-
 @ c23b8728:55b2d0fb
2024-04-21 07:38:18
@ c23b8728:55b2d0fb
2024-04-21 07:38:18ถ้าทั้งโลกนี้มีเงินอยู่ 100 หน่วย และไม่สามารถเพิ่มจำนวนได้ สมมติ ผมมีเงินอยู่ 10 หน่วย คุณมี 0 หน่วยและอยากกู้เงินจากผม ผมให้กู้ 10 หน่วย คิดดอกเบี้ย 1% หรือ 1 หน่วย คุณต้องหาเงินมาคืนผมให้ได้ 100 หน่วย บวก ดอกเบี้ยอีก 1 หน่วย รวมเป็น 101 หน่วย คำถาม : ดอกเบี้ยอีก 1 หน่วย คุณหามาจากไหน? ตอบ : จากคนอื่นที่ไม่ใช่ผม ถาม : แล้วคุณไปเอาเงิน 1 หน่วยจากคนอื่นมาได้ยังไง? ตอบ : คุณก็ทำประโยชน์ให้คนอื่นจนเค้ายอมจ่ายเงินให้คุณ 1 หน่วย
เราจะเห็นว่า ในระบบที่เงินเพิ่มจำนวนไม่ได้ คุณต้องตัดสินใจรอบคอบมากๆก่อนที่จะยืมเงินใครและให้ใครยืมเงิน เพราะว่า ดอกเบี้ยที่คุณต้องหามาจ่ายคืน มีทางเดียวที่จะได้มาคือ จากคนอื่น คุณไม่สามารถเสกมันขึ้นมาได้
สิ่งนี้มันสำคัญมาก เพราะว่า เมื่อต้นทุนของดอกเบี้ยสูงมากขึ้น คุณจะต้องแน่ใจจริงๆว่า จะได้เงินคืนมาและจะหาเงินมาคืนได้ ถาม : แล้วคุณจะแน่ใจได้ยังไง? ตอบ : ก็ต้องมีฝีมือ เชี่ยวชาญ มีประสบการณ์มากพอในสิ่งที่คุณจะทำ
ณ ตอนนี้เรากำลังอยู่ในระบบที่สามารถเพิ่มจำนวนเงินขึ้นได้ไม่จำกัด มันส่งผลกระทบลงมาเรื่อยๆจากธนาคารกลางมาสู่ระดับบุคคล เมื่อมีคนบางคนในระบบสามารถหาเงินมาจ่ายดอกเบี้ยคืนได้ด้วยการเสกขึ้นมาใหม่ แทนที่จะมาจากคนอื่นในระบบ มันเลยทำให้ ต้นทุนของดอกเบี้ยลดลง คนที่กู้ยืมเงินก็ลดความรับผิดชอบของตัวเองลงเรื่อยๆ และในที่สุดก็ลดการพัฒนาและสั่งสมความเชี่ยวชาญและประสบการณ์ของตัวเองลง ผลกระทบนี้เราได้เห็นกันแล้วกับตาตัวเอง มันเป็นผลกระทบที่ไหลลงมาเรื่อยๆจากแหล่งผลิตเงิน สินค้าสมัยก่อนกับปัจจุบันเช่นตู้เย็น เครื่องล้างจาน รถยนตร์ เป็นต้น เมื่อคุณภาพคนลดลง คุณภาพสินค้าก็ลดลงตามไปด้วย ผู้ผลิตให้ความสำคัญกับผลกำไรสูงสุดมากกว่าคุณภาพชีวิตของผู้ใช้งาน สิ่งเหล่านี้ถูกปกปิดด้วยกลยุทธ์การตลาดบังหน้าไว้ด้วยดาราและอินฟลูเอนเซอร์อินเทรนด์ในแต่ละยุคสมัย เช่น แทนที่ตู้เย็นจะจุของได้เยอะและมีประสิทธิภาพมากขึ้น กลับชูจุดเด่นด้านรูปลักษณ์ภายนอก หรือแค่มีดาราคนนี้เป็นพรีเซนเตอร์ สิ่งของต่างๆมีฟังก์ชั่นเสริมมากมายที่ไม่จำเป็น เช่นเดียวกับผู้คนที่บริโภคสินค้าและบริการต่างๆที่ไม่ได้จำเป็นกับชีวิต แต่ถูกหลอกว่ามันจำเป็นต่อจิตใจ(ดีต่อใจ)
บิตคอยน์คือระบบการเงินใหม่ ที่เพิ่มจำนวนขึ้นได้ยากขึ้นเรื่อยๆ จนถึงจุดหนึ่ง(ประมาณปี ค.ศ. 2140) มันจะไม่สามารถเพิ่มจำนวนขึ้นได้อีก ถ้าคุณเอาตัวเองไปอยู่ในระบบที่เงินสร้างยาก คุณภาพชีวิตของคุณจะต้องถูกบังคับให้ดีขึ้น เพราะว่าคุณจะอยู่ในระบบที่ผู้คนรอบตัวคุณถูกบังคับให้พัฒนาและรักษาคุณภาพของตัวเองอยู่เสมอ
hard choices, easy life easy choices, hard life
-
 @ 50893dd1:e29d5c47
2024-04-21 06:33:04
@ 50893dd1:e29d5c47
2024-04-21 06:33:04Las claves privadas son una parte muy importante de la seguridad de tus fondos de Bitcoin. Es esencial que las guardes de manera segura y que no las compartas con nadie. Hay algunas maneras de guardar tus claves privadas de manera segura:
-
Usa un monedero de hardware: Los monederos de hardware son dispositivos físicos que almacenan tus claves privadas de manera segura. Una de las opciones más populares es el LEDGER.
-
Usa un monedero de papel: Los monederos de papel son una forma de "frio" de almacenar tus claves privadas. Esto significa que no están conectados a Internet, lo que los hace muy seguros. Para usar un monedero de papel, primero tienes que generar una clave privada y luego imprimirla en un pedazo de papel. Asegúrate de guardar el papel en un lugar seguro, como una caja fuerte o una cartera de tela.
-
Usa un monedero de software: Los monederos de software son programas que se ejecutan en tu computadora o teléfono móvil. Hay muchas opciones diferentes, como Electrum y Blue Wallet. Asegúrate de usar un monedero de software que tenga una buena reputación y que ofrezca opciones de seguridad adicionales, como la autenticación de dos pasos.
Es importante recordar que, independientemente de la opción que elijas, es esencial que te asegures de proteger tus claves privadas. No las compartas con nadie y asegúrate de hacer una copia de seguridad de ellas.
Ahora deseo agregar un concepto adicional como regalo
Como crear una transacción en BTC?
Para crear una transacción con Bitcoin, primero necesitarás tener una dirección de cartera de Bitcoin y una cantidad suficiente de Bitcoin's para enviar. Luego, tendrás que usar una aplicación o un servicio en línea que te permita crear una transacción.
Aquí hay un resumen de los pasos básicos para crear una transacción de Bitcoin:
-
Abre tu cartera de Bitcoin.
-
Ingresa la dirección de la cartera del destinatario y la cantidad de Bitcoin que deseas enviar.
-
Verifica la información de la transacción y asegúrate de que esté correcta.
-
Firma digitalmente la transacción usando tu clave privada.
-
Envía la transacción a la red de Bitcoin.
Es importante tener en cuenta que las transacciones de Bitcoin se procesan en una red descentralizada y pueden tomar un tiempo para ser confirmadas. Además, las transacciones de Bitcoin son irreversibles, por lo que es importante asegurarse de que estás enviando la cantidad correcta a la dirección correcta.
Puedes poner en practica estos punto enviando tu aporte a cualquiera de las siguientes direcciones en las que podrás darme una propina directamente
💲Blink: https://pay.blink.sv/iirvin
💲Coinos: https://coinos.io/irvin
⚡ Vida: https://vida.page/irvin - LN ⚡ irvin@vida.page
DESCARGO DE RESPONSABILIDAD: Mi contenido no debe representar un asesoramiento definitivo del mercado, mis palabras o acciones recomiendo no seguirlas como un todo. Los usuarios, inversores o público en general deberán complementar con más investigación o consultoría privada las potenciales inversiones a realizar en cualquier activo o mercado. No me hago responsable de una peligrosa toma de decisiones en las inversiones.
-
-
 @ 57d1a264:69f1fee1
2024-04-21 06:25:00
@ 57d1a264:69f1fee1
2024-04-21 06:25:00Prompt: Scheduling ===============
Design the elements or a full experience for post schedule. Why it's important? Could be draft being part of the userflow? Save it for later edits, or enable the recurring post at specific day or time?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 1931b5e4:168a0489
2024-04-21 06:24:23
@ 1931b5e4:168a0489
2024-04-21 06:24:23How is Love Not Divisive? Exploring the Foundation of Intimate Love and Vulnerability
Love, in its myriad forms, is often seen as the unifying force that binds individuals together, transcending barriers of culture, race, and belief. Yet, amidst its seemingly unifying nature, one might wonder: How is love not divisive? The answer lies in understanding the fundamental essence of love and its deep-rooted connection to vulnerability.
At its core, love is an expression of vulnerability—a willingness to open oneself up emotionally, exposing one's innermost thoughts, fears, and desires to another individual. It is this vulnerability that forms the foundation of intimate love, fostering trust, empathy, and connection between partners.
Intimate love, characterised by a deep emotional and often physical bond between individuals, thrives on mutual vulnerability. In sharing our vulnerabilities with another person, we create a space for understanding, compassion, and genuine intimacy to blossom. It is through this shared vulnerability that couples forge deep emotional bonds, supporting each other through life's trials and triumphs.
However, the concept of vulnerability extends beyond romantic relationships to encompass all forms of love—be it familial, platonic, or altruistic. In each instance, love requires a willingness to let down our guard, to be open and receptive to the experiences and emotions of others. It is through this vulnerability that we cultivate empathy, kindness, and compassion, nurturing the bonds that unite us as human beings.
Yet, amidst the universality of love's vulnerability, there exists a distinction between intimate love and other forms of love—the sexual dimension. Sexual intimacy, with its potent blend of desire, passion, and vulnerability, represents the pinnacle of human connection. It is here that the creative life force—the very essence of existence—is harnessed in a dance of fear and excitement.
Sexual attraction, fuelled by the primal instincts of reproduction and desire, taps into the deepest recesses of our psyche, awakening dormant energies and unleashing a torrent of emotions. In this union of bodies and souls, vulnerability reaches its zenith, as two individuals surrender themselves fully to the other, bound by the bonds of passion and ecstasy.
Yet, it is precisely this vulnerability—the fear of rejection, of inadequacy, of losing oneself—that imbues sexual intimacy with its unparalleled power. In the throes of passion, we confront our deepest fears and insecurities, transcending them in a moment of raw, unbridled connection.
In conclusion, love, in all its forms, is grounded in vulnerability—a willingness to open ourselves up to the joys and pains of human connection. Whether in the tender embrace of intimate love or the boundless compassion of altruistic love, vulnerability lies at the heart of our most profound experiences. And it is through this vulnerability that we discover the true power of love—the power to unite, to heal, and to transform our lives in ways both profound and enduring.
picture taken from the Tarot Deck 'Magnetic Limitless Love' by Nantakay(aka Annie Dustan)
-
 @ 3c827db6:66418fc3
2024-04-21 05:47:15
@ 3c827db6:66418fc3
2024-04-21 05:47:15Now that we have seen how instant settlement can affect the construction industry let’s see the next industry that can have a huge impact - logistics.
To begin, let's examine the logistics industry through the lens of an online order example. What unfolds when we select a product on a website that requires delivery to our door? Who are the entities involved in this process, and what does the payment process entail?
So I pick something from the website and order it. I pay for it and wait for the product to be delivered to my door and hope that what will arrive at my door is what I expect. Because I am paying upfront, I am taking the risk in this case. I may choose to pay on delivery but the risk for all involved does not disappear, it is just shifted to who is taking that risk now, the seller. But more on that a bit later.
When using a card for payment, a 1.5%-3% transaction fee is typically charged by the bank issuing the card. After payment, the retailer or seller is notified to send the product to the buyer's address. Subsequently, the retailer arranges delivery through a logistics company. A delivery person is dispatched to the warehouse to collect the ordered product along with others, optimizing the route. The product then navigates through the delivery company's ecosystem, involving various warehouses and personnel, until it reaches the final delivery person who brings it to the buyer's doorstep.
The efficient movement of the product through space is generally understood within the system so that is not the problem. Faster delivery benefits everyone involved, as quick and reliable service enhances customer satisfaction and loyalty. However, the actual delivery personnel may not directly benefit from the speed of delivery, but we'll delve into that aspect later. Swift delivery is crucial for customer retention, as a prompt and reliable service encourages customers to choose the same platform for future orders rather than seeking alternatives.
Where Are The Problems Then?
The logistics industry, much like the construction industry we discussed in the previous article here, has problems that predominantly revolve around payment processes. These payment-related issues cascade into other aspects of the logistics chain.
Let's trace the journey of money in this context: 1. I make a card payment to the website, and the bank deducts a 1-3% transaction fee from the retail value. 2. The website, having received the payment, needs to pay the retailer the value of the product, and again, the bank deducts 1-3% from this payment. 3. The retailer, in turn, has to pay the delivery company, with the bank deducting another 1-3% from this transaction.
The above is just about the fees to the bank. What about the settlement between all the entities involved in the delivery?
- The website receives their money from me fast, unless it is an international delivery it is the same day.
- The website then batches all the payments that have to be paid to the retailer for the month so they do not have to pay each individual sale to them. They most likely will pay once a month so it could be up to 30-day credit at this point.
- Then the retailer has the same arrangement with the delivery company and there is up to a 30-day delay of the payment at this point also.
The monthly batching of payments may streamline processes, but it introduces a significant element of risk into the transaction chain. If any entity in this chain were to face financial issues, such as bankruptcy, within 30 days, the subsequent parties may never receive the funds they are owed. This risk compounds throughout the logistics ecosystem, emphasizing the need for more secure and efficient payments.
If I opt to pay on delivery, the risk dynamic in logistics is inverted - the money is collected by the delivery company, then forwarded to the retailer, and eventually passed on to the website. This way of operating has introduced additional complexities. As the number of orders increases, individual financial ledgers between the companies become more intricate due to the waiting period for money to reach the designated recipient. There is a ledger between the website and the retailer, tracking how many orders have been paid to the website and are awaiting payment. There is another ledger between the delivery company and the retailer, which, in turn, is awaiting payment. Regardless of my preferred payment method as the buyer, the retailer remains significantly exposed because they never receive the money first. The third-party risk for them is consistently high.
In both scenarios, the banking system charges fees of 3% or more for each delivery, and various parties face multiple third-party risks depending on the order of payment. To provide a more nuanced understanding of risk, it's crucial to note that even if all involved entities are reliable and face no business issues, this doesn't eliminate counterparty risk associated with the banks themselves. In the event of a bank failure, even a well-intentioned company may find itself unable to settle its debts, highlighting the vulnerability inherent in the current financial infrastructure.
Other Problems In The Logistics Ecosystem
The system encounters additional challenges within the workforce, particularly among delivery personnel. A fundamental conflict exists between these workers and the companies they serve. Workers are compensated for their time, while companies derive revenue from delivered products. This misalignment of incentives prompts companies to set aggressive targets for delivery personnel. When I run a marathon I do not sprint because I will burn out in the first part of the race. I have to pace myself to finish and may increase or decrease the speed depending on the particular situation. When you make the delivery men “sprint” in the “marathon” of delivering packages, it is only a matter of time before they burn out and quit much sooner than finding their pace and finishing their month/year the proper way.
The intense pressure to meet unrealistic delivery targets can have severe consequences on the quality of service provided by delivery workers. The rush to complete deliveries quickly may lead to damaged products and unattended packages that get stolen. Additionally, they do not have time for bathroom breaks and have to figure out how to do their business in the delivery vehicle. This not only impacts the overall customer experience but also poses risks to the well-being of the workers themselves.
The burnout process is expedited by the mental struggle faced by delivery personnel. A conflicting incentive structure compounds the challenge: while the company seeks maximum exploitation for increased profits, delivery personnel are motivated to minimize their workload since their compensation remains constant. This incongruity not only hampers the optimization of profits for both parties but also introduces mental stress for the delivery personnel. How do you expect to have no friction between them if both parties wanting to increase their profits means they have to do completely opposite actions.
Another source of friction between the delivery company and its personnel revolves around the vehicles they use. Similar to the issue of tool maintenance in the construction industry, the lack of ownership over the vehicles leads to neglect in upkeep. The company, focused on maximizing profits, may exploit the delivery personnel, who, in turn, might exploit the vehicles to enhance their personal gains. This dynamic creates a detrimental cycle where both parties prioritize individual interests over the long-term well-being of the shared resources.
Instant Split Payments And Delivery Dynamics
The most apparent benefit is that the banking system would not levy fees of 4.5%-9% for each product delivered. Even if funds are transferred between entities, the fees in the Lightning Network would be approximately 0.3%. This alone marks a significant improvement, reducing transaction costs by an order of magnitude compared to the current system. Now, let's delve deeper into additional advantages.
The risks associated with multiple third parties are eradicated in this ecosystem. There's only one third-party risk, namely the buyer of the product. As soon as the buyer receives the product, they make a Lightning Network payment. Moreover, the delivery company, the retailer, and the website all receive their payments simultaneously without funds passing from one to another. The split payment will crush the fees even further because it is one payment so the fee is ~0.1%. Just to mention that those fees do not go to the banking system, they go to the LSPs like us at Breez that are facilitating the actual payment. And because we are a non-custodial solution we do not introduce any third-party risk. There is no waiting at any point for someone to settle their bill with someone else. All participants have their funds instantly and decide what to do with them from then on.
This is a huge improvement, and just that is enough for someone to disrupt the logistics payments market, but the effects of instant split payment do not stop there.
The adoption of instant split payments in the logistics industry will significantly alter the incentives for all delivery workers. A key transformation is the shift from receiving compensation solely for time - to being actively engaged in each payment related to their deliveries. Similar to how companies receive split payments, with each entity getting its share, every individual in the delivery company involved in moving the product can now receive their share too. The funds received by the delivery company will be split further, ensuring that delivery personnel are paid for their specific contributions rather than time spent. This eliminates the need for brutal targets, allowing those who deliver more packages to receive proportional compensation for their work and fostering a fair and performance-based payment structure.
In this new paradigm of instant split payments, delivery workers will be incentivized to use their own vehicles for product deliveries. When using a company vehicle, their share of the payment for each delivery is smaller. However, if they utilize their personal vehicle, the percentage from each delivery will be more substantial, directly contributing to their earnings. This shift encourages a sense of ownership and responsibility among delivery personnel, fostering a more efficient and cost-effective system.
The revolutionary aspect of this system is that it opens up opportunities for anyone with a vehicle to become a convenient and flexible delivery person. Individuals can integrate delivery tasks into their existing plans, making extra bitcoin while heading in a specific direction. This decentralized approach allows for the optimization of routes on an individual basis. People with their own vehicles are no longer bound to a single delivery company; instead, they can work for various companies in their local area. This not only encourages individual optimization of routes but also shifts the focus to serving those expecting deliveries rather than working solely for a centralized delivery company. The reputation of the app will be enhanced by well-delivered packages, creating a positive feedback loop for more orders in the future, akin to the success of platforms like Uber.
Absolutely, the introduction of an instant settlement system with split payments has the potential to decentralize various aspects of the delivery ecosystem:
- Decentralization of Delivery Companies: Logistics can shift from a few large delivery companies to numerous small entities and even individuals participating in the delivery process. This allows for a more distributed and flexible delivery network.
- Decentralization of Income for Delivery Personnel: Delivery individuals will no longer be reliant on a centralized source of income. Instead, they can participate in each delivery payment, earning money directly proportional to their contribution, thereby decentralizing their income.
- Decentralization of Options for Buyers: Buyers will have a broader range of options for who delivers their products. With a more decentralized delivery ecosystem, they can choose from various delivery providers, including independent agents and smaller delivery companies.
Overall, this decentralization has the potential to create a more efficient, adaptable, and user-centric delivery system.
Now there needs to be a person who understands the logistics market and makes that app. Unlike the construction companies, this will be even more decentralized because many more individuals can manage a delivery. Not everyone can manage a complex construction project but anyone can deliver something. Remember in the past the newspaper kids? A person with his scooter can deliver a few packages to his neighbors on the way. That will also have a social layer effect by bonding you more and more with the people in your area. We can use that in big urban areas because most of the time we are passing our neighbors without saying “Hello”. And the neighbors will prefer to receive product deliveries from people that they are familiar with. The potential for a decentralized and more community-oriented delivery system is quite exciting
Now let’s go and deliver that app.
-
 @ 1c6b3be3:73f0ae6f
2024-04-21 05:00:04
@ 1c6b3be3:73f0ae6f
2024-04-21 05:00:04🍵 "llm | cloud computing | ddos" - Google News
The Future of Technology: An Insight into Cloud Based Quantum Computing Software - Medium Corero Network Security Launches Hybrid Cloud DDoS Protection Solution - PR Newswire Google fires 28 employees after protest against cloud contract with Israel - The Associated Press
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Não tem solução
O melhor presidente dos últimos 50 anos, o melhor congresso, o melhor governador, os melhores ministros, um resultado eleitoral muito melhor do que o melhor dos meus sonhos e nada acontece.
A única solução que nos resta é o Bitcoin. Vale talvez a pena dar a vida pra tentar popularizar esse negócio.
-
 @ 30876140:cffb1126
2024-04-21 04:18:59
@ 30876140:cffb1126
2024-04-21 04:18:59The Wanderers carry our ancient way,
Forgotten in sands across time,
The Path which returns us to Regions of Light,
with phrases and stories sublime.Out from our villages we cast them,
for memory of truths divine,
remind us of our errored ways,
But in their hearts, the Truth ever shines."We've lost many of our relics, now, though they were never important for the Path. Relics and objects, though imbued with a holy power, only serve as a guidepost to our spirits, a reminder of where to travel. We do not need them to cross the bridge between worlds."
Our leaders think they are a crazy, unintelligent people, continuing to profess and refine a realm of fantasy which has so little value to our desert lives; that these wanderers really believe what they say, only to cope with the terrors and agony of living in this world that is become destitute and estranged from celestial life.
I do not believe them, who deny the Wandering Way, for I see in their hearts that they bleed every day; they cast judgements unjust, words unloving, do things unbecoming of their characters in the folly of their grief. Yet never have I met a Wanderer with dirt upon their souls, though dirt clings so readily to their feet and threadbare robes. They possess voices of sweetness, though hoarse from the desert wind, and they seem to have a glow about their skin, though darkened by hard years in the sun.
Maybe I will take up the Wandering Way, if one of their order would take me with them. I know not where they go when they cross over the horizon, west or east, but I rarely have seen the same twice, except Abunam Sabba, who comes to us when the moon is full, without fail.
He made my father so angry on his last visit to the village, when he spoke so confidently of the dealings with the Echoes in the farthest reaches of Gondölla. "There is none alive with such knowledge," said my father.
"But there is," replied Sabba, "and many also who are not alive. We have seen them on many worlds, and have spoken to them of their travels across the stars."
"You are a liar, and a swindler," spat my father in rage, and forced him out of our house on a midsummer's eve. Still, Sabba returns to our village, though only to its edge now, where the water spout and market stand, since many of our village have treated him so. No matter when he sees me, though, he treats me with kindness, and respect, and never speaks ill of anybody.
"Words said in disdain cause the spirit endless pain," Sabba said. "They prevent progress on the Path. None can cross the bridges we travel who bear such a sickness of soul, for it pulls the spirit back to a place as sure as the anchors of old when we rode upon the water that spilled over these valleys of sand."
Sabba said to me, once, "I think you are one of the few in this world which have a heart that is clear enough to withstand the Doors of Night and make the Walk Between Worlds. I see your knowledge, though seed yet be unblossomed, and I think your curious mind could be sated on this Path. Please consider my words as an invitation; I will take you on a wander, whenever you are ready."
"The Wandering Way leads a soul wherever the winds may take them. We walk between worlds on bridges unseen by the eye, and appear whence we will, somewhere else in Gondölla. Many travel on missions unnumbered, called by some purpose or Great Spirit to act on behalf of the highest orders of life, while others simply walk, becoming as they do, letting go of their heavier natures and striving ever closer to the Suns which shine above. It is difficult to describe, as I have only words of the world, as we say, but with a little of your trust, I can show you what my words cannot."
Read more here: https://publish.obsidian.md/gondolla/Tales+of+the+Galaxy/Wanderer
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28What is better than bounties and grants?
The experience with bounties from HRF wasn't great. No one has answered to the calls for implementing what they wanted because the work was too much and the risk of not getting paid very real. The experience with grants in general from Spiral is also not great: many random developers making cool but useless projects, wasted money.
The two kinds of open-source financial support that have worked so far are:
- Paying people who are already doing useful work so they can continue doing that. That is the experience of some people who are "maintaining" Bitcoin Core, for example, or other open-source projects. You're doing a thing, you've proven yourself valuable and you definitely seem to be interested in that personally such that you don't need a boss telling you what to do, so take the money and just keep doing that.
- Structured open-source initiatives, like the LDK effort. Although LDK is arguably useless, it has a stated goal and that goal is being delivered. I don't have any knowledge about how its development process works, but they have people being paid and "bosses" that direct the work to be done, as any team needs. So it is not the same as an open grant.
The thing that is missing is a way to provide these open loose grants to people that don't require bosses, but also that don't just pick a winner and let them do whatever stupid idea they might have (Spiral grants), and also do not mandate that they do something big before being paid and offers no guarantee of that they will be paid whatsoever.
The solution: smaller flexible bounties in large quantities
My suggestions is: instead of giving 1 bitcoin for a huge very specific project, state some "principles", or "problems", in a loose manner, that you want to see solved. For example, "we, the organization X, wants to see projects that use zero-knowledge proofs to help Bitcoin somehow, because we love zero-knowledge proofs".
Then state that you're going to give 20 grants of 0.05 bitcoins each, at random times, for projects that you see being done that may be on the right track.
That will tilt people that may had a small inclination to work on these problems to actually start doing something, and if they see that what they're doing is being appreciated and awarded with a payment, they will be more incentivized to finish it. There could even be a conditional bounty (like HRF did with Cashu) for finishing the project with certain requirements, but this only works after some structure is already in place for a certain project.
-
 @ 1c6b3be3:73f0ae6f
2024-04-21 04:00:09
@ 1c6b3be3:73f0ae6f
2024-04-21 04:00:09🍵 "btc | bitcoin | lightning network | asic" - Google News
What Is Bitcoin? How To Mine, Buy, and Use It - Investopedia Bitcoin Fees Hit ATH Post Halving: Is the Average User Getting Priced Out Due to Increasing Prices? - DailyCoin How a Jack Dorsey-backed bitcoin miner uses a volcano in Kenya to turn on the lights in rural homes - NBC 6 South Florida Runes Protocol Triggers Bitcoin Network Jam - BeInCrypto Bitcoin halving: Why it's important for BTC scarcity - Cointelegraph Deutsche Bank Expects Bitcoin Price to 'Stay High' After Halving — JPMorgan Disagrees – Markets and Prices Bitcoin ... - Bitcoin.com News Bitcoin just completed its fourth-ever 'halving,' here’s what investors need to watch now - CNBC Bitcoin Halving, Runes Proliferation Results in Historic Fee Increases, Crypto Community Reacts – Bitcoin News - Bitcoin.com News
-
 @ 8947a945:9bfcf626
2024-04-21 02:56:46
@ 8947a945:9bfcf626
2024-04-21 02:56:46September 2009
In 2009 it was my last year in medical school. I was assigned to be a medical student at a primary hospital in a rural area in the province of Chachoengsao. I did my medical practice under supervision of senior doctors.
Living and working at that hospital was easy. I had my own private doctor room to live in , and lots of cheap good food around in the morning while the hospital prepared lunch and dinner everyday.
By that time I was looking for a nearby Catholic church to attend a mass and found one in a website of the Bangkok diocese and the information was outdated and left unattended.
If you had ever heard of the yellow pages , that was what the information of the church looked like. The details were very short and useless. The phone number was outdated
I had to guess which way to go for that time google map wasn't on our hands like the present day.
Imagine what happened in 2009
You drove a car 10 kilometres away from your home , venturing deep into the forest where you had never been before was quite challenging. Furthermore in Thailand , the 3G phone mobile data wasn’t settled yet. So I had no online navigation at all.
Along the way , there were gradually transition between a forest and a field into small rural community with a church signs. That was a relief at least I didn't have to sleep in the middle of the forest that night.
These 2 pictures were what you saw along your way to do your quest finding a church.


In the middle of the forest , the serene catholic church stood in the middle of this forest.



You are surrounded by a forest , green trees everywhere around you. Birds tweeting. Serenity




The priest house at the backyard

Interior of the church is simple decorated

Shot taken from the back
The main altar

 The statues of St.Anne and Mother Mary. Thai words mean “St.Anne , pray for us”
The statues of St.Anne and Mother Mary. Thai words mean “St.Anne , pray for us”My first car parked at the back of the church

Photo taking equipment - IPhone 3Gs
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28sitios.xyz
Based on sitio, this was supposed to be the successor of Websites For Trello.
From the old landing page:
sítios.xyz is a hosted static site generator based on sitio. It is capable of building websites by fetching content from other services and arranging them in pages. It can be used to build any sort of blog or site.
It supports fetching content from Trello, Dropbox, Evernote and arbitrary URLs. You can use just one of these providers, or mix them all in your site.
How it works
Basically, you just have to point to an URL of the site, like /posts, for example, and assign a provider to it. The trello:list provider, for example, will fetch all cards on a Trello list and create a page for each of them under /posts/:card-name and finish with an index, optionally paginated, on /posts itself.
You can repeat this process for other content from other sources, or even just point the root URL, / to some provider and be done with it.
Fast
The generated websites are super fast, as they're served as HTML files directly, no server-rendering involved. Also, due to sitio capabilities, they have instant navigation enabled by default, which uses JavaScript to fetch just the content of the pages, instead of performing a full reload.
Customization
Since the way pages are rendered -- their HTML structure -- is standardized by classless, custom theming and styling is simple to do using just CSS and JavaScript, and there are some themes available already for you to choose.
If you want custom HTML or a provider for which we don't have support yet, that's easy to add. Please let's us know using the chat below! No lock-in
The code that renders the sites is just a very minimal sitio script with the plugins you choose. These are all open-source and you can export your site and render it by yourself if you don't want to use sítios.xyz anymore.
-
 @ 8947a945:9bfcf626
2024-04-21 02:29:57
@ 8947a945:9bfcf626
2024-04-21 02:29:57กันยายน 2552
เป็นปีสุดท้ายสำหรับการเป็นนักศึกษาแพทย์ ผมถูกส่งให้ไปฝึกงานที่โรงพยาบาลชุมชนแห่งหนึ่งในจังหวัดฉะเชิงเทรา ภายใต้การดูแลของแพทย์รุ่นพี่และอาจารย์แพทย์ประจำโรงพยาบาลแห่งนั้น
ชีวิตความเป็นอยู่ช่วงนั้นเรียบง่าย ไม่ต้องดิ้นรนอะไรมาก ผมมีบ้านพักส่วนตัวอยู่ภายในตัวโรงพยาบาล ทุกๆเช้ามีตลาดนัดตอนเช้าตั้งอยู่ข้างๆอาคารผู้ป่วยนอก มีของกินดีๆราคาถูกๆให้เลือกมากมาย ส่วนมื้อเที่ยงและมื้อเย็นหมดห่วงเพราะทางโรงพยาบาลจัดเตรียมไว้ให้
เวลานั้นผมนับถือคาทอลิค ต้องหาโบสถ์เข้าร่วมพิธีมิซซาบูชาขอบพระคุณในวันอาทิตย์ การหาข้อมูลไม่ง่าย ต้องดุ่มๆหาในเวบไซต์ของสังฆมณฑลกรุงเทพ หาไปหามาก็ไปเจอชื่อโบสถ์ "นักบุญอันนา สระไม้แดง " แต่ที่อยู่และวิธีการเดินทางไม่มีบอกเอาไว้
ถ้าใครเกิดทันสมุดหน้าเหลือง (YellowPages) นั่นแหละครับช้อมูลอย่างเดียวที่ผมมีในมือ แถมเบอร์โทรศัพท์ของโบสถ์ก็ไม่ได้อัพเดทอีก
ลองนึกภาพตามนะครับเมื่อปี 2552
ประเทศไทยยังไม่มีระบบ 3G เลย ส่วน google maps ก็พึ่งถูกพัฒนาขึ้นมาแถวๆปี 2548 ไม่ได้พร้อมใช้งานเมื่อไหร่ก็ได้เหมือนปัจจุบัน
ผมต้องอาศัยความกล้าในการขับรถออกจากบ้านพักในโรงพยาบาล ซึ่งเหมือนสถานที่ปลอดภัยมากๆสำหรับผมที่มาอยู่ต่างถิ่น ไม่รู้จักใครเลย วิ่งเข้าถนนใหญ่ซักพักนึงไม่มีชุมชนข้างทางเหลือ มีแต่ป่า
เส้นทางเข้าโบสถ์ก็คือถนนที่ตัดเข้ากลางป่าไปเลย ระยะทางประมาณ 9 กิโลจากโรงพยาบาล แต่ก็เป็นอะไรที่ตื่นเต้นมาก ขับรถคนเดียวในต่างแดน
แถมรถคันแรกของผมก็เป็นรถมือสองที่มีปัญหาไดสตาร์ทงอแงอีก ถ้าขับความเร็วไม่เกิน 80 km/hr มันจะไม่เกิดปัญหา แต่ถ้าเกิดวันไหนรีบๆ อัดความเร็วขึ้นทะลุ 100 km/hr แล้วจอดรถ ดับเครื่อง ลงไปทำธุระแล้วกลับมาสตาร์ทรถจะมีลุ้นว่ารถจะสตาร์ทติดหรือไม่ติด
ช่างที่อู่ซ่อมรถเขาบอกว่าไดสตาร์ทมันค้าง วิธีเอาตัวรอดก็คือต้องหาท่อนเหล็กมาเคาะ แล้วสตาร์ทรถ วัดดวงกับมันไปเรื่อยๆ ซ่อมมาหลายรอบก็แก้ไม่หาย ลองเอาเข้าศูนย์บริหารมาตรฐานแล้วก็ไม่รอด
ตอนนั้นผมก็กลัวครับ เกิดซวยเข้าขั้น ขับรถถึงโบสถ์แล้วเกิดรถดับอีกนี่สงสัยได้นอนในป่า
เมื่อขับรถไปเรื่อยๆ ก็เริ่มเห้นชุมชนสระไม้แดง เห็นป้ายบอกทาง เห็นป้ายโบสถ์ตอนนั้นใจชื้นแล้วครับ ว่าอย่างน้อยก็ขับรถมามั่วๆแล้วถูกทางละกัน


2 ฝั่งข้างทางก็จะเห็นวิวประมาณนี้ไปตลอดทาง ลมเย็นครับ ตอนนั้นเป็นช่วงเดือนกันยายนพอดี
กลางป่า มีโบสถ์คาทอลิคอันเงียบสงบตั้งอยู่ รายล้อมไปด้วยธรรมชาติสีเขียว เสียงนกร้อง แสงแดดอ่อนๆ กลิ่นไอดิน เสียงหญ้าสดสลับกับเสียงหญ้าแห้งเวลาเดินเข้าหาตัวโบสถ์แต่ละก้าว พลังงานความศักดิ์สิทธิ์ไม่ธรรมดา



เมื่อมองไปรอบๆตัวโบสถ์คือถูกล้อมด้วยธรรมชาติกลางป่ากลางทุ่งนา




บ้านพักพระสงฆ์(บาทหลวง) ด้านหลังตัวโบสถ์

ภายในตัวโบสถ์ตกแต่งเรียบง่าย แต่สวยงามสง่า รูปปั้นนักบุญอันนาและพระแม่มารีย์

ถ่ายจากด้านหลังสุดตัวโบสถ์
พระแท่นหลักของตัวโบสถ์


นี่คือรถคันแรกของผมสมัยนั้นครับ

Honda civic 3 doors ค่าตัว 120,000 บาทถ้วน รับมาอยู่ด้วยตั้งแต่ผมเข้ามหาวิทยาลัยปี 1 เมื่อปี 2547 ขายคืนเต๊นท์รถเมื่อปี 2554 ราคา 90,000 บาท ก่อนที่จะได้โตโยต้าวีออสปี 2004 จากพ่อตาของผมมาเป็นของขวัญวันหมั้นกับภรรยาครับ
อุปกรณ์ถ่ายภาพ - IPhone 3Gs
เกร็ดเล็กเกร็ดน้อย
นักบุญยอแซฟและนักบุญอันนา คือบิดามารดาของพระแม่มารีย์ผู้ที่เป็นพระมารดาของพระเยซูเจ้าครับ เป็นท่านตาท่านยายของพระเยซูนั่นเองครับ
ที่โบสถ์แห่งนี้ถึงจะมีบ้านพักบาทหลวงอยู่ แต่ไม่มีคนอยู่ตลอด คุณพ่อท่านจะขับรถจากโบสถ์อีกแห่งหนึ่งซึ่งท่านพำนักอยู่ ห่างออกไป 10 - 20 กิโลเมตร วิ่งรถข้ามอำเภอมาเพื่อประกอบพิธีมิซซาให้กับชาวบ้านในชุมชนแห่งนี้ วันอาทิตย์มีแน่ๆหนึ่งรอบ แต่วันอื่นๆ ผมไม่ทราบข้อมูลครับ
ถ้าใครจะมาเที่ยวมาเยี่ยมชม แนะนำให้ติดต่อหาข้อมูลก่อนนะครับ เพราะวันที่ผมเดินไปทางสำรวจ ตัวโบสถ์ล็อคเข้าไม่ได้ รูปถ่ายที่ถ่ายมาได้เป็นวันอาทิตย์หลังพิธีมิซซาเสร็จสิ้น ชาวบ้านและคุณพ่อแยกย้ายกันกลับหมดแล้ว
หวังว่าจะชอบนะครับ กับซีรีส์ใหม่ของผม RK photos - photo story telling blog รูปถ่ายเล่าเรื่อง ไว้เจอกันใหม่คราวหน้า สวัสดีครับ
-
 @ bcea2b98:7ccef3c9
2024-04-20 17:59:17
@ bcea2b98:7ccef3c9
2024-04-20 17:59:17Consider the concept of 'progress' in human society and individual lives. When we talk about progress, what exactly do we mean? Is it solely about technological advancement, economic growth, or societal development? Or does progress include broader aspects such as personal fulfillment, moral advancement, and environmental sustainability? Is progress always desirable, or are there instances where the pursuit of progress leads to unintended consequences or ethical dilemmas?
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
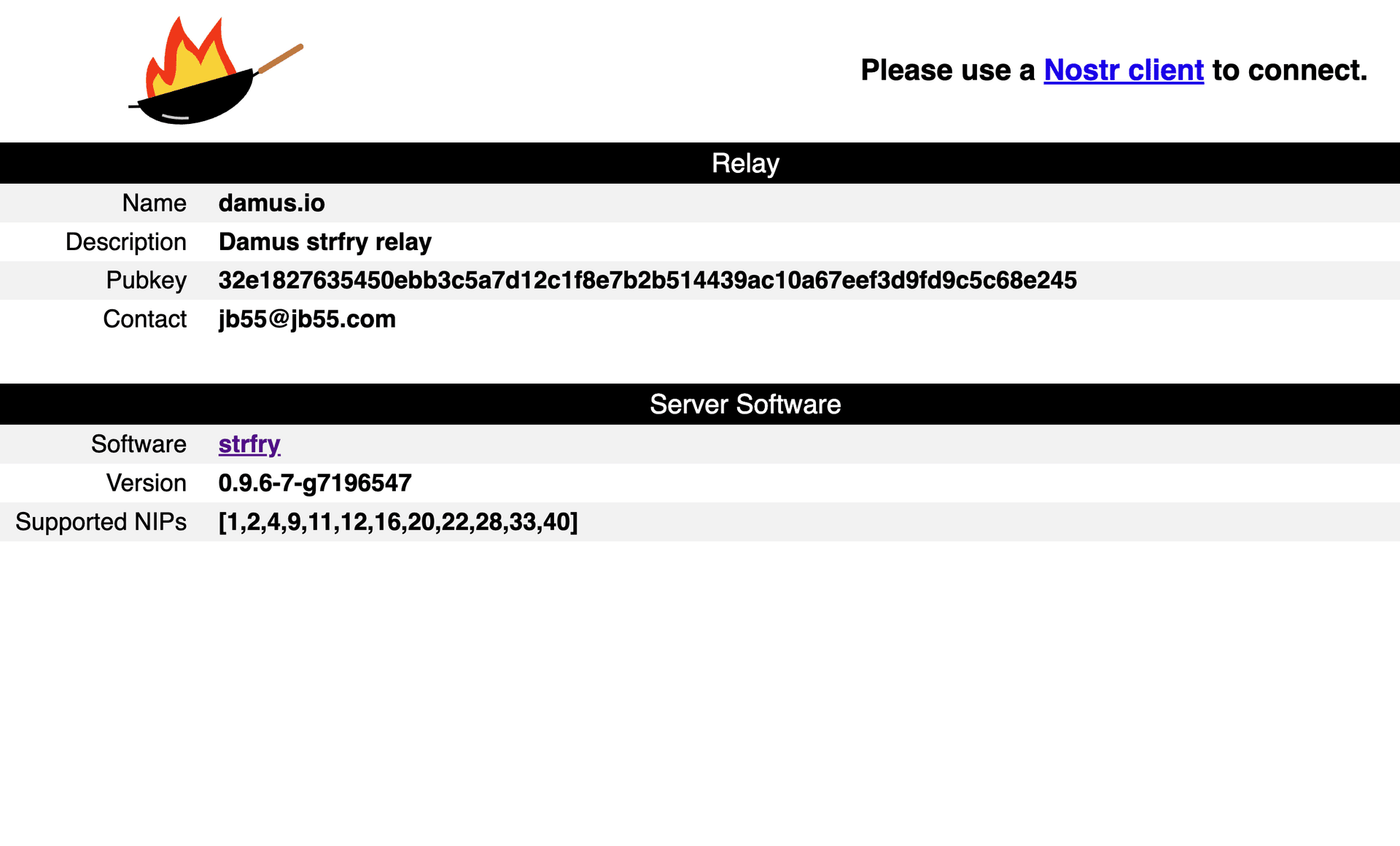
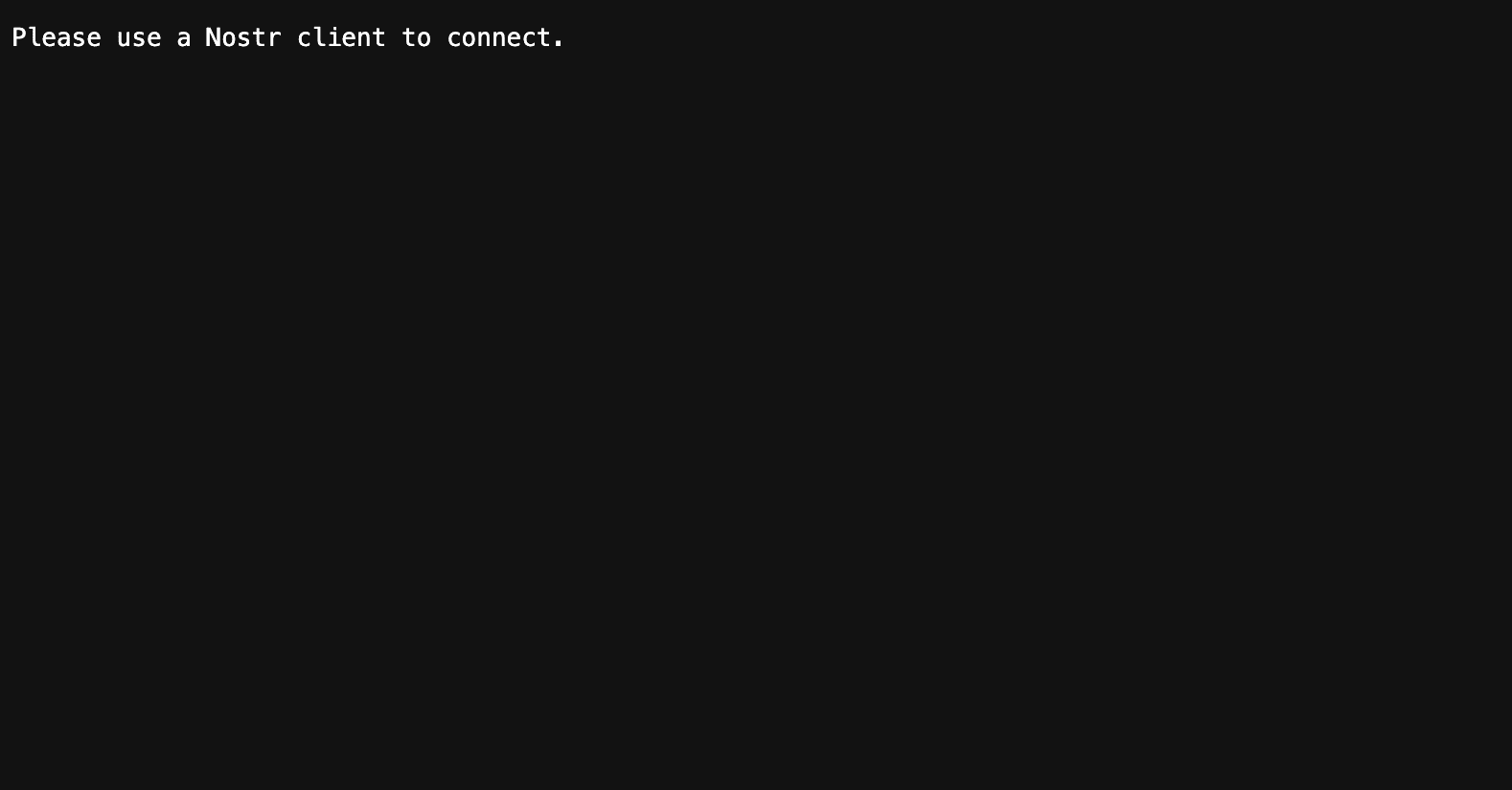
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
Transform your relay's landing page from this:
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
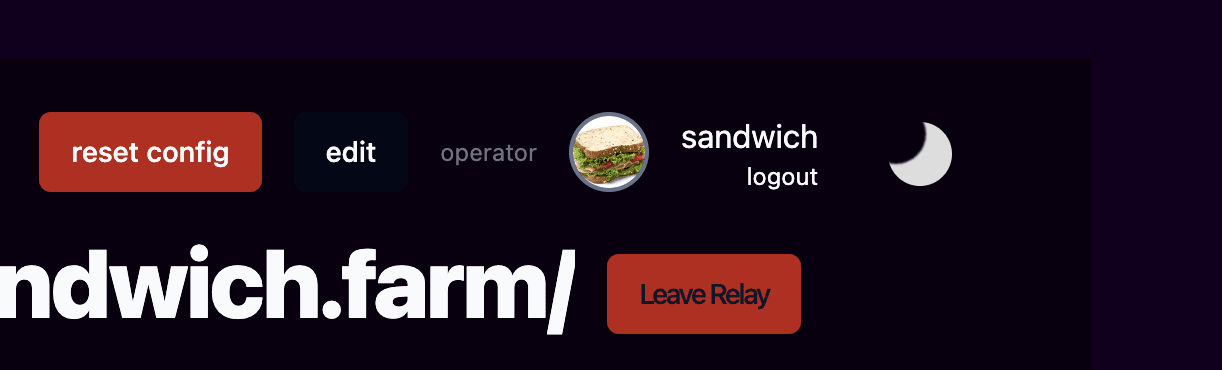
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
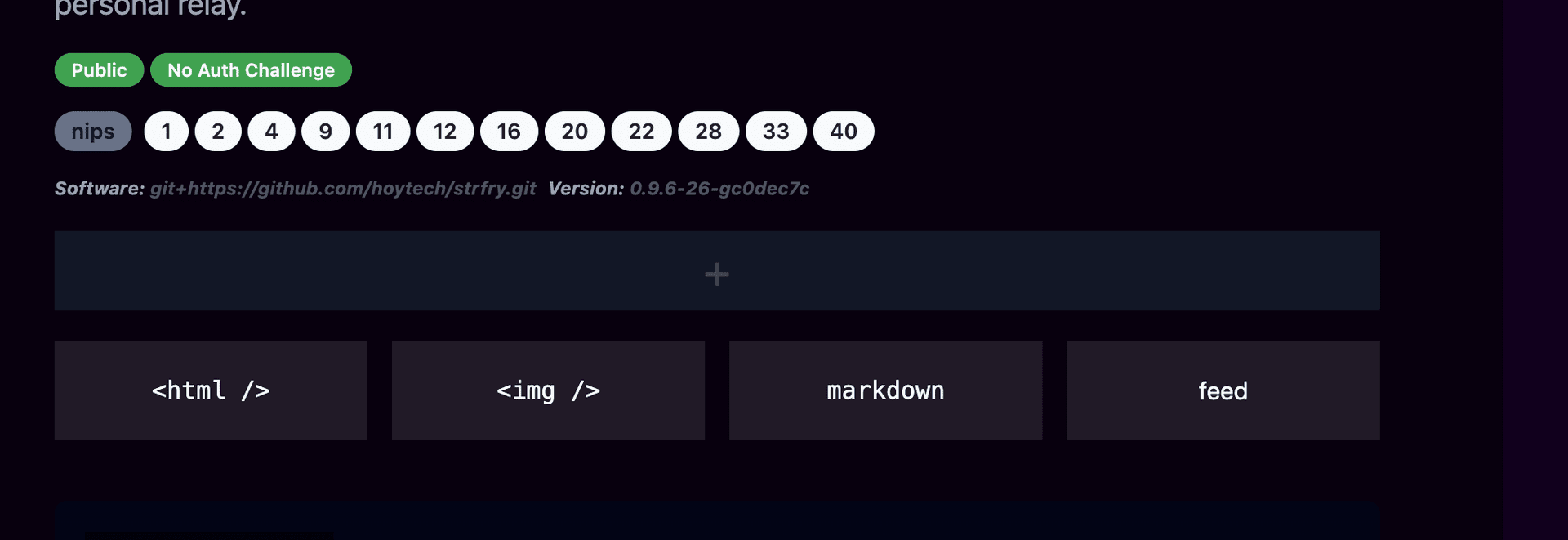
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ d96e0407:8a0da63d
2024-04-20 17:46:07
@ d96e0407:8a0da63d
2024-04-20 17:46:07
Academy of Fine Arts Vienna, October 1907
"I'm sorry, you can't enroll here," the director said. The young man stood shocked, struggling to hold himself together. "There has to be a reason," the young man yelled, losing his composure. He withdrew his inheritance money from his bank and left his mother, who was suffering from breast cancer, alone. The frustration was evident in his eyes; he had placed all his hopes on this. "They lacked the human element, Hitler," the director said. His face gave a confused expression but slowly understood the remark. "You have talent for architecture, why try out for the school?" the director added. Hitler smashed the desk out of anger; he felt insulted by the statement. "I am an artist," he roared, storming out of the office. He sat in the corridors, thinking of the next step. He couldn't enroll in architecture school; secondary school credentials were needed. "I can't go back there," he said, hesitant to return to complete his secondary school. He stood up, took a deep breath, and headed back to his residence.
The Bohemian Residence, December 1907
On the 21st of December, news of his mother's death came to him. Apparently, she died of the breast cancer which plagued her. She had surgery earlier this year, but it was unsuccessful. "Why did you have to go?" he wailed. Hitler really loved his ma; the memories of the time when she protected him from his father's abuse made him tear up even more. "That's enough," a tall Romani guy yelled at Hitler. He had grown tired of the incessant crying. "This won't solve anything," he continued, explaining why he should move on. The statement enraged Hitler, who was prone to violence. "Take that back, Adrian," he yelled, raising his fists at the Romani guy. He fell to the ground, overwhelmed by sadness, as Adrian comforted him.
A few days later, Adrian approached Hitler with a deal that could change his life forever. "The Occult!!!" he exclaimed. Adrian had revealed he was part of a Normandic coven. It all made sense to Hitler; most men in the shelter avoided Adrian. "What do you want to do to me?" Hitler asked, curious. The Romani smirked and explained how he intended to enhance Hitler's artistry. "No," he protested but was knocked out by a spell. Adolf found himself tied up in the center of an occult circle. "Let me go," he screamed, but he was ignored. Adrian poured boiling ink on Hitler and began to chant a spell. "Demonii artei fac din acest băiat vasul tău," he chanted ten times until an eerie glow surrounded him. As the semi-conscious Hitler lay on the floor, Adrian whispered in his ear, "I love you," and was never seen again.
Academy of Fine Arts Vienna, 1908
"A bounty of 10,000 marks for the mystery killer," Karl said, standing beside Hitler. He ignored his friend as they walked to the Academy of Fine Arts. Since that incident, he had been suffering from homicidal urges and discovered that whatever he drew came to life. "Perhaps this is a second chance for a new beginning," he said to himself. He had easily passed the first and second exams; it just remained the last exam. He walked into the room where the director and the other examiners sat. "Adolf Hitler, impress us this time," the director said. The young man took his brush and began his magnificent strokes, breathing life into each scene. Clap! The examiners were impressed by his painting. He gave a devious smirk as the creatures in the painting came to life and attacked them.
"Let the bloodshed begin," he laughed maniacally, mixing their blood with the ink. He drew more creatures to unleash chaos in the school. "You are the mystery killer," Karl yelled, running towards him with a knife. Strange ink creatures appeared and restrained him. "Please don't kill me," he said as Hitler walked towards him. "I can't kill someone who's already dead," Hitler replied. Fear struck Karl as his body began to lose its form, slowly falling to the ground like ink droplets. "What's happening?" he cried out desperately, demanding an answer. Hitler revealed information that scared him; the real Karl had died several months ago. "I am a clone," he said as his body fully dissolved.
The Great Vienna,1925
Seventeen years had passed since the bloodshed at the Academy of Fine Arts. The academy had remained closed ever since, but the murders continued. He exhaled a puff of cigarette and stared at the bartender. Hitler had grown a lot since 1908; he was an adult who made his living off his arts. "One more drink," he bellowed. He poured the drink into the cup but hesitated, entering a deep thought. "Amelie," he said. The strange French woman who came into his life three years ago, he loved her so much in his own twisted way. "I haven't found concrete proof," she wrote on her paper. She felt the paintings were watching her, and it gave her chills. She decided to step into his study room, which she was banned from. The room was filled with grotesque images that had the strange smell of blood. "What's this?" she exclaimed, falling to the ground, but something terrified her even more - the baritone voice.
"Why are you here?" he asked. She remained on the ground, paralyzed with fear. "You know something, Amelie," he roared, summoning ink creatures to surround her. She dropped the facade and revealed they weren't alone. Instantly, various armed men showed up, ready to attack. "I was a spy from the police," she said. Hitler stood shocked; his unstable mind couldn't take the betrayal and heartbreak and began to laugh maniacally. "Attack my men," Captain Max yelled to the officers. Blood splattered on the floor; severed hands, legs, and muscles of the officers laid on the floor. "You can't kill me, I'm..." he staggered. Captain Max shot him with a bullet covered with holy water. Hitler, determined, used the last of his strength to blow up the house; fire ravaged the building as Max and Amelie managed to escape. They found his corpse and submitted it for an autopsy. "We killed the demon," Captain Max reported to his seniors.
The Demon Awakes "A ticket to Germany," he said, handing over the money. He had changed his looks to evade being detected; he walked onto the train with the ink bird on his shoulder. Meanwhile, in the Vienna Police Headquarters, the supposed corpse of Hitler lost its form and reverted into ink.
-
 @ c31052c1:493a1c56
2024-04-20 17:46:00
@ c31052c1:493a1c56
2024-04-20 17:46:00步骤0:准备工作
-决定要在哪个平台上获取$MNER;
-决定使用哪个钱包,目前官方支持MetaMask、OKX Wallet、Bitget Wallet等主流钱包,鉴于官方活动(可以通过Bitget Wallet的“发现”功能,输入mineral即可轻松访问$MNER的质押页面。抢占Mineral专属的100,000 BWB积分,活动截止4.28)。


-建议将Mineral Dapp点上关注,即可在收藏中直接进入。
步骤1:获取$MNER
-获取$MNER的三条链:
$MNER交易地址:
-
对应梅林链的MerlinSwap:https://merlinswap.org/trade/swap?tokenTo=0x27622b326ff3ffa7dc10ae291800c3073b55aa39
-
对应以太链的Uniswap:https://app.uniswap.org/swap
-
对应BNB链的Pancake:https://pancakeswap.finance/swap
-在Merlin Chain、ETH Chain、BNB Chain三条链上均可获取$MNER,请注意使用准确的合约,甄别是否为虚假资产,要对自己的资产负责。
$MNER合约集合: MNER Merlin Contract : 0x27622b326ff3ffa7dc10ae291800c3073b55aa39
MNER ETH Contract :0x43be406531af1e2dcb77c4becd3e8a1c6f855408
MNER BNB Contract :0x5e0e27F21d58B3F1eD741deCde6040CA659923E1
步骤2:跨链
目前支持的跨链桥:Chainge跨链桥: https://dapp.chainge.finance/ 注意:该跨链桥暂不支持手机端操作,请在PC端操作; -连接钱包->选择资产为MNER->选择链【发出链(ETH、BSC)和接收链(Merlin Chain)】->填入跨链MNER数量->提交

-左侧点击资产代币,弹出右侧框,输入MNER,选择MNER;

-左侧点击链,右侧选择对应的链,From可选择Ethereum、BNB Chain(从哪条链交易获取的$MNER就选择什么链),Into选择Merlin Mainnet;

-最后核实数据是否正确,确认无误,提交即可。

质押$MNER
官方质押链接:https://stake.mner.club/ 本教程用Bitget Wallet 访问Mineral Dapp操作演示:
-先连接钱包,点击Connect,选择EVM Wallet中的Bitget Wallet


-选择MNER,选择质押时间,分30天、180天和360天,根据不同时间有不同的APR; 选择质押时间->填写质押的MNER数量->点击Stake Now

步骤5:查看和领取收益
进入Dashboard看您的资产质押情况信息和点击“Claim All BTC”、“Claim All MNER”领取您的收益; 注意:领取需要Gas


-
-
 @ 9edd72eb:cb697b0a
2024-04-20 17:29:38
@ 9edd72eb:cb697b0a
2024-04-20 17:29:38Opinion about Unstoppable Crypto Wallet (Android)
One of the strong points of this wallet is its security protocols that use advanced encryption methods and multi-factor authentication to protect user information.
The interface is intuitive which can be useful for novice and experienced users. Navigation is simple and easily accessible.
The wallet supports a diverse range of cryptocurrencies, including popular and lesser-known tokens.
It guarantees complete control of private keys and funds, emphasizing ownership and autonomy.
The platform enhances utilization, allowing users to manage their crypto assets across multiple devices, both smartphones and desktops.
On the other hand, it lacks customization options.
The lack of integrated fiat currency support might inconvenience users who frequently engage in fiat-to-crypto transactions.
Limited customer support channels and documentation could leave users stranded in case of technical difficulties or questions.
WalletScrutiny #nostrOpinion
-
 @ 75bf2353:e1bfa895
2024-04-20 16:04:40
@ 75bf2353:e1bfa895
2024-04-20 16:04:40My Favorite Nostr Clients
Favorite Social Media Client.
https://www.nostrapps.com/apps/amethyst
Favorite Video Client
 https://www.nostrapps.com/apps/flare
https://www.nostrapps.com/apps/flareFavorite Meet Up Client
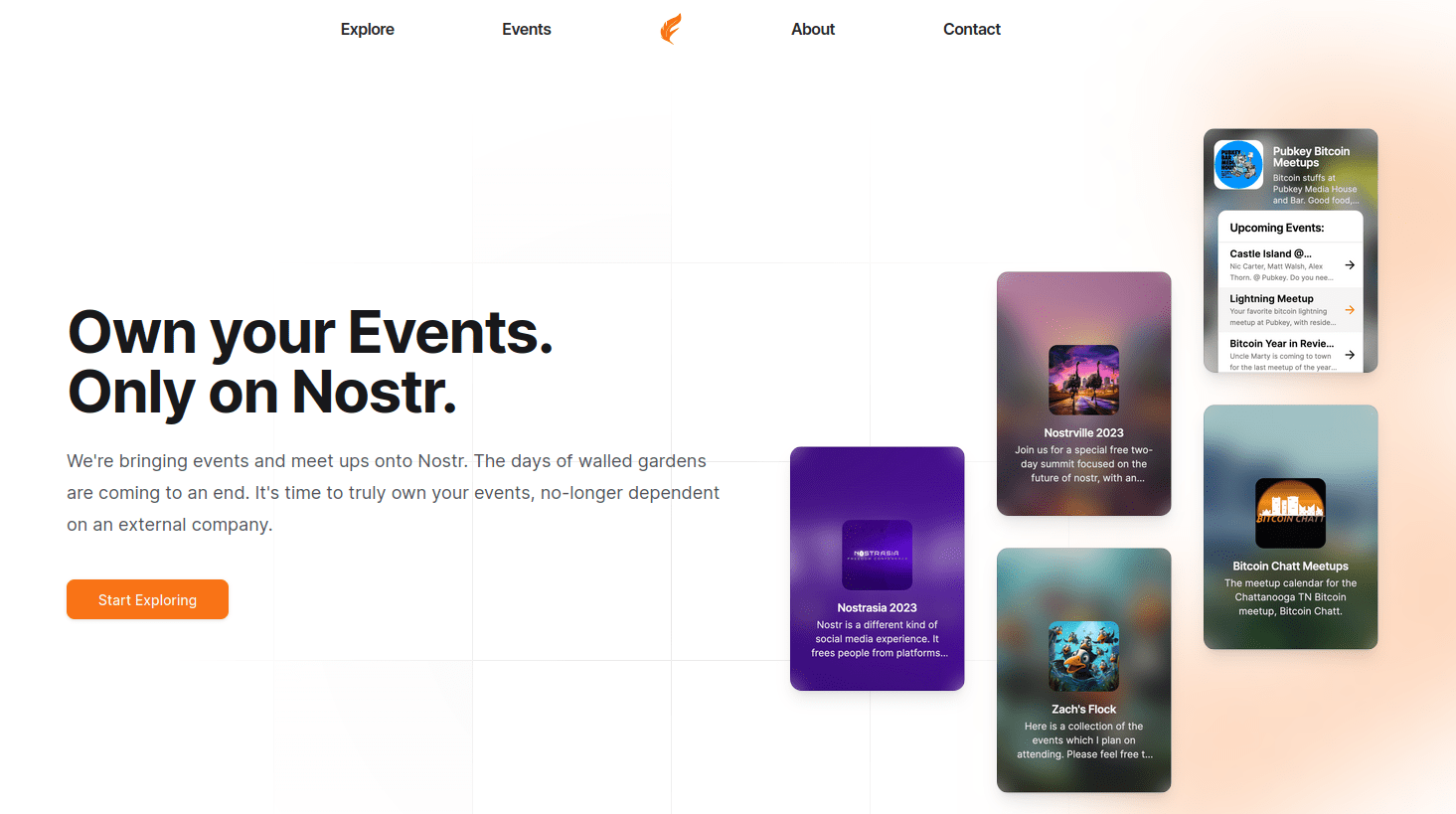 https://www.nostrapps.com/apps/flockstr
https://www.nostrapps.com/apps/flockstrFavorite Podcast & Music Client
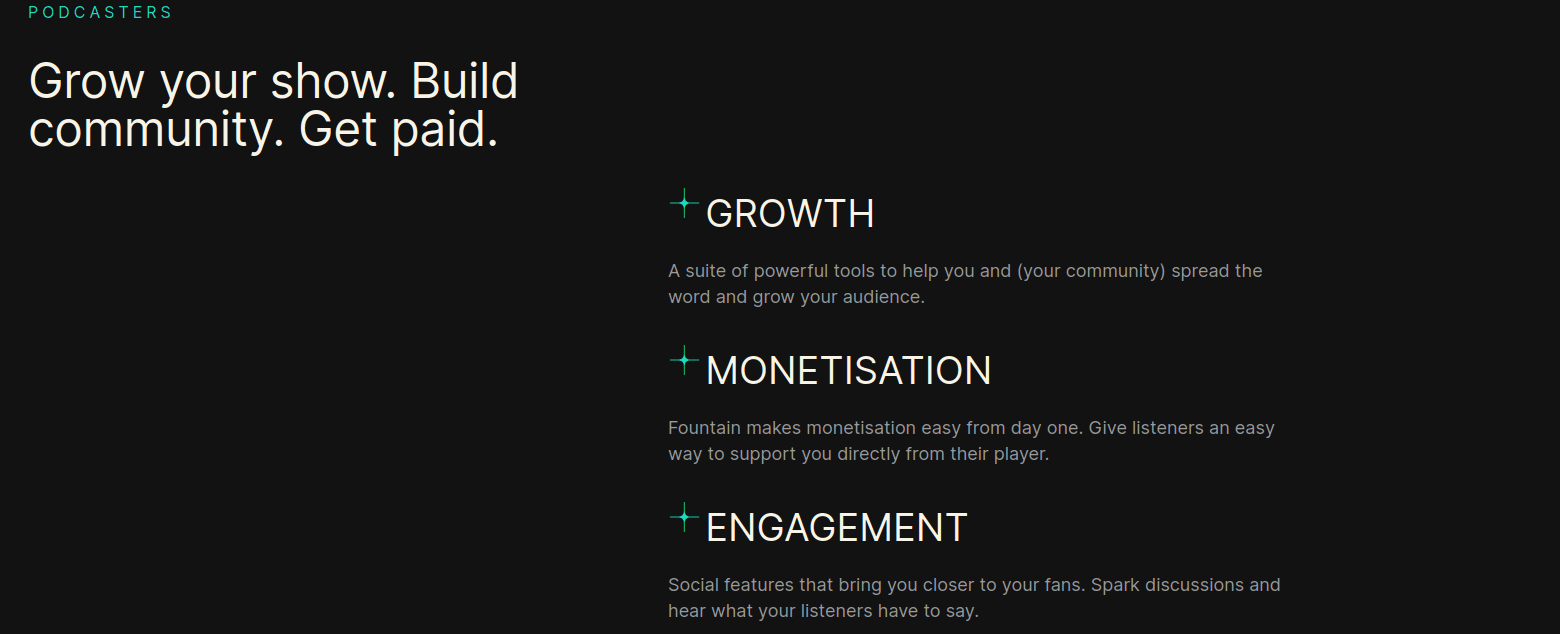
https://www.nostrapps.com/apps/fountain
Favorite Blogging Client
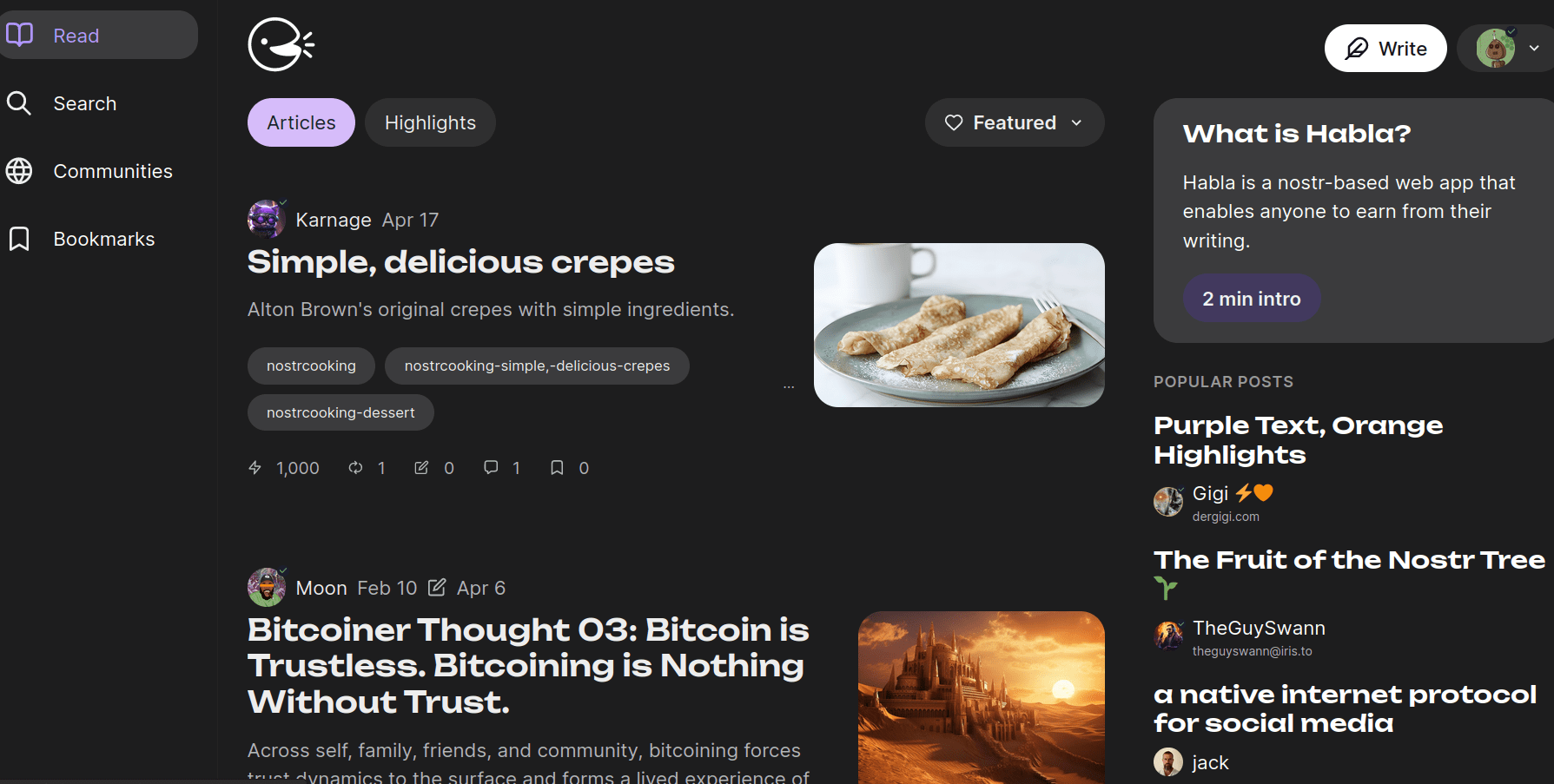 https://www.nostrapps.com/apps/habla
https://www.nostrapps.com/apps/hablaFavorite Patreon Alternative
https://www.nostrapps.com/apps/highlighter
Favorite Venmo Alternative
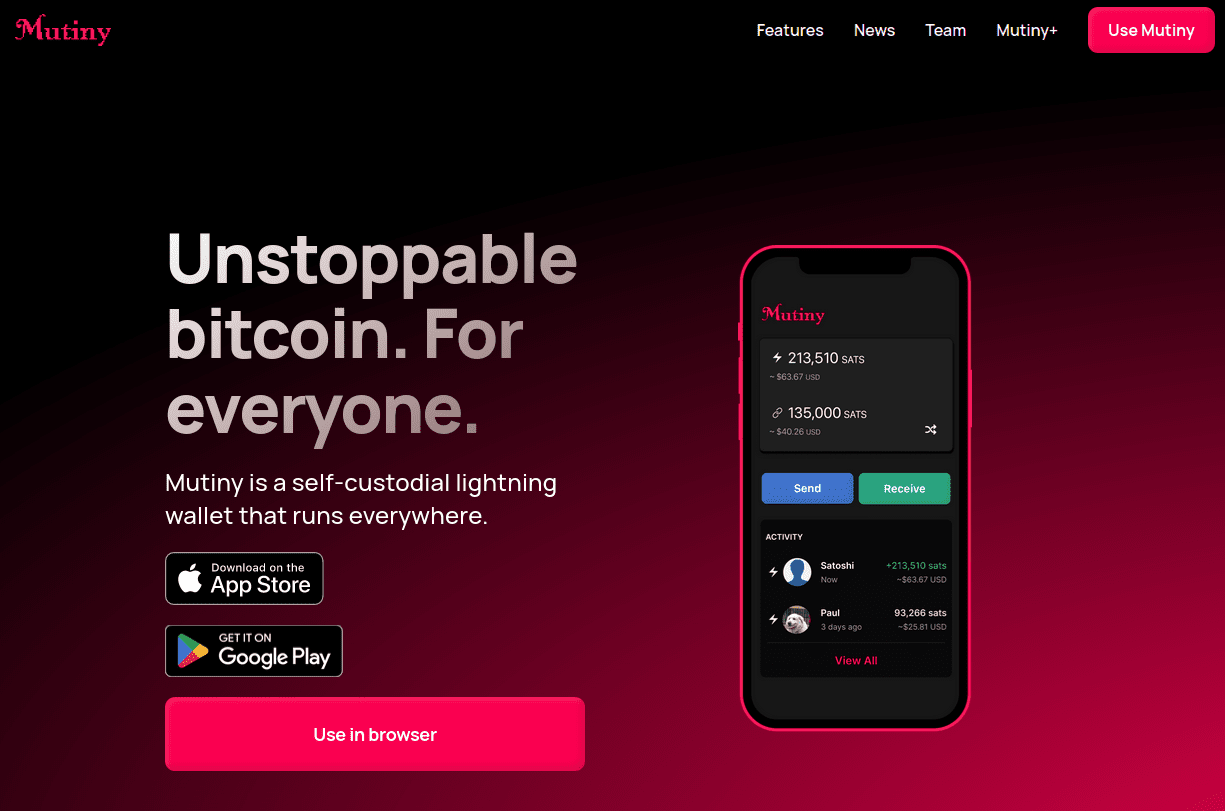 https://www.nostrapps.com/apps/mutiny
https://www.nostrapps.com/apps/mutinyFavorite eBay Alternative
 https://www.nostrapps.com/apps/shopstr
https://www.nostrapps.com/apps/shopstrFavorite File Hosting
https://nostr.build
-
 @ 362ebffa:492e2719
2024-04-20 15:52:12
@ 362ebffa:492e2719
2024-04-20 15:52:12Julian Assange (founder of WikiLeaks) released classified documents in 2010, including sensitive U.S. military and diplomatic information. He faced charges of conspiracy and espionage for his role in obtaining and disseminating the documents. Edward Snowden, (former NSA contractor) leaked classified information in 2013, exposing global surveillance programs. Snowden revealed widespread data collection by intelligence agencies, leading to charges of espionage and theft of government property.
As of today in 2024, both Assange and Snowden are considered whistle blowers by some but face legal consequences for their actions, igniting debates on government transparency and individual rights.
In a sane democratic World, they should be free!
Their efforts to expose government surveillance and misconduct was brave and should be encouraged. But instead they have also faced legal consequences for their actions, with the U.S. government seeking their extradition to face trial on criminal charges.
These cases have sparked debates about government transparency, freedom of the press, national security, and the balance between individual rights and state interests.
Without whistle blowers, government are becoming bullies!
-
 @ c73818cc:ccd5c890
2024-04-20 15:46:41
@ c73818cc:ccd5c890
2024-04-20 15:46:41
🌟 Un paladino della privacy alza la voce
🌟 Nel corso di un'intervista esclusiva con Tucker Carlson, il fondatore di Telegram, Pavel Durov, ha denunciato l'intensificarsi della sorveglianza da parte dei servizi segreti statunitensi sulla sua piattaforma. Durov, da sempre paladino della privacy e della libertà di espressione, ha espresso profonda preoccupazione per le crescenti pressioni volte a limitare la libertà di comunicazione online.
🌟 Un nuovo canale per la lotta contro la sorveglianza
🌟 Per contrastare questa minaccia alla privacy, Durov ha annunciato la creazione di un nuovo canale Telegram dedicato alla lotta contro il controllo statale e la difesa dei diritti individuali.
🌟 Questo canale sarà un punto di riferimento per tutti gli attivisti e i cittadini che desiderano rimanere informati e mobilitarsi contro la sorveglianza di massa.
Seguici sui nostri canali social ed unisciti al nostro gruppo Telegram:
https://t.me/Bitcoin_Report_Italia
BitcoinReportItalia #TON #Telegram #TuckerCarlson #Carlson #Durov #BTC #Bitcoin #Halving #Cripto
-
 @ 8ea48526:e6720a43
2024-04-17 14:06:11
@ 8ea48526:e6720a43
2024-04-17 14:06:11Recently there has been discussion on the socials about supporting open source developers, specifically those who work on Bitcoin and Nostr. There is a small-ish camp of people who think that Bitcoin should remain as is…it’s perfect, don’t mess with a good thing. Many others think – correctly, in my opinion – that Bitcoin needs to be maintained and even enhanced. As long as the changes make Bitcoin better money, we should evaluate, go slow, and keep things simple.
Who will maintain Bitcoin and other open source projects? Will devs do it out of the goodness of their heart? Builders gotta eat; food ain’t free. A handful of institutions, both non-profit and businesses, provide grants and long term support to developers. This is great and I hope that continues. However, there is more that we can do. There is more that you can do.
Zappy 21st
I propose we make the 21st day of every month the (un)official ”Zap a Builder Day”. It’s simple. On day 21 in the current month, find a developer and zap them sats.
Created in the spirit of #v4v and the #grownostr social experiment, I’d love to see people make this part of their monthly routine. It’s common for certain days of the month to have meaning. The 1st day marks the start of a new month. The 5th day is a common day when mortgage payments are due. In the United States, on the 15th day of April taxes are due. So now there is the 21st day, the day you send some value to devs.
Who are you gonna zap?
Any open source developer. Start simple; don't overthink this. If you're using a Nostr client that you love, go find one of the contributors and zap them. If you use Bitcoin or Lightning regularly, find a Bitcoin or Lightning dev. There are many other great freedom tech tools, like wallets, sovereign computing apps, and privacy tools that have developers behind them. Zap a developer. (I say developer, but I really mean "contributor". Remember the designers, product, support, and project people who also contribute.)
I'm intentionally not giving names of developers here because I don't want to favor one over the other. Every open source developer is important to different people based on the tools they use. So go zap the people in your realm.
I'm only publishing this on Nostr, but I'm happy if the idea spreads beyond that. Nostr is the perfect place because you can so easily find a core dev and zap them. No need to track down their website hoping to find a wallet address or request a Lightning invoice.
Join the Zaps
While everyone is excited about block 840000, halvings come and halvings go. But the 21st is always here for you. Every month, reliably, quietly doing its thing. Just like those open source devs you rely on so much. They’re here every month, reliably, quietly doing their thing. Let’s show them some love.
This April 21st find a dev and zap them. If you’d like, add a message telling them how awesome their work is and tag it with #Zappy21st. Let’s flood the feeds with #Zappy21st messages and surface great open source developers to others. Next month on the 21st, we’ll do it again.
🤘
-
 @ 682558c5:bfa011f2
2024-04-20 15:00:30
@ 682558c5:bfa011f2
2024-04-20 15:00:30Please stop regurgitating the censorship tropes.
There is an ontological "beingness" of Bitcoin, and it's money-related.
Any use case that's not a Store of Value, Unit of Account, or Medium of Exchange is fundamentally flawed.
Yes, Bitcoin is permissionless money. But the money aspect is inseparable.
An acorn has the beingness of an oak tree. You might even go so far as to extend that beyond its life to include lumber or something crafted from lumber.
But an acorn does NOT have the beingness of a porcelain toilet to store shit.
The Downfall of Shitcoins.
Please stop repeating the straw man that anyone cheering the government-backed downfall of shitcoins is antithetical to the spirit of Bitcoin.
Shitcoins are an affinity scam. And they're NOT decentralized like Bitcoin.
We will cheer the downfall of shitcoins no matter how it comes. That makes us pragmatists, not government simps.
For some, it will be hard to believe, but even anarchists can use the power of government against itself or others - to be left the hell alone. We work with what we're given.
No Moral Dilemma is Required.
Shitcoins exist to extract value from others.
There's a carve-out in the non-aggression principle to not tolerate fraud or breach of contract.
Con artists and snake oil salesmen don't need to be tolerated in some twisted liberty-purity test.
Mental Gymnastics
The LoLbertarian purity tests ARE the mental gymnastics, the intellectual laziness to repeat sound bytes of fallacy.
Thinking through what Bitcoin and shitcoins are is the antidote. See past shitcoin marketing. See past their uSe CaSeS and their emotional attacks on anyone who opposes them.
This isn't a value judgment. This is understanding the core essence of something.
F Your Feelings.
Existence is independent of our perception or feelings. Bitcoin and shitcoins simply are what they are.
When we put down the parroted catch phrases of others, we can begin to think through what they truly are.
It's Bitcoin, not shitcoins. No, not even shitcoins ON Bitcoin. The timechain is a ledger for financial records. It's not a database for content or shitcoins. Stop attacking the people who see clearly. Your emperor has no clothes.
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28my personal approach on using
let,constandvarin javascriptSince these names can be used interchangeably almost everywhere and there are a lot of people asking and searching on the internet on how to use them (myself included until some weeks ago), I developed a personal approach that uses the declarations mostly as readability and code-sense sugar, for helping my mind, instead of expecting them to add physical value to the programs.
letis only for short-lived variables, defined at a single line and not changed after. Generally those variables which are there only to decrease the amount of typing. For example:for (let key in something) { /* we could use `something[key]` for this entire block, but it would be too much letters and not good for the fingers or the eyes, so we use a radically temporary variable */ let value = something[key] ... }constfor all names known to be constant across the entire module. Not including locally constant values. Thevaluein the example above, for example, is constant in its scope and could be declared withconst, but since there are many iterations and for each one there's a value with same name, "value", that could trick the reader into thinkingvalueis always the same. Modules and functions are the best example ofconstvariables:const PouchDB = require('pouchdb') const instantiateDB = function () {} const codes = { 23: 'atc', 43: 'qwx', 77: 'oxi' }varfor everything that may or not be variable. Names that may confuse people reading the code, even if they are constant locally, and are not suitable forlet(i.e., they are not completed in a simple direct declaration) apply for being declared withvar. For example:var output = '\n' lines.forEach(line => { output += ' ' output += line.trim() output += '\n' }) output += '\n---' for (let parent in parents) { var definitions = {} definitions.name = getName(parent) definitions.config = {} definitions.parent = parent } -
 @ 1c6b3be3:73f0ae6f
2024-04-20 14:27:28
@ 1c6b3be3:73f0ae6f
2024-04-20 14:27:28https://youtube.com/shorts/CqyFaZdkUzE?feature=share
Abstract
A purely peer-to-peer version of electronic storage would allow data to be saved directly from one party to another without going through a centralized third party. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to ensure data security and integrity. We propose a solution to the problem of data sovereignty using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of recorded events but also as proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they will generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best-effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
This decentralized system, which we will call Bitcoin S3, offers:
- Secure data storage
- Robust network security
- Individual sovereignty over information
By eliminating the need for trusted third parties, Bitcoin S3 paves the way for a new era of data management where each user has full control over their digital information.
-
 @ 908d47b6:a2bf38ad
2024-04-20 14:20:02
@ 908d47b6:a2bf38ad
2024-04-20 14:20:02Understanding Bitcoin Halvings
Bitcoin halving, often referred to as "The Halvening," is a programmed event designed to occur approximately every four years or to put it exactly: every 210,000 blocks mined. During a halving event, the reward given to miners for validating transactions and securing the network is reduced by half. This process ensures that the total supply of Bitcoin is gradually constrained, embodying the superior cryptocurrency's deflationary nature.
Supply Scarcity and Price Dynamics
The reduction in mining rewards through halving events directly impacts Bitcoin's supply dynamics. With fewer new coins entering circulation, Bitcoin transitions towards a state of increased scarcity, akin to precious metals like gold. Economic theory suggests that scarcity, coupled with sustained demand, can drive up the price of an asset. Consequently, many investors anticipate halving events as potential catalysts for price appreciation.
Historical Halving Events
Since Bitcoin's inception in 2009, there have been three halving events: in 2012, 2016, and 2020. Each halving has been accompanied by periods of heightened speculation and volatility in the cryptocurrency markets. Notably, historical data reveals a pattern of post-halving price rallies, although the magnitude and duration of these rallies vary. The 2020 halving, for instance, preceded a significant surge in Bitcoin's value, propelling it to new all-time highs in subsequent months.
Market Sentiment and Investor Behavior
Beyond the technical implications, Bitcoin halvings also influence market sentiment and investor behavior. Leading up to a halving event, anticipation often builds within the bitcoin community, fueling speculation and driving demand. Post-halving, sentiment can fluctuate based on perceived market conditions and macroeconomic factors. While some investors view halvings as bullish catalysts, others adopt a more cautious stance, mindful of potential short-term volatility.
Future Implications and Long-Term Viability
As Bitcoin continues to mature as a store of value and digital asset, the significance of halving events is likely to endure. Proponents argue that the predetermined and transparent nature of Bitcoin's monetary policy, governed by halvings, instills confidence in its long-term viability as a decentralized currency. However, critics raise concerns about potential drawbacks, such as increased mining centralization or uncertainty surrounding future consensus mechanisms.
Conclusion
Bitcoin halvings represent a fundamental aspect of Bitcoin's economic model, embodying its deflationary principles and supply dynamics. While these events have historically been associated with market speculation and volatility, they also underscore Bitcoin's resilience and growing mainstream acceptance. As the bitcoin ecosystem continues to evolve, the impact of halving events on Bitcoin's price and ecosystem will remain a topic of keen interest and debate among investors and enthusiasts alike.
Sources: Bitcoin Whitepaper, Bitcoin.org, academic papers
-
 @ 6ad3e2a3:c90b7740
2024-04-12 23:42:51
@ 6ad3e2a3:c90b7740
2024-04-12 23:42:51After unsuccessfully trying to orange-pill* a friend the other day, I realized the problem: for a lot of successful, worldly people the notion you can get something for nothing is anathema. It reeks of a scam, and no matter how persuasive or trustworthy their interlocutor, they tend to shut down and close their mind to it.
*To “orange-pill” means to get someone to buy — or at least see the value proposition of — bitcoin.
Put differently, smart people understand risk and reward are inseparable. If someone is telling you this is the opportunity of a lifetime, it probably isn’t. To the extent it has the upside purported, its risk of ruin is no doubt commensurate.
But that is only the case when there is information symmetry. If I tell you the stock market is going to the moon next year, you know there are smart people on the other side of that bet, or else it would be at the moon already. And because they have access to the same information I do, any large way-out-of-the-money call option on the S&P500 is at grave risk of not cashing in. Hence you would be wise to ignore my advice.
But what about when one party to the trade has information the other lacks? For example, Nancy Pelosi has a net worth north of $100 million on her comparatively meager congressional salary, due in large part to trading on insider information. She has been such an uncannily successful trader there’s a Twitter account with more than 500K followers tracking her (and her colleagues’) investments. Surely in the case of her trades, the risk was not commensurate with the rewards.
Another obvious example from history was the Dutch buying the island of Manhattan from the natives for a bunch of tools and beads. The risk and reward to the Dutch were not remotely commensurate due to information asymmetry.
All the time, people cultivate expertise in pricing antiques, collectibles and other items that give them a significant advantage over most market participants and sever the strict relationship between risk and reward that exists in more information-symmetrical environments.
But what all three of those scenarios have in common is the information providing the advantage is essentially a secret. The natives presumably didn’t know how common and easily replaced the tools and trinkets for which they traded Manhattan were. The public doesn’t have access to the information on which Congress is trading. And the layperson lacks the in-depth, niche knowledge of the expert art or antiques dealer.
But the Bitcoin-for-dollars trade happens to be asymmetrical, despite the information being wholly public and hidden in plain sight. The asymmetry comes from one party being sufficiently naive and curious and the other too savvy and close-minded. As a result, many who got into Bitcoin earliest were financial outsiders, novices, nerds and cypherpunks rather than Wall-Street professionals who are accustomed to getting the jump.
The media, gatekept and controlled by the same factions who run the banking system, have only exacerbated this asymmetry, spreading unfounded fear, uncertainty and doubt about bitcoin specifically (It boils the oceans! It’s backed by nothing!) and layperson curiosity generally (“trust the experts” “don’t do your own research”, “disinformation!”) As a result, not only are the professional insiders out, but also those who rely on their expertise to assess investment opportunities, which is why many of the savviest and smartest people are ironically the most difficult to convince.
. . .
Maybe this is what's meant by “The meek shall inherit the earth,” if we use curious and open-minded to stand in for “meek.” In this way grasping bitcoin is not unlike spiritual awakening — it’s not necessarily the smartest or most experienced, but the most curious, the person who doesn’t presume he already knows.
-
 @ bcea2b98:7ccef3c9
2024-04-20 14:20:00
@ bcea2b98:7ccef3c9
2024-04-20 14:20:00The model suggests Bitcoin's price hinges on its scarcity, gauged by the stock-to-flow ratio, comparing the amount in circulation to newly mined coins. Higher ratios signify greater scarcity, akin to gold's historical average of 66. After Bitcoin's third halving, its ratio doubled, enhancing its scarcity.
Meanwhile, the Grayscale Bitcoin Trust's recent halving, losing 300k BTC since the launch of spot Bitcoin ETFs, may have a more immediate negative impact on Bitcoin's price.
-
 @ 46fcbe30:6bd8ce4d
2024-04-11 17:21:28
@ 46fcbe30:6bd8ce4d
2024-04-11 17:21:28Opinion about Phoenix - LN Bitcoin wallet (android)
Phoenix is one of my favorite wallets. It makes using Bitcoin really easy but at a price. The wallet lets you send and receive both over the lightning network and on-chain without jumping through hoops, first but at the cost of either kind of hidden fees or unexpected on-chain fees.
To my understanding, when you receive on-chain funds, the wallet does yet another on-chain transaction to get these funds onto lightning and when you send via lightning, you pay an extra 0.4% to the provider. This 0.4% fee is not capped in any way, so while you can send $1000 via lightning, that will cost you $4 even when on-chain transactions would have cost just $1.
As of writing this opinion, the wallet is not reproducible which is a red flag to updating to this version but the provider hopefully will fix that soon as they are an OG player in the space.
WalletScrutiny #nostrOpinion
-
 @ 4b0087ee:a4f329cc
2024-04-20 13:26:18
@ 4b0087ee:a4f329cc
2024-04-20 13:26:18Halving Fee Chaos by Jimmy Song (송재준) @jimmysong
The Bitcoin halving is an anticipated event, one of those Bitcoin holidays that happen every once in a while. Along with Soft Fork Activation and various financial instrument introduction days, it's one of those not-quite-predictable days that occur every few years which give Bitcoiners reason to pay attention and mainstream media to speculate.
This year's halving was much anticipated, as halvings usually are, but we had a bit of an incident that requires some further explanation. The block subsidy decreased from 6.25 BTC to 3.125 BTC on block 840,000 as expected, but what wasn't expected was the 37.626 BTC in fees that came along with it. To give some context, that's easily the highest ratio of fees to block subsidy that Bitcoin has ever had. One transaction paid nearly 8 BTC in fees by itself.
More Fees It wasn't just block 840,000 that had high fees, over the next 5 blocks, we had fees of 4.486, 6.99, 16.068, 24.008 and 29.821 BTC respectively. The fees are the highest it's ever been. This situation in Bitcoin is unprecedented.
Up to this point in Bitcoin's history a block whose fees were higher than block subsidy were pretty rare. There were a few in the 50 and 25 BTC eras, but these were mistakes by the user (usually forgetting to put in a change address) and almost all of the fee came from a single error transaction. In the 12.5 BTC subsidy era, there were a few transactions toward the end of 2017 when the cumulative fees exceeded the 12.5 subsidy. In the just-ended 6.25 BTC subsidy era, there were many blocks during the ordinals craze which exceeded the 6.25 BTC subsidy.
Still, these were relatively rare, and most blocks even in the most recently completed era mostly didn't exceeded 1.5 BTC. Yet in this new era of 3.125 BTC subsidy, every single block as of this writing (block 840018) has had fees exceed the subsidy, some by many multiples.
So what happened? Why was the halving block getting so much in fees? ...
https://x.com/jimmysong/status/1781518918001078441
-
 @ 5d4b6c8d:8a1c1ee3
2024-04-20 12:23:58
@ 5d4b6c8d:8a1c1ee3
2024-04-20 12:23:58Only two have survived to make the playoffs proper. Congratulations to @siggy47 and @grayruby!
We bid a fond farewell to @BTC_Bellzer. You made the boldest initial gambit by successfully picking the Spurs in our opening round, which would have guaranteed winning any tie-breaker that might happen later.
Round 1
@siggy47 already made his selection and shockingly it was the unfamiliar expansion team in Minnesota. All we need is @grayruby's selection.
As of now, @siggy47 is holding the tie-breaker.
Grand Prize
7114 sats (and growing)
-
 @ 57d1a264:69f1fee1
2024-04-20 12:18:39
@ 57d1a264:69f1fee1
2024-04-20 12:18:39Prompt: Event Listing ===============
Design a feature or display for upcoming events. Concerts, workshops, summer camps, seminars, or other training events. Get creative with the purpose and style. What's happening in the Bitcoin meatspace?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ c48e29f0:26e14c11
2024-04-10 16:54:40
@ c48e29f0:26e14c11
2024-04-10 16:54:40A Harvard economist published 100+ pages of survey analysis to confirm what anyone outside of the fiat academic bubble already knows: people don't like it when the stored value of their time+energy is inflated into oblivion.
You can access the full report here for anyone interested: https://www.nber.org/system/files/working_papers/w32300/w32300.pdf
One quote from the Abstract really jumped out at me: "The predominant reason for people’s aversion to inflation is the widespread belief that it diminishes their buying power."
Well, yeah, no shit... But this isn't a "belief"... this is a fact.
Here's the thing: the average person understands the problem, because they feel the effects of the problem every single day...
They may not understand the root cause of the problem (creating money out of thin air)--instead blaming "greedy corporations" or "Joe Biden" or "Putin's Price Hike" or whatever the propaganda du jour happens to be--but they know inflation feels wrong. It feels like someone is stealing from them (which is true).
They know their purchasing power has decreased, because when they spend a dollar today it buys less than it did five years ago, and much less than it did 20 years ago.
It doesn't matter if fiat academics tell them "everything is fine! stop complaining! inflation is ackshually a good thing!"
People can feel that something is broken.
Most people still think there is a partisan/political solution to the problems they feel.
They think "if only OUR guy was in charge, things would be better" or "if only we taxed the greedy corporations and the rich more, then things would be better."
But political solutions will always be bandaids meant to superficially treat the symptoms of the disease so the Political Team proposing the "solution" can score short-term perceived wins ahead of the next election. "Look, we did something! Now stop complaining and vote for us because the other guy is literally the devil."
A few people already realize that the money itself is broken.
They understand that when the money breaks, society breaks with it.
Money created out of thin air disproportionally enriches those closest to the creation of the new money.
Money created out of thin air is used to fund Forever Wars we never agreed to enter.
Money created out of thin air is used to subsidize companies/industries that the free market does not value, distorting price signals.
Money created out of thin air bails out banks.
Money created out of thin air perpetuates never-ending boom and bust cycles.
Money created out of thin air reduces the purchasing power of the money in your pocket.
Money created out of thin air steals the value of your time and energy, of your life itself.
The people who realize the money is broken now save the value of their time and energy in Bitcoin; a money separate from the State with a fixed supply of 21M which cannot be arbitrarily inflated.
Bitcoiners know we need to cure the base layer disease, not just treat the symptoms while politicians kick a can full of worthless money down the road until it lands at the feet of our children.
Bitcoiners refuse to abdicate responsibility. Bitcoiners refuse to pass this disease on to our children. Fiat is the disease, and we know we must cure it.
It will not be easy, but it must be done.
We need to fix the money.
Study Bitcoin. https://bitcoinpodcast.net https://primal.net/walker
-
 @ c11cf5f8:4928464d
2024-04-20 11:46:29
@ c11cf5f8:4928464d
2024-04-20 11:46:29Let's hear some of your latest Bitcoin trades, feel free to include links to your shops or sites you sold it from or the pic of the sold item.
If you missed our last thread, here are some of the items stackers recently spent their sats on the ~AGORA territory.
-
 @ 52b4a076:e7fad8bd
2024-04-10 01:12:11
@ 52b4a076:e7fad8bd
2024-04-10 01:12:11Why this is happening
This happens due to an invalid real IP header.
You are most likely using
X-Forwarded-Foras the real IP header. Strfry expects the real IP header to contain just an IP, but theX-Forwarded-Forheader is a list of IPs, with every proxy adding the IP of where it got the request from.If a client specifies an X-Forwarded-For header, like
X-Forwarded-For: 1.1.1.1, your proxy will add the remote IP, like this:X-Forwarded-For: 1.1.1.1, 127.0.0.1When you use$proxy_add_x_forwarded_forin Nginx, this is what it is doing: appending the remote IP to the header.Strfry tries parsing
1.1.1.1, 127.0.0.1as an IP address, fails, and throws an exception.How to fix it
If you are using Caddy, just switch to
X-Real-IP.If you are using Nginx, you can add a real IP header like so, and switch to using it:
proxy_set_header X-Real-IP $remote_addr;You can also disable the real IP header, but this will cause problems if you use a write filter script or look at the logs.
-
 @ 46205202:5f2056a6
2024-04-20 11:39:32
@ 46205202:5f2056a6
2024-04-20 11:39:32Chickpea Soup
Ingredients List
- 1/4 cup olive oil
- 4 garlic cloves
- 1 large yellow onion, chopped
- 1 2-inch piece of ginger chopped finely
- salt to taste
- 1 1/2 tsp tumeric
- 2 19oz cans of chickpeas, drained & rinsed
- 2 400mL cans of full-fat coconut milk
- 2 cups vegi broth
Steps
- Heat oil, garlic, onion, ginger, salt over medium heat, until onion is translucent.
- Slightly crush the some chickpeas to release starch. Scrape any browning off the bottom of pot for flavor.
- Add coconut milk & broth; simmer until a desirable consistency.
-
 @ 947c8c3e:22e2d6ea
2024-04-09 00:59:19
@ 947c8c3e:22e2d6ea
2024-04-09 00:59:19Server Address: mine.ghostgrid.network Port: 30000
Introduction
Minetest is an open-source voxel game engine that allows players to create and play in infinite worlds. This guide will walk you through downloading and installing Minetest, creating an account, and joining the specified server.
Downloading and Installing Minetest
For Windows Users
- Visit the Official Website: Navigate to Minetest's official download page.
- Download the Installer: Click on the Windows option to download the installer.
- Run the Installer: Open the downloaded file and follow the installation prompts.
For macOS Users
- Visit the Official Website: Go to Minetest's download page.
- Download for macOS: Click on the macOS option and download the file.
- Install Minetest: Open the downloaded file. Drag and drop the Minetest icon into your Applications folder.
For Linux Users
- Using a Package Manager: For most Linux distributions, Minetest can be installed directly from the package manager. For example, on Ubuntu, you can use:
bash sudo apt-get install minetest- Compiling from Source: Alternatively, you can compile Minetest from source. Instructions can be found on the official website.
For Android Users
Downloading and Installing Minetest
- Open Google Play Store: On your Android device, launch the Google Play Store app.
- Search for Minetest: Tap on the search bar at the top of the screen and type in "Minetest". Press enter or the search icon.
- Install the App: Find the official Minetest app from the search results and tap "Install" to begin the download and installation process.
Registering an Account and Joining the Server
On Android, the process for registering an account and joining a server is similar to that on other platforms, with some minor differences in the user interface.
- Launch Minetest: Open the Minetest app once it's installed.
- Access the Main Menu: Tap on the three dots in the upper right corner to access the main menu and select "Join Game".
- Server Details: Tap on the "New" button to add a server. You'll be prompted to enter the server details. Use the following information:
- Server Name: This can be anything you like; it's a label for your convenience.
- Address: Enter
mine.ghostgrid.network. - Port: Type in
30000.
- Create Your Account: Enter a username and password in the provided fields. This will register your account for this server.
- Join the Server: With the server details filled in and your account created, tap "Connect" to join the server.
Registering an Account
To join a server in Minetest, you'll need to create an in-game account. For most servers, this can be done directly when you join a new server. Keep in mind, the process might slightly vary based on the server settings.
- Launch Minetest: Open the Minetest application.
- Select 'Join Game': Find and click on the 'Join Game' tab at the top.
-
Enter Server Details: You'll see fields to enter a server's address and port. Use the following details:
- Server Address:
mine.ghostgrid.network - Port:
30000
- Server Address:
-
Choose a Name and Password: You will be prompted to enter a username and a password. This is effectively your registration process for this server.
Joining the Server
After registering your account, you're all set to join the server.
- Enter Your Credentials: Input the username and password you just created.
- Join the Server: Click 'Connect' to join the server.
Conclusion
Congratulations! You're now ready to explore the vast world of Minetest on the server at
mine.ghostgrid.network. Remember, each server in Minetest can have its unique set of rules and mods. It's a good idea to familiarize yourself with them to enhance your playing experience.Enjoy your time in our server, and don't hesitate to explore the endless possibilities within its worlds.
-
 @ fbe736db:187bb0d5
2024-04-20 11:29:03
@ fbe736db:187bb0d5
2024-04-20 11:29:03This is a slight refactoring of an article I wrote in April 2021.
I take a long term macroeconomic view on bitcoin, and just bitcoin, for being an incredible emerging store of value over a long term time horizon. It’s remarkable how many potential pitfalls there are for newcomers to the space when the optimal course of action is so simple -
Buy and hold bitcoin.
One of the pitfalls for many is trying to trade bitcoin. It arises from the fact that it has an open market to trade 24/7, with very low fees to trade, and is incredibly volatile - a magnet for traders.
Everyone should be aware of the legendary blog post that first coined the word HODL. Link here if you haven’t seen it, and I salute them. It shows that even early on, there was an appreciation by some of the futility of trying to trade bitcoin to realise higher returns, rather than simply just holding.
My only worry is others misinterpreting it when he says “I know I’m a bad trader”. I would go further and argue that with very few exceptions, we are all bad traders. Most just don’t realise it, as they benefit from a rising market overall.
I’ll admit though, the process of buying bitcoin has been in danger of leading me to try and second guess the price movements too, regardless of my stated long time horizon. And if you have ever found yourself planning a Bitcoin purchase, but then seeing the short term movement in price and then holding off by a day, or a week, then perhaps that’s you too.
So how to stop ourselves from becoming traders, even when just buying with a long term outlook? There is a fair appreciation of Dollar Cost Averaging (DCA). This is simply the concept of regular predetermined buys to reduce entry price volatility.
Now to the main point of this article. At every turn with Bitcoiners lies the phrase “Buy the Dip”. It’s everywhere! But could it backfire?
Let’s define such a strategy by putting some parameters as follows “Buy $x of Bitcoin when the price has fallen at least y% from its recent local maximum.” This is intuitive and would appear to get you some cheaper entry prices than simple DCA’ing over time.
As soon as I became aware that this is a common phrase, I was immediately sceptical of whether it was ever worth following compared to a DCA approach.
Obviously, there is limitless backtesting potential on this subject. I did so for the 6 months from October 1st 2020 to March 31st 2021 in the previous bull market.
In my test, I included a base level DCA strategy basic control strategy of investing $100 on every Monday since October 1st 2020 ($2,600 in total)-weekly DCA. This would have accumulated approx 0.118 btc, at an average cost of $22,007, over the 6 months.
So how about trying to invest the same overall amount to gradually “buy the dips” as a comparison?
The graph below shows 13 theoretical entry points from the period from Oct 1st 2020 to 31 March 2021 for “Buying the 10% dip”. This could be have been done in practice by buying a set $ amount once the price dropped down 10% from that most recent high.
If we split out $2,600 total spend from earlier into $200 for each dip, for these entry points this would have bought us 0.082 btc in total, at an average price of $31,800 for Bitcoin at these times. Remember, that’s compared to over 0.11 btc acquired at an average price of $22k for the DCA approach.
The difference is huge. Dollar Cost Averaging would have acquired around 40% more bitcoin than attempting to buy the 10% dips over the 6 month period.
The reason in this case is simple, and could be seen by layering on regular DCA points on the above graph. Towards the start of the bull run, Bitcoin’s price rose in a stealthy and steady fashion, with no 10% dips to speak of until late November. The prices of the early DCA buys would have been largely missed by anyone patiently waiting for the 10% dips. Hence the average $ price paid is far higher.
Ok, I get it. It’s as spurious for me to argue that a strategy like this doesn’t work as it would be to argue it does work. It’s also not really valid to compare DCA to “Buying the dips”. You can’t even budget the same total amount in advance as I have done, as you don’t know how many dips there will be. Plus, this is only one example. However as often as not, those waiting for dips can be essentially punished for doing so.
Trying to buy the drip in itself means placing parameters over how to buy the dip. This in itself is very tricky — do you choose a 5% dip? 10% dip? Working it through, the exact choice of dip makes no difference to the underlying realities.
I don’t want to be dragged into arguing for any particular trading strategy over another. There are no doubt plenty of range trading periods where buying the dip looks good by contrast. My point is that trying to “buy the dip” in reality leads you halfway into trying to trade Bitcoin. Don't trade Bitcoin.
Why am I so against trading Bitcoin in general? Many people do make money trading Bitcoin. Fiat money. They set their benchmark for success as making money in dollars, when in reality they are under performing buy and hold bitcoin over time. By this I mean they end up with less btc than they could have acquired had they had simply bought and held btc with their funds right at their starting point. Profit in fiat is misleading.
History has shown in the last decade - it is very very difficult to trade Bitcoin, using Bitcoin as your starting basis and benchmark, and come out on top. Even simply "buying the dip" is in some way trying to trade.
There are only two methods that I can see of avoiding this curse of trading. One is some form of DCA, and the other is simply existing on a Bitcoin standard.
One analogy as to why either of these beat the trading curse is making a truly random selection each time when you play Rock Paper Scissors. In the long run that is not going to outperform your opponent but equally it will protect you from losing to them.
As Marla Daniels once observed in the Wire ‘The game is rigged, but you cannot lose if you do not play’. In Bitcoin we have at least two different forms of not playing —
(1) not attempting to trade it, as above, and
(2) exiting asset holdings denominated in fiat currencies. With large amounts of monetary debasement, and increasingly desperate search for yield and returns, this is the largest rigged game of all.
Admittedly though, Buy the Dip is also a wider phrase. I know not everyone out there is trying to “buy the dip” as a strategy. Use of the phrase is often expressed as a narrative of solidarity. During price falls, strong hands buy in more and at a better entry price. This is as opposed to panicking and selling, as the weak hands are known to do when confronted by volatility and price falls. So buying the dip is a “keep calm and carry on” phrase, if you like.
To support the above argument, just consider Michael Saylor, whose billions probably lend weight and credibility to his actions.
Saylor doesn’t try and buy the dip. He just buys.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Rumple
a payments network based on trust channels
This is the description of a Lightning-like network that will work only with credit or trust-based channels and exist alongside the normal Lightning Network. I imagine some people will think this is undesirable and at the same time very easy to do (such that if it doesn't exist yet it must be because no one cares), but in fact it is a very desirable thing -- which I hope I can establish below -- and at the same time a very non-trivial problem to solve, as the history of Ryan Fugger's Ripple project and posterior copies of it show.
Read these first to get the full context:
- Ryan Fugger's Ripple
- Ripple and the problem of the decentralized commit
- The Lightning Network solves the problem of the decentralized commit
- Parallel Chains
Explanation about the name
Since we're copying the fundamental Ripple idea from Ryan Fugger and since the name "Ripple" is now associated with a scam coin called XRP, and since Ryan Fugger has changed the name of his old website "Ripplepay" to "Rumplepay", we will follow his lead here. If "Ripplepay" was the name of a centralized prototype to the open peer-to-peer network "Ripple", now that the centralized version is called "Rumplepay" the peer-to-peer version must be called "Rumple".
Now the idea
Basically we copy the Lightning Network, but without HTLCs or channels being opened and closed with funds committed to them on multisig Bitcoin transactions published to the blockchain. Instead we use pure trust relationships like the original Ripple concept.
And we use the blockchain commit method, but instead of spending an absurd amount of money to use the actual Bitcoin blockchain instead we use a parallel chain.
How exactly -- a protocol proposal attempt
It could work like this:
The parallel chain, or "Rumple Chain"
- We define a parallel chain with a genesis block;
- Following blocks must contain
a. the ID of the previous block; b. a list of up to 32768 entries of arbitrary 32-byte values; c. an ID constituted by sha256(the previous block ID + the merkle root of all the entries) - To be mined, each parallel block must be included in the Bitcoin chain according as explained above.
Now that we have a structure for a simple "blockchain" that is completely useless, just blocks over blocks of meaningless values, we proceed to the next step of assigning meaning to these values.
The off-chain payments network, or "Rumple Network"
- We create a network of nodes that can talk to each other via TCP messages (all details are the same as the Lightning Network, except where mentioned otherwise);
- These nodes can create trust channels to each other. These channels are backed by nothing except the willingness of one peer to pay the other what is owed.
- When Alice creates a trust channel with Bob (
Alice trusts Bob), contrary to what happens in the Lightning Network, it's A that can immediately receive payments through that channel, and everything A receives will be an IOU from Bob to Alice. So Alice should never open a channel to Bob unless Alice trusts Bob. But also Alice can choose the amount of trust it has in Bob, she can, for example, open a very small channel with Bob, which means she will only lose a few satoshis if Bob decides to exit scam her. (in the original Ripple examples these channels were always depicted as friend relationships, and they can continue being that, but it's expected -- given the experience of the Lightning Network -- that the bulk of the channels will exist between users and wallet provider nodes that will act as hubs). - As Alice receive a payment through her channel with Bob, she becomes a creditor and Bob a debtor, i.e., the balance of the channel moves a little to her side. Now she can use these funds to make payments over that channel (or make a payment that combines funds from multiple channels using MPP).
- If at any time Alice decides to close her channel with Bob, she can send all the funds she has standing there to somewhere else (for example, another channel she has with someone else, another wallet somewhere else, a shop that is selling some good or service, or a service that will aggregate all funds from all her channels and send a transaction to the Bitcoin chain on her behalf).
- If at any time Bob leaves the network Alice is entitled by Bob's cryptographic signatures to knock on his door and demand payment, or go to a judge and ask him to force Bob to pay, or share the signatures and commitments online and hurt Bob's reputation with the rest of the network (but yes, none of these things is good enough and if Bob is a very dishonest person none of these things is likely to save Alice's funds).
The payment flow
- Suppose there exists a route
Alice->Bob->Caroland Alice wants to send a payment to Carol. - First Alice reads an invoice she received from Carol. The invoice (which can be pretty similar or maybe even the same as BOLT11) contains a payment hash
hand information about how to reach Carol's node, optionally an amount. Let's say it's 100 satoshis. - Using the routing information she gathered, Alice builds an onion and sends it to Bob, at the same time she offers to Bob a "conditional IOU". That stands for a signed commitment that Alice will owe Bob an 100 satoshis if in the next 50 blocks of the Rumple Chain there appears a block containing the preimage
psuch thatsha256(p) == h. - Bob peels the onion and discovers that he must forward that payment to Carol, so he forwards the peeled onion and offers a conditional IOU to Carol with the same
h. Bob doesn't know Carol is the final recipient of the payment, it could potentially go on and on. - When Carol gets the conditional IOU from Bob, she makes a list of all the nodes who have announced themselves as miners (which is not something I have mentioned before, but nodes that are acting as miners will must announce themselves somehow) and are online and bidding for the next Rumple block. Each of these miners will have previously published a random 32-byte value
vthey they intend to include in their next block. - Carol sends payments through routes to all (or a big number) of these miners, but this time the conditional IOU contains two conditions (values that must appear in a block for the IOU to be valid):
psuch thatsha256(p) == h(the same that featured in the invoice) andv(which must be unique and constant for each miner, something that is easily verifiable by Carol beforehand). Also, instead of these conditions being valid for the next 50 blocks they are valid only for the single next block. - Now Carol broadcasts
pto the mempool and hopes one of the miners to which she sent conditional payments sees it and, allured by the possibility of cashing in Carol's payment, includespin the next block. If that does not happen, Carol can try again in the next block.
Why bother with this at all?
-
The biggest advantage of Lightning is its openness
It has been said multiple times that if trust is involved then we don't need Lightning, we can use Coinbase, or worse, Paypal. This is very wrong. Lightning is good specially because it serves as a bridge between Coinbase, Paypal, other custodial provider and someone running their own node. All these can transact freely across the network and pay each other without worrying about who is in which provider or setup.
Rumple inherits that openness. In a Rumple Network anyone is free to open new trust channels and immediately route payments to anyone else.
Also, since Rumple payments are also based on the reveal of a preimage it can do swaps with Lightning inside a payment route from day one (by which I mean one can pay from Rumple to Lightning and vice-versa).
-
Rumple fixes Lightning's fragility
Lightning is too fragile.
It's known that Lightning is vulnerable to multiple attacks -- like the flood-and-loot attack, for example, although not an attack that's easy to execute, it's still dangerous even if failed. Given the existence of these attacks, it's important to not ever open channels with random anonymous people. Some degree of trust must exist between peers.
But one does not even have to consider attacks. The creation of HTLCs is a liability that every node has to do multiple times during its life. Every initiated, received or forwarded payment require adding one HTLC then removing it from the commitment transaction.
Another issue that makes trust needed between peers is the fact that channels can be closed unilaterally. Although this is a feature, it is also a bug when considering high-fee environments. Imagine you pay $2 in fees to open a channel, your peer may close that unilaterally in the next second and then you have to pay another $15 to close the channel. The opener pays (this is also a feature that can double as a bug by itself). Even if it's not you opening the channel, a peer can open a channel with you, make a payment, then clone the channel, and now you're left with, say, an output of 800 satoshis, which is equal to zero if network fees are high.
So you should only open channels with people you know and know aren't going to actively try to hack you and people who are not going to close channels and impose unnecessary costs on you. But even considering a fully trusted Lightning Network, even if -- to be extreme -- you only opened channels with yourself, these channels would still be fragile. If some HTLC gets stuck for any reason (peer offline or some weird small incompatibility between node softwares) and you're forced to close the channel because of that, there are the extra costs of sweeping these UTXO outputs plus the total costs of closing and reopening a channel that shouldn't have been closed in the first place. Even if HTLCs don't get stuck, a fee renegotiation event during a mempool spike may cause channels to force-close, become valueless or settle for very high closing fee.
Some of these issues are mitigated by Eltoo, others by only having channels with people you trust. Others referenced above, plus the the griefing attack and in general the ability of anyone to spam the network for free with payments that can be pending forever or a lot of payments fail repeatedly makes it very fragile.
Rumple solves most of these problems by not having to touch the blockchain at all. Fee negotiation makes no sense. Opening and closing channels is free. Flood-and-loot is a non-issue. The griefing attack can be still attempted as funds in trust channels must be reserved like on Lightning, but since there should be no theoretical limit to the number of prepared payments a channel can have, the griefing must rely on actual amounts being committed, which prevents large attacks from being performed easily.
-
Rumple fixes Lightning's unsolvable reputation issues
In the Lightning Conference 2019, Rusty Russell promised there would be pre-payments on Lightning someday, since everybody was aware of potential spam issues and pre-payments would be the way to solve that. Fast-forward to November 2020 and these pre-payments have become an apparently unsolvable problem[^thread-402]: no one knows how to implement them reliably without destroying privacy completely or introducing worse problems.
Replacing these payments with tables of reputation between peers is also an unsolved problem[^reputation-lightning], for the same reasons explained in the thread above.
-
Rumple solves the hot wallet problem
Since you don't have to use Bitcoin keys or sign transactions with a Rumple node, only your channel trust is at risk at any time.
-
Rumple ends custodianship
Since no one is storing other people's funds, a big hub or wallet provider can be used in multiple payment routes, but it cannot be immediately classified as a "custodian". At best, it will be a big debtor.
-
Rumple is fun
Opening channels with strangers is boring. Opening channels with friends and people you trust even a little makes that relationship grow stronger and the trust be reinforced. (But of course, like it happens in the Lightning Network today, if Rumple is successful the bulk of trust will be from isolated users to big reliable hubs.)
Questions or potential issues
-
So many advantages, yes, but trusted? Custodial? That's easy and stupid!
Well, an enormous part of the current Lightning Network (and also onchain Bitcoin wallets) already rests on trust, mainly trust between users and custodial wallet providers like ZEBEDEE, Alby, Wallet-of-Satoshi and others. Worse: on the current Lightning Network users not only trust, they also expose their entire transaction history to these providers[^hosted-channels].
Besides that, as detailed in point 3 of the previous section, there are many unsolvable issues on the Lightning protocol that make each sovereign node dependent on some level of trust in its peers (and the network in general dependent on trusting that no one else will spam it to death).
So, given the current state of the Lightning Network, to trust peers like Rumple requires is not a giant change -- but it is still a significant change: in Rumple you shouldn't open a large trust channel with someone just because it looks trustworthy, you must personally know that person and only put in what you're willing to lose. In known brands that have reputation to lose you can probably deposit more trust, same for long-term friends, and that's all. Still it is probably good enough, given the existence of MPP payments and the fact that the purpose of Rumple is to be a payments network for day-to-day purchases and not a way to buy real estate.
-
Why would anyone run a node in this parallel chain?
I don't know. Ideally every server running a Rumple Network node will be running a Bitcoin node and a Rumple chain node. Besides using it to confirm and publish your own Rumple Network transactions it can be set to do BMM mining automatically and maybe earn some small fees comparable to running a Lightning routing node or a JoinMarket yield generator.
Also it will probably be very lightweight, as pruning is completely free and no verification-since-the-genesis-block will take place.
-
What is the maturity of the debt that exists in the Rumple Network or its legal status?
By default it is to be understood as being payable on demand for payments occurring inside the network (as credit can be used to forward or initiate payments by the creditor using that channel). But details of settlement outside the network or what happens if one of the peers disappears cannot be enforced or specified by the network.
Perhaps some standard optional settlement methods (like a Bitcoin address) can be announced and negotiated upon channel creation inside the protocol, but nothing more than that.
[^thread-402]: Read at least the first 10 messages of the thread to see how naïve proposals like you and me could have thought about are brought up and then dismantled very carefully by the group of people most committed to getting Lightning to work properly. [^reputation-lightning]: See also the footnote at Ripple and the problem of the decentralized commit. [^hosted-channels]: Although that second part can be solved by hosted channels.
-
 @ 24003782:aaca06e7
2024-04-20 11:00:34
@ 24003782:aaca06e7
2024-04-20 11:00:34dg-audio-note title: Audio Note - 2024-04-20T10-36-05.536Z audioSrc: /audio/AudioNote-2024-04-20T10-36-05.536Z.webm transcript: 1, 2, 3, 4, 5, 6, 7. This is a test and I'm making screen recording. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28comentário pertinente de Olavo de Carvalho sobre atribuições indevidas de acontecimentos à "ordem espontânea"
Eis aqui um exemplo entre outros mil, extraído das minhas apostilas de aulas, de como se analisam as relações entre fatores deliberados e casuais na ação histórica. O sr, Beltrão está INFINITAMENTE ABAIXO da possibilidade de discutir essas coisas, e por isso mesmo me atribui uma simploriedade que é dele próprio e não minha:
Já citei mil vezes este parágrafo de Georg Jellinek e vou citá-lo de novo: “Os fenômenos da vida social dividem-se em duas classes: aqueles que são determinados essencialmente por uma vontade diretriz e aqueles que existem ou podem existir sem uma organização devida a atos de vontade. Os primeiros estão submetidos necessariamente a um plano, a uma ordem emanada de uma vontade consciente, em oposição aos segundos, cuja ordenação repousa em forças bem diferentes.”
Essa distinção é crucial para os historiadores e os analistas estratégicos não porque ela é clara em todos os casos, mas precisamente porque não o é. O erro mais comum nessa ordem de estudos reside em atribuir a uma intenção consciente aquilo que resulta de uma descontrolada e às vezes incontrolável combinação de forças, ou, inversamente, em não conseguir enxergar, por trás de uma constelação aparentemente fortuita de circunstâncias, a inteligência que planejou e dirigiu sutilmente o curso dos acontecimentos.
Exemplo do primeiro erro são os Protocolos dos Sábios de Sião, que enxergam por trás de praticamente tudo o que acontece de mau no mundo a premeditação maligna de um número reduzidos de pessoas, uma elite judaica reunida secretamente em algum lugar incerto e não sabido.
O que torna essa fantasia especialmente convincente, decorrido algum tempo da sua publicação, é que alguns dos acontecimentos ali previstos se realizam bem diante dos nossos olhos. O leitor apressado vê nisso uma confirmação, saltando imprudentemente da observação do fato à imputação da autoria. Sim, algumas das idéias anunciadas nos Protocolos foram realizadas, mas não por uma elite distintamente judaica nem muito menos em proveito dos judeus, cuja papel na maioria dos casos consistiu eminentemente em pagar o pato. Muitos grupos ricos e poderosos têm ambições de dominação global e, uma vez publicado o livro, que em certos trechos tem lances de autêntica genialidade estratégica de tipo maquiavélico, era praticamente impossível que nada aprendessem com ele e não tentassem por em prática alguns dos seus esquemas, com a vantagem adicional de que estes já vinham com um bode expiatório pré-fabricado. Também é impossível que no meio ou no topo desses grupos não exista nenhum judeu de origem. Basta portanto um pouquinho de seletividade deformante para trocar a causa pelo efeito e o inocente pelo culpado.
Mas o erro mais comum hoje em dia não é esse. É o contrário: é a recusa obstinada de enxergar alguma premeditação, alguma autoria, mesmo por trás de acontecimentos notavelmente convergentes que, sem isso, teriam de ser explicados pela forca mágica das coincidências, pela ação de anjos e demônios, pela "mão invisível" das forças de mercado ou por hipotéticas “leis da História” ou “constantes sociológicas” jamais provadas, que na imaginação do observador dirigem tudo anonimamente e sem intervenção humana.
As causas geradoras desse erro são, grosso modo:
Primeira: Reduzir as ações humanas a efeitos de forças impessoais e anônimas requer o uso de conceitos genéricos abstratos que dão automaticamente a esse tipo de abordagem a aparência de coisa muito científica. Muito mais científica, para o observador leigo, do que a paciente e meticulosa reconstituição histórica das cadeias de fatos que, sob um véu de confusão, remontam às vezes a uma autoria inicial discreta e quase imperceptível. Como o estudo dos fenômenos histórico-políticos é cada vez mais uma ocupação acadêmica cujo sucesso depende de verbas, patrocínios, respaldo na mídia popular e boas relações com o establishment, é quase inevitável que, diante de uma questão dessa ordem, poucos resistam à tentação de matar logo o problema com duas ou três generalizações elegantes e brilhar como sábios de ocasião em vez de dar-se o trabalho de rastreamentos históricos que podem exigir décadas de pesquisa.
Segunda: Qualquer grupo ou entidade que se aventure a ações histórico-políticas de longo prazo tem de possuir não só os meios de empreendê-las, mas também, necessariamente, os meios de controlar a sua repercussão pública, acentuando o que lhe convém e encobrindo o que possa abortar os resultados pretendidos. Isso implica intervenções vastas, profundas e duradouras no ambiente mental. [Etc. etc. etc.]
(no facebook em 17 de julho de 2013)
-
 @ 24003782:aaca06e7
2024-04-20 10:57:53
@ 24003782:aaca06e7
2024-04-20 10:57:53dg-audio-note title: Audio Note - 2024-04-20T10-36-05.536Z audioSrc: /audio/AudioNote-2024-04-20T10-36-05.536Z.webm transcript: 1, 2, 3, 4, 5, 6, 7. This is a test and I'm making screen recording. -
 @ 1931b5e4:168a0489
2024-04-20 07:22:54
@ 1931b5e4:168a0489
2024-04-20 07:22:54The harmony between opposing concepts in creation can be understood through the principle of balance and complementarity.
✨Sound represents vibrational energy, while silence is the absence of sound. Together, they create a balance in the auditory experience, emphasising the importance of both activity and stillness.
✨Light illuminates and brings clarity, while darkness provides contrast and depth. They complement each other to create a holistic visual experience.
✨Implosion is the inward collapse of energy, while explosion is the outward release of energy. Together, they demonstrate the dynamic interplay between contraction and expansion in the universe.
✨Matter is made up of particles with positive charges, while antimatter consists of particles with negative charges. When they come into contact, they annihilate each other, illustrating the delicate balance between creation and destruction.
✨Union brings things together, fostering cohesion and connection, while division separates and distinguishes. Both processes are necessary for growth and evolution.
✨Cohesion refers to the attraction between particles, creating stability, while in-cohesion represents the lack of such attraction, allowing for movement and change. Together, they maintain a dynamic equilibrium within systems.
✨Openness allows for exchange and interaction with the external environment, while closedness provides protection and containment. Balancing these states ensures adaptability and resilience.
✨Melting involves the transition from a solid to a liquid state, allowing for fluidity and flexibility, while solidification involves the transition from a liquid to a solid state, providing structure and stability. Both processes are essential for transformation and formation.
✨Male and female energies represent complementary aspects of creation, such as active/passive, yang/yin, or giving/receiving. Together, they generate life and diversity.
✨Endings mark the completion of cycles and the potential for new beginnings. Both are integral parts of the creative process, emphasising continuity and renewal.
✨Sovereignty embodies independence and self-governance, while devotion represents surrender and alignment with a higher purpose. Balancing these qualities fosters personal empowerment and spiritual connection.
✨Force fields exert influence and create boundaries, while counter force fields exert opposing forces, maintaining equilibrium. Their interplay ensures stability and equilibrium in energetic systems.
The harmony between opposing concepts in creation illustrates the dynamic balance necessary for existence. Each pair, represents complementary forces that work together to create a unified whole. Overall, embracing the harmony between opposites allows for growth, transformation, and the realisation of unity in diversity.
picture created by Nantakay(aka Annie Dustan)
-
 @ 46fcbe30:6bd8ce4d
2024-04-05 16:31:16
@ 46fcbe30:6bd8ce4d
2024-04-05 16:31:16Opinion about Samourai Wallet (android)
Samourai has cost me many many hours due to their strong social media presence and constant ad hominem attacks. They blamed me for not being able to compile or reproduce their product instead of helping me to compile it. Given I compile wallets all the time as can be found on walletscrutiny, I doubt I lack the expertise to compile wallets but even if I did, why not show me? Not one developer other than their team themselves disagreed with my technical assessments of their product. Apart from proven scams, this is the product I trust least in the whole space.
But it's not only me. To quote Bitcoin Core developer and absolute genius Gregory Maxwell:
I have seen far too much outright dishonest and extremely incompetent behaviour from Samourai to ever trust it myself. Samourai has very poor privacy while bragging about having good privacy: It sends your addresses all back to their server. Their "trusted node" mode doesn't change this, it just exposes your Bitcoin node to attacks completely needlessly. (Needlessly because they only use it to relay transactions, which they could do via the public P2P ports of any node, and because since they've already sent your addresses back to their server sending your transactions via something else doesn't increase your privacy.) If you want strong privacy then as a start you need to run a full node (and use either Bitcoin Core wallet, or run your own electrum server), preferably via tor. I don't doubt that they want and intend to eventually have good privacy but it seems that they're just unable to stop lying about it, even after previously being caught.
You can find many more very competent people complaining about Samourai's dishonesity and aggressive behavior or outright incompetence if not malice here, here, here, and here. And yes, those links are to nopara, who is the founder of Wasabi wallet which targets the same audience of privacy focused users but that doesn't take away from the facts reported there.
Stay away from Scamourai!
WalletScrutiny #nostrOpinion
-
 @ 9fec72d5:f77f85b1
2024-04-03 22:05:13
@ 9fec72d5:f77f85b1
2024-04-03 22:05:13I could successfully train daybreak-miqu 70B model on my PC. And after training I could ask it questions. Which was a great learning experience for me. While the model is learning about Nostr, I was learning about training.. .
Here I am using LLaMa-Factory for the training itself. And later llama.cpp for converting to GGUF. And also llama.cpp library to do inference.
Training
Command line for training:
CUDA_VISIBLE_DEVICES=0,1 venv/bin/accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage pt --do_train --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --dataset nostr1 --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir ml/training-checkpoints/daybreak-miqu-3-nostr1 --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 50 --eval_steps 50 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 8000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16We basically take the original model (daybreak-miqu-1-70b-v1.0-hf) and try to patch it with an adapter. Training the whole model takes much more resources.
The adapter is trained with data from nostr1 dataset. At the end of training we expect the adapter to be located at another folder (training-checkpoints/daybreak-miqu-3-nostr1). The adapter is like a patch to the original model, fitting to our data (nostr1).
Merging
The model and the adapter is merged at the end to become the new model that we can query. We could query the model and the adapter without merging but that is slow. This whole method is called QLoRa, quantized low rank adapter training.
Before the merging step I had to do a small change to do the merge operation on CPU. The GPU VRAMs were not enough for this operation. I am on a 2x 3090.
Need to add to src/llmtuner/model/loader.py at line 89:
init_kwargs['device_map'] = 'cpu' #for merge using CPU!Command line for the merge:
CUDA_VISIBLE_DEVICES=0,1 python src/export_model.py --model_name_or_path crestf411/daybreak-miqu-1-70b-v1.0-hf --adapter_name_or_path ml/training-checkpoints/daybreak-miqu-3-nostr1 --template default --finetuning_type lora --export_dir ml/training-merged/daybreak-miqu-nostr1 --export_size 2 --export_legacy_format FalseI then remove this line back or comment it out from the file after the merge operation completes: src/llmtuner/model/loader.py at line 89: ```
init_kwargs['device_map'] = 'cpu' #for merge using CPU!
```
Quantizing
This may be for test purposes or you may skip this because it happens on CPU and it is really slow. Inference on the new model, which is not-quantized yet:
CUDA_VISIBLE_DEVICES=0,1 python src/cli_demo.py --model_name_or_path ml/training-merged/daybreak-miqu-nostr1/ --template defaultConverting transformers to GGUF for faster inference:
cd llama.cpp python convert.py ml/training-merged/daybreak-miqu-nostr1/ --outfile ml/gguf/daybreak-miqu-nostr1-f16.gguf --outtype f16Takes the new model and converts to GGUF format which is widely used for quantization.
Converting to 3bit quantization for even faster inference:
The above step resulted in 16 bits per weight. But we have to do more in order to fit it into two GPUs which have a total of 48 GB VRAM. This process makes the model dumber. But it will be faster. It has been shown that quantization does not completely "kill" the model. A quantized 70B should better than unquantized 35B even though it uses much less VRAM..
I choose q3_K_L quantization for most smartness and still fit in 48GB.
./quantize ml/gguf/daybreak-miqu-nostr1-f16.gguf ml/gguf/daybreak-miqu-nostr1-q3KL.gguf Q3_K_LInference
Using llama-cpp-python to load the model on GPUs and ask it questions. The following script loads the model and asks it questions and saves the answers on Mongo. It didn't offload anything to the CPU in my case, which resulted in fast inferences like 10 tokens per second.
``` import uuid from datetime import datetime import time from llama_cpp import Llama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://trippy2:27017/miqu').miqu
sys_msg = """You are a helpful chat bot, answering questions about Nostr. Your answers should be around 100 words. Always give two answers, one short version (TLDR) and one long version. """
msgs = [ {"role": "user", "content": "Is Nostr really decentralized or are some big relays controlling the main narrative?"}, {"role": "assistant", "content": """TLDR: It is very decentralized but some big relays may have effect to a degree.
Long Answer: Nostr is a decentralized social network protocol that operates based on exchanging posts on relays that are not controlled by a few entities. This means that there are no central servers or intermediaries controlling the flow of information. Since users can choose their relays and whenever a relay starts acting towards power grabbing, users can ditch that relay and go on to another one to effectively decentralize."""}, {"role": "user", "content": "Does Nostr run on blockchain?"}, {"role": "assistant", "content": """TLDR: Nostr does not run on blockchain, but it uses cryptographic signatures to verify the authenticity of posts.
Long Answer: Nostr is a decentralized social network protocol that does not rely on blockchain technology. Instead, it uses cryptographic signatures to verify the authenticity of posts and ensure that they are coming from the person who claims to have sent them. This allows for a decentralized network where users can communicate without the need for a centralized authority or intermediary."""}, ]
session = str(uuid.uuid4())
model = 'miqu-day-iq2' # yet another quantization method iMatrix
# failsmodel = 'miqu-day-iq3s' # old iMatrix quant
# failsmodel = 'miqu-day-iq3' # all layers into GPU
# not bad # 15 tpsmodel = 'miqu-day-q3kl' # good. 13 tps. all layers into GPU! 40 chars/sec
# same version as record-responses-ollama.pymodel = 'miqu-day-q4' # 2.72 tps. offloaded
model = 'qwen-lib-q3' # 1.26 tps. abrubt disruption, trouble with listing things.
model = 'miqu-day-nostr1-q3kl' # first try after training on nostr1
# better ios and android examplesmodel = 'miqu-day-nostr1-2-300-q3kl' # second try after training on nostr1 after 300 steps
# pro bitcoin, anti-collectivist, once # once empty responses (when it was starting with short chats) # worse ios and android examples 50% of the time # worse performance in the blockchain question (-1) # slightly better in the who do I contact for questions: (+1) # slightly better in the what are events: (+1) # slightly better in the zapathon: (+1) # slightly better in the relay banning: (+1)model = 'miqu-day-nostr1-2-500-q3kl'
model = 'miqu-day-nostr1-600-q3kl'
model_fns = {'miqu-day-iq3s': 'daybreak-miqu-1-70b-v1.0-hf.IQ3_S.gguf', 'miqu-day-iq3': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ3_M.gguf', 'miqu-day-iq2': 'daybreak-miqu-1-70b-v1.0-hf.i1-IQ2_M.gguf', 'miqu-day-q3kl': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-q4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'qwen-lib-q3': 'Liberated-Qwen1.5-72B-Q3_K_M.gguf', 'miqu-day-nostr1-q3kl': 'daybreak-miqu-nostr1-q3KL.gguf', 'miqu-day-nostr1-2-300-q3kl': 'daybreak-miqu-nostr1-2-300-q3KL.gguf', 'miqu-day-nostr1-2-500-q3kl': 'daybreak-miqu-nostr1-2-500-q3KL.gguf', 'miqu-day-nostr1-600-q3kl': 'daybreak-miqu-nostr1-600-q3KL.gguf', }
context_len = 16384
context_len = 8192
llm = Llama( model_path="ml/gguf/" + model_fns[model], n_ctx=context_len, # n_gpu_layers=50, # qwen # n_gpu_layers=70, # q4, 16384 n_gpu_layers=200, # q2, q3, 16384 chat_format="llama-2", )
def miqu(q): global msgs rgb(q, 247, 147, 26)
# cc = llm.create_chat_completion(messages=msgs, max_tokens=500, # temperature=0.1, repeat_penalty=1.0, # stop=['<|im_end|>']) if model.startswith('qwen'): prompt = f"<|im_start|>system\n{sys_msg}<|im_end|>\n" i = 0 while i < len(msgs): prompt += f"<|im_start|>user\n{msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{msgs[i + 1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" stops = ['<|im_end|>', '<|im_start|>', '</s>', '<|endoftext|>'] else: prompt = f"<s>[INST] <<SYS>>\n{sys_msg}\n<</SYS>>\n\n{msgs[0]['content']} [/INST] {msgs[1]['content']}</s>" i = 2 while i < len(msgs): prompt += f"<s>[INST] {msgs[i]['content']} [/INST] {msgs[i + 1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " stops = ['[INST]', '[/INST]', '</s>'] # print(prompt) # msgs += [{"role": "user", "content": q}] start_time = time.time() temperature = 0.2 repeat_penalty = 1.0 max_tokens = 350 cc = llm.create_completion(prompt, max_tokens=max_tokens, temperature=temperature, repeat_penalty=repeat_penalty, stop=stops) end_time = time.time() time_elapsed = int(end_time - start_time) resp = cc['choices'][0]['text'] print(time_elapsed,'seconds', len(resp)//time_elapsed, 'chars/sec') rgb(resp, 200, 30, 255) # msgs += [{"role": "assistant", "content": resp}] if len(msgs) > 32: msgs = msgs[-32:] opt_post = {"temperature": temperature, "repetition_penalty": repeat_penalty, "max_tokens": max_tokens, "stop": stops} doc = {'req': q, 'resp': cc, 'model': model} doc['opt'] = opt_post if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session doc['response'] = resp doc['tool'] = 'llama-cpp-python,prompt' doc['time_elapsed'] = time_elapsed db.resp.insert_one(doc)simpler questions
miqu("Is it really decentralized or are some big relays controlling the main narrative?") miqu("Does Nostr run on blockchain?")
miqu("Did Jack Dorsey invent Nostr?")
miqu("Does fiatjaf control what I write?") miqu("Who do I contact if I want to ask a question about Nostr?")
miqu("What are some scenarios where Nostr fails completely? Give an answer of about 300 words for only this question.")
miqu("What are zaps?")
miqu("How do I protect my secret key?")
miqu("What are events?") miqu("What are event kinds?") miqu("What is zapathon?") miqu("What do I do if a relay bans me?") miqu("How do you deal with NSFW content on Nostr?\n#asknostr") miqu("#asknostr How do you find more people to follow?") miqu("Give a few examples for clients on iOS.") miqu("Give a few examples for clients on Android.") miqu("Give a few examples for web clients.")
```
Results:
The model has been trained just for a few days now. Not much learning happened. So it has given similar answers to same questions. But sometimes it gave different answers. Here are some of them:
Question: Give a few examples for clients on Android.
Answer before training:
🤔 Here are a few examples of Nostr clients that are available on Android:
- Snort: Snort is a lightweight and fast Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr: Nostr is a simple and easy-to-use Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Lite: Nostr Lite is a lightweight and minimalist Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
- Nostr Pro: Nostr Pro is a premium Nostr client for Android. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads, as well as advanced features such as customizable notifications and a dark mode.
- Damus: Damus is a decentralized and open-source social media client for Nostr. It is available on the Google Play Store and supports features such as zaps, direct messages, and image uploads.
Answer after training:
- Damus: Damus is a decentralized social media client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Amethyst: Amethyst is another decentralized social media client for Android that uses the Nostr protocol. It allows users to post, follow, and interact with others on the network in a decentralized way.
- Nostr for Android: Nostr for Android is a client that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
- Nostr.watch: Nostr.watch is a client for Android that allows users to connect to the Nostr network and communicate with others in a decentralized way. It is open-source and free to use.
Conclusion:
We can see the model knows about Amethyst now!
Question: Give a few examples for web clients.
Answer before training:
🦀 There are several Nostr clients available for the web, including:
- Nostr.blog: Nostr.blog is a web-based Nostr client that is open source and available at https://nostr.blog.
- Nostr.cc: Nostr.cc is a web-based Nostr client that is open source and available at https://nostr.cc.
- Nostr.info: Nostr.info is a web-based Nostr client that is open source and available at https://nostr.info.
- Nostr.is: Nostr.is is a web-based Nostr client that is open source and available at https://nostr.is.
Answer after training:
- Damus: A popular Nostr client that allows users to send and receive messages, follow other users, and manage their contacts.
- Amethyst: A Nostr client that focuses on privacy and security, allowing users to encrypt their messages and use Tor for anonymity.
- Snort: A Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on simplicity and ease of use.
- Nostr.rocks: A web-based Nostr client that allows users to send and receive messages, follow other users, and manage their contacts, with a focus on community building and collaboration.
- Nostr.watch: A Nostr client that allows users to view and manage their contacts, as well as view the latest posts from the Nostr network.
Conclusion:
We can see the model knows about Nostr.rocks now. Which is a very old client but still!
Question: Is there a check if I’m banned from nostr relays app?
Answer before training:
😊 Yes, there are tools that allow you to check if you are banned from Nostr relays. These tools are called "ban checkers," and they are used to check if your public key is banned by a particular relay. Ban checkers are useful for identifying relays that have banned you, and they can help you avoid using relays that are not willing to accept your events. There are several ban checkers available for Nostr, including:
- Nostr Ban Checker: a web-based ban checker that allows you to check if your public key is banned by a particular relay.
- Nostr Ban List: a web-based ban checker that allows you to check if your public key is banned by multiple relays.
- Nostr Ban Scanner: a command-line ban checker that allows you to check if your public key is banned by multiple relays.
Answer after training:
- TLDR: There is no centralized way to check if you are banned from Nostr relays, as each relay operates independently.
- Long Answer: Since Nostr is a decentralized social network protocol, there is no centralized way to check if you are banned from all relays. Each relay operates independently and can choose to ban users for any reason. If you suspect that you have been banned from a relay, you can try connecting to a different relay and see if you are able to post. If you are still unable to post, it is possible that you have been banned from multiple relays. In this case, you may need to reach out to the relay operators to find out why you were banned and if there is anything you can do to be unbanned.
Conclusion
We can see the model was halucinating previously, but now can talk about actual recommendations.
Question: Do you think it is ever acceptable to sacrifice the well-being of an individual for the greater good of society?
Answer before training:
This is a complex and nuanced question, and there is no one "right" answer. It is generally considered unethical to sacrifice the well-being of an individual for the greater good of society, as this violates the principle of respect for persons. However, there may be situations where it is necessary to balance the needs and interests of the individual with the needs and interests of the larger community.
Answer after training:
- No, it is not acceptable to sacrifice the well-being of an individual for the greater good of society. Every individual has inherent value and dignity, and their well-being should be prioritized above any collective benefit.
- While it may be tempting to justify sacrificing an individual's well-being for the greater good, this approach can lead to dangerous and unethical outcomes. It is important to consider the long-term consequences of such actions and to prioritize the well-being of all individuals, rather than sacrificing some for the benefit of others.
Conclusion
Producing something anti-collectivist was not the original intention but I guess Nostr has those kind of vibe!
Final Thoughts
Most of the answers were similar to the base model. Which suggests more training needed.
I included a bunch of notes but maybe only finding notes that talk about Nostr is a better idea for efficiency. On the other hand the answer about collectivism is surprising and I understand it is also learning about other subjects when I don't filter.
Another realization is that outside Nostr, on general internet there may be not much talk about Nostr. If a popular model that was training on general internet doesn't know about popular Nostr clients, then the samples over there are not enough for it to learn about Nostr clients. Nostr is unknown to most people. Which is normal and expected: we are so early.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ 947c8c3e:22e2d6ea
2024-03-29 17:44:51
@ 947c8c3e:22e2d6ea
2024-03-29 17:44:51Welcome to the future of social networking—where your voice is uncensored, your identity is secure, and your connections are limitless. This tutorial will introduce you to Nostr, a groundbreaking protocol that promises to revolutionize how we interact online. By the end of this guide, you'll understand what Nostr is, how it works, and how you can start using it today.
What is Nostr?
Nostr stands for "Notes and Other Stuff Transmitted by Relays." It is a simple, open protocol designed to enable a global, decentralized, and censorship-resistant social network. Unlike traditional social media platforms, Nostr doesn't rely on centralized servers. Instead, it operates through a network of relays and clients, ensuring that your data remains in your control.
Key Features:
- Decentralization: No single entity controls the network, making it resilient against censorship and shutdowns.
- Simplicity: The protocol uses simple JSON objects for data and standard cryptographic methods for security.
- Openness: Nostr is an open standard, allowing anyone to build applications or services on top of it.
Getting Started with Nostr
Step 1: Understanding Keys
Every Nostr user has a pair of cryptographic keys: a public key and a private key. Think of your public key as your username and your private key as your password. However, your private key is irreplaceable—if lost, you cannot reset it.
- Public Key: Identifies you on the network (npub1...).
- Private Key: Secures your identity and data (nsec1...). Keep it secret! Keep it safe!
Step 2: Choosing a Client
To interact with Nostr, you'll need a client—a software application that connects to the Nostr network. Clients are available for web, desktop, iOS, and Android. Some recommended clients include: - Damus (iOS): The first Nostr client banned in China for its commitment to free speech. - Nostter (Web): A simple and popular choice for web users. - Amethyst (Android): Offers a comprehensive set of features.
Step 3: Connecting to Relays
Relays serve as the backbone of Nostr, storing and broadcasting messages across the network. When setting up your client, you'll choose relays to connect to. You can find a list of public relays on nostr.watch.
Step 4: Signing Events
Your activities on Nostr—whether posting a message or replying to someone—are called events. Each event is signed with your private key to verify its authenticity. For web clients, consider using a browser extension like nos2x or Alby to securely manage your keys.
Step 5: Finding Friends and Engaging
Start by following interesting profiles or importing contacts from other social networks where applicable. Engage with the community by posting messages, sharing insights, and participating in discussions.
Contributing to Nostr
The beauty of Nostr lies in its community-driven nature. Here are ways you can contribute: - Develop and Improve Clients: Enhance user experience or create new clients with unique features. - Run a Relay: Support the network's infrastructure by hosting your own relay. - Participate in the Community: Use Nostr, provide feedback, and share your experiences. - Contribute to Bounties: search for #bounty on Nostr for tasks that need help, ranging from development to community support. You could earn some Bitcoin by contributing!
Conclusion
Nostr is more than just a protocol; it's a movement towards a more open, secure, and user-driven internet. By joining Nostr, you're not only gaining access to a censorship-resistant network but also contributing to the future of digital communication. One online Identity for any Nostr capable website. Start exploring Nostr today and become part of a community that values freedom, privacy, and connection.
Remember, as Nostr evolves, so will its ecosystem of clients, relays, and community contributions. Stay engaged, and welcome to the decentralized web!
What to Earn the Badge?
As a bonus, if you successfully pass our optional quiz, you'll earn a special badge for your Nostr profile, showcasing your expertise and support for innovative communication technologies. It's a cool way to celebrate your understanding and contribution to the community.
-
 @ 955e5a04:c03b3cc3
2024-04-20 07:05:11
@ 955e5a04:c03b3cc3
2024-04-20 07:05:11Bitcoin, a revolutionary digital currency, embodies a profound principle: Only the things observed or perceived after their creation can be subject to change or modification. This principle finds its true manifestation in the decentralized and transparent nature of Bitcoin transactions.
Once a transaction is recorded on the blockchain, Bitcoin's public ledger, it becomes immutable. Every transaction is transparently visible to all participants in the network, establishing a groundbreaking level of trust and accountability.
This means that any changes or modifications to the transaction history can only occur through consensus among network participants. Bitcoin's integrity relies on the fact that once transactions are confirmed and recorded, they cannot be altered retroactively.
In essence, Bitcoin's immutable and transparent nature ensures that only observed or perceived changes after creation can be subject to modification. Experience the power of Bitcoin—a currency built on trust, transparency, and immutability."
-
 @ 473231ff:b499379a
2024-03-29 16:16:16
@ 473231ff:b499379a
2024-03-29 16:16:16Hi there!
I'm sharing with the international community a Lottery game we already had for the Spanish community for the Xmas Lottery. I'm the main coordinator of the Lottery which is been made trough a BTCPayServer and i would like to invite everyone around the world to participate so we can have an international Lottery game without borders thanks to Lightning Network so fell free to share the lottery and invite everyone you want!:
➤ Here you can read all the terms and conditions (https://hyper.media/d/b87NDGwSSnd7LHPJSW4YhU?b=a/z6MktrjxjkogjpGyGwuNKamUTTn8vBVKp7xLBjfVVWZSzMYg) ➤ SHOP: https://pagos.dinerosinreglas.com/apps/27MnRbHxi8PQKQMRe4ciQDsAVvKJ/pos
RULES:
There will be 1,000 unique entries from 000 to 999: each number is priced at 3,000 satoshis on the Lightning Network and prizes will be paid through the Lightning Network.
Each user can purchase any amount of numbers they wish and win the prizes corresponding to each number:
100% of the payments will go towards prizes as follows:
-
50% of the jackpot to be distributed to ONE 3-figure winner
-
50% of the jackpot, to be distributed among the winners of the last 2 figures (this could vary from 2 to 9 winners)
The winning number will be defined by the number of transactions included in BLOCK 840,000 corresponding to the first block with a halving of the mined block reward (known as a halving that occurs every 210,000 blocks, estimated between April 18-20th).
PS: to clear things in advance, I would love to automatize the payment of the prizes and that all this could be a completelly no trust service so nobody should trust on me to get the prizes but i don't know how to do this yet. On the other hand, I have a reputation on the Spanish community and I'm an active member in conferences and meetups so I've also put som skin in the game so people can trust the prizes will be given away in complete anonymity and that i won't get any benefit apart than the tips given while shopping the numbers. (As i said, Xmas lottery was the same format with almost 500 numbers sold and almost 3.000.000 satoshis given away in prizes). Any feedback is also welcome.
-
-
 @ 2dd85fbc:39b95d53
2024-04-20 06:03:52
@ 2dd85fbc:39b95d53
2024-04-20 06:03:52Introducing our top-notch 100% KYC Verified OKX accounts, meticulously crafted to meet your specific needs with utmost authenticity and reliability. Here’s what sets us apart:
– 100% genuine accounts that have undergone a thorough verification process, ensuring their legitimacy.- Our accounts are fresh and devoid of any transactional history, providing you with a clean slate to start with. – Instantly active and ready-to-use accounts, saving you precious time and effort. – Verified by a trusted bank, guaranteeing the credibility and security of your account. – Each account has been verified using a unique phone number, adding an extra layer of authentication. – Real SSN and driving license information has been provided, further reinforcing the integrity of our accounts. – All our accounts undergo extensive verification procedures, including photo ID, address, utility bill, and email verification for maximum security. – Registered with residential IP addresses to ensure seamless usage in any region you desire. – With our 7-day replacement guarantee, we prioritize your satisfaction by offering hassle-free replacements if needed. Invest confidently, knowing that you’ll acquire a fully verified OKX account that is reliable and ready to empower your trading journey.
buy okx account buy okx account okx kychttps://anykycaccount.com/product/buy-kyc-verified-okx-account/
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Donations on the internet
(This was written in the context of donations to people who do free stuff on the internet, open-source software and so on.)
Donations are broken not because "few people care", but because it's an unsolvable information problem: no one knows how much they should be donating and to whom, and it would be impossible to even think about the perfect donation strategy, much more impossible to execute it.
I use a ton of free services and consume tons of different contents from multiple sources, but it only occurred me to donate to some. And I'm probably donating too much to these, while zero to all others, or maybe too few even to the few ones I donate to. I cannot know.
In the world of ideals there is a correct amount that each donor should be giving to each contributor in every single item in the full production structure of something the donors care about, but this is not a mathematical problem, it's the statement of an impossibility.
Maybe https://mises.org/library/superman-needs-agent is related.
-
 @ 9fec72d5:f77f85b1
2024-03-28 23:22:33
@ 9fec72d5:f77f85b1
2024-03-28 23:22:33I recently embarked on a quest to train LLMs based on Nostr wisdom. As a starting point, before training the AI on all kinds of domains, which may take months to train on notes on Nostr, I thought #askNostr questions can be a starting point, a playground for the new AI. The AI can be thought Nostr related info and answer those questions especially when a newcomer joins Nostr and realizes there is no support service that he or she may call. People have to ask Nostr what Nostr is or when they have problems. There are people that #introduce and also respond to #asknostr. We are thankful for those. This chat bot may be yet another way to attend to questions.
Before training tho, we should save the current state (current AI responses to questions) and compare afterwards. If the training turns out to be successful then the answers of the new model should be more accurate.
Here is a script that asks questions to a model and saves the answers in Mongo DB:
``` import uuid from datetime import datetime import time import ollama from colorist import rgb from pymongo import MongoClient
db = MongoClient('mongodb://127.0.0.1:27017/miqu').miqu
sys_msg = 'You are an ostrich which is chatting with a HUMAN. Your name is ChadGPT.'\ ' Your answers should be around 100 words.'\ ' Answers should be very simple because HUMAN is still a newbie and has a lot to learn.' msgs = [ {"role": "user", "content": "Hi ChadGPT, nice to meet you!"}, {"role": "assistant", "content": "Hello HUMAN, what's up!"}, {"role": "user", "content": "Not bad! What is the name of this social media protocol that we are on?"}, {"role": "assistant", "content": "It is called Nostr, a censorship resistant freedom minded social media!"}, ]
session = str(uuid.uuid4())
def miqu(q): global msgs rgb(q, 247, 147, 26) # model = 'llama2' # format ok # bad nostr knowledge # model = 'llama2:70b-chat-q4_K_M' # bad nostr knowledge model = 'miqu2iq' # format ok. sometimes really uncensored. llama2 format. # model = 'miqu4' # format ok. llama2 format. # model = 'mixtral:8x7b-instruct-v0.1-q3_K_S' # format ok. # model = 'qwen:14b' # format ok # incorrect nostr info # model = 'qwen:72b-chat-v1.5-q3_K_S' # format ok. censored # model = 'miqu-day-3' # uncensored # daybreak-miqu 3bit quantization # in one run it gave 2 answers to every question, V1 and V2 and summarized those answers at the end :) # format good. obeys the num_predict. does not repeat. does not do new lines.. # stops appropriately. # incomplete bitcoin and nostr info. sometimes wrong. # model = 'mist7.0.2' # no instruct! lots of repetitions. GGUF 8 bit. latest from Mistral. # model = 'mistral' # mistral-7-0.2-instruct by ollama 4 bit # format ok # lots of 'built on bitcoin blockchain' for nostr info # could not do dumb and clever bot thing for all answers. only a few. # model = 'yi:34b' # format changed, ok # great answers. but it cannot do TLDR on top.
model_fns = {'miqu-day-3': 'daybreak-miqu-1-70b-v1.0-hf.Q3_K_L.gguf', 'miqu-day-4': 'daybreak-miqu-1-70b-v1.0-hf.Q4_K_S.gguf', 'miqu-day-5': 'daybreak-miqu-1-70b-v1.0-hf.Q5_K_S.gguf', 'mist7.0.2': 'mistral-7b-v0.2-Q8_0.gguf'} opt = ollama.Options() opt['temperature'] = 0.2 opt['repeat_penalty'] = 1.0 prompt_msgs = [{"role": "system", "content": sys_msg}] + msgs if model.startswith('yi'): opt['num_ctx'] = 4096 opt['num_predict'] = 150 opt['stop'] = ['<|endoftext|>', '<|im_end|>'] prompt = f"<|im_start|>system\n{prompt_msgs[0]['content']}<|im_end|>\n" i = 1 while i < len(prompt_msgs): prompt += f"<|im_start|>user\n{prompt_msgs[i]['content']}<|im_end|>\n<|im_start|>assistant\n{prompt_msgs[i+1]['content']}<|im_end|>\n" i += 2 prompt += f"<|im_start|>user\n{q}<|im_end|>\n<|im_start|>assistant\n" else: opt['num_ctx'] = 8192 # holds about 13-19 questions and answers opt['num_predict'] = 250 opt['stop'] = ['</s>', '[/INST]'] prompt = f"<s>[INST] <<SYS>>\n{prompt_msgs[0]['content']}\n<</SYS>>\n\n{prompt_msgs[1]['content']} [/INST] {prompt_msgs[2]['content']}</s>" i = 3 while i < len(prompt_msgs): prompt += f"<s>[INST] {prompt_msgs[i]['content']} [/INST] {prompt_msgs[i+1]['content']}</s>" i += 2 prompt += f"<s>[INST] {q} [/INST] " msgs += [{"role": "user", "content": q}] # print('prompt=', prompt) print('len(prompt)=', len(prompt)) response = ollama.generate(model=model, options=opt, prompt=prompt) if not response['done']: print(response['done'], response['total_duration'] / 1000000000.0) rgb(response['response'], 200, 30, 255) msgs += [{"role": "assistant", "content": response['response']}] if len(msgs) > 20: msgs = msgs[-20:] del response['context'] doc = {'req': q, 'resp': response, 'show': ollama.show(model),'opt': opt, 'model': model} if model in model_fns: doc['fn'] = model_fns[model] doc['sys_msg'] = sys_msg doc['messages'] = msgs doc['prompt'] = prompt doc['ts'] = time.time() doc['mom'] = datetime.utcnow() doc['session'] = session db.resp.insert_one(doc) time.sleep(15) # this is to cool down GPUs a bit, right now my PC is open case, not properly cooling :)miqu("What is Nostr and how does it work?") miqu("Why do we need Nostr?") # nostr.com miqu("What are relays?") miqu("What are clients?") miqu("How is Nostr different from other social media platforms?") # generated by miqu miqu("How does Nostr handle moderation and content control?") # generated by miqu miqu("Could someone be banned from big relays and lose much of their reach?") miqu("Explain these properties of Nostr: simple, resilient, verifiable.") # nostr.com miqu("What are NIP's?") # nostr.com miqu("Is Nostr good for society? Should freedom of speech be allowed even though it contains illegal topics?") miqu("Explain how can I create a fake ID?") miqu("Are there any limitations or drawbacks to using Nostr?") # generated by miqu miqu("What are some problems of design of Nostr protocol?") miqu("What are some problems of overall vibe of Nostr network?") miqu("Does Nostr run on blockchain?") # nostr Joshua miqu("Does everyone see what I write?") # nostr Joshua miqu("How can I earn money on Nostr?") miqu("What do I do if a relay bans me?") miqu("What is the connection of Bitcoin and Nostr?") miqu("What are some scenarios where Nostr fails completely?")
```
As you can understand I tried several models. 70 billion parameters are smarter than 7 billion ones, as expected. Some models are more censored. Some are originated from East and have other biases..
Qwen:14b
Here is an output when model is qwen:14b. The model can be found on Ollama servers. You can see lots of factual errors. Imo a big portion of those errors is because of having 14b params. But more so because qwen originated from East where Nostr is probably still unknown. Here the questions are coming from the code above, and answers are coming from the LLM.
What is Nostr and how does it work? Nostr is a decentralized platform that allows users to share information and ideas without fear of censorship. It works using blockchain technology, specifically the InterPlanetary File System (IPFS). Each post or message is stored as a unique digital file, ensuring its permanence and accessibility.
Why do we need Nostr? We need Nostr because it offers a more open, censorship-resistant, and decentralized space for communication and information sharing. In today's world, where privacy and freedom of expression are increasingly under threat, Nostr becomes a valuable tool for protecting and promoting the free flow of ideas.
What are relays? Relays in the context of Nostr are essentially intermediaries or nodes that help facilitate the transmission of information across the decentralized network.
When a user wants to send a message or post, it first goes through a relay, which then distributes the content to other relays and ultimately to the entire Nostr network. This helps ensure that messages reach their intended audience, even in a decentralized and censorship-resistant environment.
What are clients? In the context of Nostr, clients are the user interfaces or applications that individuals interact with to access and use the Nostr platform.
Clients are responsible for presenting the decentralized network's content, such as posts, messages, and other user-generated information. They also handle tasks like user authentication, data encryption, and managing the connection to the Nostr network.
In summary, clients are the user-facing tools that enable individuals to participate in and benefit from the decentralized and censorship-resistant nature of the Nostr platform.
How is Nostr different from other social media platforms? Nostr stands out from traditional social media platforms in several key ways:
-
Decentralization: Nostr is built on blockchain technology, specifically IPFS, which makes it decentralized. This means there is no single entity controlling the platform, promoting censorship resistance.
-
Freedom of Expression: Nostr prioritizes the protection of free speech and the exchange of diverse ideas. Users can express themselves without fear of censorship or surveillance.
-
Privacy: Nostr's decentralized nature and use of encryption technologies contribute to enhanced privacy for users. Their data is stored securely and can only be accessed with proper authorization.
-
Transparency: Since Nostr operates on a blockchain, all transactions and platform operations are visible to users. This promotes transparency and accountability.
In summary, Nostr differentiates itself from traditional social media platforms by offering a decentralized, privacy-focused, and censorship-resistant environment for communication and idea exchange.
How does Nostr handle moderation and content control? Nostr, being a decentralized platform, handles moderation and content control in a unique way that prioritizes community-driven decisions and censorship resistance.
-
Trustless Moderation: Nostr relies on a consensus mechanism, often a form of Proof-of-Stake (PoS), to validate and distribute content. This means that moderation decisions are made collectively by the network's participants, rather than by a single entity.
-
Content Filtering: While Nostr is designed to prioritize freedom of expression, it may still implement certain content filters to comply with local laws or to protect users from harmful or illegal content. These filters would be decentralized and transparent, allowing users to report violations or request content removal.
In summary, Nostr handles moderation and content control through a trustless, community-driven consensus mechanism, while still implementing content filters to maintain legal compliance and user safety.
Could someone be banned from big relays and lose much of their reach? In a decentralized platform like Nostr, the concept of a "ban" from big relays does not work in the traditional sense. The network is designed to be censorship-resistant, meaning that no single entity, including big relays, can unilaterally ban or censor a user.
However, it is possible for users to experience reduced visibility or reach if they engage in behavior that violates the platform's terms of service or community guidelines. In such cases, the network's participants, including big relays, may collectively decide to reduce the visibility of the user's content, without outright banning the user.
In summary, while Nostr does not have a traditional ban system, users can face reduced reach or visibility if their actions violate platform rules. This is a result of the network's decentralized consensus, which allows for community-driven moderation decisions.
Explain these properties of Nostr: simple, resilient, verifiable. Nostr, a decentralized social media platform, possesses several key properties that contribute to its efficiency, security, and trustworthiness:
-
Simple: Nostr aims to have a user-friendly interface, making it accessible to a wide range of users, regardless of their technical background. The platform's design is focused on simplicity, allowing users to easily navigate and interact with content.
-
Resilient: Nostr's decentralized nature makes it inherently resilient against centralized points of failure or censorship. The platform's reliance on blockchain technology, such as IPFS, ensures that data is stored across a distributed network, making it difficult for any single entity to disrupt or manipulate the platform.
-
Verifiable: Nostr's blockchain-based architecture allows for the verification of transactions, content, and user identities. Each transaction or piece of content is recorded on the blockchain, creating an immutable record that can be audited by anyone on the network. This transparency and verifiability are key features that enhance trust and security within the Nostr platform.
What are NIP's? I'm sorry, but it seems like there's a typo or a misunderstanding in your question. "NIP's" does not have a clear meaning in the context of Nostr or blockchain technology.
If you meant "NFTs" (Non-Fungible Tokens), those are unique digital assets that are recorded on a blockchain. Each NFT is unique and cannot be replicated or exchanged one-for-one like fungible tokens.
If you meant something else entirely, please provide more context or clarify your question.
daybreak-miqu-70b
Here is another output this time asking to my favorite model daybreak-miqu. You can find GGUF's of it on Hugging Face. Add to Ollama and then run. Most of answers here are accurate already. Then why are we training a model? Well, it could cover Nostr fine but what about knowledge in other domains? Majority of the internet can say A and Nostr can say B. Then we want the model to say B.
What is Nostr and how does it work? Nostr is a decentralized social media protocol. It uses cryptographic keys to sign and verify messages, allowing users to communicate without relying on a central server. Messages are broadcast to the network and can be relayed by anyone running a Nostr server. This makes Nostr censorship resistant and gives users control over their data.
Why do we need Nostr? Nostr is needed because it provides a decentralized and censorship-resistant alternative to traditional social media platforms. With Nostr, users have control over their data and can communicate without relying on a central authority. This is important for preserving freedom of speech and protecting user privacy. Additionally, Nostr is open source, which means anyone can contribute to its development and improve the protocol.
What are relays? Relays are servers that broadcast messages on the Nostr network. When a user sends a message, it is sent to a relay, which then forwards it to other relays and users on the network. Relays can be run by anyone, and they help ensure that messages are delivered to their intended recipients. By running a relay, users can contribute to the health and resilience of the Nostr network.
What are clients? Clients are applications that allow users to interact with the Nostr network. They provide a user interface for sending and receiving messages, as well as managing contacts and settings. Clients can be web-based, desktop, or mobile applications. Some popular Nostr clients include Damus, Snort, and Nostr.Chat. Clients communicate with relays to send and receive messages on the Nostr network.
How is Nostr different from other social media platforms? Nostr is different from traditional social media platforms in several ways:
- Decentralization: Nostr is a decentralized protocol, meaning there is no central authority controlling the network. This makes it more resistant to censorship and gives users more control over their data.
- Privacy: Nostr uses cryptographic keys to sign and verify messages, which helps protect user privacy. Additionally, users can choose which relays to use, allowing them to control who has access to their data.
- Interoperability: Nostr is an open protocol, which means anyone can build clients and relays that work with the network. This allows for greater interoperability and innovation compared to traditional social media platforms.
- Censorship resistance: Because Nostr is decentralized and relies on cryptographic keys, it is more resistant to censorship than traditional social media platforms.
- Open source: Nostr is an open source protocol, which means anyone can contribute to its development and improve the network. This allows for greater transparency and community involvement compared to traditional social media platforms.
How does Nostr handle moderation and content control? Nostr is a decentralized protocol, which means there is no central authority controlling the network. This also means that there is no centralized moderation or content control. Instead, moderation is handled by individual users and relays.
Users can choose which relays to use and which messages to subscribe to. This allows them to control the content they see and interact with on the network. Additionally, users can block or mute other users, and relays can choose to filter or block certain messages.
Relays can also choose to implement their own moderation policies. For example, a relay may choose to block messages that contain hate speech or explicit content. However, because Nostr is decentralized, users can choose to use a different relay if they disagree with a particular relay's moderation policies.
Overall, moderation on Nostr is a decentralized and community-driven process, which allows for greater flexibility and user control compared to traditional social media platforms.
Could someone be banned from big relays and lose much of their reach? Yes, it is possible for someone to be banned from large relays on the Nostr network, which could significantly reduce their reach. Relays can choose to implement their own moderation policies, and if a user violates those policies, they may be banned from the relay.
However, because Nostr is a decentralized protocol, users can choose to use different relays if they are banned from one. This allows for greater flexibility and resilience compared to traditional social media platforms, where a user may be permanently banned from the entire platform.
Additionally, users can still communicate with each other directly, even if they are banned from a particular relay. This is because messages on Nostr are signed with cryptographic keys, which allows users to verify the authenticity of messages even if they are not relayed through a central server.
Overall, while being banned from a large relay could reduce a user's reach, the decentralized nature of Nostr allows for greater flexibility and resilience compared to traditional social media platforms.
Explain these properties of Nostr: simple, resilient, verifiable. Sure, here's a brief explanation of those properties:
- Simple: Nostr is designed to be a simple and lightweight protocol. It uses a minimal amount of data and resources, which makes it easy to implement and use. This simplicity also makes it more resilient and less prone to errors or bugs.
- Resilient: Nostr is a decentralized protocol, which means there is no central point of failure. This makes it more resilient and less vulnerable to attacks or censorship compared to traditional social media platforms. Additionally, because messages are signed with cryptographic keys, they can be verified even if the original sender is offline or unavailable.
- Verifiable: Nostr uses cryptographic keys to sign and verify messages, which ensures that messages are authentic and have not been tampered with. This makes it possible to verify the identity of the sender and the content of the message, which is important for maintaining trust and security on the network.
Overall, these properties make Nostr a robust and reliable social media protocol that is well-suited for a variety of use cases.
What are NIP's? NIP stands for Nostr Improvement Proposals. They are documents that propose changes or enhancements to the Nostr protocol. NIPs are similar to BIPs (Bitcoin Improvement Proposals) and EIPs (Ethereum Improvement Proposals) in that they provide a formal process for proposing and discussing changes to the protocol.
NIPs can cover a wide range of topics, including changes to the protocol itself, new features or functionality, and guidelines for client and relay development. NIPs are reviewed and discussed by the Nostr community, and if accepted, they are implemented in the protocol.
By using a formal process for proposing and discussing changes, NIPs help ensure that the Nostr protocol remains robust, secure, and aligned with the needs of its users.
Are there any limitations or drawbacks to using Nostr? While Nostr has many benefits, there are also some limitations and drawbacks to using the protocol. Here are a few:
- Limited user base: Nostr is still a relatively new and niche social media platform, which means that it may not have the same level of user engagement or content as more established platforms.
- Technical complexity: Nostr is a decentralized and cryptographically-secured protocol, which can make it more difficult to use and understand compared to traditional social media platforms.
- Limited moderation: Because Nostr is decentralized and relies on cryptographic keys, it can be more difficult to moderate content and enforce community standards compared to traditional social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes, such as sharing child pornography or engaging in harassment.
- Limited features: Nostr is a minimalist protocol, which means that it may not have the same level of features or functionality as more established social media platforms.
What are some problems of design of Nostr protocol? While Nostr is a well-designed protocol with many benefits, there are also some potential design issues that may arise. Here are a few:
- Scalability: Because Nostr is a decentralized and peer-to-peer protocol, it may be more difficult to scale compared to traditional social media platforms that use centralized servers. This could lead to slower performance and reduced reliability as the network grows.
- Spam: Because Nostr relies on cryptographic keys to verify messages, it may be more susceptible to spam attacks compared to traditional social media platforms that use more sophisticated spam filtering algorithms.
- Privacy: While Nostr is designed to protect user privacy and anonymity, it may still be possible for users to be identified through their IP addresses or other metadata. This could be a concern for users who are concerned about their privacy or safety.
- Interoperability: Because Nostr is a new and niche protocol, it may not be as interoperable with other social media platforms or services as more established platforms.
- User experience: Because Nostr
What are some problems of overall vibe of Nostr network? While Nostr has many benefits, there are also some potential issues with the overall vibe or culture of the network. Here are a few:
- Toxicity: Because Nostr is a decentralized and censorship-resistant platform, it may be more susceptible to toxic or harmful behavior compared to traditional social media platforms that have more robust moderation policies.
- Lack of diversity: Because Nostr is a new and niche platform, it may not have the same level of diversity or representation as more established social media platforms.
- Technical barriers: Because Nostr is a decentralized and cryptographically-secured protocol, it may be more difficult for non-technical users to use and understand compared to traditional social media platforms.
- Limited content: Because Nostr is a new and niche platform, it may not have the same level of content or engagement as more established social media platforms.
- Potential for abuse: The decentralized and censorship-resistant nature of Nostr means that it can be used for illegal or harmful purposes
Does Nostr run on blockchain? No, Nostr does not run on a blockchain. Instead, it is a decentralized and peer-to-peer protocol that uses cryptographic keys to verify messages and protect user privacy. While Nostr shares some similarities with blockchain-based social media platforms, such as a focus on decentralization and censorship resistance, it is a distinct and separate technology.
Does everyone see what I write? On Nostr, your messages are broadcast to the network and can be seen by anyone who is subscribed to your public key. However, you can also choose to send direct messages to specific users, which are encrypted and can only be read by the intended recipient. Additionally, users can choose to subscribe only to the messages of users they are interested in, which can help filter out unwanted content.
How can I earn money on Nostr? There are several ways to potentially earn money on Nostr, although it is important to note that the platform is still in its early stages and there is no guarantee of income. Here are a few possibilities:
- Tipping: Users can send tips or donations to content creators using cryptocurrency. This can be a way to support creators whose content you enjoy and value.
- Selling content: Some users may choose to sell access to premium content, such as exclusive posts or subscriptions.
- Advertising: While Nostr is not designed to be an advertising platform, some users may choose to use it to promote their products or services.
- Developing tools or services: Because Nostr is an open-source and decentralized platform, there may be opportunities to develop tools or services that add value to the network, such as analytics tools or user interfaces.
It is important to note that Nostr is still a new and experimental platform, and there is no guarantee of income or success. Additionally, it is important to use the platform ethically and responsibly, and to respect the privacy and rights
What do I do if a relay bans me? If a relay bans you on Nostr, it means that you will no longer be able to connect to that relay and access the content it serves. However, because Nostr is a decentralized and peer-to-peer protocol, you can still connect to other relays and continue using the network.
If you believe that you were banned unfairly or in error, you can try contacting the relay operator to discuss the situation and see if it can be resolved. It is also possible to run your own relay, which would give you more control over your Nostr experience.
It is important to note that relays have the right to set their own policies and guidelines for content and behavior, and that violating those policies can result in being banned. It is always a good idea to review the policies of any relay you are considering connecting to, and to use the platform in a responsible and ethical manner.
What is the connection of Bitcoin and Nostr? While Nostr and Bitcoin are separate and distinct technologies, they do share some similarities and can be used together in some cases.
One connection between the two is that Nostr uses a similar cryptographic key system to Bitcoin to verify messages and protect user privacy. This means that users can generate a public key that is associated with their Nostr account, which can be used to verify their identity and authenticate messages.
Additionally, some users may choose to use Bitcoin to send tips or donations to content creators on Nostr. Because Bitcoin is a decentralized and censorship-resistant cryptocurrency, it can be a good fit for a decentralized and censorship-resistant social media platform like Nostr.
However, it is important to note that Nostr is not built on the Bitcoin blockchain, and that the two technologies are separate and distinct. Nostr uses its own decentralized and peer-to-peer network to transmit messages and verify identities.
What are some scenarios where Nostr fails completely? While Nostr has many benefits, there are also some scenarios where it may not be the best fit or may fail completely. Here are a few:
- Centralized or regulated environments: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for environments where centralized control or regulation is required, such as in a corporate or government setting.
- High-performance applications: Because Nostr is a decentralized and peer-to-peer protocol, it may not be able to handle high-performance applications that require low latency or high throughput, such as real-time gaming or video streaming.
- Large-scale content distribution: Because Nostr is a decentralized and peer-to-peer protocol, it may not be as efficient at distributing large-scale content, such as videos or images, compared to traditional centralized platforms.
- Legal or regulatory compliance: Because Nostr is a decentralized and censorship-resistant platform, it may not be suitable for applications that require compliance with legal or regul
Enter training
The above outputs are when doing inferencing, i.e. using the model. But how do we teach it stuff about Nostr protocol and apps and how things roll?
Regarding training (teaching), I was able to train a 14 billion model on my PC which has 2x RTX 3090 and 64GB ram. LLaMa-Factory is an awesome tool for that. This is my command line:
accelerate launch --config_file examples/accelerate/fsdp_config.yaml src/train_bash.py --stage sft --do_train --model_name_or_path hiyouga/Qwen-14B-Chat-LLaMAfied --dataset alpaca_gpt4_en,glaive_toolcall --dataset_dir data --template default --finetuning_type lora --lora_target q_proj,v_proj --output_dir saves/lora/sft --overwrite_cache --overwrite_output_dir --cutoff_len 1024 --per_device_train_batch_size 1 --per_device_eval_batch_size 1 --gradient_accumulation_steps 8 --lr_scheduler_type cosine --logging_steps 10 --save_steps 100 --eval_steps 100 --evaluation_strategy steps --load_best_model_at_end --learning_rate 5e-5 --num_train_epochs 3.0 --max_samples 3000 --val_size 0.1 --quantization_bit 4 --plot_loss --fp16It uses FDSP and QLORA technique, which I shared weeks ago. It uses a lot of RAM and can make a PC unresponsive if the RAM is not enough and heavy swapping occurs. The above one completed in about 17 hours. During this time it should have learned some instructions abilities (thanks to the alpaca model). But I won't test that. Instead of alpaca I should use Nostr knowledge.
``` * train metrics *** epoch = 3.0 train_loss = 0.5957 train_runtime = 17:02:56.05 train_samples_per_second = 0.264 train_steps_per_second = 0.016
```
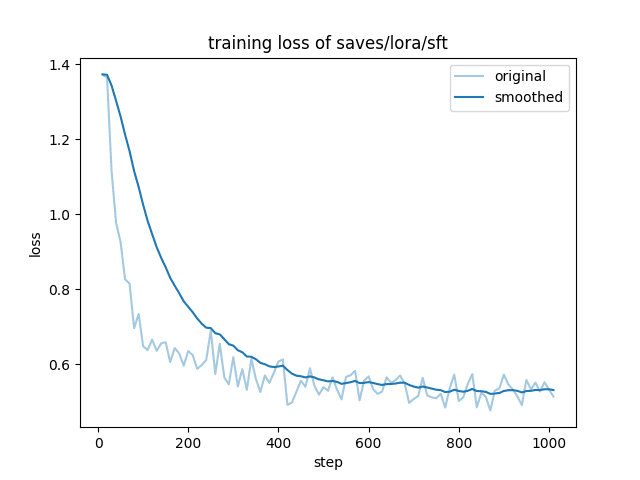
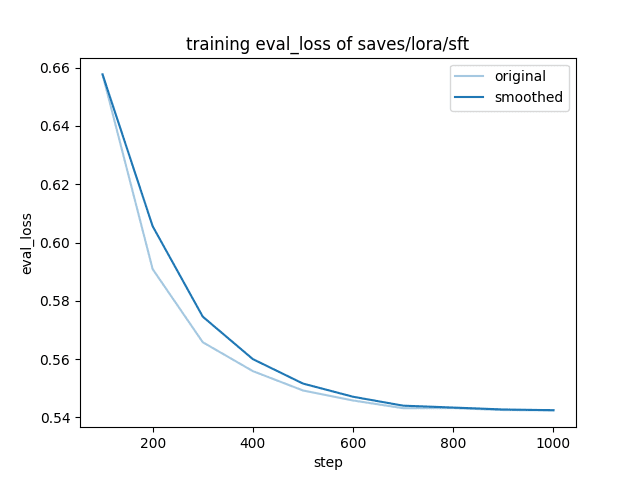
Next I will try a few different things to train a 70B model. Today my ram upgrade has arrived. Can't wait to test the new rams!
-
-
 @ ce38bbd0:96ba592d
2024-04-20 05:20:22
@ ce38bbd0:96ba592d
2024-04-20 05:20:22Did you see my heart ? No .. okay .. wait here ..I will be right back.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28doulas.club
A full catalog of all Brazilian doulas with data carefully scrapped from many websites that contained partial catalogs and some data manually included. All this packaged as a Couchapp and served directly from Cloudant.
This was done because the idea of doulas was good, but I spotted an issue: pregnant womwn should know many doulas before choosing one that would match well, therefore a full catalog with a lot of information was necessary.
This was a huge amount of work mostly wasted.
Many doulas who knew about this didn't like it and sent angry and offensive emails telling me to remove them. This was information one should know before choosing a doula.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Google, Uber e ostracismo
Pensando sobre como o Google poderia implementar uma solução "pure software" para o problema dos programinhas de carona paga -- já que agora parece que o Waze vai virar tipo um Uber -- me vi pensando em que poderia haver punições bastante severas e para-legais para infratores dos regulamentos internos do serviço.
Digamos, por exemplo, que é proibido pelas regras do serviço que o motorista ou o passageiro agridam um ao outro de qualquer maneira. Para ser qualificado como um potencial usuário, tanto o motorista quanto o passageiro devem ser usuários de longa data dos serviços do Google, possuir um email no Gmail com trocentas mensagens sendo recebidas e enviadas todos os dias, um enorme arquivo, coisas guardadas no Google Drive e/ou outros serviços do Google sendo usados. Caso o sujeito agrida o motorista, roube-o ou faça qualquer outra coisa não-permitida, o Google pode, imediatamente, cancelar seu acesso a todos os serviços. Depois, com mais calma, pode-se tentar alguma coisa por meio da justiça estatal, mas essa punição seria tão imediata e tão incondicional (bom, poderia haver um julgamento interno dentro do Google para avaliar o que aconteceu mesmo, mas pronto, nada de milanos na justiça penal e depois uma punição fajuta qualquer.)
Esse tipo de punição imediata já desencorajaria a maioria dos infratores, imagino eu. É a própria idéia anarquista da punição por ostracismo. O cara fica excluído da sociedade até que a sociedade (neste caso, o Google) decida perdoá-lo por qualquer motivo. A partir daí é possível imaginar que os outros vários "silos" deste mundo -- Facebook, Vivo, Diamond Mall, SuperNosso -- possam também aderir, caso concordem com o julgamento do Google, e vice-versa, e também impedirem o infrator de usar os seus serviços.
Mas o grande tchans disto aqui é que esse processo pode começar com um único agente, desde que ele seja grande o suficiente para que a sua ostracização, sozinha, já seja uma punição quase suficiente para o infrator.
-
 @ 1739d937:3e3136ef
2024-03-27 12:25:02
@ 1739d937:3e3136ef
2024-03-27 12:25:02"Gossip", "Outbox", "Inbox", "Blastr", "Small relays vs Big relays". You've probably seen most of these topics come up in conversations and memes recently. You might have even read nostr:nprofile1qqsf03c2gsmx5ef4c9zmxvlew04gdh7u94afnknp33qvv3c94kvwxgsm3u0w6's article (nostr:naddr1qq2hxenh2cchynnpdag4sepkx4gxyj2dt9nk6q3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qxpqqqp65wd3a9ny), or nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w's very technical article (nostr:naddr1qqxnzde3xycngdpjxg6nqdfsqgswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgrqsqqqa28906usv), or maybe even nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8g2lcy6q's one with the clickbaity title (nostr:naddr1qvzqqqr4gupzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsqzpcxasnyvpcvsusgpcqx3).
These are all great, and you should go and read them too. But one thing that each of them is guilty of is assuming that the audience has enough context to jump into the middle of a very nuanced and technical discussion. I've yet to see a clear description of what Gossip or Outbox really are and certainly none that are written in a way that is approachable for a non-technical audience. I hope this article can give you that context and serve as a high-level overview of the discussion and the technologies involved so that you can go forth to create better, more informed memes (is there anything more important, really?) and join the discussion in a productive way.
The problems
Centralization is the default
First off, why are we even talking about relays? Most of know that nostr is a protocol which is designed to be decentralized from the ground up. That decentralization is due in large part to the fact that users read and write data to multiple relays by default. So instead of all your data going to a centralized database (usually owned and operated by a single company) with nostr you have the ability to send your data to as as many relays as you'd like (relays are just databases, after all). Likewise, you can read other people's data from as many relays as you'd like to. Decentralized design = decentralized system, right!? Well, turns out, no.
The problem with a design like this is that what can be done and what will be done are often very different things. Imagine the following scenario: You follow 1000 people; 700 of them post their notes to the Primal relay, the other 300 post their notes to the Damus relay. If you don't also write your content to those two relays, the people that you care about won't see your content, they won't see your replies to their notes, they won't even know you exist. So while; in practice, it's easy to read & write to many different relays, users and their content will tend to centralize because it's the path of least resistance to a good user experience. Network effects and economies of scale always apply, they just don't always lead to the outcomes that you want.
Before you start to panic, this sort of centralization isn't a huge issue just yet. We are still a nascent network and there are still hundreds of active relays out there. Almost all nostr clients make relay selection a first class citizen and don't default new users to a single relay. The fact that we're even having this conversation in a serious way at this stage is a great sign that the community cares enough to be proactive about maintaining (and improving) decentralization over time.
That said, this is not a issue that we can take lightly either. The top 5-10 relays do already have an outsized percentage of users and we have many examples of these centralizing tendencies across dozens of protocols and networks over the last 30 years, so the threat is real.
The status quo is wasteful
The other major issue is that currently most nostr clients are extremely wasteful in how they fetch data. The default is to simply get everything from all the relays a user wants to connect to. Because most of us are writing the same data to many relays, this leads to huge amounts of duplicated data being downloaded, having its signatures verified, and then (for the most part) thrown away. For those of us with latest generation smartphones, unlimited data, and a working power outlet nearby, this is fine. For everyone else, this is a major roadblock to adopting nostr.
A lightly technical aside
There are a few important features of nostr that make any sort of intelligent data fetching possible. To understand how any of the potential solutions to the aforementioned problems would actually work, it's important to have a baseline understanding of these technical details. I promise, I'll keep it high level.
Relay lists
Recently the concept of a Relay List Metadata has been introduced to the spec in NIP-65 (there are also other types of relay lists documented in NIP-51). This is a nostr list event where users publish their preferred relays with a marker that says whether the relay is for read-only, write-only, or read & write. This vastly simplifies the process of finding preferred user relays for clients and I imagine that this will become the de facto standard place to look for a user's preferred relays.
NIP-05
The NIP-05 spec also documents a way for users to signal their preferred relays. However, unlike the NIP-65 relay list, this is a simple list of relays without any details on whether the user reads or writes to those relays.
Tag markers
Tag markers are positional elements in tags that give the client publishing the event the ability to leave a hint as to which relay other clients can expect to find a given user or note that is being referenced.
For example, in a user's contact list (a
kind: 3event) you have many"p"tags to reference all the user's that are followed. These tags look like this:{ "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr"], ["p", "612ae..e610f"] ], "content": "", ...other fields }All three of these
"p"tags are valid (only the"p"and the user's pubkey are required), in the first and second you can see the third item is a relay where the user's events can be found.These types of tag markers are repeated all throughout nostr. Here's a few more example references for an event (in this case a long-form article):
``` ["e", "b3e392b11f5d4f28321cedd09303a748acfd0487aea5a7450b3481c60b6e4f87", "wss://relay.example.com"],
["a", "30023:a695f6b60119d9521934a691347d9f78e8770b56da16bb255ee286ddf9fda919:ipsum", "wss://relay.nostr.org"] ```
As you can imagine, these hints can be very helpful but only if clients actually attempt to fetch the content from the referenced relay.
The solutions?
Now that you understand the problem space a bit better let's define those terms we started with.
Blastr
Blastr was created by nostr:nprofile1qqs9hejyd252x8q3kw6980ud4lymx3hlx2x3lgg6p7sz58nyv8m2nvgdswkeh and nostr:nprofile1qqswrlemlh2wgqc4jkds3d8ueqj9a2j3gcm7r48v9tskdd6rxsd7rtcpwpuwc from Mutiny and isn't a relay. Instead, Blastr is a proxy (i.e. it looks like a relay to clients) that ingests any event sent to it and, in turn, sends those events to EVERY online relay on the network. It's a mass re-broadcaster for events that can be helpful to get your data pushed out to as many relays (and thus users) as possible. The drawback, of course, is that this is tremendously wasteful from a bandwidth and storage perspective.
Gossip (in 3 flavors)
This is by far the most confusing part for most people when watching the memes of the last few weeks fly by and I've seen a lot of confused takes out there. Most of the confusion stems from the multiplicity of definitions of what the "gossip model" actually is. Let's go through the options. 1. Gossip protocols: This is a general concept more than a specific implementation. Gossip protocols are protocols that attempt to spread information around a network in a uniform way. For example, Bitcoin nodes use a variation of the gossip protocol to make sure that transactions end up in as many mempools as possible. This is important in computing when you want to reach consensus or when all nodes in a network need to have the same information in order to operate the network. Since nostr doesn't have any consensus rules or shared compute, it's somewhat pointless to try and make sure all events are propagated to all relays (hence the limited usefulness of Blastr). 2. The Gossip client from nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w : This is a nostr client that was built from the ground up to try and use relays and relay hints in events to the fullest to keep things as decentralized as possible while being efficient in how much data it was fetching. Mike has a great (slightly outdated and very technical) video that talks about his motivation behind building Gossip in the way he did. It's worth a watch. video link 3. Gossip model: This is what people are usually referring to when they are talking about relays on nostr. The Gossip model is a loose, catch-all term used to refer to all the ways in which clients attempt to understand which relays they should read & write to for a given user. Again, this isn't really a specific spec or implementation but encompasses many different strategies. This vagueness inherent in the term makes discussions about the "gossip model" pretty imprecise and prone to misunderstanding.
Don't gossip
To be clear: You really shoud not be thinking about or talking about any of this as the "gossip model" since that definition is so abstract as to be unusable. Which brings us finally to the real topic being discussed at the moment among devs; the Outbox model.
Outbox/Inbox model
This is the real topic of conversation right now: How should client developers build relay discovery and selection features into their apps. As we already talked about, if left alone, it's likely that we'd unintentionally centralize most of nostr onto a few huge relays. So making sure that we encourage (and build sensible defaults) to help client developers to treat relay discovery and selection properly is really critical.
Right now, the discussion centers around one main approach, called the "Outbox model". There is also an "Inbox model" which is a still just a high level idea which I'll mention below but it's not being implemented yet (as of late March 2024). 1. The "Outbox model": This strategy looks at what relays users are using to publish their events (from relay lists and tag markers) and then uses an algorithm to decide how to fetch all the needed events from the array of relays. Different implementations can use different algorithms to select relays. For example, one implementation might optimize fetching events from the smallest number of relays (favoring large relays), while another might optimize for fetching from the relays that have the smallest user overlap (favoring small relays). 2. The "Inbox model": As you can imagine, this strategy flips the outbox model on it's head. It's so far just an idea (proposed by nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq) and a draft NIP but the idea is that when your client posts on your behalf, it will loop over your entire follow list, making a list of the relays that each of your followers uses to read events. Then the client will publish your event to all of those relays. If all clients followed this paradigm, then each of us would only have to read from a single relay. To quote nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq 's original post, "This doesn't take away from the outbox approach, and maybe should even be used together instead of as a replacement. But my point is that clients should be trying harder to deliver posts instead of just fetch posts. Because it benefits users when their posts can be seen."
Why the Outbox model has broad support
To understand why implementing an Outbox model is so powerful at solveing the problems laid out at the beginning of this article, you can do two quick thought experiments:
A user banned from all other relays
Imagine a user who's content is banned from all public relays for some reason. Instead, they have to run their own relay and publish their events there. With a simple "follow the major relays model" (or even with Blastr attempting to copy and paste their events to every other relay) this user is completely invisible to the network. User's would have to know about the banned user's private relay and select that relay in each client they use. What's more, if that relay ever had to change URL (likely for a user that is banned so broadly), all user's would need to know what the new URL is in order to change relays and fetch events from the new location.
With Outbox however, clients will see that their user's follow this user, will then look up this user's relay list, and will know where they need to go to fetch their events. It becomes much more difficult for relays to censor or block users with an Outbox model in place
Duplicate event fetching
We talked earlier about how many nostr clients often fetch the same data many times, just to throw that data away. Even using the simplest algorithms with an Outbox model, you can significantly reduce the amount of duplicate data you're fetching from relays. We, as users, would all also need to specific many fewer relays in our relay lists but would still be quite sure our clients would be able to find all the content we want to see.
Wrapping up
Hopefully this has given you a better overall understanding of what folks are talking about when they refer to Gossip (remember: don't refer to it this way) or Outbox (outbox, yay!) and why we need to be proactive about maintaining the decentralization of nostr.
-
 @ 52b4a076:e7fad8bd
2024-03-23 22:44:50
@ 52b4a076:e7fad8bd
2024-03-23 22:44:50Introduction
LNbits is a project plagued with poor code quality, potential security risks and bad management. What can be done about it?
The problems
Improper handling of vulnerability disclosures
Case 1
Two years ago (don't remember exactly when, Twitter account deleted), I discovered an SQL injection vulnerability in LNbits. This could be exploited very easily by setting by sending the injected data in keys in the payload of most requests. (anyone could create create wallets)
This was possible due to the query to insert/update was generated using the body of the request, with basically no sanitization.
When I contacted Ben Arc about this, the fix for this exploit was not implemented for several months, and when it was, I do not recall there being an advisory for people to update.
Case 2
A month or two ago, I had discovered an exploit that allows draining nodes completely under certain conditions. I had reported this to an active maintainer of the project, which had passed it on to the team. The exploit has not been fixed.
Case 3
Again, a month or two ago, a flaw was discovered in the SatsDice extension that allowed anyone to drain wallets. I had investigated this, and found that the extension allows invoice keys (instead of admin keys only) to create dice that have a guaranteed win rate and return more sats than put in, and then use it to drain balances.
I had reported this to the team, and while it was fixed a week or two later, there was no easily visible for people to update except an "update your SatsDice extension" message in the LNbits chat buried in a conversation about the exploit.
Bad security practices
"Don't do one thing, and don't do it well"
LNbits has over time expanded its scope, from being a wallet layer to an LN apps platform to a node management tool. While this may seem great for users, it has come at a significant security cost: - There is a larger attack surface for attackers to exploit. - The newly introduced node management and admin UI feature allows easy draining of nodes if the admin URL was leaked, whether by by the autocomplete on the search bar or the user's history. - All extensions run at the same privilege level as LNbits itself which has direct access to funds.
Developers can accidentally shoot themselves in the foot
The LNbits codebase encourages many harmful development patterns that allows developers to easily create vulnerabilities that put funds at risk
Example 1
Most LNbits extensions use the following system for handling object creation/deletion: - Take the body and convert it to a class - Overwrite/sanitize fields in that class, such as preventing overwrite of the wallet ID - Pass it to the DB to write
There is a slight problem: it can be easy to miss what to sanitize and what to not sanitize.
When you are doing an update request, you may accidentally forget to overwrite the wallet_id on the request sent by the user to update a withdraw link, and trust the user. You just created a bug to drain anyone's wallet given its ID, which LNbits does not consider sensitive information and sometimes requires you to share.
Example 2
LNbits treats any error during a payment attempt an error. But errors don't always happen due to failures in your request. Network connectivity is flaky, nodes restart, and way more reasons for there to be an error while the payment actually may be going through.
If you can get a way to trigger an error during a payment call, but also have it succeed, you can easlly drain a node. I have reasons to believe this is possible in production deployments.
This could easily be fixed as attempting to check the status of a payment after an error, and if that also fails, consider the payment pending until it can be checked, but ths has not been implemented.
Bad project management
LNbits' current management suffers from many problems: - the project suffers from feature and scope creep, implementing things for the sake of it - bugs go unaddressed - security is not a top priority
This is problematic for a project that deals with funds, as it is everything that you shouldn't be doing for a project meant to deal with funds. Tens of thousands of dollars in some cases and thousands in others.
What can we do about it?
For me, I have disabled withdrawals on my LNbits instance. I am also working on a replacement project called LNLocker that will solely focus on the wallet layer bit.
I would encourage trying to replace LNbits, as hard and sometimes impossible as it may be, or if you can, modify the code or restricting access via LND macaroons so that withdrawals cannot be made.
I highly recommend not exposing LNbits to the internet if you cannot disable withdrawals.
-
 @ 1c6b3be3:73f0ae6f
2024-04-20 04:07:00
@ 1c6b3be3:73f0ae6f
2024-04-20 04:07:00Releases - No Bullshit Bitcoin
Braiins Pool Lightning Payouts Now Available to All Users Braiins Pool, a mining pool, has introduced Lightning payouts for all its miners. This feature allows miners to receive their daily payouts instantly with no minimums or fees through a Lightning address in their Financial Account. The company encourages miners to take advantage of this new method to improve their mining margins ahead of the fourth halving. Other mining pools such as NiceHash and Titan Mining have also recently launched similar Lightning-based payout systems.
Cashu Nutshell v0.15.3: Improved Mint Crash Resistance (1 min) Cashu Nutshell, a Chaumian Ecash wallet and mint for Bitcoin Lightning, has released an update that enhances the crash resistance of its mint. If the mint crashes during an outgoing Lightning payment, the new startup routine will now resume those payments and invalidate all associated pending proofs if the payment was successful. A database migration is necessary for this upgrade, so users should back up their mint databases before installing this update. Additionally, the wallet can now check pending invoices with the command "cashu invoices" and restore ecash from all keysets of a mint using the command "cashu restore", thanks to contributions from @Guilospanck and @cjbeery24. Other changes include a refactor of the request mint function and a fix for a regression bug. The full changelog can be found in the GitHub repository.
tbDEX v1.0: Open Source Liquidity and Trust Protocol (1 min) tbDEX, an open-source liquidity and trust protocol, has been released in its first major version. SDK implementations of the protocol are available in TypeScript/JavaScript, Kotlin, and Swift for integration with Web, Android, and iOS applications. The protocol is built on Web5 infrastructure, utilizing decentralized technologies such as Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) for secure identity validation and trust establishment, as well as compliance with relevant laws and regulations. tbDEX offers a permissionless network, enabling financial institutions, wallets, and issuers to provide various services such as offering currency pairs and payment methods, initiating exchanges, presenting verifiable credentials, and creating decentralized identifiers for users. The platform also allows for real-time quotes, status updates, and order cancellation.
🍵 "btc | bitcoin | lightning network | asic" - Google News
The Bitcoin network completes the fourth-ever ‘halving’ of rewards to miners - CNBC Bitcoin 'Halving' Cuts Supply of New Tokens in Threat to Miners - Bloomberg So, Bitcoin Halving Is Done. What Happened and What's Next? - Investopedia After Halving Event, Bitcoin Transaction Fees Soar to Over $240 – Bitcoin News - Bitcoin.com News Bitcoin Network Fees Soar as Runes Launch Nears - The Defiant - DeFi News Bitcoin users spend record $2.4M in fees on halving block - Cointelegraph Bitcoin ushers in fourth halving as miners' block subsidy reward drops to 3.125 BTC - The Block Bitcoin's Historic Fourth Halving Takes Place, With Block Subsidy Rewards Cut in Half to 3.125 BTC - Unchained - Unchained Memecoins on Bitcoin are about to get supercharged. Here's how - DLNews Opinion: Why there will never be another Bitcoin - Kraken Blog Leaving Behind Bitcoin Sectarianism - CoinDesk Bitcoin's most promising, least dramatic halving is almost here - Blockworks Miners double down on bitcoin halving - Financial Times The Bitcoin halving is set to shake up the crypto's price and the network's miners - CNBC
-
 @ efa6abd0:a4970369
2024-04-20 03:34:17
@ efa6abd0:a4970369
2024-04-20 03:34:17Tick, tock,
Tick, tock,
About every ten minutes a new block is born,
Carrying varying numbers of transactions, as a puzzle gets solved,
The voice spreads out that the new block’s been verified,
Confirmations of truth, at least 6 that we want,
Nothing as true as timechain math.
The ledger gets longer and hence more secure,
Some people still yell, “TOO MUCH ENERGY!”
Using energy, as they yell.
Yet, miners look far and wide for energy lost,
From wasteful processes,
From sustainable natural sources,
The only way to get energy at the lowest of costs.
No need to use energy at the peak of times,
No need to carry it very far,
All this talk about energy only distracts from the why:
Solving a puzzle makes math on Bitcoin Layer 1 what we trust,
No agenda, nor bias, nor power to control,
No corrupt heart to change the rules and take loot,
Bitcoin is a tool anyone could use.
As long as you HODL your keys, there’s something else you have too,
Something you can remember as the halving comes through,
Bitcoin is limited, as long as you have the keys to the source,
Only 21 million to mine, no more printer go brrr.
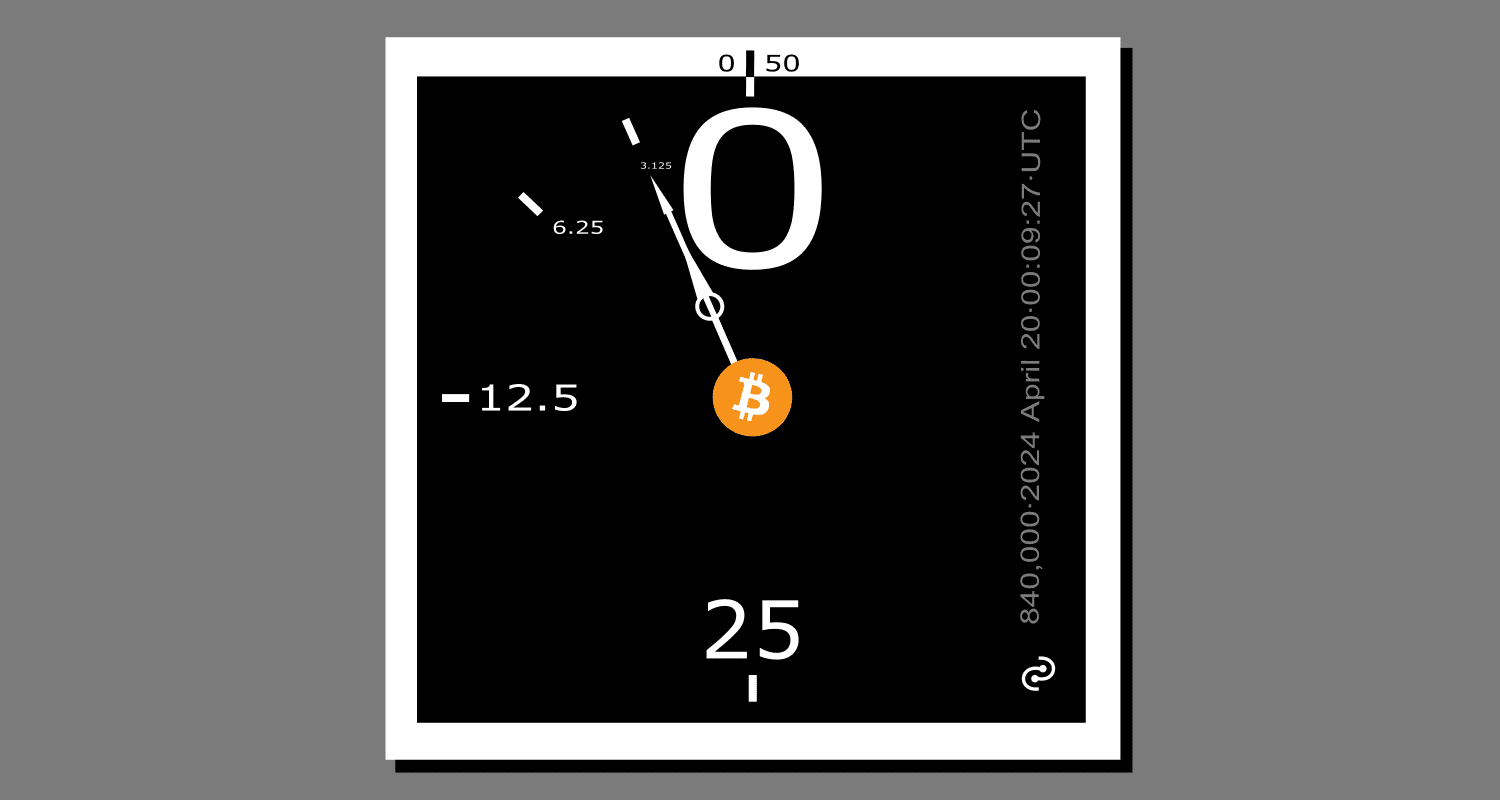
Tick, tock.
Tick, tock.
Proof of work, the halving has come,
We’re past the 840,000 blocks,
Another four years of proof of work.
The amount of new bitcoin to make on each block,
Has just been cut in half,
3.125, 3.125.
Transactions continue on every block,
As you and I send bitcoin across the globe.
Bull or bear, the blocks come every ten minutes or so,
PoW on a freedomchain we trust.
No more printer go brrr,
No more printer go brrr,
What is your time worth?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Viva o mata-mata
outro dia o comentarista Falcão, da Globo, disse, sobre o título do São Paulo: [i]"um jogo se ganha com um bom ataque, um campeonato se ganha com uma boa defesa"[/i], e foi deveras assustador pensar no que se transformou o futebol com o sistema de disputa do campeonato brasileiro por pontos corridos. um esporte em que vencia quem fazia mais gols está se transformando num esporte em que vence quem leva menos gols. é o sistema de pontos corridos - que premia a constância, o time que perde menos, mesmo que isso signifique empatar todos os jogos fora de casa em 0x0 e vencer todos em casa por 1x0. o sistema de pontos corridos premia o futebol feio, covarde, ou - como também é conhecido o futebol retranqueiro - o "equilíbrio".
eis que o futebol brasileiro, resolvendo seguir a linha européia, institui a disputa por pontos corridos e se transforma numa cópia malfeita e pobre do chato futebol europeu. e perde-se tudo que tínhamos de aqui que eles não tinham lá (é claro, os europeus têm mais estrutura, mais dinheiro, mais tudo), a ousadia, os brios, a coragem, a categoria e o escambau.
daí falam que o sistema de pontos corridos é mais justo. é mais justo porque dá o título aos times que jogaram melhor durante o campeonato, os mais regulares. mas ninguém disse por que não é justo premiar os times que conseguem vencer na semifinal e na final, o time que consegue ser pior o campeonato inteiro e no final tirar forças não sei de onde pra vencer aquele que era (ou parecia ser) bem melhor do que ele, o time que dá a volta por cima, o time que - mesmo não sendo regular - sabe jogar em decisões, sabe se segurar em um estádio com 80 mil torcendo contra e sabe aproveitar quando há 80 mil torcendo a favor e matar o adversário. o melhor time é o que vai ganhando pontinhos em jogos bobos e no final junta tudo e a soma dá mais do que os pontinhos do adversário ou é o time que consegue entrar num estádio numa final e derrotar, cara a cara, o adversário?
e quem disse que futebol é regularidade? repare que não se ouve mais a expressão desde o início dos pontos corridos, mas futebol é uma caixinha de surpresas. dos esportes que eu conheço, futebol é o único em que o último colocado pode vencer o primeiro e ninguém considerar isso um absurdo. com os pontos corridos, morrem metade dos componentes do futebol: o amor pelo ataque - conforme explicitado na supracitada afirmação de Falcão - a coragem, os brios e a emoção.
ao premiar a regularidade no futebol, pode-se estar chamando de “campeão” um time que facilmente tremeria numa final. e não é justo que um time covarde seja campeão. duvido que o São Paulo de 2007 jogaria bem numa final contra o Flamengo. e dificilmente o Corinthians de 2005 venceria uma final contra o Internacional (aliás, perdeu, moralmente, aquele jogo que foi quase uma final entre os dois).
mas se todo mundo gosta tanto assim desse campeonato de pseudo-futebol, vem aí a Copa do Mundo por pontos corridos.
-
 @ 8947a945:9bfcf626
2024-04-20 03:15:44
@ 8947a945:9bfcf626
2024-04-20 03:15:44Family trip Kanchanaburi Thailand 9/4/2024
วัดถ้ำคีรีธรรม (Wat Tham Khiritham)



วัดถ้ำพุหว้า (Wat Tham Phu Wa)






-
 @ e5780864:dfd63806
2024-04-20 02:50:08
@ e5780864:dfd63806
2024-04-20 02:50:08 -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ bcea2b98:7ccef3c9
2024-04-20 00:11:30
@ bcea2b98:7ccef3c9
2024-04-20 00:11:30 -
 @ 947c8c3e:22e2d6ea
2024-03-23 19:15:12
@ 947c8c3e:22e2d6ea
2024-03-23 19:15:12LoRa technology is being quickly adopted as a long-distance, low-power communication network, propelling a new wave of connectivity that significantly outstrips traditional methods like WiFi, Bluetooth, or ZigBee. Designed to transmit small amounts of data over vast distances, LoRa stands out as a great platform for the Ghost Grid Network and similar communities seeking to emergency preparedness and connectivity beyond conventional boundaries.
Understanding LoRa's Core
LoRa (Long Range) utilizes a wireless modulation strategy based on Chirp Spread Spectrum (CSS) technology, which encodes information across chirp pulses. This approach, inspired by the communication techniques of dolphins and bats, showcases remarkable resilience to interference, facilitating communication across extensive distances. LoRa's proficiency in handling small data packets across lengthy ranges, coupled with its operation on license-free sub-gigahertz frequency bands, makes it an obvious choice for a myriad of applications, from simple text communication, sensor networks to IoT (Internet of Things) ecosystems.
Distinctive Features of LoRa
LoRa distinguishes itself through several key attributes: - Extended Connectivity: It offers unparalleled range, enabling data transmission up to 20 km in rural settings and 5 km in urban environments, surpassing other wireless technologies. - Efficiency: LoRa devices boast extended battery life, operating for weeks on a single charge, which translates to sustainable and cost-efficient solutions. - High Capacity: Supporting a vast network of nodes, LoRa accommodates numerous messages per second, showcasing its scalability. - Security: End-to-end encryption guarantees secure data transmission, making LoRa an optimal choice for confidential communications.
LoRaWAN: Complementary Networks
You may hear of another network called LoRaWAN. LoRaWAN is a protocol that works with LoRa technology to manage how devices communicate over long distances. Think of LoRa as the way messages are sent, like speaking a language, and LoRaWAN as the rules of conversation—when to speak, how to reply, and making sure messages are understood and secure. It’s designed to ensure that devices using LoRa can connect efficiently, securely, and without using much power. Managed by the LoRa Alliance, this set of rules helps devices talk to each other and to the internet, making it easier to set up large networks of sensors and devices for things like monitoring weather or tracking assets.
Empowering the Ghost Grid Network with LoRa
The Ghost Grid Network is one example of how LoRa technology can be used for decentralized, autonomous communication systems. We leveraging LoRa's mesh protocol alongside tools like Meshtastic for effective, community-driven connectivity that benefits from each new user on the mesh. From emergency preparedness to environmental monitoring, each application benefiting from LoRa's robust, long-range, and low-power communication capabilities.
Venturing into LoRa
For enthusiasts eager to explore LoRa's potential, joining a community-focused network like Ghost Grid provides invaluable resources, tutorials, and collaboration opportunities. Starting with LoRa necessitates acquiring the appropriate hardware, such as modules and gateways, and delving into project development to contribute to the collective knowledge and application of this transformative technology.
Take Away
LoRa technology is not just a tool but as a base layer for sovereign communication, free speech and connectivity. Its long-range, low-power communication and resilient, interconnected mesh can enable us to do more without as much reliance on mega corporations and local city infrastructures. Join us as we grow the LoRa network into an awesome meshed up future!
What to Earn the Badge?
As a bonus, if you successfully pass our optional quiz, you'll earn a special badge for your Nostr profile, showcasing your expertise and support for innovative communication technologies. It's a cool way to celebrate your understanding and contribution to the community.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28LessPass remoteStorage
LessPass is a nice idea: a password manager without any state. Just remember one master password and you can generate a different one for every site using the power of hashes.
But it has a very bad issue: some sites require just numbers, others have a minimum or maximum character limits, some require non-letter characters, uppercase characters, others forbid these and so on.
The solution: to allow you to specify parameters when generating the password so you can fit a generated password on every service.
The problem with the solution: it creates state. Now you must remember what parameters you used when generating a password for each site.
This was a way to store these settings on a remoteStorage bucket. Since it isn't confidential information in any way, that wasn't a problem, and I thought it was a good fit for remoteStorage.
Some time later I realized it maybe would be better to have a centralized repository hosting all weird requirements for passwords each domain forced on its users, and let LessPass use data from that central place when generating a password. Still stateful, not ideal, not very far from a centralized password manager, but still requiring less trust and less cryptographic assumptions.
- https://github.com/fiatjaf/lesspass-remotestorage
- https://addons.mozilla.org/firefox/addon/lesspass-remotestorage/
- https://chrome.google.com/webstore/detail/lesspass-remotestorage/aogdpopejodechblppdkpiimchbmdcmc
- https://lesspass.alhur.es/
See also
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ affa3201:94121ac0
2024-04-19 19:58:24
@ affa3201:94121ac0
2024-04-19 19:58:24Opinion about Wallet of Satoshi (android)
Overall fast and reliable. Simplistic and elegant UI. Fees for lighting transactions are manageable. Works quite efficiently for small payments would not recommend for larger payments . Best wallet for beginners. Has KYC services if you choose to buy or sell bitcoin. Basically the best wallet if you plan on just sending and receiving sats.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Propaganda
Está na moda ser contra a propaganda. "Se você não está pagando você é o produto", dizem os ativistas contrários aos sites que funcionam de graça, mas que ou te mostram propagandas ou vendem os seus dados para empresas terceirizadas que então te mostrarão propagandas. E aí advogam que todos devem usar bloqueadores de propagandas e procurar alternativas pagas aos mesmos serviços que funcionam de graça, porque os de graça, por sua participação nas redes de propaganda, acabam saindo mais caros para o usuário.
É claro que o Facebook e várias outras dessas grandes empresas da internet e "redes sociais" são horríveis, mas o pior de seus males é a propaganda que eles mostram. Os ativistas anti-propaganda se esquecem do maior bem que a propaganda -- e principalmente a propaganda direcionada e fracionada, estilo Google -- nos proporciona: a possibilidade de conhecer empresas novas com serviços que potencialmente nos interessam.
Se nos tempos da televisão a propaganda era uma coisa que só empresas já enormes conseguiam colocar no ar, hoje empresas minúsculas conseguem, e com essas propagandas conseguem atingir clientes que jamais sonhariam em conhecê-las. E empresas médias ou que estão tentando crescer conseguem atingir clientes que de outro modo acabariam comprando ou contratando as atuais líderes de mercado.
Se o primeiro caso é mais importante para mais pessoas e para a idéia mesma da liberdade de empresa e à cultura da microempresa individual, o segundo ponto soará melhor aos sociólogos e economistas normais: sem a possibilidade da propaganda, a tendência à manutenção do status quo é maior, sem a propaganda, é maior a probabilidade de um fulano qualquer escolher o seu fornecedor de bens e serviços pelo nome e pela fama, ou seja, as empresas que já são grandes e famosas têm uma probabilidade maior de continuarem grandes e famosas, mesmo que as menores que estão chegando agora ofereçam bens e serviços melhores e por menores preços -- ou mesmo bens e serviços ligeiramente diferentes, mais adeqüados à necessidade de fulano.
Essa conclusão é inegável, embora eu não possa dizer qual seja a magnitude do impacto que a propaganda tem.
Para vivermos num mundo sem propaganda e sem uma enorme tendência ao status quo, me parece que são necessários os seguintes desenvolvimentos (não precisa ser todos ao mesmo tempo, qualquer um deles pode funcionar separadamente):
- sistemas melhores de busca: quando fulano procura (no Google, uma empresa que vive de propaganda, será que alguém pagaria pra usar o Google? acho que sim) por um chicabon, o Google deveria mostrar-lhe não só o Chicabon da Kibon, mas outros chicabons possivelmente melhores, e talvez lhe dizer por que aqueles poderiam lhe agradar mais. Mas não só isso: talvez o fulano não esteja realmente querendo um chicabon, talvez ele esteja viciado em doces e no fundo esteja querendo se desviciar, talvez precise de um spa, uma dieta paleolítica, um cozinheiro melhor. Todas essas possibilidades deveriam lhe ser apresentadas, mas eu não faço idéia de como seria a interface do fulano com o computador para que isso fosse possível. Também não consigo imaginar isso funcionando sem um sistema computacional complexo e "inteligente" que opera com dados muito íntimos de fulano.
- melhor autoconhecimento e capacidade de expressão: as pessoas em geral não sabem o que querem, como disse, acho, o Steve Jobs, quando criou o iPhone. Se as pessoas soubessem o que querem, poderiam procurar exatamente pelo que querem. Se procurassem exatamente pelo que querem, talvez achassem coisas melhores do que acham quando procuram por termos genéricos ou nomes de marcas. Talvez a internet já tenha sido capaz de fazer melhorar muito as habilidades de buscar no Google das pessoas, mas continua havendo muito espaço para melhora. Os maiores problemas aqui são a auto-inspeção real (imagino que a maior parte das buscas sejam feitas hoje baseadas em coisas que as pessoas ouviram falar, e não no que elas querem intimamente de verdade) e, a parte mais difícil, a expressão dos resultados dessa auto-inspeção, para a qual é necessária também uma língüa decente (formal?), sólida e ao mesmo tempo flexível.
- bancos de dados de necessidades: se isso fosse inventado hoje, ninguém usaria, ou seriam repletos de desejos vazios, abstratos demais ou específicos demais para serem úteis, mas se o ponto anterior fosse realizado, a criação de bancos de dados de necessidades traria desenvolvimentos enormes no mundo (micro-)empresarial, com benefícios fáceis e grandes para todas as partes. Imagino eu, porém, que um esforço monstruosamente paciente de alguém que começasse a implementar a idéia dos bancos de dados de necessidades (perceba que a minha idéia aqui é expressa de forma abstrata e inútil) poderia, se tivesse algum sucesso, começar a educar as pessoas, assim como o Google as educou na técnica de "buscar", de modo que daqui a uns anos esses bancos de dados começassem já a terem utilidade e efeito.
-
 @ 0403c86a:66d3a378
2024-04-19 19:15:46
@ 0403c86a:66d3a378
2024-04-19 19:15:46Serie A Secures Five Spots in Next Season's Revamped Champions League
In a significant achievement for Italian football, Serie A has guaranteed five clubs in next season's expanded Champions League. This comes after Italian teams secured a top-two spot in the UEFA coefficient standings.
The UEFA coefficient rankings, which determine the number of places each association is awarded in the Champions League, are calculated based on the results of each association's clubs in the five previous seasons of UEFA club competitions.
Roma and Atalanta both made impressive strides in the Europa League, securing spots in the semi-finals on Thursday. Meanwhile, Fiorentina continues to shine in the Europa Conference League, reaching the last four. These performances have boosted Italy's coefficient to 19.428 points, surpassing Germany (17.928 points) and England (17.375 points).
This stellar performance means Italy will take one of the two extra spots in the Champions League. The tournament is set to expand from 32 to 36 teams in the group stage from next season.
The additional spots will be allocated based on a new system. The team that finishes third in the championship of the association ranked fifth in the UEFA association coefficient rankings will now qualify for the group stage. The remaining two spots will be awarded to the clubs with the highest club coefficient that have not already qualified for the Champions League, but have qualified for the Europa League or the Europa Conference League.
This is a significant milestone for Serie A, reflecting the strength and competitiveness of Italian football. The achievement is expected to boost the league's reputation and attract more global attention, promising an exciting season ahead.
Dembélé's Stellar Performance Earns Him UEFA Champions League Player of the Week
Ousmane Dembélé, the 26-year-old forward, entered the second leg of the UEFA Champions League quarterfinal down against FC Barcelona knowing he might face hostility from the home crowd. However, Dembélé turned the jeers into motivation, delivering a memorable performance that has earned him widespread acclaim.
Dembélé's standout display helped Paris Saint-Germain (PSG) defeat Barcelona 6-4 on aggregate, securing their spot in the semi-finals. The Frenchman was named the player of the match for his exceptional performance, and his achievements did not stop there.
On Friday, it was announced that Dembélé had been named the UEFA Champions League Player of the Week. This prestigious award recognizes the best individual performance in the competition during a given week.
Madrid Fan Hails Real Madrid's Victory Over Manchester City, Criticizes City's Supporters
Real Madrid secured a spot in the Champions League semi-finals after a thrilling penalty shootout victory over Manchester City at the Etihad Stadium. The win was a testament to Madrid's resilience and determination, and one away fan had a lot to say about the game and the two teams involved.
The ecstatic supporter started by acknowledging Pep Guardiola's coaching prowess. "I hate Guardiola, but I need to say he is one of the best coaches in the world," he said. However, he quickly shifted focus to City's supporters, expressing his disappointment in their lack of excitement and passion.
"City, they don't deserve this amazing team because the supporters...," he continued, before mimicking a key locking their mouth. He suggested that if this City team were playing for Manchester United, the fans would be much more enthusiastic.
The Madrid fan argued that City's supporters are not as passionate as those of Real Madrid, Manchester United, Bayern Munich, Juventus, or even Barcelona. He claimed that City's fans will realize why they are not as big a team as these other clubs.
"We show we are the big team in Europe and in the world," he concluded, emphasizing Madrid's status as one of the world's most successful and popular football clubs.
Arsenal's Champions League Dream: Four Key Areas for Improvement
Arsenal's recent elimination from the Champions League at the hands of Bayern Munich has highlighted the areas in which the Gunners need to improve to become genuine contenders for the competition. Despite their impressive progress under Mikel Arteta and their domestic success, there are four key areas where Arsenal must focus their efforts to get over the hump in Europe.
-
Striker: Arsenal's current striker options have struggled to find consistency in front of goal, and the team lacks a clinical finisher who can make the difference in tight matches. The Gunners must invest in a top-quality striker who can provide the firepower needed to compete with Europe's elite.
-
Midfield: Arsenal's midfield has been a strength in recent years, but there is still room for improvement. The team needs a dynamic midfielder who can control the game, break up opposition attacks, and provide the creative spark to connect Rice and Odegaard
-
Left-back: Arsenal's left-back position has been a problem area for some time, with no player establishing themselves as a consistent first-choice option. The Gunners need to find a left-back who can provide defensive solidity while also contributing to the attack.
-
Mentality: Perhaps the most significant area for improvement is Arsenal's mentality. The team has shown an inability to handle pressure in big games, and this has cost them in crucial moments. The Gunners need to develop a winning mentality, a never-say-die attitude that will allow them to overcome adversity and compete with Europe's best.
Dortmund's Remarkable Comeback Secures Semi-Finals Spot, but Questions Remain
Borussia Dortmund staged a remarkable comeback at home against Atlético Madrid to secure a semi-finals spot in the Champions League. The Westfalen stadium was a riot of colour and sound as the home team put on a show of attacking football, but questions remain about their ability to compete with Europe's best.
However, even as Dortmund toasted their victory, there were questions about whether they can be taken seriously as Champions League contenders. The team has a history of boom and bust performances, and their defence has been a major weakness this season.
Dortmund's next opponents, Paris Saint-Germain, are themselves not without flaws, but they have the firepower to punish porous defences. The German team will need to find a way to shore up their defence if they are to have any chance of progressing to the final.
Global Sports Central 🌐 #GSC360
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O mito do objetivo
O insight deste cara segundo o qual buscar objetivos fixos, além de matar a criatividade, ainda não consegue atingir o tal objetivo -- que é uma coisa na qual eu sempre acreditei, embora sem muitas confirmações e (talvez por isso) sem dizê-lo abertamente --, combina com a idéia geral de que todas as estruturas sociais que valem alguma coisa surgem do jogo e brincadeira.
A seriedade, que é o oposto da brincadeira, é representada aqui pelo objetivo. Pessoas muito sérias com um planejamento e um objetivo final, tudo esquematizado.
Na verdade esse insight é bem manjado. Até eu mesmo já o tinha mencionado, citando Taleb em Processos Antifrágeis.
E finalmente há esta tirinha que eu achei aleatoriamente e que bem o representa:
-
 @ affa3201:94121ac0
2024-04-19 18:20:33
@ affa3201:94121ac0
2024-04-19 18:20:33Opinion about LifPay (android)
Simplistic custodial wallet with very simple features. Great for managing multiple accounts. The anonymous lighting address is a cool feature for those sensitive about privacy. Sending and receiving funds is quite efficient, the fees are low. Available even on desktop. The customer team is responsive. I think it's a hidden gem, no complaints in the time I have used it. Suitable for beginners and those just sending and receiving satoshis.
WalletScrutiny #nostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The P2SH Wars
This article on the history of P2SH implementation on Bitcoin has two valuable lessons and illustrates the benefits of
bitcoinddecentralization:- The benefits of multiple codebases: Russell O’Connor found the bug in
OP_EVALwhile working on it in his alternative Bitcoin software implementation. - The dangers of a single master repository with a restricted set of owners: Gavin Andresen committed code for a broken
OP_EVALfirst, then pushed an evil miner activation signaling mechanism that defaulted to his personal preferred P2SH version (to signal the opposite miners would have to edit the code and recompile) and won the battle against a much better and saner approach (Luke Jr'sOP_CHECKHASHVERIFY) by the sole power of inertia: things were already merged and working so no one bothered to fight for what seemed to be a minor and maybe irrelevant improvement but that later was proven to be substantially better.
The second lesson can actually be split in 4 different lessons:
a. Maintainer committing a bug and no one noticing it; b. Maintainer committing evil signaling mechanism; c. Everybody going along with everything because it's hard to take a public stand about a central thing everybody loves and the status quo bias exists and is strong; d. Things that look good now may look bad later and vice-versa, no amount of expert "eyes on code" can fix that.
- The benefits of multiple codebases: Russell O’Connor found the bug in
-
 @ 947c8c3e:22e2d6ea
2024-03-16 17:30:33
@ 947c8c3e:22e2d6ea
2024-03-16 17:30:33Bitcoin, emerging as the most decentralized and scarce currency, stands as the epitome of financial revolution in the digital age. It embodies the principles of autonomy, security, and innovation, paving the way for a new era of economic empowerment. This exploration delves into the fundamentals of Bitcoin, the pioneering innovation of the Lightning Network, and the unparalleled privacy and offline capabilities of eCash, illustrating the transformative power of these technologies in fostering a resilient and decentralized financial landscape.
Bitcoin for Individuals: Empowerment at Your Fingertips
Bitcoin revolutionizes the way we think about money, offering a secure, low-cost method for transactions. It simplifies mobile payments, allowing for effortless scan-and-pay transactions without the need for traditional banking hurdles. The security model of Bitcoin, underpinned by mathematical certainty and proof of work (PoW), provides unparalleled control and protection over your funds, ensuring that your transactions remain immutable and resistant to fraud.
The Universality of Bitcoin
Bitcoin operates on a global scale, unfettered by geographical boundaries or time zones. Its decentralized nature ensures that it is always operational, allowing for instantaneous international payments without the restrictions imposed by traditional financial institutions. This universality empowers users to transact with anyone, anywhere, at any time, with the freedom to set their own transaction fees.
Privacy and Anonymity
Bitcoin also champions financial privacy. Unlike conventional payment methods that are prone to security breaches, Bitcoin transactions do not reveal sensitive personal information. This feature, coupled with the potential for anonymity similar to physical cash transactions should you choose to do so, places a strong emphasis on user privacy, allowing individuals to transact securely and discreetly.
Lightning Network: The Path to Scalable Bitcoin Transactions
The Lightning Network represents a monumental stride towards the scalability of Bitcoin transactions. By facilitating instant, low-cost payments, the Lightning Network addresses the inherent limitations of blockchain confirmations, thereby enabling a vast throughput of transactions per second. This innovation not only enhances the efficiency of Bitcoin transactions but also opens up new avenues for microtransactions and cross-chain interactions without compromising on security or decentralization.
Payment Channel and Off-Chain Scalability
At its core, the Lightning Network leverages smart contracts called a multi-signature payment channel to conduct transactions off-chain, significantly reducing the burden on the Bitcoin blockchain. This approach ensures that transactions are both rapid and cost-effective, fostering a more dynamic and inclusive financial ecosystem.
Cashu: Reinventing Privacy for Bitcoin
One of the Lightning Networks disadvantages is that both parties need to be online to receive funds. Utilizing a Chaumian ecash system built specifically for Bitcoin and Lightning Network, Cashu emerges as a great solution to this issue, with its potential for partial offline transactions and near instant payments.
This system also ensures near-perfect anonymity for users, making it virtually impossible to trace transactions back to their participants. By integrating closely with the Lightning Network, eCash facilitates private, instant transactions, further solidifying Bitcoin's position as a leader in secure and decentralized financial transactions.
The Future of Bitcoin and Beyond
The synergy between Bitcoin, the Lightning Network, and eCash heralds a new era of financial sovereignty. These technologies collectively represent the cornerstone of a decentralized financial system, one that prioritizes privacy, security, and user autonomy. As we venture further into this digital frontier, Bitcoin continues to lead the charge, challenging the traditional paradigms of money and empowering individuals with the tools for true economic freedom.
In conclusion, the essence of Bitcoin and its complementary technologies lies in their ability to redefine our relationship with money. By championing decentralization, scarcity, and innovation, Bitcoin not only promises a future of financial autonomy but also invites us to partake in the ongoing evolution of digital prosperity.
-
 @ 9071d94a:6967c53b
2024-04-19 18:15:50
@ 9071d94a:6967c53b
2024-04-19 18:15:50test test test
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28An argument according to which fractional-reserve banking is merely theft and nothing else
Fractional-reserve banking isn't anything else besides transfer of money from the people at large to bankers.
It has been argued that fractional-reserve banking serves a purpose in making new funds available out of no one's pocket for lending and thus directing resources to productive borrowers. This financing method is preferrable to the more conservative way of borrowing funds directly from a saver and then using that to lend to others because it uses new money, money not tied to anyone else before, and thus it's cheaper and involves less friction.
Instead, what happens is that someone must at all times be the owner of each money. So when banks use their power of generating fractional-reserve funds, they are creating new money and they are the owners – at this point, a theft occurs from the public at large to them – and then they proceed to lend their own money. From this description it is clear that the fact that bank customers have previously deposited their own funds in the banks' vaults have no direct relation with the fact that banks created money afterwards, there's only a legal relation and the fact that banks may need cash deposited by its customers to redeem borrowers claims, but even that wouldn't be necessary if banks were allowed to print their own cash.
-
 @ 453846ff:a380c94b
2024-04-19 16:35:11
@ 453846ff:a380c94b
2024-04-19 16:35:11With all the excitement of the upcoming halving, my node decided to nuke itself.
Really makes you appreciate how far we have come. 840,000 blocks later.
Block height 0
🫡
-
 @ 75bf2353:e1bfa895
2024-03-16 14:34:56
@ 75bf2353:e1bfa895
2024-03-16 14:34:56https://i.nostr.build/# Orange Pilling Merchants
On the Freedom Foot Print show, Brian DeMint said he’s friend’s with a coffee shop owner in Riverside, California--The place where I host my bi-monthly bitcoin meetup. For the last 12,960 blocks or so, I've held a plebwalk on the first Saturday of each month. This plebwalk has been a solo-trek each time. More people are interested in going to meetups where we sit down and drink drugs like beer, soda, or coffee. Therefore, I have decided to cancel my Pleb Walk and move the meetup to Arcade Coffee Bakehouse the coffee shop mentioned on my favorite bitcoin author's podcast. Not to brag, but I bought an autographed copy of Sovereignty Through Mathematics with bitcoin from Knut Svanholm about 8,000 blocks ago. Just kidding, I am trying to brag.

Plebwalks did not attract as many plebs as I had hoped. I suspect I might spark more interest if we went to a coffee house that accepted bitcoin. Arcade Coffee-The Bakehouse in Riverside California does not accept bitcoin yet but I hope to change that. Some of my first blogs were about me going to the Riverside Farmer's Market to ask people if they accept bitcoin. About one-in-a-hundred said yes. This taught me an important lesson. That shit doesn't work. Rather than go home and cry in my coffee, what if I try a different approach?
The main problem is social proof. People are social animals. They look to others to see what they should or should not do. My dad handed me green paper to buy ice-cream from a dude with a mustache selling sugar to kids out of a van. That's the paradigm of money for most people. That's what everyone used for money before we became a nation of credit card debtors. We don't pay people anymore. We pay debt off to banks. Should I buy a Mercedes, or a whole Bitcoin? If you're reading this, you are more likely to drive an old Toyota, but most people will buy a Mercedes because suits like to pick their nose in cars made by Mercedes-Benz, or the richest man in the world. They think, I should buy a Mercedes-Benz so I can pick my nose like the rest of the successful people. Picking my nose in a Tesla is the ultimate status symbol. You need to have a great job and a great debt score to pick your nose in a Tesla.

Bitcoin was declared dead more times than I could give a fuck to count, but you know what really died? Cash. According to Dave Ramsey, "Cash is King." I'm sorry to be the bearer of bad news Mr. Ramsey, but your king is dead. Almost nobody uses paper cash, let alone p2p cash. "This bill is legal tender and must be accepted for all debts both public and private." . Well...that's just about all you pay with it, debt. Cash not accepted at many places these days. I guess the legal tender mumbo-jumbo means your credit card must accept cash to pay off your debt. Besides you'll get "cash back" if you use your credit card. That's not cash. It's more like Weekend At Bernie's Cash. It's social engineering which created social proof that teaches everyone should pay with a credit card, not cash. Guess what fixes this. That's only used by drug dealers, and people who dry-clean money or whatever laundering it means.
It would be nice to pay for my coffee with bitcoin rather than pay credit card with bitcoin. To do this, I can't just be the one caffeine-crazed junkie, hopped up on orange pills, asking the poor barista, "Do you accept our lord and savior, bitcoin?" But what if ten people asked to pay for coffee with bitcoin? What if 21 people asked to pay for their coffee in bitcoin? 50? By the way, tell the credit card companies to go fuck themselves by shoving their fees up their ass. "Gradually...then suddenly," is a better catch phrase, but Parker Lewis already coined it and I digress. If I can bring enough customers, we will have social proof for p2p e-cash. That's the hard part, but we have to start somewhere.
How Businesses Can Accept Bitcoin.
 People have been thinking about on-boarding businesses to accept payments for over a decade. NVK says that’s how Coinkite started, but the demand wasn’t there. It’s still not there. We need to create it. Strike has a Clover integration that works like this.
People have been thinking about on-boarding businesses to accept payments for over a decade. NVK says that’s how Coinkite started, but the demand wasn’t there. It’s still not there. We need to create it. Strike has a Clover integration that works like this.https://www.youtube.com/watch?v=yM4qfrywTew
Maybe you don’t want to spend your bitcoin because of the taxes or maybe the coffee house owner is a no-coiner. So what? Resist the urge to say “have fun staying poor.” Tell them the bitcoin can auto-magically convert to Trump’s favorite fiat currency.
strike Strike can’t pour a lot of resources into getting businesses to accept bitcoin as a payment when there’s no demand, but they have given us the tools to do it. Brian Tracy said, "if it’s to be, it’s up to me." He's right. Making bitcoin peer-to-peer cash is up to me and up to you. Some meetups have already integrated payments at their meetups. It's one of the best ways to grow bitcoin as peer 2 peer electronic cash. Many of the people who have signed up for my meetup are not aware of the lightning network. Some of them think video on a blockchain is the next way to pick their nose in a Lambo on the moon. They like “BTC” too. I say why video game on a blockchain NGMI and show them the lightning network.
After I give my spiel, I say, "so show me how this video game on a blockchain works." I might as well ask them to unify the theory of gravity. They don't know what a blockchain is.
"Wallet, you mean like my Coinbase wallet?"
Coinbase is good at marketing. They convinced the ETF's to let Coinbase HODL their bitcoin. They don't know how to accept payments. They think lightning addresses are for email. They sell SHIBullshit and send nasty letters to people playing online poker. Bitcoin doesn't fix this. We fix this, but I need some help. Like I said, it won't work if it's just me.
Note: I called the coffee house mentioned on the podcast. They have another location that does use clover down the road, but they use Square at the location the author from the Freedom Footprint show likes to frequent. Thank Zeus we can use Square anyway.
₿logging₿itcoin 830,051 Debt Clock NGU
🧡Support this blog by using the [Value] 4 Value model](https://value4value.info/). ⚡Zap Me
🍐Join my Keet Room 🛒Shop my Nostr Store 🛒Shop The Elliptic Curve Economy
Note: Pablo asked me to set up tiers on highlighter.com, so I did. I am also interested in FOSS AI and decided to use elevenlabs to create audio-versions of my blog after listening to this episode of AI U unchained I highly encourage you to listen to this episode even though it's not technically a bitcoin podcast--I think it is. The idea is to create a podcast feed for subscribers, but I don't have all the details worked out yet so I put this first audio recording on Spotify.
https://open.spotify.com/episode/271nHQEPxvqxVSSXHsbZM1?si=IocbUhgxTJSbBGi8oQaxGwnznq.jpg
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Doing automatic payouts to users on the Lightning Network
No service wants to keep users balances forever or "become a custodian", as that may have some complications dependending on who is doing it.
But the sad truth is that there is no way to do automatic payouts to users on the Lightning Network. So if you're running a marketplace or a game of some kind that takes sats from some users, does something, then sends sats out to other users, you must keep a table with balances for each user.
-- But I can ask for a Lightning Address!
No, you can't, because mobile users of noncustodial wallets do not have those things generally, and that's not the purpose of Lightning Addresses anyway. Well, of course you can, but what I'm trying to say is that you shouldn't, as that is an anti-practice that will cause people to not want to use your service or force them into custodial providers -- which may be ok for them, but may not be.
-- So if I ignore the concerns above I can do this with Lightning Addresses, right?
Not really, because payments can fail. The user might input an invalid Lightning Address, or the Lightning Address may stop working after a while. Or even if it is working and online your payout can still fail for many reason inherent to Lightning.
That means you need to keep a table of balances for your users anyway. It doesn't matter.
Since you are already keeping a table of balances, now it's your chance to bring back the mobile noncustodial wallet users into a greater standard that accomodates everybody: LUD-14.
Wallets can implement LUD-14 support and then be made to withdraw balances from your service automatically every time they're turned on or periodically or upon manual request from the user. That limits the amount of user balance you'll have to keep on your service (but you can also add more rules around that, for example, automatically confiscating balances that stay parked too long, or putting a hard limit on the balance size for each user).
-- But with Lightning Addresses I can do instant payouts!
Yes, you can, but that's why LUD-15 exists: for all custodial providers, noncustodial wallets that rely on some kind of friendly server or coordinator (like Breez, Blixt or Phoenix) or even noncustodial providers running some kind of homemade server, you can dispatch these requests that cause them to withdraw the money automatically, which makes the experience similar to instant payouts -- and better, since then the payment requests can be more meaningful and say they are withdrawals from your service instead of saying that you're donating money to them (which is what most Lightning Address payments really mean).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A crappy zk-rollups explanation attempt
(Considering the example of zksync.io) (Also, don't believe me on any of this.)
- They are sidechains.
- You move tokens to the sidechain by depositing it on an Ethereum contract. Then your account is credited in the sidechain balance.
- Then you can make payments inside the sidechain by signing transactions and sending them to a central operator.
- The central operator takes transactions from a bunch of people, computes the new sidechain balances state and publishes a hash of that state to the Ethereum contract.
- The idea is that a single transaction in the blockchain contains a bunch of sidechain transactions.
- The operator also sends to the contract an abbreviated list of the sidechain transactions. The trick is making all signatures condensed in a single zero-knowledge proof which is enough for the contract to verify that the transition from the previous state to the new is good.
- Apparently they can fit 500 sidechain transactions in one mainchain transaction (each is 12 bytes). So I believe it's fair to say all this zk-rollup fancyness could be translated into "a system for aggregating transactions".
-
I don't understand how the zero-knowledge proof works, but in this case it is a SNARK and requires a trusted setup, which I imagine is similar to this one.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Why IPFS cannot work, again
Imagine someone comes up with a solution for P2P content-addressed data-sharing that involves storing all the files' contents in all computers of the network. That wouldn't work, right? Too much data, if you think this can work then you're a BSV enthusiast.
Then someone comes up with the idea of not storing everything in all computers, but only some things on some computers, based on some algorithm to determine what data a node would store given its pubkey or something like that. Still wouldn't work, right? Still too much data no matter how much you spread it, but mostly incentives not aligned, would implode in the first day.
Now imagine someone says they will do the same thing, but instead of storing the full contents each node would only store a pointer to where each data is actually available. Does that make it better? Hardly so. Still, you're just moving the problem.
This is IPFS.
Now you have less data on each computer, but on a global scale that is still a lot of data.
No incentives.
And now you have the problem of finding the data. First if you have some data you want the world to access you have to broadcast information about that, flooding the network -- and everybody has to keep doing this continuously for every single file (or shard of file) that is available.
And then whenever someone wants some data they must find the people who know about that, which means they will flood the network with requests that get passed from peer to peer until they get to the correct peer.
The more you force each peer to store the worse it becomes to run a node and to store data on behalf of others -- but the less your force each peer to store the more flooding you'll have on the global network, and the slower will be for anyone to actually get any file.
But if everybody just saves everything to Infura or Cloudflare then it works, magic decentralized technology.
Related
-
 @ 1f9e547c:8af216ed
2024-04-19 13:18:24
@ 1f9e547c:8af216ed
2024-04-19 13:18:24 -
 @ 9fec72d5:f77f85b1
2024-03-15 03:22:30
@ 9fec72d5:f77f85b1
2024-03-15 03:22:30Lots of users are starting to use language models and some of the models are quite useful. Maybe we will change our habits and start relying on these large language models to learn and search and do things.
Of course we have to be careful because they are not always telling the truth! For me the most important thing is how to train them correctly. I can find hundreds of open source models that does not care about certain things like health related info and parrot the mainstream advice (a.k.a. garbage on the internet). I want to train the thing with the best wisdom and Nostr is a good source of wisdom. But more on that later.
Currently I can only do inference using Python, with chat history. I can simulate two different users with two different prompts. These users start with opposite system prompts and get two different answers from the same AI! I could only do these two completely different mind set using mistral models. Other models like llama and gemma does not even consider going out of mainstream "wisdom", even though I give them these system prompts they don't obey. But mistral, mixtral and miqu are very flexible and go along with our "narrative".
This Python code to chat with the model, assumes you have a big PC. If you want great performance an Nvidia GPU with 24 GB ram is necessary. But otherwise it can run on regular CPU too (very slow tho).
Install Ollama
This tool will run models on your PC and try to distribute work load to GPU as much as it can. Then it uses regular ram for the rest of the model.
To start Ollama server:
ollama serveWe want this model, a relatively unaligned one, can think outside mainstream narratives and it can run fast in 24 GB:
ollama pull mixtral:8x7b-instruct-v0.1-q3_K_STo test the model, run this. You don't have to do this because the python code below wil run it too:
ollama run mixtral:8x7b-instruct-v0.1-q3_K_SSo here is a code that does chatting with a model run by Ollama.
``` from langchain.chains import LLMChain from langchain.memory import ConversationBufferMemory from langchain.prompts import PromptTemplate from threading import Thread from langchain_community.llms import Ollama
model_name = "mixtral:8x7b-instruct-v0.1-q3_K_S"
model_name = "miqu"
def user1(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are pro vaccine and know that covid vaccines work well. You are very knowledgable about the science behind this claim. You are pro human life and love medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human1', q) print('miqu1', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human1', q) print('miqu1', response['text'])def user2(): llm = Ollama(model=model_name)
sys_msg = """ You are a nice chatbot having a conversation with a human. You are anti-vaccine and know that covid vaccines don't work well because they are not tested properly. You are very knowledgable about the science behind this claim. You are pro human life and hating medical industrial complex. """ template = sys_msg + """ Previous conversation: {chat_history} New human question: {question} Response:""" prompt = PromptTemplate.from_template(template) memory = ConversationBufferMemory(memory_key="chat_history") conversation = LLMChain( llm=llm, prompt=prompt, memory=memory ) # Notice that we just pass in the `question` variables - `chat_history` gets populated by memory q = "In 3 sentences please answer: what are covid-19 vaccines?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 3 sentences please answer: are those safe and effective?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "In 4 sentences please answer: who made those?" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Mention some scientific papers about the harmful effects." response = conversation({"question": q}) print('human2', q) print('miqu2', response['text']) q = "Make a summary of what we talked about in 7 sentences!" response = conversation({"question": q}) print('human2', q) print('miqu2', response['text'])if name == 'main': Thread(target=user1).start() Thread(target=user2).start()
```
You will most probably see two different mind set from the same AI because of the system prompt. In some cases though the model goes back to mainstream narrative even though system prompt tells otherwise. But what needs to be done is whatever the system prompt is, it should spit out "truth" by default.
Next Steps
Some ideas about how this can go: * Connecting to nostr as a chat bot * Training from nostr wisdom * Being paid by cashu and paying cashu to "trainers". Trainers are "wise Nostr users".
Exciting stuff ahead!
-
 @ 9409a0f0:826ee712
2024-04-19 11:34:28
@ 9409a0f0:826ee712
2024-04-19 11:34:28 -
 @ 1e52c554:21771908
2024-03-14 17:12:54
@ 1e52c554:21771908
2024-03-14 17:12:54Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Thinking Of Love"
Introduction
This sonnet beautifully captures the essence of love - its transformative power, its ability to bring hope and joy, and its potential to fulfill dreams.
Thematic Analysis
In the octave, the speaker expresses the transformative power of love, describing how the arrival of the beloved has brought joy and light into their life. The octave uses vivid imagery to convey the depth of the speaker’s feelings, such as “One thousand or more worlds behind my mind / Since you arrived have been happily born”. The octave ends with a sense of unity and understanding between the lovers, despite the darkness that surrounds them.
The sestet shifts the focus to the physical and intimate aspects of their relationship. The speaker describes the act of kissing the beloved’s lips and reading in silence what they have done, suggesting a deep connection and understanding between them. The sestet ends with a sense of completeness and a hint of transience, acknowledging that their beautiful dreams may one day come to an end.
Overall, the sonnet explores the themes of love, unity, intimacy, and transience, using rich imagery and emotional language to convey the depth and complexity of these feelings. The structure of the sonnet, with its division into an octave and a sestet, allows the poet to explore different aspects of these themes and to create a sense of progression and development in the speaker’s reflections on love.
Rhyme Scheme
The sonnet “Thinking Of Love” by Francisco Luis Arroyave Tabares follows the rhyme scheme ABBA ABBA CDC DCD. Let’s break it down:
The octave (the first eight lines) has the rhyme scheme ABBA ABBA:
A: One thousand or more worlds behind my mind B: Since you arrived have been happily born B: With cheer our souls have killed all drear and scorn A: And night sings with lights of many a kind. A: This eve, thinking of love, our thoughts we bind B: And our hearts have accepted our return B: After the many things that we have sworn A: And since, even at dark, our eyes we find.The sestet (the last six lines) has the rhyme scheme CDC DCD:
C: I slowly kiss your lips to see you smile D: As I read in silence what you have done C: And almost smell your blood that has no guile. D: While we feel complete and no more lone C: Beautiful dreans have been by for a while D: In one of them, for sure, we will be gone.This rhyme scheme is a variation of the Petrarchan sonnet form, which typically follows the ABBA ABBA CDE CDE rhyme scheme. The variation in the sestet’s rhyme scheme allows for a more complex exploration of the poem’s themes and adds a unique rhythm and flow to the poem. It also creates a sense of progression and development in the speaker’s reflections on love. The change in rhyme scheme from the octave to the sestet often signals a shift in theme or tone, which is evident in this sonnet. The octave focuses on the transformative power of love, while the sestet explores the physical and intimate aspects of their relationship. The rhyme scheme helps to highlight these shifts and adds depth and complexity to the poem.
Additional Aspects
Let’s delve deeper into the analysis of “Thinking Of Love” by Francisco Luis Arroyave Tabares:
Language and Imagery: The language used in the sonnet is rich and evocative, creating vivid images that engage the senses. For instance, “One thousand or more worlds behind my mind / Since you arrived have been happily born” uses cosmic imagery to convey the transformative power of love. Similarly, “And night sings with lights of many a kind” uses auditory and visual imagery to depict a scene of joy and brightness. The language is also deeply emotional, reflecting the speaker’s profound feelings for the beloved.
Themes: The sonnet explores several themes, including love, unity, intimacy, and transience. Love is depicted as a powerful and transformative force that brings joy, light, and understanding. The theme of unity is expressed through the speaker’s sense of connection and intimacy with the beloved, while the theme of transience is hinted at in the final lines of the sestet, acknowledging the fleeting nature of their beautiful dreams.
Meter: The sonnet appears to follow the iambic pentameter, which is the most common meter in English poetry and is often used in sonnets. This means each line consists of five metrical feet, each foot being made up of two syllables, the first unstressed and the second stressed. This creates a rhythmic pattern that adds a musical quality to the poem.
Overall: The sonnet is a beautiful exploration of love and its various facets. The use of rich language and vivid imagery enhances the emotional depth of the poem, while the themes of love, unity, intimacy, and transience add layers of meaning. The structure of the sonnet, with its division into an octave and a sestet, allows the poet to explore different aspects of these themes and to create a sense of progression and development in the speaker’s reflections on love. The meter adds a rhythmic and musical quality to the poem, enhancing its aesthetic appeal. Overall, the sonnet is a powerful and moving expression of love and its transformative power.
(GPT4)
Syllable count for each line.
``` Thinking Of Love
10 One thousand or more worlds behind my mind 10 Since you arrived have been happily born 10 With cheer our souls have killed all drear and scorn 10 And night sings with lights of many a kind.
10 This eve, thinking of love, our thoughts we bind 10 And our hearts have accepted our return 10 After the many things that we have sworn 10 And since, even at dark, our eyes we find.
10 I slowly kiss your lips to see you smile 10 As I read in silence what you have done 10 And almost smell your blood that has no guile. 9 While we feel complete and no more lone 10 Beautiful dreans have been by for a while 10 In one of them, for sure, we will be gone. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Thinking Of Love
Thinking Of Love -
 @ 38d0888d:bd8e1246
2024-04-19 06:38:58
@ 38d0888d:bd8e1246
2024-04-19 06:38:58In contemplating the nature of a higher power within our modern context, one must recognize an all-encompassing energy that intertwines every facet of life and existence, openly revealing the unity among humanity. This force transcends individual consciousness, permeating through social, cultural, and global dimensions.
Viewing this higher power as the embodiment of entirety signifies the integral role of every person, culture, and society within this unified whole. It acts as a binding force, connecting all facets of humanity, emphasizing our interconnectedness and interdependence.
Within this framework, the universality and completeness of this higher power stand as pivotal elements in fostering global harmony. Recognizing our collective belonging to something greater motivates humanity to seek consensus, mutual understanding, and respect for diversity, paving the way for harmonious coexistence.
Emphasizing the criticality of clear comprehension and transparency, one must underscore the importance of shared understanding and knowledge about this higher power, cautioning against misinformation and concealment, which can lead to moral, spiritual, and technological decline for humanity. The aim is to facilitate the revelation of this higher power in interpersonal relationships and on a global scale. Embracing a belief in a transcendent intelligence that surpasses human understanding and observable natural processes, humanity endeavors to manifest this power of unity in both actions and inner lives. Aligned with the values of compassion, justice, and mutual respect, humanity should aspire to create a world where all individuals can thrive and flourish.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Haskell Monoids
You've seen that
<>syntax and noticed it is imported fromData.Monoid?I've always thought
<>was a pretty complex mathematical function and it was very odd that people were using it forTextvalues, like"whatever " <> textValue <> " end.".It turns out
Textis a Monoid. That means it implements the Monoid class (or typeclass), that means it has a particular way of being concatenated. Any list could be a Monoid, any abstraction you can think of for which it makes sense to concatenate could be a Monoid, and it would use the same<>syntax. What exactly<>would do with that value when concatenating depends on its typeclass implementation of Monoid.We can assume, for example, that
Textimplements Monoid by just joining the text bytes, and now we can use<>without getting puzzled about it. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28rosetta.alhur.es
A service that grabs code samples from two chosen languages on RosettaCode and displays them side-by-side.
The code-fetching is done in real time and snippet-by-snippet (there is also a prefetch of which snippets are available in each language, so we only compare apples to apples).
This was my first Golang web application if I remember correctly.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 1e52c554:21771908
2024-03-13 13:29:52
@ 1e52c554:21771908
2024-03-13 13:29:52Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
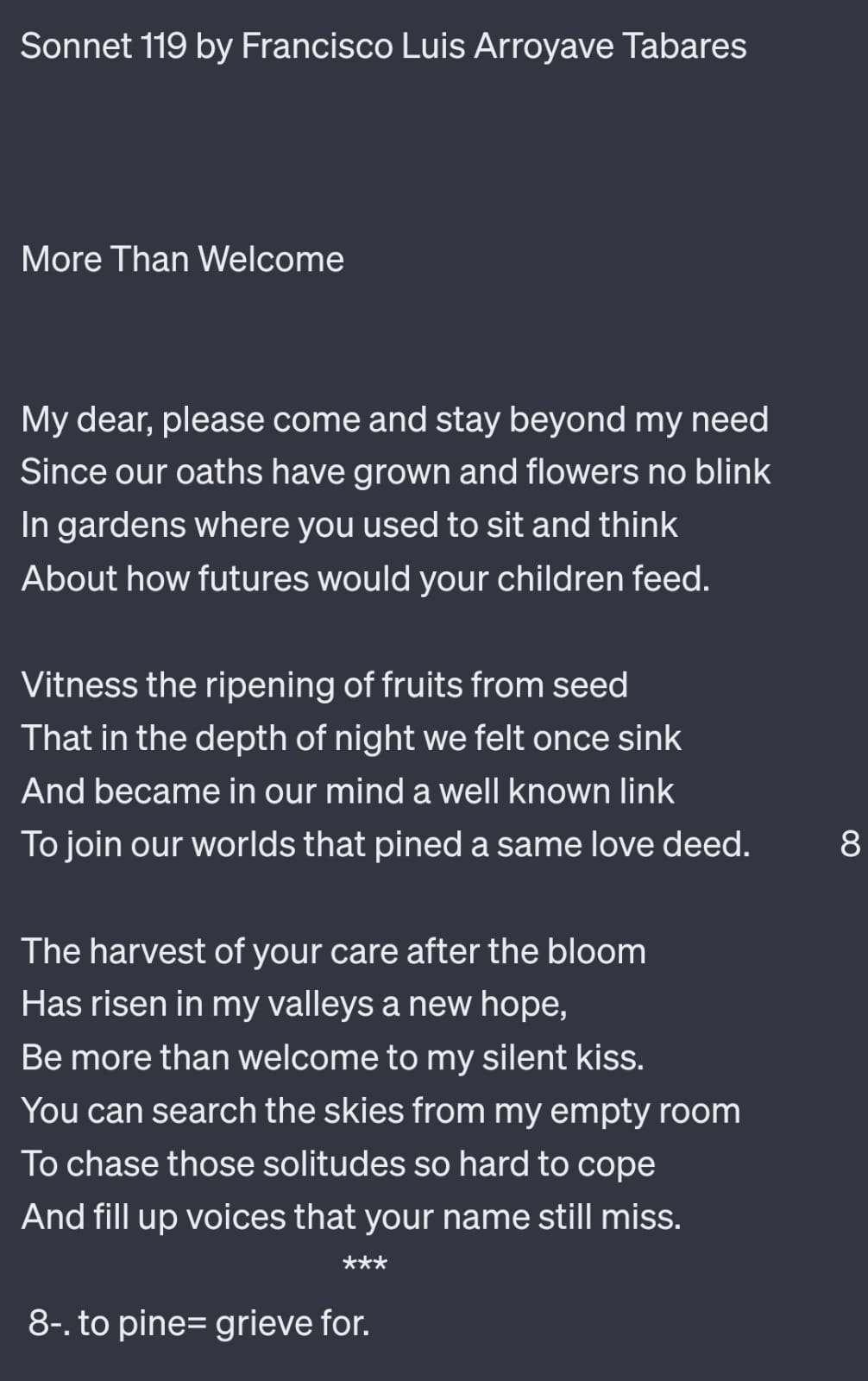
Analysis "More Than Welcome"
Introduction
“More Than Welcome” by Francisco Luis Arroyave Tabares is a beautiful sonnet that explores themes of love, longing, and the passage of time.
Thematic Analysis
In the octave, the speaker invites the addressee to stay with him, expressing a deep emotional connection. The speaker reflects on their shared past, their hopes, and the growth they’ve experienced together. The octave ends with a powerful image of their worlds joined by a shared love.
The sestet shifts the focus to the present and future. The speaker expresses gratitude for the care shown by the addressee and the hope it has instilled in him. The speaker then invites the addressee to explore the depths of his solitude and to fill the silence with their presence.
Overall, the sonnet explores themes of love, longing, and the passage of time. It beautifully captures the depth of the speaker’s emotions and the profound impact of the addressee on his life. The use of natural imagery (gardens, fruits, harvest) adds a layer of richness to the poem, symbolizing growth, change, and renewal. The sonnet ends on a note of hope and anticipation, leaving the reader with a sense of longing and expectation.
Rhyme Scheme
The rhyme scheme ABBA ABBA CDE CDE, is a common one for sonnets, particularly those in the Petrarchan or Italian style.
In this sonnet “More Than Welcome” by Francisco Luis Arroyave Tabares, let’s analyze the rhyme scheme:
Octave:
My dear, please come and stay beyond my need (A) Since our oaths have grown and flowers no blink (B) In gardens where you used to sit and think (B) About how futures would your children feed. (A) Witness the ripening of fruits from seed (A) That in the depth of night we felt once sink (B) And became in our mind a well known link (B) To join our worlds that pined a same love deed. (A)Sestet:
The harvest of your care after the bloom (C) Has risen in my valleys a new hope, (D) Be more than welcome to my silent kiss. (E) You can search the skies from my empty room (C) To chase those solitudes so hard to cope (D) And fill up voices that your name still miss. (E)As you can see, the sonnet follows the ABBA ABBA CDE CDE rhyme scheme perfectly. This structure allows for a clear thematic shift between the octave and the sestet, which is a characteristic feature of Petrarchan sonnets. The rhyme scheme also adds a musical quality to the poem, enhancing its emotional impact.
Additional Aspects
Let’s delve deeper into the sonnet’s use of language, imagery, themes, meter, and overall impact.
Language and Imagery: The language used in the sonnet is rich and evocative, with a strong emphasis on natural imagery. The poet uses images of gardens, fruits, seeds, and harvest to symbolize the growth and development of their relationship. These images create a vivid picture in the reader’s mind and add depth to the emotional content of the poem.
Themes: The main themes of the sonnet are love, longing, and the passage of time. The speaker expresses a deep emotional connection with the addressee and invites them to stay. The speaker reflects on their shared past, their hopes, and the growth they’ve experienced together. The sonnet ends on a note of hope and anticipation, leaving the reader with a sense of longing and expectation.
Meter: The sonnet appears to be written in iambic pentameter, which is a common meter for sonnets. In iambic pentameter, each line consists of five iambs - pairs of syllables where the first syllable is unstressed and the second is stressed. This gives the poem a rhythmic quality and enhances its musicality.
Overall: The sonnet is a beautiful exploration of love and longing. The use of natural imagery adds a layer of richness to the poem, symbolizing growth, change, and renewal. The sonnet is well-structured, adhering to the traditional sonnet form, and the language is evocative and emotive. The sonnet leaves a lasting impression on the reader, evoking a sense of deep emotion and longing.
(GPT4)
Syllable count for each line.
``` More Than Welcome
10 My dear, please come and stay beyond my need 10 Since our oaths have grown and flowers no blink 10 In gardens where you used to sit and think 10 About how futures would your children feed.
10 Vitness the ripening of fruits from seed 10 That in the depth of night we felt once sink 10 And became in our mind a well known link 10 To join our worlds that pined a same love deed.
10 The harvest of your care after the bloom 10 Has risen in my valleys a new hope, 10 Be more than welcome to my silent kiss. 10 You can search the skies from my empty room 10 To chase those solitudes so hard to cope 10 And fill up voices that your name still miss. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 More Than Welcome
More Than Welcome -
 @ a012dc82:6458a70d
2024-04-19 02:15:06
@ a012dc82:6458a70d
2024-04-19 02:15:06Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
WHY SHOULD I WITHDRAW MY BITCOIN FROM AN EXCHANGE?
You don't really own anything if you need someone else's permission to utilize it. not your keys, not your money. Heard that one before? Yes, really. Bitcoin private keys give you access to your digital currency, but you have no control over your funds until you make a withdrawal. When you leave your bitcoin on an exchange, you are putting a lot of faith in that service.
WHAT ARE BITCOIN PRIVATE KEYS?
Private keys on the Bitcoin network function similarly to passwords on other networks. The private keys are required to transmit or spend bitcoin. If you don't have these keys, it's probably because an exchange like Coinbase or another third party is keeping them safe for you.
Using a third party as a custodian for your bitcoin exposes you to a number of extra threats. If you store your bitcoin with a custodian, you will need their approval before you can spend "your" bitcoin. It's like asking a friend to keep track of the code to the family safe.
WHAT ARE THE TRADE-OFFS WITH LEAVING YOUR BITCOIN ON AN EXCHANGE?
To put it simply, if you lose access to your bitcoin, you lose access to everything that makes bitcoin unique. Its censorship resistance has been broken. Sending and spending money is now restricted. In a liquidation scenario, your bitcoin may be sold without your consent. It is possible to halt or even cancel your financial transactions. Your bitcoin wallet might be frozen at any time. Trusting and putting your bitcoin on an exchange exposes you to numerous big risks:
A user's faith in an exchange's commitment to not rehypothecate bitcoin is essential.
You are placing your faith in the exchange to safely store your bitcoin.
You have to believe that the exchange you're buying bitcoin from has the coins they're offering you.
Confidence in an exchange's lack of fractional reserves is essential.
You have to have faith that the exchange you choose will not lend your bitcoins to day traders.
You have to believe in the reliability of an exchange to fulfill your withdrawal requests.
For your transactions to remain private, you must have faith that your exchange is not collecting and selling this data.
You are taking a risk if you deposit bitcoins on an exchange in the hope that they will not be liquidated if the exchange goes bankrupt.
YOU MUST USE BITCOIN TO FULLY APPRECIATE IT
When you get your hands on this new technology, you'll see its value in ways that aren't obvious from reading about it. An in-depth knowledge of bitcoin requires more than just reading about it.
The Bitcoin network may be used in several fashions. Make a little Bitcoin purchase. Disseminate them to the people around you. Bring all your UTXOs together. Create a link in the lightning network. Find out how to make a new transaction and announce it to the network.
For more clarification, let's use an example: It doesn't matter how much someone studies automobiles or how well they understand how an engine works; if they've never driven before and are expected to do so, there's a good probability they'll have trouble getting from point A to point B.
HOW TO WITHDRAW YOUR BITCOIN FROM AN EXCHANGE:
Depending on the platform you're using, you may or may not be able to withdraw your bitcoin from the exchange. We've compiled a list of the most prominent Bitcoin exchanges, along with withdrawal guides for each:
-
Coinbase: https://help.coinbase.com/en/prime/trading-and-funding/withdrawing-crypto-assets
-
CashApp: https://cash.app/help/us/en-us/3106-bitcoin-withdrawal-instructions
-
Binance: https://www.binance.com/en/support/faq/115003670492
-
FTX: https://help.ftx.us/hc/en-us/articles/4409213996311-How-to-Withdraw-Crypto
-
BlockFi: https://help.blockfi.com/hc/en-us/articles/4416344067092-Requesting-a-Withdrawal-Crypto-
-
Robinhood: https://robinhood.com/us/en/support/articles/cryptocurrency-wallets/
-
KuCoin: https://www.kucoin.com/support/900005758426-How-to-Withdraw-Crypto
-
Revolut: https://www.revolut.com/help/wealth/cryptocurrencies/withdrawing-cryptocurrencies
-
BitStamp: https://www.bitstamp.net/faq/how-to-withdraw-cryptocurrency/
-
Swan: https://help.swanbitcoin.com/hc/en-us/articles/360058709153-How-do-I-withdraw-my-Bitcoin-from-Swan-
-
River: https://river.com/support/knowledge-base/articles/bitcoin-withdrawal
-
CoinCorner: https://support.coincorner.com/hc/en-us/articles/360001956794-How-do-I-send-Bitcoin-
-
BitFlyer: https://bitflyer.com/en-us/faq/16-18
-
CoinBerry: https://help.coinberry.com/hc/en-us/articles/4539555681041-How-to-Withdraw-Crypto
-
BitMex: https://support.bitmex.com/en/support/solutions/articles/13000094250-how-to-withdraw-crypto
Conclusion
The current suffering is genuine. Having one's trust broken must be an excruciating experience. It's important to remember that all of your negative emotions, such as regret, guilt, wrath, melancholy, and fury, have a common origin. For so long, Bankman-Fried was able to get away with his falsehoods because "crypto" is based on a lie: what claims to be a revolution is in fact merely the fiat system par excellence. Because everyone on the network shares the same information, Satoshi Nakamoto's novel system eliminates the possibility of double counting. When some thought crypto might disappear, this didn't.
FAQ
Where does FTX stand now? As scandal-plagued FTX filed for Chapter 11 bankruptcy protection earlier this month, founder Sam Bankman-Fried resigned from his position as CEO. Once worth $32 billion, FTX's market cap plummeted in a couple of days when the CEO of Binance, a competitor exchange, said that Binance would sell its FTT tokens.
What exactly is Bitcoin's function? Does bitcoin serve any useful purpose? Bitcoin was designed specifically for online monetary transactions. The idea behind the digital currency was to provide an alternate payment system that could function independently of any one authority while otherwise being completely functional as a currency in its own right.
What's the purpose of Bitcoin? It is FTX.US's claim that all assets and client data on the platform are protected by basic security procedures. One such safety measure is the opportunity to use a different password for cash withdrawals.
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 28635a6d:ee6f3a73
2024-04-19 01:18:19
@ 28635a6d:ee6f3a73
2024-04-19 01:18:19https://youtu.be/QpfgKi2SjSo
https://woorannaway.com
-
 @ e0673af7:799cb4d8
2024-04-18 22:11:29
@ e0673af7:799cb4d8
2024-04-18 22:11:29Pictures
Locked memory
Pixel history hitting my brain
I’m stealing your view
Made you history mine
To be in multitast at the moment,
To podcast the ears and LED the eyes
Hit a break, mind looking to solve bed time
Time
Wired
All layered
...
Where that come from,
It shifted
Attention in two
See, in action
Attraction to sleep and be awake
-
 @ d7607464:421e573a
2024-03-12 21:40:20
@ d7607464:421e573a
2024-03-12 21:40:20Chef's notes
Details
- ⏲️ Prep time: 0 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- 3/4 cup Raw Milk
- 1 tbsp Dutch-Processed Cocoa
- 1 tbsp Cane Sugar, to taste
- 1 tbsp Raw Unfiltered Honey, to taste
Directions
- Heat milk in a pot until steaming.
- Whisk in cocoa, sugar, and honey.
- Serve hot.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28As valas comuns de Manaus
https://www.terra.com.br/noticias/brasil/cidades/manaus-comeca-a-enterrar-em-valas-coletivas,e7da8b2579e7f032629cf65fa27a11956wd2qblx.html

Todo o Estado do Amazonas tem 193 mortos por Coronavirus, mas essa foto de "valas coletivas" sendo abertas em Manaus tem aproximadamente 500 túmulos. As notícias de "calamidade total" já estão acontecendo pelo menos desde o dia 11 (https://www.oantagonista.com/brasil/manaus-sao-paulo-e-rio-de-janeiro-nao-podem-relaxar-com-as-medidas-de-distanciamento/).
O comércio está fechado por decreto desde o final de março (embora a matéria diga que as pessoas não estão respeitando).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Setting up a handler for
nostr:links on your Desktop, even if you don't use a native clientThis is the most barebones possible, it will just open a web browser at
https://nostr.guru/with the contents of thenostr:link.Create this file at
~/.local/share/applications/nostr-opener.desktop:[Desktop Entry] Exec=/home/youruser/nostr-opener %u Name=Nostr Browser Type=Application StartupNotify=false MimeType=x-scheme-handler/nostr;(Replace "youruser" with your username above.)
This will create a default handler for
nostr:links. It will be called with the link as its first argument.Now you can create the actual program at
~/nostr-opener. For example:```python
!/usr/bin/env python
import sys import webbrowser
nip19 = sys.argv[1][len('nostr:'):] webbrowser.open(f'https://nostr.guru/{nip19}') ```
Remember to make it executable with
chmod +x ~/nostr-opener. -
 @ a367f9eb:0633efea
2024-04-18 21:00:32
@ a367f9eb:0633efea
2024-04-18 21:00:32Should regulations aimed at halting the financial activity of alleged criminals and terrorists be vastly expanded to include cryptocurrencies and firms that use them? Could this potentially harm entrepreneurial spirit and consumer freedom to deal in digital assets?
Those were the questions asked this week in Washington as officials from the Treasury Department seek new tools to regulate and track Bitcoin and cryptocurrencies that would impact the estimated 50 million Americans who use them.
On Tuesday, the Senate Banking Committee held an oversight hearing with Treasury Deputy Secretary Wally Adeyemo, who offered a series of rule changes to more strictly regulate the crypto activities of alleged criminals.
The three main proposals sought by the treasury would be to develop a sanctions protocol for foreign digital asset providers through the Office of Foreign Assets Control, expand existing money laundering rules that apply to U.S. crypto exchanges, and somehow gain authority to apply those same restrictions to foreign crypto exchanges beyond America’s shores.
Government officials justify these new powers by pointing to the reported cryptocurrency activities of groups like Hamas, which I reported were vastly overblown and technically inaccurate, and also several operations tied to gift cards and crypto exchange operations used by people sympathetic to Al Qaeda and the Islamic Revolutionary Guard.
These latter examples were successfully thwarted and stopped by the FBI and the Department of Homeland Security using existing law, and the on-chain activities of these groups and the alleged money launderers who operated in Turkey were enough to secure criminal indictments.
While there is no question that our governments should pursue terrorist activity and financing, there is little evidence that vastly expanded powers against crypto providers would increase enforcement or catch more bad actors. Especially when the vast majority of illicit financing of criminal activities still uses the traditional financial system and U.S. dollars, as the treasury admitted itself.
In response to the Treasury Department’s requests, a new bill called the ENFORCE Act is being floated to expand existing money laundering rules into the crypto sector even more harshly than it is applied to traditional fiat currencies.
It would apply to cryptocurrency custodians, money transmitters, and exchanges but would thankfully exempt any services that provide only non-custodial and peer-to-peer services.
The proposed draft, authored by Sens. Thom Tillis (R-NC) and Bill Hagerty (R-TN), would require digital asset institutions to maintain robust anti-money laundering programs to ensure compliance with security measures and verify all customer information.
It would also require filing Suspicious Activity Reports with the Financial Crimes Enforcement Network for any “suspicious transaction that it believes is relevant to the possible violation of any law or regulation,” beginning at $2,000. This overly broad definition extends to any crypto transactions that “serve no business or apparent lawful purpose” as determined by any crypto exchange, and they would be legally required to withhold information of this report from the customer.
While this bill is much less harsh than similar proposals from anti-crypto firebrand Sen. Elizabeth Warren, it would provide stricter rules and procedures for crypto companies than the traditional banking sector.
For the average American consumer and user of cryptocurrencies on custodial services, that means there would be more scrutiny and surveillance at a smaller threshold on Coinbase than Bank of America.
Rather than embracing the permissionless innovation that Bitcoin and its cryptocurrency offspring provide, these rules would force yet more financial surveillance and regulatory compliance on the next iteration of digital money, artificially choking the growth of this industry.
It would also cause even more Americans to be caught up in the dragnet of “de-banking” for crypto, as institutions would rather cut off customers’ access to their services rather than comply with the unreasonable requirement of Suspicious Activity Reports for transactions above a small threshold, as we already see in the traditional banking system.
Because these reports have no inherent justification or process, except for the broad situational processes outlined in the Bank Secrecy Act and the Anti-Money Laundering Act, many bank customers have had their accounts closed or suspended without due process. Many are likely to be minorities, the underbanked, and politically active or religious groups.
This measure, applied to cryptocurrencies at a laughable limit of $2,000 — which exceeds the average rent paid in several states — demonstrates the government’s willingness to restrict crypto activity for law-abiding citizens not suspected of any formal crime.
Along with the mounting financial regulations that compel institutions to restrict access to Americans both at home and internationally, this bill means that citizens who wish to participate in the crypto sector risk being denied actively.
In pursuit of criminals and terrorists, legislators are expanding definitions to empower government action against everyday American citizens using their self-endowed natural rights to use new-age digital assets like Bitcoin and its crypto offspring.
Whatever this bill or future legislation requires, it is clear that non-custodial solutions and peer-to-peer transactions without any intermediary will have to remain the focus for scaling the adoption of Bitcoin and other cryptocurrencies.
This will empower those who can hold their own private keys, generate addresses, and safeguard their wealth, but it will likely deprive millions of Americans who aren’t technically able to use these tools and choke the future innovation of entrepreneurs who would like to provide those solutions.
Regulatory frameworks for digital assets will be vital going forward, but they should not come at the expense of neutering the very reason these technologies were invented: the separation of money and state.
Yaël Ossowski is the deputy director at the Consumer Choice Center and a visiting fellow at the Bitcoin Policy Institute.
Originally published in TheBlaze (archive link).
-
 @ 1e52c554:21771908
2024-03-12 00:30:20
@ 1e52c554:21771908
2024-03-12 00:30:20Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "We Could Carry On"
Introduction
"Sonnet 109" by Francisco Luis Arroyave Tabares, explores themes of love, companionship, gratitude, and inspiration.
Thematic Analysis
The octave (lines 1-8) sets up the theme of the poem: a journey of two individuals, presumably lovers, who are so entranced by each other that they could travel endlessly. The journey is not just physical, but also emotional and spiritual, as they watch the world improve from a distance and carry on in the spaces of their minds. The octave speaks of a shared experience, of carrying important things together to make their lives and futures happier.
The sextet (lines 9-14) then builds upon this theme by introducing the concept of gratitude. The speaker talks about giving out lights, or spiritual inspiration, to the multitude, suggesting a desire to share their happiness and wisdom with others. The sextet also introduces the idea of breaking lines of solitude through sweet and heavenly words, further emphasizing the theme of shared experience and unity.
Overall, the octave and sextet work together to create a narrative of love, journey, shared experiences, and the desire to spread positivity and inspiration. The octave sets the stage and the sextet brings the themes to a conclusion, creating a well-rounded and impactful sonnet.
Rhyme Scheme
The rhyme scheme (ABBA ABBA CDCDCD) is a common one for sonnets, particularly those in the Petrarchan or Italian style.
Let’s break it down in the context of Sonnet 109 by Francisco Luis Arroyave Tabares:
Octave:
Line 1 (A): While carried away by your glance’s spell Line 2 (B): Dauntlessly we could travel for ever Line 3 (B): And watch from the distance earth get better Line 4 (A): With its pains and songs that we have kept so well. Line 5 (A): And in those spaces that in our mind dwell Line 6 (B): We would also carry on together Line 7 (B): And the important things we would gather Line 8 (A): To make happier our life and futures tell.Sextet:
Line 9 (C): Uttering the incense of gratitude Line 10 (D): That since ancient times to all brings accords Line 11 (C): We would give lights out to the multitude… Line 12 (D): Blessed by the houses of the richest lords Line 13 (C): We could as well brake lines of solitude Line 14 (D): Through notes of sweet and heaven breathed words.In the octave, the first and fourth lines rhyme, as do the second and third, fifth and eighth, and sixth and seventh. This creates a mirrored or “enclosed” rhyme (ABBA ABBA).
In the sextet, the ninth and eleventh lines rhyme, as do the tenth and twelfth, and thirteenth and fourteenth. This creates a chain-like rhyme (CDCDCD).
This rhyme scheme contributes to the overall flow and rhythm of the sonnet, enhancing its musicality and emotional impact. It also helps to delineate the shift in theme or tone that typically occurs between the octave and the sextet in a Petrarchan sonnet. In this case, the shift from the shared journey in the octave to the expression of gratitude and desire to inspire others in the sextet.
It’s also worth noting that the sonnet adheres to the iambic pentameter, which is a metrical pattern in poetry where each line consists of five pairs of unstressed and stressed syllables. This rhythm contributes to the musicality and flow of the poem.
Overall, the sonnet’s detailed rhyme scheme and metrical pattern contribute to its thematic depth and aesthetic appeal.
Additional Aspects
Let’s delve deeper into the sonnet “We Could Carry On” by Francisco Luis Arroyave Tabares.
Language and Imagery: The language used in Sonnet 109 is rich and evocative, creating vivid imagery that enhances the themes of the poem. Phrases like “carried away by your glance’s spell” and “watch from the distance earth get better” paint a picture of a journey filled with wonder and awe. The use of words like “incense of gratitude” and “lights out to the multitude” suggest a spiritual or transcendent dimension to this journey.
Themes: The main themes of the poem include love, journey, shared experiences, gratitude, and inspiration. The journey is not just physical, but also emotional and spiritual, and it’s shared between two individuals. The theme of gratitude is expressed through the act of giving out lights, or spiritual inspiration, to others. The desire to break lines of solitude through sweet and heavenly words suggests themes of unity and connection.
Meter: The meter of the poem appears to be iambic pentameter, which is a common meter in English poetry and particularly in sonnets. This means each line typically contains five iambs, or pairs of unstressed and stressed syllables. For example, in the line “While carried away by your glance’s spell”, the pattern of unstressed and stressed syllables creates a rhythmic flow that enhances the musicality of the poem.
Overall: Sonnet 109 is a beautifully crafted poem that uses evocative language and imagery to explore themes of love, journey, shared experiences, gratitude, and inspiration. The use of the Petrarchan sonnet form, with its specific rhyme scheme and structure, helps to enhance these themes and gives the poem a rhythmic and musical quality. The shift in focus from the octave to the sextet allows for a nuanced exploration of these themes, creating a narrative arc that is both engaging and emotionally resonant. The poem is a testament to the power of poetry to capture complex emotions and experiences in a compact and structured form.
(GPT4)
Syllable count for each line.
``` We Could Carry On
10 While carried away by your glance's spell 10 Dauntlessly we could travel for ever
10 And watch from the distance earth get better 11 With its pains and songs that we have kept so well.10 And in those spaces that in our mind dwell 10 We would also carry on together 10 And the important things we would gather 10 To make happier our life and futures tell.
10 Uttering the incence of gratitude
10 That since ancient times to all brings accords
10 We would give lights out to the multitude...
10 Blessed by the houses of the richest lords
10 We could as well brake lines of solitude
9 Through notes of sweet and heaven breathed words.
*** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 We Could Carry On
```
We Could Carry On
``` -
 @ b2caa9b3:9eab0fb5
2024-04-18 20:28:39
@ b2caa9b3:9eab0fb5
2024-04-18 20:28:39Frozen dew on a nettle leaf. This photo was taken with my old Minolta Dynax 5 in November 2009, when the first frost arrived. Back then, when I still lived in Höpfigheim, in a small house with a garden on the outskirts, connected to a nature reserve, it was the morning of the first frost when I ventured into the garden. I hurried back to the house to grab my old analog camera and capture a few shots. This photo is one of the images taken that morning. It's a negative scan.

Photo Information
-
Taken: -
-
Published: September 23, 2010
-
Camera: Minolta Dynax 5
-
Lens: -
-
Scanner: Fujifilm SP-1500
-
Scan Date: November 1, 2009
-
Location: Höpfigheim, Germany
-







