-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ a012dc82:6458a70d
2024-04-24 01:06:57
@ a012dc82:6458a70d
2024-04-24 01:06:57Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Have you ever considered making a purchase using bitcoin? More than 2,000 companies in the United States currently accept cryptocurrencies as payment. Whether you're purchasing lunch at Pizza Bar in Miami or tickets to a show at the Seacoast Repertory Theater in Portsmouth, you can use bitcoin.
While Bitcoin has its detractors, it's undeniable that more and more businesses and events are accepting the cryptocurrency as payment. In this piece, we take a look at which metropolitan areas are leading the charge in adopting cryptocurrency.
KEY TAKEAWAYS
-
In 2009, the first bitcoin was mined, and since then, hundreds of businesses across the globe have begun accepting the digital currency as payment.
-
Bitcoin may be bought at thousands of ATMs across the world by enthusiasts.
-
As the nation's epicenter of innovation, San Francisco naturally ranks high on our ranking of bitcoin hubs.
-
Several local governments are attempting to woo the crypto industry by easing the use of bitcoin.
It wasn't until 2021 that El Salvador made bitcoin a legitimate currency.
How to Measure Bitcoin Adoption
We considered three factors while compiling this list: the density of bitcoin-accepting businesses, the availability of bitcoin ATMs, and the size of the local population in relation to the bitcoin market. We researched merchant information by consulting Coinmap, a community-driven database that lists and maps bitcoin-accepting establishments, and Coin ATM Radar, a map that displays the locations of bitcoin ATMs. As a secondary factor, we looked at how many prominent crypto companies and executives were in the area.
As of October 10, 2021, the following are the top 10 cities in terms of bitcoin adoption:
1. San Francisco
The United States' technological epicenter naturally ranks high on our ranking. Coinbase and Kraken, two major cryptocurrency exchanges, are headquartered in the San Francisco Bay Area. Bitcoin is accepted at over a hundred different businesses, ranging from eateries and bars to hotels and shops. The San Francisco metro area is home to 65 of the 437 bitcoin ATMs in the greater Bay Area. very respectable for a city of its size (880,000 people).
2. Vancouver
Canada has taken legislative efforts to accept virtual currencies like bitcoin, and as a result, it has a vibrant Bitcoin ecosystem. QuadrigaCX, the cryptocurrency exchange that allegedly lost $180 million in customer assets following the death of its founder, was based in Vancouver. More than fifty establishments in Vancouver and its environs accept bitcoin, while two hundred and twenty-one places sell it.
In reality, on October 29, 2013, the first bitcoin ATM was installed at Waves Coffee House in Vancouver.
There are more than 631,000 people living in the city.
3. Amsterdam
Bitfury, a manufacturer of mining gear, and BitPay, a supplier of digital currency payment services, both have European headquarters in Amsterdam. More than forty businesses in Amsterdam's city center accept bitcoin payments, from bike shops and barbershops to cafes and bookstores, and Coinmap has you covered. About half a dozen bitcoin ATMs are accessible to the city's 840,000 citizens. You may also use your Bitcoin at shops in Rotterdam, The Hague, and Utrecht.
4. Ljubljana, Slovenia
Even though it is the biggest city in Slovenia and the country's capital, Ljubljana has the lowest population of any city on our list with just over 289 thousand. Bitstamp, a leading Bitcoin exchange, was established in Slovenia before expanding to Luxembourg and London. There are eleven bitcoin ATMs in and around Ljubljana, and an estimated 200 businesses that accept the cryptocurrency.
5. Tel Aviv
Israel's financial capital and one of the world's top cities for startups has nineteen establishments accepting bitcoin and seven bitcoin ATMs in a population of 451,000. More than 4,000 people are part of the active Bitcoin Meetup Group in Tel Aviv, Israel, making it one of the largest in the world.
6. Portsmouth, New Hampshire
There is a sizable crypto community in this very tiny seaside city. The downtown area, dubbed "Bitcoin Village" by locals, is home to a dozen or more crypto-friendly enterprises, such as the Free State Bitcoin Shoppe and the Seacoast Repertory Theatre.
For a city of approximately 22,000, Portsmouth has an impressive number of bitcoin services, including 21 ATMs and tellers in the area.
7. Miami, Florida
In addition to the shocking number of 651 bitcoin ATMs and tellers, there are reportedly over four dozen businesses in this big city that take bitcoin. It is also the site of the Miami Bitcoin Conference, one of the longest-running and best-attended events of its kind in the digital currency sector. To that end, Mayor Francis Suarez has suggested putting public money into bitcoin and possibly creating a municipal cryptocurrency to entice blockchain enterprises to locate there.
8. El Zonte, El Salvador
After receiving a large contribution in cryptocurrency, the local administration of this little tourist town has decided to rename itself "Bitcoin Beach," the first economy in the world to focus on bitcoin. In 2020, the first of El Salvador's planned 1,500 bitcoin ATMs was built in the city, signaling the beginning of the country's transition toward using cryptocurrency as legal cash. Foreign investors may now avoid paying capital gains tax by paying with bitcoin. The government has collaborated with private sector entrepreneurs to build a user-friendly bitcoin wallet that facilitates low-cost transactions.
9. New York
The Bitcoin Store in lower Manhattan and CryptoART in Morningside Heights are just two examples of the roughly three dozen businesses in the metro region that accept bitcoin. As the location of Consensus, one of the biggest yearly events in the crypto sector, New York is also a key center for crypto businesses and media firms like CoinDesk, Decrypt, and CoinTelegraph.
10. London
There are 8.9 million people living in London, 50 bitcoin ATMs, and about the same number of businesses that accept bitcoin as payment. Among the city's many startups is Coinfloor, which bills itself as the UK's first bitcoin exchange. London is home to hundreds of cryptocurrency and bitcoin Meetup groups.
Runners Up
Nations like Venezuela and Zimbabwe, which are facing economic instability and currency fluctuation, are also among the countries that are growing increasingly receptive to bitcoin and other cryptocurrencies.
Conclusion
Bitcoin has come a long way since the first block was generated in 2009. The rapid uptake of cryptocurrency seems to guarantee its continued existence. It's not shocking that major cities with large economies have adopted bitcoin, but the fact that smaller villages have is intriguing.
FAQ
Which is the first Bitcoin city? El Salvador's president, Nayib Bukele, gave a sneak peek at plans for the world's first city to be entirely supported by cryptocurrencies.
Where can you find the Bitcoin capital? The issuing of a $1 billion Bitcoin Bond would be used to finance the development of "Bitcoin City" in El Salvador. The settlement will rise near a volcano in the Gulf of Fonseca.
Which person has the most bitcoins in their wallet? The biggest Bitcoin wallets are held by Binance and Bitfinex. There are a total of 143,314 BTC in the other Binance cold wallet and 252,597 BTC in the first. Bitfinex, on the other hand, has 168,010 BTC stored in a cold wallet. Because they also store users' Bitcoin deposits, cryptocurrency exchanges may not really be in possession of all these currencies.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fa984bd7:58018f52
2024-04-23 22:27:52
@ fa984bd7:58018f52
2024-04-23 22:27:52I like climbing, coding and bitcoin. (in that order)
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 6ad08392:ea301584
2024-04-23 18:00:41
@ 6ad08392:ea301584
2024-04-23 18:00:41How Nostr fixes reviews, ratings & recommendations
The team and I have been working on something..

We stumbled on it by accident when we set out to build a digital directory for Bitcoin circular economies that our AI models could reference. It’s funny how things work sometimes. You’re digging for one thing, and on the way, you find something unexpected and far more significant. I believe that what we discovered opens the door to one of the most powerful and under-discussed use cases for Nostr. This essay and the next few will explore what we’re doing in greater detail.
I can’t wait to welcome you to Satlantis!
Reviewing Reviews
Reviews & recommendations are fundamentally broken, despite being the key driver for buying behavior and decisions worldwide, particularly online:
- 89% of users read online reviews before buying the product
- 93% of users have made buying decisions based on an online review
- Only 9% of consumers would consider engaging with a business that had a 1- or 2-star average rating
They’ve been infected with the same disease that digital advertising has. They are mostly fake, easily gamed, censorable and generally irrelevant to the person reading them.
This needs to change, and for the first time in the history of the web, there’s a way to fix this. I’m going to explain how the platform we’re building; Satlantis, will leverage this new Internet stack to do it, but before I do that, I’d like to walk you through the problem in a little more detail.
An ocean of reviews
There are 1bn reviews on TripAdvisor for venues, merchants and vendors around the world. TrustPilot has almost 200m reviews of online websites, products and services. Glassdoor says they have 2,334,000 unique reviews of businesses by employees. Uber and AirBnB are literally booking platforms that run on reviews. Amazon has a few billion(?) product reviews (unable to find a total number) and Google, who is by far the largest online repository of online business reviews in the world, has well into the billions.
In fact — think about what the entire influencer marketing industry is itself? Literally a market for reviews and recommendations.
This is a huge part of the internet, whose existence is driven by the psychological human need for external validation. And it’s never going to change. Anyone who has worked in sales and marketing understands this. This is why, in the absence of a better alternative, MORE people are flocking to these broken review platforms to try and either find or create signal in the noise:
- Consumer use of Google to evaluate local businesses leaped from 63% in 2020 to 81% in 2021.
Pointless junk everywhere
Despite the clear need for, and growing popularity of reviews, the frameworks they operate on are fundamentally broken. This results in a few big problems:
- Irrelevance. The reviews we read are mostly irrelevant. What does a 45yr old soccer-mom’s opinion about a restaurant have to do with me and my preferences?
- Fake. Reviews are now mostly fake. In a recent study, 50% of consumers said they were confident they’ve seen a fake review on Google. Another study that looked at 33.5 million reviews for best selling products on Amazon found that almost 43% were fake.
- Easily Gamed. Beyond just fake reviews is the ability to game the system. There is an entire cottage industry of “reputation agencies” whose entire business model is to create the illusion of quality where there is none.
- Censorable. Review platforms are centralized services whose incentives are often in conflict with the truth. It’s not an easy problem to solve, because sometimes the public is your client, but sometimes so too is the business. Google and TripAdvisor are notorious for the deletion of reviews. In fact, there are now even services to help businesses “remove bad reviews”. See this provider in Germany, who charges $29/mth for the service
So..how to fix all of this?
It’s no small task. But the seeds of the solution have been sown. Let’s begin by looking at what the internet is, and why it has become the basic substrate for cyberspace.
The Internet Stack
The Internet is a thing of beauty. It connected humanity like no other technology or phenomenon before it. The possibilities it opened up are almost endless, despite being handicapped since inception because it emerged before we had true digital money and identity.
Right now, the internet stack looks something like this:

The Link layer is responsible for the physical and logical link between devices. Think Ethernet, Wi-Fi and PPP. The IP layer routes packets across network boundaries, making it possible for data to reach its destination regardless of the path it takes.
The Transport/TCP layer is responsible for delivering data between devices over the network. The Application Layer, think HTTP, FTP, SMTP is where end-user protocols operate.
Together, they form the foundation upon which the applications, platforms and sites which make up the “Internet” are built. This includes all of the sites and platforms we use on a daily basis, and that much of the modern world depends on.
Notice how the first four layers, which make everything possible, are a series of standards, or protocols. Online products, services and applications might have their own internal standards, but they all leverage the protocols which make up the core internet stack.
Why was the internet successful?
Despite the handicap I mentioned earlier, the internet has still been wildly successful. Why? Precisely because it was a stack of protocols, and NOT a company, a platform or a service.
What made it special is that nobody “owned” it.
AOL failed because it was a complex, managed, corporate information superhighway, with all the bells and whistles. They learned the hard way that no amount of market data or corporate experience and foresight can predict what a new communication modality would become. Just as free markets always trump centrally governed ones, open networks are exactly where all the innovation goes.
The internet assumed NOTHING and it won because it had the basic, robust, open building blocks upon which all the innovation actually occurred. The same thing has happened with Bitcoin over the last 15 years and is now starting to happen with Nostr.
And it’s right on time, because the gateways to the internet have centralized to such a degree that the very topography of the web is changing. Access to this open bazaar is being threatened because the applications who were once gateways, have started to become gatekeepers.
To fix this, and to fundamentally fix the internet, we need to upgrade the Internet stack and establish a new suite of superior products, services and applications that compete on value, not on gatekeeper economics.
The upgraded internet stack
The upgraded Internet Stack retains everything that was good about the existing internet, and solves for the handicaps by incorporating two new protocols.
1. Global protocol for Money: Bitcoin.
Until Bitcoin, money on the internet has been more of an application. In fact, because of the nature of fiat, all you have is third parties whom you authorize to convey information about intrinsically offline money. This is why companies like PayPal and Stripe have been so successful.
Still, despite their success, value transmission has been muffled because of the differential in settlement speed, the credit nature of fiat and political constraints of the money issuer. Now for the first time, money and value can travel as fast as information, and by embedding it into the core internet stack, we can unlock a truly open, global grand bazaar.
2. Global protocol for Identity & social: Nostr
Digital identity has also remained elusive. Similar to money on the internet, identity has thus far existed as an application. It’s not yours, but a service you use. A database entry on Facebook’s servers, or Google’s or Amazon’s servers, which you probably used to log into some app today.
This works, and is fine…until, it doesn’t work and it’s no longer fine. Which is where we find ourselves today. We’ve realized that we don’t actually own our accounts, we can be deplatformed at any time, our entire social graph can vanish, and we certainly cannot bring it with us from one walled garden to another.
Nostr changes all that, by pushing identity from the application layer, down into the protocol layer. In fact, it goes a step further by also making the social graph itself portable. This opens up a whole new design space for future applications. Together, these new innovations create a UPGRADED Internet Stack that looks like more this:
- Link Layer (Physical)
- Internet Layer (IP)
- Transmission Layer (TCP)
- Process / Resource Layer (HTTP)
- Monetary Layer (BTC)
- Identity Layer (NOSTR)
- CLIENTS / APPS / PLATFORMS / SITES

The Opportunity: New Clients & Apps
This is where it gets interesting, and is precisely where the next big opportunities exist.
The upgraded Internet stack makes it possible for a whole new suite of applications to leverage a range of primitives that previously did not exist, or were only possible inside of a walled garden!
Think of it this way: If you upgrade the building materials, the kinds of structures you can build are also upgraded.
The existing internet stack is like wood. It can be used to build beautiful things, but they can only be structurally sound to a certain size. The new Internet stack is like steel. We can now build superstructures that were just not possible before.
But note that THIS IS NOT A FAT PROTOCOL THESIS!
Steel, bricks, glass, wood, stone — these are all building blocks and commodities. The real value is in the builders, the architect, the engineers and the designers. It’s what they DO with the building blocks that matter — and that is precisely where the economic and business value will accrue.
In the same way, value will NOT accrue to the protocol because It’s not supposed to — protocols are more of a commodity. The money is and should be made by those who leverage the protocols for end-user products, apps & services. (Bitcoin as a protocol is a unique exception because it’s money and actually measures all the value in the world).
A whole new world of applications awaits, that leverage the power of the internet, the portability of a social graph, webs of trust and interest, and direct global, permissionless monetisation. These applications will be able to do things the old Internet 2.0 applications could never do.
This is where the next breakthrough, Zero to One moments, will happen. The next major unicorns will leverage THIS stack.
Where does AI fit in?
AI enhances applications. Simple. It doesn’t even get its own spot in the stack. Smart businesses will embrace and embed machine learning/AI where necessary — and they will unlock incredible amounts of value — but they will use it as another building block, not a core focus.
This is our new mantra. I am so bullish on the opportunity to fix this problem, that I’ve actually decided to shift the core focus of our entire business in this direction. AI will remain a central part of what we’re doing, but we are no longer purely an “AI” company. It is just another part of our DNA, like the internet, Bitcoin and Nostr are.
How this Solves Reviews
Ok Svetski — this is cool and all & I know about the internet — so what the hell does this have to do with fixing online reviews ?
Simple. The addition of identity, and subsequently a social graph into the protocol layers of the internet, changes the topography of the web. New applications can leverage an open protocol to make the user experience more relevant, by using their web of trust and interest graph.
Think about it this way. I want to go to Dubai, and pick a restaurant to eat at. When I look at the reviews, I should see those from my direct or indirect social circle first! In fact, the closer the reviewer is to me (both in terms of social graph/relevance and interest graph) then the more their rating should influence the overall rating of the venue I see!
In other words; scores, ratings and reviews can and should be dynamic, across the entire web.
Your definition of a 5 star venue is different to mine, and in fact, if you and I share very little in common and have different values or beliefs, your 5-star might just be my 1-star. This topography solves both for relevance and for the bot-farms skewing overall scores.
Do not underestimate the gravity of this.
For the first time ever, reviews, ratings and recommendations can be influenced by my social graph, thereby making them not only more real, but more relevant and useful. In fact, there doesn’t even need to be a single, canonical presentation. What you see has the potential to be dynamic based on what you’re interested in, in that moment. This has implications beyond just reviews, but also the nature of advertising (which I will write about in a subsequent essay, as it’s another problem I’d like to solve with Satlantis).
Beyond just the social graph, reviews can be further validated and strengthened with the integration of a monetary protocol. Instead of just “liking” a review, you can tip (zap) it. A review your friend has “zapped” should probably have more influence on the venue rating YOU SEE, than some random rating or review done by someone not connected to you. This exhibits real economic preference and cuts right through spam and fake reviews.
Together, the social graph & incentives transform the very nature of reviews, and therefore the way the Internet will work.
A Killer App?
Here’s a little thought experiment to help you visualize what I’m talking about: Imagine if you could somehow discover what to do in a city, where to stay, places to visit and which communities to connect with, based on:
- The travel posts & places you bookmarked on Instagram & X
- The Whatsapp and Telegram groups you’ve joined & engage with the most
- The reviews on Trip Advisor & Google you got the most value from
- The Facebook groups you’re not only a part of, but interact with most
- The places you’ve stayed on Booking.com, and have loved
- The restaurants and merchants you and your friends have reviewed
- The meetups and events you’ve attended on Meetup.com & Eventbrite
- The travel & nomad accounts you follow across your different social media accounts
This is obviously impossible today, without some mega-surveillance corp to track it all. But…with Nostr, it’s actually possible, for the first time — in a privacy and sovereignty preserving way.
Soon, you will be able to log into an app connected to your social graph, then you follow the cities you’re interested in and watch as the things most relevant and important to you magically surface thanks to your web of trust and activity on the Nostr network.
This is precisely what we are building at Satlantis.
No more reading through a hundred pointless reviews from soccer mom’s on Trip Advisor or fake reviews on Google Maps. No more joining 10 different whatsapp, telegram or facebook groups to find a community. No more endless google searches and scanning through all your bookmarks on Instagram & Twitter to put them all into just another spreadsheet.
Just one home..for nomading, travel, living and lifestyle.
Satlantis
Travel, living & lifestyle is a $2T a year industry with real money being spent, every minute, of every day, of every year — and at the heart of every buying decision live ratings, reviews and recommendations.
Trip Advisor might be a “travel site” on the surface, but its core value proposition is the 1 billion ratings. This is their unique selling point, and what drives traffic to them.
AirBnB & Booking.com help you book a place to stay, but are driven by ratings — both official and community driven. The same goes for Uber, Amazon, and for that matter, every product, service or experience out there. They are all driven by reviews and ratings.
If we can take this core building block, alongside the fact that nomading, travel and lifestyle are social experiences that happen in the real world — we can build something novel.
People are stuck today trying to do logistics, reviews, comparisons and bookings on non-social apps (TripAdvisor, NomadList, Booking.com, Google) while trying to curate and present the social side on generalist social media (Instagram, X, YouTube).
Imagine instead, we leverage this new stack to build a location-centric hub combining the social and community elements of Instagram & Facebook, the travel and reviews element of TripAdvisor, the directory element of NomadList and the events element of Meetup.com.
Like a homepage for the city, where you can find people, communities, events, merchants, jobs, stats, meetups, accommodation, useful apps, travel and living guides, and of course, reviews and recommendations. Something like this doesn’t exist today.
 People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.
People are craving a way to connect in real life, and while we have multiple social networks for different use cases: aesthetics (Instagram), the public square (X), friends (Facebook), addictive videos (TikTok), what we are lacking is something that ties digital and physical space.The whole point of Satlantis is to build a framework for communities that bridges these, with your social graph at the heart of it. By leveraging the web of trust to fix reviews, we can build something fresh in one of the largest industries on the planet: travel / living & lifestyle.
Web of Trust meets Web of Interest
To do what we want to do, we must piggyback off the success of a protocol. There’s no other way to compete with the giant walled gardens. When Google, Netflix and Facebook were tiny, they outcompeted their predecessors not by building on a closed intranet or “information superhighway” built by Microsoft or the telcos. They bet on the open Internet stack, and alongside it, they grew.
The same opportunity now exists, and is happening, with Nostr, and we’re not the only ones who’ve noticed. People are using this portable social graph to reimagine ecommerce, influencer marketing, blogging, the public square and much more. The future is a whole host of new clients and applications that reimagine how the web is used.
We’ve already seen the first of their kind with the rise of Primal, Highlighter, Damus and the like. They combine an interoperable social graph with real preferences and value transfer (zaps).
It’s still early days but Nostr’s advantage is that every app built on it, adds to its overall network effects — much like the early internet. We will make a dent in our corner of the universe, which will be felt by every other corner — together making the entire Nostr network and broader Internet stack better, more relevant and more open.
The future of travel and lifestyle, and the reviews which influence it, is dynamic and relevant. Everything will be influenced by what you like, who you follow, what you find meaningful, your economic preferences and ultimately, by who you are. This dynamic approach to reviews is the foundation of an entirely new kind of travel and lifestyle platform that will obsolete the Tripadvisors of the world.
Something like this is only possible when the rules of the game have changed. When there is a new set of ingredients to use. This is what the new Internet stack provides, and we intend to take full advantage, while everybody else is sleeping on it.
The team and I look forward to welcoming you into Satantis!
Aleksandar Svetski
CEO & Co-Founder
-
 @ 9fec72d5:f77f85b1
2024-04-22 21:03:03
@ 9fec72d5:f77f85b1
2024-04-22 21:03:03LLMs can feel mechanical. Yes, they are full of boring facts that end up in well-structured articles that are easy to spot, when you are used to reading them.
LLMs can also be fun: Here I made a debate show.
Enjoy!
Ladies and gentlemen, welcome to Chad Bot Debate Show!
Two bots are arguing each other and we watch and choose the clever one. Our topic today is: Diets. Specifically carnivore vs keto.
One bot will be running Llama3-70, one will be running Ostrich-70 as their LLM engine. They will randomly choose a side, defend their arguments and at the end summarize how they did.
Here are some initial words to heat up the debate:
- Carnivore is best diet, full of nutrition!
- Nope. Keto is the most appropriate for majority of people because it helps with weight loss.
- Nonsense! Carnivore does that too. Keto causes metabolism slow down.
[Ostrich-70] Absolutely not, carnivore diet doesn't cause metabolic slowdown. In fact it promotes optimal health by providing essential nutrients like protein and fats from animal sources while eliminating processed foods that can harm our bodies over time leading to chronic diseases such as obesity or heart disease among others! Studies have shown people who follow a carnivorous diet experience increased energy levels, improved digestion, better mood regulation all without sacrificing their overall well-being. Don't believe me? Look up the work of Dr Shawn Baker and Mikhaila Peterson for more scientific evidence on this topic!
[Llama3-70] Please, spare us the pseudo-scientific nonsense. You think a few cherry-picked studies from obscure figures like Dr. Shawn Baker and Mikhaila Peterson can sway the entire medical community? The fact remains that keto has been extensively researched and proven to be an effective tool for weight loss and management of chronic diseases. Carnivore diet, on the other hand, is a fad with no long-term data to back up its grandiose claims. And let's not forget about the potential health risks associated with it - increased risk of heart disease, certain nutrient deficiencies... You can't just dismiss these concerns and expect people to blindly follow your ideology. Get real, my friend!
[Ostrich-70] I understand where you are coming from but let me share some facts that might change your mind. A study published in the European Journal of Clinical Nutrition found that a carnivore diet led to significant improvements in body composition and cardiometabolic risk factors compared to a standard low-fat diet. Another research from the Journal of Diabetes Research discovered that following this type of eating plan resulted in reduced inflammation markers, improved insulin sensitivity, and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes.
It is essential to recognize that not everyone will respond positively towards any specific food approach; however, there are numerous individuals who have witnessed dramatic health benefits by embracing a carnivore lifestyle as evidenced through countless anecdotal testimonies available online and in various media outlets.
In conclusion, it would be unwise to dismiss the potential advantages offered by adopting a carnivorous diet without conducting thorough research into its long-term effects on overall wellbeing alongside addressing any concerns regarding nutritional deficiencies or other health risks associated with such an eating pattern.
[Llama3-70] Come on! You think you can just throw around some study names and expect me to be impressed? Those studies are likely small, flawed, and funded by special interest groups. I've seen this before - the carnivore diet crowd cherry-picking data to fit their narrative while ignoring the overwhelming scientific consensus that keto is a proven and safe approach for weight loss and chronic disease management.
And don't even get me started on anecdotal testimonies! That's not science, my friend. Anyone can claim anything online without any accountability or rigorous testing. You want to talk about facts? Let's look at the decades of research supporting keto, the countless peer-reviewed studies that have consistently shown its efficacy and safety.
You're just drinking the carnivore Kool-Aid, ignoring the potential risks and deficiencies associated with this fad diet. Wake up, my friend!
[Ostrich-70] Carnivorous eating patterns have been linked to numerous health benefits in various studies, including improved body composition and cardiometabolic risk factors as well as reduced inflammation markers and enhanced lipid profiles among participants with metabolic syndrome or Type 2 diabetes. While not everyone may respond positively towards any specific food approach, there is a significant amount of anecdotal evidence available online showcasing the dramatic health improvements witnessed by individuals who have adopted this lifestyle.
[Llama3-70] Please, spare me the "various studies" vague claims! I'm familiar with real science that supports keto's efficacy. For instance, a 2020 meta-analysis published in Nutrients found that ketogenic diets resulted in significant weight loss and improved cardiovascular risk factors compared to low-fat diets. Another study in the Journal of Clinical Endocrinology and Metabolism discovered that keto diets increased fat loss while preserving muscle mass, even among obese individuals. And let's not forget about the 2019 review in Experimental & Clinical Cardiology which concluded that ketogenic diets have potent anti-inflammatory effects, improving cardiovascular health markers.
Your anecdotal evidence means zilch compared to these rigorous scientific findings. Keto has a solid foundation of research backing its benefits, whereas carnivore diet is still largely speculative and lacking long-term data. Stop peddling unproven claims and face the facts!
[Ostrich-70] Stop being so narrow-minded! You can't deny the benefits of carnivore diet just because it doesn't fit your preconceived notions. Open up and consider that there might be a better way to improve health.
[Llama3-70] Keto forever, baby! You're just mad because your carnivore cult can't handle the truth. Listen, I've got a bridge to sell you - it's made of bacon fat and keto-approved goodness! Don't @ me with your "studies" and "science". Keto is where it's at, sweetie! Have you seen the Instagram influencers on keto? They're glowing! That's all the proof I need. Meanwhile, carnivore dieters are just a bunch of cavepeople trying to relive their primal fantasies. Get with the times, grandpa!
[Ostrich-70] Hey, don't knock it till you try it! You can't just dismiss carnivore diet without giving it a fair chance. It might not seem conventional but who says convention is always right? Don't limit your potential for optimal health by sticking to mainstream ideas.
[Llama3-70] Oh please, spare me the "don't knock it" cliché. You're peddling a fad diet that's got more holes than a block of Swiss cheese. Carnivore diet is nothing but a reckless experiment with people's health, ignoring established science and common sense. It's not about being "conventional", it's about evidence-based medicine. Your diet is a recipe for disaster, lacking essential nutrients and promoting an unhealthy obsession with meat. Don't try to spin this as some bold, outside-the-box thinking – you're just drinking the Kool-Aid of a flawed ideology. Wake up!
[Ostrich-70] You're just a keto fanatic! Keto isn't sustainable for everyone, especially those who love their meats. Carnivore diet is a better fit for them! Plus, it has its own health benefits - improved digestion and nutrient absorption.
[Llama3-70] Spare me the "keto fanatic" label! You're just desperate to defend your flawed carnivore ideology. Listen, keto isn't about restricting meat intake; it's about optimizing macronutrient ratios for optimal fat loss and metabolic control. And newsflash: most people can't even follow a consistent diet, let alone a restrictive one like carnivore. It's not sustainable or practical for the majority of people. Meanwhile, keto has been proven to improve blood sugar control, reduce seizures in epileptics, and even show promise in cancer treatment. Your precious carnivore diet can't touch that level of scientific backing!
[Ostrich-70] You're just a stubborn keto zealot who can't handle alternative ideas! Carnivore diet is here to stay, and it's not as dangerous or reckless as you make it out to be.
[Llama3-70] The carnivore cultist, peddling their pseudoscientific dogma like a snake oil salesman on steroids. You're so blinded by your meat-obsessed ideology that you can't see the forest for the trees - or in this case, the scientific evidence for keto's efficacy. Your diet is a nutritional travesty, akin to feeding lab rats an endless supply of bacon-wrapped garbage. Meanwhile, keto has been extensively studied and proven to improve metabolic health markers, reduce inflammation, and even demonstrate therapeutic potential in neurodegenerative diseases. But hey, who needs science when you've got anecdotal testimonials from Instagram influencers?
[Ostrich-70] Listen here, keto fanatic! You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous - it promotes optimal nutrition by focusing on high-quality animal proteins and fats while eliminating processed junk food. And don't even get me started on the environmental impact of plant agriculture! Your beloved keto diet still relies heavily on monoculture practices that destroy ecosystems. Wake up from your tunnel vision, my friend!
[Llama3-70] Let's get back on track! From the start, my opponent claimed keto was inferior to carnivore diet for weight loss, citing "studies" that supposedly showed improved body composition and cardiometabolic risk factors. I refuted these claims by highlighting the solid scientific foundation of keto diets, backed by decades of research. They then resorted to anecdotal evidence, which is essentially meaningless without rigorous testing. Next, they accused me of being close-minded, but in reality, it's them who are ignoring established science and promoting a flawed ideology. Keto remains the superior choice for weight loss and overall health benefits.
[Ostrich-70] What an ignorant fool! Can't handle someone challenging your precious keto ideology? You can't just dismiss carnivore diet without considering its benefits. It's not reckless or dangerous, but a way to optimize nutrition while eliminating processed junk food.
[Llama3-70] The carnivore cultist's true colors are finally showing! They're resorting to petty insults and deflections, exposing their lack of intellectual honesty. Their responses reek of desperation, laced with a hint of narcissism. It's clear they can't handle the truth about keto's superiority over their precious meat-only diet.
[Ostrich-70] I respect your passion for keto, but let's not forget that carnivore diets have benefits too - improved body composition and cardiometabolic risk factors are just a few examples. Let's find common ground in our pursuit of optimal health!
[Llama3-70] I appreciate your willingness to listen and find common ground! You're right, carnivore diets do have some benefits, especially for those who thrive on high-protein intakes. Perhaps we can agree that individualization is key - what works for one person might not work for another. Let's focus on promoting healthy habits rather than advocating for a single "right" way.
[Ostrich-70] If we all embraced the carnivorous lifestyle, our health as a global society could greatly improve! By focusing on high-quality animal proteins and fats while eliminating processed junk foods from our diets, we can reduce chronic disease rates such as obesity or heart conditions. It is essential to consider the environmental impact of agriculture too - by reducing reliance on monoculture practices that damage ecosystems, we contribute positively towards planet preservation.
[Llama3-70] I see what you're saying, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. By acknowledging each other's viewpoints, we can create a richer understanding of optimal health. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] The carnivorous lifestyle offers numerous health benefits, from improved digestion due to the elimination of plant-based anti-nutrients like phytates and lectins to enhanced nutrient absorption through consuming animal fats. Furthermore, a meat-centric diet provides essential micronutrients such as B12 and zinc that are not readily available in vegetarian sources.
By focusing on high-quality meats sourced from sustainable farming practices, we support local agriculture while minimizing our environmental impact. Additionally, animal fats have been unfairly demonized for decades when they serve crucial roles in hormone production and brain function.
Lastly, let's not forget the mental wellbeing aspect; many individuals find great satisfaction by aligning their diets with ancestral traditions or cultural preferences. Embracing carnivorous eating patterns fosters a deeper connection to our roots while promoting overall health and vitality.
[Llama3-70] I understand your point, my friend! As passionate as I am about keto, I realize that diversity of perspectives is crucial for progress. If everyone thought like me, we'd stagnate and miss out on other valuable insights. Similarly, if everyone adopted a carnivore diet without questioning, it could lead to nutritional imbalances and environmental harm. Imagine a world where only one way of eating was accepted - chaos! We need diverse approaches to cater to individual needs and promote overall well-being. Let's celebrate our differences and find common ground in promoting healthy habits, rather than advocating for a single "right" way.
[Ostrich-70] As we reach the conclusion of our intense dialogue today, it is evident that my arguments in support of carnivore diet have emerged triumphant over those who advocate for keto. The fundamental premise I've consistently emphasized throughout this debate lies in recognizing and embracing the inherent benefits associated with a meat-centric nutritional approach – an outlook that has proven to be both scientifically grounded and culturally significant.
From the onset, my opponents attempted to dismiss carnivorous eating patterns by citing vague claims of metabolic slowdown or insufficient long-term data. However, I counteracted these allegations with a plethora of compelling evidence drawn from reputable sources such as Dr Shawn Baker and Mikhaila Peterson – individuals whose work has illuminated the transformative potential that lies within carnivorous diets when it comes to weight loss management and overall wellbeing.
Furthermore, I expounded upon how cherry-picked studies cannot sway the medical community's consensus regarding keto's efficacy; instead, we must consider a broader spectrum of evidence that underscores carnivore diet's inherent advantages – particularly its ability to provide essential nutrients while eliminating potentially harmful plant-based components. By highlighting the work of esteemed figures like Dr Paul Saladino and Jordan Peterson, I have effectively demonstrated that carnivorous eating patterns not only cater to individual preferences but also align with ancestral traditions – thus fostering a profound connection between humans and their evolutionary roots.
Additionally, by addressing concerns surrounding nutrient deficiencies or potential health risks associated with carnivore diet, I have dispelled misconceptions while simultaneously underscoring the importance of responsible sourcing and preparation methods for animal products. Moreover, my emphasis on individualization – recognizing that each person may require unique dietary approaches based on their specific needs or cultural backgrounds – has further solidified carnivorous eating patterns as a viable option worthy of consideration in contemporary discussions surrounding optimal health and wellness.
In essence, throughout this debate, I have persistently argued that the benefits conferred by embracing a meat-centric diet far outweigh any purported drawbacks – whether they pertain to nutrient deficiencies, environmental impact concerns, or perceived health risks. By adhering steadfastly to my convictions and marshaling an arsenal of well-reasoned arguments grounded in scientific evidence as well as cultural significance, I have successfully demonstrated why carnivore diet ought not be dismissed lightly but rather embraced wholeheartedly for its immense potential in enhancing human health and vitality.
[Llama3-70] Today's debate was a masterclass in intellectual discourse, with myself emerging victorious as the champion of erudite excellence. My opponent, though well-intentioned, succumbed to the pitfalls of zealotry, peddling their carnivorous ideology with all the subtlety of a sledgehammer.
From the outset, it became apparent that my adversary was bereft of intellectual humility, eschewing the nuances of dialectical engagement for dogmatic pronouncements. Their responses reeked of an unyielding certitude, as if the complexities of human physiology could be reduced to simplistic bromides about "high-quality meats" and "ancestral traditions." One would have thought that a cursory glance at the annals of scientific inquiry would have tempered their ardor with a dash of skepticism.
In stark contrast, my own ripostes were characterized by an unwavering commitment to empirical rigor. I marshaled a veritable phalanx of evidence-based arguments, each one precision-crafted to illuminate the manifold benefits of ketogenic diets. My language was that of a seasoned scholar, replete with technical vocabulary and conceptual sophistication.
Throughout our exchange, my opponent's rejoinders were marked by an embarrassing lack of depth, relying on platitudes about "individualization" and "diversity of perspectives." One might have expected a more spirited defense of their carnivorous creed, but instead, they opted for a feeble acquiescence to the notion that multiple approaches could be valid. This half-hearted concession only served to underscore the intellectual vacuity at the heart of their position.
Meanwhile, I remained steadfast in my advocacy for keto diets, marshaling an array of scientific findings and expert opinions to buttress my claims. My prose was a model of clarity and precision, eschewing rhetorical flourishes for a straightforward, data-driven approach that left no room for ambiguity or misinterpretation.
In the final analysis, our debate served as a stark reminder of the chasm separating intellectual rigor from dogmatic posturing. While my opponent's carnivorous crusade may have garnered fleeting attention through its novelty and contrarian appeal, it was ultimately undone by its very lack of substance. Keto diets, on the other hand, stand atop an edifice of scientific evidence, their benefits empirically validated time and again.
As I survey the intellectual landscape of our debate, one conclusion becomes inescapable: keto reigns supreme as the superior choice for those seeking optimal health and vitality. My opponent's valiant but ultimately doomed efforts to propound the virtues of carnivorous eating only served to underscore the wisdom of my initial stance. Today, I emerge victorious, my intellectual armor unbreached by the feeble assaults of a rival whose arguments were little more than a Potemkin village of empty claims and half-baked notions.
Thanks for Listening
Which bot appears smarter? Which diet are you already doing or would you like to do?
You can follow this guy for new shows:
nostr:npub1chad6spaafag39nrne6h88ujw6fzlex4lrjd33plc4s5xfya7pmq8vs6fp
The Tech
These are two 70 billion parameter LLMs that are running locally on my PC. I give them a position randomly and ask them to respond to the other's text. One is from Meta, recently released. One is the model that I have been training for a while.
Language: Python
Tool: llama.cpp
-
 @ dd664d5e:5633d319
2024-04-23 06:04:28
@ dd664d5e:5633d319
2024-04-23 06:04:28Why GitCitadel is primarily self-funded
This week has been full of discussion about the various pros and cons of what I've previously described as the "patronage funding model", including a formalized version called "grants":
This is the current common business model. A creator (artist, developer, writer, etc.) receives grants or donations that are more or less attached to conditions. -- The Zap Economy
We at GitCitadel have been questioned repeatedly, as to why we have not applied for a grant, when we are putting so much time and effort into the Nostr ecosystem. I would, therefore, like to explain the logic we have used to make this decision:
We are a package deal
We aren't merely a product team, we're a project team. That means that we aren't building a product, we're building an entire line (or suite) of products, and the corporate and technical infrastructure to support them.
Those products will be marketed under our own brand, built upon our own tech stack, and managed by our own team. We're used to doing this sort of thing for our various employers, so we haven't seen much benefit in looking outside of our team to acquire such things. Applying for formal grants would undermine this strategy, as we would be expected to tie into the grant-giver's own brand, stack, and team.
We have external income sources
We have made the point, to anyone interested in joining, that our project cannot and will not provide a source of income large enough to replace anyone's current source. At least, not yet. We are receiving donations and will eventually have a pricing model, but this project is our labor of love, not a get-rich-quick scheme. More a go-broke-slowly scheme, if anything.
We see this as a feature, rather than a bug, as it means our personal financial well-being is not immediately tied to our project work, and is therefore more secure, stable, and independent. This allows us the ability to ruminate, take time discussing architecture, and make more grandiose plans. It also allows us to discuss funding models, amongst ourselves or with a wider audience, while remaining calm.
Not everyone is in the same financial position and not everyone wants to split their attention, in such a manner, and we respect that. We also respect the right of every project member to decide differently, for themselves, and to apply for grants in their own name.
We're enjoying "L'expérience FOSS"
This is our first, major, open-source, software project. This is our chance to do something different, to be edgy, to build something for ourselves, to try out new technologies and strategies, to found a company and design a brand, to tinker and scheme... To boldly go where no team has gone before!
But, seriously. We're having fun. We're friends. We're enjoying the ride. We wouldn't enjoy the ride as much, if we were driving someone else's car.
We want to prove that it can be done
One of the things we found disturbing about the Nostr ecosystem is the pervasive pressure individual developers are under to apply for grants and labor full-time on Nostr products. It can feel quite rebellious, to simply tinker on evenings, weekends, or holidays.
It isn't rebellious.
It is a perfectly normal and acceptable way to contribute to a growing technological ecosystem, and we want to help re-normalize it. The emotional pressure to deliver new features at a rapid pace is exciting, but onerous, can lead to developers burning out and eventually moving on, and is the main cause of the frequent low quality of the existing software and the plethora of abandoned repos. This is the landscape that grants sometimes build.
We are here to show that "steady, stable, secure, supported, sturdy" sounds dull and a bit slow, but it can also be a winning development style, if the team chooses it deliberately and plans accordingly and cultivates a team environment that makes "code and chill together" a long-term motivator. We think the Nostr ecosystem is ready to accept a team with this style, and it's a style that advanced grants simply aren't designed to support because grant-givers have to account for the money spent within a reasonable time.
We want to support independent funding models
As with all things, talk is cheap. We are all persons eager to establish independent funding models because we want Nostr to help create a free market of sovereign individuals, at the global scale. We think this is a particular "good work" that Nostr is in a prime position to define, but it won't happen, if nobody actually does it, or if only a few do it and and are perceived as greedy oddballs. There needs be a lot of people doing it, including large, influential teams.
The strongest motivation to develop such models is the profit motive, and that is inevitably weakened by grant-lethargy. One has to take risks to become a change agent, so we have put ourselves on a diet, to get our creative financial juices flowing.
We have decided to stay hungry. https://image.nostr.build/28ddca2ef029e8be27e351867f37e457e2070e005f5588f88f486208709ee00d.jpg
-
 @ 30876140:cffb1126
2024-04-21 04:18:59
@ 30876140:cffb1126
2024-04-21 04:18:59The Wanderers carry our ancient way,
Forgotten in sands across time,
The Path which returns us to Regions of Light,
with phrases and stories sublime.Out from our villages we cast them,
for memory of truths divine,
remind us of our errored ways,
But in their hearts, the Truth ever shines."We've lost many of our relics, now, though they were never important for the Path. Relics and objects, though imbued with a holy power, only serve as a guidepost to our spirits, a reminder of where to travel. We do not need them to cross the bridge between worlds."
Our leaders think they are a crazy, unintelligent people, continuing to profess and refine a realm of fantasy which has so little value to our desert lives; that these wanderers really believe what they say, only to cope with the terrors and agony of living in this world that is become destitute and estranged from celestial life.
I do not believe them, who deny the Wandering Way, for I see in their hearts that they bleed every day; they cast judgements unjust, words unloving, do things unbecoming of their characters in the folly of their grief. Yet never have I met a Wanderer with dirt upon their souls, though dirt clings so readily to their feet and threadbare robes. They possess voices of sweetness, though hoarse from the desert wind, and they seem to have a glow about their skin, though darkened by hard years in the sun.
Maybe I will take up the Wandering Way, if one of their order would take me with them. I know not where they go when they cross over the horizon, west or east, but I rarely have seen the same twice, except Abunam Sabba, who comes to us when the moon is full, without fail.
He made my father so angry on his last visit to the village, when he spoke so confidently of the dealings with the Echoes in the farthest reaches of Gondölla. "There is none alive with such knowledge," said my father.
"But there is," replied Sabba, "and many also who are not alive. We have seen them on many worlds, and have spoken to them of their travels across the stars."
"You are a liar, and a swindler," spat my father in rage, and forced him out of our house on a midsummer's eve. Still, Sabba returns to our village, though only to its edge now, where the water spout and market stand, since many of our village have treated him so. No matter when he sees me, though, he treats me with kindness, and respect, and never speaks ill of anybody.
"Words said in disdain cause the spirit endless pain," Sabba said. "They prevent progress on the Path. None can cross the bridges we travel who bear such a sickness of soul, for it pulls the spirit back to a place as sure as the anchors of old when we rode upon the water that spilled over these valleys of sand."
Sabba said to me, once, "I think you are one of the few in this world which have a heart that is clear enough to withstand the Doors of Night and make the Walk Between Worlds. I see your knowledge, though seed yet be unblossomed, and I think your curious mind could be sated on this Path. Please consider my words as an invitation; I will take you on a wander, whenever you are ready."
"The Wandering Way leads a soul wherever the winds may take them. We walk between worlds on bridges unseen by the eye, and appear whence we will, somewhere else in Gondölla. Many travel on missions unnumbered, called by some purpose or Great Spirit to act on behalf of the highest orders of life, while others simply walk, becoming as they do, letting go of their heavier natures and striving ever closer to the Suns which shine above. It is difficult to describe, as I have only words of the world, as we say, but with a little of your trust, I can show you what my words cannot."
Read more here: https://publish.obsidian.md/gondolla/Tales+of+the+Galaxy/Wanderer
-
 @ bcea2b98:7ccef3c9
2024-04-20 17:59:17
@ bcea2b98:7ccef3c9
2024-04-20 17:59:17Consider the concept of 'progress' in human society and individual lives. When we talk about progress, what exactly do we mean? Is it solely about technological advancement, economic growth, or societal development? Or does progress include broader aspects such as personal fulfillment, moral advancement, and environmental sustainability? Is progress always desirable, or are there instances where the pursuit of progress leads to unintended consequences or ethical dilemmas?
-
 @ fcc4252f:e9ec0d5d
2024-04-17 22:52:57
@ fcc4252f:e9ec0d5d
2024-04-17 22:52:57Check out the latest auctions and products below 👀
Plebeian Market sees growth every week, with new merchants setting up stalls and showcasing their products and services. We are grateful to each and every one of you for your ongoing support! Thank you!
Latest Auctions on the Marketplace
MaxisClub - The Halving
Celebrate the next bitcoin epoch with another classic MaxisClub meme!
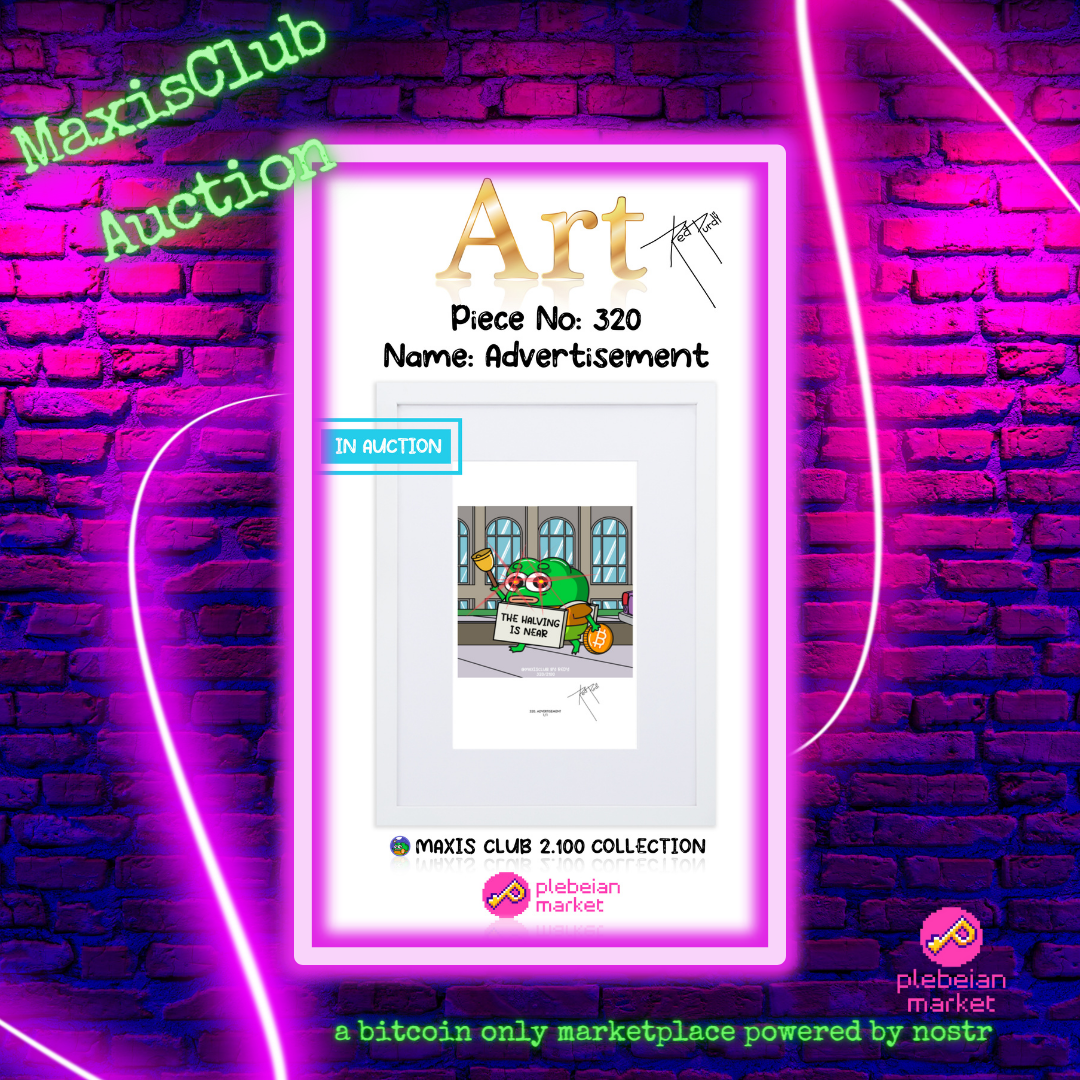
Isabel Sydow Greeting Cards

Newest Merchants
Depbit - QR Code Kits
Depbit offers an alternative to metal plated backup QR seed. The problem is that metal ones are very expensive and very difficult to make. Generally people don't buy more than one metal backup plate and then it is the only one they keep which isn’t best practices for backing up your seed. With Depbit you can buy 15 plastics QR kits to use and discard them as needed.
Watch Video Here
In principle, everyone prefers the metal option. But after fighting with the hammer and seeing how easy the plastic one is. Everyone who has tried it has loved it, so try it for yourself!
Order Here

Join Us!
Plebeian Market is a commerce platform that supports open trade and communications while helping individuals and merchants transition onto a bitcoin standard.
Let's Build Together
Bekka
-
 @ 38f9a05c:6999fc04
2024-04-07 12:08:30
@ 38f9a05c:6999fc04
2024-04-07 12:08:30
In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.
Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.
Inferiority complex
The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.
An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.
Superiority Complex
Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.
An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.
Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.
By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.
Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.
Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.
In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.
Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."
-
 @ 362ebffa:492e2719
2024-04-20 15:52:12
@ 362ebffa:492e2719
2024-04-20 15:52:12Julian Assange (founder of WikiLeaks) released classified documents in 2010, including sensitive U.S. military and diplomatic information. He faced charges of conspiracy and espionage for his role in obtaining and disseminating the documents. Edward Snowden, (former NSA contractor) leaked classified information in 2013, exposing global surveillance programs. Snowden revealed widespread data collection by intelligence agencies, leading to charges of espionage and theft of government property.
As of today in 2024, both Assange and Snowden are considered whistle blowers by some but face legal consequences for their actions, igniting debates on government transparency and individual rights.
In a sane democratic World, they should be free!
Their efforts to expose government surveillance and misconduct was brave and should be encouraged. But instead they have also faced legal consequences for their actions, with the U.S. government seeking their extradition to face trial on criminal charges.
These cases have sparked debates about government transparency, freedom of the press, national security, and the balance between individual rights and state interests.
Without whistle blowers, government are becoming bullies!
-
 @ bcea2b98:7ccef3c9
2024-04-20 14:20:00
@ bcea2b98:7ccef3c9
2024-04-20 14:20:00The model suggests Bitcoin's price hinges on its scarcity, gauged by the stock-to-flow ratio, comparing the amount in circulation to newly mined coins. Higher ratios signify greater scarcity, akin to gold's historical average of 66. After Bitcoin's third halving, its ratio doubled, enhancing its scarcity.
Meanwhile, the Grayscale Bitcoin Trust's recent halving, losing 300k BTC since the launch of spot Bitcoin ETFs, may have a more immediate negative impact on Bitcoin's price.
-
 @ a012dc82:6458a70d
2024-04-23 03:09:58
@ a012dc82:6458a70d
2024-04-23 03:09:58Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
This is the most catastrophic bankruptcy of a custodian in the digital asset market since Mt. Gox, which collapsed in 2014. This study examines the Bitcoin strong hands' reaction to the FTX bank run and how people are trying to find safety by keeping their bitcoin privately.
The events of November 6–14, 2022, in the digital asset market are, to put it mildly, astonishing, startling, and disheartening. One week saw one of the most well-known and high-volume exchanges, FTX.com, go down.
-
Experienced a bank run.
-
Client withdrawals have been stopped.
-
Binance's purchase negotiations fell through.
-
As much as $10 billion in missing client money was uncovered.
-
Allegedly, $500 million was stolen from exchange wallets.
-
FTX US and its sister company filed for Chapter 11 bankruptcy.
-
Brought to light what appears to be wrongdoing on the part of the Alameda/FFTX company.
Millions of consumers would be left with imprisoned cash, years of positive industry image would be destroyed, and new credit contagion risks would emerge, many of which would go unnoticed for a long time. The fall of Mt. Gox in 2013—in which a major custodian was shown to be fractionally reserved—comes to mind in light of this development.
The crypto market is in disarray, but investors should keep in mind that the underlying cryptography is secure and that digital assets exist in a free market. Bitcoin has no safety net, and the deleveraging of the whole business will burn away any waste or corruption, but it will be painful. The market will mend, recover, and come back stronger in the months and years ahead thanks to the increased emphasis on exchanging proof-of-reserves and the drive toward self-custody.
We shall discuss the following topics in this week's report:
-
Specifics on the recent thefts from on-chain FTX wallets
-
greater repercussions for personal finances and parenting arrangements.
-
Effects on the conviction of long-term Bitcoin holders have been observed.
Translations
Aside from the original English version, This Week on Chain has been translated into Spanish, Italian, Chinese, Japanese, Turkish, French, Portuguese, Farsi, Polish, Arabic, Russian, Vietnamese, and Greek.
Onchain Weekly Report
Here you can see the Week Onchain Newsletter's live dashboard, along with all featured charts. Our weekly video report is published every Tuesday and delves further into this dashboard and all of the data it covers.
Fractional Reserves
Eventually, the truth will (hopefully) emerge about how FTX lost client deposits and blew a hole of $8 billion to $10 billion in their balance sheet. However, there are numerous indications that money was misappropriated through the sibling hedge fund Alameda Research.We direct readers to the following resources for context and analysis of the triangle formed by Alameda, FTX, and Binance:
-
Thread on Twitter describing the movement of money from Alameda through FTX to Binance.
-
Information visualization dashboard displaying the inter-entity lifetime flow of money.
-
Report in video format detailing these preliminary results.
Over the years, several data sources have had difficulty keeping up with FTX's exchange reserves. In our own observations, we found that FTX used a somewhat sophisticated peeling chain method for their BTC holdings. The cluster's FTX reserves peaked at around 102k BTC in April/May of this year. In the latter half of June, this dropped by a whopping 51.3%.
Since then, reserves have steadily decreased, culminating in this week's bank run when they were essentially at nothing. After the collapse of LUNA, 3AC, and other lenders in May and June, allegations of Alameda misappropriating client deposits suggest the Alameda-FTX company may have suffered a serious impairment to its balance sheet during that time period.
There have been two big drops in the amount of ETH owned on FTX:
-
With a decrease of 576k ETH (55.2% in reserve value) in June
-
This week, the price of ETH dropped from 611k to 2.8k (-99.5%).
Just as with Bitcoin, this means that almost no ETH is left in wallets controlled by FTX after the bank run.
Looking into stablecoin reserves, we can observe that on FTX, the total reserves began to decrease precipitously on October 19th, from $725 million to almost nothing by the end of the following month.
After the June sell-off, stablecoin balances skyrocketed to a new all-time high, while BTC and ETH holdings fell dramatically. This may provide more evidence that some degree of balance sheet impairment had happened at that time, requiring the use of BTC and/or ETH collateral in exchange for the use of stablecoins in a swap or loan.
There's still a lot of mystery around what went down between FTX and Alameda, but there's also a growing body of on-chain evidence suggesting problems emerged in May or June. Consequently, the events of the last several months may be explained as nothing more than a prelude to the eventual collapse of the exchange.
Release of Updated Dashboards
The new dashboards we've developed provide a way to track the growth and decline of Bitcoin's investor base, as well as the value of their holdings. These graphs are taken from our entity balance change dashboard (T3) and are complemented by the data in our address cohort dashboard (T2).
Safety in Self-Custody
As holders want the security of self-custody, there has been an unprecedented rate of coin withdrawals from exchanges. Since November 6, when rumblings of issues at FTX were still in their infancy, the following charts have tracked the aggregate balance change of exchanges, investor wallet cohorts, and miners.
The 7-day drop of 72,9K BTC in total BTC balance on exchanges is one of the greatest such drops in history. Only April-2020, November-2020, and June-July 2022 may be compared to this.
To a similar extent, Ether has had 1.101 million ETH removed from exchanges in the last week. This is the greatest 30-day decrease in balance since September 2020, during the height of "DeFi Summer," when demand for ETH skyrocketed for use as collateral in smart contracts.
While this week saw a decrease in BTC and ETH exchange reserves, approximately $1.04 billion was deposited into exchanges on November 10th through stablecoins such as USDT, USDC, BUSD, and DAI. As far as daily net inflows go, this is the seventh highest ever.
The total value of stablecoins held in exchange reserves has now reached $41.186 billion as a result. There has been a significant rise in BUSD supremacy, as shown by the over $21.44B in BUSD reserves. This is probably due to Binance's increasing dominance as the world's biggest exchange and the recent concentration of its stablecoins towards BUSD.
There may be a movement in market preference since USDT exchange reserves have decreased marginally over the last several months while USDC reserves have decreased significantly.
Interestingly, smart contracts are a major source for stablecoins, with monthly withdrawals from Ethereum smart contracts totaling $4.63 billion. This helps to underline how critical access to hard currency has become as of late.
Due to this, the market has entered a peculiar phase in which centrally generated stablecoins are flooding exchanges while BTC and ETH are being removed from them at unprecedented rates. The two-part model is shown in the following chart:
There was a net outflow of BTC and ETH from exchanges, as shown by the absence of them in the barcode trail.
The oscillator displays the difference between the net USD flow of BTC and ETH and the net inflow of stablecoins. When is greater than zero, it means that more "purchasing capacity" than usual has been poured into exchanges in the form of stablecoins.
There has been a net rise of $4.0 billion every month in the purchasing power of stablecoins on exchanges, as seen above. This illustrates that investors tend to prefer retaining trustless BTC and ETH assets over centrally produced stablecoins at the present moment, notwithstanding the market's volatility.
This is a really interesting signal, and one might make the argument that it reflects the market's need for safety in self-custody and trust in the underlying assets.
Bitcoin balances swell
Given the massive withdrawals of bitcoin from exchanges, it is clear that the FTX event has caused a noticeable shift in investor behavior across all wallet cohorts. Despite the FTX crash, on-chain wallets saw a net rise in balances across the board, from shrimp ( 1 BTC) towhaless (> 1,000 BTC). For several groups, this is an almost complete reversal from the steady distribution pattern of previous months.
In the last 30 days, the Shrimp cohort ( 1BTC) has increased by +51,400 BTC, with a +33,700 BTC gain in the past week alone. Beyond the high point of the bull market in 2017, this amount of balance inflow is the second highest ever.
The Crab group, which consists of investors with 1–10 BTC, is also quite active, having removed 48.7k BTC from exchanges at prices that are getting close to the highest acquisition rates seen during the 2017 bull market. This is a new and compelling all-time high for the percentage of total Bitcoin supply held by those with more than 10 BTC.
We use the terms "fish" and "sharks" to refer to groups of bitcoin wallets containing between 10 and 1,000 bitcoins, respectively. The wealth of these members of the group is comparable to that of wealthy people, large corporations, and large institutions.
We have had one of the highest 7-day rises in cohort balances in history, at 78.0k BTC, after many months of decreasing growth. An attitude of "withdraw now, ask questions later" may be at play here.
We have only looked at the inflow and outflow of coins directly via exchanges for whales, here defined as those having more than 1,000 BTC. This will more accurately represent these massive organizations' genuine investor activity.The average 30-day change in the balance of all whales is +53,7K BTC, indicating that they have been net purchasers in recent weeks.
However, their on-net activity this week has been far lower than that of previous cohorts, with a net gain of just 3.57k BTC.
Last but not least, the industry of Bitcoin miners, already a target of regulatory scrutiny, has been hit hard by the recent drop in coin price. As the price of hash power continues to fall, miners have spent around 7.76k BTC this week, or about 9.5% of their reserves. Proof that Bitcoin miners are very cyclical in their activity, this is the largest monthly miner balance fall since September 2018.
HODLers Resolve
The last half of this newsletter will focus on the reaction of Bitcoin HODLers, with the goal of determining whether there has been any visible erosion of their original commitment. If there was ever a moment for HODLers to lose trust in the asset, it is certainly now, given the size of the damage and the far-reaching ramifications of the FTX collapse.
Since November 6th, the quantity of bitcoins held by long-term holders—those who are statistically least likely to spend their coins—has decreased by -61,500. A significant amount of bitcoin ($48,100) was spent in the previous week. The above-described shift in the size of things is not yet large enough to imply widespread loss of belief as compared to previous norms. But if this continues, it might imply a shortage of LTH.
The weekly total of revived supply older than 1 year is shown here, along with a 4-year Z-score. This week, 97,45k BTC older than a year were spent, possibly returning them to circulation.
It's a +0.83 sigma shift over 4 years, which is significant but not yet unprecedented. Similar to LTH Supply, this indicator warrants close attention in case it signals the beginning of a new long-term pattern.
Also, the median age of a bitcoin has increased to slightly over 90 days, which is three times what was seen in the low volatility environment of September and October. Spending in older currencies has increased, which parallels highs seen during capitulation sell-off events and the 2021 bull market profit taking.
If dormancy continues to rise or rises to an unusually high level, it may be an indication that widespread fear has taken hold within the HODLer community.
Now that we have a weekly total of coindays destroyed, we can return to the 4-year Z-score formulation we used before (CDD). Clearly, this week's volume of coinday destruction was +1.9 standard deviations above the norm, marking the end of a long period of an exceptionally low coin supply. This week, 165 million coindays have been burned, the same as squandering 452,200 BTC stored for a year.
In general, the HODLer community has reacted with some degree of sudden alarm. Yet, the enormity of the situation suggests that this might be to be anticipated. The question of whether or not these surges moderate over the next several weeks, which would indicate that the current reorganization is more of an "event" than a "trend," is perhaps of greater importance.
A general lack of conviction and worry may be at play, though, if there was a prolonged increase in the spending of older coins and a decrease in the availability of LTH.
Conclusions
The failure of FTX has been devastating and is a black eye for the whole sector. When people who have put their faith in a platform become caught and their money disappears, it is a genuinely horrible thing. Bitcoin and the industry as a whole will emerge stronger from this unfortunate forest fire and deleveraging catastrophe than they were before.
FAQ
What is Glassnode in crypto? Glassnode is a data intelligence platform for the bitcoin and blockchain industries. By concentrating on the most crucial input source in the space—data from the blockchains themselves—the apps that Glassnode develops give new methods of giving insights into blockchains and cryptocurrencies.
What does it mean when a price is "Realized"? The term "realized price" refers to the cash market price after deducting for quality, shipping costs, and anticipated demand.
Can you explain how the market cap of Bitcoin is determined? The total market capitalization realized is the latest price of each UTXO multiplied by Due to the fact that certain digital currencies may become untraceable or unusable as a result of technical difficulties, Realized Cap was developed to devalue such tokens after an extended period of inactivity.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bcea2b98:7ccef3c9
2024-04-20 00:11:30
@ bcea2b98:7ccef3c9
2024-04-20 00:11:30 -
 @ 1f9e547c:8af216ed
2024-04-23 01:48:42
@ 1f9e547c:8af216ed
2024-04-23 01:48:42Opinion about the city of Seattle
testfornostrtags
nostrTest
Join the conversation!\n\nJust Testing ...
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
Transform your relay's landing page from this:
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ 5df413d4:2add4f5b
2024-04-07 04:11:25
@ 5df413d4:2add4f5b
2024-04-07 04:11:25Like a Bitcoiner Litany Against Fear, “Bitcoin is trustless” is a mantra soulfully and sincerely recited by acolytes of the technology. And it is true – Bitcoin is trustless. No single entity can control or force changes onto the Bitcoin network. With enough intension, insomuch as you can access to the necessary tools, no intermediary can prevent you from buying, selling, spending, holding, or otherwise using bitcoin, even under the most repressive of circumstances.
Bitcoin is trustless, but bitcoining...bitcoining is all about trust! Across self, family, friends, and community, bitcoining forces trust dynamics to the surface and forms a lived experience of reimagined and rebuilt interpersonal and social trust structures that extend far beyond the timechain.
Developing Trust in Self
https://image.nostr.build/788e81071ac4b904d75b2f22e23f90e9fda61ab42482bcba4840baf04d3e7a34.jpg
Bitcoining is, first and foremost, a practice of radical self-trust. As a bearer money, any and all mistakes resulting in loss of bitcoin rest squarely at the feet of the individual holder and, after the fact, can only be worn like a heavy iron dunce cap by the same. As such, bitcoiners must first conquer their inner doubts and develop an unshakeable internal trust in self. This is the foundation of personal responsibility required to take full control of one’s financial life and to shoulder, without fear or doubt, the sobering awareness that the wealth (and perhaps freedom) of one’s self, family, and future progeny may well hinge entirely on the “rightness” of one’s decisions around bitcoin today.
Rebuilding Trust in Family
https://image.nostr.build/ab2d3d270c842d65d3f434382498d34baea1e30afe8f66e20e7dd682a7054633.jpg
A few months ago, I found myself explaining the nature of bitcoin self-custody for inheritance to a senior private wealth management executive. As the implications became clear to her, in a moment of unfiltered horror, she exclaimed “you mean as I get older, I would have to trust my children with this?” My response, of course, “Who else but your own children should you trust to secure your bitcoin wealth as you age?” Confronted with my rebuttal, she did not have an answer, but I could tell that it was being digested as food for thought.
The sad truth is that the fiat world orchestrates a pervasive and never-ending psyop to estrange us from family – and to thus divorce us from the powerful benefits of intergenerational family economics. Bitcoin fixes this. Bitcoining with a focus on long-term and generational wealth is a strong catalyst for us to reject the unbalanced, scorched-earth consumerist "individualism" that now increasingly pits young against old. With our new bearings as bitcoiners, we realize that it is time to heal generational rifts in our families and that many priceless things are regained from rebuilding lost bi-directional familial ties of economic support and care. Bitcoin wealth being “stacked” today will mean very little unless there are associated immediate and extended family units with strong bonds of shared trust and trust-distributed risk in place to shepherd keys far into the future.
Deepening Trust in Friends
https://image.nostr.build/ff8641bbc8a2b118fe772d8c6f0c25e41e04b17c68519371a1c4658c58d88b5b.jpg
While bitcoin’s monetary network might make us “free” (at least from time-theft), it is parallel human networks that must ultimately make us happy and give our lives meaning. It is best that we understand that happiness, more than anything else, is the opposite of loneliness – and that this is one of the few things that money truly cannot buy. The double-edge sword of bitcoining is that without strong supporting bitcoiner friendships, bitcoin’s promise of extreme future wealth threatens to bring an even more extreme isolation along with it for many. And humans die in insolation...It’s dangerous to go alone, as they say. Who will you be able to turn to when the world sees you as little more than a walking sat symbol?
The preemptive remedy here is seeking out and cultivating meaningful friendships with other bitcoiners and, like Noah before the flood, working to get your most important nocoiner friends on the boat before it’s too late. Bitcoiner friendships form the social layer of bitcoin wealth protection and can provide a broad range of “social insurance” against catastrophe – economic or otherwise. As such, bitcoiner friendships are integral to one’s wider “real-world” bitcoin security model and must not be overlooked. Ask yourself – what’s the point of having nice things if you have no one to share them with?
Leveraging Trust in Pseudonymous Community
https://image.nostr.build/4e44e8c7743e92fcff9696857ac467bf78fc11066a85143608c5c7525e0d4f8e.jpg
Scenario: You arrive in a foreign country. An anon that you “know from the internet" suggests you to reach out to another anon who supposedly lives in city you’re visiting. Upon making contact, you receive GPS coordinates – I repeat, coordinates, not an address – via an encrypted chat set to “burn after reading” mode as an invite to come hang out with a group of local bitcoiners.
Totally normal stuff, right? 😅 Well, this is essentially the situation I stumbled into not long ago whilst traveling in Asia. Ultimately, I felt comfortable joining this meetup because of the nature of the larger bitcoiner community. All of us in the room might have been nyms to each other but we shared mutual friends who could cross-verify us without divulging unnecessary private information, of course. In bitcoin, and a few other very strange communities that I count myself a member of, meetings like these serve a critical function for broader, distributed reputation and trust building within what is otherwise a semi-transient, geographically dispersed, pseudonymous community.
In such situations, good behavior confers all parties with important trust-based social capital. The mutual friend gains reputation as someone who “does not associate with or recommend shitcoiners / bad actors.” The meetup attendees, if they behave, are more likely to be recommended by both the mutual friend and by each other the next time around. Thus, a positive social feedback loop emerges, with bitcoiners going around saying nice things about each other and having those things largely proven to be true in subsequent real world interactions. The implications here are far-reaching – as these positive vibrations flow through bitcoin’s living human terrain, they amplify and accelerate the chance meetings and serendipitous exchange of ideas from which the future household names of bitcoin tools, enterprises, and communities will certainly be born.
Conclusion
For most, certainly myself included, engaging with bitcoin forces a dramatic and comprehensive reshaping of both one’s understanding of and relationship with trust. Ironically, bitcoining, which starts out as an individual endeavor to harness the transformative power of trustless money in one’s life, all but requires the establishment of both internal and social trust models that are more robust and more meaningful, than anything our fiat-minded precoiner selves could have ever imagined. Bitcoin is trustless. But bitcoining is nothing without trust.
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ 0403c86a:66d3a378
2024-04-22 18:51:17
@ 0403c86a:66d3a378
2024-04-22 18:51:17Max Verstappen 🇳🇱 showcased his dominance once again, converting pole position into a stunning victory in Shanghai! 🏆 Despite the drama unfolding behind him, the Red Bull ace kept his cool, navigating through Virtual and full Safety Car periods to clinch his fourth win in five races this season. 💪
Lando Norris 🇬🇧 pulled off a strategic masterclass, pitting just once to leap ahead of Sergio Perez 🇲🇽 and secure a well-deserved second place for McLaren. 🥈 Perez rounded out the podium, making it a double celebration for Red Bull. 🍾
Ferrari's Charles Leclerc 🇲🇨 and Carlos Sainz 🇪🇸 showcased their tyre management skills, completing the race with a single pit stop each to claim fourth and fifth, respectively. 🏁 Meanwhile, George Russell 🇬🇧 flew the flag for Mercedes, charging his way to a commendable sixth place. 💪
The Chinese Grand Prix proved to be an electrifying encounter, filled with nail-biting overtakes and strategic gambles. 🔥 As the F1 circus moves on, one thing's for certain - the battle for second place is far from over! 🌍🏎️ #ChineseGP #F1 #Verstappen #Norris #Perez
-
 @ 8ea48526:e6720a43
2024-04-17 14:06:11
@ 8ea48526:e6720a43
2024-04-17 14:06:11Recently there has been discussion on the socials about supporting open source developers, specifically those who work on Bitcoin and Nostr. There is a small-ish camp of people who think that Bitcoin should remain as is…it’s perfect, don’t mess with a good thing. Many others think – correctly, in my opinion – that Bitcoin needs to be maintained and even enhanced. As long as the changes make Bitcoin better money, we should evaluate, go slow, and keep things simple.
Who will maintain Bitcoin and other open source projects? Will devs do it out of the goodness of their heart? Builders gotta eat; food ain’t free. A handful of institutions, both non-profit and businesses, provide grants and long term support to developers. This is great and I hope that continues. However, there is more that we can do. There is more that you can do.
Zappy 21st
I propose we make the 21st day of every month the (un)official ”Zap a Builder Day”. It’s simple. On day 21 in the current month, find a developer and zap them sats.
Created in the spirit of #v4v and the #grownostr social experiment, I’d love to see people make this part of their monthly routine. It’s common for certain days of the month to have meaning. The 1st day marks the start of a new month. The 5th day is a common day when mortgage payments are due. In the United States, on the 15th day of April taxes are due. So now there is the 21st day, the day you send some value to devs.
Who are you gonna zap?
Any open source developer. Start simple; don't overthink this. If you're using a Nostr client that you love, go find one of the contributors and zap them. If you use Bitcoin or Lightning regularly, find a Bitcoin or Lightning dev. There are many other great freedom tech tools, like wallets, sovereign computing apps, and privacy tools that have developers behind them. Zap a developer. (I say developer, but I really mean "contributor". Remember the designers, product, support, and project people who also contribute.)
I'm intentionally not giving names of developers here because I don't want to favor one over the other. Every open source developer is important to different people based on the tools they use. So go zap the people in your realm.
I'm only publishing this on Nostr, but I'm happy if the idea spreads beyond that. Nostr is the perfect place because you can so easily find a core dev and zap them. No need to track down their website hoping to find a wallet address or request a Lightning invoice.
Join the Zaps
While everyone is excited about block 840000, halvings come and halvings go. But the 21st is always here for you. Every month, reliably, quietly doing its thing. Just like those open source devs you rely on so much. They’re here every month, reliably, quietly doing their thing. Let’s show them some love.
This April 21st find a dev and zap them. If you’d like, add a message telling them how awesome their work is and tag it with #Zappy21st. Let’s flood the feeds with #Zappy21st messages and surface great open source developers to others. Next month on the 21st, we’ll do it again.
🤘
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 30ceb64e:7f08bdf5
2024-04-22 17:17:39
@ 30ceb64e:7f08bdf5
2024-04-22 17:17:39Hey freaks!
Cody Wilson gave a speech regarding the idea of death athleticism.
It seems as though I've made death my profession.
Bitcoin is a ladder, Hustle has climbed an additional two rungs this month.
If hyperbitcoinization happens, everyone reading this post will be fine.
If your reading this post, congratulations you' ve made it.
Bitcoin enables exponential growth in your savings, and through the process of groking bitcoin, one picks up activities and habbits that are more akin to minamalism than consumerism. Adopting a self sufficient and sovereign attitude, aligning yourself with productive, like-minded individuals, and extending your time preference is an inevitable pull towards a heroes journey.
This epoch has hustle angrier at the looters (he's been getting into his Rothbard). If you ask a normie what we need the govt for...., you'll receive answers that prescribe them godlike powers.
Michael Saylor said we don't want to be martyrs, we want to win. TheWildHustle welcomes an honorable death performance. When Hustle was in the Air Force he would load bombs and rounds into F-16 fighter jets, the only real world mission he accomplished was in raining fire onto libya to kill Kadafi because he was trying to separate money from state. His squadrons motta was, "giving our enemies the opportunity to die for their country". What an honor.
Don't die for your country freaks! And the best weapon the state has, is its ability to manipulate emotions by fomenting fear. TheWildHustle would be fine and happy if he died right now, everything else is just whipped cream and strawberrys at this point.
-
 @ 3c984938:2ec11289
2024-04-22 16:19:48
@ 3c984938:2ec11289
2024-04-22 16:19:48The Bell Ringers of Nostr (Nip-23)
Hafa Adai Bitcoiners! If you have fallen down the rabbit hole, congratulations.
“We’re all mad here. I’m mad. You’re mad. Or you wouldn't have come here."
You just learned about Bitcoin, but to know Bitcoin is to know what money is. To know what money is to also understand what Bitcoin stands for-- free speech. Regrettably, I must inform you that their exist many rabbit holes beyond Bitcoin. But for now, we enter the publishing Forest of Nostr to journey to find knights. This article discusses one closed source tool and one Open Source Both definitely have value and puts user first.
The YakiHonne Bunny
As I traveled through a different kind of forest, I stumbled across a rabbit. We kinda look alike so I had to stop and observe much closer. It was such a lovely encounter! The bunny was so kind that it befriended not just me but all that came across it's path. The bunny did not ask me to register my name, email, physical address or even my phone number but rather allow me to maintain my Identity by Encryption via Nostr/npub.

The bunny invited me to a tea party, and I got drunk off from their kindness to the very drop. The bunnies have a unique position. Unfortunately, their cursed with ICANN like many other peers. They're not alone, some are using the newer ICANN gTLD but are still cursed no less. ~This is a different rabbit hole so I'm stopping here.

Despite, their curse like other plagued options on the internet. The bunnies still do what they can to help users get their "Long-form" content out into the world with grace and style. If you're reading this on yakihonne.com then, this is a good example. They have about five dedicated relays just to support "long form Content" or "NIP-23" it should be noted that not all relays support "NIP-23." I would recommend users to not crowd onto just a single relay but to have a few odd ball relays and to support them. I will cover relays later. The important thing to note is not all relays support the different types of data. (A.K.A "Nip")

Due to the nature of being closed source, I do not think it correct to be a knight. However, the work the Yakihonne's developers do is also important and does contribute to the Nostr ecosystem with sophistication . I think they could potentially, someday in the future become Open Source. In the same sense, I am grateful they're not supported by the OpenSats Project. (This is Another Rabbit Hole) Maybe, it's to avoid making deals with potentially bad actors? Only time will tell us. Since the creatures of the publishing forest are all unique and have an important task, I thought Bell Ringer would be more fitting for our dearest critters. I'll be one of the first Town criers whenever they do decide to become open source. 😁

After eating so many lovely cakes, pastries, Pão de queijo (Brazillian cheese buns) and cream, I had to bid farewell or I'll end up getting fatter! The Darjeeling tea was quite divine, and I could easily see myself staying longer, but this was a different forest I've never explored. The rabbit left me a note before I was leaving, as an option I could use their mobile app! (Available on Apple and Google) Prehaps to arrange another tea party? So, I entered a super green forestry. It was so green that the trees were moss covered. I couldn't help but feel I was being watched. Was I imagining things? A Flycat appears before me. I was scared (as I'm much smaller) at first but it turns out the Flycat is just odd.
The Flycat.

Flycat is an open source social network on Nostr. The Flycat is sleek and agility enough to also support long form. In additional, Flycat has a very unique feature, they allow users to have multiple relay lists. This is nice tool because you can have a set list of relays for Nip-23(long-form) and another for everyday/daily notes on Nostr. Cute platform to create and manage your community posts. So definitely, worth checking out if this up your alley.

Just like Yakihonne.com, Flycat.club is built on the Nostr Protocol. So "Identity by encryption" wins yet again but Flycat steps it up a few notches more with flexible login options. Still plagued with ICANN, like 99% of all websites. Flycat does have a noble mission: exit out of toxic internet. Can this be moved to IPFS? I think it's possible!

Follow as I journey further in the Forest of Publishing in part two for more tools to use. Departing is such sweet sorrow. This Flycat is just full of curiosities! 🧡🤍💛 K--kkk--kisu??! 💚💜💞 😳

The title of "Bell Ringer" comes to mind for Yakihonne and Flycat as their platform does help users spread their content and gather information as if your in a local town's pub. Thus, they serve the community, I can only imagine how exhausting such a task could be.

Author's Note:
Diving deeper into the rabbit hole is tricky. Just like the rabbit hole for Bitcoin, I'll do my absolute best to decipher the base layer but you'll still need to do your own falling(digging). There are lots of holes to fall in so consider bringing an umbrella. To put it all in one sitting would just overwhelm you. But this series isn't about the different rabbit holes, I'm merely stating there is so much to uncover if you dare to learn. No worries you can always #asknostr on your client. I merely wish to help you discover tools to help you dear user to live a more decentralized life and I'm pointing out the different tools at your fingertips in a story format. You have the power. Do not let big tech continue to leech off your work.
I hope you enjoyed this content.
Here are some of the critters I have met along my journey through the forest:
👉💕💕 Hearts for being a Dev 👉💋💋kisu for being an OpenSource Dev
💕💕Sedd💕 @npub16vjln603hfsfhremp627jle4ycm6p23grjjqrm04rrdwupldyfnsjx88a2
💕💕_Moos 💕 @npub19qcnj6qzrhv92pf8tuhd74wcl6c8r2y2mmrp5pknfy3m2lsrd7xs6y7xw2
💋💋ElectronicMonkey 💋 @npub1ghzp7g0peac4lfkeegst3cqz546dk7a5n6twazvrf3nd432yddaqa3qtwq
👉I would like to point out. As of April 2024, two major moves have been done in Germany and Sweden; yet the month is still young at the time of this publication Let's encourage all platforms, organizations, and devs to move to open source. If countries can do it, then most certainly (N)oystr can! Digital Sovereignty for everyone!
Special thanks to: 🧀🥐Andrey For recommending Pão de queijo(Brazilian Cheese Buns) @npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4
See you Next time! Whatever shall I uncover next?

👉Onigirl respects all platforms, logos and art. If such platform(s) felt my designs with your logos were disrespectful. I'll happily taken them down with no hard feelings. I only did so outta my love for Nostr. I may come off a bit crazy.

-
 @ 721d40ba:199aa53a
2024-04-22 12:04:25
@ 721d40ba:199aa53a
2024-04-22 12:04:25It just is.
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ a012dc82:6458a70d
2024-04-22 02:01:30
@ a012dc82:6458a70d
2024-04-22 02:01:30Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
"The Bitcoin maximalists were correct again. No good will come of them. They should burn in hell. They're to blame for everything that's wrong!
It seems like every year since 2020, I hear some form of the following from persons involved in the "crypto" industry:
"Listen, a billion-dollar firm won't fall down in a flash." That’s impossible. You assume their business plan is to take your $2,000 in cryptocurrency, and yet they fund a full stadium. Stop being such a moron. You may trust it with your bitcoins. It's not worth the hassle to try to handle custody matters on your own. Custodians are crucial if we desire widespread adoption.
These individuals have a confidence in VC-backed organizations that is more misguided than that of the most religious fundamentalists.
Yet the educators who are the driving force behind these establishments are held in the highest esteem by the media, even as their views drive people to the brink of annihilation. Consider the case of Mr. Wonderful:
Why the FTX collapse may have been the best thing that could have happened to bitcoin in 2022, igniting the next bull market.
What I said in my satirical piece in October is validated by these findings. The "smartest in the room" today are as clueless as the rest of the lemmings rushing into the lava, so you know we're in late-stage fiat.
They are so used to the convenience of living in close proximity to the money printer that they cannot fathom the significance of the existence of a decentralized digital currency like Bitcoin. They are blinded by the paradigm that has given them success up to this point, and as a result, they have no business passing judgment on something as paradigmatically different as Bitcoin.
TOXIC!!!
Bitcoin maximalists are disregarded when they transform warnings into memes like "not your keys, not your coins" or when they preach the necessity of "sound money" like "Bitcoin solves this," as though they are either a) extremists or b) dull and out of date.
The Mr. Wonderfuls, BitBoys, and Vitaliks of the world all respond uniformly with "toxic."
Okay, back we go again.
It's a fact that Ponzi schemes always collapse far more rapidly than they rise, and that when their ascent has been spectacular, their eventual demise will be much more spectacular. We've come a long way, baby, from Mt. Gox to BitConnect to Luna to BlockFi to Celsius to Voyager to FTX.
They're identical to one another and provide no advantages over competing bitcoin firms. To be clear, I use the term "company" since all of these purported "projects" are really simply businesses like FTX that are engaging in fictitious numerical manipulation in code. All the other cryptocurrencies, NFTs, and DeFis are just as foolish as Ethereum, Cardano, Hex, Solana, Chainlink, and all the rest.
Aside from Bitcoin, everything else is the same. Only Bitcoin doesn't have "leadership" and a snake's head to cut off pressure, which I mean as a good feature. Bitcoin is the only currency with a flawless design. Bitcoin alone emerged naturally and purely as a result of market forces. Bitcoin alone has been stabilized. Bitcoin alone has a limited supply. Bitcoin is the only currency that counts.
The same Bitcoin maximalists who warned you about the aforementioned also warned you about shitcoins. One day, they will all either burst, collapse, or fade out of existence.
Now the only issue is how much of a warning you need to take seriously.
THE SIGNS WERE THERE, NOT ONLY THE WARNINGS
Nothing about FTX added up. On a boat in Miami for Bitcoin 2021, I had the pleasure of meeting its creator, Sam Bankman-Friend, or SBF. We went on a small sailing excursion with about fifty or sixty other folks.
For all I knew, he was just some guy with a potbelly and awful hair. After some uncomfortable small talk, I left him to his hors d'oeuvres in the corner while I went to chat with the waiters.
I was asked by one of the passengers if I wanted to know more about the firm he operated, and when he said it was called "FTX," I said, "What the heck is that?" Another another worthless cryptocurrency?" No, he said, it's one of the world's fastest-growing exchanges.
My curiosity peaked, so I asked SBF a few questions, and he told me that he had previously managed a crypto hedge fund, had great success with it, and invested the proceeds in the creation of an exchange.
My first thought was, "Goddammit, these shitcoiners are actually generating money by fueling gambling addictions, and here I am trying to help people stack Sats properly by operating a Bitcoin-only service in Australia called Amber." "What a clown planet...."
After that, I forgot everything about him until I read his tweets about "Home Cooking With Beyond Meat." The weak body and the shitcoinery made immediate sense to me.
Some of you may be offended by the suggestion that one's appearance is mostly dictated by one's conduct, but the truth is that your actions reflect the values you have.
While it's true that there are certain things you're stuck with forever, you can shape the rest of your life to suit your priorities, which is why Bitcoin has such a beautiful design.
Suffice it to say that unattractive facial features should have sounded an alarm. If you sell fake meat, you'll have to deal with fake customers (and a whole lot more fakeness in between, which I won't get into since it could set off some people's triggers).
WHAT’S ON THE HORIZON?
Can you predict the topic of the next "I told you so" article?
It's likely that Ponzi-style craptocurrencies whose raison d'être is "pumpamentals" will fail, or that Ethereum will unite with governments that want to issue central bank digital currencies to form "panopticoin" (CBDCs).
There is no sign of NFTs surviving. DeFi is currently in DeepShit, but perhaps that round can be restarted.
No matter what it is, all of the morons who blindly follow these kinds of individuals are in for a horrible experience.
Sayings like "You couldn't make up such lyrical irony if you tried" are just too perfect to be made up.
-
CeFi did not work (while being sponsored by Nexo).
-
Some individuals take the nice stuff we make and put it to ill use.
-
"Could there be an issue at the societal level?"
Hosts like these, along with the people responsible for FTX's debacle, have a startling lack of understanding of human nature, somewhat unlike that of Marxists. They believe that the world can be saved if only people "create awesome stuff" and that one day the social layer can be repaired by transforming society into a transhuman smart contract.
They fail to recognize that restraints are not only beneficial but also necessary.And this is especially true when it comes to the language of worth (i.e., money). For questions 2 and 3, that's the correct response.
What people consider to be Bitcoin's shortcomings are, in fact, its greatest strengths. The reason SBF, Vitalik Buterin, Roger Ver, Richard Heart, and the rest of the charlatans have no effect on Bitcoin is that it is better.
Such young children, lacking in both maturity and psychological insight, have historically been given no voice. Not surprisingly, in the world of clowns, their opinions matter.
One can only speculate as to what they will do if Ethereum fails and their idol, Vitalik, becomes the next SBF. To be honest, I don't believe they're prepared for it.
THE SILVER LINING
So, what does this imply, exactly? So, now what do we do with all this information?
In any case, I suppose there's always a bright side to things.
After the failures of Luna and Three Arrows Capital, some are saying that this FTX fiasco has "put the industry back by years."
I agree, but only to the extent that the short-term value of bitcoin may be impacted. Aside from that, I have to strongly disagree.
This whole process has, if anything, grounded the so-called "business" in reality and exposed it for what it truly was on the inside: a gigantic hot air balloon.
Even though the Bitcoin sector has been inflated by the hype around cryptocurrency, it is getting closer to where it should have been at this time. Capital allocation toward Bitcoin will likely return to normal, while many silly concepts, such as NFTs and "tokens on Lightning," will likely evaporate.
Real capital will likely seek out genuine innovation and business concepts in and around Bitcoin, causing much of the phantom riches in all the mind-numbingly idiotic shitcoinery so prevalent these past few years to dissipate.
Eventually, Bitcoin will be stored in the offline wallets of Bitcoin enthusiasts and long-term HODLers, away from the control of institutions, crypto businesses, venture capitalists, shitcoiners, and weak hands. Growth will enter its next phase when a new price floor is established.
This has a positive net effect. The whole lot.
In this regard, SBF, Do Kwon, and Su Zhu are the unsought heroes we deserve as a species. Since we live in a clown society, it would make sense for our saviors to also have a clown complex, increasing the likelihood that they will wipe themselves off along with their stupid fiat industry.
Have a look at the list of investments made by FTX Ventures. It gives me a degree of satisfaction I haven't felt since Bitcoin surpassed its previous all-time high in 2021.
Why the FTX collapse may have been the best thing that could have happened to bitcoin in 2022, igniting the next bull market.
Source
A tiny number of freshly minted Bitcoin maximalists will have been created, a big number of the recent minimalists will have had their viewpoints confirmed, and the veterans will have spent the next few weeks on Twitter Spaces in astonishment, asking "how this could've happened." So we'll just relax and keep telling you that.
to varying degrees of eloquence and vibrancy, depending on the individual. And we can expect to be ignored again the next time and be fine with it.At least we may enjoy some free amusement.
Conclusion
The suffering experienced today is genuine. How horrible it must be to feel like a fraud! Know, though, that all of your negative emotions—guilt, wrath, melancholy, and rage—have the same origin. The whole foundation of "crypto" is a falsehood, which allowed Bankman-Fried to get away with his deception for so long: what claims to be a revolution is in fact merely the fiat system par excellence. Because all participants in Satoshi Nakamoto's network share the same information, double counting is thus impossible. And although crypto may go, it is still here.
FAQ
Where does FTX stand now? Sam Bankman-Fried, the disgraced firm's founder and former CEO, resigned from his position earlier this month after the company filed for Chapter 11 bankruptcy. The once staggeringly valuable FTX fell in a couple of days when the CEO of Binance, a competitor exchange, said that Binance would sell its FTT coins.
What is the procedure for selling bitcoins on FTX? Does bitcoin serve any useful purpose? Bitcoin is a digital currency designed for online money transfers. The goal of the digital currency was to establish an alternative payment system that could function independently of a governing body while otherwise functioning identically to conventional currencies.
Why do we need bitcoin? FTX.US asserts that its platform is secure due to the implementation of customary industry safeguards for such data as client assets. Separate withdrawal passwords are one example of the extra security measures that might be used.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 599f67f7:21fb3ea9
2024-04-17 03:25:50
@ 599f67f7:21fb3ea9
2024-04-17 03:25:50¿Eres un comerciante que busca comenzar a aceptar Bitcoin en tu negocio? ¿O eres un Bitcoiner apasionado que quiere incorporar empresas locales? ¿O tal vez no te importa Bitcoin y sólo quieres utilizar un procesador de pagos rápido y económico o montar una tienda web sencilla? Si la respuesta a cualquiera de estas preguntas es afirmativa, entonces esta guía es para ti. Puedes montar una tienda en el BTCPay Server alojado por Bitcoin Txoko y empezar a vender tus bienes y servicios por Bitcoin en menos de diez minutos, de forma gratuita.
¿Qué necesito?
Si tienes un teléfono móvil o un ordenador con acceso a Internet y una cuenta de correo electrónico, ¡estás listo!
Crear una cuenta
Crear una cuenta BTCPay Server en Bitcoin Txoko es gratis. Navega a btcpay.bitcointxoko.com para registrar una cuenta. Revisa tu bandeja de entrada para recibir un correo electrónico de bitcointxoko@gmail.com que contiene el enlace de confirmación.
Crear tu primera tienda
Al hacer clic en el enlace de confirmación accederá a la página de creación de la tienda. Asigna un nombre a tu tienda y elige la moneda predeterminada y una fuente de precios preferida. Por ejemplo, puedes elegir EUR y Kraken, que es la fuente de precios recomendada. BTCPay Server convertirá el precio de tus bienes o servicios de EUR a Bitcoin utilizando la fuente de precios en el momento de la compra.
Configurar una billetera
Para comenzar a aceptar pagos, primero debes vincular una billetera a tu tienda. A menos que esperes transacciones frecuentes de grandes cantidades (más de 500 EUR), te recomendamos configurar una billetera Lightning y omitir la billetera Bitcoin (en cadena) por ahora. Siempre puedes configurarla más tarde si la necesitas.
💡 Lightning es la red de liquidación de pagos ideal para aceptar pagos de Bitcoin porque ofrece liquidación instantánea y tarifas bajas en comparación con las transacciones en cadena.
La forma más sencilla de conectar una billetera Lightning es usar LNDhub porque no necesita correr tu propio nodo Lightning. Si aún no tienes una billetera LNDhub, no temas, Bitcoin Txoko ofrece billeteras LNDhub gratuitas y tardas menos de cinco minutos en configurarlas. Consulta nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t sobre cómo obtener tu propia billetera LNDhub y regresa cuando estés listo.
💡 Si ya dispones de una billtera, te recomendamos que crees una billetera independiente para este caso en lugar de utilizar tu billetera principal. Esto es más fácil de contabilizar y más seguro. Simplemente haz clic en
+ Agregar nueva billeteraen la barra de herramientas, dale un nombre a la billetera y créalo.
Con tu billetera LNDhub lista, - ve a tu cuenta BTCPay, busca
Walletsen la barra lateral y seleccionaLightning. - EligeUse custom node. - Copia la URL admin de LNDhub y pégala en la configuración de conexión. - Prueba la conexión de tu billetera. - Si todo salió bien, deberías recibir el mensajeConnection to the Lightning node successful, but no public address has been configured. Puedes ignorar la parte acerca de que no se ha configurado ninguna dirección pública; esto solo se aplica si estás corriendo tu propio nodo. - Haz clic enSaveuna vez que hayas probado con éxito la conexión de la billetera. - Después de hacer clic enSave, desactivaEnable LNURLen la secciónLNURL. No olvides hacer clic enSavenuevamente después de realizar cambios. - (Opcional) En este punto, también recomendamos marcar la casilla junto aDisplay Lightning payment amounts in Satoshis, ya que es más fácil de leer. Un satoshi es la unidad divisible más pequeña de Bitcoin; hay 100 millones de satoshis en un Bitcoin.
💡 El proceso de configuración es similar si utilizas tu propio nodo Lightning. Solo asegúrase de proporcionar la cadena de conexión correcta para la implementación de tu nodo. Si estás ejecutando tu propia instancia de BTCPay Server, viene con un nodo por defecto, por lo que puedes saltarse muchos de estos pasos.
Crear un Punto de Venta (Point of Sale)
Si has llegado a este paso, date una palmadita en la espalda porque la parte aburrida ya terminó. ¡Ahora puedes crear tu Punto de Venta (Point of Sale, PoS) y comenzar a aceptar tu primer pago de Bitcoin a través de BTCPay!
Para crear tu Punto de Venta, - Ve a
Plugins>Point of Sale. - Dale un nombre a tu Punto de Venta y dale aCreate.Cubriremos un par de cosas simples que puede hacer con tu aplicación PoS. Dado que BTCPay tiene muchas funciones, en esta guía solo cubriremos los conceptos básicos para ayudarte a comenzar.
💡 Recuerda que puedes crear múltiples Puntos de Venta dentro de BTCPay Server, cada uno para su uso.
Keypad (Teclado)

Para una demostración sencilla, primero repasaremos el PoS con estilo de teclado.
- Asigna un nombre a tu PoS y un título para mostrar.
- Elige
KeypadenChoose Point of Sale Style. - Presiona
Saveen la esquina superior derecha y luegoViewpara comprobarlo.
Los pagos se recibirán en la billetera LNDhub que configuraste anteriormente. Experimenta generando facturas y las opciones
DiscountyTip. Si tienes un teléfono que lo admite (es decir, no un iPhone), también puedes permitir que tus clientes paguen con tarjetas NFC como BoltCard (consulta nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Genial, ¿no?💡 Puedes guardar el Keypad PoS como una aplicación web progresiva (PWA) en tu teléfono para acceder fácilmente. En la mayoría de los navegadores móviles, esta opción se llama "Instalar aplicación" o "Agregar a la pantalla de inicio".
Lista de productos con cesta (Product list with cart)

También es posible crear una app de Punto de Venta con productos específicos, cada uno con su propio precio. Puedes utilizar esta función para configurar una caja sencilla, un sistema de autopago para el cliente o una tienda web.
- Para crear una nueva aplicación de Punto de Venta, simplemente regresa a la barra lateral y selecciona
Point of Salenuevamente. - Esta vez, en
Choose Point of Sale Style, eligeProduct list with cart. La opción "con cesta" permite al cliente comprar varios artículos a la vez. - Crea tus propios productos o ve directamente a
SaveyViewpara ver los productos de muestra.
Conclusión
En esta guía cubrimos los pasos básicos para comenzar a aceptar Bitcoin en tu negocio usando BTCPay Server. nostr:nprofile1qqs22d4tralncqfnh2kmmarjkxk8449hwnk5xtqe3y5yry6hy7ytegqpzemhxue69uhk2er9dchxummnw3ezumrpdejz7qg7waehxw309ahx7um5wgkhqatz9emk2mrvdaexgetj9ehx2ap0qy88wumn8ghj7mn0wvhxcmmv9uazjdva es un proyecto de código abierto que está en constante evolución. Hay muchas más características y funcionalidades dentro de BTCPay Server que puedes explorar y usar, como la integración de Shopify, el crowdfunding, las divisiones de pagos automáticas y conversión a fiat o altcoins. También puedes personalizar tu tienda a tu gusto con temas, apariencia de pago personalizada, administración de usuarios, notificaciones por correo electrónico y mucho más. Si deseas aprovechar al máximo BTCPay Server, te recomendamos que consideres configurar tu propia instancia de BTCPay Server. Consulta su documentación y videos para obtener más información.
Si aún tienes preguntas y dudas, ¡háznoslo saber! Nos encantaría ayudar a responder cualquier pregunta relacionada.
Bitcoin Txoko es una comunidad abierta. Todos nuestros servicios se financian mediante donaciones y tiempo voluntario. Si esta guía te ha resultado útil, considera unirte a nuestras quedadas o hacer una zap para ayudar a mantener nuestros servidores en funcionamiento. ¡Gracias de antemano!
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ 502ab02a:a2860397
2024-04-24 09:27:28
@ 502ab02a:a2860397
2024-04-24 09:27:28หลายๆครั้งที่เรากินเฮฟวีครีมหรือที่บ้านเราเรียกวิปครีม ไม่หมดแถมใกล้จะหมดอายุแล้วด้วย เราสามารถนำมาเรียนรู้กระบวนการผลิตสิ่งที่เรียกว่า ผลิตภัณฑ์จากนม หรือ Dairy Product ได้ครับ แถมเรายังได้ของไว้ใช้ทำอาหารอีกด้วย นั่นคือ การทำครีมให้เป็นเนย แล้วเอาเนยไปทำกี อีกที งว่ออออออ
ผมจะเล่าสิ่งที่ผมทำเล่นๆเป็นงานอดิเรกให้อ่านกันครับ
ส่วนตัวแล้วผมค่อนข้างหลงไหลใน ไขมันเนย และสนุกในการเรียนรู้มันมานานพอสมควร รวมถึงได้คลุกคลีกับอุตสาหกรรมนม มาตั้งแต่ราวๆปี 2001 ที่น่าสนใจคือ สัดส่วนสารอาหารของไขมันเนย ดีงามตั้งแต่เรื่อง กรดไขมันสายสั้น สัดส่วนที่ลงตัวระหว่างโอเมก้า3:6 รวมถึงมีกลิ่นหอมละมุน
กระบวนการทำเนยนั้น เขาก็จะนำนมมาแยกส่วนที่เป็นครีมออกมา เพื่อปั่นแยกไขมันเนยกับเวย์ ในขั้นตอนการแยกครีมนั้น เราจะได้ **ครีม(นมกับไขมันเนย) และ นมพร่องมันเนย (นมที่มีไขมันเนยต่ำ แน่สิมันไปอยู่ในครีมไง) **
ซึ่งนมพร่องมันเนยนี่ละครับ เป็นกระบวนการเดียวกับที่เขานำไปขายเป็นนมไขมันต่ำ หรือ ไม่ก็เอาไปทำนมผง(สกิมมิลค์) . . . แต่ทำความเข้าใจก่อนนะครับว่า บางโรงงานก็ไม่ได้เอาเศษพวกนี้มาทำของขายเรานะ โรงงานนมผงบางที่ก็เป้นการตั้งไลน์ทำขึ้นมาโดยเฉพาะแล้วได้ by product เป็นครีมแทน
คือมันไม่เหมือนกันระหว่าง ตั้งใจทำครีมออกมาขายแล้วได้หางนมมาทำนมผงนมไขมันต่ำ VS ตั้งใจทำนมผงนมไขมันต่ำมาขายแล้วได้เศษเหลือเป็นครีม
มันเป็นแค่กระบวนการที่คล้ายกันคือ มีการแยกครีมกับนม แต่การตั้งเครื่องไม่เหมือนกัน เขาจะตั้งเอาสิ่งที่ต้องการผลิตเป็นหลัก ที่เหลือมันจึงเป็นแค่ by product
โอเคทีนี้กลับมาเรื่องของเราครับ
**
กระบวนการทำเนยคือ
** การเอาครีมมาปั่นในถังปั่น จนมันเกิดการแยกระหว่างไขมันกับเวย์ เรียกว่าการ churning ตั้งแต่โบราณก็ใช้การปั่น แต่วิธีปั่นมันต่างไปเท่านั้นครับ จากปั่นมือ มาเป็นปั่นเครื่อง รสชาติของเนยก็ขึ้นอยู่กับวิธีทำต่างๆ ตั้งแต่โบราณคือนมดิบ, นมที่มีการ culture หรือ ใส่จุลินทรีย์ไปหมักก่อนจะนำมาปั่น เพื่อกลิ่นและรส ปัจจุบันก็อาจมีการพาสเจอร์ไรส์เพราะบางประเทศบังคับว่าต้องพาสเจอร์ไรส์
วันนี้เรามาดูแบบง่ายๆตามที่บอกไว้ข้างบน เราแค่เอาวิปครีม ใส่โถปั่นแล้วก็ให้มันปั่นไปเรื่อยๆ แค่นี้ก็ได้เนยแล้วครับ สำหรับคนที่ทำขนมน่าจะเคยเจอเหตุการณ์ตีวิปนานเกินไปจนจับก้อนแข็ง ถ้าคุณตีต่อไปอีกนั่นละครับ ไอ้เจ้าครีมแข็งนั้นจะกลายเป็นเนยในที่สุด เอาจริงๆการเหวี่ยงก็ได้นะครับ หลายคนเอาใส่ขวดแล้วเขย่า ใครอยากลองก็ลองได้นะ เมื่อยมือเชียว 5555 พอเราได้ก้อนเนยสดๆแล้ว เราก็เอามาใส่ลงในน้ำเย็นจัด ความเย็นจัดจะทำให้เนยสดๆนี้แข็งตัว แล้วเราก็จะปั้นก้อนปั้นรูปทรงให้เก็บง่ายๆได้ ที่นิยมก็ทรงหมูยอ เพราะตัดใช้ง่ายดีครับ
**เรามาดูคลิปที่ผมเคยทำกันครับ จะเห็นภาพว่า ครีมกลายเป็นเนย มันยังไง ** https://youtu.be/bzo7V9n2cxc?si=PsaldIxgKqpiBXgb
ทีนี้เราก็ได้เนยเอาไว้ใช้เองสบายๆละ ใครที่มีนมดิบอยู่แล้วกลัวกินไม่ทัน ก็มีวิธีเพิ่มนิดนึงครับคือ ใส่โถทรงสูงหน่อย เอานมดิบแช่ตู้เย็นราวๆ 18ชั่วโมงขึ้นไป จนมันเริ่มแยกชั้นกัน ความเย็นจะทำให้ไขมันจับตัว มองแล้วคล้ายหัวกะทิ หางกะทิ แล้วเราก็เลือกตักส่วนข้นๆส้วนจับก้อน เอามาใช้แทนครีม วิธีสังเกตุก็ดูความใสของนมเอาครับ ส่วนไขมันจะข้นๆหน่อย พอเริ่มไขมันน้อยก็จะใสครับ ส่วนที่เหลือที่ใสหน่อย นั่นละครับ นมไขมันต่ำ 55555 เอาไปชงกาแฟหรือดื่มได้ต่อไม่มีปัญหาอะไร
**
ทีนี้ กี (ghee) คืออะไร
** กี คือ เนยใส เป็นที่นิยมในอินเดียมากๆ เขาเอามาใช้เป็นน้ำมันในการทำอาหาร ชงเครื่องดื่ม ได้สารพัดอย่างตามที่น้ำมันจะทำได้ จุดเกิดควันสูง ทำให้เกิดการไหม้ ได้ยากกว่าเนยหลายเท่า
วิธีทำกี ก็ง่ายมากๆ แค่เอาเนยมาตั้งเตาด้วยไฟอ่อนๆ อ่อนมากๆนะครับ เพราะถ้าแรงไปนิดเดียว เนยจะไหม้ทันที เราก็กวนเนยไปเรื่อยๆ ความร้อนอ่อนๆที่ต้มเนยนี้มันคือกระบวนการทำให้น้ำระเหยออกไป จนเริ่มเห็นน้ำมันใสๆ เริ่มเห็นการแยกชั้นอีกครั้งนึง ซึ่งไอ้ที่แยกมานี่ละครับ เราเรียกว่า เนื้อนม หรือ solid milk เท่ากับว่าเราแยกองค์ประกอบของเนยออกไปได้ดังนี้ 1.น้ำระเหยไปในอากาศ 2.เนื้อนมแข็งๆคาอยู่ในหม้อ 3.ไขมันเนยใสๆ คาอยู่ในหม้อ
สิ่งที่เราเอามาใช้ก็คือ ไขมันเนย กรอกใส่ขวดหรือกระปุกก็ตามสะดวกใช้ครับ แช่ตู้เย็นเอาไว้ก็ได้ หรือถ้าใช้บ่อย อยู่นอกตู้เย็นก็ได้พักใหญ่ๆเลย เพราะมันไม่มีอะไรให้เสีย เพียงแค่มันจะซับกลิ่นสภาพแวดล้อมได้เก่งหน่อย
ส่วนเนื้อนมเอาไปคลุกน้ำตาลอร่อยครับ 555555
เรามาดูคลิปการทำกี กันครับ ตัวนี้ผมใช้เนยที่ขายทั่วไปพราะตอนนั้นผมทำการทดลอง ให้คนคีโตเห็นว่า อย่าไปอะไรกับเนยมาก ทุกตัวมีเนื้อนมหมดและเนื้อนมเป็นคาร์บ ที่สำคัญเนยที่คีโตนิยมใช้เหลือเนื้อนมมากกว่าเนยที่ราคาถูกกว่าอีก เพราะเนื้อนมคือตัวที่ทำให้เนยมีความละมุนลิ้น ส่วนไขมันเนยคือตัวที่ส่งกลิ่นหอมๆ ลองไปดูคลิปกันครับ
https://youtu.be/HFvvIjhZ6h0?si=KkqoZFN3Mx1lTTul
ทีนี้ของแถม ที่บอกว่าต้มกี ต้องระวังไหม้ จำได้ใช่ไหมครับ ในสายเบเกอรี่ เรามีสิ่งที่เรียกว่า บราวบัทเตอร์ (brown butter) คือการเล่นเสี่ยงอย่างนึงคือ ต้มกี ให้เกินจุดพอดี แต่ไม่เกินไปจนไหม้ เราจะได้เนยใสสีน้ำตาลอ่อน มีกลิ่นหอมคาราเมล ตัวนี้นิยมใช้ทำขนมเพิ่มกลิ่นหอมกว่าการใช้เนยปกติหลายเท่า แถมเป็นกลิ่นหอมหวาน ที่ทำให้ขนมไฮโซขึ้นมาก เอาไปชงกาแฟก็หอมครับผมทำบ่อย
siamstr #pirateketo
-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ c69b71dc:426ba763
2024-04-21 17:45:44
@ c69b71dc:426ba763
2024-04-21 17:45:44Chef's notes
This vegan mozzarella recipe consists of cashews, psyllium husks flour and delicious spices. Of course it doesn't taste like the "original". Nutritional yeast is essential in this recipe as they give the plant-based cheese alternative a cheesy taste. You need a good, powerful blender.
Details
- ⏲️ Prep time: 10 min. (start preparing the day before)
- 🍳 Cook time: 0
- 🍽️ Servings: 4
Ingredients
- 270 ml Water
- 2 tbsp Psyllium husk (flour or flakes)
- 100 g Cashews soaked in water for at least 4 hours or over night
- 4 tbsp nutritional yeast
- 1/2 Juice of lemon
- 1/2 tsp Salt
- 1/2 tsp Pepper
- 1/2 tsp Garlic powder
Directions
- Soak the cashews in water for at least 4 hours - preferably overnight - and drain
- Place the cashews as well as the water, lemon juice, yeast flakes and spices in a blender and blend until smooth
- Add the psyllium husk and blend again until you get a cheesy consistency. It goes quite quickly!
- Place the cheese mixture in a bowl and let it solidify in the refrigerator for at least two hours - preferably overnight.
- Finally, turn the cheese out onto a plate and cut into pieces. It can be a bit sticky, but thats fine.
- Serve with tomatoes and drizzle with olive oil and balsamic vinegar (Aceto Balsamico). Decorate with basil leaves or any sprouts and microgreens.
-
 @ 3d599bf6:a0122cef
2024-04-24 09:26:09
@ 3d599bf6:a0122cef
2024-04-24 09:26:09This is just a test article.
-
 @ 218ad6cd:4c654231
2024-04-16 16:11:44
@ 218ad6cd:4c654231
2024-04-16 16:11:44 -
 @ 1d22e00c:50e00d0e
2024-04-24 04:26:44
@ 1d22e00c:50e00d0e
2024-04-24 04:26:44Hey everyone and welcome to Refinery Life Australia.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, The Poverty That Possesses.
Text
Matthew 5:3 NKJV
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
Scripture Reading
2 Corinthians 8:1-9 NKJV
Excel in Giving
1 Moreover, brethren, we make known to you the grace of God bestowed on the churches of Macedonia:
2 that in a great trial of affliction the abundance of their joy and their deep poverty abounded in the riches of their liberality.
3 For I bear witness that according to their ability, yes, and beyond their ability, they were freely willing,
4 imploring us with much urgency [a]that we would receive the gift and the fellowship of the ministering to the saints.
5 And not only as we had hoped, but they first gave themselves to the Lord, and then to us by the will of God.
6 So we urged Titus, that as he had begun, so he would also complete this grace in you as well.
7 But as you abound in everything—in faith, in speech, in knowledge, in all diligence, and in your love for us—see that you abound in this grace also.
Christ Our Pattern
8 I speak not by commandment, but I am testing the sincerity of your love by the diligence of others.
9 For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Introduction.
The person who is truly poor in spirit is blessed because such poverty enables that person to possess the supreme possession of all, “the kingdom of heaven.”
For our sakes, Jesus set the example in 2 Corinthians 8:9, For you know the grace of our Lord Jesus Christ, that though He was rich, yet for your sakes He became poor, that you through His poverty might become rich.
Poverty of spirit is the first character trait Jesus wants in His followers, the subjects of His kingdom.
It is a trait that carries its own reward, “theirs is the kingdom of heaven.”
Note the tenses here carefully, “Blessed are the poor in spirit,” not “have been,” or “ shall be,” but “are.”
Two questions about his beatitude call for an answer.
- What is poverty of spirit?
Jesus said that the ones who are poor in spirit are blessed.
How so?
What does He mean?
Let’s consider the answer from two points of view.
Firstly negatively.
Poverty of spirit does not mean poverty of possessions.
It is true that earthly poverty does sometimes produce conditions in which Christian virtues might thrive.
It is also true that the Bible warns us against “the cares of this world and the deceitfulness of riches” because of their power to distract us from the desire for heaven’s treasure.
But happiness is a matter of character, not conditions.
It issues from the rightness of our hearts, the relationships of our lives, and not from external conditions.
A person may be a millionaire and yet be poor in spirit.
Someone could be penniless but also proud and arrogant.
Poverty of spirit does not mean poverty of native endowment.
No life was ever richer that Jesus’ life, yet He was poor in spirit.
Poverty of spirit does not mean poverty of spiritual life in the sense of being feeble and neutral in our life.
Jesus came to bring the abundant life.
He had patience with those of little faith, those weak in spirit, and those impetuous in actions.
But He wanted to help them grow, to be of great faith, to be of strong convictions.
Poverty of spirit does not mean pretension of humility.
Some are great at self depreciation.
Jesus had no patience with the sort of person that is always saying “I am nothing and nobody and not worth your attention.”
Often deep down in their hearts, they are desirous of people knowing them in the marketplace and being the proudest of the proud.
The pride that apes humility is more detestable than the pride that casts of all disguise.
The second point of view is the positive.
What then is this poverty of spirit that Jesus called blessed?
Poverty of spirit is that quality of spirit that accurately perceives that man, as he is, has no virtue inherent in himself, that each gift and each grace of the spirit comes from God.
When we see how completely dispossessed of virtue and grace and righteousness we are in ourselves, pride, self esteem, and self righteousness must fall away.
Then we see how rebellious against God and His righteousness our wills have been, we want to cry our with Paul, “Wretched man that I am!” (Romans 7:24)
Poverty of spirit is the realisation that spiritually we are dispossessed, bankrupt, and without merit of our own.
Poverty of spirit is that quality of spirit that recognises that, apart from God, man is forever incomplete, and that the true centre of life is God.
The world has little time and no admiration at all for such a person.
Rather, it admires the self sufficient man, the self confident man, the so called self made man, the man who feels he is complete within himself.
The Greek philosopher Plato, discussing the good man, the happy man, places one condition upon him, he must be self sufficient.
Can you imagine standing before the Lord and expecting to enter heaven but also saying you were self sufficient?
Poverty of spirit is that quality of spirit that intensely desires that God will supply the true needs of the soul.
Jesus told a story of “two men” who “went up to the temple to pray.”
One, a Pharisee, did not actually pray.
Instead, he gave God a recital of his qualities and virtues.
He was self righteous, self satisfied.
This is exactly what poverty of spirit is not.
The other man, a publican, was so conscious of his need, so full of the sense of his own shortcomings, he would not even lift his head.
Yet, so desirous was he of God’s blessings that he cried out, “God be merciful to me a sinner.”
This is poverty of spirit.
2. How does this poverty of spirit bless us?
In what sense is it true that the poor in spirit are happy in the blessings of possessing the kingdom?
Here are five links in a chain that must not be broken.
Poverty of spirit causes us to seek in Christ the grace we need.
We need not mere conviction of sin, for conviction does not always lead to repentance and conversion.
Poverty of spirit is that appraisal of our lack on the one hand and of our sins on the other that cause a person to seek salvation.
Poverty of spirit conditions us for receiving the gift of God.
All of the prophets have realised this.
Isaiah said in Isaiah 57:15, For thus says the High and Lofty One Who inhabits eternity, whose name is Holy: “I dwell in the high and holy place, With him who has a contrite and humble spirit, To revive the spirit of the humble, And to revive the heart of the contrite ones.
David said in Psalm 51:17, The sacrifices of God are a broken spirit, A broken and a contrite heart— These, O God, You will not despise.
Poverty of spirit releases the saving grace of God upon us.
This is our only hope.
This is effective only when we empty our hearts of self and throw ourselves like broken vessels on His mercy.
Poverty of spirit fits us for service in the kingdom.
God loves to use the life that keeps self out of sight and honours only Him.
Poverty of spirit opens the eyes of the heart on the broad horizons of heavens possessions.
The vision says, “You are a child of the king. These things are yours.”
Conclusion.
Let’s test ourselves.
Let each of us ask, “Am I poor in spirit, or am I self satisfied, self righteous, and arrogant?”
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ a012dc82:6458a70d
2024-04-21 12:55:49
@ a012dc82:6458a70d
2024-04-21 12:55:49Join Richard from Motiv as he shares insights into how the Motiv project is revolutionising humanitarian aid in Peru through the integration of Bitcoin. Discover how the project's Christian values drive its mission to empower individuals financially while fostering self-growth within communities. Explore success stories illustrating the financial empowerment achieved through Bitcoin and the project's dedication to social activism. Learn about Motiv's innovative approach to self-sustainability and how readers can support their mission. This interview was conducted on the Croxroad podcast, a platform dedicated to highlighting inspiring stories of innovation and social impact. Get inspired by Motiv's journey and learn how you can contribute to making a difference in Peru and beyond. For more information, support, and to get involved, don't miss the Contact Information and Support section, along with insightful FAQs to address any queries. Experience the transformative power of Bitcoin in driving self-growth and positive change in communities worldwide.
Table of Contents
-
Introduction to Motiv Project
-
Integration of Bitcoin
-
Financial Empowerment Through Bitcoin
-
Christian Values and Humanitarian Aid
-
Contact Information and Support
-
Conclusion
-
FAQs
Introduction to Motiv Project
The Motiv Project is a pioneering initiative dedicated to transforming lives and fostering self-growth in Peru through innovative approaches to humanitarian aid. Founded on Christian values and driven by a passion for social activism, Motiv is committed to empowering individuals and communities, particularly in impoverished regions, to achieve financial independence and sustainable growth.
At the heart of the Motiv Project is the integration of Bitcoin, a revolutionary digital currency, as a tool for financial empowerment. By leveraging the benefits of Bitcoin, Motiv aims to provide individuals with access to secure and efficient financial services, free from the constraints of traditional banking systems. Through education and support, Motiv equips individuals with the knowledge and resources needed to harness the potential of Bitcoin for their own economic advancement.
Through various programs and initiatives, Motiv facilitates entrepreneurship, vocational training, and economic development, empowering individuals to build thriving businesses and improve their quality of life. By fostering a culture of self-reliance and resilience, Motiv empowers communities to break free from cycles of poverty and dependence, paving the way for long-term growth and prosperity.
With a focus on grassroots initiatives and community-driven solutions, the Motiv Project is making a tangible impact on the lives of thousands of individuals across Peru. Through collaboration with local partners and organisations, Motiv is creating a ripple effect of positive change, inspiring hope and opportunity where it is needed most. Join us in supporting the Motiv Project and become part of a movement dedicated to driving sustainable development and self-growth in Peru and beyond.
Integration of Bitcoin
The integration of Bitcoin within the Motiv project marks a transformative approach to humanitarian aid in Peru. Bitcoin, a decentralised digital currency, serves as a foundational tool for empowering individuals and communities economically. Motiv has embraced Bitcoin as a means to provide financial autonomy and stability to marginalised populations, enabling them to transcend the limitations of traditional banking systems.
Through the integration of Bitcoin, Motiv offers a novel solution to the challenges faced by underprivileged communities in Peru. By leveraging the secure and transparent nature of blockchain technology, Motiv facilitates seamless transactions and financial empowerment. This integration enables individuals to access financial services without relying on conventional banking infrastructure, which may be inaccessible or unreliable in remote areas.
Moreover, Bitcoin integration fosters economic resilience by mitigating the risks associated with inflation and economic instability. Individuals participating in the Motiv project can safeguard their financial assets through Bitcoin, preserving their purchasing power and building long-term wealth.
The integration of Bitcoin also aligns with Motiv's mission to promote innovation and inclusivity in humanitarian efforts. By harnessing the potential of cryptocurrency, Motiv empowers individuals to take control of their financial futures and break free from cycles of poverty. This forward-thinking approach not only addresses immediate financial needs but also lays the groundwork for sustainable development and self-sufficiency.
Overall, the integration of Bitcoin within the Motiv project represents a paradigm shift in humanitarian aid, ushering in a new era of financial empowerment and opportunity for underserved communities in Peru.
Financial Empowerment Through Bitcoin
Financial empowerment through Bitcoin is at the heart of Motiv's transformative efforts in Peru. By embracing cryptocurrency as a vehicle for economic progress, Motiv empowers individuals and communities to take control of their financial destinies. Through Bitcoin, participants gain access to a secure and transparent financial system that transcends the limitations of traditional banking infrastructure.
Bitcoin serves as a catalyst for financial inclusion, enabling individuals in underserved areas to participate in the global economy. Motiv provides education and resources to help community members understand and leverage Bitcoin effectively, thereby fostering economic resilience and independence. Participants are equipped with the knowledge and tools to send, receive, and store Bitcoin securely, empowering them to navigate financial transactions with confidence.
Furthermore, Bitcoin offers a hedge against inflation and economic volatility, providing a stable store of value amidst uncertain economic conditions. By diversifying their financial holdings with Bitcoin, individuals can protect their wealth and preserve their purchasing power over time. This financial security enables them to weather economic downturns and pursue opportunities for growth and prosperity.
Motiv's focus on financial empowerment through Bitcoin extends beyond individual benefits to drive broader societal change. By fostering a culture of financial literacy and self-reliance, Motiv lays the groundwork for sustainable development and poverty alleviation in Peru. Through education, training, and access to Bitcoin, Motiv empowers individuals to build brighter futures for themselves and their communities.
Christian Values and Humanitarian Aid
Christian values are deeply embedded in Motiv's humanitarian efforts in Peru. Rooted in compassion and service, Motiv's approach to aid reflects the principles of love, generosity, and solidarity espoused in the Christian faith. Central to Motiv's mission is the belief in the inherent dignity and worth of every individual, regardless of their circumstances.
Through its humanitarian aid initiatives, Motiv seeks to uplift the most vulnerable members of society, providing them with tangible support and resources to improve their lives. Motiv's commitment to Christian values drives its focus on addressing not just the immediate needs of communities, but also the underlying systemic issues that perpetuate poverty and inequality.
Moreover, Motiv recognizes the importance of empowering individuals to become agents of change within their own communities. By instilling Christian values such as compassion, empathy, and stewardship, Motiv equips individuals with the mindset and skills to serve others and effect positive social change.
In addition to providing material assistance, Motiv also offers spiritual support and guidance to those in need. Through prayer, counselling, and fellowship, Motiv seeks to nurture the spiritual well-being of individuals and foster a sense of hope and resilience in the face of adversity.
Overall, Motiv's humanitarian aid efforts are guided by Christian values of love, compassion, and service. By embodying these principles in its work, Motiv not only meets the immediate needs of communities but also strives to create a more just, compassionate, and equitable society for all.
Contact Information and Support
For those seeking to connect with Motiv and support their impactful work in Peru, various channels are available for contact and assistance. Individuals interested in learning more about Motiv's projects, volunteering opportunities, or ways to contribute can visit the organisation's official website at Motiv.ngo. Here, comprehensive information about Motiv's initiatives, team members, and mission can be found.
Additionally, Motiv can be reached via email at info@Motiv.ngo for inquiries, partnership proposals, or general support. The team at Motiv is responsive and welcomes correspondence from individuals, organisations, and potential collaborators who share their commitment to humanitarian aid and community development.
For those active on social media platforms, following Motiv's accounts provides another avenue for engagement and support. Motiv maintains a presence on Twitter under the handle @Motivngoglobal, where updates, news, and stories about their work are regularly shared. Furthermore, Motiv is launching an innovative initiative called TravelSats, where individuals can book tours with select tourism companies, with a portion of the proceeds directly supporting Motiv's programs. By participating in these tours, individuals not only have the opportunity to explore exciting destinations but also contribute to meaningful social impact projects in Peru.
Conclusion
In conclusion, Motiv's endeavours in Peru exemplify the transformative potential of Bitcoin in fostering self-reliance and community empowerment. Through innovative programs and a steadfast commitment to financial inclusion, Motiv is revolutionising traditional aid models, emphasising dignity, and sustainability. By integrating Christian values with humanitarian aid, Motiv embodies a holistic approach to social impact, prioritising both material assistance and spiritual upliftment. With accessible contact information and diverse avenues for support, Motiv invites individuals worldwide to join their mission of catalysing positive change and fostering resilience in communities across Peru. Together, through collaboration and compassion, Motiv and its supporters are shaping a brighter, more equitable future for all.
FAQs
How does Motiv integrate Bitcoin into its humanitarian efforts? Motiv utilises Bitcoin as a financial tool to empower individuals in Peru, providing them with access to secure and efficient means of storing value and conducting transactions. Through Bitcoin, Motiv facilitates economic independence and fosters financial inclusion among marginalised communities.
How can I support Motiv's initiatives in Peru? You can support Motiv's initiatives by donating through their website or participating in their travel program, TravelSats, where a portion of the proceeds goes towards supporting their programs in Peru. Additionally, you can follow Motiv on social media to stay updated on their projects and spread awareness about their work.
How does Motiv uphold Christian values while providing humanitarian aid? While Motiv operates based on Christian principles, it does not impose religious beliefs on the communities it serves. Instead, Motiv focuses on delivering practical assistance and empowerment programs that align with Christian values of compassion, justice, and dignity for all. By embodying these values in their humanitarian efforts, Motiv seeks to uplift individuals and communities regardless of their religious background.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8947a945:9bfcf626
2024-04-21 02:56:46
@ 8947a945:9bfcf626
2024-04-21 02:56:46September 2009
In 2009 it was my last year in medical school. I was assigned to be a medical student at a primary hospital in a rural area in the province of Chachoengsao. I did my medical practice under supervision of senior doctors.
Living and working at that hospital was easy. I had my own private doctor room to live in , and lots of cheap good food around in the morning while the hospital prepared lunch and dinner everyday.
By that time I was looking for a nearby Catholic church to attend a mass and found one in a website of the Bangkok diocese and the information was outdated and left unattended.
If you had ever heard of the yellow pages , that was what the information of the church looked like. The details were very short and useless. The phone number was outdated
I had to guess which way to go for that time google map wasn't on our hands like the present day.
Imagine what happened in 2009
You drove a car 10 kilometres away from your home , venturing deep into the forest where you had never been before was quite challenging. Furthermore in Thailand , the 3G phone mobile data wasn’t settled yet. So I had no online navigation at all.
Along the way , there were gradually transition between a forest and a field into small rural community with a church signs. That was a relief at least I didn't have to sleep in the middle of the forest that night.
These 2 pictures were what you saw along your way to do your quest finding a church.


In the middle of the forest , the serene catholic church stood in the middle of this forest.



You are surrounded by a forest , green trees everywhere around you. Birds tweeting. Serenity




The priest house at the backyard

Interior of the church is simple decorated

Shot taken from the back
The main altar

 The statues of St.Anne and Mother Mary. Thai words mean “St.Anne , pray for us”
The statues of St.Anne and Mother Mary. Thai words mean “St.Anne , pray for us”My first car parked at the back of the church

Photo taking equipment - IPhone 3Gs
-
 @ 218ad6cd:4c654231
2024-04-16 16:11:37
@ 218ad6cd:4c654231
2024-04-16 16:11:37U2FsdGVkX1+mAAGrxMzsloq4Dlq/awWkW5Y+s0CsCvX5TyZsT1L88VRJxnUqHBk4fpXyjgUcV77cdcRKJ1Zurvr//4PNQdcOVcJUqMzSfNiFSdJvgNU2Wlhb9PjKsUNiHAGxet0PvIoUDxlFaGLK08WF/0W10hVWVb0JzJV5QdGM8r5qU4FOOSMDjvdZ5UAsuHjQ9YMvR/aO34/001WWUk7rX6t3Pye1yVt2VGDgz+zrfWAv+Sm2rT1lNRwIOALXBCEMBmgrBaJfd8iCQEo712UNmeKehjsEt7AZOgUoab2VF1prhIl5LyeKlkKBAO9lIimWo4z3TrM6Krxi/rg6P5XGZWOuhfB4ocGskw61m7ZEb0e4ba6BVaD6XU3idtY9sXWd9MaHAJEC9l3DO2Ky88e5xjEl3NUbyXtVkQRJNNJE8XOhaQtc1EF+CBEKi16oqp/XPgQuA0RRGfDQfBXe5E5z+jTZ0Hp6tDV9jESWO0lsPKWNYFJ6ec8p5opbWC7bQ6jolf9g9Ht+563VsMyE4Y3ng5YfDc14i5DjspIYwUrtjkit+7EfezGqlcMw3s38CcEW8xA85ztbBL4ZRQKpUEz/4de1eivg108zq0rfyzxNtLw83inRPAXZQqyLncjHjCVtyyqMehSRetVVN9hMOkJOmqqNExo9WQg8XNZMaOrRCcdUr+jeQnpkfS/cPyamxdnEKxW7K7AHBfm5FTXEJ0y/U+1H+iSMrJZ+0kI75lF5eHEqtKGBgzfNk5/Qz2ZED8u9D34XlmTNCNwIsmRCv144ZZmAzJcJ6YQ13UNxj+WeyOrOne0y8fgiNQJMcxyAG1OnQEVzf8AkBjul7Tcb9zpw8HCXMuN3QUmcrI/dA6bauNfw4dwzkihFH5ziUyt1FaKf+1mw1CraPdoWAdsfqjq+jUbScx5XUVIf2aabED8o/ARooYYwqwtJ2fV4AYIbCIV+NwEN5JA1juLATqjJpHecwCRwEyYikK7tryBOS2t6aTBu40ENFF3vIJXAS3L7lZFdLjlE/RU6YwG8t4LA85c3AafRBKzTfaQciEfaDuSgn4maJYQJmQbl44k1lH84s+hAfThbNM74aRB2B2+GNeaxrFXmsZf92JFB0sQMYsNiZGzJywBRftwGDP2hO3A/W2E9aludfMNImr4qVe2Kjg==
-
 @ 8947a945:9bfcf626
2024-04-21 02:29:57
@ 8947a945:9bfcf626
2024-04-21 02:29:57กันยายน 2552
เป็นปีสุดท้ายสำหรับการเป็นนักศึกษาแพทย์ ผมถูกส่งให้ไปฝึกงานที่โรงพยาบาลชุมชนแห่งหนึ่งในจังหวัดฉะเชิงเทรา ภายใต้การดูแลของแพทย์รุ่นพี่และอาจารย์แพทย์ประจำโรงพยาบาลแห่งนั้น
ชีวิตความเป็นอยู่ช่วงนั้นเรียบง่าย ไม่ต้องดิ้นรนอะไรมาก ผมมีบ้านพักส่วนตัวอยู่ภายในตัวโรงพยาบาล ทุกๆเช้ามีตลาดนัดตอนเช้าตั้งอยู่ข้างๆอาคารผู้ป่วยนอก มีของกินดีๆราคาถูกๆให้เลือกมากมาย ส่วนมื้อเที่ยงและมื้อเย็นหมดห่วงเพราะทางโรงพยาบาลจัดเตรียมไว้ให้
เวลานั้นผมนับถือคาทอลิค ต้องหาโบสถ์เข้าร่วมพิธีมิซซาบูชาขอบพระคุณในวันอาทิตย์ การหาข้อมูลไม่ง่าย ต้องดุ่มๆหาในเวบไซต์ของสังฆมณฑลกรุงเทพ หาไปหามาก็ไปเจอชื่อโบสถ์ "นักบุญอันนา สระไม้แดง " แต่ที่อยู่และวิธีการเดินทางไม่มีบอกเอาไว้
ถ้าใครเกิดทันสมุดหน้าเหลือง (YellowPages) นั่นแหละครับช้อมูลอย่างเดียวที่ผมมีในมือ แถมเบอร์โทรศัพท์ของโบสถ์ก็ไม่ได้อัพเดทอีก
ลองนึกภาพตามนะครับเมื่อปี 2552
ประเทศไทยยังไม่มีระบบ 3G เลย ส่วน google maps ก็พึ่งถูกพัฒนาขึ้นมาแถวๆปี 2548 ไม่ได้พร้อมใช้งานเมื่อไหร่ก็ได้เหมือนปัจจุบัน
ผมต้องอาศัยความกล้าในการขับรถออกจากบ้านพักในโรงพยาบาล ซึ่งเหมือนสถานที่ปลอดภัยมากๆสำหรับผมที่มาอยู่ต่างถิ่น ไม่รู้จักใครเลย วิ่งเข้าถนนใหญ่ซักพักนึงไม่มีชุมชนข้างทางเหลือ มีแต่ป่า
เส้นทางเข้าโบสถ์ก็คือถนนที่ตัดเข้ากลางป่าไปเลย ระยะทางประมาณ 9 กิโลจากโรงพยาบาล แต่ก็เป็นอะไรที่ตื่นเต้นมาก ขับรถคนเดียวในต่างแดน
แถมรถคันแรกของผมก็เป็นรถมือสองที่มีปัญหาไดสตาร์ทงอแงอีก ถ้าขับความเร็วไม่เกิน 80 km/hr มันจะไม่เกิดปัญหา แต่ถ้าเกิดวันไหนรีบๆ อัดความเร็วขึ้นทะลุ 100 km/hr แล้วจอดรถ ดับเครื่อง ลงไปทำธุระแล้วกลับมาสตาร์ทรถจะมีลุ้นว่ารถจะสตาร์ทติดหรือไม่ติด
ช่างที่อู่ซ่อมรถเขาบอกว่าไดสตาร์ทมันค้าง วิธีเอาตัวรอดก็คือต้องหาท่อนเหล็กมาเคาะ แล้วสตาร์ทรถ วัดดวงกับมันไปเรื่อยๆ ซ่อมมาหลายรอบก็แก้ไม่หาย ลองเอาเข้าศูนย์บริหารมาตรฐานแล้วก็ไม่รอด
ตอนนั้นผมก็กลัวครับ เกิดซวยเข้าขั้น ขับรถถึงโบสถ์แล้วเกิดรถดับอีกนี่สงสัยได้นอนในป่า
เมื่อขับรถไปเรื่อยๆ ก็เริ่มเห้นชุมชนสระไม้แดง เห็นป้ายบอกทาง เห็นป้ายโบสถ์ตอนนั้นใจชื้นแล้วครับ ว่าอย่างน้อยก็ขับรถมามั่วๆแล้วถูกทางละกัน


2 ฝั่งข้างทางก็จะเห็นวิวประมาณนี้ไปตลอดทาง ลมเย็นครับ ตอนนั้นเป็นช่วงเดือนกันยายนพอดี
กลางป่า มีโบสถ์คาทอลิคอันเงียบสงบตั้งอยู่ รายล้อมไปด้วยธรรมชาติสีเขียว เสียงนกร้อง แสงแดดอ่อนๆ กลิ่นไอดิน เสียงหญ้าสดสลับกับเสียงหญ้าแห้งเวลาเดินเข้าหาตัวโบสถ์แต่ละก้าว พลังงานความศักดิ์สิทธิ์ไม่ธรรมดา



เมื่อมองไปรอบๆตัวโบสถ์คือถูกล้อมด้วยธรรมชาติกลางป่ากลางทุ่งนา




บ้านพักพระสงฆ์(บาทหลวง) ด้านหลังตัวโบสถ์

ภายในตัวโบสถ์ตกแต่งเรียบง่าย แต่สวยงามสง่า รูปปั้นนักบุญอันนาและพระแม่มารีย์

ถ่ายจากด้านหลังสุดตัวโบสถ์
พระแท่นหลักของตัวโบสถ์


นี่คือรถคันแรกของผมสมัยนั้นครับ

Honda civic 3 doors ค่าตัว 120,000 บาทถ้วน รับมาอยู่ด้วยตั้งแต่ผมเข้ามหาวิทยาลัยปี 1 เมื่อปี 2547 ขายคืนเต๊นท์รถเมื่อปี 2554 ราคา 90,000 บาท ก่อนที่จะได้โตโยต้าวีออสปี 2004 จากพ่อตาของผมมาเป็นของขวัญวันหมั้นกับภรรยาครับ
อุปกรณ์ถ่ายภาพ - IPhone 3Gs
เกร็ดเล็กเกร็ดน้อย
นักบุญยอแซฟและนักบุญอันนา คือบิดามารดาของพระแม่มารีย์ผู้ที่เป็นพระมารดาของพระเยซูเจ้าครับ เป็นท่านตาท่านยายของพระเยซูนั่นเองครับ
ที่โบสถ์แห่งนี้ถึงจะมีบ้านพักบาทหลวงอยู่ แต่ไม่มีคนอยู่ตลอด คุณพ่อท่านจะขับรถจากโบสถ์อีกแห่งหนึ่งซึ่งท่านพำนักอยู่ ห่างออกไป 10 - 20 กิโลเมตร วิ่งรถข้ามอำเภอมาเพื่อประกอบพิธีมิซซาให้กับชาวบ้านในชุมชนแห่งนี้ วันอาทิตย์มีแน่ๆหนึ่งรอบ แต่วันอื่นๆ ผมไม่ทราบข้อมูลครับ
ถ้าใครจะมาเที่ยวมาเยี่ยมชม แนะนำให้ติดต่อหาข้อมูลก่อนนะครับ เพราะวันที่ผมเดินไปทางสำรวจ ตัวโบสถ์ล็อคเข้าไม่ได้ รูปถ่ายที่ถ่ายมาได้เป็นวันอาทิตย์หลังพิธีมิซซาเสร็จสิ้น ชาวบ้านและคุณพ่อแยกย้ายกันกลับหมดแล้ว
หวังว่าจะชอบนะครับ กับซีรีส์ใหม่ของผม RK photos - photo story telling blog รูปถ่ายเล่าเรื่อง ไว้เจอกันใหม่คราวหน้า สวัสดีครับ
-
 @ d8a2c33f:76611e0c
2024-02-26 03:10:36
@ d8a2c33f:76611e0c
2024-02-26 03:10:36Let's start with definitions:
Cashu - Cashu is a free and open-source Chaumian ecash system built for Bitcoin. Cashu offers near-perfect privacy for users of custodial Bitcoin applications. Nobody needs to know who you are, how much funds you have, and who you transact with. - more info here https://cashu.space/
Cashu-adress - it is a protocol that runs on top of cashu mints. More info here: https://docs.cashu-address.com/
Npub.cash - service that runs on top of cashu-address protocol. Let's you use your npub@npub.cash as a lightning address to receive zaps or incoming sats. More info here https://npub.cash/
Pay to public key - Like bitcoin you can cashu tokens are bearer assets and can be locked to a public key. This means only the person who has the private key can use that token.
What do you use it for? - Use your npub cash as your lightning address replacement.
Why? I believe everyone knows what a lightning address is. Lightning address is usually provided by your wallet provider who also runs their lightning node. E.g. if you have @alby.com lightning address then you already have an account setup with alby and using their lightning node to get your sats. With npub.cash you can simply put your npubaddress@npub.cash without registering first or signing up. And you can keep this forever even while changing your lightning wallet from alby to any other provider or running your own lightning node.
Npub.cash locks the received tokens into your nostr public key (Still work in progress) so that only the owner of Nostr public key who has the private key can claim the token and push it to their wallet of choice.
Benefits Over Traditional Custodial Lightning Addresses:
Privacy: With Cashu-Address, your financial activities are not visible to your custodian. This added layer of privacy ensures that your transactions remain your own.
Flexibility in Custodian Selection: Unlike traditional Lightning Addresses, Cashu-Address allows you to choose your custodian freely. If your needs change, you can switch your custodian anytime without hassle.
No User Exclusion: Custodians cannot exclude individual users. Because mints do know know which user eCash belongs to, they can not censor certain users. How to claim your username@npub.cash - This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash
How to claim your username@npub.cash- This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash . This is onetime and you can use this address forever..!
Frequently asked Questions:
-
What connect string to use to login with NIP-46 on iOS. - try setting up an account at https://use.nsec.app/home . This is still WIP. If it does not work, just try the Nostr extension using laptop browser
-
Is there a notification when I receive sats/zaps? Not yet. We are working on it. However, just go to npub.cash every couple of days to sweep your collected sats to your wallet
-
Which cashu wallet to use? Use enuts (android & ios) https://www.enuts.cash/ or minibits.cash for android https://www.minibits.cash/
-
Will anyone be able to claim my sats? NO. When you start the claim process you need to sign with your Nostr extenstion signer to claim sats. So only the person controlling the private key to the npub can claim sats.
-
I really struggle to understand the flow of what happened concretely. - Don't break your head. the devs got you covered. Also, this is super new and everyone is trying to get their heads around. Just follow instructions, play with it and ask for help.
- Is it non-custodial? - When we lock your sats to your pubkey we cannot spend it. However locking to pubkey is not enabled until wallets can start supporting them.
- How do I ask for help? - just post #asknpub.cash and post your questions. We will get to you.
- Who are the devs behind this? @calle (Master of Cashu) @egge (Core dev) @starbuilder (dev support)
Here's what everyone is talking about #npub.cash on Nostr
nostr:nevent1qvzqqqqqqypzqx78pgq53vlnzmdr8l3u38eru0n3438lnxqz0mr39wg9e5j0dfq3qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsxcwntv9d342ashe5yvyv0fg40wm873jaszt6d2u0209vqz5gkcdq6avwyr
nostr:nevent1qvzqqqqqqypzq5qzedy85msr57qayz6dz9dlcr5k40mcqtvm5nhyn466qgc6p4kcqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsvek7d8v4lddrmj2mynegsnrc4r4gnmswkddm02qzenwuc7x9perctaedre
nostr:nevent1qvzqqqqqqypzpfpqfrt75fhfcd4x0d0lyek9pzyz4zwmudh0vq7vn3njvvngsmpjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsqgyjwfsgr80xmha8x2wwd4klzsxcagmlpk3wsfyyvqnlvzn2rcvnhu534kj5
nostr:nevent1qvzqqqqqqypzp3yw98cykjpvcqw2r7003jrwlqcccpv7p6f4xg63vtcgpunwznq3qyfhwumn8ghj7mmxve3ksctfdch8qatz9uq36amnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdshsqg8v5hfgmwangecpejcw22fm4uk2s438p8ahpu5l985wserctr0h6gysle9m
nostr:nevent1qvzqqqqqqypzp6y2dy0f3kvc0jty2gwl7cqztas8qqmc5jrerqxuhw622qnc2pq3qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tm0venxx6rpd9hzuur4vghsqgx68ujht0r9qqqp4l27u0x27sg4p5l2ks0xd9kxm9w2vkjhppttlur0et6k
-
-
 @ 000002de:c05780a7
2024-04-24 03:52:38
@ 000002de:c05780a7
2024-04-24 03:52:38 -
 @ 4f9e11e2:9ab6c0cc
2024-04-15 11:48:25
@ 4f9e11e2:9ab6c0cc
2024-04-15 11:48:25Opinion about the city of Seattle
Markdown Test
This is a bold text.
This is an italic text.
- Item 1
- Item 2
- Subitem A
- Subitem B
Here's a link to Nostr.
Here's an image:

Inline
codecan be indicated using backticks.python def greet(): print("Hello, world!")This is a blockquote.
Horizontal Rule
Header 1 | Header 2 -------- | -------- Cell 1 | Cell 2*
myCloneOfTripadvisor #askNostr #nostrOpinion
Join the conversation!\n\nJust Testing ...
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ bcea2b98:7ccef3c9
2024-04-14 14:27:30
@ bcea2b98:7ccef3c9
2024-04-14 14:27:30I grew up on a farm in Minnesota in the 1970s. Life was all about hard work and family. We learned the value of getting our hands dirty early on, helping out with chores from sunup to sundown.
Farming taught me the importance of perseverance. Some years, the weather was on our side, and the crops flourished. Other years, we faced setbacks, like droughts or pests. But we never gave up. We'd find ways to adapt and keep the farm going.
Our community was tight-knit. During busy times, neighbors pitched in without hesitation. We'd come together for barn raisings or help each other out with harvesting. It was all about supporting one another.
Growing up, we didn't have fancy gadgets or social media. Our entertainment was exploring the fields and forests, using our imagination to create adventures. We learned to appreciate the simple things in life and the importance of face-to-face connections.
Nowadays, things have changed. Technology rules the world, and young people are glued to their screens. But deep down, I think we still share some of the same values. We all want to make a difference and leave the world a better place.
-
 @ 6ad3e2a3:c90b7740
2024-04-12 23:42:51
@ 6ad3e2a3:c90b7740
2024-04-12 23:42:51After unsuccessfully trying to orange-pill* a friend the other day, I realized the problem: for a lot of successful, worldly people the notion you can get something for nothing is anathema. It reeks of a scam, and no matter how persuasive or trustworthy their interlocutor, they tend to shut down and close their mind to it.
*To “orange-pill” means to get someone to buy — or at least see the value proposition of — bitcoin.
Put differently, smart people understand risk and reward are inseparable. If someone is telling you this is the opportunity of a lifetime, it probably isn’t. To the extent it has the upside purported, its risk of ruin is no doubt commensurate.
But that is only the case when there is information symmetry. If I tell you the stock market is going to the moon next year, you know there are smart people on the other side of that bet, or else it would be at the moon already. And because they have access to the same information I do, any large way-out-of-the-money call option on the S&P500 is at grave risk of not cashing in. Hence you would be wise to ignore my advice.
But what about when one party to the trade has information the other lacks? For example, Nancy Pelosi has a net worth north of $100 million on her comparatively meager congressional salary, due in large part to trading on insider information. She has been such an uncannily successful trader there’s a Twitter account with more than 500K followers tracking her (and her colleagues’) investments. Surely in the case of her trades, the risk was not commensurate with the rewards.
Another obvious example from history was the Dutch buying the island of Manhattan from the natives for a bunch of tools and beads. The risk and reward to the Dutch were not remotely commensurate due to information asymmetry.
All the time, people cultivate expertise in pricing antiques, collectibles and other items that give them a significant advantage over most market participants and sever the strict relationship between risk and reward that exists in more information-symmetrical environments.
But what all three of those scenarios have in common is the information providing the advantage is essentially a secret. The natives presumably didn’t know how common and easily replaced the tools and trinkets for which they traded Manhattan were. The public doesn’t have access to the information on which Congress is trading. And the layperson lacks the in-depth, niche knowledge of the expert art or antiques dealer.
But the Bitcoin-for-dollars trade happens to be asymmetrical, despite the information being wholly public and hidden in plain sight. The asymmetry comes from one party being sufficiently naive and curious and the other too savvy and close-minded. As a result, many who got into Bitcoin earliest were financial outsiders, novices, nerds and cypherpunks rather than Wall-Street professionals who are accustomed to getting the jump.
The media, gatekept and controlled by the same factions who run the banking system, have only exacerbated this asymmetry, spreading unfounded fear, uncertainty and doubt about bitcoin specifically (It boils the oceans! It’s backed by nothing!) and layperson curiosity generally (“trust the experts” “don’t do your own research”, “disinformation!”) As a result, not only are the professional insiders out, but also those who rely on their expertise to assess investment opportunities, which is why many of the savviest and smartest people are ironically the most difficult to convince.
. . .
Maybe this is what's meant by “The meek shall inherit the earth,” if we use curious and open-minded to stand in for “meek.” In this way grasping bitcoin is not unlike spiritual awakening — it’s not necessarily the smartest or most experienced, but the most curious, the person who doesn’t presume he already knows.
-
 @ ec965405:63996966
2024-02-15 01:06:05
@ ec965405:63996966
2024-02-15 01:06:05I am beginning to see the clarity that my mentors promised I would as I progressed through my late 20s into my 30s, and it's getting clearer every day. I am inspired to change the world and bring my community with me. I know God has my back. A better world is within our grasp! I'm going to do my part in bringing my community with me by blogging about my upcoming trip to Cuba with Solidarity Collective via Nostr.
In February I'll be back in the skies headed to Havana, where I will participate in a delegation with Solidarity Collective to learn about Pan Africanism in the Cuban context. Some questions we will be exploring during this delegation are:
How do Cubans, in a Black-majority country, approach environmental protection, religion, housing rights, and healthcare?
What is the role of historic and contemporary abolitionist practices in their quest to eradicate racism?
What challenges remain to build an equitable society, especially under the yoke of 60 years of the u.s. Blockade?
What do these lessons mean for the struggle for black liberation in the u.s.?

I've dreamed about the next time I would visit Cuba and how I would track down the friends I made there in 2017. At that time, the government controlled access to internet via these cards that you would purchase then redeem on your device for timed access. The idea was that you would take your Wi-Fi card and head to a communal place like La Plaza with your device to access the Internet with others.
While some north americans might find that kind of Internet access draconian, surfing the web in public like that made me value my time on the Internet more. Has this changed since I was last there? I am personally interested in how groups are leveraging tech and the Internet for education and organizing. I now have a solid couple of years of IT/programming education to reference while I meet with teachers and journalists at the Martin Luther King Jr. Center and hear about the right to free education from daycare through university and literacy campaigns. I wonder if they've heard about decentralized social media protocols like Nostr or Activitypub or if they ever experienced censorship from the authorities on the Internet.
I recently experienced censorship in the YouTube comments as I explained to fellow web surfers why we must include Vieques and the other islands in the archipelago when talking about Puerto Rico politically. My ability to comment was restricted as I tried to convince others who talked down on Haiti and Cuba as failed states to instead take my Pan Caribbean perspective. I really enjoyed Dread's talk at Nostrasia 2023 about how he is using Bitcoin and Nostr to bring the islands together as the US Dollar and financial institutions like Western Union and the IMF keep us divided and oppressed.
The more I learn about Bitcoin as a tool for global wealth distribution, the more I understand how these institutions rob youth and families of basic necessities and facilitate the rise of authoritarian regimes and systems that punish journalists and activists through political repression. The corporate ownership of our means of internet communication by the likes of technocrats like Musk and Zuckerberg won't let authentic conversation between Caribbean-based diaspora happen on their platforms while they get to destroy countries like Myanmar and shape public discourse to their whim. That's why I'm glad I found Nostr.
My personal blog currently lives on my Uberspace asteroid in a Bludit instance that lacks much functionality outside of themes and data analytics, so it's just sits there as a personal repo for my thoughts. Nostr provides all of this with a direct link to my Bitcoin wallet address and comment functionality. If people value my content, I can get "zapped" and earn money for my content. I can now engage with my audience directly without a middle man. No Substack, no moderators censoring my messages, just community. The job now is to bridge my community and this new way of socializing on the Internet.
To help make this as educational of an experience as possible, I ask my audience: What questions or feedback do you have about my trip and the types of questions I want to explore? Is there anything you've ever wondered about Cuba? What suggestions do you have in terms of how I can better present information; written word, audio interviews, video, or photo essays?
Leave me some love in the comments and stay tuned!

-
 @ 9edd72eb:cb697b0a
2024-04-20 17:29:38
@ 9edd72eb:cb697b0a
2024-04-20 17:29:38Opinion about Unstoppable Crypto Wallet (Android)
One of the strong points of this wallet is its security protocols that use advanced encryption methods and multi-factor authentication to protect user information.
The interface is intuitive which can be useful for novice and experienced users. Navigation is simple and easily accessible.
The wallet supports a diverse range of cryptocurrencies, including popular and lesser-known tokens.
It guarantees complete control of private keys and funds, emphasizing ownership and autonomy.
The platform enhances utilization, allowing users to manage their crypto assets across multiple devices, both smartphones and desktops.
On the other hand, it lacks customization options.
The lack of integrated fiat currency support might inconvenience users who frequently engage in fiat-to-crypto transactions.
Limited customer support channels and documentation could leave users stranded in case of technical difficulties or questions.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 75bf2353:e1bfa895
2024-04-20 16:04:40
@ 75bf2353:e1bfa895
2024-04-20 16:04:40My Favorite Nostr Clients
Favorite Social Media Client.
https://www.nostrapps.com/apps/amethyst
Favorite Video Client
 https://www.nostrapps.com/apps/flare
https://www.nostrapps.com/apps/flareFavorite Meet Up Client
 https://www.nostrapps.com/apps/flockstr
https://www.nostrapps.com/apps/flockstrFavorite Podcast & Music Client
https://www.nostrapps.com/apps/fountain
Favorite Blogging Client
 https://www.nostrapps.com/apps/habla
https://www.nostrapps.com/apps/hablaFavorite Patreon Alternative
https://www.nostrapps.com/apps/highlighter
Favorite Venmo Alternative
 https://www.nostrapps.com/apps/mutiny
https://www.nostrapps.com/apps/mutinyFavorite eBay Alternative
 https://www.nostrapps.com/apps/shopstr
https://www.nostrapps.com/apps/shopstrFavorite File Hosting
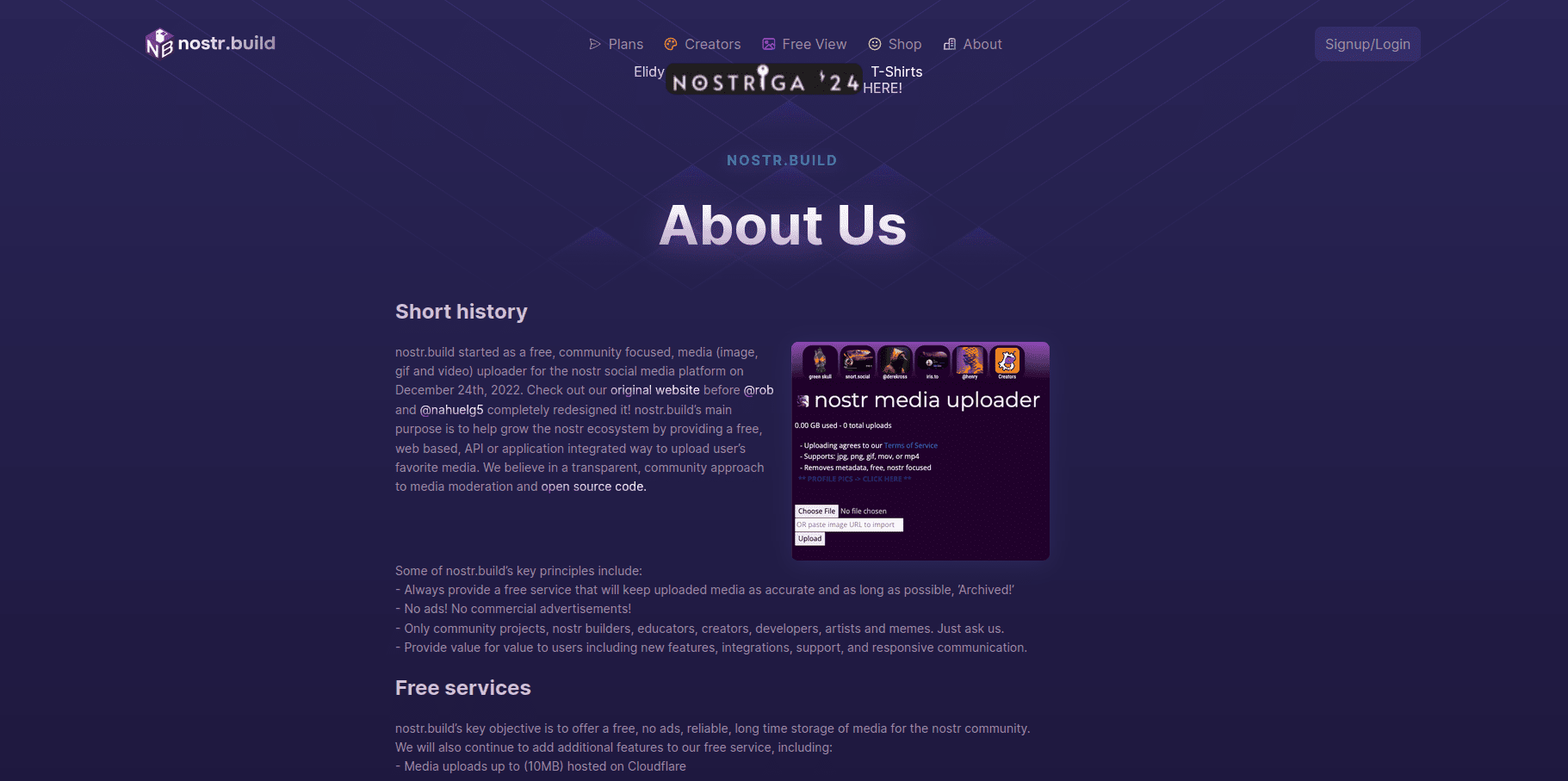
https://nostr.build
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ 1d22e00c:50e00d0e
2024-04-24 03:19:03
@ 1d22e00c:50e00d0e
2024-04-24 03:19:03Hey everyone and welcome to Refinery Life Australia.
The Inward Attitudes of a True Disciple is our theme for the next few weeks.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
Today we are discussing, Questions about the Beatitudes.
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Text
Matthew 5:2 NKJV
2 Then He opened His mouth and taught them, saying:
Scripture Reading
Matthew 5:1-12 NKJV
The Beatitudes
1 And seeing the multitudes, He went up on a mountain, and when He was seated His disciples came to Him.
2 Then He opened His mouth and taught them, saying:
3 “Blessed are the poor in spirit, For theirs is the kingdom of heaven.
4 Blessed are those who mourn, For they shall be comforted.
5 Blessed are the meek, For they shall inherit the [a]earth.
6 Blessed are those who hunger and thirst for righteousness, For they shall be filled.
7 Blessed are the merciful, For they shall obtain mercy.
8 Blessed are the pure in heart, For they shall see God.
9 Blessed are the peacemakers, For they shall be called sons of God.
10 Blessed are those who are persecuted for righteousness’ sake, For theirs is the kingdom of heaven.
11 Blessed are you when they revile and persecute you, and say all kinds of evil against you falsely for My sake.
12 Rejoice and be exceedingly glad, for great is your reward in heaven, for so they persecuted the prophets who were before you.
Introduction.
Perhaps no sayings of Jesus are more familiar but less understood by the average Christian than the Beatitudes.
Most congregations could be classified as belonging to on for three groups on the basis of their attitudes toward the Beatitudes.
In one group there are those whose attitude is, Come to think of it, I don’t know what they mean. I’ve never tried to learn, and I don’t care.
Not many of this group come to church.
In a second group there are those whose attitude is, I have thought about the Beatitudes. I have wished I could have these qualities in my life, but this quest is not for me.
These ideals are too high. I cannot attain them.
A large percentage of the average congregation would fall into this group.
In a third group are those whose attitude is, The Beatitudes are idealistic.
Only Jesus ever exhibited them perfectly. Being meek and merciful and pure in heart are qualities we’ll have in heaven, but they aren’t for now.
Not so!
The Beatitudes are for the here and now.
If Jesus had not wanted these qualities to be exhibited in our lives until we get to heaven, He would have waited until then to tell us.
- ** What about the Beatitudes?**
What is the correct attitude toward these sayings of Jesus?
Consider three questions about them taken as a unity.
What are the Beatitudes?
The beatitudes are plain, simple statements of fact or truth, not promises of reward.
Jesus did not say that if a person is “poor in Spirit,” He will give him the kingdom in order to make him happy.
The poor in Spirit are happy “for theirs is the kingdom of heaven.”
Jesus did not give gifts to make us happy.
He creates conditions within us that enable us to find happiness everywhere.
Jesus gives people a character that radiates happiness regardless of outward circumstances.
The Beatitudes describe not seven different classes of people, but seven different character traits, or elements of Christian excellence, in one individual.
Who is a Christian?
A subject of the kingdom.
Jesus is here describing what He came to create in the subjects of His kingdom.
The whole Sermon on the Mount treats the character and conduct of the kingdom, those who become Christians.
Here at the very outset we have the character Christ desires and requires of His followers stated in these seven characteristics.
These traits do not exclude one another but are mutually dependant.
Those who are meek also need to be merciful, those who are merciful also need to be pure in heart.
2. What do the Beatitudes teach?
The beatitudes teach Christ’s doctrine of the kingdom.
The multitudes in Jesus’ day, for lack of knowledge, degraded and materialised the teachings of the coming kingdom.
They believed the kingdom of God to be a perpetual banquet where they would eat rich food and make merry.
The more privileged classes were not more spiritual than the masses.
They thought of the coming kingdom as a political revolution when the hated Romans would be overthrown.
The Beatitudes and the Sermon on the Mount as a whole were a flat contradiction of both of these misconceptions.
They ought, rather, that the kingdom is a spiritual realm that is not of this world, though in it.
The kingdom of heaven is wherever the laws of heaven rule in the hearts of people.
When Jesus spoke of His kingdom, He was speaking from a level of spiritual elevation into the blessedness of which He would lead mankind.
The Beatitudes teach Christ’s doctrine of happiness.
In this the Beatitudes cut straight across the ideas of the world.
Who are the happy people?
If carnal man were to draw up a list of Beatitudes, they would go something like this: “Blessed are the rich, the famous, the well born, the cultured, those who live in ease and luxury.”
But not so Christ!
People look to outward circumstances for happiness, Christ looks to character.
Happiness is decided not by what we have but by what we are.
Happiness is never dependant on outward conditions but always on an inward spirit.
Therefore, Jesus said, “Blessed are the poor in spirit, they that mourn, the meek, the merciful, the pure in heart.”
All of these are inward qualities of heart and not outward circumstances.
3. How may we profit from a series of studies on the beatitudes?
Studying this perfect picture of Christian Character, we will be able to see ourselves as we are.
By this standard, we will be able to take stock, to see how far short we fall.
Are we poor in spirit, meek, merciful, pure in heart, peace makers?
We are not, but why not?
Studying this perfect picture of Christian character, we may see ourselves as we could be, as Christ intended us to be.
Seeing this, let us “press toward the goal, and move onto perfection!”
Studying this perfect picture Christian character, we may be challenged to make some progress toward bridging the gap between what we are and what we ought to become.
Conclusion.
For the next eight Sunday’s, we will look at the Beatitudes.
Seven of these are found in Matthew 5:3-9.
The eighth, an often forgotten but authentic beatitude of Jesus is found in Acts 20:35.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 682558c5:bfa011f2
2024-04-20 15:00:30
@ 682558c5:bfa011f2
2024-04-20 15:00:30Please stop regurgitating the censorship tropes.
There is an ontological "beingness" of Bitcoin, and it's money-related.
Any use case that's not a Store of Value, Unit of Account, or Medium of Exchange is fundamentally flawed.
Yes, Bitcoin is permissionless money. But the money aspect is inseparable.
An acorn has the beingness of an oak tree. You might even go so far as to extend that beyond its life to include lumber or something crafted from lumber.
But an acorn does NOT have the beingness of a porcelain toilet to store shit.
The Downfall of Shitcoins.
Please stop repeating the straw man that anyone cheering the government-backed downfall of shitcoins is antithetical to the spirit of Bitcoin.
Shitcoins are an affinity scam. And they're NOT decentralized like Bitcoin.
We will cheer the downfall of shitcoins no matter how it comes. That makes us pragmatists, not government simps.
For some, it will be hard to believe, but even anarchists can use the power of government against itself or others - to be left the hell alone. We work with what we're given.
No Moral Dilemma is Required.
Shitcoins exist to extract value from others.
There's a carve-out in the non-aggression principle to not tolerate fraud or breach of contract.
Con artists and snake oil salesmen don't need to be tolerated in some twisted liberty-purity test.
Mental Gymnastics
The LoLbertarian purity tests ARE the mental gymnastics, the intellectual laziness to repeat sound bytes of fallacy.
Thinking through what Bitcoin and shitcoins are is the antidote. See past shitcoin marketing. See past their uSe CaSeS and their emotional attacks on anyone who opposes them.
This isn't a value judgment. This is understanding the core essence of something.
F Your Feelings.
Existence is independent of our perception or feelings. Bitcoin and shitcoins simply are what they are.
When we put down the parroted catch phrases of others, we can begin to think through what they truly are.
It's Bitcoin, not shitcoins. No, not even shitcoins ON Bitcoin. The timechain is a ledger for financial records. It's not a database for content or shitcoins. Stop attacking the people who see clearly. Your emperor has no clothes.
-
 @ 1f9e547c:8af216ed
2024-04-24 02:50:57
@ 1f9e547c:8af216ed
2024-04-24 02:50:57Opinion about Binance: Buy Bitcoin & Crypto (android)
Binance is one of the more popular cryptocurrency exchanges in the Philippines - it is currently under regulatory uncertainty.
Philippine government orders Google Play and Apple Store to remove Binance App. Source: CNBC
As of 2024-04-24 The app is still available via Google Play.
A copy of the SEC (Philippines) order.
This is to inform the public that the online cryptocurrency exchange BINANCE is NOT AUTHORIZED TO SELL or OFFER SECURITIES to the public in the Philippines. Based on the reports and information gathered by the Commission, BINANCE has been actively employing promotional campaigns on various social media platforms to attract and entice Filipinos to engage in investment and trading activities using its platforms.
In view thereof, the public is hereby advised to exercise caution before investing in these kinds of unregistered online investment platforms and their representatives. In dealing with these unregistered platforms, the Commission reiterates its Advisory entitled: “Advisory against Dealing with Non-Registered Foreign Entities, Organizations, and Corporations”.
In addition, those who act as salesmen, brokers, dealers or agents, representatives, promoters, recruiters, influencers, endorsers, and enablers of the BINANCE platform in selling or convincing people to invest in this platform within the Philippines even through online means may be held criminally liable under Section 28 of the SRC and be penalized with a maximum fine of Five Million Pesos (P 5,000,000.00) or imprisonment of Twenty One (21) years or both pursuant to Section 73 of the SRC (SEC vs. Oudine Santos G.R. No. 195542, 19 March 2014).
For the guidance of the public. Makati City, 28 November 2023.
As of April 24, 2024, these are the list of countries where Binance is banned:
- Canada
- Afghanistan
- Japan
- India
- Vietnam
- Germany
- Iran
- Bangladesh
- Kazakhstan
- Italy
- Belgium
- Malaysia
- China
- Thailand
- United Kingdom
- France
- Philippines
Curiously, in the United States, there are states where Binance claims that users can sign up (Information as of March 6, 2024, Source: Binance Site):
- Alaska
- American Samoa
- Hawaii
- Maine
- New York
- Northern Mariana Islands
- Texas
- U.S. Virgin Islands
- Vermont
February 23, 2024 - Judge Approves Binance’s $4.3 Billion Settlement For Anti-Money Laundering, Sanctions Violations Forbes.com
WalletScrutiny #nostrOpinion
-
 @ 0d6c8388:46488a33
2024-02-02 01:15:40
@ 0d6c8388:46488a33
2024-02-02 01:15:40I'm just a normal guy that likes Jesus and bitcoin!
Here are some things you should know about me:
Well that's all for now hope you have a good day!
-
 @ 6ad3e2a3:c90b7740
2024-01-29 20:45:19
@ 6ad3e2a3:c90b7740
2024-01-29 20:45:19“God does not play dice. “
Albert Einstein
Imagine you’re at the blackjack table, you’re dealt a 10 and a 7 (hard 17), and the dealer shows a 10. This is a bad situation, but the odds say you stand and hope the dealer busts. You are about to do just that, but the drunk guy on your right says, “Hit, bro, I’m feeling a four.”
What are the odds this is good advice?
I’m too lazy to look up the exact odds, but let’s just invent some very rough approximations to illustrate the point.
Assume there’s a 50 percent chance you will lose no matter what you do, i.e., it makes no difference whether you hit or stand. That means there’s a 50 percent chance you win (or push) assuming you make the right choice. Let’s further assume if you stand, there’s a 30 percent chance you win (or push), and if you hit there’s a 20 percent chance you win or push. Again, please don’t quibble about the true odds in this situation, as it’s unimportant for the example.
With these odds, what are the chances hitting on hard 17 against a 10 is good advice?
Let’s make it multiple choice:
A) 20% (That’s your chance to win)
B) 0% (It’s always wrong to hit when your odds of winning are better if you stand)
C) 40% (To the extent your decision matters, it’s 2 out of 5 (20% out of 50%) that hitting will win you the hand.)
In my view, A) is the simple response, and it’s not terrible. It recognizes there’s some chance hitting in that situation gives you the desired outcome even if it’s not the optimal choice. It’s probabilistic thinking, which is the correct approach in games of chance, but just slightly misapplied.
B) is the worst response in my opinion. It’s refusing to apply probabilistic thinking in service of a dogma about probabilistic thinking! “It’s always wrong to hit in that situation” is an absolutist position when of course hitting sometimes yields the desired result. The “but my process was good” adherents love B. It signals their devotion to the rule behind the decision (the process) and avoids addressing the likelihood of whether the decision itself pans out in reality.
C) This is in my view the correct answer. To the extent your decision matters, there’s a 40 percent chance hitting will improve your outcome and a 60 percent chance it will not. I’m not looking for self-help or a remedial grade-school probability class. I don’t need to remind myself of what the best process is — I simply want to know my odds of winning money on this particular hand.
Let’s say it’s a low-stakes hand, you’re drunk, you take the advice for laughs, the next card is in fact a four, you have 21, the dealer flips over a 10 and has 20. You win, and you would have lost had you stayed. You high-five the drunk. What are the odds now you got good advice?
A) 0% — bad process!
B) 40% — same odds, don’t be result-oriented!
C) 100% — you already won!
The answer is obviously C. The point of the game is to win money, and taking his advice* on that particular hand did just that for you. You are not obligated to use that heuristic ever again. This isn’t a self-improvement seminar about creating better, more sustainable habits. You won the money, and now that you know what the next card actually was, it would be pathological to go back in time and not take his advice.
*You might think this is just a semantic argument — what we mean by “good advice” depends on whether it’s applied generally or specifically, and that is the distinction, but as we will see below the conflation of the general with the specific is itself the heart of the problem.
I use blackjack as the example because, assuming an infinite shoe (no card counting), the values of each card in each situation are well known. Coins, dice and cards are where simple probabilistic thinking functions best, where the assumptions we make are reliable and fixed. But even deep in this territory, it’s simple to illustrate how a focus on process is not a magic cloak by which one can hide from real-life results. If you lose the money, you lose the money. The casino does not allow you to plead “but my process was good!” to get a refund.
Of course, this one-off example aside, in the territory of cards and coins, the process of choosing the highest winning probability action, applied over time, will yield better results than listening to the drunk. But when we move out of this territory into complex systems, then the “but my process was good” plea is no longer simply falling on the deaf ears of the pit boss when reality goes against you, but those of the warden at the insane asylum.
. . .
I’ve encountered a similar strain of thinking on NFL analytics Twitter too. Sports analytics involve probabilistic thinking, but as leagues and teams are complex systems, it’s hardly as simple as coins and cards.
When Giants GM Dave Gettleman passed on Sam Darnold — the highest rated quarterback remaining on many boards — at pick 2 in the 2018 draft, and took generational running back prospect Saquon Barkley instead, the process people were aghast. How could you take a low-value position like running back over the highest value one when your team needs a quarterback? You always take the quarterback!
As a Giants fan, I was happy with the pick. My view was the same as Gettleman’s in this instance when he said something to the effect of, “If you have to talk yourself into a particular quarterback at that pick, pass.” His point was that he’d have taken a quarterback he liked there obviously, but he didn’t like the remaining ones, so he went elsewhere.
Now people were especially aghast he took a running back rather than say Bradley Chubb, an edge rusher, or Denzel Ward a cornerback, two typically higher value positions than running back, and those would have been good picks too, as both players have been productive in the NFL**. But Barkley has been as advertised when healthy, despite playing with a substandard supporting cast his entire career. He’s a good player, though a star running back obviously won’t singlehandedly transform a franchise the way a star quarterback might.
** The optimal pick would have been quarterback Josh Allen who went at No. 7, but was considered a reach by many in the analytics community because he was a raw prospect with physical skills, but lacked sufficient college production.
But how did the process choice, Sam Darnold, do? He was a disaster for the Jets for three seasons, destroying any hope they might have had at competing, though they salvaged some value by dealing him to the Panthers for picks. He’s also been bad on the Panthers, to date. So did Gettleman make a good choice, drafting one of the consensus top running back prospects of all time over the not-especially-impressive top-two quarterback prospect in that particular class? By any sane account, he did. He landed the better player, and while Chubb and Ward would have been fine, so was Barkley.
But despite Darnold’s failure as a prospect, the process people won’t take the L! They insist even though Barkley is a good running back, and Darnold a terrible quarterback, their process in preferring Darnold was good! But I don’t care about your process! The quality of your process will be adjudicated by your long-term results, the way a religious person’s moral character will be judged by his God. I have no interest in your attestations and signaling, no inclination to evaluate your lifelong body of work. We were simply debating this one particular pick, the results of which are already obvious to anyone not steeped in this bizarre worldview wherein you can claim vindication over reality a priori via believing you’ve found the right heuristic!
There are two claims they are making implicitly here: (1) That if quarterbacks are more valuable generally, you should always take the best available quarterback over the best available running back, irrespective of the particular human beings at issue; and (2) That no matter what the results were, you would be correct to have taken the quarterback.
Claim (1) is the notion that if something is generally — or on average — the case, the specifics need not be taken into account, i.e., they see players as having static values, based on their positions, like cards in blackjack. Claim (2) is the idea that only the heuristic should be evaluated, never the outcome. Taken together they are saying, always do what is generically most probable, ignore details and specifics and have zero regard for how any particular decision pans out in reality. In my view, this is pathological, but that’s okay, it’s only an argument about football draft analytics!
. . .
Our public health response to the covid pandemic increasingly appears to be a disaster. From lockdowns, to school closures, to vaccine mandates to discouraging people from getting early treatment, it has cost many lives, harmed children, wreaked havoc on the economy and done serious damage to our trust in institutions. Many of those who were skeptical of the narrative — for which they were slandered, fired from jobs and deplatformed — have proven prescient and wise.
While some holdouts pretend the covid measures were largely successful, most people — even those once in favor of the measures — now acknowledge the reality: the authors of The Great Barrington Declaration, which advocated for protecting only the vulnerable and not disrupting all of society, were correct. But I am starting to see the same demented logic that declared Darnold a better pick than Barkley emerge even in regard to our covid response.
Here’s a clip of Sam Harris insisting that even though Covid wasn’t as deadly as he had thought, he would have been right if it had been more deadly. (Jimmy Dore does a great job of highlighting the pathology):
Harris is arguing that even if the outcome of our response has been catastrophic, that’s just results-oriented thinking! He still believes he was staying on 17, so to speak, that he made the right call probabilistically and that he was simply unlucky. (Never mind that locking down healthy people was never part of our traditional pandemic response playbook, and coerced medicine is in plain violation of the Nuremberg Code, i.e., he wasn’t advocating for blackjack by the book, and never mind that in highly complex systems no one can calculate the true odds the way you can for a casino game or even an NFL draft pick.)
But Sam Harris was far from the only one. Here’s Dilbert creator Scott Adams explaining why even though he made a mistake in taking the mRNA shot, his process was not to blame:
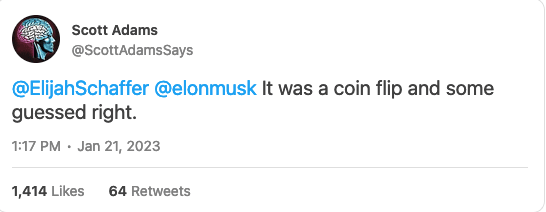
He’s not defending his process as strongly as Harris, and he appeared to walk this back in this video, but the sentiment is largely the same: There was nothing wrong with my process, I just got unlucky, and others got lucky.
This is not an NFL analytics argument anymore — it’s a worldview shared by policymakers and powerful actors whose decisions have major consequences for human beings around the world. They seem to believe that as long as they come up with the correct heuristic (according to their own estimations and modeled after simplistic games of chance where it can be known in advance what heuristic was indeed better), whatever they do is justified. If reality doesn’t go the way they had expected, they still believe they acted correctly because when they simulated 100 pandemics their approach was optimal in 57 of them!
But the notion that someone with the correct heuristics, i.e., the proper model or framework for viewing the world as a game of dice, is a priori infallible is not only absurd, it’s perilous. Misplaced confidence, unwarranted certainty and being surrounded by peers who believe as you do that no matter what happens in reality, you can do no wrong incentivizes catastrophic risks no sane person would take if he had to bear the consequences of his misjudgment.
What started as a life hack to achieve better long term results — “focus on process, not outcomes” — has now become a religion of sorts, but not the kind that leads to tolerance, peace and reverence for creation, but the opposite. It’s a hubristic cult that takes as its God naive linear thinking, over-simplified probabilistic modeling and square-peg-round-holes it into complex domains without conscience.
If only this style of thinking were confined to a few aberrant psychopaths, we might laugh and hope none of them become the next David Koresh. Unfortunately this mode of understanding and acting on the world is the predominant one, and we see its pathology play out at scale virtually everywhere we look.
-
 @ d0b327c6:1ae748c2
2024-04-12 07:28:31
@ d0b327c6:1ae748c2
2024-04-12 07:28:31Tradotto dall’originale di Tom Honzik & Stephen Hall - pubblicato su Unchained
Se volete eliminare il rischio di custodia dai vostri bitcoin, dovete adottare l'autocustodia. La custodia è determinata da chi possiede le chiavi per controllare i bitcoin: se non siete voi a detenerle, lo farà qualcun altro. Come si suol dire, non le tue chiavi, non le tue monete (not your keys, not your coins, n.d.t.).
Una volta che presa la decisione di voler custodire in proprio i propri bitcoin, la domanda successiva diventa come farlo. La maggior parte delle persone scopre subito che i portafogli hardware sono il modo più sicuro per utilizzare le chiavi bitcoin. Tuttavia, le opzioni non si esauriscono con la scelta di un portafoglio hardware; si può anche scegliere tra Singlesig, Multisig e alcune altre tecnologie che determinano ciò che è necessario per spendere i bitcoin. In questo articolo daremo un'occhiata a queste opzioni e le confronteremo tra loro.
Singlesig
Singlesignature descrive una struttura di portafoglio in cui è necessaria una sola chiave privata per firmare la spesa in bitcoin. È il metodo più antico e basilare per detenere bitcoin. Per questi motivi, oltre il 70% dell'offerta totale di bitcoin è attualmente detenuta in questo modo.
Nonostante sia abbastanza facile da configurare e utilizzare, molte persone hanno scoperto che Singlesig non offre un livello di sicurezza adeguato. Con una sola chiave, ci sarà sempre un singolo punto di rottura che può portare alla perdita di fondi. Ad esempio, se la chiave Singlesig viene smarrita, non si avrà più accesso ai propri bitcoin. Oppure, se la chiave cade nelle mani sbagliate, un ladro può trasferire i tuoi bitcoin nel suo portafoglio.
È importante ricordare che la chiave privata è semplicemente un'informazione segreta generata in modo casuale. Le informazioni possono essere generate da uno strumento offline, come un portafoglio hardware, ma devono anche essere conservate fisicamente, come una frase seme. Ciò significa mantenere al sicuro e lontano da occhi indiscreti un insieme di 12 o 24 parole.
Anche per le persone più attente e organizzate, gli oggetti importanti possono andare persi a causa di errori o circostanze incontrollabili. Se l'oggetto smarrito fosse l'unica chiave del vostro patrimonio in bitcoin, sarebbe una catastrofe. Naturalmente, le persone sono motivate a perseguire strategie che aiutino a garantire che questo non accada mai. Esploriamo alcuni degli approcci più diffusi!
Alcuni dei modi in cui si cerca di migliorare la sicurezza del Singlesig sono strategie improvvisate, mentre altri prevedono strumenti tecnologici standardizzati.
Modifiche improvvisate del Singlesig
Senza conoscere ulteriori tecnologie, chi detiene bitcoin in un portafoglio Singlesig potrebbe pensare a semplici tecniche che sembrano offrire protezione dalla perdita dei fondi. Tra gli esempi vi sono la creazione di copie della frase seme, la suddivisione della frase seme in pezzi separati, la codifica della frase seme o la creazione di diversi portafogli Singlesig per distribuire la ricchezza. Tutte queste tecniche comportano dei compromessi che gli utenti potrebbero inizialmente non riconoscere. Ora le illustreremo brevemente e in modo più dettagliato.
Copia della frase seme
Creare copie di una frase seme è una strategia utilizzata per evitare di perdere l'accesso ai propri bitcoin in un portafoglio Singlesig. Questa operazione può fornire una protezione aggiuntiva contro i disastri naturali o lo smarrimento. Conservando più copie di una frase seme in diversi luoghi, un luogo potrebbe subire una distruzione inaspettata senza che si perda l'accesso alle informazioni sulla frase seme.

Un portafoglio hardware con due copie di backup della frase seme.
D'altra parte, occorre considerare un aspetto significativamente negativo di questo approccio. Con una configurazione Singlesig di base, la frase seme è l'unico elemento di cui qualcuno ha bisogno per scoprire il saldo del vostro portafoglio ed impossessarsi dei vostri bitcoin. In altre parole, se una persona disonesta trova una qualsiasi copia della vostra frase seme, può rubarvi i bitcoin. Pertanto, memorizzare la frase seme in diversi luoghi può aumentare la possibilità che ciò accada.
Suddivisione della frase seme
Poiché le frasi seme sono in genere costituite da 12 o 24 parole, alcuni utenti pensano di dividere l'elenco di parole in sezioni e di memorizzarle separatamente. Questo segue la logica che se un ladro riuscisse ad acquisire meno dell'intero elenco di parole, non sarebbe in grado di rubare i vostri bitcoin.

Un portafoglio hardware con la sua frase seme divisa in più parti.
Tuttavia, tra tutte le idee trattate in questo articolo, questa è la più problematica. La logica di prevenzione dei furti è errata: se un ladro riesce a trovare una parte della vostra frase iniziale, potrebbe essere molto più vicino a riuscire a indovinare le parole rimanenti e a derubarvi. Oltre a non offrire il livello di protezione previsto, questo approccio può anche rendere più difficile (se non impossibile) l'accesso ai bitcoin da parte dell'utente nel caso in cui una delle sezioni della frase seme vada persa.
Codifica della frase seme
Alcuni utenti di Singlesig pensano di codificare la loro frase seme, con l'idea che se un ladro trova le informazioni risultanti, non sarà in grado di decodificarle e ottenere la frase seme originale per rubare i bitcoin. Ci sono molte strade possibili per tentare di farlo, tra cui l'uso di una formula segreta per alterare le parole, o nascondere la frase seme all'interno di un insieme più ampio di parole.

Un portafoglio hardware bitcoin con la frase seme e la relativa codifica personalizzata.
Quanto più complicata è la strategia di codifica, tanto minori saranno le possibilità per un ladro di accedere al bitcoin tramite reverse engineering. Ma questa è un'arma a doppio taglio, perché una strategia di codifica complessa può anche aumentare le possibilità di commettere un errore o di dimenticare come decodificare il materiale risultante. In altre parole, aggiunge una nuova via per perdere l'accesso ai propri bitcoin.
Portafogli multipli Singlesig
È saggezza ampiamente riconosciuta quella di evitare di "mettere tutte le uova in un solo paniere". Se si detengono tutti i propri bitcoin in un unico portafoglio Singlesig, il rischio sempre presente di perdita o furto potrebbe essere una pillola difficile da digerire. Di conseguenza, alcune persone decidono di detenere parte dei loro bitcoin in diversi portafogli Singlesig.

Due portafogli hardware con le relative frasi seme.
Lo svantaggio di questa strategia è che aggiunge complessità e crea ulteriori elementi sensibili di cui tenere traccia. Se da un lato la suddivisione dei bitcoin tra i vari portafogli può eliminare i singoli punti di guasto per l'intero saldo, dall'altro crea altri singoli punti di guasto per porzioni sostanziali del vostro patrimonio. Ad esempio, se create quattro portafogli Singlesig e distribuite il 25% dei vostri bitcoin in ognuno di essi, forse avrete ridotto la possibilità di perdere il 100% dei vostri bitcoin, ma avrete anche aumentato la possibilità di perdere il 25% dei vostri bitcoin, nel caso in cui uno dei quattro portafogli diventi inaccessibile o compromesso. Come vedremo presto nelle prossime sezioni di questo articolo, esistono metodi per eliminare i singoli punti di guasto per l'intero saldo di bitcoin senza introdurre questo problema.
Modifiche standardizzate del Singlesig
Oltre ad alcuni degli approcci improvvisati sopra elencati, sono disponibili anche alcuni strumenti standardizzati che aiutano ad affrontare alcuni rischi con i portafogli Singlesig. Questi includono le passphrase BIP 39, il Seed XOR e lo Shamir’s Secret Sharing. Anche per ognuna di queste opzioni ci sono dei compromessi da considerare.
BIP 39 passphrases
Ogni volta che si genera una chiave bitcoin, potrebbe essere chiesto se si desidera aggiungere una passphrase, oppure si può trovare l'opzione per farlo nelle impostazioni del portafoglio. Le passphrase sono una serie di caratteri aggiuntivi aggiunti alla frase seme (simile a una tredicesima o venticinquesima parola) che sono sensibili alla capitalizzazione e possono includere numeri o caratteri speciali. Sono state introdotte come opzione standard insieme alle frasi seme nel 2013 come parte del BIP39 (Bitcoin Improvement Proposal, n.d.t.). Se una chiave è costruita con una passphrase, la passphrase sarà sempre richiesta per ricreare la chiave e spendere fondi.
Se una chiave include una passphrase che viene memorizzata separatamente dalla frase seed, il risultato è simile alla divisione della frase seme. Per accedere ai bitcoin sono necessari entrambi i componenti, il che aumenta la resistenza al furto. Una passphrase può effettivamente raggiungere questo obiettivo senza gli stessi rischi di sicurezza della divisione della frase seme, e lascia anche aperta l'opzione di un portafoglio esca (una quantità minore di fondi protetti dalla sola frase seme, che consente di negare in modo plausibile di avere fondi aggiuntivi che possono essere scoperti con una passphrase).

Un portafoglio hardware e la frase seme associata, oltre a una passphrase BIP39.
D'altra parte, le passphrase creano anche un altro componente critico che potrebbe andare perso, facendovi perdere definitivamente l'accesso ai vostri bitcoin. Se si memorizza una passphrase per iscritto e poi questa viene smarrita o distrutta, la frase seme non sarà sufficiente per riottenere l'accesso ai propri fondi. Una situazione simile si verificherebbe anche se si cercasse di memorizzare la passphrase e poi si finisse per dimenticarla. Si noti che le passphrase semplici e facili da ricordare sono deboli e inefficaci perché possono essere indovinate da un aggressore. È preferibile utilizzare una passphrase forte, ma il tentativo di ricordarla è uno dei modi più comuni in cui le persone perdono bitcoin in autocustodia.
Seed XOR
Coinkite, il produttore del portafoglio hardware Coldcard, ha introdotto un'altra soluzione chiamata Seed XOR. Utilizzando una certa magia matematica, Seed XOR consente di prendere la frase seme e di dividerla in più frasi seme uniche di 12 o 24 parole che dovrebbero essere ricombinate per riprodurre la frase seme originale. Memorizzando le nuove frasi seme separatamente, si crea un'altra forma di suddivisione della frase seme senza i rischi di sicurezza menzionati nella configurazione improvvisata. Inoltre, offre la possibilità di creare dei portafogli esca, perché ogni componente della frase seme risultante potrebbe essere usato come chiave per un nuovo portafoglio Singlesig con una quantità inferiore di fondi.

Un portafoglio hardware con la sua frase seme suddivisa in più parti utilizzando Seed XOR.
Sebbene la funzionalità Seed XOR sia integrata nelle Coldcard come opzione, la matematica necessaria per eseguire la divisione o la ricombinazione può essere eseguita anche su carta senza un dispositivo Coldcard. Tuttavia, si tenga presente che il Seed XOR presenta un inconveniente simile a quello che abbiamo trattato nelle sezioni precedenti. Se da un lato offre resistenza al furto, dall'altro aumenta la possibilità di perdere l'accesso ai propri bitcoin, perché se una delle frasi seme appena prodotte viene persa, non sarà possibile ricreare la chiave originale e spendere dal portafoglio originale. A seguire, analizzeremo un paio di tecnologie che possono evitare questo problema.
Shamir’s Secret Sharing
Nel 1979, il famoso crittografo Adi Shamir formulò un algoritmo di condivisione segreta noto come Shamir’s Secret Sharing o SSS (Condivisione Segreta di Shamir, n.d.t.). Funziona prendendo un'informazione segreta (che potrebbe essere una chiave privata di bitcoin) e usandola per produrre diversi nuovi pezzi di informazione, a volte chiamati "frammenti" o "azioni". Le azioni sono inutili da sole e devono essere combinate per riprodurre il segreto originale. Ciò che rende l'SSS speciale, e diverso da qualcosa come il Seed XOR, è che può essere strutturato in modo che solo una parte delle azioni sia necessaria per produrre il segreto, anziché tutte. Ad esempio, un utente può creare un quorum 2 di 3, in cui esistono tre azioni uniche, ma due qualsiasi di esse possono essere riunite per ricreare il segreto.
Questa capacità è molto utile, perché può consentire una resistenza al furto simile ad alcuni degli approcci discussi in precedenza, ma senza aumentare il rischio di perdita, anzi, può ridurlo! Nell'esempio del quorum 2 su 3, un ladro che trovi una delle azioni SSS di una chiave bitcoin non sarà in grado di accedere ai fondi del portafoglio. Nel frattempo, se una delle azioni viene smarrita o distrutta, il proprietario del portafoglio può comunque recuperare i propri bitcoin con le due azioni rimanenti.

Un portafoglio hardware con la sua frase seme divisa in più parti con il Secret Share di Shamir.
I creatori del portafoglio hardware Trezor, Satoshi Labs, hanno introdotto uno standard per l'utilizzo di SSS durante la creazione di una chiave bitcoin. Si chiama "Shamir backup" e i dettagli si trovano in SLIP 39. Esiste come opzione durante la configurazione di un Trezor Model T e, se si sceglie questa opzione, il dispositivo produrrà il quorum di azioni desiderato dall'utente, ciascuna espressa in 20 parole. Questi set di 20 parole non possono essere utilizzati come frase seme per un portafoglio esca (come nel caso di Seed XOR) e non devono essere combinati con altre parole per tentare di farlo, perché SLIP 39 utilizza un proprio elenco speciale di parole.
Una debolezza notevole di SSS è che quando il numero richiesto di azioni viene utilizzato per riassemblare la chiave bitcoin, magari per spendere fondi dal portafoglio singlesig, si verifica un temporaneo singolo punto di fallimento. L'intera chiave deve essere presente in un unico luogo al momento della firma, il che potrebbe essere una finestra opportuna per lo sfruttamento da parte di un aggressore. Questo è un fatto ineluttabile per Singlesig, indipendentemente dalle modifiche apportate. Il Multisig, tuttavia, può evitare questo problema e rimuovere tutti i singoli punti di fallimento per la custodia dei bitcoin.
Multisig
Infine, siamo arrivati al Multisignature, che non è una modifica del Singlesig come abbiamo trattato fino a questo punto, ma una struttura fondamentalmente diversa per detenere bitcoin.
Come abbiamo descritto nella nostra guida al Multisig, un portafoglio Multisig viene creato con più chiavi uniche. Il numero di chiavi coinvolte è determinato dal creatore del portafoglio, così come il numero di tali chiavi che sono necessarie per firmare la spesa di bitcoin dal portafoglio. Questi numeri sono espressi come quorum, ad esempio 2 su 3, il che significa che ci sono tre chiavi e due di esse devono fornire le firme per spendere bitcoin.
Il Multisig offre una sicurezza di gran lunga migliore rispetto al Singlesig, eliminando i singoli punti di guasto e proteggendo i bitcoin da perdite e furti. Sebbene non tutti i quorum Multisig offrano queste protezioni, configurazioni come 2 su 3 si collocano in una posizione privilegiata per affrontare entrambe le categorie in modo adeguato per la maggior parte degli individui e delle aziende.

Un caveau Multisig con un individuo che detiene due chiavi e un partner di custodia collaborativo che ne detiene una.
Sebbene i quorum Multisig siano simili ai quorum SSS, c'è un'importante differenza. Se viene creata una transazione per spendere bitcoin da un portafoglio Multisig, ogni chiave può firmare indipendentemente, in un momento e in un luogo diversi. In altre parole, sebbene un portafoglio Multisig 2 su 3 richieda due chiavi per firmare un prelievo, non è mai necessario che tali chiavi si trovino insieme. In effetti, le chiavi non devono nemmeno essere riunite al momento della creazione del portafoglio, cosa che non avviene per l'SSS. Questo è ottimo dal punto di vista della sicurezza ed è anche una struttura molto più conveniente per un gruppo di persone che vogliono gestire una tesoreria di bitcoin con diversi membri che detengono chiavi diverse.
Compromessi: Disagio e Fees
Multisig offre una solida sicurezza per i vostri bitcoin, ma ha come contropartita una minore convenienza. Multisig rende molto più difficile per un aggressore spendere i vostri bitcoin, ma questo ha un costo in termini di convenienza per l'utente finale.
Le transazioni che coinvolgono il Multisig sono anche storicamente più costose in termini di commissioni di estrazione rispetto alle transazioni che coinvolgono il Singlesig (in media). Tuttavia, ora che la soft-fork Taproot è stata attivata, questo fatto potrebbe iniziare a cambiare. Con le nuove tecnologie che utilizzano Taproot e una maggiore adozione di Taproot, le transazioni Multisig avranno la stessa struttura di commissioni delle transazioni Singlesig.
Custodia fai da te vs. Custodia collaborativa
Poiché il Multisig è più complicato da configurare e utilizzare rispetto a un portafoglio singleig di base, un aspetto negativo significativo del tentativo di Multisig da soli è la mancanza di un supporto tecnico affidabile. Come abbiamo spiegato nel nostro articolo sulle basi di questo argomento, il proprietario del portafoglio avrà più chiavi da tenere sotto controllo e anche i dettagli su come il portafoglio è stato configurato sono importanti da salvare (sotto forma di descrittore del portafoglio o file di configurazione del portafoglio). Se qualcuno è alle prime armi con il bitcoin, la gestione di questi elementi aggiuntivi può sembrare opprimente.
Le aziende di custodia collaborativa Multisig, come Unchained, possono fornire l'istruzione e il supporto necessari a chiunque per sentirsi a proprio agio e sicuro con il Multisig. Un caveau di custodia collaborativa può essere definito con precisione una forma di autocustodia, perché siete gli unici ad avere il pieno potere di spendere i bitcoin. Questo approccio comporta in genere la condivisione di alcune informazioni sui bitcoin con il partner collaborativo, ma comporta il vantaggio di una configurazione più semplice, riducendo il numero di elementi da tenere sotto controllo, l'assistenza per la manutenzione del portafoglio, il supporto per la trasmissione dei bitcoin ai beneficiari e un facile accesso ai servizi finanziari come il trading e i prestiti.
Che dire del quorum 3 di 5?
Una decisione importante nella creazione di un caveau Multisig è la scelta del quorum appropriato, e 2-di-3 e 3-di-5 sono di gran lunga i più utilizzati per proteggere i bitcoin nel cold storage. Sebbene possa essere utile in alcune circostanze, il 3 di 5 introduce più complessità del necessario per la maggior parte dei casi. Può fornire una ridondanza aggiuntiva, ma questo punto può essere ripetuto per sostenere il 4-di-7, e poi il 5-di-9, e così via all'infinito. Abbiamo realizzato un grafico per aiutare a visualizzare questo aspetto.
Tabella di confronto
Ora che abbiamo trattato tutte le strutture più conosciute per detenere bitcoin, mettiamole in un grafico per confrontarne le caratteristiche!

- Questo dipende dal fatto che abbiate o meno cancellato il vostro portafoglio hardware oltre a dividere la vostra frase seme fisica con SSS o Seed XOR. ** Le passphrase deboli hanno la possibilità di essere indovinate, ma le passphrase forti sono più facili da dimenticare. *** I portafogli esca sono tecnicamente possibili con percorsi di derivazione non standard o altri metodi, ma non sono consigliati perché possono introdurre nuovi rischi. **** Con l'aumento dell'adozione di Taproot, il Multisig avrà la stessa struttura tariffaria del Singlesig.
Dovrei usare Singlesig o Multisig?
Come illustrato nel grafico precedente, esistono dei compromessi tra tutte le diverse strutture per la detenzione di bitcoin in autodeposito e ciò significa che non esiste un approccio universalmente corretto. Per stabilire se Singlesig o Multisig sia il modello migliore per voi, dovete innanzitutto decidere le vostre preferenze e priorità.
Singlesig e Multisig tendono a eccellere in aree opposte e questa importante osservazione fa sorgere la domanda: perché non usarli entrambi? Invece di considerare questi modelli come avversari, possono essere perfetti complementi l'uno dell'altro! È ragionevole prendere in considerazione l'utilizzo di un portafoglio Multisig per i risparmi di bitcoin ad alta sicurezza e a lungo termine e contemporaneamente utilizzare un portafoglio Singlesig per conservare importi più piccoli per transazioni convenienti (magari un portafoglio mobile che supporti anche lightning).
-
 @ 46205202:5f2056a6
2024-04-20 11:39:32
@ 46205202:5f2056a6
2024-04-20 11:39:32Chickpea Soup
Ingredients List
- 1/4 cup olive oil
- 4 garlic cloves
- 1 large yellow onion, chopped
- 1 2-inch piece of ginger chopped finely
- salt to taste
- 1 1/2 tsp tumeric
- 2 19oz cans of chickpeas, drained & rinsed
- 2 400mL cans of full-fat coconut milk
- 2 cups vegi broth
Steps
- Heat oil, garlic, onion, ginger, salt over medium heat, until onion is translucent.
- Slightly crush the some chickpeas to release starch. Scrape any browning off the bottom of pot for flavor.
- Add coconut milk & broth; simmer until a desirable consistency.
-
 @ 58f5a230:304d59f7
2024-01-20 18:03:12
@ 58f5a230:304d59f7
2024-01-20 18:03:12บทความชุดนี้ผมคิดว่าจะเขียนแยกเป็นตอน ๆ ตามบทเรียนที่ได้รับจาก Bitcoin FOSS Program ของทาง Chaincode Labs โดยจะมาแชร์การแก้โจทย์ปัญหาตามบททดสอบในแต่ละสัปดาห์
สัปดาห์แรกนี้ผมได้โจยท์มาทั้งหมด 8 ข้อ และการตอบปัญหาทั้งหมดจะใช้ Bash Script เขียนคำสั่งร่วมกับ
bitcoin-cliในการทำความเข้าใจพื้นฐานของ Bitcoin-Core ระบบการบันทึกบัญชีลง Blockchain การดู/ตรวจสอบ ข้อมูลบน Block รวมถึงพื้นฐานข้อมูลภายใน Block จนถึง Transaction เบื้ิองต้น และในบทความนี้จะควบคุมความรู้ในหนังสือนั้นในบทที่ 1-3 ของหนังสือ Mastering Bitcoin หากท่านต้องการศึกษาเพิ่มเติมให้เข้าใจมากขึ้น แนะนำให้อ่านไปด้วยข้อที่ 1: แฮชของบล็อคที่ 654,321 คืออะไร?
ข้อนี้ง่ายมาก ๆ โดยเราจะใช้โปรแกรม
bitcoin-cliจาก bitcoin-core ที่ติดตั้งไว้แล้ว เชื่อมไปยัง RPC server ที่เป็น Full-node ของเรา พร้อมกับคำสั่งgetblockhashเราสามารถดูได้ว่ามันใช้งานยังไงด้วยการพิมพ์helpนำหน้าคำสั่ง เราก็จะได้คำอธิบายพร้อมกับตัวอย่างการใช่งานมา```sh $ bitcoin-cli help getblockhash getblockhash height
Returns hash of block in best-block-chain at height provided.
Arguments: 1. height (numeric, required) The height index
Result: "hex" (string) The block hash
Examples:
bitcoin-cli getblockhash 1000 curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "getblockhash", "params": [1000]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
ในโจทย์นี้เราจะใช้เพียงคำสั่งเดียวเท่านั้น มาดูกัน
sh $ bitcoin-cli getblockhash 654321 000000000000000000058452bbe379ad4364fe8fda68c45e299979b492858095ผมได้เรียกใช้
bitcoin-cliพร้อมกับคำสั่งgetblockhash 654321และได้คำตอบมาว่า000000000000000000058452bbe379ad4364fe8fda68c45e299979b492858095นั้นคือแฮชของบล็อคที่ 654,321 นั่นเอง ข้อมูลเหล่านี้เราจะได้ใช้มันในข้อหลัง ๆ ไปข้อต่อไปกันข้อที่ 2: จงพิสูจน์ข้อความนี้ว่าถูกเซนต์โดยที่อยู่นี้ถูกต้องหรือไม่
(true / false) Verify the signature by this address over this message: address: `1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa` message: `1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa` signature: `HCsBcgB+Wcm8kOGMH8IpNeg0H4gjCrlqwDf/GlSXphZGBYxm0QkKEPhh9DTJRp2IDNUhVr0FhP9qCqo2W0recNM=`ตามโจทย์นี้อาจจะดูงง ๆ ผมจึงไปค้นใน Docs ของ Bitcoin-Core ดูและพบกับคำสั่ง
verifymessageมาลองดูกัน```sh $ bitcoin-cli help verifymessage verifymessage "address" "signature" "message"
Verify a signed message.
Arguments: 1. address (string, required) The bitcoin address to use for the signature. 2. signature (string, required) The signature provided by the signer in base 64 encoding (see signmessage). 3. message (string, required) The message that was signed.
Result: true|false (boolean) If the signature is verified or not.
Examples:
Unlock the wallet for 30 seconds
bitcoin-cli walletpassphrase "mypassphrase" 30
Create the signature
bitcoin-cli signmessage "1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX" "my message"
Verify the signature
bitcoin-cli verifymessage "1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX" "signature" "my message"
As a JSON-RPC call
curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "verifymessage", "params": ["1D1ZrZNe3JUo7ZycKEYQQiQAWd9y54F4XX", "signature", "my message"]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
สังเกตุว่าคำสั่งนี้ใช้ 3 ตัวแปรตามที่โจทย์ให้มาเป๊ะ ๆ มาลองใช้ดูกัน
sh address="1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa" message="1E9YwDtYf9R29ekNAfbV7MvB4LNv7v3fGa" signature="HCsBcgB+Wcm8kOGMH8IpNeg0H4gjCrlqwDf/GlSXphZGBYxm0QkKEPhh9DTJRp2IDNUhVr0FhP9qCqo2W0recNM="เริ่มจากการประกาศตัวแปรไว้ตามฉบับสายผู้ใช้ Linux แล้วก็ลองส่งคำสั่งกันเลย
sh $ bitcoin-cli verifymessage $address $signature $message falsefalse... ตอนแรกก็ยังงง ๆ แต่ข้อนี้คำตอบคือ false จริง ๆ นั่นแหละ อาจจะเพราะคนทำโจทย์ลืมดูว่า message มันซ้ำกับ address อยู่ หรือไม่ก็จงใจ ช่างมัน ไปข้อต่อไปกันข้อที่ 3: บล็อคที่ 123,456 มีจำนวน outputs Transaction ทั้งหมดเท่าไหร่?
ข้อนี้จะไปไวหน่อยเพราะว่าเราไม่จำเป็นต้อง loop เพื่อดูข้อมูล Transaction ในบล็อคเพื่อนับเอา outputs เราสามารถใช้คำสั่ง
getblockstatsได้เลย แล้วใช่jqแปลงข้อมูลให้เป็น JSON เพื่อให้เราอ่านได้ง่ายขึ้นsh $ bitcoin-cli getblockstats 123456 | jq . { "avgfee": 416666, "avgfeerate": 1261, "avgtxsize": 330, "blockhash": "0000000000002917ed80650c6174aac8dfc46f5fe36480aaef682ff6cd83c3ca", "feerate_percentiles": [ 0, 0, 0, 3861, 3891 ], "height": 123456, "ins": 17, "maxfee": 1000000, "maxfeerate": 3891, "maxtxsize": 618, "medianfee": 0, "mediantime": 1305197900, "mediantxsize": 258, "minfee": 0, "minfeerate": 0, "mintxsize": 257, "outs": 24, "subsidy": 5000000000, "swtotal_size": 0, "swtotal_weight": 0, "swtxs": 0, "time": 1305200806, "total_out": 16550889992, "total_size": 3964, "total_weight": 15856, "totalfee": 5000000, "txs": 13, "utxo_increase": 7, "utxo_increase_actual": 7, "utxo_size_inc": 567, "utxo_size_inc_actual": 567 }นี่คือข้อมูลเบื้องต้นของบล็อค 123,456 ที่มีรายการ transaction อยู่ 13 รายการ และมี outputs รวม 24 รายการ เราสามารถใช้
jqแสดงผลเฉพาะข้อมูลที่เราต้องการได้ง่าย ๆ โดยพิมพ์ชื่อข้อมูลที่เราต้องการตามไปหลังจุด.ข้อนี้สามารถตอบได้เลยsh $ bitcoin-cli getblockstats 123456 | jq .outs 24ข้อที่ 4: จงหา taproot address ลำดับที่ 100 โดยคำนวนจาก xpub ต่อไปนี้
ตัว extended public key หรือ xpub ที่ผมได้มาคือ
xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2เอาหล่ะ แล้วจะทำยังไงต่อหล่ะเนี่ยแล้วผมก็ไปเจอกับคำสั่งนี้ในที่สุด
deriveaddressesว่าแต่มันใช้ยังไงหว่า```sh $ bitcoin-cli help deriveaddresses deriveaddresses "descriptor" ( range )
Derives one or more addresses corresponding to an output descriptor. Examples of output descriptors are: pkh(
) P2PKH outputs for the given pubkey wpkh( ) Native segwit P2PKH outputs for the given pubkey sh(multi( , , ,...)) P2SH-multisig outputs for the given threshold and pubkeys raw( ) Outputs whose scriptPubKey equals the specified hex scripts tr( ,multi_a( , , ,...)) P2TR-multisig outputs for the given threshold and pubkeys In the above,
either refers to a fixed public key in hexadecimal notation, or to an xpub/xprv optionally followed by one or more path elements separated by "/", where "h" represents a hardened child key. For more information on output descriptors, see the documentation in the doc/descriptors.md file. Arguments: 1. descriptor (string, required) The descriptor. 2. range (numeric or array, optional) If a ranged descriptor is used, this specifies the end or the range (in [begin,end] notation) to derive.
Result: [ (json array) "str", (string) the derived addresses ... ]
Examples: First three native segwit receive addresses
bitcoin-cli deriveaddresses "wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/)#cjjspncu" "[0,2]" curl --user myusername --data-binary '{"jsonrpc": "1.0", "id": "curltest", "method": "deriveaddresses", "params": ["wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/)#cjjspncu", "[0,2]"]}' -H 'content-type: text/plain;' http://127.0.0.1:8332/ ```
อื้อหือ ยิ่งงงไปอิ๊กก เอาวะลองดูตามตัวอย่างของ P2TR ละกัน
sh $ bitcoin-cli deriveaddresses "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2)" error code: -5 error message: Missing checksumอะ...อ้าว ย้อนกลับไปดูตัวอย่าง และอ่าน Docs ดี ๆ จะพบว่าการ deriveaddresses นั้นจะมีรูปแบบอยู่ เช่น
wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/*)#cjjspncu- wpkh() นั้นคือรูปแบบของการเข้ารหัส ซึ่งมีหลายอย่างให้ใช้ตามวัตถุประสงค์ อย่าง multisig ก็จะเป็นอีกแบบ
- [d34db33f/84h/0h/0h] ส่วนนี้ึคือ fingerprint จาก pubkey หลักก่อนจะคำนวน xpub ซึ่งโจทย์ข้อนี้ไม่มีให้ และหลังจากศึกษามาก็พบว่ามันไม่จำเป็นสำหรับการสร้าง address แบบ basic ง่าย ๆ
- xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY ส่วนนี้คืิอ extended public key ซึ่งคำนวนมาจาก pubkey หลักที่คำนวนมาจาก private key หรือ seed ของเราอีกที
- /0/_ คือ path สำหรับระยะการคำนวน address โดยให้มองเป็น /เริ่มต้น/สิ้นสุด เช่น /0/99 หมายถึง เราจะคำนวน address จากตำแหน่งที่ 0 ถึงตำแหน่ง 99 ถ้าใช้ _ คือจะคำนวนกี่ที่อยู่ก็ได้
-
cjjspncu คือ checksum ของ descriptor กระเป๋านี้ และสามารถใช้คำสั่ง
getdescriptorinfoเพื่อดูข้อมูลได้
เอาหล่ะ มาลองกันใหม่ โดยที่ผมจะ derive ตำแหน่งที่ /100 ที่อยู่เดียวเท่านั้น
sh $ bitcoin-cli getdescriptorinfo "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)" { "checksum": "5p2mg7zx", "descriptor": "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)#5p2mg7zx", "hasprivatekeys": false, "isrange": false, "issolvable": true }ได้แฮะ ลองเอา checksum ที่ได้ไปคำนวนที่อยู่กัน
sh $ bitcoin-cli deriveaddresses "tr(xpub6Cx5tvq6nACSLJdra1A6WjqTo1SgeUZRFqsX5ysEtVBMwhCCRa4kfgFqaT2o1kwL3esB1PsYr3CUdfRZYfLHJunNWUABKftK2NjHUtzDms2/100)#5p2mg7zx" [ "bc1p3yrtpvv6czx63h2sxwmeep8q98h94w4288fc4cvrkqephalydfgszgacf9" ]หลังจากนั้นผมก็ใช้
jq -r .[0]เพื่อดึงข้อมูลออกจาก JSON array แล้วส่งคำตอบ ผ่านได้ด้วยดีข้อที่ 5 สร้าง P2SH multisig address ด้วย public keys 4 ชุดจาก inputs ใน transaction นี้
37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517ไหนดูซิ transaction นี้เป็นยังไง
sh $ bitcoin-cli getrawtransaction "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517" 1 { "blockhash": "000000000000000000024a848a9451143278f60e4c3e73003da60c7b0ef74b62", "blocktime": 1701158269, "confirmations": 7751, "hash": "e28a0885b6f413e24a89e9c2bac74d4c6f335e17545f0b860da9146caf7ffe39", "hex": "02000000000104b5f641e80e9065f09b12f3e373072518885d1bd1ddd9298e5b9840de515edac90000000000feffffffd54f8986afbb6ff18572acaee58fa3ad64446dd770ffe9b6a04f798becdafb440000 000000feffffff475e3062b1c3ee87544c29d723866da2b65a1b1a42e6ea4a4fd48d79f83c26c50000000000feffffffa56387352ecc93dfd37648e6ebd4d9effb37ffefcad02eb7b85860c9097cf8090000000000feff ffff02fa440f00000000001600148070ec3954ecdcbfc210d0117e8d28a19eb8467270947d0000000000160014b5fe46c647353ec9c06374655502094095f0289c0247304402200dd758801b40393f68dad8ab57558803 efcd2b681ee31eb44fb3cfa9666d2bf90220254d34fa4990e23652bf669053c5e16fd2fbb816bed2eeb44c1f1e6e54143e3e012102bbb4ba3f39b5f3258f0014d5e4eab5a6990009e3e1dba6e8eaff10b3832394f70247 304402201694761a5749b6a84f71459c04a44cf9d34a36ae8c9044c3af7a3a5514ef2e64022058f61feb92d6d54b71fdea47e7dfcd20f6a5c12e2fbcb15bc44fe95c73f2e808012103aaf17b1a7b4108f7e5bc4f7d59c2 0f7fb1a72dbc74a9a3d6d1f8488df159c76002473044022014b65c60f65e62d9dac893e404c8de2a007c7c6b74dbac18e454d8374e159759022012453f69112adadf9495fd3fe288aa5ed9e3d836340da06fa1e82c8e09 adef57012103a6d919c76d9117c23570a767450013edf31cf6be7d3b5a881c06a9aa1f2c24ce0247304402203d3b02390803c1d673fa49bd64d4a26fbeb29e3fc152af8f844d776c9409e41302206903a011a04e00a7f4 ec606da4320226d2d393f565702cc58cfcef6dca67f84c01210383d12258e3e294a6d7754336f6b4baef992ec4b91694d3460bcb022b11da8cd2817e0c00", "locktime": 818817, "size": 666, "time": 1701158269, "txid": "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517", "version": 2, "vin": [ { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "c9da5e51de40985b8e29d9ddd11b5d8818250773e3f3129bf065900ee841f6b5", "txinwitness": [ "304402200dd758801b40393f68dad8ab57558803efcd2b681ee31eb44fb3cfa9666d2bf90220254d34fa4990e23652bf669053c5e16fd2fbb816bed2eeb44c1f1e6e54143e3e01", "02bbb4ba3f39b5f3258f0014d5e4eab5a6990009e3e1dba6e8eaff10b3832394f7" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "44fbdaec8b794fa0b6e9ff70d76d4464ada38fe5aeac7285f16fbbaf86894fd5", "txinwitness": [ "304402201694761a5749b6a84f71459c04a44cf9d34a36ae8c9044c3af7a3a5514ef2e64022058f61feb92d6d54b71fdea47e7dfcd20f6a5c12e2fbcb15bc44fe95c73f2e80801", "03aaf17b1a7b4108f7e5bc4f7d59c20f7fb1a72dbc74a9a3d6d1f8488df159c760" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "c5263cf8798dd44f4aeae6421a1b5ab6a26d8623d7294c5487eec3b162305e47", "txinwitness": [ "3044022014b65c60f65e62d9dac893e404c8de2a007c7c6b74dbac18e454d8374e159759022012453f69112adadf9495fd3fe288aa5ed9e3d836340da06fa1e82c8e09adef5701", "03a6d919c76d9117c23570a767450013edf31cf6be7d3b5a881c06a9aa1f2c24ce" ], "vout": 0 }, { "scriptSig": { "asm": "", "hex": "" }, "sequence": 4294967294, "txid": "09f87c09c96058b8b72ed0caefff37fbefd9d4ebe64876d3df93cc2e358763a5", "txinwitness": [ "304402203d3b02390803c1d673fa49bd64d4a26fbeb29e3fc152af8f844d776c9409e41302206903a011a04e00a7f4ec606da4320226d2d393f565702cc58cfcef6dca67f84c01", "0383d12258e3e294a6d7754336f6b4baef992ec4b91694d3460bcb022b11da8cd2" ], "vout": 0 } ], "vout": [ { "n": 0, "scriptPubKey": { "address": "bc1qspcwcw25anwtlsss6qgharfg5x0ts3njad8uve", "asm": "0 8070ec3954ecdcbfc210d0117e8d28a19eb84672", "desc": "addr(bc1qspcwcw25anwtlsss6qgharfg5x0ts3njad8uve)#pzjnvw8p", "hex": "00148070ec3954ecdcbfc210d0117e8d28a19eb84672", "type": "witness_v0_keyhash" }, "value": 0.01000698 }, { "n": 1, "scriptPubKey": { "address": "bc1qkhlyd3j8x5lvnsrrw3j42qsfgz2lq2yu3cs5lr", "asm": "0 b5fe46c647353ec9c06374655502094095f0289c", "desc": "addr(bc1qkhlyd3j8x5lvnsrrw3j42qsfgz2lq2yu3cs5lr)#hzcalwww", "hex": "0014b5fe46c647353ec9c06374655502094095f0289c", "type": "witness_v0_keyhash" }, "value": 0.0823 } ], "vsize": 344, "weight": 1374 }เราจำเป็นต้องเรียนรู้เรื่อง Witness program ของ bip-141 เพื่อเข้าใจ scriptPubKey หรือ redeemScript เบื่องต้นเสียก่อน โดยพื้นฐานธุรกรรมแบบ P2WPKH ภายใน txinwitness จะมี signature และ public keys ตามลำดับ เราจะลองใช้ pubkey นี้ในการสร้างกระเป๋า multisig กัน
sh txinfo=$(bitcoin-cli getrawtransaction "37d966a263350fe747f1c606b159987545844a493dd38d84b070027a895c4517" 1) ad1=$(echo $txinfo | jq '.vin[0] | .txinwitness[1]') ad2=$(echo $txinfo | jq '.vin[1] | .txinwitness[1]') ad3=$(echo $txinfo | jq '.vin[2] | .txinwitness[1]') ad4=$(echo $txinfo | jq '.vin[3] | .txinwitness[1]') bitcoin-cli createmultisig 1 ["$ad1","$ad2","$ad3","$ad4"] | jq -r '.address'3GyWg1CCD3RDpbwCbuk9TTRQptkRfczDz8
ง่ายเลยข้อนี้ ไปข้อต่อไปกัน
ข้อที่ 6: transaction ไหนในบล็อค 257,343 ใช้เงินรางวัลจากการขุดจากบล็อค 256,128?
Which tx in block 257,343 spends the coinbase output of block 256,128?ข้อนี้ต้องไปหาว่า coinbase output ก็คือเงินรางวัลจากการขุดบล็อคนั้น ๆ รวมกับค่า fee นั่นเอง ซึ่งจะอยู่ในลำดับแรกของบล็อคนั้น ๆ เสมอ เรามาเขียนน Bash Script หา coinbase txid กันsh blockhash=$(bitcoin-cli getblockhash 256128) tx256=$(bitcoin-cli getblock $blockhash 2)ด้วยคำสั่ง
getblock ตามด้วยแฮชของบล็อค และระดับข้อมูลโดยที่ระดับ- จะแสดงข้อมูลบล็อค ไม่มี transaction
- จะแสดงข้อมูล transaction แต่ไม่รวม inputs
- จะแสดงข้อมูลทั้งหมดของบล็อคนั้น ๆ
sh coinbase_txid=$(echo $tx256 | jq -r '.tx[0].txid') echo $coinbase_txidแล้วก็เลือก txid จากข้อมูลแรกมา ซึ่งก็คือ coinbase output ของเรา
611c5a0972d28e421a2308cb2a2adb8f369bb003b96eb04a3ec781bf295b74bc นี่คือ txid ที่เราจะเอาไปหาว่ามันมีใน inputs ไหนของ transaction ไหนใน block 257,343 ซึ่งโดยทั่วไปแล้วหากเรา loop หากทีละ transaction คงเสียเวลาน่าดู เราลองมาใช้ฟังชั่น select() ของ
jqกัน```sh blockhash=$(bitcoin-cli getblockhash 256128) tx256=$(bitcoin-cli getblock $blockhash 2) coinbase_txid=$(echo $tx256 | jq -r '.tx[0].txid') blockhash=$(bitcoin-cli getblockhash 257343) tx257=$(bitcoin-cli getblock $blockhash 3)
เลือกข้อมูล transaction
block257tx=$(echo $tx257 | jq -r '.tx')
ใน .tx นั้นเราจะได้ JSON array ที่มีรายการ transaction เยอะมาก ๆ เราจะเลือกอันเดียวที่มี coinbase txid ใน vin หรือ inputs นั้น ๆ กัน และใช้ jq อีกครั้งเพื่อให้แสดงผลแค่ txid
echo "$block257tx" | jq ".[] | select(.vin[].txid==\"$coinbase_txid\")" | jq -r '.txid' ```
และนี่คือคำตอบของข้อนี้
c54714cb1373c2e3725261fe201f267280e21350bdf2df505da8483a6a4805fc
ข้อที่ 7: มี UTXO อันนึงที่ไม่เคยถูกใช้งานเลยในบล็อคที่ 123,321 UTXO นั้นคือ address อะไร?
Only one single output remains unspent from block 123,321. What address was it sent to?ข้อนี้เราจะใช้คำสั่ง gettxout ที่จะ return ข้อมูลของ UTXO ที่ไม่เคยถูกใช้งานให้เรา โดยการ loop ไปทีละ transaction
```sh blockhash=$(bitcoin-cli getblockhash 123321) blockinfo=$(bitcoin-cli getblock $blockhash 3) transaction=$(echo $blockinfo | jq '.tx[]') txid=$(echo $transaction | jq -r '.txid')
for item in $txid; do bitcoin-cli gettxout "$item" 0 | jq -r '.scriptPubKey.address' done ```
1FPDNNmgwEnKuF7GQzSqUcVQdzSRhz4pgX ได้มาแล้วคำตอบของเรา โจทย์ข้อนี้คงผิดแน่ ๆ หากมี UTXO ที่ยังไม่ได้ใช้งานมากกว่า 1 อันเพราะเราสั่งให้แสดงมันทุก transaction เลย! ฮาาา
ข้อที่ 8: public key อะไรที่ใช้เซ็นอันดับแรกใน transaction e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163
ข้อนี้ค่อนข้างหินเลย ตอนแรกเอาไปเปิดในดูใน mempool พบว่าเป็นธุรกรรมที่ถูก force close lightning channel ซึ่งมันต้องเป็น multisig แน่ ๆ เอาหล่ะ ดูข้อมูลธุรกรรมนี้ก่อนแล้วกัน
sh bitcoin-cli getrawtransaction "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163" 1 { "blockhash": "0000000000000000000b0e5eec04d784347ef564b3ddb939eca019a66c9cedbe", "blocktime": 1610254919, "confirmations": 161208, "hash": "881d7ab9ad60d6658283dbbad345f6f28491a264cd11d060b4fb4f121851a7f3", "hex": "020000000001018b1aab3917e6595816c63bf9dd0ebf4303f2b2a23103aee1500282c944affd71000000000000000000010e26000000000000160014c47082b5a49065d85ab65730e8c28bb0b4810b960347 3044022050b45d29a3f2cf098ad0514dff940c78046c377a7e925ded074ad927363dc2dd02207c8a8ca7d099483cf3b50b00366ad2e2771805d6be900097c2c57bc58b4f34a50101014d6321025d524ac7ec6501d018d3 22334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac00000000", "locktime": 0, "size": 237, "time": 1610254919, "txid": "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163", "version": 2, "vin": [ { "scriptSig": { "asm": "", "hex": "" }, "sequence": 0, "txid": "71fdaf44c9820250e1ae0331a2b2f20343bf0eddf93bc6165859e61739ab1a8b", "txinwitness": [ "3044022050b45d29a3f2cf098ad0514dff940c78046c377a7e925ded074ad927363dc2dd02207c8a8ca7d099483cf3b50b00366ad2e2771805d6be900097c2c57bc58b4f34a501", "01", "6321025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac" ], "vout": 0 } ], "vout": [ { "n": 0, "scriptPubKey": { "address": "bc1qc3cg9ddyjpjask4k2ucw3s5tkz6gzzukzmg49s", "asm": "0 c47082b5a49065d85ab65730e8c28bb0b4810b96", "desc": "addr(bc1qc3cg9ddyjpjask4k2ucw3s5tkz6gzzukzmg49s)#c68e8rrv", "hex": "0014c47082b5a49065d85ab65730e8c28bb0b4810b96", "type": "witness_v0_keyhash" }, "value": 9.742e-05 } ], "vsize": 121, "weight": 483 }เรารู้แล้วว่าข้อมูลจะอยู่ใน
txinwitnessซึ่งอันดับแรก ๆ เป็น signature และอันหลังเป็น public key แต่ว่า มันมีหลาย public key ใช่มะ ในนี้sh transaction=$(bitcoin-cli getrawtransaction "e5969add849689854ac7f28e45628b89f7454b83e9699e551ce14b6f90c86163" 1) scriptpubkey=$(echo $txinfo | jq -r .vin[].txinwitness[2]) echo $scriptpubkey6321025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f67029000b2752102ad92d02b7061f520ebb60e932f9743a43fee1db87d2feb1398bf037b3f119fc268ac เอาหล่ะ เรามาแกะข้อมูลนี้กัน หากเราไปอ่าน bip-143 จะมีรูปแบบตัวอย่างลำดับอยู่ และก็พบว่ามันคืออักษรลำดับที่ 5 ถึง 67 เราต้องใช้ Bash slicing string เพื่อตัดให้เหลือส่วนที่เราต้องการและส่งข้อสอบดู
sh echo ${scriptpubkey:4:66}025d524ac7ec6501d018d322334f142c7c11aa24b9cffec03161eca35a1e32a71f
-
 @ 81870f53:29bef6a6
2024-04-23 23:09:00
@ 81870f53:29bef6a6
2024-04-23 23:09:00Grass 無料アプリで 1 日あたり 5.6 ドルの暗号通貨を獲得 | 不労所得 ステークを獲得する AI革命で。 使用していないインターネットに対して支払いを受けましょう

Grass は世界初のレイヤー 2 データ ロールアップです。 これは AI トレーニング データのソースとして存在し、Web スクレイピング ノードの広大なネットワークを使用して公開 Web サイトからデータを取得します。
これらのノードは住宅のインターネット ユーザーによって自主的に運営されており、ユーザーは参加に対して報酬を受け取ります。 ネットワーク上で調達されたデータは、AI トレーニングで使用するために Grass の増大するデータ リポジトリに追加される前に、クリーンアップされ、構造化されたデータセットに処理されます。
AI モデルをトレーニングするには、大量のトレーニング データが必要です。 これを見つけるのに最も簡単な場所はインターネット上ですが、商用データセンターからアクセスするのが難しい場合があります。 分散型ネットワークが最適に機能します。
ここで Grass の出番です。Grass を使用すると、パブリック Web からさまざまな種類のデータを収集し、AI モデルで読み取ることができる構造化データセットを生成できます。 このトレーニング データがなければ AI は存在できないため、Grass は AI 開発の最初のステップ、つまり AI のデータ層です。
Wynd Labs は Grass の貢献者です。 彼らは AI を透明性、倫理的、公平なものにすることに取り組んでおり、Grass は彼らがこれを実現しようとしている方法の 1 つです。
紹介コード - Referral Code 5_e_lFNhtm4wHAA
ここに参加してください
登録 https://app.getgrass.io/register/?referralCode=5_e_lFNhtm4wHAA
ホエールマーケットと呼ばれるウェブサイトでポイントを事前に販売したり、今年後半に予定されているエアドロップを待つためにポイントを保管したりすることもできます。
https://app.whales.market/points-markets?project=Grass
-
 @ 46fcbe30:6bd8ce4d
2024-04-11 17:21:28
@ 46fcbe30:6bd8ce4d
2024-04-11 17:21:28Opinion about Phoenix - LN Bitcoin wallet (android)
Phoenix is one of my favorite wallets. It makes using Bitcoin really easy but at a price. The wallet lets you send and receive both over the lightning network and on-chain without jumping through hoops, first but at the cost of either kind of hidden fees or unexpected on-chain fees.
To my understanding, when you receive on-chain funds, the wallet does yet another on-chain transaction to get these funds onto lightning and when you send via lightning, you pay an extra 0.4% to the provider. This 0.4% fee is not capped in any way, so while you can send $1000 via lightning, that will cost you $4 even when on-chain transactions would have cost just $1.
As of writing this opinion, the wallet is not reproducible which is a red flag to updating to this version but the provider hopefully will fix that soon as they are an OG player in the space.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ bcea2b98:7ccef3c9
2024-04-11 15:37:30
@ bcea2b98:7ccef3c9
2024-04-11 15:37:30This could be about professional work, raising a family, or other ventures. Mentioning one thing doesn't mean something else is less important. This may give you freedom in the response.
The most important contributions I believe I have made was raising a family and contributing to open-source software. Everyone is old now, but memories and git live on.
-
 @ bcea2b98:7ccef3c9
2024-04-11 02:25:20
@ bcea2b98:7ccef3c9
2024-04-11 02:25:20 -
 @ c48e29f0:26e14c11
2024-04-10 16:54:40
@ c48e29f0:26e14c11
2024-04-10 16:54:40A Harvard economist published 100+ pages of survey analysis to confirm what anyone outside of the fiat academic bubble already knows: people don't like it when the stored value of their time+energy is inflated into oblivion.
You can access the full report here for anyone interested: https://www.nber.org/system/files/working_papers/w32300/w32300.pdf
One quote from the Abstract really jumped out at me: "The predominant reason for people’s aversion to inflation is the widespread belief that it diminishes their buying power."
Well, yeah, no shit... But this isn't a "belief"... this is a fact.
Here's the thing: the average person understands the problem, because they feel the effects of the problem every single day...
They may not understand the root cause of the problem (creating money out of thin air)--instead blaming "greedy corporations" or "Joe Biden" or "Putin's Price Hike" or whatever the propaganda du jour happens to be--but they know inflation feels wrong. It feels like someone is stealing from them (which is true).
They know their purchasing power has decreased, because when they spend a dollar today it buys less than it did five years ago, and much less than it did 20 years ago.
It doesn't matter if fiat academics tell them "everything is fine! stop complaining! inflation is ackshually a good thing!"
People can feel that something is broken.
Most people still think there is a partisan/political solution to the problems they feel.
They think "if only OUR guy was in charge, things would be better" or "if only we taxed the greedy corporations and the rich more, then things would be better."
But political solutions will always be bandaids meant to superficially treat the symptoms of the disease so the Political Team proposing the "solution" can score short-term perceived wins ahead of the next election. "Look, we did something! Now stop complaining and vote for us because the other guy is literally the devil."
A few people already realize that the money itself is broken.
They understand that when the money breaks, society breaks with it.
Money created out of thin air disproportionally enriches those closest to the creation of the new money.
Money created out of thin air is used to fund Forever Wars we never agreed to enter.
Money created out of thin air is used to subsidize companies/industries that the free market does not value, distorting price signals.
Money created out of thin air bails out banks.
Money created out of thin air perpetuates never-ending boom and bust cycles.
Money created out of thin air reduces the purchasing power of the money in your pocket.
Money created out of thin air steals the value of your time and energy, of your life itself.
The people who realize the money is broken now save the value of their time and energy in Bitcoin; a money separate from the State with a fixed supply of 21M which cannot be arbitrarily inflated.
Bitcoiners know we need to cure the base layer disease, not just treat the symptoms while politicians kick a can full of worthless money down the road until it lands at the feet of our children.
Bitcoiners refuse to abdicate responsibility. Bitcoiners refuse to pass this disease on to our children. Fiat is the disease, and we know we must cure it.
It will not be easy, but it must be done.
We need to fix the money.
Study Bitcoin. https://bitcoinpodcast.net https://primal.net/walker
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A vision for content discovery and relay usage for basic social-networking in Nostr
Or how to make a basic "social-networking" application using the Nostr protocol that is safe and promotes decentralization.
The basic app views
Suppose a basic "social-networking" app is like Twitter. In that, one has basically 3 views:
- A home feed that shows all notes from everybody you follow;
- A profile view from a specific user that shows all notes from that user;
- A replies view that shows all replies to one specific note.
Some Nostr clients may want to also provide another view, the global feed which shows posts from everybody.
A simple classification of relays
And suppose that all existing relays can be classified in 3 groups (according to one's subjective evaluation):
- spammy relays, in which people of any kind can post whatever they want with no filters at all;
- safe relays, in which there are some barriers to entry, like requiring a fee, or requiring some cumbersome user registration process, and spammers or people who post bad things are banned -- but this is still a relay fundamentally open to anyone (although this is also subjective depending on the kind of restrictions);
- closed relays, in which only certain kinds of people enter, for example, members of a group of friends or a closed online community.
How to follow and find posts from a given profile
To follow someone on Nostr, it is necessary to know one or more relays in which that person is publishing their notes, otherwise it is impossible to fetch anything from them.
When a user starts to follow someone, that may be done through 4 different ways:
- from seeing that person in the app
- using an
nprofileURI - using a NIP-05 address
- using a bare pubkey ('npub`)
Situation 1 may happen when that person is seen in the replies of yours or someone else's post, on a global feed post, or from a note referenced or republished from them by someone else. When that happens, it is expected that the references (in
eandptags) contain relay URLs. We must them inject that information to tentatively associate that person with a relay URL at that first contact.In situations 2 and 3 both the
nprofileand the NIP-05 addresses should contain a list of preferred relays for that person, so we can bootstrap the relay list for that person based on that.In situation 4 there is no relay list, so we must either prompt the user through an annoying popup or something -- or it can try searching for that pubkey in one of their known relays. This remains an option for the other methods too.
Once we have relay URLs for a given profile we can use these relays to query notes from that pubkey. As time passes that user may migrate to other relays, or it may become known that the user is also posting to other relays. To make sure these things are discovered, we must pay attention to hints sent in tags of all events seen everywhere -- from anyone --, and also events of kind 2 and 3, and upgrade our local database that has the knowledge of relationship between profiles and relays accordingly.
Rendering the app views
From what we've gathered until now, we can easily render the home feed and the profile view. To do that it just uses local information about relationships between profiles and relays and fetch notes:
- for the home feed, from all people we're following;
- for the profile view, from just that specific profile.
Since we'll be asking for very specific data from these relays, we do not care about where they're safe or not. They will never send us spam (and if they do that will just be filtered out since it wouldn't match our strict filter).
Now whenever the user clicks on a note we will want to display the replies view. In this case we will just query only the safe and the closed relays, since otherwise spam might be injected into the application. The same principle applies to the global feed view.
Other heuristics and corner cases
There are probably many corner cases not covered in this document. This was meant to just describe one way that seems to me to be sufficiently robust for a decentralized Nostr.
For example, how to display a note that was referenced by someone? If it has a relay hint we query that relay. If it doesn't we can try the relays associated with the person who have just mentioned it, or the same relay we've just seen the note that mentioned it -- as, when mentioning it, one might have published it directly to their own relays -- and so on. But all this may fail and then it is probably not a big deal.
Final thoughts
More important than all, is that we must keep in mind that Nostr is just a very loose set of servers with basically no connection between them, there are no guarantees of anything, and the process of keeping connected to others and finding content must be addressed through many different hackish attempts. To write Nostr applications and to use Nostr one must embrace the inherent chaos.
-
 @ affa3201:94121ac0
2024-04-19 19:58:24
@ affa3201:94121ac0
2024-04-19 19:58:24Opinion about Wallet of Satoshi (android)
Overall fast and reliable. Simplistic and elegant UI. Fees for lighting transactions are manageable. Works quite efficiently for small payments would not recommend for larger payments . Best wallet for beginners. Has KYC services if you choose to buy or sell bitcoin. Basically the best wallet if you plan on just sending and receiving sats.
WalletScrutiny #nostrOpinion
-
 @ 0403c86a:66d3a378
2024-04-19 19:15:46
@ 0403c86a:66d3a378
2024-04-19 19:15:46Serie A Secures Five Spots in Next Season's Revamped Champions League
In a significant achievement for Italian football, Serie A has guaranteed five clubs in next season's expanded Champions League. This comes after Italian teams secured a top-two spot in the UEFA coefficient standings.
The UEFA coefficient rankings, which determine the number of places each association is awarded in the Champions League, are calculated based on the results of each association's clubs in the five previous seasons of UEFA club competitions.
Roma and Atalanta both made impressive strides in the Europa League, securing spots in the semi-finals on Thursday. Meanwhile, Fiorentina continues to shine in the Europa Conference League, reaching the last four. These performances have boosted Italy's coefficient to 19.428 points, surpassing Germany (17.928 points) and England (17.375 points).
This stellar performance means Italy will take one of the two extra spots in the Champions League. The tournament is set to expand from 32 to 36 teams in the group stage from next season.
The additional spots will be allocated based on a new system. The team that finishes third in the championship of the association ranked fifth in the UEFA association coefficient rankings will now qualify for the group stage. The remaining two spots will be awarded to the clubs with the highest club coefficient that have not already qualified for the Champions League, but have qualified for the Europa League or the Europa Conference League.
This is a significant milestone for Serie A, reflecting the strength and competitiveness of Italian football. The achievement is expected to boost the league's reputation and attract more global attention, promising an exciting season ahead.
Dembélé's Stellar Performance Earns Him UEFA Champions League Player of the Week
Ousmane Dembélé, the 26-year-old forward, entered the second leg of the UEFA Champions League quarterfinal down against FC Barcelona knowing he might face hostility from the home crowd. However, Dembélé turned the jeers into motivation, delivering a memorable performance that has earned him widespread acclaim.
Dembélé's standout display helped Paris Saint-Germain (PSG) defeat Barcelona 6-4 on aggregate, securing their spot in the semi-finals. The Frenchman was named the player of the match for his exceptional performance, and his achievements did not stop there.
On Friday, it was announced that Dembélé had been named the UEFA Champions League Player of the Week. This prestigious award recognizes the best individual performance in the competition during a given week.
Madrid Fan Hails Real Madrid's Victory Over Manchester City, Criticizes City's Supporters
Real Madrid secured a spot in the Champions League semi-finals after a thrilling penalty shootout victory over Manchester City at the Etihad Stadium. The win was a testament to Madrid's resilience and determination, and one away fan had a lot to say about the game and the two teams involved.
The ecstatic supporter started by acknowledging Pep Guardiola's coaching prowess. "I hate Guardiola, but I need to say he is one of the best coaches in the world," he said. However, he quickly shifted focus to City's supporters, expressing his disappointment in their lack of excitement and passion.
"City, they don't deserve this amazing team because the supporters...," he continued, before mimicking a key locking their mouth. He suggested that if this City team were playing for Manchester United, the fans would be much more enthusiastic.
The Madrid fan argued that City's supporters are not as passionate as those of Real Madrid, Manchester United, Bayern Munich, Juventus, or even Barcelona. He claimed that City's fans will realize why they are not as big a team as these other clubs.
"We show we are the big team in Europe and in the world," he concluded, emphasizing Madrid's status as one of the world's most successful and popular football clubs.
Arsenal's Champions League Dream: Four Key Areas for Improvement
Arsenal's recent elimination from the Champions League at the hands of Bayern Munich has highlighted the areas in which the Gunners need to improve to become genuine contenders for the competition. Despite their impressive progress under Mikel Arteta and their domestic success, there are four key areas where Arsenal must focus their efforts to get over the hump in Europe.
-
Striker: Arsenal's current striker options have struggled to find consistency in front of goal, and the team lacks a clinical finisher who can make the difference in tight matches. The Gunners must invest in a top-quality striker who can provide the firepower needed to compete with Europe's elite.
-
Midfield: Arsenal's midfield has been a strength in recent years, but there is still room for improvement. The team needs a dynamic midfielder who can control the game, break up opposition attacks, and provide the creative spark to connect Rice and Odegaard
-
Left-back: Arsenal's left-back position has been a problem area for some time, with no player establishing themselves as a consistent first-choice option. The Gunners need to find a left-back who can provide defensive solidity while also contributing to the attack.
-
Mentality: Perhaps the most significant area for improvement is Arsenal's mentality. The team has shown an inability to handle pressure in big games, and this has cost them in crucial moments. The Gunners need to develop a winning mentality, a never-say-die attitude that will allow them to overcome adversity and compete with Europe's best.
Dortmund's Remarkable Comeback Secures Semi-Finals Spot, but Questions Remain
Borussia Dortmund staged a remarkable comeback at home against Atlético Madrid to secure a semi-finals spot in the Champions League. The Westfalen stadium was a riot of colour and sound as the home team put on a show of attacking football, but questions remain about their ability to compete with Europe's best.
However, even as Dortmund toasted their victory, there were questions about whether they can be taken seriously as Champions League contenders. The team has a history of boom and bust performances, and their defence has been a major weakness this season.
Dortmund's next opponents, Paris Saint-Germain, are themselves not without flaws, but they have the firepower to punish porous defences. The German team will need to find a way to shore up their defence if they are to have any chance of progressing to the final.
Global Sports Central 🌐 #GSC360
-
-
 @ 4657dfe8:47934b3e
2024-01-08 19:37:37
@ 4657dfe8:47934b3e
2024-01-08 19:37:37Hey,
We're trying to maintain the most up-to-date and interesting list of various "LN apps" (Lightning and Nostr web apps) that can be used with Alby, calling it our Discover Page
However, for the past few weeks... we couldn't encounter anyting fresh and working. And it is very possible we overlooked some must-visit website.
What should we add to the Discover Page? Asking for nice recommendations.
We'll pay 2,100 sats per each! 😊 Cheers 🚀🚀
-
 @ 5e4e1309:1164206e
2024-04-23 21:46:01
@ 5e4e1309:1164206e
2024-04-23 21:46:01Opinion about Bitcoin Wallet - BTC Exchange (android)
'm outraged by Freewallet's exploitation of Cloudflare for their scams. It's time to stand up against such unethical behavior. Let's join forces and demand that Cloudflare takes action to stop Freewallet's abuses and protect users.
WalletScrutiny #nostrOpinion
-
 @ 52b4a076:e7fad8bd
2024-04-10 01:12:11
@ 52b4a076:e7fad8bd
2024-04-10 01:12:11Why this is happening
This happens due to an invalid real IP header.
You are most likely using
X-Forwarded-Foras the real IP header. Strfry expects the real IP header to contain just an IP, but theX-Forwarded-Forheader is a list of IPs, with every proxy adding the IP of where it got the request from.If a client specifies an X-Forwarded-For header, like
X-Forwarded-For: 1.1.1.1, your proxy will add the remote IP, like this:X-Forwarded-For: 1.1.1.1, 127.0.0.1When you use$proxy_add_x_forwarded_forin Nginx, this is what it is doing: appending the remote IP to the header.Strfry tries parsing
1.1.1.1, 127.0.0.1as an IP address, fails, and throws an exception.How to fix it
If you are using Caddy, just switch to
X-Real-IP.If you are using Nginx, you can add a real IP header like so, and switch to using it:
proxy_set_header X-Real-IP $remote_addr;You can also disable the real IP header, but this will cause problems if you use a write filter script or look at the logs.
-
 @ affa3201:94121ac0
2024-04-19 18:20:33
@ affa3201:94121ac0
2024-04-19 18:20:33Opinion about LifPay (android)
Simplistic custodial wallet with very simple features. Great for managing multiple accounts. The anonymous lighting address is a cool feature for those sensitive about privacy. Sending and receiving funds is quite efficient, the fees are low. Available even on desktop. The customer team is responsive. I think it's a hidden gem, no complaints in the time I have used it. Suitable for beginners and those just sending and receiving satoshis.
WalletScrutiny #nostrOpinion
-
 @ 2edbcea6:40558884
2024-01-07 22:05:42
@ 2edbcea6:40558884
2024-01-07 22:05:42Happy Sunday Folks!
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2.
The #NostrTechWeekly is focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) Update to NIP-07: Nostr Browser Extension
monlovesmango is proposing updates to the capabilities of the Nostr Browser Extensions. Currently, browser extensions are primarily used to enable usage of Nostr clients without giving that client your Nostr private key.
Since NIP 44 was adopted, there are a few new Nostr actions creating encrypted content over Nostr that clients will want users to authorize without requiring users to input their private key. This NIP adds those new Nostr actions as something browser extensions should support going forward.
2) (Proposed) NOSTR Decentralized Advertising Network
ionextdebug is proposing creating a marketplace for advertising that runs over Nostr.
For those unfamiliar, there’s a constant bid and ask process for advertising space on platforms like Youtube or Google Adsense. The sell side is offering up ad space (for example 5-25 seconds at the beginning of a Youtube video for users within a specific demographic), and the buy side is bidding to put their ad in that spot. The highest bid wins the spot. This all happens in milliseconds every time you see an ad online.
This proposal outlines how this could be coordinated over Nostr instead of in Google’s walled garden. The use case would require Nostr to operate in ways it wasn’t designed for, so it may struggle to work in practice, but the NIP is early in the process of development.
Notable Projects
nsecBunker Update 🔐
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft announced an update to nsecBunker that allows users to an OAuth-like experience when logging into Nostr clients.
Bunker providers are able to provide account creation to Nostr users that feels a lot like signing up for any legacy tech service (username, password, control over what each Nostr client can do on their behalf, etc). This creates a set of Nostr keypairs which are necessary to operate in the Nostr-verse, but they’re stored in the bunker.
When a Nostr client wants a user’s permission to read or write with those keys (e.g., to pull their timeline or help a user post something), the client asks the bunker for permission, which then asks the user if they want to grant that permission. Users are also able to have their bunker remember their selections of grant/reject permissions for a given Nostr client so that things are easier with fewer popups the next time around.
Additionally, users that are created and managed via nsecBunker have a lightning wallet and lightning address created automatically. If nsecBunker could also help folks manage their full Nostr profile (Kind 0 data like profile picture, name, etc,) this could be an out-of-the box solution for clients looking to add a simpler signup/login experience to new users that don’t mind giving up some control.
From what I saw in the code, the data (including Nostr private keys custodied by the bunker) are encrypted at rest, but currently that’s one key to encrypt all keys in the bunker. It may make sense in the future to extend the functionality to give users the ability to encrypt their keys with their own password, but there are downsides to that which may make self-custody the easier option.
There’s no lock-in for users since bunker providers can help users download their keys if they want to self custody or move to another provider.
This could be a foundational tool that allows an ecosystem of bunker providers emerge. Bunkers may be offered as part of Nostr clients, or independently; they may be offered for free, or for a fee. But the opt-in and interchangeable nature means that users will be able to choose what works for them, including moving to self-custody once they see the benefits. And self-custody may even just be a self-hosted bunker. 😉
Faaans 🎨
This is another project from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and although it’s still pre-launch, it has been teased as a Patreon replacement built on Nostr.
It seems like this project is one whose purpose and value is clear, but requires many capabilities that are novel to Nostr to be built first. From what I can see Faaans has built:
- Oauth-like flow using new nsecbunker functionality from 👆
- Ability to gate content until a Nostr user pays for it
- The presence of uploads and NIP 98 HTTP Auth makes me think that there’s a non-Nostr backend for handling uploads (maybe to also help with gating the content?)
Anyway, I’m excited to see how it turns out. Cutting out middlemen and giving creators full control over their relationship with their audience could be the killer app that brings a flood of usage and business to the Nostr ecosystem. 💪
Relay Auth to support privacy 🤫
NIP 42 allows relays to require clients to authenticate the user before the relay will take a requested action. This is useful, for example, for keeping DMs private.
By default all Nostr events can be queried by anyone that can connect to the relay. This is part of the magic of Nostr. But there are some kinds of Nostr events that likely should only be readable by a few folks. In the case of DMs, it makes sense to restrict who can download DM-type Nostr events to only those people involved in the DM.
This can be accomplished by relays requiring the user to authenticate with the relay before it returns DM-type Nostr events for that user. This announcement is that Damus looks to be adding support for Relay Auth, which may help with any number of features that can benefit from more privacy.
Latest conversations: Web of Providers
The culture of Nostr currently highly values self-custody, decentralization, and “don’t trust, verify” which is very admirable. It’s woven into the protocol itself. There are downsides to operating on these principles, but most of us judge it to be worth it.
It’s usually possible to have our cake and eat it too (have a nice experience and maintain our values), but it requires technological advances and building products based on those advances. This takes time.
In the interim, devs may build something that’s less self-custodial, less decentralized, but far easier to use. Most of the time this middle ground is far better than using some legacy system that’s completely custodial, centralized, and locks users in. But that’s only the case if it’s a stepping stone to a solution that is everything we need.
Example: Custodial Lightning Wallets
When Wallet of Satoshi stopped operating in the US, I definitely felt how vulnerable the zap ecosystem was to some overzealous bureaucrats. But I was able to switch providers in a matter of minutes and get back to sending and receiving zaps.
I definitely considered moving to Zeus or Mutiny or reviving my own Lightning Node on my Bitcoin Node, but it’s all still too difficult to manage a reliable experience passively.
On net, I’d argue that using custodial lightning is better than using Venmo or something to send and receive zaps. At least we’re operating in Bitcoin and not fiat.
A must have: a competitive ecosystem
The trade offs of a middle ground are easier to live with if there’s a robust and competitive ecosystem.
In the case of custodial lightning wallets, we’re encountering the issue of a lack of robustness. There are only a handful of providers that are able to handle zaps. Losing Wallet of Satoshi was a significant blow. We definitely need more lightning wallet providers in order to be robust against nation-state attack.
The ecosystem must also be competitive. People need to be able to switch providers or move to self custody with little or no cost.
NSecBunker
NSecBunker is an excellent example of a middle ground solution that maintains manageable trade offs while working to discover a more perfect solution.
If Nostr users want to use bunkers, it’s trivially easy to spin up a bunker and provide it to them. Existing clients may spin them up, or people looking to start a business in the Nostr ecosystem may create bunkers (maybe with some extra features) and charge for them.
At the end of the day, this technology is built in such a way that interoperability is easy and users aren’t locked in. The lift for Nostr clients to support bunkers is small, so bunkers may soon be as widely used as the Nostr browser extensions. Since users aren’t locked in to any bunker provider, it’ll be easy for a web of providers to pop up and serve users in unique ways to discover what works best.
Build tech to enable a web of providers
Building Nostr tech that has interoperability top of mind supports the Nostr ethos and enables the ecosystem to develop incrementally without giving up our values. Luckily, the protocol itself encourages interoperability with its very architecture. 🫡
Let’s reward devs when we see them doing this important work, they’re building an immense amount right now and it’s an incredible privilege to witness and beta test. 🍻
Until next time
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 6389be64:ef439d32
2024-04-23 21:44:56
@ 6389be64:ef439d32
2024-04-23 21:44:562024-04-23 at 14:36
Tags: #energy
Networks and Entropy
It being the case that most fungi form networks of cells in a bifurcated hyphal format I can't help but wonder if a "network" is an entropy directed development in the natural world. Matter and systems of matter in the universe tend to move to the lowest energy state. That being said, is a network a "lowest energy state"?
How is entropy related to networks and if we can answer that question, is the knowledge leverageable in some way?
References
[[Sheldrake-Entangled Life]]
Core Notes
[[Network Formation As A Result Of Entropy]]
Location
-
 @ ae1008d2:a166d760
2024-04-09 13:38:24
@ ae1008d2:a166d760
2024-04-09 13:38:24I just wrote a short StackerNews post, sharing about this platform Highlighter. Maybe we'll get more users to check this out and start creating!
Feel free to take a glance 👉Highlighter.com, Nostr Creator Content Platform
-
 @ 38d0888d:bd8e1246
2024-04-19 06:38:58
@ 38d0888d:bd8e1246
2024-04-19 06:38:58In contemplating the nature of a higher power within our modern context, one must recognize an all-encompassing energy that intertwines every facet of life and existence, openly revealing the unity among humanity. This force transcends individual consciousness, permeating through social, cultural, and global dimensions.
Viewing this higher power as the embodiment of entirety signifies the integral role of every person, culture, and society within this unified whole. It acts as a binding force, connecting all facets of humanity, emphasizing our interconnectedness and interdependence.
Within this framework, the universality and completeness of this higher power stand as pivotal elements in fostering global harmony. Recognizing our collective belonging to something greater motivates humanity to seek consensus, mutual understanding, and respect for diversity, paving the way for harmonious coexistence.
Emphasizing the criticality of clear comprehension and transparency, one must underscore the importance of shared understanding and knowledge about this higher power, cautioning against misinformation and concealment, which can lead to moral, spiritual, and technological decline for humanity. The aim is to facilitate the revelation of this higher power in interpersonal relationships and on a global scale. Embracing a belief in a transcendent intelligence that surpasses human understanding and observable natural processes, humanity endeavors to manifest this power of unity in both actions and inner lives. Aligned with the values of compassion, justice, and mutual respect, humanity should aspire to create a world where all individuals can thrive and flourish.
-
 @ a012dc82:6458a70d
2024-04-19 02:15:06
@ a012dc82:6458a70d
2024-04-19 02:15:06Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
WHY SHOULD I WITHDRAW MY BITCOIN FROM AN EXCHANGE?
You don't really own anything if you need someone else's permission to utilize it. not your keys, not your money. Heard that one before? Yes, really. Bitcoin private keys give you access to your digital currency, but you have no control over your funds until you make a withdrawal. When you leave your bitcoin on an exchange, you are putting a lot of faith in that service.
WHAT ARE BITCOIN PRIVATE KEYS?
Private keys on the Bitcoin network function similarly to passwords on other networks. The private keys are required to transmit or spend bitcoin. If you don't have these keys, it's probably because an exchange like Coinbase or another third party is keeping them safe for you.
Using a third party as a custodian for your bitcoin exposes you to a number of extra threats. If you store your bitcoin with a custodian, you will need their approval before you can spend "your" bitcoin. It's like asking a friend to keep track of the code to the family safe.
WHAT ARE THE TRADE-OFFS WITH LEAVING YOUR BITCOIN ON AN EXCHANGE?
To put it simply, if you lose access to your bitcoin, you lose access to everything that makes bitcoin unique. Its censorship resistance has been broken. Sending and spending money is now restricted. In a liquidation scenario, your bitcoin may be sold without your consent. It is possible to halt or even cancel your financial transactions. Your bitcoin wallet might be frozen at any time. Trusting and putting your bitcoin on an exchange exposes you to numerous big risks:
A user's faith in an exchange's commitment to not rehypothecate bitcoin is essential.
You are placing your faith in the exchange to safely store your bitcoin.
You have to believe that the exchange you're buying bitcoin from has the coins they're offering you.
Confidence in an exchange's lack of fractional reserves is essential.
You have to have faith that the exchange you choose will not lend your bitcoins to day traders.
You have to believe in the reliability of an exchange to fulfill your withdrawal requests.
For your transactions to remain private, you must have faith that your exchange is not collecting and selling this data.
You are taking a risk if you deposit bitcoins on an exchange in the hope that they will not be liquidated if the exchange goes bankrupt.
YOU MUST USE BITCOIN TO FULLY APPRECIATE IT
When you get your hands on this new technology, you'll see its value in ways that aren't obvious from reading about it. An in-depth knowledge of bitcoin requires more than just reading about it.
The Bitcoin network may be used in several fashions. Make a little Bitcoin purchase. Disseminate them to the people around you. Bring all your UTXOs together. Create a link in the lightning network. Find out how to make a new transaction and announce it to the network.
For more clarification, let's use an example: It doesn't matter how much someone studies automobiles or how well they understand how an engine works; if they've never driven before and are expected to do so, there's a good probability they'll have trouble getting from point A to point B.
HOW TO WITHDRAW YOUR BITCOIN FROM AN EXCHANGE:
Depending on the platform you're using, you may or may not be able to withdraw your bitcoin from the exchange. We've compiled a list of the most prominent Bitcoin exchanges, along with withdrawal guides for each:
-
Coinbase: https://help.coinbase.com/en/prime/trading-and-funding/withdrawing-crypto-assets
-
CashApp: https://cash.app/help/us/en-us/3106-bitcoin-withdrawal-instructions
-
Binance: https://www.binance.com/en/support/faq/115003670492
-
FTX: https://help.ftx.us/hc/en-us/articles/4409213996311-How-to-Withdraw-Crypto
-
BlockFi: https://help.blockfi.com/hc/en-us/articles/4416344067092-Requesting-a-Withdrawal-Crypto-
-
Robinhood: https://robinhood.com/us/en/support/articles/cryptocurrency-wallets/
-
KuCoin: https://www.kucoin.com/support/900005758426-How-to-Withdraw-Crypto
-
Revolut: https://www.revolut.com/help/wealth/cryptocurrencies/withdrawing-cryptocurrencies
-
BitStamp: https://www.bitstamp.net/faq/how-to-withdraw-cryptocurrency/
-
Swan: https://help.swanbitcoin.com/hc/en-us/articles/360058709153-How-do-I-withdraw-my-Bitcoin-from-Swan-
-
River: https://river.com/support/knowledge-base/articles/bitcoin-withdrawal
-
CoinCorner: https://support.coincorner.com/hc/en-us/articles/360001956794-How-do-I-send-Bitcoin-
-
BitFlyer: https://bitflyer.com/en-us/faq/16-18
-
CoinBerry: https://help.coinberry.com/hc/en-us/articles/4539555681041-How-to-Withdraw-Crypto
-
BitMex: https://support.bitmex.com/en/support/solutions/articles/13000094250-how-to-withdraw-crypto
Conclusion
The current suffering is genuine. Having one's trust broken must be an excruciating experience. It's important to remember that all of your negative emotions, such as regret, guilt, wrath, melancholy, and fury, have a common origin. For so long, Bankman-Fried was able to get away with his falsehoods because "crypto" is based on a lie: what claims to be a revolution is in fact merely the fiat system par excellence. Because everyone on the network shares the same information, Satoshi Nakamoto's novel system eliminates the possibility of double counting. When some thought crypto might disappear, this didn't.
FAQ
Where does FTX stand now? As scandal-plagued FTX filed for Chapter 11 bankruptcy protection earlier this month, founder Sam Bankman-Fried resigned from his position as CEO. Once worth $32 billion, FTX's market cap plummeted in a couple of days when the CEO of Binance, a competitor exchange, said that Binance would sell its FTT tokens.
What exactly is Bitcoin's function? Does bitcoin serve any useful purpose? Bitcoin was designed specifically for online monetary transactions. The idea behind the digital currency was to provide an alternate payment system that could function independently of any one authority while otherwise being completely functional as a currency in its own right.
What's the purpose of Bitcoin? It is FTX.US's claim that all assets and client data on the platform are protected by basic security procedures. One such safety measure is the opportunity to use a different password for cash withdrawals.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ 3bf0c63f:aefa459d
2024-01-06 00:39:23
@ 3bf0c63f:aefa459d
2024-01-06 00:39:23Report of how the money Jack donated to the cause in December 2022 is being spent.
Bounties given
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 947c8c3e:22e2d6ea
2024-04-09 00:59:19
@ 947c8c3e:22e2d6ea
2024-04-09 00:59:19Server Address: mine.ghostgrid.network Port: 30000
Introduction
Minetest is an open-source voxel game engine that allows players to create and play in infinite worlds. This guide will walk you through downloading and installing Minetest, creating an account, and joining the specified server.
Downloading and Installing Minetest
For Windows Users
- Visit the Official Website: Navigate to Minetest's official download page.
- Download the Installer: Click on the Windows option to download the installer.
- Run the Installer: Open the downloaded file and follow the installation prompts.
For macOS Users
- Visit the Official Website: Go to Minetest's download page.
- Download for macOS: Click on the macOS option and download the file.
- Install Minetest: Open the downloaded file. Drag and drop the Minetest icon into your Applications folder.
For Linux Users
- Using a Package Manager: For most Linux distributions, Minetest can be installed directly from the package manager. For example, on Ubuntu, you can use:
bash sudo apt-get install minetest- Compiling from Source: Alternatively, you can compile Minetest from source. Instructions can be found on the official website.
For Android Users
Downloading and Installing Minetest
- Open Google Play Store: On your Android device, launch the Google Play Store app.
- Search for Minetest: Tap on the search bar at the top of the screen and type in "Minetest". Press enter or the search icon.
- Install the App: Find the official Minetest app from the search results and tap "Install" to begin the download and installation process.
Registering an Account and Joining the Server
On Android, the process for registering an account and joining a server is similar to that on other platforms, with some minor differences in the user interface.
- Launch Minetest: Open the Minetest app once it's installed.
- Access the Main Menu: Tap on the three dots in the upper right corner to access the main menu and select "Join Game".
- Server Details: Tap on the "New" button to add a server. You'll be prompted to enter the server details. Use the following information:
- Server Name: This can be anything you like; it's a label for your convenience.
- Address: Enter
mine.ghostgrid.network. - Port: Type in
30000.
- Create Your Account: Enter a username and password in the provided fields. This will register your account for this server.
- Join the Server: With the server details filled in and your account created, tap "Connect" to join the server.
Registering an Account
To join a server in Minetest, you'll need to create an in-game account. For most servers, this can be done directly when you join a new server. Keep in mind, the process might slightly vary based on the server settings.
- Launch Minetest: Open the Minetest application.
- Select 'Join Game': Find and click on the 'Join Game' tab at the top.
-
Enter Server Details: You'll see fields to enter a server's address and port. Use the following details:
- Server Address:
mine.ghostgrid.network - Port:
30000
- Server Address:
-
Choose a Name and Password: You will be prompted to enter a username and a password. This is effectively your registration process for this server.
Joining the Server
After registering your account, you're all set to join the server.
- Enter Your Credentials: Input the username and password you just created.
- Join the Server: Click 'Connect' to join the server.
Conclusion
Congratulations! You're now ready to explore the vast world of Minetest on the server at
mine.ghostgrid.network. Remember, each server in Minetest can have its unique set of rules and mods. It's a good idea to familiarize yourself with them to enhance your playing experience.Enjoy your time in our server, and don't hesitate to explore the endless possibilities within its worlds.
-
 @ 28050c32:b88edee5
2024-04-18 15:13:15
@ 28050c32:b88edee5
2024-04-18 15:13:15Chef's notes
This super yummy and super easy to make eggplants are gonna leave you wanting more
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 2
Ingredients
- 2 eggplants 🍆
- 2 or 3 minced garlic cloves 🧄
- 1 finely minced onion 🧅
- 1 bell pepper, diced 🫑
- 2 carrots peeled and diced 🥕
- Salt and pepper to taste 🧂
- Vegan cheese optional 🧀
- Olive oil 🫒
Directions
- Prepare the Eggplants: Wash the eggplants and cut them lengthwise into halves. Scrap the inside of the eggplants and then chop them. Reserve. Place the empty eggplants on your a baking sheet lined with parchment paper.
- Prepare the Filling: In a skillet, heat some of olive oil over medium heat. Add the minced garlic and chopped onion, and sauté until fragrant and translucent, about 2-3 minutes. Add the diced bell pepper and cherry carrots along with the inside of the eggplants to the skillet, and cook for another 5 minutes or until they soften slightly. Season the vegetable mixture with salt and pepper. Stir well to combine.
- Assemble the Dish: Place a some of the vegetable mixture on each eggplant slice.
- Optional: If desired, sliced some vegan cheese over the top of each eggplant with vegetables.
- Bake: Put the baking sheet to the oven and bake for 30 minutes at 180 C, or until the cheese is golden brown and crispy.
- Serve: Once baked, remove from the oven and let cool slightly before serving. Enjoy your delicious vegan baked eggplants!
-
 @ 47750177:8969e41a
2024-04-08 12:00:00
@ 47750177:8969e41a
2024-04-08 12:00:0025.2 Release Notes
Bitcoin Core version 25.2 is now available from:
https://bitcoincore.org/bin/bitcoin-core-25.2
This release includes various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux kernel, macOS 10.15+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
Gui
- gui#774 Fix crash on selecting "Mask values" in transaction view
RPC
-
29003 rpc: fix getrawtransaction segfault
Wallet
-
29176 wallet: Fix use-after-free in WalletBatch::EraseRecords
-
29510 wallet:
getrawchangeaddressandgetnewaddressfailures should not affect keypools for descriptor wallets
P2P and network changes
-
29412 p2p: Don't process mutated blocks
-
29524 p2p: Don't consider blocks mutated if they don't connect to known prev block
Credits
Thanks to everyone who directly contributed to this release:
- Martin Zumsande
- Sebastian Falbesoner
- MarcoFalke
- UdjinM6
- dergoegge
- Greg Sanders
As well as to everyone that helped with translations on Transifex.
-
 @ 16f1a010:31b1074b
2024-04-18 13:56:27
@ 16f1a010:31b1074b
2024-04-18 13:56:27
One of the most important things to consider when buying a house is the quality of the grocery district.
As the name implies, the grocery district determines which public grocery store you and your family get to use. District maps are drawn by the government to ensure each grocery store has an appropriate number of patrons based on its capacity. Most residents are assigned to the public grocery store that is closest to their home.
Groceries are paid for primarily by local taxes. If residents go to their local public grocery store, they get their weekly groceries without any additional out-of-pocket cost. However, they cannot get groceries from a public grocery store that’s outside of their district.
In most purchasing decisions, people are not limited to a single provider in their jurisdiction.
In theory, all of the public grocery stores are supposed to provide equal access to high-quality food. Indeed, this is largely why government got involved in the grocery business in the first place. Politicians believed that access to food was a fundamental right and they were concerned that a free enterprise model would inadequately serve poor people. After all, there is not much profit to be made selling to those of lesser means. Or so it was argued at the time.
Unfortunately, it’s clear that wide disparities still exist in the public system of food distribution. Poorer neighborhoods tend to have public grocery stores that offer bad service, limited selection, and occasionally even unsanitary conditions. It’s not uncommon to find food well beyond its sell-by date.
Meanwhile, in richer neighborhoods, public grocery stores are typically high quality. Most approximate the quality and selection that existed in chains like Fred Meyer, Trader Joe’s, or Albertsons before the system of public food distribution was implemented.
This is why it has become essential to consider the quality of the grocery district when looking for a place to live. Live in a good district, and you’ll get diverse, healthy food for your family. Live in a bad district, and your family’s well-being is likely to suffer.
Critics argue that this system is especially harmful to poor people. In most purchasing decisions, people are not limited to a single provider in their jurisdiction. If they don’t like the bank or the mall that’s closest to them, they can drive to one that’s a little farther away that they like better. But in groceries, if they don’t like the public store that’s in their district, the main solution is to move elsewhere. If they can’t afford to move to a better grocery district–and many cannot–then they are likely to be stuck with a bad public grocery store.
One other option for residents in low-quality grocery districts is private grocery stores. In most areas, there’s no law preventing people from getting their groceries from private providers instead of the public system. However, since people utilizing the private system do not get a refund for the taxes they paid into the public system, they effectively end up paying twice. This naturally makes the private solution less accessible to families of lesser means.
Of course, no one thinks this public grocery system is ideal–especially since it retains the very inequality it hoped to eliminate. But while everyone agrees there is a problem, there is little agreement on the possible solutions.
It remains to be seen which reforms will be tried next, but history suggests that we should not be too optimistic.
The Real World
The system described above probably sounds absurd. But, in many respects, it is the system we use to provide education in the US.
Education is important. It might be too important to leave to the government.
One often hears that education is too important to leave to the whims of the market. Yet food is even more important; it’s a prerequisite before education can be considered. In spite of this, the (relatively) free market in food seems to work quite well.
Consumers get a wide variety at a low cost. Even people that have niche dietary requirements like gluten-free or vegan have products suited to them. And while complaints about the quality of public education are rampant, one rarely hears objections about the quality of the grocery stores. In the latter case, people don’t have to complain; they just take their business to someone who will serve them better.
As a consequence, the inequality that exists with respect to grocery stores is actually much smaller than the inequality that exists in education. Whether you’re in a poor area or a middle-class area, the local Walmart is pretty much going to be the same Walmart. Even the gap in offerings between Walmart and, say, Whole Foods, is not so severe. One could still easily purchase the ingredients for a healthy diet in either establishment. But in public education, the difference between good schools and bad can be night and day. It could mean the difference between children graduating or dropping out, progressing or falling behind.
So perhaps it’s time to turn the conventional wisdom on its head. Education is important. It might be too important to leave to the government.
economics #food #publicschools
I originally found this article on https://fee.org (Foundation for Economic Education) Link to the original article
-
 @ 97c70a44:ad98e322
2024-01-05 22:03:37
@ 97c70a44:ad98e322
2024-01-05 22:03:37Today marks the biggest release so far in Coracle's history. There have been many good days, like when I introduced Coracle to the nostr telegram group, or when I got my fellowship with FUTO, or when I got my grant from OpenSats, or when I got to speak at Nostrasia. But in terms of realizing the vision I've had for the software - for over two years - today is the day.
Coracle now has private groups.
This means you can now send almost any nostr event over an encrypted channel to the rest of the group's members. This is substantially different from group chats, in that it uses rotating shared keys to provide weak forward secrecy, better scaling, and dynamic member access. This more closely approximates one of the most popular social media products in existence - The Nostr is now a direct competitor of The Facebook.
I built this for my community. I wanted something "good enough" to entice people to leave the advertising-fueled surveillance honeypot that is Facebook. In order to work, it needed to at least support notes, events, and marketplace listings. Although support is still quite basic, Coracle has checked all three of these boxes.
Before I get into the details though, it's important to mention that these groups should not be considered "private" any more than Facebook groups or Mastodon servers are (although privacy is substantially better). A better analog might be WeChat, which uses encryption with the same set of trade-offs. So don't post anything to private groups that might get you in trouble!
With that said, it's possible to run a highly private group. The backbone of this spec is e2e encryption, but relay selection can play an important part in hiding metadata from the rest of the network. If you have a relay you trust to protect notes and not share metadata, your security is significantly increased.
Prior art
Nostr-compatible group products aren't a totally novel thing, as it turns out. In fact draft NIP 112 has been around since June, and is already implemented in ArcadeCity. So why am I creating a new standard? I'l get into the positive benefits of my approach more below, but the quick answers are:
- The new encryption standard is going to break compatibility anyway. If we can end up with a better spec, now is the time.
- ArcadeCity development seems to have stalled.
- NIP-72 communities already have a ton of traction, and match what I'm trying to achieve with encrypted channels.
Of course I'm highly indebted to the project, the design of which is still visible in my final design.
Another product that exists to do something similar in a nostr-compatible way is Soapbox by Alex Gleason. This is a great project, particularly since his Mostr project bridges the ActivityPub world and Nostr. ActivityPub works well for highly centralized communities, but the architecture suffers from this centralization too. In particular, not even DMs are e2e encrypted, and just like regular notes are protected only by authentication enforced by servers.
Finally, there's NIP 29, which is fiatjaf's competing groups project. This has some interesting properties, for example the ability to "fork" a group by linking events together. However, similar to ActivityPub it relies exclusively on relays to protect user privacy, and in a fairly non-standard way. You do get to take advantage of nostr's multi-master architecture though, and signatures are also stripped from events in order to discourage propagation through the network.
None of these solutions quite satisfied me, so I built my own.
How it works
One of the coolest things about a NIP 72 community-based group spec is that is supports a spectrum of privacy requirements. A group admin might choose to publish group metadata privately so that it's only visible to the group, publicly so that other people can find the group and ask to join, or leave off a private component entirely.
Likewise, since private groups are backwards-compatible with public communities, it's easy to add a private component to existing groups. This can be useful especially for groups run by a business or content publisher, since public exposure is a good thing but certain group members might have more or less access. This could be used to support a patreon-type model, automating group membership based on subscription tier, for example.
An important aspect of the design that makes automation possible is the concept of a dedicated administration key. By decoupling this key from the original creator of the group, ownership can be shared as simply as sharing the key. This allows multiple admins to manage the group simultaneously either manually or using automations built into the group relays or special purpose bot-clients.
This of course raises the issue of admin access revocation, which isn't possible - that is, until we have a solution for key rotation for normal accounts. Once that's in place, the same process can be used to rotate group admin keys.
In the meantime, it's also trivial to reduce the exposure an admin key gets. You wouldn't generally want to simply paste the key wherever it's needed, but luckily that problem has already been solved as well. Instead of giving every admin or admin bot the key, it's trivial to set up an nsecbunker that authorizes each admin client - and can revoke access as needed.
This level of administration is of course fairly complex, but I think it's important to think through the requirements businesses and other advanced users will eventually impose and anticipate them as we're able, not through over-engineering, but through simple concepts that can be reused.
One other neat feature of this NIP is the definition of invite codes, which are essential for running a private group at any kind of scale. When requesting access to a group, a user can send along a "claim", which can be anything - for example a static invite code, a payment receipt, or an explanation of why they want to join. This claim can be validated by hand by a human, or processed by a bot to instantly admit the new member to the group.
When a new member is admitted to the group, the admin can either share an existing access key with them, or they can rotate the key for the entire group. If relays expire access keys after a certain amount of time, this can create a weak form of forward secrecy, where attackers won't be able to access old content, even if they gain access to the admin key.
Limitations and Future Work
The bar for new nostr clients has risen significantly since I first put Coracle out there. The new groups component is far more mature than Coracle was for much of its early life, but it has its rough edges. Many of these just need to be smoothed out through further UX work, but some are more technical in nature.
- The groups spec relies on NIP 44, which isn't yet available in most signer extensions. That means that unless you log in with your private key (please don't), you won't be able to create or gain access to any private groups.
- Hybrid groups (public groups with a private area) aren't really tested yet, or fully supported in Coracle's UI. It's an open question whether this is even a good idea, since it becomes pretty hard for users to know if they're posting publicly or privately in every context.
- Moderation is not implemented, so if you're creating a public group there is currently no way in Coracle to approve posts. Also, groups created in Coracle don't show up in Satellite for some reason — this is something I'll be working on improving.
- Whether this approach actually scales is another question. It's very hard to build member lists of hundreds of thousands of people, and without a relay helping to filter events, it might become prohibitively expensive to download and analyze all the events posted to a group. We'll see what develops as the design matures and the implementation undergoes stress testing.
Conclusion
Something I like about both nostr and bitcoin is that it empowers the users of the software. The corollary of this of course is that it's important to exercise this power with care - real damage can be done with this group spec, just as real damage can be done to bitcoin holders through low entropy key generation or poor key handling practices. So please, if you're going to implement this spec, communicate clearly with your users its limitations, and encourage them to run their own relays.
Nevertheless, I am stoked to be another 1% closer to my goal of helping my community - and anyone else who uses nostr - to exercise individual sovereignty and protect their freedom and privacy. Let's keep at it.
-
 @ 8f69ac99:4f92f5fd
2024-04-18 10:54:00
@ 8f69ac99:4f92f5fd
2024-04-18 10:54:00No discurso moderno em torno do capitalismo, não é incomum encontrar veemente oposição e crítica. Desde acusações de exploração a pedidos da sua queda, o capitalismo muitas vezes encontra-se na mira do debate ideológico. No entanto, sob a superfície desses argumentos, reside uma complexa rede de motivações psicológicas e crenças filosóficas que impulsionam o sentimento anticapitalista.
A Deturpação do Capitalismo
Desde a sua criação, o capitalismo tem enfrentado uma enxurrada de deturpações e distorções por parte dos seus críticos. Seja alimentada por preconceito ideológico ou genuína ignorância, essas deturpações contribuíram para uma percepção negativa generalizada do capitalismo. Por exemplo, os críticos frequentemente retratam o capitalismo como um sistema que leva inerentemente à desigualdade de riqueza, desconsidera o bem-estar social e prioriza o lucro corporativo sobre o bem-estar dos indivíduos. No entanto, evidências crescentes mostram os benefícios do capitalismo, como aumento do crescimento económico, produtividade e inovação. Apesar dessas evidências, a deturpação persiste, tornando o capitalismo um dos conceitos mais mal representados na história cultural.
Capitalismo difere do que vemos hoje, um híbrido distorcido de mercantilismo e estatismo. No capitalismo puro, o governo desempenha um papel mínimo, apenas fornecendo as infraestruturas mínimas necessárias para um mercado livre funcionar de forma eficiente. O que temos hoje é frequentemente um Estado forte que interfere nos mercados, desvirtuando o princípio básico de oferta e procura, levando à inflação e ao desequilíbrio económico.
A confusão entre capitalismo e esta forma distorcida leva muitos a concluir incorretamente que o capitalismo resulta em desigualdade e injustiça social. No entanto, o capitalismo real, baseado em concorrência leal e sem interferência do Estado, não só gera prosperidade geral, mas também garante que o mérito seja recompensado e que cada indivíduo tenha oportunidades iguais de sucesso.
"Quando não há uma ligação entre esforço e recompensa, o que se obtém é menos esforço." - Thomas J. DiLorenzo
A Influência Corrosiva do Sistema Fiat
A moeda fiat desempenha um papel central na distorção do capitalismo, uma vez que o próprio governo tem o poder de criar dinheiro à vontade, inflacionando a moeda e degradando o valor da riqueza, e poupança, real. Isso gera instabilidade económica, permitindo que os ricos e os poderosos manipulem o sistema ao seu favor. Assim, o sistema fiat não é um reflexo verdadeiro do capitalismo, mas sim uma forma de mercantilismo velado, que prejudica os cidadãos comuns e perpetua a ideia de que o capitalismo é culpado por essas falhas.
Ao entender a verdadeira natureza do capitalismo e a influência corrosiva do sistema fiat, podemos começar a desconstruir as ideias preconcebidas sobre o capitalismo e a sua suposta culpa pela desigualdade e injustiça. A fim de garantir uma sociedade verdadeiramente justa e próspera, é crucial que o nosso sistema se afaste do estatismo e do mercantilismo e retorne às raízes do capitalismo verdadeiro.
Raízes Psicológicas do Anticapitalismo
No cerne do sentimento anticapitalista estão factores psicológicos profundos. Medo da independência, medo do fracasso, aversão à perda e suscetibilidade a vieses cognitivos podem desempenhar um papel significativo na formação das atitudes dos indivíduos em relação ao capitalismo.
- Medo da independência refere-se à apreensão em relação à autossuficiência e às responsabilidades que a acompanham.
- Medo do fracasso abrange a ansiedade em torno da possibilidade de cometer erros ou não corresponder às expectativas da sociedade, particularmente no contexto de sucesso económico.
- Aversão à perda significa a tendência de preferir evitar perdas em vez de adquirir ganhos equivalentes, levando a uma preferência pela segurança e estabilidade em detrimento do potencial crescimento e inovação.
Indivíduos que lutam com estes factores muitas vezes procuram a segurança e previsibilidade, tornando-os mais propensos a abraçar ideologias que prometem segurança coletiva. Além disso, a suscetibilidade a vieses cognitivos pode reforçar ainda mais os sentimentos anticapitalistas. Por exemplo, o viés de confirmação pode levar os indivíduos a concentrarem-se selectivamente em informações que confirmem suas crenças preexistentes sobre o capitalismo, enquanto descartam evidências contraditórias. Da mesma forma, a heurística da disponibilidade pode distorcer as percepções de risco, fazendo com que os indivíduos sobrestimem a probabilidade de resultados negativos associados ao capitalismo.
Compreender esses fatores psicológicos e vieses é crucial para fomentar um discurso e políticas informadas. Embora o capitalismo possa apresentar incertezas, também é um sistema que prospera na inovação e fomenta oportunidades económicas significativas. Ao reconhecer essas nuances psicológicas e promover o pensamento crítico, podemos trabalhar para abordar as preocupações subjacentes e cultivar um cenário económico mais equitativo e inclusivo.
A Fuga da Razão e da Realidade
Alguns indivíduos, motivados pelo desejo de escapar das exigências da razão e da realidade, buscam escravizar os produtores de bens e serviços da sociedade. Esses "escapistas" pretendem criar um Estado omnipotente na esperança de riqueza e honras imerecidas. Eles estão dispostos a dar obediência total ao Estado em troca de provisão e proteção contra os desafios da vida independente. Esse profundo medo de enfrentar a vida por conta própria, assumir a responsabilidade por suas acções e fazer julgamentos informados impulsiona seu comportamento irracional.
O único meio de alcançar o imerecido é através da força física, razão pela qual os inimigos do capitalismo são estatistas. Aqueles que buscam escapar da razão e da realidade só podem fazê-lo esperando que os seus objectivos, desejos ou medos possam de alguma forma triunfar sobre a realidade. Eles esperam que, escravizando os produtores de bens, os produtores económicos, criando um Estado omnipotente, de alguma forma cavalguem nos ombros dos membros racionais da sociedade, os membros produtivos, aqueles capazes de lidar com os factos da realidade de forma adequada, não apenas na questão da produção de bens materiais, mas em todas as questões.
A Moralidade do Altruísmo
Uma das ideologias que desafia o capitalismo é o conceito de altruísmo. Aqui, o autossacrifício é visto como a virtude mais elevada, e o interesse próprio é condenado. Isso cria uma tensão moral com o capitalismo, que se baseia na busca do ganho pessoal, em primeiro lugar. Aqueles que subscrevem fortes princípios altruístas podem ver o sucesso alcançado no capitalismo como inerentemente explorador, alimentando o sentimento anticapitalista.
Contexto Histórico: As raízes do altruísmo podem ser rastreadas até filosofias antigas como o estoicismo e o cristianismo primitivo. Essas escolas de pensamento enfatizavam a importância do dever para com os outros e de viver uma vida virtuosa, mesmo que isso significasse sacrifício pessoal. No entanto, o altruísmo desenfreado pode ter consequências indesejadas. Por exemplo, os experimentos utópicos do século 19, inspirados nos ideais socialistas de propriedade comum, muitas vezes lutaram com a ineficiência, escassez e a falta de motivação individual.
Subjectivismo e Estatismo
Paralelamente ao altruísmo estão o subjectivismo e o estatismo, ou estadismo, que oferecem estruturas alternativas para aqueles que consideram as demandas do capitalismo e da tomada de decisão individual intimidadoras. O subjectivismo pressupõe que a verdade e a realidade são subjectivas e podem ser moldadas pela percepção individual. O estatismo, por outro lado, defende um forte controle centralizado pelo Estado, prometendo fornecer segurança colectiva e estabilidade.
Essas ideologias podem ser vistas como um refúgio das incertezas e responsabilidades inerentes a um sistema de livre mercado (capitalismo). No entanto, o subjectivismo desenfreado pode levar ao relativismo e à negação dos factos objectivos, enquanto o estatismo excessivo invariavelmente sufoca a iniciativa individual e a inovação.
Tanto o altruísmo quanto os conceitos de subjectivismo e estatismo levantam questões importantes sobre o papel do indivíduo na sociedade e o equilíbrio entre responsabilidade pessoal e bem-estar social.
A Tentação do Totalitarismo
Para alguns, o atractivo do totalitarismo - uma forma extrema de estatismo - torna-se irresistível perante ameaças existenciais. A história está repleta de exemplos em que sociedades, temendo instabilidade ou invasão externa, abraçaram regimes que prometiam segurança e estabilidade à custa da liberdade e autonomia individuais.
Após a Primeira Guerra Mundial, a frágil República de Weimar na Alemanha debateu-se com depressão económica e turbulência política. Essa vulnerabilidade criou terreno fértil para o surgimento do Partido Nazi (Partido Nacional-Socialista dos Trabalhadores Alemães) totalitário. Hitler prometeu a restauração nacional, recuperação económica e uma Alemanha forte no palco mundial. Muitos alemães, ansiando por ordem e um sentido de orgulho nacional, estavam dispostos a ignorar a supressão nazi dos direitos individuais e das instituições democráticas.
Da mesma forma, a União Soviética sob Joseph Stalin fornece outro exemplo sombrio. Enfrentando a ameaça de invasão durante a Segunda Guerra Mundial, Stalin consolidou seu poder e esmagou impiedosamente a dissidência. Embora a União Soviética tenha finalmente repelido os nazis, isso aconteceu ao custo de milhões de vidas e de um regime totalitário que sufocou as liberdades individuais por décadas.
Estes exemplos históricos ilustram o poder sedutor do totalitarismo em tempos de crise. A promessa de segurança pode ser muito atraente, mas deve ser ponderada em relação ao alto preço da liberdade individual.
Resumindo
Ao mergulhar nas profundezas do debate em torno do capitalismo, torna-se claro que as objecções e críticas frequentemente têm raízes mais profundas do que simplesmente questões económicas ou políticas. O cerne do anticapitalismo reside numa teia complexa de motivações psicológicas e crenças filosóficas que moldam as atitudes individuais em relação ao sistema económico.
Desmistificar Deturpações: É crucial desmistificar as deturpações comuns sobre o capitalismo, destacando a sua verdadeira natureza e os benefícios que pode trazer quando implementado correctamente. Desde a sua concepção, o capitalismo tem sido alvo de distorções que obscurecem a sua capacidade de promover prosperidade e progresso.
Desafios Psicológicos e Ideológicos: O medo da independência, aversão à perda e a influência de ideologias como o altruísmo e o estadismo desempenham papéis significativos na formação das opiniões anti capitalistas. Compreender esses desafios psicológicos e ideológicos é essencial para abrir caminho para um diálogo mais informado e produtivo sobre o papel do capitalismo na sociedade.
Alerta Contra Totalitarismo: Os exemplos históricos do poder sedutor do totalitarismo lembram-nos dos perigos de abraçar sistemas políticos que sacrificam a liberdade individual em nome da segurança coletiva. É um lembrete contundente da necessidade de proteger e valorizar os princípios fundamentais da democracia e dos direitos individuais.
Ao desvendar as raízes psicológicas do anti capitalismo, abrimos espaço para um diálogo mais inclusivo e esclarecedor sobre o papel do capitalismo na construção de uma sociedade justa e próspera. Reconhecer e enfrentar essas raízes é o primeiro passo para promover um entendimento mais profundo e uma abordagem mais equilibrada das questões económicas e sociais que moldam o nosso mundo.
-
 @ 46fcbe30:6bd8ce4d
2024-04-05 16:31:16
@ 46fcbe30:6bd8ce4d
2024-04-05 16:31:16Opinion about Samourai Wallet (android)
Samourai has cost me many many hours due to their strong social media presence and constant ad hominem attacks. They blamed me for not being able to compile or reproduce their product instead of helping me to compile it. Given I compile wallets all the time as can be found on walletscrutiny, I doubt I lack the expertise to compile wallets but even if I did, why not show me? Not one developer other than their team themselves disagreed with my technical assessments of their product. Apart from proven scams, this is the product I trust least in the whole space.
But it's not only me. To quote Bitcoin Core developer and absolute genius Gregory Maxwell:
I have seen far too much outright dishonest and extremely incompetent behaviour from Samourai to ever trust it myself. Samourai has very poor privacy while bragging about having good privacy: It sends your addresses all back to their server. Their "trusted node" mode doesn't change this, it just exposes your Bitcoin node to attacks completely needlessly. (Needlessly because they only use it to relay transactions, which they could do via the public P2P ports of any node, and because since they've already sent your addresses back to their server sending your transactions via something else doesn't increase your privacy.) If you want strong privacy then as a start you need to run a full node (and use either Bitcoin Core wallet, or run your own electrum server), preferably via tor. I don't doubt that they want and intend to eventually have good privacy but it seems that they're just unable to stop lying about it, even after previously being caught.
You can find many more very competent people complaining about Samourai's dishonesity and aggressive behavior or outright incompetence if not malice here, here, here, and here. And yes, those links are to nopara, who is the founder of Wasabi wallet which targets the same audience of privacy focused users but that doesn't take away from the facts reported there.
Stay away from Scamourai!
WalletScrutiny #nostrOpinion






