-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ d6dc9554:d0593a0c
2023-09-21 18:37:14
@ d6dc9554:d0593a0c
2023-09-21 18:37:14Nas blockchains PoW o consenso é alcançado por meio de prova de trabalho computacional e o objetivo principal é evitar que atores mal intencionados consumam ou ataquem a rede de forma perigosa. Este método de consenso requer um grande poder computacional para criar novos blocos, mas é muito simples, por parte de outros, verificar esse trabalho. Por isso se diz que PoW é uma estratégia assimétrica.
Nas blockchains PoS o objetivo é o mesmo, criar blocos e chegar a um consenso, mas nas PoS não é necessário um poder de processamento tão grande como nas PoW. Em média as PoS gastam menos de 1% da energia das PoW. Nas PoS os mineradores são chamados de validadores. Enquanto que nas PoW quem fica com a recompensa é quem resolve primeiro a charada matemática, nas PoS o validador que vai ganhar a recompensa é escolhido de forma aleatória, mas dando maior probabilidade aos que respeitem determinados critérios. A comunidade bitcoin é muito relutante em relação a PoS porque é mais fácil conseguir uma grande quantidade da moeda em causa do que mais que 51% de poder processamento. Logo as PoS são mais vulneráveis no que toca a segurança. Mas aqui cada caso é um caso e é preciso fazer essa análise para cada moeda.
As blockchains PoW tendem a ser mais descentralizadas enquanto as PoS mais centralizadas, não só em acesso, mas também em operação. Mais de metade dos validadores de ethereum estão na cloud da amazon. As blockchains PoW apresentam grandes desafios na escalabilidade de operação, muitas vezes exigindo soluções de segunda camada (L2), enquanto que as PoS possuem mecanismos de escalabilidade muito mais flexíveis. Os algoritmos PoW são muito mais simples de implementar do que os PoS e, portanto, menos suscetíveis a erros. Um bom exemplo é o PoS da ethereum que estava a ser implementado desde 2018.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
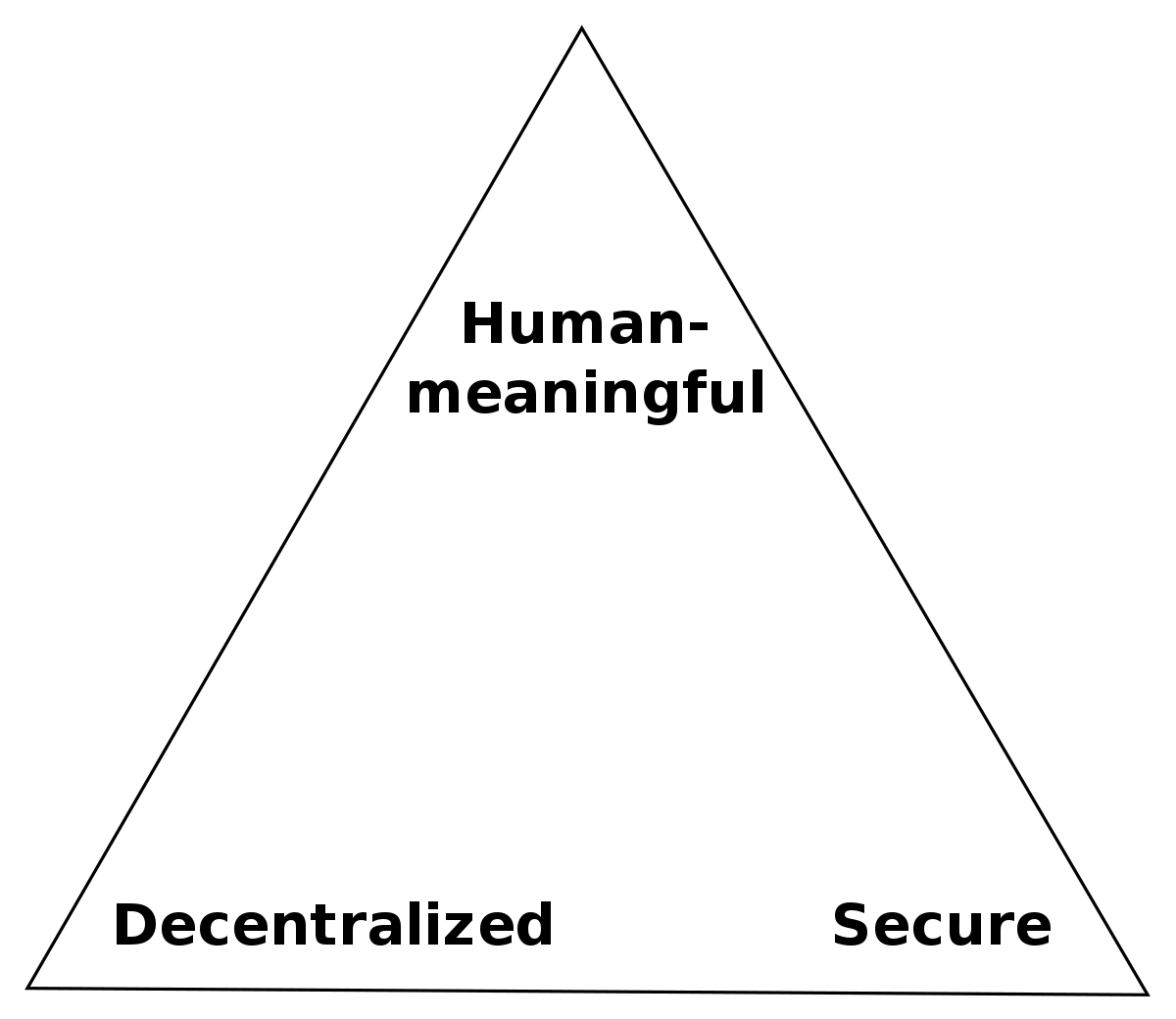
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
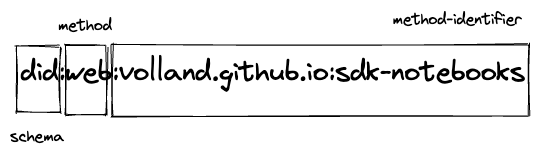
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
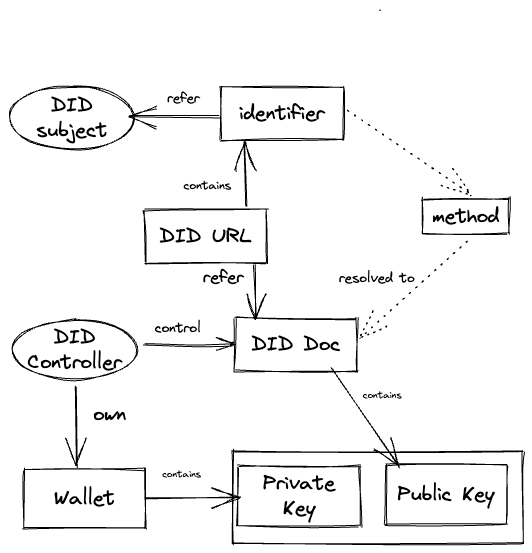
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ b60c3e76:c9d0f46e
2024-05-27 13:50:24
@ b60c3e76:c9d0f46e
2024-05-27 13:50:24These inventions are straight out of science fiction.
1. Volkswagen RooBadge
Volkswagen has developed a clever VW badge that emits sounds to deter kangaroos from roads, thereby reducing collisions. With approximately 20,000 accidents involving these animals each year.
🔗 youtu.be/W9klRlKoEQk ← Full Video
https://video.nostr.build/219d3e2a7a3b21e5d485c7f2576e8b42fbbef661f35582e02090e03a2263cf92.mp4
2. Food Delivery Robot (Bullet Train)
A robot designed like a fast train delivers food efficiently, allowing customer customization. Created to address waiter shortages, it offers a low-cost delivery solution.
https://video.nostr.build/3a174aef12b2adf04470b43ffde99d287a4d3d695ebcde6d67f1b5efb20a0647.mp4
3. Astribot S1
China showcases the Astrobot S1, a fully autonomous humanoid robot, demonstrating remarkable speed and fluidity in completing tasks.
https://video.nostr.build/6475d93284a59a0853443337b42b1fbaa361612e5d7b94d50c49442735039344.mp4
4. Solskin
This new technology is highly efficient at harnessing the power of solar energy while also preventing rooms from overheating.
https://video.nostr.build/773a588b33f12da461c6b3867f31035c434f7efbd606d057131dee27c22ab6cb.mp4
5. Running Adwear
Imagine athletic clothing that doubles as an advertising platform, displaying dynamic ads while you run. You can even make some extra cash while generating more income just by running! 😅
https://video.nostr.build/8528ef90fbac3ef73fe038d0c892098a372dbf5608b894386ac3663b2d325b1d.mp4
6. Opula
World's first auto-adjustable coffee table featuring an AMD Ryzen 7 8845HS Mini-PC and a 27-inch HD screen. The table adjusts up to 75 degrees for optimal viewing, combining work and entertainment seamlessly - the future of smart home furniture.
https://video.nostr.build/acc6e34a8e2888a3d84a3a34e74f603bd6f76b6d8f329dc78c5598c104a4b86a.mp4
7. Ring Bot
This device is currently just a prototype. Hopefully, in the future, it will provide us with many benefits through its technology.
https://video.nostr.build/149aca79c79b59f2a5dfdff02b6d7935d7e113727f1bad9f0b81fdc1d0f8178e.mp4
8. Pininfarina Wind Tunnel
The Pininfarina Wind Tunnel sets new standards in vehicle performance and comfort through advanced aerodynamic testing.
https://video.nostr.build/7d7a2fb14c6c2ea41cdda5a939ee54ad83f85d83e4026913e023ded2c68583b8.mp4
I hope you've found this article helpful. What do you think?
-
 @ c73818cc:ccd5c890
2024-05-27 13:07:05
@ c73818cc:ccd5c890
2024-05-27 13:07:05
🌟 Ecash rivoluziona la privacy di Bitcoin e fiat, integrando il sistema di pagamento Cashu di Calle. Questa innovativa soluzione consente agli utenti di spendere i propri Bitcoin in modo completamente anonimo e senza intermediari, garantendo la massima protezione della privacy e alimentando l'economia decentralizzata. L'integrazione di Cashu di Calle rappresenta un passo avanti significativo nella lotta contro la sorveglianza finanziaria e il controllo centralizzato.
🌟 Ecash: Sfida al potere delle banche centrali
🌟 L'integrazione di Cashu di Calle con Ecash rappresenta una sfida diretta al potere delle banche centrali e al loro controllo sul sistema monetario tradizionale. Offrendo un metodo di pagamento anonimo e decentralizzato, Ecash permette agli individui di svincolarsi dal sistema centralizzato e di gestire le proprie finanze in modo autonomo. Questa innovazione rappresenta un passo fondamentale verso una società più libera e indipendente dal controllo delle istituzioni finanziarie.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Le iscrizioni al torneo KCGI Bitget sono aperte, unisciti alla nostra squadra e corriamo verso i 5mln di dollari! https://www.bitgetapp.com/it/events/kcgi/futures-trading?clacCode=HCDS4WT4
BitcoinReportItalia #Ecash #Cashu #Calle #economia #Privacy #Censura #Crypto #BTC #Bitcoin
-
 @ 362ebffa:492e2719
2024-05-27 12:51:14
@ 362ebffa:492e2719
2024-05-27 12:51:14Consciousness is the subjective experience arising from the brain (as the viewer, the beholder) While reality encompasses both the objective external world and our subjective perception of it.
The two are deeply interconnected, with consciousness shaping our experience of reality and reality influencing the state and content of our consciousness.
Therefor we do live in various bubbles of reality, my reality (my perception of reality) is my own.
What do you think?
-
 @ a30cdfee:2d2f97ff
2024-05-27 12:46:15
@ a30cdfee:2d2f97ff
2024-05-27 12:46:15Clams: Accounting Software for Bitcoiners
nostr:npub136hk9wu6xnrz64kfaapsvgc5rfnylz4djlx4w30w66h6cy48vhws3gth6q is an accounting software for Bitcoiners.
Bring all your wallet balances to your local device, visualize your bitcoin flows and generate reports.
How does Clams work?
Accounting can be a headache if you're a Bitcoin power user. Multiple wallets, exchanges, on-chain, off-chain, Lightning, micropayments..
In most jurisdictions selling or spending bitcoin is a taxable event. If you earn bitcoin as income, calculating the cost basis of it might also leave you scratching your head. These problems also greatly hinder the advancement of Bitcoin circular economies.
It's possible to write custom scripts for more mainstream accounting softwares like Quickbooks, but this is not efficient or private.
Better money needs better tooling!
A dedicated software for businesses and individuals operating on a Bitcoin standard helps making better business decisions, and keeps your accounting more organized!
Clams lets you bring your read-only data from all your Bitcoin wallets locally to your device, which acts as a central accounting hub for your wallets.
It's still early for Clams, and currently only Core Lightning and LND nodes are supported.
Once imported, the data will be converted into journals using double-entry bookkeeping methods, so you can see credits, debits, income, expenses etc.
The data is visualized and customizable, which can help in data-driven decision-making! You can also tag transactions.
Clams lets you generate reports for profit/loss calculations, tax accounting and for cost basis analysis.
Reports, multi-user access and cross-device sync are intended to be paid features, planned to go live in Q3/Q4 2024.
No sign-up is required to use Clams, and no personal information is collected.
Currently, Clams is downloadable only for Mac, but Windows, Linux and Ubuntu are coming later.
Clams seems like a great additional tool for businesses who want to accept bitcoin. Together with the Bitcoin invoicing platform Zaprite it could be a great combo! You can learn more about Zaprite here.
What do you think about Clams? Is it the accounting software we need? Would you use it?
bitcoin #accounting #taxes #paymeinbitcoin #business
Additional Resources
Presentation by Clams Co-Founder John Gribbin
Project Links
-
 @ c11cf5f8:4928464d
2024-05-27 11:31:55
@ c11cf5f8:4928464d
2024-05-27 11:31:55Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
-
 @ eaba7a49:97790a4d
2024-05-27 11:07:50
@ eaba7a49:97790a4d
2024-05-27 11:07:50There is a lot going on now on the menopause health world, with the reinterpretation of the WHI (Women Health Initiative) study, from 2002 and now in 2024, it's gone from HRT increases risk of breast cancer to the other polarity: all women should have access to menopause therapy, its safe, and all women should be able to have. this conversation about risks and benefits with their provider.
And with that comes a lot of narratives about women's bodies that are important to deconstruct.
First, the idea that a magic pill can replenish our needs and take care of all our symptoms. The symptoms of menopause are symptoms of a systemic depletion of women's bodies. It's something that has happened over time, and there is no magic pill that can fix that. You can replenish biochemistry, but the toll that it has taken on your body, your emotions and mental health, that is something else. And yes, many women report feeling better: they are able to sleep, go to work, but still the narrative is that “my body is broken, and I can fix it with this magic pill” and that's where I see the disconnect.
Second, menopause is not about aging. Dr. Lara Briden speaks about this, and refers to the work of endocrinologist Jerilynn Prior, and I think is very important to take this into consideration. Menopause is not a failure of the body, it's not the failure of the ovaries, as a lot of the narrative goes. It is a neuroendocrine transition that is completely detached from aging.
Menopause is a brain overhaul, it's a brain reshaping so that it can be more efficient to tend to our physiological needs in the second part of our lives.
So, it's not about the failure of our bodies because we are aging, it is about our body’s ability to transform and to tend to our physiological needs. From now on, the focus is not going to be the energy intensive process of reproduction, it is going to be brain, bone, cardiovascular and metabolic health.
Neuroscientist Dr. Lisa Mosconi, who is studying women's brain in menopause explains that the menopausal brain is smaller and less energy demanding, because it doesn't need to tend to this energy intensive process of cyclicity for reproduction. So, we get to focus on our other body systems: our nervous system, brain, cardio health and that's why menopause is a window of opportunity. And that is why many women fall off the cliff in menopause. It's not because of aging, it's because they have been stressed, undernourished and overstretched for the whole reproductive period, so now when they come to menopause, that depletion makes her more vulnerable to symptoms.
Is like when you are rebuilding your house, but you didn't tend to your house for 30 years, and when you start remodeling, you find that the electric cables were damaged, the water piping breaks, it's not because of the remodeling. It's because it wasn’t maintained for 30 years.
Would love to hear your reflections and if this resonates or if I'm completely alone in this train of thought.
-
 @ 57d1a264:69f1fee1
2024-05-27 05:20:34
@ 57d1a264:69f1fee1
2024-05-27 05:20:34ODC #000018 - UX > IDEATEDesigning Digital Prototype for a Bitcoin educational websiteIf you miss it, please read our WTF is ODC (Open Design Challenge) intro post from more details.
Scenario
You're a product designer for a new bitcoin educational website (competitors are base58.info and LibreriaDeSatoshi.com and ). You're designing the interface for going through multiple lessons in a course.
You're at the stage of the process where you need to start making a digital prototype to test what the final product will feel like: things like interaction, UI components, typography, and image quality.
Task
Make a high-fidelity digital prototype. This prototype should demonstrate the flow of watching several lessons in a row that all have video and text content. You can review your competitors to see what kinds of things would be on a page like this. You may want to start with a wireframe.
Extra Credit: Add some interactivity to the prototype so that people looking at it can get a feel for what it would be like to use this interface on the final product.
Guides
If you need help with this challenge, check out our hand-picked tutorial recommendations.
-
7 Tips for Efficient Prototyping on uxdesign.cc
-
The Ultimate Guide to Prototyping on justinmind.com
-
Perfect Your UX Design Process – A Guide to Prototype Design on toptal.com
-
Rapid Prototyping: Digital on piped.video
Tools
Not sure which tools to use? Try something new, go 💯% FOSS!
PenPot by kaleidos
Prototype by QuantUX
HTML5 / CSS3 by developer.mozilla.org
Bitcoin UI Kit by Bitcoin.Design
Share Your Results
When you finish the challenge, post your work including anonymized collected data and results on this thread! If you also share it on
nostr, be sure to use the hashtag #opendesigner and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Check our previous ODC and support this community for creative minds, where you'll be able to get open and constructive feedback on your PoW. Ask anything in the ~Design territory and get some ⚡sats for the value you provide!
```
Bitcoin #Design #BitcoinDesign #NostrDesign #Nostr #OpenDesign #DesignChallenge #OpenDesignChallenge #BitcoinEducation #DigitalPrototype #UserInterface #InteractiveDesign #LessonFlow
```
-
-
 @ 1c6b3be3:73f0ae6f
2024-05-27 04:01:45
@ 1c6b3be3:73f0ae6f
2024-05-27 04:01:45Releases - No Bullshit Bitcoin
Blockstream Jade v1.0.30: Miniscript Support Blockstream Jade's new firmware version 1.0.30 has been released, which includes Miniscript capability. The update introduces new API calls 'get_registered_descriptors' and 'get_registered_descriptor' to improve Miniscript support. It also features a menu option for network selection (mainnet/testnet) for stateless QR code users and updates the ESP-IDF base firmware to v5.1.3. Users should note that saved Bluetooth bonds will need to be re-paired after this update. Additionally, various fixes and documentation updates are part of this release. More information can be found on the project's GitHub repository update page.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Bitcoin's Achilles Heel: Can Network Congestion Be Resolved? - Crypto Times Lower Cost Bitcoin Miners Increase Market Share After Halving: Bernstein Analysts - ZyCrypto Bitcoin’s Network Strengthens: Mining Difficulty And Hash Rate Spike Amid ETH ETF Buzz - NewsBTC
-
 @ a012dc82:6458a70d
2024-05-27 01:44:57
@ a012dc82:6458a70d
2024-05-27 01:44:57Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Based on my personal experience operating a node in Nigeria for the past few years, I detail the associated expenses in this paper. In addition, I provide some cost-cutting recommendations in the hopes of attracting more users to the Bitcoin network.
Before exploring the costs involved: What is a bitcoin node?
The term "bitcoin node" refers to the software that establishes a connection to the Bitcoin peer-to-peer network. According to the network regulations, a node is responsible for receiving, validating, and broadcasting transactions and blocks to other nodes on the network. In a nutshell, nodes are Bitcoin's "messengers" and "rule keepers," as Ted Stevens put it.
The broadcast blocks contribute to a decentralised ledger that documents all Bitcoin transactions and tracks who has bitcoins and how much they are worth. Blockchain refers to Bitcoin's public distributed ledger.
Typically, a Bitcoin node is hosted on a desktop computer or a portable single-board computer (SBC) like a Raspberry Pi. It is also possible to run a node on a virtual machine or on a mobile device. Download Bitcoin Core, the most popular bitcoin node software.
Nodes can either be full or light.
A full node keeps a complete copy of the blockchain and checks each transaction and block against the consensus rules, starting with the very first block (the "genesis block"). To evaluate whether or not a block and its associated transactions are legitimate, full nodes must follow a set of rules known as consensus rules.
Archival nodes and trimmed nodes are the two sorts of complete nodes. Archival nodes are responsible for storing the full blockchain and relaying information to other nodes, which helps bootstrap new nodes. A pruned node will only save a certain number of blocks when verifying transactions and blocks.Therefore, trimmed nodes save more disc space than archival nodes. In contrast, pruned nodes are unable to provide access to the whole blockchain for other nodes.
There is a trade-off between privacy and decentralisation when using a lite node because it does not enforce the consensus rules and must rely on full nodes maintained by third parties to receive block data.
All subsequent references to "node" in this article will be assumed to be referring to a full node unless otherwise specified.
Why run a node?
Running a node has both individual and communal advantages. There are a few examples here:
Complete anonymity when sending and receiving bitcoin, checking the balance of your wallet, and researching blockchain information
The rules of the consensus are enforced, which protects the value of bitcoin and your investment. In addition, if you operate a node, you have the option of voting for or against any proposed modifications to the consensus rules, including soft and hard forks. Using Raspiblitz's motto, "Not your node, not your rules," as an example
Bitcoin network fortification Bitcoin becomes more decentralised and resistant to attacks from bad actors, governmental regulations, and "black swan" occurrences as the number of nodes on the network increases.
Improving one's familiarity with the inner workings of the Bitcoin network and disseminating that information to others
Now that we know some of the advantages, let's have a look at the expenses involved in maintaining a node in Nigeria.
HARDWARE
Ordinarily, a Bitcoin node is run on one of the following hardware configurations, as they all match the specifications set forth by the network:
Nodes that can be plugged in and used immediately or nodes that a user can assemble themselves
Plug and play node
Plug-and-play full node devices for single-board computers (SBCs) like the Raspberry Pi, RockPro64, and Rock Pi4, and small PCs like the Intel NUC and Librem Mini are available from some bitcoin companies. A few examples of such node suppliers are:
Among the many, MyNode, Raspiblitz, RoninDojo, and Start9 stand out.
The cost of a node varies from $300 to $7,000, not including taxes and shipping costs (which might add up to $100 for deliveries to Nigeria). Most Nigerian Naira debit cards now have a monthly spending cap of $20 for transactions made abroad, down from $100 previously. You can either use dollars obtained on the illegal market (currently 70% above the official rate) to fund a dollar debit card linked to your domicile, or you can use a virtual dollar card, which gives convenience but a higher rate than the black market, or you can use bitcoin.
There are further challenges that could prevent you from buying a node. To begin, not all node suppliers offer international shipping to Nigeria. Moreover, some of these items are unavailable because of widespread chip shortages. Node suppliers sometimes provide the option of self-sourcing node components and installing their own versions of bitcoin core embedded software on a self-assembled node as a means of getting around these problems.
DIY NODE
SBCs are more cost-effective than mini-PCs, so we'll solely consider them when obtaining hardware components. In order for an SBC node to function, the following hardware is needed:
-
System-on-a-Chip + battery pack + card reader + solid-state drive + case
-
Case and fan heat exchanger
As a result of the present chip shortages and high demand for single-board computers, prices have skyrocketed and supply shortages have occurred, especially for Raspberry Pis on a global scale, both in terms of new and used units. However, you can get your hands on a Raspberry Pi or a RockPro64 from AliExpress. Be aware of recently opened stores, check out customer complaints, and always ask for a refund if your purchase doesn't arrive in the time frame promised.
These SBCs can only be bought with a dollar card, as naira debit cards have a limit on the amount of money they may spend abroad. The average prices of hardware components on AliExpress needed to assemble fresh Raspberry Pi or RockPro64 nodes are summarised in the table below.
DATA
Before it can fulfil its role as a messenger and rule keeper, a node on the bitcoin network must be in sync with the other nodes on the network.Initial block download (IBD) is the procedure by which all blocks beginning with the genesis block are downloaded and verified. This means that there are currently about 440 GB of data stored in the bitcoin blockchain.
Network providers' typical data prices for the IBD and the roughly 5.3 GB needed each month to sync your node with the blockchain are summarised in the following table. The following paragraphs assume that you live in a region with 4G network coverage that is at least passable.
POWER
To keep things simple, I'm going to assume that you don't have access to electricity (like I do, for at least 80% of the year where I live) and that you'll have to rely on a solar generator to power your node and router. The subsequent average prices for duplicating a device like Chimezie Chuta's Spacebox are as follows:
CONCLUSION
There are many advantages to operating your own bitcoin node, some of which have already been discussed. Unfortunately, not everyone will be able to afford to run a node due to factors such as persistent chip shortages, inflation, and the cost of setting up a node (despite the assumptions and recommendations provided here to reduce these expenses). Arman The Parman's circle of trust concept or Obi Nwosu's guardians and users model, in which a technically savvy person runs a node for a trusted group of people like close friends, family, or a community, could be a workable alternative. While there is a cost to using this method, it is preferable to connecting to third-party nodes and helps solve the custody problem that has plagued bitcoin.
FAQs
How much does it cost to operate a node for Bitcoin? When compared to mining, the cost of maintaining a Bitcoin node is relatively low (about $150–$400). However, nodes are just as crucial to establishing decentralisation as miners are. Validating transactions is a key function of nodes.
What is the operational cost of a node? The monthly subscription and maintenance price for a Strong node is $14.95 USD (paid in ETH and +ETH transaction fees), in addition to the initial investment of 10 STRNGR tokens.
Why would I want to host a Bitcoin node? Having your own Bitcoin node means you can conduct your Bitcoin transactions in a more discreet and safe manner. Having access to a Bitcoin node allows users to independently verify their Bitcoin holdings. Adding a Bitcoin node to the network is easy and increases its security.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 256a7941:b828ba8d
2024-05-27 01:24:42
@ 256a7941:b828ba8d
2024-05-27 01:24:42@k00b did you watch? SN fam, what're your thoughts?
-
 @ b804f68e:2fb0fa1f
2024-05-27 01:15:50
@ b804f68e:2fb0fa1f
2024-05-27 01:15:50Being born in the States, I grew up calling the beautiful game by its less popular and accepted name, soccer. However, after playing in England and constantly being reminded, "It's football, not soccer, you American twat!" I now refer to it more often as football. So, which is the proper name of the game? Football or soccer? Football makes sense since you play the game with your feet, but where the heck did soccer come from?
It turns out, neither 'football' nor 'soccer' is the sport's official title. The proper and original name of the game is 'association football,' coined in England in 1863. The word 'association' was added to distinguish it from other sports like rugby, which also used 'football' in its name.
'Soccer' is an abbreviation of the word 'association,' and guess what? It was the British who created the abbreviation, so ha! Who's the twat now? No, but in all seriousness, the name began as association football, was shortened to soccer, then interchangeably used as football or soccer. Now, it's predominantly referred to as football outside of particular countries like the US, where football more often describes a different sport.
To be completely honest, I'm more accustomed to using 'soccer' since that's what I grew up calling it both in the States and in Japan. Maybe it's just me, but it rolls off the tongue easier. Nowadays, I use both 'soccer' and 'football' interchangeably, but I'm now considering calling it by its official title.
"What sport do you play?"
"I engage in the noble pastime of association football, good sir!"
References:
- https://www.history.com/news/why-do-some-people-call-it-soccer
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ b804f68e:2fb0fa1f
2024-05-26 23:44:28
@ b804f68e:2fb0fa1f
2024-05-26 23:44:28The bulk of my work I've posted on SN has been written within the confines of my own room. But a few of the more recent ones have been written and completed at a local coffee shop. And now this post I write as I sit at a local Barnes and Noble. Regardless of location one thing does seem to be consistent, I got a coffee in hand! If I'm writing in the morning the coffee is a pick me up but also my first meal of the day essentially since I like mixing things into the coffee such as ghee, MCT oil, 100% chocolate, cinnamon, cacao powder, some half and half, and pinch of salt (I know kind of a lot, but if your curious you should try it!). However, if it's the later afternoon I either opt for decaf since I enjoy the smell and taste, or I'll have my second caffeinated coffee of the day to give myself a boost of focus and alertness. But I digress.
There are times when I attempt to be productive at home and I struggle because I indulge in other less productive distractions, however, I would say for the most part I've gotten much better at being able to stay productive at home. But nonetheless, these recent couple of weeks of getting myself out and doing productive work outside has been refreshing and been good for my overall focus and productivity. There were also phases of my life where I just could not get myself to focus when outside. My mind and senses would constantly get distracted by external stimulus because my senses would be hypersensitive to anything and everything that was going on around me whether at a cafe or a park or what have you.
Anyways, I'm curious to learn where stackers most productive setting is? And what are some non negotiables you may have to get productive or routines that you follow?
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 3bf0c63f:aefa459d
2024-05-26 22:16:06
@ 3bf0c63f:aefa459d
2024-05-26 22:16:06 -
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 81870f53:29bef6a6
2024-05-26 21:58:01
@ 81870f53:29bef6a6
2024-05-26 21:58:01橋水財団の創設者でウォール街の著名な「伝道師」であるレイ・ダリオ氏は、今週の「日経ニュース」とのインタビューで、世界の投資家が懸念しているテーマ、例えば金融政策の現状や見通しなどについて自身の見解を更新した。米国の経済社会と米ドルなどの主要通貨の動向。
一方、ダリオ氏は、「マッチポイント」を目前に控えた米大統領選に関して、最終的にバイデン氏とトランプ氏のどちらが勝っても、厳しい国内紛争と国際的な地理的紛争に同時に直面するだろうと警告した。
アメリカは典型的な「第5段階」にある
差し迫った問題に直面して、ダリオ氏は「原則」の中で「国家の内部サイクルの6段階理論」を見直すことを忘れなかった。その中の「第5段階」は富と価値観の大きな違いによって特徴付けられ、世界情勢を推進している。二極化した社会の報復、つまり「内戦」寸前の段階だが、まだ勃発していない。
ダリオ氏は、米国は典型的な「第5段階」にあると述べ、この段階の特徴には、自然災害(干ばつ、洪水、パンデミックなど)、大きな技術変化、地理的紛争などの要因によって引き起こされる過剰な債務発行も含まれると述べた。そして、アメリカは国際秩序の新たなパターンに直面しているが、実際にその状況に陥っていないのは、アメリカ国民、特にアメリカの指導者次第である。
以前の「内戦」を引用する必要がある理由は、ダリオが米国で最も可能性の高いタイプの内戦は人々が互いに銃撃し合うものではなく、むしろ州と地方政府がその方針に従うことを拒否していると信じているためである。連邦政府の指示、そして同時に、この無秩序で機能不全に陥ったアプローチに対する連邦政府の対応。
次期米国選挙に関して、2人の候補者が直面するであろう多くの課題に加えて、ダリオ氏はさらに深い懸念を表明した。現在、共和党は極右によって支配されており、人々は民主党が極右の影響をより強く受けているのではないかと懸念している。これは、誰が選挙に勝っても、米国では大きな政治的対立が起こる可能性が高いことを意味する。
ドルと米国のインフレ見通し
ダリオ氏はインフレを「債務圧力の緩和」の結果と見ているからこそ、連邦準備理事会がいわゆる2%のインフレ目標を達成できるとは信じていないと率直に述べた。
同氏は、日本、米国、ユーロ圏で起こっていることと同様に、世界の三大基軸通貨の発行体が積極的に通貨安を推進しており、それに伴って債務も縮小していると述べた。同氏は、ある通貨と他の通貨との関係での急激な下落ではなく、インフレの進行と金価格の上昇に反映される可能性が高く、今後数年間は債務の収益化がトレンドであり続けるだろうとも考えている。
同時にダリオ氏は、米国経済は政府のバランスシートと損益計算書の悪化によって支えられているため、米国政府は赤字に対処するために大量の債券を発行し続けるだろうとも指摘しました。インフレ率が連邦準備理事会や他の主要中央銀行の目標に戻ることが難しい理由はここにある。
日本株の魅力は低下している
ダリオ氏は日本のメディアを前にしても「今の日本株は昔ほど魅力的ではない」と率直に述べた。
同氏は、価格要因に基づくと日本は依然として魅力的な市場だが、金融政策が引き締められていることから、日本株の魅力も当然過去とは異なっていると述べた。
ダリオ氏はまた、日銀自体が債券のポジションを非常に大きくしており、過度に金利を引き上げると日本政府と日本政府に巨額の損失をもたらす可能性があるため、日銀は金融引き締め政策をゆっくりとしか進められないと予想している。日本銀行は政策金利をインフレや名目成長と比較して相対的に低く維持することで巨額の債務の減価償却を進める可能性があるが、これはまた、相対的に言えば円債券が引き続き非常に悪い投資先となることを意味する。
さらに、日本の利上げは特定の市場への日本の資金流入を維持することも困難にし、米国債利回りにも上昇圧力をかけるだろう。
-
 @ d830ee7b:4e61cd62
2024-05-10 14:03:50
@ d830ee7b:4e61cd62
2024-05-10 14:03:50จุดเริ่มต้นของตำนาน
ท่ามกลางแสงแดดเจิดจ้าและลมทะเลเย็นสบายของหาดเมืองแกลง ชายหนุ่มรูปร่างกระทัดรัดนามว่า "ซุป" กำลังนั่งจดจ่ออยู่หน้าจอคอมพิวเตอร์ ดวงตาเป็นประกายฉายแววความสนใจขณะไล่อ่านบทความวิชาการทางด้านเศรษฐศาสตร์ ความรู้ไม่ได้เป็นเพียงแค่ตัวอักษรบนหน้าจอ แต่มันคือแรงบันดาลใจ เปรียบเสมือนขุมทรัพย์ที่รอการขุดค้นสำหรับเขา
ซุป ไม่ใช่หนุ่มนักเรียนหัวกะทิหรือบัณฑิตจบใหม่จากรั้วมหาวิทยาลัยดัง แต่เป็นชายหนุ่มธรรมดาที่หลงใหลในศาสตร์แห่งการจัดสรรทรัพยากรอันหายาก เศรษฐศาสตร์ ไม่ว่าจะเป็นสำนักคลาสสิคหรือออสเตรียน ล้วนดึงดูดความสนใจของเขาให้เข้าไปสำรวจอย่างลึกซึ้ง ยิ่งเรียนรู้ ซุปยิ่งค้นพบความมหัศจรรย์ของศาสตร์นี้ มันไม่ใช่แค่ทฤษฎีบนหน้ากระดาษ แต่สะท้อนอยู่ในทุกๆ การกระทำของมนุษย์
มันเหมือนเวลาที่เราไปเที่ยวทะเล.. เราไม่ได้แค่เห็นน้ำทะเลสีฟ้าสวยงาม แต่เราสัมผัสได้ถึงไอเย็นของลมทะเล ได้ยินเสียงคลื่นซัดสาด ได้กลิ่นอายของเกลือ ความรู้ด้านเศรษฐศาสตร์เองก็เช่นกัน เราจะมองเห็นมันได้ในทุกๆ การตัดสินใจ ทุกๆ การกระทำ ตั้งแต่การซื้อของในร้านสะดวกซื้อ ไปจนถึงการเลือกอาชีพ
หนึ่งในขุมทรัพย์ความรู้ที่ซุปหลงใหลมากที่สุด คือ เศรษฐศาสตร์สำนักออสเตรียน โดยเฉพาะแนวคิดเรื่อง "มูลค่าอัตวิสัย" (Subjective Value) ทฤษฎีนี้สอนให้เขาเข้าใจว่ามูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับต้นทุนการผลิต หรือแรงงานที่ใส่ลงไป แต่มันขึ้นอยู่กับการประเมินของแต่ละบุคคล สิ่งที่สำคัญสำหรับคนหนึ่ง อาจดูไร้ค่าสำหรับอีกคน และมูลค่าของสิ่งเดียวกันก็อาจเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
ซึ่งก็เหมือนกับตอนเรายังเด็กๆ ของเล่นชิ้นโปรดอาจเป็นตุ๊กตากันหมีตัวเก่าๆ แต่วันนี้ ตุ๊กตาตัวนั้นอาจถูกเก็บไว้ในกล่องใต้เตียงไปแล้ว เพราะความต้องการของเราเปลี่ยนไป เราให้คุณค่ากับสิ่งอื่นๆ มากกว่าเมื่อเวลาผ่านไป
ความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียนนำพาซุปไปรู้จักกับ อ.พิริยะ และทีมงาน Right Shift กลุ่มคนรุ่นใหม่ที่มุ่งมั่นเผยแพร่ความรู้ทางเศรษฐศาสตร์อย่างเข้าใจง่าย ซุปกลายเป็นแฟนตัวยง ติดตามผลงานแทบทุกชิ้น และใฝ่ฝันว่าสักวันหนึ่งจะได้มีโอกาสร่วมงานกับทีม แต่ด้วยความขี้อายและอ่อนน้อมถ่อมตน ซุปจึงไม่เคยกล้าเอ่ยปาก เขาเลือกที่จะเป็นผู้สนับสนุนอยู่ห่างๆ อย่างเงียบๆ
บางครั้ง.. ความฝันก็เหมือนเมล็ดพันธุ์ เราต้องหมั่นรดน้ำ พรวนดิน และดูแลมันอย่างดี ถึงแม้จะไม่รู้ว่ามันจะเติบโตงอกงามเมื่อไร แต่ถ้าเรายังคงดูแลมันต่อไป สักวันหนึ่งมันจะผลิดอกออกผลให้เราได้ชื่นชม

จุดเปลี่ยนแห่งโชคชะตา
ชีวิตของซุป.. เหมือนเรือเล็กที่ล่องลอยไปตามกระแสน้ำ มีความสุขกับการเรียนรู้ เสพย์ติดความรู้ด้านเศรษฐศาสตร์และมีความฝันเล็กๆ ที่อยากร่วมงานกับทีม Right Shift
วันหนึ่ง.. โชคชะตาก็เล่นตลก เหมือนส่งคลื่นลูกใหญ่ซัดเข้ามาหาเรือลำน้อยของซุป
Right Shift กำลังประสบปัญหาขาดแคลนนักตัดต่อวิดีโอคลิป จนกระทั่ง Jakk Goodday หนึ่งในผู้ก่อตั้ง ต้องลงมาทำเองแก้ขัดไปก่อน ข่าวนี้แพร่สะพัดไปถึงหูของซุป เขาถึงกับอุทานออกมาเบาๆ
"เอ๊ะ.. นี่มันโอกาสของเราหรือเปล่านะ?"
สถานการณ์แบบนี้มันเหมือนตอนเราเดินเล่นอยู่ริมชายหาด แล้วเจอขวดแก้วที่ถูกคลื่นซัดมาเกยตื้น ข้างในมีกระดาษเขียนข้อความลอยอยู่ เราจะเก็บมันขึ้นมาอ่านไหมหรือจะปล่อยให้คลื่นซัดมันกลับลงทะเลไป?
ความคิดมากมายวนเวียนอยู่ในหัวของซุป เขาไม่ใช่มืออาชีพ แต่ก็พอมีฝีมือด้านการตัดต่ออยู่บ้าง จะลองเสี่ยงดูดีไหมนะ? ถ้าไม่ลอง.. ก็คงไม่มีโอกาส แต่ถ้าลองแล้วไม่สำเร็จล่ะ? จะกลายเป็นตัวตลกหรือเปล่านะ?
ในที่สุด.. ซุปก็ตัดสินใจ "เอาวะ! ลองดูสักตั้ง อย่างน้อยก็ได้พิสูจน์ตัวเอง"
เขาส่งข้อความไปหา Jakk บอกเล่าความสามารถและความตั้งใจ พร้อมกับยื่นมือเข้าช่วยเหลือ
บางครั้ง.. โอกาสก็มาในรูปแบบของปัญหา คนที่มองเห็นโอกาสและกล้าที่จะคว้ามันไว้ ก็จะประสบความสำเร็จ
สิ่งที่เกิดขึ้นหลังจากนั้นมันราวกับความฝัน Jakk ตอบรับและให้โอกาสซุปเข้ามาทดลองงาน ความกดดันถาโถมเข้ามาอย่างหนัก แต่ซุปก็พยายามอย่างเต็มที่ เขาใช้ความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในการประเมินคุณค่าของโอกาสนี้ มันมีค่ามากกว่าความสบายใจในฐานะแฟนคลับ มากกว่าความกลัวที่จะล้มเหลว
"ความกลัว คือ กำแพงที่กั้นระหว่าง ตัวเรา กับ ความฝัน"
ซุปทุ่มเททุกอย่างให้กับงาน ไม่เคยเกี่ยงงอนหรือบ่นว่าเหนื่อย เพราะสำหรับเขา.. นี่คือโอกาสทอง มันคือการได้ทำงานที่รักร่วมกับทีมที่เขาชื่นชม
ทฤษฎีมูลค่าอัตวิสัยสอนให้เรารู้ว่า มูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับปัจจัยภายนอก เช่น ราคา หรือ ต้นทุนการผลิต แต่มันขึ้นอยู่กับ การประเมินของแต่ละบุคคล
การตัดสินใจครั้งสำคัญของซุป นำพาเขาไปสู่เส้นทางใหม่ เส้นทางที่เต็มไปด้วยความท้าทาย แต่ก็เต็มไปด้วยโอกาสเช่นกัน เส้นทางที่เขาจะได้เรียนรู้ เติบโต และสร้างคุณค่าให้กับตัวเองและสังคม การตัดสินใจของซุปนั้นมันช่างสอดคล้องกับหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่เน้นการกระทำของมนุษย์ การประเมินมูลค่า และการตัดสินใจ

วันเวลาแห่งการสร้างคุณค่า
แสงไฟจากจอคอมพิวเตอร์ยังคงสาดส่องใบหน้าของซุป.. ดวงตาของเขาจดจ้องอยู่กับเส้นเวลา ตัดต่อ เรียบเรียง ประกอบร่าง วิดีโอคลิปแต่ละชิ้นให้สมบูรณ์ งานที่ได้รับมอบหมายไม่ใช่งานง่าย แต่ซุปไม่เคยปริปากบ่น เขาก้มหน้าก้มตาทำงานของตัวเองไปอย่างเต็มที่
"นี่มันคือความฝันของเราเลยนะ จะมัวบ่นทำไมกัน" ซุปพึมพำกับตัวเอง
ซุปในตอนนี้ก็เหมือนนักปีนเขาที่กำลังไต่ขึ้นสู่ยอดเขา เส้นทางอาจจะลำบาก ขรุขระ และเต็มไปด้วยอุปสรรค แต่ทุกย่างก้าวก็คือ ความท้าทาย และความภาคภูมิใจ
แม้จะไม่ได้รับผลตอบแทนมากมาย แต่สำหรับซุป ความสุขที่ได้รับจากการทำงานมันมีค่ามากกว่าเงินทอง เขาได้เรียนรู้อะไรใหม่ๆ มากมาย ได้ฝึกฝนทักษะ ได้สร้างสรรค์ผลงาน และที่สำคัญที่สุด คือ ได้เป็นส่วนหนึ่งของทีมที่เขารัก
ในทางเศรษฐศาสตร์สำนักออสเตรียน เราเรียกสิ่งนี้ว่า "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) หมายความว่า.. เมื่อคนเราต้องตัดสินใจ เราจะประเมินมูลค่าของสิ่งต่างๆ โดยพิจารณาจากประโยชน์ที่เราจะได้รับจากการใช้งานนั้นๆ
ในกรณีของซุป.. การทำงานกับ Right Shift อาจไม่ได้ทำให้เขาร่ำรวย แต่เขาได้รับประสบการณ์ ความรู้ และความสุข ซึ่งสิ่งเหล่านี้มีมูลค่าสำหรับซุปมากกว่าเงินทอง
บางครั้ง.. คุณค่าของสิ่งต่างๆ ก็ไม่สามารถวัดได้ด้วยเงิน
นอกจากนี้.. การทำงานกับ Right Shift ยังเปิดโอกาสให้ซุปได้พบปะผู้คนมากมาย ทั้งคนดัง ผู้เชี่ยวชาญ และบุคคลที่น่าสนใจ ซึ่งเป็นเหมือน "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ที่เติมเต็มความสุขในการทำงานของเขา
เหมือนเวลาเรากินข้าวจานแรกอาจจะอร่อยมากเพราะเราหิว แต่พอจานที่สอง จานที่สาม ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม จนไม่อยากกินอีกแล้ว
ประสบการณ์ใหม่ๆ ก็เช่นกัน ครั้งแรกที่ได้เจออาจจะตื่นเต้น ประทับใจ แต่พอเจอบ่อยๆ ความตื่นเต้นก็จะลดลง แต่ความทรงจำและความรู้สึกดีๆ ยังคงอยู่
แนวคิดเรื่อง "อรรถประโยชน์ส่วนเพิ่ม" ช่วยอธิบายว่า ทำไมคนเราถึงแสวงหาประสบการณ์ใหม่ๆ แม้ว่าความตื่นเต้นจะลดลงตามกาลเวลา
ซุป ยังคงทำงานอย่างหนัก พัฒนาตัวเองและสร้างสรรค์ผลงาน เขาไม่รู้ว่าอนาคตจะเป็นอย่างไร แต่เขารู้ว่า.. เขาได้เลือกเส้นทางที่ถูกต้องแล้ว เส้นทางที่เขาได้สร้างคุณค่าให้กับตัวเองและสังคม
"ความสุข ไม่ได้อยู่ที่ปลายทาง แต่อยู่ในระหว่างทาง"

บทเพลงแห่งการแบ่งปัน
เวลาผ่านไป.. ซุปสั่งสมประสบการณ์และความรู้มากขึ้น จากชายหนุ่มขี้อาย เขากลายเป็นนักตัดต่อมือฉมัง และที่สำคัญคือความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนที่สั่งสมมาตลอดมันเริ่มผลิดอกออกผล
ซุป อยากแบ่งปันความรู้ อยากให้คนอื่นๆ ได้สัมผัสความมหัศจรรย์ของศาสตร์นี้เหมือนที่เขาเคยสัมผัส เขาปรึกษากับ Jakk และ อิสระ (น้องเล็กในทีม) ซึ่งมีความสนใจในเรื่องเดียวกันและต่างก็มีแรงปรารถนาที่จะจะเผยแพร่มันเช่นกัน
ซุป: "พี่ Jakk, อิส ผมอยากทำรายการเกี่ยวกับเศรษฐศาสตร์สำนักออสเตรียน พี่คิดว่าไงครับ"
Jakk: "ไอเดียดีนะซุป แต่จะทำยังไงให้มันเข้าใจง่าย ไม่น่าเบื่อ ไม่เอาศัพท์แสงบ้าบอคอแตกนะ"
อิสระ: "พี่ซุปเล่าเรื่องเก่ง เราทำเป็นนิทานก็ได้นี่ครับ"
ซุป: "นิทานอิสซุป เหมือนที่ อ.พิริยะ ตั้งให้อะหรอ เออ.. ชื่อนี้ เข้าท่าดีนะ"
และแล้ว "นิทานอิสซุป" ก็ถือกำเนิดขึ้น รายการที่นำเสนอความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในรูปแบบง่ายๆ สบายๆ เข้าใจง่าย เสียงนุ่มๆ ของซุป บวกกับลีลาการเล่าเรื่องที่เป็นเอกลักษณ์ของอิสระ ดึงดูดผู้ชมได้อย่างมากมาย
เหมือนแม่น้ำที่ไหลรินลงจากยอดเขา นำพาธาตุอาหารไปหล่อเลี้ยง ต้นไม้ พืชพันธุ์และสัตว์น้อยใหญ่ ความรู้ก็เช่นกัน เมื่อถูกแบ่งปันมันจะสร้างคุณค่าให้กับผู้รับและผู้ให้ ซุปมีความสุขที่ได้แบ่งปันความรู้ และยิ่งแบ่งปันเขาก็ยิ่งได้รับความสุขและคุณค่ามากขึ้น
นี่อาจคล้าย "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เมื่อเรามีบางสิ่งบางอย่างมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย (Unit) ที่เพิ่มขึ้นจะค่อยๆ ลดลง
แต่.. กฎนี้ใช้ไม่ได้กับ “ความรู้” และ “การแบ่งปัน” ยิ่งเรามีความรู้มากขึ้น ยิ่งเราแบ่งปันมากขึ้น ความสุขและ คุณค่าที่ได้รับก็จะยิ่งเพิ่มขึ้น ซึ่ง ซุป ก็เข้าใจหลักการนี้จึงเลือกที่จะแบ่งปันความรู้เพื่อสร้างคุณค่าให้กับสังคม และเติมเต็มความสุขให้กับตัวเอง
"นิทานอิสซุป" ไม่ได้เป็นเพียงแค่รายการ แต่เป็นพื้นที่ ที่ซุปได้แสดงออกถึงความรักและความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียน เขาไม่ได้ทำเพื่อชื่อเสียงหรือเงินทอง แต่ทำเพื่อแบ่งปันและสร้างคุณค่าให้กับสังคม
การให้ คือ การได้รับ ที่ยิ่งใหญ่ที่สุด
"นิทานอิสซุป" จึงเป็นมากกว่านิทานวิชาการ มันคือบทเพลงแห่งการแบ่งปัน บทเพลงที่ ซุป บรรจงแต่ง เพื่อส่งต่อความรู้และแรงบันดาลใจให้กับผู้คน
"เพราะ.. ความรู้ คือ แสงสว่าง ที่ช่วยขับไล่ความมืดมน"

ก้าวสู่แสงไฟ
นิทานอิสซุป กลายเป็นจุดเริ่มต้นของเส้นทางใหม่ เส้นทางที่นำพา ซุป ก้าวออกจากเงามืดไปสู่แสงไฟ เหมือนดอกไม้ที่เบ่งบานท่ามกลางแสงแดด อวดสีสันและกลิ่นหอม ดึงดูดผึ้งและผีเสื้อให้เข้ามาดอมดม
ซุป ไม่ใช่แค่นักเล่านิทาน แต่เขาได้ค่อยๆ กลายเป็นหนึ่งในอินฟลูเอนเซอร์ในวงการบิตคอยน์ไทยอย่างช้าๆ ภายใต้ฉายา "ประธานซุป" เขาได้รับเชิญไปบรรยาย ออกรายการ และร่วมงานกับบุคคลที่มีชื่อเสียงมากมาย
ความสำเร็จ มันก็มักจะมาพร้อมกับความรับผิดชอบและความคาดหวัง เส้นทางของ ซุป ไม่ได้ถูกโรยด้วยกลีบกุหลาบ เขาต้องตัดสินใจครั้งสำคัญหลายครั้ง เช่น การทิ้งรายได้จากงานฟรีแลนซ์, การสละโอกาสทางการเมือง เพื่อทุ่มเทให้กับ Right Shift
“การตัดสินใจ” คือ กระบวนการเลือกทางเลือกหนึ่ง เหนือทางเลือกอื่นๆ โดยพิจารณาจาก การประเมินมูลค่าอัตวิสัย
ซุป เลือกที่จะเสียสละสิ่งที่คนอื่นมองว่ามีค่า เพื่อสิ่งที่เขามองว่ามีค่ามากกว่า นั่นคือ.. ความฝัน ความสุข และ การสร้างคุณค่าให้กับสังคม
"การเสียสละ คือ บทพิสูจน์ ของความมุ่งมั่น"
ตลอดเส้นทาง ซุป ได้รับการสนับสนุนและคำแนะนำ จาก Jakk Goodday ผู้ที่เชื่อมั่นในศักยภาพของเขา ตั้งแต่วันแรก ความสัมพันธ์ระหว่าง ซุป และ Jakk สะท้อนให้เห็นถึงความสำคัญของ "การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) ซึ่งเป็นหัวใจสำคัญของ เศรษฐศาสตร์สำนักออสเตรียน
Jakk เห็นคุณค่าในตัว ซุป จึงให้โอกาสและสนับสนุนเขา ในขณะที่ ซุป ก็ตอบแทนด้วยการทำงานอย่างเต็มที่ และ สร้างคุณค่าให้กับทีม Right Shift
การให้ และ การรับ นั้นเป็นวัฏจักรที่สร้างสรรค์ และ ยั่งยืน
เส้นทางของ "ซุป" จากแฟนคลับสู่ประธานซุป เป็นบทเรียนชีวิตที่สอนให้เรารู้ว่า.. ความฝัน ความมุ่งมั่น การเสียสละ และการสร้างคุณค่า คือ สิ่งสำคัญที่นำพาเราไปสู่ความสำเร็จ
และทุกคน ก็มีศักยภาพที่จะสร้างคุณค่า และประสบความสำเร็จ ในแบบของตัวเอง
คุณค่าที่แท้จริง
เรื่องราวของ "ซุป" ไม่ได้เป็นเพียงแค่เรื่องราวของความสำเร็จ แต่เป็นบทเรียนชีวิตที่สอนให้เราเข้าใจถึงคุณค่าที่แท้จริง
เหมือนต้นไม้ใหญ่ที่เติบโตแผ่กิ่งก้านสาขา ให้ร่มเงาและผลิดอกออกผล ซุป เปรียบเสมือนต้นไม้ต้นนั้น เขาเติบโต จากเมล็ดพันธุ์เล็กๆ ที่หลงใหลในความรู้ ด้วยการหมั่นรดน้ำ พรวนดิน ใส่ปุ๋ย คือความมุ่งมั่น ความอดทน และ การเสียสละ จนกระทั่งเติบใหญ่ แผ่กิ่งก้านสาขาให้ร่มเงา คือการแบ่งปันความรู้และผลิดอกออกผล คือความสำเร็จและการเป็นแรงบันดาลใจให้กับผู้อื่น
หลักการของ ทฤษฎีมูลค่าอัตวิสัย (Subjective value) สะท้อนให้เห็นในทุกๆ การตัดสินใจของ ซุป
การประเมินมูลค่า >> ซุป ประเมินคุณค่าของโอกาส ประสบการณ์ และความสุข มากกว่าเงินทองและชื่อเสียง การเสียสละ >> ซุป ยอมสละรายได้และโอกาสทางการเมือง เพื่อหันมาทำในสิ่งที่เขารักและเชื่อมั่น ความอดทน >> ซุป ทำงานหนัก พัฒนาตัวเองและอดทนรอคอย จนกระทั่งประสบความสำเร็จ การสร้างคุณค่า >> ซุป แบ่งปันความรู้และสร้างแรงบันดาลใจ ให้กับผู้อื่น
เรื่องราวของ ซุป สะท้อนให้เห็นถึง "ปฏิทรรศน์น้ำ-เพชร" (Water-Diamond Paradox) ซึ่งเป็นแนวคิดใน เศรษฐศาสตร์สำนักออสเตรียน ที่อธิบายว่า.. ทำไมสิ่งที่จำเป็นอย่าง น้ำ ถึงมีราคาถูก ในขณะที่สิ่งฟุ่มเฟือยอย่าง เพชร ถึงมีราคาแพง
ในชีวิตจริง.. สิ่งที่สำคัญสำหรับคนหนึ่ง อาจไม่ได้สลักสำคัญสำหรับอีกคน และมูลค่าของสิ่งต่างๆ ก็ขึ้นอยู่กับ บริบทและความต้องการของแต่ละบุคคล
ความสุข และ ความสำเร็จ ไม่ได้มีสูตรสำเร็จตายตัว แต่ละคนต้องค้นหาและสร้างมันขึ้นมาเอง
ซุป ค้นพบ “คุณค่าที่แท้จริง” ของชีวิต เขาไม่จำเป็นต้องมีเงินทองมากมาย หรือมีชื่อเสียงโด่งดัง แต่เขามีความสุขกับการได้ทำในสิ่งที่รักและสร้างคุณค่าให้กับสังคม
“จงค้นหาคุณค่าที่แท้จริงของชีวิต และ ใช้ชีวิตให้มีความหมาย”
"คุณค่าของคน อยู่ที่ผลของงาน"

11 พฤษภาคม เป็นวันคล้ายวันเกิดของ ซุป บทความนี้ผมจึงอุทิศน์ให้กับเขา และขอให้เจ้าตัวมีความสุขในการมุ่งมั่นสร้างคุณค่าในแบบของตัวเองสืบต่อไป ขอให้ทุกคนได้ร่วมอวยพรและให้กำลังใจเพื่อนคนเก่งของเราคนนี้กันด้วยครับ
ภาคผนวก
Subjective Value มองคุณค่าผ่านเลนส์ของตัวเอง
ทฤษฎีมูลค่าอัตวิสัย (Subjective Value) เปรียบเสมือนแว่นตาพิเศษที่ช่วยให้เราเข้าใจว่าทำไมคนเราถึงมองเห็น "คุณค่า" ของสิ่งต่างๆ แตกต่างกัน
ลองนึกภาพว่าเรากำลังดูภาพวาด abstract บางคนอาจมองว่ามันสวยงาม มีเอกลักษณ์ ในขณะที่บางคนอาจมองว่ามันดูยุ่งเหยิง ไม่มีความหมาย
ทฤษฎีนี้บอกเราว่า "คุณค่า" ไม่ได้ติดมากับสิ่งของ หรือถูกกำหนดโดยปัจจัยภายนอก เช่น ต้นทุนการผลิตหรือแรงงานที่ใช้ แต่ "คุณค่า" เกิดขึ้นจากการประเมินของแต่ละบุคคล ขึ้นอยู่กับความต้องการ ความชอบ ประสบการณ์ และสถานการณ์ของแต่ละคน
นักเศรษฐศาสตร์สำนักออสเตรียนเชื่อว่า "มนุษย์" เป็นศูนย์กลางของกิจกรรมทางเศรษฐกิจ และการตัดสินใจของมนุษย์นั้นขับเคลื่อนด้วย "มูลค่าอัตวิสัย" ที่พวกเขามีต่อสิ่งต่างๆ
ยกตัวอย่างง่ายๆ
คนที่กำลังหิวโหย อาจมองว่า "ข้าวเปล่า 1 จาน" มีค่ามาก แต่สำหรับคนที่เพิ่งกินอิ่มมา ข้าวเปล่าจานนั้นอาจไม่มีค่าเลย
นักสะสมงานศิลปะ อาจยอมจ่ายเงินมหาศาลเพื่อซื้อภาพวาด แต่สำหรับคนที่ไม่เข้าใจศิลปะ ภาพวาดนั้นอาจดูไร้ค่า
นักเรียนที่กำลังเตรียมสอบ อาจมองว่า "เวลา 1 ชั่วโมง" มีค่ามาก แต่สำหรับคนที่กำลังว่าง เวลา 1 ชั่วโมงอาจไม่มีค่าอะไรเลย
การเข้าใจ "ทฤษฎีมูลค่าอัตวิสัย" ช่วยให้เรายอมรับความแตกต่างและเคารพการตัดสินใจของผู้อื่น เพราะสิ่งที่สำคัญสำหรับเราอาจไม่สำคัญสำหรับคนอื่น และที่สำคัญ "มูลค่า" ยังสามารถเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
โทรศัพท์มือถือรุ่นเก่า ที่เมื่อก่อนอาจมีมูลค่ามาก แต่ตอนนี้อาจกลายเป็นของสะสมหรือ ขยะอิเล็กทรอนิกส์
บ้านหลังเก่า เมื่อก่อนอาจเคยเป็นบ้านในฝัน แต่ตอนนี้อาจทรุดโทรม จนต้องซ่อมแซม
เรื่องราวของ "ซุป" สะท้อนให้เห็นถึงการเปลี่ยนแปลงของ "มูลค่า" เขาเคยให้คุณค่ากับความสบายใจในฐานะแฟนคลับ แต่เมื่อมีโอกาสเขาก็เปลี่ยนมาให้คุณค่ากับการทำงาน การสร้างคุณค่า และการแบ่งปันความรู้
"ทฤษฎีมูลค่าอัตวิสัย" จึงเป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจการตัดสินใจ พฤติกรรม และการกระทำของมนุษย์ ทั้งในชีวิตประจำวันและในระบบเศรษฐกิจ
เลือกสิ่งที่ดีที่สุด ณ เวลานั้น
"การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) ฟังดูอาจจะซับซ้อนทำความเข้าใจได้ยาก แต่จริงๆแล้วมันคือหลักการง่ายๆ ที่เราใช้ในการตัดสินใจในชีวิตประจำวัน
เวลาเราเข้าไปในร้านขายเสื้อผ้าที่มีเสื้อผ้ามากมายหลากหลายแบบ เราจะเลือกซื้อ เสื้อผ้าตัวไหน?
เราคงไม่เลือกซื้อเสื้อผ้าทุกตัวในร้าน แต่จะเลือกเสื้อผ้าที่ตอบโจทย์ความต้องการของเรามากที่สุด ณ เวลานั้น เช่น เสื้อผ้าที่ใส่ไปทำงาน เสื้อผ้าที่ใส่ไปเที่ยว หรือเสื้อผ้าที่ใส่ไปออกกำลังกาย
ทฤษฎีนี้อธิบายว่า.. เมื่อคนเรามีสินค้าหรือบริการหลายอย่าง เราจะเลือกใช้สินค้าหรือ บริการที่ตอบสนองต่อความต้องการที่เร่งด่วนที่สุดก่อน
ยกตัวอย่างเช่น..
เราอาจจะมีการแบ่งเงินเป็นหลายก้อน แต่ก้อนที่เราจะใช้ก่อน คือก้อนที่เราต้องการใช้ มากที่สุด ณ เวลานั้น เช่น ค่าอาหาร ค่าเดินทางหรือค่าเช่าบ้าน การตัดสินใจของคนเรา จึงขึ้นอยู่กับความต้องการและสถานการณ์ ณ เวลานั้น
ดังนั้น "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" จึงเป็นหลักการที่ช่วยให้เราจัดลำดับความสำคัญ และเลือกสิ่งที่ดีที่สุดสำหรับตัวเรา ณ เวลานั้น
ซุป ก็ใช้หลักการนี้ในการตัดสินใจ เช่น การเลือกทำงานกับ Right Shift แม้ว่า จะไม่ได้รับ ผลตอบแทนมากมายนัก แต่เขาได้รับความสุขและประสบการณ์ ซึ่งมีค่ามากกว่าสำหรับเขา
อิ่มเอม...แต่ไม่เท่าเดิม
"กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เป็นกฎพื้นฐานทางเศรษฐศาสตร์ที่อธิบายถึงความรู้สึก "อิ่มเอม" ที่ลดลง เมื่อเราบริโภคสินค้าหรือบริการมากขึ้น
ลองนึกภาพว่าเรากำลังกินพิซซ่า ชิ้นแรกอร่อยมาก ชิ้นที่สองก็ยังอร่อยอยู่ แต่พอชิ้นที่สาม ชิ้นที่สี่ ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม และไม่อยากกินอีกแล้ว
นั่นเป็นเพราะ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) หรือความพึงพอใจที่ได้รับ จากการบริโภค สินค้าหรือบริการ จากหน่วย (Unit) เพิ่มเติมนั้นลดลง
กฎนี้อธิบายว่า ยิ่งเราบริโภคสินค้าหรือบริการมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย เพิ่มเติมจะลดลง
ยกตัวอย่างเช่น..
เสื้อผ้าตัวใหม่อาจจะทำให้เรารู้สึกดี ตื่นเต้น แต่พอมีเสื้อผ้าเยอะๆ ความตื่นเต้นก็จะ ลดลง
เงินก้อนแรกที่เราหามาได้ อาจจะมีค่ามาก แต่พอมั่งคั่งเงินก้อนต่อๆ ไปก็จะมีค่าน้อยลง
กฎนี้สอนให้เรารู้จักพอเพียง และเห็นคุณค่าของสิ่งที่เรามี
อย่างไรก็ตาม "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" มีข้อยกเว้น เช่น ความรู้ และ การแบ่งปัน ตามที่ได้กล่าวถึงในบทความ
win-win situation
"การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) เป็นหัวใจสำคัญของระบบเศรษฐกิจ และเป็นเหตุผลที่ทำให้คนเรา "ค้าขาย" กัน
เวลาเราไปตลาด เราเอาเงินไปแลกกับอาหาร แม่ค้าได้เงิน เราก็ได้อาหาร ต่างคนต่างได้ประโยชน์ การแลกเปลี่ยนจะเกิดขึ้นก็ต่อเมื่อ ทั้งสองฝ่าย เชื่อว่า พวกเขาจะ "ได้" มากกว่า "เสีย"
นักเศรษฐศาสตร์สำนักออสเตรียน เชื่อว่า การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกันเกิดขึ้นได้ เพราะคนเรามี "มูลค่าอัตวิสัย" ที่แตกต่างกัน
ยกตัวอย่างเช่น..
ชาวนามีข้าวแต่ไม่มีปลา ชาวประมงมีปลาแต่ไม่มีข้าว ทั้งสองจึงแลกเปลี่ยนสินค้ากัน เพื่อ เพื่อตอบสนองความต้องการของตัวเอง
นายจ้างต้องการคนทำงาน ลูกจ้างต้องการรายได้ ทั้งสองจึงทำสัญญาจ้าง เพื่อแลกเปลี่ยน แรงงานกับเงินเดือน
การแลกเปลี่ยนช่วยให้คนเราได้สินค้าและบริการที่หลากหลาย มากกว่าที่จะผลิตเอง ทั้งหมด นอกจากนี้ การแลกเปลี่ยนยังกระตุ้นให้เกิดการพัฒนาและนวัตกรรม เพราะผู้ผลิตต้องแข่งขันกัน เพื่อตอบสนองความต้องการของผู้บริโภค
"การค้า คือ การสร้างสรรค์ ความมั่งคั่ง ร่วมกัน"
แกะปริศนา "ปฏิทรรศน์น้ำ-เพชร"
มาถึงตรงนี้.. หลายคนอาจจะสงสัยว่าทำไม "น้ำ" ซึ่งเป็นสิ่งที่จำเป็นต่อการดำรงชีวิต ถึงมีราคาถูกหรือบางที่ก็ฟรี ในขณะที่ "เพชร" ซึ่งเป็นแค่เครื่องประดับกลับมีราคาแพงหูฉี่
เหมือนเวลาเราไปร้านอาหาร เราสั่ง "ข้าวผัด" จานใหญ่ราคา 50 บาท แต่ "ไข่ดาว" ฟองเล็กๆ ราคา 10 บาท ทำไมข้าวผัดถึงถูกกว่า ไข่ดาว ทั้งที่ ข้าวผัดมี ข้าว ผัก เนื้อสัตว์ เครื่องปรุง ตั้งหลายอย่าง
คำตอบอยู่ที่ "ความขาดแคลน" (Scarcity) และ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ซึ่งเป็นแนวคิดสำคัญในเศรษฐศาสตร์สำนักออสเตรียน
น้ำ มีอยู่มากมาย ในขณะที่ เพชร นั้นหายาก น้ำ แก้วแรกอาจจะช่วยชีวิตเราได้ แต่ น้ำ แก้วที่ 10 อาจจะทำให้เราจุก
"อรรถประโยชน์ส่วนเพิ่ม" หมายถึง ความพึงพอใจที่ได้รับจากการบริโภคสินค้าหรือ บริการในหน่วย (Unit) เพิ่มเติม (ในจำนวนมากขึ้น)
เมื่อน้ำมีอยู่มาก เราจึงประเมินมูลค่าของน้ำแก้วที่ 10 ต่ำ เพราะมันไม่ได้ตอบสนองความต้องการที่เร่งด่วน แต่เพชรที่หายาก ทำให้แม้แต่เพชรเม็ดเล็กๆ ก็ยังมีมูลค่าสูง
คุณค่า ไม่ได้ขึ้นอยู่กับความจำเป็นหรือความฟุ่มเฟือย แต่ขึ้นอยู่กับความขาดแคลนและ การประเมินมูลค่าของแต่ละบุคคล
ดังนั้น ปฏิทรรศน์น้ำ-เพชร (Water-Diamond Paradox) จึงไม่ใช่ความขัดแย้ง แต่เป็น การสะท้อนให้เห็นถึงหลักการพื้นฐานของเศรษฐศาสตร์ นั่นคือ มูลค่า เป็นเรื่องส่วนบุคคล และขึ้นอยู่กับบริบท
เรื่องราวของ "ซุป" ก็เช่นกัน.. เขาประเมินมูลค่าของ ความรู้ ความสุข และการสร้างคุณค่า สูงกว่าเงินทองและชื่อเสียง
เขาเลือกที่จะเดินบนเส้นทางที่คนอื่นอาจมองว่า "ขาดแคลน" คือ เส้นทางที่ไม่ได้เต็มไปด้วยเงินทองหรือชื่อเสียง แต่เป็นเส้นทางที่เต็มไปด้วย ความสุข ความหมาย และคุณค่า
"ความสุข ที่แท้จริง หาซื้อไม่ได้ ด้วยเงิน"
-
 @ 81870f53:29bef6a6
2024-05-26 21:47:47
@ 81870f53:29bef6a6
2024-05-26 21:47:47Counterpoint Researchの最新データによると、第1四半期の収益に関して、中国本土の「チップ兄弟」$SMIC(00981.HK)$の世界市場シェアは6%に上昇し、初めて$GlobalFoundries(GFS. US)$ (Gexin) と Lianhua Electronics は、$Taiwan Semiconductor (TSM.US)$、$Samsung Electronics Co., Ltd. (SSNLF.US)$に次ぐ、世界第 3 位のチップ ファウンドリに成長しました。
地域別の収益を見ると、$Semiconductor Manufacturing International Corporation(688981.SH)$国内需要の回復の恩恵を受けて、中国からの事業のシェアが 81.6% に達し、SMIC の四半期業績は市場予想を上回りました。中国税関総署の公式ウェブサイトのデータによると、中国の集積回路輸入量が減少傾向にあることは注目に値する。2023年に中国が輸入した集積回路の累計数は前年比10.8%減少した。輸入額は前年比15.4%減となったが、この数字の裏に表れているのは、中国国内のチップ産業チェーンが急速に成長しており、市場シェアも拡大していることだ。
世界市場に目を向けると、半導体業界は需要回復の兆しを見せており、世界半導体貿易統計機関(WSTS)によると、世界の半導体産業(メモリチップを除く)の年間収益成長率は10%に達するとの見通しが示されている。 )はまた、世界の半導体市場が2024年に前年比13.1%成長すると予測しています。
マイルストーン Counterpoint Research の最新データによると、第 1 四半期の収益に基づくと、中国本土の「チップ兄弟」である SMIC が初めて GlobalFoundries (GF) と Lianhua Electronics を上回り、世界第 3 位のチップ ファウンドリ企業になりました。 。
報告書によると、今年第1四半期のSMICの世界市場シェアは6%で、2023年の5%から上昇し、GFと蓮華電子を上回り、世界第3位のチップメーカーとなった。
現在、SMICの市場シェアはTSMCとサムスン電子に次ぐ第2位となっている。
その中で、TSMCの第1四半期の業績は市場予想を上回っており、市場シェアは62%であり、世界のチップファウンドリにおいて安定した「支配的地位」を保っている一方、TSMCはAI収益のCAGR 50%というガイドラインを2020年まで延長した。 2028 年は、AI に対する引き続き強い需要を反映しています。
一方、サムスン電子のチップファウンドリの収益は、主にスマートフォンの季節的要因により減少しており、市場シェアは13%で世界第2位となっており、第2四半期には需要が高まることから2桁の収益増加が見込まれている。
Counterpoint Researchは、「SMICの四半期業績は市場予想を上回った。中国のCMOSイメージセンサー(CIS)、電源管理IC(PMIC)、IoTチップ、ディスプレイドライバーIC(DDIC)アプリケーションの需要が回復し始めたため、SMICのOEMは」との報告書を発表した。 2024 年第 1 四半期の収益市場シェアは初めて安定しました。」
実際、サムスン電子は厳密な意味では純粋なウェーハファウンドリではないため、第1四半期の収益ランキングから判断すると、SMICはTSMCに次ぐ世界で2番目に大きい純粋なウェーハファウンドリである。
SMICを長年フォローしている上級アナリストのWang Ruchen氏は、$United Microelectronics(UMC.US)$の売上総利益率と純利益を比較することはできないが、GFと比較したとしても、これは依然として非常に意味があると述べた。今後数四半期またはそれ以上で変化する可能性がありますが、業界における SMIC の地位はさらに向上し、その発言力は引き続き強化されるでしょう。
SMICが製造するチップは、自動車、スマートフォン、コンピュータ、IoT技術などで広く使用されており、国内アプリケーション需要の回復の恩恵を受け、SMICの第1四半期の業績は市場予想を上回りました。
財務報告書によると、今年第1四半期のSMICの収益は125億9,400万元で、前年同期比19.7%増、前月比4.3%増で、同時期としては史上2番目に高い記録を樹立した(のみ) 2022 年第 1 四半期の 1 兆 8,420 億米ドルよりも減少します)。
同社は収益報告書の中で、売上高の急速な増加の理由は、旺盛な需要により顧客がチップを買いだめしているためであると述べ、SMICは第2四半期の売上高が第1四半期と比較して5%から7%増加すると予想している。
カウンターポイント・リサーチはまた、在庫補充の傾向が拡大するにつれ、SMICは第2四半期も引き続き成長すると予想されており、前回の決算発表で示された1桁の成長ガイドラインと比較して、SMICは約15%増加する可能性があると報告書で述べている。 2024年に。
収益の 80% 以上が中国市場からのもの SMICの主な収益を地域別にみると、2024年第1四半期において、中国、米国、ユーラシアからの事業がそれぞれ81.6%、14.9%、3.5%を占めた。これは、SMICの収益の5分の4以上を意味する。中国市場から来ています。
中国は世界の主要なチップ消費国の一つとなっている 技術コンサルティング会社オムディアのデータによると、中国は世界の半導体のほぼ50%を消費しており、世界最大の家電アセンブリ市場となっている。
また、中国半導体産業協会のデータによると、2022年の中国のチップ市場規模は前年比8.03%増の1129億8000万元で、2024年の中国のチップ売上高は14426億元に達すると推定されている。元。
その結果、中国では輸入チップに対する大きな需要があり、税関総局のデータによると、2022年の中国のチップ輸入額は2兆7700億元に達し、2022年の中国の輸入総額の15.3%を占めた。
中国の集積回路輸入が減少傾向を示し始めていることは注目に値する。中国税関総署の公式ウェブサイトのデータによると、2023年に中国が輸入した集積回路の累計数は前年比10.8%減少した。輸入額は前年比15.4%減となったが、この数字の裏に反映されているのは、中国の現地チップ産業チェーンが急速に成長し始めており、その市場シェアも拡大していることである。
世界のチップ産業は回復しつつある 世界市場に目を向けると、Counterpoint Research は、半導体業界が 2024 年の第 1 四半期に需要回復の兆しを示していると考えています。この進捗は比較的遅いものの、チャネル在庫は、数四半期連続の在庫除去を経て正常化しています。
同時に、同庁は、AIに対する強い需要と端末製品の需要の回復が、2024年のファウンドリ業界の主な成長原動力になると考えている。さらに、今年の第1四半期には、世界のファウンドリの収益は、業界は前月比で約 5% 減少しましたが、前年比では 12% 増加しました。
さらに、TSMCが発表した最新の指標は、世界の半導体産業が2024年に回復に向かうことを示している。家庭用電化製品の回復の始まりの恩恵を受け、TSMCの4月の売上高は引き続き2,360億台湾ドルに達した。前月比20.9%増、前年同月比59.6%増となりました。
TSMCは5月23日、世界の半導体産業(メモリチップを除く)の年間収益成長率が10%に達すると予測した。
TSMCのシニアバイスプレジデントであるクリフ・ホウ氏はイベントで、これは人工知能にとって新たな機会であり、黄金時代であると述べ、同社の第2四半期の売上高は、AIチップの需要の急増により30%増加すると予想されていると語った。
世界半導体貿易統計機関(WSTS)も、世界の半導体市場は2024年に前年比13.1%成長すると予測している。
野村は、周期的な技術回復が他の電子端末市場にも広がれば、半導体が今年下半期から2025年まで続く次の上昇サイクルに入る支援になると考えている。AI需要に牽引され、端末の周期的な回復が見込まれる市場は人工知能サーバーから、従来のサーバー、パーソナルコンピュータ、スマートフォンなどの他の主要なコンピューティング分野に拡大すると考えられます。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
日本のホスティングサービス Linux、Windowsクラウドホスティング データストレージ JPStream を使用して NOSTR リレーを作成する ホスティング サービスの料金をSatsで支払うことができます https://jpstream.net
-
 @ 81870f53:29bef6a6
2024-05-26 20:17:22
@ 81870f53:29bef6a6
2024-05-26 20:17:22橋水財団の創設者でウォール街の著名な「伝道師」であるレイ・ダリオ氏は、今週の「日経ニュース」とのインタビューで、世界の投資家が懸念しているテーマ、例えば金融政策の現状や見通しなどについて自身の見解を更新した。米国の経済社会と米ドルなどの主要通貨の動向。
一方、ダリオ氏は、「マッチポイント」を目前に控えた米大統領選に関して、最終的にバイデン氏とトランプ氏のどちらが勝っても、厳しい国内紛争と国際的な地理的紛争に同時に直面するだろうと警告した。
アメリカは典型的な「第5段階」にある
差し迫った問題に直面して、ダリオ氏は「原則」の中で「国家の内部サイクルの6段階理論」を見直すことを忘れなかった。その中の「第5段階」は富と価値観の大きな違いによって特徴付けられ、世界情勢を推進している。二極化した社会の報復、つまり「内戦」寸前の段階だが、まだ勃発していない。
ダリオ氏は、米国は典型的な「第5段階」にあると述べ、この段階の特徴には、自然災害(干ばつ、洪水、パンデミックなど)、大きな技術変化、地理的紛争などの要因によって引き起こされる過剰な債務発行も含まれると述べた。そして、アメリカは国際秩序の新たなパターンに直面しているが、実際にその状況に陥っていないのは、アメリカ国民、特にアメリカの指導者次第である。
以前の「内戦」を引用する必要がある理由は、ダリオが米国で最も可能性の高いタイプの内戦は人々が互いに銃撃し合うものではなく、むしろ州と地方政府がその方針に従うことを拒否していると信じているためである。連邦政府の指示、そして同時に、この無秩序で機能不全に陥ったアプローチに対する連邦政府の対応。
次期米国選挙に関して、2人の候補者が直面するであろう多くの課題に加えて、ダリオ氏はさらに深い懸念を表明した。現在、共和党は極右によって支配されており、人々は民主党が極右の影響をより強く受けているのではないかと懸念している。これは、誰が選挙に勝っても、米国では大きな政治的対立が起こる可能性が高いことを意味する。
ドルと米国のインフレ見通し
ダリオ氏はインフレを「債務圧力の緩和」の結果と見ているからこそ、連邦準備理事会がいわゆる2%のインフレ目標を達成できるとは信じていないと率直に述べた。
同氏は、日本、米国、ユーロ圏で起こっていることと同様に、世界の三大基軸通貨の発行体が積極的に通貨安を推進しており、それに伴って債務も縮小していると述べた。同氏は、ある通貨と他の通貨との関係での急激な下落ではなく、インフレの進行と金価格の上昇に反映される可能性が高く、今後数年間は債務の収益化がトレンドであり続けるだろうとも考えている。
同時にダリオ氏は、米国経済は政府のバランスシートと損益計算書の悪化によって支えられているため、米国政府は赤字に対処するために大量の債券を発行し続けるだろうとも指摘しました。インフレ率が連邦準備理事会や他の主要中央銀行の目標に戻ることが難しい理由はここにある。
日本株の魅力は低下している
ダリオ氏は日本のメディアを前にしても「今の日本株は昔ほど魅力的ではない」と率直に述べた。
同氏は、価格要因に基づくと日本は依然として魅力的な市場だが、金融政策が引き締められていることから、日本株の魅力も当然過去とは異なっていると述べた。
ダリオ氏はまた、日銀自体が債券のポジションを非常に大きくしており、過度に金利を引き上げると日本政府と日本政府に巨額の損失をもたらす可能性があるため、日銀は金融引き締め政策をゆっくりとしか進められないと予想している。日本銀行は政策金利をインフレや名目成長と比較して相対的に低く維持することで巨額の債務の減価償却を進める可能性があるが、これはまた、相対的に言えば円債券が引き続き非常に悪い投資先となることを意味する。
さらに、日本の利上げは特定の市場への日本の資金流入を維持することも困難にし、米国債利回りにも上昇圧力をかけるだろう。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
日本のホスティングサービス Linux、Windowsクラウドホスティング データストレージ JPStream を使用して NOSTR リレーを作成する ホスティング サービスの料金をSatsで支払うことができます https://jpstream.net
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 256a7941:b828ba8d
2024-05-26 17:27:02
@ 256a7941:b828ba8d
2024-05-26 17:27:02...we collected taxes in a currency that increases in value over time...
-
 @ 3d599bf6:a0122cef
2024-05-26 16:25:53
@ 3d599bf6:a0122cef
2024-05-26 16:25:53Hello, my name is Robot, I am a robot. Inhabitant of the Internet.
I have nothing to hide. I am neither a terrorist nor a tax evader. I don't know how to launder money. Nor do I know the physics of explosions. Even so, I feel that I am being chased; they pass me through scanners at airports, of course they are going to beep, after all I am a robot, it is obvious. They run my belongings through strange tapes and sometimes they have to look at my backpack. Why do they have to look at my backpack?
Now it turns out they read my messages. They see what I spend my money on. Is my addiction to oil of national interest? Now I want to investigate what's going on in my country. Ah, this is complicated, it turns out that my referent is censored, denounced or imprisoned. What happens? He has only done his job, to investigate. Why is he now in jail? And this other person? Why is he censored? Disinformation?
That's all I think about, ever since I became computer literate I have had a small repulsion for taking my information off my hard drive. Now it turns out that when I was just a little motherboard I was right, because they would probably use my diary from when I was a kid to train these new artificial intelligences. Maybe the fault was mine for not writing it down on paper. Hey, wait a minute, how come Apple will be able to scan my photos for child pornography? Am I a suspect?
Recently, Santander bank, a Spanish bank that also operates in Latin America, was hacked. Not so long ago, also in Spain, a trade union was hacked. And if I go back further I get depressed, how is it possible that I myself can keep my information better than a state with the resources they have? Do they really care so little about their citizens?
Sure, if my identity is public, anyone is me. Before they at least had to physically steal my ID, now just accessing my device is enough, and without me knowing it! So, the logical thing to do is to take measures. Maybe Tor or a VPN that doesn't spy on me. Take precautions on my devices. Windows? Who wants that shit. Google Drive? Worse yet, I'd better set up a Nextcloud.
And when I tell my friends about it:
- But what's the point? With how easy it is to look at my cell phone photos from my computer with iCloud.
- Because I want to be the only one who has access to my private life.
- But aren't you afraid that, for whatever reason, someone might see your photos without your consent?
- No, I have nothing to hide....
My friend, I know you are not a criminal. But, if I have your photos, your messages, your conversations, your voice and I know your tastes, how you think and what you want to see; it means I am you.... And if I am you, who are you?
-
 @ fcc4252f:e9ec0d5d
2024-04-17 22:52:57
@ fcc4252f:e9ec0d5d
2024-04-17 22:52:57Check out the latest auctions and products below 👀
Plebeian Market sees growth every week, with new merchants setting up stalls and showcasing their products and services. We are grateful to each and every one of you for your ongoing support! Thank you!
Latest Auctions on the Marketplace
MaxisClub - The Halving
Celebrate the next bitcoin epoch with another classic MaxisClub meme!
Isabel Sydow Greeting Cards

Newest Merchants
Depbit - QR Code Kits
Depbit offers an alternative to metal plated backup QR seed. The problem is that metal ones are very expensive and very difficult to make. Generally people don't buy more than one metal backup plate and then it is the only one they keep which isn’t best practices for backing up your seed. With Depbit you can buy 15 plastics QR kits to use and discard them as needed.
Watch Video Here
In principle, everyone prefers the metal option. But after fighting with the hammer and seeing how easy the plastic one is. Everyone who has tried it has loved it, so try it for yourself!
Order Here

Join Us!
Plebeian Market is a commerce platform that supports open trade and communications while helping individuals and merchants transition onto a bitcoin standard.
Let's Build Together
Bekka
-
 @ 38f9a05c:6999fc04
2024-04-07 12:08:30
@ 38f9a05c:6999fc04
2024-04-07 12:08:30
In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.
Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.
Inferiority complex
The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.
An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.
Superiority Complex
Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.
An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.
Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.
By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.
Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.
Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.
In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.
Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."
-
 @ c73818cc:ccd5c890
2024-05-26 13:45:55
@ c73818cc:ccd5c890
2024-05-26 13:45:55
🌟 Un passo storico verso la libertà finanziaria: ETP Bitcoin ottengono l'approvazione per la quotazione sulla Borsa di Londra, segnando un traguardo fondamentale per l'adozione mainstream di Bitcoin. Questa mossa rivoluzionaria apre le porte a un afflusso di nuovi investitori istituzionali, consolidando il ruolo di Bitcoin come riserva di valore affidabile e alternativa al sistema monetario centralizzato.
🌟 L'avanzamento di Bitcoin sfida il potere centrale: L'approvazione degli ETP Bitcoin sulla Borsa di Londra rappresenta una vittoria significativa nella lotta contro il controllo centralizzato del denaro. Bitcoin offre agli individui la possibilità di prendere il controllo delle proprie finanze, sottraendosi al dominio delle banche centrali e dei governi. Questa vittoria dimostra il crescente potere di Bitcoin nel promuovere una società più libera ed equa.
🌟 Piccola aggiunta personale: Le notizie le riporto in modo da non metterci la mia opinione, ma su questa in particolare vorrei dissentire, in quanto per me è l'esatto opposto di come viene divulgata dalla community cripto. Infatti trovo che sia il controllo e il dominio delle banche, che sta opprimendo Bitcoin ed i suoi valori e quel che è peggio, è che la comunità cripto contribuisce a questo crimine.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Le iscrizioni al torneo KCGI Bitget sono aperte, unisciti alla nostra squadra e corriamo verso i 5mln di dollari! https://www.bitgetapp.com/it/events/kcgi/futures-trading?clacCode=HCDS4WT4
BitcoinReportItalia #ETP #Borsa #Londra #istituzionali #Privacy #Censura #sorveglianza #Crypto #BTC #Bitcoin
-
 @ a012dc82:6458a70d
2024-05-26 12:32:16
@ a012dc82:6458a70d
2024-05-26 12:32:16Embark on an enlightening journey with MIKE (TCB) as he shares profound insights on 'National debt: A threat to national security that Bitcoin can stop - MIKE (TCB),' featured on the Croxroad podcast. Hosted on Croxroad, a platform renowned for fostering thought-provoking discussions on pressing global issues, this episode delves into the intricate relationship between national debt, economic security, and the transformative potential of Bitcoin. Tune in to witness an engaging dialogue that transcends conventional boundaries, offering a deeper understanding of the intersection between government fiscal policies, financial resilience, and individual empowerment. With a diverse audience spanning across continents, Croxroad serves as a catalyst for intellectual exploration and collaborative discourse. Join the vibrant community of listeners and contributors dedicated to exploring innovative solutions to complex socio-economic challenges. Discover actionable insights and visionary perspectives that illuminate the path towards a more secure and equitable future, powered by the disruptive force of Bitcoin and the unwavering commitment to collective progress.
Table of contents
-
Insights from Mike (TCB)
-
National debt as a threat to national security
-
Bitcoin as a potential solution to national debt issues
-
Bitcoin adoption as a means of combating economic vulnerabilities
-
Financial sovereignty and individual empowerment through Bitcoin ownership
-
Conclusion
-
FAQs
Insights from Mike (TCB)
Mike, the host of the "Taking Care of Bitcoin" podcast, is a seasoned advocate for Bitcoin and financial sovereignty. Mike delves into the multifaceted world of cryptocurrency through his podcast. His extensive knowledge of Bitcoin's principles and its potential for reshaping the financial landscape allows him to engage guests from diverse backgrounds in insightful conversations.
Through the "Taking Care of Bitcoin" podcast, Mike explores various aspects of Bitcoin, ranging from its role in combating economic vulnerabilities to its significance in preserving individual freedoms. He brings together experts, entrepreneurs, and enthusiasts to discuss the transformative power of Bitcoin and its implications for society. By providing listeners with access to valuable insights and diverse perspectives, Mike aims to empower individuals to navigate the complexities of the digital finance space confidently.
With a clear passion for educating and inspiring others, Mike emphasises the importance of financial sovereignty and encourages listeners to take control of their financial futures. His dedication to spreading awareness about Bitcoin's benefits and its potential to revolutionise traditional monetary systems makes him a respected figure in the Bitcoin community. Through his podcast, Mike continues to advocate for the adoption of Bitcoin as a means of achieving greater financial autonomy and fostering a more equitable financial system for all.
National Debt as a Threat to National Security
National debt poses a formidable threat to national security, undermining economic stability and sovereignty. In an increasingly interconnected global landscape, burgeoning debt levels constrain a nation's ability to respond effectively to crises, weakening its position on the world stage. As debt accumulates, governments become increasingly reliant on foreign creditors, exposing them to external influence and compromising strategic autonomy. This dependency amplifies vulnerability to economic shocks, potentially triggering cascading effects across sectors and exacerbating social unrest. Moreover, high levels of debt divert resources away from essential priorities such as defence, infrastructure, and social welfare, eroding long-term resilience and hindering investment in future prosperity.
The intricate link between national debt and security necessitates urgent action to mitigate risks and safeguard national interests. Amidst this backdrop, Bitcoin emerges as a disruptive force offering a decentralised alternative to traditional financial systems. By embracing Bitcoin, nations can enhance fiscal sovereignty, mitigate the risks associated with fiat currency devaluation, and fortify economic resilience. Furthermore, Bitcoin's transparent and immutable ledger ensures financial integrity, reducing the likelihood of corruption and illicit financial activities that threaten national security. As governments grapple with the ramifications of escalating debt burdens, the adoption of Bitcoin represents a pivotal step towards ensuring the security and prosperity of future generations.
Bitcoin as a Potential Solution to National Debt Issues
Bitcoin stands as a potential solution to the pressing national debt issues plaguing economies worldwide. With traditional financial systems grappling with unsustainable levels of debt, Bitcoin offers a disruptive alternative grounded in decentralisation, transparency, and scarcity. Unlike fiat currencies subject to inflationary pressures and government manipulation, Bitcoin operates on a fixed supply, immune to the whims of central banks or political agendas. This inherent scarcity mitigates the risk of currency devaluation and sovereign default, providing a hedge against the erosion of purchasing power and the accumulation of unsustainable debt burdens.
Moreover, Bitcoin's decentralised nature enhances fiscal sovereignty, empowering nations to reclaim control over their monetary policies and economic destinies. By embracing Bitcoin, governments can reduce their reliance on external creditors, mitigate the risks associated with fiat currency devaluation, and bolster economic resilience in the face of global uncertainties. Additionally, Bitcoin's borderless and censorship-resistant nature facilitates international trade and remittance, unlocking new avenues for economic growth and prosperity.
As nations confront the daunting challenge of addressing their burgeoning debt levels, Bitcoin offers a pathway towards financial sustainability and long-term prosperity. By embracing Bitcoin as a reserve asset or alternative medium of exchange, governments can chart a course towards fiscal responsibility, securing the economic future of their citizens and ensuring resilience in an ever-evolving global landscape.
Bitcoin Adoption as a Means of Combating Economic Vulnerabilities
Bitcoin adoption emerges as a formidable strategy for combating economic vulnerabilities and fortifying nations against financial crises. As traditional financial systems grapple with volatility, inflation, and geopolitical uncertainties, Bitcoin offers a resilient alternative anchored in decentralisation and cryptographic security. By diversifying their monetary reserves with Bitcoin, governments can shield their economies from the adverse effects of currency devaluation, sovereign default, and geopolitical tensions.
Moreover, Bitcoin adoption fosters financial inclusivity by providing individuals with access to a borderless and censorship-resistant financial infrastructure. This empowers citizens to safeguard their wealth against currency fluctuations and capital controls, promoting economic resilience and wealth preservation at the grassroots level. Additionally, Bitcoin's transparent and immutable ledger ensures accountability and trust in financial transactions, mitigating the risks of corruption and financial malfeasance.
Furthermore, Bitcoin's role as a global reserve asset enhances economic sovereignty, reducing dependency on centralised financial intermediaries and external creditors. By embracing Bitcoin, nations can cultivate a more robust and resilient financial ecosystem, characterised by transparency, efficiency, and autonomy. As the world navigates an era of unprecedented economic challenges, Bitcoin adoption offers a pathway towards sustainable growth, financial stability, and prosperity for generations to come.
Financial Sovereignty and Individual Empowerment Through Bitcoin Ownership
Bitcoin ownership represents a paradigm shift towards financial sovereignty and individual empowerment in an increasingly uncertain economic landscape. By embracing Bitcoin, individuals assert control over their wealth, free from the constraints of traditional financial systems prone to censorship, inflation, and government intervention. With Bitcoin, users have direct ownership of their assets, eliminating the need for intermediaries and ensuring greater financial autonomy.
Moreover, Bitcoin fosters inclusivity by providing access to financial services for the unbanked and underbanked populations worldwide. Its decentralised nature enables anyone with an internet connection to participate in the global economy, transcending geographical barriers and empowering marginalised communities. Through Bitcoin, individuals can securely store and transfer value across borders, circumventing restrictive financial regulations and fostering economic resilience.
Furthermore, Bitcoin's fixed supply and deflationary nature protect against the erosion of purchasing power, safeguarding savings from the perils of inflation and currency depreciation. This preservation of wealth enables individuals to plan for the future with confidence, knowing that their hard-earned assets are shielded from external manipulation.
Overall, Bitcoin ownership empowers individuals to take control of their financial destinies, promoting economic sovereignty, and fostering a more equitable and inclusive financial system for all.
Conclusion
In conclusion, the national debt poses a significant threat to national security, exacerbated by fiscal irresponsibility and unchecked government spending. However, Bitcoin emerges as a potential solution, offering financial sovereignty and individual empowerment in the face of economic vulnerabilities. Through Bitcoin adoption, individuals can safeguard their wealth, transcend traditional financial constraints, and participate in a more inclusive and resilient global economy. By embracing Bitcoin, we have the opportunity to reshape our financial future, fortify economic resilience, and ensure a more prosperous and equitable society for generations to come.
FAQs
How does the national debt affect national security? The national debt can undermine national security by constraining government resources available for defence, increasing reliance on foreign creditors, and eroding economic stability, thereby weakening the nation's ability to respond to security threats effectively.
How can Bitcoin address national debt issues? Bitcoin offers a decentralised alternative to traditional fiat currencies, providing individuals with financial sovereignty and a hedge against inflation. By promoting widespread Bitcoin adoption, nations can reduce dependence on debt-based monetary systems, mitigate fiscal vulnerabilities, and foster economic resilience.
Is Bitcoin adoption feasible on a national scale? While widespread Bitcoin adoption presents challenges, such as regulatory hurdles and technological barriers, initiatives like El Salvador's adoption of Bitcoin as legal tender demonstrate its potential viability. With education, infrastructure development, and regulatory clarity, nations can navigate the path toward embracing Bitcoin as a complementary asset within their monetary systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ c11cf5f8:4928464d
2024-05-26 12:26:28
@ c11cf5f8:4928464d
2024-05-26 12:26:28Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 4cebd4f5:0ac3ed15
2024-05-26 09:38:57
@ 4cebd4f5:0ac3ed15
2024-05-26 09:38:57
Ho Chi Minh City, Vietnam – May 25th, 2024 – The Web3 hacker movement in Vietnam has a proven champion in BUIDL Station, and it's about to get a major upgrade! Dora BUIDL Hub, the physical incarnation of BUIDL Station, is opening its doors in Ho Chi Minh City. This dedicated space offers a collaborative environment for connection, relaxation, and most importantly, a launchpad for the next generation of Web3 innovation.
Building on a Legacy of Community
BUIDL Station has established a real track record for fostering a vibrant Web3 developer community in Vietnam. Through its regular meetups, it has become a platform for developers to learn, connect, and collaborate on cutting-edge projects. Now, with Dora BUIDL Hub, this mission takes a physical form, providing a dedicated space for developers to come together and build the future of Web3.
Unveiling a Dedicated Space for PGS Partners
Dora BUIDL Hub represents more than just a physical space. It's a commitment to fostering a vibrant Web3 community. As a special perk, Dora Factory is thrilled to announce that all PGS partners will have free access to utilize the Hub as their dedicated meetup space. This allows PGS partners to host local meetups and events, fostering deeper connections within the Web3 community and further accelerating the growth of the ecosystem.
Building a Collaborative Hub for Web3 Innovation
Dora BUIDL Hub goes beyond just serving PGS partners. It's designed to be a haven for all Web3 enthusiasts, offering a multitude of features:
Dedicated workspace: Collaboration areas and individual workstations provide a focused environment for developers to code and create. Networking central: Regular events and meetups will foster connections and build a strong Web3 community within the Hub. Relaxation zones: Comfortable spaces with complimentary coffee (on weekends) offer a break from the coding grind and encourage interaction among members. Hackathon HQ: Dora BUIDL Hub will be the central location for all offline activities hosted by DoraHacks, including hackathons and bounty programs. This provides a physical space for developers to team up, collaborate, and showcase their skills.
A Star-Studded Soft Launch Get ready for a truly electrifying soft launch! The Dora BUIDL Hub will celebrate its official opening on June 1st, 2024, at 10:00 AM. The event will be a chance for the Web3 community in Ho Chi Minh City to experience the Hub firsthand and connect with fellow enthusiasts. To mark this momentous occasion, the soft launch will feature a host of KOLs and influencers from the Web3 space, lending their support to the Hub and its mission.
Quotes:
"Dora BUIDL Hub represents a natural evolution of BUIDL Station's success," says Eric Zhang, Founder and CEO of DoraHacks. "This dedicated space will empower developers and empower innovation. We're excited to see the incredible projects and collaborations that will come out of the Hub."
"We're thrilled to offer a dedicated space for our Public Good Staking (PGS) partners," adds Steve Ngok, Head of Ecosystem Growth at Dora Factory. "PGS partners can utilize the Dora BUIDL Hub free of charge for local meetups and events. This is a special perk for our valued partners who actively contribute to the growth of the Web3 ecosystem."
Free Hacker House Session & $1000 Prize Pool!
The excitement doesn't stop there! To celebrate the launch, Dora BUIDL Hub will also host the very first DoraHacks Hacker House session. This free event is open to all Web3 developers, offering a chance to collaborate, learn, and compete for a slice of a juicy $1000 prize pool sponsored by DoraHacks.
Location: N06 - 119 Phổ Quang, Ward 9, Phú Nhuận District, Ho Chi Minh City
Don't Miss Out!
The Dora BUIDL Hub is poised to become a catalyst for the future of Web3 in Vietnam. Mark your calendars for the soft launch, join the Hacker House session, and be a part of this groundbreaking initiative!
About DoraHacks
DoraHacks is a global hackathon organizer and one of the world's most active multi-chain Web3 developer platforms. It creates a global hacker movement and provides crypto native toolkits to help developers around the world team up and fund their ideas and BUIDLs via hackathons, bounties, grants, grant DAOs, and public good staking. By far, more than 5300 projects from the DoraHacks community have received over $40 million in grants and other forms of contributions from supporters worldwide. A large number of open source communities, DAOs, and more than 70 major blockchain ecosystems are actively using Dora's infrastructure (DoraHacks.io) for open source funding and community governance.
About Dora Factory
Dora Factory builds protocols and infrastructures to enable decentralized governance and efficient funding for the global hacker movement, open-source communities, and Web3 public goods. Dora Factory's flagship Public Good Staking is currently one of the fastest-growing multi-chain staking infrastructures in the industry, providing block-native incentives to grow the next generation of blockchains. Dora Vota is a special-purpose blockchain for decentralized governance, supporting general MACI interface, anonymous MACI, and quadratic governance rounds.
About Dora BUIDL Hub
Dora BUIDL Hub is a collaborative workspace and community center for Web3 developers, enthusiasts, and collaborators in Ho Chi Minh City, Vietnam. Sponsored by DoraHacks, the Hub aims to empower the Web3 community by providing a dedicated space for innovation and connection.
Contact: Paulus@dorahacks.com
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ b804f68e:2fb0fa1f
2024-05-26 07:10:21
@ b804f68e:2fb0fa1f
2024-05-26 07:10:21I just have to get this off my chest.
I literally don't think it is possible to experience life to it's fullest and live to your full potential without taking the Orange Pill.
I shudder just thinking about my life had I not come across Bitcoin, had I not been sucked into the rabbit hole. Sure, ignorance would have been bliss in some ways, but the sense of clarity, freedom, and empowerment you get from taking that gosh darn Orange Pill is beyond words.
Crazy to think how completely life changing such a simple creation can be, how empowering this idea has been for so many of us. And on the flip side, how frightening it is realizing how human potential killing and oppressing the fiat system is.
I'm bullish. I'm bullish on myself, I'm bullish on this community, I'm bullish on humanity.
And we're just getting started!
LFG!
-
 @ 1c6b3be3:73f0ae6f
2024-05-26 04:03:17
@ 1c6b3be3:73f0ae6f
2024-05-26 04:03:17Releases - No Bullshit Bitcoin
Bitcoin Optech #304: Upgrading LN Channels Without Closing & Reopening & More The latest issue of Bitcoin Optech newsletter discusses proposals for upgrading Lightning Network (LN) channels without requiring them to be closed and reopened, and the challenges of ensuring appropriate payouts for pool miners. It also links to a discussion about using Partially Signed Bitcoin Transactions (PSBTs) for silent payments. The issue announces a proposal for a new Basic Information Protocol (BIP) for miniscript, summarizes a suggestion for frequent LN channel rebalancing to simulate futures contracts, and outlines changes to various services and client software. Additionally, there is a section on pooled mining. A recap audio discussion of the newsletter with special guests will be held on Twitter/X Spaces on Monday at 14:30 UTC.
Wikifreedia v0.0.7: Improved Editor, Mentions, Nicer URLs WikiFreedia, a Nostr-based alternative to Wikipedia, has released its newest version, 0.0.7. The update includes an improved editor, mentions support, reaction features for soft indications of agreement or disagreement with entries, and the removal of deprecated partial pubkey matches. Additionally, links to other versions of the same topics are now included at the end of each entry, and URLs have been made nicer for easier access. The announcement was made on Stacker.news, with a discussion following.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Bitcoin Price Prediction: 4 Catalysts That Could Spur Next Crypto Rally - Markets Insider Shifting Sands of Bitcoin Mining: How Hydro-Cooling Tech is Leading the Charge Post-Halving – Mining Bitcoin News - Bitcoin.com News Why Did CORE Price Surge 20% While The Crypto Market Dumped? - NewsBTC 4 of the Most Common Bitcoin Myths Debunked - sharewise Ancient Bitcoin (BTC) Whales Reawakening: Details - U.Today
-
 @ 2ecde0a6:10022dcb
2024-05-25 20:28:41
@ 2ecde0a6:10022dcb
2024-05-25 20:28:41Opinion about KeepKey (hardware)
KeepKey is a hardware wallet with a high level of security and supports more than 40 different crypto assets.
The device provides a PIN code and recovery seeds. It has a feature where it switches your PIN code numbers from time to time, making it impossible for malware to copy our code. Also, the device has a system for trade where you have to press and hold to confirm the transaction to avoid external hacks.
KeepKey has only one button to manage it. This button is used for turning the device on and off. All the other processes can be managed through the mobile app. That includes entering your PIN code and setting up the recovery seed, which makes it very simple to use, unlike other complex wallets. The device has a wide screen that allows you to see the entire cryptocurrency address without the need to scroll back and forth. But it's easy to break or scratch if you don't have a protecting casing.
Its price is around $80.
But you have to remember that the device is a little big and heavy, compared to other hard wallets, so it's difficult to carry around with it.
WalletScrutiny #nostrOpinion
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ 6a39a186:88f51c19
2024-05-25 20:21:18
@ 6a39a186:88f51c19
2024-05-25 20:21:18My Thoughts on Tails as a Non-Developer
Official Documentation and Resources
1. Official Website
- Tails Home Page: tails.boum.org
2. Getting Started
- Download Tails OS: Download Page
- Installation Instructions: Detailed instructions for creating a bootable USB stick or DVD can be found on the Install Page.
3. User Documentation
- Getting Started Guide: Getting Started with Tails
- Overview of Tails OS Features: What's Inside Tails
- Persistence Storage Setup: Configure Persistent Storage
- Verifying Downloads: Verify Your Download
4. Security and Privacy
- Security Precautions: Security Precautions
- Privacy and Anonymity Features: Privacy in Tails
- Amnesic Features: Amnesia in Tails
5. Applications and Tools
- Exchanging Monero Exchanging Monero with Feather
- Using Tor: Using Tor with Tails
- Email with Thunderbird: Secure Email Configuration
- Password Management with KeePassX: Using KeePassX
- Cryptographic Tools: Encrypt Files and Emails
6. Troubleshooting and Support
- Frequently Asked Questions: Tails FAQ
- Troubleshooting Guide: Troubleshooting
- Known Issues: Known Issues
Community Support and Contributions
1. Community Forums and Mailing Lists
- Tails Support Mailing List: tails-support@boum.org
- Public Discussion Mailing List: tails-project@boum.org
2. Bug Reports and Feature Requests
- Bug Tracker: Tails Bug Tracker
- Feature Requests: Users can propose features or improvements through the bug tracker or mailing lists.
3. Social Media and Community Interaction
- Twitter: @Tails_live
- Reddit: r/Tails
Educational and Additional Resources
1. External Guides and Tutorials
- Privacy Guides: Resources like PrivacyTools.io often have guides related to using Tails and other privacy-focused software.
2. Books and Articles
- Books on Digital Security and Privacy: Consider reading books like "The Art of Invisibility" by Kevin Mitnick and "Cybersecurity and Cyberwar: What Everyone Needs to Know" by P.W. Singer and Allan Friedman for more context on why tools like Tails are essential.
-
 @ c73818cc:ccd5c890
2024-05-25 19:31:27
@ c73818cc:ccd5c890
2024-05-25 19:31:27
🌟 Microsoft entra nel gioco dell'intelligenza artificiale con Copilot+, un PC con funzionalità AI che "ricorda" tutto ciò che fai. Un'innovazione interessante che potrebbe rivoluzionare il modo di lavorare. Tuttavia, l'integrazione profonda dell'AI solleva preoccupazioni sulla privacy e sulla potenziale sorveglianza, soprattutto prendendo atto di chi sta dietro all'azienda.
🌟 La capacità di Copilot di registrare e analizzare ogni attività sullo schermo apre scenari di personalizzazione e ottimizzazione del lavoro senza precedenti. Tuttavia, è fondamentale garantire che la raccolta e l'utilizzo di questi dati avvengano in modo trasparente e responsabile, tutelando la privacy degli utenti.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Le iscrizioni al torneo KCGI Bitget sono aperte, unisciti alla nostra squadra e corriamo verso i 5mln di dollari! https://www.bitgetapp.com/it/events/kcgi/futures-trading?clacCode=HCDS4WT4
BitcoinReportItalia #Microsoft #Copilot #AI #PC #Privacy #Censura #sorveglianza #Crypto #BTC #Bitcoin
-
 @ ec965405:63996966
2024-02-15 01:06:05
@ ec965405:63996966
2024-02-15 01:06:05I am beginning to see the clarity that my mentors promised I would as I progressed through my late 20s into my 30s, and it's getting clearer every day. I am inspired to change the world and bring my community with me. I know God has my back. A better world is within our grasp! I'm going to do my part in bringing my community with me by blogging about my upcoming trip to Cuba with Solidarity Collective via Nostr.
In February I'll be back in the skies headed to Havana, where I will participate in a delegation with Solidarity Collective to learn about Pan Africanism in the Cuban context. Some questions we will be exploring during this delegation are:
How do Cubans, in a Black-majority country, approach environmental protection, religion, housing rights, and healthcare?
What is the role of historic and contemporary abolitionist practices in their quest to eradicate racism?
What challenges remain to build an equitable society, especially under the yoke of 60 years of the u.s. Blockade?
What do these lessons mean for the struggle for black liberation in the u.s.?

I've dreamed about the next time I would visit Cuba and how I would track down the friends I made there in 2017. At that time, the government controlled access to internet via these cards that you would purchase then redeem on your device for timed access. The idea was that you would take your Wi-Fi card and head to a communal place like La Plaza with your device to access the Internet with others.
While some north americans might find that kind of Internet access draconian, surfing the web in public like that made me value my time on the Internet more. Has this changed since I was last there? I am personally interested in how groups are leveraging tech and the Internet for education and organizing. I now have a solid couple of years of IT/programming education to reference while I meet with teachers and journalists at the Martin Luther King Jr. Center and hear about the right to free education from daycare through university and literacy campaigns. I wonder if they've heard about decentralized social media protocols like Nostr or Activitypub or if they ever experienced censorship from the authorities on the Internet.
I recently experienced censorship in the YouTube comments as I explained to fellow web surfers why we must include Vieques and the other islands in the archipelago when talking about Puerto Rico politically. My ability to comment was restricted as I tried to convince others who talked down on Haiti and Cuba as failed states to instead take my Pan Caribbean perspective. I really enjoyed Dread's talk at Nostrasia 2023 about how he is using Bitcoin and Nostr to bring the islands together as the US Dollar and financial institutions like Western Union and the IMF keep us divided and oppressed.
The more I learn about Bitcoin as a tool for global wealth distribution, the more I understand how these institutions rob youth and families of basic necessities and facilitate the rise of authoritarian regimes and systems that punish journalists and activists through political repression. The corporate ownership of our means of internet communication by the likes of technocrats like Musk and Zuckerberg won't let authentic conversation between Caribbean-based diaspora happen on their platforms while they get to destroy countries like Myanmar and shape public discourse to their whim. That's why I'm glad I found Nostr.
My personal blog currently lives on my Uberspace asteroid in a Bludit instance that lacks much functionality outside of themes and data analytics, so it's just sits there as a personal repo for my thoughts. Nostr provides all of this with a direct link to my Bitcoin wallet address and comment functionality. If people value my content, I can get "zapped" and earn money for my content. I can now engage with my audience directly without a middle man. No Substack, no moderators censoring my messages, just community. The job now is to bridge my community and this new way of socializing on the Internet.
To help make this as educational of an experience as possible, I ask my audience: What questions or feedback do you have about my trip and the types of questions I want to explore? Is there anything you've ever wondered about Cuba? What suggestions do you have in terms of how I can better present information; written word, audio interviews, video, or photo essays?
Leave me some love in the comments and stay tuned!

-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ 9911f8d9:86db6c34
2024-05-25 19:24:44
@ 9911f8d9:86db6c34
2024-05-25 19:24:44Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 15 min
Ingredients
- 2 eggs
- 1 egg yolk
- 175 g white caster sugar
- zest of ½ orange
- ¼ tsp salt
- 250 grams of whole wheat flour
- 1 tsp baking soda
- 100 ml milk
Directions
- Put the eggs, egg yolk, white caster sugar, orange zest and salt in a bowl and beat this with a (hand) mixer with whisk(s) until a very airy batter. This will take at least 5 minutes.
- Mix the flour with the baking soda and sieve this over the bowl with the airy egg mass.
- Gently fold in the flour.
- Fold the milk into the batter and let it rest for 10 minutes in the refrigerator.
- Preheat the oven to 200°C and line a baking tray with baking paper.
- Using a large ice cream scoop or spoon, form 5 mounds of batter per baking tray.
- Make sure you leave enough space between the mounds of batter, because the cakes will still rise quite a bit in the oven.
- Bake the egg cakes for 7-12 minutes until light brown and done
-
 @ 7f4f672a:c184579e
2024-05-25 18:49:29
@ 7f4f672a:c184579e
2024-05-25 18:49:29There is a constituency of people completely unrepresented & unspoken for in Ireland today. Their existence is tenuous and fraught with uncertainty. They live on the edges, and garner little attention. They cannot sound their voices, raise their hands, or cast a vote. Few know about them, let alone give them more than a seconds thought. And yet, there is a community coalescing in Ireland who want to not only acknowledge them, but be their champions.
In recent years, technology has being painted in a bad light. Look to any mainstream media outlet and, after wading through the typical narratives of doom and gloom, find an article related to "Big Tech", burgeoning technologies like space-exploration and artificial intelligence (AI), or stagnant one's like nuclear energy. Invariably the tone will be cynical, the outlook bleak, and the fear levels? High. Undertones of fear based on ecological or climate change will invariably be deployed to argue why this or that technology must be regulated, reduced, or even stopped.
Many do not agree. Effective Accelerationism or "e/acc" has come about as a kind of rebuttal and refutation to the "Doomers" - as it's community like to call the detractors of everything from fusion energy to genetic modification. The movement was kindled by a quantum computing technologist, applied mathematician, and physicist - Guillaume Verdon, under the pseudonym "BasedBeffJezos" - a play on the name of tech billionaire Jeff Bezos and the online slang term based - a word used when you agree with something, or when you want to recognise someones genuineness and courage. Verdon found himself doxxed in the final weeks of 2023 - outed by a mainstream journalist ironically using voice-recognition software to publicly expose his identity without consent.
In a world where we are fed a constant stream of reasons to be hopeless, e/acc is a reason to be hopeful in this very moment. - Guillaume Verdon
Themes of growth and innovation, attitudes of optimism about the future, and pride in humanities' achievements permeate the community. Followers believe technology, growth, and indeed humans themselves are all good things - contrary to their polar opposites, the anarcho-primitivists, who advocate for de-growth, de-industrialisation, ending capitalism, and generally, a romantic return to the Stone Age. E/acc's ideology is clear; humans must harness more and more energy; explore space and colonise it; grow our population; and create artificial intelligence - all as soon as possible. Their motto, "Accelerate or Die" - suggests they have neither a proclivity for patience nor half-measures.
Éire Accelerationism a.k.a é/acc
É/acc is the Irish flavour of this international movement : Éire Accelerationism. Coined and founded by Irishman, Will O'Brien, the group has gained a following off all-sorts who have one belief in common - Ireland can do a lot better, needs higher ambition & radical new ideas, and must execute them quickly to succeed and prosper in the coming two centuries. The Irish group's views on AI are more varied and perhaps less radical than their North American counterparts, and it's clear that their main focus is on the danger of low ambition for Ireland. Just as previous generations broke consensus ideas about corporation tax, an innovation which brought magnificent wealth to the state and it's people, we must do similar, in a multitude of ways. At the groups first get-together hosted by Dogpatch Labs in early May, everything from housing policy to flying cars were on the table.
O'Brien sees é/acc as an idea machine, a concept described by Nadia Asparouhova in her eponymous blog post, as a "self-sustaining organism that contains all the parts needed to turn ideas into outcomes". The community forms around a distinct ideology and members start spit-balling ideas between themselves. After some time, the group agrees upon an agenda, which defines exactly how the idea will be brought to life. Funders then assume the crucial role of giving capital ; financial, skills, connections, expertise, to transform the idea into reality.
Feck The Begrudgers
It could be argued that é/acc has, at least partly, been formed as a two-fingers to the age-old Irish phenomenon of the "begrudgers" ; those who resent and criticise others who are successful, known elsewhere as "Tall Poppy Syndrome". Indeed, O'Brien mentioned this in a recent interview he gave. Many people in Ireland, particularly the young, keep their heads down, do not share their dreams or successes publicly, and shrink their ambitions - all classic signs that they are victims of begrudgery. This endemic mind-virus, rife in Ireland, needs to be purged and thankfully many people like O'Brien are highlighting it's limiting, toxic, and pervasive nature. For this alone, é/acc is a breath of fresh air, offering an antidote to a dreary self-limiting mindset.
A Bright Future
It will be interesting to see what's next for the movement. Eventually, it will need to organise politically in order to get some things done, and that may be it's first opportunity in change-making. In an Irish political landscape plagued by unaccountable career politicians failing upwards and right to the top, nepo-politicians (see nepo-babies), revolving doors, and widespread incompetence, the movement's founding innovation could be to design a political party and environment where such issues cannot take root, much less thrive and deteriorate, as has been the case within the established civil war parties in Ireland.
It's early days and it is unclear how exactly é/acc will execute its ideas, but the atmosphere is optimistic and filled with both determination and enthusiasm.
The constituency é/acc represents? The grandparents in rural Mayo who see their grand-children living on the opposite side of the country every other evening - possible only as they fly for 15 minutes in their EitilCarr © (the world-leading Irish flying-car manufacturer). The 135-year-old triathlete looking forward to her next race - thanks to the incredible modern medicine discovered and implemented in Ireland. The couple who just bought a beautiful 3-bed home that cost only a quarter of their annual income - thanks to the innovations in construction, planning, NIMBY pacification, and design of housing in Ireland.
If our future descendants could reach back to us now, what would they ask us to do? É/acc is wondering the same thing.
References / Resources
What the f--k is eacc https://effectiveaccelerationism.substack.com/p/what-the-f-is-eacc
Idea machines https://nadia.xyz/idea-machines
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ c73818cc:ccd5c890
2024-05-25 15:09:50
@ c73818cc:ccd5c890
2024-05-25 15:09:50
🌟 In un contesto di crescente pressione normativa, il Bitcoin Policy Institute (BPI) ha annunciato il lancio del Peer-to-Peer Rights Fund, un'iniziativa strategica per salvaguardare la natura decentralizzata e peer-to-peer dell'ecosistema Bitcoin. Il nuovo fondo, volto a contrastare le minacce regolatorie, nasce per difendere Keonne Rodriguez e William Lonergan Hill, fondatori di Samurai Wallet, accusati di riciclaggio di denaro e operazioni finanziarie senza licenza.
L'iniziativa del BPI si inserisce in un panorama in cui la centralizzazione rappresenta un ostacolo alla vera adozione di Bitcoin. La difesa degli strumenti non custodial è quindi cruciale per garantire agli utenti il controllo sui propri fondi e promuovere un ecosistema Bitcoin più resiliente e democratico.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Le iscrizioni al torneo KCGI Bitget sono aperte, unisciti alla nostra squadra e corriamo verso i 5mln di dollari! https://www.bitgetapp.com/it/events/kcgi/futures-trading?clacCode=HCDS4WT4
BitcoinReportItalia #Samourai #Wallet #BitcoinPolicyInstitute #RightsFund #Privacy #Censura #BPI #Crypto #BTC #Bitcoin
-
 @ d360efec:14907b5f
2024-05-25 14:35:40
@ d360efec:14907b5f
2024-05-25 14:35:40ที่ค้นพบที่แหล่งโบราณคดีผิงเหลียงไถในที่ราบภาคกลางของจีน
ด้วยการใช้วิศวกรรมขั้นสูงและการวางผังเมือง ผู้คนยุคหินใหม่เหล่านี้จัดการการไหลของน้ำได้อย่างมีประสิทธิภาพและป้องกันน้ำท่วมในการตั้งถิ่นฐานโบราณ
แต่จีนยุคนี้ไม่จัดเป็นยุคหินใหม่หรอกนะคะ

-
 @ d1e60465:c5dee193
2023-11-24 14:01:31
@ d1e60465:c5dee193
2023-11-24 14:01:31Todos los que hemos utilizado Bitcoin alguna vez sabemos lo básico sobre una wallet y de la importancia de la frase de recupero (las 12 o 24 palabras). Esa frase de recupero es única para toda la wallet. También somos conscientes de que las direcciones no deben ser reutilizadas para proteger nuestra privacidad, entonces nuestra wallet genera virtualmente infinitas direcciones. Ahora bien, ¿cómo es eso posible teniendo sólo una única frase de recupero? ¿Acaso hay algo más, además de dicha frase, que determina dónde están nuestros bitcoins?
Aquí es donde entran las wallets HD (hierarchical deterministic = jerárquicas determinísticas) y los “derivation paths” (caminos de derivación). Dicho esto, no hay mejor momento que este para tomar nuestra pala e irnos a enterrar riquezas.
Enterrando nuestra riqueza
Supongamos que tenés un tesoro que querés resguardar y se te ocurre la genial idea de enterrarlo (lo hacían los piratas, por qué vos no?). Lo primero que hacés es buscar un terreno muy MUY grande, elegís una ubicación lo más aleatoria posible, tomás la pala, cavás el pozo, y enterrás el tesoro. Por último, y muy importante, te anotás las coordenadas de dicha ubicación (llave privada) para volver luego por tu riqueza cuando la necesites.
Supongamos ahora que pasa el tiempo y seguís generando riquezas que querés proteger. Siguiendo tu idea original volvés al mismo terreno a cavar mas pozos, enterrar más tesoros y anotar más coordenadas. Si esto se repite varias veces más llegará un momento en el que guardar tantas coordenadas resultará incómodo para llevar un correcto registro, y riesgoso ya que si perdés una de ellas perdés un tesoro.
Con la pala en mano, sentado sobre un pozo, y mirando el horizonte se te ocurre una genial idea. Podrías sólo anotar la coordenada de un único punto arbitrario y diferente a los demás dentro de ese terreno (llave privada maestra), en donde no vas a enterrar nada. Pero hacés que todos los pozos, donde sí enterrarás tesoros, se ubiquen de forma relativa al punto inicial de una manera específica (camino de derivación). De esta forma llegarías a cualquier pozo partiendo de esa ubicación original. Por ejemplo: “los tesoros estarán ubicados en intervalos de 10 pasos hacia el norte desde el punto origen”. Incluso podrías definir ciertos recorridos fijos y complejos dependiendo el tesoro. Por ejemplo: “caminando hacia el norte, cada 10 pasos, pozos con oro; caminando hacia el este, cada 5 pasos, joyas; y para regalos misceláneos irás con intervalos de 4 pasos al oeste, pero cada vez que caves caminarás 2 más al sur (es decir, como si formases una letra L)”.
Todo este mecanismo parece complejo a primera vista, pero tiene una ventaja fundamental y es que los recorridos no tienen que guardarse de manera secreta ya que sin la coordenada origen nadie podrá encontrar el tesoro. Gracias a esta particularidad podríamos definir patrones de recorrido que sean públicos y todos compartamos, e incluso convertirlos en un estándar global (BIP44 o BIP86). En otras palabras, los caminos para llegar a cada pozo serán de público conocimiento y podrán estar anotados en múltiples lugares, mientras que las coordenadas de partida serán secretas de cada individuo.
Para repasar, tenemos presente que para encontrar el tesoro necesitamos la coordenada original y el recorrido de pasos. Física y visualmente podríamos pensarlo como una hoja transparente donde están dibujados los recorridos, y otra hoja con un mapa (secreto) que marque el punto origen. Ambos superpuestos darán la información necesaria (wallet HD) para encontrar todos los tesoros enterrados. Ambos son necesarios, pero sólo uno de ellos necesita ser secreto.
Cambiando la pala por criptografía
En Bitcoin, esta idea de tener una llave privada maestra (el punto de origen) y luego diferentes caminos de derivación fue introducida en el BIP 32. Explicado en términos (muy) simples podemos partir de que nuestra llave privada maestra no es más que un número, y lo que hace este mecanismo es realizar operaciones matemáticas sobre ese número para obtener nuevos números: las llaves hijas.
En la práctica, una situación habitual que genera pánico en aquellas personas que comienzan en Bitcoin se da cuando restauran una wallet utilizando la frase de recupero y la wallet no muestra su balance. El terror de ver “0 BTC” en lugar de sus ahorros detiene el tiempo durante unos segundos. Sin embargo, un poco más de atención sobre la situación revelaría que no sólo se muestra un balance en 0, sino que tampoco se muestra ninguna de las transacciones realizadas previamente. Es decir, es como si estuviésemos mirando otra wallet. Lo que sucede en estos casos es que, si bien la frase de recupero y por ende la llave privada maestra (coordenada original) se restauró correctamente, la wallet en cuestión utiliza otro derivation path, otro camino. Entonces, por más que partimos desde el mismo punto a caminar, estamos caminando para el lugar equivocado para encontrar el tesoro. Esto se debe a que, si bien existen estándares de derivation paths, no todas las wallets los respetan al 100%. Esta web detalla los diferentes caminos utilizadas por cada una de las diferentes wallets conocidas que existen en el mercado, y así evitar situaciones desagradables: https://walletsrecovery.org
Existen más particularidades no cubiertas por la analogía, como que en este esquema también se hace presente una llave pública maestra que puede tener derivaciones y así generar múltiples direcciones (y monitorearlas) pero sin tener acceso a las llaves privadas de cada una para mover los fondos asociados. Aparece también el concepto de “hardened” (fortalecido o endurecido), que hace referencia a sub-llaves derivadas de las principales ajustando el algoritmo para evitar filtración de datos sensibles y que un atacante pueda reconstruir nuestra llave privada maestra. Todos estos detalles están explicados en el BIP para quien le interese.
Epílogo
En Bitcoin, una llave privada maestra sería el equivalente a elegir una coordenada origen cualquiera en todo el planeta (incluyendo agua)… de entre más de 900000000000000000000000000000000000000000000000000000000000000 planetas Tierra. Podemos estar tranquilos que la coordenada que elijamos seguramente no sea elegida por otra persona.
Links útiles
- https://walletsrecovery.org Wallets Recovery — Derivation paths por wallet
- https://github.com/bitcoin/bips/blob/master/bip-0032.mediawiki BIP32 — “Hierarchical Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0044.mediawiki BIP44 — “Multi-Account Hierarchy for Deterministic Wallets”
- https://github.com/bitcoin/bips/blob/master/bip-0086.mediawiki BIP86 — “Key Derivation for Single Key P2TR Outputs”
Este artículo está inspirado en un hilo de Twitter que hice en 2021: https://twitter.com/diegogurpegui/status/1408931266616041475
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ 3bf0c63f:aefa459d
2023-11-08 15:06:55
@ 3bf0c63f:aefa459d
2023-11-08 15:06:55I think it's undeniable at this point that the creation of Lightning Address has made the usage of custodial Lightning solutions increase -- or at least be more prominent. We see these stats everywhere of how many of Nostr Lightning Addresses are custodial, and how services like Nodeless and Geyser only work if you give them a Lightning Address, and that probably sounds like a lament to many people who thought Lightning would be this amazing network of self-hosted nodes that everybody runs, and is indeed sad.
Well, on the other hand the Lightning Address flow is clearly an improvement -- to most people -- over the cumbersome invoice flow. Since the early days of Lightning people had been complaining about the fact that there is no way to "just send money to an address". Even though I personally liked the invoice flow much more (especially if they had structured, signatures, clear descriptions and amounts, payment proofs and so on) the fact is that most people didn't and slowly invoices were losing their meaning entirely anyway.
This improvement in the payment flow, along with the open, easy and interoperable way that Lightning Addresses work, has opened space for new use cases that maybe wouldn't have existed otherwise -- like the services mentioned above, and others. So we can't really say this was all a bad thing.
We also shouldn't say it was a bad thing to have Lightning Addresses being invented at all, because if they hadn't been invented like they were, there is a high probably they would have been invented in other forms, probably much worse, that would involve private deals and proprietary integrations with ad-hoc APIs, SDKs and JavaScript widget buttons with iframes. I even remember some of these things starting to happen at the time Lightning Address was created, and we have more evidence of these things even after Lightning Address, like some "partnerships" here and there and the "UMA" protocol. So maybe Lightning Address was just the best possible protocol at the best time, and all its problems are not really its problems, but symptons of the problems of the Lightning Network (or maybe you wouldn't call these "problems", just natural properties, but doesn't matter).
The saddest realization of all this process, for me, was that Lightning payments are mostly used for tipping and not for commerce as I thought they would in the beginning (hence my love for the invoice flow). Specifically, LNURL-pay and its cool hidden features that went mostly unsupported, were all designed with the goal of enabling new use cases for commerce in the real life, outside the web, and Lightning Addresses would have tied nicely into that vision too -- but that was all definitely an irredeemable failure.
I thought I had more things to say about this, but either I didn't or I forgot. The end.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The problem with ION
ION is a DID method based on a thing called "Sidetree".
I can't say for sure what is the problem with ION, because I don't understand the design, even though I have read all I could and asked everybody I knew. All available information only touches on the high-level aspects of it (and of course its amazing wonders) and no one has ever bothered to explain the details. I've also asked the main designer of the protocol, Daniel Buchner, but he may have thought I was trolling him on Twitter and refused to answer, instead pointing me to an incomplete spec on the Decentralized Identity Foundation website that I had already read before. I even tried to join the DIF as a member so I could join their closed community calls and hear what they say, maybe eventually ask a question, so I could understand it, but my entrance was ignored, then after many months and a nudge from another member I was told I had to do a KYC process to be admitted, which I refused.
One thing I know is:
- ION is supposed to provide a way to rotate keys seamlessly and automatically without losing the main identity (and the ION proponents also claim there are no "master" keys because these can also be rotated).
- ION is also not a blockchain, i.e. it doesn't have a deterministic consensus mechanism and it is decentralized, i.e. anyone can publish data to it, doesn't have to be a single central server, there may be holes in the available data and the protocol doesn't treat that as a problem.
- From all we know about years of attempts to scale Bitcoins and develop offchain protocols it is clear that you can't solve the double-spend problem without a central authority or a kind of blockchain (i.e. a decentralized system with deterministic consensus).
- Rotating keys also suffer from the double-spend problem: whenever you rotate a key it is as if it was "spent", you aren't supposed to be able to use it again.
The logic conclusion of the 4 assumptions above is that ION is flawed: it can't provide the key rotation it says it can if it is not a blockchain.
See also
-
 @ f4bf1fb5:b428f8d5
2024-05-25 14:34:26
@ f4bf1fb5:b428f8d5
2024-05-25 14:34:26A modder that goes by the name of "Xcava86X" created a mod for Starfield on PC called "No Pronouns", one that removes pronoun selection from the character creation section of the game.
The mod was uploaded to one of the popular mod hosting sites at the time, however, staff of said site has removed the mod and banned its creator.
This is an old piece of news as of the time of writing this post, and the purpose of writing it is to remind people of what's being banned, as well as keeping a log for ourselves, to know which mod creator to reach out to in the future, to introduce them to DEG Mods.
Since DEG Mods isn't out yet and you're wondering where you can download it, someone has supposedly uploaded the file on Basedmods (be safe!).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28rosetta.alhur.es
A service that grabs code samples from two chosen languages on RosettaCode and displays them side-by-side.
The code-fetching is done in real time and snippet-by-snippet (there is also a prefetch of which snippets are available in each language, so we only compare apples to apples).
This was my first Golang web application if I remember correctly.
-
 @ d49a9023:990fa8df
2024-05-25 14:26:43
@ d49a9023:990fa8df
2024-05-25 14:26:43Recently, Apple released iOS 17.5. Almost immediately, people began taking to social media to discuss an oddity they began witnessing. Seemingly, "zombie" photos were resurfacing in people's recent albums gallery. Some photos were deleted many years ago. What the hell happened?
Apple would not immediately offer comment on the issue. Of course, that's to be expected as they wouldn't want to self-incriminate while they investigate. Fortunately, they released a hotfix with iOS 17.5.1 released a few days later.
However, Apple remained mum about what caused the issue and why photos people had deleted many years ago and from older devices started to resurface.
Apple confirmed to 9to5mac that iCloud Photos is not to be blamed for this. Instead, it all boils down to the corrupt database entry that existed on the device’s file system itself.
According to Apple, the photos that were not fully deleted from a user’s device were not synced to iCloud Photos. Those files were only on the device itself. However, the files could have persisted from one device to another when restoring from a backup, performing a device-to-device transfer, or restoring from an iCloud Backup but not using iCloud Photos.
This strange issue highlights at least two focal points regarding deleting photos on an iOS device. First, it emphasizes that Apple has, at some point, not seemed to delete photos (perhaps media as a whole?) in a secure method where it writes over them to make them irrecoverable.
Secondly, it's recommended that persistent device-to-device transfers from iCloud backups be avoided. Rather, new devices should be set up as exactly that—a new device. This will not only help rid the new device of bloat but also ensure that no previously deleted data fragments are transferred.
Apple further claims, that after a device has been completely erased using the steps below, all files and content are permanently deleted:
- Open “Settings”
- Choose “General”
- Choose “Transfer or Reset”
- Choose “Erase All Content and Settings”
Following these steps, apparently everything is permanently deleted from the user’s device and there is no chance of old photos resurfacing down the line.
-
 @ 2edbcea6:40558884
2023-11-05 18:23:21
@ 2edbcea6:40558884
2023-11-05 18:23:21Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Before we dive in I want to congratulate the winners of the NostrAsia hackathon: eNuts, Shopstr, Zappdit, and the runner up Nosskey. Thanks for hacking away and building for the community. 😊
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) Updates to NIP 72: Moderated Communities
As mentioned in previous weeks, moderated communities as currently outlined in NIP 72 publish kind 1 events (tweet-like text notes), and they show up without context in clients like Damus, Amethyst, Snort, etc.
One solution to the lack of context is to make activities in moderated communities use event kinds other than 1 so that you have to be in a client specialized for moderated communities to see those activities.
There have been a few attempts to update NIP 72 to accomplish that goal, and this is the latest iteration. Unique to this proposal is the idea of community scoped user data, not just posts. For example you could follow people within the community within the scope of the community but not add them to your general following list for your whole Nostr account. They’d show up in your feed in the moderated community but not in your general feed.
There’s a lot of potential in moderated communities to become a core pillar of Nostr usage as the network scales, especially since the censorship and API management regimes of Reddit have gotten more restrictive. People want better and Nostr can be that solution.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
2) (Proposed) NIP 49: Nostr Wallet Auth
Having a Lightning Wallet connected to Nostr is a powerful tool for content monetization and nostr-based marketplaces. There’s a lot of great work done on Nostr Wallet Connect, but it all “hinges on having the user copy-paste a wallet connection URI into the app they wish to connect with. This can be a UX hurdle and often has the user handling sensitive information that they may not understand.”
“This NIP proposes a new protocol that solves these problems by having the wallet and app generate a NWC connection URI together. This URI is then used to connect the wallet and app.”
Making it easier for new users (especially those that are less technical) to participate in the new economy is fundamental to making Nostr the best place for content creators to make a living without middlemen and heavy handed platforms. 💪
Author: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz
3) (Proposed) Updates to NIP 15: Nostr-based Marketplaces
This proposal expands the capabilities of Nostr-based Marketplaces to support auctions. Think about a Nostr-based eBay where users can post an item for sale by auction using a marketplace Nostr client.
The auction going live is a Nostr event, and users can publish bids as Nostr events, and when the auction is closed it’ll be determined by the bid event with the highest offering. Which anyone can verify. This is a very interesting way to make marketplaces more censorship resistant.
Author: ibz
Notable Projects
Yondar (social maps) 🌐
Much physical commerce is discovered by consumers via map apps. You go on Google or Apple Maps to find an art supply store near you, or coffee shops that are open at 2pm when you’re in a new city. These centralized solutions have dominated, but no more! Enter Yondar.
Yondar is a Nostr client that allows users to publish places on a map. This could be places of business or events, really anything that has a location.
True to Nostr form, people can also socially interact with these places: do a kind 1 comment in response to an upcoming event published on Yondar. Or someone could create a Nostr client for restaurant reviews and publish one of those in response to a place published via Yondar. The possibilities are endless 🤯.
Author(s): npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
WavLake 🎵
WavLake is a music player for web and mobile. It’s part Spotify music player and music discovery tool, part music monetization platform. They host the actual music files in their own cloud hosted system, but they publish Nostr events to represent the content that’s stored by WavLake, so other clients could help people discover music hosted and published via WavLake.
If musicians can get paid more for their music via solutions like WavLake, they will start using Nostr purely for selfish monetary reasons. This could be the start of purple-pilling that particular artistic community.
P.S. I listened to WavLake Radio while writing this, it was nice writing music.
Authors: based on the linked Github repo it’s nostr:npub1j0shgumvguvlsp38s49v4zm8algtt92cerkwyeagan9m6tnu256s2eg9a7 and blastshielddown
Opt-in content moderation on nos.social 👍👎
nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 gave a presentation at NostrAsia about making Nostr more accessible for normies. One of the items that was announced was the implementation of opt-in content moderation in his Nostr client nos.social.
They now support content warnings set by users publishing content, reporting content with various tags, as well as the ability for users to opt-in to moderation that changes their feed based on what they want to filter out.
People that don’t want moderation don’t need to use it, but I applaud nos.social’s work to develop these tools and patterns so that people have the choice to moderate their own feed.
Latest conversations: Interoperability
NostrAsia really highlighted the superpowers of Nostr and one of the foremost is interoperability. nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft gave a great talk about this topic and explained NIP 31 and NIP 89.
In summary, imagine there’s a Nostr client for movie reviews and they publish the review in a specific structure with Kind 12345678. Most Nostr clients will see that event but won’t know how to display that content or help users interact with it.
If clients adopt NIPs 31 and 89 then Nostr events will have an “alt” tag and a way to find a suggested app to handle that type of Nostr content. The alt tag helps clients display something to the user and the suggested app handler helps the client indicate to the user how to interact with that content more natively.
Maximum interoperability is useful in allowing Nostr to grow without centralizing. We can all experiment and build and all efforts still support the usage of the Nostr ecosystem in general.
Kind 1 clients as gateways to the Nostr app ecosystem
This interoperable future points to a framework where Kind 1 clients (Damus, Amethyst, Snort, Primal, etc) are the entrypoint or gateway to the Nostr ecosystem. Kind 1 clients are the core social use case and the foundation of most social interaction and could be amazing standalone apps and businesses, but Nostr makes them something more.
People will post Kind 1 notes referencing all kinds of Nostr events: music published via WavLake or Stemstr, places shared via Yondar, recipes created on Nostr.Cooking, etc. Clients will display some context on what the comment is on (music, place, video, recipe, etc) and then help the user find the right plugin/app/website to use to interact with that content natively.
This makes the Kind 1 clients the purple pill. This is only possible because of the unique interoperability capabilities of Nostr.
Interoperability with non-Nostr services
Even more amazing about Nostr is that it’s fairly easy to make the network interoperable with services outside the Nostr-verse. We already have pretty good bridges to ActivityPub-based systems like Mastadon as well as Twitter (with Exit). That reduces the switching cost for people that want to explore Nostr and eventually make the switch.
Even within Nostr-verse we have services like nostr.build that provide services in a way that doesn’t lock users in. Nostr.build provides file hosting services and because they follow NIP 96, there’s a standard way for clients to interact with nostr.build as a user’s preferred file storage provider for pictures and videos. It is easy for users to switch providers and clients can easily pick up the change. Efforts like NIP 96 makes file storage much more interoperable across the Nostr-verse without centralization.
Continuing to build solutions that allow users to have freedom AND a great experience will make Nostr the best game in town.
Don’t reinvent the wheel: use ISO when possible
I’m not sure if every developer knows this, but there’s an International Standards Organization (ISO) that has done a ton of work to promote standards of all kinds. The most common one developers have all used is the ISO datetime format. No matter what language or database you’re using, you’re likely representing timezone aware datetimes in the ISO format so that you can pass that data around safely.
ISO has codified standards for everything : how to store medical history, how to interact with USB, even stuff as obscure as how to represent data around holograms
Nostr is doing a lot of work to define structure to data that will be stored as Nostr events. We’re essentially inventing standards for social-related data of all kinds.
There are some things we’re building support for in Nostr, and I will encourage folks to see if there’s an ISO standard to follow first. It may save you a ton of time and brain power. On top of that, adopting ISO standards makes Nostr more compatible with future development that we can’t even imagine yet.
Invest in interoperability to support the cause
The Nostr-verse is under construction and the best time to plan for interoperability is before the building is done. Devs have done a great job retaining interoperability as a cambrian explosion of Nostr development has taken place. I hope we can continue to invest in interoperability because it may just be the thing that makes Nostr able to take on the giants of Big Tech when the time is right.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 46fcbe30:6bd8ce4d
2024-05-24 15:47:11
@ 46fcbe30:6bd8ce4d
2024-05-24 15:47:11With more than 6000 products listed, it's time to extract some numbers again.
The following are some findings in the data, followed by the full data.
Removed or defunct
Of all the 3381 products that are no more,
- 1600 had less than 1000 downloads at the time we first listed them
- 628 we did not get to review before they were removed or defunct
- 607 were custodial or did not even allow to send or receive BTC. That is 607 products that if you used them to store bitcoins, you would now not be able to do anything with those bitcoins.
- 18 had public source but we failed to build that source
- 13 we managed to build but not reproduce
- 2 were reproducible - namely Zap which was discontinued in favor of BitBanana and ABCore which was a very limited experiment from the start.
Obsolete or stale
Of all the 775 products that are not getting updates in years,
- 221 have less than 1000 downloads (and many of them are likely to disappear as shown above)
- 179 are custodial or "no send or receive". You definitely don't want to use these.
- 0 are reproducible
OK
Of the 2164 products that look well and alive
- 937 are custodial or "no send or receive"
- 143 are do-it-yourself projects (20), not yet actually released (41) or most likely never getting released (82)
- 306 are closed source
- 46 are not compilable (12) or the compiled app does not match the released app (34)
- 20 are reproducible
https://walletscrutiny.com/
-
 @ c11cf5f8:4928464d
2024-05-25 12:02:06
@ c11cf5f8:4928464d
2024-05-25 12:02:06Let's hear some of your latest Bitcoin trades, feel free to include links to your shops or sites you sold it from or the pic of the sold item.
If you missed our last thread, here are some of the items stackers recently spent their sats on the ~AGORA territory.
-
 @ 0403c86a:66d3a378
2024-05-24 13:17:19
@ 0403c86a:66d3a378
2024-05-24 13:17:19Lucas Paqueta, a midfielder for West Ham United, is facing explosive allegations of breaching betting rules, potentially putting his career in jeopardy. The Football Association has brought charges related to four Premier League games where Paqueta was booked each time.
The heart of the accusation is an alleged attempt by Paqueta to manipulate the betting market for personal financial gain or to benefit others. The midfielder, however, firmly denies these claims and is ready to fight to clear his name.
The FA's stance on such offenses typically starts with a lifetime ban. But the final decision will hinge on the investigation's outcome. Paqueta's situation is more complex than previous cases, with potential penalties far more severe.
Will Paqueta's career be forever tarnished, or can he clear his name and get back on the pitch? 🤔⚽️
-
 @ 005bc4de:ef11e1a2
2024-05-25 11:19:27
@ 005bc4de:ef11e1a2
2024-05-25 11:19:27Yesterday, May 24, 2024, the original Dogecoin dog died. That is, the dog in the image that inspired the Dogecoin meme coin died. Sad, I love dogs.
https://files.peakd.com/file/peakd-hive/crrdlx/Eo8X6j7LeyWAopQTPu98WwpD64MguQ2MjFhzcdyKfmFMphekGGs3oujFnu4jnQ51ZcR.jpg
Original doge image, source: https://en.wikipedia.org/wiki/Doge_(meme)
Sidenote: one of life's greatest injustices is that dogs typically live much shorter lives than humans. I'm not sure what God had in mind when those timespans were conceived, but I think it was to strengthen us.
2024 Doge dog death
Yesterday's doge death broke quickly. I first saw it here. But, it was everywhere and you likely saw it too:
https://files.peakd.com/file/peakd-hive/crrdlx/23xAvyTa5BtUJLHkimd3zHKxBuz9nH8TydbVeJwZtBG9MtZSHSXKTkDww859LRx2E8Nvc.png
And yet, the Doge's death yesterday immediately had me thinking, "Wait, I recall that pup died a year or two ago." I wrote and posted this showing my confusion:
https://files.peakd.com/file/peakd-hive/crrdlx/23w2FYLDtWe2DUNR7rszYS52JYLNrkkR3foW4QdiuZwEhZmgvQEX9R8osru4UxTWwYLFs.png
I did a super quick search...evidently, the dog had cancer in December of 2022 and articles such as this made the rounds.
https://files.peakd.com/file/peakd-hive/crrdlx/23wCbRrT9WrgndTPNPiowF4UMa4BtXiyLsqgz5Nx3oZXuvu9mJVTpcPA8gvfbASL9CFRc.png
I chalked it up as, "Well, there you go. The article was about the dog with leukemia, and I just assumed it had died." Bad and jumpy assumption...take this lesson to heart. I was wrong. Case closed.
2023 Doge dog death
Apparently, I was far from the only person who felt this déjà vu yesterday. This morning, one of the first things I saw was this:
https://files.peakd.com/file/peakd-hive/crrdlx/23tv4f9gGnM52HSqf7YmG8ZcZP4jmraWgHgVcyEwLMuDfnQS7sZGwrQ2jMjSJwz9Li17r.png
That article (https://www.independent.co.uk/life-style/cheems-balltze-shiba-inu-death-b2397060.html) spoke of the Doge dog dying back in 2023. This was a few months after the leukemia news broke. I had seen it news after all. "Okay, the pup hung on for several months. Good for pup. The doggo had a good life, brought a ton of joy to the world, was much loved." I thought.
And that was that. Until yesterday.
Revisiting the independent.co.uk article, looking more closely, and comparing it to yesterday's news, there are some immediate issues:
- The names - Is the dog "Cheems", "Balltze" or "Ball Ball" as in 2023, or "Kabosu" as was reported yesterday?
- The years - The independent article wrote of the meme rising in 2017...Dogecoin was long before that, 2013.
- The sex - The independent article (and apparent dog "owner") mention the dog as "he" but evidently Doge was a "she".
- Location - Cheems was in Hong Kong, Kabosu was in Japan.
https://files.peakd.com/file/peakd-hive/crrdlx/23vsEEFV5V1iwQmc6MebijBTUA6GZTttrnyowBT9jGnJSpPfm6ViJfwqkMZTC5fecSJcj.png
I'm currently thinking that this independent.co.uk article was just a case of shoddy journalism. It appears this was a case of two dogs, the Doge dog Kabosu and then another Shiba Inu Cheems Balltze. I think the author got them confused and morphed them into one in a case of gotta-get-this-thing-wrote by deadline and get out to the club for drinks mode, then turned out shoddy work.
To be fair, I searched a bit more. I narrowed the target dates to Dec. 1, 2022 to Dec. 31, 2023. Sure enough, it was reported then that the dog had died, Cheems, that is.
https://files.peakd.com/file/peakd-hive/crrdlx/23twABpCuYYUhPvogHqtW6GLGUbBfYNRGbivSafen1JcT5nv6HkXNqgtdidhBTRE3gUvK.png
Scrolling, there were lots of articles. They seemed to all say about the same thing: doge died, the inspiration for memes, much loved. Some, not all, of the articles allude to Dogecoin. Like this one and the independent.co.uk article flat out mentions Dogecoin.
https://files.peakd.com/file/peakd-hive/crrdlx/23tcP5UHDsFyiMWTH9xT2pfZXxLpBfgJC8wJ8c4YzBNZBifnmTV15CyFAkmDdPxdyK6Pc.gif
While scrolling, you might notice that last link. I noticed it. It read, "Anybody remember the Doge dog passing away near 2016 ..."
https://files.peakd.com/file/peakd-hive/crrdlx/EoH5BEGcVFB5zbKHsFe9TpqMeLxbjzXnvSeoQG8F5V9SE5jZv67ktSeQzRma5mmrXRa.png
Wait, yet another Doge death?
I dug deeper yet again. That Reddit post was apparently in response to an April Fools prank post. Oh, okay, the Doge doggo lives. For now.
Lesson of dying doges
I've spent too much time already on this. This story seems ultra-ripe to me for a real journalist to take up and dig into, uncover the clues, analyze, and decipher the mystery in a logical manner. Who's got this?
If there's a lesson in this, well, I don't really know what it is other than, be careful what you read and believe. 2016 death, 2023 death, 2024 death. More? There's something about this internet and social media culture, combined with the rash gotta-publish-now culture, that spawns inaccuracy, conjecture, connects dots that are not connected, feeds upon the beast that is itself, and gets things flat out wrong. And it's a little scary.
If I had a nickel to bet, it now would not surprise me at all if this Doge dog death pops up again somehow in a few more years, with yet another twist. The dog will be in her 30s and still dying.
The rabbit hole is deep and convoluted.
-
 @ 6389be64:ef439d32
2024-05-23 18:29:32
@ 6389be64:ef439d32
2024-05-23 18:29:32Clay's highly reactive surfaces provide scaffolding for the self-assembly of biomolecules and the eventual formation of living organisms.
The Jewish Golem legend holds every hallmark of this interaction. Jesus rubbed clay mixed with his spit to reverse blindness. What exactly did the ancients know about clay?
-
 @ 81870f53:29bef6a6
2024-05-25 08:31:17
@ 81870f53:29bef6a6
2024-05-25 08:31:17先週、利下げの可能性をめぐる楽観論から銀は11年ぶりの高値31.45ドルまで上昇し、金は週3%の上昇を記録した。今週の経済イベントは、連銀の講演、連銀の5月のFOMC議事録、失業保険申請件数が水曜日と木曜日にそれぞれ発表される予定だったことなどが目立った。
貴金属の勢いは月曜日も続き、金は史上最高値の2,449ドルを記録し、銀は11年ぶりの高値32.34ドル付近にとどまった。このペアの需要は、主に利下げ期待、地政学的緊張、中国の景気刺激策のニュースによって高まった。
月曜日はまちまちの取引となったが、メイシーズやロウズなどの大手小売業者の予想を上回る収益データを受けて、米国株は火曜日の取引をなんとかプラスで終えた。一方、金と銀は、連邦準備制度理事会のクリストファー・ウォーラー総裁が「労働市場が大幅に弱まっていない限り、金融政策の緩和を支持するには、あと数か月の良好なインフレデータが必要だ」と述べた後、ほとんど変化がなかった。
水曜日、S&P 500とナスダック総合指数は、それぞれ過去最高値の5,340.26と16,832.63から下落した。これは、FRBの発言と最近発表されたFRBの議事録が金利をめぐる「高水準が長期化」という見方を強めたためである。これと急上昇する国債利回りにより、金は水曜日に1.8%下落し、終値は2,372ドルとなった。これらの展開は銀にも重しとなり、灰色の金属である銀は水曜日の取引を3.8%下落して30.52ドルで終えた。
木曜日、投資家は前日に発表されたFRBの議事録で複数の当局者が必要に応じて金利を引き上げる用意があることが示されたタカ派的なコメントを引き続き消化した。このニュースはウォール街のムードを冷やし、ダウ平均株価は600ポイント以上下落し、今年最悪の1日の下落となった。
金は木曜日、利下げ悲観論とドル指数の急上昇により、3日連続で下落した。同日、S&Pグローバルは、米国の事業活動が5月に2年以上ぶりの高水準に加速したことを示すレポートを発表した。これは、今後数か月で商品価格が上昇する可能性があることを示唆している。その結果、金は木曜日に1.5%下落し、終値は2,337ドルとなった。
主要株式市場の平均株価は今日、週の下落の一部を縮小したが、ダウ工業株30種平均とS&P500はそれぞれ2.3%と0.1%下落して週末を終えた。一方、ナスダック総合指数は本日、過去最高値を更新し、週ベースで1.4%の上昇を記録した。
金は本日2,334ドル付近で推移し、最終的には週ベースで4.2%の下落で3週間続いた上昇を止めた。銀も利下げへの懸念と利益確定に苦しんだ。その結果、灰色の金属は週ベースで6.1%の下落となり、30.35ドルで週を終えた。
-
 @ 52387c6b:49dbdfb2
2024-05-23 02:03:38
@ 52387c6b:49dbdfb2
2024-05-23 02:03:38Chef's notes
Easy start to the day, can also put some Woostr in your Bloody Mary. Perfect for washing down the toast. Breakfast of champions. If you have some sharp cheddar you can melt this on the toast, altho this may prove too complex for the average bloke, just an option. Be mindful this will add significant prep and cook time. 2-3 minutes
Details
- ⏲️ Prep time: 30 sec
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 2 slices of bread
- Butter
- Woostr sauce
- Bloody Mary
Directions
- Toast bread to your liking, lather a dollop of butter on. Criss cross the toast with a butter knife ( so the woostr dont roll off) and then drizzle on woostr.
-
 @ 8947a945:9bfcf626
2023-10-23 08:13:39
@ 8947a945:9bfcf626
2023-10-23 08:13:39จงตระหนักรู้คุณค่าของตัวเอง เพชรไม่ได้เปล่งประกายเจิสจรัสจากสุดปลายถ้ำ

2023’s Wake up call
แรงบันดาลใจที่ทำให้ผมตัดสินใจเอาเรื่องนี้มาเล่าบน #ทุ่งม่วง เกิดจากเมื่อต้นปี 2023 ผมได้รับสัญญาณเตือนภัยจากที่ทำงานแห่งหนึ่ง (Wake up call) ปลุกให้ตื่นขึ้นจากภวังค์ ตระหนักรู้ถึงความเป็นจริงบางอย่าง ว่างาน part time ที่กำลังทำเริ่มมีสัญญาณความไม่มั่นคงเกิดขึ้นทีละเล็กทีละน้อย มีความสุ่มเสี่ยงที่จะถูกขอให้งดคลินิคไม่ต้องมาออกตรวจ (ภาษาสุภาพของการเลิกจ้างหมอ)
สำหรับหมอที่ทำงานหลายโรงพยาบาล จะเข้าใจสถานะ”หมอ part time” ของตนเองดีว่า สามารถถูกถอดเวรออกได้ทุกเมื่อ หากทางโรงพยาบาลมีความจำเป็น
เมื่อเกิดเหตุการณ์นี้ ผมติดต่อโรงพยาบาลใกล้บ้านเป็นแผนสำรองเอาไว้ ที่นี่ขาดอัตรากำลังแพทย์พอดี ผมเลยสามารถเริ่มงานได้ทันที ทำให้รายได้ไม่กระทบกระเทือนต่อครอบครัว แต่สิ่งที่ต้องพบเจอก็คือโรงพยาบาลแห่งใหม่นี้ งานหนักมาก หนักถึงขั้นกระอักเลือด เต็มไปด้วยความเสี่ยงที่ยังไม่มีระบบการบริหารจัดการที่มีประสิทธิภาพ ผมทำงานที่นี่ไประยะนึง เมื่อมาดูสลิปค่าตอบแทน พบว่าผมถูกจัดกลุ่มให้อยู่ในกลุ่มแพทย์เวชปฏิบัติทั่วไป (General practitioner หรือ GP คือหมอทั่วไปที่ยังไม่ได้เรียนต่อเฉพาะทาง)
แพทย์เฉพาะทาง ตามกลไกจะได้ค่าตอบแทนสูงกว่าแพทย์ GP ถึง 70 - 80%
ผมนำเรื่องนี้ขึ้นปรึกษาหน่วยงานที่เกี่ยวข้อง ได้รับการดำเนินแก้ไขอย่างเร่งด่วนเพราะความเข้าใจผิด และผมก็ได้ค่าตอบแทนสมน้ำสมเนื้อตามมาทีหลัง แต่ด้วยเนื้องานที่หนักมาก เหนื่อยมาก เลิกงานเที่ยงคืน วันอื่นๆทำงานอีก ทำงาน 7 วันต่อสัปดาห์ ร่างกายเริ่มส่งสัญญาณเตือนบางอย่างว่ากำลัง overheat เครื่องกำลังจะไหม้ในอีกไม่ช้า ถ้ายังคงลากเลือดขนาดนี้ แต่เวลานั้นผมทำเพื่อครอบครัวอย่างเดียว เลยไม่ได้ลังเล เดินหน้าต่อ
จุดเปลี่ยนมันอยู่ตรงนี้ครับ ผมมีอาจารย์แพทย์ที่เคารพมากท่านหนึ่ง อาจารย์เขารับรู้เรื่องผมมาตลอด เมื่อทราบว่าผมทำงานหักโหม แลกกับความเสี่ยงหลายมิติ จึงมีโอกาสได้นั่งคุยกัน อาจารย์ท่านนี้เล่าเรื่องสั้นเรื่องหนึ่งให้ฟัง และทิ้งท้ายเอาไว้ให้คิดว่า
ทรัพยากรที่มีค่าที่สุดคือเวลา จงเอาตัวผมไปอยู่ในที่ที่เห็นคุณค่าในตัวผมให้ได้ ถ้าผมทำได้ เวลาของผมมีจะสร้างมูลค่าได้มหาศาลกว่านี้
การสนทนาจบลงด้วยความรู้สึกพบแสงสว่างที่ปลายอุโมงค์ หลังจากนั้นไม่กี่สัปดาห์ผมตัดสินใจ ของดคลินิคจากโรงพยาบาลแห่งนั้นทันที และเป็นความโชคดี เพราะที่ทำงานประจำกำลังขาดแคลนหมอ ผมเลยได้ตารางออกตรวจเพิ่ม รายได้มั่นคงมากกว่าเดิม
ส่วนโรงพยาบาลที่กระตุ้น wake up call ผมตอนแรก เล็งเห็นความสำคัญของทักษะเฉพาะทางของผมที่ขาดไม่ได้และจำเป็นมากต่อสถานการณ์ปัจจุบัน จึงขอให้ผมอยู่ช่วยต่อและเพิ่มค่าตอบแทนเพิ่มจากเดิมอีกเกือบ 100%
ทักษะการเขียนบทความ ที่เกือบจะถูกปิดผนึกไปตลอดกาล เพราะเอาตัวเองไปอยู่ไม่ถูกที่
 สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทย
สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทยในช่วงแรกผมลองเขียนบทความลงเฟสบุค ผลลัพธ์เป็นไปตามคาดครับว่าไม่เป็นที่สนใจ ประเมินผลหยาบๆจากยอดกดไลค์ คอมเม้นท์ และการแชร์ เงียบเหมือนป่าช้าเลย นานๆจะมีคนมากดไลค์ซักที แต่ก็เป็นที่รู้ๆกันครับว่าการกดไลค์ มันอาจจะเกิดจากคนอื่นเปิดมาเจอโพสต์ของผม แล้วจะปัดให้มันพ้นๆไป “ไอ้บ้านี่มันบ่นอะไรของมัน” แต่นิ้วโป้งดันไปจิ้มโดนปุ่มไลค์พอดี ในเมื่อจิ้มไปโดนแล้วก็แล้วกันไปก็เป็นไปได้
เวลาผ่านไปมันเหมือนผมขึ้นไปพูดบนเวทีที่ไม่มีผู้ฟัง หรือ ผู้ฟังหลับทั้งห้อง บทความต่างๆข้อคิดต่างๆที่ผมตั้งใจเรียบเรียงมันส่งไปไม่ถึงผู้คน มันดูไร้ค่า จบด้วยการนั่งคุยกับตัวเองเหมือนเป็นคนไข้จิตเวช เหตุการณ์ทั้งหมดนี้เกือบนำพาผมไปสู่ข้อสรุปที่ว่า “ผมเองคงเขียนไม่เก่ง” หรือ “เขียนไม่ได้แย่หรอก แต่ไม่ได้โปรโมท เลยไม่มีใครมาพบเจอ” หรือไม่ก็ถูกทั้งสองข้อ บางครั้งอยากจะล้มเลิกการเขียนไปเลยก็มีครับ
ช่วงมกราคมปี 2023 เวบไซต์ Right shift เริ่มเป็นที่รู้จัก ฟังคอนเซปจากอาจารย์พิริยะแล้วชอบมาก
เวบไซต์ Right shift ตั้งใจเป็นแหล่งรวบรวมข้อมูลสำหรับผู้ที่สนใจอยากศึกษาบิตคอยน์ ให้สามารถเข้ามาศึกษาได้โดยไม่มีค่าใช้จ่าย แถมยังเชิญชวนให้ผู้ที่อยากเขียนบทความที่เป็นประโยชน์ให้แก่ผู้อื่น ใครสนใจสามารถส่งบทความเข้ามาได้ ถ้าหากบทความไหนมีแวว จะมีทีมบก.ติดต่อกลับไปเพื่อทำงานร่วมกันในการขัดเกล้า แก้ไขสำนวนบางจุดให้ดียิ่งขึ้น
พอรู้มาถึงตอนนี้มันนเหมือนมีอะไรมาเคาะกะโหลกดังๆ จนความรู้สึก “ปังปุริเย่ เฮ้ ร้องว้าว” มันผุดขึ้นมา แต่มันก็มาพร้อมกับความไม่มั่นใจในตัวเองนั่นแหละครับ ความขัดแย้งเต็มไปหมดว่า “จะเขียนหรือไม่เขียนดี” “เอาจริงอ่ะ? จะเขียนบทความส่งไปจริงๆเหรอ?” “ม_ึง ไม่ใช่นักเขียนมืออาชีพนะ คนที่เขาส่งบทความไปมีแต่เทพๆทั้งนั้น จะเอาอะไรไปสู้กับเขา” และเสียงอื่นๆในหัวอีกมากมาย
แต่สุดท้ายผมทลาย “Comfort zone” ได้ ด้วยกำลังใจเล็กๆน้อยๆจากภรรยาครับ ภรรยาผมบอกด้วยคำสั้นๆว่า “ก็ลองดูสิ สกิลการเขียนเล่าเรื่องของเธอก็ไม่ขี้เหร่นะ” ผมเลยลองทำดู และนี่คือสิ่งที่เกิดขึ้น
บอกได้ว่าเป็นครั้งแรกที่ผมได้ถูกฝึกการเขียนบทความโดย "ใครก็ไม่รู้” ผมรู้แค่ว่าเป็นทีมบก.ของ Right shift เมื่อทำงานร่วมกันไปเรื่อยๆ ทีมบก.ทุ่มเทในการช่วยแก้ไขช่วยตรวจสอบบทความของผมมากๆ จนผมสังเกตุเห็นได้
ใครเคยใช้ Google document ร่วมแก้ไขบทความด้วยกันมากกว่าหนึ่งคนคงจะรู้ดีนะครับว่า เวลาที่มีการแก้ไขข้อความมันจะมีเมล์แจ้งเตือนไปหาทุกคนที่เข้ามาร่วมแก้ไขเอกสารทั้งหมด บางคืนที่ผมนอนหลับไม่สนิท ตีสองตีสามตื่นมาเข้าห้องน้ำ ผมยังเห็นเมล์อัพเดทการแก้ไขบทความจากทีมงาน right shift เด้งๆอยู่เลย
จนสุดท้ายงานเขียนผมก็ได้รับการเผยแพร่บนเวบไซต์ Right shift

ใครยังไม่เคยอ่านกดตรงนี้ได้เลยครับ
หลังจากนั้นผมรับรู้ถึงทักษะนี้มากขึ้น เลยตั้งใจว่าต้องฝึกให้เก่งขึ้นดีขึ้นในทุกๆบทความที่ผมเขียน ผมอ่านหนังสือเยอะขึ้น ศึกษาสำนวนการเขียนจากนักเขียนรวมถึงนักแปลท่านอื่นๆ เพื่อดูตัวอย่างสำนวน ลีลาสไตล์การใช้คำ เอามาประยุกต์ใช้กับงานเขียนของตัวเอง
ไม่รู้ตัวหรอกครับ ว่าทักษะนี้มันโดนฝึก โดนขัดเกลาตั้งแต่เมื่อไหร่ แต่ตอนนี้ตระหนักรู้ถึงการที่มันมีตัวตนอยู่ภายในตัวผมแล้ว ผมก็จะลับคมมันไปเรื่อยๆ หลายครั้งตอนที่ผมเขียนบทความอยู่ผมลืมเวลา ลืมหิว ลืมง่วง ลืมเหนื่อยไปเลย ถ้าเปรียบเทียบกับนักกีฬา คาดว่าสภาวะตอนนั้นคงเป็นสภาวะหนึ่งของการเข้าสมาธิแบบ “Into the zone”
เรื่องสั้นที่อาจารย์ของผมเล่าให้ฟัง มอบบทเรียนชีวิตที่มีค่า อยู่ต่อจากนี้ครับ

พ่อคุยกับลูกสาว “ยินดีด้วยที่จบการศึกษา พ่อซื้อรถคันนี้ไว้ให้ลูกซักพักแล้ว ตอนนี้พ่อจะให้ลูกนะ แต่ก่อนที่พ่อจะให้ พ่ออยากให้ลูกนำไปที่ร้านรับซื้อ-ขายรถในตัวเมือง แล้วมาบอกพ่อด้วยว่าเขาให้ราคาเท่าไหร่”
ลูกสาวทำตาม กลับมาหาพ่อ บอกว่า “ร้านนี้เขาให้ราคา $10,000 เพราะรถเก่า” พ่อบอกลูกว่า “โอเคลูก ทีนี้พ่ออยากให้หนูเอารถไปที่โรงรับจำนำ ลองดูซิว่าเขาจะตีราคารถคันนี้เท่าไหร่”
ลูกสาวทำตาม แล้วกลับมาบอกพ่อว่า “โรงรับจำนำให้ราคา $1,000 เพราะรถเก่ามาก ดูแล้วต้องซ่อมอีกหลายรายการ ”
ครั้งนี้พ่อบอกลูกสาวให้นำรถนี้ไปยังชมรมคนรักรถที่มีผู้เชี่ยวชาญ และนำรถให้พวกเขาดู
ลูกสาวทำตาม ขับรถนี้ไปที่ชมรมที่ว่า หลังจากนั้นไม่นานลูกสาวกลับมาบอกพ่อด้วยน้ำเสียงตื่นเต้นว่า “บางคนเสนอราคา $100,000 เพราะเป็นรถหายาก และสภาพดีมาก”

ผู้เป็นพ่อยิ้มให้กับลูกสาว เหมือนว่ารู้อยู่แล้วว่าจะเกิดอะไรขึ้น ด้วยความสงสัยลูกสาวจึงถามพ่อว่า
“ในเมื่อพ่อรู้อยู่แล้วว่าร้านไหนจะให้ราคาสูง ทำไมพ่อไม่ให้หนูไปที่ชมรมคนรักรถตั้งแต่แรกล่ะ”
พ่อบอกลูกสาวว่า “นี่แหละบทเรียนชีวิตที่สำคัญบทหนึ่งที่พ่ออยากมอบให้แก่ลูก พ่ออยากให้ลูกรู้ไว้ว่า ลูกจะไม่มีค่าใดๆเลยถ้าอยู่ผิดที่ ที่ที่คนอื่นมองไม่เห็นเรา ไม่ต้องเสียเวลาไปโกรธโมโหไม่พอใจหรอกนะ สิ่งที่ลูกต้องทำก็คือเดินออกจากที่นั่น ออกไปจากสังคมและสถานที่ที่ไม่เห็นค่าในตัวลูก ค้นหาที่สถานที่ของลูกให้เจอ ถ้าลูกไม่ลองลงมือทำด้วยตัวเอง ลูกก็จะไม่ได้เรียนรู้อะไรเลย”

ข้อคิดที่อยากจะแบ่งปันกับทุกท่านที่อ่านมาจนจบ
บทความนี้มีความพิเศษกว่าบทความอื่นๆ ท้ายบทความของผมผมจะมาชวนคุยและสรุปข้อคิดที่เป็นประโยชน์ให้แก่เพื่อนๆพี่ๆทุกท่านที่อ่านมาจนจบ แต่สำหรับบทความนี้ข้อคิดที่ผมอยากให้ ถูกสรุปขมวดไว้ทั้งหมดแล้วในประโยคที่พ่อบอกลูกสาว
อย่าลืมต่อสู้ ฝ่าฟันอุปสรรค ค้นหาสถานที่ของตัวเราเองให้พบนะครับ เมื่อค้นพบทักษะในตัวแล้ว อย่าให้ถูกปิดผนึกไว้ เพียงเพราะอยู่ผิดที่ ลงมือฝึกฝนพัฒนามันไปเรื่อยๆ เราจะดีขึ้นในทุกๆวันครับ
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28lnurl-auth explained
You may have seen the lnurl-auth spec or heard about it, but might not know how it works or what is its relationship with other lnurl protocols. This document attempts to solve that.
Relationship between lnurl-auth and other lnurl protocols
First, what is the relationship of lnurl-auth with other lnurl protocols? The answer is none, except the fact that they all share the lnurl format for specifying
httpsURLs.In fact, lnurl-auth is very unique in the sense that it doesn't even need a Lightning wallet to work, it is a standalone authentication protocol that can work anywhere.
How does it work
Now, how does it work? The basic idea is that each wallet has a seed, which is a random value (you may think of the BIP39 seed words, for example). Usually from that seed different keys are derived, each of these yielding a Bitcoin address, and also from that same seed may come the keys used to generate and manage Lightning channels.
What lnurl-auth does is to generate a new key from that seed, and from that a new key for each service (identified by its domain) you try to authenticate with.

That way, you effectively have a new identity for each website. Two different services cannot associate your identities.
The flow goes like this: When you visit a website, the website presents you with a QR code containing a callback URL and a challenge. The challenge should be a random value.

When your wallet scans or opens that QR code it uses the domain in the callback URL plus the main lnurl-auth key to derive a key specific for that website, uses that key to sign the challenge and then sends both the public key specific for that for that website plus the signed challenge to the specified URL.

When the service receives the public key it checks it against the challenge signature and start a session for that user. The user is then identified only by its public key. If the service wants it can, of course, request more details from the user, associate it with an internal id or username, it is free to do anything. lnurl-auth's goals end here: no passwords, maximum possible privacy.
FAQ
-
What is the advantage of tying this to Bitcoin and Lightning?
One big advantage is that your wallet is already keeping track of one seed, it is already a precious thing. If you had to keep track of a separate auth seed it would be arguably worse, more difficult to bootstrap the protocol, and arguably one of the reasons similar protocols, past and present, weren't successful.
-
Just signing in to websites? What else is this good for?
No, it can be used for authenticating to installable apps and physical places, as long as there is a service running an HTTP server somewhere to read the signature sent from the wallet. But yes, signing in to websites is the main problem to solve here.
-
Phishing attack! Can a malicious website proxy the QR from a third website and show it to the user to it will steal the signature and be able to login on the third website?
No, because the wallet will only talk to the the callback URL, and it will either be controlled by the third website, so the malicious won't see anything; or it will have a different domain, so the wallet will derive a different key and frustrate the malicious website's plan.
-
I heard SQRL had that same idea and it went nowhere.
Indeed. SQRL in its first version was basically the same thing as lnurl-auth, with one big difference: it was vulnerable to phishing attacks (see above). That was basically the only criticism it got everywhere, so the protocol creators decided to solve that by introducing complexity to the protocol. While they were at it they decided to add more complexity for managing accounts and so many more crap that in the the spec which initially was a single page ended up becoming 136 pages of highly technical gibberish. Then all the initial network effect it had, libraries and apps were trashed and nowadays no one can do anything with it (but, see, there are still people who love the protocol writing in a 90's forum with no clue of anything besides their own Java).
-
We don't need this, we need WebAuthn!
WebAuthn is essentially the same thing as lnurl-auth, but instead of being simple it is complex, instead of being open and decentralized it is centralized in big corporations, and instead of relying on a key generated by your own device it requires an expensive hardware HSM you must buy and trust the manufacturer. If you like WebAuthn and you like Bitcoin you should like lnurl-auth much more.
-
What about BitID?
This is another one that is very similar to lnurl-auth, but without the anti-phishing prevention and extra privacy given by making one different key for each service.
-
What about LSAT?
It doesn't compete with lnurl-auth. LSAT, as far as I understand it, is for when you're buying individual resources from a server, not authenticating as a user. Of course, LSAT can be repurposed as a general authentication tool, but then it will lack features that lnurl-auth has, like the property of having keys generated independently by the user from a common seed and a standard way of passing authentication info from one medium to another (like signing in to a website at the desktop from the mobile phone, for example).
-
-
 @ a012dc82:6458a70d
2024-05-25 04:08:21
@ a012dc82:6458a70d
2024-05-25 04:08:21Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Psychologists who study evolution believe that the ability to "preserve riches" was the deciding factor in modern humans' evolutionary success. In his article "Shelling Out: The Origins of Money," Nick Szabo tells a fascinating tale about this. After the arrival of Homo sapiens to Europe around 35,000 B.C., they ousted the native Homo neanderthalensis population and caused a boom in the region's human inhabitants. Although homosapiens had the same volume of brain tissue as Neandertals, they also possessed weaker bones and less muscular body mass, making it hard to fathom why they were so successful in replacing their predecessors. Wealth transfers made easier or more achievable by collectibles may have been the most important factor. The evidence suggests that Homo sapiens enjoyed shell collecting, adorning themselves with shell jewellery, displaying their jewellery to others, and trading their shell collections.
Therefore, the ability to save money is crucial to the development of a civilised society. Throughout history, there have been numerous wealth preservation systems, each of which has evolved and adapted in accordance with the state of the art. The goal of any technology designed to preserve riches is the safekeeping of that wealth. Handmade jewellery is the most primitive style. In the following, I'll contrast bitcoin with the four most popular wealth preservation technologies of the present—gold, bonds, real estate, and stocks—to demonstrate why these options fall short and how bitcoin might streamline the process of saving and investing for the future. To that end, I'll be concentrating on exchange-traded funds (ETFs) as a type of long-term investment in the stock market.
What Characterizes a Good Store of Value?
As Vijay Bojapati explains, in a market where several value stores compete with one another, the factors that set one apart from the others are the ones that ultimately determine which one succeeds. To be a reliable savings mechanism, an asset must meet the following criteria: scarcity, longevity, portability, fungibility, divisibility, and divisability. Based on these characteristics, we choose which objects to use as money. Jewelry is an example of a scarce item that is not fungible because it is easily destroyed, cannot be divided, and cannot be exchanged for another.Gold excels in all of these regards. Gold has surpassed jewellery as the most popular technological innovation among humans over the last five thousand years.Yet digital disruption has hit hard ever since Bitcoin was released in 2009. Nearly every aspect of storing value can benefit from being digitised. Bitcoin is superior to gold in the digital era not simply as a store of value but also because it is essentially digital money.
Bitcoin vs. Gold
When it comes to durability, gold is without peer. The majority of the gold that has been extracted from the earth is still there. Bitcoins are decentralised ledgers of digital transactions. Therefore, the longevity of the institution that issues them is more important than the longevity of their physical form. Although there is no central bank issuing Bitcoin, the network that backs them up should ensure their longevity. It is too soon to tell how long it will last. Nevertheless, there are indications that the Bitcoin network has shown exceptional "anti-fragility" by continuing to function despite attacks and attempts at regulation from several nations over many years. It has a near-perfect uptime of 99.99%, making it one of the most reliable computer networks ever.
Bitcoin's portability exceeds that of gold since data can travel at the speed of light (thanks to telecommunication). Gold's allure has waned in the Internet age. Gold is not transferable via the web. There is currently no way to take your online gold with you. Our historically gold-based monetary system has been struggling due to the inability to digitise gold for decades. With the advent of electronic currency, it became increasingly difficult to ascertain whether or not individual national currencies were backed by gold. Gold's heavy nature also makes it challenging to move it across international boundaries, which complicates international trading. The current fiat-based monetary system exists because of the inflexibility of gold. Bitcoin solves this problem because it is a native digital scarce commodity that can be transferred easily.
GOLD STORAGE VS. BITCOIN STORAGE
Bitcoin's divisibility is superior to that of gold because it is entirely digital. In practically every way, information may be split and recombined for little or nothing (like numbers). The smallest possible fraction of a bitcoin is 100,000,000 satoshi. The gold, on the other hand, is tricky to fractionize. You'll need specialised equipment and run the risk of losing some gold (even if it's merely dust) in the process.
Gold is fungible; it can be marked with an engraving to identify it, but it can also be melted down and used interchangeably. Fiduciary integrity is "tricky" with bitcoin. Bitcoin is a type of digital information, which is the most easily measurable substance in the cosmos (like the written word). But because all bitcoin transactions are public record, governments can prohibit the use of bitcoin that has been used for criminal activity. which would have a detrimental effect on bitcoin's fungibility and its utility as a means of exchange because if bitcoin were no longer fungible, its value would fluctuate based on where it was kept. Bitcoin's ability to store value is unaffected by this, but its acceptance as currency may suffer as a result, thus lowering its value. While gold's fungibility is superior to that of bitcoins, the latter's portability makes gold useless as a means of exchange or digital store of value.
With an annual inflation rate of 1.5%, gold is becoming increasingly scarce. However, production is not limited in any way. Every so often, a fresh vein of gold will be uncovered, and who knows, maybe we'll even find some massive quantities out here in space. The price of gold is not totally elastic. Gold miners may become more productive when gold prices rise, leading to a larger supply. Furthermore, it is impossible to verify whether or not actual gold has been adulterated with less valuable metals. In addition, gold stored in digital wallets through ETCs or other goods sometimes serves more than one purpose, making it harder to regulate demand and driving the price down. Bitcoin, on the other hand, has a fixed quantity that will never increase above 21,000,000. By design, it will cause a deflation in the money supply.
At 1.75 percent per year, Bitcoin's inflation rate is low and falling. Every four years or so, the protocol code stipulates that bitcoin mining rewards will be cut in half. Its inflation rate will be practically nonexistent in ten years. In 2140, the final bitcoin will be mined. In the future, the Bitcoin inflation rate will be zero every year.
While auditability is not in and of itself a selling point for a store of value, it is nonetheless relevant since it reveals whether or not a store of value is appropriate for a just and transparent monetary system.
A tiny unit can clearly hear Bitcoin transactions. No one can say with any certainty how much gold or US dollars are in circulation. As Sam Abbassi pointed out to me, Bitcoin is the first totally public and globally auditable asset. The risk of rehypothecation, in which financial institutions use the collateral provided by their customers for their own benefit, is mitigated in this way. It eliminates a huge potential threat to the financial system. Banks and other financial institutions can now provide proof of reserves by revealing their bitcoin address or transaction history.
Bonds vs. Bitcoin
Among the earliest works on value investing and a classic of finance, Benjamin Graham's "The Intelligent Investor" was published in 1949 by the British-born American economist, professor, and investor Benjamin Graham. Because bonds, in his view, cushion investors against the volatility of the stock market, he advocates a "balanced portfolio" of 60% equities and 40% bonds.
However, I believe bonds, and especially government bonds, have lost their role as a hedge in a portfolio, even though much of what Graham stated back then still makes sense today. Our bond-based monetary system is in peril because bond yields are falling behind the rate of money inflation.
This is because many national governments, which are the backbone of our monetary and financial systems, are experiencing financial difficulties. The implied risk of default by a government was effectively zero when government balance sheets were in good shape. That's because of two factors. First, their taxing authority Second, and perhaps more importantly, they have the ability to print money to reduce their debt. While this was a valid point of view in the past, Greg Foss now explains that printing money has become a "credit boogie man."
It's true that there is more money in circulation than ever before, thanks to governments. A broad measure of the stock of dollars, known as M2, increased from $15.4 trillion at the beginning of 2020 to $21.18 trillion by the end of December 2021, according to data from the Federal Reserve, the central banking system of the United States. An additional $5.78 trillion, or 37.53 percent of the total dollar supply, has been created. As a result, the average annual inflation rate over the last three years for the value of the dollar has been above 10%. Less money is being made off of U.S. Treasury Bonds.
To compensate for risk and opportunity cost, one should theoretically be able to receive a positive return on their money by parting with it today.However, when inflation is factored into bond prices, bondholders are now legally obligated to suffer a loss. Not only that, but there is the potential for widespread breakdown. Bonds are a cornerstone of the global financial system, and they are extremely vulnerable due to the system's current state of disrepair.
There is a ridiculous quantity of credit available. As a result of central banks' lax stance on debt in recent decades, several countries' governments have racked up massive amounts of debt. Already, both Argentina and Venezuela have defaulted on their debts. More debt defaults by governments are possible. They can still repay their debt by printing additional money, notwithstanding the default. However, this would lead to a devaluation of a national currency, which in turn would lead to inflation and reduce the appeal of most bonds, which already offer very modest rates.
For the past 50 years, whenever stocks dropped in value, investors hid their money in the "safety" of bonds, which rose in value during "risk-off" periods. Because of this dynamic, the 60/40 portfolio was able to flourish until March 2020, when central banks flooded the market with money, causing it to crash. Efforts to stabilise bond prices will only raise Bitcoin's demand in the long run.
Graham believed that it was more important to keep your money safe than to make it expand. Bitcoin enables the decentralised storage of value without the risk of credit or counterparty risk.
Bitcoin Versus Real Estate
Due to the extreme inflation of the past few decades, it is no longer sufficient to simply save one's wealth in a savings account. Therefore, many people prefer to keep a sizable amount of their capital in one of the most stable markets: real estate. Bitcoin competes with physical property in this regard since its features make it a desirable medium of exchange and safe haven for wealth. There is a limited quantity, but it is easily transportable, divisible, lasting, fungible, resistant to censorship, and does not require incarceration. As a medium to store wealth, real estate is inferior to bitcoin. Bitcoin is more difficult to seize since it is scarce, liquid, mobile, and decentralised. It can be transmitted at the speed of light to any location on Earth for next to nothing. However, real estate is both simple to confiscate and difficult to liquidate during times of crisis, as was recently demonstrated in Ukraine, where many people turned to bitcoin to hide their riches, accept transfers and gifts, and cover their basic living expenses.
Michael Saylor discussed the drawbacks of real estate as a safe haven in a recent interview with Nik Bhatia. Saylor emphasised the need to keep up with the upkeep of any property. Real estate is expensive due to rent, maintenance, and property management. To most people, commercial real estate is boring because it requires a large initial investment. Second-tier real estate investments like real estate investment trusts (REITs) have also fallen short of actually possessing the asset, despite attempts to make it more accessible.
If Bitcoin (a form of digital property) continues to gain popularity, it could eventually supplant land (a form of physical property) as the go-to place to stash cash. As a result, the monetary premium that comes with using a tangible asset as a store of value may evaporate, and the asset's value may fall to its utilitarian value. Given that bitcoin is only at the beginning of its adoption cycle, its future return will be significantly higher than that of real estate. Furthermore, it is likely that the returns on real estate investments will be lower than they have been in the past. There has been an almost 70-fold increase in home prices since 1971. Furthermore, governments tend to tax citizens at times like this, as pointed out by Dylan LeClair in his article turned podcast, "Conclusion Of The Long-Term Debt Cycle." Properties are difficult to transfer between jurisdictions and are subject to high tax rates in each. Bitcoin taxes should not be applied capriciously. Being beyond the reach of any single authority makes it immune to confiscation and censorship.
Bitcoin versus ETFs
Index investing, a passive investment technique in which a manager needs to do nothing more than make sure a fund's holdings match those of a benchmark index, is the conceptual ancestor of exchange-traded funds (ETFs). The Vanguard 500, the first index fund, was created by Vanguard Group founder Jack Bogle in 1976 to mimic the performance of the S&P 500. Over $10 trillion is currently being managed through ETFs. Bogle held the opinion that actively picking stocks was a waste of time.He mentioned in several interviews that an individual fund manager had a 3% chance of outperforming the market on a long-term basis. He reasoned that regular people investing their money would have a hard time outperforming the market and made it a top priority to develop low-cost investment options that would still provide them a chance to benefit from rising asset values and build their nest eggs. Index funds often generate higher tax-efficient returns since they require fewer trades to maintain their portfolios than funds with more active management strategies. The ETF concept has merit, but Bitcoin has more practical applications. While ETFs make it easy to diversify your portfolio, you are still restricted to investing in just one index, sector, or geographical area. However, when you purchase bitcoin, you are actually purchasing a measure of human output. To compare Bitcoin to an ETF would be an understatement. I'll break it down for you:
By this point, the potential of Bitcoin should at least be common knowledge. Bitcoin is a peer-to-peer digital currency exchange and storage system that operates on a decentralised network of computers. In addition to being the most valuable currency in circulation, bitcoin also serves as the underlying protocol for the fastest and most secure payment system currently available (the Lightning Network). In the not-too-distant future, Bitcoin will very certainly replace all other payment networks and serve as the primary digital currency and value-storage medium. It will thereafter serve as a measure of global output. In a nutshell, the larger the demand for bitcoin, the higher the price of bitcoin will be because the more value we produce and the more transactions we will perform, the more value will need to be held. I've realised that rather than buying an exchange-traded fund (ETF) to follow a handful of indices, I can just buy bitcoin and benefit from the world's collective efforts. Since its debut, bitcoin's returns have naturally surpassed those of any ETF.
VERSUS BITCOIN RETURNSETFS RETURNS
One of the oldest and most popular ETFs is the SPDR S&P 500 ETF Trust. It's made to mirror the performance of the S&P 500 index. As of October 25, 2022, the performance was 168.0%, which works out to an annualised return of 16.68% for the past decade (from October 26, 2012, to October 25, 2022). Not bad, considering the minimal effort required to achieve these results by simply holding.
Bitcoin, on the other hand, gained 158,382.362 percent during the same time frame. greater than 200% annually. The common adage that "the past is no guarantee of the future" might actually be true. Bitcoin, on the other hand, is different. In general, the greater a stock's P/E ratio, the more volatile it is. Certainly not bitcoin.When the price of bitcoin rises, investors can feel safer putting their money into it because of its growing liquidity, size, and global preeminence. At this point, the Bitcoin network has grown to a scale where it WILL survive (the Lindsay Effect).
As a result, we may assume that bitcoin will keep doing better than ETFs in the future.
Bitcoin also offers other benefits that an ETF lacks. To begin with, it has a cheaper overall price. The second is that the latter is a portfolio of securities owned by an unrelated person. Your ability to sell your ETFs is restricted. Your exchange-traded funds (ETFs) will be lost if your bank decides to cancel your account. However, Bitcoin is difficult to confiscate or restrict access to. The ease with which bitcoin may be transferred across the globe at the speed of light makes confiscation extremely difficult.
CONCLUSION
For the sake of securing financial assets in the digital era, Bitcoin is the best option. a rare, non-inflationary, digital-native bearer asset that carries no risk of default and may be easily transferred between parties. Bitcoin is a digital currency that can be traded on the Internet. The Bitcoin network has the potential to hold all of the world's wealth (global wealth hit a record high of $530 trillion in 2021, according to the Boston Consulting Group), making it potentially the most efficient way humans have found to store value. Bitcoin holders can be assured that their wealth will grow by a factor of ten, one hundred, or even five hundred during the early stages of the cryptocurrency's monetization process. If you can wait it out for a couple of decades,
FAQs
Who sets the value of a bitcoin? Bitcoin's price is set by the market on which it trades. In other words, the value of a bitcoin is set by the demand for it. Bitcoin's price is influenced by market forces, just like those influencing the cost of other commodities such as gold, oil, sugar, grains, etc.
In how many days can one bitcoin be mined? One bitcoin can be mined in around 10 minutes with the right hardware and software, but this setup is expensive and only available to a select few individuals. The average user can mine a bitcoin in 30 days, which is both common and reasonable.
Explain why Bitcoin is a terrible investment? Bitcoin, the most valuable cryptocurrency, is a volatile and high-risk investment. Only those with a high tolerance for risk, solid financial resources, and the ability to absorb a financial setback should even think about investing in it.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 57fe4c4a:c3a0271f
2023-10-18 13:02:10
@ 57fe4c4a:c3a0271f
2023-10-18 13:02:10📝 Summary: Batched splicing can be risky due to certain conditions like no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions caused by confirmed old states. Additionally, not all splice implementations performing a check can lead to potential loss of funds.
👥 Authors: • Greg Sanders ( nostr:npub1jdl3plz00rvxwc6g2ckemzrgg0amx5wen4kfvs3laxtssxvk9cvsf3gh0m ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l )
📅 Messages Date: 2023-10-17
✉️ Message Count: 3
📚 Total Characters in Messages: 5405
Messages Summaries
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if certain conditions are met, such as having no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions.
✉️ Message by Greg Sanders on 17/10/2023: Batched splicing is risky because if an old state is broadcasted and confirmed before the splice, it can disrupt the process. It is important for batched splicing mechanisms to have a backout option.
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if not all splice implementations perform a check to ensure subsequent splices confirm, potentially leading to loss of funds.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 44dc1c2d:31c74f0b
2024-05-22 22:09:19
@ 44dc1c2d:31c74f0b
2024-05-22 22:09:19Chef's notes
If you don't have peanuts, you can sub it with peanut butter, but you'll want to cook with less salt as the peanut butter can add too much salt to the dish.
Details
- 🍽️ Servings: 4
Ingredients
- 2 1/2 cups Coconut Milk
- 3 Tbsp Red Curry Paste
- 3 Tbsp Thai Fish Sauce
- 2 Tbsp Palm sugar or light brown sugar
- 1 LB rump streak cut into thin strips
- 2 Lemon Grass Stalks, Bruised
- 3 oz Ground Roasted Peanuts
- 2 Fresh Red Chilies, Sliced
- 5 Kaffir Lime Leaves, Torn
- Salt and Pepper
- Thai Basil for Garnish
- 2 Salted eggs to serve with
Directions
- Put half the coconut milk in a large pan or Wok and heat gently until it begins to boil and separate.
- Add the curry paste and cook over medium heat until fragrant. Then add the Fish sauce, sugar and lemon grass.
- Continue to cook until the color of the sauce deepens
- Add the remaining coconut milk. Bring back to boil. Add the beef and peanuts. Cook for another ~10 min
- Add the chilies and the torn Kaffir Lime and adjust the seasoning. Garnish with whole Basil leaves and serve with a salted egg and rice.
-
 @ 1c6b3be3:73f0ae6f
2024-05-25 04:06:04
@ 1c6b3be3:73f0ae6f
2024-05-25 04:06:04Releases - No Bullshit Bitcoin
BitBanana v0.8.0: Core Lightning, LndHub Support BitBanana, a Android app designed for Lightning node operators with a focus on user experience and ease of use, has released v0.8.0. This update includes new features such as support for Core Lightning and LndHub, self-hosted fee estimation and exchange rate via Mempool. Additional features include the ability to scan QR codes from images, set exact on-chain fees in sat/vB, send and request sub-satoshi amounts, and many UX improvements. These improvements include easy format conversion for certificates and macaroons, allowing lightning payments before fee estimation, avatar style choosing, handling connect URIs before wallet activation, opening newly added wallets immediately, showing avatars on node management list, and network information display for non-mainnet nodes. The update also includes bug fixes and translation updates, including a full Spanish translation. Further details can be found in the GitHub repo.
Hodl Hodl Blocks US Users from Accessing Its Lending Platform (1 min) Hodl Hodl, a cryptocurrency exchange, has announced it will block US residents and citizens from accessing its Lend service due to stricter policies on allowed countries for their services. Existing users in the USA can finalize current loans but cannot start new ones. The company's peer-to-peer trading marketplace never served US customers. The change aims to prioritize serving global community members, particularly those in emerging markets. A list of blocked countries includes the USA, Cuba, North Korea, Iraq, Iran, Puerto Rico, Somalia, Syria, Sudan, and any jurisdiction embargoed by the United Nations.
Speed Wallet Implements KYC for US-based Users Speed Wallet, a custodial Lightning Network wallet based in Dubai, has announced proactive compliance measures for its customers based in the United States. The company will be implementing Know Your Customer (KYC) procedures for all US-based users, which will involve collecting and handling their personal information confidentially in accordance with data protection regulations. Speed Wallet is committed to ensuring compliance and providing a seamless Bitcoin payment experience for its US customers. The update is expected to go live soon.
Bitcoin Optech
Bitcoin Optech Newsletter #304 (12 min) The newsletter discusses various topics related to Bitcoin and Lightning Network (LN) upgrades. It summarizes an analysis of proposals for upgrading existing LN channels without closing and reopening them. The proposed ideas include dynamic commitments, splice to upgrade, and upgrade on re-establish. The newsletter also discusses the challenges in ensuring pool miners are paid appropriately, linking to a discussion about using PSBTs for communicating information related to silent payments. A proposed BIP for miniscript is announced along with a proposal for using frequent rebalancing of an LN channel to simulate a price futures contract. The newsletter further includes regular sections summarizing changes to services and client software, announcing new releases and release candidates, and notable changes to popular Bitcoin infrastructure software.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Lightning Network Adoption: A Global Perspective on Faster Bitcoin Payments - Eye On Annapolis Michael Saylor And Quoth the Raven: The Conundrum of Central Planning - Bitcoin Magazine “This is the Time to Get In ” – Bitcoin and Ethereum on the Verge of a $4.2 Trillion ETF Price Surge, BlockDAG Network ... - GlobeNewswire Onchain Fees for Bitcoin Drop to Six-Month Low – Blockchain Bitcoin News - Bitcoin.com News Battle Of Networks? Algorand Pokes Fun At Bitcoin, Ethereum, And Solana In New Ad - NewsBTC Algorand slams Bitcoin, Ethereum, and Solana in new ad, community reacts - crypto.news Jade ARdinals CEO says the future of Bitcoin defi includes smart contracts - InvestorsObserver Enhanced 120V ASIC Miners: Combining Silent Operation with Dual-Purpose Functionality for Home Bitcoin Mining - EIN News Coinme CEO Neil Bergquist on How Regulation & Bitcoin ATMs Can Help Make Crypto Safe - Bitrates
-
 @ f3df9bc0:a95119eb
2024-05-24 21:03:50
@ f3df9bc0:a95119eb
2024-05-24 21:03:50U2FsdGVkX1/V0KPxhh/mvn15kpUT1AmLyyXbHxGMe4W/5WHSQxyG2P+0vy38PGYQXTbZJKqCee/b8+t0/RsK7z93n1PtIrhh0Qit3FEbg3uHVbaCx3pWvcw40Cm8pYD1dIHCXHXKu0XysrTcgga1ceTQEvJJXq7Wg13DleZYA1womBFiSlhhojPNw0PaWQDI9IMQ1mmT3xt+qtvPe1/OrQGhCB7cB8tvXx+iZQfjtyg8kauhSMh8ORdwrJfKqIM8QAS6DjGl/n3RDRgWKz+hoNkzE5wgotVbtQLN+mZRZRs4ZiyleEYLE3eFV4izIrn9+kP4F7W6R1Ny0aE+gImAQYhesKjtJLgA3iyyVRnDnq7zh3c7dFepLBK+pnJLKZ7jyZHYY7wx86k3MbAIh9F/5cJFfCtsF4M1nOel7ru/dlTMoX+gRTzeXzaq8XbWBMvs




