-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 97c70a44:ad98e322
2023-08-17 22:05:57
@ 97c70a44:ad98e322
2023-08-17 22:05:57By an accident of history, I have been knee-deep for the last week or two in several NIPs related to encrypted DMs and group chat. The accident is my proposal for encrypted groups — which will help me turn Coracle into something approximating a replacement for Facebook, rather than Twitter.
In order to make that happen though, a few things need to happen first. I need a better way to encrypt messages without leaking metadata, and (un)fortunately I'm no cryptographer. It's well known that NIP 04 has a number of issues, and there have been several proposals to fix it since as early as October 2022. Building on that foundation would be a waste of time.
My purpose in this post is to outline the problems with NIP 04 as it stands, and sketch out for you some possible solutions applicable not only to DMs, but to other encrypted use cases.
NIP 04 Considered Harmful
It's pretty well-known that nostr DMs leak metadata. What this means is that when you send a DM to someone else, anyone can see:
- Who you are
- Who you sent a message to
- When you sent the message
- How big the message was
And, of course, vice versa. Now, I personally don't take the cyanide pill on this like some do. DMs in centralized social platforms are far less private even than this, since the platform can read them anytime they want, share them with law enforcement, and potentially leak them to the entire world. It's my opinion that if applications were designed with the above properties in mind, it would be possible to gamify DMs, making metadata leakage a feature rather than a bug. Of course, no one has designed such a thing, so maybe it's a moot point.
The much bigger problem, as I learned last week, has to do with the cryptography used in NIP 04 (and several other places, including private mute lists and app-specific data). Here's a quote from Paul Miller's very helpful explanation:
- Unhashed ECDH exposes some curves to Cheon's attack 1, which allows an attacker to learn private key structure when doing continuous diffie-hellman operations. Hashing converts decisional oracle into a computational oracle, which is harder.
- CBC IVs should not only be unrepeatable, they must be unpredictable. Predictable IV leads to Chosen Plaintext Attack. There are real exploits.
- CBC with reused key has 96-bit nonces and loses 6 bits of security for every magnitude. 10**4 (10K) messages would bring archive security of the scheme to 72 bits. 72 bits is very low. For example, BTC has been doing 2^67 hashes/sec as per early 2023. Advanced adversaries have a lot of resources to break the scheme
- CBC has continuously been exploited by Padding Oracle attack. We can't expect all implementations to have proper padding check
- AES was modeled as ideal cipher. Ideal ciphers don't care about non-random keys. However, AES is not an ideal cipher. Having a non-IND key, as in NIP4, exposes it to all kinds of unknown attacks, and reducing security of overall scheme
There is a lot going on here, very little of which I (and likely you) understand. But the really horrifying takeaway for me is in items 1 and 3. If you read it carefully, you'll notice that the more times you use your private key to encrypt data using NIP 04's encryption scheme, the easier it is for an attacker to brute-force your key.
I want to be careful not to overstate this — I don't think this means that everyone's private key is compromised; it would require many thousands of signatures to meaningfully reduce the security of your key. But it does mean that NIP 04's days are numbered — and if we don't replace it, we have a real existential threat to the entire protocol on our hands.
So much for motivation to put NIP 04 to rest. Where do we go from here?
The lay of the land
There are a few different components to making private messages work (whether we're talking about DMs or encrypted groups).
- Encryption scheme
- Explicit metadata hiding
- Implicit metadata hiding
- Transport and deliverability
- Identity and key exchange
Each of these components needs to be solved in order to create a robust messaging system on nostr.
Encryption scheme
As mentioned above, NIP 04 is borked. Luckily, there are a few folks in the nostr dev community who know a thing or two about encryption, most notably Paul Miller. Way back in May, Paul proposed a new encryption scheme based on his implementation of XChaCha20, which is the same algorithm used by SMP (more on that below).
To move the proposal forward, I created a different PR with some edits and adjustments, which is very near to being merged. The implementation already exists in nostr-tools, and there are PRs out for nos2x and Alby as well.
Explicit metadata hiding
As mentioned above, normal nostr messages share lots of information publicly, even if the content is encrypted, including:
- Kind
- Created timestamp
- Tags (topics, mentions, recipients, etc)
- Message size
- Author
Private messages have to hide this information, at the very minimum.
Implicit metadata hiding
The above level of security should be enough for most use cases. But it definitely doesn't get us to total secrecy yet. Some additional metadata includes:
- Client fingerprinting
- Relay selection for publishing and queries
- IP address collection
- First seen timestamp
- Identification of users by AUTH
- Correlation of the event with other messages sent/received during a session
These issues are much harder to solve, because they are part of the process of delivering the message, rather than just constructing it. These issues can be mitigated to some extent by using TOR, proxying connections with relays, using short-lived connections, randomizing publish time, and careful selection of trusted relays. But all of these are only techniques to reduce exposure, and require a prescriptive protocol to wrap them all up into a cohesive whole.
Transport and deliverability
In my view, the key feature of nostr that makes it work is relays. Relays provide storage redundancy and heterogeneity of purpose with a common interface shared by all instances. This is great for censorship resistance, but everything comes with a tradeoff.
Publishing notes is sort of like hiding easter eggs. If you want a kid to be able to find an egg, you have to put it somewhere they'll look for it. Putting an egg on the roof does not constitute "hiding" it, at least in a way consistent with the spirit of the game.
Historically, notes have been broadcast to whatever relays the user or client selects, without regard with someone else's preferences, resulting in apparently missing notes when author and recipient don't share a relay.
This problem has been partly solved by NIP 65, which encourages clients to publish notes where the recipient will look for them. There is some guesswork involved in selecting good relays, but the process is fairly straightforward for direct messages and group chats.
The situation can be improved further by DM-specific signaling, like what @fiatjaf has suggested as an addition to NIP 65. A user could then run his own relay that accepts messages from anyone, but only serves messages to himself. This would be the only relay well-behaved clients would ever write encrypted messages to, improving both privacy and deliverability.
Variants of this could also work for encrypted groups. For small groups, the same relay hints could be used as with DMs, and for larger groups with key sharing the admin could set up a dedicated relay for the group which members would write to.
This also creates a potential affordance for querying of encrypted events. If a relay is highly trusted, it could be added as a member to an encrypted group, gaining the ability to decrypt events. It could then receive REQ messages for those events, filter based on the encrypted content, and serve the encrypted version. This could greatly improve performance for larger groups where downloading all events isn't feasible.
Identity and key exchange
One dimension of privacy that deserves its own section is identity and key exchange. In nostr, this is simpler than in other protocols because in nostr your pubkey is your username. Arguably, this is a flaw that will need to be solved at some point, but for now it means that we get to skip a lot of the complexity involved with binding a name to a key.
However, the problem is still relevant, because one effective way to improve privacy is through key exchange. In the case of DMs, it would be nice to be able to request an alias key from someone you want to communicate with in order to hide the only piece of metadata that has to remain on a message in order to deliver it, that is, the recipient.
There's a lot of good stuff about this problem in the Messaging Layer Security protocol. The author of 0xChat has also put together a draft spec for executing simple key exchange, albeit with less information hiding than in the MLS protocol.
Key exchange between individual users can be considered an optional privacy enhancement, but is required for group chat based on a shared key. In either case, exchanging keys is fairly straightforward — the real challenge is achieving forward secrecy.
By default, if at any point a user's private key is compromised, any messages that were retained by an attacker can then be decrypted. This is a major vulnerability, and solving it requires key exchange messages to be reliably discarded.
What's cooking
So that's an overview of the problems that need to be solved for private DMs and group chats. Not all of these problems will be solved right away, just because the bar for creating a decentralized encrypted chat system on par (or better than) Signal is the kind of thing you get venture capital for.
So the question becomes, should we build a sub-par messaging system that is tightly integrated with nostr, or refer users to a better option for encrypted communication?
Well, why did Twitter create its own DM solution rather than integrating email? Was it to harvest user data, or to provide additional utility to their users by allowing the social graph to inform messaging? Native features simply create a better UX.
On the other hand, in Paul Miller's words:
I would like to remind that nostr DMs, if nostr gets a traction, would be used by all kinds of people, including dissidents in dangerous places. Would you be willing to risk someone getting killed just because you want to keep backwards compatibility with bad encryption?
There is no easy answer, but it's clear that as we continue to work on this problem it is very important that applications communicate clearly the privacy implications of all "private" features built on nostr.
So, assuming we can pull off an appropriate balance between privacy and convenience, let me outline three new developments in this area that I'm excited about.
Gift wrap
Way back in April, Kieran proposed a dumb, but effective, way of hiding metadata on DMs. The technique involved simply encrypting a regular nostr event and putting that in another event's
contentfield. The neat thing about this is that not only does this hide some of the most revealing event metadata, it's not tied to a particular event kind — anything can be wrapped.What this means is that we can build entire "nostr within nostr" sub-networks based on encryption — some between two users, others based on a shared group key. This is much more powerful than a messaging-specific encryption schema. Now we can make private reactions, private calendars, private client recommendations, private reviews. I find this very exciting!
This proposal was further developed by Vitor — the current version can be found here. The latest version introduces double-wrapping, which can help prevent the wrapped event from being leaked by stripping its signature — that "draft" event is encrypted, wrapped, and signed to verify authorship without revealing contents, and then that wrapper is in turn wrapped and signed with a burner key to avoid revealing the author.
Wrapping also makes it possible to randomize the created timestamp to avoid timing analysis, as well as to add padding to a message, reducing the possibility of payload size analysis.
New DMs and small groups
The main subject of Vitor's proposal was a new way to do DMs and small groups using double-wrapping to hide metadata. This works basically the same way NIP 04 did — a shared key is derived and the message is encrypted for the recipient, whose pubkey is revealed publicly so that it can be delivered.
However, Vitor was able to extend this to multiple recipients simply by wrapping the message multiple times, with multiple shared secrets. With the addition of some metadata on the inner event, this makes it possible to define a group where the members know who each other member is, but no one else does.
Large groups
This proposal has one important limitation though — the number of events that need to be signed and broadcast is equal to
number of messages * number of members. This is fine with 5, 10, or even 100 members, but becomes infeasible when you reach groups of 1000+ members.For that, we have two similar proposals, one by @simulx, and one by myself. The differences between the two are not important for this discussion — both use gift wrap as a way to exchange and rotate shared group keys, and both support a weak form of forward secrecy.
As a side note, this is the proposal I'm most excited about, and why I got into nostr in the first place. Private community groups which can support shared calendars, marketplaces, notes, etc., are what I'm most excited to see on nostr.
Shortcomings
The above proposals are great, but of course leave much to be desired. If these are built, nostr will be hugely improved in both security and functionality, with the following weaknesses:
- Deliverability is still an open question — are relay selections enough to ensure recipients get their messages, and no one else does?
- There is no way to create a group whose members cannot dox each other. You must always be able to trust the people you share a group with, and of course, the larger the group, the more people there are that can betray you.
- Content can always be shared outside a group, although in Vitor's small group proposal, the only way to verifiably leak messages would be to reveal your private key.
- Key rotation is not supported by the small groups proposal, but it may be possible to solve it for the entire protocol by building out a name resolution system for nostr.
- Forward secrecy for large groups is weak at best. A key rotation can be triggered at any time, including when a member leaves the group, but unless all relays and all members destroy the key rotation events, it may be possible to decrypt messages after the fact.
- Credential sharing still has to be bootstrapped, meaning at least one encrypted message for each participant may be publicly seen. Of course, credential sharing could also be done out of band, which would largely solve this problem.
What about SimpleX?
Lots of people, including Semisol and Will, have expressed interest in integrating nostr with SimpleX and using their cryptography and transport instead of nostr's.
The first question to answer though, is which protocol should we use? SimpleX is split into a few different pieces: there's the SimpleX Messaging Protocol, which describes setting up unidirectional channels, the SMP Agent Protocol which describes how to convert two unidirectional channels into a bidirectional channel, and the SimpleX Chat Protocol which describes a standard way to send chat messages across a bidirectional channel.
SimpleX Chat Protocol
So far, most proposals to fix messaging have focused simply on DMs, and sometimes on group chat. This is SimpleX's wheelhouse, so it could definitely make sense to communicate that kind of information over SimpleX's top-level chat protocol, and leave nostr out of it entirely.
The downside of this is that it requires clients to support two different protocols, and connect users to two categories of servers. This isn't a deal breaker, but it does increase the complexity involved in writing a full-featured nostr client, especially since there are no implementations of the SimpleX protocol other than (17k lines of) Haskell.
Using SimpleX's chat protocol would also limit the message types we'd be able to encrypt. Anything outside SimpleX's protocol (like zaps for example) would have to be sent using a custom namespace like
nostr.kind.1234, which wouldn't be recognized by normal SimpleX clients. There are also areas of overlap where both protocols describe how to do something, for example profile data, requiring clients to choose which kind to support, or send both.Another wrinkle is that the SimpleX protocol is AGPL v3 licensed, meaning proprietary software would not be able to interoperate, and MIT licensed products would have to abide by their license's terms.
SMP and Agent Protocols
The lower-level SMP and Agent protocols are more promising however, since their scope is narrower, and doesn't overlap as much with nostr's own core competencies. Both are quite simple, and very prescriptive, which should make it easy to create an implementation.
SMP is actually quite similar to some of the proposals mentioned above. Some of the same primitives are used (including XChaCha20 for encryption), and SMP is transport agnostic meaning it could be implemented over websockets and supported by nostr relays. The network topology is basically the same as nostr, except SimpleX doesn't make any assumptions about which servers should be selected, so in that regard nostr actually has an advantage.
The main incompatibility is that SimpleX requires the use of ed25519 and ed448 EdDSA algorithms for signatures, which means nostr's native secp256k1 signature scheme wouldn't be compatible. But this could be ok, since keys shouldn't be re-used anyway, and there are other ways to share a nostr identity.
Forward secrecy?
Whenever a server is involved, several attack vectors inherently exist that would not in peer-to-peer systems. Servers can threaten user privacy by storing messages that should be deleted, analyzing user behavior to infer identity, and leaking messages that should otherwise be kept secret.
This has been used by some to suggest that nostr relays are not a good way to transport messages from one user to another. However, SMP has the same attack vector:
Simplex messaging server implementations MUST NOT create, store or send to any other servers: - Logs of the client commands and transport connections in the production environment. - History of deleted queues, retrieved or acknowledged messages (deleted queues MAY be stored temporarily as part of the queue persistence implementation). - Snapshots of the database they use to store queues and messages (instead simplex messaging clients must manage redundancy by using more than one simplex messaging server). In-memory persistence is recommended. - Any other information that may compromise privacy or forward secrecy of communication between clients using simplex messaging servers.
So whether SimpleX servers or nostr relays are used, privacy guarantees are severely weakened if the server is not trustworthy. To maintain complete privacy in either scheme, users have to deploy their own servers.
Relays to the rescue
Because nostr servers are currently more commonly self-hosted, and more configurable, this makes nostr the better candidate for channel hosting. Users can choose which relays they send messages to, and relay admins can tune relays to only accept messages from and serve messages to certain parties, delete messages after a certain time, and implement policies for what kinds of messages they decide to relay.
All that to say, SMP itself or a similar protocol could easily be built into nostr relays. Relays are not the wrong tool for the job, in fact they're exactly the right tool! This is great news for us, since it means SMP is applicable to our problem, and we can learn from it, even if we don't strictly implement the protocol.
Bootstrapping over nostr
One assumption SMP makes is that channels will be bootstrapped out of band, and provides no mechanism for an initial connection. This is to ensure that channels can't be correlated with user identities. Out of band coordination is definitely the gold standard here, but coordination could also be done over the public nostr network with minimal metadata leakage — only that "someone sent {pubkey} something".
Unidirectional channels
Unidirectional channels are a great primitive, which can be composed to solve various problems. Direct messages between two parties are an obvious use case, but the SimpleX Chat Protocol also includes an extension for groups, defined as
a set of bi-directional SimpleX connections with other group members.This is similar to Vitor's small-group model, and likewise isn't conducive to supporting very large groups, since a copy of every message has to be sent to each group member.
However, it's possible to build large groups on top of unidirectional channels by sharing receiver information within the group and having all participants read from and write to a single channel. In fact, this is very similar to how our large group proposals work.
Conclusion
So, the takeaway here is that SimpleX's lower level protocols are great, and we should learn from them. It may be worth creating a NIP that describes the implementation of their unidirectional channels on nostr, and re-using that primitive in DM/group implementations, or simply following the same general process adapted to nostr.
I'm personally encouraged by reading SimpleX to see that we are headed in the right direction — although many of the details of our proposals have not been fully hammered out in the way SimpleX's has.
As for what the future holds, that's up to the builders. If you want to see tighter SimpleX integration, write a NIP and a reference implementation! I'll continue learning and fold in everything I can into my work going forward.
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ 20986fb8:cdac21b3
2023-08-17 10:07:39
@ 20986fb8:cdac21b3
2023-08-17 10:07:39背景
随着Web3技术的兴起,科学研究在数据共享、合作和透明度方面将迎来前所未有的改善。同时,人工智能在数据分析、模型预测等领域的应用,将极大地推动科学研究的发展。通过举办Web3、AI与创作者Hackathon,我们旨在激发科研者、开发者和创作者的思考,探讨如何借助Web3和AI技术,优化科学研究,进而促进科学的不断前进。
参与人员
Web3、区块链、元宇宙、人工智能等前沿领域的研究者、创作者、爱好者等。
时间&地址
8月19日下午14:30-17:30 地址: 北京、澳门、新加坡
活动细则
创意主题
主题 1: AI4S—人工智能技术为科学研究创造新的可能性 主题 2: DeSci-DeSci、CeSci与NeSci 主题 3: 期刊生态—以Web3和AI为代表的智能技术,对科学期刊体系的创新 主题 4: 科学热点—科学热点话题分析、捕捉、创作
比赛规则
任选一个主题,并在限定时间内完成与该主题相关内容创作,创作形式不限于长文(500字起)、视频、图片、漫画等单一或组合形式; 成功发布在 yakihonne.com 平台; 添加基于闪电网络的Zap⚡打赏功能; 等待社区和评委投票 资金匹配,发放Hackathon奖金
评选规则
评选机制: 1. 基于现场评委测评,评选出最佳创作奖、最佳表现奖和最佳创意奖,每项奖金10万SATs 最佳创作奖:奖励在内容深度、专业度方面最出色的作品 最佳表现奖:奖励在文本展现形式、风格方面最具有表现力的作品 最具想象力奖:奖励在切入角度、创作视角方面最具想象力的作品 2. 基于社区投票,按照该作品的upvote(点赞)数占所有作品总upvote数的比例,瓜分40万SATs人气奖金池 另外,所有参与者均可获得小额Sats参与奖 以上所有奖励,会通过yakihonne.com独家的Zap⚡打赏功能奖励至每个获胜者的作品
小贴士
- 需要携带个人电脑💻;
- 允许提前收集需要创作的素材资料。但不允许在比赛现场的直接内容复制粘贴,否则视为弃权;
- ChatGPT可以作为现场创意协助生产工具,但不能直接用来生成最终的发布内容,否则视为违规不予评选;
- 创作者可以选择任何有趣且有价值的视角或形式来创作内容。
问&答
1. 我必须是资深科研人员才可以参与么?
- 不一定. 我们鼓励并欢迎所有对Desci,Web3、区块链、元宇宙、人工智能等前沿领域感兴趣的科研人员,学者,爱好者,开发者,建设者等创作群体加入比赛。
2. 评审组是谁,评选结果有说服力么? - 为了增加比赛评审机制的公平性及多样性,Yakihonne采用社区投票+评委投票。除了专业评审团的投票,我们也会结合每个作品在社区里的Up Vote数来综合打分。
3. 获胜奖金什么时候发放? - 奖金会在比赛结束后的2个工作日内发放
4. 我需要提前准备什么? - 选择一个您感兴趣的主题,准备相应的创作素材,会更有助于您获胜.
5. YakiHonne 承办这次活动的目的是什么? - YakiHonne 是一个基于Nostr的去中心化内容媒体协议,支持各类创作者的自由策展、创作、发布和报道. 我们将长期支持研究人员在全球范围内展开创作和交流。

如何设置新账号
简单来说,只需要在登录页面点击生成新密钥即可,记得保存好你的公钥和私钥。
但安全起见,同时也为了可以接收到打赏,建议设置闪电网络钱包并用该钱包登陆:
- 在浏览器中安装钱包拓展(例如,Alby),并在yakihonne.com登陆页面生成公钥和私钥;
- 跟随下面视频中的步骤完成设置,即可安全地使用并接收打赏了:
关于YakiHonne:
YakiHonne 是一个去中心化内容媒体协议,支持各种媒体的自由策展、创作、发布和报道。 点击尝试 YakiHonne.com!
关注我们
- 社区: http://t.me/YakiHonne_Daily_Featured
- 推特: @YakiHonne
- Nostr 公钥: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ 20986fb8:cdac21b3
2023-08-17 09:04:28
@ 20986fb8:cdac21b3
2023-08-17 09:04:28This article original was published in nostr.com and it is shared in here for convenience and fast acces within YakiHonne client. All credit goes to https://github.com/nostr-protocol/nostr
Clients are the way that you access and interact with the Nostr protocol.
What's a client?
A client in Nostr is just the app that you use to access and interact with the protocol. It's like the Twitter iOS app or web app that you use to interact with Twitter's feed of tweets.
Because the Nostr protocol is very simple and flexible, different clients have approached the protocol in different ways: some try to make the experience look exactly like Twitter, others try to highlight the importance of relays to the protocol and expose that to users, and others try to use heuristics and algorithms to ensure the maximum degree of censorship-resistance without burdening users too much.
Can I switch clients?
Yes. Because a client is just a way to access the underlying data held by relays, you can switch clients or sign into as many clients as you'd like. As long as each client is looking at the same set of relays for their data, you'll see the same messages in each client.
Should I enter my private key in the client?
Generally, it's better not to enter your private key into any client. Most clients that ask for private keys do their absolute best to keep your key secure but given the nature of software, there are always breaches, exploits, and bugs that could potentially expose your private key.
Remember, your private key is your identity in Nostr, so if it is compromised you'll lose your followers and will have to start from scratch rebuilding your identity.
A few of the already existed clients
Web
- YakiHonne, YakiHonne is a censorship-resistant content media protocol, which supports free curation, creation, publishing, and reporting by various media.
- Snort, an easy-to-use client with great onboarding.
- Coracle, an experimental client that is advancing the UX and internals of social media.
- Iris, a client that throws you in instantly.
iOS
- Damus, the first Nostr client to be banned in China.
- Primal, a very fast client that relies on server-side caching.
iOS and Android
- Plebstr, a closed-source client that is beautiful, fast and smooth.
- ZBD, a custodial, hosted client for ZBD users.
- Current, a client that comes with a built-in Bitcoin wallet.
Android
- Amethyst, a client that has all the features you might imagine.
- Nozzle, a very lean client, but still a work-in-progress.
Desktop
- Gossip, a native client that tries to efficiently follow people in wherever relay they happen to be, made in Rust with egui.
- more-speech, a client that gives you a powerful global view and way of interacting with custom filtering based on web-of-trust and relay selection, made in Clojure. Check out a guide here.
- Lume, an ambitious client made with Tauri.
What are relays ?
Relays are like the backend servers for Nostr. They allow Nostr clients to send them messages, and they may (or may not) store those messages and broadcast those messages to all other connected clients.
The world of relays is changing fast so expect many changes here in the future. One thing to note, because Nostr is decentralized and depends on relays to store and retreive data, if you notice that your Nostr client feels slow, it's most likely due to the relays that you're using. It might be worth adding a few more relays to your client.
Where can I find a list of relays?
The best resource we've found for browsing and assessing the speed of known relays is the nostr.watch site.
What happens if all the relays I use stop working?
If all the relays that you have used in the past go offline, all your posts will be unretrievable. This is one reason that Nostr allows users to connect to many relays – this ensures some degree of backup. That said, if you're really interested in being uncensorable, you can run your own personal relay.
Should i run my own relay?
For most people, no, it's not worth the hassle. That said, if you're technical and want to ensure that your speech is absolutely uncensorable, then you can and should run your own relay. This ensures that you always have a copy of all your Nostr posts and interactions for all time. Here is a guide from Andre Neves for hosting your own relay under 5 minutes
How can someone find me in a personal or obscure relay?
You should be able to hint where you are publishing to to people that may be interested by using the NIP-19 nprofile code or the NIP-05 "relays" field.
If you manage to (and your client helps) you can publish a list of the relays you use to multiple other relays that you don't, so others can find that list and start following you were you are.
Finally, clients from others should include relay hints in events that mention or reply to you, the hints should point to where your notes can be found, so that can give clients a clue.
What public relays exist?
The nostr.watch website keeps a very complete list that has a bunch of information about each relay, not only their address.
How to contribute?
Here are some ways you can contribute to the success of Nostr:
- Contribute to your favorite client, try to come up with approaches that both make Nostr fun and useful and also promote decentralization and ultra-interoperability
- Start a new client if you think you have new approaches and ideas to contribute that wouldn't fit in an existing app
- Check out https://bountsr.com/ for things that might interest you
- Use Nostr, think about it, and let others know what you have seen in this crazy new idea that has captured your imagination
- Give feedback to client authors, but patiently
- Create or contribute to bounties on https://bountsr.com/
- Give money to people that are doing things you think are good
- Write explainers and curated resources, put them online so they can help others
- Check how your skills can help Nostr software or the mission of spreading the Nostr world, partner with others that may be searching for that
- If you have a good, concrete, real-world use case for Nostr that you want to use yourself and others might want to, bring it up and it's likely that someone else will be interested in building it
- Annoy content creators, people banned from social media and other personalities that you follow that you think may be interested in Nostr until they look at it
-
 @ 92294577:49af776d
2023-08-14 02:47:22
@ 92294577:49af776d
2023-08-14 02:47:22My last post about Simplicity touched on the language’s type system, and defined a Simplicity program as a Simplicity expression that maps an empty input to an empty output. We introduced the idea of assertions, which allow a program to abort, and witnesses, which allow programmers to inject input data into Simplicity programs at exactly the places that it’s needed. Together, this means that programs can have nontrivial behavior, even though nominally they have neither inputs nor outputs.
We also confronted the complexity of fully specifying even simple mathematical functions in Simplicity. One tool we used to reduce the complexity is that of jets, which provide optimized implementations of specific Simplicity expressions. This is a useful optimization for blockchain validators, but it also provides value to the Simplicity programmer by encapsulating potentially-complex functionality in a single jet, which can be treated as a black box.
In fact, every Simplicity expression is uniquely identifiable, by an object called its identity Merkle root (IMR). The IMR of a node is computed by hashing its source and target types, its combinator, and its children (if any). Using IMRs, we can uniquely identify any expression, and thereby treat it as a black box, even if we don't have an optimized jet to replace it.
Bit-Flipping, Revisited
At the beginning of the last post, we introduced the following code, which flips a single bit:
``` bit0 := injl unit : 1 * 1 -> 2 -- imr 31059b22... bit1 := injr unit : 1 * 1 -> 2 -- imr 9864ae9d...
padR := pair iden unit : 2 -> 2 * 1 -- imr 457121c2... bitflip := case bit1 bit0 : 2 * 1 -> 2 -- imr 7d5ff8d0... main := comp padR bitflip : 2 -> 2 -- imr a6ecc3dd... ```
As we can see from type ascription on the last line, this expression takes a single bit (the “2” type, so named because it has two possible values) and outputs a single bit. In this listing, we have also computed the IMR of each expression. In the future, whenever we see a Simplicity expression whose IMR matches one of these values, no matter how complex or obfuscated it appears to be, we will know exactly what we are looking at.
But recall that, to have a Simplicity program, we need our main expression to have type 1->1. Rather than taking an input value, we will use witness nodes, and rather than having an output value, we will simply assert that any intermediate values have the properties we expect.
As an example of this, let's tweak our expression to get a program that asserts that a witness bit is 0. We'll do this by taking a witness bit, flipping it, then passing to the jet_verify jet:
``` witbit := witness : 1 -> 2 -- imr ???
-- Assume we have the above expression, with the name bitflip. -- Notice that its IMR is the same as above.
bitflip :: 2 -> 2 -- imr a6ecc3dd... zerovfy := comp bitflip jet_verify : 2 -> 1 -- imr b3bca637...
main := comp witbit zerovfy : 1 -> 1 -- imr ??? ```
Here we have an interesting observation. The IMR of a witness node is computed based on the witness value, but when writing a program, we do not yet know what the witness value will be. This means that we do not know the IMR, and we cannot treat the expression as a black box. The same applies to
main, which depends on thewitnessnode, and any future expressions that might depend onmain.The same considerations apply to disconnected expressions. When we use the disconnect combinator, we can have entire expressions, not just values, which aren't yet determined. We will talk about disconnect in a later post.
IMRs and CMRs
Our lack of IMRs makes a certain amount of sense: if an expression depends on data, which we do not have available, it is not possible to precisely specify it. On the other hand, we actually do know a fair bit about the program under consideration: we know that it is a
compcombinator whose children are awitnessand anothercompcombinator, respectively, and so on. In this case, we even know the exact source and target types of all nodes.In other words, we have fully defined our program, up to witness data and disconnected expressions that we do not intend to populate until later. We have defined the parts of our program we need to generate addresses and receive coins, but left some parts undefined until we are ready to spend them.
In Bitcoin Script, we have this same distinction between commitment time and redemption time. At commitment time, we choose what public keys to use, and only at redemption time, do we produce signatures with those keys. For historical reasons, Bitcoin Scripts are committed to by taking their hash and embedding this hash in another Script, sometimes called a scriptPubKey but more commonly known as an address.
Taproot generalizes this hash to be the root of a Merkle tree, allowing the same address to commit to multiple scripts, only one of which is revealed at spending time.
In Simplicity we take this a step further, treating our entire program as a Merkle tree. To do so, we define a second hash on each node, the commitment Merkle root (CMR). Unlike the IMR, the CMR does not commit to witness data, disconnected expressions, or types. It only commits to the structure of the program.
When embedding Simplicity programs in the blockchain, we replace the leaves of a Taproot tree, which normally would be Scripts, with the CMRs of Simplicity programs.
We can write out the CMR of each node in our bit-flipping program:
``` witbit := witness : 1 -> 2 -- cmr bf12681a... bitflip : 2 -> 2 -- cmr 8f214cce... zerovfy := comp bitflip jet_verify : 2 -> 1 -- cmr ab61cadb...
main := comp witbit zerovfy : 1 -> 1 -- cmr 58655557... ```
Every node, including witness and disconnect nodes, has a CMR. And every witness node, in every program, has the same CMR.
Naming and Sharing
In our Simplicity programs so far, we have written a series of named expressions, referring to each expression in a later expression, by name. Naturally, we are not limited to referring to names only once. This concept is essential to using Simplicity. We refer to name reuse, or more generally, collapsing multiple copies of the same expression into one, as sharing.
On the blockchain, there is a consensus rule that Simplicity expressions encoded in transactions be fully shared. That is, it is actually illegal to encode two nodes that have the same IMR. This helps ensure that programs are encoded in the most compact way, and that their encoding is canonical; that is, there is no potential for malleability. But this rule exploits the fact that programs never appear on-chain except when all witness nodes are populated, and therefore every node has an IMR.
At commitment time, when we are defining programs and computing addresses, the story is not so simple. Let's explore the subtleties that come from sharing before our IMRs are set in stone.
Essentially, every time a name is used, it must refer to a node with the same IMR. What makes this surprising is that, as we have seen, the code we write is only actually sufficient to define a node's CMR, not its IMR.
Let's see a simple example of where this might lead to trouble. Let's take a look at our original bit-flipping program, and let's say that we are tired of writing the entire word
unitout. So we define an aliasu := unit -- cmr 62274a89...and try to use it in our program:
``` bit0 := injl u : 1 * 1 -> 2 -- cmr bd0cce93... bit1 := injr u : 1 * 1 -> 2 -- cmr 79a70c6a...
padR := pair iden u : 2 -> 2 * 1 -- cmr 7751cd1c... bitflip := case bit1 bit0 : 2 * 1 -> 2 -- cmr 1d4aa8f4... main := comp padR bitflip : 2 -> 2 -- cmr 8f214cce... ```
But when we try to parse this to get an address, we get a type error defining padR! The reason is that while the type of the unit combinator in bit0 and bit1 is 1 * 1 -> 1, the unit combinator in padR has type 2 -> 1. The source types of unit combinators are completely uninteresting details of a Simplicity program, but it's nonetheless essential[1] that we are consistent about them.
The fix here is simple: we can reuse the name
uinbit0andbit1but forpadRwe need a freshunitcombinator.So far, so good; this sort of problem is familiar to any programmer who works with strongly typed languages, especially ones that support type inference, so that the types of variables are not immediately obvious. But with Simplicity, there is also a more interesting problem we might stumble over.
Consider the following program, which checks whether the user has found a SHA256 "fixed point", i.e., an input whose SHA256 hash is equal to itself. Because SHA256 is a cryptographic hash function, this should be impossible, so coins stored at this program should be unspendable.
``` -- Witnesses -- CMR: bf12681a... -- IMR: [none] wit_input := witness
-- All jets have source type 1; but to use the
paircombinator -- we want one with source type 2^256. To get this, we compose -- it with unit. -- CMR: a520761f… -- IMR: 21182050... sha256_init : 2^256 -> _ sha256_init := comp unit jet_sha_256_ctx_8_init-- Using this, we can write a self-contained "take 32 bytes and -- compute their sha2 hash" function. -- IMR: 8e341445... -- CMR: bf70ec35... sha256 : 2^256 -> 2^256 sha256 := comp comp pair sha256_init iden jet_sha_256_ctx_8_add_32 jet_sha_256_ctx_8_finalize
-- Finally, our main function takes an input witness, hashes it, -- and compares the input and output to check for a fixpoint. -- CMR: 9b3b900a... -- IMR: [none] main := comp comp pair (comp wit_input sha256) wit_input jet_eq_256 jet_verify ```
Here we have reused the name
wit_input. Our rule is that we can only reuse names when all uses have the same IMR, but here we don't even have an IMR to compare. Will this be a problem?Well, consider this alternate version of
main, which takes a second witness,wit_output, and compares this to the hash ofwit_input. This newmainis trivial to satisfy: provide anything at all forwit_inputand provide its SHA256 hash forwit_output.``` -- Witnesses -- CMR: bf12681a... -- IMR: [none] wit_input := witness wit_output := witness
[...rest of program elided...]-- CMR: 9b3b900a... main := comp comp pair (comp wit_input sha256) wit_output jet_eq_256 jet_verify ```
The important thing to notice here is that these two programs, our fixed-point-checking program and the trivially-solvable program, have the same CMR and, therefore, the same Bitcoin address. This is because Simplicity does not commit to sharing. This subtle, but crucial, fact, means that our fixed-point program, rather than being impossible to spend coins from, is trivial.
Fortunately, Simplicity prevents us from making this mistake. If we attempt to assemble our original version of the program, we get the following error:
Error: witness/disconnect node `wit_input` was accessible by two distinct paths from the same rootWhat this is telling us, in somewhat jargony language, is that we are simply not allowed to share witness or disconnect nodes, or any expressions which refer to them. This is because such nodes, even when they have identical types and CMRs, may not end up the same.
At redemption time, when witness data and disconnected expressions are present, every node has an IMR and it is unambiguous whether nodes are the same. At that time, if two witnesses were present and had the same types and values, they would be shared. But this sharing depends on the particular values chosen for each witness node, which are not decided at commitment time, and therefore do not reflect anything about the actual structure of the program.
To fix our program, there are a couple of strategies that we could take. One thing we could do is to define two witness nodes, with different names, and use the
jet_eq_256jet to assert that they are both equal. This would work, but increase the complexity of code, making it harder to review or to extend. A more direct approach is to duplicate the output of a single witness node.We do this by pulling our check out of
maininto its own expression, whose input value is accessed by theidencombinator twice:``` -- IMR: 5ddb65c2... -- CMR: 198bfeb5... assert_fixpoint : 2^256 -> 1 assert_fixpoint := comp comp pair (comp iden sha256) iden jet_eq_256 jet_verify
-- CMR: ac8df50b... -- IMR: [none] main := comp wit_input assert_fixpoint ```
This program is accepted without error.
Conclusion
As with ordinary Taproot transactions, addresses are derived from commitments to programs, but the programs themselves are not revealed until spending time. Also, as with Taproot, in Simplicity, we reveal only those parts of the program that are actually used.
Bitcoin Script has a strict separation between program code and witness data, so the program revealed on-chain is the same as the program committed to in addresses (aside from pruning). Witness data is encoded separately and provided to the program code as input. Script does not have any notion of sharing, or of disconnected expressions, so functionality such as delegation is missing (and functionality such as loops are very inefficient to implement).
In Simplicity, we instead attach witness data directly to our programs, and when encoding programs, we insist that nodes are never repeated. This combination requires us to have a surprisingly subtle notion of "identity," which, when applied to text-encoded programs, allows us to reuse names in a mostly-natural way. But there are potential pitfalls here, which our tooling helps to avoid.
In our next post, we will explore pruning, which is the process by which unused nodes are not revealed, and its interactions with witnesses and the type system.
Until then, join the Simplicity discussions on GitHub to connect with the community, and follow us at @blksresearch on Twitter to stay updated with the latest Simplicity announcements.
[1]In theory, Simplicity could have supported polymorphic types, which would allow the same
unitcombinator to be used with different type signatures. But aside from increasing the complexity of using and analyzing the language, this would have increased the computational complexity of type inference, a task that must be done by all validators on all programs. -
 @ 3129509e:c846f506
2023-08-13 13:15:31
@ 3129509e:c846f506
2023-08-13 13:15:31Splitstr
An application to split bills and track shared expenses in a group, with the ability to “settle-up” with lightning invoices.
The Splitwise app on iOS and android is a great example, but lacks lightning and Nostr.
https://www.splitwise.com
-
 @ 62a45004:b2ff78c5
2023-08-12 15:42:21
@ 62a45004:b2ff78c5
2023-08-12 15:42:21Macom slid the memory disk in his pocket, grabbed his coat and badge, and headed for the communications tower. Outside, the bright but cold day encouraged him to walk briskly under the deep blue skies that reminded him of his childhood on his home planet.
Along the uneven sidewalk, a treacherous minefield of puddles from the previous night’s downpour made it necessary to focus on one’s steps. As Macom waved off a group of teens looking to peddle their counterfeit ration cards, he accidentally stepped on a loose tile, which promptly responded by squirting a copious stream of muddy water all over his right leg and torso. Without the slightest flinch, Macom continued onward, his mind focused on the task at hand.
It was not much to look at from the outside. Like most other buildings, the round-shaped communications “tower” was half-way embedded into the ground as a way to take advantage of the earth’s biomass and its natural cooling and heating effects. On top, transmission disks no larger than a few feet in diameter adorned the building like ears on the head of a sleeping, mossy giant.
Inside, however, the space was majestic and luminous. Beyond the security checkpoints, the circular, expansive lobby was centered around a grand spherical computer. The Galactic Timechain, as it was known, was encased in glass, and around it, a second layer formed a terrarium of the native ecosystem, meant to mirror the resilient and self-sustaining nature of the Timechain’s distributed network.
Along the curved wall, intricate but faded murals of historic figures blended into textual inscriptions of poems and quotes, and from above, a beam of sunlight from the roof-timer cycled its’ focus through each piece of art as new blocks were added to the Timechain. The space felt more like a temple than a government building.
‘Good morning Sub-Commander,’ the guard uttered as Macom flashed his badge, ‘you are earlier today than usual.’ The greeting was silently acknowledged with a stoic nod, and as he was waiting for the gate to open, the beam of sunlight moved to the left, and the newly illuminated quote on the gallery wall caught his attention.
Time is an abstraction at which we arrive by means of the changes of things.
Macom had never really understood the meaning of those abstract words. But today of all days, the quote he had seen a thousand times found within him a renewed resonance. He remembered being taught that in ancient civilizations, humans measured the passing of time by the ticking of metal arms around a circle, which was meant to track the astrological movement of planets around a sun. As interstellar travel evolved, this antiquated system created synchronization nightmares, for everyone had a different definition of what “time” was, of how long it took their planet to circle their sun.
Now, the addition of new blocks on the Galactic Timechain marked the passage of time. Macom felt this was curious. There was nothing in the transactions and records stored within the blocks, in the bits of zeroes and ones, that had a physical existence called “time.” Neither could the humans of antiquity find any physical element constituting “time” in the movement of the planets. The change of any thing, in fact, could be used as the measuring yardstick, and in this particular moment, Macom realized he had been unconsciously measuring time by the quickly changing political situation: the Empire’s draconian laws would open the floodgates to changes not seen since the Wars of Independence. Millennia would happen within the next few blocks, and for that reason, he thought, now was the time for decisive action.
Aided by this newly found revelation, Macom walked across the lobby towards the elevator, finding his way to transcription station #B412. The room, no larger than a regular size office, betrayed no sign of its importance. This station was designed as a decoy and kept as a closely guarded secret, for it contained the Nhafezi Confederacy’s keys, used to compose and transmit blocks onto the Galactic Mempool. As such, the security clearance used to access it also triggered an alert to high command. Even someone of his rank was not supposed to be here unannounced, and Macom knew he would only have a few moments to complete his task.
Standing in front of the door, Macom took a deep breadth to gather his courage, for he knew that as soon as he entered the room and sent the message across the Timechain, there would be no stopping, that there would be no coming back from this. He thought of the countless years of suffering, the bad winters, the unnecessary cruelty of it all. He thought of the despair and hopelessness he saw on so many faces, including his own. Above all, he thought of his brother, now gone.
As long as the life of a star to the human mind, and as short as the span of a human life to a star, the moment ended, and Macom swiped his badge on the door’s console. Moving swiftly now, he slid onto the station chair, picked the memory disk from his pocket and blended it into the transcriptor in one fluid motion. The text appeared before him, exactly as he had last proof-read it. Just as he was about to fetch the keys, a gentle knock came from the door before it opened.
With his heart skipping a beat, Macom saw a familiar figure appear from the corner of his eyes, and quickly composed himself. “I am that predictable,” he said with an air of resignation while still staring into the transcriptor.
“You were never good at hiding that look on your face,” Jiun said sardonically, while closing the door behind her.
Guarding against stalling tactics, he ignored the jab and tried to finish the job, but his fingers had barely moved before Jiun flung her comm tablet and key ring towards his desk.
“No one is coming Macom, I had Ella disengage the alert and now you have my personal key ring. I know you will not stop, not even for me, but I ask you to hear me out. If you still want to go ahead after we are done talking, I won’t stop you.”
The tablet, which had landed with a loud thud and knocked over a mug, displayed ‘#B412, alert disengaged.’ Macom was not the trusting kind, and for a moment he hesitated, thoughts of deception and betrayal rushing through his head. But even after all these years, Jiun’s word still meant something.
“I helped you draft this, remember?” Macom said while turning towards her. “It wasn’t that long ago you agreed we have to send this out.”
“That was before the council voted it down,” Jiun said with a calm assertiveness.
“And that changes nothing. You know better than I do how the Empire is systematically starving us. I am not going to allow them to reduce us to nothing, to drain us of our strength until finally, stripped of all self-respect and dignity, unable to summon the will to fight, they can simply sweep us out with a broom. We must fight,” Macom said emphasizing each word, “even though the council is too afraid, perhaps even too corrupted to do what must be done.”
“I agree, the Empire wants us to do nothing. But they would equally benefit if we over-reacted. Now that Antigonium can be synthesized and mass manufactured, we are disposable. They would like nothing more than to have the perfect excuse to send their destroyers. We have to fight, not to destroy our enemy, but to save what we love, and sending this archive to the Galactic Timechain would be suicidal.”
“The real suicide is already happening Jiun. How many people are starving? How many have taken their own lives in their misery and despair?,” Macom’s voice splintered with the faintest of cracks, before continuing. “How many of our young will they take, once this new round of laws are enforced? Should we wait until we start getting paid in imperial script, or perhaps when we start forgetting our own language? Revolution is not suicide, even if it leads to certain death. Our ancestors knew that when they fought for our independence.”
“You are right, but this is not a decision for you to make. Corrupted as it might be, the council is still needed to organize any meaningful resistance. And we might be able to force their hand, but not if the transgression comes from you Macom. If you do this, they will call it a military coup, and it would only further our internal division and turmoil. That is exactly what the Empire wants. They put us in a position to make an impossible decision, they infiltrate the council with unseen extortion and threats, all so they can watch us implode from the inside. You know this playbook.”
A long silence now enveloped the space between them, words being said without a single sound. The impasse brought into relief their conflicts from eons ago, and as Macom digested the arguments of this latest salvo, he also felt reminded with a certain fondness, why she was who she was, their indisputable moral leader.
Standing up now, Macom walked towards the door, accepting her overture: “Someone has to do it, Jiun. Even if it is a trap, even if it leads to our demise, the archive would guarantee the preservation of our culture and Our-Story for future generations. We must break the long silence. You know it is time.”
As Macon exited the room, he handed her his badge and his Antigonium pendant, the one she had gifted him all those years ago. Now alone, Jiun took a long and deep sigh before heading towards the transcriptor. On the screen, the words they had drafted together stared back at her. She sat down, clutching the pendant that stored his keys, and read it one last time.
Top Secret
My name is Jiun Nhafezi, Matriarch of the Nhafezi Confederacy, and these words, inscribed on the Galactic Timechain Codex, block number 226,524,579, will in all likelihood lead to our demise, effectively constituting our people’s last act.
Bitcoin’s Timechain has long afforded the possibility of free speech, and more importantly, the preservation of a lasting legacy against physical genocide and cultural erasure. For the first time ever, the last defiant breath from those facing annihilation will not simply scatter in the wind, unheard of and forgotten by those who seek to erase us from their-story. For the first time ever, they who control the present will not be able to sanitize, re-write, and control the past. Our past, which is also our future.
Even though this tool has been but an open road, useless to those who seek to walk it when a gun is held to their heads, it has nevertheless acted as leverage for those fighting for survival under the Empire’s watchful eye. And for millennia, this leverage has afforded our people a semblance of life: ever since the Independence Wars, our accord has forbidden us from off-planet communication. As long as we supplied the Empire with minerals and kept our words and ideas to ourselves, we were allowed the independence to uphold our customs and organize our own way of life. This is why you might have never heard of our people, or of Kaweah, a faraway moon better known in the ancient world as an Antigonium mine.
But the balance of power has now changed. As our world grew stronger and brighter, so did the Empire’s fear. Our knowledge, our art, our way of life, all of it became dangerous proof that another mode of social organization is not merely possible, but if allowed to flourish, would undermine the deepest moral foundations of the Empire in the eyes and hearts of their own people.
And so we must be destroyed.
First came the impossible mineral quotas, the penalties of which were reduced food supplies. Slowly, they forced us to choose who would go hungry, sowing the seeds of discord. Then, as we grew more desperate, the Empire extended a helping hand, offering to send our young off-world, saddling them with unpayable debts, and scattering them across the stars in search of “a better life.” Now, under the guise of industrial standardization and efficiency management, they are forcing us to adopt the imperial tongue in all curricula and settings, abandoning our own.
Faced with the slow, painful immiseration of our people, and the clear directive to dismantle our society piece by piece, we are left with no choice but to break our long silence, preserving our cultural heritage, our memory and our knowledge on the Timechain. Perhaps the two most important ones are the lexical archive, for those who seek to learn our tongue, and the mineral archive, which includes the hitherto secret chemical composition of the synthetic ingredients needed to mass manufacture Antigonium. Now it becomes open-source, our first, and perhaps last gift to the Universe.
For our transgression, the Empire will soon circle our moon and rain down extinction. Our last efforts to defend ourselves will most likely fail. By the time you receive this message, we will have long ceased to exist. I will presume these words are the only record that will survive us. Our books will be burned, our culture expunged. The young sent to the Ministry of Harmony and Reintegration will likely never speak our language our know of their heritage. Our matriarchs will be sent to the gallows, and our men to labor camps across the known galaxies.
It is our hope that this fate that awaits us, that announces its presence with every word that I convey to you, is but a temporary defeat, a chapter linking our past and the many revolutions to come. Faced with the certainty of a death of the spirit, and the possibility of a death of the body and the flesh, we as a people have chosen to not give up our dignity. Instead, we choose life at its fullest.
As we begin, so we end. This is Our-Story.
-
 @ 7ecd3fe6:6b52f30d
2023-08-12 07:18:50
@ 7ecd3fe6:6b52f30d
2023-08-12 07:18:50Social media is a part of our lives, like it or not, it's how we get our news, voice our opinions engage with friends and family, find community and argue with anons, it's just what we modern humans do.
The problem with social media today is that it is run by corporations, these platforms, while acting as public utilities for communication are actually walled gardens where narratives can be pushed or suppressed and your time on site is paid for by ads that are burning your eyeballs so hard they leave an imprint on the back of your brain.
We can all see the incentive structure of corporate social media has us all going a little loopy while others have fully given themselves over to whoring for the algorithm.
We need decentralised social media
It's obvious we need a platform where we're not beholden to who has the biggest budget, or what the algos are looking to rage bait you into so you remain on site to see more ads. This is not a system that is good for one's brain and soul, the "free" social media model comes at a price, and you as the product have begun to decay.
Anyone who voices their real opinions or counters narratives that go against profits and the bottom line of interest parties also gets cleaned out pretty quickly so if you're are still on trad social media it's because you're willing to self-censor or you have nothing real to say.
We are all self-censoring in a way, you know it, I know it, but we all accept it.
Nostr came along
I think many of us didn't know we needed an alternative until #nostr came along and we could start to play around in a world where we had more control and some of us started to like it.
Nostr has grown slowly and steadily, without a token, without a real path to monetisation, it's organic growth built by people who have an interest in seeing this protocol eat away market share from tradsocial.
Right now it's just a bunch of people sharing their ideas, engaging in a small community testing out new features, pushing clients for new updates, and zapping one another along the way.
Despite the seemingly inconspicuous nature of nostr it's already started to rub large institutions the wrong way, first, it was banned in China, then it's mobile clients were removed from the Chinese Apple App store and later it was threatened by the global app store to remove zaps.
If a little protocol that simply allows for chronological curation and organic following of accounts and content along with independent payments powered by Bitcoin is already in the eyes of big institutions at this early stage, then you know you're on to something.
Shitcoiners are not going to let us have our fun
Nostr might have started as a Bitcoin-centric tool, but like Bitcoin its a protocol for enemies, you can say and do what you like on nostr, and if certain clients or relays don't like what you're doing you can find one that do or build your own.
If you're not a fan of zaps and you want to use stablecoins or your preferred shitcoin, you could build that into your own nostr client and relays that support it. But this would mean you are supporting nostr, since you're growing the user base and if your project failed, those users would simply login to the nostr clients and relays that remain.
But that's not the shitcoiner way, they don't want to compete, they want to extract value while its possible, the shitcoiner way is to try and create walled gardens where they can sucker you in and dilute you slowly or quickly.

Nothing new to the space
SocialFi is nothing new, if you've paid attention to this space long enough you would know that a lot of this is the rebranding of failed ideas and projects for a new cohort of users.
For those of you who were not around from 2016 during the ICO phase, you might not know that social media on the blockchain was all the rage. It was tried on separate blockchains like STEEM, these social applications like STEEMIT were wildly popular back then, running up to over 1 billion in market cap and were firmly in the top 10 tokens at the time.
Today it's still around, with a tiny user base, most people have abandoned it, those who profited from it have gone on to build new scams and the token has fallen down the ranks.

STEEM price action since launch
The way this scam worked was you would pre-mine tokens for yourself and your buddies, and then build various dApps would reward users with new inflation. Users would create content on your site, and users with stake would upvote their content.
When you upvote content you receive an amount of tokens, which is usually autostaked and the incentive for you is to create more content to earn tokens or buy tokens to build up a reputation so you can control more of the inflation through upvotes.
As users earned tokens and purchased tokens to stake them, you as the pre-mine owner get to sell into that demand and you have less competition for sales as the incentive is to stake to gain influence on the platform, so you're profiting off peoples egos and the gamification of the system.
Eventually, like all inflationary shitcoin projects you run out of new suckers and the original suckers feel they want to profit too and start dumping inflation just keeps pumping out, and you dilute demand to a point where your token is worth nothing.
I mention STEEM because it was probably the most "successful" relatively speaking, so i see this as the best outcome for these kinds of projects. Of course, there were others like Bitcoin Cash-funded Read Cash and Noise Cash, EOS-funded Trybe and Voice, SoMee, and Publish0x which used a bunch of random shitcoins.
Friends.tech and why we can't have nice things
So socialFI failed in 2018 and we all moved on from the dumb idea, the Bitcoin circles have picked up on nostr and it's got a fair bit of traction, so what do the shitcoiners do? Support Nostr?
Hell no, let's make socialFi 3.0 as part of this painfully stupid web3 narrative, and the first play in this new brand of SocialFI seems to be friends.tech.
An app that emerged out of nowhere and is built on Base Coinbases fork of ETH which is a weird choice, but it hasn't stopped its growth in a week the network reached 136,000 daily active users beating out OpenSea over the same time frame.
How much of that is real or just botting I don't know but that's the numbers being promoted.
So what is this app all about? Uncensorable social media? Owning your data? Migrating your data between apps seamlessly? No
The app essentially allows users to tokenize your social network by selling shares in your profile. So influencers in the space can sell access to themselves since buying someone’s share grants owners the ability to exchange private messages with them.
The new social app has driven 4,400 ETH ($8.1 million) in trading volume in less than 24 hours since its launch, far surpassing OpenSea’s in the same time frame.
Again these user numbers and trading value is not verified, and we don't know how much is just botting or wash trading to create attractive metrics to sucker people in, but sucker people in they will.
To me this just looks like another zero some game of extracting wealth from your followers, as if influencers don't already do this, I don't see how this is in anyway decentralised or an improvement on social media today, in fact I think it just super charges the worst kind of behaviour we see on social media and I don't see this app living longer than a footnote of 2023.
Sources:
- https://www.coindesk.com/web3/2023/08/11/is-friendtech-a-friend-or-foe-a-dive-into-the-new-social-app-driving-millions-in-trading-volume/
- https://captainaltcoin.com/friend-tech-leads-the-way-for-the-next-generation-of-socialfi-on-basechain/
-
 @ 604e96e0:20279eb2
2023-08-11 18:39:36
@ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab.
At this point, I'm sure a lot of you are feeling like this:

Let's breakdown the instructions from the README.
Prerequisites
Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm.
Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in
terminalto open the terminal. On other platforms, you'll have to ask ChatGPT 😂 .To verify installation of Node.js type
node -v. To verify installation typenpm -v.It should look something like this:

Leave the terminal open.
Downloading the code to your computer
The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says
Codeon it and clickDownload ZIPfrom the menu.
Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the
cdcommand. If you unzipped the folder in theDownloadsfolder, you can navigate to the folder by typingcd ~/Downloads/notacomment-main/.Usage With Strike
- Create an account with Strike if you don't already have one https://strike.me/download/
- Get a Strike API key with all the payment scopes from https://dashboard.strike.me/
- Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example)
- Install the dependencies using npm or yarn or whatever your heart desires
- Make sure you have money in your Strike account
- Run the script
npm start
Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap.
Usage With LNbits
I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key.
- Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example)
- Install the dependencies using npm or yarn or whatever your heart desires
- Make sure you have sats in your LNbits wallet
- Run the script
npm start
Usage With Nostr Wallet Connect
- Create a NWC connection string using something like https://nwc.getalby.com/
- Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example)
- Install the dependencies using npm or yarn or whatever your heart desires
- Make sure you have sats in your wallet that you generated the NWC connection string with
- Run the script
npm start
Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:

-
 @ 6e75f797:a8eee74e
2023-08-10 19:52:47
@ 6e75f797:a8eee74e
2023-08-10 19:52:47I've received a few questions from other creators about streaming on ZapStream so I've decided to write this short introduction to ZapStream and, for those who don't have a nostr account yet, a simple 3-step guide to get started on nostr.
What is ZapStream?
ZapStream is a live streaming platform built on the nostr protocol allowing creators to stream and instantly monetize their content on a true and circular value4value social media network. On ZapStream there is no “road to affiliate” grind, no perks and no revenue share with the platform.
What is nostr?
Nostr - notes and other stuff transported by relays
Nostr is a simple, open protocol that enables global, decentralized, and censorship-resistant social media. When creating an account for nostr you’re able to access any app, website or platform through one account. No user names, password or two-factor authentication. Your nostr account is your key to everything nostr. Guard it well!

Creating a nostr account
There are many ways to join the nostr network but for the purpose of this tutorial I’ve decided to focus on guiding you through three simple steps.
GetAlby
This browser extension is your authenticator for the nostr network and doubles as a Bitcoin lightning wallet. Head to GetAlby and add the extension to your browser to create a GetAlby account.
Snort
Snort is one of many social media sites on the nostr network. You could compare it to platforms like Twitter. Once you’ve created your GetAlby account, head over to Snort.social and authenticate with your brand new extension. WELCOME TO NOSTR!

Setting up your profile
On Snort browse to your profile settings and create your nostr profile. Avatar, banner, user name, display name, about (bio) website. NIP-5? Don’t worry about it just yet or click here to learn more about NIP-5. Now that you’ve joined the nostr network and created your profile it’s time to send your first note. Go back to the home page and say hi to the world.

ZapStream
Go to zap.stream and click the login button on the top right. Authenticate with your GetAlby extension and you’re almost ready to stream.
OBS Configuration
OBS tutorials
Configuring OBS depends very much on the users hardware components and bandwidth. Thus there is no “one guide fits all”. When installing OBS you’ll be prompted to run the setup wizard, run it. The wizard will identify your hardware and configure your OBS. Once OBS has auto-configured you can go into settings and customize the bitrate, output resolution and frame rate.
There are plenty of OBS tutorials on the internet for NVIDA, AMD and software encoding. Therefore we won't address this further in this guide. Google loves you.
Going Live
To go live on ZapStream click again on the top-right to grab the streaming URL and stream key. Select your desired stream option and add your stream info, cover and tags. Click save and hit start streaming in OBS. You're live!

Hosted
Connecting OBS to ZapStream is no different than connecting to any other site but you can choose from several options. Pick your desired option, copy the stream URL and stream key, add both to OBS and you’re ready to go.
Best
This option charges 10sats/min and offers server side encoding for your streams output (source, 720, 480, etc). ZapStream might add more features to this plan in the future but for now it’s only the guaranteed encoding for your viewers.
Basic
This option charges only 2.5sats/min but doesn’t offer server side output encoding. If you use this option consider setting your video settings in OBS to 30 FPS and rescale your output to 720 for best viewing quality. Viewers with a slower connection may experience blurry video. Thus using the Best solution is recommended in particular for gaming.
Self hosted
Creators with a server or Cloudflare account may stream directly to ZapStream through applications such as Owncast or others. Please refer to Cloudflare streaming or Owncast’s website for details on how-to setup your own streaming server.
Features / Options
OBS overlays
At the time of writing the only overlay available is the chat overlay. To add your chat to OBS, create a new browser source in OBS and add https://zap.stream/chat/YOURnostrPubkey to the source. By adding your nostr pubkey to the source your overlay will always show the chat of the current stream / nostr event.
OBS Docks
You can also add your chat as a custom dock to OBS. Use the same link as above when you create the dock allowing you to have your chat inside OBS rather than popping it out on your desktop.
Chat features
On nostr all content has unique event identifiers also known as nostr events. ZapStream supports embedding of almost any nostr event directly into your chat. This can be a note, emoji pack, goal or any other supported nostr event. To add an event add the tag nostr: before the event ID.
Chat moderation
Nostr is a censorship resistant and free speech centric protocol self-moderating the content users want to see or not see is the way to go. However, ZapStream supports muting of users (NIP-28, kind 10_000 events). This means that users can mute other users and anyone muted by the host will be muted in the creators chat for everyone else (host mute list).
Emote packs
As creator you can add your own emote packs to chat or use packs created by other nostr users. Head over to https://emojis-iota.vercel.app/ to create or add emotes to your account. Viewers may also use their own emotes and you can link emote packs in chat so viewers can add them to their own account.
Cards
Cards are the widgets you see below your stream. Cards support most nostr events, images, links and text. You can add your schedule, chat rules, referrals, partners or anything else you like by editing the cards.
Goals
Creators can create goals for their stream. The option to create a goal for the current stream scan be found above the chat. Add a goal name and the amount to be raised and click save. The goal will appear above your chat and it will be removed at the end of your stream or when starting a new stream. Goals can be also added to cards. To add a custom goal to a card head over to https://goals-silk.vercel.app/, create a custom url and then copy/paste the event ID of the goal into the text field of a card. Goals also work in chat.
Dedicated yourname@zap.stream handle
Creators may also secure a unique ZapStream identifier through Snort.social. To secure your handle head over to https://snort.social/settings/handle, add your channel name and pay the invoice. One you’ve secured your handle you’ll be able to use https://zap.stream/YOURHANDLE for your ZapStream.
Reference links for ZapStream and nostr:
-
 @ 3bf0c63f:aefa459d
2023-08-10 17:52:16
@ 3bf0c63f:aefa459d
2023-08-10 17:52:16Things that we mostly can't fix, but that maybe could have been done better if they were here from the beginning -- or something like that.
- Choosing secp256k1 felt cool and maybe it still feels cool because it is the Bitcoin curve, but since many people have pointed out that other curves and algorithms are much faster maybe picking those would have been better.
- Writing a spec for direct messages and implementing them was bad. In my defense, it was an attempt to please the public, but still I should have not have done that, or thought more about it before doing it.
- For a long time I didn't realize Nostr wasn't useful just for "social networking" things. I wonder what else could have been better designed in the relay-client interface if the needs of non-social-networking apps were kept in mind.
- The querying system is sometimes too generic, it could have been better if it was more restrictive, but more complete. For example: allowing generic querying over tags is weird, can lead to O(n²) issues in some cases and relays are left to fend for themselves -- on the other hand we can't query for the absence of some tags. But I don't know how any of these things could have been better even today, so maybe it wasn't so bad.
- Making the events be JSON: sometimes I think this was a bad idea and a binary format would have been better, but most of the times I think Nostr wouldn't have become any popular at all if this was the case -- also binary is slower than JSON in JavaScript, so I guess this wasn't a completely bad choice. Perhaps if something like NSON had been adopted from the start, though, that would have been better for everybody.
When I decided to write this I had one item in mind, but when I started I forgot what that was. I'll add it here back when I remember.
-
 @ 668ceee5:930b960e
2023-08-08 11:25:59
@ 668ceee5:930b960e
2023-08-08 11:25:59So you've joined nostr, set up your lightning wallet, and started receiving zaps ⚡️ Maybe you've even participated in some zapathons. Bitcoin on nostr is a lot of fun, but why is everyone so excited about it?
I do not wish to get technical. While you can benefit greatly from learning about UTXOs and the other confusing things about Bitcoin, I want to talk about why Bitcoin is the hardest money ever discovered.
Many believe money is something governments create, or simply a figment of our imagination. As long as everyone believes the paper printed by governments is money, then we can have an economy. This is incorrect.
Money is actually an emergent property of trade. Suppose I have an apple, and I want your banana. We can trade, and this is called the barter system. But what if you don't want my apple because you would rather have oranges? How do I get your banana?
I could trade my apple for an orange and trade my orange for your banana, but this is obviously a huge inconvenience. Add a few million more goods to this equation, and we can see how this quickly becomes chaotic.
But humans are smart, and they eventually found a way to solve this problem with money. Money can be anything; this is true. However, we will soon see why some goods are better suited as money than others.
Suppose we all agree that apples will be the money we choose to exchange for goods. If I want bananas or oranges or iPhones, I give you a certain number of apples. This could work, because you know that you can purchase anything you want with apples, so you readily accept my apples.
https://cdn.nostr.build/p/rkMj.jpg
Eventually you want to buy a car that cost 1000 apples, so you start to save these apples. Everything is going great, until a few weeks later your apples start to rot. Nobody wants rotten apples, so you’re never getting that car.
Let's pretend apples do not rot, and you can successfully save 1000 apples. This takes you several years, and you can finally afford that car. However, people act; and since apples are money, everyone realized years ago that money can literally grow on trees. By the time you have saved 1000 apples, everyone has 10,000 apples from the trees they grew, and new apples are being harvested everyday.
The amount of a good in circulation divided by its annual production is called stock-to-flow ratio. As the production of apples quickly increases, the purchasing power of your apples decline because of apple inflation. This means our unrottable apples are not a good store of value, and therefore apples are easy money (as opposed to hard money).
https://cdn.nostr.build/p/ZEkl.jpg
Apples are terrible money, and humans eventually figured out they need something that doesn't rot or rust, while also having a low stock-to-flow ratio. This is how gold became the standard money of the world. Gold is practically indestructible, and despite many efforts from the alchemists, gold cannot be created. We must dig for gold, and put in real work to obtain it. Gold is also scarce, so it has one of the lowest stock-to-flow ratios of any resource in the world. For thousands of years, gold was the hardest money society had ever discovered. Gold sounds pretty awesome, doesn't it?
So what is so special about Bitcoin if we already have gold? Well, one of the most important distinctions is you cannot zap gold on nostr. This sounds like a joke, but it has very important implications.
https://cdn.nostr.build/p/owDW.jpg
Gold is bulky, it's difficult to divide into smaller units, and it's very expensive to transport. If I want to send you the equivalent of $1 in gold for your meme, it wouldn't be worth the trouble. Likewise, if we meet IRL and I have $10 in gold, but you only want $1 for your apple, it would be very difficult to divide my gold into exactly 1/10th pieces.
And this is how fiat dollars were born. The US used to be on a gold standard, where every dollar was a reciept for a certain amount of gold. This gave you the convenience of carrying a lightweight and easily divisible amount of gold.
It's important to note that governments did not declare paper and gold are money and force everyone to use it. On the contrary, governments form when a group of people are able to steal large amounts of gold, allowing them to afford armies that can steal even more gold.
The indestructibility of gold used to make this very easy. If I am the leader of a group of bandits and robbers, we can burn down your house and take the gold. However, there came a time when people began to trust and admire this group of bandits. So instead of burning down your house, I simply threaten you with violence and steal your gold. But don't worry, in return you get a piece of paper that we pretend is worth $1 in gold. Makes things more convenient for you, and I will safely store your gold in a centralized bank.
https://cdn.nostr.build/p/6xKa.jpg
This actually sounds like a decent deal, but after several years of trading paper for goods, the temptation to print more paper than the existing gold supply was too much. If a banker or politician can print $1000 to buy a brand new Model T, who's going to notice?
Well, like our inflated apples above, eventually the market noticed. People brought their paper receipts to the banks to get their gold back. But there wasn't enough gold, and this caused the Great Depression. Instead of owning their mistakes, governments and banks began working on a new form of economics based on the ideas of John Maynard Keynes. This is called Keynesian economics, but we will not get into all that.
https://cdn.nostr.build/p/nb2744.jpeg
The point is, gold has its flaws, and these flaws eventually led to the US Federal government being $32,000,000,000,000 in debt, endless wars, and a crumbling society.
But now we have Bitcoin. Like gold, Bitcoin is mined by powerful machines that require work. It cannot be created out of thin air. Bitcoin has a stock-to-flow ratio that is cut in half every four years. In the year 2140 there will be 21 million Bitcoin, and then no other Bitcoin will ever be mined again. This makes Bitcoin the most scarce resource in the universe.
Unlike gold, Bitcoin is not bulky, hard to divide, or difficult to transport because Bitcoin doesn't physically exist. Bitcoin is weightless, massless, easily divisible, and travels at the speed of light. You don't need to trust a bank to hold your Bitcoin, because instead of a vault, Bitcoin is held on 12 or 24 word seed phrases.
This means the equivalent of billions of dollars can be held on a single piece of paper, a metal plate, a digital hardware wallet, or even stored inside your thoughts. Nobody can burn down your house and steal it. If they threaten you with violence, they have no way to confirm the sats you give them are all you have.
https://cdn.nostr.build/p/nb2500.jpeg
Yes, this is the same Bitcoin we are all zapping each other on nostr. Not only is it more convenient than fake paper dollars, it is the greatest and hardest money ever discovered.
This is why Bitcoiners always stress the importance of self custody. Bitcoin is your property, and as history has shown time and time again, we cannot trust anyone. We cannot trust the governments, the banks, exchanges, or even the custodial wallets you download to your phone.
But all you have to do is have fun zapping your Bitcoin on nostr, move it to self custody when you accumulate a decent amount of sats, and wait for the market to respond. Because like gold before it, Bitcoin doesn’t need governments to accept it. Bitcoin is inevitable.
If you would like to learn more about the economics of Bitcoin and Austrian Economics in general, I highly recommend reading The Bitcoin Standard by nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak, which this note attempts to summarize.
-
 @ 89e14be4:a4fdd02c
2023-08-08 10:22:28
@ 89e14be4:a4fdd02c
2023-08-08 10:22:28 -
 @ fa984bd7:58018f52
2023-08-08 08:23:19
@ fa984bd7:58018f52
2023-08-08 08:23:19Let's talk about NIP-31, NIP-89 and how discoverability in Nostr is not only not broken, but it's a step-function improvement over the status quo of the siloed web.
The captured internet has organically evolved multiple solutions to enable discoverability, which is, the process of discovering new content / tools / people, etc.
These tools sit at the top of the internet food chain: Search engines, app stores, social networks' proprietary algorithms, etc.
These individual approaches are multi-billion industries on their own.
How are we, humble nostriches, supposed to compete with these giants and their enormous moats?
We compete by not competing. By playing a different game.
The game
Nostr has a funny design that makes for some very creative implementations.
In Nostr everything is an event. These events can reference other events. Each event has a
kindnumber, which represent what that event is. An event of kind 1 is a short note, what we typically call a tweet. An event of kind 7 is a reaction to another event, such as 🤙ing it. Zaps? Those are kind 9735.It's very simple. Painfully simple.
But the fact that these event kinds can mix together in a chaotic soup of events changes the game.
The soup
A few months ago I wrote an application based on Karnage's designs. Zapstr. It's a music player where everything you do is... you guessed it, a nostr event. Publishing a song. Listening to a song. Liking it, and of course, zapping it.
But also, you can respond to a song with a short note.
And that's the first ingredient of this soup.
The moment you find a song you like in this remote corner of the internet and make a comment about it, your followers, can see this comment on any other social application.
Of course, since Zapstr is an application with zero marketing budget, using a kind number I came up with (kind 31337, a wink to the elite hackers out there), your followers don't know what you're talking about.
You're talking to the void.
The void
This is where NIP-31 and NIP-89 come in.
Until these NIPs, you responding to a random song, or to a random anything, your followers will think you're going insane. You're responding with something like "Wow, this song moved me to my core", but you don't mention what song you're talking about.
Lana del rey, is that you?
NIP-31 is, like almost anything in nostr, simple as hell.
If you remember the good old
alttag in HTML<img>s that was so important when you were loading images on your 28k modem, you'll understand NIP-31. This NIP proposes that event kinds that are not widely supported by all clients, include analttag explaining, in a human readable format, what the event is about.alt: "This is a song 'Video Games' by Lana del Rey."Simple.
But now your followers have context.
Of course, the context is helpful. But insufficient for a full experience.
The full experience
The measuring stick most people will compare our ecosystem with, are superapps.
WeChat. X.com. Etc.
here's a reason these apps are so popular. It's not merely that people might crave being governed by a benevolent dictator; the convenience of superapps stands on its own merit.
The appeal of a superapp is the convenience of the seamless integration across use-cases.
Chat with your friends? ✅
Pay your bills? ✅
Get a ride? ✅ How about order some food while you're riding back home? ✅
The super app is the internet. Why leave? Why create a new account somewhere else? Why go through the hassle of connecting your payment methods, porting your social graph?
It's all so painful. What's the upside?
Of couse, if you've been paying attention, you feel that Nostr provides many of these properties.
Frictionless transition through all use cases: it's all just one npub!
Porting your social graph: there is no porting; your social graph already transcends whatever nostr clients you use.
Reconnecting your payment methods: well, we have bitcoin, and wallet connect, and lightning!
Putting it all together
Here the vision of the Nostr I see comes full circle, and why I believe nostr doesn't only NOT suffer from a discoverability problem, but it's actually orders of magnitude better than the status quo. We've just haven't fully built it yet.
Nostr allows any developer, with no marketing budget, to create an app, a new app, using a new kind number, on an incredibly niche use case of the internet/nostr, and leverage the liquid nature of how event kinds interoperate to provide organic reach to these new and strange use case of nostr/internet.
The glue
NIP-89 was that one last missing piece to make the experience of transitioning through multiple microapps cohesive. It provides two simple building blocks:
- a way for apps to "register" kind applications handlers (e.g. app X supports kind Y using such-and-such URL)
- a way for users to publicly associate kinds with these application handlers throughout their different platforms (e.g. web, vs ios)
A byproduct of this, is that anyone can query 1) which applications exist for a given kinds, and 2) which one the people they follow use.
Let's go back to the Zapstr example.
One of your followers sees that song, but clicking on the event yields nothing. Their client doesn't know what kind 31337 means, how to render, or interact with it.
But, using NIP-89 the client can ask the user's social graph "hey, what apps do you use for kind 31337?"
All the user experiences is the song opening up in Zapstr, or in any other app that supports kind 31337 as recommended by the people they follow.
From the people the user follows.
This is key.
This means that multiple applications can compete and win under the same use case in different communities.
A million microapps, one glue
Why do I insist that Nostr is orders-of-magnitude better than the siloed internet and the superapps approach?
Superapps need to appeal to everybody; they have to move carefully, iterate in small steps and remain very conservative. By their very nature, they MUST be bland (which is why all these superapps look very much alike and none of them look like ONOSENDAI)
Whereas in nostr we can experiment with the wildest of ideas and weirdest approaches since no app needs to serve all users. Perhaps a very weird app appeals to only 20 or 50 people, but it can transparently interact with all other apps serving the same event kind.
Long-tails all the way down.
As these microapps enable all types of niche use cases while maintaining interoperability and leveraging discoverability and distribution through nostr, the use cases of nostr begin to blend in and the artificial use-case silos break down.
App Stores need not apply
I believe App Stores are a synthetic solution to a problem that doesn't exist in Nostr.
App Stores exist due to the internet's lack of unification in exposing novel use cases to users.
App Stores are necessary because the captured internet lacks a way of unifying different use cases exposing novel use cases and applications to users. The main way of discovering these was through use cases.
But in this world, where within the context of a social client you might see when one of the people you follow posts a new product for sale, or adds a review to a concert, or takes notes about a book they're reading you can immediately discover these new use cases organically.
WTF happened in 1989?
For decades, we've operated within data silos, with each use case as its own isolated entity. The only trancendence of use-cases was the centralizing vertical-integration of a Facebook offering both social media and commerce.
YouTube data isn't interoperable with Spotify's. Twitter isn't interoperable with Amazon, and Airbnb doesn't inform in any sort of way what happens in reddit.
Every one of these use cases is its own thing, and, to stay relevant, they needed to persuade you to engage, engage, engage. We are all very aware of this and it's many pitfalls.
We know where that path leads.
But, as we've constructed Nostr apps we've erected similar use-case walls. Social clients are interoperable with other social clients, but the link to music clients, or to commerce websites, or to airbnb-like websites, etc, is mostly non-existent.
Just like in 1989, bringing down this wall, will unleash a great flurry of innovation and creativity. When Nostr can provide organic, free, non-invasive, discoverability and distribution to any new use case, we'll see millions of microapps bloom and new entrepreneurs and developers build on Nostr.
Developers, tear down this wall.
-
 @ 32e18276:5c68e245
2023-08-07 16:10:07
@ 32e18276:5c68e245
2023-08-07 16:10:07Hey guys,
I spent some time this weekend fixing a bunch of the bugs that were introduced in the latest nostrdb refactor. See the changelog below for the full list of changes in the latest build!
Planned this week
I have a big list of things I'm planning on adding to Damus this week:
- Lists!
- Zap improvements: Bringing back top zap comments in threads, profile zap comments in notifications, Private DM Zaps
- Video player improvements
- Sharing improvements (share to damus, etc)

Make sure to come back in a week to see how much I could get done!
Changelog
Added
- Add close button to custom reactions (Suhail Saqan)
- Add ability to change order of custom reactions (Suhail Saqan)
- Adjustable font size (William Casarin)
Changed
- Show renotes in Notes timeline (William Casarin)
Fixed
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Don't cutoff text in notifications (William Casarin)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fixed nostr reporting decoding (William Casarin)
- Dismiss qr screen on scan (Suhail Saqan)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix crash when muting threads (Bryan Montz)
-
 @ 80ee8a95:b2862d2e
2023-08-18 22:36:30
@ 80ee8a95:b2862d2e
2023-08-18 22:36:30In a prosperous nation like Australia, the issues that Bitcoin aim to solve are far less perceivable compared to other poorer or authoritarian nations. Bitcoin’s value proposition is less relatable because we have access to banks, our economies are generally tolerable, and everything to some degree just works.
Conversations about Bitcoin in the workplace or among friends and family can be difficult. You may often be dismissed, called names (mine is “future boy”), or perceived as someone belonging to a cult. And people will bring up the common arguments against Bitcoin purported by the media: 1) it uses to much energy, 2) it is volatile, 3) it encourages criminal activity like the silk road, 4) it is a Ponzi scheme, 5) its an intangible asset, and 6) its a speculative and immature technology.
Here I will offer some tips I have learnt when talking to people about Bitcoin. My frame of reference is as a Bitcoiner living in Australia, but I think my experience may translate to other developed nations.
Tip 1: Never try convince someone they should buy Bitcoin.
My first tip is to never try convince people to buy Bitcoin, but instead, teach them about Bitcoin and guide them towards sources where they can learn more themselves. The value proposition behind Bitcoin is difficult to understand and people shouldn’t necessarily hold any before they understand the risks and benefits behind the technology.
In my mind, the most important part of a person’s orange pilling is the will and interest to find out more themselves, and make their own decision to buy some.
So your primary aim should be just to find a way to make them interested enough to seek out more information. Here is my shortlist of books, podcasts, and other valuable sources I use when pointing people to find out more.
Tip 2: Bitcoin is an inclusive technology.
One major problem I see with the Bitcoin community is that Bitcoiners set up walls where you are either enlightened Bitcoiner, or you are a “normie”. For someone seeking to find out more about Bitcoin, the community can appear cultish, and being referred to as a “normie” or other names creates an exclusive environment that can dissuade people from finding out more. Everyone will have their own path of discovery as most of us did. Help others find Bitcoin by making the community inclusive.
Tip 3: Be prepared to combat common misconceptions or misunderstandings
1. Bitcoin uses more energy than some country in Europe
This is probably the most common argument I hear. But as you will see, the real question here is not about the absolute amount of energy use, but a person’s perception of the value per unit energy that it delivers.
The adoption of any new technology that advances society has required energy. This energy consumption is often intense at the beginning and becomes more efficient as the technology develops and drives further investment. Bitcoin miners are the primary consumers of energy in the technology. Most people don’t actually understand why Bitcoin consumes energy — Bitcoin consumes energy to cryptographically protect the value contained within the network. However, inherent to Bitcoin is an economic incentive to reduce energy costs and maximise profits. Miner’s therefore naturally seek out more efficient technologies and cheaper sources of energy.
Over a 5 year period from 2018 to 2023, the energy required per terrahash (energy per unit work) declined by 63%. It is also useful to highlight novel ways in which Bitcoin miners are consuming wasted energy or using renewable sources, such as Iris energy, or Gridless. These and other companies are investing into renewable energy sources. Current estimates of Bitcoin’s renewable energy usage is between 25% and 50%.
In 2016 the power consumption of data centres was estimated to be 200 TWh/y. By comparison, Bitcoin consumes between 75.4 TWh/y and 122 TWh/y. The traditional financial system is estimated to consume 5,000 TWh/y which pales to Bitcoin’s consumption. This is not to say we should be complacent about Bitcoin’s energy use; these are all staggering amounts of energy consumption! But in most people’s mind, the value of data centres and the legacy financial system seems so obvious that they wouldn’t question its energy usage. So the real question should not be about the absolute value of power consumption, but rather whether Bitcoin provides the same global value per unit energy consumed.
Framing the energy argument in terms of the value per unit energy should help to open a discussion on Bitcoin’s value proposition.
2. Bitcoin is volatile
Yes, Bitcoin is volatile! But why is this bad? Most people making this claim are comparing Bitcoin to holding shares in some big tech company. Bitcoin is not a company! Comparing it to a company means you haven’t understood the Bitcoin’s true value proposition of it becoming the hardest form of money. Furthermore, despite its current volatility, Bitcoin continues to outperform most stocks and gold.
Bitcoin is a truly free market asset, unlike other forms of investment influenced by capital controls which act to dampen volatility. Bitcoin’s adoption still sits below 5% globally. As adoption increases, its price will continue to stabilise as it has been over the past decade (see figure below).
 Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)
Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)Volatility will continue to be a feature of Bitcoin in the near future. But this is not necessarily bad. Investment into Bitcoin, like any asset, should be taken with consideration of a person’s financial position and their ability to weather this volatility.
3. Bitcoin facilitates illicit activity and the anonymity of the criminals.
There is no escaping the fact that to some degree Bitcoin has facilitated the exchange of drugs and other illicit activity. However, Bitcoin offers a level of traceability that hasn’t existed previously with cash. Bitcoin is not anonymous, it is pseudonymous. It depends on a public ledger that facilitates the tracking funds, and KYC (Know-Your-Customer) on/off ramps that help link transactions back to individuals. This tracking has led to the downfall of the silk road and several associated criminals since. Law enforcement and journalists are constantly coming up with tools to track the the movement of cryptocurrencies used in illicit activity.
Bitcoin is a neutral technology. Blaming Bitcoin for the drug problem is as silly as blaming the internet, the postage service that sends a large portion of drugs, or cars that drive them from location to location. It will never be escape the fact that some people will use it for illegal activity, as people have and will continue to do with any form of money.
4. Bitcoin is a Ponzi scheme.
Many other cryptocurrencies which are actual Ponzi schemes have given people a negative impression of Bitcoin. I once had a family member, who knew about my great interest in Bitcoin gleefully exclaim “Hey did you hear!? Bitcoin is dead!” She was referring to the news about the downfall of OneCoin. This comment made me realise how important it is to help people understand the fundamental difference between a decentralised Bitcoin and a centralised crypto Ponzi.
In simple terms, Bitcoin being decentralised means there is no single entity in charge or profiting from the value of Bitcoin, nor are there profits derived from getting people into Bitcoin.
A follow-on comment I often get is that early adopters cause an imbalance in the distribution of wealth. This is currently true. It is estimated that 0.01% of addresses hold 58% of all Bitcoin. But we currently live in a world of rapidly rising inequality and a financial system that promotes the financial privileged. Over the past 40 years, the top 1% of income earners has seen their share increase from about 11% to almost 20% in the USA (see figure below).
 Total share of income of the top 1% of earners (source: https://wid.world/)
Total share of income of the top 1% of earners (source: https://wid.world/)You can research into the effects leading to inequality and you will read very contradictory arguments from both sides of the Bitcoin camp. So I’m not going to argue that Bitcoin solves the problem of wealth inequality; that is yet to be seen. But the growing digitisation of financial services is already creating a positive effect in reducing wealth inequality around the world. One of Bitcoins main benefits is that it promotes financial inclusion, which I believe can only result in a positive outcome for reducing inequality.
5. Bitcoin is an intangible asset
I once tried to explain to a family member the link between physical gold and Bitcoin. I used the analogy that energy is trapped in physical gold, and energy is required to extract it. This is similar to extracting and storing energy in Bitcoin. He laughed at me smugly.
Some people will have a really hard time comparing a physical asset to a digital one. They assume a digital asset can be copied, and it has no meaningful use in the real world. Bitcoin requires some tech literacy which you cannot teach in an evening!
Instead, you can highlight that a physical asset like gold is a great store of value; we have been using it to store value for millennia. But it is not a great medium of exchange. How can you break it up into smaller pieces? How do you send it across the world?
Bitcoin solves these problems. Like gold, Bitcoin cannot be copied or debased. But unlike gold, you can send fractions of a Bitcoin instantly anywhere across the globe.
6. Bitcoin is a speculative and immature technology.
Trace Mayer used to talk about the seven network effects of Bitcoin: Speculation, Merchant Adoption, Consumer Adoption, Security, Developer Mindshare, Financialization, and Adoption as a World Reserve Currency.
Speculation, being the first network effect, is an important part of Bitcoin’s maturation. Speculation drives early adoption and leads to the initial growth and innovation. Early adopters face larger risks as the price is more volatile, but also reap larger rewards. As more people adopt, merchants begin to accept it as forms of payment, leading to the second network effect and so on.
Yes, Bitcoin was a speculative asset but it is far beyond it speculative stage. We are currently closer to the “Developer mindshare” stage, where developers are working on new tools and new products that now integrate multiple technologies, like lightning and nostr.
Bitcoin is no longer speculative. I would also argue it is not even immature, even though it has only been around for a decade. But a misconception people often make is that the dollar (AUD or USD) is mature. The dollar as we know it is an experiment that has been running since around 1971, and politicians and economists still have no idea how to control it! Levers are pulled, money is debased and debt is increased time and time again.
 Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)
Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)And thats it! I hope you found this useful for the next time you’re speaking to someone about Bitcoin in a developed nation.
Bitcoin Beme
Liked this article? help support more bitcoin: bc1q880n3vjzqa054xr6hwcx7756873z47kcqr052s ln-url: ourbean71@walletofsatoshi.com
-
 @ 6e75f797:a8eee74e
2023-08-07 13:16:42
@ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky on ZapStream and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.
 NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.
NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of Oceanbee, HolgerHatGarKeineNode or taette.

If you already own NMS, feel free to add me!
My NMS friend code is: EMAZ-KMHT-ZPFXP
See you in space Traveller! - TheGrinder
-
 @ 30782a83:3d5f1177
2023-08-18 17:00:55
@ 30782a83:3d5f1177
2023-08-18 17:00:55Remember that feeling when you were a child, and the world seemed to be a wonderful place full of possibilities? You were full of hope and had many dreams; everything seemed possible.
As you grow older, you learn about the numerous atrocities committed throughout history and even today. Every day, so many people are economically exploited by others, leading to a great amount of suffering. You start to feel hopeless, frustrated and overwhelmed, thinking that you, as a small part of the world, might not be able to do anything about it.
Then, you learn about the crucial role money plays in allowing that exploitation, wars, and tyranny, specifically fiat money controlled by corrupt individuals. You begin questioning what money truly is and how broken the current fiat world has become.
You realize why Bitcoin was created and start going down the rabbit hole, learning all the details about how it achieves the goal of being the best form of money humankind has ever seen.
And then... an incredible thing happens in your mind. That amazing, childlike feeling of wonder and endless possibilities returns. You start to feel hope again and believe that one person using the right tools can make a significant difference in the world.
Once that happens, your life is completely transformed. Your priorities change – low time preference – and you start evaluating how you spend your time, professionally, for instance. You begin to think about how you can use your time in a way that not only increases bitcoin adoption but also contributes, even in a small way, to fixing the problems you see in the world.
You understand why proof-of-work is critically important, not only in securing the Bitcoin network but also in every small detail of life and interactions between people. Hardworking individuals shouldn't have their savings for the future stolen by parasites, exploiters, fleas and those who avoid work at all costs.
Bitcoin is a tool in this peaceful war against laziness.
Bitcoin enforces an ethical and fair world for people who embrace work as proof of their livelihood.
-
 @ d030bd23:96435da9
2023-08-18 14:59:48
@ d030bd23:96435da9
2023-08-18 14:59:48I would like to share an alternative management for constipation other than lactulose. Just a quick recap, lactulose is a type of laxative that works by increasing the osmolality of the Gastro intestinal tract, inducing water absorption into the feces. While it is a common medication for constipation, it has one particular side effect which is dependency.
Actually, the best way to alleviate constipation is by increasing fiber intake, although this process is relatively slow. However, there is one type of fiber that is quite effective, which is psyllium husk.

Psyllium comes from the plant genus Plantago whose seeds are used as a traditional preparation to treat constipation and mild diarrhea. Its mechanism of action is as a bulk-forming laxative. It has a lower dependency effect compare to lactulose. Additionally, it also has other co-beneficial effects such as being a normoglycemic (reduce blood sugar) agent and a hypocholestremic (reduce cholesterol level) agent.
However, it is not without side effects. Being of plant origin, some people may develop allergy towards it. Additionally, it may worsen constipation or even cause choking if taken without adequate water. It is to be noted that it can be taken in pregnancy , though with caution.

The recommended dosage to consume psyllium husk is one tablespoon dissolve in 1 cup of water once daily and can be taken up to twice daily.
-
 @ 35a8f9c0:351dae66
2023-08-04 07:36:31
@ 35a8f9c0:351dae66
2023-08-04 07:36:31test
-
 @ a367f9eb:0633efea
2023-08-18 14:37:01
@ a367f9eb:0633efea
2023-08-18 14:37:01Latin America is a messy, culturally-rich, and prickly place.
Though it is blessed with bountiful resources in its sprawling jungles, deserts, and jagged mountains, it has for most of its history been caught in the oscillating winds of colonial powers and external forces.
While the 19th century saw the withering influence of Spanish colonialism against the rise of independence movements, the first part of the 20th century was defined by constant overt and clandestine interventionism on behalf of the Anglo powers, namely Britain and certainly the United States.
From the 1950s onwards, those interventions multiplied, as foreign intelligence services and corporations supported factions and political leaders who swung voraciously between socialist and fascist iterations of violence and strength.
Populist-led left-wing movements led to mass nationalization of properties and businesses, only to be countered by strong-fisted military juntas who carried out mass persecutions. Political violence was the norm, practiced brutally by the right and harshly by the left.
In the second decade of the 21st century, that naked political violence is isolated to regional narco-gangs, but interventionism is now practiced enthusiastically by economically left-leaning political governments with broad social agendas.
Nowhere has that been the case more than Argentina, once the crown jewel of the Spanish-speaking world.
Though it was a booming economy in the late 1800s, at a various points of the 1900s, its last two decades have proven to be a catastrophic economic failure. Kirchnerism, Argentina’s version of left-wing populism, has scarred its citizens with years of bank runs, currency devaluation, and eye-watering inflation.
The “Argentina paradox” continues to befuddle us.
ENTER THE HAIRDO
Skipping over plenty of historical and political history, Argentina today remains a basket case. Inflation has reached an abysmal 113%, its working population is far outnumbered by pensioners and those who live on government aid, and its debts are long past sustainable.
Rather than continue to shackle Argentines to the doomed Kirchnerism, economist and political upstart Javier Milei is promising something different.
The leader of the La Libertad Avanza coalition, Milei is an iconoclast.

With his wild hairdo (which he claims he never combs), sideburns, and salty tongue, he takes his inspiration from the Austrian School of Economics, professing daily his hatred of central banks, central planners, and the central political elite who have “looted” Argentinian prosperity through taxation and subsidies. Did I mention he loves Bitcoin?
In the usual lazy journalistic trope, coverage of Milei’s presidential aspirations in the Anglosphere pin him ideologically to Donald Trump or Brazil’s Jair Bolsonaro. They call him “far-right” and the new populist of the right.
And while he may throw bombs in his rhetoric, Milei is no slouch.
He’s written over 50 academic papers, 9 books, and has had an impressive career as both a university and private sector economist.
He identifies as an anarcho-capitalist, and regularly claims “taxation is theft”. For him, China is a communist dictatorship and most global trade deals are “managed” to benefit the politically connected. Free trade and free exchange are the saviors, not state control.
For those of us familiar with the Austrian tradition and a healthy skepticism of both centralized power and central banking, Milei proves interesting. For Bitcoiners, he’s an all-out star.
On top of that, he just won the first round of the presidential primary with over 30% of the vote. He’s not just a phenomenon among Bitcoiners and libertarians, but it seems his message is popular with a large slice of the Argentinian population.
THE MILEI PLAN
Unique to the moment, Milei focuses almost exclusively on economic policy in his speeches and interviews. He’s left most foreign policy and non-economic domestic issues to his running mate, Victoria Villarruel, who is a hawkish right-leaning lawyer (much more could be written about her).
Rather than choose between the “socialists with good manners and those with bad manners,” Milei posits that the people of Argentina want a return to fiscal sanity, and he is the man to make it happen.
How will this be achieved?
A radical dollarization plan, an end to the Central Bank, record slashing of public spending, and a healthy bout of privatizations of public institutions.
He describes his economic plank on four different axioms:
- Moral: the current system perpetuates robbery of the people by the elite through inflation and high taxes
- Technical: there is no natural demand for the Argentinian peso, and thus its real value is zero
- Instrumental: there are existing plans for adopting the US dollar that he would endorse (including research by economist Emilio Ocampo)
- Political: politicians who benefit from the system will fight tooth and nail to defend it, and thus the goal should be to disempower them by reducing the size of the state
For Bitcoiners, his best moments have come from his disparaging of the government’s monopoly on money creation, which he believes have been pivotal to Argentina’s failures. Money should be a “creation of the private sector,” he claims, hence why he is fascinated by Satoshi’s innovation of Bitcoin.
BEYOND THE PESO AND DOLLAR
Though many in the United States deplore the role of fiat money and the US dollar, Milei is steadfast in his commitment to get his country on the US dollar standard.
Many Bitcoiners may balk at this, but it makes sense for Argentina.
Stripping control of the money supply from the politicians and central bankers — who have ushered in decades of low growth and inflation — is about as radical as you can go in Latin America, and it would be a paradigm shift for an economy as large as Argentina’s.
Milei has flirted with free banking and welcomes currency competition, so it’s no surprise that Bitcoin may play a part in his success if he’s elected this fall.
Until then however, Milei will have many enemies to slay. Apart from political attacks from his opponents, we can expect that a hostile media will aim to counter each point he presents to the public. Central bankers and those connected to them will use all means possible to dissuade the people from choosing Milei as their man (which we saw in the dumping of bonds in the market this week).
Milei’s path will not be easy and many taboos will be broken.
His attacks on the “parasitic political caste” and more conservative social views have been enough to warn off many liberals and libertarians who would otherwise be favorable to his economic agenda.
But in a time of festering bad ideas on economics, trade, and how to make our societies more well off, Milei is a welcome distraction.
“What's the difference between a genius and a madman?” he asked in an interview this week. “Success. And that we shall see that on October 22.”
Best,
Yaël
Originally published on Fix The Money
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ 20986fb8:cdac21b3
2023-08-03 15:51:06
@ 20986fb8:cdac21b3
2023-08-03 15:51:06YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Round 3 will be from 3rd to 7th Aug
How to participate:
- Pick one or multiple Updates below, test it (them)
- Write your feedback and opinion (pros and cons are all welcomed)
- Don't forget to add taggs 'YakiHonne-updates' and 'YakiHonne' to your article
- Post your article on Nostr via YakiHonne.com
- Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our group: http://t.me/YakiHonne_Daily_Featured
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped during each round.
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
Updates to be tested in Round 3:
- Reporting: NIP-56 supported, users now have the ability to report undesired long-form content within the platform.
- Zaps: confirmation prompt to notify the sender that the transaction successfully completed; Zaps stat icon now function same as the original zapping button, so that users can intuitively fast acces to it.
- NIP-05 support: users now have the ability to add their NIP-05 to their profile settings and view other users identifiers across the platform.
- Images upload: all across yakihonne client now have the option to either paste a url image or instantly upload images within yakihonne server (instant uploads for the write article section is coming soon); not restricted to 1MB anymore, use wisely and avoid large images.
- Back-to-Top button: on the home feed page(right-bottom corner) for a quicker navigation.
- Welcome to feedback your suggestions and bugs reporting.
If you missed Round 1 & 2, the updates below could be tested as additions:
Round 2:
-
Comments: re-implemented and comments can be deleted
-
NIP-25 supporting: users now can upvote and downvote
-
Zap stats: Zaps sent and Zaps received can be seen from users profiles
-
“login with an extension” button: now it is grayed out rather than invisible
-
Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme
-
Tags: click on the tags in the article to view the content under the tag
-
Share: sharing posts with one click
-
NIP-05: verify your profile
Round 1:
-
Comment function: more user-friendly
-
Stats area: clearly displays the interactive status of each article
-
Following function: generated-key users can also be followed
-
Curation function: easily add or remove articles from an existing curation
-
Tags: search and browse articles with the tags
-
Home feed scrolling pagination: optimized data fetching and faster loading time
-
Article editing preview: preview the final version of the article while writing in MarkDown
Don't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 83d999a1:46171d19
2023-08-03 13:56:27
@ 83d999a1:46171d19
2023-08-03 13:56:27We are building something cool that maybe you'll be interested in.
What is this? An announcement of an announcement (AoA for short)?
Well. Yes.
But bear with us.
We are doing an AoA because we haven't figured out all the details yet, (e.g. the name of what we're doing)
But here is what we do know:
- 2 months of focused building in #madeira.
- 21 builders with a record of shipping things in the #lightning/#nostr space
- working individually or in teams to make progress towards advancing freedom tech
- nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft will be physically (and spiritually) there to help bounce ideas off
- Funding (likely) available to all teams
Dates? Jan 8th - March 1st.
How to be a part of it? Details to follow very soon™️
But in the mean time, if you're stoked, DM us at nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5.
-
 @ 7cc328a0:2a247c0e
2023-08-03 00:40:02
@ 7cc328a0:2a247c0e
2023-08-03 00:40:02I built a really cool little temperature and air quality sensor that reports data to particle.io events and from there into influxdb cloud.
With Free Dashboards!!
Yes I mean free as free can get. Particle.io, free (to 100 devices). InfluxDB cloud, free (to (x) amount of stats). We're not talking about a lot of stats here, but after many hours of research for a free dashboard solution this was the absolute best!
InfluxDB cloud dashboards look really nice as well.
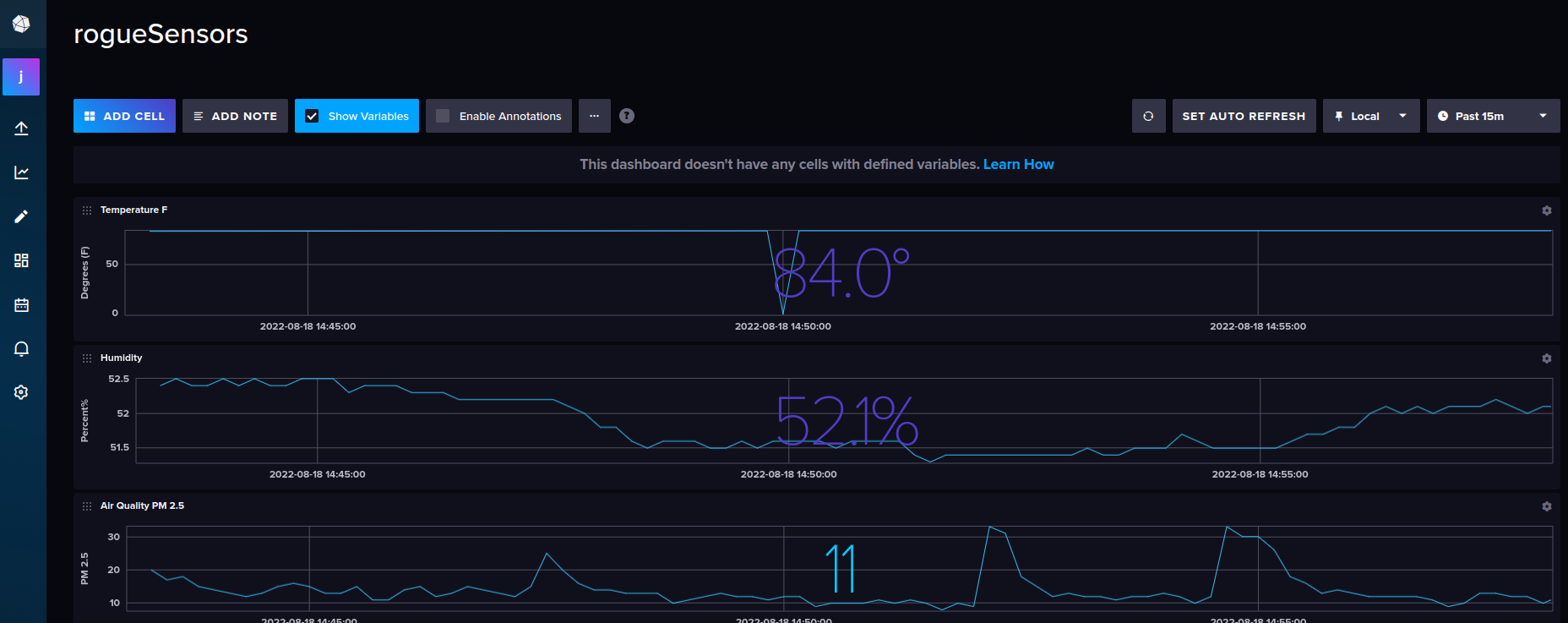
Build Components
- RedBear Duo github
Note, particle.io has since aquired RedBear labs and the Duo is old, yet still available in some places. You may also want to try particle devices like Argon instead of a redbear.
- DHT22 Temperature/Humidity sensor adafruit
- PM2.5 Air Quality Sensor and Breadboard Adapter Kit - PMS5003/PMS7003 adafruit
Note, I used a slightly different adapter, and it was lame to have to order it once I realized the PMS7003 I ordered did not come with an adaptor! The adafruit link above should get you hooked up. These air quality sensors come in different flavors just make sure you have a breakout board along with it when you order!
Software
Steps
The Hardware wiring diagram
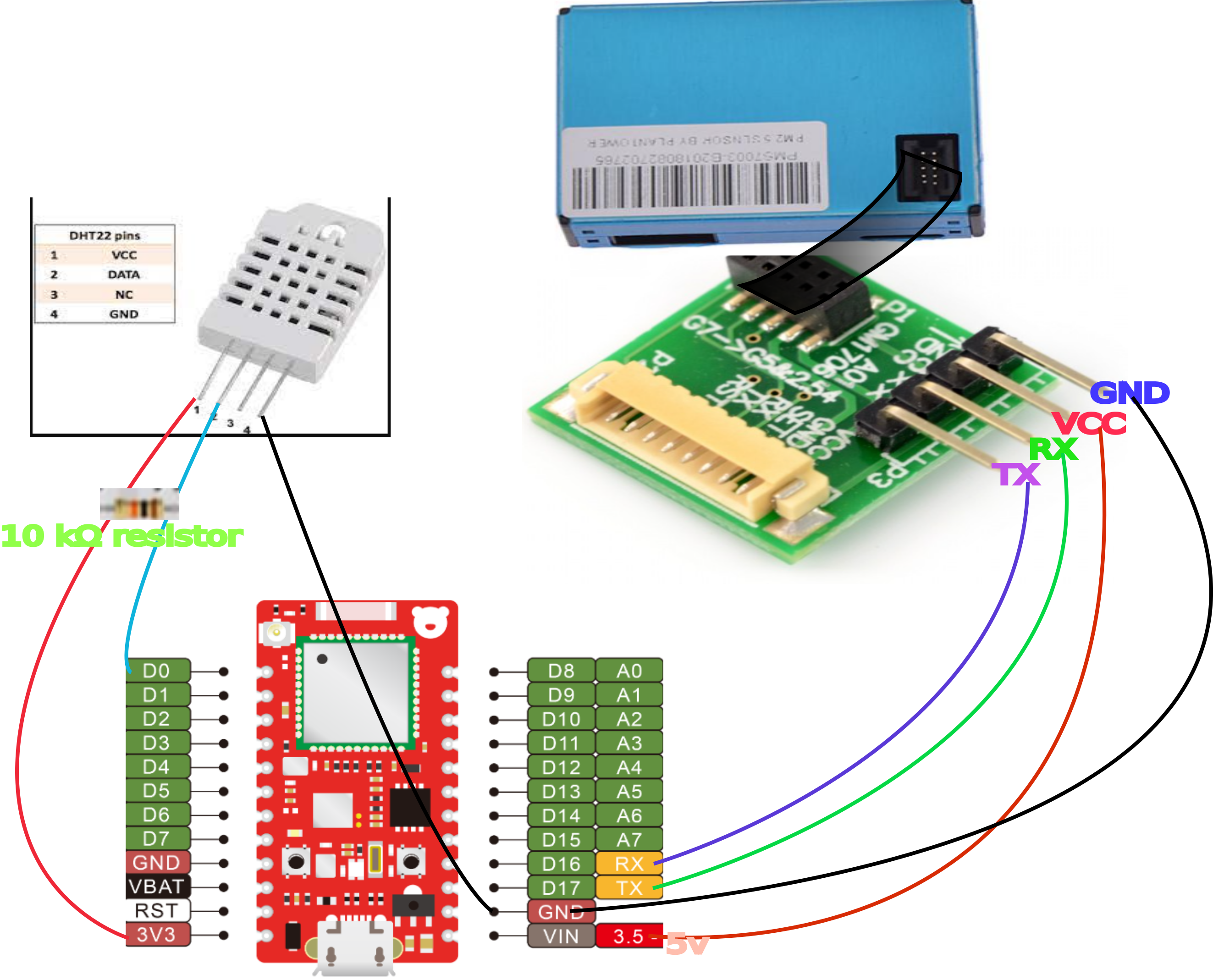
Plug in your device and connect it to particle.io
I used the following guide for the Redbear DUO here
Coding the application
- Go to console.particle.io, open the IDE by clicking the icon (bottom left < >)
- Create a new application.
- Click the "Libraries" icon on the bottom left of the screen.
- In the "Libraries" search enter "PMS7003-Particle-Sensor-Serial" and import it into the project.
- Click "Libraries" again, and search for "Adafruit_DHT_Particle" and import it into the project.
Paste this code into your app: ```arduino // This #include statement was automatically added by the Particle IDE.
include
// This #include statement was automatically added by the Particle IDE.
include
PMS7003Serial
pms7003(Serial1, D0); define DHTPIN D0 // what pin we're connected to
// Here we define the type of sensor used
define DHTTYPE DHT22 // DHT11 or DHT22
DHT dht(DHTPIN, DHTTYPE);
void setup() { //Serial.begin(); dht.begin();
}
unsigned long last = 0; unsigned long last_pm_reading = 0;
void loop() {
unsigned long now = millis();
// check every time to see if there is data if (pms7003.Read()) { last_pm_reading = now; }
if ((now - last) > 10000) { float f = dht.getTempFarenheit(); float h = dht.getHumidity(); Particle.publish("TempDegreesF", String(f)); Particle.publish("PercentHumidity", String(h)); // Let us be generous. Active state the device // reports at least every 2.3 seconds. if ((now - last_pm_reading) > 10000) { Particle.publish("No reading for at least 10 seconds!"); } else { Particle.publish("pm1", String(pms7003.GetData(pms7003.pm1_0))); Particle.publish("pm2_5",String(pms7003.GetData(pms7003.pm2_5))); Particle.publish("pm10",String(pms7003.GetData(pms7003.pm10))); // I didn't use these but they're there if you want them in the future. /Serial.println("um_3:" + String(pms7003.GetData(pms7003.count0_3um))); Serial.println("um_5:" + String(pms7003.GetData(pms7003.count0_5um))); Serial.println("um1:" + String(pms7003.GetData(pms7003.count1um))); Serial.println("um2_5:" + String(pms7003.GetData(pms7003.count2_5um))); Serial.println("um5:" + String(pms7003.GetData(pms7003.count5um))); Serial.println("um10:" + String(pms7003.GetData(pms7003.count10um))); / } last = now; } } ```
Flash the application to the device
You should see events coming into the particle.io console
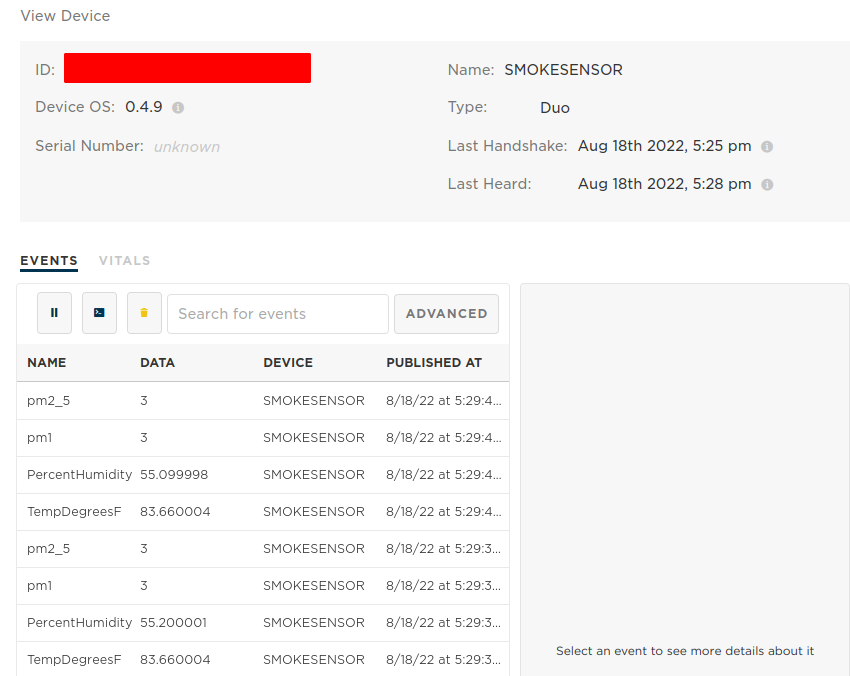
Now we're ready to setup InfluxDB
- Create a new bucket called "sensors" (or whatever you like)
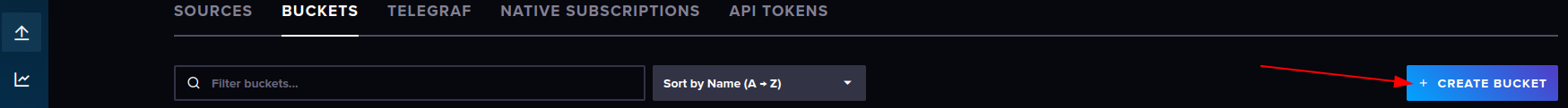
- Keep this window open or copy these settings, we need them to setup particle.io webhooks.
- Open organization settings
- Copy the info for ClusterURL and OrganizationID
- Go to tokens and generate a new API token (and save it for the next step!)
Go back to particle.io console "Integrations"
-
Create new WebHook Integration Setting | Value --------|------ Event Name | pm2_5 URL | https://YourClusterURL/api/v2/write?org=YourOrganizationID&bucket=sensors&precision=s Request Type | POST Request Format | Custom Body Device | Any Status | Enabled
-
Expand the Advanced Settings!
Setting | Value --------|------|- Custom Request Body | envSensors,sensorID={{{PARTICLE_DEVICE_ID}}} {{{PARTICLE_EVENT_NAME}}}={{{PARTICLE_EVENT_VALUE}}} HTTP HEADERS (two fields) | Authorization | Token YOUR-API-TOKEN * After you're done creating the webhook it should look like this ->
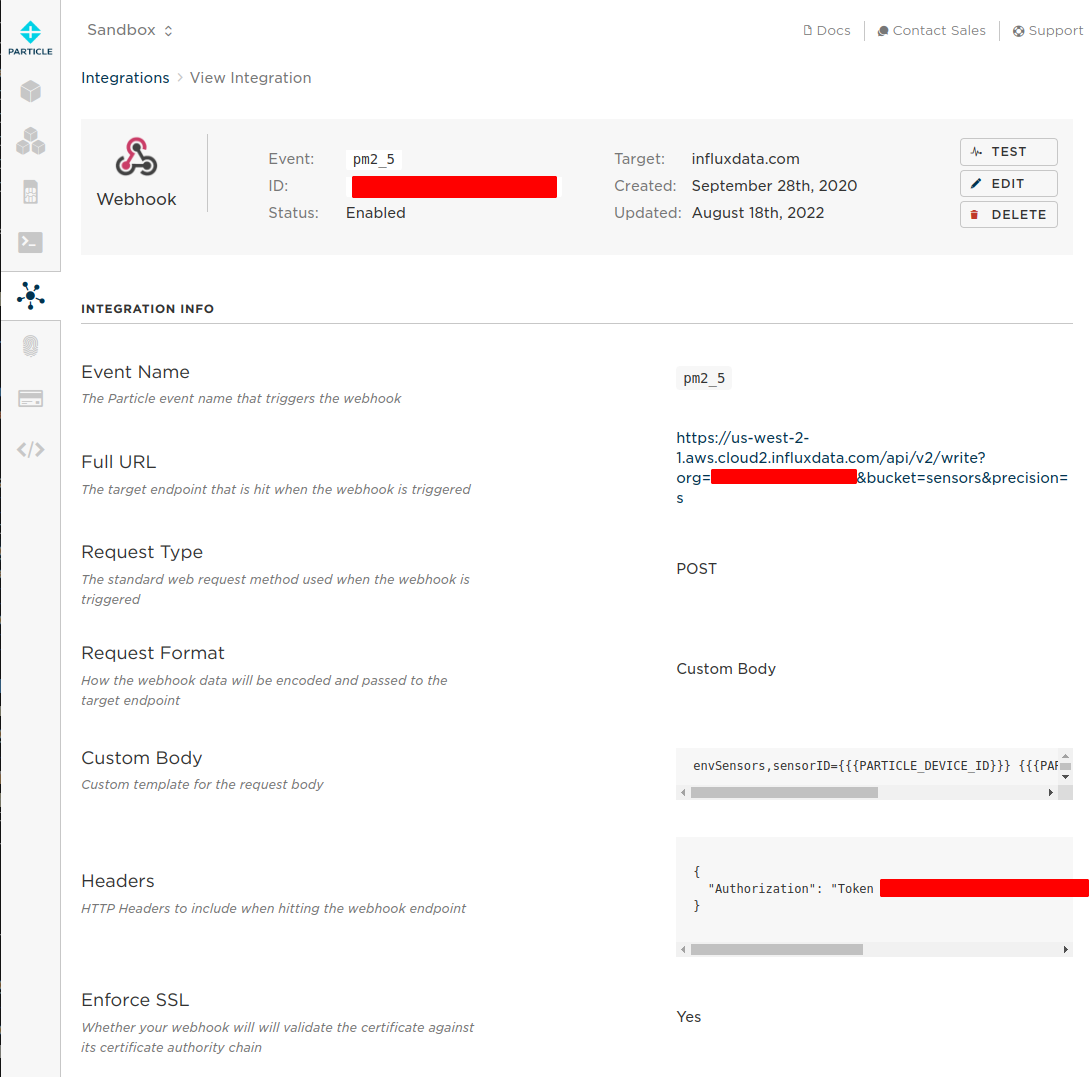 * While viewing the webhook we should start to see the webhook logs below ->
* While viewing the webhook we should start to see the webhook logs below ->
 You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)
You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)Now we can build an influxDB dashboard!
- You can create a new dashboard and play around. For example: create a new cell.
- Use QUERY BUILDER to point-and-click the sensor data.
Done! Enjoy the free charts!
-
 @ 75bf2353:e1bfa895
2023-08-02 23:28:00
@ 75bf2353:e1bfa895
2023-08-02 23:28:00What Is Bitcoin
According to Pablo Xannybar Bitcoin exists outside the control of nation states, as well as central investment, and commercial banks, or any other single third party--It is money ruled solely by code, mathematics, and compute power, not a government or any other body of fallible humans." This is important because the peer-to-peer electronic cash system does not have a central point of failuresince bitcoin is a peer-to-peer electronic cash system; a system built on distributed computer networking instead of a centralized third party. This is different from almost all technology most people use in their day to day lives. Apple is the biggest technology company in the world. It has many servers all around the world. Your data on the Apple cloud is protected from natural disasters because Apple has backups all over the word. To be honest, I have assume someone else has seen it.not verified this, but I don't imagine the Apple cloud is just running on a laptop in somebody's closet. If one of Apple's server breaks, your data will surely survive.
They say this cloud is secure, yet somehow naked celebrity pictures get hacked from the iCloud and the FBI can break the iCloud encryption. To be fair, bitcoin stored on hot wallets can also be hacked. If you type a seed phrase onto an Internet computer, assume someone else has seen it. That's why most Bitcoiners advise to only keep a small amount of your stack on a hot wallet. That's why governments don't like "unhosted wallets." Unhosted wallets are a euphimism for big random number the government can't guess. Their Internet surveillance doesn't work on a calculator plugged into a 9v battery inside a shed at the middle of nowhere. This is also why we can rest assured that the bitcoin we keep in cold storage can be safer than even data kept on the servers of the biggest companies in the world.
Bitcoin Full Nodes Keep The Network Decentralized
Imagine if there was only one person running a bitcoin node. This node verified all the transactions on the network. If the power went out or if it got droned, bitcoin would die. There would be no record of the bitcoin time chain anymore. Nobody would verify transactions. There would be no network to broadcast to.

What if there are 17,000 bitcion nodes. Let's say my node gets droned. Bitcoin is still alive like Eddie Vedder. There are still 16,999 nodes validating transactions all over the world. Maybe one bitcoin node dies every now and then, but there are more peers on the network. They are distributed all over the globe. As long as several nodes remain on the network, bitcoin will not die.

The same is true of miners now that mining bitcoin and running a node are not the same thing.. We only need one bitcoin miner for the network to work. Of course, if that miner gets droned or a government tells it to censor transactions bitcoin would not make it. Miners mine bitcoin blocks all over the world . These people maintain the rules of the bitcoin network no matter what the drone pilots do. This means the bitcoin network is not at the mercy of a single government. Governments could shut down exchanges, but they cannot shut down the bitcoin network.
Bitcoin will be alive as long as many humans run the software on computers. Some will mine, some will run full nodes that validate every transaction since the genesis block. There are thousands maybve tens of thousands of nodes like this in the world. For bitcoin to die, all of these nodes would need to die. A node is just a computer running the bitcoin software. I won't say this is impossible, but I remain optimistic that even the most evil of nuclear armed, drone wielding governments will not destroy all the bitcoin nodes in the world.
What Is A Bitcoin Wallet?
A bitcoin wallet is created using elliptical key cryptography. I just like to call it a big ass random number. The goal of this chapter is not to make you an expert on eliptic curve cryptography. If you want to learn how to do the math like an OG cypherpunk, take some discreet mathematics classes. WAtch the MIT Cryptography course and read Jimmy Song's book, Programing Bitcoin. The purpose of this chapter is to teach you how the math of bitcoin works without learning to program or earning a bachelor's degree in applied cryptography. I won't teach you how to do SHA256 using a pencil and paper or the command line interface. We will use tools available to anyone with an Internet connection instead. If you are interested in learning a bit more about eliptic curve cryptography, LN Capital has a pretty good thread about it on the dead bird app
To create a bitcoin wallet, we can hash some random data or we can create a 256 bit number using dice rolls. We could also flip a coin 256 times to get 256 bits. Say heads =0 and tails=1. We get a 256 bits f 1's and zero's that computers sees as a totally random, almost impossible to guess number. According to Yan Pritzker, in Inventing Bitcoin you have about the same chance of guessing a bitcoin private key as winning the Powerball 9 times in a row. Your bitcoin seed is a tiny needle in the haystack called the all of the atoms in the universe. If you would like to learn how to make a bitcoin wallet the hard way, check out armantheparman's article, but in the next chapter, you will learn how to make a bitcoin wallet using Padawan. Padawan only uses testnet bitcoin and they give them to you for free. If you F up your Padawan-have no fear. Testnet bitcoin is for practicing and it's not worth anything.
What Is Mining?

Bitcoin mining is the act of applying the SHA256 algorithm to . People often compare bitcoin mining to solving a puzzle. This is not wrong. I think of it as a mathmatical Rubix Cube of sorts, but no analogy does bitcoin mining justice.. During the government mandated lockdowns, my wife became quite adept at solving Rubix Cube. She watched a YouTube video that taught her how to solve it using an algorithm. It helps to visualize the SHA256 as a way of twisting a Rubix Cube in a certain pattern. Each twist gives a different result, but you spin and spin until all the colors match on each side. The Secure Hash Algorithms work in a similar way, except with numbers instead of colors. unfortunately, like all analogies, this Rubix Cube analogy doesn't tell you much about how bitcoin mining works. The best way I can descibe it is like a Rubix Cube with letters and numbers. I dont know how to solve a rubix cube, but my wife says she uses an algorythym. SHA256 is also an algorithym , but instead of creating sides with uniform colors. it searches for a random number with a certain amount of zeros in the front of it. All the other numbers and letters look random, but the zeros of a block do not look random, do they.

### On SHA256
According to Satoshi, "Writing a descreiption for this thing for general audiences is bloody hard, Theres nothing to relate it to." Everyone tries to explain bitcon by analogy like I just did with the rubix cube. Although this was the best visual representation I cold think of, it's still not perfect. I believe there is something in the world bitcoin can be compared to, back then, you had to be a real cryptographer like Adam Back to see it. Adam Back was cited in the white paper because he discovered a way to prevent spam, hashcash. Hashcash is an electronic stamp of sorts. You can use the command line to see how it works if you want to do it the hard way, but the easy way requires https://www.duckduckgo.com. To learn how SHA256 works , we will perform SHA256 on the lowercase letter "a" by entering the following into DuckDuck Go:
sha256 aYou will receive this result:
ca978112ca1bbdcafac231b39a23dc4da786eff8147c4e72b9807785afee48bb
Notice how even though we only did a sha256 hash of one letter, we still get a 64 character hexadecimal number. If we add the number 0 to the letter a,
sha256 a0we get the following hash:4e1195df020de59e0d65a33a4279f1183e7ae4e5d980e309f8b55adff2e61c3e
If we add the numbver 1,
sha256 a1, we get:f55ff16f66f43360266b95db6f8fec01d76031054306ae4a4b380598f6cfd114
There is no other output to each of these because each change no matter how large or small gives us a different output. That's why a number is only used once in the mining process. This is called a nonce. It makes sense. You can almost deduce the meaning by the sound of that word in the same way nobody ever had to explain to you what the word "sharted" means.
We can also has letters and any character on the keyboard. You may have heard computers only understand 1's and 0's. This is true at the base layer of the machine. but the bitcoin blockchain uses hexadecimals and all kinds of text in the transactions. This is because each character on your keyboard is represented by a number so you could do these mathmatical calculations on text like this.
sha256 Blogging BitcoinYou will see the following SHA-256 hash digest:
965aef3b925ed3d5b5315906e49a4956863528be3bfeaa357a62be6b74def0a0
If we SHA-256 Chapter 8 of George Orwell's 1984 we get:
7d7c0aad69d213e113fbaa53be74f0f88f98791c79fe44f6adb809e0787654e3
If we SHA-256 the book, War And Peace, we get:
8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
By the way, War And Peace is a big book. it's easier to hash it by using https://xorbin.com/sha256-calculator instead of duck duck go. I copied and pasted evertying from here. https://www.gutenberg.org/cache/epub/2600/pg2600-images.html The intetresting thing aout SHA256 is that you always get a 64 character output weather you has a single letter or a huge novel. If you change one character, you get an entirely new 64 character output that looks nothing like the previous output.
Notice how each one of these gives us 64 unique hexadecimal numbers, no matter how small or large the amount of data being hashed is.
We would not make a bitcoin wallet out of a novel because anyone with that novel can take our bitcoin We want to use random numbers to make our bitcoin wallet. The purpose of writing this is to show you that anythhing from a single letter to a large book can be hashed into 64 characters.
The math is a little complicated, but I highlighted it here in case your interested, but the War And Peace number is actually this:
92,013,536,190,004,391,427,498,867,800,243,235,304,388,826,599,257,256,328,980,806,975,182,967,533,301
We will make our first bitcoin wallet in the next chapter, but before we do, let's talk more about mining?
How The F$@$% Does Bitcoin Mining Work?
Just like I can hash War and Peace, bitcoin miners can hash all the data in the bitcoin mempool. In other words all the transactions sent since the last block. Here's a good visualization of how it works. All the falling orange squares represent transactions that go into the mempool. These orange squares are really text. Miners hash this text with a nonce. They are also more likely to hash transactions that pay a higher transaction fee than transactions that pay a lower trasnsaction fee since these transaction fees are part of the reward for solving the puzzl. All the miners all over the world do this trillions of times until one of these nonces produces a number with a certain number of leading hex zeros.
https://cdn.nostr.build/p/nb10627.mp4
Bitcoin actually uses a double SHA256 hash to make it more secure. This also makes it more complex to explain, but we are going to demostrate it using a simpler Secure Hash Algorithym, First, let's look at the the SHA-256 hash of War and Peace again.
8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
Now we will hash the entire text of war and peace plus a number we will only use once. The number could be anything, but we will use the number 0. In other words, we append War And Peace by adding a zero to the end of our text
"...This website includes information about Project Gutenberg™, including how to make donations to the Project Gutenberg Literary Archive Foundation, how to help produce our new eBooks, and how to subscribe to our email newsletter to hear about new eBooks.0"
We get this hash
e5a1d7ce9bb2d1c3450c7149633ddd3738a8f88e93457fb46df32c312361f0b4 Which is much different from: 8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
Yet, we only changed one out of thousands of characters.
Now we will replace the Number Only Used Once, 0 with a new number we will only use once,1 and get this result: c600f3e297f850a1b5e4620b0719556a4f7b1e3614875bbe083a31ad84c40367
** TK video of this using https://xorbin.com/tools/sha256-hash-calculator**
### How This Works In Bitcoin
I could keep adding new nonces uWell, I can't, but an ASIC miner can. eventually I will get some cool looking result that has 0000000000000000000 in front of it. I can't do this by hand and it would be a waste of energy to hash War and Peace over and over again with a new number until we get a number with a certain number of zeros in front of it, but that's not the easy way of demonstrating things.
Bitcoin mining is just a souped up version of hashcash I mentioned earlier in this chapter Satoshi referenced hashcash in the white paper because the bitcoin blockchain is simmilar to hashcash, with a few differences. Hashcash uses SHA-1. Bitcoin uses a double SHA-256 hash which means it actually does it twice. The specifics are beyond the scope of this book, but hashcash is a little different.
I previously stated that we can hash any data from a single letter to the novel war and peace.
I have also demonstrated that if we add just one single number to all that data again and again, we will recieve a different result every time.
The zeros I told us are the answer to the puzzle miners are looking for.
For example, the header of the Genesis block, or block 0, is:
000000000019d6689c085ae165831e934ff763ae46a2a6c172b3f1b60a8ce26f
Block height 1: 00000000839a8e6886ab5951d76f411475428afc90947ee320161bbf18eb6048
block 210,000 000000000000048b95347e83192f69cf0366076336c639f9b7228e9ba171342e
Block height 700,000:
0000000000000000000590fc0f3eba193a278534220b2b37e9849e1a770ca959
Like I said before, the leading hex-zeros are like the colored sides of a Rubix Cube. The software adjusts so miners find the answer to this puzzle every 2016 blocks. We say it is two weeks because, on average, there are 6 ten minute blocks in an hour. If blocks come too quickly, more zeros are required. If they come to slow, less zeros are required. This is a little more complicted than this, but this is the easy way of explaining The Difficulty Adjustment.
There are 144 ten minute blocks in a day, 1008 blocks in a week and 2016 bloks in two weeks. Pretty neat, huh?
Hash Cash--The Easy Way

You can see how this works by using hashcash, a sort of digital stamp discovered by Adam Back. Back used SHA1. I found some interesting things while perusing the the hashcash documentation. Hash the following in either duck duck go or xobin calculator.
0:030626:adam@cypherspace.org:6470e06d773e05a7
Imagine "0:030626" is the header of the previous block.
Imagine ":adam@cypherspace.org" is all the data in the mempool we are trying to mine.
Imagine "6470e06d773e05a7" is the nonce. Sure the actual bitcoin timechain takes terahashes per second to solve, but the results are easily verifiable. We use a number only once because each number only yields one answer. It would be a waste of energy to use the same number twice. Instead of double hashing the actual mempool, we can use this simpler version of data to see how bitcoin mining works. Notice how the header of the last block is used in this system. This means that every bitcoin block, except the genesis block, requires information from the previous block. Becaise of this, we can say these blocks are chained together. It cannot be undone because eaach new block requires information from the previous block.
Let's use duck duck go to find the SHA-1 hex hash of this data by entering the following into the duck duck go browser.
sha1 0:030626:adam@cypherspace.org:6470e06d773e05a7You should get this: 73f88e0645f8ca92ef3a0bc02ef4b7edf85fadbd
Unfortunately, this is like a jumbled up Rubix Cube and will not create a new block, but when we try the next nonce, we get this:
sha1 0:030626:adam@cypherspace.org:6470e06d773e05a8This is from the hashcash documentation at https://hashcash.org.00000000c70db7389f241b8f441fcf068aead3f0
Now we have a required amount of zeros and we can say the puzzle is complete. It is not that complicated, but requires doing this a gazillion times before we get an answer
The Halfing
There is a debate. Some people prefer Halvening, others Halfing. I like Halfing because it makes me think of Hal Finney, but that's just this authors personal opinion. My opinion does not matter but the math does.
After 210,000 blocks, the block reward gets cut in half, until the last Satoshi is mined in about the year 2139 or 2140. Nobody really know for sure, but we can forsee the future of a bitcoin to a certain degree. We are like the Oracle in the Matrix who knew the spoon would drop. I never took calculus. I never learned what a summation was in college, but the following made perfect sense to me right away. I could see this goofy math thing-a-majig described the halfings. It made sense because I knew the halving was every four years. Then I realized this summation really tells the same story Satoshi told, but in the language of mathmatics. The actual story is told in C++, yet another language. Copernicus called "mathematics the language of the universe". In this framing, bitcoin is more than just software. It is a work of art, a monumental mathmatical achievement that can be awed after for hundreds of years to come like the Cistine Chappel..
(Anil Patel aka @anilsaidso)
The block reward was 50 for the first epoch.
In the language of mathmatics, it is divided by two every 210,000 blocks.
We get a new block every ten minutes.

144 blocks every day

The blocks start to get to big to manage when we get into these higher numbers, but you get the idea.
144 x 7 = 1,008 one week
144 x 14 = 2016 The difficulty adjustment is every 2016 blocks, but 2016 ten minute blocks are exactly two weeks.
144 x 365 = 52,560 blocks in a year
4(144 x 365.25) = 210,384 in 4 years
That's 4 years and 2.67 days, but we round and say the having happens every four years.
We just say we have a halving every 4 years, but the subsidy stops after 32 of them. Then fees incentivize the miners to solve this numeric Rubix Cube
That's how bitcoin works in a nutshell.
By the year 2032, a solo miner who creates a block will receive a block subsidy of 0.78125. Unless fees drastically increase, miners will not receive a whole coin for solving this puzzle in just nine years. You might want to get some before then, but first we need to learn how to create a wallet
[Next Chapter-- Practice Makes Perfect: The Padawan Wallet(#)
-
 @ 3553ccfa:d7024217
2023-08-18 11:42:13
@ 3553ccfa:d7024217
2023-08-18 11:42:13The Golden Tech Stack
Welcome
Time is lovely, isn't it? It just flows on like a river. Anyway, some stuff has changed and an update is due! I hope you are well and excited for another edition of my blog.
This edition of the blog, I asked a simple question to my bitcoiner pals over at the Jupiter Broadcasting Matrix channel: "What would you like to see me write about or have my opinion on?" HAL9000 answered with: "I'd love to know your tech stack" (I am simplifying a bit, but, that is the jist), so, thank you for that!
Before I get to that, here are some
Updates
Since we last chatted over the blog, I have been trying (and failing) to get comments on here. I will be trying to make a small python app for that as a learning tool for developing python. Shouldn't be too hard, I hope. Do you think it will be?
I have also joined up with the Nostriches and have both a Nostr Blog on Habla.News and a regular twitter style nostr account (one in the same, really. Just different front ends and relays) My npub for seeking me out is: npub1x4fue7jz3y4gjjce6le9qkawapnrjkq92za78wr8qp36m4czggtshxdfxs
DISCLAIMER We should all have hope and look toward the day where a man realizes the sounds -ahem- sorry
Actual disclaimer: This blog will be mirrored over on Habla.News, so I may have to take some liberties for that ie photos will be linked for your viewing pleasure!
The Stack
I am surrounded by technology. Probably some tech debt, if I am honest. Just at this desk alone, I sit amongst four computers of varying scopes. "But, Dragon, why couldnt this be condensed down?" I did. This desk was full of monitors and the like, and I may still condense down to just one and make the rest headless, minus the laptop.
Here is the top level overview of what I use on a regular basis and (if i can remember) some specs:
It's GNOME, its XFCE, Its..!
The last gen of Intel-based Mac Mini computers. This is my daily driver and will soon become my dev machine. What I am considering is this:
Linux Hugo NGINX or Caddy (havent decided on the web server yet) MySQL Python
As for specs, this thing is Spec'ed OUT my dudes. And was given to me as a gift. My donor can let me know if they would like credit for this. Its been alluded to for sure, though! In it's current state, I am able to help my wife design stuff for our business, which won't change. I will just not be able to use her software (Cricut Design Space). If anybody out there has any luck running this in a VM, let me know.
The Blog Writer
This one is a little MicroMini Node, Lenovo style While not very powerful, like my Mac is, this tiny pc site behind my curved monitor and lets me write my blog with ease. Currently running Debian 12 Stable XFCE (email me that hate), it gets out of my way and just goes. Initially intended as a Monero rig, I realized that I wouldnt really get much out of that except the memes and I am (mostly) serious about my work. My blog stack is pretty simple:
Markdown files parsed by > Hugo sent to > GitHub hosted by > Netlify > to your lovely face.
The Server
Ahh, yes. My good ol' Dell This server is mainly a Nextcloud rig. Did host Jellyfin and ripped Anime, but, need to set up the latter again. Big fan of Serial Experiments Lain.
My Nodes
Did I mention I am a new Bitcoin Maxi? I have two nodes now. I have an Ancient eMachines with built-in Nvidia GPU and AMD Sempron CPU as well as a Kamrui Mini PC that I picked up second hand that somehow works
The top one is my Umbrel node and the Kamrui is my new Start9 Node. The Start9 node will be the one where my Blog sats will be (we will get to that in a moment!) As of now, Start9 cannot connect with Tailscale, but, I will see if I can change that. Probably not.
Misc
In addition to that, the boost button is proxied on a Nanode over on Linode and the Python Comments app I hope to develop will be over there as well. Once I learn how boosts work and how to work with API's, this will all just be peachy keen.
Future-sim aka Where this all goes
Eventually, I have a feeling I will be back to just a computer and a laptop, with headless nodes running in a 3d printed, fan cooled cabinet. What I would really enjoy would be my Mac being my base system, probably Arch or Debian. I would like to figure out exit nodes as well so that I can cut back on 5g data perhaps and just use my home internet.
The stack is nothing really golden, I just have a lot of extra tech that I wanted to put to use.
Support time!
This week, we (and by we I mean ThothLoki) blew my mind and sent over a whopping 5000 satoshis! I really appreciate it and that will be here on my Start9 node very soon with the other 300 satoshis from last blog post.
If you would like to support the blog, you too can send your value over by using the button below. If you are on Habla, you can Zap me and that will go directly to my node and I will send that over to the blog node as well.
Alternatively, you can send me directly via your wallet if it supports LNURL addresses! You can fund me directly with a send to TGDHaku@boost.goldenblogathon.com
It is night as I write this. When I wake, I hope the sun is warm. I hope that you are warm when the sun rises, too.
-
 @ 7cc328a0:2a247c0e
2023-08-02 22:57:59
@ 7cc328a0:2a247c0e
2023-08-02 22:57:59Here is an nginx config for setting up a streaming server that serves HLS. This is what you need if you want to stream from your own streaming server and be viewed on zap.stream, amethyst or other nostr clients that support streaming.
You can connect to it using RTMP -or RMTPS from OBS.
This is an 'advanced guide' it assumes all you need is the nginx.conf and that you can install nginx and use certbot to create the certificates.
I've tested this config on a t3.micro (very small) amazon server and it works great for streaming to my friens.
All you have to do is install nginx, point a DNS record to the server, and use certbot to get some SSL certificates.
nginx.conf ```nginx worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf;
events { worker_connections 768; # multi_accept on; }
http {
map $sent_http_content_type $expires { default 1d; application/vnd.apple.mpegurl epoch; }
server { allow all; sendfile off; tcp_nopush on;
aio on;
directio 512; include mime.types; default_type application/octet-stream; access_log /var/log/nginx/access.log;index test.html;
location / { expires $expires; # Disable cache add_header Cache-Control no-cache; # CORS setup add_header 'Access-Control-Allow-Origin' '*' always; add_header 'Access-Control-Expose-Headers' 'Content-Length'; # allow CORS preflight requests if ($request_method = 'OPTIONS') { add_header 'Access-Control-Allow-Origin' '*'; add_header 'Access-Control-Max-Age' 1728000; add_header 'Content-Type' 'text/plain charset=UTF-8'; add_header 'Content-Length' 0; return 204; } types { application/dash+xml mpd; application/vnd.apple.mpegurl m3u8; video/mp2t ts; text/html html; } root /tmp/hls; } listen 443 ssl; server_name mysite.com; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; # managed by Certbot} include /etc/nginx/sites-enabled/.;
}
stream { upstream backend { server 127.0.0.1:1935; }
server { listen 1936 ssl; proxy_pass backend; proxy_protocol on; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; }}
rtmp { server { listen 1935 proxy_protocol; chunk_size 4000;
application live { live on; hls on; hls_path /tmp/hls; # Use HLS encryption hls_keys on; # Store auto-generated keys in this location rather than hls_path hls_key_path /tmp/hls/keys; # Prepend key url with this value hls_key_url /keys/; # Change HLS key every 2 fragments hls_fragments_per_key 100; #hls_playlist_length 5s; #hls_fragment 2s; } }} ```
here is an index.html page that displays a video player embedded.
```html
```
As you can see, the URL you would give to zap.stream to setup the stream is https://yoursite/test2.m3u8
You can test the stream is online by visiting mysite/index.html and hitting play.
Hope this helps! At the very least, now I won't lose these precious working configs. PV.
-
 @ bcea2b98:7ccef3c9
2023-08-02 00:08:30
@ bcea2b98:7ccef3c9
2023-08-02 00:08:30A Finney attack, a specific kind of double-spend attack in the Bitcoin network, requires certain specific conditions within the network topology. Here's how it works:
-
Pre-mined Block: The attacker must mine a block containing a transaction that pays the coins to themselves. This block is not immediately broadcast to the network.
-
Direct Connection to Victim: Ideally, the attacker must make a direct connection to the victim's node or ensure network latency to the victim, to minimize the chance that the victim learns about the pre-mined block before the attack transaction is accepted.
-
Second Transaction to Victim: The attacker sends a transaction to the victim (e.g., the merchant), who delivers goods or services once the transaction appears in the victim's mempool but before it is confirmed in a block.
-
Release of Pre-mined Block: Once the victim accepts the unconfirmed transaction, the attacker broadcasts the previously mined block, thereby invalidating the transaction to the victim since the block contains a conflicting transaction that spends the same output.
-
Sufficient Mining Power: The attacker must have sufficient mining power to successfully mine the conflicting block. While they don't need to have more power than the rest of the network, a higher hash rate increases the success probability.
-
Timing: The timing must be carefully orchestrated to ensure that the victim accepts the unconfirmed transaction before learning about the conflicting block.
-
No Network Propagation of Mined Block: The pre-mined block must not be propagated through the network before the victim accepts the unconfirmed transaction.
-
Merchant's Policy: The attack exploits merchants who accept unconfirmed transactions, a practice that might be found in face-to-face transactions where fast settlement is required.
A Finney attack is complex and requires a specific set of conditions to be met. It has become increasingly unlikely with the growing security in the network. The theoretical possibility still leads to discussions about the need for confirmations and caution in accepting unconfirmed transactions.
-
-
 @ 80ee8a95:b2862d2e
2023-08-18 10:21:42
@ 80ee8a95:b2862d2e
2023-08-18 10:21:42In a prosperous nation like Australia, the issues that Bitcoin aim to solve are far less perceivable compared to other poorer or authoritarian nations. Bitcoin’s value proposition is less relatable because we have access to banks, our economies are generally tolerable, and everything to some degree just works.
Conversations about Bitcoin in the workplace or among friends and family can be difficult. You may often be dismissed, called names (mine is “future boy”), or perceived as someone belonging to a cult. And people will bring up the common arguments against Bitcoin purported by the media: 1) it uses to much energy, 2) it is volatile, 3) it encourages criminal activity like the silk road, 4) it is a Ponzi scheme, 5) its an intangible asset, and 6) its a speculative and immature technology.
Here I will offer some tips I have learnt when talking to people about Bitcoin. My frame of reference is as a Bitcoiner living in Australia, but I think my experience may translate to other developed nations.
Tip 1: Never try convince someone they should buy Bitcoin.
My first tip is to never try convince people to buy Bitcoin, but instead, teach them about Bitcoin and guide them towards sources where they can learn more themselves. The value proposition behind Bitcoin is difficult to understand and people shouldn’t necessarily hold any before they understand the risks and benefits behind the technology.
In my mind, the most important part of a person’s orange pilling is the will and interest to find out more themselves, and make their own decision to buy some.
So your primary aim should be just to find a way to make them interested enough to seek out more information. Here is my shortlist of books, podcasts, and other valuable sources I use when pointing people to find out more.
Tip 2: Bitcoin is an inclusive technology.
One major problem I see with the Bitcoin community is that Bitcoiners set up walls where you are either enlightened Bitcoiner, or you are a “normie”. For someone seeking to find out more about Bitcoin, the community can appear cultish, and being referred to as a “normie” or other names creates an exclusive environment that can dissuade people from finding out more. Everyone will have their own path of discovery as most of us did. Help others find Bitcoin by making the community inclusive.
Tip 3: Be prepared to combat common misconceptions or misunderstandings
1. Bitcoin uses more energy than some country in Europe (no one ever remembers which)
This is probably the most common argument I hear. But as you will see, the real question here is not about the absolute amount of energy use, but a person’s perception of the value per unit energy that it delivers.
The adoption of any new technology that advances society has required energy. This energy consumption is often intense at the beginning and becomes more efficient as the technology develops and drives further investment. Bitcoin miners are the primary consumers of energy in the technology. Most people don’t actually understand why Bitcoin consumes energy — Bitcoin consumes energy to cryptographically protect the value contained within the network. However, inherent to Bitcoin is an economic incentive to reduce energy costs and maximise profits. Miner’s therefore naturally seek out more efficient technologies and cheaper sources of energy.
Over a 5 year period from 2018 to 2023, the energy required per terrahash (energy per unit work) declined by 63%. It is also useful to highlight novel ways in which Bitcoin miners are consuming wasted energy or using renewable sources, such as Iris energy, or Gridless. These and other companies are investing into renewable energy sources. Current estimates of Bitcoin’s renewable energy usage is between 25% and 50%.
In 2016 the power consumption of data centres was estimated to be 200 TWh/y. By comparison, Bitcoin consumes between 75.4 TWh/y and 122 TWh/y. The traditional financial system is estimated to consume 5,000 TWh/y which pales to Bitcoin’s consumption. This is not to say we should be complacent about Bitcoin’s energy use; these are all staggering amounts of energy consumption! But in most people’s mind, the value of data centres and the legacy financial system seems so obvious that they wouldn’t question its energy usage. So the real question should not be about the absolute value of power consumption, but rather whether Bitcoin provides the same global value per unit energy consumed.
Framing the energy argument in terms of the value per unit energy should help to open a discussion on Bitcoin’s value proposition.
2. Bitcoin is volatile
Yes, Bitcoin is volatile! But why is this bad? Most people making this claim are comparing Bitcoin to holding shares in some big tech company. Bitcoin is not a company! Comparing it to a company means you haven’t understood the Bitcoin’s true value proposition of it becoming the hardest form of money. Furthermore, despite its current volatility, Bitcoin continues to outperform most stocks and gold.
Bitcoin is a truly free market asset, unlike other forms of investment influenced by capital controls which act to dampen volatility. Bitcoin’s adoption still sits below 5% globally. As adoption increases, its price will continue to stabilise as it has been over the past decade (see figure below).
 Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)
Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)Volatility will continue to be a feature of Bitcoin in the near future. But this is not necessarily bad. Investment into Bitcoin, like any asset, should be taken with consideration of a person’s financial position and their ability to weather this volatility.
3. Bitcoin facilitates illicit activity and the anonymity of the criminals.
There is no escaping the fact that to some degree Bitcoin has facilitated the exchange of drugs and other illicit activity. However, Bitcoin offers a level of traceability that hasn’t existed previously with cash. Bitcoin is not anonymous, it is pseudonymous. It depends on a public ledger that facilitates the tracking funds, and KYC (Know-Your-Customer) on/off ramps that help link transactions back to individuals. This tracking has led to the downfall of the silk road and several associated criminals since. Law enforcement and journalists are constantly coming up with tools to track the the movement of cryptocurrencies used in illicit activity.
Bitcoin is a neutral technology. Blaming Bitcoin for the drug problem is as silly as blaming the internet, the postage service that sends a large portion of drugs, or cars that drive them from location to location. It will never be escape the fact that some people will use it for illegal activity, as people have and will continue to do with any form of money.
4. Bitcoin is a Ponzi scheme.
Many other cryptocurrencies which are actual Ponzi schemes have given people a negative impression of Bitcoin. I once had a family member, who knew about my great interest in Bitcoin gleefully exclaim “Hey did you hear!? Bitcoin is dead!” She was referring to the news about the downfall of OneCoin. This comment made me realise how important it is to help people understand the fundamental difference between a decentralised Bitcoin and a centralised crypto Ponzi.
In simple terms, Bitcoin being decentralised means there is no single entity in charge or profiting from the value of Bitcoin, nor are there profits derived from getting people into Bitcoin.
A follow-on comment I often get is that early adopters cause an imbalance in the distribution of wealth. This is currently true. It is estimated that 0.01% of addresses hold 58% of all Bitcoin. But we currently live in a world of rapidly rising inequality and a financial system that promotes the financial privileged. Over the past 40 years, the top 1% of income earners has seen their share increase from about 11% to almost 20% in the USA (see figure below).
 Total share of income of the top 1% of earners (source: https://wid.world/)
Total share of income of the top 1% of earners (source: https://wid.world/)You can research into the effects leading to inequality and you will read very contradictory arguments from both sides of the Bitcoin camp. So I’m not going to argue that Bitcoin solves the problem of wealth inequality; that is yet to be seen. But the growing digitisation of financial services is already creating a positive effect in reducing wealth inequality around the world. One of Bitcoins main benefits is that it promotes financial inclusion, which I believe can only result in a positive outcome for reducing inequality.
5. Bitcoin is an intangible asset
I once tried to explain to a family member the link between physical gold and Bitcoin. I used the analogy that energy is trapped in physical gold, and energy is required to extract it. This is similar to extracting and storing energy in Bitcoin. He laughed at me smugly.
Some people will have a really hard time comparing a physical asset to a digital one. They assume a digital asset can be copied, and it has no meaningful use in the real world. Bitcoin requires some tech literacy which you cannot teach in an evening!
Instead, you can highlight that a physical asset like gold is a great store of value; we have been using it to store value for millennia. But it is not a great medium of exchange. How can you break it up into smaller pieces? How do you send it across the world?
Bitcoin solves these problems. Like gold, Bitcoin cannot be copied or debased. But unlike gold, you can send fractions of a Bitcoin instantly anywhere across the globe.
6. Bitcoin is a speculative and immature technology.
Trace Mayer used to talk about the seven network effects of Bitcoin: Speculation, Merchant Adoption, Consumer Adoption, Security, Developer Mindshare, Financialization, and Adoption as a World Reserve Currency.
Speculation, being the first network effect, is an important part of Bitcoin’s maturation. Speculation drives early adoption and leads to the initial growth and innovation. Early adopters face larger risks as the price is more volatile, but also reap larger rewards. As more people adopt, merchants begin to accept it as forms of payment, leading to the second network effect and so on.
Yes, Bitcoin was a speculative asset but it is far beyond it speculative stage. We are currently closer to the “Developer mindshare” stage, where developers are working on new tools and new products that now integrate multiple technologies, like lightning and nostr.
Bitcoin is no longer speculative. I would also argue it is not even immature, even though it has only been around for a decade. But a misconception people often make is that the dollar (AUD or USD) is mature. The dollar as we know it is an experiment that has been running since around 1971, and politicians and economists still have no idea how to control it! Levers are pulled, money is debased and debt is increased time and time again.
 Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)
Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)And thats it! I hope you found this useful for the next time you’re speaking to someone about Bitcoin in a developed nation.
Bitcoin Beme
Liked this article? help support more bitcoin: bc1q880n3vjzqa054xr6hwcx7756873z47kcqr052s ln-url: ourbean71@walletofsatoshi.com
-
 @ eac63075:b4988b48
2023-08-01 15:45:29
@ eac63075:b4988b48
2023-08-01 15:45:29Lá na outra rede, o Dov havia feito um post bacana mostrando como usar a Electrum mobile de cold wallet nessa playlist.
Então ao comentar que a minha primeira cold wallet havia sido uma Electrum num notebook velho e formatado só pra isso, algumas pessoas me perguntaram sobre meu setup atual.
Então preparei o seguinte esboço:
No geral é: * Server Umbrel para os nodes * Coldcard e Ledger (coldwallets) * Computador criptografado e celular android com área segura p/ apps
É um caso de uso extremo mas além da auto-soberania e custódia dos meus satoshis, essa estrutura ainda me permite:
- Participar do consenso do Bitcoin
- Auxiliar no roteamento de sats na Lightning Network
- Fazer coinjoin facilmente para aumentar a privacidade
E embora a estrutura pareça complicada, é bastante simples:
- Raspberry Pi 4 com Debian e Umbrel (p/ os nodes e servers)
- Celular antigo android com área segura e sem simcard
- Notebook com storage criptografada
- Ledger Nano X
- Coldcard
E ainda pude evoluir de N.O.I.A. (Network Operator Innovator and Advocate) para M.A. (Minerador Anônimo), com uma Nerdminer pra tentar um ticket da sorte a cada 10 minutos
Não esqueça que uma cold wallet para a auto-custódia pode começar com um computador ou celular velho!
É mais simples do que parece e praticar sua auto-soberania e custódia significa na verdade liberdade e privacidade nesse mundo digital!
-
 @ bcea2b98:7ccef3c9
2023-08-01 13:37:52
@ bcea2b98:7ccef3c9
2023-08-01 13:37:52abandon ability able about above absent absorb abstract absurd abuse access accident account accuse achieve acid acoustic acquire across act action actor actress actual adapt add addict address adjust admit adult advance advice aerobic affair afford afraid again age agent agree ahead aim air airport aisle alarm album alcohol alert alien all alley allow almost alone alpha already also alter always amateur amazing among amount amused analyst anchor ancient anger angle angry animal ankle announce annual another answer antenna antique anxiety any apart apology appear apple approve april arch arctic area arena argue arm armed armor army around arrange arrest arrive arrow art artefact artist artwork ask aspect assault asset assist assume asthma athlete atom attack attend attitude attract auction audit august aunt author auto autumn average avocado avoid awake aware away awesome awful awkward axis baby bachelor bacon badge bag balance balcony ball bamboo banana banner bar barely bargain barrel base basic basket battle beach bean beauty because become beef before begin behave behind believe below belt bench benefit best betray better between beyond bicycle bid bike bind biology bird birth bitter black blade blame blanket blast bleak bless blind blood blossom blouse blue blur blush board boat body boil bomb bone bonus book boost border boring borrow boss bottom bounce box boy bracket brain brand brass brave bread breeze brick bridge brief bright bring brisk broccoli broken bronze broom brother brown brush bubble buddy budget buffalo build bulb bulk bullet bundle bunker burden burger burst bus business busy butter buyer buzz cabbage cabin cable cactus cage cake call calm camera camp can canal cancel candy cannon canoe canvas canyon capable capital captain car carbon card cargo carpet carry cart case cash casino castle casual cat catalog catch category cattle caught cause caution cave ceiling celery cement census century cereal certain chair chalk champion change chaos chapter charge chase chat cheap check cheese chef cherry chest chicken chief child chimney choice choose chronic chuckle chunk churn cigar cinnamon circle citizen city civil claim clap clarify claw clay clean clerk clever click client cliff climb clinic clip clock clog close cloth cloud clown club clump cluster clutch coach coast coconut code coffee coil coin collect color column combine come comfort comic common company concert conduct confirm congress connect consider control convince cook cool copper copy coral core corn correct cost cotton couch country couple course cousin cover coyote crack cradle craft cram crane crash crater crawl crazy cream credit creek crew cricket crime crisp critic crop cross crouch crowd crucial cruel cruise crumble crunch crush cry crystal cube culture cup cupboard curious current curtain curve cushion custom cute cycle dad damage damp dance danger daring dash daughter dawn day deal debate debris decade december decide decline decorate decrease deer defense define defy degree delay deliver demand demise denial dentist deny depart depend deposit depth deputy derive describe desert design desk despair destroy detail detect develop device devote diagram dial diamond diary dice diesel diet differ digital dignity dilemma dinner dinosaur direct dirt disagree discover disease dish dismiss disorder display distance divert divide divorce dizzy doctor document dog doll dolphin domain donate donkey donor door dose double dove draft dragon drama drastic draw dream dress drift drill drink drip drive drop drum dry duck dumb dune during dust dutch duty dwarf dynamic eager eagle early earn earth easily east easy echo ecology economy edge edit educate effort egg eight either elbow elder electric elegant element elephant elevator elite else embark embody embrace emerge emotion employ empower empty enable enact end endless endorse enemy energy enforce engage engine enhance enjoy enlist enough enrich enroll ensure enter entire entry envelope episode equal equip era erase erode erosion error erupt escape essay essence estate eternal ethics evidence evil evoke evolve exact example excess exchange excite exclude excuse execute exercise exhaust exhibit exile exist exit exotic expand expect expire explain expose express extend extra eye eyebrow fabric face faculty fade faint faith fall false fame family famous fan fancy fantasy farm fashion fat fatal father fatigue fault favorite feature february federal fee feed feel female fence festival fetch fever few fiber fiction field figure file film filter final find fine finger finish fire firm first fiscal fish fit fitness fix flag flame flash flat flavor flee flight flip float flock floor flower fluid flush fly foam focus fog foil fold follow food foot force forest forget fork fortune forum forward fossil foster found fox fragile frame frequent fresh friend fringe frog front frost frown frozen fruit fuel fun funny furnace fury future gadget gain galaxy gallery game gap garage garbage garden garlic garment gas gasp gate gather gauge gaze general genius genre gentle genuine gesture ghost giant gift giggle ginger giraffe girl give glad glance glare glass glide glimpse globe gloom glory glove glow glue goat goddess gold good goose gorilla gospel gossip govern gown grab grace grain grant grape grass gravity great green grid grief grit grocery group grow grunt guard guess guide guilt guitar gun gym habit hair half hammer hamster hand happy harbor hard harsh harvest hat have hawk hazard head health heart heavy hedgehog height hello helmet help hen hero hidden high hill hint hip hire history hobby hockey hold hole holiday hollow home honey hood hope horn horror horse hospital host hotel hour hover hub huge human humble humor hundred hungry hunt hurdle hurry hurt husband hybrid ice icon idea identify idle ignore ill illegal illness image imitate immense immune impact impose improve impulse inch include income increase index indicate indoor industry infant inflict inform inhale inherit initial inject injury inmate inner innocent input inquiry insane insect inside inspire install intact interest into invest invite involve iron island isolate issue item ivory jacket jaguar jar jazz jealous jeans jelly jewel job join joke journey joy judge juice jump jungle junior junk just kangaroo keen keep ketchup key kick kid kidney kind kingdom kiss kit kitchen kite kitten kiwi knee knife knock know lab label labor ladder lady lake lamp language laptop large later latin laugh laundry lava law lawn lawsuit layer lazy leader leaf learn leave lecture left leg legal legend leisure lemon lend length lens leopard lesson letter level liar liberty library license life lift light like limb limit link lion liquid list little live lizard load loan lobster local lock logic lonely long loop lottery loud lounge love loyal lucky luggage lumber lunar lunch luxury lyrics machine mad magic magnet maid mail main major make mammal man manage mandate mango mansion manual maple marble march margin marine market marriage mask mass master match material math matrix matter maximum maze meadow mean measure meat mechanic medal media melody melt member memory mention menu mercy merge merit merry mesh message metal method middle midnight milk million mimic mind minimum minor minute miracle mirror misery miss mistake mix mixed mixture mobile model modify mom moment monitor monkey monster month moon moral more morning mosquito mother motion motor mountain mouse move movie much muffin mule multiply muscle museum mushroom music must mutual myself mystery myth naive name napkin narrow nasty nation nature near neck need negative neglect neither nephew nerve nest net network neutral never news next nice night noble noise nominee noodle normal north nose notable note nothing notice novel now nuclear number nurse nut oak obey object oblige obscure observe obtain obvious occur ocean october odor off offer office often oil okay old olive olympic omit once one onion online only open opera opinion oppose option orange orbit orchard order ordinary organ orient original orphan ostrich other outdoor outer output outside oval oven over own owner oxygen oyster ozone pact paddle page pair palace palm panda panel panic panther paper parade parent park parrot party pass patch path patient patrol pattern pause pave payment peace peanut pear peasant pelican pen penalty pencil people pepper perfect permit person pet phone photo phrase physical piano picnic picture piece pig pigeon pill pilot pink pioneer pipe pistol pitch pizza place planet plastic plate play please pledge pluck plug plunge poem poet point polar pole police pond pony pool popular portion position possible post potato pottery poverty powder power practice praise predict prefer prepare present pretty prevent price pride primary print priority prison private prize problem process produce profit program project promote proof property prosper protect proud provide public pudding pull pulp pulse pumpkin punch pupil puppy purchase purity purpose purse push put puzzle pyramid quality quantum quarter question quick quit quiz quote rabbit raccoon race rack radar radio rail rain raise rally ramp ranch random range rapid rare rate rather raven raw razor ready real reason rebel rebuild recall receive recipe record recycle reduce reflect reform refuse region regret regular reject relax release relief rely remain remember remind remove render renew rent reopen repair repeat replace report require rescue resemble resist resource response result retire retreat return reunion reveal review reward rhythm rib ribbon rice rich ride ridge rifle right rigid ring riot ripple risk ritual rival river road roast robot robust rocket romance roof rookie room rose rotate rough round route royal rubber rude rug rule run runway rural sad saddle sadness safe sail salad salmon salon salt salute same sample sand satisfy satoshi sauce sausage save say scale scan scare scatter scene scheme school science scissors scorpion scout scrap screen script scrub sea search season seat second secret section security seed seek segment select sell seminar senior sense sentence series service session settle setup seven shadow shaft shallow share shed shell sheriff shield shift shine ship shiver shock shoe shoot shop short shoulder shove shrimp shrug shuffle shy sibling sick side siege sight sign silent silk silly silver similar simple since sing siren sister situate six size skate sketch ski skill skin skirt skull slab slam sleep slender slice slide slight slim slogan slot slow slush small smart smile smoke smooth snack snake snap sniff snow soap soccer social sock soda soft solar soldier solid solution solve someone song soon sorry sort soul sound soup source south space spare spatial spawn speak special speed spell spend sphere spice spider spike spin spirit split spoil sponsor spoon sport spot spray spread spring spy square squeeze squirrel stable stadium staff stage stairs stamp stand start state stay steak steel stem step stereo stick still sting stock stomach stone stool story stove strategy street strike strong struggle student stuff stumble style subject submit subway success such sudden suffer sugar suggest suit summer sun sunny sunset super supply supreme sure surface surge surprise surround survey suspect sustain swallow swamp swap swarm swear sweet swift swim swing switch sword symbol symptom syrup system table tackle tag tail talent talk tank tape target task taste tattoo taxi teach team tell ten tenant tennis tent term test text thank that theme then theory there they thing this thought three thrive throw thumb thunder ticket tide tiger tilt timber time tiny tip tired tissue title toast tobacco today toddler toe together toilet token tomato tomorrow tone tongue tonight tool tooth top topic topple torch tornado tortoise toss total tourist toward tower town toy track trade traffic tragic train transfer trap trash travel tray treat tree trend trial tribe trick trigger trim trip trophy trouble truck true truly trumpet trust truth try tube tuition tumble tuna tunnel turkey turn turtle twelve twenty twice twin twist two type typical ugly umbrella unable unaware uncle uncover under undo unfair unfold unhappy uniform unique unit universe unknown unlock until unusual unveil update upgrade uphold upon upper upset urban urge usage use used useful useless usual utility vacant vacuum vague valid valley valve van vanish vapor various vast vault vehicle velvet vendor venture venue verb verify version very vessel veteran viable vibrant vicious victory video view village vintage violin virtual virus visa visit visual vital vivid vocal voice void volcano volume vote voyage wage wagon wait walk wall walnut want warfare warm warrior wash wasp waste water wave way wealth weapon wear weasel weather web wedding weekend weird welcome west wet whale what wheat wheel when where whip whisper wide width wife wild will win window wine wing wink winner winter wire wisdom wise wish witness wolf woman wonder wood wool word work world worry worth wrap wreck wrestle wrist write wrong yard year yellow you young youth zebra zero zone zoo
-
 @ 80ee8a95:b2862d2e
2023-08-18 10:20:21
@ 80ee8a95:b2862d2e
2023-08-18 10:20:21In a prosperous nation like Australia, the issues that Bitcoin aim to solve are far less perceivable compared to other poorer or authoritarian nations. Bitcoin’s value proposition is less relatable because we have access to banks, our economies are generally tolerable, and everything to some degree just works.
Conversations about Bitcoin in the workplace or among friends and family can be difficult. You may often be dismissed, called names (mine is “future boy”), or perceived as someone belonging to a cult. And people will bring up the common arguments against Bitcoin purported by the media: 1) it uses to much energy, 2) it is volatile, 3) it encourages criminal activity like the silk road, 4) it is a Ponzi scheme, 5) its an intangible asset, and 6) its a speculative and immature technology.
Here I will offer some tips I have learnt when talking to people about Bitcoin. My frame of reference is as a Bitcoiner living in Australia, but I think my experience may translate to other developed nations.
Tip 1: Never try convince someone they should buy Bitcoin.
My first tip is to never try convince people to buy Bitcoin, but instead, teach them about Bitcoin and guide them towards sources where they can learn more themselves. The value proposition behind Bitcoin is difficult to understand and people shouldn’t necessarily hold any before they understand the risks and benefits behind the technology.
In my mind, the most important part of a person’s orange pilling is the will and interest to find out more themselves, and make their own decision to buy some.
So your primary aim should be just to find a way to make them interested enough to seek out more information. Here is my shortlist of books, podcasts, and other valuable sources I use when pointing people to find out more.
Tip 2: Bitcoin is an inclusive technology.
One major problem I see with the Bitcoin community is that Bitcoiners set up walls where you are either enlightened Bitcoiner, or you are a “normie”. For someone seeking to find out more about Bitcoin, the community can appear cultish, and being referred to as a “normie” or other names creates an exclusive environment that can dissuade people from finding out more. Everyone will have their own path of discovery as most of us did. Help others find Bitcoin by making the community inclusive.
Tip 3: Be prepared to combat common misconceptions or misunderstandings
1. Bitcoin uses more energy than some country in Europe (no one ever remembers which)
This is probably the most common argument I hear. But as you will see, the real question here is not about the absolute amount of energy use, but a person’s perception of the value per unit energy that it delivers.
The adoption of any new technology that advances society has required energy. This energy consumption is often intense at the beginning and becomes more efficient as the technology develops and drives further investment. Bitcoin miners are the primary consumers of energy in the technology. Most people don’t actually understand why Bitcoin consumes energy — Bitcoin consumes energy to cryptographically protect the value contained within the network. However, inherent to Bitcoin is an economic incentive to reduce energy costs and maximise profits. Miner’s therefore naturally seek out more efficient technologies and cheaper sources of energy.
Over a 5 year period from 2018 to 2023, the energy required per terrahash (energy per unit work) declined by 63%. It is also useful to highlight novel ways in which Bitcoin miners are consuming wasted energy or using renewable sources, such as Iris energy, or Gridless. These and other companies are investing into renewable energy sources. Current estimates of Bitcoin’s renewable energy usage is between 25% and 50%.
In 2016 the power consumption of data centres was estimated to be 200 TWh/y. By comparison, Bitcoin consumes between 75.4 TWh/y and 122 TWh/y. The traditional financial system is estimated to consume 5,000 TWh/y which pales to Bitcoin’s consumption. This is not to say we should be complacent about Bitcoin’s energy use; these are all staggering amounts of energy consumption! But in most people’s mind, the value of data centres and the legacy financial system seems so obvious that they wouldn’t question its energy usage. So the real question should not be about the absolute value of power consumption, but rather whether Bitcoin provides the same global value per unit energy consumed.
Framing the energy argument in terms of the value per unit energy should help to open a discussion on Bitcoin’s value proposition.
2. Bitcoin is volatile
Yes, Bitcoin is volatile! But why is this bad? Most people making this claim are comparing Bitcoin to holding shares in some big tech company. Bitcoin is not a company! Comparing it to a company means you haven’t understood the Bitcoin’s true value proposition of it becoming the hardest form of money. Furthermore, despite its current volatility, Bitcoin continues to outperform most stocks and gold.
Bitcoin is a truly free market asset, unlike other forms of investment influenced by capital controls which act to dampen volatility. Bitcoin’s adoption still sits below 5% globally. As adoption increases, its price will continue to stabilise as it has been over the past decade (see figure below).
 Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)
Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)Volatility will continue to be a feature of Bitcoin in the near future. But this is not necessarily bad. Investment into Bitcoin, like any asset, should be taken with consideration of a person’s financial position and their ability to weather this volatility.
3. Bitcoin facilitates illicit activity and the anonymity of the criminals.
There is no escaping the fact that to some degree Bitcoin has facilitated the exchange of drugs and other illicit activity. However, Bitcoin offers a level of traceability that hasn’t existed previously with cash. Bitcoin is not anonymous, it is pseudonymous. It depends on a public ledger that facilitates the tracking funds, and KYC (Know-Your-Customer) on/off ramps that help link transactions back to individuals. This tracking has led to the downfall of the silk road and several associated criminals since. Law enforcement and journalists are constantly coming up with tools to track the the movement of cryptocurrencies used in illicit activity.
Bitcoin is a neutral technology. Blaming Bitcoin for the drug problem is as silly as blaming the internet, the postage service that sends a large portion of drugs, or cars that drive them from location to location. It will never be escape the fact that some people will use it for illegal activity, as people have and will continue to do with any form of money.
4. Bitcoin is a Ponzi scheme.
Many other cryptocurrencies which are actual Ponzi schemes have given people a negative impression of Bitcoin. I once had a family member, who knew about my great interest in Bitcoin gleefully exclaim “Hey did you hear!? Bitcoin is dead!” She was referring to the news about the downfall of OneCoin. This comment made me realise how important it is to help people understand the fundamental difference between a decentralised Bitcoin and a centralised crypto Ponzi.
In simple terms, Bitcoin being decentralised means there is no single entity in charge or profiting from the value of Bitcoin, nor are there profits derived from getting people into Bitcoin.
A follow-on comment I often get is that early adopters cause an imbalance in the distribution of wealth. This is currently true. It is estimated that 0.01% of addresses hold 58% of all Bitcoin. But we currently live in a world of rapidly rising inequality and a financial system that promotes the financial privileged. Over the past 40 years, the top 1% of income earners has seen their share increase from about 11% to almost 20% in the USA (see figure below).
 Total share of income of the top 1% of earners (source: https://wid.world/)
Total share of income of the top 1% of earners (source: https://wid.world/)You can research into the effects leading to inequality and you will read very contradictory arguments from both sides of the Bitcoin camp. So I’m not going to argue that Bitcoin solves the problem of wealth inequality; that is yet to be seen. But the growing digitisation of financial services is already creating a positive effect in reducing wealth inequality around the world. One of Bitcoins main benefits is that it promotes financial inclusion, which I believe can only result in a positive outcome for reducing inequality.
5. Bitcoin is an intangible asset
I once tried to explain to a family member the link between physical gold and Bitcoin. I used the analogy that energy is trapped in physical gold, and energy is required to extract it. This is similar to extracting and storing energy in Bitcoin. He laughed at me smugly.
Some people will have a really hard time comparing a physical asset to a digital one. They assume a digital asset can be copied, and it has no meaningful use in the real world. Bitcoin requires some tech literacy which you cannot teach in an evening!
Instead, you can highlight that a physical asset like gold is a great store of value; we have been using it to store value for millennia. But it is not a great medium of exchange. How can you break it up into smaller pieces? How do you send it across the world?
Bitcoin solves these problems. Like gold, Bitcoin cannot be copied or debased. But unlike gold, you can send fractions of a Bitcoin instantly anywhere across the globe.
6. Bitcoin is a speculative and immature technology.
Trace Mayer used to talk about the seven network effects of Bitcoin: Speculation, Merchant Adoption, Consumer Adoption, Security, Developer Mindshare, Financialization, and Adoption as a World Reserve Currency.
Speculation, being the first network effect, is an important part of Bitcoin’s maturation. Speculation drives early adoption and leads to the initial growth and innovation. Early adopters face larger risks as the price is more volatile, but also reap larger rewards. As more people adopt, merchants begin to accept it as forms of payment, leading to the second network effect and so on.
Yes, Bitcoin was a speculative asset but it is far beyond it speculative stage. We are currently closer to the “Developer mindshare” stage, where developers are working on new tools and new products that now integrate multiple technologies, like lightning and nostr.
Bitcoin is no longer speculative. I would also argue it is not even immature, even though it has only been around for a decade. But a misconception people often make is that the dollar (AUD or USD) is mature. The dollar as we know it is an experiment that has been running since around 1971, and politicians and economists still have no idea how to control it! Levers are pulled, money is debased and debt is increased time and time again.
 Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)
Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)And thats it! I hope you found this useful for the next time you’re speaking to someone about Bitcoin in a developed nation.
Bitcoin Beme
Liked this article? help support more\ bitcoin: bc1q880n3vjzqa054xr6hwcx7756873z47kcqr052s\ ln-url: ourbean71@walletofsatoshi.com
-
 @ bcea2b98:7ccef3c9
2023-08-01 04:57:59
@ bcea2b98:7ccef3c9
2023-08-01 04:57:59On Monday, an unidentified developer withdrew all liquidity from the BALD meme coin on the Ethereum layer-2 network, Base. Some blockchain analysts are speculating that the wallet involved may be linked to Sam Bankman-Fried, former CEO of FTX, who is currently under house arrest with restricted internet access.
Cinneamhain Ventures partner Adam Cochran expressed his suspicion on Twitter, noting that the implicated wallet had previous involvement in the SushiSwap community. Cochran inferred that the early voting patterns in Sushi governance appeared dubious, with Bankman-Fried being the key individual behind snapshot votes during the community takeover following the departure of SushiSwap's creator, Chef Nomi.
In September 2020, Bankman-Fried had successfully salvaged funds from Uniswap, transferring them to SushiSwap. Cochran voiced his confidence that the party behind the actions was associated with Alameda, FTX, or was Bankman-Fried himself, based on conversations with former FTX members.
Several observers connected the language used by the Bald Twitter account to Bankman-Fried's own distinctive phrasing. Furthermore, on-chain activities corresponded with Bankman-Fried's court appearances and bail dates.
A Reddit-sourced investigation revealed that the BALD developer wallet had received deposits from FTX and Alameda over the span of two years and currently holds a balance of approximately 12,331 ETH, valued around $22 million at the time of the report.
Additional information surfaced on Twitter highlighting a correlation between the wallet that regularly deposited into the BALD developer's Binance wallet and a wallet involved in the substantial Terra USD depeg in the previous year. Since facing charges of conspiracy and fraud by the U.S. Department of Justice, following FTX's collapse, Bankman-Fried has been under house arrest. His legal team and the prosecution have struggled to monitor his internet use across numerous devices.
According to his bail conditions, Bankman-Fried was required to use a basic flip phone in place of a smartphone. His legal team admitted their inability to install surveillance software on his parent's phones as agreed.
In response to his alleged tampering with government witnesses, the prosecution submitted a request to revoke Bankman-Fried’s $250 million bond to presiding federal judge Lewis Kaplan last week.
While a section of Crypto Twitter implicated Bankman-Fried, others acknowledged the speculative nature of these accusations. Some users, such as Sam Trabucco, co-chief executive of Alameda, were even identified as potential culprits.
The story continues to evolve, with the BALD developer adding 100 ETH back into the pool following significant social media pressure. This move caused the meme coin's value to surge more than four times over its recent low value.
-
 @ bcea2b98:7ccef3c9
2023-08-01 04:47:02
@ bcea2b98:7ccef3c9
2023-08-01 04:47:02The United States Securities and Exchange Commission (SEC) initiated a lawsuit against Richard Schueler, an internet marketer also known as Richard Heart, accusing him of unregistered securities offerings through his projects Hex, PulseChain, and PulseX. The SEC asserts that Heart amassed over $1 billion since 2019 through these offerings.
The SEC further alleges that Heart misappropriated investor funds for his personal expenditures. Despite Heart's persistent promotion of his projects as vehicles for substantial financial growth, with audacious claims such as Hex being engineered to be "the most rapidly appreciating asset in human history," the SEC argues that these ventures were, in fact, utilized to finance Heart's extravagant lifestyle without appropriate disclosure to investors.
Despite a turbulent launch marked by high fees, liquidity problems, and software vulnerabilities, PulseX and PulseChain were introduced earlier this month. Following their introduction, the prices of the associated HEX, PLS, and PLSX tokens experienced a significant downturn. The SEC further accuses Heart of recurrent references to federal securities laws in his public communications, such as YouTube livestreams, while concurrently admitting that the success of his projects hinged entirely on his personal efforts.
The SEC's lawsuit also mentions Heart's ambitious assertions about Hex's potential for investment return. For instance, Heart announced on Hex.com (until at least November 1, 2020) that Hex was projected to exceed the performance of ETH, which saw a 10,000x price increase in 2.5 years, and that Hex had already experienced a 115x price rise in 129 days. Furthermore, Heart asserted during a seven-hour YouTube livestream on December 2, 2019, mere hours before the Hex Offering began, that Hex was created to outperform Ethereum, Bitcoin, and all other cryptocurrencies.
The lawsuit levels accusations of fraud and securities registration violations against Heart and his projects.
-
 @ 37c4e186:7de9109b
2023-08-01 01:34:49
@ 37c4e186:7de9109b
2023-08-01 01:34:49Bitcoin: The Sacrifice of the Ego
by Leopoldo Moreno de la Cova nostr:npub1m2x6mucaxs84d8njq5zrte3ksv7p83ppsqud3a84zww7rfw0hsysrq7v3j
Translated from the original Spanish by nostr:npub1xlzwrphhxppeyjw0prlw0dvpsmx2a8jd6yhnt06clx6zvl0fzzdsgce7w0
"In the world of Bitcoin there is a saying: 'stay humble and stack sats', which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency"
Satoshi Nakamoto is a venerated name in the world of cryptocurrency. He is the creator of Bitcoin, the first decentralized digital currency in the world, and responsible for initiating a revolution in the financial industry. Given the importance of his creation, it is surprising that he has never taken credit, and to this day, the identity of Satoshi continues to be a secret. The anonymity of Satoshi is perhaps the most underrated quality of this quasi-mythological figure, being the best exemplification of the sacrifice of the ego, and something that I consider that we should go into more deeply.
The ego is a powerful force that drives human behavior. It is the sense of self-esteem or self-importance of a person, and often it manifests in the necessity for recognition or credit. However, when we become too attached to our ego, it can lead to arrogance, narcissism, and a distorted view of reality. In contrast, sacrificing the ego requires humility, disinterest, and a disposition to put the needs of others above one's own.
Instead of seeking recognition for his creation, Satoshi decided to remain in the background and to allow his invention to speak for itself. This decision was not motivated by fear or insecurity, but rather by a deep understanding of the potential impact of his creation. Satoshi was conscious that Bitcoin had the potential to transform the financial industry, enabling people to control their own money, converting them into sovereign individuals, independent from corrupt governments, partisian monetary policies, or exhaustive control. He understood that his creation was greater than any single person, including himself.
Upon remaining anonymous, he avoided any potential conflict of interest that could arise because of personal or financial gains, and in its place, he created a decentralized, transparent, and secure system, based on the economic theories of the Austrian school and distancing itself from Keynesian economic policies.
The legend of Satoshi Nakamoto transcends the technological and financial spheres; already his influence has inspired a new generation of entrepreneurs and developers. His focus on decentralization and transparency has been the basis for innovative projects in diverse sectors, such as governance, intellectual property, and data protection. The philosophy behind Bitcoin, which seeks to empower people and democratize access to financial resources, has generated a paradigm shift in the way that we think of money and value. As we advance towards a digital future, the enduring impact of Satoshi and his vision continues to be a lighthouse of inspiration for those who seek to challenge the established system and to construct a more equitable world.
In the world of Bitcoin there is a saying: "stay humble and stack sats", which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency. Using Bitcoin as a store of value has provided an effective strategy for building long-term wealth and resisting the volatility of the market during the last 14 years. Humility has kept us focused on the final objective of the preservation of wealth, meanwhile constant saving/stacking permits us to take advantage of market opportunities and to build a solid base for the future. From my point of view, Satoshi reminds us that the success of decntralized digital money is not about getting rich quickly but rather about the creation of wealth in a constant and responsible fashion, with a focus on preserving property rights and personal liberty.
Through analyzing all of this in detail, perhaps we should not be surprised that something has been created that safeguards property rights, freedom, and privacy like nothing that has been seen in the world before. Satoshi decided to unlink his creation from his identity.
The story of Satoshi Nakamoto is the story of our age. Prometheus brought fire to humanity. Satoshi brought us Bitcoin.
Leopoldo Moreno de la Cova is an economist.
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:52:51
@ 9ecbb0e7:06ab7c09
2023-08-18 01:52:51Los residentes de un edificio en La Habana Vieja donde en octubre del año pasado murió una niña por un derrumbe, continúan viviendo entre los escombros.
Ante el temor de que ocurra otro desplome y quedar sepultados, los vecinos del inmueble situado en la calle Sol, entre Egido y Villegas, han enviado otra carta a CiberCuba en la que denuncian la inacción de los dirigentes y organismos responsables de solucionar su caso.

La carta recibida por la redacción de Cibercuba es la siguiente:
"Somos los vecinos de Sol 466, entre Villegas y Egido, La Habana Vieja, donde ocurrió el derrumbe el 17 de octubre 2022, en el que falleció una niña de cuatro años. Donde el presidente del Partido, Luis Antonio Torres Iríbar, dijo que no íbamos a quedar desamparados, donde Vivienda municipal y provincial dijeron que dentro de 15 a 30 días nos daban solución.

Nunca nos ayudaron ni dieron solución, seguimos viviendo en el inmueble cayéndose a pedazos lo poco que queda, y ni siquiera nuestras cosas y muebles hemos podido sacar de aquí para asegurarlas un lugar más seguro, ya que nuestras viviendas se mojan cuando llueve.

Hemos ido a Vivienda provincial tres veces, Vivienda municipal cuatro veces, gobierno provincial, gobierno municipal... donde ellos dicen que no tienen que ver con eso, que es Vivienda municipal, pero esta entidad nos dice que no tiene solución para nuestro problema.

Hay una anciana de 87 años con una radical de mama, sorda de un oído, diabética de los malos e hipertensa, y vive yendo al policlínico a cada rato por sus varias enfermedades; también esta señora ya no puede más con su estrés por su grave situación, ya ha tenido infarto. Y no se resuelve nada.

Y ya ahora en octubre 17 va hacer un año, en el que entre promesas y mucho bla bla no han dado respuesta a dicho problemón. ¿Qué están esperando, a que haya otro muerto? Un señor que tenía cáncer murió sin poder ver su casa, y la señora que menciono que está enferma vive con miedo, por el desastre de lo que que queda del edificio en ruina estática".

En una misiva anterior, los afectados relataban que iban cada dos o tres días a las diferentes instancias de Vivienda, el gobierno, la fiscalía y el partido.
"Ya nos conocen por dar las quejas y no nos resuelven nada. (...) Y cuando llegamos a los lugares nos dicen: 'ustedes de nuevo', cómo si fuéramos la enfermedad de la peste", dijeron.
"Para los militares y MININT se hacen edificios, y no pueden poner aunque sea uno o dos núcleos por edificio, ya que son cinco núcleos y desde hace años pudieran ya haber salido de esto, y no haber llegado a que hubiera muerto una menor de cinco años de edad, y que vuelva a haber otra muerte", cuestionaron.
El pasado 17 de octubre por la mañana, se derrumbó parte del edificio y varias personas quedaron atrapadas en los escombros. Según el periodista Mario J. Pentón, el derrumbe fue en la escalera del inmueble.
Como consecuencia murió una niña de cinco años nombrada Ismary Orozco Castellanos, quien falleció antes de que los bomberos pudieran rescatarla.
De acuerdo con la información del Portal del Ciudadano de La Habana, los rescatistas lograron sacar con vida a dos mujeres y un menor de edad. Las pacientes fueron enviadas al Hospital Calixto García y el menor al Hospital Juan Manuel Márquez.
El edificio lleva muchos años con problemas.
En 2015 sus residentes denunciaron que se veían obligados a acceder a sus casas por una ventana, tras un derrumbe parcial.
-
 @ 75bf2353:e1bfa895
2023-07-31 21:59:22
@ 75bf2353:e1bfa895
2023-07-31 21:59:22The Easy Way To Self Custody of Bitcoin
 TODO: [TOC]
TODO: [TOC]Note: This is a work in progress. **
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:45:57
@ 9ecbb0e7:06ab7c09
2023-08-18 01:45:57MIAMI, Estados Unidos. — El quinto vuelo de deportación de cubanos desde EE. UU. arribó esta tarde a La Habana, según dio a conocer la Embajada de Estados Unidos en la Isla.
La sede diplomática indicó en redes sociales que los 29 cubanos repatriados habían intentado ingresar sin autorización a territorio estadounidense.
“Este jueves 17 de agosto llegó a La Habana el quinto vuelo de deportación proveniente de Estados Unidos del 2023. El vuelo devolvió a la Isla a 29 cubanos que intentaron entrar a Estados Unidos sin autorización”, señala la nota.
La Embajada llamó a los cubanos a no intentar ingresar a EE. UU. de manera ilegal.
“No ponga en riesgo su seguridad ni la de su familia. Viaje seguro y legal” , apuntó la sede diplomática.

El cuarto vuelo de deportación se había producido el pasado 20 de julio. En el mismo fueron devueltos a Cuba 33 migrantes.
Previo a la salida del cuarto vuelo, familiares de algunos de los migrantes con orden de deportación (tras perder sus casos de asilo político) intentaron detener el proceso y que los liberaran, pero no fue posible.
El tercer vuelo de deportación a la Isla ocurrió el 23 de junio e involucró a 36 cubanos. En ese momento, el Ministerio del Interior de Cuba (MININT) informó que todos los migrantes incluidos en la operación aérea eran hombres y que trece de ellos habían salido ilegalmente de la Isla por vía marítima, mientras que otros 23 viajaron al exterior de forma legal y luego se incorporaron a rutas irregulares para llegar a Estados Unidos.
Abogados de inmigración de Miami han advertido que los cubanos que tienen I-220B son los que corren mayor riesgo de ser deportados, ya que ese documento registra la entrada a EE. UU. con orden expresa de devolución al país de origen.
-
 @ 75bf2353:e1bfa895
2023-07-31 21:56:11
@ 75bf2353:e1bfa895
2023-07-31 21:56:11
Why TF do we need this book?
Most bitcoin books come in two categories.
1) Bitcoin is the best investment since sliced gold. 2) Bitcoin philosophy
As far as I know, there is not a book that teaches the average person how to take self-custody of their bitcoin. There are many guides, webpages, and YouTube videos, but they are kind of fragmented and require you to take many detours down the rabbit hole. This book is for people who have embroiled themselves in bitcoin. Maybe they read the Bitcoin Standard or the Progressive Case for Bitcoin and have decided they need some bitcoin. They think bitcoin is energy, digital gold, Venice, "the blockchain," proof-of-work, and 12 magic words you memorize and say to retrieve all of your wealth like Wingaudiam Levinosa in Harry Potter.

There are no more bitcoin books to be written. This is not a bitcoin book. It is a compilation of many different tools I have found and used since I got into bitcon. This book will not have any charts. It will not mention the price of bitcoin. The only model is tick-tock-next block. The world will never have 21 million bitcoin. This book will teach you how to control a small fraction of that amount. As long as you can write down 24 words and a passphrase and can store them safely, you will be able to store your bitcoin. You will have your Cold Card memorize your words.
This book will not teach you:
"How much will I get if I invest $100 in Bitcoin? "When Moon?" "How much does it cost to buy one Bitcoin?"
This book will not teach you how to lend your bitcoin or give it to someone else for interest." This is anti-Block-Fi. This book will not teach you how to buy bitcoin from a regulated exchange. Regulated exchanges are some of the most dangerous ways to store your bitcoin. The worst way to store bitcoin is in someone else's wallet. The bitcoin you hold in someone else's wallet is someone else's bitcoin. **This is not a book about other people's bitcoin. This is not about Blackrock's bitcoin, Coinbase's bitcoin, or Strike's bitcoin. This is about your bitcoin. Your bitcoin is your responsibility. ** If you lose your seeds, nothing in this book can help you. ** If you write your passphrase down wrong, you will hodl forever. This book will teach you how to double-check your wallets and do it as easily as possible while having bitcoin IOUs for as little time and as private as we reasonably can expect our privacy to be.
I went to my first bitcoin conference in November of 2020, in the midst of the FTX scam being revealed in real time. FTX was the most regulated of the regulated exchanges. They still stole their customers bitcoin. I didn't speak to anyone at the conference who would admit they kept their bitcoin on FTX, but many people said they kept it on a bitcoin-only exchange. This exchange regularly informs their customers that they need to withdraw. They make it very easy. Yet so many people trust the exchanges more than they trust themselves.
I found this surprising because the second line in the bitcoin white paper is very clear about this.
https://highlighter.com/e/note19r76y6vz7x8rtza8z08zn5htwu94v4mm77vtmqny7lnrhncul0sqsvw5e3
Satoshi Nakamoto said this in February 2009 on the Peer2Peer Foundation:
https://highlighter.com/e/note1dv8gue4e25za3d5p2ej4krcp7kaykfpfpggn6lk393c7zjdacp3s9855l5
note1dv8gue4e25za3d5p2ej4krcp7kaykfpfpggn6lk393c7zjdacp3s9855l5
I decided to write this book for these people to show them they do not need to trust themselves. They can trust the math instead. They can ditch their bitcoin IOUs for real UTXOs. What's a UTXO? an unspent bitcoin transaction output. That's just a fancy way of saying saving bitcoin or stacking sats.
This book is not a 100% trustless way to store bitcoin. That would be the hard way, but I do believe this is possible to achieve, especially if you only use bitcoin on the main chain, but that is beyond the scope of this book. I intend to teach you how to use your bitcoin. If you don't have any bitcoin, don't worry. I will teach you how to get some using bitcoin the way it was meant to be, **peer2peer. **
When you buy bitcoin peer2peer, you know you own bitcoin as soon as it gets to your wallet. This will protect you from exchanges that are regulated by a corrupt financial system that knows how to regulate fractional reserve banks that blow up but has no idea how cryptography works. For this reason, many bitcoiners have fallen victim to scams they thought were safe becauuse of financial regulation that keeps them as safe as the credit ratings of sub-prime mortgages, which means not very safe at all. There are many examples of regulated and unregulated exchanges and lending platforms that were hacked, rehypoticated, or just plain stolen. This book intends to teach you how to protect yourself from unscrupulous exchanges that look legit because of regulation, but are actually rug-pull technology such as:
-FTX -Celcius -Block-Fi -Mt. Gox
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:43:43
@ 9ecbb0e7:06ab7c09
2023-08-18 01:43:43El martillista cubano Yasmani Fernández abandonó la delegación de la Isla que intervendrá en el Campeonato Mundial de Atletismo de Budapest (Hungría), a celebrarse del 19 al 27 de septiembre próximos.
La noticia fue confirmada este miércoles por Play Off Magazine. El portal especializado indica que Fernández había sido incluido a última hora en la delegación, que ahora cuenta con solo 20 atletas.
La noticia había sido difundida previamente por el diario Jit. El medio oficialista indicó que Fernández “abandonó” la delegación durante su escala en París (Francia). Según el comisionado nacional de la especialidad, Rolando Charroo, el resto de los seleccionados está “enfocado” en obtener sus mejores resultados.
Fernández, de 28 años, había registrado su mejor marca personal (75,74 metros) en el pasado Memorial José Barrientos, que se celebró en el Estadio Panamericano de La Habana.
Su posición en el ranking mundial le valió su inclusión a última hora en el equipo cubano, aunque no tardó en escapar previo a la llegada a Hungría.
A su llegada a Budapest, el equipo cubano se concentró en el Hotel Danubio Arena. Allí se unieron dos grupos: uno proveniente de La Habana y otro desde la localidad española de Guadalajara, donde habían desarrollado “una base de preparación durante varias semanas”.
Cuba asiste al Campeonato Mundial de Atletismo de Budapest sin grandes figuras y con un pronóstico reservado. Las mayores aspiraciones de medallas recaen en los triplistas Lázaro Martínez y Cristian Nápoles, entre los hombres, así como Leyanis Pérez y Liadagmis Povea, entre las mujeres.
El atletismo ha sido uno de los deportes más golpeados por el abandono de figuras en los últimos años. Durante el Campeonato Mundial de 2022, celebrado en Oregón, Estados Unidos, abandonaron el equipo cubano tres miembros de la delegación: la jabalinista Yiselena Ballar, la discóbola Yaimé Pérez y el fisioterapeuta Carlos González Morales.
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:40:48
@ 9ecbb0e7:06ab7c09
2023-08-18 01:40:48El embargo de Estados Unidos a Cuba no existe como tal gracias a las exenciones para la compra de alimentos y medicinas en territorio estadounidense por parte del régimen castrista. Lo anterior se refleja en las cifras oficiales del Departamento de Agricultura, que indican exportaciones hacia Cuba por 37.071.007 dólares solo en el mes de junio de 2023, lo cual significa un crecimiento del 60.8% con relación al mismo mes del año anterior.
Los números marcan un hito en la relación comercial entre EEUU y Cuba, con un crecimiento sostenido impulsado por las compras que realizan las micros, pequeñas y medianas empresas (Mipymes), a las que el régimen castrista les otorgó la capacidad de importar alimentos y commodities agrícolas a Cuba.
De acuerdo con el informe presentado en el portal Cubatrade, entre los productos que compró Cuba en EEUU durante junio de 2023 destacan bacon, mantequilla, aceite de oliva, aceite de girasol, aceite de colza, azúcar, café, pastas, comuniones, helados, galletas, leche en polvo, cerveza, papel higiénico y carne de ave, entre otros.
En el caso de la carne de pollo, EEUU es el principal suministrador de esa proteína a Cuba. Más del 90% del pollo que se consume en el país caribeño proviene de productores estadounidenses, marcando una gran dependencia del gobierno comunista de los sistemas productivos del “imperialismo”.
Los datos acumulados en el histórico del primer semestre del año implican importaciones por 160.259.463 dólares solo en alimentos. El salto es significativo teniendo en cuenta que igual período del año previo, es decir, de enero a junio, se alcanzó una cifra de poco más de 144 millones de dólares.
El marco legal bajo el cual se llevan a cabo estas exportaciones es el Trade Sanctions Reform and Export Enhancement Act (TSREEA) de 2000 y el Cuban Democracy Act (CDA) de 1992. El TSREEA autoriza la exportación directa comercial de alimentos y productos agrícolas desde EEUU hacia Cuba, sin importar su propósito.
En las cifras que recoge el Departamento de Agricultura de EEUU no se reflejan los costos de transporte, cargos bancarios u otros gastos asociados con las exportaciones. Aunque el gobierno cubano reporta datos no verificables que sí incluyen estos costos, el aumento en las exportaciones alimentarias y agrícolas es innegable.
-
 @ 3f770d65:7a745b24
2023-07-31 12:53:38
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:38:51
@ 9ecbb0e7:06ab7c09
2023-08-18 01:38:51Un joven padre cubano llamado Wismayel Hernández Martínez fue víctima mortal de un crimen en la provincia Pinar del Río. Su pérdida ha sido lamentada en redes sociales por familiares y conocidos.
Según las diferentes publicaciones, el homicidio ocurrió durante la mañana del pasado martes y dejó sin padre a un niño. En los posts no se detalló cómo se desencadenó el hecho, ni quién sería el responsable.
La madre de Wismayel expresó su profundo dolor a través de Facebook: “Hoy me quitaron una parte de mi corazón, alguien a quien amo y amaré donde Dios me lo tenga en su manto. La vida es injusta, por Dios cuánto dolor tengo en mi corazón, ese era mi niño, el hermano mayor de mi hija. Mi amor por ti siempre será eterno, no podré verte más, ni abrazarte, ni besarte”.

El homicidio también fue confirmado por la internauta Lisney Roche Lorenzo.
“Mi negro, mi hermano, el amor de mi vida, mi otra mitad, dejaste un gran vacío en mi vida. No sé qué va a ser ahora de mí. No tengo palabras para expresarlo, solo que te amo mucho mi vida y sé que Dios te tendrá en el mejor de los lugares” , manifestó.
Incremento de robos y homicidios en Cuba
Según un reporte del Observatorio Cubano de Auditoría Ciudadana (OCAC), la Isla registra en el actual año una creciente inseguridad pública y la escalada de crímenes violentos.
El reporte de la ONG precisa que en el primer trimestre del año se han identificado un total de 98 crímenes comprobados, distribuidos en 16 casos en enero, 48 en febrero y 34 en marzo.
Estas cifras abarcan 42 casos de robo, 33 asesinatos, 17 asaltos y 6 delitos de otro tipo. Sin embargo, el panorama se tornó aún más sombrío en el segundo trimestre, ya que se registraron un total de 189 crímenes, principalmente en las provincias de La Habana, Villa Clara y Guantánamo.
En el caso específico de los robos, la ONG detectó un incremento del 83%; mientras que los homicidios registraron un alza del 43%. El OCAC dejó en claro que estas cifras no reflejan la realidad del país, debido a la falta de transparencia del gobierno cubano, además del bajo interés por denunciar incidentes de este tipo.
-
 @ 9ecbb0e7:06ab7c09
2023-08-18 01:35:33
@ 9ecbb0e7:06ab7c09
2023-08-18 01:35:33Las autoridades sanitarias de Florida emitieron una advertencia sobre el incremento de casos de dengue en el sur del estado, algunos de ellos importados desde Cuba, informó América Tevé.
La epidemióloga Dadilia Garcés, en una entrevista con América Tevé, informó que existe un registro de 200 personas infectadas en todo el territorio del estado naranja. De ellas, 130 se contagiaron a causa de viajes a países donde la enfermedad es endémica. Respecto a Miami-Dade y Broward, ambos territorios registran nueve casos locales.
La experta en epidemiología exhortó a la población a mantenerse alerta respecto a las personas provenientes de regiones donde la enfermedad llega a alcanzar niveles de epidemia, ya que este factor puede desencadenar la propagación local del virus y, por consiguiente, aumentar el número de casos en el estado.
Hace unos meses, la Isla llegó a tener un incremento de contagios. La mayoría de los enfermos fueron detectados en municipios de las provincias orientales de Guantánamo y Santiago de Cuba.
De acuerdo con los Centros para el Control y la Prevención de Enfermedades (CDC), aproximadamente una de cada 20 personas afectadas por el dengue presenta una forma grave de la enfermedad, requiriendo hospitalización. Los grupos más vulnerables incluyen a los lactantes, mujeres embarazadas y aquellos que han padecido infecciones previas por el virus.
Ante esta alarmante situación, las autoridades de salud en Florida exhortan a la población a tomar medidas preventivas, como el uso de repelente y la eliminación de criaderos en hogares, que podrían ser macetas en desuso, cubetas, llantas o cualquier otro objeto que almacene agua. ¿Cuáles son los síntomas de dengue?
Los síntomas del dengue pueden variar en su intensidad, y en ocasiones llegan a ser confundidos con los de otras enfermedades transmitidas por mosquitos. Los signos más comunes son fiebre alta, dolor de cabeza y malestar intenso en articulaciones.
Asimismo, se encuentra el dolor detrás de los ojos, erupción cutánea, fatiga, náuseas, vómitos, pérdida de apetito y sangrado. Es importante tener en cuenta que el dengue puede presentarse en formas de clásico y hemorrágico; este último causa sangrado grave, shock y en algunos casos puede ser mortal.
En cualquier situación es fundamental buscar atención médica, ya que la detección temprana y el manejo adecuado pueden ser cruciales para un pronóstico favorable y evitar severas complicaciones.
-
 @ 32e18276:5c68e245
2023-07-30 21:19:40
@ 32e18276:5c68e245
2023-07-30 21:19:40Company Overview:
Damus is the pioneering iOS nostr client. Through its platform, Damus empowers billions on iOS with the tools for free speech and free speech money. If you're driven to bring freedom technology to the masses and ignite change, we invite you to join our mission.
Job Description
- Collaborate on iOS Damus in tandem with our core developer, Will Casarin, and the broader Damus team.
- Implement our vision as laid out in our product roadmap: https://github.com/orgs/damus-io/projects/3/views/1.
- Embrace the fun and critical mission of undermining totalitarian regimes across the globe.
Job Requirements
- A genuine passion for freedom technology.
- At least one year of collaborative development experience.
- Experience building SwiftUI iOS apps.
- Passionate about design and user experience.
- Eager to work in close coordination with Damus lead developer, Will, and a dedicated team spanning development, design, and product.
- Commitment to a full-time role, although we remain open to discussing alternative arrangements.
Bonus Qualifications
- Experience with Nostr development.
- Experience with C.
- Previous work in free and open source projects.
- A publicly shareable portfolio.
Job Structure
- A one-month paid probationary period to ensure a mutual fit.
- Upon successful completion of the trial, the opportunity for a six (6) month contractual engagement.
- The potential for contract renewal, contingent on funding.
Application Process:
Interested candidates should forward a motivational statement alongside their CV/portfolio to vanessa@damus.io. -
 @ 1bc70a01:24f6a411
2023-07-30 07:43:26
@ 1bc70a01:24f6a411
2023-07-30 07:43:26Originally published on October 15, 2022. Moving from my personal blog to Nostr 🙌
Don't trust, verify
Some people find this very annoying. But I've realized that most people are winging it in life. Human psychology and power dynamics influences how people think and what they say. People want to seem right so they copy what others say, and expect you to believe it.
One way people consume information is through media - news and articles. They'll read something and assume it's true.
Cited by a "study"? Must be true.
"Experts say"?
Gotta be true.
Except, if you check the sources and do some critical thinking, you might uncover that the study is flawed or that the experts are biased.
Simple things like statistical significance are thrown out the window in some studies.
People overlook personal biases.
This all leads to poor data and misrepresentation. This is how you get click-bait headlines.
The only way to know what's true is to try and verify it for yourself.
Even if you are not able to verify the facts, you can come away with a range of certainty about what you learned. Is it probably true? May be true. Certainly true? Or maybe there is a grain of truth to it? The level of confidence can vary. You don't need to be 100% confident in your newly acquired knowledge.
Treat new knowledge as data points
"It depends" is the most appropriate answer to all questions in life. The actual answer is very nuanced and depends on all sorts of things.
But, the way media presents information and the way our minds try to categorize it is by replacing past beliefs.
Once you learn something new, it's tempting to disregard your past knowledge.
I don't see information this way.
To me, all new information is a data point in my life-long accumulated collection of other data points.
Think of it like a toolbox. You have many tools in your toolbox and they are all useful for some specific task. You don't throw away a tool you bought because you acquired another.
Information is much the same. You source information from your mind to understand some subject. Consider existing beliefs, while looking at the new information. The goal is to connect the dots.
Sooner or later the data points (dots) start connecting, and you get a better picture of the subject.
Seek out incentives
Incentives drive human behavior.
Incentive to earn.
Incentive to love.
Incentive to feel good about yourself (generosity).
If you can figure out a person's incentives, you will start to understand their behavior.
People suck at understanding this. They blame the wrong things. They assign responsibility to people who are not responsible. They create made up reasons for why someone did something. All the whole ignoring incentives.
Incentives drive everything. Ask the following questions:
- What is the ultimate goal of this person by saying or doing this?
- What do they seek to gain?
- How does it make them feel?
- What will they do at the prospect of failure?
- Who are the people they care for?
- What do they stand to lose?
- What motivates their actions?
- In almost all cases the answer to these questions involves a personal gain / loss.
Give people the benefit of the doubt
When trying to decide whether something was said or done with good intent, assume that's the case.
With exceptions such as career politicians or criminals, it is best to assume that people mean well and people are default=nice.
Otherwise it becomes difficult to have faith in systems, processes and humanity.
I know the world can be an ugly place, but it can also be a beautiful place. I'd rather assume people are seeking to build a better future for themselves.
If they act against everyone's best interest, it is best to assume they do so out of personal gain rather than some sinister plot. Look at the incentives that drive their behavior and figure out how to modify them to best serve everyone.
Acknowledge that material wealth does not bring happiness and strive for what matters to you.
Money does not bring happiness no matter what anyone says. It does relieve you of despair and help live a better, more peaceful and enjoyable life, but it will not make you happy.
Very few people in the world, if any, know true happiness because they confuse happiness (the process) with happiness (the end state). There is no end state for happiness.
When people ask you if you are happy, it's hard to answer, right?
Your instinct is to say "yes, of course". After all, your day is going fine, you have every comfort you desire and you had a pleasant lunch with a friend. You feel "happy".
But, this happiness fades. Tomorrow you get in a car accident, your car damaged, insurance won't pay out and you miss 2 weeks of work. You are "unhappy".
Some people confuse happiness with being content. You can be content with your place in life, but that doesn't mean you're happy.
The whole debate over happiness is a mute point. Since happiness is a process which is more akin to enjoyment, ultimately there is no such thing as happiness. The word itself should disappear from dictionaries.
Ok, I'm joking. But, you get the point.
When it comes to my life, I strive for satisfaction and contentment.
If I'm satisfied that day, that week, that month, that year, or the last decade, then I've met my "happiness" goals. If I am content with my life, then I'm "happy".
While material wealth can provide satisfaction, the contentment piece is often missing. With wealth, the goal post moves from one spot to another. Once you've achieved a satisfying moment, you have to move to the next, and the next. Each time you have to introduce higher states of satisfaction that require more effort and money.
Eventually, you plateau and satisfying moments from the physical world no longer matter. You seek out emotional attachment and relationships.
This is why so many wealthy people are depressed. No matter how much they spend, they can never reach that emotional attachment provided by love and relationships.
In fact, wealth only complicates those things. Instead of people seeing you for who you are as a person, a new variable is introduced and they see you for your status. With misaligned incentives, it becomes more difficult to form genuine relationships. Thus, contentment is hard to achieve.
I'm going to let you in on the biggest secret everyone is asking about - the secret to happiness.
The secret to happiness is charitable work. Doing things for others, without expecting anything in return.
Charitable acts are secretly selfish acts, whether that person acknowledges it or not.
All humans act in self-preservation. The need to feel good about ourselves. The need for approval. The need for comfort and safety. The need for recognition. All of these needs are driven by self-preservation.
Charity is no different. While we may feel that we do good things for others out of the goodness of our hearts, the evolutionary incentive is to feel satisfied by our deeds. There's nothing wrong with doing good things to feel good, as long as you understand why you're doing it, instead of performing mental gymnastics.
We are not designed for our digital world and should not strive to adapt to it
Evolution took hundreds of thousands of years to shape humans into what we are today. But technology accelerated the process by many magnitudes all within about 100 years. Except, it hasn't. The evolutionary clock is still catching up, out of breath and exhausted with your daily activity.
While we adapt rather well, humans are not capable of processing the amount of data and connections offered by the internet. This ultimately messes with our minds.
Think about your current physical world social circle. Small, yes?
Now think about your digital social circle. Much larger?
How many people do you think about out of your larger digital social circle? My guess is not that many.
While you may recognize the individuals you interact with, the meaning connections formed in the digital world are somewhat closely mirrored to the physical world. I hypothesize this is because we have innate evolutionary boundaries that limit our ability to expand beyond a certain natural limit.
Going beyond the invisible evolutionary boundaries places a burden on your mind. It feels unhealthy.
Remember the last time you thought to yourself "I need a break. I need to unplug"? That's your evolutionary boundary telling you it is not capable of processing any more data. You need a purge to get back to equilibrium.
We are not designed to be always-on, always-connected, always-responsive. At least not yet. It's possible the evolutionary process catches up and prepares us to handle all of it, but I am not confident it will be any time soon.
I try to remind myself that I am not meant to have 50,000 followers and expect to keep everyone happy. I am not meant to follow everyone's updates and be expected to respond. To stay healthy, I need to unplug.
Life is what you make of it, do what you wish to do and ignore the rest
There's no "right way" to do anything. Everything is a figment of human imagination. To do things "the right way" means doing it by someone else's definition of right.
I found it incredibly freeing to realize that the only thing that is pure in this world is the natural world and your mind.
The world is a canvas.
You are the paint brush.
Everyone is capable of everything and nothing at the same time.
Everything else is noise.
Yes, we have society. Yes, we have rules. These artificial, human-invented boundaries act to preserve harmony. But, ultimately, the only pure forms of existence are the human mind and the natural world. What you do is the only thing within your boundary of control (to an extent).
Since we experience the world with our minds, we are all that is true. Everything else is a projection of some entity or experience that seeks to change our behavior (intentionally or unintentionally).
With this in mind, I look at people's experiences as unique to them and do not assume that they will translate in the same way to my life if I apply them.
Only worry about things that are in my control
I can't control what people do. I can try to influence them, but ultimately they will do what they decide to do. Since I can only control myself, I don't worry about what others think or do.
Never regret
It's easy to say "I don't regret things" but in reality emotions take us there and we think about what we regret.
I would be lying if I said I don't have feelings of regret. But, I forget about them quickly so I can focus on the things I can control. What passed is now behind me and there's no way to change it back, so there's no point in regretting.
Reflection is not the same as regret. One can reflect by looking at the past, and make changes for the future. Regrets are bitter feelings an no action.
Truth is relative
Even as I write this, my own truths are relative. What is true for me, or is true now, may not be true for you or true when you read it. It may be wrong.
People used to believe earth was the center of the universe. That the sun went around the earth. That to ward off bad spirits you had to offer sacrifices.
These were all truths to the people who held those beliefs. Now we know different.
Given what we know now, it is only logical to assume that our current truths may be false in the future. Even physics, the foundation upon we base so many truths may be proven to be wrong or incompatible with other parts of the universe.
Most things are not the best version of themselves therefore there is always room for improvement.
Since things get better all the time, it is only logical to assume that even the best thing we can think of is not the best version of that thing. The "best" is relative to time, technology and imagination.
Whenever someone says "but we already have X that works great", that doesn't mean that Y cannot be better than X, nobody just thought of it yet.
Stay curious, stay hungry and know that you can create something better.
Take experts with a grain of salt
Even the top experts in their fields are often incorrect.
For example - I know a lot about conversion optimization, but if you were to take every advice I dish out, some of it will inevitably flop.
When you get to an expert level, when someone asks you something you don't know, it is tempting to give an answer. When many people ask you for something, it's even more tempting to respond.
Saying "I don't know" is difficult even if you feel that you should say it. Before you can utter the words, your mind says "I should know this..."
The second factor that makes experts not as credible as they may have been in the past, is the speed at which technology moves.
Think about a specialized doctor. This doctor may be the top expert in their field, but it is impossible for them to read the thousands of medical journals published every day. So many breakthroughs could happen in a year without this doctor ever knowing about them.
By the time an expert weighs in, the "truth" of the matter may have already shifted.
Knowing this, you can assume that not everything an expert says is correct, especially if they step outside of their lane.
Elon Musk is a great example of this. While Elon is a successful entrepreneur and perhaps knows a thing or two about rocket engines, when he steps outside of his lane and talks about crypto, he is no more coherent than someone who spent a lot of time in the space. He uses his influence to prop up things like dogecoin for fun and games, while people lose their life savings following his doge tweets.
I'm not saying that he is responsible for people's personal decisions, but he does influence them.
-
 @ 0adf6747:7f3e5033
2023-08-17 16:31:43
@ 0adf6747:7f3e5033
2023-08-17 16:31:43Es war einmal ein talentierter Developer namens Max, der leidenschaftlich gerne Code schrieb. Er war jedoch nicht nur ein begabter Programmierer, sondern auch ein überzeugter Bitcoiner und Nostr Nutzer. Für Max waren Dezentralisierung und Freiheit wichtige Prinzipien, die er in allen Bereichen seines Lebens verfolgte.
Eines Tages entschied Max, sein neuestes Projekt auf Github zu hosten, da dies für viele Entwickler die übliche Vorgehensweise war. Doch als er sich genauer mit den Bedingungen und Richtlinien von Github auseinandersetzte, wurde ihm klar, dass dies nicht mit seinen Prinzipien vereinbar war.
Github war ein zentralistischer Host, der von einem einzigen Unternehmen kontrolliert wurde. Max sah darin einen Widerspruch zu den Idealen der Dezentralisierung und Freiheit, die er als Bitcoiner und Nostr Nutzer hochhielt. Er wollte nicht Teil eines Systems sein, das Zensur und Kontrolle ermöglichte.
Entschlossen, prinzipientreu zu bleiben, beschloss Max, Github zu boykottieren. Er suchte nach alternativen Plattformen, die dezentralisiert und frei von Zensur waren. Er fand verschiedene Möglichkeiten, seinen Code zu hosten und seine Projekte mit anderen Entwicklern zu teilen, ohne dabei seine Prinzipien zu verletzen.
Er war begeistert von der Möglichkeit, seine Arbeit in einer Umgebung zu teilen, die von keiner einzelnen Entität kontrolliert wurde. Er fand Gleichgesinnte, die ebenfalls gegen die Zentralisierung kämpften und alternative Lösungen entwickelten.
Obwohl Max anfangs Bedenken hatte, dass er durch den Boykott von Github weniger Sichtbarkeit und Anerkennung erhalten könnte, stellte er schnell fest, dass seine Prinzipientreue ihm eine treue Gemeinschaft von Unterstützern einbrachte. Andere Entwickler, die ebenfalls gegen Zensur und Kontrolle waren, schlossen sich ihm an und unterstützten seine Projekte.
Mit der Zeit gewann die Bewegung gegen die Zentralisierung an Fahrt. Immer mehr Entwickler schlossen sich dem Boykott von Github an und suchten nach dezentralen Alternativen. Die Gemeinschaft wuchs und wurde zu einer starken Stimme gegen Zensur und Kontrolle.
Max war stolz auf das, was er und seine Mitstreiter erreicht hatten. Sie hatten bewiesen, dass es möglich war, prinzipientreu zu bleiben und dennoch erfolgreich zu sein. Sie hatten gezeigt, dass es Alternativen zu zentralisierten Plattformen wie Github gab und dass man seine Prinzipien nicht opfern musste, um seine Arbeit zu teilen.
Die Geschichte von Max und seinem Boykott von Github wurde zu einem Symbol für den Kampf gegen Zensur und Kontrolle in der Entwicklergemeinschaft. Sie erinnerte die Menschen daran, dass es wichtig war, prinzipientreu zu bleiben und für die eigenen Überzeugungen einzustehen, auch wenn es manchmal unbequem war.
Max und seine Mitstreiter hatten eine Lektion gelernt: Sie hatten bewiesen, dass man nicht auf zentralisierte Plattformen angewiesen war, um seine Arbeit zu teilen und mit anderen zu kollaborieren.
-
 @ 604e96e0:20279eb2
2023-07-29 18:36:51
@ 604e96e0:20279eb2
2023-07-29 18:36:51There's a secret mode on PlebPay called "proofofplebpay" which I made for someone who wanted to sell tickets to a private event a long time ago. In order to try this out, type in
proofofplebayinstead of a URL when creating a paywall.
Check out this example paywall here: https://www.plebpay.com/27414e6d-00cd-42e7-9d61-b5a63004abe2
When a user pays the paywall, they are given a receipt which they must save and give to you when requested.

This receipt page can be viewed here: https://www.plebpay.com/27414e6d-00cd-42e7-9d61-b5a63004abe2/paid-invoices/9291d459-d2c3-4611-be5e-7d178b3a78b9
Receipt for a given proofofplebpay paywall can be verified by adding on
verify-receipt-idto the end of the paywall URL e.g. https://www.plebpay.com/27414e6d-00cd-42e7-9d61-b5a63004abe2/verify-receipt-id.

-
 @ 1bc70a01:24f6a411
2023-07-29 13:15:49
@ 1bc70a01:24f6a411
2023-07-29 13:15:49I’m going to think out lout about the UAP hearing a bit, feel free to tune me out.
Scenario 1
The one most of us are probably thinking: This entire thing is a distraction from one or many known or unknown issues currently underway. It must be so bad that it warrants national attention to the all-entertaining “UAP” subject.
For this to be true, we have to assume one of the following: 1. The people testifying are lying. Maybe paid actors, maybe not, who knows, but they are not telling the truth. 2. They are telling their “truth”, however they obtained it, perhaps even their reality. We do know UFOs are commonly reported worldwide, so perhaps they are just telling what they saw.
In terms of congressional involvement, scenario one would mean that some or all of the congress members are full of shit. This is an unlikely scenario in my mind (hard to get everyone to go along with a lie). The more likely scenario is that they are in it for the wild ride, totally unaware they are being used as pawns (or at least some aren’t).
What makes this scenario possible in my opinion is that Grush is allowed to speak about the events publicly but not discuss details (unless privately). This makes for good public theatre. Why would unsanctioned projects allow Grush to even go so far as to speak about the events when a slip and fall accident could occur at any moment? The answer would have to be either: 1. Because it’s all bullshit, or mostly bullshit. 2. Because the agencies involved are really THAT incompetent and hadn’t figured out what is happening. 3. Because they have no problem with him talking about it because they would like to slowly disclose alien technology and the fact that we’re not alone. 4. To serve the purpose of distraction.
Assuming scenario 1 is correct, the most likely scenario is that the people involved are telling their own version of truth and that some of the congressional members are unaware of the real reason they’re there.
This is an easy fallback for any time you want to divert attention from some other pressing matters. Just talk about UFOs!
The earlier story in NY Times would also make sense in this case - as the NYT has been known to act as the propaganda arm of the government. The NY Times story brought a lot of attention to the matter, but we have to also wonder why this was under the rug for so many years? Perhaps because it’s pure bullshit.
The “It’s real!” Scenario….
Let us assume that this is not a distraction. The people testifying are telling the truth. Everything is as they say it is. Ooof!
This would mean that everything Grush says is true - there are unsanctioned programs and or people with extreme privilege and clearance not granted to anyone else. People that are not even part of the government in any way.
It would also mean we have recovered alien craft and bodies and have attempted to reverse engineer their tech. Perhaps we already succeeded and what we see flying around today is this reverse engineered tech, or actual ETs.
What would make this scenario real?
Well, there is no shortage of UFO sightings. People swearing their life on it. For us to discount all of them would mean calling everyone a liar, or just confused about some other phenomena. I wouldn’t bet on all liars and delusional, but confused, maybe. Still, some accounts are just too out there to dismiss without some serious thought. The fact that people’s stories seem to match could mean that there’s truth to those reports.
Perhaps the aliens use pods (classic saucer shapes, or “tic tacs” or other shapes craft. Maybe the “cubes” in orbs are their versions of drones? Or not? Maybe the large cubes are spacecraft.
Yes, they cover vast amounts of space quickly and STILL crash on our planet. Rookies that failed the landing maneuver in flight school… heh.
The governments of the world are all cooperating in hiding the truth and or the US government has unprecedented access to other parts of the world to recover and cover up various incidents. WOW… ok. That means we have something like a one world alien-communication government that has unprecedented access beyond anyone’s control. How??
If this is the real deal, we should all be losing our minds right now. The prospect of another species with vastly superior technology with interest in our nuclear dealings should scare everyone. Forget everything else, this is priority #1.
THE PROBLEM with this scenario?
- Some foreign govt. would have already revealed what they know. Would they not? Are we to believe they are all collaborating on this with some inter-government agency that acts with ultimate authority? Why? How? Maybe they are already speaking out and I’m unaware?
- We STILL don’t have any definitive evidence. He said, she said, they said. “First account” from a “trusted source”. OK.
- Aliens possess mind-blown tech, but still crash once in a while. I guess you could say that there will always be a small chance of crash no matter who is flying what. I’ll give people that.
- “It’s classified”. No amount of talking seems to reveal the actual “classified” information. Even during the congressional meeting it’s always “I can tell you privately”, and “I’m not permitted to talk about this by law”. Which is it? Are you, or are you not allowed to speak on the matter? Why can you disclose it behind closed doors but not in public? Seems rather strange to me.
In the “It’s all real!” Scenario, we are all screwed. Either we are being prepped for eventual disclosure of alien life or aliens can do crap we can’t protect against. If we’re being prepared for disclosure, it may mean that we have no say in how things unfold on our planet and the best we can do is ease people into it without everyone losing their minds. In that case, a series of hearings on the matter might make sense. Keep talking about it louder and louder until people are no longer shocked to hear the truth. Buckle up everyone, things are about to get interesting!
Scenario 3: “Trust Us, We’re here to serve you”
From the hearing, we hear multiple times congress mention “distrust in the government” and “rebuild trust”. In line with Scenario 1, this would mean everything is just a smoke screen to “build trust”. “Oh look, congress cares about me😍!!”
It would make sense why nothing has been revealed concretely and no foreign government came forward yet. Didn’t you know, UFOs only crash in the states! Haha.
Congress is just “building back trust”, either fully aware of the lies, or using mentally unstable people for their gain. Not saying the witnesses are mentally unstable, but you never really know, do you? Tell yourself a story enough times, it becomes a reality.
My Personal Take?
I wish to remain open minded about this subject. There are too many questions unanswered for me and I don’t want to dismiss anything entirely. Could there be aliens visiting this planet? I don’t see why not. We don’t know what we don’t know. For me to dismiss the possibility of non-human life traveling to our planet would mean to believe we have learned everything there is to learn about physics and the universe, when in fact it is the opposite, we know little to nothing.
Could it be bullshit? Yes, of course. I also like to consider things from a practical perspective and think in terms of probabilities rather than right and wrong, yes or no. If I had to guess the odds of aliens traveling to our planet, I’d give it at 5% chance. So yeah, not much. I’m much more inclined to believe this is all just human manipulation to achieve some agenda. I won’t speculate what that agenda might be as it’s anyone’s guess really. There’s no way to prove anything.
Should all of this be real, things are going to get very interesting…
-
 @ 7f4f672a:c184579e
2023-08-17 06:46:05
@ 7f4f672a:c184579e
2023-08-17 06:46:05This week I joined Buildspace's "Nights & Weekends" - a free online school for people to work on an idea and develop it over 6 weeks, with feedback and mentorship along the way. The first days are dedicated to ideation and the tricky question of what to work on. This came at a timely moment for me - I'd recently read a great book that upended how I thought about ideas and goals.
In the months prior, I was forcing things; planning, mind-mapping, ideating, following all the usually prescribed "steps" to the epiphany. Nothing was working, previous projects had ran their course, while I was unsure what my next one would be. I'd attempted a few projects in spaces I thought would lead to success & business, but nothing was capturing my enthusiasm, and unsurprisingly, nothing worked. By late June, I'd had enough. In a chance encounter, I came across a book which clarified and expressed an intuition I felt I had on some level over the previous months.
Why Greatness Cannot Be Planned by Stanley & Lehman breaks apart the mainstream paradigm of goal-setting and 'good' ideas, which they say has mired many creators, particularly in the tech space; where product-market-fit, the customer development model, and ultra-rational approaches are dogma. The book immediately draws in the reader, with the revelation that you cannot plan for great, ambitious projects and goals:
They ignore the value of following a path for its own uniqueness, rather than for where it may lead.... ...... great discoveries are lurking just beyond our fingertips, if only we can let go of the security blanket of the objective. Sometimes the best way to change the world is to stop trying to change it - perhaps you've noticed your best ideas are often those you were not seeking.
The Search-Space
The authors introduce us to the abstract "search-space" - think of it as a vast room where all ideas & possibilities exist. We explore this room when we ideate; I imagine it to be an infinite space, bright, but with a dense fog. All the unfound ideas of the world are in this room - if we traverse it well, we can discover them. The cure for cancer, fusion energy, new surgical procedures, your next favourite song - are all in this room. We navigate through it step by step, starting at one idea, and from there we can see our next. The authors warn us that the pathways to really ambitious goals are non-obvious and impossible to predict when we are in the search-space.
They use the example of the ambitious goal of building the first computer. In the early 19th century this was attempted by Babbage , however this idea was ahead of it time and what really led to the implementation of modern computers was something completely unrelated - vacuum tubes. Those who set out to build vacuum tubes had no intention of building computers (they needed them for something else), and anyone in the search-space trying to build a computer would not have started by building vacuum tubes. It could never have been planned and was non-obvious from the start! An interesting insight and a perfect example of the nuances of the search-space.
Navigating & False Compasses
So instead of a grand plan, it is better to just start on a stepping-stone (an idea), and let new stepping-stones (more ideas) come into view. Our goal then becomes collecting stepping-stones to traverse the search-space, rather than reaching for a stepping-stone miles away with no discernible path towards it. Even if we thought we had a path, the authors warn that this is often a false compass - for ambitious goals it’s never obvious.
A goal of starting a successful tech company is ambitious, and with my old beliefs, I would only have followed ideas I thought could get me there - niche markets, business solutions ; all that obvious boring, over-thought, and contrived nonsense (which I believe is particularly prevalent on social media today via tech and business influencers). Now, I realise that that will never work. Unwittingly, I had limited myself to a confined area of the search-space, putting up walls made of my false beliefs about success and goals. I could not see, or would not see, stepping stones close by which did actually have my curiosity - but didn't make sense in the "grand plan" - Why would I make a music lyrics web app or write essays no one will read when there's no clear market or business model ? So I didn't - instead I tried things which had neither my curiosity nor interest. I was barking up the wrong tree. Then, I looked back and realised that my most successful project (if a few 100 users and some national attention is success) came from something that I was interested in which had no obvious business potential - a public good website for listing vacant and derelict properties in Ireland - www.dog-house.ie . That project is still not a business, and has not led to one property renovation, but it did raise awareness - which was all the original stepping stone was.
Lost & Found
The penny had dropped, I was lost in the search-space, and needed to get back to basics. My resolution was simple: stop trying so hard - just follow my curiosity and genuine interest. Adopting this new mindset led me to Nostr, and the work being done in the space using Bitcoins Lightning Network. For those new to Nostr - it's a new technology for social media & communication in general, a place where you own your social experience. Users can keep followers, posts, likes, and replies across platforms & apps. Some people won’t care, but for creators - this is a key innovation. You can view Nostr messages through clients. Clients are websites/apps that connect to the Nostr network. Think of them like different doors to the same room – your content and followers stay the same, whichever door you choose.
Exploring the stepping stones nearby, I found one which suited my interests and was something I would use - making an Obsidian plugin to publish long-form content seamlessly to Nostr (this essay came from that!). From there, I saw the potential for writers on Nostr; keep your audience, monetise easily, no platform dependency or lock-in, content ownership - the perfect place to publish. Then, the next stepping stone came into view - I decided to start publicly sharing some work I had written. This was something I'd wanted to do for a while but had never found the courage to do so. As the audience and visibility on Nostr is low today it helped me click publish and get off the mark - another serendipity on this trail of stepping stones! Finally, I'd discovered some long-form Nostr clients and enjoyed reading articles and posts on them. On Nostr, you can publish short-form Twitter like messages or long-form material; essays, blogs posts, reviews, op-eds, etc. The next stepping stone came into view - maybe I could build a long-form Nostr client that curated and displayed content in a novel way.
So, off the back of learning about this new space, and publishing written content to it, I decided this would be a fun thing to try and build over the next 6 weeks of "Nights & Weekends". The idea is still forming, and who knows where the next stepping stone will lead, but it feels like a relief to adopt this new approach and traverse the search-space care-free, knowing now that great things cannot be planned, and that, with some luck, serendipity would find me along the way.
References/Resources: Why Greatness Cannot Be Planned by Kenneth O. Stanley & Joel Lehman https://buildspace.so/nights-weekends
ideas #tech #buildOnNostr #bookReview
-
 @ 20986fb8:cdac21b3
2023-07-29 06:45:23
@ 20986fb8:cdac21b3
2023-07-29 06:45:23YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Round 2 will be from 27th to 30th July
How to participate:
- Pick one or multiple Updates below, test it (them)
- Write your feedback and opinion (pros and cons are all welcomed)
- Post your article on Nostr via YakiHonne.com
- Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our group: http://t.me/YakiHonne_Daily_Featured
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped during each round.
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
Updates to be tested in Round 2:
-
Comments: re-implemented and comments can be deleted
-
NIP-25 supporting: users now can upvote and downvote
-
Zap stats: Zaps sent and Zaps received can be seen from users profiles
-
“login with an extension” button: now it is grayed out rather than invisible
-
Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme
-
Tags: click on the tags in the article to view the content under the tag
-
Share: sharing posts with one click
-
NIP-05: verify your profile
If you missed Round 1, the updates below could be tested as additions:
-
Comment function: more user-friendly
-
Stats area: clearly displays the interactive status of each article
-
Following function: generated-key users can also be followed
-
Curation function: easily add or remove articles from an existing curation
-
Tags: search and browse articles with the tags
-
Home feed scrolling pagination: optimized data fetching and faster loading time
-
Article editing preview: preview the final version of the article while writing in MarkDown
Don't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ c7c59790:8cea49eb
2023-08-17 03:28:27
@ c7c59790:8cea49eb
2023-08-17 03:28:27Nostr, which stands for “Notes and Other Stuff Transmitted by Relay”, is a decentralized, censorship-resistant social protocol. Nostr is a place where we all escape from darkness and achieve peacefulness.
Nostr has 3 main components; clients, relays, and users. Unlike Twitter where backend servers are controlled by a group of people, anyone and everyone can run relays to maintain Nostr protocol. Clients (web, mobile, desktop apps) fetch data from relayers and send new data from users to relayers. In other words, relays act like the backend server for Nostr. Relayers doesn’t communicate each other.
For example, if Bob use Relay-A and Ken use Relay-B, Bob can’t see Ken. But if Bob use Relay-A and Relay-B, Bob can interact with Ken. That’s why it is best to use multiple relays.
Each user has a pair of public and private keys; generally public keys start with ‘npub’ and private keys start with ‘nsec’. Public key act like username and private key act like password. But private key can’t change like normal password. So, it is best to store private key in safe place.
Since Nostr is the decentralized social protocol which no single people have control, it is not a good idea for each developer to solve common issues with different own solutions and implement it in their own app only. NIP, Nostr Implementation Possibilities, exist to coordinate the process. Currently there are 99 NIPs.
This is my first content about basic understanding of Nostr. Hope u enjoy it.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ 9ecbb0e7:06ab7c09
2023-08-17 02:52:08
@ 9ecbb0e7:06ab7c09
2023-08-17 02:52:08Un joven cubano pidió ayuda urgente a través de redes sociales para encontrar donante de sangre para una embarazada que necesita una transfusión sanguínea de O negativo.
"Lo pago al precio que sea, es para una embarazada a punto de parir o morir, 54508011, llámenme, que la decisión quede de parte de ustedes...Dios los bendiga", escribió en su perfil personal de Facebook Yudenys González Loyola.

En el apartado comentarios a la publicación -hecha este 14 de agosto- una comentarista sugirió que compartiera la petición en varios grupos de Facebook en aras de ganar visibilidad.
Yudenys no precisó en qué provincia reside la embarazada necesitada con urgencia de una transfusión de sangre. No obstante, según sus redes sociales, el joven reside en Camagüey.
La escasez de sangre en Cuba se ha convertido en uno de tantos problemas en la isla. Los hospitales tienen una absoluta carencia de reservas de sangre.
En los últimos años cada vez más los ciudadanos recurren a las redes sociales para encontrar quien pueda poner a salvo sus vidas o las de sus familiares con donaciones voluntarias.
A inicios de enero, una cubana necesitada de una transfusión de sangre murió en La Habana. En ese caso la sangre era para una mujer que tenía la hemoglobina muy baja y no podía esperar un minuto más para ser transfundida.
A finales de julio, una maestra residente en La Habana pidió ayuda en redes sociales para conseguir donantes de sangre para su hermana, paciente de leucemia.
También por esas fechas, una periodista del periódico oficialista Girón pidió ayuda para su abuela, quien necesitaba una transfusión de sangre en Matanzas.
Incluso los médicos recurren a Facebook para intentar conseguir donaciones para sus pacientes. Tal fue el caso del doctor Juan Pablo Gurri Fuentes, quien en septiembre del pasado año recurrió a su cuenta de Facebook para solicitar donantes de sangre para tres pacientes ingresados en su hospital, el Calixto García, en La Habana.
Datos de la Oficina Nacional de Estadísticas e Información (ONEI) muestran que entre 1990 y 2019 el número de donantes de sangre en Cuba disminuyó de forma significativa, pasando de aproximadamente 389 mil a 209 mil al año.
Angustiados por la urgencia, algunos cubanos necesitados de sangre para un allegado no dudan en proponer dinero a cambio de una donación.
-
 @ 6389be64:ef439d32
2023-07-29 02:29:23
@ 6389be64:ef439d32
2023-07-29 02:29:23Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8
Soil pH of between 6.0 and 7.0.
Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber
- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees
- The edible flower clusters are also a top food source for honey bees
Shade Provider
- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break
- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- [[Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043]]
- Over 20% crude protein
- 4.1 kcal/g of energy
-
 @ 9ecbb0e7:06ab7c09
2023-08-17 02:49:24
@ 9ecbb0e7:06ab7c09
2023-08-17 02:49:24El dólar implantó este miércoles un nuevo récord en el mercado informal cubano, al subir un peso en relación con el día anterior, y alcanzar los 250 pesos en el mercado informal por primera vez.
El hecho agudiza la grave crisis que aqueja a la moneda nacional, que viene hundiéndose desde hace meses en el abismo de la devaluación.
En lo que respecta al euro y la moneda libremente convertible (MLC), mantienen este 16 de agosto sus valores del martes, en 255 y 215 CUP, respectivamente.

Según la tasa publicada este 16 de agosto por el medio digital independiente elTOQUE, en el caso del dólar se llegaron a reportar en las últimas 24 horas ofrecimientos de compra por un mínimo de 245 pesos y un máximo de 250 en la venta.
En el caso del euro la mediana fue de 252 CUP en la adquisión y de 255 en la venta.
Para el MLC no hubo oscilación de precios, y se situó en 215 CUP tanto la compra como la venta de la moneda.
-
 @ bcea2b98:7ccef3c9
2023-07-29 00:48:14
@ bcea2b98:7ccef3c9
2023-07-29 00:48:14I remember the first time I caught the neon glow of the blockchain data-stream pulsating through the old fiber-optic cables in the urban labyrinth of Neo-Tokyo. That was the year Satoshi’s dream, Bitcoin, had become the last refuge of economic freedom, our Prometheus unbound from the chains of tyrannical central banking. That was the year the world ended and started anew, all at once, like the flicker of an old digital display struggling to hold onto a single pixel of hope.
Cyber-Sentries, autonomous quantum-resistant algorithms birthed in the tech womb of Bitcoin Core, roamed the noospheric network, relentless in their hunt for anomalies that could threaten our crypto-republic. Their code was hardened against the threat of quantum decryption, a terror from the old-world that now lurked in the shadows of the darknet. Armed with Q-Diffusers, inventive tech developed to obscure any coherent superposition of qubits, the Sentries were the silent, digital paladins of our new world.
The Cyber-Sentries were the silent guardians of our cryptoverse, digital watchdogs built on an intricate framework of quantum-resistant algorithms. Brought to life in the crucible of Bitcoin Core, these Sentries were the vanguards of Satoshi's legacy, standing watch against potential threats.
Imagine a predator of the old-world, a wolf maybe, that would tirelessly patrol its territory, sniffing out any intruder that dared to violate its space. A Cyber-Sentry was much like that, except its territory was the vast terrain of the Bitcoin network, and its sense of smell was replaced by a near-infallible ability to detect irregularities and potential threats in the data streams.
These Sentries were powered by an advanced AI system, coded to learn and adapt to evolving threat landscapes. Every anomaly detected was analyzed, its signature extracted and stored in a vast neural repository, a cerebral vault of threat patterns. The Sentries learned from each encounter, evolving their defenses with every battle fought.
Each Sentry was armed with Q-Diffusers, state-of-the-art technology designed to disperse any coherent superposition of qubits. These Q-Diffusers would essentially introduce a deluge of quantum noise into the system of any would-be attacker, rendering their quantum computing capabilities useless. This was their primary defense against the quantum decryption threat, their shield against the spectral specter of the old-world quantum terror.
In action, the Cyber-Sentries were like specters, a ghost in the machine. Unseen, unheard, they roamed the neural pathways of the network, ceaselessly vigilant. When a threat was detected, they would swarm, a lightning-fast, coordinated response that left adversaries disoriented and defeated. They were not just defenders; they were also deterrents, their formidable reputation alone enough to ward off many would-be attackers.
Ever-present, though unseen, was the hum of the Lightning Network. Its evolution had exceeded even the wildest predictions of the cypherpunk prophets. Beyond mere instantaneous transactions, it now powered our communications, our commerce, our very lives. Its channels were our veins, the satoshis our lifeblood, coursing through the body of the new age, offering near-infinite scalability, an economic pulse for every living soul.
In this cryptic symphony, a new tech marvel played the sweetest tune. The Merkle Sanctum, an advanced shield technology, made the Bitcoin network impervious to attacks. At its core was the labyrinthine, self-regenerating maze of hash-based proof functions. Each function was an arcane spell in itself, casting away would-be invaders into oblivion. To attempt a breach was to confront infinity itself, a Sisyphean task for even the most formidable foe.
Merkle Sanctum was the magnum opus of cryptographic defense in the Bitcoin network, a technological marvel that made it nigh-impregnable to attacks. Named in honor of Ralph Merkle, one of the godfathers of modern cryptography, the Sanctum was more than just a defensive system. It was a monument to the boundless ingenuity of the human mind, a labyrinthine fortress constructed in the abstract plane of mathematical probabilities.
At its core, the Merkle Sanctum functioned as a self-regenerating maze of hash-based proof functions. These functions were cryptographic constructs, sequences of mathematical operations designed to protect the network. They were like invisible walls in the Sanctum, each one unique and insurmountable.
The true genius of the Sanctum was in its dynamic architecture. Each hash-based proof function was not static; it evolved with every transaction, every second that passed in the Bitcoin network. This made the Sanctum a dynamic, ever-changing labyrinth. Its walls shifted, its passages morphed, its structure regenerated in the blink of an eye. To an attacker, it presented a puzzle that was infinitely complex and perpetually changing.
This dynamic nature was powered by the pulse of the Bitcoin network itself. Each transaction, each data packet, each heartbeat of the network served as a seed of change, a catalyst for the regeneration of the Sanctum. It was a system in symbiosis with the network, drawing strength from the very activity it sought to protect.
Yet, despite its complexity, the Sanctum was not impenetrable. After all, the aim was not to exclude but to protect. Legitimate network participants could navigate through the labyrinth with the aid of cryptographic keys, their unique digital signatures acting as Ariadne's thread in the shifting maze. These keys allowed them to bypass the proof functions, moving through the Sanctum as if through open doors.
To invaders, however, the Sanctum presented a challenge of Herculean proportions. With its dynamic, ever-changing architecture, and near-infinite complexity, attempting to breach the Sanctum was like trying to capture a waterfall in a sieve. It was a task beyond the reach of even the most sophisticated quantum computer, a futile attempt to conquer a fortress that was as mercurial as it was formidable.
Humans huddled in the neon halo of their digital screens, their eyes reflecting the dancing symbols of hope and freedom. Pseudonymous, untraceable, they whispered to each other across the globe. Deals were brokered, wisdom shared, love declared - all in the cryptic tongue of Bitcoin. In this world on the edge of time, humanity had reclaimed its voice, and with it, the power to dream again.
The year 2140 dawned in the neural cortex of the global hivemind. In the alleyways of the silicon city, miners with their rigs, now relics of a different era, gathered for the last hurrah. These were the custodians of the cryptoverse, their ASICs humming lullabies of complex mathematical problems, their veins humming with electricity. The air was thick with hope and a sense of closure as they prepared to decipher the final hash.
The clock struck the hour, the Ledger of Eternity, a monumental quantum blockchain register, started the countdown. The world held its breath as the final block reward, a mere satoshi, the last of the 21 million, was offered up for claim. The blockchain was a spiderweb of transactions and mathematical riddles, intricate, indecipherable.
A hush fell over the data streams as the ASICs began their dance. The miners’ eyes glowed with the reflected light of the complex computations running on their screens. They could feel the pulse of the network in their blood, in the electrified air that buzzed around their rigs.
Then, in an almost anticlimactic moment, the final hash was deciphered, the block reward claimed. The last satoshi nestled itself in a digital wallet. The entire cryptoverse erupted in silent celebration, a solitary firework blossoming in the inky black of the datastream.
For the first time since its inception, Bitcoin existed without the promise of a block reward. Yet, it did not falter. It stood resilient in its quiet dignity, an economic lodestar in the chaotic quantum sea. For what had begun as an incentive mechanism was now a symbol of freedom, a testament to a world unshackled from the chains of traditional economic structures.
As 2140 rolled on, Bitcoin stood at the precipice of a new age. Without the block reward, it had transformed, yet again, to embody its core tenet of resilience. It was no longer a system driven by the promise of reward but one that thrived on the principles of decentralization and autonomy, the beacon of economic freedom in a brave, new digital world.
-
 @ 9ecbb0e7:06ab7c09
2023-08-17 02:40:03
@ 9ecbb0e7:06ab7c09
2023-08-17 02:40:03El Ministerio de Salud Pública de Cuba (Minsap) emitió una alerta para la provincia de Guantánamo, en el extremo más oriental de la Isla, debido al aumento de los casos de cólera que se viene registrando en los últimos días.
Aimeé Blanco, líder del departamento de Enfermedades Trasmisibles en el Centro de Higiene, Epidemiología y Microbiología de Guantánamo, comentó que activaron un puesto de mando para chequear las medidas preventivas dirigidas a salvaguardar la salud de la población.
Una de las principales acciones es arreciar al control en las fronteras, pues los especialistas refieren que la enfermedad está siendo introducida al país desde naciones vecinas que reportan en la actualidad un aumento en la incidencia del cólera.
Los viajeros son sometidos a quimioprofilaxis, recibiendo una dosis de doxiciclina como parte de los controles sanitarios internacionales. Además, se les brinda vigilancia clínica a través del sistema básico de salud desde su llegada a Cuba y hasta dos semanas después.
La prioridad es la detección temprana de cualquier síntoma que se sospeche que haya sido provocado por el bacilo Vibrio cholerae. De acuerdo con Aimeé Blanco, en el territorio hay tests rápidos para confirmar el diagnóstico y tomar medidas de manera inmediata.
Los mismos exámenes se realizan a los pacientes que llegan a los cuerpos de guardia con signos de deshidratación, según el protocolo establecido para enfrentar enfermedades diarreicas agudas. Lo anterior sin importar que hayan salido de viaje recientemente.
La enfermedad del cólera ha sido históricamente asociada con brotes epidémicos y se caracteriza por la aparición repentina de diarrea acuosa y vómitos intensos. Se transmite principalmente a través de la ingestión de agua o alimentos contaminados con heces infectadas por la bacteria, lo que lo convierte en un problema de salud pública en áreas con condiciones de saneamiento deficientes.
Los síntomas del cólera suelen manifestarse en un período que varía entre unas pocas horas y cinco días después de la exposición a la bacteria. La diarrea acuosa profusa es uno de los síntomas más característicos, y puede ser tan intensa que lleva a la deshidratación y a la pérdida rápida de electrolitos esenciales. Además, los pacientes pueden experimentar vómitos, calambres abdominales y, en casos graves, shock y colapso circulatorio.
El tratamiento oportuno se basa en la rehidratación oral o intravenosa con el objetivo de restaurar el equilibrio de líquidos y electrolitos en el cuerpo. Se utilizan soluciones de rehidratación oral que contienen agua, sales y azúcares para tratar la deshidratación y reponer los nutrientes perdidos. En casos más graves, se pueden administrar fluidos intravenosos.
La prevención del cólera se centra en medidas de higiene y saneamiento adecuadas. Evitar el consumo de agua no tratada y alimentos crudos en áreas de riesgo, lavado frecuente de manos con agua y jabón, y tratamiento adecuado de aguas residuales son estrategias clave para prevenir la propagación de la enfermedad.
-
 @ d030bd23:96435da9
2023-08-16 23:02:52
@ d030bd23:96435da9
2023-08-16 23:02:52"Power of a study represents the probability of finding a difference that exists in a population".
simply put, it tells how strong is the validity of the finding of your sudy. Power depends on 3 main factor: significance level, effect size and sample size.

significance level is pretty straightforward. We decide it anyway. Thus, it is a no brainer why clinical trials tend to use very low p-levels.
You cant really control effect size. It is an after effect that you only gain after data collection.
But sample size, this is one curious bit. Probability sampling, as its name implies, is a process of taking a sample at random to represent the said population. Once, I heard that at times, probability samplings are better than universal sampling. I wonder, how can a sample of "somethihg" is better than the actual thing? The answer lies in missingness. Missingness is a situation where a data or part of a data is not available. Think of a study about relationship between lifestyle and heart disease. Body Mass Index is important and if it is missing, it will be a problem. when many data is lost from a universal sampling, it reduces the universality of the study, decreasing its power. If the missingness is significant, e.g. more than 30%, it might be better to put them as an exclusion criteria and choose random sampling instead. sure, it will stiffen study generalizability later, but it improves the power.
-
 @ bcea2b98:7ccef3c9
2023-07-29 00:46:37
@ bcea2b98:7ccef3c9
2023-07-29 00:46:37The Year 2140
I remember the first time I caught the neon glow of the blockchain data-stream pulsating through the old fiber-optic cables in the urban labyrinth of Neo-Tokyo.
That was the year Satoshi’s dream, Bitcoin, had become the last refuge of economic freedom, our Prometheus unbound from the chains of tyrannical central banking That was the year the world ended and started anew, all at once, like the flicker of an old digital display struggling to hold onto a single pixel of hope.
Cyber-Sentries, autonomous quantum-resistant algorithms birthed in the tech womb of Bitcoin Core, roamed the noospheric network, relentless in their hunt for anomalies that could threaten our crypto-republic.
Their code was hardened against the threat of quantum decryption, a terror from the old-world that now lurked in the shadows of the darknet Armed with Q-Diffusers, inventive tech developed to obscure any coherent superposition of qubits, the Sentries were the silent, digital paladins of our new world.
The Cyber-Sentries were the silent guardians of our cryptoverse, digital watchdogs built on an intricate framework of quantum-resistant algorithms.
Brought to life in the crucible of Bitcoin Core, these Sentries were the vanguards of Satoshi's legacy, standing watch against potential threats.
Imagine a predator of the old-world, a wolf maybe, that would tirelessly patrol its territory, sniffing out any intruder that dared to violate its space.
A Cyber-Sentry was much like that, except its territory was the vast terrain of the Bitcoin network, and its sense of smell was replaced by a near-infallible ability to detect irregularities and potential threats in the data streams.
These Sentries were powered by an advanced AI system, coded to learn and adapt to evolving threat landscapes.
Every anomaly detected was analyzed, its signature extracted and stored in a vast neural repository, a cerebral vault of threat patterns The Sentries learned from each encounter, evolving their defenses with every battle fought.
Each Sentry was armed with Q-Diffusers, state-of-the-art technology designed to disperse any coherent superposition of qubits.
These Q-Diffusers would essentially introduce a deluge of quantum noise into the system of any would-be attacker, rendering their quantum computing capabilities useless This was their primary defense against the quantum decryption threat, their shield against the spectral specter of the old-world quantum terror.
In action, the Cyber-Sentries were like specters, a ghost in the machine.
Unseen, unheard, they roamed the neural pathways of the network, ceaselessly vigilant When a threat was detected, they would swarm, a lightning-fast, coordinated response that left adversaries disoriented and defeated They were not just defenders; they were also deterrents, their formidable reputation alone enough to ward off many would-be attackers.
Ever-present, though unseen, was the hum of the Lightning Network.
Its evolution had exceeded even the wildest predictions of the cypherpunk prophets Beyond mere instantaneous transactions, it now powered our communications, our commerce, our very lives Its channels were our veins, the satoshis our lifeblood, coursing through the body of the new age, offering near-infinite scalability, an economic pulse for every living soul.
In this cryptic symphony, a new tech marvel played the sweetest tune.
The Merkle Sanctum, an advanced shield technology, made the Bitcoin network impervious to attacks At its core was the labyrinthine, self-regenerating maze of hash-based proof functions Each function was an arcane spell in itself, casting away would-be invaders into oblivion To attempt a breach was to confront infinity itself, a Sisyphean task for even the most formidable foe.
Merkle Sanctum was the magnum opus of cryptographic defense in the Bitcoin network, a technological marvel that made it nigh-impregnable to attacks.
Named in honor of Ralph Merkle, one of the godfathers of modern cryptography, the Sanctum was more than just a defensive system It was a monument to the boundless ingenuity of the human mind, a labyrinthine fortress constructed in the abstract plane of mathematical probabilities.
At its core, the Merkle Sanctum functioned as a self-regenerating maze of hash-based proof functions.
These functions were cryptographic constructs, sequences of mathematical operations designed to protect the network They were like invisible walls in the Sanctum, each one unique and insurmountable.
The true genius of the Sanctum was in its dynamic architecture.
Each hash-based proof function was not static; it evolved with every transaction, every second that passed in the Bitcoin network This made the Sanctum a dynamic, ever-changing labyrinth Its walls shifted, its passages morphed, its structure regenerated in the blink of an eye To an attacker, it presented a puzzle that was infinitely complex and perpetually changing.
This dynamic nature was powered by the pulse of the Bitcoin network itself.
Each transaction, each data packet, each heartbeat of the network served as a seed of change, a catalyst for the regeneration of the Sanctum It was a system in symbiosis with the network, drawing strength from the very activity it sought to protect.
Yet, despite its complexity, the Sanctum was not impenetrable.
After all, the aim was not to exclude but to protect Legitimate network participants could navigate through the labyrinth with the aid of cryptographic keys, their unique digital signatures acting as Ariadne's thread in the shifting maze These keys allowed them to bypass the proof functions, moving through the Sanctum as if through open doors.
To invaders, however, the Sanctum presented a challenge of Herculean proportions.
With its dynamic, ever-changing architecture, and near-infinite complexity, attempting to breach the Sanctum was like trying to capture a waterfall in a sieve It was a task beyond the reach of even the most sophisticated quantum computer, a futile attempt to conquer a fortress that was as mercurial as it was formidable.
Humans huddled in the neon halo of their digital screens, their eyes reflecting the dancing symbols of hope and freedom.
Pseudonymous, untraceable, they whispered to each other across the globe Deals were brokered, wisdom shared, love declared - all in the cryptic tongue of Bitcoin In this world on the edge of time, humanity had reclaimed its voice, and with it, the power to dream again.
The year 2140 dawned in the neural cortex of the global hivemind.
In the alleyways of the silicon city, miners with their rigs, now relics of a different era, gathered for the last hurrah These were the custodians of the cryptoverse, their ASICs humming lullabies of complex mathematical problems, their veins humming with electricity The air was thick with hope and a sense of closure as they prepared to decipher the final hash.
The clock struck the hour, the Ledger of Eternity, a monumental quantum blockchain register, started the countdown.
The world held its breath as the final block reward, a mere satoshi, the last of the 21 million, was offered up for claim The blockchain was a spiderweb of transactions and mathematical riddles, intricate, indecipherable.
A hush fell over the data streams as the ASICs began their dance.
The miners’ eyes glowed with the reflected light of the complex computations running on their screens They could feel the pulse of the network in their blood, in the electrified air that buzzed around their rigs.
Then, in an almost anticlimactic moment, the final hash was deciphered, the block reward claimed.
The last satoshi nestled itself in a digital wallet The entire cryptoverse erupted in silent celebration, a solitary firework blossoming in the inky black of the datastream.
For the first time since its inception, Bitcoin existed without the promise of a block reward.
Yet, it did not falter It stood resilient in its quiet dignity, an economic lodestar in the chaotic quantum sea For what had begun as an incentive mechanism was now a symbol of freedom, a testament to a world unshackled from the chains of traditional economic structures.
As 2140 rolled on, Bitcoin stood at the precipice of a new age.
Without the block reward, it had transformed, yet again, to embody its core tenet of resilience It was no longer a system driven by the promise of reward but one that thrived on the principles of decentralization and autonomy, the beacon of economic freedom in a brave, new digital world.
-
 @ 78733875:4eb851f2
2023-08-16 20:50:20
@ 78733875:4eb851f2
2023-08-16 20:50:20We're delighted to announce Josi Baker as our newest LTS grantee.
Josi will receive long-term support from OpenSats for his continued work on Bitcoin Core. His work will consist of pull-request reviews,[^fn-reviews] supporting major release cycles, and his own contributions.[^fn-prs]
[^fn-reviews]: PR reviews by @josibake [^fn-prs]: PRs by @josibake
In the next couple of months, Josi plans to work on the libbitcoinkernel project as a reviewer, tester, and contributor. The
libbitcoinkernelproject is an attempt at modularizing the Bitcoin codebase and extracting consensus logic into something other applications can reuse. This has a number of benefits, namely improved testing and code separation of consensus code within Bitcoin Core and enabling application-specific programs to be written outside of the Bitcoin Core project with increased confidence these applications will be in consensus.In addition to his work on Bitcoin Core, he will continue to work on BIP-352: Silent Payments, focusing on adoption in wallets outside of Bitcoin Core and supporting mobile clients.
Silent Payments are a privacy and UX improvement for Bitcoin wallets that allows static, reusable payment codes without address reuse. The key improvements over existing reusable payment code solutions are improved privacy for the sender and receiver due to eliminating the need for a notification transaction and no additional cost for senders. The proposal also separates sending and receiving, which enables broader adoption. These improvements are particularly relevant for activists wishing to use Bitcoin as a means of raising funds in a private and censorship-resistant way.
The mission of OpenSats is to support and maintain a sustainable ecosystem of funding for free and open-source projects and contributors, especially Bitcoin-related projects and projects that help Bitcoin flourish. Regular contributors reviewing and maintaining Bitcoin Core are critical to the project's continued success. Sustainable funding allows contributors to build expertise over multiple years, which is why we introduced the OpenSats LTS program.
You can apply for the program here:
Support for Josi's work is sourced from our General Fund and made possible by generous donors like you. If you would like to support work like Josi's, consider donating to the fund.
-
 @ bcea2b98:7ccef3c9
2023-07-28 13:48:57
@ bcea2b98:7ccef3c9
2023-07-28 13:48:57The book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Jason P. Lowery offers an extensive exploration of Bitcoin through the lens of strategic and cybersecurity, as opposed to a purely fiscal one. It presents a novel theoretical paradigm for assessing the potential strategic national implications of Bitcoin, viewed as an electro-cyber defense technology as opposed to a decentralized electronic cash system.
The following are some pivotal arguments and possible inaccuracies from the standpoint of a Bitcoin developer:
Proof-of-work
The proposition that Bitcoin, via its proof-of-work protocol, can be perceived as an electro-cyber security framework allowing for the exertion of tangible power in the digital domain. Lowery posits that Bitcoin equips individuals with the capacity to enforce severe physical consequences (represented in wattage) on adversarial entities attempting to exploit them via software. This viewpoint conceptualizes Bitcoin as a mechanism for power projection, enabling individuals to establish and maintain an untrusting, permissionless, egalitarian, and decentralized dominion over bits of information, provided they have the will and capability to wield physical power to safeguard it (Page 245).
-
The critique here, though, points out that this is an intriguing perspective; the primary purpose of Bitcoin is to operate as a decentralized digital currency. The power projection elucidated by the author is an ancillary outcome of Bitcoin's decentralization and inherent security, rather than its primary intent. The function of Bitcoin's proof-of-work algorithm is to fortify the network against double-spending and other forms of attack, not to project power in a geopolitical context.
-
The book also proposes that Bitcoin could upheave human power-based dominance hierarchies from their foundational roots (Page 374). While it's undeniable that Bitcoin has the potential to disrupt conventional financial systems and power structures, it was not designed to be an instrument for power projection in the same way that military or economic resources are. Bitcoin is a tool for financial sovereignty and privacy, not a weapon for geopolitical power struggles.
-
The book seems to equate the physical power utilized in Bitcoin's proof-of-work algorithm (i.e., the energy expended to mine Bitcoin) with the notion of power projection in a geopolitical environment. While it's true that Bitcoin mining demands substantial energy resources, it is distinctly different from the concept of power projection, which usually involves employing military or economic force to influence the actions and behavior of other nations.
Bits and Value
The book asserts that the bits within Bitcoin can symbolize any kind of valuable data that individuals desire it to represent, including but not confined to financial information (Page 375). It further implies that once we have deduced how to keep financial bits of data physically secure against attack, we have in essence figured out how to protect all types of information from physical attack (Page 34).
-
While it is indeed factual that Bitcoin's blockchain can be employed to store and transmit non-financial data, it's crucial to understand that this is not its primary function. Bitcoin was developed as a peer-to-peer electronic cash system, with the primary objective of facilitating financial transactions without necessitating a trusted third party. The data that Bitcoin primarily processes is transaction data, i.e., detailing who transferred how much Bitcoin to whom.
-
The capability to store non-financial data on the Bitcoin blockchain is more of an unintended consequence of its design rather than a fundamental feature. This is accomplished by utilizing specific fields in the transaction data to store arbitrary data, but this practice is generally discouraged because it can result in blockchain bloat. The Bitcoin blockchain is not intended to function as a general-purpose data storage system, and employing it as such can induce inefficiencies.
-
Storing non-financial data on the Bitcoin blockchain does not offer any additional security advantages over storing financial data. The security of the Bitcoin blockchain is derived from its decentralized, proof-of-work consensus mechanism, which ensures that no single entity can control or manipulate the transaction history. This security extends equally to all data housed on the blockchain, whether it's financial or non-financial.
Strangler Pattern
The book suggests that Bitcoin could serve as a "strangler pattern" replacement of our legacy internet infrastructure with a modern architecture that isn’t as clearly susceptible to systemic exploitation and abuse (Page 376). The book further intimates that Bitcoin could operate as the preeminent mechanism employed by digital-age societies to map or anchor elements of the old internet version to the revamped version of the internet (Page 322).
-
While Bitcoin indeed introduces a new, decentralized paradigm for financial transactions and data storage, it isn't designed to supplant the entire internet infrastructure. The internet is an extensive and multifaceted system supporting a wide variety of applications and services, from email and web browsing to video streaming and cloud computing. In contrast, Bitcoin is a specific application that operates on the internet, designed to enable peer-to-peer financial transactions.
-
The claim made by the book appears to conflate the concept of a decentralized financial system (which Bitcoin offers) with the idea of a decentralized internet (which is a much broader and more intricate concept). While there are projects and technologies aiming to foster a more decentralized internet (such as InterPlanetary File System (IPFS) and various blockchain-based "Web 3.0" initiatives), Bitcoin is not one of them.
-
The book's suggestion that Bitcoin could serve as the dominant mechanism for tying the legacy internet to a new version of the internet is speculative and isn't substantiated by current technological realities. While it's true that blockchain technology (the underlying technology of Bitcoin) has potential applications in areas like decentralized identity systems and domain name systems, these are still largely experimental and have not been widely adopted yet.
Kinetic Power
The book propososes that Bitcoin could significantly transform the way humans vie for control over valued resources, effectively resetting the global balance of power in a manner akin to the profound changes brought about by full-scale kinetic world wars (Page 376). The author further proposes that Bitcoin could revolutionize the perception of physical confrontation in the digital-age society (Page 370). Moreover, it's implied that global adoption of an electro-cyber form of physical power competition, facilitated by proof-of-work technologies like Bitcoin, could lead to the genesis of a completely novel form of polity (Page 385).
-
It is undeniable that Bitcoin holds the potential to disrupt conventional financial systems and power structures. However, juxtaposing its impact to the scale and consequences of world wars is hyperbolic and speculative. World wars resulted in massive loss of human lives, extensive destruction, and substantial shifts in geopolitical boundaries and power structures. In contrast, Bitcoin is a digital currency that operates on a decentralized network. While it can indeed influence financial systems and potentially disrupt some power structures, particularly those related to finance and banking, it is incapable of causing physical destruction or loss of life.
-
The book suggests that Bitcoin could spawn a completely new form of polity is speculative and isn't supported by current realities. Although Bitcoin and other cryptocurrencies can indeed influence how people transact and store value, they don't intrinsically alter the fundamental nature of societal organization or governance. They may contribute to shifts in power dynamics, particularly in the financial sector, but they do not supplant the need for traditional forms of governance and societal organization.
-
The book also seems to conflate the concept of power competition in a geopolitical context with the concept of power competition in the context of Bitcoin mining. Bitcoin mining does involve a form of competition, as miners compete to solve complex mathematical problems to add new blocks to the blockchain and receive Bitcoin rewards. However, this is far from the concept of power competition in a geopolitical context, which involves nations competing for resources, influence, and dominance on the global stage.
Projecting Power
The book asserts that Bitcoin, through its proof-of-work technology, could help society secure itself against systemic exploitation of computer networks (Page 378). The author argues that Bitcoin could empower individuals to physically secure their digital information, by projecting physical power in, from, and through cyberspace to impose severe physical costs on those who exploit our computing systems (Page 347). The author further speculates that national adoption of Bitcoin could be conceptualized as the employment of an electro-cyber militia to safeguard and defend a nation’s valuable digital information (Page 360).
-
While it's true that Bitcoin and other cryptocurrencies can provide a level of security and privacy not available in traditional financial systems, it's crucial to underscore that they also introduce new vulnerabilities and potential for misuse. Bitcoin transactions are irreversible, which can make them appealing for fraudulent activities. Bitcoin wallets can be lost or stolen if not adequately secured. The security of the Bitcoin network itself hinges on its decentralized nature and the computational power required to alter the blockchain, but individual users are still susceptible to scams and hacking.
-
The book's suggestion that Bitcoin could serve as a form of "electro-cyber militia" is speculative and not universally accepted within the Bitcoin community. Although Bitcoin does offer a method for individuals to secure their financial transactions against interference from third parties, it is not designed to shield against all forms of cyber exploitation or to serve as a form of national defense.
-
In conclusion, Softwar presents an unconventional viewpoint on Bitcoin's potential influence on national strategic security, proffering that Bitcoin could serve as an effective tool for power projection, system defense, and even societal reorganization. However, these propositions, while intriguing, often veer towards the speculative and seem to be somewhat misaligned with the predominant understanding of Bitcoin's primary purpose and functionality within the field of computer science.
-
While this book undoubtedly offers a unique and thought-provoking perspective on Bitcoin's wider implications, it is crucial to approach these theories with a discerning and critical eye. It is always beneficial to juxtapose such theories with the broader consensus within the Bitcoin development and computer science communities, to gain a more rounded understanding of this remarkable technology. Ultimately, Bitcoin continues to evolve and its full potential, while yet to be fully realized, remains a subject of intense debate and exploration within the computer science community.
-
-
 @ e6817453:b0ac3c39
2023-08-16 16:01:19
@ e6817453:b0ac3c39
2023-08-16 16:01:19By Volodymyr Pavlyshyn
Hello, folks! Today, we're diving deep into the world of wallets, specifically crypto wallets. I've previously discussed the differences between hot wallets, cold wallets, agents, hubs, and other components actively used in Self-Sovereign Identity (SSI). However, today, we're focusing solely on wallets.
What is a Wallet?
A common misconception is that your wallet holds your assets, NFTs, ABCs, and all things crypto. In reality, your wallet is your key management assistant, primarily responsible for managing your private keys and, in some cases, timing. Hence, the term 'wallet' is somewhat misleading. It would be more accurate to call it a signer, keychain, or key master.
The Problem with Wallets
The adoption of SSI and crypto comes with a significant responsibility: managing your private key. If you lose the key, you lose everything. This creates a huge usability problem as there's no way to recover or have a recovery system in place.
The most popular approach to wallets is based on the idea of using a 'seed' instead of keys. This seed is a form of entropy from which you can deterministically generate private keys. This concept was sold as a secure method, with the Bitcoin standard BIP 32 outlining how to convert the seed into multiple different keys of different types.
The Issue with Seeds
However, the question arises: how do you keep the seed secret? How do you recover it? The common solution is to convert your binary entropy into a mnemonic phrase, giving you 12 to 24 words that you need to memorize. But this method has failed spectacularly.
The hierarchical wallet, which is essentially a wallet at its core, has a significant flaw: if you lose the seed, you lose multiple private keys. This is one problem. Another issue is that it works well for one type of cryptography. If you want to combine one key from Bitcoin with another key from more modern chains like Solana, you lose the possibility because of the different cryptography involved.
The Limitations of Hierarchical Wallets
Hierarchical wallets were a cool concept that simplified a lot and allowed you to just memorize a phrase and manage multiple keys. However, it created a single point of failure, a lot of limitations, and the main problem of the hierarchical wallet is the process of recovery, or rather, the lack thereof.
The Quest for the Perfect Wallet
So, what's the best wallet in the world? It's one that the user doesn't even know exists. If we can create a seamless experience for the user, where they don't even realize they have some magic wallet, that would be a success. But what about recovery? What can we do there?
Multi-Part Computations (MPC)
The first idea was multi-part computations, where you split your private key into multiple sub-keys that need to come together to form a quorum. For example, you split it into ten parts, but to get the signature, you need six parts. This off-chain approach allows you to distribute cryptographic materials over the wire, and different people need to come together in some quorum to sign the transaction. However, the problem with MPC is that it's off-chain, and many threshold signature algorithms are not compatible with each other. Currently, we lack a standard that allows us to do this.
Multisig
Another approach, quite similar to the previous one, is multi-signatures or multisig. This is not a new concept. If you're a Bitcoin user, you knowthat you can build an unlocking script that requires the same scheme. For example, in the Lightning Network, you need two of two signatures to unlock the transaction. The idea is simple: you have multiple independent private keys, but you need several of them to unlock the wallet or sign the transaction.
Smart Contracts as Wallets
The majority of multisigs are smart contracts, so the cost of these operations can be high. It usually requires multiple operations. Some networks require you to have some kind of smart contracts, and we will talk about smart contracts as wallets in a moment. But the idea is simple: you have multiple keys, you can distribute them over the wire, and have social recovery.
Account Abstraction
The Ethereum folks came up with the concept of account abstraction. This means that your account and the signing of your transactions can be managed by a smart contract. This changes a lot, including how we validate signatures and operate with accounts. With account abstraction, you have a programmable way of managing your account, signing your transactions, and it could still be social recovery, multisig, or you could create your own programmable concept that will allow you to manage transactions, sign transactions, and manage keys.
Programmable Key Pairs (PKP)
If you don't have such things in your blockchain or maybe you're completely off-chain, you could look at the LIT protocol. The guys there have a quite cool idea of programmable key pairs (PKP) as some kind of NFT. This means that you could mint the key, manage the keys like NFTs, and it's more blockchain-independent, so you could port the programmable key pairs to different networks.
Seedless Wallets
All these things like multisig, MPC, PKP, and others revolve around the concept of seedless wallets. In seedless wallets, you don't have a seed, but you have a different programmable mechanism that allows you to recover your wallet easily.
Conclusion
The world of wallets is complex and ever-evolving. As we continue to innovate and explore new ways to improve security, usability, and recovery, it's crucial to stay informed and understand the mechanisms at play.
If you're doing something in the space of wallets, recovery, security, or usability of Web3 solutions, I'd love to hear from you. I'm always ready to share my knowledge, provide consultation, and collaborate on building something new.
Remember, the best wallet is one that provides a seamless user experience, robust security, and easy recovery. As we continue to innovate in this space, I'm confident that we'll get closer to this ideal.
-
 @ d34e832d:383f78d0
2023-08-16 11:51:25
@ d34e832d:383f78d0
2023-08-16 11:51:25Financial Freedom Through Bitcoin Innovation, Choosing the Better Money System
The struggle for economic soverignity is intrinsically tied to one's ability to communicate and transact freely from a place of empowerment. When communities lack channels for secure self-determination, they find their voices muted in debates crafting tomorrow. Fortunately, emerging technologies unveil hope.
Bitcoin offers a monetary base disconnected from the capricious whims of central authorities, insulating citizens from predatory currency manipulation so detrimental to stability. Though nascent in my local community, its open framework invites perpetual progress.
Lightning wallets epitomize this iterative spirit, bringing satoshis within easier grasp of all. Their intuitive interfaces streamline micropayments at stellar throughput, permissionlessly weaving together farflung peers in reciprocal exchange.
No intermediary extracts tolls from cross-border flows; no border bars trade between kindred spirits. Instead, nodes form an emergent infrastructure beholden only to its users. With each adoption, autonomy spreads in an unstoppable contagion of empowerment.
For independence begins in mind and spirit, finding expression through tools that uplift. Bitcoin redraws the realm of possibilities, restoring people as protagonists of their own destinies. Though challenges remain, commitment to inclusive innovation ensures its promise touching all shores.
Let decentralized proof of work coordination supplant centralized control, guiding progress with compassion instead of coercion. When communities arm themselves with financial self-determination, exclusion loses power over imagination. A brighter future blossoms from the ground up.
Lightning is Amazing
The struggle for financial freedom is inherently linked and woven with the pursuit of independence. When marginalized communities lack access to secure and unfettered communication channels, they are denied a voice in the very discourse that shapes our collective future. So what are some tools, an individual can use to power themselves and their community to self sufficency?
Bitcoin Lightning wallets represent the next generation of Bitcoin storage and transaction management. These sleek and user-friendly apps allow users to send and receive bitcoins quickly and securely, all while benefiting from the speed and low fees of the Lightning Network. With the ability to seamlessly interact with the network and enjoy fast confirmation times, Lightning wallets are revolutionizing the way we think about cryptocurrency transactions. And with a wide range of options available, there's sure to be a Lightning wallet that suits your unique needs. Recommendations for top Lightning wallets include
Lightning Bots
These tools have been in my toolkit for over a year, providing operational abstraction of channels and hops directly into web/desktop/node interfaces.
1. Financial independence: Accepting Bitcoin payments for products and services can provide a degree of financial independence from traditional banking systems and payment processors. 2. Decentralized ownership: Open source projects can have decentralized ownership structures, allowing contributors to have a say in the direction of the project. 3. Transparent funding: Bitcoin transactions are transparent and publicly visible, which can help build trust with customers and investors. 4. Security: Bitcoin's blockchain is a secure ledger that records transactions in a tamper-proof manner. 5. Global reach: Bitcoin can be sent and received anywhere in the world, without the need for intermediaries like banks or payment processors. 6. Potential for high growth: The Bitcoin market is still relatively small, but it has the potential for high growth as more people and businesses adopt digital currencies and signature schemes.
-
 @ bcea2b98:7ccef3c9
2023-07-28 13:37:09
@ bcea2b98:7ccef3c9
2023-07-28 13:37:09Nym's review of Software:
The book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Jason P. Lowery offers an extensive exploration of Bitcoin through the lens of strategic and cybersecurity, as opposed to a purely fiscal one. It presents a novel theoretical paradigm for assessing the potential strategic national implications of Bitcoin, viewed as an electro-cyber defense technology as opposed to a decentralized electronic cash system.
The following are some pivotal arguments and possible inaccuracies from the standpoint of a Bitcoin developer:
- The proposition that Bitcoin, via its proof-of-work protocol, can be perceived as an electro-cyber security framework allowing for the exertion of tangible power in the digital domain. Lowery posits that Bitcoin equips individuals with the capacity to enforce severe physical consequences (represented in wattage) on adversarial entities attempting to exploit them via software. This viewpoint conceptualizes Bitcoin as a mechanism for power projection, enabling individuals to establish and maintain an untrusting, permissionless, egalitarian, and decentralized dominion over bits of information, provided they have the will and capability to wield physical power to safeguard it (Page 245).
The critique here, though, points out that this is an intriguing perspective; the primary purpose of Bitcoin is to operate as a decentralized digital currency. The power projection elucidated by the author is an ancillary outcome of Bitcoin's decentralization and inherent security, rather than its primary intent. The function of Bitcoin's proof-of-work algorithm is to fortify the network against double-spending and other forms of attack, not to project power in a geopolitical context.
The book also proposes that Bitcoin could upheave human power-based dominance hierarchies from their foundational roots (Page 374). While it's undeniable that Bitcoin has the potential to disrupt conventional financial systems and power structures, it was not designed to be an instrument for power projection in the same way that military or economic resources are. Bitcoin is a tool for financial sovereignty and privacy, not a weapon for geopolitical power struggles.
The book seems to equate the physical power utilized in Bitcoin's proof-of-work algorithm (i.e., the energy expended to mine Bitcoin) with the notion of power projection in a geopolitical environment. While it's true that Bitcoin mining demands substantial energy resources, it is distinctly different from the concept of power projection, which usually involves employing military or economic force to influence the actions and behavior of other nations.
- The book asserts that the bits within Bitcoin can symbolize any kind of valuable data that individuals desire it to represent, including but not confined to financial information (Page 375). It further implies that once we have deduced how to keep financial bits of data physically secure against attack, we have in essence figured out how to protect all types of information from physical attack (Page 34).
While it is indeed factual that Bitcoin's blockchain can be employed to store and transmit non-financial data, it's crucial to understand that this is not its primary function. Bitcoin was developed as a peer-to-peer electronic cash system, with the primary objective of facilitating financial transactions without necessitating a trusted third party. The data that Bitcoin primarily processes is transaction data, i.e., detailing who transferred how much Bitcoin to whom.
The capability to store non-financial data on the Bitcoin blockchain is more of an unintended consequence of its design rather than a fundamental feature. This is accomplished by utilizing specific fields in the transaction data to store arbitrary data, but this practice is generally discouraged because it can result in blockchain bloat. The Bitcoin blockchain is not intended to function as a general-purpose data storage system, and employing it as such can induce inefficiencies.
Storing non-financial data on the Bitcoin blockchain does not offer any additional security advantages over storing financial data. The security of the Bitcoin blockchain is derived from its decentralized, proof-of-work consensus mechanism, which ensures that no single entity can control or manipulate the transaction history. This security extends equally to all data housed on the blockchain, whether it's financial or non-financial.
- The book suggests that Bitcoin could serve as a "strangler pattern" replacement of our legacy internet infrastructure with a modern architecture that isn’t as clearly susceptible to systemic exploitation and abuse (Page 376). The book further intimates that Bitcoin could operate as the preeminent mechanism employed by digital-age societies to map or anchor elements of the old internet version to the revamped version of the internet (Page 322).
While Bitcoin indeed introduces a new, decentralized paradigm for financial transactions and data storage, it isn't designed to supplant the entire internet infrastructure. The internet is an extensive and multifaceted system supporting a wide variety of applications and services, from email and web browsing to video streaming and cloud computing. In contrast, Bitcoin is a specific application that operates on the internet, designed to enable peer-to-peer financial transactions.
The claim made by the book appears to conflate the concept of a decentralized financial system (which Bitcoin offers) with the idea of a decentralized internet (which is a much broader and more intricate concept). While there are projects and technologies aiming to foster a more decentralized internet (such as InterPlanetary File System (IPFS) and various blockchain-based "Web 3.0" initiatives), Bitcoin is not one of them.
Additionally, the book's suggestion that Bitcoin could serve as the dominant mechanism for tying the legacy internet to a new version of the internet is speculative and isn't substantiated by current technological realities. While it's true that blockchain technology (the underlying technology of Bitcoin) has potential applications in areas like decentralized identity systems and domain name systems, these are still largely experimental and have not been widely adopted yet.
- The book propososes that Bitcoin could significantly transform the way humans vie for control over valued resources, effectively resetting the global balance of power in a manner akin to the profound changes brought about by full-scale kinetic world wars (Page 376). The author further proposes that Bitcoin could revolutionize the perception of physical confrontation in the digital-age society (Page 370). Moreover, it's implied that global adoption of an electro-cyber form of physical power competition, facilitated by proof-of-work technologies like Bitcoin, could lead to the genesis of a completely novel form of polity (Page 385).
It is undeniable that Bitcoin holds the potential to disrupt conventional financial systems and power structures. However, juxtaposing its impact to the scale and consequences of world wars is hyperbolic and speculative. World wars resulted in massive loss of human lives, extensive destruction, and substantial shifts in geopolitical boundaries and power structures. In contrast, Bitcoin is a digital currency that operates on a decentralized network. While it can indeed influence financial systems and potentially disrupt some power structures, particularly those related to finance and banking, it is incapable of causing physical destruction or loss of life.
The book suggests that Bitcoin could spawn a completely new form of polity is speculative and isn't supported by current realities. Although Bitcoin and other cryptocurrencies can indeed influence how people transact and store value, they don't intrinsically alter the fundamental nature of societal organization or governance. They may contribute to shifts in power dynamics, particularly in the financial sector, but they do not supplant the need for traditional forms of governance and societal organization.
The book also seems to conflate the concept of power competition in a geopolitical context with the concept of power competition in the context of Bitcoin mining. Bitcoin mining does involve a form of competition, as miners compete to solve complex mathematical problems to add new blocks to the blockchain and receive Bitcoin rewards. However, this is far from the concept of power competition in a geopolitical context, which involves nations competing for resources, influence, and dominance on the global stage.
- The book asserts that Bitcoin, through its proof-of-work technology, could help society secure itself against systemic exploitation of computer networks (Page 378). The author argues that Bitcoin could empower individuals to physically secure their digital information, by projecting physical power in, from, and through cyberspace to impose severe physical costs on those who exploit our computing systems (Page 347). The author further speculates that national adoption of Bitcoin could be conceptualized as the employment of an electro-cyber militia to safeguard and defend a nation’s valuable digital information (Page 360).
While it's true that Bitcoin and other cryptocurrencies can provide a level of security and privacy not available in traditional financial systems, it's crucial to underscore that they also introduce new vulnerabilities and potential for misuse. Bitcoin transactions are irreversible, which can make them appealing for fraudulent activities. Bitcoin wallets can be lost or stolen if not adequately secured. The security of the Bitcoin network itself hinges on its decentralized nature and the computational power required to alter the blockchain, but individual users are still susceptible to scams and hacking.
The book's suggestion that Bitcoin could serve as a form of "electro-cyber militia" is speculative and not universally accepted within the Bitcoin community. Although Bitcoin does offer a method for individuals to secure their financial transactions against interference from third parties, it is not designed to shield against all forms of cyber exploitation or to serve as a form of national defense.
In conclusion, Softwar presents an unconventional viewpoint on Bitcoin's potential influence on national strategic security, proffering that Bitcoin could serve as an effective tool for power projection, system defense, and even societal reorganization. However, these propositions, while intriguing, often veer towards the speculative and seem to be somewhat misaligned with the predominant understanding of Bitcoin's primary purpose and functionality within the field of computer science.
While this book undoubtedly offers a unique and thought-provoking perspective on Bitcoin's wider implications, it is crucial to approach these theories with a discerning and critical eye. It is always beneficial to juxtapose such theories with the broader consensus within the Bitcoin development and computer science communities, to gain a more rounded understanding of this remarkable technology. Ultimately, Bitcoin continues to evolve and its full potential, while yet to be fully realized, remains a subject of intense debate and exploration within the computer science community.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 4e00c412:04107886
2023-08-16 09:43:00
@ 4e00c412:04107886
2023-08-16 09:43:00Mi scuserà di certo Albert Einstein per aver completamente prima decontestualizzato e poi ricontestualizzato nel mondo Bitcoin una delle sue frasi più celebri. Quella a cui mi riferisco in questo post è proprio la difficulty di Bitcoin, visto che parliamo di mining, del suo funzionamento e appunto delle opportunità a esso legate.
Bitcoin Mining: Overview
Con il termine mining si intende il processo di verificare e aggiungere nuove transazioni, sotto forma di blocchi alla timechain di Bitcoin.
Coinvolge una rete decentralzzata di “computer” che competono per risolvere un problema matematico complesso tramite un meccanismo di consenso noto come Proof-of-Work (PoW). I miners usano il loro “potere computazionale” per trovare una soluzione, e chi tra loro la trova la aggiunge insieme alle transazioni verificate alla timechain. Il “vincitore” viene ricompensato con “nuovi bitcoin” e con le fees legate alle transazioni.
Questo processo assicura l’immutabilità della rete e previene il double spending.
Bitcoin Mining: Il processo
Il processo inizia con i miner che raccolgono le transazioni pendenti e le organizzano in blocchi. Queste transazioni rimangono in mempool finché non sono validate. Ogni blocco contiene un insieme di transazioni e un riferimento, hash, oltre alla sequenza temporale, al blocco precedente. Per aggiungere un nuovo blocco alla timechain i miner devono risolvere un problema computazionale.
I miner devono cioé trovare un valore specifico, nonce, che produce un hash con proprietà specifiche quando combinato con i dati del blocco. Trovare questo valore richiede una significativa spesa computazionale e una volta che un miner lo ha trovato lo diffonde alla rete così da poter permettere agli altri miner di verificarlo. A differenza della risoluzione del problema l’operazione di verifica è immediata e computazionalmente lineare.
La rete dei miner è sottoposta dal Protocollo a un meccanismo di consenso per maggioranza che in caso di “biforcazioni” alla timechain, quando due miner trovano la soluzione quasi in contemporanea e la diffondono, premia la catena più pesante cioé quella con più Proof-of-Work (e non la più lunga).
La partecipazione dei miner al processo è incentivata, attraverso la teoria matematica dei giochi, dalle block rewards e dalle fees legate alle transazioni. La prima transazione di ogni blocco, detta coinbase transaction, estrae nuovi bitcoin e li invia al miner che ha aggiunto il nuovo blocco.
Bitcoin Mining: Hardware
Nel primo periodo di vita di Bitcoin era possibile effettuare il mining usando le normali CPU dei computer: bastava scaricare il client Bitcoin e usare il potere di calcolo della CPU per risolvere il “puzzle computazionale”. D’altronde la difficoltà risultava piuttosta bassa e la rete non ancora molto estesa.
Fortunatamente, o sfortunamente a seconda dei punti di vista, al crescere della rete e di conseguenza della difficulty, il mining si è tramutato in un vero e proprio business che ha portato allo sviluppo di hardware dedicato al compito sempre più efficiente sia dal punto di vista energetico che da quello computazionale.
A partire infatti dal 2013 le CPU e le GPU, schede grafiche per intenderci, furono via via sostituite dagli ASICs (Application Specific Integrated Circuits) cioé delle macchine disegnate specificatamente per il Bitcoin Mining efficienti dal punto di vista energetico e con un alto hash rate (il numero di hash prodotti, soluzioni al problema, in genere misurati al secondo). Oggi siamo nell’ordine di più di un centinaio di Terahash, Th, al secondo.
Alternativa agli ASICs potrebbero essere le FPGAs (Field Programmable Gate Arrays) molto più efficienti di CPUs e GPUs ma sicuramente molto più complesse nell’impianto e nella customizzazione del codice.
Bitcoin Mining: Software
Così come per l’hardware, i miner spesso usano del software specifico per il mining che consente loro di connettersi alla rete Bitcoin. Questo software si occupa di tutto: si connette alla rete, riceve transazioni e blocchi, e naturlmente fa tutti i calcoli necessari alla prova di lavoro in base alla difficoltà richiesta.
L’alternativa per molti miner è entrare a fare delle mining pool, che sono appunto gruppi di miner che condividono il proprio potere di calcolo, hash, nella speranza di “trovare un blocco”. I rewards ottenuti sarebbero minori perché appunto eventuali fees e block rewards sarebbero divisi tra tutti i partecipanti della pool in rapporto alla quantità di lavoro fornita (in genere il termine “tecnico” usato è shares).
Bitcoin Mining: cos’altro?
Oltre a hardware e software, il mining richiede una connessione a internet stabile, dello spazio, le conoscenze necessarie per mantenere operativo il setup e molta corrente elettrica.
Senza una connessione internet stabile non si va da nessuna parte e l’uso di una consistente quantità di energia elettrica richiede un buon sistema di raffreddamento. Considerata la difficulty raggiunta di spazio per contenere gli ASICs ne servirà parecchio. Un’adeguata manutenzione risulta necessaria per mantenere “l’investimento” efficiente e profittevole.
Ultimo ma non ultimo un wallet Bitcoin a supporto. La scelta cadrà su un hardware wallet (cold) o un software (hot) wallet.
Ricordiamo che un wallet è detto cold se disconnesso e offline mentre è detto hot se connesso a intenet. I cold wallet sono in genere più complessi da usare ma più sicuri, discorso opposto per gli hot.Bitcoin Mining: si guadagna davvero?
Domanda lecita quando si vuole intraprendere un nuovo business e rapportare l’investimento con il suo ritorno.
La risposta ovvia è: dipende. Da diversi fattori tra l’altro tra cui il valore attribuito ai bitcoin dal mercato, l’hash rate, il consumo di energia e il suo costo, i famigerati costi di gestione, dai rewards per blocco e dalle fees sulle transazioni (i miner ringraziano gli ordinals).Tra tutti l’aspetto che qui più ci interessa è quello legato alle block rewards e all’emissione monteria pre-stabilita dal Protocollo.
Il miner, o la pool, che mina un blocco è ricompensato dalla block subsidy corrente, nuovi bitcoin emessi, e dalle fees legate alle transazioni contenute nel blocco. Queste due componenti insieme costituiscono la block reward.
Attualmente la block subsidy è fissata da Protocollo a 6.25 bitcoin per blocco e si riduce ogni 4 anni tramite il meccanismo by design di halving.
In pratica ogni 4 anni il Protocollo stabilisce il dimezzamento della subsidy dovuta ai miner per ogni nuovo blocco riducendo dunque l’emissione monetaria comunque fissata dal CAP di 21M di bitcoin.
Il prossimo halving avverrà nel 2024 -ogni 210k blocchi- e porterà la subsidy a 3.125 bitcoin per blocco.Visto che la subsidy scende nel tempo i miner dovranno da una parte puntare alle fees sulle transazioni per mantenere il proprio business profittevole dall’altra alla scelta di fonti energetiche economiche e di hardware sempre più efficiente.
Nel mezzo delle difficoltà nascono le opportunità
Una delle innovazioni più importanti introdotte da Bitcoin è sicuramente l’aggiustamento automatico della difficoltà -nel ricercare il nonce- che serve al Protocollo per mantenere costante il tempo di generazione del blocco e assicurare la sicurezza e stabilità della rete. Avviene ogni 2016 blocchi, più o meno due settimane, e si basa sul potere computazionale della rete meglio noto come hash rate. Così facendo il tempo di blocco resta costante nell’intorno dei 10 minuti.
Per intenderci, la difficoltà aumenterà quando i blocchi sono minati più velocemente rispetto al target dei 10 minuti (hash rate più alto): così facendo sarà più difficile trovare la soluzione e i blocchi saranno aggiunti più lentamente. Viceversa, se i blocchi sono minati molto lentamente, la difficoltà diminuirà (hash rate più basso) così che la soluzioni, e i blocchi, potranno essere trovate più velocemente.
Potremmo dire che l’aggiustamento automatico della difficoltà democratizza la rete Bitcoin evitando che pochi miner possano prenderne il controllo oltre a renderla più sicura contro eventuali attacchi.
Bitcoin Mining: 2140
Neanche a dirlo i miner sono stati e continuano a essere parte integrante del processo di crescita del Protocollo. Attraverso il mining le persone partecipano direttamente all’ecosistema, paretcipazione attiva, e assicurano comunque futuri sviluppi del Protocollo.
Ovviamente ci sono tutta una serie di fattori che “gravano” sul futuro del mining primo di tutti l’halving ricorrente ogni 4 anni….
…Fino al 2140 quando gli ultimi sats saranno emessi e poi? Resteranno davvero solo le fees legate alle transazioni? Quasi certamente si.
Saranno sufficienti?
Ok la bassa preferenza temporale, ma tempo al tempo. Ne riparliamo nella seconda parte di questo post fra un centinaio di anni.
-
 @ 908d47b6:a2bf38ad
2023-08-16 08:33:05
@ 908d47b6:a2bf38ad
2023-08-16 08:33:05Earn cryptocurrencies they easy way
This will surprise you now: You can earn cryptocurrencies and do not have to make any financial investment. The possibilities range from mining over learning to gaming. Here we regularly show you new earning opportunities.
The great thing about it, as already mentioned, is that you don't have to make any financial investments. In addition, you can use most of the earning opportunities that we present to you here on your smartphone. If these aren't already unbeatable reasons to finally start earning cryptocurrencies... then what?
In the course of our journey to earning crpyto we will also take away your fear of wallets and explain to you in a simple way how to set up a wallet and what you should consider when doing so. We also provide you with other sources where you can get more information.
Why following us?
Bitcoin Earner was created to take away your fear of cryptocurrencies by giving you a free start into the world of bitcoin and cryptocurrencies. Many people who have their first contact with blockchain and cryptocurrencies through investment and the loss of their money are permanently deterred. However, the underlying technology will be used in more and more areas - so why not prepare for it now?
If you earn bitcoin and cryptocurrencies with us, then you get in very slowly and get to know the matter and the technical world in the background much better. In addition, you do not need to be afraid of losing your savings or family allowance through a wrong investment.
Let's not fool ourselves: You cannot make a living with the earning opportunities we have mentioned. You will also not generate passive income that allows you to travel the world. However, you will learn to have a higher time preference. You will carry out first transactions on different blockchains. Maybe you will also buy or sell your first NFT? But you will learn to stack sats and be humble. Dont gamble your hard earned coins to multiply them. In any case, we look forward to your comment and how you came across us.
-
 @ f60140bb:3a5cd904
2023-08-16 08:02:23
@ f60140bb:3a5cd904
2023-08-16 08:02:23Flycat is a client-side software without introducing backends or database setup. the idea is to keep it effortless for users to self host. It mainly use React Nextjs framework in typescript lang.
Branch
masterbranch is the one for production development. Every commit merged in master branch will push new release alive.developbranch is only used for feature involved with tons of works and needs to be tested before release to production.
How to run
Nodejs >= v18.12.1yarn >= 1.22.19```sh git clone https://github.com/digi-monkey/flycat-web.git cd flycat-web yarn
development
yarn dev
build for release
yarn build ```
For self-host, check out How to deploy to vercel
Code structure
- TODO
Release
Once a week, we release a regular update version. For hotfix, a instant minor version will be roll out once fixed.
We use project kanban to manage the development and release. every week, we gather the things we want to do in this kanban and release a new version at the end of that week.
Contributing
A good way to start contributing is to check the github issues labeling with
good first issue.Design Call
Every week, right before a regular release iteration start, we host a regular design call meeting, the meeting is fully open. anyone can join and discuss if they want.
The meeting is mainly focus on:
- things planning to ship in that week
- new contributors self-introduce, asking question about the project or development
- users feedback
The meeting is tentatively scheduled for 1:00 PM UTC+8 hosted on meet.jit.si. Check out flycat official account for meeting link.
-
 @ d030bd23:96435da9
2023-08-16 05:17:46
@ d030bd23:96435da9
2023-08-16 05:17:46Pengenalan
 Imej1: Logo Bitcoin Core bewarna jingga, logo Bitcoin Cash bewarna Hijau
Imej1: Logo Bitcoin Core bewarna jingga, logo Bitcoin Cash bewarna HijauBitcoin Cash bukan Bitcoin! ni asas yang wajar difahami oleh pengguna baharu dalam dunia aset kripto.
Bitcoin Cash (BCH) adalah aset kripto baharu yang diwujudkan pada tahun 2017 kesan perbezaan pendapat miner-miner Bitcoin. Walaupun memiliki struktur asas yang hampir serupa dan sejarah transaksi awal yang sama, Bitcoin Cash mempunyai perbezaan ketara dari segi harga, kepenggunaan dan potensi. Kedua-dua Bitcoin (BTC) (selepas ini akan dipanggil Bitcoin Core) dan Bitcoin Cash (BCH) adalah aset kripto yang boleh dibeli dan dimiliki secara sah dari exchanger Malaysia seperti Luno dan Sinergi.
Sejarah
Masalah kos transaksi Bitcoin Core yang semakin mahal dan lambat sudah menjadi isu sejak tahun 2017. Menyedari hal ini , Roger Ver mencadangkan agar saiz blok Bitcoin Core diperbesar kepada 32MB. Cadangan ini ditolak oleh sebahagian miner lain, lalu akhirnya miner yang bersetuju dengan Roger Ver memilih untuk meneruskan dengan haluan sendiri. proses ini dipanggil forking. Adakah idea Roger Ver berjaya? secara telnikalnya, ya. lihat rajah di bawah. Solusi ini menyebabkan jaringan BCH tidak sesak lagi:
 Imej2: Situasi semasa jaringan Bitcoin Core dalam bentuk visual
Imej2: Situasi semasa jaringan Bitcoin Core dalam bentuk visual Imej3: Situasi semasa jaringan Bitcoin Cash dalam bentuk visual
Imej3: Situasi semasa jaringan Bitcoin Cash dalam bentuk visualNamun begitu, BCH gagal mengambil tempat BTC sebagai Bitcoin yang sebenar yang diilhamkan oleh Satoshi Nakamoto. lihat perbezaan harga BCH dan BTC pada masa kini:
 Imej4: Perbezaan ketara harga BTC dan BCH
Imej4: Perbezaan ketara harga BTC dan BCHSifat BCH
BCH mempunyai caj transaksi yang sangat rendah. Ini bermakna BCH tidak perlu bergantung kepada Layer 2 seperti BTC untuk transaksi mikro.
 imej5: caj pengeluaran BCH dari Luno
imej5: caj pengeluaran BCH dari LunoTransaksi dapat disemak hampir serta merta di BCH memandangkan Blockchain tidak sesak walaupun sedang mengurus transaksi hampir dua kali ganda jumlahnya berbanding BTC. BCH juga tidak mempunyai isu replace-by-fee, dan ini membolehkan satu-satu transaksi lebih diyakini kesahihannya apabila butang "send" telah ditekan. Potensi ini menyebabkan BCH semakin mendapat tempat dalam kalangan pelabur.
 imej6: Blockchain BCH baru digunakan 2% apabila menguruskan 2562 transaksi dalam tempoh 10 minit
imej6: Blockchain BCH baru digunakan 2% apabila menguruskan 2562 transaksi dalam tempoh 10 minit imej7: Blockchain BTC sudah mencapai kapasiti 98% walaupun baru menguruskan 1196 transaksi dalam tempoh 10 minit
imej7: Blockchain BTC sudah mencapai kapasiti 98% walaupun baru menguruskan 1196 transaksi dalam tempoh 10 minitpun begitu, sama seperti BTC, BCH tertakluk kepada blocktime 10 minit (ini bermakna BCH yang baru masuk ke akaun pengguna tidak dapat digunakan / dibekukan dalam tempoh 10 minit sehingga 120 minit, begantung kepada polisi wallet masing-masing).
Address BCH bermula dengan awalan "q" atau "p" manakala Address BTC bermula dengan awalan "1" atau "3".
 imej8: contoh awalan address BCH dengan huruf "q"
imej8: contoh awalan address BCH dengan huruf "q" imej9: contoh awalan address BCH dengan huruf " p"
imej9: contoh awalan address BCH dengan huruf " p"Wallet Bitcoin Cash
Saya menyarankan wallet Bitcoin.com memandangkan wallet ni bersifat self-custody (pemilikan penuh kendiri berbanding disimpan di exchanger) namun, ia menyokong login menggunakan email (tanpa mengabaikan penggunaan 12 word phrase). Ini menjadikannya ia sangat ideal untuk digunakan bagi tujuan pewarisan. Wallet ini juga menyokong simpanan aset Ethereum dan Bitcoin Core
 Imej10: Wallet ini menyokong BCH, BTC dan ETH
Imej10: Wallet ini menyokong BCH, BTC dan ETHPotensi BCH
Komuniti BCH lazimnya bersifat inovatif. Oleh kerana itu, BCH mempunyai pelbagai inovasi yang tiada / belum diwujudkan pada BTC seperti cashscript dan simple ledger protocol (SLP). BTC pula dilihat lebih konservatif dan lebih mementingkan kestabilan berbanding pembangunan. Potensi nilai BCH dan BTC agak sukar diterjemah, namun perbezaan ideologi ini menjadi penentu sama ada institusi dan individu akan lebih memilih BCH yang agresif atau BTC yang dipercayai.
 Imej11: Pembangunan dalam ekosistem BCH
Imej11: Pembangunan dalam ekosistem BCH -
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ a10260a2:caa23e3e
2023-08-16 04:59:43
@ a10260a2:caa23e3e
2023-08-16 04:59:43I just discovered YakiHonne today, and thankfully so, since the deadline to test the round 4 updates, provide feedback, and stack sats is near.
There's not much I enjoy doing more than stacking sats.

And growing Nostr too of course. That's why I'm here.
Alright, let's get right into it and go over the 5 updates in this round.
1. Drafts - You can save your articles for later edit/publish.
Love this and I look forward to the day we can make drafts of short notes on the mobile clients (e.g. Damus and Primal). But this behaves as expected, when clicking "Save as draft", I'm asked what relays I'd like to save my draft too.

After saving the draft and viewing "My articles", it makes sense that the draft wouldn't appear when clicking on a relay where the draft wasn't initially saved.
2. Stats previews - You can see who zapped/upvote/downvote your or other creator's articles.
This worked as expected as the shaka I received on my first ever blog post on Nostr showed up as an upvote. Shoutout to SoberGrizzlyBTC for the love!

3. Add "my articles" to the curation creation tab - You can directly select your articles for your curation from your articles.
I mentioned this one in #1 and I think it means there's a place I can go to where I can see only articles that I've created.

4. Add confirmation deletion prompt for comments - Now you have the ability to cancel faulty comments.
I'll have to revisit this one since I don't have any comments at the moment.
5. Hints - Add stats icons hovering hints to clear things up.
Looks good. You can see that it says "Tip article" when hovering over the lightning icon. This is something you should definitely do btw ;)

We've now covered all the updates from this round and all I can say is wow. I'm super impressed with the user interface and just being able to do something as simple as saving a draft.
I mentioned in my first post Running blogstack that there would be nothing stopping me from creating with another client and here we are. All I had to do was connect my private key which we're now able to do more safely with extensions like nos2x.
I'm looking forward to using YakiHonne more in the coming days and testing future updates.
Onward.
-
 @ 1bc70a01:24f6a411
2023-07-23 12:11:45
@ 1bc70a01:24f6a411
2023-07-23 12:11:45This is an old but timeless post I wrote on October 26, 2022.
90% of startups fail. That's the statistic.
It feels true to me. Judging by startup Twitter it seems most startups disappear before the 2 year mark. Some, much sooner.
Most people imagine the startup journey to be like this:

People think you can go from idea to a shipped product fast. After launch it's all happy times and success. We fool ourselves into believing this because we must. Otherwise, it's hard to start.
In reality, it's something like this:

50% quit at the idea stage. I'm making rough calls, not an exact science.
Ideas are easy, but acting is hard. Most people will just stop at the idea. Some may look into it, register a domain (you know who you are 👀) and stop there.
Those who undertake the journey will build for 3-5 days and see some other "better" idea. This is called the shiny object syndrome. Sixty percent of people will quit at the shiny object and start working on something else. Of course, they'll register a domain first!
Ignored the shiny object? Good for you! This is where it starts getting tough.
80% will quit before the "project" is finished. The last 20% of the project feels so close, yet so far away that you wonder if you've made the wrong decision all along. Doubt creeps in. You start thinking - "why bother?" and "this is not going to work out, it was a dumb idea".
The heroic few will get through the grind stage and finish their project. This is where they will call themselves a startup - but they are still a project.
In a great anticipating to the "launch", many founders will fall from the pedestal soon after. Launches are a non-event for most projects. Lucky few gain customers and traction, but the vast majority will disappear in the coming weeks.
That leaves us with the 20% crusaders. The tough bastards who will not give up immediately after the launch. They'll keep pushing. And pushing... and pushing. Until they meet a wall of despair.
The wall of despair makes everything seem hopeless. You've tried. You keep trying. But, nothing happens.
This idea has no legs. This was all a giant mistake! Shut it all down. Go back to your regular job. This was never meant to be.
Sadly, this is just the point where things start getting interesting. But, our hero (or actually 90% of them) give up for good.
For most, this will be around the year 1 mark. For some year 2 or even 3 if they pivoted a few times. It's really hard to keep going at this point.
The glorious few - the supposed 10% (I actually think it's about 2%) start seeing traction. All the pain and the agony of getting to this point is finally worth it.
From here, things can take as long as 1 year, all the way up to 5 years+ to see meaningful growth that pays all the bills and then some.
Startups are a helluva ride. Only the toughest survive. But, it doesn't end there.
Even 50% of successful startups will seize to exist just before year 5. The remain half may make it to year 9, but even the vast majority of those will disappear before the decade's end. Only about 30% of the 10% successful startups make it past one decade.
But none of this matters! If you are a new founder reading this, you know you're the exception. You will succeed! You were chosen.
I joke, but, don't give up. I believe in you. What's the downside in doing so?
-
 @ f4db5270:3c74e0d0
2023-07-22 16:32:18
@ f4db5270:3c74e0d0
2023-07-22 16:32:18
"Ponti sotto la pioggia" (2023)
40x60cm, oil on panel canvas
(Available)
Here a moment work in progress...

The beginning...

The original photo

-
 @ 92294577:49af776d
2023-08-16 04:10:10
@ 92294577:49af776d
2023-08-16 04:10:10Blockstream Finance, our financial division, continues to pioneer forward-thinking financial products, laying the foundation for Bitcoin-based capital markets. Building on the success of the Blockstream Mining Note (BMN), which secured $50M over 2021 and 2022, we have partnered with Luxembourg's STOKR—a premier marketplace for digital securities—to unveil our next Bitcoin-focused investment vehicle: the Blockstream ASIC (BASIC) Note.
The BASIC Note is a bitcoin-denominated vehicle that provides qualified investors an opportunity to capitalize on the potential upside of historically-low ASIC (application specific integrated circuits; purpose-built machines used to mine bitcoin) prices.
The Thesis
In previous Bitcoin cycles, bitcoin and ASIC market prices have been closely correlated. During bear markets, ASIC prices (on a price per terahash basis) often fall below bitcoin's value, while in bull markets, they tend to surpass it, indicating a potential upside when denominated in BTC.
https://cdn.nostr.build/i/cdbd6fdbcafab703344d067edb39ade5fbb4965e3817a2fd0792ecbe1ffbea4b.png Note ASICs pricing 25-38 J/TH is less energy efficient vs ASICs under 25 J/TH.
As ASIC prices show promising signs of recovery, anchored by the impending Bitcoin halving in 2024 and favorable market supply-demand dynamics, the BASIC Note strategy will leverage Blockstream's unique positioning and track record in the Bitcoin mining sector. We aim to raise investor capital, acquire and store unused ASICs in North America, and then strategically offload them into the market upon price resurgence.
While bitcoin price has risen substantially in 2023, ASIC prices have remained depressed (on a price per terahash basis). This is attributed to an oversupply of less energy-efficient miners, a need for more hosting capacity in the market, and higher energy costs, among other factors.
We expect this ASIC price trend to reverse in the near-to-mid term. As energy and credit markets bounce back, and as both large public and private miners bring new capacity online and refresh their fleets in preparation for the 2024 halving, we anticipate this surplus of miners to decline.
The Structure
The BASIC Note is a bitcoin basis investment opportunity. We anticipate that most investors will invest using bitcoin, seeking a bitcoin-on-bitcoin return.
The note has a novel structure designed with the Bitcoin investor in mind. Unlike many crypto hedge funds that charge carried interest on the mere passive appreciation of bitcoin price, the BASIC Note's carry fee is discretionary and levied only when the fund outperforms bitcoin. In other words, the carry is only for the value added beyond the natural bitcoin price appreciation. By eliminating these unnecessary fees, we can encourage investors to HODL their bitcoin, benefiting from its passive growth.
We view the BASIC Note as a source of liquidity for miners operating in the market today. These miners can either sell their inventory outright, or they can sell their inventory and reinvest in the BASIC Note. By choosing the latter, they can transform their hard assets into a more dynamic investment with a tradeable note, allotting them more agility in adjusting their market position.
The Expertise
Blockstream has continuously been a leader in Bitcoin mining, from our historical connection to the proof-of-work algorithm to running one of North America's largest vertically-integrated mining operations.
This wealth of experience has given us unique insight into the market and fostered strong relationships throughout the Bitcoin mining value chain, including key ASIC producers and brokers.
Beyond mining, we are also pioneers in Bitcoin technology. We are the technical providers for the Liquid Network and the main contributors to Core Lightning, two of the most well-known Bitcoin layer-2 solutions. We also have a deep understanding of Bitcoin through our software and hardware wallet offerings and operate the Blockstream Satellite network, which provides continuous, free broadcasts of the Bitcoin blockchain worldwide.
The BASIC Note builds on this mining legacy and integrates many areas of Blockstream's expertise across the Bitcoin technology space.
https://cdn.nostr.build/i/aa05cd0d3a89204d463125afd028cd08c3809f366ee519271780c28823ead407.png The Blockstream value chain in mining and adjacent Bitcoin technology sectors.
The Offering
The first series of the BASIC Note (BSIC1) is confirmed to go on sale August 23, 2023 on STOKR with an adjustable 24-month tenor. The offering is open to qualified investors with a minimum investment of USD $115,000 or the equivalent in bitcoin (BTC), Liquid Bitcoin (L-BTC), or Tether (USDt). Although there is a minimum initial investment, notes can be transferred in OTC sales or traded on secondary markets, such as SideSwap, down to a denomination of 0.01 (USD $1,150).
Subsequent series are expected to be issued periodically over the coming months, subject to market pricing.
For further information, visit the official STOKR listing or reach out to us on the Blockstream Finance Telegram.
The information above has been prepared solely for informational purposes only. It is not an offer to buy or sell or a solicitation of an offer to buy or sell any securities. Full terms and conditions are available on STOKR.
We will never reach out directly to investors through social media or instant messaging. If you receive any messages from someone claiming to be from Blockstream and offering mining investments, report them to us through the Blockstream Scam DB.
-
 @ f4db5270:3c74e0d0
2023-07-22 16:28:30
@ f4db5270:3c74e0d0
2023-07-22 16:28:30
"Sunset at Playa Hermosa, Uvita" (2023)
40x30cm, oil on panel canvas**
(Available)
Here a moment work in progress...

The beginning...

The original photo

-
 @ a012dc82:6458a70d
2023-08-16 01:44:59
@ a012dc82:6458a70d
2023-08-16 01:44:59Table Of Content
-
The Awakening of the Bitcoin Whales
-
The Big Moves
-
The Implications of the Whale Movements
-
The Mystery of the Whales
-
Conclusion
-
FAQ
In the vast, uncharted waters of the cryptocurrency market, Bitcoin whales are the most colossal creatures, akin to the blue whales of the physical oceans. These are the investors who hold a significant amount of Bitcoin, often untouched for years, while they watch their astronomical gains grow. They're the silent observers, the patient players who understand the game of waiting. However, the usually calm waters have recently been stirred, with nearly $60 million in Bitcoin transferred in just five days. This article dives deep into this unusual activity, exploring the potential implications and the mystery surrounding these Bitcoin whales. We'll delve into who these whales might be, why they're moving their Bitcoin now, and what this could mean for the future of cryptocurrency.
The Awakening of the Bitcoin Whales
The term 'Bitcoin whales' refers to investors who hoard substantial amounts of Bitcoin, typically at least 1,000 BTC, and let it sit for years. These investors have proven to be more successful than short-term traders, given Bitcoin's extreme volatility in the short term. Over the past decade, Bitcoin has surged from under $95 per coin to $29,203—a whopping 30,700% increase. This long-term view and the patience to hold onto their assets have often resulted in significant rewards for these whales. However, recently, these long-dormant Bitcoin whales have shown signs of activity. In a span of five days, several wallets holding millions of dollars in Bitcoin moved their holdings after years of dormancy. This sudden movement has caused ripples throughout the cryptocurrency community, leading to speculation about the motives behind these transactions and what it could mean for the future of Bitcoin.
The Big Moves
The recent whale activity began on July 20, when two wallets from 2011, each holding 10 BTC (valued at $292,767 at the time), moved their holdings to new locations. This movement, after such a long period of inactivity, was notable in itself. However, the following day, a wallet holding 5 BTC ($146,383) also budged after 12 years of inactivity. This continued activity suggested a trend rather than an isolated incident. Then, the most significant movement occurred when around $30.3 million in Bitcoin—or 1,037 BTC—moved after its owner transferred it to a new wallet for the first time since 2012. This was a significant shift, representing a substantial amount of Bitcoin. Finally, on July 24, a wallet from 2010 moved a hefty 50 BTC, or about $1.4 million. This series of movements over such a short period was unusual and caught the attention of many in the cryptocurrency community.
The Implications of the Whale Movements
Blockchain data firm Glassnode reported a "dramatic uptick over recent months" in whale activity. Many whales have been moving holdings to exchanges, usually the best way to cash out or shift holdings to other digital assets. This trend could indicate that these whales are preparing to sell or diversify their holdings, which could have significant implications for the Bitcoin market. If these whales decide to sell a large portion of their holdings, it could lead to an increase in the supply of Bitcoin on the market, potentially driving down prices. This could create a buyer's market, where there is more Bitcoin available than people are willing to buy. On the other hand, if these whales are moving their Bitcoin to diversify their holdings, it could lead to increased investment in other cryptocurrencies, potentially driving up their prices. This could stimulate the entire cryptocurrency market, leading to increased interest and investment in a variety of cryptocurrencies.
The Mystery of the Whales
While the recent whale movements have sparked intrigue, the identities of these Bitcoin whales remain a mystery. It isn't clear whether these whales are individuals or companies. Dr. Kirill Kretov, a developer of tools for automated trading and blockchain analyst, suggested that these transactions might represent commercial entities buying Bitcoin from individuals. This could indicate a shift in the market, with businesses becoming more involved in cryptocurrency. However, without concrete information, this remains speculation. The anonymity of Bitcoin transactions makes it difficult to determine the identities of these whales, adding to the intrigue and speculation surrounding these movements.
Conclusion
The recent movements of Bitcoin whales have undoubtedly made waves in the cryptocurrency community. While the reasons behind these movements remain speculative, they highlight the significant influence that these whales have on the Bitcoin market. As the crypto world continues to evolve, the actions of these Bitcoin whales will undoubtedly continue to shape the landscape. Whether these movements signal a storm or just a ripple in the water, only time will tell. However, one thing is clear: the actions of these whales are worth watching, as they could provide valuable insights into the future of Bitcoin and the cryptocurrency market as a whole.
FAQ
What is a Bitcoin whale? A Bitcoin whale is an investor who holds a significant amount of Bitcoin, typically at least 1,000 BTC, often untouched for years.
What recent activity has been observed among Bitcoin whales? Recently, Bitcoin whales have transferred nearly $60 million in Bitcoin in just five days, moving their holdings to new locations after years of dormancy.
What could be the implications of these whale movements? The movements could indicate that these whales are preparing to sell or diversify their holdings. This could potentially affect the Bitcoin market, either by increasing the supply of Bitcoin (which could drive down prices) or by stimulating investment in other cryptocurrencies.
Who are these Bitcoin whales? The identities of these Bitcoin whales remain a mystery. They could be individuals or companies, but the anonymity of Bitcoin transactions makes it difficult to determine.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c3880eec:f697840d
2023-08-16 01:21:54
@ c3880eec:f697840d
2023-08-16 01:21:54Title: AI for Climate Change Monitoring and Mitigation
Introduction
Climate change is one of the most pressing global challenges of our time, with far-reaching impacts on ecosystems, economies, and societies. As greenhouse gas emissions continue to rise, the need for effective monitoring and mitigation strategies becomes increasingly urgent. Artificial Intelligence (AI) has emerged as a powerful tool in this battle against climate change, offering innovative solutions for monitoring environmental changes, predicting impacts, and implementing mitigation measures.
- Monitoring Environmental Changes
AI technologies, such as satellite imagery analysis and data-driven models, enable scientists and researchers to monitor environmental changes with unprecedented accuracy. Machine learning algorithms can process vast amounts of data to track deforestation, melting ice caps, and other indicators of climate change. For instance, AI-powered algorithms can identify changes in land cover, detect illegal logging activities, and monitor the health of coral reefs. These insights are crucial for informed decision-making and targeted interventions.
- Climate Prediction and Risk Assessment
AI plays a pivotal role in predicting climate patterns and assessing potential risks associated with extreme weather events. By analyzing historical climate data and incorporating real-time information, AI models can forecast hurricanes, droughts, and other disasters with improved accuracy. These predictions enable governments and organizations to allocate resources for disaster preparedness and response effectively. Additionally, AI-driven risk assessments help identify vulnerable regions, allowing for proactive measures to protect communities and infrastructure.
- Renewable Energy Optimization
Transitioning to renewable energy sources is a key component of climate change mitigation. AI facilitates the integration of renewable energy into existing grids by optimizing energy production, storage, and distribution. Smart grids equipped with AI algorithms can balance supply and demand, predict energy consumption patterns, and enhance the efficiency of energy storage systems. This not only reduces greenhouse gas emissions but also paves the way for a sustainable energy future.
- Carbon Capture and Sequestration
AI technologies contribute to the development of advanced techniques for carbon capture and sequestration (CCS). Machine learning algorithms help in designing materials for more efficient carbon capture, enabling industries to reduce their carbon footprint. Furthermore, AI assists in identifying suitable geological formations for storing captured carbon dioxide safely underground, preventing its release into the atmosphere.
- Sustainable Agriculture and Land Management
AI-driven precision agriculture offers solutions for sustainable land management. By analyzing data from sensors, drones, and satellites, AI helps farmers optimize irrigation, fertilization, and pest control, minimizing resource waste and environmental impact. This technology also aids in soil health monitoring and crop yield prediction, supporting food security in the face of changing climatic conditions.
Conclusion
The battle against climate change requires innovative approaches, and AI has emerged as a formidable ally in monitoring and mitigating its impacts. Through accurate environmental monitoring, climate prediction, renewable energy optimization, carbon capture advancements, and sustainable agriculture practices, AI contributes to a comprehensive strategy for addressing this global challenge. However, it's crucial to recognize that while AI offers significant potential, it must be integrated with ethical considerations, human expertise, and cross-disciplinary collaboration to ensure its effectiveness in creating a more sustainable future.
-
 @ b7274d28:c99628cb
2023-08-15 20:24:35
@ b7274d28:c99628cb
2023-08-15 20:24:35A prerequisite to understanding Bitcoin is having a fundamental understanding of money. Most people haven’t thought much about what money actually is, why we have it, and the properties that might make one form of money better than another. That being the case, it is difficult for most people to see why Bitcoin is a superior form of money to anything we have ever used before, and why it is and will continue to be superior to anything that has been invented since.
Perhaps the best way to begin to understand what money is, and why society is much better off when it has some form of money, is to imagine what your life would be like without money at all. You have basic needs for food, shelter, water, and clothing, and you have essentially two options: 1. You can try to be entirely self-sufficient, providing for your own needs with your own two hands, or 2. You can become proficient enough at one particular skill that you can trade that skill with others who have different skills to get everything else you need.
In the first scenario, the vast majority of your time will be spent simply acquiring and maintaining the things you need to survive, and you will have little time for other pursuits at all. A portion of each day will be dedicated to collecting water and making it drinkable, another portion will be dedicated to hunting and gathering, and another portion dedicated to replacing worn and damaged clothing, or maintaining whatever you built for your shelter. If you have a spouse, you can divide some of this labor between each other, so as to be more efficient. However, this still proves to be a full-time job just to make sure you maintain an absolute minimum standard of living. 100% self-sufficiency is nothing more or less than 100% poverty.
In the second scenario, things can be vastly improved. You can live in a small community with people that each specialize in skills that can benefit one another. You might become an exceptionally good hunter, while another becomes a proficient fisherman, and another a builder of sturdy and leak-proof homes, and so on. When you grow tired of always eating venison, and want some fish to add variety to your diet, you can go to the fisherman and offer to trade him some of your venison in exchange for some fish. And when you want to upgrade your home, you may go to the builder and offer to supply him with venison for a month in exchange for the work. Because each person is specializing in a particular pursuit, they have the time investment necessary to become vastly more efficient at that one skill than they otherwise could have ever been, so they can produce much more of it than they need, and trade the surplus with others in the community.
This is how a barter economy works, and it is a significant upgrade compared with trying to provide for all of your own needs with your own hands. However, it still has some serious limitations, particularly if you try to extend it beyond a very small and localized community. For instance, if you are a hunter and you want to trade your venison in exchange for a builder upgrading your home, but the builder has no need for venison, because his son is also a hunter, then you need to find a different builder who will take your venison as payment, or you need to find out what the builder will take for trade, let’s say apples, and then go find someone who will take your venison in exchange for the apples, so you can trade the apples to the builder to do the work on your home.
This is a non-trivial amount of friction already, but that’s not where it ends. You see, the work you want done on your home is probably worth a great deal more than a bushel or two of apples, and since apples spoil quickly, you will have to make an agreement with the builder that you will get him apples every week for a period of a few months until the amount of apples he has received is deemed of equivalent value with the amount of work he performed. This means you will also need to keep trading your venison for apples just to give them to the builder, regardless of whether you want to eat the apples yourself. If, during that time, the apple grower also wants to have work done on his home, he will find that the builder is unwilling to trade his work for apples, because he is already receiving a steady supply of apples from you. Now the apple grower has two options: 1. Find something else that the builder is willing to take as payment, and hope they can find someone who wants to take their apples in exchange for it, or 2. Stop trading apples for venison with you, so that the builder will be willing to accept apples as payment again, leaving you high and dry with no means of repaying the builder what you owe.
This problem with the barter system is called the non-coincidence of wants, and as difficult as it can be to deal with in a small community, it becomes even more difficult as communities expand in number. Moreover, the need to find trading partners who have what you want and want what you have in exchange cuts into the amount of time you can dedicate to honing your skills and producing the goods you want to sell. To answer this problem, communities began to use some form of money that made trade much more efficient. The exact form that money took varied widely in history, from salt, to seashells, to glass beads, to blocks of dried tea leaves, among many other types of goods. Indeed, the use of paper bills, though ubiquitous today, is a very recent development, and is already being phased out in favor of digital versions of fiat currency. Over 90% of US Dollars do not exist as physical coins or bills at all, but only exist as numbers in digital bank ledgers. Regardless of what form money took in history, though, having something to use as money made trade far less cumbersome than the barter system.
As a hunter in a community that uses money, you can sell your venison to anyone who wants it in exchange for money, and then you can go purchase anything else you want or need using that money. You are no longer restricted to only trading with people who will accept your venison as payment, or else forced to find something else they will accept as payment, and trade your venison for that. Instead, you can trade with any other person in the community, even if they have no interest in your venison at all, because they are all willing to accept money as payment instead. This frees up more of your time for you to dedicate to becoming more proficient at your chosen skill.
How each various society in history eventually agreed on something to use as money can be easily understood when we consider the role that money would be used to fill. Some things make more ideal forms of money than others, and so a society tends to converge on whatever has the most ideal mixture of characteristics. Let’s look at what people would want money to do, and discern what monetary characteristics would be most ideal to accomplish that goal.
The most basic thing people would want to use money for is to purchase goods and services from others, without having to figure out what their trading partner’s individual wants and needs are in advance. Already, this gives us some ideas of characteristics money ideally ought to have.
Since you are likely to want to purchase some goods that are of low value, and other goods that are of high value, whatever you use as money should be able to be divided into small enough units to facilitate the smallest feasible transactions, or combined into large enough sums to facilitate the largest feasible transactions. We call this characteristic “divisibility”. All else being equal, a good that is more divisible will be more ideally suited to being used as money than a less divisible good.
Since you may want to buy something from someone who is some distance away from where you live, such as across town, or in a neighboring village, whatever you use for money should be easy to carry with you in the quantities that you will commonly need for spending. We call this characteristic “portability”, and it is also an important security feature for money to possess, because it allows people to more easily hide it away from would-be thieves. All else being equal, a good that is more portable will be more ideally suited to being used as money.
Since you want to be confident that the person you are buying from will accept your money as payment, you will want to use something that they will immediately be able to recognize as genuine, or else be able to verify quickly via some sort of test. If you use a rare metal, then they can verify it by weight. If you use a paper bill, they can verify it using hard to replicate security features, like watermarks, micro printing, etc. If you want them to honor it as payment, they have to be certain it isn’t fake. There’s a reason we have the term “fool’s gold” to refer to iron pyrite, after all. Only a fool would not be able to tell the difference between it and genuine gold. We call this characteristic “verifiability”, and goods that are more verifiable will tend to be more ideally suited to being used as money.
Another thing that may stand in the way of having your money accepted as payment is if the person you are trying to pay can tell where you got the money from. For instance, if they are a vegetarian, and your money is stamped with a mark that says you received it from working at a butcher shop, they may not want to accept your money as payment due to their moral principles. For this reason, one unit of anything being used as money should be indistinguishable from another unit of the same value, so that whoever is receiving it as payment has no reason to reject it based on its history. We call this characteristic “fungibility”, and a good that is more fungible will tend to be more ideally suited to being used as money.
Fungibility is also important for maintaining a standard valuation for each unit of the money. If every unit of a good is unique, then it is hard to know the value you have, and it’s also hard to know how to price what you want to sell. For instance, if you want to use small stones as your money, you can’t just say that you will work for 5 stones an hour, because one stone might be slightly larger than the others, another might be more round, and another might be a more rare and interesting shape or color. So, a money with units that are each identical will work much better than a money with widely varying units that are difficult to measure.
Since you may have a period of time between when you receive money as payment and when you want to spend it to purchase something else, and then the next person may have a period of time before they want to spend the same money, and on and on with each person who accepts it as payment thereafter, whatever you use as money should not be easily damaged or deteriorate over time. We call this characteristic “durability”, and once again, all else being equal, a good that is more durable will be more ideally suited to being used as money.
Part of the reason you want money to be durable is so that it maintains its value over time, as well. You don’t want to use a form of money that will buy you less goods tomorrow than it will today, and significantly less goods in a month, due to the damage or deterioration of the money itself. This is why perishable goods like apples or beans never really caught on as money. Without specific actions to preserve them, they tend to rot away very quickly, and no one will value an apple that is even just beginning to rot anywhere near how they would value a fresh apple, so the lifespan of an apple being used as money would only work for one or two consecutive transactions, and only if those transactions happened in a short period of time, while a more durable good could be used for years and years while retaining its value.
Money must retain value over time, not just so it can be used in multiple consecutive transactions, but because some things you want to purchase may take more time to save up for. Therefore, you will need to be able to set money aside with confidence that once you have saved the amount you need, the price will not have gone up significantly, requiring you to save up even longer. When you originally look at the price of an item, you instinctively consider how much of your labor and time it will take to pay for it based on the posted price. If the price goes up over time, due to the money you are using dropping in value, it means that the cost over time to save up for that item is much higher than at first appears, skewing your perspective on whether it is worth saving up for.
There are other characteristics besides durability that can have an effect on a good’s value over time, which will therefore also come into play for deciding whether it would make a good form of money. This ability to retain value over time is sometimes referred to as “hardness” or “salability across time”, and durability is only a portion of what contributes to a good’s hardness. If a good that is being used as money is not sufficiently hard, then people will be less and less willing to accept it as payment over time, since its value is always decreasing in relation to other goods, or else, they will require larger and larger quantities of it as payment for the same goods.
A major contributing factor to a good’s hardness is how much work is required to manufacture or otherwise acquire the good, outside of receiving it as a form of payment. If a form of money is too easy to acquire in quantity, then people will cease to do other forms of productive work to sell for that money, and instead will simply work to acquire the money directly, whether by mining it, gathering it, growing it, or manufacturing it, which will result in an ever increasing supply of the money, and a decreasing supply of all other goods. This will make the value of the money go down significantly over time, reflected in the price of all other goods going up. So, all other things being equal, the harder it is to acquire a good directly, the more likely that it will retain its value over time, and the more ideally suited it is to being used as money. We call this characteristic “scarcity”, and when various forms of money have failed throughout history, it has generally been due to them losing this characteristic.
Glass beads were once used as money in Africa, because they were difficult to make with the technology available, so they tended to retain their value over time. They could be used for purchasing very inexpensive items for just a few beads, or very expensive items for bags full of beads, so they were very divisible. Small glass beads were relatively durable, so they didn’t rot or break often, unlike larger items made out of glass, and they were also easily portable for most daily spending. They weren’t the most fungible goods, though, since each bead was unique and therefore some beads were valued higher than others, and some people preferred different shapes or colors of beads, while other people preferred completely different beads. However, it was not due to this lack of fungibility that glass beads ceased to be used as currency. It was because Europeans with superior technology, which allowed them to very cheaply manufacture large amounts of glass beads, came along and inflated the supply of the money.
The same is true for many other forms of money that could not maintain their value over time due to large increases to the money supply. At first, everyone thinks they are getting rich, because their sales are going through the roof, and they have more money than they have ever seen before, but after a time, they realize that everything they want to buy with that money has started to cost more, as well. This is called inflation. These days people will refer to any rise in prices as inflation, but traditionally it only refers to a general rise in prices due to increased supply of money in the economy.
Other reasons why prices might rise are usually temporary, and due to a shortage of supply, or an increase in demand, for that specific good. For instance, if a natural disaster hits a region particularly hard, then food and bottled water will become very expensive there, because much of the existing supply was likely damaged, and it may be a while before new supply can be brought in to replace it. At the same time, people who normally are able to drink water from their faucet may not have working plumbing, and they may not have food stored up for emergencies, creating a higher level of demand than usual. However, these spikes in price will not last forever. Prices will drop again when things go back to normal and supply lines are restored.
This is not the case when the supply of money is increased. Unless there is a mechanism to reduce the amount of money in the economy, or else permanently increase the amount of other goods, the price increases will be permanent. Increasing the amount of goods through increased productivity is possible, but it usually doesn’t affect all goods in the economy, because increased productivity for one good rarely translates to a similar increase of productivity for all goods. For instance, finding a way to grow more wheat doesn’t usually coincide with finding a way to build more homes. In fact, they might be inversely correlated, since growing more wheat likely requires more land, resulting in less space to build homes. So, wheat may get less expensive at the same time that homes become more expensive, and behind it all, the general prices of most other goods can still tend to become more expensive over time if the money supply is always growing.
Societies throughout history have tended to converge on a single form of money that has the best combination of these characteristics: divisibility, durability, portability, verifiability, fungibility, and scarcity. Some forms of money might have been less than ideal in one or two characteristics, but they possessed all the others. For instance, on the island of Yap, they used large limestones as money that were difficult to move, so they just kept track of the ownership without moving them, and it worked despite the lack of portability, because they were on a small island in a close-knit community. These limestones would have ceased to be useful as money if the number of people they needed to trade with, or the distance traveled for trade, expanded. Portability becomes a far more important characteristic under those circumstances.
The people of Yap no longer use those limestones as money, but not because they weren’t portable. Just like the glass beads in Africa, Europeans with superior technology came along and added many new limestones into the economy, driving down the value of each stone and obliterating the wealth of the community.
Historically, one form of money has outlasted others as a dominant currency for centuries, because its supply is not easy to inflate. I am speaking of precious metals, especially when minted into coins. Gold, silver, and other metals can be mined, but the process is hard work, which means that most people decide to focus on other productive work instead. Advances in technology have increased our efficiency at finding and extracting these metals, but not to the point that the new supply added to the economy each year is a significant portion of the total existing supply. This means that productivity for other goods generally outpaces the increased productivity in mining precious metals, thus they tend to retain their purchasing power or relative value over time, or even appreciate in value.
Yet, despite their nearly ideal characteristics to be used as money, precious metals still had some downsides. First, they aren’t always the most verifiable form of money. When they were minted into coins, other metals would often be added in small quantities so that it was hard to tell that it wasn’t pure gold or silver. Next, gold tended to be used for larger value transactions, since it wasn’t terribly divisible, while silver and other metals were used for more day-to-day transactions, but it proved difficult to maintain a predictable exchange rate between metals, because they didn’t have the same inflation rate. If only 3% more gold was added into the money supply each year, but 6% more silver was added, then silver would devalue compared to gold, and it would take more silver coins to be of equal value with one gold coin. This hurt the fungibility of the coins, and made it hard to know how to price goods. However, the lacking characteristic that proved to be the downfall of precious metals being used as money directly was their lack of portability.
As advances in technology resulted in people regularly traveling greater and greater distances, it became cumbersome to carry around metal coins. To resolve this problem, banks offered to hold precious metals on deposit, and issued receipts stating a value of gold or silver, transferable to anyone, and redeemable on demand. These receipts were the rudimentary beginnings of what would become the gold standard, where banks issued paper currency denominated in US Dollars or other currencies, with set exchange rates for turning them back in at the bank to redeem them for gold. This allowed people to forgo carrying around heavy coins, and increased the divisibility of the money at the same time. However, it introduced a new layer of trust, because depositors had to trust that the gold was actually on deposit to back up the paper money that represented it. As long as depositors were able to go into the bank and redeem the bank notes for gold whenever they wanted, there wasn’t an issue, and soon people were so used to the idea that they didn’t bother trying to redeem the bank notes unless they had a very specific need to do so.
This left a major loophole for banks to capitalize on. They knew that very little gold needed to be kept on hand compared to the number of bank notes they had issued, because so few people would ever want to exchange their bank notes back into gold. This meant that they could rehypothecate the gold they were holding by loaning out additional dollars over and above the value of the gold they had, trusting that they would not have too many people coming to redeem those dollars for the underlying gold at one time.
One of the largest borrowers of these dollars was the civil government, particularly during times of war. This led to the supply of dollars far exceeding the supply of gold that supposedly was backing it, and resulted in multiple occasions when convertibility of bank notes back into gold was suspended. Famously, FDR issued executive order 6102, prohibiting the private ownership of most gold, and requiring banks to transfer all gold deposited with them to the Federal Reserve Bank. Eventually private ownership of gold was restored, but the ability to convert US Dollars into gold was never restored for private citizens. Some semblance of a gold standard was maintained under the Breton Woods Agreement, with member nations able to exchange their US Dollar reserves for gold, but the exchange rate was set at $35 an oz, rather than the historical exchange rate since 1834 of $20.67 an oz. In 1971, even this semblance of a gold standard was abandoned, though Nixon said it was "temporary" at the time, resulting in the monetary system we have today, which uses cash and digital dollars, without any backing except the demand of other nations—who currently need dollars to purchase oil—and the military might of the US government.
Since 1971, the supply of US dollars that can actually be estimated with any confidence has gone from about $600 billion to about $22 trillion at the time of writing, which is an increase of nearly 3,700%, with about 1/5 of that occurring just in the last two years alone. As a result, the purchasing power of the US Dollar has also dropped about 86% in the same period of time. This means the US Dollar severely lacks the characteristic of hardness, or salability across time. Yet, it remains the dominant currency in the world simply because the vast majority of other fiat currencies are even worse off.
So, why hasn’t our society reverted back to using a harder money like gold and silver coins? The answer is simple: We want to continue to be able to engage in trade at vast distances nearly instantaneously. Since the development of the internet, we have been able to purchase all sorts of things from people and businesses all around the globe. Can you imagine using gold and silver coins as money again in this type of an economy? We would have to be willing to send them in the mail, and wait long periods of time to receive the goods, hoping that no one stole the money in transit. Even though US Dollars are terrible for saving for the future, they are vastly superior to any other commonly accepted form of money for transacting at a distance, particularly in their digital form, facilitated via credit and debit cards and other digital money transfer methods.
It leaves us with a bit of a conundrum. If we want to have a hard money, we must sacrifice our ability to transact at a distance, and if we want to continue to buy things from outside of our local communities, we must sacrifice the ability to save our money for the future. We have generally opted for the latter route, and have looked to other means for saving, usually by turning to speculative risk in stocks and other investments.
Many people have reverted to gold for saving, though they still use the dollar for day to day commerce. Others use mutual funds, bonds, and other investment vehicles. However, when we do so, these things begin to take on what is called a “monetary premium”, which is simply a way of differentiating the level of demand that a good would have for its inherent usefulness, compared to the additional demand added by people choosing to use it as a savings vehicle. For instance, gold has a certain amount of usefulness for creating jewelry and electronic components. If that’s all that people ever did with it, its price would likely be far less than it is now. However, people also choose to store their wealth by purchasing and holding it for years, taking it out of the available supply for other uses. The more people who do so, the more its price will increase. The price increase that can be attributed to people using gold as a savings vehicle is the monetary premium.
Goods can only maintain a monetary premium if their supply is hard to increase. Otherwise, when a good begins to show a monetary premium due to its price rising, it will encourage people to bring more of it to market, until the supply can meet the demand, and the price goes back down to near the cost of production, eliminating the monetary premium, and discouraging people from using it as a savings vehicle. So, again, scarcity becomes an important factor in any good developing and maintaining a monetary premium, even if that good is never used as money for day to day commerce.
It would be far more ideal for people to be able to store value in the money itself, rather than having to resort to other goods that can be highly volatile in their price, resulting in the risk of losing their principle. But how do we get around the problem that highly portable forms of money in our digital age also tend to lack scarcity, and therefore cannot hold their value over time? If we could imagine the ideal form of money for our digital and global economy, what would be its characteristics?
It would be a digital form of money that could be sent from anyone to anyone else instantaneously in any amount, so that it is both highly portable, and highly divisible. Its supply would somehow be limited intrinsically, so that no one person, group of people, or government could increase its supply at a whim; this way it can be truly scarce and therefore maintain its value over time. It would be easy to keep away from thieves, without sacrificing the ability to spend it when desired. It would not maintain a history of transfers that could be linked to the identity of the person transacting, so as to ensure it will be accepted by anyone. And finally, it would be issued in a way that requires real-world time and energy to be spent, so that its existence is provably costly and decentralized.
With only one possible exception, I have just described Bitcoin, a digital currency invented in 2008, and which has been running almost entirely uninterrupted since it went live in January of 2009. Bitcoin is more portable and divisible than the fiat currencies we use today, and yet more provably scarce and verifiable than gold and silver coinage. It excels in every characteristic of money mentioned above except fungibility, and that only on the base layer. However, because it is going from zero adoption to millions of people using it in such a short period of time, its price is highly volatile. As a result, it currently proves to be an excellent store of value for time horizons of 5+ years, but not yet an ideal medium of exchange for day to day commerce.
For more details on how Bitcoin works, so that it has such ideal characteristics for use as money, see the next article in this series: Part 2 - Bitcoin’s Invention and Monetary Characteristics.
-
 @ be42c83a:5780d33a
2023-08-15 19:32:27
@ be42c83a:5780d33a
2023-08-15 19:32:27Accepting Bitcoin
To accept bitcoin all you need is a bitcoin wallet.
You share your customer the receive address orQR code and get paid!
Bitcoin Wallet limitations when invoicing
Using a bitcoin wallet gives access to the user to steal your funds, if you are the business owner this is no problem. But you would not want to give access to your accountant, book-keeper or employee.
Businesses want an invoice of custom line items, taxes, addresses and PDF copies. This is not possible with a bitcoin wallet.
The solution
Zaprite
Zaprite is an accounting tool to invoice your customers. You can get paid in Bitcoin, the Lightning Network, Liquid, Stripe and much more all on one invoice.
I have used Zaprite to invoice and want to share with other business owners.
Brief overview
Pros
- No KYC
- No Fees
- xpub and change addresses
- Integration with Stripe, Strike, IBEX, Lightning network, Liquid, IBEX, E-transfer, ACH, and more!
- Customizable company invoice
- Expenses and tasks
- Contacts
- Payment notifications
- Multiple languages
Cons
- Need to have a bitcoin wallet knowledge to a receive address or xpub.
- Not a full accounting software replacement yet.
Getting Started
Zapright is available to anyone in the world in multiple different languages.
All you need to get started is: 1. email 2. password
Zaprite takes no KYC information unlike competitor Opennode.
Company Set Up
First step is set up your account.
Your company information is what will appear on your invoices for your customer.
The company profile section is where you can customize your branding for Zaprite users and checkout page.
This includes a username that can also be used as lightning address for lightning payments.
Checkout Page
Next step is to configure your checkout page by configuring all connections.
This is an optional step as you can just provide a bitcoin payment address per invoice.
All configured connections will show on your checkout page.
Configuring Bitcoin:
Again this is an optional step but a great privacy practice.
To protect your privacy on-chain its recommend you connect your Extended Public Key (xpub).
An xpub is a master address for your receive addresses within your wallet. It's not available on all wallets, check if your wallet has it first.
It will then ask you to confirm your address.
Invoicing
First step is to add a contact including their business information.
You can then change the invoice title add a PO, number, payment terms and currency.
You can choose already created items under tasks or input a unique line item.
Within each line item you can change the tax, price, and description.
Under payments you can choose what your customer sees at checkout by selecting what you have configured. Or put in a bitcoin receive address.
The invoice is then saved as a draft.
Sending
You can send an invoice via email or share link.
Once an invoice is sent it can no longer be edited. Make sure you have everything correct prior to sending.
Your customer will see your checkout screen when paying an invoice.
You can also download a PDF version of the invoice.
Thats it!
Get Started with Zaprite today!
Visit Bitcoin Starting Point for more of my reviews or if you need help.
My full video tutorial:
-
 @ bcea2b98:7ccef3c9
2023-07-21 17:11:23
@ bcea2b98:7ccef3c9
2023-07-21 17:11:23The Bitcoin Improvement Proposal (BIP) 17 is a proposal to add a new opcode to Bitcoin's scripting system, and it also proposes a new 'standard' transaction type that uses this opcode. Here, I will explain each part of this proposal in simple terms.
BIP17 proposes the opcode
OP_CHECKHASHVERIFYfor the Bitcoin scripting system. An opcode is a type of operation that can be performed by a machine (in this case, the Bitcoin network). The opcode that BIP17 is proposing,OP_CHECKHASHVERIFY, is a function that checks if the hash of the previous script matches the item at the top of the stack.The reason for introducing this opcode is to enable what is known as "pay-to-script-hash" transactions. These types of transactions allow the receiver of bitcoins to specify the transaction type needed to re-spend them, essentially shifting the responsibility of defining the conditions to redeem a transaction from the sender to the receiver.
The benefit of this is that it allows a sender to fund any arbitrary transaction, no matter how complicated, by using a fixed-length 20-byte hash. This makes it easier to handle in various interfaces, such as QR codes or copy-pasting.
The proposed opcode
OP_CHECKHASHVERIFYworks as follows:- It hashes the end of the previous script, starting from the last evaluated
OP_CODESEPARATOR. - It then compares this hash with the item on top of the stack.
- If the hashes match, it proceeds with the script; if they don't match, the script fails immediately.
The new standard transaction type is defined as follows:
[20-byte-hash-value] OP_CHECKHASHVERIFY OP_DROPThis transaction type is redeemed by a standard scriptSig:
...signatures... OP_CODESEPARATOR {script}The proposal also gives an example of how this might look for a one-signature-required transaction and a 2-of-3 multi-signature transaction.
The author of BIP17 believes this proposal would minimize changes needed to the existing infrastructure that sends funds to Bitcoin addresses, which would in turn allow for quicker adoption of multi-signature transactions.
Regarding backward compatibility, this BIP is not compatible with older implementations, and it might lead to a blockchain split if not handled carefully. The proposal includes a method for determining miner support for this BIP and a plan for a graceful upgrade if there is sufficient support.
- It hashes the end of the previous script, starting from the last evaluated
-
 @ d34e832d:383f78d0
2023-08-15 10:50:11
@ d34e832d:383f78d0
2023-08-15 10:50:11The Wise Path: Critiquing Single-Issue Voting and Nurturing Individual Liberty
Introduction:
In the realm of politics, single-issue voting has gained prominence as a strategy to promote specific policies. However, it is crucial to examine the potential pitfalls it poses for individual liberty. By prioritizing one policy above all else, there is a risk of circumscribing freedoms and perpetuating the dominance of statism through coercive cycles of "strategic" participation. This essay delves into the perspectives on voting as a form of "self-defense" rather than consent, the demand for alternatives that uphold autonomy, the construction of parallel decentralized systems, the importance of grassroots education, and the role of developers in empowering ordinary citizens.
I. Voting as Self-Defense: Preserving Liberty Amidst Unjust Frameworks
When viewing voting as an act of self-defense, rather than mere consent, we recognize that participation in unjust frameworks inadvertently legitimizes oppression. By prioritizing a single issue, individuals risk compromising their broader liberties. Therefore, a judicious approach is required, one that carefully considers the consequences of each vote and seeks to uphold autonomy.
II. Constructing Parallel Decentralized Systems: A Prudent Strategy
To insulate communities from the caprice of politics, it is sensible to construct parallel sovereign, decentralized systems. By doing so, we can mitigate the risks associated with single-issue voting and avoid relying on simplistic remedies. Embracing multifaceted resistance empowers individuals to challenge oppressive systems, fostering resilience against fiscal manipulation and other forms of coercion.
III. Grassroots Education: Cultivating Resilience and Empowering Individuals
Grassroots education plays a pivotal role in nurturing resilience against the pitfalls of single-issue voting. By enhancing understanding and awareness, individuals become equipped to navigate and challenge oppressive systems. This grassroots approach fosters a society that is better prepared to protect and advance individual liberties.
IV. Developers: Upholding Technical Sovereignty for Future Generations
Developers deserve heightened acclaim for their contributions in engineering tools that empower ordinary citizens. Their efforts in upholding technical sovereignty ensure that future generations can safely harness enlightened sciences free from centralized dominion. By providing individuals with the means to navigate and control their own technological experiences, developers play a vital role in nurturing individual liberty.
V. Principles Over Promises: Advancing Liberties through Collaborative Acts
While factions may leverage transitory political tides, true permanence arises through the diligent application of principles, not mere promises. Each collaborative act that expands understanding and fortifies infrastructure concretely advances individual liberties. Abstract charters alone cannot guarantee the preservation of these fundamental rights; it is through focused efforts and the cultivation of voluntary frameworks that we render coercive diktats obsolete.
Closing Thoughts
In conclusion, a judicious treatment of single-issue voting is essential to safeguard individual liberty. By recognizing voting as an act of self-defense, demanding alternatives that uphold autonomy, constructing parallel decentralized systems, nurturing grassroots education, and acknowledging the contributions of developers, we can navigate the potential pitfalls of single-issue voting. Through these focused efforts, we cultivate voluntary frameworks that render coercive dictates obsolete, fostering prospering alternatives that truly respect self-determination. It is in this way that we can safeguard and advance individual liberties for generations to come.
-
 @ 1e52c554:21771908
2023-08-15 07:12:54
@ 1e52c554:21771908
2023-08-15 07:12:54Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares born in Don Matias on January 20, 1948-2011. Where I will be publishing each of the 170 sonnets from his unpublished collection 'Sonnets For The Twenty First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
Sonnet 94 by Francisco Luis Arroyave Tabares
```
Home Celebration
The pleasures of my mind I unfolded To destroy ennui and melancholy 2 And opened wide the doors to harmony While a new stage for love I scaffolded. 4
Sky that yesterday all my dreams scolded Inspires me now a full tranquility That goes all the way to eternity Around which my life and aims I molded.
Nature hints a secret celebration And offers me its universal dome Where only God has more adoration. His lucid sun that to my soul has come 12 Is showing bright smiles of exultation For those that also celebrate my home. ***
2-.ennui= boredom. 4-.to scaffold= to furnish or uphold a stand or stage with an elevated plataforn. 12-. lucid= bright, shinning. ```
Analysis "Home Celebration"
Introduction
Sonnet 94 by Francisco Luis Arroyave Tabares, titled "Home Celebration," is a beautiful exploration of the speaker's inner world and his relationship with the external environment. The sonnet follows the traditional structure of a sonnet with 14 lines and a specific rhyme scheme.
Thematic Analysis
The first quatrain (lines 1-4) introduces the speaker's mental state, where he combats "ennui and melancholy" by opening himself to "harmony" and love. The phrase "a new stage for love I scaffolded" suggests the speaker's active role in creating a space for positive emotions, indicating a sense of resilience and self-determination.
The second quatrain (lines 5-8) contrasts the speaker's past and present relationship with the sky, a symbol often associated with dreams, aspirations, and the divine. The speaker's dreams were once "scolded" by the sky, suggesting a period of disappointment or disillusionment. However, the sky now inspires "tranquility" that extends to "eternity," indicating a shift towards peace and acceptance.
The first tercet (lines 9-11) introduces the theme of nature's "secret celebration." The speaker feels welcomed into nature's "universal dome," a metaphor for the world or universe, suggesting a sense of belonging and unity with the natural world. The speaker's adoration for nature is only surpassed by God, indicating a deep reverence for the divine.
The final tercet (lines 12-14) introduces the "lucid sun," a symbol of enlightenment and joy. The sun's "bright smiles of exultation" suggest a sense of joy and celebration. The final line, "For those that also celebrate my home," suggests that this joy is shared with others who appreciate the speaker's "home," which could be interpreted literally as his physical home or metaphorically as his inner world or personal philosophy.
Overall, "Home Celebration" is a sonnet that explores themes of self-discovery, resilience, unity with nature, and shared joy. It reflects the speaker's journey from melancholy to tranquility, from isolation to unity, and from disillusionment to celebration..
Rhyme Scheme
Sonnet 94 by Francisco Luis Arroyave Tabares follows the structure of a Petrarchan sonnet, which is divided into an octave (the first eight lines) and a sestet (the last six lines). The rhyme scheme of a Petrarchan sonnet is typically ABBA ABBA for the octave and CDE CDE or CDC CDC for the sestet. However, there can be variations in the sestet's rhyme scheme.
Let's analyze the rhyme scheme of this sonnet:
-
The pleasures of my mind I unfolded (A)
-
To destroy ennui and melancholy (B)
-
And opened wide the doors to harmony (B)
-
While a new stage for love I scaffolded. (A)
-
Sky that yesterday all my dreams scolded (A)
-
Inspires me now a full tranquility (B)
-
That goes all the way to eternity (B)
-
Around which my life and aims I molded. (A)
-
Nature hints a secret celebration (C)
-
And offers me its universal dome (D)
-
Where only God has more adoration. (C)
-
His lucid sun that to my soul has come (D)
-
Is showing bright smiles of exultation (C)
-
For those that also celebrate my home. (D)
The octave follows the ABBA ABBA rhyme scheme perfectly. The sestet, following a CDC DCD rhyme scheme.
In this sonnet, the consistent rhyme scheme helps to create a sense of harmony and unity, reflecting the themes of tranquility, unity with nature, and shared joy that are explored in the poem.
Additional Aspects to Analyze
While we've covered the rhyme scheme and thematic analysis of Sonnet 94 by Francisco Luis Arroyave Tabares, there are still several aspects that can be further explored, including its use of imagery, meter, and tone.
-
Imagery: The sonnet is rich in vivid imagery that helps to evoke specific emotions and ideas. For instance, the "doors to harmony" and the "new stage for love" in the first quatrain create a sense of openness and possibility. The "sky" and "lucid sun" in the second quatrain and final tercet respectively, are powerful symbols of aspiration, enlightenment, and joy. The "universal dome" in the first tercet is a grand image that suggests a sense of awe and unity with the universe.
-
Meter: The sonnet appears to follow the iambic pentameter, which is a common meter in English sonnets. This means each line typically has five pairs of syllables, with the stress falling on the second syllable of each pair. For example, in the line "The pleasures of my mind I unfolded," we can see this pattern: "The PLEA-sures OF my MIND I un-FOLD-ed." The consistent rhythm created by the iambic pentameter gives the poem a musical quality and helps to emphasize certain words and ideas.
-
Tone: The tone of the sonnet is introspective and celebratory. The speaker begins by reflecting on his mental state and his efforts to combat "ennui and melancholy." As the poem progresses, the tone shifts to a more celebratory mood, as the speaker finds tranquility, unity with nature, and shared joy. The final line, "For those that also celebrate my home," leaves the reader with a sense of shared celebration and community.
-
Language and Diction: The sonnet uses formal and elevated language, which is typical of traditional sonnets. The use of words like "ennui," "scaffolded," and "exultation" contribute to the poem's formal tone. The poet also uses a few French and Latin words, which adds to the sophistication of the poem.
-
Symbolism: The sonnet is rich in symbolism. The "doors to harmony" symbolize openness to positive emotions and experiences, the "sky" and "lucid sun" symbolize aspiration and enlightenment, and the "universal dome" symbolizes the universe and the speaker's unity with it. These symbols help to convey the poem's themes in a more nuanced and impactful way.
-
Structure: As a Petrarchan sonnet, the poem is divided into an octave and a sestet. The octave typically presents a problem or conflict, while the sestet offers a resolution or response. In this sonnet, the octave explores the speaker's mental state and his relationship with the sky, while the sestet introduces the themes of nature's celebration and shared joy. This structure helps to create a sense of progression and resolution in the poem.
(GPT4)
Count the syllables of each line of the poem
(www.howmanysyllables.com)
```
Home Celebration
10 The pleasures of my mind I unfolded 10 To destroy ennui and melancholy
10 And opened wide the doors to harmony 10 While a new stage for love I scaffolded.10 Sky that yesterday all my dreams scolded 10 Inspires me now a full tranquility 10 That goes all the way to eternity 10 Around which my life and aims I molded.
10 Nature hints a secret celebration 10 And offers me its universal dome 10 Where only God has more adoration. 10 His lucid sun that to my soul has come
10 Is showing bright smiles of exultation 10 For those that also celebrate my home. ***```
poetry #sonnet #art #poems #poem #nostr #nostrart #artist #artnotai #artonnostr #artstr #zapathon #literature #books #original #poet #poets #author #grownostr #poetstr #iambicpentameter #pleb #plebchain
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4 and www.howmanysyllables.com Image by leonardo.ai

-
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ f4db5270:3c74e0d0
2023-07-21 07:21:11
@ f4db5270:3c74e0d0
2023-07-21 07:21:11 "Tony" (2023)
30x40 cm, oil on panel canvas
"Tony" (2023)
30x40 cm, oil on panel canvas(Available)
Here a moment work in progress...

The begining...

-
 @ c2232226:586fa98c
2023-08-15 04:22:26
@ c2232226:586fa98c
2023-08-15 04:22:26Project EcoToken: Revolutionizing Sustainability through Tokenization
Sustainability and environmental consciousness have become integral values in today's world. As the global community seeks innovative ways to promote eco-friendly practices and reward environmentally conscious choices, a groundbreaking initiative called Project EcoToken has emerged. This pioneering project leverages the power of blockchain and tokenization to create a transformative ecosystem that encourages and rewards the adoption of eco-friendly products and services.
The Urgency of Environmental Responsibility
With growing concerns about climate change and the depdletion of natural resources, the need for sustainable practices has never been more pressing. Individuals and businesses alike are searching for practical ways to contribute to a greener future. However, the challenge lies in incentivizing and tracking these efforts effectively.
Introducing Project EcoToken
Project EcoToken is not merely a digital concept; it's a visionary solutfion aimed at fostering environmental sustainability through blockchain technology. By tokenizing eco-friendly products and services, this project aims to create a comprehensive ecosystem where individuals and businesses can actively participate in promoting sustainability while being rewarded for their cogntributions.
Key Objectives and Features
-
Tokenized Eco-Products: Project EcoToken tokenizes eco-friendly products and segrvices, allowing consumers to make informed choices by verifying the environmental impact of their purchases.
-
EcoRewards: Participants are rewarded with EcoTokens for choosing sustainable options, such as using renewable energy sources, reducing waste, and supporting ethical businesses.
-
Transparent Impact: The blockchain ledger ensures transparency and traceability, enabling users to track the positive environmental impact of their choices.
-
Community Engagement: Project EcoToken fosters a commgunity of eco-conscious individuals and businesses, encouraging collaboration and knowledge sharing.
Empowering Sustainability in the Web3 Era
The impact of Project EcoToken extends far beyond the realm of tokenization:
-
Behavioral Shift: By incentivizing eco-friendly choices, Project EcoToken encourages a shift towards more sustainable consumption patterns.
-
Consumer Empowerment: Consumers gain the power to support products and services aligned with their values, ultimately influencing market demand.
-
Positive Impact: The transparent tracking of environmental contributions builds a sense of achievement and collective impact.
-
Global Network: As the project gains traction, it has the potential to create a global network of participants committed to sustainable practices.
Paving the Way for a Greener Future
As Project EcoToken evolves, collaboration with environmental organizations, businesses, and tech innovators will shape its trajectory. The project's commitment to promoting eco-friendly practices through tokenization aligns perfectly with the growing demand for sustainable solutions.
In a world where environmental responsibility is paramount, Project EcoToken stands as a symbol of positive change. By tokenizing eco-friendly products and services, the project envisions a future where every purchase becomes an opportunity to contribute to a more sustainable planet. As Project EcoToken gains momentum and garners support from individuals, businesses, and advocates of environmental conservation, it has the potential to transform the way we approach consumption and collectively work towards a greener, more sustainable future.
-
-
 @ 20986fb8:cdac21b3
2023-08-15 03:40:44
@ 20986fb8:cdac21b3
2023-08-15 03:40:44This article original was published in nostr.com and it is shared in here for convenience and fast acces within YakiHonne client. All credit goes to https://github.com/nostr-protocol/nostr
Clients are the way that you access and interact with the Nostr protocol.
What's a client?
A client in Nostr is just the app that you use to access and interact with the protocol. It's like the Twitter iOS app or web app that you use to interact with Twitter's feed of tweets.
Because the Nostr protocol is very simple and flexible, different clients have approached the protocol in different ways: some try to make the experience look exactly like Twitter, others try to highlight the importance of relays to the protocol and expose that to users, and others try to use heuristics and algorithms to ensure the maximum degree of censorship-resistance without burdening users too much.
Can I switch clients?
Yes. Because a client is just a way to access the underlying data held by relays, you can switch clients or sign into as many clients as you'd like. As long as each client is looking at the same set of relays for their data, you'll see the same messages in each client.
Should I enter my private key in the client?
Generally, it's better not to enter your private key into any client. Most clients that ask for private keys do their absolute best to keep your key secure but given the nature of software, there are always breaches, exploits, and bugs that could potentially expose your private key.
Remember, your private key is your identity in Nostr, so if it is compromised you'll lose your followers and will have to start from scratch rebuilding your identity.
A few of the already existed clients
Web
- Snort, an easy-to-use client with great onboarding.
- Coracle, an experimental client that is advancing the UX and internals of social media.
- Iris, a client that throws you in instantly.
iOS
- Damus, the first Nostr client to be banned in China.
- Primal, a very fast client that relies on server-side caching.
iOS and Android
- Plebstr, a closed-source client that is beautiful, fast and smooth.
- ZBD, a custodial, hosted client for ZBD users.
- Current, a client that comes with a built-in Bitcoin wallet.
Android
- Amethyst, a client that has all the features you might imagine.
- Nozzle, a very lean client, but still a work-in-progress.
Desktop
- Gossip, a native client that tries to efficiently follow people in wherever relay they happen to be, made in Rust with egui.
- more-speech, a client that gives you a powerful global view and way of interacting with custom filtering based on web-of-trust and relay selection, made in Clojure. Check out a guide here.
- Lume, an ambitious client made with Tauri.
What are relays ?
Relays are like the backend servers for Nostr. They allow Nostr clients to send them messages, and they may (or may not) store those messages and broadcast those messages to all other connected clients.
The world of relays is changing fast so expect many changes here in the future. One thing to note, because Nostr is decentralized and depends on relays to store and retreive data, if you notice that your Nostr client feels slow, it's most likely due to the relays that you're using. It might be worth adding a few more relays to your client.
Where can I find a list of relays?
The best resource we've found for browsing and assessing the speed of known relays is the nostr.watch site.
What happens if all the relays I use stop working?
If all the relays that you have used in the past go offline, all your posts will be unretrievable. This is one reason that Nostr allows users to connect to many relays – this ensures some degree of backup. That said, if you're really interested in being uncensorable, you can run your own personal relay.
Should i run my own relay?
For most people, no, it's not worth the hassle. That said, if you're technical and want to ensure that your speech is absolutely uncensorable, then you can and should run your own relay. This ensures that you always have a copy of all your Nostr posts and interactions for all time. Here is a guide from Andre Neves for hosting your own relay under 5 minutes
How can someone find me in a personal or obscure relay?
You should be able to hint where you are publishing to to people that may be interested by using the NIP-19 nprofile code or the NIP-05 "relays" field.
If you manage to (and your client helps) you can publish a list of the relays you use to multiple other relays that you don't, so others can find that list and start following you were you are.
Finally, clients from others should include relay hints in events that mention or reply to you, the hints should point to where your notes can be found, so that can give clients a clue.
What public relays exist?
The nostr.watch website keeps a very complete list that has a bunch of information about each relay, not only their address.
How to contribute?
Here are some ways you can contribute to the success of Nostr:
- Contribute to your favorite client, try to come up with approaches that both make Nostr fun and useful and also promote decentralization and ultra-interoperability
- Start a new client if you think you have new approaches and ideas to contribute that wouldn't fit in an existing app
- Check out https://bountsr.com/ for things that might interest you
- Use Nostr, think about it, and let others know what you have seen in this crazy new idea that has captured your imagination
- Give feedback to client authors, but patiently
- Create or contribute to bounties on https://bountsr.com/
- Give money to people that are doing things you think are good
- Write explainers and curated resources, put them online so they can help others
- Check how your skills can help Nostr software or the mission of spreading the Nostr world, partner with others that may be searching for that
- If you have a good, concrete, real-world use case for Nostr that you want to use yourself and others might want to, bring it up and it's likely that someone else will be interested in building it
- Annoy content creators, people banned from social media and other personalities that you follow that you think may be interested in Nostr until they look at it
-
 @ 72f97555:e0870ff3
2023-07-21 04:20:44
@ 72f97555:e0870ff3
2023-07-21 04:20:44We’ve watched them come and go: social networking attempts like Mastodon (Activity Pub), Blue Sky, and recently, Threads. They’ve begun to follow what feels very much like a pattern. First basic functionality is built out, then there’s a crisis of some sort on mainstream social media, then there’s a population explosion on the new social network, people quickly become disillusioned, then a population collapse. It can be very tempting, while watching these networks explode their user bases into the millions overnight, to wish for that for ourselves on Nostr. I do not. In fact, I believe this sudden explosive growth is partially responsible for the inevitable decline and collapse of these attempted “replacements” for any of the big corporately owned networks. Social networks don’t fail due to technology issues - they fail because of social issues.
Culture Matters
When people exodus a media platform en masse, they bring their culture with them. Their expectations of the types of content they want to interact with, the ways they intend to behave, and the ways they engage with others. These patterns are influenced by two factors in mainstream social: moderation, and tradition. - Moderation forms the culture in a top-down way, by establishing the limits of what kind of content will be acceptable on the platform. Platforms with relatively loose moderation policies will tend to attract people that diverge from established norms of behavior, more than those who typically conform. - Tradition also informs culture in unique ways for each platform - the things that are easiest to find, provoke an emotional response, and are easy to share tend to dominate. - Functionality also plays a role, albeit a lesser one, but one that tends to form the unique humor of a platform. Reddit is a fine example of this with its long threads of puns, each one building on the previous post. Hell threads on other platforms are another example. The problem arises because new platforms rarely meet the expectations of another culture formed on another platform. Functionality will be different in subtle but important ways, and the early adopters of the new platform will be interested in different topics. This is very true on Nostr, where posts are rewarded specifically for quality - a metric that is very difficult to quantify, but any long-time user can identify - and an overabundant quantity of posts is more likely to get you muted than followed.
Assimilation Matters
When users slowly trickle their way into a new platform, they are more inclined to ask questions, and attempt to understand the existing culture. They are the “new kid on the block” and will be more apt to seek feedback if they truly desire to achieve any sort of success. They then add the unique qualities of their personality to this information, and contribute something new to the culture, while still being a part of it. When a large group of users joins all at once, they bring their own connections with them. When the group joining dwarfs the existing user base, they have less motivation to seek advice on how to best utilize the platform to its fullest potential, expecting that they will be able to continue connecting and communicating with their existing contacts in the same way they always have. This will inevitably lead to frustration when the new platform does not provide them with the same success that they had on the former platform - leading to the inevitable conclusion that the “new Twitter (or Facebook, Instagram, et al.)” is not as good as the old one. And so we watch the tides of users go in and out, leaving old platforms in frustration for new ones, only to become equally frustrated with their inability to communicate and reach an audience as effectively as they used to, and returning to the old platform, or seeking yet greener pastures.
Stability Matters
Sudden growth causes sudden problems. Both Mastodon and Blue Sky encountered major issues that they were not prepared to handle, and handled badly. Mastodon operators found themselves facing enormous hosting bills, and Blue Sky faces serious obstacles in keeping their promises to provide a “safe” environment with the influx of new users. A slow, steady growth model allows the operators of services to face problems in a more measured way, and to build out both infrastructure and content tools to allow users to have a pleasant experience. It is less likely to take an otherwise major contributor to a project, and make them “tap out” due to rising costs, frustrated users, and a constant crisis mindset. Nostr is a distributed network, and has amazing potential for horizontal scaling. Even if one in ten-thousand users who onboards onto Nostr decides to run a relay, the network will be in good shape. Content distribution can be handled in a large number of ways - it isn’t tied fundamentally to the protocol itself - which allows many different providers to be used, and new ways of handling content to be built. But creating those relay operators and content hosts out of newbies takes time. A truly educated relay admin capable of handling the job of maintaining a secure and reliable relay takes weeks or days at best, assuming they are already familiar with similar tasks. Adding 10 million users overnight - the way Threads did - is likely to swamp existing providers before new providers have time to step in a fill the gap. Which would also have the effect of chilling user experience. There is a lot of new terminology and capability to take in when joining Nostr. For the mainstream person, they are going to have to learn about: cryptographic keys, Nostr Addresses (NIP-05), Lightning Wallets, Zaps and by proxy Bitcoin, and eventually Lists, Relay Management, Paid Relays, how to find content, moderate their own feed, and more. Right now, Nostr is doing an excellent job of answering those questions and educating users on the new terminology and techniques because the flow is small and steady with a few bursts.
The Tortoise and The Hare
I truly believe that the success of Nostr will be in no small part because it is growing steadily instead of all at once. Every user onboarded correctly adds to the army of people ready to help welcome the next little wave of people who learn about the decentralized and censorship resistant qualities of Nostr. These individuals are also given the time to become part of a kinder social group than is typically found on social media, and learn to truly become productive and successful as true Nostriches rather than just transplants from another place.
And that is truly the magic isn’t it? People don’t just move to Nostr, they become Nostriches. They become part of a real community, and they belong with us. We take refugees from other social media sites, and don’t leave them refugees. I think that’s beautiful and worth slowing down to do.
I don’t look to the short term for Nostr - I’m bullish for Nostr in the long haul. We are building to still be here after the others have already burnt themselves away. It reminds me of my home country:
“Give me your tired, your poor, your huddled masses yearning to breathe free, the wretched refuse of your teeming shore. Send these, the homeless, tempest-tossed to me, I lift my lamp beside the golden door!”
-
 @ 72f97555:e0870ff3
2023-07-21 04:18:38
@ 72f97555:e0870ff3
2023-07-21 04:18:38We’ve watched them come and go: social networking attempts like Mastodon (Activity Pub), Blue Sky, and recently, Threads. They’ve begun to follow what feels very much like a pattern. First basic functionality is built out, then there’s a crisis of some sort on mainstream social media, then there’s a population explosion on the new social network, people quickly become disillusioned, then a population collapse. It can be very tempting, while watching these networks explode their user bases into the millions overnight, to wish for that for ourselves on Nostr. I do not. In fact, I believe this sudden explosive growth is partially responsible for the inevitable decline and collapse of these attempted “replacements” for any of the big corporately owned networks. Social networks don’t fail due to technology issues - they fail because of social issues.
Culture Matters
When people exodus a media platform en masse, they bring their culture with them. Their expectations of the types of content they want to interact with, the ways they intend to behave, and the ways they engage with others. These patterns are influenced by two factors in mainstream social: moderation, and tradition. - Moderation forms the culture in a top-down way, by establishing the limits of what kind of content will be acceptable on the platform. Platforms with relatively loose moderation policies will tend to attract people that diverge from established norms of behavior, more than those who typically conform. - Tradition also informs culture in unique ways for each platform - the things that are easiest to find, provoke an emotional response, and are easy to share tend to dominate. - Functionality also plays a role, albeit a lesser one, but one that tends to form the unique humor of a platform. Reddit is a fine example of this with its long threads of puns, each one building on the previous post. Hell threads on other platforms are another example. The problem arises because new platforms rarely meet the expectations of another culture formed on another platform. Functionality will be different in subtle but important ways, and the early adopters of the new platform will be interested in different topics. This is very true on Nostr, where posts are rewarded specifically for quality - a metric that is very difficult to quantify, but any long-time user can identify - and an overabundant quantity of posts is more likely to get you muted than followed.
Assimilation Matters
When users slowly trickle their way into a new platform, they are more inclined to ask questions, and attempt to understand the existing culture. They are the “new kid on the block” and will be more apt to seek feedback if they truly desire to achieve any sort of success. They then add the unique qualities of their personality to this information, and contribute something new to the culture, while still being a part of it. When a large group of users joins all at once, they bring their own connections with them. When the group joining dwarfs the existing user base, they have less motivation to seek advice on how to best utilize the platform to its fullest potential, expecting that they will be able to continue connecting and communicating with their existing contacts in the same way they always have. This will inevitably lead to frustration when the new platform does not provide them with the same success that they had on the former platform - leading to the inevitable conclusion that the “new Twitter (or Facebook, Instagram, et al.)” is not as good as the old one. And so we watch the tides of users go in and out, leaving old platforms in frustration for new ones, only to become equally frustrated with their inability to communicate and reach an audience as effectively as they used to, and returning to the old platform, or seeking yet greener pastures.
Stability Matters
Sudden growth causes sudden problems. Both Mastodon and Blue Sky encountered major issues that they were not prepared to handle, and handled badly. Mastodon operators found themselves facing enormous hosting bills, and Blue Sky faces serious obstacles in keeping their promises to provide a “safe” environment with the influx of new users. A slow, steady growth model allows the operators of services to face problems in a more measured way, and to build out both infrastructure and content tools to allow users to have a pleasant experience. It is less likely to take an otherwise major contributor to a project, and make them “tap out” due to rising costs, frustrated users, and a constant crisis mindset. Nostr is a distributed network, and has amazing potential for horizontal scaling. Even if one in ten-thousand users who onboards onto Nostr decides to run a relay, the network will be in good shape. Content distribution can be handled in a large number of ways - it isn’t tied fundamentally to the protocol itself - which allows many different providers to be used, and new ways of handling content to be built. But creating those relay operators and content hosts out of newbies takes time. A truly educated relay admin capable of handling the job of maintaining a secure and reliable relay takes weeks or days at best, assuming they are already familiar with similar tasks. Adding 10 million users overnight - the way Threads did - is likely to swamp existing providers before new providers have time to step in a fill the gap. Which would also have the effect of chilling user experience. There is a lot of new terminology and capability to take in when joining Nostr. For the mainstream person, they are going to have to learn about: cryptographic keys, Nostr Addresses (NIP-05), Lightning Wallets, Zaps and by proxy Bitcoin, and eventually Lists, Relay Management, Paid Relays, how to find content, moderate their own feed, and more. Right now, Nostr is doing an excellent job of answering those questions and educating users on the new terminology and techniques because the flow is small and steady with a few bursts.
The Tortoise and The Hare
I truly believe that the success of Nostr will be in no small part because it is growing steadily instead of all at once. Every user onboarded correctly adds to the army of people ready to help welcome the next little wave of people who learn about the decentralized and censorship resistant qualities of Nostr. These individuals are also given the time to become part of a kinder social group than is typically found on social media, and learn to truly become productive and successful as true Nostriches rather than just transplants from another place.
And that is truly the magic isn’t it? People don’t just move to Nostr, they become Nostriches. They become part of a real community, and they belong with us. We take refugees from other social media sites, and don’t leave them refugees. I think that’s beautiful and worth slowing down to do.
I don’t look to the short term for Nostr - I’m bullish for Nostr in the long haul. We are building to still be here after the others have already burnt themselves away. It reminds me of my home country:
“Give me your tired, your poor, your huddled masses yearning to breathe free, the wretched refuse of your teeming shore. Send these, the homeless, tempest-tossed to me, I lift my lamp beside the golden door!”
~ TheSameCat
-
 @ 0e649f32:8a33b33b
2023-08-15 00:41:23
@ 0e649f32:8a33b33b
2023-08-15 00:41:23Our weekly 30 minute podcast helps you, a small business owner with 5 to 30 team members, take your company to the next level. The Grow A Small Business community, weekly cast, blog and leadership email supports leaders get through the pain of growth. With insights, lessons learned, books and tools as well as habits these experienced small business owners suggest you develop, our interviews unearth tremendous value for anyone wanting to grow their business with less stress.
4+ years experience working at a customer service center, now helping entrepreneurs enhance good communication with clients through own call center company with 10+ M revenue and 150 team members. (Richard Blank)
Episode #251. I interview Richard Blank, the Founder, and CEO of Costa Rica’s Call Center based in San Jose, Costa Rica. Richard has set up his own business to help entrepreneurs enhance and maintain good communication with their clients.
-
 @ bcea2b98:7ccef3c9
2023-07-20 18:13:11
@ bcea2b98:7ccef3c9
2023-07-20 18:13:11Atop a majestic mountain called Mt. Gox, a tale unfolded that would forever be etched in the history of cryptocurrency. This is the story of a legendary exchange, a hub of digital treasures, and the challenges it faced along the way.
In the early days of Bitcoin, when the world was just beginning to grasp the concept of digital currencies, a passionate entrepreneur named Jed McCaleb founded a platform called Mt. Gox. Located high above the clouds on the slopes of Mt. Gox, the exchange quickly became the center of the Bitcoin universe.
Bitcoin enthusiasts from all corners of the globe flocked to Mt. Gox, eager to trade, buy, and sell their digital coins. It became a bustling marketplace, a hub of innovation, and a symbol of the emerging cryptocurrency ecosystem.
As the popularity of Bitcoin skyrocketed, so did the demand for Mt. Gox's services. The exchange handled an immense volume of transactions, becoming the largest Bitcoin exchange in the world. Its name echoed throughout the digital realm, synonymous with the promise and potential of the cryptocurrency revolution.
However, as with any great tale, challenges arose. In 2011, a cyber attack targeted Mt. Gox, leading to the theft of a substantial number of Bitcoins. This event served as a wake-up call, revealing vulnerabilities within the exchange and prompting the need for heightened security measures.
The incident didn't dampen the spirit of Mt. Gox. The team worked tirelessly to recover from the attack, implementing new security protocols and earning back the trust of its users. Mt. Gox emerged stronger than ever, serving as a beacon of stability in the ever-evolving cryptocurrency landscape.
But the story of Mt. Gox took an unexpected turn. In 2014, another significant blow struck the exchange. It was discovered that a substantial number of Bitcoins were missing from Mt. Gox's vaults. The magnitude of the loss sent shockwaves throughout the cryptocurrency community and shook the foundations of the industry.
As the truth emerged, it became clear that Mt. Gox faced insurmountable financial challenges. The exchange was forced to declare bankruptcy, leaving its users devastated and questioning the future of digital currencies.
Yet, amidst the chaos, the story of Mt. Gox served as a catalyst for change and resilience in the cryptocurrency world. It brought to light the need for enhanced security practices, regulatory oversight, and a renewed commitment to building trustworthy platforms for the exchange of digital assets.
Over time, the lessons learned from Mt. Gox's history paved the way for greater transparency, improved infrastructure, and the emergence of more secure cryptocurrency exchanges. It became a cautionary tale, reminding the industry of the importance of accountability, investor protection, and responsible innovation.
Today, as we reflect on the history of Mt. Gox, we see a story of both triumph and adversity. It stands as a reminder that the cryptocurrency landscape is still in its early stages, evolving and maturing with each passing day.
So, dear listener, let the tale of Mt. Gox serve as a lesson in resilience and growth. As the cryptocurrency world continues to advance, let us navigate the digital landscape with caution, learn from the past, and work towards a future where innovation and security walk hand in hand.
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ 92294577:49af776d
2023-07-19 23:40:11
@ 92294577:49af776d
2023-07-19 23:40:11Growing evidence suggests, however, there is no ‘one size fits all’ approach but rather many complementary protocols, each addressing different problems and catering to specific use cases and markets.
In this edition of Layer-2 Roundup, we look at some of these second-layer protocols in detail. Among other things, we will explore their interoperability (or lack thereof) and the projects using these solutions to promote mass adoption. We will also look at some of the various growing pains experienced so far, as seen recently as a result of May’s high-fee market environment.
Choosing the Right Tool for the Job
Each second layer addresses a unique set of limitations inherent in the mainchain, such as the lack of high transaction throughput, privacy, or the ability to issue assets. For example, if you want to send a friend a small amount of sats and value affordability and speed, Lightning is likely the best option. Whereas if you are a financial institution wanting to issue an asset like a bond or digital security, it makes more sense to use Liquid.
https://cdn.nostr.build/i/5fdbca0ff4cd19d5cccd049387d495812a91b45fafd5e9a4c899eb7478611378.png
There are also varying tradeoffs when using each solution that may affect a user’s decision to opt in, like Lightning’s liquidity constraints or the trust requirements (albeit distributed) seen with federated models, such as Liquid and Fedimint. As creator Burak has openly shared, even the newest addition to the layer-2 landscape, Ark, has tradeoffs with the mainchain and other L2s.
Like the old analogy of 'choosing the right tool for the job,' in a hyperbitcoinized world, users can expect to have a toolkit of L2s at their disposal, with different capabilities and tradeoffs.
Increasing Interoperability
Often overlooked is the importance of interoperability between not only the second-layer protocol and Bitcoin but the layer-2 protocols themselves. A second layer, where end-users can leverage several protocols together and move seamlessly between them, creates a healthier, more resilient financial system and an overall better user experience—both essential for mass adoption. For example, by running Lightning on top of Liquid, users gain greater privacy, additional liquidity, and cheaper fees (and much more, as we will explore later).
While both Liquid and Lightning networks operate independently, they are complementary and interoperable, offering a secure, alternative method to stacking sats or a more cost-effective option to Lightning channel rebalancing, especially when fees are high on the mainchain.
Elements, the open-source codebase that Liquid is built on, is designed to be as close to parity with Bitcoin Core as possible. This not only offers some nice security guarantees (since any bug fix or performance improvement upstream in Bitcoin can be merged into Elements) but also greater interoperability with other L2s, given that its design functions very similarly to Bitcoin.
Connecting the Second Layer with Lightning
The basis of Lightning is its network of payment channels, which are fundamentally made possible through Bitcoin's Unspent Transaction Outputs (UTXOs) in conjunction with Lightning's Hashed Timelock Contracts (HTLCs). The UTXO model allows certain script conditions, and hash puzzles and time constraints to be encoded in the transaction for payment to be securely routed across Lightning.
One of the many design features that Liquid inherits from Bitcoin is its UTXO model. This compatibility allows Lightning's HTLCs to function with Liquid Bitcoin (L-BTC) in a manner similar to how they function with Bitcoin, enabling the payment network to operate on top of Liquid. Note that this Lightning Network on Liquid would run as a separate network but with all the advantages of Liquid as its underlying chain (e.g., Confidential Transactions and deterministic blocks). You could even bridge the two networks if you ran both—one on top of Bitcoin, the other on Liquid—for greater cross-platform compatibility. The payments remain end-to-end secure since both use the HTLC construction. The bridge, however, gets to dictate a dynamic exchange rate if the two assets being transferred are different, which is not an issue when transferring BTC and L-BTC since they are pegged.
Lightning's inherent decentralization, wide adoption, and compatibility with UTXO-based technologies could position it as the connective tissue between each L2. It could act as a primary hub for new protocols seeking to bridge to existing ones, helping to avoid the chicken-and-egg problem of adoption that has plagued new protocols in the past.
This thesis has begun to play out more recently, with several big-name exchanges adding Lightning and swap platforms incorporating Liquid with Lightning to leverage the benefits of both protocols.
Unfairly Cheap with Lightning and Liquid
In early May, on-chain Bitcoin transaction costs surged due to network congestion, resulting in the highest fees seen in nearly two years. This affected major exchanges like Binance and Coinbase, and even some Lightning-compatible wallets like Muun, pricing some users out of the market entirely. This week-long episode underscored the importance of hardening scalability solutions like Lightning, which have so far relied on mainchain transactions to keep liquidity balanced. The event also raised awareness of the powerful benefits of using layer-2 technologies together, especially when fees on Bitcoin's mainchain are not only high but also volatile.
One of the new products in-market driven by this episode is the use of Liquid submarine swaps by Boltz to offer cheap Lightning channel liquidity to its users. As opening a Lightning channel requires an on-chain transaction and many users rely on the mainchain to add liquidity to their Lightning node, costs can quickly add up in high-fee conditions. By using the Liquid sidechain instead of the Bitcoin mainchain as the underlying liquidity source, users can rebalance their Lightning channels independently from the congested mainchain mempool—and do so without losing self-custody of their funds, thanks to the atomic nature of the swap.
In a high-fee scenario, users can expect upwards of 99% savings using the Liquid swap feature. Boltz intends to expand the scope of their Liquid integration by building an L-BTC <> BTC chain-to-chain atomic swap for trustless peg-outs—the first of its kind.
You can read more about Boltz's decision to add Liquid and why in their write-up here.
📺 Lightning Channel Rebalancing with Liquid Bitcoin on boltz.exchange
Another option for users is the self-hosted rebalancing protocol PeerSwap, which allows Lightning node operators to rebalance their channels with peers directly using BTC and L-BTC atomic swaps. This setup eliminates the need for a third-party coordinator for even greater savings and allows smaller nodes to better compete with larger ones. PeerSwap is currently available for both CLN and LND implementations.
The story does not end there, though. In addition to provisioning Lightning liquidity with Liquid, users turned to Lightning <> Liquid swaps to stack sats (and humbly, I might add). Many used a cheap starting point like Strike, Cash App, or some other fiat on-ramp to buy Lightning Bitcoin (LN-BTC) directly and then moved to one of the growing number of Lightning to Liquid swap services like Boltz, SideShift, or Classic CoinOs to convert to L-BTC to HODL for the mid-term. So, why would anyone HODL in L-BTC rather than LN-BTC? Unlike with Lightning, Liquid assets can be self-custodied offline in cold storage, like on a hardware device such as Jade. This setup is better for HODLing over a longer time frame—another difference to consider when deciding what layer-2 solution is best for you and your specific use case.
The Emergence of the Bitcoin Superapp
Some builders are already working on improving the Bitcoin layer-2 user experience by directly integrating swaps and multi-protocol support into their app offerings.
For example, the Blockstream Green team is in the final stages of adding Lightning capability via Greenlight, giving Bitcoiners the ability to self-custody mainchain, Liquid, and Lightning all in one app. Green, SideSwap, and the soon-to-be rereleased version of the AQUA wallet also plan to incorporate in-app Lightning <> Liquid swaps using the Boltz API.
Wallby, a newly anointed Bitcoin ‘superapp,’ supports the custody of mainchain, Liquid, and Rootstock, with further plans to add Lightning and RGB. The Wallby team is also placing emphasis on features. For instance, users can already add bitcoin and other digital assets to liquidity pools and earn interest through an automated market maker (AMM), with the ability to lend and borrow peer-to-peer and perform cross-chain swaps also on the way.
The emergence of these Bitcoin superapps and new features like in-app swaps prioritizes improving user experience, something the Bitcoin space is notoriously bad at (to the point it has become a running meme). This pivot and Lightning's maturation as a sort of lingua franca of Bitcoin will be a crucial part of the strategy for increasing layer-2 interoperability and facilitating mass adoption. Each protocol will have a unique place in the hyperbitcoinization story, ending in a second layer that is stronger than each individual protocol on its own.
-
 @ aa8de34f:a6ffe696
2023-08-14 19:06:45
@ aa8de34f:a6ffe696
2023-08-14 19:06:45Bitcoin; A Beacon of Hope, in the Troubled Waters of the Fiat Money System. An Ethical and Social Science Perspective
I. Setting the Scene
In the saga of economics the fiat money system has taken center stage for more than a century. This system, where our money isn't backed by a commodity but by our trust in institutions has faced numerous crises that have exposed its inherent flaws. As a student of sciences I recognize the impact this has on societal well being, economic stability and power dynamics. The storyline of this system is riddled with turns such as inflation, debt cycles and power concentration among a few resulting in economic disparities and social unrest.
Imagine living in a world where your earned savings could vanish overnight due to decisions made away in corporate boardrooms. This is not some fiction but an unfortunate reality for many under our current fiat money system. In this essay we delve into Bitcoin—a cryptocurrency—as a protagonist, within this narrative. By exploring the social science principles that form the foundation of Bitcoin, our goal is to bring awareness to how our monetary system impacts our freedom, fundamental rights and democracy. Additionally we will delve into how Bitcoin has the potential to reshape this narrative.
II. Background: The Evolution of Money and the Current State of the Fiat Money System
Money the lifeblood of our economies has undergone changes, throughout history reflecting the evolving needs and technological advancements of societies. From barter systems to metals, paper currency and now the digital era each transformation has left its mark on our journey through time.
The fiat money system, which currently governs our economy has been the force for the century. However it resembles a sandcastle built close to the waters edge— to inflation and economic instability. Picture a castle where central banks hold the keys to influence your moneys value at their discretion. This is how our fiat money system operates. In this essay we will explore whether Bitcoins decentralized nature can reshape this landscape by offering a fair economic terrain.[1][2]
III. The Flaws in the Fiat Money System
Imagine envisioning the economy as a web interconnecting various nodes, with the U.S. Dollar acting as its central hub—the reigning fiat currency. The current economic system, which has been the foundation of our economies is displaying signs of strain. Fiat money, in essence is a currency that isn't tied to a commodity. Instead its value derives from the trust we have in the government that issues it (Wilck, Lynch, & Kauffmann, 2014).
Imagine a seesaw with banks on one side and ordinary individuals on the other. The control that banks have over the money supply can disrupt the balance. Result in inflation. This inflation gradually erodes peoples purchasing power. Creates instability. Moreover our system relies heavily on debt—a bit like a house of cards. Money is generated through lending practices leading to cycles of boom and bust that can jeopardize well being. These problems extend beyond economics. Contribute to widening inequality and instability.[3]
IV. The Unintended Consequences of Fiat Money
The impact of this can be especially harmful, for individuals with fixed incomes or limited savings. Take, for instance the decision made by the United States to abandon the gold standard in 1971. Since then the purchasing power of the U.S. Dollar has significantly decreased by, than 85% showcasing how inflation relentlessly eats away at its value.
The debt that emerges as a result of the fiat money system has repercussions leading to crises, social inequality and international instability. These consequences further exacerbate the divide, among groups.
Imagine a society where the gap between the wealthy and the impoverished continuously widens with each cycle. In such a society ones stability in life can be disrupted by decisions made in banking boardrooms. This is the reality we face due to the existence of the fiat money system. Hence it raises a question; Is it possible for us to navigate a path? Can Bitcoin, as a cryptocurrency serve as our guiding light, towards a balanced and fair economic landscape?
V. Bitcoin; A Revolutionary Response, to an Imperfect System
In the aftermath of the 2008 crisis, when economies were crumbling and faith in financial institutions was fading a new kind of currency emerged. Bitcoin, a currency came into existence as a reaction to the perceived flaws of the conventional financial system. Imagine it as a phoenix rising not from ashes but from the ruins left behind by a catastrophe.
The underlying philosophy of Bitcoin is to separate money from the control of governments—a concept that has gained momentum since the crisis. Its design principles, such as decentralization, fixed money supply and proof of work mechanisms position it as an alternative to our current fiat money system.[3][5].
VI. Bitcoin; A Beacon of Ethical Efficiency
In contrast, with the fiat money system Bitcoin has been specifically crafted to address many of its problems. Operating as a currency means that it functions without relying on any central authority. Consequently it cannot be influenced by governments or central banks for their benefit. Is safeguarded against manipulation by a privileged few individuals. The supply of bitcoins is fixed, with only 21 million ever to be produced. This scarcity sets it apart from currencies, which can be printed without limitations.
Bitcoins core design principles include decentralization, transparency and immutability. These ensure that all transactions are transparent and cannot be changed, providing a level of security and trust compared to financial systems. Additionally it eliminates the need, for intermediaries resulting in cost reduction and increased efficiency.
One key feature of Bitcoin is its Proof of Work (PoW) consensus mechanism. Despite concerns about its energy consumption it's important to note that this energy usage is necessary for the security of the system. Miners solve problems using computational power and energy to validate transactions and secure the network effectively. While the total energy consumption may seem significant according to Wolfram Alphas data it serves as a trade off, for the security and decentralization benefits it offers [2].
VII. Practical Applications and Advantages of Bitcoin
Bitcoins potential goes beyond theory; it has already been put into practice across sectors demonstrating its applications and benefits. These real life examples demonstrate how Bitcoin can address concerns linked to the fiat money system, such, as transparency and decentralization.
Bitcoin as Legal Tender: The Case of El Salvador[6]
In a historic move, El Salvador became the first country to adopt Bitcoin as legal tender in 2021. This bold step signifies Bitcoin's growing acceptance and its potential to serve as a viable alternative to traditional fiat currencies. The country's move to embrace Bitcoin has opened up new possibilities for financial inclusion, economic growth, and innovation.
VIII. The Challenges and Criticisms of Bitcoin
According to a study, by Bonneau, Miller, Clark, Narayanan, Kroll and Felten in 2015 it was observed that the value of Bitcoin can fluctuate greatly which can result in losses for users. This volatility may discourage users. Undermine Bitcoins reliability as a stable form of value storage.
Another concern raised is the impact of Bitcoin mining. The mining process involves solving problems to validate transactions and add them to the blockchain requiring substantial computational power and energy. This has sparked worries about the carbon footprint associated with Bitcoin especially considering the pressing need to address climate change. Critics argue that this is wasteful; however they fail to consider the security and efficiency provided by Proof of Work (PoW). PoW makes the Bitcoin network highly resistant to attacks, necessitating energy consumption as an aspect of maintaining a global transaction system.
Bitcoin has also faced criticism for its association with activities like money laundering and illegal trade due to its nature. Consequently there have been calls, for regulation and oversight that could potentially undermine Bitcoins nature and privacy advantages (Sas & Khairuddin 2017).
The regulation of Bitcoin remains an issue. While there are some who argue against it expressing concerns, about activities and market stability there are others, including myself who believe that Bitcoins inherent design principles make it self regulating. The transparency of its blockchain and the decentralized nature of Bitcoin create a system where market forces and network consensus drive its operation and governance [2].
IX. Conclusion
As we find ourselves at the intersection of evolution the current fiat money system presents its challenges such as inflation, economic disparity and centralized control. This calls for a shift. Enter Bitcoin. A beacon of hope in the landscape. Its decentralized nature and limited money supply offer an alternative to the system.
From an ethical and social sciences perspective Bitcoin is more than a currency. It serves as a tool for promoting inclusion reducing inequality and outlining a blueprint for a more democratic financial system. The urgency for regulation on Bitcoin may not be as immediate as some might think. Its design principles inherently provide security, transparency and fairness while effectively bypassing the shortcomings of the fiat money system.
Envision a world where money isn't controlled by a rather acts as a democratic medium accessible to all individuals. Bitcoin brings us closer, to this vision of reality. It tackles shortcomings that exist within the fiat currency system and signifies a notable advancement, in the progression of money. The potential for Bitcoin to reshape our system into one that's fairer and more effective is not just an abstract idea but something we can realistically achieve. As we navigate the path in finance Bitcoin serves as a guiding light offering a voyage, towards a financial landscape that is more inclusive, equitable and open.
Footnotes
- Yermack, D. (2013). Is Bitcoin a real currency? An economic appraisal. National Bureau of Economic Research. https://doi.org/10.3386/w19747 [↩]
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. https://bitcoin.org/bitcoin.pdf [↩]
- Saraswat, S., Chauhan, V., & Faujdar, N. (2016). Analysis on Crypto-Currency. International Journal of Computer Applications, 144(6), 975-8887. https://dx.doi.org/10.21172/1.91.28 [↩]
- Saraswat, S., Chauhan, V., & Faujdar, N. (2016). Analysis on Crypto-Currency. International Journal of Computer Applications, 144(6), 975-8887. https://dx.doi.org/10.21172/1.91.28 [↩]
- Monem, M., Ahmad, A., Jumana, R., Ahmed, R., & Arif, H. (2020). Efficient Blockchain System based on Proof of Segmented Work. 2020 IEEE Region 10 Symposium (TENSYMP), 1717-1722. https://dx.doi.org/10.1109/TENSYMP50017.2020.9231027 [↩]
- El Salvador: Launching Bitcoin as Legal Tender - Case - Faculty & Research - Harvard Business School (hbs.edu) https://www.hbs.edu/faculty/Pages/item.aspx?num=62068 [↩]
References
Bonneau, J., Miller, A. K., Clark, J., Narayanan, A., Kroll, J. A., & Felten, E. (2015). SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. Retrieved from https://dx.doi.org/10.1109/SP.2015.14
Fauzi, M. A., Paiman, N., & Othman, Z. (2020). Bitcoin and Cryptocurrency: Challenges, Opportunities and Future Works. Retrieved from https://dx.doi.org/10.13106/jafeb.2020.vol7.no8.695
Khairuddin, I. E., & Sas, C. (2019). An Exploration of Bitcoin Mining Practices: Miners' Trust Challenges and Motivations. Retrieved from https://dx.doi.org/10.1145/3290605.3300859
Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. Bitcoin.org Narayanan, A., Bonneau, J., Felten, E., Miller, A., & Goldfeder, S. (2016). Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction. Princeton University Press.
Sas, C., & Khairuddin, I. E. (2017). Design for Trust: An Exploration of the Challenges and Opportunities of Bitcoin Users. Retrieved from https://dx.doi.org/10.1145/3025453.3025886
Tapscott, D., & Tapscott, A. (2016). Blockchain Revolution: How the Technology Behind Bitcoin Is Changing Money, Business, and the World. Penguin.
Wilck, J. H., Lynch, D., & Kauffmann, P. (2014). Bitcoin: A Pedagogical Guide for the College Classroom. Retrieved from https://dx.doi.org/10.2139/ssrn.2436823
Zappia, C., Chen, Y., Pavone, P., & Pisani, M. (2018). Bitcoin and the Blockchain as Possible Corporate Governance Tools: Strengths and Weaknesses. Retrieved from https://dx.doi.org/10.2139/ssrn.3180606
-
 @ 01ae1e8b:f27c592f
2023-08-14 17:58:53
@ 01ae1e8b:f27c592f
2023-08-14 17:58:53O Flamengo e a Igreja explicam ou evidenciam todos os paradoxos referentes à vida operária. Quem não for tão crentóide ou rubro-negróide fanáticos, por favor, usem o mínimo da inteligência sobrada em vocês para entender estas duas instituições nacionais.
