication. Nostr, an emerging protocol that fosters open and global communication free from centralized control, offers developers a unique opportunity to contribute to the future of social interactions on the internet. Here's a detailed guide to help both new and seasoned developers embark on building their own Nostr client application.
Step 1: Choose Your Programming Language
The first step in building your Nostr client is selecting a programming language. Popular choices include:
- JavaScript: Widely used, with extensive support for asynchronous operations which are crucial in client-server communications.
- Python: Known for its simplicity and readability, making it an excellent choice for beginners.
- Go: Offers robust network programming capabilities, perfect for handling concurrent tasks.
```markdown
"Choose a language that you are comfortable with, or that best suits the needs of the project." ```
Step 2: Set Up Your Development Environment
Once you've picked a programming language, set up your development environment. This involves:
- Installing necessary compilers or interpreters.
- Setting up package managers (like npm for JavaScript, pip for Python).
- Installing dependencies and libraries needed for Nostr.
Ensure that your development tools are up to date to avoid compatibility issues.
Step 3: Dive Into the Nostr Protocol
To effectively build on Nostr, understanding the protocol is crucial. Familiarize yourself with:
- Message Types: Know the different kinds of messages that can be sent and received.
- Event Structure: Understand how data is structured within the system.
- Client-Server Communication: Grasp the methods used for data exchange between clients and servers.
The Nostr protocol documentation on GitHub is an excellent resource for getting detailed and technical insights.
Step 4: Implement Basic Functionality
Start coding by implementing fundamental functionalities:
- Connect to a Relay Server: This is your application's gateway to receiving and sending messages.
- Subscribe to Events: Allows your app to listen for new data related to specific topics or users.
- Send Events: Enable your app to publish messages to the network.
Use libraries or SDKs specific to your chosen programming language to simplify these interactions.
Step 5: Add User Authentication
Security is paramount, especially in decentralized networks. Implement user authentication by:
- Generating and managing public and private keys.
- Using cryptographic libraries to handle key generation securely.
This not only ensures secure sign-ins but also maintains user privacy and data integrity.
Step 6: Build a User Interface
Your client needs a user-friendly interface. Design your UI to be intuitive and accessible, incorporating features like:
- Posting Messages: Users should be able to easily compose and send messages.
- Interactions: Allow liking, replying, and following other users.
- Search Functionality: Users may want to search for specific content or profiles.
Step 7: Test Your Application
Before going live, rigorously test your application to iron out any bugs and ensure all features are functioning correctly. Consider:
- Unit testing individual components.
- Integration testing to see how different parts interact.
- Beta testing with potential users to gather feedback.
Step 8: Deploy Your Application
Once satisfied with your application's functionality and stability, deploy it. Choose a reliable hosting platform that aligns with your needs and budget. Ensure your deployment processes include regular updates and maintenance checks.
Conclusion
Building a Nostr client application is a rewarding project that contributes to a more decentralized and open future of social networking. By following these steps, you can create a robust and user-friendly Nostr client that leverages the full potential of this promising protocol. Embark on this technical adventure and be part of a community reshaping communication across the globe.
Exploring Resources for Building Nostr Apps with NDK Library
If you're interested in building apps using the Nostr Development Kit (NDK) library, there are several valuable resources available online to guide you through the process. Whether you're a beginner or an experienced developer, these tutorials and documentation sources can help you kickstart your Nostr app development journey.
1. nostr.how
Description: This website offers a comprehensive step-by-step guide to assist you in creating your first Nostr app. It covers various programming languages such as JavaScript, Python, or Go, catering to a diverse range of developers. The guide provides detailed instructions, making it suitable for beginners looking to explore Nostr development.
2. nostr-dev-kit/ndk
Description: The official GitHub repository for the NDK library is an invaluable resource for developers. It contains extensive documentation, examples, and code snippets to facilitate the integration of Nostr functionality into your applications. Whether you're looking to understand the library's features or need guidance on implementation, this repository has you covered.
3. nostr-resources.com
Description: Nostr Resources is a dedicated website offering a plethora of tutorials, libraries, and projects related to Nostr development. Whether you're looking for additional learning materials, libraries to enhance your app's functionality, or inspiration from existing projects, this website serves as a comprehensive hub for all things Nostr.
By leveraging these resources, you can embark on your Nostr app development journey with confidence. Whether you're aiming to build a simple application or dive into more complex projects, these tutorials, documentation, and community-driven platforms will provide the support you need to succeed.
Happy Nostr app development!
Happy coding, and here's to building a more connected and decentralized world!
-
 @ d34e832d:383f78d0
2024-05-05 15:34:18
@ d34e832d:383f78d0
2024-05-05 15:34:18Bitcoin, renowned for its P2P nature, also exemplifies how to secure a digital currency against a myriad of potential threats. Here’s a comprehensive look at the various measures in place designed to uphold the security of the Bitcoin network
Understanding Bitcoin's Security Measures
1. Proof of Work (PoW)
The foundation of Bitcoin's resilience is the Proof of Work algorithm. It compels miners to solve complex mathematical problems to validate transactions and mine new blocks, making any attack costly and technically demanding.
``` Impact of PoW:
"PoW makes it economically unsustainable for attackers to alter any aspect of the blockchain."
```2. Mempool Policies
Bitcoin controls which transactions are allowed into the next block through strict mempool policies. This prevents spam transactions which can clog the network under an array of transactions with minimal fees.
``` Role of Mempool Policies:
"By enforcing rules about the format, size, and fee requirements, Bitcoin ensures only legitimate transactions are processed." ```
3. Peer Address Bucketing and Protection
To counteract eclipse attacks—where an attacker might dominate a node's connections—Bitcoin nodes utilize peer address bucketing. This diversity prevents attackers from isolating a node from the rest of the network.
``` Preventing Eclipse Attacks:
"Diverse peer connections essential for the decentralization that Bitcoin aims for." ```
4. Blockrelay-only Connections
These connections allow nodes to receive blocks without exposing transaction details, effectively minimizing the risk of an eclipse attack.
5. Misbehaving Peer Disconnection
Nodes monitor peers consistently and disconnect from those that show signs of suspicious activity or protocol violations, which preserves network resources and counters denial-of-service attacks.
``` Monitoring Peers:
"Active surveillance of peer activities ensures a robust defensive perimeter." ```
6. Peer Rotation and Eviction
Regular rotation and eviction of peers ensure no single participant can monopolize a node’s network, enhancing security against both Sybil and eclipse attacks.
7. Protected and Anchor Peers
Certain peers are assigned as 'protected' or 'anchor' to ensure nodes have stable, reliable connections to well-known, good actors within the network. This defense strategy ensures continuity and reliability.
Evolving Threats and Proactive Improvements
The Bitcoin network’s security measures are not static; they evolve to address new vulnerabilities and sophisticated attack vectors as they arise. Discussions and developmental insights can be seen actively on platforms like GitHub under various pull requests and issues discussion, enriching community engagement and development.
Closing Thoughts
Bitcoin’s multilayered security strategies demonstrate its architectural sophistication in safeguarding users' assets. Through proactive community involvement and constant technological advancements, Bitcoin continues to stand as a paragon of secure, P2P digital energy. Interested readers can dive deeper into specific discussion and updates on GitHub linked below.
Further Reading and Sources
Stay secure and informed as we forge ahead in the continually evolving landscape of Bitcoin.

Fortifying the Bitcoin Lightning Network: A Security Overview
The Bitcoin Lightning Network, an innovative layer enabling faster transactions than the Bitcoin main chain, faces unique security challenges intrinsic to its design as a real-time gross settlement system. Here, we delve into the various protective strategies vital for safeguarding Lightning nodes against unauthorized access and potential attacks, tailored to both new and seasoned participants in the cryptocurrency space.
Holistic Approach to Security
The security of a Lightning node isn't about focusing on one single facet; it's about fortifying every layer of the system.
```
"Security for a Lightning node encompasses every layer of the system, from network access points to the storage of private keys." ```
This holistic approach forms the backbone of effective security strategy, emphasizing that a chain is truly only as strong as its weakest link.
Regular Updates and Patches
One of the most crucial practices in maintaining a secure node is keeping the software up to date. This includes:
- Regular updates to Lightning software like LND, c-lightning, and Eclair
- Applying patches to the node's operating system to close any vulnerabilities that could be exploited by malicious actors
``` Consistent Updates:
"Staying updated with the latest software patches is essential to protect against known exploits and vulnerabilities." ```
Limiting Exposure
Given the experimental stage of the Lightning Network, limiting the amount of funds put at risk is wise:
- Only allocate an amount of money that you are comfortable potentially losing
- Use multiple nodes to diversify risk rather than placing all funds into a single node
Secure Storage of Keys
The keys that control funds on the node must be securely stored because they are a prime target for theft:
- Encrypting the hard disk where keys are stored
- Utilizing hardware modules designed for secure key storage
- Implementing multi-factor authentication to increase security layers
``` Key Security:
"The secure storage of keys is paramount, involving strategies ranging from disk encryption to the use of specialized hardware security modules." ```
Enhanced Network Security Measures
Network security can prevent many external attacks:
- Setting up robust firewalls
- Monitoring network traffic for any unusual activities
- Securing endpoints to guard against intrusion
Educational Empowerment
Encouraging continuous education regarding security updates, threats, and best practices is essential. Knowledge empowers users to make informed decisions and recognize potential security threats before they manifest.
Community and Developer Support
Leveraging community knowledge and developer support can provide solutions and guidance for any security concerns that arise:
- Engage with forums and read publications from trusted sources
- Participate actively in community support channels like Lightning Dev mailing list
Closing Case
The security of the Bitcoin Lightning Network is a dynamic, ongoing process that demands vigilance, proactive strategies, and a well-rounded approach. By understanding and implementing these detailed protective measures, users and operators can significantly enhance the security integrity of their Lightning operations.
Further Learning and Official Documentation
For those looking for more depth on operating a Lightning node securely, consider the following resources:
- The GitHub Lightning Book provides extensive information on node operations and security.
- Engaging with the developmental community through active forums and mailing lists can offer real-time insights and help.
Secure, learn, and evolve; your journey in the Lightning Network awaits!
-
 @ d34e832d:383f78d0
2024-05-05 08:30:22
@ d34e832d:383f78d0
2024-05-05 08:30:22Specific challenges coupling the use of differential heuristics in A* algorithm aim to overcome in the Lightning Network
The Lightning Network presents a labyrinth of challenges when it comes to efficient routing, with obstacles like varying channel capacities, fees, and availability complicating the process. Differential heuristics within the A algorithm are engineered to tackle these obstacles head-on, aiming to overcome specific challenges, including:
 Reducing the Number of Nodes Visited During Pathfinding*
Reducing the Number of Nodes Visited During Pathfinding*In the sprawling expanse of the Lightning Network, conventional pathfinding algorithms often get lost in a maze of possibilities. Differential heuristics act as a guiding light, leading the search algorithm directly to the optimal route while minimizing the number of nodes visited. This efficiency streamlines the pathfinding process, as highlighted in [0].
 Handling Irregular Terrain or Obstacles
Handling Irregular Terrain or ObstaclesJust as hikers navigate rugged landscapes, differential heuristics navigate the irregular topology of the Lightning Network. Each channel represents a unique terrain feature, with its own set of challenges. By adapting to these obstacles, differential heuristics optimize routing decisions, ensuring transactions flow smoothly across the network ([2]).
 Improving Pathfinding Efficiency
Improving Pathfinding EfficiencyTime is of the essence in Lightning Network transactions. Differential heuristics inject speed into the pathfinding process by leveraging multiple heuristics and their differences. This optimization not only saves computational resources but also ensures lightning-fast routing, essential for seamless transactions ([4]).

Adapting to Dynamic Changes
The Lightning Network is in constant flux, with channels opening, closing, and balances shifting. Differential heuristics are adept at navigating this ever-changing landscape, adjusting their strategies dynamically. While cached data may need occasional recalibration, the adaptability of differential heuristics ensures swift responses to network dynamics ([5]).
In essence, differential heuristics within the A* algorithm serve as beacons of efficiency in the Lightning Network's intricate web. By addressing challenges related to pathfinding efficiency, dynamic adaptability, and network complexity, they pave the way for smoother transactions and an enhanced user experience.
Sources: - [0]: Optimizing Pathfinding Efficiency - [1]: Improving Payment Success Rates - [2]: Navigating Irregular Terrain - [3]: Ensuring Security and Privacy - [4]: Efficient Pathfinding Strategies - [5]: Understanding Lightning Network Dynamics
-
 @ d34e832d:383f78d0
2024-05-05 06:46:49
@ d34e832d:383f78d0
2024-05-05 06:46:49The Lightning Network, a second-layer solution built on top of the Bitcoin blockchain, offers a promising avenue for fast and cost-effective transactions. However, routing payments through this network presents its own set of challenges. Let's delve into the different approaches to routing transactions on the Lightning Network and how they address these challenges.
Source Routing
Traditionally, the Lightning Network has relied on source routing, where the sender calculates the entire payment route before initiating the transaction. While this method ensures strong privacy since only the sender knows the complete path, it can become less efficient as the network grows due to the increasing complexity of finding optimal routes.
JITRouting (Just-In-Time Routing)
JITRouting is an improvement that learns from past routing attempts. When a payment fails, the network uses this information to avoid inefficient paths in future attempts. This adaptive approach enhances routing efficiency by leveraging past failures to guide future routing decisions.
Multipath Payments (MPP)
To overcome the limitations of single-path payments, Lightning incorporates Multipath Payments (MPP). This approach splits a payment into smaller parts routed separately through the network, increasing the likelihood of successfully routing large payments without relying on a single path with sufficient capacity.
Use of Differential Heuristics in A* Algorithm
The Lightning Network community explores the use of differential heuristics in the A* algorithm for map preprocessing. This technique reduces the number of nodes visited during pathfinding, especially in complex network topologies, optimizing route discovery and enhancing network efficiency.
Permuteroute Algorithm
The Permuteroute algorithm offers an alternative approach to route discovery by efficiently finding paths between nodes without scanning a large number of channels. While providing immediate benefits, it is considered alongside broader improvements like incorporating past pathfinding attempts into mission control within Lightning software.
Collaborative Routing with Routing Hints
Collaborative routing involves using routing hints included in payment requests to suggest intermediate nodes or channels that could facilitate the payment. This method improves routing efficiency and potentially enhances privacy by offering multiple route options.
These diverse approaches underscore the ongoing development and optimization efforts within the Lightning Network community. By leveraging these strategies, the Lightning Network aims to provide a scalable, efficient, and private framework for routing micropayments over Bitcoin.
Sources:
- [0]: GitHub Discussion on Lightning Network Routing
- [1]: Understanding Multipath Payments on Lightning Network
- [2]: Exploring Differential Heuristics in A* Algorithm
- [3]: Permuteroute Algorithm Proposal
- [4]: Collaborative Routing with Routing Hints
Harnessing the Power of Multipath Payments in Lightning Network Routing
Can multipath payments be used in combination with other routing strategies to further enhance routing efficiency?
Multipath payments (MPP) offer a promising avenue to improve routing efficiency on the Lightning Network. When integrated with other routing strategies, MPP not only enhances transaction success rates but also optimizes fee management, privacy, and network load distribution.
Combining MPP with Source-Based Pathfinding
Source-based pathfinding, where the sender calculates the route, can be seamlessly integrated with MPP. By splitting large payments into smaller parts and finding multiple optimal routes simultaneously, this combination improves success rates while balancing the network load. This approach, as discussed in [3], ensures better channel capacity utilization and reduces congestion.
MPP and JIT Routing
Just-In-Time Routing (JITRouting), while not explicitly mentioned in the provided context, dynamically adjusts routing decisions based on real-time network conditions. When paired with MPP, JITRouting can adapt the sizes of payment parts or choose different routes based on changing channel capacities. This adaptive strategy ensures efficient payment completion, even in the face of sudden network changes.
Strategic Fee Optimization
Leveraging MPP allows senders to strategically optimize fees by choosing the most cost-effective paths for each payment fragment, as suggested in discussions from [0] and [5]. By splitting payments and selecting routes based on fee structures, this approach minimizes transaction costs without compromising efficiency.
Enhancing Privacy with MPP
Integrating MPP with privacy-enhancing techniques, such as onion routing for each part of a multipath payment, further obscures transaction trails. By diversifying payment paths, MPP makes it challenging for observers to trace fund movements, enhancing overall transaction privacy.
Incorporating MPP into Lightning Network Routing
Incorporating MPP into Lightning Network routing strategies not only addresses the limitations of individual approaches but also maximizes their strengths. This synergy results in a more resilient, efficient, and private Lightning Network, showcasing the ongoing innovation within the Lightning community.
By harnessing the power of MPP alongside other routing strategies, the Lightning Network continues to evolve, offering faster, more cost-effective, and private transactions for users worldwide.
Sources: - [0]: Linux Foundation - MPP and Fee Optimization - [1]: Linux Foundation - Privacy Enhancement with MPP - [2]: Linux Foundation - JITRouting and MPP - [3]: Lightning Network Book - Understanding Routing Strategies - [4]: Linux Foundation - Optimizing Network Load with MPP - [5]: Linux Foundation - Strategic Fee Optimization

Maximizing Routing Effectiveness with Routing Hints in the Lightning Network
How do routing hints improve collaborative routing effectiveness in the Lightning Network?
Routing hints serve as invaluable tools within the Lightning Network, significantly enhancing collaborative routing effectiveness by providing essential information to streamline payment processes. These hints, embedded within payment requests, offer insights into potential routes or intermediate nodes, optimizing transaction pathways and bolstering network efficiency.
Facilitating Payments Through Unannounced Channels
Unannounced channels, concealed from the public channel graph, are vital components of Lightning Network transactions. Routing hints, as detailed in [2] and [3], empower payments to navigate through these hidden channels effectively. By leveraging routing hints, participants can exploit unannounced channels, expanding routing options and bolstering the network's capacity to facilitate transactions discreetly.
Improving Payment Success Rates
Routing hints enhance payment success rates by revealing alternative paths beyond the public network graph, as discussed in [0]. When conventional routes face constraints such as capacity limitations, routing hints offer alternative pathways, ensuring smoother transaction completion. This flexibility minimizes transaction failures and optimizes the overall efficiency of the Lightning Network.
Enhancing Privacy and Security
Beyond facilitating payment delivery, routing hints fortify transaction privacy and security. By steering transactions away from heavily monitored channels, these hints safeguard user anonymity. Moreover, routing hints contribute to security by diversifying transaction pathways, mitigating potential threats targeting transaction flows, as highlighted across the provided sources.
Supporting Decentralization Efforts
Routing hints play a pivotal role in advancing the Lightning Network's decentralization agenda. By empowering payments to traverse diverse channels, including unannounced ones, these hints foster network inclusivity. Smaller nodes and those with unannounced channels can actively participate, redistributing routing responsibilities and promoting a more decentralized network architecture.
In essence, routing hints are indispensable elements that bolster collaborative routing within the Lightning Network. By expanding routing possibilities, enhancing privacy, and supporting decentralization initiatives, routing hints contribute to a more robust and efficient Lightning Network ecosystem.
Sources: - [0]: Enhancing Payment Success Rates - [1]: Understanding Lightning Network Routing - [2]: Exploring Channel Graph Dynamics - [3]: Ensuring Security and Privacy - [4]: Navigating Through Unannounced Channels - [5]: Optimizing Routing Efficiency - [6]: Advancing Transaction Privacy - [7]: Strategies for Routing HTLCs
-
 @ d34e832d:383f78d0
2024-05-03 05:31:59
@ d34e832d:383f78d0
2024-05-03 05:31:59
Bitcoin mining has often been critiqued for its environmental impact and energy consumption. However, a deeper dive reveals a nuanced story where innovative strategies are turning mining into a viable and sustainable part of the future energy economy. The key to this transformation? Harnessing stranded energy resources and user-contributed processing power to enhance network security and efficiency.
Utilizing Stranded Energy: A Win-Win Situation
Stranded energy refers to energy produced from sources that are geographically isolated or temporally inconsistent, making it difficult or economically unfeasible to transport this energy to places where it can be used. Examples of stranded energy include overproduced wind power on windy nights or flared natural gas at oil production sites unable to connect to the natural gas grid.
Bitcoin mining offers a revolutionary solution by using this otherwise wasted energy. By setting up mining operations near sources of stranded energy, miners can convert excess energy into economic value without the extensive carbon footprint associated with long-range energy transmission. This synergy not only makes mining operations more sustainable but also encourages the development and funding of renewable energy projects.
The Role of User-Provided Processing Power
When individuals contribute their computing resources to the Bitcoin network, they help decentralize the network. This decentralization is vital—it prevents any single entity from monopolizing the network, thereby enhancing security. This is described technically as increasing the network’s 'hash rate,' which essentially strengthens the network’s resilience against attacks.
- Security enhancement: A higher hash rate means that an attacker would need a prohibitively expensive amount of computing power to compromise the network.
- Democratic participation: By allowing anyone with a computer to contribute to the network's processing power, Bitcoin remains open and accessible, upholding its foundational principles.
Efficiency and Profitability in Mining Operations
The profitability of Bitcoin mining hinges largely on two factors: the cost of electricity and the efficiency of mining hardware. Regions with lower energy costs naturally attract more miners, but the efficiency of the operation also plays a crucial role. Advanced mining hardware that can compute more hashes per joule of energy consumed dictates the competitive edge.
- Operational efficiency: Utilizing cutting-edge technology that maximizes hash power while minimizing energy consumption is crucial. Efficient operations use less power for the same or higher output, directly influencing the bottom line.
- Adaptability: Miners must rapidly adapt to changes in network difficulty and Bitcoin price fluctuations to stay profitable.
Case in Closing
Far from being a static or regressive industry, Bitcoin mining exemplifies innovative adaptation to our rapidly changing energy landscape. By tapping into stranded energy sources, miners can transform waste into wealth, affirming Bitcoin mining's role in a sustainable energy future. Additionally, by encouraging broad, P2P participation, the network remains secure and robust against threats. On the front of profitability, efficiency remains key. The miners who will thrive are those who not only manage costs effectively but also innovate continuously to keep up with technological and economic shifts. Bitcoin mining is not just surviving; it's poised for a natural, profitable future.
P.S
Dear Parker Lewis,
I wanted to extend my gratitude for introducing the concept of Utilizing Stranded Energy during your online talk I look forward to continuing to follow your work and learning more about this fascinating intersection of energy and Bitcoin.
Thank You
-
 @ d34e832d:383f78d0
2024-05-02 20:05:43
@ d34e832d:383f78d0
2024-05-02 20:05:43
Bitcoin's security and decentralization stand as pillars upon which its entire ecosystem is built. At the heart of this structure lies Bitcoin mining, a process that not only validates transactions but also fortifies the network against malicious attacks. Let's delve into the intricate dance between mining, security, and decentralization that sustains the world's most renowned cryptocurrency.
Unraveling Bitcoin Mining
Mining, in the context of Bitcoin, involves a network of validators, known as miners, dedicating computational power to solve complex mathematical puzzles. These puzzles serve as a gatekeeper, ensuring that only legitimate transactions find their way onto the blockchain. As miners successfully solve these puzzles and add blocks to the chain, they are rewarded with newly minted bitcoins and transaction fees. This intricate process accomplishes several crucial tasks:
1. Transaction Validation and Network Security
Mining acts as a shield, safeguarding the integrity of Bitcoin transactions. By aggregating transactions into blocks and cryptographically linking them to the existing blockchain, miners make it virtually impossible for fraudulent activities to occur without detection. Any attempt to alter a transaction would necessitate re-mining affected blocks, a task so computationally intensive that it serves as a formidable deterrent against foul play.
2. Decentralization
At the core of Bitcoin's ethos lies decentralization, and mining is the mechanism that brings this vision to fruition. By distributing the responsibility of transaction validation across a global network of independent miners, Bitcoin ensures that power remains diffused. This decentralized structure mitigates the risk of a single entity gaining undue influence over the network, preserving its resilience and trustworthiness.
3. Consensus Mechanism
Bitcoin's Proof-of-Work (PoW) consensus mechanism relies on mining to maintain order and security within the network. Through PoW, miners engage in a competitive race to validate transactions and append blocks to the blockchain. This competition not only ensures the network's robustness but also makes it economically infeasible for malicious actors to orchestrate a 51% attack—a scenario where a single entity controls the majority of the network's computational power.
4. Network Resilience
By incentivizing miners with rewards, Bitcoin fosters a community of nodes committed to upholding network security. This incentive structure not only attracts participants but also ensures a continuous supply of computational power dedicated to maintaining the network's integrity. As a result, Bitcoin remains resilient against external threats, capable of withstanding adversarial attempts to disrupt its operations.
The Ongoing Evolution of Mining
The importance of mining for Bitcoin's security and decentralization cannot be overstated. Continuous discussions and improvements within the community underscore the commitment to enhancing mining efficiency, reducing environmental impact, and bolstering network resilience. These efforts, evident in open forums and developer contributions, lay the groundwork for Bitcoin's continued success and longevity in the ever-evolving landscape of digital finance.
In closing, mining stands as a cornerstone of Bitcoin's architecture, underpinning its security, decentralization, and trustworthiness. As Bitcoin continues to redefine the financial landscape, mining remains steadfast in its role as the guardian of the network's integrity, ensuring that the promise of decentralized, censorship-resistant digital currency endures.
Sources
[0]: Bitcoin Core GitHub Pull Request [1]: Bitcoin Core GitHub Pull Request [2]: Bitcoin Core GitHub Issue [3]: Bitcoin Core GitHub Pull Request [4]: Bitcoin Core GitHub Issue [5]: Chaincode Labs Glossary [6]: Bitcoin Core GitHub Issue [7]: Bitcoin Core GitHub Pull Request [8]: Bitcoin Core GitHub Issue [9]: Bitcoin Core GitHub Pull Request
A Deeper Look At The Future Ahead
Emerging technologies and innovations continue to shape the field of Bitcoin mining, potentially impacting its future in various ways. Some of the notable developments include:
Advancements in Mining Hardware: Continuous improvements in the efficiency and processing power of ASIC (Application-Specific Integrated Circuit) miners enhance the competitiveness and profitability of mining operations. Innovations that reduce power consumption while increasing hash rates can significantly impact the sustainability and environmental footprint of Bitcoin mining.
Renewable Energy Sources: There's a growing trend towards utilizing renewable energy sources for Bitcoin mining operations. Solar, wind, hydroelectric, and geothermal energy can provide more sustainable and cost-effective power solutions. This shift not only addresses environmental concerns but also aligns with the broader goals of enhancing the long-term sustainability of the mining industry.
Decentralized Mining Pools: Innovations in pool structures and protocols aim to further decentralize mining efforts. By distributing control and decision-making among pool participants, these technologies can mitigate the risks associated with centralized pools dominating the hash rate distribution. This could lead to a more equitable and resilient mining ecosystem.
Improved Cooling Technologies: Efficient cooling solutions are critical for maintaining optimal operation of mining hardware. Advances in cooling technologies, such as immersion cooling systems, promise to significantly reduce the energy consumption associated with mining. These innovations can lead to lower operational costs and extend the lifespan of mining equipment.
Blockchain Interoperability and Layer 2 Solutions: While not directly related to mining technology, advancements in blockchain interoperability and the development of Layer 2 solutions (such as the Lightning Network) can indirectly affect Bitcoin mining by altering transaction patterns, fees, and the overall scalability of the network.
Smart Contracts and Mining Protocols: The integration of smart contracts into mining operations could automate certain aspects of the mining process, including payouts, pool governance, and compliance with regulatory requirements. This could streamline operations and introduce new levels of transparency and trustworthiness.
These innovations represent just a fraction of the ongoing research and development within the Bitcoin mining sector. As the ecosystem evolves, it's likely that we'll see further advancements that address current challenges related to energy consumption, efficiency, decentralization, and environmental impact. The active engagement of the community, as seen in discussions on platforms like GitHub ([0], [1], [5]), will continue to play a crucial role in guiding these developments and shaping the future landscape of Bitcoin mining.
Sources
[0]: GitHub Issue 2345 [1]: GitHub Issue 22866 [2]: GitHub Issue 22866 [3]: GitHub Pull Request 18844 [4]: GitHub Issue 23669 [5]: GitHub Issue 23669 [6]: GitHub Issue 20178 [7]: GitHub Pull Request 19937 [8]: GitHub Pull Request 19937 [9]: GitHub Pull Request 19937
-
 @ d34e832d:383f78d0
2024-05-02 18:14:34
@ d34e832d:383f78d0
2024-05-02 18:14:34
The Bitcoin network stands as a testament to the power of open-source software, embodying principles of decentralization, transparency, and collaboration. At the heart of this groundbreaking ecosystem lies Bitcoin Core, an open-source project that forms the foundation of the entire network. But what exactly is the role of open-source software in the development and maintenance of Bitcoin? Let's delve into this essential relationship and explore its profound implications for the future of digital finance.
Fostering Innovation and Security
The open-source nature of Bitcoin Core cultivates an environment conducive to innovation and security. By making its source code freely accessible, Bitcoin invites scrutiny from a global community of developers and security experts. This collective oversight serves as a potent mechanism for identifying and rectifying vulnerabilities promptly, bolstering the robustness and resilience of the network against potential threats.
Embracing Collaboration and Inclusivity
One of the hallmarks of open-source projects is their collaborative ethos, which aligns seamlessly with Bitcoin's decentralized philosophy. Developers from diverse backgrounds and locations can contribute to Bitcoin's development, irrespective of their affiliations or credentials. This meritocratic approach ensures that ideas and contributions are evaluated based on their merits rather than the status of their origin, fostering an inclusive and dynamic ecosystem of innovation.
Enabling Auxiliary Tools and Applications
Beyond Bitcoin Core, the open-source model extends to a myriad of auxiliary tools and applications that augment the functionality of the Bitcoin network. Wallet software, blockchain explorers, and privacy-enhancing technologies are just a few examples of the diverse ecosystem of projects that benefit from the collaborative nature of open-source development. Projects like Tor, which enhance privacy and security on the internet, underscore the interconnectedness of various open-source initiatives in advancing the overarching goal of a more private, secure, and open digital landscape.
Ensuring Transparency and Sustainability
Transparency is a cornerstone of open-source software, and Bitcoin is no exception. Discussions and debates surrounding Bitcoin's development take place openly on platforms like GitHub, enabling stakeholders to engage in constructive dialogue and decision-making processes. This transparent approach not only enhances the accountability of developers but also fosters a sense of community ownership and stewardship over the network's evolution.
In conclusion, open-source software plays a pivotal role in the development, maintenance, and evolution of the Bitcoin network. It embodies the core principles of decentralization, transparency, and collaboration, driving innovation, security, and inclusivity within the digital finance ecosystem. As Bitcoin continues to redefine the future of money, the collaborative spirit of open-source development will remain instrumental in shaping its trajectory towards a more decentralized and equitable financial system.
Sources
[0]: Bitcoin Core GitHub Pull Request [1]: Bitcoin Core GitHub Issue [2]: Onboarding to Bitcoin Core [3]: Bitcoin Core GitHub Issue [4]: Bitcoin Core GitHub Pull Request [5]: Bitcoin Core GitHub Pull Request [6]: Bitcoin Core GitHub Pull Request [7]: Bitcoin Core GitHub Issue
A Look At The Ecosystem
Exploring the Rich Tapestry of Open-Source Tools in the Bitcoin Ecosystem
The Bitcoin ecosystem thrives on collaboration and innovation, powered by a vibrant array of open-source tools and applications. These projects, developed and maintained by a global community of contributors, play a vital role in enhancing the functionality, security, and usability of Bitcoin. Let's delve into some examples that illustrate the diverse landscape of open-source innovation within the Bitcoin space.
Wallet Software
Open-source wallet applications form the cornerstone of Bitcoin's user experience, offering secure and feature-rich solutions for managing digital assets. These wallets, often equipped with advanced features like multisig transactions and hardware wallet integration, benefit from continuous improvement driven by community contributions. By leveraging the collective expertise of developers worldwide, open-source wallets ensure that users have access to robust and trustworthy tools for safeguarding their Bitcoin holdings.
Blockchain Explorers
Blockchain explorers serve as windows into the Bitcoin network, providing users with valuable insights into transaction details, block information, and network statistics. These tools are essential for transparency, enabling users to verify the integrity of transactions and monitor network activity in real-time. The open-source nature of blockchain explorers fosters trust and accountability, as the community collaborates to ensure the accuracy and reliability of the data presented.
Privacy-Enhancing Technologies
Projects focused on enhancing privacy for Bitcoin users thrive within the open-source ecosystem, offering innovative solutions to protect sensitive financial information. Technologies like mixers and CoinJoin implementations benefit from transparency and verifiability, as their code is open for scrutiny by anyone. By embracing open-source principles, privacy-enhancing projects empower users to take control of their financial privacy while contributing to the broader goal of advancing privacy standards within the Bitcoin network.
Development Tools
A plethora of development tools bolster the resilience and security of Bitcoin software, aiding developers in identifying and mitigating potential vulnerabilities. Static analysis tools, dynamic analysis tools, and fuzzing tools are among the essential resources utilized by Bitcoin developers to ensure the robustness of their code. These tools, often open-source themselves, benefit from community feedback and contributions, driving continuous improvement in software quality and security.
Node and Mining Software
In addition to Bitcoin Core, various open-source projects focus on running full nodes, mining software, and network monitoring tools. These projects play a crucial role in maintaining the decentralized nature of the Bitcoin network, enabling individuals to participate in consensus and transaction validation. By embracing open-source principles, node and mining software projects leverage the collective expertise of the community to enhance network security and reliability.
To close, the Bitcoin ecosystem owes much of its resilience and innovation to the collaborative spirit of open-source development. By fostering transparency, inclusivity, and continuous improvement, open-source tools empower users to engage with Bitcoin securely and confidently. As the ecosystem continues to evolve, the principles of open-source software will remain fundamental to its success and longevity.
Sources
[0]: Bitcoin Core GitHub Pull Request [1]: Bitcoin Core GitHub Pull Request [2]: Bitcoin Core GitHub Issue [3]: Bitcoin Core GitHub Issue [4]: Bitcoin Core GitHub Issue [5]: Bitcoin Core GitHub Pull Request [6]: Bitcoin Core GitHub Issue
-
 @ 6389be64:ef439d32
2024-05-02 18:06:52
@ 6389be64:ef439d32
2024-05-02 18:06:522024-05-02 at 11:00
Tags: #networking
Immuno-suppressant
Fungi have developed, among other chemical keys, the ability to modify plant physiology at the macro scale. Fungi dose plants with immuno-suppressants to stifle immune responses. The same happens with organ transplant patients. This is the only way the fungi can link with plant tissues.
References
[[Sheldrake-Entangled Life]]
Core Notes
Location
662 ^ref-38313
-
 @ d34e832d:383f78d0
2024-05-02 17:10:24
@ d34e832d:383f78d0
2024-05-02 17:10:24
In the ever-evolving landscape of Bitcoin, the role of Bitcoin nodes in validating and propagating transactions on the blockchain remains paramount. But what exactly do Bitcoin nodes do, and why are they crucial for the integrity of the network? Let's explore this intricate ecosystem and uncover the fundamental principles behind Bitcoin nodes and blockchain validation.
Understanding Bitcoin Nodes
Bitcoin nodes serve as the backbone of the P2P network, each playing a vital role in verifying and propagating transactions across the blockchain. But why are nodes essential, and what functions do they perform?
The Importance of Full Nodes
Running a Bitcoin node is akin to exercising your right to defend liberty. While not everyone may choose to run a node, its significance lies in the collective power it bestows upon the network. Just as a well-armed populace can deter tyranny, widespread node deployment serves as a bulwark against centralized control and censorship.
Ensuring Transaction Validity
At its core, the role of Bitcoin nodes is to ensure the validity of transactions and maintain the integrity of the blockchain. By following a set of predefined rules, nodes verify the legitimacy of transactions and safeguard the network against fraudulent activity. This commitment to transparency and accountability is essential for preserving the trust and credibility of the Bitcoin ecosystem.
Propagating Transactions on the Blockchain
Bitcoin nodes play a pivotal role in the propagation of transactions across the blockchain, ensuring that every transaction is accurately recorded and verified. But what mechanisms enable nodes to fulfill this critical function?
Real-Time Consensus Maintenance
Beyond transaction validation, Bitcoin nodes contribute to real-time consensus maintenance, ensuring that all participants adhere to the same set of rules and protocols. This consensus mechanism is essential for upholding the decentralized nature of the network and safeguarding against malicious attacks or disruptions.
Resilience and Recovery
In addition to real-time consensus maintenance, Bitcoin nodes exhibit resilience and recovery capabilities, enabling the network to withstand unforeseen challenges or catastrophic events. By maintaining a distributed network of nodes, Bitcoin ensures that no single point of failure can compromise the integrity or security of the blockchain.
The Future of Bitcoin Nodes
As we look ahead, the question arises: Will the task of securing and protecting Bitcoin nodes become easier or more challenging in the years to come? The answer to this question holds profound implications for the future of P2P, consensus and security in the Bitcoin ecosystem.
Upholding P2P Decentralization
The ongoing evolution of Bitcoin nodes underscores the perpetual struggle to uphold decentralization and safeguard against centralization trends. While challenges may arise, the commitment to running full nodes remains paramount for preserving the integrity and sovereignty of the Bitcoin network.
Embracing Innovation
As technology continues to advance, the Bitcoin community must embrace innovation and adaptation to address emerging threats and challenges. By fostering a culture of collaboration and continuous improvement, Bitcoin nodes can evolve to meet the evolving needs of the network and its users.
In conclusion, Bitcoin nodes serve as the cornerstone of the decentralized network, ensuring the integrity, security, and resilience of the blockchain. As the Bitcoin landscape continues to evolve, the role of Bitcoin nodes will remain indispensable in safeguarding the principles of decentralization, transparency, and sovereignty.
"Running a Bitcoin node isn't just about preserving the integrity of the network—it's about defending the principles of liberty and decentralization for generations to come."
So, let us continue to support and advocate for the widespread deployment of Bitcoin nodes, for they are the guardians of our digital sovereignty and the embodiment of our collective commitment to freedom and innovation.











