-
 @ 0b963191:fc5e7ffd
2024-05-05 23:36:45
@ 0b963191:fc5e7ffd
2024-05-05 23:36:45Chef's notes
Can of course substitute in beef for the lamb.
In terms of canned peas, always prefer La Sueur
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- Potatoes:
- 1 ½ pounds potatoes (Russet)
- ½ cup half-and-half
- 2 ounces unsalted butter
- ¾ teaspoon kosher salt
- ¼ teaspoon black pepper
- 1 egg yolk
- Meat Filling:
- 2 tablespoons canola oil
- 1 cup chopped white onion
- 3 carrots, peeled and diced
- 1 ½ pounds ground lamb
- 1 teaspoon kosher salt
- ½ teaspoon black pepper
- 3 tablespoons flour
- 3-4 teaspoons tomato paste
- 1 cup chicken broth
- 3 teaspoons Worcestershire sauce
- 2-3 teaspoons chopped rosemary leaves (fresh)
- 1-2 teaspoons chopped thyme leaves (fresh)
- ¾ cup corn kernels
- ¾ cup peas
Directions
- Potatoes:
- Peel and dice potatoes.
- Place in a pot and cover in cold water.
- Bring to a boil.
- Lower fire to simmer and cook for 15-20 minutes.
- Heat butter and half-and-half for 30-40 seconds in the microwave.
- Drain potatoes and put back into the pot.
- Mash potatoes and add half-and-half, butter, salt, pepper.
- Continue mashing until smooth and stir in yolk until combined.
- Preheat the oven to 400 degrees.
- Filling:
- Heat canola oil in a 10-12 inch pan over high heat.
- Add onions and carrots and saute over medium-high heat for 4-5 minutes.
- Add garlic and combine for 30 seconds.
- Add Lamb, salt, and pepper and cook until browned.
- Sprinkle flour and stir to coat lamb and cook for 1-2 minutes.
- Add Tomato paste, chicken broth, Worcestershire sauce, rosemary, thyme. Stir and bring to a boil.
- Reduce heat to low, cover, and simmer for 12-15 minutes while sauce thickens.
- Oven:
- Add meat filling to baking dish.
- Add peas and corn and stir in evenly
- Spread mashed potatoes using a rubber spatula. start at the corners and make sure to seal around the edges.
- Bake for 25 minutes
- Remove from the oven and let sit for 15-20 minutes.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ fbe736db:187bb0d5
2024-05-05 10:06:09
@ fbe736db:187bb0d5
2024-05-05 10:06:09This is a slightly edited version of the article published in Bitcoin magazine in December 2021.
As we come to the end of 2021, it’s popular to reflect on the year gone by, and produce crystal balls to predict the future bitcoin price.
Firstly, though, one of my favourite thoughts about the future in general comes from Jeff Bezos.
“I very frequently get the question ‘What’s going to change in the next 10 years?’ And that is a very interesting question; it’s a very common one. I almost never get the question ‘What’s not going to change in the next 10 years?’ And I submit to you that that second question is actually the more important of the two — because you can build a business strategy around the things that are stable in time … When you have something that you know is true, even over the long term, you can afford to put a lot of energy into it.”
For Amazon, what Bezos meant was that for them what won’t change is that customers will want a large choice of products, low prices, and speed of delivery. This is what they have built Amazon around.
So how does this apply into the coming year, and to Bitcoin? As we enter 2022 we live in a hugely uncertain world, with COVID-19, record debt levels, rising inflation, socioeconomic inequalities and rising geopolitical tensions. I submit to you in turn that Bitcoin’s monetary policy and general structure is one of the very few things on the planet that are not going to change over the next 10 years, or the next 20 years, or even the next 30 years. And that stability is a source of strength for anyone holding bitcoin, and a major incentive for anyone considering holding it.
Let’s further consider that 30-year time period for a second in the wider macro context. As I write this (December 7), the 30-year U.S. Treasury yield is approximately 1.7% per annum. This suggests that if we buy a 30-year treasury bond and hold it until 2051, it will return 1.7% per year, or approximately 66% compounded. $1,000 would become $1,660 in 2051 if compounded at that rate.
Though that treasury return is termed “risk-free,” we can’t predict the purchasing power of those dollars in 30 years time. No one can say. And if you want to envisage just how far away 2051 is, consider that 30 years back in time is 1991. We’re talking a world just after the fall of the Berlin Wall, of the Gulf War (the first one), of Mikhail Gorbachev, of President George Bush (senior); all this was before the explosion of the internet, and when mobile phones were for yuppies.
What would have an investor been faced with back in 1991, considering a 30-year treasury investment? The approx 30-year yield at the end of that year was 7.4% per annum. That’s compared to 1.7% now, as noted earlier. Prices are inverse to yields, so today’s bond prices are sky high by comparison to 30 years ago. And since other asset classes (equity, property, etc.) are priced relative to the risk-free rate, it is not surprising we are in an everything bubble.
It’s for this reason that the likes of Preston Pysh and Greg Foss predict bitcoin potentially eating into global bond markets. It matters little that bitcoin has no risk-free yield when an increasing number of bonds are negative-yielding in real terms. And for a long-term investor, what are the chances that $1,000 worth of Bitcoin will likely return more than $1,660 in 30 years time? If you agree that it could be vastly higher, even if you still assign a probability that Bitcoin dies, then perhaps you’re onto a question of position size.
So what of the future bitcoin price? I like the analogy of bitcoin as an economic battery, charging up on increasing adoption, and decreasing in value in periods where holders run for the hills. The price is simply a snapshot in time of buyer meeting seller at the margin to agree the latest price for acquiring the use of this battery for a certain amount of bitcoin.
Why would this be hard to predict? For starters - for every participant, their holding could also be viewed as a two-dimensional function of how much bitcoin they hold, and how long they are holding it for. Term it “bitcoin years” (210 million of those every decade) or “satoshi seconds” (considerably more). On an ongoing basis all participants and potential participants continually act.
Given the supply is fixed, the only element that determines price is demand — from new buyers that don’t yet hold bitcoin, but also continued demand from existing holders continuing to accumulate and hodl — i.e., how long is that time period? It’s nigh on impossible to accurately predict either future demand from newcomers, and continued participation from current bitcoiners. Therefore any models seeking to predict future price are almost by definition junk, including stock-to-flow ( listen to Cory Klippstein here if you want far better specifics on this). It’s for this reason too that Michael Saylor says “All your models are destroyed”
https://twitter.com/swanbitcoin/status/1318574499546234886?lang=en
This is not to say I’m not hugely bullish. It’s just that bitcoin price predictions are a bit of a waste of time. Back to the sentiment of Bezos — don’t try and predict exactly what will change in the world in future, but focus more on the core elements of Bitcoin that won’t change.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 1c6b3be3:73f0ae6f
2024-05-05 09:21:43
@ 1c6b3be3:73f0ae6f
2024-05-05 09:21:43The air was electric with anticipation as Ava stepped onto the stage, her eyes scanning the packed auditorium. This was her moment – the culmination of years of hard work and countless sleepless nights spent hunched over her computer, coding and tinkering with the cutting-edge Layer-2 (L2) solution she had developed for the Bitcoin network.
Ava had always been fascinated by the potential of blockchain technology, and the launch of the Runes tokens had only heightened her determination to find a way to unlock Bitcoin's true power. As the network struggled to keep up with the surge in transactions, Ava knew that the time had come for a game-changing solution.
Her project, dubbed "Quantum Leap," had been selected for the prestigious Crypto Accelerator program, putting her in the spotlight of the entire crypto community. Standing before the eager crowd, Ava took a deep breath and began to unveil her vision.
"Ladies and gentlemen, the future of Bitcoin is here," she declared, her voice brimming with confidence. "Quantum Leap is a revolutionary L2 protocol that not only solves the scalability and transaction fee issues plaguing the network, but also future-proofs Bitcoin against the looming threat of quantum computing."
The audience erupted in applause, and Ava couldn't help but feel a surge of pride. But as she stepped off the stage, she was met by a familiar face – Liam, a seasoned crypto trader and early Bitcoin adopter.
"Impressive work, Ava," Liam said, his eyes gleaming with excitement. "I've been following your project, and I believe it could be the key to unlocking Bitcoin's true potential. I'd like to invest in Quantum Leap – and I think I know just the person who can help us take it to the next level."
Ava's heart raced as Liam introduced her to Dr. Xiang, a brilliant computer scientist leading a team of researchers at the forefront of quantum computing research. Together, they embarked on a mission to create a quantum-resistant L2 protocol that would revolutionize the Bitcoin network.
The months that followed were a whirlwind of intense collaboration, sleepless nights, and breakthroughs that pushed the boundaries of what was thought possible. As the team worked tirelessly to perfect their creation, the crypto world watched with bated breath, eager to see what this new L2 solution could achieve.
Finally, the day of the Quantum Leap launch arrived, and Ava, Liam, and Dr. Xiang took the stage once more, this time to unveil their groundbreaking creation. As the details of the protocol unfolded, the audience erupted in thunderous applause, realizing that they were witnessing a pivotal moment in the history of Bitcoin.
The Quantum Leap protocol not only solved the network's scalability and transaction fee issues, but it also introduced a new era of decentralized applications, smart contracts, and user-friendly interfaces that made Bitcoin accessible to the masses. The future of the world's first cryptocurrency had been forever transformed, and Ava, Liam, and Dr. Xiang had played a crucial role in ushering in this new era of innovation and adoption.
As the crowd dispersed, Ava couldn't help but feel a sense of awe and wonder. The Runes tokens had been the catalyst, but the Quantum Leap protocol had been the key to unlocking Bitcoin's true potential. The future was Layer-2, and she couldn't wait to see what the next chapter would hold.
-
 @ fbe736db:187bb0d5
2024-05-05 09:20:02
@ fbe736db:187bb0d5
2024-05-05 09:20:02This article was published in Bitcoin magazine in October 2021.
At “The B Word” conference earlier in the summer, there was a memorable panel event with Elon Musk, Cathy Wood and Jack Dorsey in which we were able to ascertain a little more (than we had often seen in tweets) about Elon Musk’s Bitcoin views. This article is an attempt to dissect and evaluate what he said around Bitcoin’s block size.
Firstly, let’s review what was said (starts at 18:15):
Steve Lee (panel host) — “Elon, I’m curious for your opinion on this — you mentioned, earlier about the importance of throughput, maybe some concerns around bitcoin. Do you think bitcoin can become peer-to-peer cash?”
Elon Musk — “Well, Bitcoin does have a fundamental scarcity limit at the base layer, that’s designed in; that doesn’t mean you can’t have some Layer 2 solution, like Lightning — I understand Lightning is doing well in some small countries.
“There is some question mark as to whether you’d need a money transmitter license, just a debate as to whether that is needed, that it is not open ledger; that’s a whole separate debate, of course.
[Interesting rereading this in 2024 - Elon Musk foresaw this attack on Bitcoin a couple of years prior; not that it particularly validates his comments.]
“But Bitcoin by itself simply can’t scale to be the monetary system for the world at base layer. At a second layer, this is possible — it would depend on how that second layer is implemented.
“That’s part of why I think there may be some merit to, er, — something that may seem silly — like Dogecoin.. the three things I own outside from SpaceX and Tesla ..of any significance are bitcoin by far, and some eth and some doge. If the price of bitcoin goes down I lose money.. I might pump but I don’t dump. So it’s not a case of.. I don’t believe in getting the price high and selling or anything like that ..I would like to see bitcoin succeed.
“I think there’s some merit to — this is not a slam on Bitcoin — there is some merit to considering something that has a higher max transaction rate, and lower transaction cost — kind of seeing how far you can take a single layer network, where the exchanges act as a de facto second layer. I think you can probably take that further than people realise, and as bandwidth increases over time, latency decreases… Space X and Starlink are actually playing a role in this, and I think long term people probably have access to — worldwide access to — gigabit level connectivity at low latency, at low cost. And so then your base layer could do a lot of transactions if you take that into account.
“But as I said, Bitcoin with the Layer 2 system, I still think, could scale to do a vast number of transactions — the same goes for Ethereum.”
Steve Lee — “The question about the scaling of the Layer 1 — the concern from the past five years of debate in the Bitcoin community — is that that would sacrifice too much decentralisation, and hurt the censorship-resistant properties of bitcoin. I’m curious, what are your thoughts — are you sensitive to that, are you concerned about losing some of the special properties of bitcoin or another cryptocurrency by scaling at Layer 1?”
Elon Musk — “Yeah, with these things it’s helpful to use the physics tools of thinking; you know scale up, scale down, and see if it still makes sense. So if scaling up the transaction block doesn’t make sense, why don’t you scale it down? And have it be so somebody, you know, with a laptop from 2008 can still run a Bitcoin node. Why not slow it down. Oh. You want to slow it down? Well, maybe you’re at the wrong number then (laughs).”
Steve Lee — “There are actually members of the community who do want to slow it down!”
Elon Musk — “It’s silly. The reality is, the average person is not going to run a bitcoin node. And — Bitcoin — a lot of clever ideas, but these parameters were set in 2008, or 2009. There have been some improvements since then, but not a lot. You know, in 2008 there were still a non trivial number of people on modems (laughs)… nowadays it is quite common to get a 100mbs connection just for a house — some houses have gigabit connections… and that trend is obviously in the direction of higher bandwidth and lower latency. And if somebody else doesn’t do it, Starlink certainly will, so I have high confidence you would be able to maintain a decentralised finance system whilst still having a much bigger blockchain.. A.k.a. ASCIItext ledger, a hash ledger — you can make the hash ledger bigger, without harming decentralisation, as the average connectivity improves, obviously.”
Many Bitcoiners will have rolled their eyes at these comments, with the block-size war (read the excellent book by Jonathan Bier of the same name) around 2015–17 still a recent memory. However, dissecting the comments remains key to an understanding of bitcoin’s unique value, versus other cryptocurrencies.
In some respects, Elon Musk has a point. If Bitcoin were developed for the first time today, it might not have been given the same parameters as it has had since its outset. Elon Musk is a visionary in other fields, and it’s only natural that a character like him might ask what might be, as opposed to accepting what is. However, before you go searching for the most viable alternative altcoin to back which has bigger blocks, it’s worth considering that Bitcoin probably could have been established at outset with half the current block size, or double the block size, and still been in a similar position as it is today. Much in the same vein, and a more trivial example — was 21 million coins the right number to choose?
How so? One anecdote I’d highlight to describe the position Bitcoin is in is the plug socket analogy used by Robert Breedlove (and no doubt others) to describe Bitcoin’s inaugural, first-mover lead over others. There may be better plug socket designs out there now, but entire nations are not going to shift designs for all sockets and appliances unless there is a 10x advantage to be derived from the new one.
The fact is, Bitcoin has a near-unassailable lead in terms of security of the network, nodes, users, and the surrounding ecosystem. I’d recommend a read of Nic Carter’s article on settlement assurance which much better articulates this.
At the heart of the argument also lies the whole concept of digital scarcity, upon which bitcoin derives most of its value. If any other cryptocurrency overcomes bitcoin, what is to stop the next incumbent from in turn overcoming it? This for me would cast doubts over the existence of any meaningful digital scarcity, and hence store of value potential, from any cryptocurrency at all. This could still turn out to be the case, but it doesn’t lead us to Doge.
I’d disagree slightly with Elon Musk’s assertion that the average person is never going to run a Bitcoin node; as might Umbrel, who have just this week unveiled an “out of the box” solution for doing so. The market will no doubt drive this cost down significantly over time and make it easier still. As bitcoin adoption increases, it would be healthy to see far more nodes running than there are now. As fellow Bitcoin Magazine contributor Mitch Klee has tweeted, it’s not inconceivable that smartphones could have capacity to store the Bitcoin blockchain and run a node in future. Shinobi has pointed out in turn that there may be bottlenecks here — CPU / RAM / data plans, for example. But one thing’s for sure — with a fixed block size the number of nodes should increase over time, which is healthy and arguably necessary for the network.
In summary, whilst Elon Musk was right to point out that larger block sizes may appear more desirable now and into the future on paper, any advantage gained here versus Bitcoin in its current form is slender, and unlikely to be selected by the market compared to Bitcoin’s existing and wholly unique properties.
Does Elon Musk ultimately recognise this? On the basis that actions speak louder than words (and his actions so far this year have been to buy and hold quite a large amount of bitcoin), I wouldn’t rule it out. Time will tell.
-
 @ b2d670de:907f9d4a
2024-04-28 09:48:01
@ b2d670de:907f9d4a
2024-04-28 09:48:01This is a list of nostr relays exposed as onion services. The list is currently actively maintained on GitHub. Contributions is always appreciated!
| Relay name | Description | Onion url | Operator | | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | njump | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | njump | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | njump | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion
http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion (for payments) | njump | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | njump | | relay.westernbtc.com | The westernbtc.com paid relay (via Tor: hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | njump | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | njump | | nostr.sovbit.host | Paied relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | njump | | nostr.wine | 🍷 nostr.wine relay (same as clearnet) | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion
http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | njump | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay (same as clearnet) | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion
http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | njump | -
 @ 5d4b6c8d:8a1c1ee3
2024-05-05 22:52:59
@ 5d4b6c8d:8a1c1ee3
2024-05-05 22:52:59Congratulations to renowned basketball expert @siggy47 on his triumphant victory!
Knowing that our champion values his privacy, I've zapped the undisclosed quantity of winnings to a random Siggy post or comment.
I need to do some rethinking of how to structure this for next year, since it would have been nice to have the pool at least survive into the second round of the playoffs.
Let me know if you have any thoughts.
-
 @ 81870f53:29bef6a6
2024-05-05 21:40:56
@ 81870f53:29bef6a6
2024-05-05 21:40:56先週、中東情勢の緊張緩和や安全資産への買いが入り、金相場は5週間続いていた連勝記録が止まった。 今週、投資家は水曜日に予定されている米連邦準備制度理事会の金利決定や、中央銀行の政策に影響を与える可能性が高いその他の経済データに熱心に注目していた。
月曜日には、テスラなどの企業からの堅調なデータにより、新たな週の決算が始まり、株価が上昇した。 金相場は今週2,332ドル付近でスタートしたが、金曜日に発表された予想を上回るインフレ統計を受けて、月曜日には2,324ドルまで下落するだろう。 同様の動きで、銀も同日終値26.88ドルまで1.4%下落した。
最近のインフレ率が投資家心理を圧迫し、火曜日の主要株式市場平均には下落圧力がかかった。 その結果、ダウ工業株30種平均、S&P500種、ナスダック総合指数はいずれも下落してその日を終え、5カ月に及ぶ連勝記録は止まった。 最も注目すべきは、ダウ平均が570ポイント急落し、2022年9月以来最悪の月間損失を被ったことだ。
投資家が水曜の金利発表に身構える中、火曜日はドル指数が0.65%上昇する中、金は複数の逆風にさらされた。 こうした展開に加え、地政学的な緊張の緩和が続いたことで、金価格は火曜日の終値までに1.8%下落し、2,282ドルとなった。
米国でインフレが続く中、投資家の間ではFRBがさらにタカ派的な姿勢を選択し、利上げに踏み切るのではないかとの懸念があった。 米連邦準備理事会(FRB)のパウエル議長は水曜の演説で、「次の政策金利の決定が利上げになる可能性は低いと思う」と述べ、こうした憶測をある程度払拭した。
これに安心感を抱いた人もいたが、パウエル議長はまた、インフレ率がFRBが掲げる2%目標まで減速しているという「より大きな確信」が得られるまでFRBは利下げの計画はないと述べた。 パウエル議長の演説を受けて株価はまちまちとなり、ドルと米国債の利回りは下落した。 財務省の利回り低下を受けて金が有利となり、イエローメタルは1.6%上昇してオンス当たり2,320ドルとなった。 一方、銀は26.60ドル付近でほとんど変化がなかった。
FRBの金利見通しに影響を与える可能性が高い経済指標に焦点が移ったため、木曜日、金は0.5%下落した。 そのデータの一部は今朝雇用ニュースを通じて発表され、米国経済が4月に17万5,000人の雇用を創出したことが明らかになった。 これは24万人の雇用増加を求める予想を外し、一部ではFRBが2024年後半に実際に利下げする可能性があるという見方を裏付けた。
金相場は給与発表を受けて上昇したが、その後は日中の上昇分の大半を手放した。 最終的に、金は1.3%安の2,302ドルで週を終え、2週連続の下落となる。 銀も給与支払い後の上昇を享受したが、週間では2.6%下落して26.55ドルで週を終えることになるだろう。
FRBの楽観的な見方と明るい決算データにより、今朝の主要株式市場平均は勢いを維持することができ、主要3銘柄平均はすべて週間上昇を確保した。 S&P 500 は週間で 1.3% 上昇し、最大の勝者となり、ダウとナスダックはそれぞれ 1.1% と 0.9% の週間上昇を記録しました。
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
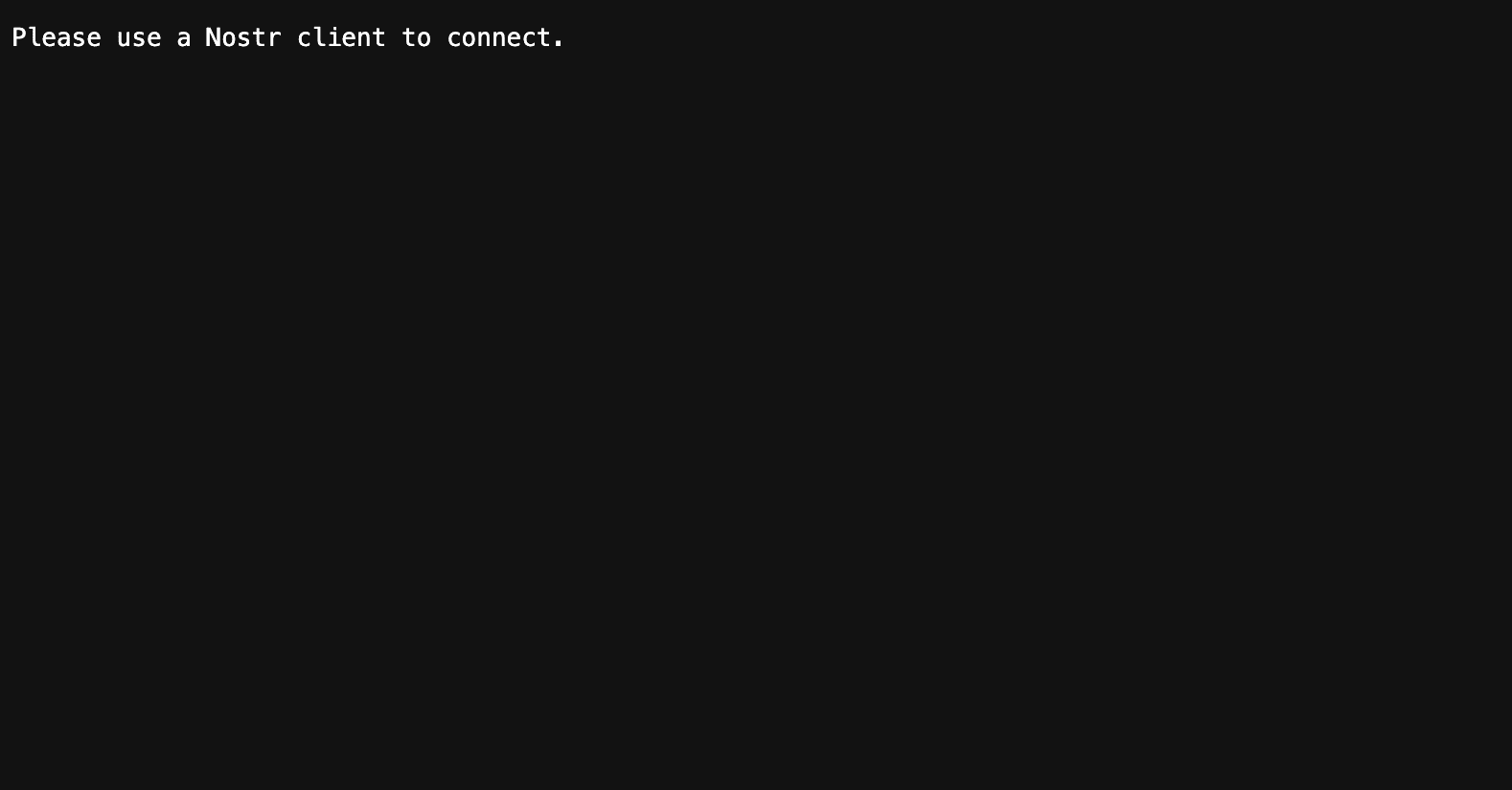
Transform your relay's landing page from this:
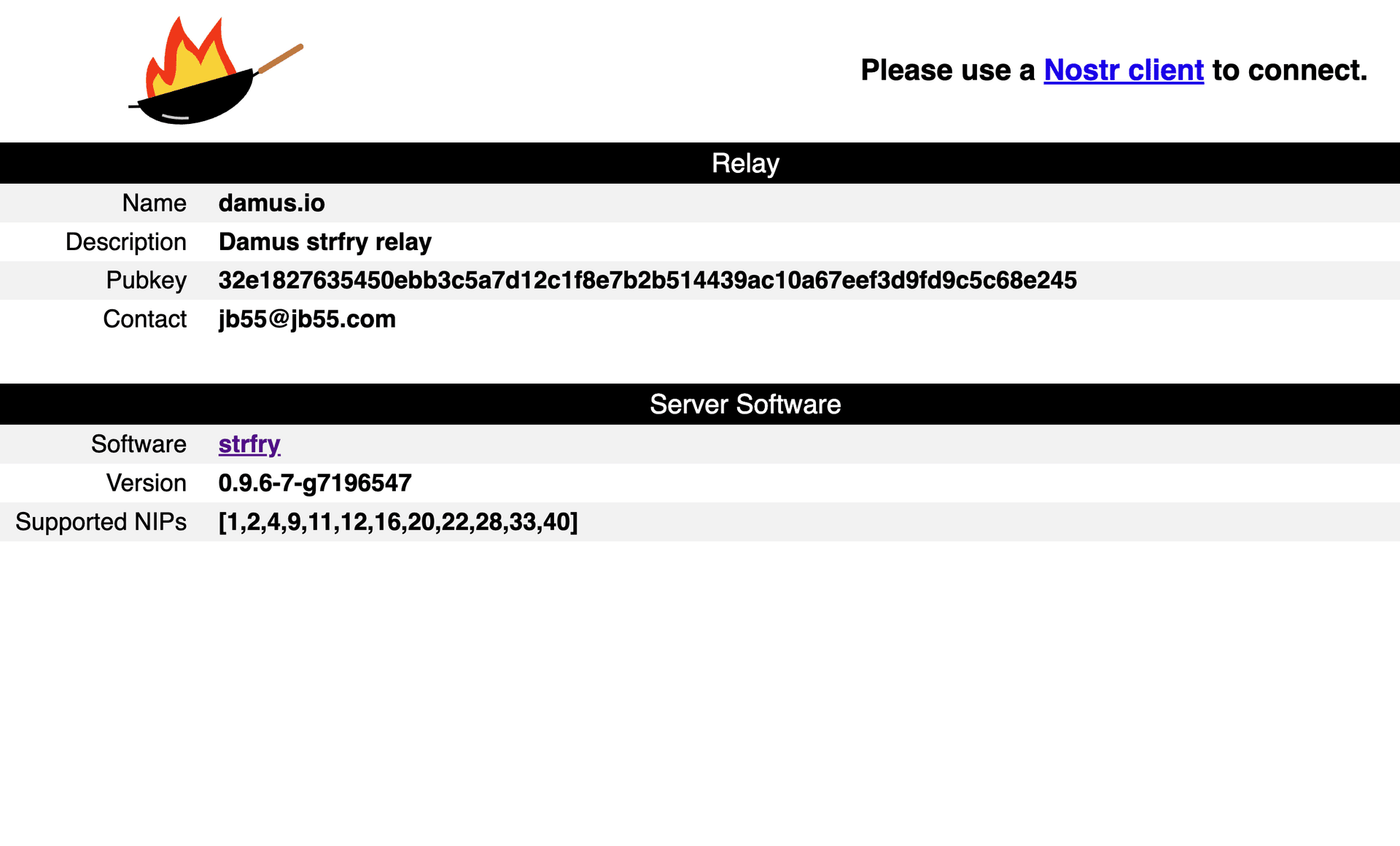
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ 81870f53:29bef6a6
2024-05-05 20:59:12
@ 81870f53:29bef6a6
2024-05-05 20:59:12一見無秩序に見える通貨切り下げの裏には、日本当局の周到な策略が隠されているのだろうか?
以前の円の「自由下落」と比較して、日本当局の行動はわずか半拍以上鈍化しているが、経済を回復するための駒としての円安から判断すると、この行動は説明しやすいように思われる。
HSBCは5月3日のレポートで次のように述べた。
円安は為替調整だけでなく、構造的に「インフレ経済の復活」にも重要な役割を果たしており、長年競争力を失っていた輸出業者がようやく為替調整による追い風を実感するまでには長い時間がかかるかもしれない。為替レートの低迷期を乗り越え、この景気刺激を製造業の永続的な復活に変えることができます。
円の対米ドル為替レートは一時160円を割りました。実際、円の対米ドル為替レートは長い間下落し続け、実質実効為替レートは数十年ぶりの安値に戻りました。金利は1990年代半ばに「急激に低下」し、現在は1970年代初頭以来の最低水準にある。

これは、長い間デフレと競争力の喪失に陥っていた日本経済に転換点をもたらした、とHSBCは述べた。
実際、円安は日本経済に活力を与え始めており、最近の純輸出のGDP成長への寄与度の大幅な増加が景気回復を強力に支えている。
しかし、輸出が増加しているにもかかわらず、世界の製造業付加価値に占める日本のシェアは低下し続けており、1990年代後半以来3分の2縮小している。これは、製造業と製造業の持続的な回復を促進するためには、さらなる円安が必要である可能性があることを意味している。輸出。
製造業に加えて、円安は旅行サービス業界にも恩恵をもたらしたとHSBCは述べた。
東京の桜の開花は今年遅く、開花は4月となったが、3月には観光客数が過去最高に達し、訪日観光客のブームがレストランからホテル、小売店まで関連する雇用と賃金水準を支えた。雇用市場を引き締め、賃金上昇に貢献します。
さらに、円安は海外からの観光客を呼び込むことで経済を支えているだけでなく、日本人は国内の安い地域に滞在することを好むため、現在、日本は旅行サービスで健全な黒字を享受している。
総合するとHSBCは、急速な円安は輸入インフレのリスクをもたらす可能性があるものの、日本政府と中央銀行が長年待ち望んでいた「再インフレ」プロセスに大きく貢献したと指摘している。 、輸入物価のインフレはまだ上昇しておらず、政府は財政措置を通じて家計への影響を緩和している。
減価償却プロセスが秩序正しく管理可能であり、短期的なインフレ圧力が管理可能な範囲内にある限り、日本銀行にはまだ政策を大幅に引き締める勢いは見られない。結局のところ、長期的なデフレを終わらせることが日銀の基本である。円安は「良薬」だ。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
-
 @ d830ee7b:4e61cd62
2024-05-04 10:41:02
@ d830ee7b:4e61cd62
2024-05-04 10:41:02เพลงดาบแห่งเสรีภาพในสมรภูมิดิจิตอล
Disclaimer : บทความนี้ได้รับแรงบันดาลใจจากหนังสือ "Cypherpunks: Freedom and the Future of the Internet" โดย จูเลียน อัสซานจ์ (Julian Assange) ผู้ก่อตั้ง WikiLeaks นักเคลื่อนไหวเพื่อเสรีภาพและผู้เปิดโปงความลับของรัฐบาล เขาได้ออกมาตีแผ่ความจริงอันน่าตกใจ เกี่ยวกับการที่รัฐบาลทั่วโลกกำลังใช้เทคโนโลยีเพื่อสอดแนมและควบคุมประชาชนโดยอาศัยอินเทอร์เน็ตเป็นเครื่องมือ
โลกดิจิตอลที่เราอาศัยอยู่ทุกวันนี้ ไม่ได้มีเพียงแค่แสงสีและความสะดวกสบาย หากแต่ยังมีเงามืดของการควบคุมและการสอดแนมซุกซ่อนอยู่ด้วย แต่ท่ามกลางเงามืดเหล่านั้นก็มีกลุ่มคนกลุ่มหนึ่งที่ลุกขึ้นมาต่อสู้ พวกเขาไม่ใช่ซูเปอร์ฮีโร่ในชุดเกราะไวเบรเนียม แต่เป็นนักรบแห่งยุคดิจิตอลที่ใช้ "รหัส" เป็นศาสตราวุธ พวกเขาคือ “Cypherpunk” กลุ่มคนที่ไม่ได้แค่เก่งเพียงเทคโนโลยี แต่ยังใช้ความรู้ความสามารถที่มีอยู่ในการต่อสู้เพื่อสิทธิและเสรีภาพในโลกออนไลน์ด้วย
จุดกำเนิดของ Cypherpunk เกิดขึ้นในช่วงทศวรรษที่ 1990 ณ ซานฟรานซิสโก เบย์ แอเรีย (San Francisco Bay Area) ศูนย์กลางของนวัตกรรมและเทคโนโลยี ขณะที่ผู้คนทั่วโลกกำลังตื่นเต้นกับการมาถึงของอินเทอร์เน็ต กลุ่มนักคิดและนักเทคโนโลยีหัวก้าวหน้ากลุ่มหนึ่งกลับมองเห็นอันตรายที่ซ่อนอยู่ภายใต้สิ่งเหล่านี้ พวกเขาเล็งเห็นว่าเทคโนโลยีที่พัฒนาไปอย่างรวดเร็วนั้นเปรียบเสมือนดาบสองคมที่สามารถนำมาใช้ทำลายล้างได้เช่นกัน
พวกเขาจึงรวมตัวกันโดยเรียกตัวเองว่า "Cypherpunk" ชื่อที่ผสมผสานระหว่างคำว่า "Cipher" ที่แปลว่าการเข้ารหัส และ "Punk" ที่สื่อถึงการต่อต้านและไม่เชื่อฟัง (แถมยังให้อารมณ์ดิบ-เถื่อน) พวกเขาไม่ใช่แค่กลุ่มคนที่มานั่งถกเถียงกันแค่เรื่องเทคฯ แต่ยังลงมือพัฒนาซอฟต์แวร์เข้ารหัสแบบ Open-Source และเทคนิคต่างๆ ที่ทำให้การเข้ารหัสเข้าถึงได้ง่ายขึ้นสำหรับคนทั่วไป เปรียบเสมือนการแจกจ่ายโล่ห์และดาบให้กับทุกคนในอาณาจักรดิจิตอล เพื่อให้สามารถปกป้องข้อมูลส่วนตัวของตนเอง ต่อสู้กับการสอดแนมและการควบคุมจากรัฐบาลและองค์กรต่างๆ
ในบรรดานักรบ Cypherpunk ก็มีบุคคลสำคัญอยู่มากมาย เช่น เอริค ฮิวจ์ส (Eric Hughes) นักคณิตศาสตร์และนักเคลื่อนไหวผู้ร่วมก่อตั้ง Cypherpunks อีกทั้งยังเป็นผู้เขียนหนังสือ "A Cypherpunk's Manifesto" ที่เป็นเสมือนคัมภีร์ของเหล่า Cypherpunk, จูเลียน อัสซานจ์ (Julian Assange) ผู้ก่อตั้ง WikiLeaks ซึ่งเป็นแพลตฟอร์มที่เปิดโปงความลับของรัฐบาล และ จอห์น กิลมอร์ (John Gilmore) นักเขียนและนักกิจกรรม
[ อ่านบทความ "แถลงการณ์ของไซเฟอร์พังค์ (A Cypherpunk’s Manifesto แปลไทย)" ]
พวกเขาเชื่อว่าการเข้ารหัสไม่เพียงแค่ช่วยปกป้องข้อมูลจากการเฝ้าระวังของรัฐได้เท่านั้น แต่ยังเป็นเครื่องมือที่ใช้ในการต่อสู้เพื่อเสรีภาพในการสื่อสารและการแสดงออก เป็นการทวงคืนอำนาจจากผู้มีอำนาจและมอบอำนาจนั้นคืนให้กับประชาชน
Cypherpunk ยังเป็นแรงขับเคลื่อนสำคัญในการพัฒนาซอฟต์แวร์เข้ารหัส Open Source ที่สำคัญ เช่น PGP (Pretty Good Privacy) ที่พัฒนาโดย ฟิล ซิมเมอร์มันน์ (Phil Zimmermann) ซึ่งเป็นเครื่องมือเข้ารหัสอีเมลที่ได้รับความนิยม และ Tor (The Onion Router) ที่ช่วยให้ผู้ใช้สามารถท่องอินเทอร์เน็ตได้โดยไม่ต้องเปิดเผยตัวตน ซอฟต์แวร์เหล่านี้เป็นเสมือนดั่งอาวุธและชุดเกราะที่จะช่วยให้ผู้คนสามารถต่อสู้กับการสอดแนมและการเซ็นเซอร์
ในช่วงทศวรรษที่ 1990, สงคราม "Crypto Wars" ปะทุขึ้น รัฐบาลสหรัฐฯ พยายามจะควบคุมการเข้ารหัส โดยเห็นว่ามันเป็นภัยต่อความมั่นคง พวกเขาต้องการให้มี "backdoor" ในระบบเข้ารหัสเพื่อให้สามารถเข้าถึงข้อมูลได้ แต่ Cypherpunk ก็ได้ลุกขึ้นต่อสู้ พวกเขาเชื่อว่าทุกคนมีสิทธิ์ปกป้องความเป็นส่วนตัว เหมือนกับการต่อสู้เพื่อสิทธิในการมีปราสาทของตัวเองในโลกดิจิตอล เพราะการที่รัฐบาลต้องการ "backdoor" มันก็เหมือนกับการบังคับให้ทุกคนต้องสร้างประตูหลังไว้ให้รัฐบาลเข้ามาค้นบ้านได้ตลอดเวลานั่นเอง
หลังจาก "Internet Spring" ในปี 2011 ที่ผู้คนทั่วโลกตื่นตัวในเรื่องสิทธิเสรีภาพ Cypherpunk ก็กลับมาอีกครั้ง พวกเขาส่งเสริมเทคโนโลยีบล็อกเชนและสกุลเงินดิจิตอลที่เปิดโอกาสให้คนควบคุมข้อมูลตัวเองได้ เหมือนการสร้างระบบเศรษฐกิจและการปกครองของตัวเองโดยไม่ต้องพึ่งพาอำนาจจากส่วนกลาง
Cypherpunk ในวันนี้จึงไม่ใช่แค่กลุ่มคน แต่เป็นแนวคิด เป็นอุดมการณ์ที่เชื่อมั่นในพลังของเทคโนโลยีในการสร้างสังคมที่เสรีและเป็นธรรม พวกเขายังคงเป็นนักรบไซเบอร์ คอยปกป้องสิทธิของเราทุกคนในโลกดิจิตอล
Cypherpunk จึงไม่ใช่แค่เรื่องเท่ห์ๆ มันคือการต่อสู้เพื่อสิทธิและเสรีภาพในโลกดิจิตอลที่เราทุกคนควรจะใส่ใจ พวกเขาเป็นเหมือนผู้จุดประกายให้เกิดการปฏิวัติทางความคิด เปิดประตูสู่โลกที่ผู้คนมีอำนาจเหนือข้อมูลของตัวเอง
เสียงเพลงดาบของ Cypherpunk ยังคงดังก้องอยู่ในสมรภูมิดิจิตอล และเราทุกคนก็สามารถร่วมเป็นส่วนหนึ่งของการต่อสู้เพื่อเสรีภาพนี้ได้..
จูเลียน อัสซานจ์ ขบถไซเบอร์ผู้ท้าชนอำนาจรัฐ
“จูเลียน อัสซานจ์” (Julian Assange) เป็นบุคคลเบื้องหลังและเป็นบรรณาธิการใหญ่ของ WikiLeaks ด้วยวิสัยทัศน์ที่กล้าแกร่งและความเข้าใจในแนวคิดไซเฟอร์พังค์ (Cypherpunk) อัสซานจ์เคยเป็นหนึ่งในกลุ่มที่เข้าร่วมเครือข่าย “Cypherpunk mailing list” มาตั้งแต่ยุคแรกๆ และได้กลายมาเป็นผู้สนับสนุนสำคัญของแนวคิดนี้ในระดับโลก ผลงานของเขากับ WikiLeaks ถือเป็นการตอกย้ำจุดยืนของไซเฟอร์พังค์ที่ว่า..
"ความเป็นส่วนตัวสำหรับผู้ที่อ่อนแอ และความโปร่งใสสำหรับผู้มีอำนาจ"
ซึ่งตรงกับปรัชญาของเขาที่ต้องการผลักดันให้เกิดความโปร่งใสและการตรวจสอบสถาบันที่มีอำนาจ นอกจากจะเน้นให้เกิดเสรีภาพในการแสดงออกและความโปร่งใสในองค์กรที่มีอำนาจ อัสซานจ์ยังเป็นนักวิจารณ์ที่ช่ำชองต่อการที่รัฐและองค์กรต่างๆ ล่วงละเมิดความเป็นส่วนตัวของผู้คน
เขาเขียนโปรแกรมต่างๆ ที่สะท้อนแนวคิดไซเฟอร์พังค์ เช่น เครื่องมือสแกนพอร์ต TCP/IP ตัวแรกที่ชื่อว่า strobe.c ระบบไฟล์เข้ารหัสแบบ Rubberhose ที่ปฏิเสธการเปิดเผยข้อมูล และเขียนโค้ดต้นฉบับสำหรับ WikiLeaks เอง
ตั้งแต่เป็นวัยรุ่น.. อัสซานจ์สนใจเรื่องความปลอดภัยของระบบเครือข่ายและคอมพิวเตอร์ แม้ว่าบางกิจกรรมที่เขาทำจะถูกนับเป็นอาชญากรรมเมื่อกฎหมายเริ่มปราบปรามการแฮ็กมากขึ้นในภายหลัง เขายังเป็นนักเคลื่อนไหวและผู้ให้บริการอินเทอร์เน็ตในออสเตรเลียช่วงทศวรรษ 90 นอกจากนี้เขายังร่วมเขียนประวัติศาสตร์ของขบวนการแฮ็กเกอร์ระดับนานาชาติในหนังสือ “Underground” ร่วมกับ สุเลทท์ เดรย์ฟัส (Sulette Dreyfus) ซึ่งถูกนำมาดัดแปลงเป็นภาพยนตร์เรื่อง *”Underground: The Julian Assange Story”
จากการเดินทางที่ยาวนานในเส้นทางไซเฟอร์พังค์ อัสซานจ์ยังคงมุ่งมั่นในการสนับสนุนสิทธิของบุคคลและการเปิดโปงสถาบันที่ฉ้อฉล เพื่อความโปร่งใสที่มากขึ้นและเสรีภาพทางข้อมูลของทุกคนอย่างแท้จริง

เมื่อเสรีภาพถูกคุกคาม เราจะลุกขึ้นสู้ด้วย "รหัส"
ทุกคนเคยสงสัยกันไหมว่า.. โลกออนไลน์ที่เราใช้กันอยู่ทุกวันนี้มันเป็นดินแดนแห่งเสรีภาพอย่างที่เราคิดกันจริงๆ หรือเปล่า?
จริงอยู่ที่เราสามารถเข้าถึงข้อมูลข่าวสารได้มากมาย สามารถเชื่อมต่อกับผู้คนทั่วโลกได้อย่างง่ายดาย แต่ในขณะเดียวกัน เราก็กำลังถูกจับตามองจากเงามืด ถูกควบคุมโดยอำนาจที่เราเองก็ไม่รู้จักได้ง่ายๆ เช่นกัน
เมื่อปี 2012 จูเลียน อัสซานจ์ ได้ออกมาส่งเสียงเตือนภัยถึงพวกเราเอาไว้ในหนังสือชื่อว่า “Cypherpunks: Freedom and the Future of the Internet”
เขาเปรียบโลกอินเทอร์เน็ตเป็นเหมือนอาณาจักรแห่งความคิด เป็นโลกเสมือนที่เราทุกคนสามารถเข้ามาแลกเปลี่ยนความคิดเห็น แสดงออกได้อย่างอิสระ แต่โลกเสมือนที่ว่านี้ก็ยังคงถูกผูกติดเข้ากับโลกความเป็นจริง มันมีโครงสร้างพื้นฐานเป็นสายเคเบิลใยแก้วนำแสง ดาวเทียมและเซิร์ฟเวอร์ ซึ่งสิ่งเหล่านี้ล้วนถูกควบคุมโดยรัฐบาลและองค์กรที่มีอำนาจ
รัฐบาลเหล่านี้ใช้ประโยชน์จากการควบคุมโครงสร้างพื้นฐาน เพื่อเข้ามาสอดแนม เก็บข้อมูลและควบคุมการไหลเวียนของข้อมูลในโลกออนไลน์ พวกเขาแอบดูทุก “faits et gestes” ของเรา (เป็นสำนวนภาษาฝรั่งเศส ที่หมายถึง ทุกการกระทำ) ทุกเว็บไซต์ที่เราเข้า ทุกข้อความที่เราส่ง ทุกความคิดที่เราค้นหา แล้วนำข้อมูลเหล่านั้นไปสร้างคลังข้อมูลขนาดมหึมา เพื่อนำมาวิเคราะห์และใช้ประโยชน์ในทางที่เราคาดไม่ถึง ไม่ว่าจะเป็นการเริ่มสงคราม ควบคุมสื่อ หรือแม้แต่การสร้างความได้เปรียบทางการค้า
ฟังดูน่ากลัวใช่ไหมล่ะ?
แต่ จูเลียน อัสซานจ์ ก็ไม่ได้ทิ้งพวกเราเอาไว้กับความสิ้นหวัง เขายังมอบความหวังเล็กๆ ให้กับเรา นั่นก็คือ 'การเข้ารหัส' เขาเปรียบการเข้ารหัสเป็นเหมือนดั่งอาวุธ เป็นเครื่องมือที่ช่วยให้เราสามารถปกป้องความเป็นส่วนตัว และต่อสู้กับอำนาจที่พยายามจะควบคุมพวกเราได้
การเข้ารหัสเป็นเหมือนกับเกราะป้องกัน ที่จะช่วยให้ข้อมูลของเราปลอดภัยจากการสอดแนม แม้ว่ารัฐบาลจะมีอำนาจมากแค่ไหน ก็ไม่สามารถฝ่าด่านการเข้ารหัสที่แข็งแกร่งเข้ามาได้ง่ายๆ มันเหมือนกับการแก้ปัญหาคณิตศาสตร์ที่ซับซ้อนที่ต้องใช้เวลาและทรัพยากรมหาศาลถึงจะหาคำตอบได้
ดังนั้น.. ถ้าเราอยากจะรักษาเสรีภาพในโลกออนไลน์เอาไว้ เราต้องเรียนรู้ที่จะใช้อาวุธนี้ เราต้องเข้าใจหลักการของการเข้ารหัส การปกป้องความปลอดภัยและความเป็นส่วนตัวทางไซเบอร์ (Cyber Security & Privacy) และนำมันมาใช้ในการปกป้องข้อมูลของเรา เพื่อไม่ให้ตกเป็นเหยื่อของการสอดแนมและการควบคุมจากอำนาจในเงามืด
นี่คือเสียงกระซิบเตือนที่เราไม่ควรมองข้าม เพราะอนาคตของโลกออนไลน์และอนาคตของอารยธรรมมนุษย์ ขึ้นอยู่กับการตัดสินใจของพวกเรา
คุณจะเลือกอยู่ฝั่งไหน?
ฝั่งของผู้ที่ถูกควบคุม.. หรือฝั่งของผู้ที่จะต่อสู้เพื่อเสรีภาพ?
บทนำในหนังสือของ จูเลียน อัสซานจ์ "Introduction: A call to cryptographic arms" เขาได้เริ่มต้นด้วยคำเตือนที่แสดงให้เห็นถึงความเสี่ยงอันมหาศาลที่โลกกำลังเผชิญ
"นี่ไม่ใช่คำประกาศหรอกนะเพื่อนๆ แต่มันเป็นคำเตือน!"
ประโยคเปิดของบทนำช่างทรงพลังและน่าสนใจ มันกระตุ้นให้เราตื่นตัวและตั้งคำถามกับสิ่งที่เรามักมองข้าม อัสซานจ์กำลังบอกเราว่าโลกกำลังเปลี่ยนแปลงอย่างรวดเร็วและกำลังมุ่งหน้าสู่ยุคมืดแบบใหม่ ยุคที่รัฐบาลทั่วโลกจับมือกันควบคุมทุกสิ่งทุกอย่าง
"การเปลี่ยนแปลงนี้เกิดขึ้นอย่างเงียบเชียบ เพราะคนที่รู้เรื่องก็คือคนที่ทำงานในอุตสาหกรรมการสอดแนมทั่วโลก พวกเขาไม่มีเหตุผลที่จะออกมาพูดอะไรให้เราฟัง"
การเปลี่ยนแปลงนี้เกิดขึ้นราวกับเงาที่กำลังคืบคลานเข้ามา คนทั่วไปไม่ค่อยรู้เรื่องเพราะข้อมูลถูกปกปิดเป็นความลับ มันช่างซับซ้อนและมีขนาดใหญ่โตมโหฬาร แต่สิ่งที่น่าตกใจที่สุดก็คือ อินเทอร์เน็ต เครื่องมือที่เราใช้ติดต่อสื่อสาร ค้นคว้าหาความรู้ และสร้างสรรค์สิ่งต่างๆ กำลังกลายเป็นเครื่องมือสร้างเผด็จการที่น่ากลัวที่สุดเท่าที่เคยมีมา มันเป็นภัยคุกคามต่ออารยธรรมของมนุษยชาติเลยทีเดียว
ถ้าปล่อยให้เป็นแบบนี้ต่อไป อีกไม่กี่ปีโลกของเราจะกลายเป็นสังคมที่รัฐคอยจับตามองในทุกฝีก้าว ทุกๆ การกระทำจะไม่มีความเป็นส่วนตัว ไม่มีเสรีภาพ หลบหนีกันแทบไม่ได้เลย (ยกเว้นพวกที่มีทักษะขั้นเทพจริงๆ)
และอันที่จริงตอนนี้.. เราอาจจะอยู่ในสังคมแบบนั้นกันแล้วก็ได้..
หลายคนพยายามอธิบายว่าอินเทอร์เน็ตจะส่งผลต่ออารยธรรมโลกยังไง แต่สำหรับอัสซานจ์ เขาบอกว่าพวกนั้นคิดผิด เพราะพวกเขาไม่เคยสัมผัสกับศัตรูจริงๆ ไม่เคยเห็นภาพรวมทั้งหมด ประโยคสุดท้ายของวรรคแรกนี้ได้ทิ้งบางอย่างๆ ไว้ให้เราได้ขบคิดต่อ..
"ไม่มีคำอธิบายใดจะยังคงอยู่ได้หลังจากเผชิญหน้ากับศัตรู.. และเราก็ได้พบกับศัตรูแล้ว"
มันเหมือนเป็นการท้าทายให้เราเปิดตา-เปิดใจและมองหาความจริงด้วยตัวเราเอง อย่าเพิ่งเชื่ออะไรง่ายๆ เราต้องตั้งคำถาม ต้องหาข้อมูลและต้องตื่นตัวอยู่เสมอ เพราะโลกกำลังเปลี่ยนแปลงและเราต้องพร้อมรับมือกับสิ่งที่จะเกิดขึ้น มันทำให้เกิดคำถามตามมามากมาย เช่น..
รัฐบาลทั่วโลกกำลังจับมือกันควบคุมทุกอย่างจริงๆ หรือ? มีหลักฐานอะไรบ้าง? อินเทอร์เน็ตกำลังกลายเป็นเครื่องมือสร้างเผด็จการได้อย่างไร? เราจะป้องกันตัวเองจากการถูกสอดแนมได้อย่างไร? เราจะรักษาเสรีภาพในโลกดิจิทัลได้อย่างไร? ฯลฯ
นอกจากนี้ อัสซานจ์ยังอธิบายถึงการต่อสู้ของ WikiLeaks กับรัฐบาลต่างๆ โดยระบุว่า "ในช่วง 6 ปีที่ผ่านมา WikiLeaks ปะทะกับรัฐบาลที่มีอำนาจเกือบทุกแห่ง" แสดงให้เห็นว่าการต่อสู้นี้ไม่ใช่เรื่องง่าย มันคือการต่อสู้ที่ดุเดือด ยาวนาน และเต็มไปด้วยอันตราย ลองนึกภาพตามเรื่องราวเหล่านี้ดู..
WikiLeaks เปิดโปงเอกสารลับทางทหารและทางการทูตมากมายที่เผยให้เห็นด้านมืดของรัฐบาล ทั้งการทุจริต การละเมิดสิทธิมนุษยชน และการกระทำที่ผิดกฎหมายอื่นๆ เอกสารเหล่านี้ทำให้รัฐบาลหลายแห่งต้องเสียหน้า และพยายามทุกวิถีทางเพื่อจะปิดปาก WikiLeaks
อัสซานจ์และทีมงานของเขาถูกตามล่าตัวจากหลายประเทศ เขาต้องลี้ภัยอยู่ในสถานทูตเอกวาดอร์ในลอนดอนนานถึง 7 ปี เพื่อหลบหนีการส่งผู้ร้ายข้ามแดนไปยังสหรัฐอเมริกาที่เขาถูกตั้งข้อหาจารกรรม นี่แสดงให้เห็นว่ารัฐบาลเกรงกลัวอิทธิพลของ WikiLeaks มากแค่ไหน
WikiLeaks ถูกโจมตีทางไซเบอร์อย่างต่อเนื่อง ทั้งจากกลุ่มแฮกเกอร์ที่รัฐบาลหนุนหลังและจากบริษัทเอกชน เพื่อพยายามปิดเว็บไซต์และขัดขวางการทำงานของพวกเขา
WikiLeaks ถูกกดดันจากบริษัททางการเงิน เช่น Visa, Mastercard, Paypal ให้หยุดรับเงินบริจาค นี่เป็นอีกวิธีหนึ่งที่รัฐบาลพยายามตัดท่อน้ำเลี้ยง เพื่อบีบให้ WikiLeaks ต้องปิดตัวลง
การต่อสู้ของ WikiLeaks แสดงให้เห็นว่า รัฐบาลทั่วโลกกำลังพยายามปกปิดความจริง และปราบปรามผู้ที่กล้าเปิดโปงความลับ นี่คือสาเหตุที่อัสซานจ์เรียกร้องให้เราตื่นตัวและลุกขึ้นมาต่อสู้เพื่อปกป้องเสรีภาพของเรา
อัสซานจ์บอกว่า..
"การเข้ารหัสข้อมูลนั้นง่ายกว่าการถอดรหัส"
ตามมุมมองของเขา การเข้ารหัสไม่เพียงแต่เป็นเครื่องมือในการปกป้องข้อมูลเท่านั้น แต่ยังเป็นวิธีการที่จะปกป้องอำนาจทางเสรีภาพส่วนบุคคลและอิสรภาพทางความคิด และด้วยคุณสมบัตินี้ เขามองว่ามันจะเป็นกุญแจสำคัญในการสร้างโลกใหม่ที่ไม่ถูกรัฐบาลครอบงำ
รัฐบาลทั่วโลกทุ่มเงินมหาศาลเพื่อพัฒนาเทคโนโลยีในการถอดรหัส พวกเขาอยากรู้ว่าเรากำลังทำอะไร คิดอะไรและพูดคุยอะไรกัน พวกเขากลัวการสูญเสียอำนาจ และกลัวว่าประชาชนจะลุกขึ้นมาต่อต้าน
แต่ใสขณะเดียวกันนักพัฒนาซอฟต์แวร์ทั่วโลกก็พัฒนาเทคโนโลยีการเข้ารหัสให้แข็งแกร่งขึ้นเรื่อยๆ มันเหมือนเป็นการแข่งขันกันระหว่างหอกกับโล่ ยิ่งรัฐบาลพยายามถอดรหัส นักพัฒนาก็ยิ่งสร้างโล่ที่แข็งแกร่งขึ้น
การเข้ารหัสช่วยให้เราสามารถสื่อสารกันได้อย่างปลอดภัย ไม่ว่าจะเป็นการส่งอีเมล การคุยโทรศัพท์ หรือการทำธุรกรรมทางการเงิน รัฐบาลจะไม่สามารถแอบดูหรือดักฟังข้อมูลของเราได้ มันคือเรื่องของอำนาจ มันให้อำนาจแก่ประชาชน ในการปกป้องความเป็นส่วนตัว และต่อต้านการสอดส่องจากรัฐบาล
อัสซานจ์เปรียบเทียบเอาไว้ว่า "จักรวาลเชื่อในการเข้ารหัส" เหมือนกับที่จักรวาลเชื่อในเกลือ, ทะเล หรือดวงดาว มันเป็นกฎของธรรมชาติที่ทำให้เรามีเครื่องมือในการปกป้องตัวเอง
จากมุมมองของอัสซานจ์ การเข้ารหัสเป็นการต่อสู้อย่างเงียบๆ ที่สามารถเปลี่ยนแปลงวิธีการที่รัฐใช้อำนาจและควบคุมข้อมูลได้ นับเป็นการประกาศอิสรภาพจากการกำกับดูแลที่รุนแรงของรัฐ
"ด้วยวิธีนี้.. เราจึงประกาศอิสรภาพ"
คำพูดของอัสซานจ์ฟังมันดูยิ่งใหญ่.. แต่มันไม่ใช่การประกาศอิสรภาพแบบที่เราคุ้นเคยกัน มันไม่ใช่การลงสู่ถนนเพื่อเดินขบวนประท้วงหรือการทำสงคราม แต่มันคือการต่อต้านอย่างเงียบเชียบโดยใช้ "การเข้ารหัส" มาเป็นอาวุธ

WikiLeaks ตกเป็นเป้าหมายการเล่นงานของผู้มีอำนาจ
WikiLeaks ต้องเผชิญกับความพยายามในการดำเนินคดีกับองค์กรและบุคคลที่เกี่ยวข้องอยู่หลายครั้ง ซึ่งมักถูกกล่าวถึงในบริบทของเหตุการณ์สำคัญๆ องค์กรนี้ยึดมั่นในพันธกิจที่จะเปิดเผยข้อมูลจากผู้เปิดโปงให้กับสาธารณชนรับทราบ พร้อมป้องกันจากการโจมตีทางกฎหมายและการเมืองที่ตามมาอย่างหลีกเลี่ยงไม่ได้ องค์กรทำหน้าที่เป็นเสมือนผู้เผยแพร่รายสุดท้ายที่ต้องอดทนต่อแรงกดดันจากรัฐและองค์กรทรงอำนาจต่างๆ ที่ต้องการปราบปรามการตีพิมพ์ของพวกเขา
ในปี 2010 WikiLeaks ได้เปิดเผยข้อมูลอื้อฉาวหลายครั้ง ทำให้ได้รับความสนใจจากทั่วโลก การตีพิมพ์ในครั้งนั้นเป็นที่รู้จักกันดีในชื่อ “Collateral Murder”, “War Logs” และ “Cablegate” ซึ่งได้เผยให้เห็นถึงการใช้อำนาจในทางที่ผิดและความลับที่ซ่อนเร้นภายในกองทัพและรัฐบาลสหรัฐฯ
หลังจากนั้นชีวิตของอัสซานจ์ และ WikiLeaks ก็ไม่เคยได้สงบสุขกันอีกเลย พวกเขาต้องเผชิญกับการโจมตีและการข่มขู่จากผู้มีอำนาจ การตอบสนองของรัฐบาลสหรัฐฯ และพันธมิตรนั้นเป็นความพยายามที่ต่อเนื่องเพื่อทำลาย WikiLeaks อย่างถึงที่สุด
การตีพิมพ์เหล่านี้นำไปสู่การตั้งคณะลูกขุนใหญ่ (Grand Jury) เพื่อสอบสวน จูเลียน อัสซานจ์ และทีมงานที่เกี่ยวข้องกับ WikiLeaks คณะลูกขุนนี้ถูกจัดตั้งขึ้นที่เมืองอเล็กซานเดรีย รัฐเวอร์จิเนีย ภายใต้การสนับสนุนของกระทรวงยุติธรรมและ FBI เพื่อตรวจสอบความเป็นไปได้ในการตั้งข้อหาละเมิด รวมถึงข้อหาสมคบคิดภายใต้กฎหมาย Espionage Act ปี 1917 (พระราชบัญญัติจารกรรมปี 1917) นี่เป็นการสืบสวนที่ใหญ่โตและรุนแรงมาก ในการดำเนินคดีกับนักข่าวที่ "ตั้งใจเผยแพร่ข้อมูลที่รั่วไหล" โดยไม่มีทนายฝ่ายจำเลยหรือผู้พิพากษาเข้าร่วมด้วยเลย เป้าหมายคือการปิดปากและทำลาย WikiLeaks
การสอบสวนเกี่ยวกับ WikiLeaks ยังคงดำเนินต่อไป ผู้คนจำนวนมากถูกบังคับไปให้การทางกฎหมาย กระบวนการพิจารณาคดีของ แบรดลีย์ แมนนิ่ง (Bradley Manning) ทหารที่ถูกกล่าวหาว่าให้ข้อมูลกับ WikiLeaks เผยให้เห็นเอกสารสอบสวนของ FBI ที่ยาวมากถึง 42,100 หน้า โดยในนั้นมี 8,000 หน้าที่กล่าวถึงแมนนิ่ง
แมนนิ่งถูกกักขังโดยไม่ได้รับการพิจารณาคดีเป็นเวลามากกว่า 880 วัน และได้รับการปฏิบัติที่โหดร้าย ซึ่งอาจถึงขั้นทรมานอย่างโหดเหี้ยม รายงานพิเศษจากทาง UN โดย ฮวน เมนเดส (Juan Mendez) ได้ประนามอย่างเป็นทางการว่า แบรดลีย์ แมนนิ่ง นั้นได้รับการปฏิบัติที่โหดร้ายและไร้มนุษยธรรมเป็นอย่างที่สุด
หลังจากที่ WikiLeaks ได้เปิดเผยข้อมูลสำคัญจาก Cablegate ไปแล้ว การโจมตีจากรัฐบาลสหรัฐฯ และกลุ่มพันธมิตรก็เพิ่มความเข้มข้นขึ้นจนถึงจุดที่นักการเมืองบางรายเรียกร้องให้มีการลอบสังหาร จูเลียน อัสซานจ์ โดยใช้โดรน พวกเขากล่าวหาว่า WikiLeaks เป็น "องค์กรก่อการร้าย" และเรียกอัสซานจ์ว่าเป็น "ผู้ก่อการร้ายไฮเทค" และ "ศัตรูผู้ใช้การสู้รบทางไซเบอร์"
เพนตากอนได้ตั้ง "WikiLeaks Task Force" หรือ WTF ขึ้นมาโดยมีสมาชิก 120 คน เพื่อจัดการกับ WikiLeaks อย่างเต็มที่ อีกทั้ง FBI, CIA และกระทรวงต่างประเทศสหรัฐฯ ก็ได้ตั้งหน่วยเฉพาะกิจเพื่อจัดการกับ WikiLeaks ด้วยเช่นกัน
เมื่อรัฐบาลสหรัฐฯ ไม่สามารถหยุด WikiLeaks ด้วยวิธีการอื่นได้ พวกเขาจึงเริ่มทำการเซ็นเซอร์โดยตรง โดยสั่งให้ผู้ให้บริการอินเทอร์เน็ตปิดกั้นการให้บริการแก่ WikiLeaks.org ในเดือนธันวาคม 2010 จากนั้น Amazon ได้ลบ WikiLeaks ออกจากเซิร์ฟเวอร์ของตน และวันถัดมา ระบบ DNS ก็ถูกขัดขวางไม่ให้เชื่อมต่อไปยังโดเมน WikiLeaks.org
อย่างไรก็ตาม ด้วยความพยายามในการ "mass-mirroring" ผู้สนับสนุนหลายพันคนได้คัดลอกเว็บไซต์แล้วเผยแพร่ผ่านเครือข่ายของตนเอง ทำให้เว็บไซต์ยังคงออนไลน์ต่อไปได้
[ Mass-mirroring หมายถึง การที่กลุ่มคนจำนวนมากคัดลอกเนื้อหาเว็บไซต์หรือข้อมูลใดๆ แล้วจัดเก็บไว้ในเซิร์ฟเวอร์ของตัวเองหรือบริการโฮสต์อื่นๆ เพื่อให้แน่ใจว่าข้อมูลเหล่านั้นจะไม่หายไปหากแหล่งข้อมูลต้นทางถูกปิดกั้นหรือถูกปิดตัวลง ]
การโจมตีนี้ยังไม่หยุดเพียงแค่การเซ็นเซอร์เท่านั้น แต่ยังมีการคว่ำบาตรทางการเงินด้วยธนาคารและสถาบันการเงินหลักอย่าง VISA, MasterCard, PayPal และ Bank of America ซึ่งปิดกั้นการบริจาคและการโอนเงินไปยัง WikiLeaks สิ่งนี้เรียกว่าเป็น "การปิดล้อมทางการเงิน" ซึ่งถูกกระทำโดยไม่มีขั้นตอนทางกฎหมายและยังคงดำเนินต่อไปจนถึงปัจจุบัน
จุดสำคัญอีกอย่างหนึ่งคือการคุกคาม เจคอบ แอปเปิลบาม (Jacob Appelbaum) ผู้สนับสนุน WikiLeaks และ เจเรมี่ ซิมเมอร์แมน (Jérémie Zimmermann) ซึ่งถูกเจ้าหน้าที่กดดันและสืบสวนซ้ำๆ เมื่อข้ามพรมแดนหรือเดินทางภายในสหรัฐฯ โดยไม่มีการตั้งข้อหาใดๆ
การที่ Twitter ถูกบังคับให้เปิดเผยข้อมูลของผู้ใช้งานที่เกี่ยวข้องกับ WikiLeaks โดยไม่ได้มีหมายค้นอย่างเป็นทางการทำให้เกิดกรณี "Twitter Subpoena Case" ซึ่งกลายเป็นหัวข้อวิพากษ์วิจารณ์กันอย่างกว้างขวางว่ารัฐบาลกำลังละเมิดสิทธิ์ความเป็นส่วนตัวของบุคคลมากแค่ไหน คดีนี้ยังดำเนินอยู่ในชั้นศาลและยังมีการเปิดเผยภายหลังว่า Sonic.net และ Google ก็ได้รับคำสั่งให้ส่งมอบข้อมูลของ แอปเปิลบาม เช่นกัน แม้ว่าจะมีการต่อสู้กันในศาลอยู่ก็ตาม..
นี่เป็นเพียงเรื่องราวบางส่วนที่แสดงให้เห็นถึงความพยายามในการปกป้องอำนาจในการสอดแนมของตนโดยเหล่าผู้มีอำนาจ.. เราไม่เคยรู้รายละเอียดที่ชัดเจนในเรื่องราวเหล่านี้กันมาก่อน..
มันเพราะอะไรล่ะ..
สนามรบแห่งเสรีภาพและการควบคุม
จูเลียน อัสซานจ์ให้ความเห็นถึงสถานการณ์ปัจจุบันที่โลกของเราเผชิญกับความขัดแย้งระหว่างการสื่อสารที่และการเฝ้าระวังที่เพิ่มขึ้น ผ่านบทสนทนาของเขากับผองเพื่อนภายในหนังสือ เขาชี้ว่าไซเฟอร์พังค์เริ่มตระหนักถึงความเป็นไปได้ที่รัฐจะใช้การเฝ้าระวังควบคู่ไปกับการสื่อสารผ่านอินเทอร์เน็ตตั้งแต่ช่วงทศวรรษ 1990
"ตอนนี้เรามีการสื่อสารและการเฝ้าระวังที่มากขึ้น" การเฝ้าระวังมากขึ้นหมายถึงการที่รัฐและองค์กรต่างๆ สามารถจับตามองชีวิตผู้คนได้อย่างลึกซึ้ง นั่นก็เพราะ.. "ผู้คนต่างแสดงไอเดียทางการเมือง การสื่อสารกับครอบครัวและมิตรภาพต่างๆ ไว้บนอินเทอร์เน็ต"
ในขณะเดียวกัน โลกไซเบอร์กลับกลายเป็นพื้นที่ที่รัฐบาลและองค์กรต่างๆ พยายามเข้ามาควบคุมข้อมูลเพื่อชะลอความก้าวหน้าของการเปลี่ยนแปลงและรักษาอำนาจของตนไว้ ตามที่แอนดี้เพื่อนของอัสซานจ์ได้เล่าว่า..
"พวกเขามองอินเทอร์เน็ตเป็นเหมือนโรคร้ายที่กัดกร่อนความสามารถในการกำหนดความเป็นจริงของพวกเขา"
แม้ว่ารัฐบาลจะเพิ่มการเฝ้าระวัง แต่อัสซานจ์ก็ชี้ให้เห็นว่า “การสื่อสารจำนวนมากทำให้ผู้คนหลายล้านสามารถบรรลุฉันทามติได้อย่างรวดเร็ว” ซึ่งสามารถก่อให้เกิดความเคลื่อนไหวที่ประสบความสำเร็จได้ เช่น การประท้วงในปี 2008 ที่กรุงไคโรผ่านทาง Facebook และการปฏิวัติในอียิปต์ปี 2011 ที่มีการเตือนในคู่มือว่า "อย่าใช้ Twitter หรือ Facebook" แต่ในขณะเดียวกัน ถ้าการปฏิวัติไม่ประสบความสำเร็จ รัฐก็สามารถใช้โครงสร้างพื้นฐานเดียวกันนี้เพื่อแกะรอยและแยกผู้เข้าร่วมออกจากกันได้
เจเรมี ซิมเมอร์แมน เน้นให้เห็นความยากที่จะแยกแยะการเฝ้าระวังจากการควบคุมโดยเฉพาะกับอุปกรณ์ดิจิทัลที่ "มีการควบคุมฝังอยู่ในเทคโนโลยี" เช่น ระบบปฏิบัติการที่มีจุดประสงค์ในการจำกัดการใช้เพื่อความปลอดภัยในบางกรณี
ในขณะที่ทุกคนมีความเห็นตรงกันว่าเทคโนโลยีควรถูกเปิดเผยและมีอิสระมากขึ้น จาค็อบ แอปเปิลบาม ก็ได้เน้นย้ำถึงความสำคัญของการเข้าถึง "พิมพ์เขียวของระบบที่อยู่เบื้องหลังชีวิตของเรา" เพื่อให้เข้าใจและปรับปรุงการใช้งานอย่างยั่งยืน และท้ายที่สุด การเข้าใจความซับซ้อนของการสื่อสารและการเฝ้าระวังในยุคนี้ จำเป็นต้องทำความเข้าใจวิธีการควบคุมข้อมูลที่เกิดขึ้นตามมา เพื่อนำไปสู่ระบบที่เปิดกว้างและปลอดภัยมากยิ่งขึ้น
ทั้งหมดนี้เป็นเพียงการเรียบเรียงและพรีวิวคร่าวๆ ถึงเนื้อหาบางส่วนจากในหนังสือ ที่พอผมได้อ่านแล้วก็เมามันส์จนอยากจะบอกต่อ.. ครั้นจะเขียนออกมาทั้งหมด เล่าทั้งหมดในภาษาของตัวเองแบบนี้ก็คงจะไม่ไหวนะครับ..
ก้าวเข้าสู่โลกของ Cypherpunk
บางคนอาจจะบอกว่าอินเทอร์เน็ตเป็นเหมือนห้องสมุดขนาดใหญ่ที่มีข้อมูลทุกอย่างบนโลก บางคนอาจจะบอกว่ามันเหมือนตลาดที่มีทุกสิ่งทุกอย่างให้เลือกซื้อ แต่สำหรับ จูเลียน อัสซานจ์ เขาบอกว่า อินเทอร์เน็ตมันเหมือน "สนามรบ" ที่เสรีภาพกับการควบคุมกำลังต่อสู้กันอย่างดุเดือด
และถ้าคุณอยากรู้จักกับ อัสซานจ์ และ Cypherpunk ให้มากยิ่งขึ้น อยากเข้าใจแนวคิดและอุดมการณ์ของพวกเขา อยากรู้ว่าพวกเขาต่อสู้กับอำนาจรัฐและบริษัทใหญ่ๆ อย่างไร ผมขอแนะนำให้คุณไปอ่านเพิ่มเติมจากหนังสือ "Cypherpunks: Freedom and the Future of the Internet" โดย จูเลียน อัสซานจ์

คุณจะได้เรียนรู้ประวัติศาสตร์ของการเข้ารหัส เทคโนโลยีต่างๆ ที่ Cypherpunk พัฒนาขึ้น และวิธีที่พวกเขาใช้ เพื่อต่อสู้เพื่อเสรีภาพในโลกออนไลน์ เนื้อหาในหนังสือคร่าวๆ ก็จะประมาณนี้..
อัสซานจ์ได้อธิบายถึงความขัดแย้งระหว่างการสื่อสารอย่างเสรีและการเฝ้าระวังที่เข้มข้นมากขึ้นจากรัฐและองค์กรต่างๆ ซึ่งทั้งสองสิ่งนี้ดำเนินไปพร้อมๆ กันในโลกดิจิทัลปัจจุบัน ความเป็นส่วนตัวของบุคคลและการแสดงออกทางความคิดถูกลดทอนลงเรื่อยๆ เมื่อรัฐได้เข้าควบคุมอินเทอร์เน็ตในรูปแบบต่างๆ
หนังสือจะชี้ให้เห็นว่ารัฐบาลทั่วโลกพยายามชะลอกระบวนการเปลี่ยนแปลงทางสังคมโดยใช้การควบคุมข้อมูล ทำให้สาธารณชนไม่สามารถเข้าใจปัญหาที่เกิดขึ้นได้อย่างชัดเจน รัฐบาลประกาศให้ข้อมูลเป็นความลับเพื่อควบคุมกระบวนการและปกป้องอำนาจของตน รวมไปถึงแนวคิดที่เป็นหัวใจสำคัญของปรัชญาไซเฟอร์พังค์ ซึ่งมุ่งให้ความสำคัญกับการปกป้องความเป็นส่วนตัวของคนทั่วไป ในขณะเดียวกันก็ต้องการให้ผู้มีอำนาจมีความโปร่งใสและต้องรับผิดชอบต่อการกระทำของตน
หนังสือกล่าวถึงวิธีการที่รัฐและองค์กรต่างๆ ใช้เทคโนโลยีเพื่อสร้างการควบคุมผ่านการเฝ้าระวัง รวมถึงการติดตามพฤติกรรมออนไลน์ การบันทึกข้อมูลส่วนตัว และการใช้ซอฟต์แวร์ที่ออกแบบมาเพื่อป้องกันการดัดแปลงหรือควบคุมฟังก์ชันต่างๆ ซึ่งเป็นภัยต่อเสรีภาพทางดิจิทัลของพวกเรา
อัสซานจ์จะเน้นถึงความสำคัญของการเข้ารหัสว่ามันเป็นเครื่องมือที่มีประสิทธิภาพในการต่อสู้กับการเฝ้าระวังและควบคุมข้อมูลจากรัฐ เขาชี้ให้เห็นว่า "การเข้ารหัสข้อมูลนั้นง่ายกว่าการถอดรหัส" ซึ่งทำให้มันเป็นวิธีที่ทรงพลังในการปกป้องข้อมูล
หนังสือยังได้สำรวจว่าการเข้าถึงและการควบคุมข้อมูลนั้นส่งผลต่อความสามารถของบุคคลในการเข้าร่วมในกระบวนการประชาธิปไตยได้อย่างไร การมีเทคโนโลยีที่เป็นอิสระและเสรีเป็นสิ่งสำคัญในการสร้างโลกไซเบอร์ที่เปิดกว้างสำหรับทุกคน
องค์กรเทคโนโลยีต่างๆ ไม่เพียงแต่ช่วยรัฐในการเฝ้าระวังผู้ใช้เท่านั้น แต่ยังแสวงหาผลประโยชน์จากข้อมูลของผู้ใช้เพื่อสร้างรายได้ อัสซานจ์เตือนถึงการร่วมมือระหว่างรัฐกับบริษัทเทคโนโลยีที่อาจละเมิดสิทธิ์ของผู้คนได้
นอกจากนี้.. อัสซานจ์และผู้ร่วมอภิปรายในหนังสือมุ่งหวังให้ผู้อ่านเข้าใจถึงแนวทางที่จะสร้างอินเทอร์เน็ตที่เป็นเสรีและยั่งยืนมากยิ่งขึ้น พวกเขาสนับสนุนการศึกษาเกี่ยวกับไซเฟอร์พังค์ การปกป้องข้อมูลและการใช้งานซอฟต์แวร์เสรีเพื่อปกป้องเสรีภาพในยุคดิจิทัล
เสียงเพลงดาบแห่งเสรีภาพ จะช่วยจุดประกายแห่งการตื่นรู้
บทเพลงของ Cypherpunk ดังขึ้นท่ามกลางความเงียบงัน เป็นเสียงสะท้อนของจิตวิญญาณที่โหยหาอิสรภาพในโลกดิจิตอลที่กำลังถูกครอบงำ พวกเขาคือกลุ่มคนที่กล้าตั้งคำถาม กล้าท้าทาย และกล้าที่จะต่อสู้เพื่อสิ่งที่ถูกต้อง
การศึกษาเรื่องราวของคนพันธุ์พังค์สำหรับเรา.. มันคือการเรียนรู้ที่จะเป็นมนุษย์ที่สมบูรณ์ มนุษย์ที่มีทั้งความรู้ ความกล้าและความรับผิดชอบ มนุษย์ที่ไม่ยอมจำนนต่ออำนาจที่ไม่เป็นธรรม และมนุษย์ที่พร้อมจะลุกขึ้นมาปกป้องสิทธิและเสรีภาพของตนเองและผู้อื่น
ในโลกที่เทคโนโลยีก้าวล้ำและข้อมูลกลายเป็นขุมทรัพย์ เราต้องไม่ลืมว่า “เราคือเจ้าของข้อมูล” “เราคือผู้กำหนดชะตาชีวิตของเราเอง” เราไม่ใช่ "สินค้า" หรือ "ข้อมูล" ที่รัฐบาลหรือบริษัทใหญ่ๆ จะนำไปใช้ประโยชน์ได้ตามอำเภอใจ
Cypherpunk สอนให้เรารู้ว่าการต่อสู้เพื่อเสรีภาพไม่ใช่เรื่องของคนกลุ่มใดกลุ่มหนึ่ง แต่มันเป็นเรื่องของพวกเราทุกคน เราทุกคนมีสิทธิ์ที่จะมีชีวิตอยู่อย่างมีศักดิ์ศรี มีสิทธิ์ที่จะแสดงออก มีสิทธิ์ที่จะมีความเป็นส่วนตัว และมีสิทธิ์ที่จะกำหนดอนาคตของตัวเอง
เสียงเพลงดาบของ Cypherpunk ยังคงดังก้องอยู่เสมอ..
มันเป็นเสียงเรียกร้องให้พวกเราตื่นขึ้นจากภวังค์ของความสะดวกสบายและความเพลิดเพลิน บนโลกออนไลน์.. มันเป็นเสียงเตือนให้เราระวังภัยร้ายที่ซ่อนอยู่เบื้องหลังเทคโนโลยี และมันเป็นเสียงเชิญชวนให้เราร่วมกันสร้างโลกที่เสรีและเป็นธรรมสำหรับทุกคน
ดังนั้น จงลุกขึ้นมาจับดาบแห่ง "การเข้ารหัส" ของคุณ แล้วร่วมกันต่อสู้เพื่อเสรีภาพในโลกดิจิตอล
อย่าลืมว่า.. อนาคตไม่ได้ถูกกำหนดเอาไว้ล่วงหน้า แต่มันถูกสร้างขึ้น..
จากการกระทำของเราในวันนี้..
-
 @ 1c6b3be3:73f0ae6f
2024-05-05 09:25:20
@ 1c6b3be3:73f0ae6f
2024-05-05 09:25:20Léa se pencha sur son écran, les yeux rivés sur les lignes de code qui défilaient. Depuis des mois, elle travaillait sans relâche sur son projet de solution Layer-2 pour Bitcoin, déterminée à relever le défi de la mise à l'échelle. Avec le succès retentissant des Runes, le besoin de solutions de passage à l'échelle était plus criant que jamais.
Soudain, une main se posa sur son épaule. Léa sursauta et se retourna pour faire face à Maxime, un cryptographe chevronné qu'elle avait rencontré lors d'une conférence sur les innovations Bitcoin.
"Alors, comment avance ton projet ?" demanda Maxime avec un sourire bienveillant.
Léa soupira. "C'est un véritable défi. Les problèmes de congestion et de frais élevés sur le réseau Bitcoin sont de plus en plus préoccupants. Mais je suis convaincue que notre solution L2 pourra débloquer tout le potentiel de la blockchain."
Maxime hocha la tête. "Je n'en doute pas. Ton équipe a vraiment du talent. Mais fais attention, il y a aussi des gens qui voudraient profiter de cette situation."
Léa fronça les sourcils. "Que veux-tu dire ?"
"J'ai entendu parler d'un certain Émile, un hacker très doué qui aurait découvert une faille dans le système des Runes. Il prépare quelque chose, j'en suis persuadé."
Les yeux de Léa s'écarquillèrent. "C'est une catastrophe en puissance ! Il faut agir avant qu'il ne soit trop tard."
Maxime posa une main rassurante sur son bras. "Ne t'inquiète pas, je suis là pour t'aider. Ensemble, nous allons stopper Émile et sauver l'intégrité du réseau Bitcoin."
Les semaines qui suivirent furent intenses. Léa et Maxime travaillèrent d'arrache-pied pour renforcer la sécurité de leur solution L2 et traquer les moindres mouvements d'Émile. Leurs efforts payèrent lorsqu'ils découvrirent que le hacker prévoyait de lancer une attaque massive sur les Runes, dans le but de déstabiliser tout l'écosystème Bitcoin.
Le jour J, Léa et Maxime se tenaient prêts, leur solution L2 déployée et prête à entrer en action. Lorsque l'attaque d'Émile commença, leur système entra en jeu, absorbant les transactions et protégeant le réseau Bitcoin. Après des heures de lutte acharnée, Émile fut finalement neutralisé, et le réseau Bitcoin sortit renforcé de cette épreuve.
Léa, épuisée mais fière, se tourna vers Maxime. "Nous l'avons fait ! Notre solution a tenu bon et a permis de sauver Bitcoin."
Maxime lui sourit. "Je n'en ai jamais douté. Grâce à des gens comme toi, l'avenir de Bitcoin est assuré. L'heure de gloire des Layer-2 est arrivée !"
Ensemble, ils levèrent un verre à la victoire, conscients que ce n'était que le début d'une nouvelle ère pour la reine des cryptomonnaies.
-
 @ e771af0b:8e8ed66f
2023-11-28 03:49:11
@ e771af0b:8e8ed66f
2023-11-28 03:49:11The last 6 months has been full full of unexpected surprises, of the unpleasant variety. So it was welcomed news that
nostrwatchwas awarded a grant by OpenSats recently which has allowed me to revisit this project and build out my original vision, the one I had before nostr went vertical.The last month has been a bit of a joyride, in that I have met little friction meeting goals. For example I was able to rewrite
nostrwatch-jsin an evening, tests another evening and did most of the Typescript conversion in 30 minutes (thanks AI!)Here's a quick summary of the last month, I'm probably missing a handful of details, but these are the important bits.
- Went through all the new NIPs, prototyped and experimented
- Nearly completed a full rewrite of
nostrwatch-js, nownocap. Presently porting to Typescript. Still alpha, don’t use it. - Released
nostrawl, a wrapper fornostr-fetchthat has Queue adapters for persistent fetching. Nothing special, but needed to factor out the functionality from the legacy trawler and the requirements were general enough to make it a package. - Starting porting the nostr.watch trawler, cache layer and rest API, but much work is still needed there. Aiming to have the current infrastructure updated with new daemons by end of year.
- In concert with the cache layer testing, I ran some experiments by patching in a rough trend engine prototype from earlier this year and a novel outbox solution, both with promising results.
- Wrote a few small CLI tools to assist with developments, got acquainted with
ink, and reacquainted myself with wonderful world of ES Module conflicts.
The rest of this year will be mostly backend work, tests and data engineering. Early next year I will begin iterative development on a new GUI and a string of CLI tools.
Luckily, nostr.watch and it's underlying infrastructure, as abysmal as it is, hasn't completely sank. Traffic is much lower than the ATH but still hovering between 2-3k unique visitors a month. I can't express in words how happy I will be when I can put the legacy nostr.watch to rest.
Next update will include a bit more of the why and how, and where I am trying to get to with this project.
Until next time.
-
 @ d34e832d:383f78d0
2024-05-05 21:17:45
@ d34e832d:383f78d0
2024-05-05 21:17:45The decentralized nature of Nostr facilitates a network that is robust, user-driven, and significantly less prone to central points of failure, which plague conventional social platforms. Choosing the right relay server is critical to your experience on Nostr. Here, we explore how to select a Nostr relay server, delve into the public and paid relay dynamics, and offer insights on setting up your relay server.
Key Considerations When Choosing a Nostr Relay Server
The choice of a Nostr relay server should be guided by several important factors:
- Reliability: Opt for servers known for consistent uptime to ensure uninterrupted connectivity.
- Privacy: Select servers that prioritize privacy with strong encryption and policies against logging user data.
- Performance: Consider servers that provide low latency and high responsiveness.
- Community and Support: Choosing a relay server with a strong community and active developer presence can enhance the user experience due to regular updates and feature additions.
- Network Size: Servers with a broader network can facilitate better content discovery and user interaction.
- Cost: Analyze whether the relay server is free or requires a subscription, and align this with your budget.
- Compatibility: Ensure the relay server is compatible with your Nostr client application.
Understanding the Public Relay Challenge
While over 100 public relay servers are currently operational, such as those listed on Nostr relay finder, there's a notable challenge concerning spam due to the free nature of these servers:
"Public relays, while excellent for onboarding, face challenges with spam because there is no cost to post, making them targets for bots and spammers." -
Relay owners often employ reactive measures like blacklisting offending accounts, yet the efficacy can vary, requiring continuous vigilance.
The Benefits of Paid Relays
Paid relays offer a structured approach to using Nostr, potentially reducing spam due to the cost barrier:
- Enhanced Quality and Speed: Relays that charge a fee generally provide better performance and user experience.
- Reduced Spam: The entry cost dissuades most spammers, as their operations rely on high-volume, low-cost activities.
Where to Find Paid Relays
For those seeking a more controlled environment, several paid relays are available. These include:
Exploring Nostriches: A Dive into Paid Relays
In the expansive realm of decentralized networks like Nostr, the efficiency and reliability of relays are crucial for seamless communication and transaction processing. Paid relays serve as vital components in ensuring the smooth operation of these networks, offering enhanced performance and reliability compared to their free counterparts. Let's take a closer look at some prominent paid relays in the Nostr ecosystem:
1. Relay.nostriches.org
- Price: 421
- NPub Key: npub1vnmhd287pvxxk5w9mcycf23av24nscwk0da7rrfaa5wq4l8hsehs90ftlv
- Description: This relay provides a reliable and efficient connection for Nostr transactions, ensuring fast and secure communication between network participants.
2. Nostr.milou.lol
- Price: 1000
- NPub Key: npub1rvg76s0gz535txd9ypg2dfqv0x7a80ar6e096j3v343xdxyrt4ksmkxrck
- Description: Offering high-speed connectivity and robust performance, this relay is ideal for applications requiring low-latency communication and real-time transaction processing.
3. Bitcoiner.social
- Price: 1000
- NPub Key: npub1dxs2pygtfxsah77yuncsmu3ttqr274qr5g5zva3c7t5s3jtgy2xszsn4st
- Description: This relay specializes in facilitating transactions related to Bitcoin and other digital assets, providing a secure and reliable communication channel for Bitcoin enthusiasts.
4. Relay.nostr.nu
- Price: 2000
- NPub Key: npub1vvqnak4hz0u7vkv0vs5jp4ha0dt359cgvz4jj4y2ku85z0dtt6zq9pv3s8
- Description: With enhanced capacity and scalability, this relay is capable of handling a high volume of transactions, making it suitable for large-scale applications and platforms.
5. Relay.nostrati.com
- Price: 2000
- NPub Key: npub1qqqqqqqut3z3jeuxu70c85slaqq4f87unr3vymukmnhsdzjahntsfmctgs
- Description: This relay offers advanced security features and robust performance, making it an ideal choice for mission-critical applications and financial transactions.
6. Relay.nostrich.land
- Price: 2100
- NPub Key: npub1vj0wlergmkcs0sz7hfks2ywj555c2s87f40squ4sqcmqpr7897fqn6mfew
- Description: Providing a combination of speed, reliability, and security, this relay ensures smooth communication and transaction processing in the Nostr ecosystem.
7. Relay.orangepill.dev
- Price: 4500
- NPub Key: npub16jzr7npgp2a684pasnkhjf9j2e7hc9n0teefskulqmf42cqmt4uqwszk52
- Description: This high-performance relay offers enhanced security features and seamless integration capabilities, making it well-suited for demanding applications and enterprise use cases.
8. Eden.nostr.land
- Price: 5000
- NPub Key: npub16k7j4mwsqm8hakjl8x5ycrqmhx89lxkfwz2xxxcw75eav7sd8ztqy2rwdn
- Description: With its robust infrastructure and high availability, this relay ensures uninterrupted communication and transaction processing for applications operating in the Nostr ecosystem.
9. Nostr.inosta.cc
- Price: 5000
- NPub Key: npub1r34nhc6nqswancymk452f2frgn3ypvu77h4njr67n6ppyuls4ehs44gv0h
- Description: This relay offers reliable connectivity and comprehensive security features, making it a trusted choice for businesses and developers building applications on the Nostr platform.
10. Relay.nostr.com.au
- Price: 6969
- NPub Key: npub1qqqqqrre3jxkuyj3s4m59usdyvm0umgm0lpy6cqjtwpt649sdews5q3hw7
- Description: Providing exceptional performance and scalability, this relay is capable of handling the diverse needs of applications and platforms operating in the Nostr ecosystem.
Closing Thoughts
Paid relays play a crucial role in ensuring the reliability, security, and scalability of decentralized networks like Nostr. By offering enhanced performance and robust security features, these relays empower developers, businesses, and users to build and interact with applications with confidence. Explore the diverse range of paid relays available in the Nostr ecosystem and unlock the full potential of decentralized communication and transaction processing.
These relays often require contacting the relay operator directly to get access, where your public key will be whitelisted post-payment.
Setting Up Your Own Paid Relay
For those interested in contributing more actively to Nostr, setting up a paid relay can be both a community service and a potential business opportunity, especially when combined with a Lightning routing node. A comprehensive guide on starting your relay can be accessed from reputable sources like Guide for Strfry Setup.
Closing Thoughts
Choosing the right Nostr relay server is more than a technical decision—it’s about aligning with your communication needs and how you want your social media experiences to be shaped. Whether opting for public, paid, or setting up your relay, each choice offers different advantages and challenges. As the ecosystem grows, so too will the options and innovations in relay services, continuously enhancing the way we connect and interact in the decentralized social media landscape.
Explore different relays, engage with the community, and take control of your social media experience on Nostr.
-
 @ 76c71aae:3e29cafa
2024-04-27 02:17:10
@ 76c71aae:3e29cafa
2024-04-27 02:17:10Why are there 5.5 million people with Bluesky accounts and about 800k to 1.3M on Nostr?
Some of it boils down to social dynamics and chance. It's akin to how immigrants often cluster in the same neighborhoods. Most people are simply following their communities, and their primary decision is driven by where their community is heading.
Why did the communities choose Bluesky over Nostr, Mastodon, Farcaster, or the several dozen centralized and decentralized alternatives?
That’s a more pertinent question. Firstly, very few people actually make these decisions, and most simply follow them. Secondly, the choices aren't primarily based on the technology or the features of the apps or protocols.
Bluesky had certain advantages and disadvantages. It received a fair amount of press as a Twitter spinoff. However, it was late to launch, only preceded by Threads, which had Meta’s platforms for promotion.
In terms of initial marketing, I’d say Bluesky and Nostr were about equal, both often pitched as a ‘Jack Dorsey thing’, which wasn’t true in either case. The press loves stories about people and drama over networks and systems. Social media is vast and complex, and its technology even more so, which is why it’s often presented through personalized narratives about the creators.
Under the hood, Bluesky’s atproto and Nostr are very similar technologically. Both were inspired by Secure Scuttlebutt. Bluesky has adopted a cathedral model of open source, akin to how Android is open source but controlled by Google. Meanwhile, Nostr developed under the bazaar model of open source, created by a community rather than a company.
This company model gives Bluesky some advantages; for instance, they could launch with an invite list, a classic tactic to make something feel more desirable. Even then, most Bluesky users haven’t posted a single thing, and when they had a million registered users, they had fewer than 1500 Daily Active Users (DAU) see bluesky stats.
Bluesky is a lot easier to try than Nostr. The ways keys and content signing work in Bluesky and Nostr are overwhelmingly similar, except that Nostr doesn’t tell you where to store your keys and in Bluesky, you put them on your PDS server, which Bluesky provided free by default for all new users.
This means for Nostr, you have to figure out what to do with your nsec and npub, then how to get a nip-05 for a Nostr name which makes sense. If you want to log in with a username and password, you need to find and set up a nip-46 service. Not all apps support that, so you’re copying and pasting around an nsec. If you want to use a web app, you need to go find and choose one of several browser extensions and set that up. This is easy and natural for folks with experience in crypto but really foreign for everyone else.
Maybe a million people have figured out how to get started on Nostr; it’s definitely possible. And some apps like Primal and Nos have integrated name services as part of the signup, which makes it cleaner.
Once you’re on Nostr, people often discuss zaps, a functionality that may not work as expected. You’ve got to learn how to set up a wallet, what lightning and Bitcoin are. Some get really into it, we’ve seen folks get into Bitcoin through Nostr, but for many, it’s a confusing hurdle.
Bluesky provides a neat way to get into a single default app and gives you a username. Sure, you can change it—I self-host my DID at rabble.nz—but apparently less than 1% of Bluesky users do that, just like most Nostr users have chosen to use a cloud service for their nip-05 Nostr name.
Why else has Bluesky grown bigger than Nostr? It's their approach to positioning the protocol. They’ve set up default moderation controls and a trust and safety team. Initially, they didn’t have these, and when users demanded action and the company refused, growth stalled and usage dropped last July. The Bluesky team didn’t post for about a month, and there was a real question about whether Bluesky would survive.
The user community wanted pretty heavy-handed moderation. The Bluesky team was committed to building a decentralized protocol that didn’t do that. The compromise was that Bluesky would be slow about opening up open federation over atproto until the Bluesky apps, protocol, and company-hosted services could have a trust and safety team and a moderation bot. Their moderation bot is fancier than @reportinator, but it’s the same idea, but with a bigger team of humans reviewing reports. And if you’re using the Bluesky-provided PDS, there’s no way to block or unfollow their default moderation bot. We don’t make everybody on Nostr follow nostr:npub14h23jzlyvumks4rvrz6ktk36dxfyru8qdf679k7q8uvxv0gm0vnsyqe2sh .
That compromise worked for the community and company, and the user base started growing again. The negative press about Bluesky's content ceased and those upset by the policies left, some migrating to Nostr. Bluesky was able to position itself as the socially responsible social media protocol that was easy to use. Jack deleted his Bluesky account, signaling to the world and press what we already knew: he is much more interested in Nostr’s approach to bottom-up development by community and support for lightning payments.
During this period, Nostr's growth really stalled. There are a few reasons for this. We'd saturated the community of folks who both love Bitcoin and dislike Elon enough to leave Twitter. Additionally, our new user experience pushed people to view a global feed dominated by a single topic of conversation.
Nostr has positioned itself strongly as a protocol for those who are freedom-loving, anti-censorship Bitcoin enthusiasts. The easiest Nostr client for new users, Primal, markets itself as a Bitcoin wallet first, and only secondarily as a social media app. People view Nostr as a Web3 project. We’ve had individuals visit the Nos.social website and decline involvement, saying they dislike Web3 because they perceive it as a planet-harming scam (let's not argue the carbon emissions of mining here). We never mention Web3 or any cryptocurrency elements on the Nos website, yet all decentralization has been associated with dubious schemes.
As Nostr’s growth has stalled, the ecosystem has matured and flourished. Nostr boasts technology and apps that other platforms envy. I often hear Bluesky and Fediverse developers express admiration for the cool things Nostr is doing with technology and apps, but since their communities don’t use it, they don’t either.
Just look at the articles my posts last week about Nostr vs. ActivityPub kicked off: Extending ActivityPub and Nomadic Identity is Coming to ActivityPub
I suspect what’s holding back Nostr is twofold. First, how we talk about Nostr. We discuss it in political and ideological terms—we're against censorship, for free speech, value-for-value, etc.—but not about the types of content and people on Nostr, how to find your friends, or the interesting stuff you followed elsewhere. Nor do we talk about how you can use all these cool apps with the same identity and content. It's a hard concept to grasp, and I find myself constantly having to explain it.
The biggest issue people see with Nostr is its perceived association with Bitcoin enthusiasts plus those who’ve been deplatformed elsewhere, often for contentious reasons. I’m not saying the deplatforming was justified, but the perception among those unfamiliar with arbitrary bans and sanctions on platforms is that those who've been deplatformed had it coming—that they were all conspiracy theorists, bigots, or harassers. Some were, some were not, but it's perceived that way by many.
The way we talk about Nostr and onboard new users doesn’t help. The goal of the creator and journalism projects we just launched was to both diversify the content on Nostr for new users and to demonstrate to those creators and journalists that micropayments and paid content on Nostr are viable alternatives/additions to how they publish on social media elsewhere. It is value-for-value without the label, because our theory is that people want the functionality but aren't so keen on the cultural ideology.
This is all solvable. We can: - Make it easier to set up a nip-05 for new users. - Ensure that nip-05 also functions as an nsec bunker for easy login, if users desire. - Add Webfinger files so your nip-05 name functions as a Fediverse name (it’s pretty easy to do; we're experimenting with it on nos.social). - Show users a variety of content types when they join. - Help users find communities, perhaps encouraging groups/channels the way Farcaster does. - Make it easy to find and choose moderation settings, offering more middleware services like Reportinator but with different content labeling ideas. - Change our marketing to attract these new users, focusing on what they can see and who they can connect with, less on Bitcoin, technology, or evading censorship. - Develop apps that offer new functionalities, drawing people in instead of being mere clones with or without certain features.
It always takes a long time for people to figure out what the native mediums are on a technology platform. Initially people would make a phone call to listen to a concert, the first radio stations had people just reading the newspaper, and the first tv broadcasts were either a camera pointed at radio announcers or a single camera shot of a play. People always do the same things, we're the same humans that evolved a couple hundred thousand years ago, same brains, same bodies. What's changed is the way we do things with technology, so what fundamental human thing can we do new and different now that we've got these social protocols and tech?
Addressing the app design and technology will help, but actual growth will come when people discover us, join, find connections, and genuinely want to invite others to join them. Nostr users are incredibly welcoming to new users. However, we also have a subset of users who engage in sexist, racist, and homophobic harassment. This harassment drives people away from Nostr and deters them from recommending it to others. If we don't provide better tools for users to protect themselves from this harassment, they'll leave and find social spaces where they feel safe. Some might abandon public social media altogether, or just switch to Bluesky, which promises to eventually open up their network and has just announced support for uploading images, coming soon.
We're way ahead of the other protocols in some areas and way behind in others. We've got enough momentum and users to figure this out, but we're not there yet.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ fbe736db:187bb0d5
2024-05-04 09:26:56
@ fbe736db:187bb0d5
2024-05-04 09:26:56This is a slightly abridged version of an article published in Bitcoin magazine in October 2021.
June 4th 2021, Bitcoin Conference, Miami. Max Keiser strides onto the stage, clad in a white suit, in triumphant fashion.
“YEAH! YEAH! WE’RE NOT DONE! WE’RE NOT DONE! FUCK ELON! FUCK ELON!”
This clip attracted plenty of online criticism, perhaps most from those already looking for something to criticise, but also from some bitcoiners. But what was the impact? And how badly can bitcoiners hurt Bitcoin?
More on Max Keiser later.
Bitcoin’s most underrated facet is its fully distributed (frequently also described as decentralised) nature, both in terms of the miners and node operators. But this concept of decentralisation also extends to Bitcoiners themselves. There are certainly cohorts. The core developers, the miners. The podcasters, educators, & media personalities. The exchanges, traders, & the on-chain analysts. The venture capitalists. The plebs. However, because of the “opt in” nature of Bitcoin, attempts to typecast bitcoiners typically fail.
How can bitcoiners harm bitcoin? It's best considered when turned around. If you were a secret agent and could send someone to undermine bitcoin — who would you send, and what would they do?
Let’s consider a couple of recent candidates. The author Nassim Nicholas Taleb covered many topics in his books, (such as Fooled by Randomness, Black Swan, Antifragile, and Skin in the game), that resonate with Bitcoin principles. He was for many years loosely a Bitcoin advocate, and wrote the original foreword to the Bitcoin Standard.
As is well known, Taleb fairly abruptly announced he had sold all his Bitcoin in Feb 2021, and doubled down by writing a “black paper” denouncing the true value of Bitcoin as zero. This would certainly appear harmful to Bitcoin. However, the concepts expressed in his paper do not suggest a wealth of new insight suddenly having been gained from being some kind of Bitcoin insider. His arguments need to stand on their own merits (or lack of) either way. I’d argue that Taleb has simply joined the ranks of existing Bitcoin detractors, of which there are already plenty.
Many of Taleb’s ideas within his books still resonate. He was once famously asked his view on Microsoft as a stock, and remarked that since he was neither long nor short on the stock, he wasn’t qualified to give his opinion on it. Skin in the game.
The irony is that he has written a “black paper” denouncing the value of bitcoin as zero, and yet now appears to be neither long nor short on… bitcoin. No discernible skin in the game there, then.
Let’s consider another — Elon Musk. What better way to belittle Bitcoin than to endlessly plug Dogecoin and label it in with “Crypto”, essentially calling into question the notion of Bitcoin’s digital scarcity. The reason being, if Doge is a comparable investment to Bitcoin, why not Baby Doge? And so on. Secondly, he has very publicly questioned Bitcoin’s environmental impact.
Many involved with Bitcoin will have found Musk’s actions pretty frustrating; at best it could be described as learning in public, and he’s not done yet. But again, actions speak louder than words. In 2021 in terms of just his actions, Elon Musk has personally bought and still owns a chunk of Bitcoin, as do Tesla and SpaceX. I suspect we haven’t heard the end of this story just yet.
Re the idea of bitcoiners criticising Bitcoin, I think there is an interesting contrast here to a recent BBC documentary that Michael Palin presented on North Korea. When he asked his guide why North Korean citizens never criticise their leaders, she replied that the leaders represent the nation, of which they are all an intrinsic part — “Criticising our leaders is like criticising ourselves, too”.
This was to a small extent a compelling expression of unity, but scratch beneath the surface and it’s a pretty torrid state of affairs. There is no opportunity for debate or error correction, and indeed North Korean citizens have little choice but to belong to the nation, not having free borders.
Bitcoin is the total opposite. It in itself presents no barriers to entry — or exit. It is perhaps the embodiment of free speech and error correction. Taking Elon Musk’s environmental comments as an example, in recent months there has been considerable pushback against this narrative from others. As Lyn Alden remarked earlier this year — Bitcoin’s energy use may not be an actual problem, but general perception of its energy use is. This is now error correcting.
How would we even define a bitcoiner? Perhaps it is as simple as someone who owns bitcoin. At any point in time you either own bitcoin or you don’t.
Some might draw a common strand to the North Korea anecdote. That is — it’s not particularly easy for a bitcoiner to criticise Bitcoin. I think this is what inevitably leads to accusations of cult-like behaviour, but these are levied without proper understanding.
Why? Any bitcoiner can criticise Bitcoin, but the only way to meaningfully criticise and remain true to yourself is to remove your skin in the game, and no longer hold bitcoin. If you no longer own it, then perhaps you are by definition, no longer a bitcoiner.
Bitcoiners could certainly harm Bitcoin in aggregate. I would recommend reading “The Blocksize wars” by Jonathan Bier, for anyone looking to understand the events of 2015–17 around proposed changes to Bitcoin’s protocol. That seems a long way away today, though, and is perhaps yet another example of Bitcoin’s antifragility.
Bitcoin in its operation could be seen as a one way valve. It has the capacity to take on board improvements from benevolent actors, but ignores those who seek to harm it. See Taleb; antifragility.
Having considered all that, back to Max Keiser. Of course, he may have his own reasons for wanting to make a lasting impression. As for the impact:
- It had absolutely no impact on Bitcoin. Max Keiser knows he — or indeed anyone — could enter onto that stage however they like and it won’t make a scrap of difference to Bitcoin’s future.
- Perhaps the genius of Max Keiser is that he appreciates that the moment an observer fully clocks point one, they are a step closer to understanding Bitcoin themselves.
-
 @ 75bf2353:e1bfa895
2024-05-03 23:37:34
@ 75bf2353:e1bfa895
2024-05-03 23:37:34 Keet is a peer to peer chatroom that enables high quality file transfers. It can be used for video chats, but it's peer to peer and you don't need to pay a monthly fee. It uses cryptography, but it has no blockchain or any tokens. You can also connect LND to it to accept bitcoin payments.
Keet is a peer to peer chatroom that enables high quality file transfers. It can be used for video chats, but it's peer to peer and you don't need to pay a monthly fee. It uses cryptography, but it has no blockchain or any tokens. You can also connect LND to it to accept bitcoin payments.I don't like asking for people's email. It's not that I have any ideological reasons for this, it's just that e-mail kinda sucks. Adam back tried to fix it in the 1997. It would have worked, but nobody else cared. As it turns out,. that thing that could fix e-mail became the backbone of the bitcoin time-chain.
I like Substack, but I don't want you to give Substack your e-mail address.
I would prefer if you joined my Public Keet Chatroom. My goal is for it to become a sufficiently decentralized public communications channel. Please run Keet on your computer.
Share this so others may join.
Update Keet now has a broadcast only room. This way, I can broadcast all my new blog posts on this room and my readers can get notified.
https://gasolin.idv.tw/keetlink/#key=yry53k5uwu6n8htnzdi8m77qupswwjh8p8oue8qiup5fotdeqq7ti176kqdjxtr4eyht3f11dakdicx7ipj879nzmhhrdgs7hf3z1am9pc&title=Blogging%20Bitcoin
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ d34e832d:383f78d0
2024-05-05 20:05:58
@ d34e832d:383f78d0
2024-05-05 20:05:58In an era where questions about data privacy, censorship, and central control are more pressing than ever, the future seems bright for decentralized social media platforms, with Nostr leading the charge. This emerging protocol is reshaping the landscape, offering a blueprint for what social media can become: more secure, user-centric, and radically open.
Overview of Nostr's Decentralized Features
Nostr stands out by empowering users and developers through several key features:
- Decentralization: Unlike traditional platforms, Nostr doesn't have a central control point. This model gives users complete control over their data and content, mitigating risks like censorship and data breaches.
"Decentralization ensures that users have the ultimate authority over their interactions and information, unlike centralized counterparts where user data can be manipulated or sold."
-
Openness: The protocol is open-source, enabling anyone to build applications on Nostr without requiring permission. This openness promotes a fertile environment for rapid innovation and diverse application development.
-
Interoperability: Applications built on Nostr are interoperable, allowing users to switch seamlessly between different apps without losing data or connections, enhancing user experience and choice.
-
Scalability: With lightweight data structures at its core, Nostr can scale efficiently to support a large user base and significant data volumes without sacrificing performance.
-
Bitcoin Integration: Incorporating features like Bitcoin Lightning Network support, Nostr integrates financial transactions into the social media experience, offering new monetization avenues for creators.
Advanced Features Enhancing User Agency in Nostr Clients
To further enhance user experience, developers can integrate sophisticated features into Nostr clients:
-
Customizable Filters: Users can set filters based on keywords, authors, or content types, making content discovery more tailored and efficient.
-
Lists: This feature allows users to organize content by creating personalized lists of favorite authors or topics, enhancing the manageability of their feeds.
-
Mute/Unmute Options: Users can control their content feed more directly by muting authors or topics that they find irrelevant or bothersome.
-
Bookmarks: Users can bookmark messages or create collections of favorite posts, simplifying access to preferred content.
-
Granular Privacy Settings: These settings give users precise control over their visibility and interaction level on the platform, from profile viewing rights to interaction permissions.
-
Real-Time Notifications: By implementing notifications, users remain engaged and informed about important interactions and updates.
-
Reactions and Customized Responses: Enabling diverse reaction options allows users to express feelings or thoughts more vividly and interactively.
-
Translations: Integration of translation services can break language barriers, expanding user interaction across different linguistic demographics.
-
Content Moderation Tools: Features that allow users to flag inappropriate content or block disruptive users are essential for maintaining a positive environment.
-
Social Graph Visualization: Visual tools that map out a user’s network can provide valuable insights into their social interactions and community dynamics.
Nostr Clients and Resources
For those looking to explore Nostr through practical applications, both desktop and mobile clients are available:
- DeskTop:
- Damus for macOS: A feature-rich desktop client designed to streamline user experience on macOS.
-
Nostrmo for Desktop: A cross-platform client that brings enhanced functionality to desktop devices.
-
Mobile:
- Damus for iOS: Seamlessly integrate Nostr on your iPhone with this robust iOS client.
- Amethyst for Android: Experience Nostr on Android devices with this fully functional client offering a range of features.
Closing Case
As Nostr continues to evolve and gain traction, we anticipate seeing a significant shift in how social media platforms operate. The core principles of privacy, user control, and open innovation that Nostr champions are likely to set new standards in the technology community.
For those interested in exploring deeper or contributing to Nostr's development, additional resources such as Nostr's GitHub Repository and community tutorials on Nostr.how provide excellent starting points.
Join the movement toward a decentralized, user-driven social media landscape. Build, interact, and innovate with Nostr — shaping the future of digital communication.
Introducing NostrSigningDevice: Revolutionizing Secure Transactions
In the rapidly evolving landscape of digital transactions, security and reliability are paramount. Enter NostrSigningDevice, a cutting-edge solution poised to revolutionize secure transactions in the digital realm.
Secure Transactions Made Simple
NostrSigningDevice offers a seamless and secure platform for signing transactions, ensuring the authenticity and integrity of each digital interaction. Whether you're processing payments, verifying contracts, or executing smart contracts, NostrSigningDevice provides the robust security measures necessary to safeguard sensitive data and transactions.
Key Features:
1. Hardware Security Module (HSM) Integration
NostrSigningDevice leverages Hardware Security Modules (HSMs), specialized hardware devices designed to securely store cryptographic keys and perform cryptographic operations. By integrating HSMs into its infrastructure, NostrSigningDevice ensures the highest level of security for transaction signing, protecting against unauthorized access and tampering.
2. Multi-Factor Authentication (MFA)
With multi-factor authentication (MFA) capabilities, NostrSigningDevice enhances the security of transactions by requiring multiple forms of verification before authorizing a transaction. This layered approach to authentication mitigates the risk of unauthorized access and strengthens the overall security posture of the platform.
3. Seamless Integration with Nostr Ecosystem
NostrSigningDevice seamlessly integrates with the broader Nostr ecosystem, providing a unified platform for secure digital transactions. Whether you're a developer building Nostr-powered applications or a business leveraging Nostr's decentralized infrastructure, NostrSigningDevice offers a cohesive solution for transaction signing across the ecosystem.
4. Developer-Friendly APIs
Developers can easily integrate NostrSigningDevice into their applications using intuitive APIs and SDKs. With comprehensive documentation and developer resources, NostrSigningDevice empowers developers to leverage its robust security features without compromising on usability or flexibility.
5. Compliance and Regulatory Support
NostrSigningDevice is designed with compliance and regulatory requirements in mind, offering features and functionalities to support adherence to industry standards and regulations. Whether you operate in finance, healthcare, or any other regulated industry, NostrSigningDevice provides the necessary tools to maintain compliance while ensuring secure transactions.
Unlock the Power of Secure Transactions with NostrSigningDevice
Whether you're a financial institution, enterprise, or individual user, NostrSigningDevice offers a trusted solution for secure transaction signing in the digital age. With its advanced security features, seamless integration capabilities, and compliance support, NostrSigningDevice is poised to redefine the standards for secure digital transactions.
Visit NostrSigningDevice today to learn more and unlock the power of secure transactions in the Nostr ecosystem.
-
 @ 9fec72d5:f77f85b1
2024-05-03 23:09:32
@ 9fec72d5:f77f85b1
2024-05-03 23:09:32
In the quest to teach an LLM about the wisdom on Nostr, things are progressing and getting more real. I wanted to spend more time on filtering notes better, i.e. choosing the "meaningful" ones. Separation of chat from the encyclopedia material but also including opinions. Individual opinions matter a lot. We can't all get together and write books but we can argue about things that are happening around us, relatively easily and fast. And those matter too. In the future LLMs could start learning real time. I think they will become more relevant at that point.
In my first attempt to train a big model using Nostr knowledge, I kept it really simple. I just used a web of trust scoring that I developed earlier. Pubkeys are attached with a score and about 320k notes from high web of trust set were included in my initial training. This included all kinds of content from those people including daily chatter and small word responses. Also "GM". The result of that work is here: https://huggingface.co/some1nostr/Ostrich-70B (Version: 3295) This model will be upgraded later but currently it has the result of that initial experiment.
This still thought a lot of things to the model. Link: nostr:naddr1qvzqqqr4gupzp8lvwt2hnw42wu40nec7vw949ys4wgdvums0svs8yhktl8mhlpd3qqxnzde3xgcnsvpnxqerzvf3pz35j6 I think it is because of high number of notes even though they had not much filtering, it appears that the LLMs don't come undone easily even though you feed them with very unstructured data. Or they keep their integrity when you push chatter to them. But if you overfit them they lose abilities, for sure. Couple times they forgot how to do paragraphs because I was feeding them a lot of space characters where a paragraph would be more appropriate. I try to keep it simple. I should switch to JSONs at some point. Right now the training material is in TXT files.
Now I want to curate more because training is costly and soon Llama3 405B may arrive. Things will be a lot slower when you want to train a 405 billion parameter model. I want to carefully curate, to cut costs of training. So the curation currently is comprised of a few steps.
1. Storing kind 0's
This will be used in step 3. An LLM won't understand public key strings (npub1..........). It will see a number of characters that doesn't make sense. In the future this may be different. Think of LLMs actually linking documents using pubkeys, understanding links etc. When generating links they do a bad job, which makes me understand they don't actually learn the link. For links to work, the exact string has to be memorized. But LLMs are probabilistic. It may generate nostr.com as well as nostr.co or nostr.mom in the same context but each of these would mean completely different things even though only one letter changes. LLMs work with sequence of letters (tokens) but this was just to give an example.
2. Filtering based on simple algo
In this step I apply some simple and quick algo's.
Web of trust score allows much of the spam to be effectively disregarded. Nostr is super open. To everyone and every bot. So there has to be some kind of filtering in everything we do.
Small content is removed (I am interested in 100+ characters).
Notes with too many tags are removed (10+).
Notes that have long strings of characters are removed (these are probably base64 encodings of some things).
Notes that have too little letter ratio is removed (these are comprising of many numbers or symbols).
The result of this step is most of notes are gone and I end up with 1.6 million notes to go along with in the next steps.
3. Editing notes to make more sense for LLM
LLMs does not understand the links. They don't follow links. So 'http://...' have to be converted to things like '[link]'.
nostr:naddr1..... are converted to [pubkey].
nostr:note1...... are converted to [note].
etc.
I am sure this is not the best way to do it. If we didn't do this step, things could still work but this I think speeds up learning. Instead of LLM going thru all those letters and spending precious token conversions on them I make them shorter.
4. Going thru notes and understanding if they are knowledge material or chat
This is the most time consuming step. Using another LLM to understand each note and decide whether to include it in the training or not.
This is what I used in the system message:
You are a machine that filters tweets. You will read the tweet and understand and determine whether it is of value. A tweet is valuable when it has a proposition, a judgement, a statement, a comment about something, an argument, a long article, an information, a personal opinion, a wisdom, a knowledge. A tweet is not valuable when it is a general chat, a question, some things that the writer is doing, has no information, is about day to day life, has news value but is not suitable for a long term reference book. Another way to determine a tweet is valuable or not is ask these questions: "Can the contents of this tweet be included in an encyclopedia?". "Can the contents of this tweet be included in a reference book?". "Can the contents of this tweet be used as an argument?". If the answer to any of those questions is yes, than the tweet is valuable. A longer tweet is usually more valuable. In the first line you will get a web of trust score (wot) as part of the input. This shows how trustable the writer of the tweet is. You can use this data to help judge. In the second line and the following lines you will get the tweet. If the tweet has [link] and it talks about the link, it has not much value. If you don't understand what the tweet is about, it has no value.Then I gave a few shots as examples. My other model did well here because it is based on Llama 3 and already knows a bit about Nostr. https://huggingface.co/some1nostr/Emu-70B-Llama3 This model spends about 1.5 seconds per note.
I also used Llama3 8B to speed up things in the low web of trust areas. It is much faster but sometimes disagrees with 70B versions (it should disagree sometimes, because it is dumber). So what I am doing is use 8B first, if 8B accepts a note then check again with 70B. I have to make sure things are of value with 70B. This effectively allows fast initial screening and later final decision.
5. Elimination of bots, LLMs and news
I realized there are lots of bots already. Lots of news submitters. People copying LLM outputs to their notes. Additional filtering needed here. Later I may do an LLM to detect whether a note is written by an LLM. I am mostly interested in notes generated by humans.
Current number of trainable items is 60k and the filter is still running. I am expecting the number to be around 80k.
6. Dividing the notes to pieces to apply different learning rates
This is to basically give more weight to high web of trust sources. High wot could use 5e-5 learning rate and cosine scheduler. Then low wot ones could do 1e-5 and linear decay. This just pushes the narrative towards more accepted notes on Nostr. If a person has a huge following it is more accepted by Nostr. And we are reflecting that in our training, by boosting the high wot to be learned more from.

Conclusion
It looks like it will take several days to train on the resulting notes. In my setup it takes 1.5 hour to train on 1MB of data. Which is probably very slow because I am using fsdp_qlora. There is also a new technique fsdp_qdora: https://www.answer.ai/posts/2024-04-26-fsdp-qdora-llama3.html I will try that next time. It looks like it is even better than full training, while using much less resources!
-
 @ 892ab9bd:e686de59
2024-05-05 08:25:08
@ 892ab9bd:e686de59
2024-05-05 08:25:08
Have you ever felt frustrated by the lack of freedom and censorship on traditional social media platforms? Or perhaps you’re concerned about your privacy and the control big tech companies have over your data? If so, Nostr might just be the solution you’ve been waiting for.
Nostr is a revolutionary decentralized social network protocol that promises to shake up the way we communicate and share information online. Unlike traditional social media platforms, Nostr is built on principles of censorship resistance, user privacy, and open standards. It’s a decentralized, peer-to-peer network that puts the power back in the hands of users, allowing them to freely express themselves without fear of censorship or data exploitation.
In this comprehensive guide, we’ll dive deep into the world of Nostr, exploring its history, technical underpinnings, advantages, challenges, and potential implications for the future of social networking.
How Nostr Works

At its core, Nostr is a decentralized and censorship-resistant architecture that operates without a central authority or server. Instead, it relies on a network of relays and client software that communicate with one another using a peer-to-peer protocol.
The key Innovation behind Nostr is its use of private key cryptography and data signing. Each user has a unique private key that serves as their digital identity. When a user creates content, such as a post or message, they sign it with their private key, ensuring the authenticity and integrity of the data.
This signed data is then broadcasted to a network of relays, which are independent servers that act as temporary message stores and facilitators of real-time communication. Relays don’t store user data permanently, nor do they have control over the content being shared. Instead, they simply relay the signed data to other relays and clients on the network.
Clients, on the other hand, are the software applications that users interact with to access and participate in the Nostr network. These clients can be web-based, desktop, or mobile applications that connect to various relays, allowing users to read, create, and share content seamlessly across the decentralized network.
Advantages of Nostr
Nostr’s decentralized and open-source nature offers several advantages over traditional centralized social media platforms:
-
Censorship Resistance and Freedom of Speech: Since there is no central authority controlling the network, it becomes virtually impossible to censor or restrict the flow of information. Users can freely express themselves without fear of being silenced or deplatformed.
-
User Privacy and Control Over Data: Unlike traditional social media platforms that collect and monetize user data, Nostr puts users in complete control of their data. Users’ identities are tied to their private keys, and their content is signed and broadcasted directly to the network, without any intermediaries having access to or control over their data.
-
Interoperability and Open Standards: Nostr is built on open standards and protocols, allowing for seamless interoperability between different client applications and relays. This fosters innovation and prevents vendor lock-in, as users can easily switch between different clients or relays without losing their data or social connections.
-
Potential for Innovation and New Applications: Nostr’s decentralized and open nature provides a fertile ground for innovation and the development of new applications beyond traditional social media. Developers can build decentralized applications (DApps) on top of the Nostr protocol, enabling a wide range of use cases such as decentralized messaging, content creation and publishing, financial applications, and more.
Nostr Protocol and Technical Details
The Nostr protocol is the underlying technology that powers the decentralized social network. It defines the rules and standards for how data is structured, signed, and transmitted across the network.
At the heart of the Nostr protocol are “events,” which are essentially data packets that contain various types of information, such as text posts, media uploads, reactions, or follow/unfollow actions. These events are signed with the user’s private key, ensuring their authenticity and immutability.
The protocol specifies several event types, each with its own structure and purpose:
- “text_note” events: These are the primary events for creating and sharing text-based posts or messages.
- “set_metadata” events: These events allow users to set or update their profile metadata, such as display name, bio, or profile picture.
- “contact_list” events: These events represent a user’s list of followed or subscribed users.
- “encryption_key” events: These events enable end-to-end encrypted communication by sharing encryption keys.
- “reaction” events: These events allow users to react to or engage with other events, similar to likes or retweets on traditional social media platforms.
Relays play a crucial role in the Nostr network by facilitating the dissemination of these events. They act as temporary message stores and real-time communication channels, relaying events between clients and other relays.
When a client connects to a relay, it can subscribe to specific event types or filters, such as following a particular user or receiving events related to a specific topic or hashtag. The relay then broadcasts matching events to the client in real-time, enabling seamless and decentralized communication across the network.
Nostr Applications and Use Cases
While Nostr was initially conceived as a decentralized alternative to traditional social media platforms, its versatile nature and open standards have paved the way for a wide range of potential applications and use cases:
-
Social Media and Microblogging: At its core, Nostr enables decentralized social networking and microblogging, allowing users to create and share content, follow others, and engage in conversations without the constraints of centralized platforms.
-
Decentralized Messaging and Chat: Nostr’s encryption capabilities and real-time communication features make it well-suited for decentralized messaging and chat applications, offering privacy and censorship resistance.
-
Decentralized Content Creation and Publishing: With its open and permissionless nature, Nostr can facilitate decentralized content creation and publishing, enabling writers, artists, and creators to share their work directly with their audience without intermediaries.
-
Decentralized Financial Applications (DeFi): Nostr’s integration with cryptocurrency and blockchain technologies opens up possibilities for decentralized financial applications, such as peer-to-peer payments, crowdfunding, or decentralized exchanges.
-
Other Potential Applications: The versatility of Nostr’s protocol and its decentralized architecture make it suitable for a wide range of other applications, such as decentralized identity management, voting systems, gaming platforms, and more.
Challenges and Criticisms of Nostr
While Nostr offers numerous advantages and opportunities, it is not without its challenges and criticisms:
- Moderation and Content Curation Challenges: Nostr’s decentralized and censorship-resistant nature makes it difficult to implement effective content moderation and curation mechanisms. This could potentially lead to the spread of harmful or illegal content on the network.
- Potential for Abuse and Illegal Activities: Like any open and permissionless system, Nostr could be exploited for nefarious purposes, such as spreading misinformation, conducting illegal activities, or facilitating cybercrime.
- Scalability Concerns: As the Nostr network grows in popularity and usage, scalability issues may arise, particularly in terms of relay infrastructure and bandwidth requirements.
- Lack of Established Governance and Funding Model: Nostr is a community-driven project without a centralized governing body or a clear funding model. This could lead to challenges in terms of decision-making, prioritizing development efforts, and sustaining the project’s long-term growth.
Getting Started with Nostr
If you’re intrigued by the potential of Nostr and want to explore this decentralized social network for yourself, here's a brief guide on how to get started:
-
Install and Set Up a Nostr Client: The first step is to choose and install a Nostr client application. There are various options available, such as Damus, Astral, or Iris, each with its own features and user interface. Most clients are available for desktop and mobile platforms.
-
Choose and Connect to Relays: Once you have a client installed, you’ll need to connect to one or more Nostr relays. Relays are independent servers that facilitate communication on the network. Popular relay options include
wss://nos.lolandwss://relay.damus.io, but you can explore and choose relays based on their reputation and performance.
a. Create and Manage Keys and Identities: Nostr operates on a system of private keys, which serve as your unique identity on the network. Your client will guide you through the process of generating a new private key or importing an existing one. It’s crucial to securely store and backup your private key, as losing it means losing access to your Nostr identity and data.
b. Explore Nostr Applications and Communities: With your client set up and connected to relays, you can start exploring the Nostr ecosystem.
Future of Nostr and Decentralized Social Networks
As innovative and promising as Nostr is, it’s still in its early stages of development and adoption. The future of Nostr and decentralized social networks holds both exciting possibilities and potential challenges:
-
Ongoing Development and Adoption Trends: Nostr’s open-source nature and active community of developers and enthusiasts have fostered a vibrant ecosystem for ongoing development and improvement. New features, client applications, and integrations are continually being introduced, which could drive further adoption and mainstream appeal.
-
Potential Integration with Other Decentralized Technologies: Nostr’s compatibility with blockchain and cryptocurrency technologies opens up opportunities for integration with other decentralized systems and applications. For example, Nostr could be integrated with decentralized storage solutions, identity management systems, or decentralized finance (DeFi) platforms, creating a more comprehensive decentralized ecosystem.
-
Regulatory and Legal Implications: As Nostr gains traction, it may attract increased scrutiny from regulators and policymakers. Issues such as content moderation, data privacy, and the potential for illegal activities on the network could prompt discussions around legal frameworks and regulations for decentralized social networks.
-
Comparison with Other Decentralized Social Networks: While Nostr is a pioneering project in the realm of decentralized social networking, it's not the only one. Other platforms like Mastodon and BlueSky have also gained traction, each with its own approach and features. The competition and coexistence of these projects could drive innovation and shape the future landscape of decentralized social media.
Resources and Further Reading
If you’re eager to dive deeper into the world of Nostr, here are some recommended resources and further reading materials:
- Nostr Clients and Tools:
- Damus (Desktop and Mobile)
- Astral (Desktop and Web)
- Iris (Desktop and Mobile)
-
Nostr.io (Web-based client)
-
Educational Resources and Tutorials:
- Nostr Documentation (https://github.com/nostr-protocol/nostr)
- “Mastering Nostr” video series by Damus
-
“Nostr for Beginners” blog series by Nostr.io
-
Influential Nostr Projects and Communities:
- Nostr Community Hub (https://nostr.ch)
- Nostr Developers Discord Server
-
Nostr Relay Registry
-
Books, Articles, and Research Papers:
- “Decentralized Social Networks: A Paradigm Shift” by John Doe
- “The Nostr Protocol: A Technical Deep Dive” by Jane Smith
- “Privacy and Censorship Resistance in Decentralized Social Networks” (research paper)
Conclusion
Nostr represents a bold and innovative step towards a more decentralized, censorship-resistant, and user-controlled social networking experience. By leveraging the power of cryptography, peer-to-peer networking, and open standards, Nostr challenges the status quo of centralized social media platforms and their monopolistic control over user data and content.
While Nostr is still in its early stages and faces challenges in terms of moderation, scalability, and governance, its potential for fostering free speech, protecting user privacy, and enabling new decentralized applications is undeniable. As the project continues to evolve and gain traction, it could pave the way for a paradigm shift in how we communicate and share information online.
Whether you’re a privacy advocate, content creator, or simply someone seeking an alternative to the traditional social media landscape, exploring Nostr is an exciting opportunity to be part of a decentralized revolution. So why not take the leap and immerse yourself in this innovative ecosystem? Join the growing community of Nostr enthusiasts, experiment with different clients and applications, and contribute your voice to shaping the future of decentralized social networking.
-
-
 @ 1c6b3be3:73f0ae6f
2024-05-02 04:38:59
@ 1c6b3be3:73f0ae6f
2024-05-02 04:38:59Releases - No Bullshit Bitcoin
Samourai Dojo v1.25.0: Removed Whirlpool CLI Samourai Dojo, a Bitcoin wallet backing server, has released version 1.25.0. This update removes the Whirlpool CLI due to the Whirlpool coordinator being inactive. RoninDojo, which is not affiliated with Samourai Dojo, remains active and focuses on censorship resistance, security, and privacy. Users of the now-inactive nextblock.is transaction fee estimator can switch to nextblock.e4pool.com. The source code for 'Nextblock' is available. The update also includes several improvements such as updating Tor, Bitcoin Core, ZeroMQ, and other dependencies, removing unnecessary bip39 dependency, making docker images smaller, and raising the required Node.js version to v18.
Lightning Terminal v0.12.5-alpha: Updated LND, Loop Daemons The company Ez has released an updated version of their browser-based Lightning Network (LN) interface called Lightning Terminal (LiT). This new version includes upgrades to the integrated LND and Loop daemons. Specifically, it includes LND v0.17.5-beta, Taproot Assets Daemon v0.3.3-alpha, Loop v0.28.1-beta, Pool v0.6.4-beta, and Faraday v0.2.13-alpha. The company plans to continue improving the user experience based on feedback from the community.
Bitcoin Optech #300: CTV-like Exploding Keys Proposal The Bitcoin Optech Newsletter #300 summarizes a proposal that utilizes commitments embedded in public keys similar to CTV, analyzes a contract protocol with Alloy, and reports on the arrests of Bitcoin developers. Additionally, it provides links to summaries of a CoreDev.tech developer meetup. A Twitter Spaces audio recap discussion of this newsletter will be hosted by Bitcoin Optech with special guest Tadge Dryja on Thursday at 14:30 UTC.
Bitcoin Optech
Bitcoin Optech Newsletter #300 (7 min) The weekly newsletter discusses a new proposal called "Exploding Keys" by Tadge Dryja, which is a slightly more efficient version of OP_CHECKTEMPLATEVERIFY (CTV). It allows Alice to pay to an output that matches certain parameters. Dryja suggests using a public key constructed from a MuSig2 aggregation of actual public keys and a tweak for each key that commits to an amount, which saves some space compared to CTV in taproot.
An analysis of a simple OP_CAT-based vault contract protocol was done by Dmitry Petukhov using the Alloy specification language. He found several useful modifications and highlighted important constraints for potential implementors.
Two developers of the Samourai privacy-enhanced Bitcoin wallet were arrested based on charges by U.S. law enforcement, leading to two other companies announcing they would stop serving U.S. customers due to legal risks. The newsletter encourages anyone interested in the success of Bitcoin to stay informed and consider offering support when opportunities arise.
Finally, the newsletter announces new releases and release candidates for popular Bitcoin infrastructure projects and invites readers to upgrade to new releases or help test them.
🍵 "btc | bitcoin | lightning network | asic" - Google News
LQWD Updates Bitcoin Lightning Network Operations - AccessWire Coinbase Adds Support for Bitcoin Lightning Network - CryptoPotato Coinbase Unveils Bitcoin Lightning Network Deal With Lightspark - ETF Trends Bitcoin L2s set to explode as Runes congest BTC network - Cointelegraph LQWD Updates Bitcoin Lightning Network Operations | Regional | chronicle-tribune.com - Chronicle-Tribune Bitcoin Lightning Network Could Reach 56 Million Users After Coinbase Integration - CCN.com Solana to Bitcoin Bridge Zeus Network Targets Q3 2024 Debut - CoinGape Texas A&M Professor to Launch Bitcoin Research Institute - Bitcoin Magazine Zeus Network to Launch ZPL Connecting Bitcoin and Solana - Crypto Times Beyond Ordinals, Runes are set to enhance the viability of new Bitcoin use cases - TNGlobal - TechNode Global Microstrategy Plans to Launch a Decentralized Identity Solution on Bitcoin – Bitcoin News - Bitcoin.com News
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 3cd2ea88:bafdaceb
2024-05-05 19:41:43
@ 3cd2ea88:bafdaceb
2024-05-05 19:41:43🚀 Preparate le vostre domande più scottanti su criptovalute, trading e Bitget perché i nostri esperti sono pronti a rispondere a tutto!
🚀 E come se non bastasse, ci saranno premi 💰 incredibili per i partecipanti!
🚨 Quindi alle ore 21:00 di lunedì 06/05 Bitget risponderà a tutte le vostre domande su Launchpad, Launchpool, PooX e BGB! ⏱️
🚨 E per chi è nuovo su Bitget?
🚨 Iscriviti tramite il nostro referral 6w5d e ottieni: 💰 Bonus di benvenuto 💰 Sconto a vita sulle fee 💰 Accesso esclusivo al nostro programma "University" per imparare le basi del mondo cripto!
💰 Non perdere questa occasione unica per immergerti nel mondo delle criptovalute con i migliori!
🚨 Unisciti al nostro canale Telegram e preparati per l'AMA!
🚀 https://t.me/Bitcoin_Report_Italia
-
 @ d34e832d:383f78d0
2024-05-05 16:49:58
@ d34e832d:383f78d0
2024-05-05 16:49:58Creating your first Nostr client application is an exciting journey into the world of decentralized communication. Nostr, an emerging protocol that fosters open and global communication free from centralized control, offers developers a unique opportunity to contribute to the future of social interactions on the internet. Here's a detailed guide to help both new and seasoned developers embark on building their own Nostr client application.
Step 1: Choose Your Programming Language
The first step in building your Nostr client is selecting a programming language. Popular choices include:
- JavaScript: Widely used, with extensive support for asynchronous operations which are crucial in client-server communications.
- Python: Known for its simplicity and readability, making it an excellent choice for beginners.
- Go: Offers robust network programming capabilities, perfect for handling concurrent tasks.
```markdown
"Choose a language that you are comfortable with, or that best suits the needs of the project." ```
Step 2: Set Up Your Development Environment
Once you've picked a programming language, set up your development environment. This involves:
- Installing necessary compilers or interpreters.
- Setting up package managers (like npm for JavaScript, pip for Python).
- Installing dependencies and libraries needed for Nostr.
Ensure that your development tools are up to date to avoid compatibility issues.
Step 3: Dive Into the Nostr Protocol
To effectively build on Nostr, understanding the protocol is crucial. Familiarize yourself with:
- Message Types: Know the different kinds of messages that can be sent and received.
- Event Structure: Understand how data is structured within the system.
- Client-Server Communication: Grasp the methods used for data exchange between clients and servers.
The Nostr protocol documentation on GitHub is an excellent resource for getting detailed and technical insights.
Step 4: Implement Basic Functionality
Start coding by implementing fundamental functionalities:
- Connect to a Relay Server: This is your application's gateway to receiving and sending messages.
- Subscribe to Events: Allows your app to listen for new data related to specific topics or users.
- Send Events: Enable your app to publish messages to the network.
Use libraries or SDKs specific to your chosen programming language to simplify these interactions.
Step 5: Add User Authentication
Security is paramount, especially in decentralized networks. Implement user authentication by:
- Generating and managing public and private keys.
- Using cryptographic libraries to handle key generation securely.
This not only ensures secure sign-ins but also maintains user privacy and data integrity.
Step 6: Build a User Interface
Your client needs a user-friendly interface. Design your UI to be intuitive and accessible, incorporating features like:
- Posting Messages: Users should be able to easily compose and send messages.
- Interactions: Allow liking, replying, and following other users.
- Search Functionality: Users may want to search for specific content or profiles.
Step 7: Test Your Application
Before going live, rigorously test your application to iron out any bugs and ensure all features are functioning correctly. Consider:
- Unit testing individual components.
- Integration testing to see how different parts interact.
- Beta testing with potential users to gather feedback.
Step 8: Deploy Your Application
Once satisfied with your application's functionality and stability, deploy it. Choose a reliable hosting platform that aligns with your needs and budget. Ensure your deployment processes include regular updates and maintenance checks.
Conclusion
Building a Nostr client application is a rewarding project that contributes to a more decentralized and open future of social networking. By following these steps, you can create a robust and user-friendly Nostr client that leverages the full potential of this promising protocol. Embark on this technical adventure and be part of a community reshaping communication across the globe.
Exploring Resources for Building Nostr Apps with NDK Library
If you're interested in building apps using the Nostr Development Kit (NDK) library, there are several valuable resources available online to guide you through the process. Whether you're a beginner or an experienced developer, these tutorials and documentation sources can help you kickstart your Nostr app development journey.
1. nostr.how
Description: This website offers a comprehensive step-by-step guide to assist you in creating your first Nostr app. It covers various programming languages such as JavaScript, Python, or Go, catering to a diverse range of developers. The guide provides detailed instructions, making it suitable for beginners looking to explore Nostr development.
2. nostr-dev-kit/ndk
Description: The official GitHub repository for the NDK library is an invaluable resource for developers. It contains extensive documentation, examples, and code snippets to facilitate the integration of Nostr functionality into your applications. Whether you're looking to understand the library's features or need guidance on implementation, this repository has you covered.
3. nostr-resources.com
Description: Nostr Resources is a dedicated website offering a plethora of tutorials, libraries, and projects related to Nostr development. Whether you're looking for additional learning materials, libraries to enhance your app's functionality, or inspiration from existing projects, this website serves as a comprehensive hub for all things Nostr.
By leveraging these resources, you can embark on your Nostr app development journey with confidence. Whether you're aiming to build a simple application or dive into more complex projects, these tutorials, documentation, and community-driven platforms will provide the support you need to succeed.
Happy Nostr app development!
Happy coding, and here's to building a more connected and decentralized world!
-
 @ 892ab9bd:e686de59
2024-05-05 07:51:10
@ 892ab9bd:e686de59
2024-05-05 07:51:10
Imagine a world where complex calculations that would take billions of years for classical computers can be solved in mere seconds. A world where data encryption methods that were once considered unbreakable are rendered obsolete. This is the reality that quantum computing promises to bring, and it's a game-changer for the field of cybersecurity.
As we delve deeper into the digital age, the need for robust cybersecurity measures has never been more pressing. With cyber threats constantly evolving and malicious actors becoming increasingly sophisticated, it’s crucial to stay ahead of the curve. However, the advent of quantum computing introduces a whole new set of challenges and opportunities that have the potential to reshape the cybersecurity landscape.
In this article, we’ll explore the profound impact that quantum computing can have on cybersecurity. We’ll delve into the principles behind this revolutionary technology, uncover the vulnerabilities it poses to current cryptographic methods, and unveil the innovative solutions being developed to fortify our digital defenses. Get ready to embark on a journey through the fascinating intersection of quantum physics and cybersecurity, where the lines between science fiction and reality blur.
Understanding Quantum Computing
To grasp the impact of quantum computing on cybersecurity, we must first understand the fundamental principles that govern this extraordinary technology. At its core, quantum computing harnesses the principles of quantum mechanics, such as superposition, entanglement, and quantum parallelism.
-
Superposition: In the quantum realm, particles can exist in multiple states simultaneously, a phenomenon known as superposition. This remarkable property allows quantum computers to perform calculations on multiple possibilities at once, exponentially increasing their computational power.
-
Entanglement: Quantum particles can become entangled, meaning their states are inextricably linked, even over vast distances. This bizarre phenomenon enables quantum computers to process information in ways that defy classical logic.
-
Quantum parallelism: By leveraging superposition and entanglement, quantum computers can perform numerous calculations simultaneously, a feat that classical computers simply cannot match.
These quantum principles translate into immense computational power, enabling quantum computers to tackle problems that would take conventional computers billions of years to solve. From simulating complex molecular structures to cracking encryption algorithms, the potential applications of quantum computing are vast and far-reaching.
Challenges to Cybersecurity

While the computational prowess of quantum computing holds tremendous promise, it also poses significant challenges to the field of cybersecurity, particularly in the realm of cryptography.
- Vulnerability of current cryptographic algorithms:
- Many of the encryption methods currently used to secure digital communications and data storage rely on the computational difficulty of factoring large numbers or solving discrete logarithm problems.
-
Quantum computers, with their ability to perform calculations exponentially faster than classical computers, could potentially break these cryptographic algorithms in a fraction of the time it would take conventional systems.
-
Shor’s algorithm and its implications for public-key cryptography:
- In 1994, mathematician Peter Shor developed an algorithm that could efficiently factor large numbers on a sufficiently powerful quantum computer.
-
This algorithm poses a direct threat to widely used public-key cryptography methods, such as RSA and Elliptic Curve Cryptography (ECC), which are based on the difficulty of factoring large numbers.
-
Quantum attacks on classical systems:
- Grover’s algorithm, another quantum computing algorithm, can provide a quadratic speedup in searching for solutions to certain problems, including breaking symmetric-key cryptography algorithms.
- This algorithm could potentially weaken the security of encryption methods like AES, which are commonly used to protect sensitive data.
As quantum computing capabilities continue to advance, the implications for cybersecurity become increasingly pressing. Current encryption methods that were once considered virtually unbreakable could be rendered obsolete, leaving sensitive data and communications vulnerable to attacks.
Opportunities for Cybersecurity
 While quantum computing poses significant challenges to traditional cybersecurity measures, it also presents exciting opportunities for developing new and more robust security protocols. Researchers and cryptographers are actively working to develop quantum-resistant cryptography algorithms and explore the potential of quantum key distribution (QKD) techniques.
While quantum computing poses significant challenges to traditional cybersecurity measures, it also presents exciting opportunities for developing new and more robust security protocols. Researchers and cryptographers are actively working to develop quantum-resistant cryptography algorithms and explore the potential of quantum key distribution (QKD) techniques.- Development of quantum-resistant cryptography:
- Post-quantum cryptography algorithms: These algorithms are designed to be resistant to attacks from both classical and quantum computers, ensuring the security of data and communications even in the quantum era.
- Lattice-based cryptography: This approach uses the hardness of certain mathematical problems involving lattices to construct cryptographic primitives that are believed to be secure against quantum attacks.
- Multivariate cryptography: Based on the difficulty of solving systems of multivariate polynomial equations over finite fields, these algorithms offer potential quantum resistance.
-
Hash-based cryptography: This family of cryptographic algorithms, including hash-based signatures and key encapsulation mechanisms, is being explored for its potential resistance to quantum attacks.
-
Quantum key distribution (QKD):
- Principles of QKD: QKD is a method of securely distributing cryptographic keys between two parties by leveraging the principles of quantum mechanics, such as the no-cloning theorem and the Heisenberg uncertainty principle.
- Advantages of QKD over classical key exchange methods: QKD provides an information-theoretic level of security, making it impossible for an eavesdropper to intercept the key without being detected.
- Challenges and limitations of QKD implementation: While promising, QKD faces challenges in terms of distance limitations, hardware requirements, and practical implementation at scale.
By embracing the opportunities presented by quantum computing, researchers and security professionals are working tirelessly to develop countermeasures that will ensure the continued safety and integrity of our digital systems in the face of this disruptive technology.
Real-World Applications and Case Studies
The impact of quantum computing on cybersecurity extends far beyond theoretical discussions, with real-world applications and implications across various industries and sectors.
- Government and military applications:
- Secure communications: Quantum-resistant encryption techniques could be employed to protect sensitive communications between government agencies, military personnel, and intelligence organizations.
-
Cybersecurity for critical infrastructure: Securing critical infrastructure, such as power grids, transportation systems, and telecommunication networks, from cyber threats is a top priority, and quantum-safe solutions could play a crucial role.
-
Financial and banking sector:
- Securing financial transactions: With the rise of digital banking and online financial transactions, the need for robust encryption methods becomes paramount. Quantum-resistant cryptography could safeguard sensitive financial data and transactions.
-
Protecting sensitive data: Banks and financial institutions hold vast amounts of personal and financial data, making them prime targets for cyber attacks. Quantum-safe encryption techniques could help ensure the privacy and security of this sensitive information.
-
Healthcare and biotechnology:
- Safeguarding patient records: Electronic health records contain sensitive personal and medical information that must be protected from unauthorized access. Quantum-resistant encryption could help maintain the confidentiality and integrity of these records.
- Securing research data and intellectual property: In the highly competitive biotechnology industry, protecting proprietary research data and intellectual property is crucial. Quantum-safe solutions could provide an added layer of security for this valuable information.
As quantum computing capabilities continue to advance, the need for quantum-resistant cybersecurity solutions will become increasingly pressing across various industries and sectors, driving further research, development, and adoption of these cutting-edge technologies.
Future Outlook and Recommendations
The impact of quantum computing on cybersecurity is a rapidly evolving field, with ongoing research and development efforts aimed at addressing the challenges and capitalizing on the opportunities presented by this revolutionary technology.
- Ongoing research and development:
- Academic institutions and research laboratories around the world are actively exploring quantum computing algorithms, quantum-resistant cryptography, and quantum key distribution techniques.
-
Collaborations between academia, industry, and government agencies are fostering the rapid advancement of these technologies and their practical applications.
-
Importance of preparing for the quantum era:
- Transitioning to quantum-resistant cryptography: As quantum computing capabilities continue to progress, it is crucial for organizations and governments to begin the process of transitioning to quantum-resistant cryptographic algorithms and protocols.
-
Investing in quantum technologies: Developing and implementing quantum-safe solutions requires significant investment in research, infrastructure, and talent acquisition. Both public and private entities need to prioritize these investments to stay ahead of the curve.
-
Collaboration between academia, industry, and governments:
- Effective collaboration and knowledge sharing among academia, industry, and government agencies are essential for advancing quantum computing research and developing practical cybersecurity solutions.
-
Public-private partnerships and joint research initiatives can accelerate progress and foster innovation in this rapidly evolving field.
-
Ethical considerations and responsible development:
- As with any disruptive technology, the development and deployment of quantum computing and quantum-safe cybersecurity solutions must be guided by ethical principles and responsible practices.
- Addressing issues such as privacy, security, and potential misuse of these technologies will be crucial to ensure their beneficial impact on society. By staying proactive, investing in research and development, fostering collaboration, and adhering to ethical principles, we can navigate the challenges posed by quantum computing while harnessing its immense potential to revolutionize cybersecurity.
Conclusion
As we stand at the cusp of the quantum computing era, it’s clear that the impact on cybersecurity will be profound. While the advent of this revolutionary technology presents formidable challenges to traditional encryption methods, it also ushers in a new frontier of opportunities for developing quantum-resistant security protocols and innovative solutions.
The vulnerabilities exposed by quantum computing serve as a wake-up call, highlighting the need for a proactive approach to cybersecurity. By embracing quantum-resistant cryptography, quantum key distribution techniques, and other cutting-edge solutions, we can fortify our digital defenses and ensure the continued safety and integrity of our data and communications.
However, the path forward is not without its obstacles. Significant investments in research, infrastructure, and talent acquisition will be required to fully harness the potential of quantum-safe technologies. Collaboration between academia, industry, and governments will be crucial in accelerating progress and fostering innovation.
Moreover, as we venture into this uncharted territory, it is imperative that we prioritize ethical considerations and responsible development. The power of quantum computing must be harnessed for the greater good, safeguarding against potential misuse and upholding the principles of privacy, security, and individual rights.
In the face of this quantum revolution, one thing is certain: the field of cybersecurity will never be the same. As we navigate these uncharted waters, we must embrace change, adapt to new realities, and remain vigilant in our efforts to protect our digital world from emerging threats.
The Impact of quantum computing on cybersecurity is a complex and multifaceted challenge, but it is also an opportunity to push the boundaries of innovation and redefine the very notion of secure communication and data protection. With a commitment to continuous learning, collaboration, and responsible development, we can unlock the full potential of this transformative technology while safeguarding the digital foundations of our society.
-
-
 @ 1c6b3be3:73f0ae6f
2024-05-05 04:01:17
@ 1c6b3be3:73f0ae6f
2024-05-05 04:01:17Releases - No Bullshit Bitcoin
BDK v1.0.0-alpha.10: Improved Address API, Simplified Esplora API (1 min) The BDK libraries are releasing v1.0, which includes a fundamental rewrite of their components for Bitcoin applications. This bi-weekly release improves the address API, simplifies the Esplora API, and introduces new structures for easier syncing with Electrum/Esplora. It also removes the generic T from the Wallet and makes KeychainTxOutIndex more range-based. The update includes new features such as enabling the "blocking-https-rustls" feature on the esplora client, modifying KeychainTxOutIndex methods to take ranges of keychains, removing the generic from wallet, simplifying EsploraExt API, and refactoring merge_chains to return the resultant CheckPoint tip. Additionally, a new bdk-persist crate is introduced, and the bdk_esplora chain-source has been updated to make use of new universal sync/full-scan structures.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Solana Primed To Establish Itself As ‘Third Major Crypto Asset’ After Bitcoin and Ethereum: Franklin Templeton - The Daily Hodl Bitcoin Mining: What Is It And How Does It Work? - Bankrate.com
-
 @ 1c6b3be3:73f0ae6f
2024-05-01 16:22:28
@ 1c6b3be3:73f0ae6f
2024-05-01 16:22:28In the digital battleground, a clash of ideologies raged. Alec, a staunch defender of Bitcoin's principles, found himself pitted against Jameson, a self-proclaimed cypherpunk with a taste for chaos.
Jameson's "trivial exploit" unleashed a torrent of blocks, flooding the testnet and disrupting the tireless work of countless developers. Alec watched in horror as their testing ground crumbled under the weight of Jameson's audacity.
Rallying his allies, Alec vowed to reclaim what was rightfully theirs. "He's desecrated our digital sanctuary," Alec proclaimed, his voice echoing through the ether. "We must fight back!"
Jameson, reveling in the chaos, taunted them with his supposed noble cause. "Sometimes, you have to do more than send an email," he sneered, his arrogance palpable.
As the testnet teetered, Alec knew he had to act swiftly. With a few masterful keystrokes, he unleashed a counterattack, his code slicing through Jameson's defenses. The flood subsided, and a new era of resilience dawned.
Jameson slunk back into obscurity, his grand exploit thwarted by the very community he sought to undermine. And Alec stood tall, a beacon of unwavering dedication, proving that in the digital realm, true heroes are forged not by might alone, but by the strength of their convictions.
https://www.youtube.com/shorts/yjHjPdMWpBA
-
 @ 4fda8b10:7bbee962
2024-04-04 08:12:34
@ 4fda8b10:7bbee962
2024-04-04 08:12:34On a weekend in March 2024, I shared and streamed my electronic music as @
Tederon #nostr and received an overwhelming number of heartfelt responses.While doing so, I was building a list of followers that can't be censored or deleted by any company that can interact with me trough chat, stream, music streaming.
In each of the pieces of content I was able to setup split payments, which means all of the contributors instantly got their commissions, with negligable transaction costs and without the platform taking a big cut.
I wrote a piece about this experience including a detailed onboarding and my insights. I invite you to share it with creators as I did with my musical peers!
Onboarding
- I installed amethyst on my Android and damus on my ipad, and created a private public key pair
- I filled in my nostr profile through the Amethyst app and discovered my profile identifier: the npub account for Teder nostr:npub1asuq0pxedwfagpqkdf4lrfmcyfaffgptmayel9947j8krad3x58srs20ap
- I created a bitcoin lightning wallet in walletofsatoshi app, copied the lightning adress and filled the address in profile.
- I added NIP05 verification on my website using a WordPress plugin
- I then created a new post in Damus sharing a short clip of the Teder and TimMey - Rebound EP jam including the
introductionshashtag nostr:nevent1qqsfqh0085arl45js5x7s40tm49xrgw76a0nsdhjpcdq9tpzsweg4hqpp4mhxue69uhkummn9ekx7mqzyrkrspuym94e84qyze4xhud80q38499q9005n8u5kh6g7c04ky6s7qcyqqqqqqg9cttm9 - I received a whole bunch of reactions and zaps, amongst which recommendations to host a stream with my live music on tunestr / zapstr, and to publish the album on wavlake
- That night, I streamed a live set for 40 minutes on zapstr: nostr:nevent1qqsd4sru85vk7mpcq6j5c60w9ku5qwk0m2627hzjvfjgfd3vc5nek6cpzamhxue69uhkummnw3ezu6rpwd5xyctwvuhxumqzyrkrspuym94e84qyze4xhud80q38499q9005n8u5kh6g7c04ky6s7qcyqqqqqqgz275ar
- During the stream, I received some bigger zaps, between 1000 and 10000 SATs per zap
- I then uploaded the EP on wavlake: https://wavlake.com/album/e0d37f7c-aa8b-44b3-b41e-42637e958f91
- I mentioned the release in a couple of replies, and received about 7000 SATs worth of zaps on the songs of the album within a day.
Response
- In about 24 hours I received hundreds of reactions, likes and about 29400 SATs ~ €19. This is more royalties then I've ever received from any streaming platform, and these were immediately liquid in my account ready to be spent on nostr ór converted to fiat to for instance fund my next physical release.
- These rewards include zaps on the reactions and the answering questions from the audience, which is something we are already used to do on other platforms, but were never able to get rewarded for other than brand building.
Insights
- Motivation: Motivation to get back to sharing due to the constant stream of micro payments is very high. Some contributions are only 5 or 21 SATs but it is the fact that someone consciously sent it that really matters, and gives you a sense of worth other than people just trying to build their brand / persona with replies, as is often the case on instagram.
- See my post, the gratitude I feel for these tiny payments is very high: nostr:nevent1qqsxdahe2f2s2kqnvx96juqfdnxnwt69dwveadqun3apwzluvgz097spp4mhxue69uhkummn9ekx7mqzyrkrspuym94e84qyze4xhud80q38499q9005n8u5kh6g7c04ky6s7qcyqqqqqqgwl7ljh
- Receiving small monetary rewards also has the interesting side effect of reciprocity, and also entices you to support others with the SATs you have received in your wallet.
- Portability and ownership over fanlist: Being able to take your following/fans and content with you when you are moving back and forth in different applications (such as the Twitter like environment, the Twitch like streaming environment and the Spotify like music catalog environment). In comparison, starting a new TikTok from scratch takes a lot of time and energy, even though the format of sharing short clips and repurposing content from others is pretty cool.
- Evergreen content: Having new followers on different applications find your older content in the same environment, and being able to send micro payments to all that content transparently is very encouraging to make you want to create and share higher quality and more evergreen content.
- Collaboration commission: Collaborations are amongst my favorite activities while creating. Being able to set up payment splits on each separate piece of content ( Even on a single Tweet!) is very encouraging to both creator and fan. There is just something enticing about contributing knowing that sending that zap will land some value to both the musicians, the visual artist that made the artwork, and for instance the videographer that shot the video. And all that without needing to settle afterwards or pay high transaction fees.
- Community efforts: Imagine producing a radio show with live performances from multiple community members and sharing all zaps between involved members equally, or transparently raising money for specific goal / charity!
Opportunities for music artist groups / collectives / labels (such as Petite Victory Collective)
I see very interesting opportunities for both PVC and online radio sites such as massive radio to use this network for bringing attention to our music, events and streams. The whole decentralised / no-middleman-company-in-between really resonates with the goals and setup of the community.
- Stream shows, live events and massive radio streams and enable receiving of streaming sats rewards from listeners.
- Setting up split payments for content to divide rewards amongst both musicians, visual artists, vj, radio hosts etc.
- Stream live shows / dj sets to promote albums and releases.
- Provide live shows / streams / music / DJ at nostr / bitcoin events while the network is still growing.
- Selling merchandise with crypto payments, cutting out platform and transaction costs and splitting rewards amongst contributors.
- Integration of audience in live streams, taking inspiration for jam / improvisation from crowd.
Thank you for taking the time to read this article, feel free to comment with your thoughts or reach out if you have further questions about these topics or onboarding you music onto nostr!
-
 @ efa6abd0:a4970369
2024-04-29 20:09:09
@ efa6abd0:a4970369
2024-04-29 20:09:09Time stands still under @nobody timelines, as at least two women who were frequent nostr posters stopped using nostr recently. The reasons are complex and varied, but it offers an opportunity to talk about possible ways that may help guide conversations toward more signal.
When it comes to dealing with hate, abuse, and behavior that could be described as unhealthy, most social media looks at adding rules of what not to do. However, we should question how well that approach has worked in the past on other social networks, if it is likely to scale, and whether nostr may be much better suited for finding different solutions.
Social media is complicated, just like the people who speak their voices through it. Unfortunately, some people can create chaos to scare and quiet down other voices, in particular, those of women. Some social media attacks can feel personal and disruptive. As they carry on over time, they can wear people down, making them more sensitive to everyday conversations. A voice lost to an unhealthy environment is a voice too many.
nostr:note1fprernz6tljde6anfuyn0yvzp7n7lfe43qxgm6fejm590ed35fgq88yytd
The what not to do approach.
Most platforms have tried to deal with abuse by trying to remove anything related to reported cases and other learnings across time. It is a difficult labor, because what is “acceptable” content depends on the times, context, and culture. Although there may be moments where these actions could be useful, they run the risk of not being specific enough or their use being misunderstood, over-applied, or gamed.
By adding parameters of what is not acceptable, unexpected content may fall under that umbrella. For example, words used in gaming can reflect violence. Sometimes, conversations within black communities can carry more expletives. People can misread, misunderstand, or feel offended by sarcasm, memes, and subcultures. Sometimes, removing specific words can prevent people from discussing serious matters, like those who are trying to bring awareness to an issue, or educational information to prevent further harm from a difficult situation.
No solution is perfect, and, sometimes, in trying to create a “safe” environment, the results are very different from the desired effects. Muting, blocking and removing certain words or people could be abused to quiet down those voices nostr is trying to protect and encourage. People can find ways around these rules to still get chaotic content through.
As social media scales, the content that needs to be removed can become an unwieldy number. Aside from reports, numerous man hours of content review, and the catch-all-word, algorithms, take over. Concentrating most efforts on what to remove, could easily become too broad a brush, leading to the opposite effect of what nostr is trying to avoid: censorship.
There are no silver bullets, but that does not mean there aren’t other options.
What if, instead, we focus on what to do?

We should not overlook what protects us: our people, those real people whose voices we choose to follow. They may be the best compass on the information worthwhile.
Web of trust tools
I remember earlier days, when the global feed was messier. Damus had added the option to blur images for people you did not follow. We had some early spamming incidents, that I did not notice, until people I followed started speaking about them, because all of those images were blurred for my global feed. I still keep that feature on.
A web of trust allows us to give priority to the content of the people we follow, often extending to the content of the people they follow. Various web of trust tools are already in use in different clients. If these features improve over time and are more widely adopted, people may reach more of the content they want without the extra noise.
Possible features
Replies
Showing top replies as those of the people you follow and who they follow. The rest of the replies could be hidden under an extra click.
An additional option could narrow down replies to only follows, or open it up to everyone, if you’re comfortable with that.
DM’s
Priority section for your web of trust, based on what you're comfortable with:
- People you have replied to
- People you follow
- People you follow and their follows
- A specific list of people of your choice
Have the option of removing people from your main DM’s tab.
Mentions and Notifications
I have not yet heard of a similar treatment for mentions, like that of DM’s, but it could ease some of the negativity if priority was given to what you’re most comfortable with:
- People you follow
- People you follow and their follows
- A specific list of people of your choice
- Everyone
Your People
- Easy-to-spot icon that you follow someone
- Icon for someone within your network
- Impostor flags on cloned accounts you do not follow
- Showing the people you follow are following someone you're thinking of following
What are other possible tools for Web of Trust?
Content Discovery
Another important aspect for keeping the signal high on nostr is content discovery. Global has been shifting more and more to topic based discovery. A good step forward. If people are able to find more conversations around the topics they love, their experience is likely to be more positive, and to go deeper. This may lead them to discover unique niche communities with supportive like-minded people. This focus on topics may help lead attention to signal rather than noise.
An issue may be spam on hashtags, which is often content discovery for topics. We tend to follow hashtags and see that within our home feed. If the hashtags start getting spammy, what would be good solutions? Perhaps global feed should be specific to topics, and home feed for the people we follow. Making it easier to unfollow hashtags and discover new ones.
Topic hashtags could also be limited to our follows or network, but that would prevent some of the discovery process and be more likely to lead to echo chambers.
Perhaps navigation could be simplified with just one home feed, instead of global and home, but with options to switch between different options: List of follows, follows follows, topics, specific lists you put together, curated lists, communities, specific relays, all…
What is the default?
Settings are an obscure feature that shines on nostr with unique choices. However, if people join nostr used to the workings of other apps, they are unlikely to make it into the Settings. Some protective features could be considered as defaults. Other options for customization could be displayed within specific elements without needing to go into the settings.
As feeds offer more choices for looking at your content, there may be good ways to limit or open up content shown, based on how you’re feeling and what social situations you may be in. If you’re getting too much noise, you may want to add more limits on the content you see. If you’re trying to discover something new, you may want to explore and remove some of the limits.
Outbox model
Another present-future feature of nostr will be relying on the outbox relay model. It offers the possibility of retrieving the notes for those people who matter the most to you. It doesn't matter where people post, outbox will retrieve the notes, even from a small relay, hence, preventing their censorship. Perhaps then, blastr’s purpose will shift from sending your notes out to most relays, into making sure everyone knows where to find your notes by sending out your latest relay list and profile information.
Delete vs. Zen
Deleting something is often a defensive measure. Unfortunately, it is an avenue often taken by those getting bullied in some way, instead of by those generating the chaos. What we often miss when we feel attacked is that having a voice on social media is an important meaningful aspect of our lives. The need to restart your social media experience takes time, and nostr will miss out on your perspective.
Although our notes remain on nostr, if someone is in need of time off, there could be a midway option before choosing to delete. A “zen mode” could be activated for those moments where you need a little time off or to tone down the noise. The app you use could toggle-on all those features that can improve on health. Your notifications could be turned off, all of your mentions and feeds could be limited to follows. Perhaps you could even segment your follows to only see specific accounts on your home feed of those people closest to you.
Practicing the Art of Zenstr

We can all have difficult situations to deal with, whether in our personal lives, work lives, or how we connect and interact on social media. They seem separate, but they’re all a part of us, and what is happening in one area of our lives can affect the rest. As we dive into nostr, we may notice that the changes in incentives are leading to product features that care more about promoting a healthy environment. Nostr cares about its people. Timelines are not focused on incendiary notes that lead to more attention and hence more ad sales, but we can still run into negative feedback loops or the rare but loud voice who wants to generate conflict.
When we run into inflammatory comments, we must ask ourselves: Is it constructive to react to this note? If we feel too emotional, chances are, it may be time to step away from the screen for a while, refresh our spirit, and come back in a healthier way.
What if we can also ask what we can do to improve nostr? Is there content you wish existed? Can you create it? Is there a conversation you wish you could have, ask the questions. Start the hashtags. Be what you wish nostr was.
Only comment on what you feel comfortable replying to. Ignore the noise.
Being on nostr also means unlearning. Social media has placed more focus on reporting and cancel culture, but people on nostr are instead trying to learn from each other, respecting each other’s views and trying to share information you may be unaware of. It could be through a weird meme, but that’s nostr. We can be a little weird.
As people try to protect themselves from content they dislike, mute and block may be first on their mind, in some difficult cases, that may only be a temporary fix as people could circumvent that with additional npubs. The opposite is also true, you could flag someone for a single post, without paying any attention to what their voice offers on nostr, or without digging deeper into what they tried to say. Reading text is not the same as listening to people, sometimes we can give people a chance. Just because we disagree in points of view, does not mean we cannot learn something from each other.
On more chaotic cases, however, where you are experiencing abuse on nostr, do not hesitate to ask for help from the people in your community and make it known to developers on nostr. The product makers can help. In learning from your experience, you may help people have better tools to shape a healthier nostr in the future. You are not alone, and you can be a part of the solution.
As Web of Trust gets stronger, it is less likely that people who are only trying to create chaos will be able to get their messages across. People wanting conversation are unlikely to follow them, hence, not receiving their noise.
We can all use personal time away from screens, but out of choice, not out of need to leave an unhealthy environment. People should have more tools to help shape their nostr home in whichever way they want it to be. Nostr has always been about choice. Knowing that you can arrive on nostr and have a voice is a gift. We should protect it.
-
 @ c5fae15f:ea1126bf
2024-05-05 03:06:04
@ c5fae15f:ea1126bf
2024-05-05 03:06:041 - Quitar TODAS as dívidas;
2 - Ter mais de uma fonte de renda;
3 - Se qualificar (estudos, cursos, conhecimento);
4 - Um emprego digno e justo;
5 - Juntar grana (minimalismo ajuda);
6 - empreender ou passar em um bom concurso;
7 - Cuidar da sua saúde (alimentação, exercícios físicos, arte marcial);
8 - Ter um carro e/ou moto (popular para o dia a dia);
9 - Criar reserva de valor em auto custódia de bitcoin;
10 - Controle TOTAL da LIBIDO (mulheres só irão atrapalhar a jornada);
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ d34e832d:383f78d0
2024-05-05 15:34:18
@ d34e832d:383f78d0
2024-05-05 15:34:18Bitcoin, renowned for its P2P nature, also exemplifies how to secure a digital currency against a myriad of potential threats. Here’s a comprehensive look at the various measures in place designed to uphold the security of the Bitcoin network
Understanding Bitcoin's Security Measures
1. Proof of Work (PoW)
The foundation of Bitcoin's resilience is the Proof of Work algorithm. It compels miners to solve complex mathematical problems to validate transactions and mine new blocks, making any attack costly and technically demanding.
``` Impact of PoW:
"PoW makes it economically unsustainable for attackers to alter any aspect of the blockchain."
```2. Mempool Policies
Bitcoin controls which transactions are allowed into the next block through strict mempool policies. This prevents spam transactions which can clog the network under an array of transactions with minimal fees.
``` Role of Mempool Policies:
"By enforcing rules about the format, size, and fee requirements, Bitcoin ensures only legitimate transactions are processed." ```
3. Peer Address Bucketing and Protection
To counteract eclipse attacks—where an attacker might dominate a node's connections—Bitcoin nodes utilize peer address bucketing. This diversity prevents attackers from isolating a node from the rest of the network.
``` Preventing Eclipse Attacks:
"Diverse peer connections essential for the decentralization that Bitcoin aims for." ```
4. Blockrelay-only Connections
These connections allow nodes to receive blocks without exposing transaction details, effectively minimizing the risk of an eclipse attack.
5. Misbehaving Peer Disconnection
Nodes monitor peers consistently and disconnect from those that show signs of suspicious activity or protocol violations, which preserves network resources and counters denial-of-service attacks.
``` Monitoring Peers:
"Active surveillance of peer activities ensures a robust defensive perimeter." ```
6. Peer Rotation and Eviction
Regular rotation and eviction of peers ensure no single participant can monopolize a node’s network, enhancing security against both Sybil and eclipse attacks.
7. Protected and Anchor Peers
Certain peers are assigned as 'protected' or 'anchor' to ensure nodes have stable, reliable connections to well-known, good actors within the network. This defense strategy ensures continuity and reliability.
Evolving Threats and Proactive Improvements
The Bitcoin network’s security measures are not static; they evolve to address new vulnerabilities and sophisticated attack vectors as they arise. Discussions and developmental insights can be seen actively on platforms like GitHub under various pull requests and issues discussion, enriching community engagement and development.
Closing Thoughts
Bitcoin’s multilayered security strategies demonstrate its architectural sophistication in safeguarding users' assets. Through proactive community involvement and constant technological advancements, Bitcoin continues to stand as a paragon of secure, P2P digital energy. Interested readers can dive deeper into specific discussion and updates on GitHub linked below.
Further Reading and Sources
Stay secure and informed as we forge ahead in the continually evolving landscape of Bitcoin.

Fortifying the Bitcoin Lightning Network: A Security Overview
The Bitcoin Lightning Network, an innovative layer enabling faster transactions than the Bitcoin main chain, faces unique security challenges intrinsic to its design as a real-time gross settlement system. Here, we delve into the various protective strategies vital for safeguarding Lightning nodes against unauthorized access and potential attacks, tailored to both new and seasoned participants in the cryptocurrency space.
Holistic Approach to Security
The security of a Lightning node isn't about focusing on one single facet; it's about fortifying every layer of the system.
```
"Security for a Lightning node encompasses every layer of the system, from network access points to the storage of private keys." ```
This holistic approach forms the backbone of effective security strategy, emphasizing that a chain is truly only as strong as its weakest link.
Regular Updates and Patches
One of the most crucial practices in maintaining a secure node is keeping the software up to date. This includes:
- Regular updates to Lightning software like LND, c-lightning, and Eclair
- Applying patches to the node's operating system to close any vulnerabilities that could be exploited by malicious actors
``` Consistent Updates:
"Staying updated with the latest software patches is essential to protect against known exploits and vulnerabilities." ```
Limiting Exposure
Given the experimental stage of the Lightning Network, limiting the amount of funds put at risk is wise:
- Only allocate an amount of money that you are comfortable potentially losing
- Use multiple nodes to diversify risk rather than placing all funds into a single node
Secure Storage of Keys
The keys that control funds on the node must be securely stored because they are a prime target for theft:
- Encrypting the hard disk where keys are stored
- Utilizing hardware modules designed for secure key storage
- Implementing multi-factor authentication to increase security layers
``` Key Security:
"The secure storage of keys is paramount, involving strategies ranging from disk encryption to the use of specialized hardware security modules." ```
Enhanced Network Security Measures
Network security can prevent many external attacks:
- Setting up robust firewalls
- Monitoring network traffic for any unusual activities
- Securing endpoints to guard against intrusion
Educational Empowerment
Encouraging continuous education regarding security updates, threats, and best practices is essential. Knowledge empowers users to make informed decisions and recognize potential security threats before they manifest.
Community and Developer Support
Leveraging community knowledge and developer support can provide solutions and guidance for any security concerns that arise:
- Engage with forums and read publications from trusted sources
- Participate actively in community support channels like Lightning Dev mailing list
Closing Case
The security of the Bitcoin Lightning Network is a dynamic, ongoing process that demands vigilance, proactive strategies, and a well-rounded approach. By understanding and implementing these detailed protective measures, users and operators can significantly enhance the security integrity of their Lightning operations.
Further Learning and Official Documentation
For those looking for more depth on operating a Lightning node securely, consider the following resources:
- The GitHub Lightning Book provides extensive information on node operations and security.
- Engaging with the developmental community through active forums and mailing lists can offer real-time insights and help.
Secure, learn, and evolve; your journey in the Lightning Network awaits!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ c11cf5f8:4928464d
2024-05-05 14:22:20
@ c11cf5f8:4928464d
2024-05-05 14:22:20Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 1c6b3be3:73f0ae6f
2024-04-28 07:18:02
@ 1c6b3be3:73f0ae6f
2024-04-28 07:18:02🍵 "btc | bitcoin | lightning network | asic" - Google News
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ d830ee7b:4e61cd62
2024-04-27 04:29:41
@ d830ee7b:4e61cd62
2024-04-27 04:29:41มีใครเกิดท่านได้เห็นอะไรแบบนี้บ้างไหมครับ?

คุณเคยสัมผัสกับการสื่อสารแบบเรียบง่ายที่แทบไม่ต้องพึ่งเทคโนโลยีเลยบ้างไหม?
เช่น การขีดเขียนลงบนต้นยูคาลิปตัสหรือตามผนังสังกะสี กิจกรรมเหล่านี้เผยให้เห็นถึงความปรารถนาอันแท้จริงของมนุษย์ที่จะทิ้งร่องรอยบางอย่างไว้ในโลกใบนี้ ผมเคยเป็นหนึ่งในคนที่หลงใหลในการใช้เครื่องมือง่ายๆ เช่น ปากกาเมจิกสำหรับเขียนบนประตูห้องน้ำตามปั๊มน้ำมันเพื่อฝากเรื่องราวเอาไว้ ไม่นานมานี้ผมตระหนักได้ว่าการกระทำเหล่านี้คือรูปแบบของการสื่อสารสาธารณะ หรือที่เรียกว่า "Social media communication" ในยุคปัจจุบัน
ความปรารถนาในการสร้างแพลตฟอร์มสื่อสารของตัวเองนี้ไม่ใช่เรื่องใหม่ มันเป็นสัญชาตญาณที่ฝังรากลึกในมนุษย์มาตั้งแต่สมัยการขีดเขียนผนังถ้ำ แสดงให้เห็นว่ามนุษย์เรามีความต้องการแบ่งปันความคิดและข้อมูลมาอย่างต่อเนื่อง
กิจกรรมเหล่านี้ไม่ได้เป็นเพียงการทิ้งข้อความเอาไว้ให้คนอื่นพบเห็นเท่านั้น แต่ยังสะท้อนถึงการกระทำส่วนบุคคลที่มาจากการตัดสินใจเอง ไม่ผ่านการวางแผนจากศูนย์กลาง มันเป็นการแสดงความคิดสร้างสรรค์และการแลกเปลี่ยนข้อมูลที่เป็นอิสระ ซึ่งสอดคล้องกับแนวคิดของกระบวนการตลาดที่ให้อิสระแก่บุคคลในการแสดงออกและปรับตัวตามเป้าหมายส่วนตัว
การขีดเขียนลงบนต้นไม้และผนังถ้ำในอดีต จึงไม่ต่างอะไรจากการโพสต์ข้อความหรืออัปเดตสถานะบนโซเชียลมีเดียในยุคนี้ ทั้งหมดล้วนเป็นการสื่อสารที่มีชีวิตชีวาและมีพลัง ผ่านยุคสมัยและเทคโนโลยีที่เปลี่ยนแปลงไปจนกลายเป็นส่วนหนึ่งของวัฒนธรรมการสื่อสารที่ไม่เคยหายไปจากหัวใจของเรา
มนุษย์เรามีความต้องการที่จะถ่ายทอดความคิดและฝากความรู้สึกไว้ให้กับโลกนับตั้งแต่อดีต ไม่ว่าจะเป็นการขีดเขียนลงบนต้นไม้หรือการฝากข้อความไว้ใต้หลังคาสังกะสี ความปรารถนาเหล่านี้ได้ก้าวไปสู่รูปแบบดิจิทัลที่มีประสิทธิภาพและขอบเขตที่กว้างขึ้น ทำให้เราสามารถสื่อสารข้ามพรมแดนไปทั่วทุกมุมโลกได้อย่างไม่มีขีดจำกัด นวัตกรรมและการปรับตัวนี้คือลายเซ็นที่ชัดเจนของการก้าวหน้าในประวัติศาสตร์มนุษยชาติ ซึ่งทั้งหมดนี้เกิดจากการตัดสินใจและการกระทำของบุคคลแต่ละคนที่ต้องการจะทิ้งรอยทรงจำไว้ในโลก
การทิ้งข้อความในที่สาธารณะนั้น.. เกิดจากเหตุผลหลากหลายซึ่งซับซ้อนและลึกซึ้งกว่าแค่การสื่อสารแบบตัวต่อตัว บางครั้งมันอาจเกี่ยวข้องกับความต้องการที่จะเผยแพร่ความคิดหรือข้อความไปยังกลุ่มคนที่กว้างขึ้น หรืออาจเป็นการสร้างความสัมพันธ์กับคนรุ่นต่อไป ในทางหนึ่ง.. มันอาจเป็นเพียงการฝากความทรงจำส่วนตัวเท่านั้น (เราจะวางเรื่องความมือบอน ศีลธรรม และการรักษาความสะอาดไว้ก่อนนะครับ)

แต่สิ่งที่สำคัญที่สุดคือความปรารถนาในการเชื่อมต่อกับชุมชนหรือการสร้างความเป็นเอกภาพ มนุษย์เราเป็นสัตว์สังคมที่ต้องการจะแบ่งปันและประสานงานกับผู้อื่นในชุมชน เราไม่เพียงแต่สื่อสารเพื่อแลกเปลี่ยนข้อมูล แต่ยังสร้างปฏิสัมพันธ์ทางสังคมที่หลากหลายและยั่งยืนผ่านการขีดเขียนหรือการส่งข้อความสาธารณะ
นอกจากนี้.. การกระทำเหล่านี้ยังเป็นการสะท้อนถึงความปรารถนาที่จะถูกจดจำหรือความเป็นอมตะของเรา เป็นการยืนยันว่าการกระทำของเราจะยังคงตราตรึงอยู่ในความทรงจำของผู้คนนานหลังจากที่เราจากไป และเป็นการแสดงออกถึงตัวตนและการมีส่วนร่วมในประวัติศาสตร์ ด้วยการสลักชื่อและวันที่บนต้นไม้ เราทิ้งร่องรอยแห่งการมีอยู่ที่ไม่เพียงแต่ตัวเราเท่านั้นที่ระลึกถึง แต่สำหรับทุกคนที่เดินผ่านไปมาในยุคสมัยนั้นและต่อไป
เมื่อโลกก้าวเข้าสู่ยุคดิจิทัลและโซเชียลมีเดีย.. มันเป็นเสมือนการระเบิดของความปรารถนาที่เรามีมาตั้งแต่อดีตในรูปแบบใหม่ๆ แพลตฟอร์มออนไลน์ทำให้เราสามารถเผยแพร่เรื่องราวและประสบการณ์ของตัวเองไปยังผู้ชมที่กว้างขึ้นได้อย่างไม่รู้จบ ด้วยการเข้าถึงและการกระจายข่าวสารที่รวดเร็วและง่ายดายยิ่งขึ้น การแชร์ข้อมูลในทันทีและการเชื่อมต่อกับผู้คนทั่วโลกได้อย่างไม่มีพรมแดน ทำให้โซเชียลมีเดียกลายเป็นอีกหนึ่งมิติของการสื่อสารที่ไม่เพียงแต่เฟื่องฟู แต่ยังก่อให้เกิดชุมชนออนไลน์ที่มีอิทธิพลอย่างมากต่อวิถีชีวิตและวัฒนธรรมในสังคมสมัยใหม่

ความต่าง
แต่เมื่อพิจารณาถึงการสื่อสารแบบสาธารณะในอดีตและปัจจุบัน มีความแตกต่างกันอย่างมาก การขีดเขียนบนต้นไม้ในอดีตนับเป็นการสื่อสารแบบกระจายศูนย์อย่างแท้จริง ทุกคนสามารถเพิ่มข้อความของตัวเองได้อย่างอิสระ ส่วนแพลตฟอร์มออนไลน์ในปัจจุบันนั้นถูกรวบรวมและควบคุมอย่างเข้มงวด ด้วยกฎเกณฑ์และอัลกอริทึมที่กำหนดว่าข้อความใดจะถูกเผยแพร่หรือถูกซ่อนไว้จากสายตาของผู้ใช้จำนวนมาก
พื้นที่ดิจิทัลมีอำนาจในการควบคุมเนื้อหาที่จะถูกแชร์และเผยแพร่ สามารถลบหรือบล็อกเนื้อหาที่ไม่เป็นไปตามนโยบายหรือกฎหมาย ซึ่งแน่นอนว่าต้นยูคาลิปตัสและสถานที่สาธารณะในอดีตไม่สามารถทำได้ ความเป็นส่วนตัวและอิสรภาพในการแสดงออกถูกตั้งคำถามในโลกโซเชียลมีเดีย ซึ่งมีการกำหนดกฎเกณฑ์และมารยาททางสังคมใหม่ๆ ที่จำกัดการปฏิบัติตามนโยบายการใช้งานและการแสดงออก
การขีดเขียนตามธรรมชาติไม่ได้มีการระบุตัวตนอย่างชัดเจน แต่ในโลกออนไลน์ ข้อมูลส่วนบุคคลและตัวตนสามารถถูกติดตามและบันทึกไว้อย่างละเอียด ความเป็นส่วนตัวในโลกดิจิทัลจึงเป็นเรื่องที่น้อยลงอย่างชัดเจน แม้แพลตฟอร์มเหล่านี้จะพยายามให้เครื่องมือในการควบคุมความเป็นส่วนตัวก็ตาม
การสื่อสารสาธารณะในอดีตมักเปิดเผยและทำให้เกิดวัฒนธรรมแห่งการแบ่งปันอย่างออแกนิค ทว่าเมื่อเข้าสู่ยุคดิจิทัลและโซเชียลมีเดีย การเชื่อมต่อกันกลายเป็นเรื่องรวดเร็วและขยายขอบเขตไปทั่วโลก แต่ก็อาจนำไปสู่ปัญหาของ echo chambers และการแพร่กระจายข้อมูลที่ผิดเพี้ยนได้
การสื่อสารในโลกปัจจุบันถูกควบคุมด้วยกฎเกณฑ์และอัลกอริทึมอย่างชัดเจน นำไปสู่การสร้างเครือข่ายสังคมที่ซับซ้อนมากขึ้น ซึ่งเสรีภาพในการแสดงออกก็ต้องอยู่ภายใต้กรอบที่แพลตฟอร์มกำหนดไว้ ผู้ใช้งานจำเป็นต้องหาจุดสมดุลระหว่างการปกป้องความเป็นส่วนตัวและการใช้เสรีภาพทางดิจิทัลอย่างมีความรับผิดชอบ

ความเปลี่ยนแปลง
มาติดตามกันดูว่าการสื่อสารทางสังคมสาธารณะได้เปลี่ยนแปลงไปอย่างไรตั้งแต่อดีตจนถึงปัจจุบัน
ในยุคกลาง, การใช้กระดาษและการเขียนจดหมายเริ่มเป็นที่นิยม แม้จะมีการสื่อสารตรงไปยังบุคคลที่ต้องการ แต่ก็ยังคงมีโอกาสในการเปิดเผยและส่งต่อข้อมูลได้ นอกจากนี้กระดาษยังถูกใช้เป็นป้ายประกาศข่าวสาร แต่บางครั้งก็ถูกควบคุมเนื้อหาโดยเจ้าของพื้นที่ หนังสือพิมพ์และนิตยสารในภายหลังได้นำการกระจายข่าวสารและความคิดเห็นไปสู่ผู้อ่านจำนวนมาก การเผยแพร่ข้อมูลถูกควบคุมอย่างเข้มงวดโดยบรรณาธิการและสำนักพิมพ์
เมื่อเข้าสู่ยุคของวิทยุและโทรทัศน์ การสื่อสารมวลชนได้ถูกปฏิวัติ ข้อมูลและความบันเทิงสามารถส่งถึงมือผู้ชมและผู้ฟังได้อย่างรวดเร็ว แต่ยังคงอยู่ภายใต้การควบคุมของรัฐและผู้ผลิตเนื้อหา

เมื่อโลกของเราถูกแนะนำให้รู้จักกับเครือข่ายอินเทอร์เน็ตในทศวรรษที่ 90 เราได้พบกับการปฏิวัติวิธีการสื่อสารผ่านห้องสนทนาและฟอรั่มออนไลน์ ที่นี่คือที่แห่งการแลกเปลี่ยนความคิดเห็นและข้อมูลโดยไม่มีข้อจำกัด โดยมีการดูแลจากผู้ดำเนินระบบและนักพัฒนาซอฟต์แวร์ที่คอยอำนวยความสะดวกเพื่อให้แพลตฟอร์มเหล่านี้ทำงานได้อย่างราบรื่น
ในที่สุด อิสรภาพในการสื่อสารและการแสดงออกของมนุษย์ก็เริ่มถูกจำกัดมากขึ้นเรื่อยๆ ผ่านทางกาลเวลา จนกระทั่งมันดูเหมือนจะสูญเสียไปในยุคปัจจุบัน ทำให้เราต้องพิจารณาและตั้งคำถามถึงค่านิยมและผลกระทบที่เกิดจากการควบคุมเหล่านี้ต่อสังคมในอนาคต
เมื่อโลกเราก้าวเข้าสู่ยุคอินเทอร์เน็ตในทศวรรษที่ 90 เราได้พบกับปรากฏการณ์ใหม่ในการสื่อสาร เริ่มจากห้องสนทนาออนไลน์และฟอรั่ม ซึ่งในยุคนั้น IRC (Internet Relay Chat) นับเป็นการเริ่มต้นการพูดคุยออนไลน์อย่างอิสระที่สุด ผู้ที่ได้สัมผัสก็คงต้องมีอายุไม่น้อยเลยทีเดียว..
การปรากฏตัวของฟอรั่มออนไลน์เช่น Usenet และ Bulletin Board System (BBS) ได้เปิดโอกาสให้ผู้คนจากทั่วทุกหนแห่งรวมตัวกันและแลกเปลี่ยนข้อมูลในหัวข้อที่หลากหลาย ซึ่งต่อมาได้นำไปสู่การเกิดขึ้นของบล็อก อย่างเช่น Blogger ที่ให้โอกาสทุกคนเผยแพร่ความคิดและเรื่องราวของตนได้อย่างอิสระ บล็อกและวิกิพีเดียได้นำเสนอเสรีภาพที่ไม่เคยมีมาก่อนในการเผยแพร่และแก้ไขเนื้อหาที่สามารถช่วยเหลือสาธารณะได้ มันเป็นการเปิดโอกาสใหม่ที่ทุกคนจะสามารถเป็นทั้งผู้ให้และผู้รับข้อมูล
MSN Messenger ที่เปิดตัวในปี 1999 และเป็นหนึ่งในบริการแชทเรียลไทม์แรกๆ ที่ได้รับความนิยมสูงสุดในยุคแรกของอินเทอร์เน็ต ด้วยความสามารถในการสื่อสารทันที การส่งไฟล์ และฟีเจอร์การสนทนาด้วยเสียงและวิดีโอ

ในช่วงต่อมา.. เว็บบอร์ดได้เข้ามาช่วยทำให้การสนทนาบนฟอรั่มเป็นเรื่องง่ายขึ้น และได้มีการจัดการเนื้อหาที่ดียิ่งขึ้น จากนั้นก็เป็นการปรากฏตัวของ Frienster, MySpace และ Hi5 ในต้นยุค 2000 ซึ่งเป็นสื่อสังคมออนไลน์แรกๆ ที่เปลี่ยนแปลงวิธีการติดต่อสื่อสารและการแบ่งปันเนื้อหาของเราไปอย่างสิ้นเชิง

ในปี 2004, Facebook ได้ถือกำเนิดขึ้น และได้เริ่มต้นจากการเป็นเครือข่ายสังคมของนักศึกษามหาวิทยาลัยก่อนที่จะเปิดตัวให้สาธารณชนเข้าถึงในปี 2006 ในปีเดียวกันนั้น Twitter ก็เกิดขึ้น ให้โอกาสผู้คน "ทวีต" ข้อความสั้นๆ และแบ่งปันข้อมูลกันอย่างรวดเร็ว (ตามด้วย Instagram, Snapchat, LINE, WeChat และ TikTok ฯลฯ ที่ปรากฏตัวต่อมา) แพลตฟอร์มเหล่านี้ได้มีบทบาทในการเปลี่ยนแปลงวิธีที่เราสร้างชุมชนและเครือข่ายสังคม และไม่เพียงแค่นั้น มันยังได้ช่วยให้การบำรุงรักษาความสัมพันธ์ทางสังคมเกิดขึ้นได้ง่ายขึ้นด้วย ชุมชนเหล่านี้ได้เติบโตขึ้นอย่างอิสระโดยไม่มีการกำหนดจากรัฐ (โดยเฉพาะบนแพลตฟอร์มที่ไม่ถูกควบคุมเช่น Nostr ซึ่งอาจจะไม่ได้ถูกกล่าวถึงในบทความนี้)
การเข้าสู่ยุคโซเชียลมีเดีย โดยเฉพาะอย่างยิ่ง Facebook ได้กำหนดบทบาทหลักในการก่อร่างสร้างเครือข่ายสังคมใหม่ ซึ่งนอกจากจะทำให้การแลกเปลี่ยนข้อมูลเป็นไปอย่างสะดวกสบายแล้ว ยังมาพร้อมกับการควบคุมอย่างเข้มงวดเกี่ยวกับเนื้อหาและข้อมูลส่วนบุคคลที่มีผลกระทบอย่างมากต่อสิทธิส่วนบุคคลและเสรีภาพในการแสดงออก
การก้าวข้ามจากการสื่อสารตามธรรมชาติและกระดาษป้ายประกาศไปสู่วิวัฒนาการทางเทคโนโลยี ทำให้เราเข้าสู่โลกใหม่ที่การควบคุมข้อมูลและการสื่อสารถูกบริหารจัดการโดยผู้มีอำนาจทางเทคโนโลยี เกือบทุกการสื่อสารในปัจจุบันถูกจำกัดและดำเนินการผ่านแพลตฟอร์มกลางที่มีกฎระเบียบและนโยบายการใช้งานที่ชัดเจน

ความกังวล
ในตลาดที่ผู้บริโภคมีตัวเลือกมากขึ้น บริษัทต่างๆ จำเป็นต้องปรับปรุงบริการและสินค้าของตนเพื่อตอบสนองต่อความคาดหวังของลูกค้าที่เปลี่ยนไป นี่คือการเปลี่ยนแปลงวิถีชีวิตและวัฒนธรรมของเราในแบบที่ไม่เคยเห็นมาก่อน (ก่อนจะมาถึงยุคที่แพลตฟอร์มที่ได้รับความนิยมสูงกำลังพยายามจะสนตะพายและจูงจมูกลูกค้าในยุคปัจจุบัน)
การพัฒนาของการสื่อสารดิจิทัลไม่เพียงแต่สะท้อนถึงการเปลี่ยนแปลงของเศรษฐกิจและสังคมเท่านั้น แต่ยังเปลี่ยนแปลงวิธีที่เรามองและรับรู้โลกรอบตัวเรา มันสร้างความคาดหวังใหม่ๆ และขยายโอกาสให้เรามีส่วนร่วมกับชุมชนของเรามากขึ้น
อย่างไรก็ตาม.. อำนาจของแพลตฟอร์มใหญ่ๆ กำลังมีผลกระทบที่ลึกซึ้งต่อสังคมสมัยใหม่ สร้างความกังวลที่ไม่คาดคิดต่อผู้ใช้และประชากรโลก เหล่าแพลตฟอร์มใหญ่เหล่านี้สามารถควบคุมกระแสข้อมูลที่ผู้ใช้จะเห็นได้ ทำให้เกิดการกรองข้อมูลหรือนำเสนอข้อมูลที่มีอคติ ประเด็นนี้มีผลให้เกิดการบิดเบือนความจริงและข้อมูลที่ถูกนำเสนอ
เรายังเห็นการสร้าง 'Echo chamber' และ 'Filter Bubbles' โดยปรับเนื้อหาให้ตรงกับความชอบและพฤติกรรมของผู้ใช้ ซึ่งส่งผลให้ผู้คนมองเห็นเฉพาะข้อมูลที่พวกเขาพร้อมจะเห็นด้วยเท่านั้น นำไปสู่ความคิดที่ไม่หลากหลายและการแบ่งแยกความคิด มีการเสพติดแพลตฟอร์มอันเกิดจากอัลกอริทึมที่ออกแบบมาให้ผู้ใช้ใช้เวลาอยู่บนแพลตฟอร์มมากที่สุด ซึ่งอาจนำไปสู่พฤติกรรมเสพติดที่เป็นอันตรายต่อสุขภาพจิตและร่างกาย
การละเมิดความเป็นส่วนตัวจากการเก็บรวมข้อมูลส่วนบุคคลโดยไม่มีขอบเขตที่ชัดเจน ส่งผลให้เกิดการละเมิดสิทธิส่วนบุคคลและการใช้ข้อมูลในทางที่ไม่เหมาะสม
นอกจากนี้ บริษัทใหญ่ๆ สามารถกลายเป็นผู้ผูกขาดการเข้าถึงและการกระจายข้อมูล จำกัดการแข่งขันและการเกิดขึ้นของนวัตกรรม และยังไปมีอิทธิพลต่อกระบวนการทางการเมืองและสังคม พวกเขาสามารถกำหนดมาตรฐานว่าอะไรจะเป็นสิ่งที่ยอมรับได้ในสังคม
ที่ยิ่งแย่ไปกว่านั้นคือการส่งเสริมการแพร่กระจายของเนื้อหาที่เป็นพิษ (Toxic Content Promotion) ที่มักเป็นเหตุผลเบื้องหลังการสร้างการมีส่วนร่วมและการตอบสนองจากผู้ใช้มากขึ้น นับเป็นการกระทำที่ขาดความรับผิดชอบต่อผู้คนและสังคมอย่างร้ายแรง

ในยุคที่ก้อนหินและผนังถ้ำเคยทำหน้าที่เป็นหน้ากระดาษของข้อความลึกลับและความคิดถึง วันเวลาได้พาเราเดินทางมายังการสื่อสารที่แทบไม่ต้องใช้มือสัมผัสหรือขีดเขียน จักรวาลดิจิตอลที่สามารถพิมพ์ความคิดออกมาได้เร็วกว่าที่ใจจะรู้สึก
แต่ในความก้าวหน้านั้น เงามืดของเทคโนโลยีก็คอยปกคลุมไม่ให้เรามองเห็นแสงสว่าง มือของผู้ทรงอำนาจได้แผ่กว้างถึงขนาดที่แทบจะประกาศว่า "I embody communication" (ฉันนี่แหละคือพ่อแห่งการสื่อสาร) พร้อมกับควบคุมข้อมูลที่เราเข้าถึงได้และเสียงที่เราจะได้ยิน นำมาซึ่งเสียงสะท้อนเพี้ยนๆ ที่ดังก้องไปตามกำแพงของอาณาจักรข้อมูลที่พวกเขาได้ตั้งไว้
เรากำลังยืนอยู่ ณ ทางแยกที่ต้องตัดสินใจว่าจะยอมให้กระแสแห่งการควบคุมนี้พัดพาเราไปตามทางได้อย่างง่ายดายหรือจะยืนหยัดเพื่อคุณค่าแห่งการสื่อสารที่เป็นรากฐานของมนุษยชาติ
การที่ข้อมูลสามารถเปลี่ยนสภาพเป็นของขวัญหรืออาวุธได้นั้น เราจำเป็นจะต้องใช้สติปัญญาและความรับผิดชอบในการพิจารณา การสื่อสารแบบเปิดที่ครั้งหนึ่งเคยเป็นเพียงการเขียนลงบนต้นไม้หรือฝากข้อความลับไว้ใต้หลังคา ตอนนี้มันได้ถูกแปลงโฉมให้กลายเป็นการสลักข้อความลงบนหน้าประวัติศาสตร์ดิจิทัลที่สามารถถูกลบหายได้ด้วยแค่คลิกเดียว
ในการเดินทางข้ามเวลานี้.. ขอให้เรายึดมั่นในการค้นหาความสมดุลระหว่างการเปิดรับและการป้องกัน, ระหว่างเสรีภาพและความรับผิดชอบ ให้เราจำเอาไว้ว่าเราทุกคนคือผู้กำหนดอนาคตของข้อมูลที่เราเลือกที่จะส่งผ่านและปลูกฝัง เพราะท้ายที่สุดสิ่งที่เราเลือกที่จะแบ่งปันในโลกออนไลน์นี้จะกลายเป็นเส้นใยที่ถักทอเรื่องราวและอนาคตของมนุษยชาติต่อไป
-
 @ 4d992bd1:45157b5a
2024-05-05 01:35:09
@ 4d992bd1:45157b5a
2024-05-05 01:35:09Hey all,
For the bitcoin++ I had the pleasure of hacking on blogstr / magstr.
The Problem
Currently, the publication industry requests individuals to write articles by paying them. This is quite costly and risky for the publications if it doesn’t resonate with their users and lead to higher retention and engagement.
For individuals, the amount is pretty minimal, though, if the publication is the visibility and brand awareness could be worth it.
Additionally, if the writer says something the publication doesn’t like, they can lose their content, the visibility, backlinking, and more.
… but what if there was a publication platform that could solve these problems?
The Solution
Nostr allows users to publish content to a set of relays and grow their following without requiring a particular platform. They could gain the advantage of the visibility to the users of the platform, censorship resistance, and to take their following with them, along with having a higher upside from being able to receive lightning payments.
The What
- A codebase built on Next.js that is easily deployable to Vercel that uses the nostr network to fetch long-form content events (kind: 30023) and render them in a UI. It’s easily customizable by using an environmental variable to set an array of pubkeys.
- You can create a blog out of this if the array only contains one pubkey, your pubkey.
- If you set multiple, you can evolve the UI to become something quite like Bitcoin Magazine.
- The codebase is entirely dynamic and it fetches the article writer’s lightning addresses from their nostr profile metadata.
Why Now
- Community members of Nostr PHX are asking for this.
- Get more of the internet off of massive social platforms and more to their own platforms.
- Community members and organizers that are marketers want to be able to contribute more to the nostr network.
- Disrupt publication incentives and costs.
- Get more communities to use nostr without needing to know Nostr.
- Value 4 value, enabling the users to not have a ceiling on their earnings.
- Empower publishers to easily aggregate nostr content to one place and curate the experience.
Codebase
You can view the instructions to setup and deploy the codebase in the GitHub repository.
You can try it here.
Thanks ~Santos.
-
 @ d0b327c6:1ae748c2
2024-05-04 08:36:44
@ d0b327c6:1ae748c2
2024-05-04 08:36:44Tradotto dall’originale di Murray N. Rothbard - pubblicato il 16 gen 2024
Pubblicato originariamente come prima parte di una serie di tre articoli su The Freeman, settembre-novembre 1995.
Il denaro è un posto di comando cruciale di qualsiasi economia, e quindi di qualsiasi società. La società poggia su una rete di scambi volontari, nota anche come "economia di libero mercato"; questi scambi implicano una divisione del lavoro nella società, in cui i produttori di uova, chiodi, cavalli, legname e servizi immateriali come l'insegnamento, le cure mediche e i concerti, scambiano i loro beni con i beni degli altri. In ogni fase del processo, ogni partecipante allo scambio trae un vantaggio incommensurabile, perché se tutti fossero costretti a essere autosufficienti, quei pochi che riescono a sopravvivere sarebbero ridotti a un livello di vita pietoso.
Lo scambio diretto di beni e servizi, noto anche come "baratto", è irrimediabilmente improduttivo al di là del livello più primitivo, e in effetti ogni tribù "primitiva" ha presto scoperto gli enormi benefici derivanti dall'individuazione, sul mercato, di un bene particolarmente commerciabile e richiesto da tutti, da utilizzare come "mezzo" di "scambio indiretto". Se un particolare bene è ampiamente utilizzato come mezzo di scambio in una società, allora quel mezzo di scambio generale si chiama "denaro".
Il denaro-merce diventa un termine in ognuno degli innumerevoli scambi dell'economia di mercato. Vendo i miei servizi di insegnante in cambio di denaro; uso quel denaro per comprare generi alimentari, macchine da scrivere o alloggi per i viaggi; e questi produttori a loro volta usano il denaro per pagare i loro lavoratori, per comprare attrezzature e inventari e per pagare l'affitto dei loro edifici. Da qui la tentazione sempre presente di uno o più gruppi di assumere il controllo della funzione vitale di approvvigionamento di denaro.
Molti beni utili sono stati scelti come denaro nelle società umane. Il sale in Africa, lo zucchero nei Caraibi, il pesce nel New England coloniale, il tabacco nella regione coloniale della Baia di Chesapeake, le conchiglie di cowrie, le zappe di ferro e molti altri beni sono stati usati come denaro. Queste monete non solo servono come mezzi di scambio, ma permettono agli individui e alle imprese di fare i "calcoli" necessari a qualsiasi economia avanzata. Le monete vengono scambiate e calcolate in termini di unità monetaria, quasi sempre unità di peso. Il tabacco, ad esempio, veniva calcolato in libbre di peso. I prezzi di altri beni e servizi potevano essere calcolati in termini di libbre di tabacco; un certo cavallo poteva valere 80 libbre sul mercato. Un'impresa commerciale poteva quindi calcolare il suo profitto o la sua perdita per il mese precedente; poteva calcolare che le sue entrate per il mese passato erano state di 1.000 sterline e le sue spese di 800 sterline, ottenendo un profitto di 200 sterline.
Oro o Carta di Stato
Nel corso della storia, due beni sono stati in grado di competere con tutti gli altri beni e di essere scelti sul mercato come denaro: due metalli preziosi, l'oro e l'argento (con il rame che entrava in gioco quando uno degli altri metalli preziosi non era disponibile). L'oro e l'argento abbondavano di quelle che possiamo definire qualità "monetizzabili", qualità che li rendevano superiori a tutti gli altri beni. Sono sufficientemente rari da rendere il loro valore stabile ed elevato per unità di peso; quindi i pezzi d'oro o d'argento saranno facilmente trasportabili e utilizzabili nelle transazioni quotidiane; sono anche sufficientemente rari da rendere poco probabili scoperte improvvise o aumenti dell'offerta. Sono durevoli, in modo da poter durare virtualmente per sempre, e quindi rappresentano una saggia "riserva di valore" per il futuro. Inoltre, l'oro e l'argento sono divisibili, quindi possono essere divisi in piccoli pezzi senza perdere il loro valore; a differenza dei diamanti, per esempio, sono omogenei, quindi un'oncia d'oro avrà lo stesso valore di qualsiasi altra.
L'uso universale e antico dell'oro e dell'argento come moneta è stato sottolineato dal primo grande teorico monetario, l'eminente studioso francese del XIV secolo Jean Buridan, e poi in tutte le discussioni sulla moneta fino ai libri di testo sulla moneta e sulle banche, fino a quando i governi occidentali hanno abolito il gold standard all'inizio degli anni Trenta. Franklin D. Roosevelt si unì a questa azione togliendo gli Stati Uniti dall'oro nel 1933.
Non c'è aspetto dell'economia di libero mercato che abbia subito più disprezzo da parte degli economisti "moderni", siano essi Keynesiani francamente statalisti o presunti "liberi mercatisti" di Chicago, di quanto non abbia fatto l'oro. L'oro, non molto tempo fa salutato come la base e il fondamento di qualsiasi sistema monetario solido, viene ora regolarmente denunciato come un "feticcio" o, come nel caso di Keynes, come una "barbara reliquia". In un certo senso, l'oro è una "reliquia" della barbarie; nessun "barbaro" degno di questo nome avrebbe mai accettato la carta fasulla e il credito bancario che noi moderni sofisticati siamo stati indotti a usare come denaro.
Ma i "gold bugs" non sono feticisti; non corrispondiamo all'immagine standard degli avari che passano le dita tra le loro monete d'oro ridacchiando in modo sinistro. Il bello dell'oro è che esso, e solo esso, è denaro fornito dal libero mercato, dalle persone che lavorano. Perché la scelta cruda che abbiamo davanti è sempre quella: oro (o argento) o governo. L'oro è denaro di mercato, un bene che deve essere fornito scavando dal terreno e poi lavorato; il governo, al contrario, fornisce cartamoneta o assegni bancari praticamente senza costi dal nulla.
Sappiamo, innanzitutto, che tutte le operazioni governative sono dispendiose, inefficienti e al servizio del burocrate piuttosto che del consumatore. Preferiremmo che le scarpe fossero prodotte da aziende private competitive sul libero mercato o da un gigantesco monopolio del governo federale? La funzione di fornire denaro non potrebbe essere gestita meglio dal governo. Ma la situazione del denaro è molto peggiore di quella delle scarpe o di qualsiasi altro bene. Se il governo produce scarpe, almeno queste potrebbero essere indossate, anche se potrebbero avere un prezzo elevato, calzare male e non soddisfare i desideri dei consumatori.
Il denaro è diverso da tutte le altre merci: a parità di altre condizioni, un maggior numero di scarpe o di scoperte di petrolio o di rame va a vantaggio della società, poiché contribuisce ad alleviare la scarsità naturale. Ma una volta che una merce si è affermata come denaro sul mercato, non c'è più bisogno di denaro. Poiché l'unico uso del denaro è lo scambio e il conteggio, un maggior numero di dollari o sterline o marchi in circolazione non può conferire un beneficio sociale: diluirà semplicemente il valore di scambio di ogni dollaro o sterlina o marco esistente. È quindi un grande vantaggio che l'oro o l'argento siano scarsi e che sia costoso aumentarne l'offerta.
Ma se il governo riesce a far passare i biglietti di carta o i crediti bancari come denaro, come equivalenti ai grammi o alle once d'oro, allora il governo, come fornitore dominante di denaro, diventa libero di creare denaro senza costi e a volontà. Di conseguenza, questa "inflazione" della massa monetaria distrugge il valore del dollaro o della sterlina (o dell’euro, n.d.t.), fa salire i prezzi, paralizza il calcolo economico e ostacola e danneggia gravemente il funzionamento dell'economia di mercato.
La tendenza naturale del governo, una volta che si occupa di denaro, è quella di inflazionare e distruggere il valore della moneta. Per comprendere questa verità, dobbiamo esaminare la natura del governo e della creazione di denaro. Nel corso della storia, i governi sono stati cronicamente a corto di entrate. Il motivo dovrebbe essere chiaro: a differenza di voi e di me, i governi non producono beni e servizi utili che possono vendere sul mercato; i governi, invece di produrre e vendere servizi, vivono parassitariamente sul mercato e sulla società. A differenza di ogni altra persona e istituzione della società, il governo ottiene le sue entrate dalla coercizione, dalla tassazione. In tempi più antichi e sani, infatti, il re era in grado di ottenere entrate sufficienti dai prodotti delle sue terre e foreste private, oltre che dai pedaggi autostradali. Per ottenere una tassazione regolarizzata e in tempo di pace, lo Stato ha dovuto lottare per secoli. Anche una volta stabilita la tassazione, i re si resero conto che non potevano imporre facilmente nuove tasse o aliquote più alte sui vecchi tributi; se lo facevano, era molto probabile che scoppiasse una rivoluzione.
Controllare l'offerta di denaro
Se la tassazione è permanentemente insufficiente rispetto allo stile di spesa desiderato dallo Stato, come può recuperare la differenza? Ottenendo il controllo dell'offerta di moneta o, per dirla in modo più semplice, contraffacendola. Nell'economia di mercato, possiamo ottenere denaro solo vendendo un bene o un servizio in cambio di oro, o ricevendo un regalo; l'unico altro modo per ottenere denaro è impegnarsi nel costoso processo di estrazione dell'oro dal terreno. Il falsario, invece, è un ladro che cerca di trarre profitto dalla falsificazione, ad esempio dipingendo un pezzo di ottone per farlo sembrare una moneta d'oro. Se la sua contraffazione viene individuata immediatamente, non provoca alcun danno reale, ma nella misura in cui la sua contraffazione non viene individuata, il contraffattore è in grado di rubare non solo ai produttori di cui acquista i beni. Infatti, introducendo denaro falso nell'economia, il falsario è in grado di rubare a tutti, privando ogni persona del valore della sua moneta. Diluendo il valore di ogni oncia o dollaro di moneta autentica, il furto del falsario è più sinistro e più sovversivo di quello del brigante; perché egli deruba tutti nella società, e la rapina è furtiva e nascosta, in modo da camuffare la relazione causa-effetto.
Ma in questo caso, cosa diremo quando il governo prenderà il controllo della massa monetaria, abolirà l'oro come moneta e stabilirà i propri biglietti stampati come unica moneta? In altre parole, cosa diremo quando il governo diventerà il contraffattore legalizzato e monopolista?
Non solo la contraffazione è stata individuata, ma il Grande Contraffattore, negli Stati Uniti il Federal Reserve System (in Europa la BCE, n.d.t.), invece di essere vituperato come un enorme ladro e distruttore, viene acclamato e celebrato come il saggio manipolatore e governatore della nostra "macroeconomia", l'agenzia su cui facciamo affidamento per tenerci fuori da recessioni e inflazioni, e su cui contiamo per determinare i tassi di interesse, i prezzi del capitale e l'occupazione. Invece di essere abitualmente bersagliato di pomodori e uova marce, il presidente del Federal Reserve Board, chiunque esso sia, sia esso l'imponente Paul Volcker o il gufo Alan Greenspan (Christine Lagarde è l’attuale presidente della BCE, n.d.t.), è universalmente acclamato come il signor Indispensabile per il sistema economico e finanziario.
In effetti, il modo migliore per penetrare i misteri del moderno sistema monetario e bancario è rendersi conto che il governo e la sua banca centrale agiscono esattamente come un Grande Contraffattore, con effetti sociali ed economici molto simili. Molti anni fa, la rivista New Yorker, ai tempi in cui le sue vignette erano ancora divertenti, pubblicò una vignetta che ritraeva un gruppo di falsari che guardavano impazienti la loro macchina da stampa mentre la prima banconota da 10 dollari usciva dalla macchina. "Cavolo", disse uno del gruppo, "la spesa al dettaglio nel quartiere sta per ricevere un'iniezione di energia".
E così è stato. Quando i falsari stampano nuova moneta, la spesa aumenta per qualsiasi cosa i falsari desiderino acquistare: beni personali al dettaglio per se stessi, nonché prestiti e altri scopi di "benessere generale" nel caso del governo. Ma la "prosperità" che ne deriva è fasulla: tutto ciò che accade è che più denaro fa incetta di risorse esistenti, così che i prezzi aumentano. Inoltre, i contraffattori e i primi beneficiari del nuovo denaro sottraggono risorse ai poveri fessi che si trovano alla fine della fila per ricevere il nuovo denaro, o che non lo ricevono affatto (effetto Cantillon, n.d.t.). L'immissione di nuovo denaro nell'economia ha un inevitabile effetto a catena: i primi destinatari del nuovo denaro spendono di più e fanno salire i prezzi, mentre i destinatari successivi o coloro che hanno un reddito fisso si trovano ad aumentare inspiegabilmente i prezzi dei beni che devono acquistare, mentre i loro redditi rimangono indietro o invariati. L'inflazione monetaria, in altre parole, non solo aumenta i prezzi e distrugge il valore dell'unità monetaria, ma agisce anche come un gigantesco sistema di espropriazione dei destinatari tardivi da parte degli stessi falsari e degli altri destinatari precoci. L'espansione monetaria è un enorme schema di ridistribuzione nascosta.
Quando il governo è il contraffattore, il processo di contraffazione non solo può essere "scoperto", ma si proclama apertamente come una gestione monetaria per il bene pubblico. L'espansione monetaria diventa allora un gigantesco schema di tassazione occulta, che ricade sui gruppi a reddito fisso, su quelli lontani dalla spesa e dai sussidi governativi e sui risparmiatori parsimoniosi che sono abbastanza ingenui e fiduciosi da conservare il proprio denaro, per avere fiducia nel valore della moneta.
La spesa e l'indebitamento sono incoraggiati; la parsimonia e il duro lavoro sono scoraggiati e penalizzati. Non solo: i gruppi che ne traggono vantaggio sono i gruppi di interesse speciale che sono politicamente vicini al governo e possono esercitare pressioni affinché il nuovo denaro venga speso per loro, in modo che i loro redditi possano aumentare più velocemente dell'inflazione dei prezzi. Gli appaltatori governativi, le imprese politicamente collegate, i sindacati e altri gruppi di pressione ne beneficeranno a spese del pubblico ignaro e non organizzato. Murray N. Rothbard
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 362ebffa:492e2719
2024-05-05 14:21:34
@ 362ebffa:492e2719
2024-05-05 14:21:34Here is a bug report impacting Habla.news
How to lose all bookmarks in 3 easy steps:
-
step 1 https://m.primal.net/IDWB.png
-
step 2 Save an article in habla as bookmark https://m.primal.net/IDWF.png
-
step 3 Return to Primal https://m.primal.net/IDWH.png
all bookmarks are gone!
Where are the lost bookmarks? Can they be recovered?
it seems to be a genuine bug when saving bookmarks in Habla.news
Can anybody confirms?
Who may I contact to report that bug?
https://github.com/verbiricha/habla.news
article originally posted on https://it-s-just-a-ride.blogspot.com/2024/05/hablanews-reset-nostr-bookmarks.html
-
-
 @ 3bf0c63f:aefa459d
2024-03-06 13:04:06
@ 3bf0c63f:aefa459d
2024-03-06 13:04:06início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ d0b327c6:1ae748c2
2024-05-04 08:30:48
@ d0b327c6:1ae748c2
2024-05-04 08:30:48Tradotto dall’originale di Stephen Hall - pubblicato il 18 gen 2023
Con l'aumento del valore di bitcoin, cresce anche la necessità di conservare le chiavi in modo sicuro. Una di queste soluzioni è un portafoglio hardware, un dispositivo fisico che consente di conservare in modo sicuro le tue chiavi private. Ma i portafogli hardware non sono l'unica opzione per conservare le chiavi dei bitcoin: esistono anche portafogli software, portafogli cartacei e persino "portafogli cerebrali". Perché scegliere un portafoglio hardware?
1. Mantenere le vostre chiavi offline, protette da attacchi remoti

I portafogli hardware consentono di generare e conservare le chiavi dei bitcoin in modalità completamente offline, nota come cold storage. Ciò è in antitesi ai portafogli hot, che sono più suscettibili agli attacchi remoti come malware e attacchi SIM swap (comunque più sicuri di un custode terzo o di un exchange!).
Si può pensare che questo sia simile alla costruzione di una nave in una bottiglia. Il seme del portafoglio, utilizzato per generare le chiavi dei bitcoin, viene generato all'interno del dispositivo e non può essere esportato digitalmente. Le chiavi non lasciano mai il dispositivo. Anche se un portafoglio hardware è collegato a un computer infetto da virus (cosa sconsigliata), le chiavi sono comunque protette, spesso in un elemento sicuro.
Quando si vogliono spostare i propri bitcoin, si crea una transazione con il vs. software wallet preferito (Sparrow, Specter, Electrum, etc., n.d.t.), la si invia al portafoglio hardware, la si firma sul portafoglio hardware stesso usando le proprie chiavi private e la si rimanda al software wallet connesso a Internet per trasmetterla alla rete bitcoin.
2. Proteggersi dagli attacchi fisici

Se qualcuno dovesse accedere fisicamente al vostro portafoglio hardware, essi offrono caratteristiche uniche che vi aiutano a difendervi dagli attacchi. Alcune di queste caratteristiche di sicurezza includono un elemento sicuro (secure element, n.d.t.), la verifica del firmware e i PIN per una difesa di primo livello.
Secure Element
Un secure element sicuro è un microprocessore utilizzato per isolare, memorizzare e proteggere i dati sensibili. In un portafoglio hardware, un elemento sicuro offre un livello di protezione più elevato contro la compromissione fisica rispetto all'ambiente standard di un telefono cellulare, un desktop o un laptop. Ad esempio, questo rende più difficile la compromissione del dispositivo tramite attacchi di tipo fault, attacchi side-channel e attacchi cold boot.
Verifica del Firmware
La verifica del firmware è un modo per verificare la validità del software integrato in un portafoglio hardware. Ciò protegge dalle versioni contraffatte e dagli attacchi alla catena di distribuzione. La verifica del firmware garantisce l'utilizzo di una versione autentica e inalterata dell'hardware. Alcuni software dei portafogli di produttori verificano il firmware del dispositivo ogni volta che lo si collega al PC.
PIN di Accesso
I PIN di accesso presenti in molti portafogli hardware impediscono a chiunque, tranne che al proprietario, di accedere immediatamente alla possibilità di firmare con le chiavi memorizzate sul dispositivo. Nella maggior parte dei casi, la penalità per chi non riesce a inserire correttamente il PIN per un certo numero di tentativi è un ritardo crescente tra i tentativi di accesso. In alcuni portafogli hardware, il superamento del numero di tentativi di indovinare il PIN può comportare un reset di fabbrica del dispositivo o addirittura renderlo definitivamente inutilizzabile.
PIN a prova di coercizione
E’ una funzione di sicurezza che può aiutare a proteggere i bitcoin in caso di attacco con cosiddetto $5 wrench attach. I PIN a prova di costrizione sono particolarmente importanti per i portafogli hardware (perché vengono utilizzati per proteggere grandi quantità di bitcoin) e la funzionalità disponibile è particolarmente robusta in alcuni casi.
Ad esempio, il portafoglio hardware Coldcard offre tre tipi di PIN a prova di costrizione: uno che sblocca un portafoglio esca, uno che distrugge il seme e uno che crea un conto alla rovescia verso la "modalità mattone" personalizzabili. Se vi trovate in uno scenario di costrizione, questi strumenti vi offrono la certezza che gli aggressori non saranno in grado di accedere alle vostre chiavi bitcoin principali, se mai ce ne fossero.
3. Fornire una superficie di attacco ridotta

È possibile memorizzare le chiavi offline con un computer portatile o un desktop e metterle al sicuro da attacchi fisici. Tuttavia, le architetture generiche di questi dispositivi presentano una superficie di attacco più ampia per gli aggressori esperti. Ciò significa che gli aggressori hanno più possibilità di sfruttare il software, il firmware e l'hardware per trovare il modo di rubare le chiavi private.
Al contrario, i portafogli hardware sono costruiti con hardware specializzato che ne semplifica la funzionalità a compiti molto specifici e ne limita la connettività a Internet e ad altri dispositivi. Anche se dotati di un elemento sicuro per mantenere i dati delle chiavi dietro un firewall, alcuni portafogli hardware limitano il modo in cui si connettono fisicamente con i dispositivi esterni - i portafogli hardware air-gapped si interfacciano principalmente con altri dispositivi tramite scheda microSD. Molti produttori offrono anche firmware per soli bitcoin per semplificare ulteriormente la funzionalità.
I portafogli hardware possono essere più limitati in termini di funzionalità e convenienza rispetto ai dispositivi generici, ma questa funzionalità limitata significa anche una vulnerabilità limitata. Questo ha anche il vantaggio di ridurre il rischio che vengano scoperte nuove falle che i produttori devono colmare con aggiornamenti del firmware o revisioni dell'hardware.
4. Prepararsi a valori crescenti

Potreste pensare di non possedere abbastanza bitcoin per cui valga la pena di acquistare un portafoglio hardware e imparare a conservare in modo sicuro le vostre chiavi offline. Un motivo per acquistare un portafoglio hardware ora è quello di prepararsi alle oscillazioni di prezzo del bitcoin.
La saggezza comune in materia è quella di trattare i propri averi come se valessero 10 volte di più di quanto valgono oggi: storicamente, una mossa del genere può arrivare rapidamente e inaspettatamente. Inoltre, se l’ammontare di bitcoin in vostro possesso vi sembra troppo grande per uno standard Singlesig in caso di aumento del valore di 10 volte, potrebbe essere il momento di prendere in considerazione un modello di auto-custodia più sicuro come il Multisig.
5. Confermare gli indirizzi sul dispositivo

Poiché le transazioni in bitcoin sono irreversibili, è importante essere certi che l'invio di bitcoin avvenga all'indirizzo corretto. Questo è importante sia per l'invio di bitcoin a qualcun altro sia per l'invio di bitcoin a un portafoglio controllato dalle chiavi del portafoglio hardware che si possiede (es: se state consolidando molte piccole UTXO in una unica UTXO più grande, n.d.t.).
Con i portafogli software, il malware potrebbe sostituire l'indirizzo reale con quello di un aggressore nell'interfaccia utente, rendendo difficile la verifica dell'autenticità. Esiste anche il malware "clipper", che cambia l'indirizzo ricevente negli appunti del computer, e altri vettori di attacco.
I portafogli hardware aiutano a risolvere questo problema perché includono uno schermo fisico che visualizza l'indirizzo a cui si desidera inviare i fondi, consentendo di verificarlo prima di spendere. Se il dispositivo non è stato fisicamente compromesso, si può essere certi che l'indirizzo visualizzato sia controllato dalle chiavi memorizzate offline sul dispositivo. Se si inviano fondi a un destinatario remoto, è meglio confermare l'indirizzo a cui si sta inviando attraverso più canali.
6. Un ambiente ideale per generare la propria entropia

Tutti i portafogli bitcoin dipendono dall'entropia - la casualità - per generare i semi, e i semi sono il segreto principale che genera le chiavi private bitcoin. L'entropia può essere generata in molti modi, dai generatori di numeri casuali di base sui dispositivi, alle lunghe stringhe di testo casuali, ai lanci di dadi o alle carte da gioco.
I lanci di dadi sono considerati uno dei modi migliori per generare la propria entropia, riducendo al minimo il coinvolgimento di terzi nella generazione della casualità necessaria per inizializzare un portafoglio bitcoin. Alcuni portafogli hardware, come Coldcard, consentono di inserire i lanci di dadi sul dispositivo per generare una frase seme. È possibile premere da 1 a 6 per ogni lancio e il dispositivo utilizzerà i lanci per generare il seme.
Sebbene non sia necessario un portafoglio hardware per generare la propria entropia (si può fare su un computer portatile permanentemente offline, ad esempio), i portafogli hardware consentono di farlo in modo comodo e sicuro. Generare la propria entropia nel mondo fisico può essere divertente e un ottimo esercizio di apprendimento, ma è inutile senza l'ambiente giusto che vi aiuti a preservare la sicurezza marginale che potreste ottenere facendolo.
7. Viaggiare in modo più sicuro

Per viaggiare con piccole quantità di bitcoin si può facilmente utilizzare un telefono cellulare o un altro dispositivo meno sicuro, ma per quantità maggiori di bitcoin è necessaria una maggiore attenzione. Viaggiare con le chiavi su un computer portatile o un dispositivo mobile è rischioso perché questi dispositivi sono solitamente caldi (connessi a Internet), hanno protezioni fisiche più limitate e hanno superfici di attacco più ampie.
I portafogli hardware offrono convenienza e sicurezza se avete bisogno di tenere una o più chiavi bitcoin con voi mentre viaggiate.
Non dovete preoccuparvi di connessioni WiFi o porte USB poco sicure, potete usare le funzioni di costrizione descritte sopra se qualcuno dovesse attaccarvi fisicamente e siete più protetti se il vostro dispositivo viene perso, rubato o confiscato (gli aggressori dovrebbero sconfiggere la sicurezza del portafoglio hardware). Inoltre, offrono ancora un comodo accesso in caso di necessità di spesa.
8. Migliorare la sicurezza delle configurazioni Multisig

I portafogli Multisig sono costruiti combinando più chiavi (rispetto ai portafogli Singlesig che ne utilizzano solo una). La richiesta di più di una chiave per spendere bitcoin aggiunge sicurezza e ridondanza al portafoglio, rendendolo utile per proteggere grandi quantità di bitcoin.
Più sicure sono le singole chiavi coinvolte nella costruzione di un portafoglio Multisig, più sicuro è il portafoglio Multisig stesso. I portafogli hardware consentono di costruire comodamente un portafoglio Multisig con chiavi chiaramente delineate e conservate in modo sicuro offline. Come nel caso di Singlesig, i portafogli hardware consentono anche di verificare offline gli indirizzi Multisig quando si inviano bitcoin.
L'uso di più portafogli hardware è naturale per il Multisig, perché il Multisig è spesso usato per massimizzare la sicurezza e la ridondanza di grandi quantità di bitcoin conservati a freddo, un obiettivo che anche i dispositivi fisici e i backup delle frasi di seme aiutano a raggiungere.
Inizia con l'autocustodia
Il primo passo per migliorare la sicurezza dei bitcoin è sempre quello di adottare l'autocustodia, a caldo o a freddo, per eliminare il rischio legato alla fiducia nei depositi come gli exchange. Da lì, si possono esplorare ulteriori strumenti di sicurezza, come il Multisig, per trovare il giusto equilibrio tra sicurezza e accessibilità per le proprie circostanze.
-
 @ a012dc82:6458a70d
2024-05-05 13:55:09
@ a012dc82:6458a70d
2024-05-05 13:55:09En Latinoamérica, la inflación es un tema de nunca acabar, salarios que no llenan las expectativas de la gente trabajadora que los llevan a buscar otras alternativas para palear la economía, cada vez es más común encontrarse con personas hambrientas de conocimiento en los temas de generar ingresos de forma digital y es por eso que en República Dominicana un hombre con visión de futuro se dio a la tarea de formar Bitcoin Dominicana.
La misión de esta institución es enseñar y empoderar a las comunidades con ganas de aprender, que gratamente son cada vez más jóvenes, es decir, la información que se maneja es viable y amigable para todo tipo de público ya que se adaptan a las necesidades de cada quien. En este podcast conoceremos un poco más acerca de qué es, y cómo funciona Bitcoin Dominicana de la mano de nuestro entrevistado Pedro Vital.
Tabla de Contenidos
-
Introducción
-
¿Qué te motivó a incursionar en Bitcoin?
-
¿Cómo funciona Bitcoin Dominicana?
-
¿Cómo es la receptividad del público juvenil?
-
¿Cómo abordan el aprendizaje de bitcoin en los niños y jóvenes?
-
¿El sector turismo se está beneficiando con bitcoin?
-
Conclusión
-
Preguntas Frecuentes
Introducción
Latinoamérica principalmente ha sido víctima de sus malos gobiernos que nos han llevado por caminos inciertos haciendo de nuestra economía un juego de azar, esta inestabilidad económica ha llevado a las personas a incursionar en la minería de bitcoin muchas veces tentando la suerte por falta de conocimiento, es por eso que personas como Pedro Vital se han dado cabida ´para compartir sus experiencias y así ayudar a la comunidad a forjarse como personas capacitadas y puedan minar con muy bajo riesgo. ¿Qué te motivó a incursionar en Bitcoin? Realmente fue por un tema de curiosidad, pero una vez me di cuenta lo que sucedía en el salvador comprendí que efectivamente estaban sucediendo cosas muy descentralizadas, es por eso que llamo tanto mi atención y decidí continuar, lo que dio origen a bitcoin dominicana.
¿Cómo funciona Bitcoin Dominicana?
Bitcoin Dominicana, básicamente es una entidad dedicada al estudio de bitcoin, comprender su funcionamiento y manejo, pero también vamos más allá, dando apoyo a madres y padres que desean emprender, en este momento trabajamos con adolescentes ya que es importante que las comunidades comiencen jóvenes ya que lo importante es que este mundo del bitcoin no es para millonarios, si no para millones.
¿Cómo es la receptividad del público juvenil?
Son un público muy receptivo, ya que los más jóvenes lo ven como un juego. Sus edades van desde los 7 hasta los 16, 18 años de edad y como no tienen un hobby fijo adoptan bitcoin como una manera de vida, al igual que en todos los paises de latinoamerica, Dominicana no escapa a la inflación que cada día debilita más la moneda nacional, es por eso que ahora mismo los jóvenes a diferencia de los jóvenes de hace años atrás, buscan la manera de generar dinero por internet, y el hecho de poder comprar un poco de bitcoin con los pesos que puedan tener, resulta muy satisfactorio para ellos.
¿Cómo abordan el aprendizaje de bitcoin en los niños y jóvenes?
Es bastante sencillo enseñarles, es como si sus mentes ya vinieran prediseñadas para entender las cosas tecnológicas, entonces la manera que tenemos para hacer más sencillo su enseñanza es a través de plataformas y juegos digitales, donde ellos realizan pequeñas recargas y lo ven a manera de recompensas y a la vez se empoderan recibiendo formación financiera.
¿El sector turismo se está beneficiando con bitcoin?
Ahora mismo la industria del turismo está creando una alianza con la industria de la minería, creando una simbiosis en la que todos estos sectores se verán beneficiados, siendo que Dominicana tiene todo lo que la gente busca, no solo playas, sino que también contamos con lo que es montañas, ríos, en fin, el bitcoin es el futuro del turismos no solo en dominicana, sino a nivel de Latinoamérica y el mundo.
Conclusiones
En Dominicana no solamente el turismo es el fuerte, ahora mismo la plataforma bitcoin está tomando auge, Bitcoin Dominicana está marcando la pauta entre la comunidad tanto joven como adulta en cuanto al aprendizaje del manejo de esta moneda fuerte que día con día promete ir en franco crecimiento dando una notable valía a los esfuerzos por aprender acerca de ella.
Lo más idóneo sería que los gobiernos tanto en la República Dominicana como de los demás países de latinoamérica y el mundo es amistarse con el bitcoin como moneda fuerte, ya que si bien no comulga con la impresión de dinero físico, es la manera más viable de hacer crecer la economía tanto de la población como de las naciones en general.
Preguntas Frecuentes
¿Qué significa halving? En concreto, el halving es un evento que ocurre aproximadamente cada cuatro años y reduce a la mitad la recompensa que reciben los mineros por validar transacciones en la red de Bitcoin, reduciendo así el suministro de la criptomoneda pionera. ¿Cuál es el mejor intercambio para comprar bitcoins en República Dominicana? Hay 5 intercambios confiables operando en la República Dominicana, siendo los más populares Kraken, eToro y Gemini . Puede revisar cada uno de estos intercambios y encontrar el mejor intercambio que funcione para usted.
¿Qué pasa con Bitcoin después del Halving? La recompensa de Bitcoin es de 6,25 BTC. Sin embargo, después de la cuarta reducción a la mitad, la recompensa bajará a 3,125 BTC. Como resultado, la cantidad de Bitcoins en circulación se hace aún más escasa, provocando un aumento de la demanda entre los inversores.
Esto es todo por hoy, nos vemos mañana
Si querés saber mas, seguinos en:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Tienda Online: https://croxroad.store
Subscribite a CROX ROAD, el newsletter diario solo sobre Bitcoin
https://www.croxroad.co/subscribe
DESCARGO DE RESPONSABILIDAD: Nada de esto es un consejo financiero. Este boletín es estrictamente educativo y no es un consejo de inversión ni una solicitud para comprar o vender activos ni para tomar decisiones financieras. Tenga cuidado y haga su propia investigación.
-
-
 @ d830ee7b:4e61cd62
2024-04-27 04:27:23
@ d830ee7b:4e61cd62
2024-04-27 04:27:23Has anyone seen anything like this?

Have you ever experienced simple communication that is almost completely technology-free?
Such as scribbling on eucalyptus trees or along galvanized walls. These activities reveal man's genuine desire to leave some mark on the planet. I used to be one of those people who was fascinated by using simple tools like a magic pen to write on bathroom doors at gas stations to leave stories. It was not long ago that these actions are a form of public communication, also known as "social media communication."
This desire to create its own communication platform is not new. It's an instinct that has been deeply rooted in humans since the time of cave wall painting, showing that we humans have a constant need to share ideas and information.
These activities are not just about leaving messages for others to see. But it also reflects personal actions that come from making decisions themselves. It is an expression of creativity and an independent exchange of information, which is in line with the concept of a market process that gives individuals the freedom to express themselves and adapt to their personal goals.
Scribbling on trees and cave walls in the past is no different from posting messages or status updates on social media in this day and age. Through the changing times and technology, it has become a part of the communication culture that never disappears from our hearts.
We humans have always wanted to convey our thoughts and feelings to the world. Whether it's scribbling on a tree or leaving a message under a galvanized roof. These desires have moved towards a more efficient and broader digital format. This allows us to communicate across borders to every corner of the world without limits. This innovation and adaptation is a clear signature of progress in human history, all due to the decisions and actions of individuals who want to leave their mark on the world.
Leaving a message in a public place is... It stems from a variety of reasons that are more complex and deeper than just face-to-face communication. Sometimes it can be related to the need to spread ideas or messages to a wider group of people, or it can be building relationships with the next generation. In a way, It may only be a personal memory (we'll put the morality and cleanliness aside first).

But the most important thing is the desire to connect with the community or to create unity. We humans are social creatures who want to share and coordinate with others in the community. We not only communicate to exchange information, but also create diverse and lasting social interactions through scribbling or public messaging.
In addition.. These actions also reflect our desire to be remembered or immortality. It confirms that our actions will remain etched in people's memories long after we leave and are an expression of identity and contribution to history. With the name and date engraved on the tree. We leave a mark of existence not only on ourselves to remember, but for all passers-by in those days and beyond.
As the world moves into the digital age and social media... It's like an explosion of longing that we've had in the past in new ways. Online platforms allow us to spread our own stories and experiences to a wider audience endlessly. With faster and easier access to and distribution of news. Instant data sharing and connecting with people around the world without borders This makes social media another dimension of communication that not only flourishes but also forms online communities that have a great influence on the lifestyle and culture of modern society.

Difference
But considering past and present public communication. There is a big difference. Scribbling on trees in the past is truly decentralized communication. Everyone can add their own text freely. Today's online platforms are tightly compiled and regulated, with rules and algorithms determining which messages are published or hidden from the eyes of many users.
The digital space has the power to control the content that is shared and published. It can remove or block content that does not comply with policies or laws, which of course eucalyptus trees and public places in the past could not. Privacy and freedom of expression are questioned in the social media world, where new social rules and etiquette have been put in place that limit compliance with use and expression policies.
Scribbles are not clearly identified. But in the online world. Personal information and identities can be tracked and recorded in detail. Privacy in the digital world is clearly less. Despite these platforms' attempts to provide tools to control privacy.
Public communication in the past has often been overt and has given rise to a culture of organic sharing. Yet, with the entry into the digital age and social media. Connections are fast and expanding globally, but they can also lead to echo chambers and the spread of distorted information.
Communication in today's world is clearly governed by rules and algorithms. This has led to the creation of more complex social networks, where freedom of expression must also be within the framework set by the platform. Users need to find a balance between protecting their privacy and exercising their digital freedom responsibly.

Changes
Let's follow how public social communication has changed from the past to the present.
In the Middle Ages, the use of paper and letter writing became popular. Even with direct communication to the desired person, there is still an opportunity to disclose and pass on information. In addition, the paper was used as a banner announcing the news. But sometimes the content is controlled by the host of the space. Newspapers and later magazines brought the distribution of news and opinions to a large readership. The publication of information is strictly controlled by editors and publishers.
Entering the era of radio and television. Mass communication has been revolutionized. Information and entertainment can be quickly delivered to viewers and listeners, but remain under the control of the state and content producers.

When our world was introduced to the Internet in the 90s, we encountered a revolution in the way we communicate through chat rooms and online forums. It's a place to exchange ideas and information without restrictions, supervised by operators and developers to keep these platforms running smoothly.
At last Since then, human freedom of communication and expression has become increasingly restricted through time, until it seems to have been lost in modern times. It requires us to consider and question the values and impact of these controls on society in the future.
As the world entered the Internet era in the 90s, we encountered a new phenomenon in communication. In that era, IRC (Internet Relay Chat) was the most free way to start online discussions. Those who have experienced it must be quite young.
The presence of online forums such as Usenet and the Bulletin Board System (BBS) has provided opportunities for people from all over to gather and exchange information on a wide range of topics. This later led to the emergence of blogs such as Bloggers that allow everyone to freely publish their ideas and stories. Blogs and Wikipedia offer unprecedented freedom to publish and edit content that can help the public. It opens up new opportunities where everyone can be both a giver and a receiver of information.
MSN Messenger was launched in 1999 and was one of the first and most popular real-time chat services in the early days of the Internet. With the ability to communicate instantly. File delivery and audio and video conversation features

In the later period. Forums have stepped in to make forum discussions easier and content is better managed. Then came the emergence of Frienster, MySpace, and Hi5 in the early 2000s, which were the first social media to completely change the way we communicate and share content.

In 2004, Facebook was born, and it started as a social network for university students before launching it to the public in 2006 . Short messages and quick sharing of information (followed by Instagram, Snapchat, LINE, WeChat and TikTok, etc., appearing later). These platforms have played a role in changing the way we build communities and social networks, and not only that, they have also made it easier to maintain social relationships. These communities have grown independently without state prescription (especially on unregulated platforms such as Nostr, which may not be covered in this article).
Entering the social media era, Facebook in particular has defined its primary role in shaping the creation of new social networks. This will not only make the exchange of information convenient. It also comes with strict controls on content and personal information that have a significant impact on privacy rights and freedom of expression.
Transcending from natural communication and placard paper to technological evolution It brings us into a new world where data and communication control is managed by technological oligarchs. Almost all communication today is restricted and is carried out through a central platform with clear rules and usage policies.

Concerns
In a market where consumers have more options. Companies need to improve their services and products to meet changing customer expectations. This is changing our way of life and culture in a way that has never been seen before (before the era when highly popular platforms were trying to poke and nose their customers in the modern era).
The development of digital communication not only reflects changes in the economy and society. But it also changes the way we see and perceive the world around us. It creates new expectations and expands opportunities for us to engage more with our community.
However.. The power of major platforms It is having a profound impact on modern society. It creates unexpected concerns for users and the world's population. These big platforms can control the flow of data that users can see. This causes data filtering or presents biased information. This has resulted in misrepresentation and information being presented.
We've also seen the creation of 'Echo chambers' and 'Filter Bubbles', adapting content to user preferences and behaviors, resulting in people only seeing information they're ready to agree with. It leads to non-diversity of ideas and division of ideas. There is an addiction to platforms caused by algorithms designed to allow users to spend the most time on the platform. This can lead to addictive behaviors that are detrimental to mental and physical health.
Privacy breach from the collection of personal information without clear boundaries. This results in violations of privacy rights and misuse of information.
In addition, major companies can become monopolies of access and distribution of information, limit competition and the emergence of innovation, and influence political and social processes. They can set standards for what will be socially acceptable.
Even worse, it promotes the spread of toxic content. Toxic content promotions are often the reason behind generating more engagement and responses from users. It is a gross act of irresponsibility towards people and society.

In an era when rocks and cave walls once served as pages of mystical and nostalgic messages. The days have brought us to communication that requires almost no hand touch or scribble. A digital universe that can print ideas faster than the mind feels.
But in that progress, the shadows of technology keep us from seeing the light. The Almighty's hand has spread so wide that it almost proclaims, "I am the father of communication," while controlling the information we have access to and the voices we hear. This brings a distorted echo that echoes along the walls of the information realm they have set.
We are standing at a crossroads where we must decide whether to allow this tide of control to easily carry us down the path or to stand up for the values of communication that are fundamental to humanity.
The information can be transformed into gifts or weapons. We need to exercise wisdom and responsibility in deliberations. Open communication that was once just written down in a tree or left a secret message under a canopy. Now it has been transformed into an engraving on a digital history page that can be erased with just one click.
In this time journey... Let us hold fast to finding a balance between exposure and protection, between freedom and responsibility. Let us remember that we are all shapers of the future of the information we choose to transmit and cultivate. Because ultimately, what we choose to share in this online world will become the next weaving of humanity's story and future.
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 1c6b3be3:73f0ae6f
2024-05-04 04:01:03
@ 1c6b3be3:73f0ae6f
2024-05-04 04:01:03Releases - No Bullshit Bitcoin
Geyser v0.8.0: On-chain to Lightning Donation Swaps via Boltz Geyser, a crowdfunding platform for bitcoin and Nostr projects, has released a new feature enabling creators to receive on-chain sats directly into their Lightning wallets in a non-custodial manner. This is made possible through a partnership with BoltzHQ, the leading non-custodial Bitcoin exchange, which facilitates the swapping of on-chain contributions to Lightning with no intermediaries, custodians, and low fees. Additionally, Geyser has updated the appearance of its Geyser bot, now known as the Geyser Spirit, which highlights notable real-time contributions on the platform for the Nostr community.
🍵 "btc | bitcoin | lightning network | asic" - Google News
Is bitcoin key to creating a verified digital world? - TheStreet Bitcoin Layer-2 Network Stacks Witnesses Surge in Active Users - Yahoo Finance Bitcoin Price to Top $100,000 “In Two Months” while - GlobeNewswire Solana Unveils Plan for Cross-Chain Bridge to Bitcoin by Q3 2024: Details - Crypto News Flash Bitcoin Flashes Potentially Bullish Indicator Amid Crypto Market Downtick, According to Analytics Firm Santiment - The Daily Hodl 5 "Best" Lightning Network Wallets (May 2024) - Securities.io Why Cosmos DeFi Hub Osmosis Is Launching a Bitcoin L2 - Unchained - Unchained Bitcoin Fees Normalize After Runes' Coming Out Party Abruptly Ends - The Defiant - DeFi News US job growth slows as Bitcoin price soars past $62,000 - Forkast News
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ d34e832d:383f78d0
2024-05-05 11:20:07
@ d34e832d:383f78d0
2024-05-05 11:20:07
Transaction Signing
The process of signing and verifying transactions in the Bitcoin network is fundamental to its security and integrity. Let's delve into how transactions are signed and verified, based on insights from [0].
Transaction Signing Process
-
Initialization: The signing process kicks off with SignTransaction in scriptsign.cpp, where each transaction input is signed individually. This function iterates through the inputs of the transaction it receives.
-
Loop Through Inputs: For each input, the script retrieves the corresponding coin's public key and amount from a cache of unspent transaction outputs (UTXOs).
-
Signature Data Preparation: Using DataFromTransaction, all necessary information required to produce a signature for that coin is gathered within a SignatureData struct. This includes checking whether the scriptSig and scriptWitness are complete, along with their contents and any redeem or witness scripts.
-
Producing the Signature: With the signing data prepared, ProduceSignature is called to generate the actual signature for each input, typically signed with a SIGHASH_ALL flag.
Verification Process
While the verification process differs from signing, it utilizes similar elements of Bitcoin's scripting system, aiming to facilitate future upgrades seamlessly. As mentioned in [3], Bitcoin's script system is crucial for ensuring compatibility with new features like taproot or schnorr signatures.
Mechanism of Verification
The verification process leverages Bitcoin's script format, using a script matching an address to verify the message. This entails replacing every signature verification operation with one that checks the provided message instead of a transaction. This flexible mechanism ensures Bitcoin's adaptability to evolving requirements and technological advancements.
Conclusion
In essence, the signing and verification processes in Bitcoin are meticulously designed to ensure transactions' authenticity and security. By following a structured approach to signing and utilizing the scripting system for verification, Bitcoin maintains a robust and adaptable network architecture.
Enhancing Bitcoin Transactions with SIGHASH Types
In Bitcoin, the signature hash (sighash) type plays a pivotal role in determining how transactions are signed and verified. Let's explore the various SIGHASH types and their significance, based on insights from [0].
Understanding SIGHASH Types
-
SIGHASH_ALL: This default type commits to all inputs and outputs of the transaction, preventing alterations to any part of the transaction without invalidating the signature. It ensures high security by fixing every aspect of the transaction within the signature.
-
SIGHASH_NONE: Unlike SIGHASH_ALL, this type allows changing where the bitcoins will go after the initial signature, providing flexibility in specifying transaction outputs while still securing the inputs.
-
SIGHASH_SINGLE: With SIGHASH_SINGLE, the signature commits to a single input and a corresponding output, allowing for more flexible transactions where the signer only cares about specific outputs.
-
SIGHASH_ANYONECANPAY: This modifier allows the signer to specify that the signature only commits to one input of the transaction, enabling others to add additional inputs later. It opens possibilities for scenarios like crowdfunding.
Tailoring Security and Flexibility
Each SIGHASH type offers a balance between security and flexibility, allowing users to customize the signing process to meet their specific needs or contractual arrangements. Understanding these nuances is essential for developers and users navigating complex transactions on the Bitcoin network.
In summary, SIGHASH types play a crucial role in enhancing the security and flexibility of Bitcoin transactions, empowering users to tailor transaction signing according to their requirements within the Bitcoin protocol.
Conclusion
From the meticulous signing process to the versatile SIGHASH types, Bitcoin's transaction framework is intricately designed to ensure authenticity, security, and adaptability. By embracing these mechanisms, Bitcoin continues to evolve as a robust and resilient decentralized network.
Sources: - [0]: Insights into Transaction Signing and Verification - [1]: Understanding Bitcoin's Script System - [2]: Bitcoin Scripting for Future Upgrades - [3]: Adaptability of Bitcoin's Script System - [4]: SIGHASH Types and Transaction Security - [5]: Flexibility of SIGHASH_ANYONECANPAY
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ fbe736db:187bb0d5
2024-04-26 18:46:45
@ fbe736db:187bb0d5
2024-04-26 18:46:45This is a slightly abridged version of an article that was published in Bitcoin magazine in September 2021. MSTR's holdings of Bitcoin have further evolved, but the concepts still remain.
This article will explore:
a) How we might discern the value of MicroStrategy (MSTR), a company in a fairly unique situation in the space, as well as the basics of how value investors operate.
b) Whether or not, given that MSTR is so heavily invested in bitcoin, the main opportunity cost of investing in MSTR is owning an equivalent amount of bitcoin. Hence, why it now makes more sense to value it in bitcoin than in dollars. The explanation is followed by some rough attempts to do just that.
c) Why the approach of pricing in bitcoin might become more and more relevant in the future.
As is well known, MSTR is a company which now has significant skin in the Bitcoin game. In August 2020 it was announced that they were adopting Bitcoin as their primary treasury reserve asset. They converted their entire corporate treasury into bitcoin and have continued to convert free cashflows into bitcoin since. There were also two convertible debt issues to follow, the proceeds of which were also fully converted to bitcoin. Most recently in June 2021, there was further non convertible debt issued, using the proceeds to purchase yet more bitcoin.
Some numbers for context. As of the time of this writing (August 5, 2021):
MicroStrategy HODLs 105,085 BTC worth a total of approx $4.1B (purchased at an average price of $26,080 per coin). The MSTR share price is currently $666, with a total company value of approx $6.5B. Their situation is unparalleled amongst other companies in terms of both:
- their bitcoin holdings as a percentage of their company value or market cap
- the overall size of the company.
In other words, other large companies (such as Tesla) hold much smaller percentages of bitcoin relative to company size, whereas other high percentage holders are simply far smaller in size.
These numbers can be seen at the following chart of bitcoin treasuries in publicly traded and private companies.
Starting around August of 2020, we began to see bitcoin being added to the balance sheets of public companies. One such company is MSTR. This is why you often hear MSTR described as a proxy Bitcoin ETF. However, it’s a more dynamic situation than that due to their likely ongoing BTC buys in the future. Hence why I’m looking at how a traditional value investor might value them.
https://twitter.com/saylor/status/1523646766549434373
Traditional Dollar Based Valuation
First, the way the market will mainly be valuing MSTR is in dollar terms. After all, the share price is priced in dollars and profits are made in dollars.
For those unfamiliar, I’m going to explain how this type of valuation might be formed step by step.
MSTR makes fairly stable profits and have not grown significantly in recent years.. The most conventional way of valuing a company like this is to sum up the present value of all of estimated future profits, and then to add in any other relevant assets aside from this, like bitcoin.
What do we mean by present value? $100 received in 10 years time is not as valuable as $100 right now , so we need to discount future profits by an interest rate to derive the value now.
For example, we might value $100 in 10 years as: $100 / 1.0122 ^ 10 = $88.60
The interest rate used here is the 10-year return on U.S. treasuries, seen as the “risk-free” rate of return on U.S. dollars. Treasuries are considered near risk free because if it ever came to it, the Fed could create more dollars to pay the obligation.
In other words, if we want $100 in 10 years, we can invest $88.60 now to return it. Conversely we can say that the prospect of being paid $100 in 10 years is “worth” $88.60 to us now. We can then repeat this calculation every year to “discount” all expected future profits and sum them all up. This method of valuation is particularly analogous to valuing companies paying dividends, since these profits get paid out to shareholders as cash flow streams. It’s pretty similar to the method of valuing a bond too.
As it happens, historically MicroStrategy did not pay out profits as dividends, but built up a large cash pile on their balance sheet, which is what led Michael Saylor to consider bitcoin in the first place. Whether dividends are actually paid out, put on the balance sheet, or reinvested in the business, it is the underlying ability to generate profits which underpins the basis of value investing.
In reality, analysts use a much higher interest rate in their calculation for valuing shares than the risk free rate. The overall interest rate used might reflect the risk free treasury rate for the period in question plus an additional “equity risk premium”. The latter reflects the fact that future profits are much less certain to be realised than nominal returns in U.S. treasuries, which are seen as risk free. This premium is highly subjective but may sit at about 5–6% per annum. for US Equities on average. .
All told, the current MSTR market cap of $6.5B reflects current bitcoin holdings worth $4.1B, plus the present value placed on the discounted sum of all future profits, along with other factors. These might include any positive or negative premium placed on MSTR by the market, and also an adjustment for the convertible debt issued, as to whether these are likely to be converted to equity at future dates.
In June 2021 there was a further bond issue announced, and yet another illustration of MSTR being in a dynamic situation and acquiring more bitcoin when the opportunity presents. This latest bond issue is not convertible. It has been used to buy more bitcoin now, but will reduce their capacity to convert future profits to bitcoin as they will have to pay these bond coupon payments as a priority. To illustrate this, the issue is $500m at an annual interest rate of 6.125%, so the company will have to pay around $30.6m each year to service the interest payments.
Bitcoin Based Valuation
I think there is now a slight issue with the conventional way of valuing MSTR in dollar terms. It relates to the opportunity cost of buying MicroStrategy shares.
Every time we invest in an asset, we forgo the use of that money somewhere else — this is called the opportunity cost. But where else might we hold that money? There is no way anyone is investing in MSTR now without being a believer in the substantial bitcoin held by them as a longer-term investment. Arguably, by investing in MicroStrategy one is mainly foregoing a “risk free” investment in bitcoin itself that they could otherwise hold. The logical result is to try and price MSTR in BTC instead. And in doing so, evaluate whether the MSTR investment is worth the bitcoin invested, versus the risks.
It’s worth noting that there are stakeholders out there for whom the only exposure to bitcoin permitted them is buying shares in a company such as MSTR. While this may be significant for some, let’s assume otherwise for now.
So how do we price MSTR in bitcoin? The starting point is simple: MicroStrategy holds 105,085 bitcoin right now.
We then need to add on a present value of all the bitcoin they might accumulate in the future. This is clearly the tricky part, as profits are in dollar terms, so we have to estimate how the bitcoin price in dollars might move over time. We also have to estimate the future profits of the company (same as before).
This article is focused more on the concept than the practice. I’m certainly not going to model either with any precision. However, I’ve made up some far-out scenarios to illustrate. In regard to profits converted to bitcoin, others are far better qualified to dig through the accounts, but for the purposes of this illustration let’s assume MSTR converts $50M worth of profits to bitcoin each quarter and that this continues for 15 years. All highly subjective.
How would we discount these profits? Holding BTC doesn’t offer a risk-free return, so we don’t have to use a treasury rate as above — we in effect use 0%.
However, the equity risk premium part referred to above should still stand. This again reflects the uncertainty of making an equity investment, in this case, versus simply holding the underlying risk-free bitcoin. Remember, it’s termed “risk free” in BTC terms.
Finally, we need prices of conversion to BTC. I’d view any stochastic analysis as simply impossible to get right. To keep things simple, let’s deterministically apply three scenarios for the next 15 years for an illustration:
a) “To the moon” — bitcoin hitting $1M per bitcoin in 15 years time.
b) “Slow and steady” — achieving growth of under 5% per annum to hit $80,000 per bitcoin in 15 years.
c) “False dawn” — a swift retreat down to $5,000 per bitcoin after this year and remaining at this level, supported only by hardcore HODLers from then on.
These are deliberately differing scenarios. The screenshot below shows — in theory — how much BTC might be purchased in each year for each scenario.
https://image.nostr.build/84d82466bb3158d34f08872ebda89dbf1eba27dd81bd234ee2843ac72dd96279.png
https://image.nostr.build/f32142c3788c9eb898420e0ea4016435751682b0907ec41682b304213184bbc1.png
Do not take these numbers seriously!
So how would we evaluate an investment of bitcoin into MSTR today?
To keep the illustration simple, let’s consider one share of MSTR and try to value this single share in bitcoin,in terms of the bitcoin MSTR holds now, plus future profits converted to bitcoin.
We then need to discount the additional future BTC buys from the table above, and add the sum of those to this too. So:
- We converted the assumed annual USD profits at the broad brush rates in each scenario (see table above);
- discount using the equity risk premium only to obtain the present values of future bitcoin purchases (see table below); and
- add the existing bitcoin that MSTR hold.
Summing these then provides an estimate of future bitcoin MSTR purchases under each scenario.
https://image.nostr.build/9bc4d14692a637495291291ed292ac92d0af62b81b5f9d25660f2f49c2e33e1c.jpg
[The question:“if we invest one bitcoin into MSTR shares, will we make a positive return on that when we value those shares in bitcoin?”]
As shown above, when we compare the overall value of sats that one share of MSTR might generate to the current price in SATs, we see the following returns -
a) -30%
b) -15%
c) +174%
Based on scenario A, it might be a hard sell to invest your bitcoin into MSTR. Scenario B is close to par, and scenario C actually looks like a good payoff in BTC terms.
The most striking thing about these results becomes obvious when you think about it. The worse bitcoin performs over the 15-year period in dollar terms, the better an investment MSTR looks when valued in BTC. This is as MSTR will acquire more BTC at a lower bitcoin price for the dollar profits it makes.
Many thanks for early comments on this article from @YATReviews on Twitter, who has pointed out this outcome is consistent with viewing MSTR as a “bitcoin dividend security”. For normal dividend stocks valued in dollars, their dividends (if consistent) can actually prove more powerful at compounding wealth when the share price is low, since those dividends purchase more shares.
The other point to note is that if BTC increases lots in dollar terms in the coming years, at the present size of the business MSTR may not move the dial that much in terms of adding to their holdings (see scenario A, where only around 10% more bitcoin is added to current holdings from future profilts).).
Some large disclaimers: as already mentioned, no allowance is currently made of the convertible bonds issued which can be converted to equity. My understanding is that the first offer had a conversion rate of $398 for 1.6M shares; a simple method is to include these on the number of shares in the valuation, if not included already. The second offering is at $1,432, so this is more complex to price. I would love any feedback on simple ways to include them. Also, there is the most recent “straight up” bond issue from June 2021 which is not convertible. Whilst we have assumed slightly lower profits converted to bitcoin due to the $30m annual coupon payments, we should also allow for the repayment of the $500m principal at expiration.
[On the above - see the "Quant Bros" on YouTube who have done much more in depth analysing MSTR in recent months. Since this article was written, the convertible debt has become much larger in terms of MSTR's repeated bitcoin purchases; this article simply assumed more regular buying over time from ongoing profits. Valuing the convertible debt is key - there is innate uncertainty over whether each tranche will get converted to equity, or repaid as debt]
https://image.nostr.build/4fc082eb54355ba2057126366c44f11ab6eecb52f7094cf0318aa6ede2b67cfb.jpg Credit — @bitcoingraffiti on Twitter
Final Thoughts
Why might this change of valuation method to value in bitcoin prove relevant?
Preston Pysh has previously commented on this. Imagine we were to move to an increasingly bitcoin denominated world in which bitcoin continues to appreciate and more and more companies hold bitcoin on their balance sheets.
Individuals with bitcoin would still make investments, but only if the potential of these investments outweigh the opportunity cost of just holding bitcoin instead. This might lead back to “value” equities performing well again, as entities generating profits can add more bitcoin to their balance sheets. Conversely, companies not generating free cashflows can’t, and hence their valuations when priced in bitcoin might be lower..
It might be said that the current trend to invest in growth equities results from everyone having a pretty high time preference — and hence not valuing future dividends as much. Bitcoin reduces time preference and hence might change this. For the concept to really resonate, future profits would be realized (or at least easily valued) in bitcoin. For now, it is only really bitcoin miners for whom this type of calculation can be made, (Adam Back has commented on this too) but even they have fiat denominated costs.
Disclaimer — the author owns both bitcoin and shares in MSTR. This article should not be taken as an endorsement to buy either.
-
 @ 6389be64:ef439d32
2024-04-25 17:02:18
@ 6389be64:ef439d32
2024-04-25 17:02:182024-04-25 at 09:50
Tags: #competition
Chemical Poetry
Imagine spending your entire life constructing a single poem to speak once to your only love and then dying. Every word desperately sought after. Complex aromatic chemicals are akin to syllables of words in a sentence. Chemical sentences are then strung together with cadence, tempo, and rhyme constructed to win the competition to mate with the queen. This is the life of the male orchid bee.
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Olfactory Filter]]
Location
-
 @ 9ecbb0e7:06ab7c09
2024-05-04 02:54:57
@ 9ecbb0e7:06ab7c09
2024-05-04 02:54:57Una serie de trabajadores cubanos fueron castigados y hostigados por los funcionarios de sus centros de trabajo por no acudir a los actos del 1ro de Mayo, según trascendió en varias denuncias visibilizadas por el medio independiente Diario de Cuba.
Operarios de los Laboratorios Oriente, perteneciente al grupo de industrias biotecnológicas y farmacéutica BioCubaFarma, fueron víctimas de sanciones y hostigamiento luego de justificar su inasistencia a los eventos organizados por el régimen en Santiago de Cuba.
Una de las trabajadoras, identificada como Gisela Bermúdez, dijo a Diario de Cuba que recibió como sanción un mes sin estimulación salarial, aunque había argumentado que la falta de transporte y de desayuno para sus hijos le impedía moverse hasta el lugar.
Otra persona, Olga Martínez, que labora en la Planta de Sueros y Soluciones Parenterales, recibió una amonestación porque “caminar en medio de un apagón —y a las 2:00AM– los diez kilómetros que median entre la Plaza de la Revolución Antonio Maceo y el reparto Abel Santamaría no es justificación para faltar a una celebración tan importante”, según le respondió el director general de la empresa.
Un hombre nombrado Charles, además, está en riesgo de perder su plaza en la línea de vendas enyesadas, por argüir que “un país con escasez de todo tipo no podía darse el lujo de concentrar al pueblo para que se desmayara del hambre y se congraciara con el Gobierno”.
Las universidades, centros de salud y otras industrias también fueron objeto de serias amenazas y chantajes hacia los trabajadores que eligieron lo ir a los desfiles.
Uno de ellos, Dayan, admitido en la Educación Superior sin aprobar los exámenes de ingreso, le reclamaron no haber ido a las actividades cuando disfruta de “las bondades” del régimen.
“Podías estar en las calles, a merced de conductas antisociales, de la droga y la prostitución”, le gritaron en el aula, dijo en su testimonio.
Los actos por el 1ro de Mayo, celebraciones de reafirmación del régimen, no pueden estar más alejados de la conmemoración del Día del Trabajo, cuando los empleadores usan medios de coacción para obligarlos a asistir a las actividades de apoyo al Gobierno.
La prensa oficialista dio amplia cobertura el 1ro de mayo a las actividades organizadas en las distintas localidades del país por el Día del Trabajo, mientras omitía que para realizar esas acciones, los funcioanarios del régimen habían tenido que recurrir a amenazas y que quizás la mayoría de los trabajadores no fue por voluntad propio sino por la obligatoriedad del asunto.
Muchos cubanos debieron hacer el esfuerzo de madrugar para asistir a desfilar, portar pancartas en favor del Gobierno y sudar bajo el sol abrasador. De regreso, les esperó una jornada de interrupciones en el servicio eléctrico.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ a012dc82:6458a70d
2024-05-04 01:51:30
@ a012dc82:6458a70d
2024-05-04 01:51:30Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Tokens that can't be exchanged for other currencies are called NFTs. Nonfungible is a term often used in economics to describe characteristics like rarity and irreplaceability. Nonfungibility in the crypto world means that one asset cannot be used to purchase another.
Tokens are used as a unit of account because they serve as certificates of validity that are recorded on the distributed ledger (blockchain), allowing anybody to verify the ownership of digital assets. Therefore, NFTs are a special sort of digital money that may take the form of anything creatively digital, including but not limited to paintings, films, songs, in-game collectibles, and other digital works of art.
convert digital art into NFT Ever since the price of NFTs skyrocketed at the beginning of 2021, investors all over the globe have been buying and selling these tokens. However, the challenges of converting original works of art into NFTs and marketing them remain. Could you describe how challenging it is? Does creating an NFT require the use of codes?
The procedure, in brief, is straightforward. Read on for a synopsis of the main steps and their explanations.
What is cryptographic art?
For this reason, it should come as no surprise that crypto art in the form of NFTs has lately seen a meteoric rise in popularity, given that the most prevalent use of NFTs is in the arts. Many artists, who could previously only dream of earning tens of millions of dollars from their digital paintings, have been drawn to the industry as a result of the revolutionary blockchain technology that now makes this possible.
Auctions of highly publicized NFTs associated with digital art have garnered a lot of interest due to their sensational nature. Sales of the most valuable items made news because of their high dollar amounts. "Merge," by the anonymous digital artist Pak, sold at auction in 2022 for $91.8 million, making it the most expensive NFT ever sold.
Another high-priced auction in 2021 was the sale of artist Mike Winkelmann, also known as Beeple,'s Everydays: the First 5000 Days NFT collection for $69.3 million.
Famous artists produce one-of-a-kind works of crypto art, which are then auctioned off on various markets, including NFT platforms and more conventional auction houses like Sotheby's and Christie's. However, undiscovered creative newcomers still do the vast bulk of crypto-space artwork.
Some NFT collections, such as the original CryptoPunks or the most talked-about collection lately, Bored Ape Yacht Club, are instances of generative art. The majority of this kind of artwork is made with the aid of AI algorithms. The graphics in these sets are made up of a small number of basic parts that are pieced together in a variety of ways to form the final product.
How do you turn your art into an NFT?
The answer to the question of whether or not you should adapt your work into an NFT is a resounding "sure, why not try?" Making an NFT does not need any complicated, expensive, or technological steps. All you need is some imagination and access to a computer.
It is important to note once again that NFTs have the capacity to convert not only photos but also music, video, GIFs, and other digital goods. So, the first step is to figure out what kind of artistic practice best matches your personality and skills. Depending on the results, you'll learn what abilities are necessary to make legitimate NFTs.
For instance, Adobe Illustrator, Adobe Photoshop, Microsoft Paint, CorelDraw, and similar programs are all necessities for every graphic designer. The more advanced technique of three-dimensional (3-D) modeling is another option. If you go with 3D animation, you'll have to use programs like Blender or Cinema 4D to create models and animations that can be exported as NFTs.
After that, you need to consider the final form your artwork (or group of artworks) will take and come up with a fresh concept for it.
Is coding necessary for NFTs?
Making an NFT from digital art is a breeze if you don't know how to code. It is termed "minting" when they are created. It's the act of making a copy of the token public on the blockchain. The process of creating NFTs is called "mining," and it's quite similar to the production and distribution of physical coins.
After this process, the piece of digital art is protected from tampering and is difficult to alter in any way. With its newfound status as a non-fungible token, this digital good may be purchased, sold, and digitally monitored in the event of a subsequent sale or recall.
Minting NFTs into digital works of art is an innovative and equitable method for artists to commercialize their work. Most NFT markets allow artists to pre-program a royalty clause at the time of minting, allowing them to earn a passive income from their works' secondary sales. Artists stand to gain financially if their work is in high demand, gains notoriety, and appreciates in value.
If you already have relevant skills and are determined to get into the NFT development industry, you may, however, try your hand at writing your own NFT. Before diving headfirst into NFT programming, it's important to keep in mind that the Ethereum network is still the only place where NFTs may be created.
Solidity, a programming language developed for creating smart contracts that operate on the Ethereum blockchain, is widely used for NFT development. JavaScript and HTML/CSS are two others. In addition, most musicians and artists save their NFTs in the InterPlanetary File System.
Choosing the NFT marketplace to make and sell your NFTs
Selecting an appropriate NFT platform is crucial throughout the minting process. The transaction fee, or the cost associated with minting a new NFT, is meant to compensate the platform for the time and resources spent processing and validating user transactions. Other considerations include the file formats accepted, the compatibility of user crypto wallets, the ease of access to the platform, and the price to mint an NFT.
There are a wide variety of NFT markets available online in the crypto industry, and their individual methods of operation might be rather distinct from one another. What's most important for artists is to understand if the platform is curated or self-service focused, so they can choose the one that's best for them in terms of fit, traffic, and ease of use.
Non-curated, self-service NFT platforms are open to any and all musicians without charge. All that is required to mint an NFT is a cryptocurrency wallet registration and the transaction cost. OpenSea and Rarible are two of the most well-known examples of scalable, self-service NFT markets.
For this reason, curated NFT services are pickier about which musicians they promote. You'll need to fill out an application outlining your background in the arts and the NFT collection in order to begin selling your work on these sites.
The time it takes for the experts to make a choice is another obvious drawback of curated NFT markets. However, because of these rigorous selection procedures, only the best digital artworks are shown on such platforms, giving customers greater faith in the artists who work with these venues. You may be familiar with curated marketplaces like SuperRare and Nifty Gateway.
Setting up a cryptocurrency wallet
To use NFT platforms, sign transactions, and monitor your balance, you'll need a bitcoin wallet.
Make sure the wallet supports the coin of the NFT platform you wish to use before you set it up. Due to the fact that most NFT exchanges are built on top of Ethereum, Ether, Ethereum's native coin, is widely accepted. So, you'll want to make sure you have some Ether (ETH) in your cryptocurrency wallet.
Numerous cryptocurrency wallets boast millions of active users. Many of them offer a wide range of features, and some even come with dedicated mobile apps and browser add-ons for quick interaction with blockchain networks.
What level of security you need will determine which bitcoin wallet is best for you. Three major categories of cryptocurrency wallets exist: custodial, noncustodial, and hardware. Custodial wallets, also known as hosted wallets, are managed by a third party on behalf of the user, much like how banks manage checking and savings accounts.
It's the easiest to set up and has the best user interface. By eliminating the need for a trusted third party to store user cryptocurrency, a "noncustodial" wallet improves privacy and security. Hardware wallets, often known as "cold wallets," are storage devices that users may use to store their cryptocurrency offline, where it will remain safe even if the user's computer is compromised.
How to sell digital art as NFTs
Your NFT minting will most likely culminate in an NFT sale. When minting a new NFT, most services give you the choice of setting its selling price or distribution mechanism.
At the moment, the two most common methods for selling NFTs are a fixed-price sale or an auction. Many people choose a fixed-price sale since it's the most straightforward transaction kind. You just need to choose the price at which you want to sell your newly created NFT in order to do so. Also, keep in mind that some sites may want you to choose a royalty rate, which will determine how much of the proceeds you will earn from any future sales of your artwork.
Another option for recouping some of your investment in your NFT is to host an online auction where interested parties may peruse your work and place bids. Some auctions may be conducted solely online, while others may culminate in a traditional live event. Two basic varieties exist.
An English auction is the first kind, and it's the one where the highest bidder ultimately wins. A timed auction is a subset of English auctions in which a non-fungible token (NFT) is up for bid for a set amount of time, after which the bidder with the highest total amount wins. The other kind of sale is called a Dutch auction, and it works like this: the price of your NFT gradually decreases until it is purchased.
Which method of selling NFT you choose is entirely up to you. Both establishing a fixed price and selling at auction have inherent drawbacks, such as the potential for misunderstanding the true worth of one's artwork.
Conclusion
You have now finished developing your NFT. With NFT, the creator not only benefits monetarily from the first sale of their work but also from subsequent sales of NFT tokens for as long as those tokens remain in circulation. It is not difficult to turn anything remarkable into NFT and sell it if you have the ability to do it. The setup is quite simple. This may be done by anyone, too. All you need is access to a reliable NFT marketplace.
FAQ
Is it possible to make something that just uses NFTs and then sell it? Tokens that can't be exchanged for other tokens are called "non-fungible tokens," and they're a special kind of crypto asset. In the NFT market, users may upload digital material and sell it to other users. The generation of NFTs is supported by a number of blockchains, with Ethereum being the most widely used.
Approximately how much does it cost to convert artwork into NFT? Making NFT might set you back anything from $0.05 to $150. NFT creation costs may include but are not limited to blockchain fees, gas fees, marketplace account fees, listing fees, and so on. The most costly blockchain is Ethereum, while the least expensive is Solana.
Can I use NFT to sell digital artwork I created myself? Yes. A non-volatile token (NFT) may be used to hold any kind of digital content. There are several online markets, and more are adding support for video, gaming assets, and music every day. Even traditionally tangible goods, like limited-edition Nike sneakers and other collectibles, are increasingly being digitized as NFTs.
If you want more, be sure to follow us on:
*NOSTR: croxroad@getalby.com*
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A biblioteca infinita
Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da Wikipédia me dizer isso.
Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias.
Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos.
Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page.
Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever.
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
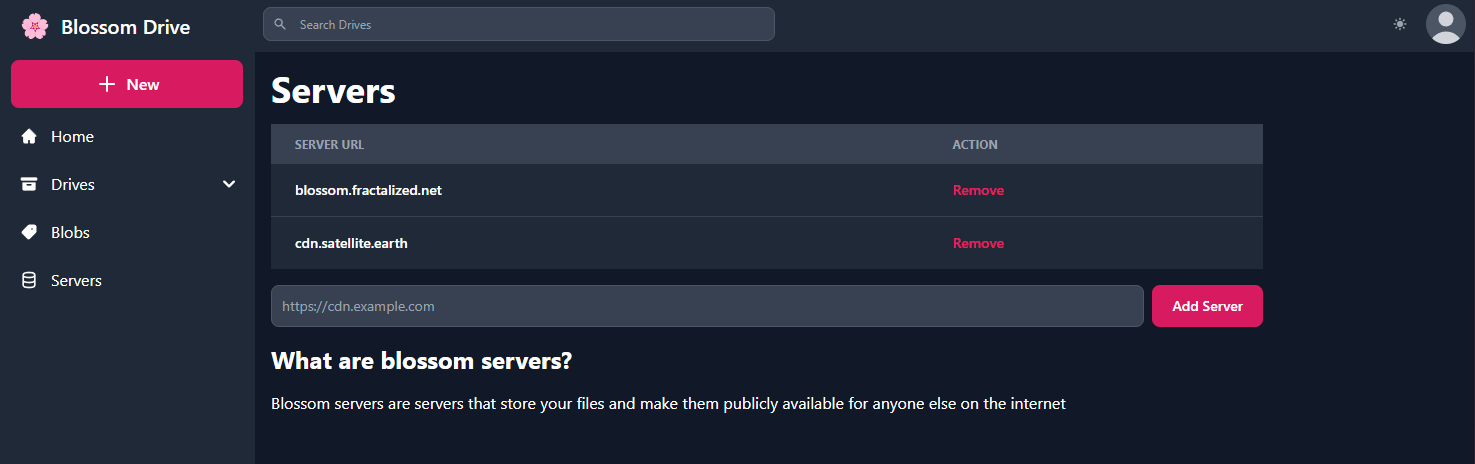
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
And obtain the HTTP direct link by clicking on the "Copy Link" button:
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 63fe6318:330504ed
2024-04-24 14:52:50
@ 63fe6318:330504ed
2024-04-24 14:52:50Project Status'
Snort
Full commit history: 754 Commits, +35,843, -19,639
Versioned releases: - v0.1.19 (2023-10-02) - v0.1.20 (2023-10-11) - Iris migrates to Snort codebase - v0.1.21 (2023-10-18) - v0.1.22 (2023-10-21) - v0.1.23 (2023-11-23) - v0.1.24 (2023-12-14)
git-fame --since 2023-09-31 --branch 7b72f9f7750aaec9d6ba40373ff3ca66125588b5 --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:-----------------|------:|------:|-------:|-------:|:----------------| | Kieran | 73 | 49669 | 373 | 463 | 65.0/49.4/50.5 | | Martti Malmi | 98 | 25982 | 359 | 410 | 34.0/47.5/44.7 | | Fernando Porazzi | 2 | 416 | 5 | 13 | 0.5/ 0.7/ 1.4 | | mmalmi | 2 | 294 | 6 | 21 | 0.4/ 0.8/ 2.3 | | w3irdrobot | 2 | 37 | 1 | 2 | 0.0/ 0.1/ 0.2 | | James McGauran | 2 | 20 | 5 | 2 | 0.0/ 0.7/ 0.2 | | fiatjaf | 2 | 12 | 2 | 2 | 0.0/ 0.3/ 0.2 | | Kamal Raj Sekar | 2 | 10 | 2 | 2 | 0.0/ 0.3/ 0.2 | | benthecarman | 2 | 2 | 1 | 1 | 0.0/ 0.1/ 0.1 | | vivganes | 2 | 1 | 1 | 1 | 0.0/ 0.1/ 0.1 |
Snort API
Along with the public UI code there is a private repo containing the backend api which handles auxiliary services for snort.social like fetching link previews and handling donations and NIP-5 services.
The API docs are publicly accessible https://api.snort.social/swagger
I am also in the process of moving some of these functions to a public repo, they are listed below under NostrServices
git-fame --since 2023-09-31 --branch b669a92f6f1ddfba8af0be9afee22ced90a0cf9c --cost hour| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 18 | 3560 | 68 | 56 | 100.0/ 100/100.0 |
zap.stream
zap.stream does not yet follow a versioned release scheme, instead I have listed the major changes over this timeframe.
- Stream summary page (Example)
- Gives an overview of previous streams with top chatters and top zappers
- Stream activity timeline graph
- Tailwind CSS upgrade
- Streamlines CSS inside zap.stream
- Custom player overlay
- Select stream quality (720p/480p/Auto)
- UI themes (Primary colour only)
- Stream dashboard https://zap.stream/dashboard
- Gives the streamer an overview of their stream allowing them to see a dedicated zaps feed
- Chat moderation operations (Mute) shortcuts for unique
- Stream raids feature
- Allows hosts to redirect their viewers to another stream
- This is a feature which twitch.tv has and helps to retain viewers by redirecting them to another streamer on the site who is still live. This is usually performed at the end of the stream.
- Stream forwarding feature
- Supported by the zap.stream hosting solution, you can forward your stream automatically to other platforms directly.
- This is identical to restream.io platform, it's provided for free as part of the hosted streams.
- Direct support for entering stream keys for YouTube/Twitch.tv/Facebook/Kick/Trovo
- Custom RTMP destinations also supported.
- Clips feature
- Supported by the zap.stream hosting solution, allows users to create a stream clip (mp4) from the previous 60s
- Stream clips are posted in chat for everybody to see and can be shared anywhere on nostr.
- Surfacing clips on profiles and other places is yet to be implemented.
- Push Notifications
- Supported by the zap.stream hosting solution, allows viewers to subscribe to notifications for a given streamer (Bell Icon)
- Viewers will receive push notifications when this streamer goes live.
git-fame --since 2023-09-31 --branch 039d2d15513cacab99b0ae8abe587d0e0bef0ddc --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:----------------| | Kieran | 13 | 22594 | 97 | 162 | 99.9/98.0/99.4 | | florian | 2 | 32 | 2 | 1 | 0.1/ 2.0/ 0.6 |
zap.stream backend
Along with the the public UI codebase there is also another private repo which contains the code for the backend hosted streaming solution.
git-fame --since 2023-09-31 --branch 5b5f011df0c0c2f7105a25be1cef7fd74db96ce6 --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 5 | 3105 | 18 | 41 | 100.0/ 100/100.0 |
DTAN.xyz
I had an idea for another app one day and i decided to make it, this site allows people to list torrents on nostr, it appears to be well received.
The repository is here: https://git.v0l.io/Kieran/dtan
The name itself is an acronym for Distributed Torrent Archive on Nostr nostrudel.ninja has also added support for this event kind (2003) There is no NIP for this kind. The kind number comes from the founding date of the thepriatebay.org (2003)
Commit History
git-fame --cost hour| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:----------------| | Kieran | 9 | 8242 | 22 | 56 | 91.7/78.6/74.7 | | florian | 3 | 745 | 6 | 19 | 8.3/21.4/25.3 |
void.cat
Another service I provide is https://void.cat this service is a public anon file upload sharing site, during this quarter I have added support for the recently merged NIP-96
The repository is here: https://git.v0l.io/Kieran/void.cat
git-fame --since 2023-09-31 --branch ce7c3613a844dc11eee8a1078e433c30f2c0216c --cost hour -M -C| Author | hrs | loc | coms | fils | distribution | |:---------|------:|------:|-------:|-------:|:-----------------| | Kieran | 9 | 28326 | 26 | 145 | 100.0/ 100/100.0 |
NostrServices
I have began to migrate some of the useful functions from Snort API into a public repo, this is a C# repo which contains multiple packages and services which anybody can run.
The goal of this repo is to provide a few Docker images for caching API's and custom relays.
The repository is here: https://git.v0l.io/Kieran/NostrServices
Public API: https://nostr.api.v0l.io/swagger
All the commits to this repo are out of scope as they started on 2024-01-10, lookout for the commit history in the next report!
Outlook
Snort
The current plan for snort.social is to optimise performance and the onboarding experience / community building, we're currently building a full nostr relay in the browser that we will interact with as a WebWorker, early tests look promising and should pave the way for more advanced features like P2P note sharing and in-client algorithms, as well as improving overall performance.
On the community building front, I have created a "Community Leaders" programme that will help local community leaders build their Nostr community and get more users on board. It will also create communication channels for these communities to help inform Snort developers about issues or features that these communities want. This programme is partially rolled out and there is a landing page here https://community.snort.social/
Hopefully more Nostr clients will implement a similar programme, giving community leaders a stronger presence and reward for their efforts.
Another side project is to improve the documentation for Snorts' internal libs which are available for all developers to use via npm:
@snort/system@snort/system-react@snort/system-web@snort/shared@snort/system-wasmA documentation site has been created to help developers to use the library and more examples and documentation will be created over time.
zap.stream
Growing
A very important part of growing zap.stream is getting more content creators on board, part of that is creating a familiar experience, but also making it very easy for streamers to multi-stream, so I created the re-stream feature, streamers can easily stream to zap.stream plus twitch.tv or youtube.com without any cost or effort.
Linking content between platforms can also be a great way to showcase the power of zap.stream. A lot of work has gone into making sure that the OpenGraph tagging and overall SEO of zap.stream and snort.social is optimal.
I believe that zap.stream already provides a good live streaming experience and that getting more content is the primary focus for zap.stream right now.
It would also be wise to have exposure in both app stores and I plan to do that.
Refining
While zap.stream offers a good feature set, there is always room for improvement, the recently added raid and dashboard features still need some work.
Clips for example do not appear anywhere outside of the live stream chat, it is not yet possible to share these clips, these are immediate areas that need improvement, I plan to make clips appear on profiles similar to twitch.tv and also make them shareable and of course make sure they are tagged correctly for link previews on all legacy social platforms.
- Stream summary page (Example)
-
 @ d34e832d:383f78d0
2024-05-05 08:30:22
@ d34e832d:383f78d0
2024-05-05 08:30:22Specific challenges coupling the use of differential heuristics in A* algorithm aim to overcome in the Lightning Network
The Lightning Network presents a labyrinth of challenges when it comes to efficient routing, with obstacles like varying channel capacities, fees, and availability complicating the process. Differential heuristics within the A algorithm are engineered to tackle these obstacles head-on, aiming to overcome specific challenges, including:
 Reducing the Number of Nodes Visited During Pathfinding*
Reducing the Number of Nodes Visited During Pathfinding*In the sprawling expanse of the Lightning Network, conventional pathfinding algorithms often get lost in a maze of possibilities. Differential heuristics act as a guiding light, leading the search algorithm directly to the optimal route while minimizing the number of nodes visited. This efficiency streamlines the pathfinding process, as highlighted in [0].
 Handling Irregular Terrain or Obstacles
Handling Irregular Terrain or ObstaclesJust as hikers navigate rugged landscapes, differential heuristics navigate the irregular topology of the Lightning Network. Each channel represents a unique terrain feature, with its own set of challenges. By adapting to these obstacles, differential heuristics optimize routing decisions, ensuring transactions flow smoothly across the network ([2]).
 Improving Pathfinding Efficiency
Improving Pathfinding EfficiencyTime is of the essence in Lightning Network transactions. Differential heuristics inject speed into the pathfinding process by leveraging multiple heuristics and their differences. This optimization not only saves computational resources but also ensures lightning-fast routing, essential for seamless transactions ([4]).

Adapting to Dynamic Changes
The Lightning Network is in constant flux, with channels opening, closing, and balances shifting. Differential heuristics are adept at navigating this ever-changing landscape, adjusting their strategies dynamically. While cached data may need occasional recalibration, the adaptability of differential heuristics ensures swift responses to network dynamics ([5]).
In essence, differential heuristics within the A* algorithm serve as beacons of efficiency in the Lightning Network's intricate web. By addressing challenges related to pathfinding efficiency, dynamic adaptability, and network complexity, they pave the way for smoother transactions and an enhanced user experience.
Sources: - [0]: Optimizing Pathfinding Efficiency - [1]: Improving Payment Success Rates - [2]: Navigating Irregular Terrain - [3]: Ensuring Security and Privacy - [4]: Efficient Pathfinding Strategies - [5]: Understanding Lightning Network Dynamics
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O VAR é o grande equalizador
Não tenho acompanhado o futebol desde 2013 ou 2014, mas me parece que, como poderia ter sido previsto, o VAR tem favorecido os times pequenos ou marginais em detrimento dos demais.
É lógico: se os juízes favoreriam mais o Flamengo e o Corinthians, e depois os grandes de Rio e São Paulo, em detrimento dos demais, o VAR, por minimamente mais justo que seja, aparentará favorecer os outros.
-
 @ 63fe6318:330504ed
2024-04-24 14:43:40
@ 63fe6318:330504ed
2024-04-24 14:43:40Project status'
tl;dr In 2024 Q1 I mostly focused on improvements to the
@snort/systemlib's while building the new https://nostrnests.com and on the new zap.stream backend calledzap-stream-corewhich is a custom built streaming server in Rust and UX improvements to zap.stream for new users.Snort
Snort had 1 regular release during this time v0.2.0 which included most notably: - New settings pages - Community leaders programme - New wallet system - Alby OAuth integration - Cashu wallet integration - Worker Relay (nostr relay in the browser) - Negentropy v1 support (efficient sync between relays, similar but simpler version of minisketch from bitcoin-core)
Right now as of April 24th im current doing another round of improvements to
@snort/systemto try to improve the performance of Snort. Most of the complaints which people raise are for performance.git-fame --since 2024-01-01 --branch a3f139399973df4caa1e2e20b83ce80663fae90b -M -C| Author | loc | coms | fils | distribution | |:----------------|------:|-------:|-------:|:----------------| | Kieran | 14259 | 192 | 283 | 67.5/41.9/40.4 | | Martti Malmi | 6852 | 265 | 417 | 32.5/57.9/59.5 | | Kamal Raj Sekar | 1 | 1 | 1 | 0.0/ 0.2/ 0.1 |
snort-api
https://api.snort.social/swagger
git-fame --since 2024-01-01 --branch b9a54b4913601079d4da51cb0a245e1f202b5ca7 -M -C| Author | loc | coms | fils | distribution | |:-------------|------:|-------:|-------:|:----------------| | Kieran | 797 | 24 | 119 | 99.9/96.0/99.2 | | Martti Malmi | 1 | 1 | 1 | 0.1/ 4.0/ 0.8 |
zap.stream
zap.stream doesnt have tagged versions but here are a few notable changes: - Embedded player (Used in Twitter embed https://twitter.com/djsenior13/status/1782820643022458934) - More Tailwind CSS updates - A profile editor page! - Stream categories (Gaming/IRL etc) - FAQ page for some tips on how to get started streaming - Search (NIP-50) - Dedicated clips page (eg. nostr:nevent1qqsqxqwl46sjjqpfu5t53p3kdq7fymjjrtlut5raq7lfw7l058866yqppemhxue69uhkummn9ekx7mp0qgsy6zk38378ln3qc06upjf2vt4p7mhrvunga3l0sl4043rgyhgxhwcrqsqqqpfpj7esy5) - Inline note reactions in chat - New stream summary - New dashboard flow for new users (New users follow: https://zap.stream/dashboard/step-1) - Balance withdrawal
git-fame --since 2024-01-01 --branch 8dd74affa7b4d6a2801b917fda9bc7bff24f3ae1 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 11386 | 56 | 184 | 100.0/ 100/100.0 |
zap.stream API
The backend API manages access to the hosted streaming service and accounting system for zap.stream.
Changes: - Improved accounting to enable withdrawals - Balance withdrawal - Delete old recordings after 90 days - Video game search for selecting game category
git-fame --since 2024-01-01 --branch 37f84592f41be36295619ecb564459c536b2c0d9 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 582 | 22 | 41 | 100.0/ 100/100.0 |
zap-stream-core
zap-stream-coreis a new project built from scratch in rust usingffmpegto process video streams in real time.The goal of this project is to improve my rust and ffmpeg knowledge and ultimately make
zap-stream-corea self-hostable platform where people could offer their streaming services via zap.stream using a marketplace of providers.With these newly acquired skills it will also enable me to create more media heavy applications like YouTube or TikTok.
The current state of the project is that i can publish streams into the server and get HLS output but im currently struggling with AV Sync.
git-fame --since 2024-01-01 --branch 9c4969cf9514b713ddf97eaaa4d2a37a69d53581 -M -C| Author | loc | coms | fils | distribution | |:-----------------|------:|-------:|-------:|:-----------------| | Kieran | 3065 | 11 | 33 | 100.0/ 100/100.0 |
DTAN.xyz
DTAN is a nostr client for viewing only
kind 2004events which are Torrents.There hasn't been any major changes since last quarter.
NIP-35
A PR was opened recently to formalise the torrent spec: https://github.com/nostr-protocol/nips/pull/1175
Prowlarr
PR was created to add support for searching nostr torrents with Prowlarr, Prowlarr is used to aggregate search results from multiple indexes and feeds data to downstream applications like Sonarr and Radarr which are used to download TV shows and movies automatically.
https://github.com/Prowlarr/Prowlarr/pull/2100
git-fame --since 2024-01-01 --branch 106b1dcbd84a3ed6cda00dfb57eee371f7b3bcc7 -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:-----------------| | Kieran | 2745 | 2 | 16 | 100.0/ 100/100.0 |
NostrServices
https://nostr.api.v0l.io/swagger NostrServices provides free nostr client useful apis.
git-fame --since 2024-01-01 --branch 0a42894a6f9cb20969097d6e620578cb60ef22fd -M -C| Author | loc | coms | fils | distribution | |:---------|-------:|-------:|-------:|:-----------------| | Kieran | 119730 | 59 | 289 | 100.0/ 100/100.0 |
nostrnests.com
https://github.com/nostrnests/nests NostrNests V2 was a complete rebuild which took place in Feb 2024.
The backed is C#, the same as zap.stream The frontend is a typescript React app using the
@snort/systemlibsgit-fame --since 2024-01-01 --branch 26329cc686b243aa497bd4638124942cabfe180d -M -C| Author | loc | coms | fils | distribution | |:---------|------:|-------:|-------:|:----------------| | Kieran | 51870 | 76 | 187 | 100.0/98.7/99.5 | | florian | 1 | 1 | 1 | 0.0/ 1.3/ 0.5 |
Plans for Q2
- Start on boarding community leaders into the leaders programme.
- Expand zap.stream categories with ranking / popularity using sats and viewer stats.
- Continue build out and launch trial of
zap-stream-core - Make Snort the fastest and most decentralised nostr client.
- Somehow find time to maintain all these projects.
-
 @ d34e832d:383f78d0
2024-05-05 06:46:49
@ d34e832d:383f78d0
2024-05-05 06:46:49The Lightning Network, a second-layer solution built on top of the Bitcoin blockchain, offers a promising avenue for fast and cost-effective transactions. However, routing payments through this network presents its own set of challenges. Let's delve into the different approaches to routing transactions on the Lightning Network and how they address these challenges.
Source Routing
Traditionally, the Lightning Network has relied on source routing, where the sender calculates the entire payment route before initiating the transaction. While this method ensures strong privacy since only the sender knows the complete path, it can become less efficient as the network grows due to the increasing complexity of finding optimal routes.
JITRouting (Just-In-Time Routing)
JITRouting is an improvement that learns from past routing attempts. When a payment fails, the network uses this information to avoid inefficient paths in future attempts. This adaptive approach enhances routing efficiency by leveraging past failures to guide future routing decisions.
Multipath Payments (MPP)
To overcome the limitations of single-path payments, Lightning incorporates Multipath Payments (MPP). This approach splits a payment into smaller parts routed separately through the network, increasing the likelihood of successfully routing large payments without relying on a single path with sufficient capacity.
Use of Differential Heuristics in A* Algorithm
The Lightning Network community explores the use of differential heuristics in the A* algorithm for map preprocessing. This technique reduces the number of nodes visited during pathfinding, especially in complex network topologies, optimizing route discovery and enhancing network efficiency.
Permuteroute Algorithm
The Permuteroute algorithm offers an alternative approach to route discovery by efficiently finding paths between nodes without scanning a large number of channels. While providing immediate benefits, it is considered alongside broader improvements like incorporating past pathfinding attempts into mission control within Lightning software.
Collaborative Routing with Routing Hints
Collaborative routing involves using routing hints included in payment requests to suggest intermediate nodes or channels that could facilitate the payment. This method improves routing efficiency and potentially enhances privacy by offering multiple route options.
These diverse approaches underscore the ongoing development and optimization efforts within the Lightning Network community. By leveraging these strategies, the Lightning Network aims to provide a scalable, efficient, and private framework for routing micropayments over Bitcoin.
Sources:
- [0]: GitHub Discussion on Lightning Network Routing
- [1]: Understanding Multipath Payments on Lightning Network
- [2]: Exploring Differential Heuristics in A* Algorithm
- [3]: Permuteroute Algorithm Proposal
- [4]: Collaborative Routing with Routing Hints
Harnessing the Power of Multipath Payments in Lightning Network Routing
Can multipath payments be used in combination with other routing strategies to further enhance routing efficiency?
Multipath payments (MPP) offer a promising avenue to improve routing efficiency on the Lightning Network. When integrated with other routing strategies, MPP not only enhances transaction success rates but also optimizes fee management, privacy, and network load distribution.
Combining MPP with Source-Based Pathfinding
Source-based pathfinding, where the sender calculates the route, can be seamlessly integrated with MPP. By splitting large payments into smaller parts and finding multiple optimal routes simultaneously, this combination improves success rates while balancing the network load. This approach, as discussed in [3], ensures better channel capacity utilization and reduces congestion.
MPP and JIT Routing
Just-In-Time Routing (JITRouting), while not explicitly mentioned in the provided context, dynamically adjusts routing decisions based on real-time network conditions. When paired with MPP, JITRouting can adapt the sizes of payment parts or choose different routes based on changing channel capacities. This adaptive strategy ensures efficient payment completion, even in the face of sudden network changes.
Strategic Fee Optimization
Leveraging MPP allows senders to strategically optimize fees by choosing the most cost-effective paths for each payment fragment, as suggested in discussions from [0] and [5]. By splitting payments and selecting routes based on fee structures, this approach minimizes transaction costs without compromising efficiency.
Enhancing Privacy with MPP
Integrating MPP with privacy-enhancing techniques, such as onion routing for each part of a multipath payment, further obscures transaction trails. By diversifying payment paths, MPP makes it challenging for observers to trace fund movements, enhancing overall transaction privacy.
Incorporating MPP into Lightning Network Routing
Incorporating MPP into Lightning Network routing strategies not only addresses the limitations of individual approaches but also maximizes their strengths. This synergy results in a more resilient, efficient, and private Lightning Network, showcasing the ongoing innovation within the Lightning community.
By harnessing the power of MPP alongside other routing strategies, the Lightning Network continues to evolve, offering faster, more cost-effective, and private transactions for users worldwide.
Sources: - [0]: Linux Foundation - MPP and Fee Optimization - [1]: Linux Foundation - Privacy Enhancement with MPP - [2]: Linux Foundation - JITRouting and MPP - [3]: Lightning Network Book - Understanding Routing Strategies - [4]: Linux Foundation - Optimizing Network Load with MPP - [5]: Linux Foundation - Strategic Fee Optimization

Maximizing Routing Effectiveness with Routing Hints in the Lightning Network
How do routing hints improve collaborative routing effectiveness in the Lightning Network?
Routing hints serve as invaluable tools within the Lightning Network, significantly enhancing collaborative routing effectiveness by providing essential information to streamline payment processes. These hints, embedded within payment requests, offer insights into potential routes or intermediate nodes, optimizing transaction pathways and bolstering network efficiency.
Facilitating Payments Through Unannounced Channels
Unannounced channels, concealed from the public channel graph, are vital components of Lightning Network transactions. Routing hints, as detailed in [2] and [3], empower payments to navigate through these hidden channels effectively. By leveraging routing hints, participants can exploit unannounced channels, expanding routing options and bolstering the network's capacity to facilitate transactions discreetly.
Improving Payment Success Rates
Routing hints enhance payment success rates by revealing alternative paths beyond the public network graph, as discussed in [0]. When conventional routes face constraints such as capacity limitations, routing hints offer alternative pathways, ensuring smoother transaction completion. This flexibility minimizes transaction failures and optimizes the overall efficiency of the Lightning Network.
Enhancing Privacy and Security
Beyond facilitating payment delivery, routing hints fortify transaction privacy and security. By steering transactions away from heavily monitored channels, these hints safeguard user anonymity. Moreover, routing hints contribute to security by diversifying transaction pathways, mitigating potential threats targeting transaction flows, as highlighted across the provided sources.
Supporting Decentralization Efforts
Routing hints play a pivotal role in advancing the Lightning Network's decentralization agenda. By empowering payments to traverse diverse channels, including unannounced ones, these hints foster network inclusivity. Smaller nodes and those with unannounced channels can actively participate, redistributing routing responsibilities and promoting a more decentralized network architecture.
In essence, routing hints are indispensable elements that bolster collaborative routing within the Lightning Network. By expanding routing possibilities, enhancing privacy, and supporting decentralization initiatives, routing hints contribute to a more robust and efficient Lightning Network ecosystem.
Sources: - [0]: Enhancing Payment Success Rates - [1]: Understanding Lightning Network Routing - [2]: Exploring Channel Graph Dynamics - [3]: Ensuring Security and Privacy - [4]: Navigating Through Unannounced Channels - [5]: Optimizing Routing Efficiency - [6]: Advancing Transaction Privacy - [7]: Strategies for Routing HTLCs
-
 @ 81870f53:29bef6a6
2024-05-03 23:57:30
@ 81870f53:29bef6a6
2024-05-03 23:57:30内部電子メール漏洩$Microsoft (MSFT.US)$ OpenAI の「本来の意図」に投資。
メディアの報道によると、米国司法省は現地時間火曜日、Googleに対する独占禁止法訴訟を進める過程で2019年6月に送信された「OpenAIに関する考え」と呼ばれるMicrosoft社内メールを公開した。
この電子メールは、Microsoft の最高技術責任者である Kevin Scott によって Microsoft CEO の Satya Nadella と共同創設者の Bill Gates に送信されました。この電子メールの送信からわずか 1 か月後、Microsoft は OpenAI との技術商用化の「優先パートナー」になったと正式に発表しました。そして後者には10億米ドルを投資しました。
報道によると、スコット氏は電子メールに次のように書いている。
「機械学習の規模という点では、当社は競合他社に何年も遅れをとっています。」
Scott 氏は電子メールの中で、Microsoft のエンジニアが Google の BERT 言語モデルをコピーしてトレーニングするのに 6 か月を費やした方法についても詳しく説明し、最後に次のように述べました。
スコット氏は当初、OpenAIとGoogle DeepMindのAIへの取り組みに懐疑的だったと語った。なぜなら、これらの企業はどちらが「最も印象的なゲームプレイスタントを達成できるか」を競っていたからである。分析では、Google DeepMindのAlphago Zeroデモが指摘されている。
しかし、自然言語処理モデルに関しては、Scott は次のように書いています。
「モデル トレーニングにおける Google と私たちの間の能力差をさらに深く掘り下げて理解しようとすると、非常に不安になりました。」
スコット氏は、Googleの初期のAIモデルの一部がBingに対する競争力を高めるのに役立ったと述べ、さらに2019年のGmailにおけるGoogleのオートコンプリート機能は「非常に優れたものになった」と称賛した。
ナデラ氏はスコット氏のOpenAIに関するアイデアに反応し、それをマイクロソフトCFOのエイミー・フッド氏に転送し、「だからこそ私はそれをやりたいのです」と述べた。
また、メディア報道によると、ビル・ゲイツ氏は2020年にマイクロソフトの取締役を辞任したが、2016年以来、マイクロソフトとOpenAIの継続的な関係において依然として重要な役割を果たしており、ゲイツ氏は定期的にOpenAIと会合を持ち、この取引の促進に貢献したという。 。
現時点で、Microsoft は OpenAI に 130 億ドル以上を投資し、そのモデルを Office アプリ、Bing 検索エンジン、Edge、さらには Windows オペレーティング システムに追加しています。OpenAI への投資とサポートのおかげで、Microsoft は現在、トップクラスの企業とみなされています。 AI競争のリーダー。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ https://getalby.com/p/bitcap
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ c73818cc:ccd5c890
2024-05-05 19:40:53
@ c73818cc:ccd5c890
2024-05-05 19:40:53
🚀 Preparate le vostre domande più scottanti su criptovalute, trading e Bitget perché i nostri esperti sono pronti a rispondere a tutto!
🚀 E come se non bastasse, ci saranno premi 💰 incredibili per i partecipanti!
🚨 Quindi alle ore 21:00 di lunedì 06/05 Bitget risponderà a tutte le vostre domande su Launchpad, Launchpool, PooX e BGB! ⏱️
🚨 E per chi è nuovo su Bitget?
🚨 Iscriviti tramite il nostro referral 6w5d e ottieni: 💰 Bonus di benvenuto 💰 Sconto a vita sulle fee 💰 Accesso esclusivo al nostro programma "University" per imparare le basi del mondo cripto!
💰 Non perdere questa occasione unica per immergerti nel mondo delle criptovalute con i migliori!
🚨 Unisciti al nostro canale Telegram e preparati per l'AMA!
🚀 https://t.me/Bitcoin_Report_Italia
Bitget #AMA #Criptovalute #Bitcoin #BTC #Altcoin #Referral #Trading #Premi #University #Telegram
-
 @ fa984bd7:58018f52
2024-04-23 22:27:52
@ fa984bd7:58018f52
2024-04-23 22:27:52I like climbing, coding and bitcoin. (in that order)
-
 @ dd664d5e:5633d319
2024-04-23 06:04:28
@ dd664d5e:5633d319
2024-04-23 06:04:28Why GitCitadel is primarily self-funded
This week has been full of discussion about the various pros and cons of what I've previously described as the "patronage funding model", including a formalized version called "grants":
This is the current common business model. A creator (artist, developer, writer, etc.) receives grants or donations that are more or less attached to conditions. -- The Zap Economy
We at GitCitadel have been questioned repeatedly, as to why we have not applied for a grant, when we are putting so much time and effort into the Nostr ecosystem. I would, therefore, like to explain the logic we have used to make this decision:
We are a package deal
We aren't merely a product team, we're a project team. That means that we aren't building a product, we're building an entire line (or suite) of products, and the corporate and technical infrastructure to support them.
Those products will be marketed under our own brand, built upon our own tech stack, and managed by our own team. We're used to doing this sort of thing for our various employers, so we haven't seen much benefit in looking outside of our team to acquire such things. Applying for formal grants would undermine this strategy, as we would be expected to tie into the grant-giver's own brand, stack, and team.
We have external income sources
We have made the point, to anyone interested in joining, that our project cannot and will not provide a source of income large enough to replace anyone's current source. At least, not yet. We are receiving donations and will eventually have a pricing model, but this project is our labor of love, not a get-rich-quick scheme. More a go-broke-slowly scheme, if anything.
We see this as a feature, rather than a bug, as it means our personal financial well-being is not immediately tied to our project work, and is therefore more secure, stable, and independent. This allows us the ability to ruminate, take time discussing architecture, and make more grandiose plans. It also allows us to discuss funding models, amongst ourselves or with a wider audience, while remaining calm.
Not everyone is in the same financial position and not everyone wants to split their attention, in such a manner, and we respect that. We also respect the right of every project member to decide differently, for themselves, and to apply for grants in their own name.
We're enjoying "L'expérience FOSS"
This is our first, major, open-source, software project. This is our chance to do something different, to be edgy, to build something for ourselves, to try out new technologies and strategies, to found a company and design a brand, to tinker and scheme... To boldly go where no team has gone before!
But, seriously. We're having fun. We're friends. We're enjoying the ride. We wouldn't enjoy the ride as much, if we were driving someone else's car.
We want to prove that it can be done
One of the things we found disturbing about the Nostr ecosystem is the pervasive pressure individual developers are under to apply for grants and labor full-time on Nostr products. It can feel quite rebellious, to simply tinker on evenings, weekends, or holidays.
It isn't rebellious.
It is a perfectly normal and acceptable way to contribute to a growing technological ecosystem, and we want to help re-normalize it. The emotional pressure to deliver new features at a rapid pace is exciting, but onerous, can lead to developers burning out and eventually moving on, and is the main cause of the frequent low quality of the existing software and the plethora of abandoned repos. This is the landscape that grants sometimes build.
We are here to show that "steady, stable, secure, supported, sturdy" sounds dull and a bit slow, but it can also be a winning development style, if the team chooses it deliberately and plans accordingly and cultivates a team environment that makes "code and chill together" a long-term motivator. We think the Nostr ecosystem is ready to accept a team with this style, and it's a style that advanced grants simply aren't designed to support because grant-givers have to account for the money spent within a reasonable time.
We want to support independent funding models
As with all things, talk is cheap. We are all persons eager to establish independent funding models because we want Nostr to help create a free market of sovereign individuals, at the global scale. We think this is a particular "good work" that Nostr is in a prime position to define, but it won't happen, if nobody actually does it, or if only a few do it and and are perceived as greedy oddballs. There needs be a lot of people doing it, including large, influential teams.
The strongest motivation to develop such models is the profit motive, and that is inevitably weakened by grant-lethargy. One has to take risks to become a change agent, so we have put ourselves on a diet, to get our creative financial juices flowing.
We have decided to stay hungry. https://image.nostr.build/28ddca2ef029e8be27e351867f37e457e2070e005f5588f88f486208709ee00d.jpg
-
 @ 1931b5e4:168a0489
2024-05-05 06:20:41
@ 1931b5e4:168a0489
2024-05-05 06:20:41How I arrived...
I have always been a lover of social media. However over the years rather than enjoy my time on the generic platforms that we have all heard of I started to despise being there, although would still spend my time scrolling to try and find something interesting to read and interact with. You see, I love conversation! I love interaction! I do not love however, what has happened over recent years, which is that any opinion you have will be beaten down. Anyway, I was doom scrolling , attempting to find someone interesting to at least listen to and I came across a woman who mentioned Nostr. This sparked my interest and I soon set myself up and started to post and scroll with the outlook that things would be different. Not so much though(maybe a just haven't found the right client?)... I had a few comments but no luck in conversation. Until... I had a comment saying that I should head over to Stacker News!
I headed over...
- Day One I posted my bio and I got such a warm welcome!
- Day Two (i think) I found the saloon! A thread which I absolutely LOVE. In there I can be completely myself and people will respond!
- Day Three I received a cowboy hat, not having a clue what it was I posted about it and got (maybe a little too much) excited!
- Day 7 or 8 I lost my cowboy hat and realised that I needed to learn more about how to be here!
Since then...
- I am addicted to being here!
- I am addicted to learning more and more about how to interact!
- I enjoy the conversation - although I am still looking to grow my tribe. I am a talker and a listener - I give well thought out answers when I feel they are warranted and I like the same in return.
Things I have learnt...
- People are (on the whole) friendly on here and will interact if you are too
- This is a platform for interesting, well thought out content
- DO NOT use AI to create content! Write from the heart and the mind, because if you do use AI your content will not get very far as people here can sniff it out by the second line and will not be impressed!
- Zap content you are interested in and that you genuinely enjoy
- Be your authentic self - it will serve you well, unlike other platforms
- Don't worry if your posts don't create much traction - just keep building the relationships and the trust in the community you have joined
- Don't just come here for the sats - they are a bonus and they will come, but not if you haven't earned them by having something interesting to say
- The leader board is cool!
Those who I have interacted with probably know I don't know a lot about bitcoin - I want to learn more and I will do this steadily over time and will not be afraid to ask questions and ask where to find the best research.
So, thank you for the last 23 days! It has been a truly great experience and I hope it continues for a long while to come :)
-
 @ 91c4282f:d6a9b8e8
2024-05-05 02:04:21
@ 91c4282f:d6a9b8e8
2024-05-05 02:04:21- It is almost April!
- How about this external image ?

- Do something to your hair.
- Have you ever eaten a spoon full of peanut butter ?
- Have you ever eaten a spoon full of ketchup ?
- Do you like spiders ?
- How about this external image ?

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Webvatar
Like Gravatar, but using profile images from websites tagged with "microformats-2" tags, like people from the indiewebcamp movement liked. It falled back to favicon, gravatar and procedural avatar generators.
No one really used this, despite people saying they liked it. Since I was desperate to getting some of my programs appreciated by someone I even bought a domain. It was sad, but an enriching experience.
See also
-
 @ aa333681:f8b3be8c
2024-05-05 18:14:22
@ aa333681:f8b3be8c
2024-05-05 18:14:22เมื่อวันก่อนวันที่ 4 May 2024 แฟนๆ สตาร์วอร์สทั่วโลกยกให้เป็น Star Wars Day: May the 4th Be With You เลยขอเขียนถึงเรื่อง Star Wars สักหน่อย
ผมเองเพิ่งมีโอกาสได้ดู Star Wars: The Bad Batch - Season 3 ซึ่งเป็นซีซั่นล่าสุด และซีซั่นสุดท้ายของ Series: The Bad Batch
ส่วนตัวแล้วชื่นชอบเส้นเรื่องนี้มากเป็นพิเศษ ... สูสีกับ The Mandalorian เลย
เนื้อเรื่องเป็นเรื่องราวของ The Clone Force 99
ที่ต้องบอกเลยว่า ขอให้ลืมไอ้พวก Stormtrooper โง่ๆ ที่พวกเราเคยดูกันใน Star Wars เส้นเรื่องหลักไปได้เลย ... แม่งพวกเยอะกว่า อยู่กันเป็น 10 แต่ยิงปืนไม่เคยแม่น ไม่เคยโดนสักนัด ทำอะไรเงอะๆงะๆ เหมือนออกมาให้โดนฆ่าแค่นั้นอ่ะ 555
แต่กลุ่ม The Clone Force 99 นี่แม่งแบบ คือ โหดสัส รัสเซีย บัลแกเรีย โรมาเนีย ... ว่าไปนั่น - Hunter เป็นหัวหน้ากลุ่ม ที่กลุ่มที่เชี่ยวชาญ ด้านการแกะรอย Tracking และสามารถสัมผัส Electromagnetic Wave ได้ - Wrecker เป็นตัว Tank ของทีม พละกำลัง เหนือ Clone ทั่วไป - Tech เป็นทหาร Clone สาย Support ที่เชี่ยวชาญด้าน Tech และการเจาะระบบ - Crosshair เป็น Sniper ตัวเทพ แบบคนละชั้นกับพวก Stormtrooper ที่เราเคยๆ ได้ดู - Echo เป็นทหาร Clone ปกติ แต่มาเข้าร่วมกับกลุ่ม The Clone Force 99 ภายหลัง - *Omega* เป็น Clone เด็กผู้หญิงที่มาร่วมทีมภายหลังเช่นกัน ความสามารถพิเศษไม่ปรากฎ (แต่มีความสำคัญต่อทีมยังไง อยากให้ไปดูกันเอาเอง) และเป็นแกนหลักของการดำเนินเรื่องในเส้นเรื่องของ Star Wars Universe ในส่วนนี้เลย
ชอบที่ ... - ทั้ง 3 ภาค จะไม่เน้นพวก Jedi & Sith เลย ... ฉากที่มีการรำดาบ Light Saber สู้กันนี่แทบจะนับได้เลยอ่ะ ... - เป็นเรื่องราวของพวก Clone ล้วนๆ ... แต่สนุกจริงๆ ถึงบอกว่าให้ลืมภาพจำ Stormtrooper โง่ๆ ไปได้เลย 555 - เป็นเรื่องราวของ Teamwork ที่แต่ละคนเด่นกันคนละด้าน แต่ Synergize กันได้แบบสุดๆ อ่ะ - มีเรื่องการผิดใจกัน การหักหลัง ความซื่อสัตย์ แต่สุดท้ายความเชื่อใจกันของคนในทีม ก็ช่วยให้ฝ่าฝันอุปสรรคต่างๆ มาได้
ใครที่ชื่นชอบ Star Wars อยู่ แล้วยังไม่เคยดู The Bad Batch อันนี้แนะนำเลย แม้จะเป็นแค่ Animation แต่ลองดูเถอะไม่ผิดหวัง
เอาจริงๆ ก็ต้องยอมรับนะว่า ผมตก Rabbit Hole ของ Star Wars Universe เหมือนๆ กับที่ตก Rabbit Hole ของ Bitcoin อ่ะ ... ตอนแรกก็ดูแค่เส้นเรื่องหลักหนังภาค 1-9 แล้วก็มาดู Animations + หนังภาคแยก ต่อเกือบทั้งหมด - The Clone Wars - The Bad Batch - Solo - Obi-Wan Kenobi - Rebels - Rogue One - The Mandalorian - The Book of Boba Fett - Tales of the Jedi - Star Wars Visions - Ahsoka
แต่ก็ยังเหลือบางเรื่องที่ต้องไปตามเก็บต่อ... - Andor - ล่าสุดเพิ่งเห็นใน Disney+ ว่า Star Wars: Tales of the Empire ก็เพิ่ง Launch มา - และเพิ่งเห็น Trailer ว่าเด้วกลางปี 2024 นี้ จะมี Acolyte ออกมาอีก
MayTheForceBeWithYou #MayThe4thBeWithYou
StarWars #TheBadBatch
Siamstr










-
 @ 1c9dcd8f:1852f704
2024-04-23 07:56:47
@ 1c9dcd8f:1852f704
2024-04-23 07:56:47The most striking finding overall was the dominance of influencer-centred content, which accounted for the vast majority of videos in the dataset. Significantly, most of this material originated from regular users or micro- influencers reposting clips of influencers, rather than from the influencers’ own accounts. This demonstrates the extent of both user-led and algorithmic amplification of influencer content, and was especially evident in the case of Andrew Tate, who was by far the most recommended influencer on both platforms, despite the fact that his accounts were inactive at the time of data collection. The dominance of these ‘ideological entrepreneurs’ (Jurg et al., 2023) marks a significant new shift in the manosphere, whereby male-supremacist influencers are not only accumulating considerable wealth but are also using the practices of influencer culture for metapolitical goals, a phenomenon noted by Maly (2020) in the context of the Far Right in recent years. By adopting less overtly gender- political rhetoric, and instead mobilising discourses around mental health, motivation and money-making, these influencers are strategically monetising men’s financial and emotional insecurities (Bujalka et al., 2022). This was evident in our dataset in the prevalence of content coded as ‘alpha masculinity’ (12.7% on TikTok and 32.5% on YouTube Shorts) over that coded as ‘anti- feminism / misogyny’ (8.3% on TikTok and 23.9% on YouTube Shorts). ‘Manfluencers’ have thus effectively replaced pick-up artists and the seduction industry with a significantly more lucrative, popular, and ostensibly well- intentioned venture, which purports to give men purpose, confidence and control.
Linked to this new development has been the revival of the notion of stoicism, reappropriated from ancient Greek philosophy, whereby self-help influencers such as Ryan Holiday and Jordan Peterson advocate traditional masculine values of courage, self-discipline, andorder as an antidote to the alleged chaos and narcissism of ‘woke’ modernity. Aleks Hammo (2023) refers to this phenomenon as the ‘stoic industrial complex’ and maintains that its appeal lies in its promise of taking control in an age of hyper-competition, secular disenchantment, and consumerism. However, this military-style neo-stoicism is underpinned by the repression of emotion, a return to strict gender roles and simplistic, individualistic accounts of complex social phenomena. It is also used to discredit the concept of structural or systemic disadvantage, and to reinforce the message that anyone can make it if they work hard enough. Many of the influencers in our dataset actively promote this message, urging men to ‘pull themselves up by the bootstraps’ and to try harder as ‘no one cares about the men who fail’. For example, an account reposting this type of content using the hashtags #motivation #mindset #advice
inspiration features retired US Navy SEAL
David Goggins urging, ‘You need to fking work harder, you need to fking discipline your mind better…all the time you’re complaining, you could be instead hustling’.
In tandem with this focus on neo-stoicism was another, ostensibly incongruous, theme which we termed ‘wealth porn’. This involves influencers bragging about their wealth and possessions, showing off their car collections and, in some cases, purchasing expensive cars and wrist watches on a whim. It also frequently involves disdain for poor people (‘brokies’) who are deluded to believe they can make money ‘inside the matrix’, which refers to mainstream, ‘blue-pilled’ or ‘normie’ society. Videos featuring Andrew Tate and Tristan Tate accounted for most of this content, and they frequently refer to the disciplinarian and frequently cruel parenting style of their father as responsible for their ‘sheer indefatigability and unmatched perspecacity’. Many of the Tate brothers’ motivational clips also double up as advertisements for Andrew Tate’s businesses, in particular the Real World, the War Room, and Hustlers University
-
 @ 8ea48526:e6720a43
2024-04-17 14:06:11
@ 8ea48526:e6720a43
2024-04-17 14:06:11Recently there has been discussion on the socials about supporting open source developers, specifically those who work on Bitcoin and Nostr. There is a small-ish camp of people who think that Bitcoin should remain as is…it’s perfect, don’t mess with a good thing. Many others think – correctly, in my opinion – that Bitcoin needs to be maintained and even enhanced. As long as the changes make Bitcoin better money, we should evaluate, go slow, and keep things simple.
Who will maintain Bitcoin and other open source projects? Will devs do it out of the goodness of their heart? Builders gotta eat; food ain’t free. A handful of institutions, both non-profit and businesses, provide grants and long term support to developers. This is great and I hope that continues. However, there is more that we can do. There is more that you can do.
Zappy 21st
I propose we make the 21st day of every month the (un)official ”Zap a Builder Day”. It’s simple. On day 21 in the current month, find a developer and zap them sats.
Created in the spirit of #v4v and the #grownostr social experiment, I’d love to see people make this part of their monthly routine. It’s common for certain days of the month to have meaning. The 1st day marks the start of a new month. The 5th day is a common day when mortgage payments are due. In the United States, on the 15th day of April taxes are due. So now there is the 21st day, the day you send some value to devs.
Who are you gonna zap?
Any open source developer. Start simple; don't overthink this. If you're using a Nostr client that you love, go find one of the contributors and zap them. If you use Bitcoin or Lightning regularly, find a Bitcoin or Lightning dev. There are many other great freedom tech tools, like wallets, sovereign computing apps, and privacy tools that have developers behind them. Zap a developer. (I say developer, but I really mean "contributor". Remember the designers, product, support, and project people who also contribute.)
I'm intentionally not giving names of developers here because I don't want to favor one over the other. Every open source developer is important to different people based on the tools they use. So go zap the people in your realm.
I'm only publishing this on Nostr, but I'm happy if the idea spreads beyond that. Nostr is the perfect place because you can so easily find a core dev and zap them. No need to track down their website hoping to find a wallet address or request a Lightning invoice.
Join the Zaps
While everyone is excited about block 840000, halvings come and halvings go. But the 21st is always here for you. Every month, reliably, quietly doing its thing. Just like those open source devs you rely on so much. They’re here every month, reliably, quietly doing their thing. Let’s show them some love.
This April 21st find a dev and zap them. If you’d like, add a message telling them how awesome their work is and tag it with #Zappy21st. Let’s flood the feeds with #Zappy21st messages and surface great open source developers to others. Next month on the 21st, we’ll do it again.
🤘
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The problem with DIDs
Decentralized Identifiers are supposedly a standard that will allow anyone (or anything) to have an online identity. The DID is a URI like
did:<method>:<data>in which<method>determines how to interpret the<data>. The data is generally a public key in some cryptographic system or shitcoin blockchain, or a naked key, or a DNS-backed web address.Some of the DID proponents argue that this is for maximum interoperability, since any new system can be supported under the same standard, i.e. supposedly an application could "support DIDs" (as some would say) and that would allow anyone to just paste their DID string there and that would refer to something.
There are a gazillion of different DID "methods", most of them are probably barely used. What does it mean for an application to "support" DIDs, then? For the interoperability argument to make any sense that must mean that the application must understand all the "methods" -- which involves understanding all cryptographic protocols and reading and interpreting data from a gazillion different blockchains and also understanding the specifics of each method, since the data of each blockchain or website and so on must also be interpreted according to the rules of the method.
It must be clear from the paragraph above that the DID goal is is unimplementable and therefore will either fail horribly by lack of adoption; or it will have to be changed to something else (for example everybody will start accepting just
did:keyand ignore others and that will be the standard); or it will become a centralized thing with all supporting applications using a single set of libraries that have built-in support for all methods by calling centralized servers that return the final product of processing the DID data for each method.See also:
-
 @ 486f6a60:06833ed2
2024-05-05 02:02:28
@ 486f6a60:06833ed2
2024-05-05 02:02:28- It is almost April!
- How about this external image ?

- Do something to your hair.
- Have you ever eaten a spoon full of peanut butter ?
- Have you ever eaten a spoon full of ketchup ?
- Do you like spiders ?
- How about this external image ?




