-
 @ 92294577:49af776d
2023-08-16 04:10:10
@ 92294577:49af776d
2023-08-16 04:10:10Blockstream Finance, our financial division, continues to pioneer forward-thinking financial products, laying the foundation for Bitcoin-based capital markets. Building on the success of the Blockstream Mining Note (BMN), which secured $50M over 2021 and 2022, we have partnered with Luxembourg's STOKR—a premier marketplace for digital securities—to unveil our next Bitcoin-focused investment vehicle: the Blockstream ASIC (BASIC) Note.
The BASIC Note is a bitcoin-denominated vehicle that provides qualified investors an opportunity to capitalize on the potential upside of historically-low ASIC (application specific integrated circuits; purpose-built machines used to mine bitcoin) prices.
The Thesis
In previous Bitcoin cycles, bitcoin and ASIC market prices have been closely correlated. During bear markets, ASIC prices (on a price per terahash basis) often fall below bitcoin's value, while in bull markets, they tend to surpass it, indicating a potential upside when denominated in BTC.
https://cdn.nostr.build/i/cdbd6fdbcafab703344d067edb39ade5fbb4965e3817a2fd0792ecbe1ffbea4b.png Note ASICs pricing 25-38 J/TH is less energy efficient vs ASICs under 25 J/TH.
As ASIC prices show promising signs of recovery, anchored by the impending Bitcoin halving in 2024 and favorable market supply-demand dynamics, the BASIC Note strategy will leverage Blockstream's unique positioning and track record in the Bitcoin mining sector. We aim to raise investor capital, acquire and store unused ASICs in North America, and then strategically offload them into the market upon price resurgence.
While bitcoin price has risen substantially in 2023, ASIC prices have remained depressed (on a price per terahash basis). This is attributed to an oversupply of less energy-efficient miners, a need for more hosting capacity in the market, and higher energy costs, among other factors.
We expect this ASIC price trend to reverse in the near-to-mid term. As energy and credit markets bounce back, and as both large public and private miners bring new capacity online and refresh their fleets in preparation for the 2024 halving, we anticipate this surplus of miners to decline.
The Structure
The BASIC Note is a bitcoin basis investment opportunity. We anticipate that most investors will invest using bitcoin, seeking a bitcoin-on-bitcoin return.
The note has a novel structure designed with the Bitcoin investor in mind. Unlike many crypto hedge funds that charge carried interest on the mere passive appreciation of bitcoin price, the BASIC Note's carry fee is discretionary and levied only when the fund outperforms bitcoin. In other words, the carry is only for the value added beyond the natural bitcoin price appreciation. By eliminating these unnecessary fees, we can encourage investors to HODL their bitcoin, benefiting from its passive growth.
We view the BASIC Note as a source of liquidity for miners operating in the market today. These miners can either sell their inventory outright, or they can sell their inventory and reinvest in the BASIC Note. By choosing the latter, they can transform their hard assets into a more dynamic investment with a tradeable note, allotting them more agility in adjusting their market position.
The Expertise
Blockstream has continuously been a leader in Bitcoin mining, from our historical connection to the proof-of-work algorithm to running one of North America's largest vertically-integrated mining operations.
This wealth of experience has given us unique insight into the market and fostered strong relationships throughout the Bitcoin mining value chain, including key ASIC producers and brokers.
Beyond mining, we are also pioneers in Bitcoin technology. We are the technical providers for the Liquid Network and the main contributors to Core Lightning, two of the most well-known Bitcoin layer-2 solutions. We also have a deep understanding of Bitcoin through our software and hardware wallet offerings and operate the Blockstream Satellite network, which provides continuous, free broadcasts of the Bitcoin blockchain worldwide.
The BASIC Note builds on this mining legacy and integrates many areas of Blockstream's expertise across the Bitcoin technology space.
https://cdn.nostr.build/i/aa05cd0d3a89204d463125afd028cd08c3809f366ee519271780c28823ead407.png The Blockstream value chain in mining and adjacent Bitcoin technology sectors.
The Offering
The first series of the BASIC Note (BSIC1) is confirmed to go on sale August 23, 2023 on STOKR with an adjustable 24-month tenor. The offering is open to qualified investors with a minimum investment of USD $115,000 or the equivalent in bitcoin (BTC), Liquid Bitcoin (L-BTC), or Tether (USDt). Although there is a minimum initial investment, notes can be transferred in OTC sales or traded on secondary markets, such as SideSwap, down to a denomination of 0.01 (USD $1,150).
Subsequent series are expected to be issued periodically over the coming months, subject to market pricing.
For further information, visit the official STOKR listing or reach out to us on the Blockstream Finance Telegram.
The information above has been prepared solely for informational purposes only. It is not an offer to buy or sell or a solicitation of an offer to buy or sell any securities. Full terms and conditions are available on STOKR.
We will never reach out directly to investors through social media or instant messaging. If you receive any messages from someone claiming to be from Blockstream and offering mining investments, report them to us through the Blockstream Scam DB.
-
 @ 6efb74e6:41285536
2023-08-14 12:12:48
@ 6efb74e6:41285536
2023-08-14 12:12:48Shawarma is typically made from lamb or chicken that has been marinated, cut into thin strips, and then placed on a rotisserie spit. It is what you would typically see in any number of kabab shops around the world. Originating in the Ottoman Empire it is a popular street food in the middle east.
This recipe is perhaps not a classic version, as it has been tweaked by me, none the less it is delicious. I have used it for lamb and chicken, but a sturdy fish (like mackerel) would hold up to the strong flavor in the marinade. It could be used for a beef roast too!
The marinade will be enough for a 2-3 kg lamb leg roast with a little marinade to spare.
proofofwork: 20 minutes (recommended marinade time overnight)
YIELD: 1 1/2 cups of marinade
INGREDIENTS 2 Tblsp black peppercorns 5 ea cloves ½ tsp cardamom pods ½ tsp fenugreek seeds 1 Tblsp fennel seeds 1 Tblsp cumin seeds 1 ea star anise ½ ea cinnamon stick ½ tsp nutmeg grated ¼ tsp ground ginger 1 Tblsp smoked paprika 1 Tblsp sumac ¾ Tblsp sea salt 25g ginger, fresh grated 3 ea garlic cloves crushed 40g coriander chopped- stems & leaves 60ml lemon juice, fresh 120ml olive oil 1 lamb leg (about 2.5-3 kg bone in)
METHOD -Put peppercorns, cloves, cardamom, fenugreek, fennel, cumin, star anise & cinnamon in a cast iron pan & dry roast on medium heat for a minute or 2 until the spices begin to pop & release their aromas. TAKE CARE NOT TO BURN THEM! -Add the ground spices, nutmeg, ginger & paprika, toss for a few more seconds, just to heat them, then transfer to a spice grinder. -Process the spices to a uniform powder, I use an electric coffee grinder or you can go old school with a mortar and pestle. -Transfer to a medium bowl & stir in all the remaining ingredients (except the lamb) -Use a small knife to score through the leg of the lamb in a few places making 1.5cm deep slits through the fat & meat to allow the marinade to seep in. -Place in a large roasting tin & rub the marinade all over the lamb; use your hands to massage the meat well. -Cover the tin with foil & leave aside for at least a couple of hours or preferably chill overnight. -Roast the lamb at 200C for about 1 hour and 15 minutes. Probe with a thermometer and check the internal temperature. 54-60C for a pink centre. -Rest the lamb for a good 20 mins.
enjoy #chefstr #foodstr #yumstr #grownostr #yumstr
-
 @ 92294577:49af776d
2023-08-14 02:47:22
@ 92294577:49af776d
2023-08-14 02:47:22My last post about Simplicity touched on the language’s type system, and defined a Simplicity program as a Simplicity expression that maps an empty input to an empty output. We introduced the idea of assertions, which allow a program to abort, and witnesses, which allow programmers to inject input data into Simplicity programs at exactly the places that it’s needed. Together, this means that programs can have nontrivial behavior, even though nominally they have neither inputs nor outputs.
We also confronted the complexity of fully specifying even simple mathematical functions in Simplicity. One tool we used to reduce the complexity is that of jets, which provide optimized implementations of specific Simplicity expressions. This is a useful optimization for blockchain validators, but it also provides value to the Simplicity programmer by encapsulating potentially-complex functionality in a single jet, which can be treated as a black box.
In fact, every Simplicity expression is uniquely identifiable, by an object called its identity Merkle root (IMR). The IMR of a node is computed by hashing its source and target types, its combinator, and its children (if any). Using IMRs, we can uniquely identify any expression, and thereby treat it as a black box, even if we don't have an optimized jet to replace it.
Bit-Flipping, Revisited
At the beginning of the last post, we introduced the following code, which flips a single bit:
``` bit0 := injl unit : 1 * 1 -> 2 -- imr 31059b22... bit1 := injr unit : 1 * 1 -> 2 -- imr 9864ae9d...
padR := pair iden unit : 2 -> 2 * 1 -- imr 457121c2... bitflip := case bit1 bit0 : 2 * 1 -> 2 -- imr 7d5ff8d0... main := comp padR bitflip : 2 -> 2 -- imr a6ecc3dd... ```
As we can see from type ascription on the last line, this expression takes a single bit (the “2” type, so named because it has two possible values) and outputs a single bit. In this listing, we have also computed the IMR of each expression. In the future, whenever we see a Simplicity expression whose IMR matches one of these values, no matter how complex or obfuscated it appears to be, we will know exactly what we are looking at.
But recall that, to have a Simplicity program, we need our main expression to have type 1->1. Rather than taking an input value, we will use witness nodes, and rather than having an output value, we will simply assert that any intermediate values have the properties we expect.
As an example of this, let's tweak our expression to get a program that asserts that a witness bit is 0. We'll do this by taking a witness bit, flipping it, then passing to the jet_verify jet:
``` witbit := witness : 1 -> 2 -- imr ???
-- Assume we have the above expression, with the name bitflip. -- Notice that its IMR is the same as above.
bitflip :: 2 -> 2 -- imr a6ecc3dd... zerovfy := comp bitflip jet_verify : 2 -> 1 -- imr b3bca637...
main := comp witbit zerovfy : 1 -> 1 -- imr ??? ```
Here we have an interesting observation. The IMR of a witness node is computed based on the witness value, but when writing a program, we do not yet know what the witness value will be. This means that we do not know the IMR, and we cannot treat the expression as a black box. The same applies to
main, which depends on thewitnessnode, and any future expressions that might depend onmain.The same considerations apply to disconnected expressions. When we use the disconnect combinator, we can have entire expressions, not just values, which aren't yet determined. We will talk about disconnect in a later post.
IMRs and CMRs
Our lack of IMRs makes a certain amount of sense: if an expression depends on data, which we do not have available, it is not possible to precisely specify it. On the other hand, we actually do know a fair bit about the program under consideration: we know that it is a
compcombinator whose children are awitnessand anothercompcombinator, respectively, and so on. In this case, we even know the exact source and target types of all nodes.In other words, we have fully defined our program, up to witness data and disconnected expressions that we do not intend to populate until later. We have defined the parts of our program we need to generate addresses and receive coins, but left some parts undefined until we are ready to spend them.
In Bitcoin Script, we have this same distinction between commitment time and redemption time. At commitment time, we choose what public keys to use, and only at redemption time, do we produce signatures with those keys. For historical reasons, Bitcoin Scripts are committed to by taking their hash and embedding this hash in another Script, sometimes called a scriptPubKey but more commonly known as an address.
Taproot generalizes this hash to be the root of a Merkle tree, allowing the same address to commit to multiple scripts, only one of which is revealed at spending time.
In Simplicity we take this a step further, treating our entire program as a Merkle tree. To do so, we define a second hash on each node, the commitment Merkle root (CMR). Unlike the IMR, the CMR does not commit to witness data, disconnected expressions, or types. It only commits to the structure of the program.
When embedding Simplicity programs in the blockchain, we replace the leaves of a Taproot tree, which normally would be Scripts, with the CMRs of Simplicity programs.
We can write out the CMR of each node in our bit-flipping program:
``` witbit := witness : 1 -> 2 -- cmr bf12681a... bitflip : 2 -> 2 -- cmr 8f214cce... zerovfy := comp bitflip jet_verify : 2 -> 1 -- cmr ab61cadb...
main := comp witbit zerovfy : 1 -> 1 -- cmr 58655557... ```
Every node, including witness and disconnect nodes, has a CMR. And every witness node, in every program, has the same CMR.
Naming and Sharing
In our Simplicity programs so far, we have written a series of named expressions, referring to each expression in a later expression, by name. Naturally, we are not limited to referring to names only once. This concept is essential to using Simplicity. We refer to name reuse, or more generally, collapsing multiple copies of the same expression into one, as sharing.
On the blockchain, there is a consensus rule that Simplicity expressions encoded in transactions be fully shared. That is, it is actually illegal to encode two nodes that have the same IMR. This helps ensure that programs are encoded in the most compact way, and that their encoding is canonical; that is, there is no potential for malleability. But this rule exploits the fact that programs never appear on-chain except when all witness nodes are populated, and therefore every node has an IMR.
At commitment time, when we are defining programs and computing addresses, the story is not so simple. Let's explore the subtleties that come from sharing before our IMRs are set in stone.
Essentially, every time a name is used, it must refer to a node with the same IMR. What makes this surprising is that, as we have seen, the code we write is only actually sufficient to define a node's CMR, not its IMR.
Let's see a simple example of where this might lead to trouble. Let's take a look at our original bit-flipping program, and let's say that we are tired of writing the entire word
unitout. So we define an aliasu := unit -- cmr 62274a89...and try to use it in our program:
``` bit0 := injl u : 1 * 1 -> 2 -- cmr bd0cce93... bit1 := injr u : 1 * 1 -> 2 -- cmr 79a70c6a...
padR := pair iden u : 2 -> 2 * 1 -- cmr 7751cd1c... bitflip := case bit1 bit0 : 2 * 1 -> 2 -- cmr 1d4aa8f4... main := comp padR bitflip : 2 -> 2 -- cmr 8f214cce... ```
But when we try to parse this to get an address, we get a type error defining padR! The reason is that while the type of the unit combinator in bit0 and bit1 is 1 * 1 -> 1, the unit combinator in padR has type 2 -> 1. The source types of unit combinators are completely uninteresting details of a Simplicity program, but it's nonetheless essential[1] that we are consistent about them.
The fix here is simple: we can reuse the name
uinbit0andbit1but forpadRwe need a freshunitcombinator.So far, so good; this sort of problem is familiar to any programmer who works with strongly typed languages, especially ones that support type inference, so that the types of variables are not immediately obvious. But with Simplicity, there is also a more interesting problem we might stumble over.
Consider the following program, which checks whether the user has found a SHA256 "fixed point", i.e., an input whose SHA256 hash is equal to itself. Because SHA256 is a cryptographic hash function, this should be impossible, so coins stored at this program should be unspendable.
``` -- Witnesses -- CMR: bf12681a... -- IMR: [none] wit_input := witness
-- All jets have source type 1; but to use the
paircombinator -- we want one with source type 2^256. To get this, we compose -- it with unit. -- CMR: a520761f… -- IMR: 21182050... sha256_init : 2^256 -> _ sha256_init := comp unit jet_sha_256_ctx_8_init-- Using this, we can write a self-contained "take 32 bytes and -- compute their sha2 hash" function. -- IMR: 8e341445... -- CMR: bf70ec35... sha256 : 2^256 -> 2^256 sha256 := comp comp pair sha256_init iden jet_sha_256_ctx_8_add_32 jet_sha_256_ctx_8_finalize
-- Finally, our main function takes an input witness, hashes it, -- and compares the input and output to check for a fixpoint. -- CMR: 9b3b900a... -- IMR: [none] main := comp comp pair (comp wit_input sha256) wit_input jet_eq_256 jet_verify ```
Here we have reused the name
wit_input. Our rule is that we can only reuse names when all uses have the same IMR, but here we don't even have an IMR to compare. Will this be a problem?Well, consider this alternate version of
main, which takes a second witness,wit_output, and compares this to the hash ofwit_input. This newmainis trivial to satisfy: provide anything at all forwit_inputand provide its SHA256 hash forwit_output.``` -- Witnesses -- CMR: bf12681a... -- IMR: [none] wit_input := witness wit_output := witness
[...rest of program elided...]-- CMR: 9b3b900a... main := comp comp pair (comp wit_input sha256) wit_output jet_eq_256 jet_verify ```
The important thing to notice here is that these two programs, our fixed-point-checking program and the trivially-solvable program, have the same CMR and, therefore, the same Bitcoin address. This is because Simplicity does not commit to sharing. This subtle, but crucial, fact, means that our fixed-point program, rather than being impossible to spend coins from, is trivial.
Fortunately, Simplicity prevents us from making this mistake. If we attempt to assemble our original version of the program, we get the following error:
Error: witness/disconnect node `wit_input` was accessible by two distinct paths from the same rootWhat this is telling us, in somewhat jargony language, is that we are simply not allowed to share witness or disconnect nodes, or any expressions which refer to them. This is because such nodes, even when they have identical types and CMRs, may not end up the same.
At redemption time, when witness data and disconnected expressions are present, every node has an IMR and it is unambiguous whether nodes are the same. At that time, if two witnesses were present and had the same types and values, they would be shared. But this sharing depends on the particular values chosen for each witness node, which are not decided at commitment time, and therefore do not reflect anything about the actual structure of the program.
To fix our program, there are a couple of strategies that we could take. One thing we could do is to define two witness nodes, with different names, and use the
jet_eq_256jet to assert that they are both equal. This would work, but increase the complexity of code, making it harder to review or to extend. A more direct approach is to duplicate the output of a single witness node.We do this by pulling our check out of
maininto its own expression, whose input value is accessed by theidencombinator twice:``` -- IMR: 5ddb65c2... -- CMR: 198bfeb5... assert_fixpoint : 2^256 -> 1 assert_fixpoint := comp comp pair (comp iden sha256) iden jet_eq_256 jet_verify
-- CMR: ac8df50b... -- IMR: [none] main := comp wit_input assert_fixpoint ```
This program is accepted without error.
Conclusion
As with ordinary Taproot transactions, addresses are derived from commitments to programs, but the programs themselves are not revealed until spending time. Also, as with Taproot, in Simplicity, we reveal only those parts of the program that are actually used.
Bitcoin Script has a strict separation between program code and witness data, so the program revealed on-chain is the same as the program committed to in addresses (aside from pruning). Witness data is encoded separately and provided to the program code as input. Script does not have any notion of sharing, or of disconnected expressions, so functionality such as delegation is missing (and functionality such as loops are very inefficient to implement).
In Simplicity, we instead attach witness data directly to our programs, and when encoding programs, we insist that nodes are never repeated. This combination requires us to have a surprisingly subtle notion of "identity," which, when applied to text-encoded programs, allows us to reuse names in a mostly-natural way. But there are potential pitfalls here, which our tooling helps to avoid.
In our next post, we will explore pruning, which is the process by which unused nodes are not revealed, and its interactions with witnesses and the type system.
Until then, join the Simplicity discussions on GitHub to connect with the community, and follow us at @blksresearch on Twitter to stay updated with the latest Simplicity announcements.
[1]In theory, Simplicity could have supported polymorphic types, which would allow the same
unitcombinator to be used with different type signatures. But aside from increasing the complexity of using and analyzing the language, this would have increased the computational complexity of type inference, a task that must be done by all validators on all programs. -
 @ 5111a093:bc2ddc63
2023-08-13 14:33:19
@ 5111a093:bc2ddc63
2023-08-13 14:33:19Background image by Gerd Altmann from Pixabay
Building a Lightning Node
Hello Bitcoiners A while ago I built a lightning node including a Bitcoin node which is mandatory for the lightning node. You don't need much technical know-how to build this. When you worked with computers and know how to set up an operating system, you will be able to set up a lightning node too. You can also buy a complete ready-to-go node, but where is the fun? It's also possible to run it on a Linux-based system but I went for the Raspberry solution.
Things you need:

I bought a one-time used Raspberry Pi on eBay including the power supply and case. The storage drive, drive enclosure, and the 16GB microSD I got from Amazon. I had a cable at home. I just describe the way I did it and what I used. You will find other ways on the internet. | Raspberry Pi 4 | harddrive with case | | --- | --- | |https://images.ecency.com/DQmS6UKtSQKNA4VyFroTF1xgu4efq1qdxbrbzQh6FckJdE9/1691928173519.jpg | https://images.ecency.com/DQmdkhzTyKMMzhWTcFqiwVHyY74qK2hEHzsDcvG2aRKndpw/1691928173507.jpg |
Raspberry Pi opened

The installation process is easy. You get umbrelOS from the website umbrel.com. There is also a step-by-step guide. Download the umbrelOS file and the flash software to flash the umbrelOS on the microSD card. You do this on your computer with a card reader. The flashing process takes a while but not too long. After the flash is finished, you insert the microSD card into your Raspberry Pi. Connect the SSD and connect your ethernet cable with your router and your Raspberry Pi. Connect the power supply and turn your Raspberry Pi on. After ~5min the installation should be ready. Go to your browser and enter umbrel.local


You will probably see another start screen the first time and you have to choose a username and a password.

The umbrelOS is pretty much like a phone and works with apps. Easy to use! Check the app store and look for the Bitcoin node and install it. Get a coffee now or go for a walk. It will take several hours until the blockchain is completely synced. You can install the lightning node app too but it needs the Bitcoin node fully synced first to be able to work. Look at the size of the blockchain. It's huge!

After syncing is complete open the lightning node app. Here you have to deposit some BTC. I think it was around $300 in BTC which is needed. You need to open channels to other nodes later and there is a minimum requirement of BTC in your wallet. I think it was 0.01 BTC at least. Click deposit and scan the QR code with your favorite Bitcoin wallet.
Now you can open channels to other users and support the lightning network. Yeah, I know and I've heard it before.. It's not a network. There are some websites with lists of channels but I found another app in the store which shows your node to others and you can start a triangle (3 nodes) or pentagon (5 nodes) capacity. I really like this idea. With the triangle, the first node opens a channel to the second node. The second node opens a channel to the 3rd node and the 3rd node opens a channel to the first node. You'll find lightningnetwork+ in your umbrel app store.

It's called a liquidity swap. Check the requirements first before you open for application.


At the end a little warning. When you are in your lightning node app, you will see a difference between the BTC wallet and lightning wallet. Don't send BTC from the main blockchain to the lightning wallet or the other way around. It should not work but just in case.
Any questions? Leave a comment!
This is a cross-post from my Hive account

 Images and screenshots are from me, umbrel.com, my node and zbd
Images and screenshots are from me, umbrel.com, my node and zbd -
 @ 3129509e:c846f506
2023-08-13 13:15:31
@ 3129509e:c846f506
2023-08-13 13:15:31Splitstr
An application to split bills and track shared expenses in a group, with the ability to “settle-up” with lightning invoices.
The Splitwise app on iOS and android is a great example, but lacks lightning and Nostr.
https://www.splitwise.com
-
 @ ec42c765:328c0600
2023-08-13 10:54:21
@ ec42c765:328c0600
2023-08-13 10:54:21[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
-
 @ 7cc328a0:2a247c0e
2023-08-03 00:40:02
@ 7cc328a0:2a247c0e
2023-08-03 00:40:02I built a really cool little temperature and air quality sensor that reports data to particle.io events and from there into influxdb cloud.
With Free Dashboards!!
Yes I mean free as free can get. Particle.io, free (to 100 devices). InfluxDB cloud, free (to (x) amount of stats). We're not talking about a lot of stats here, but after many hours of research for a free dashboard solution this was the absolute best!
InfluxDB cloud dashboards look really nice as well.
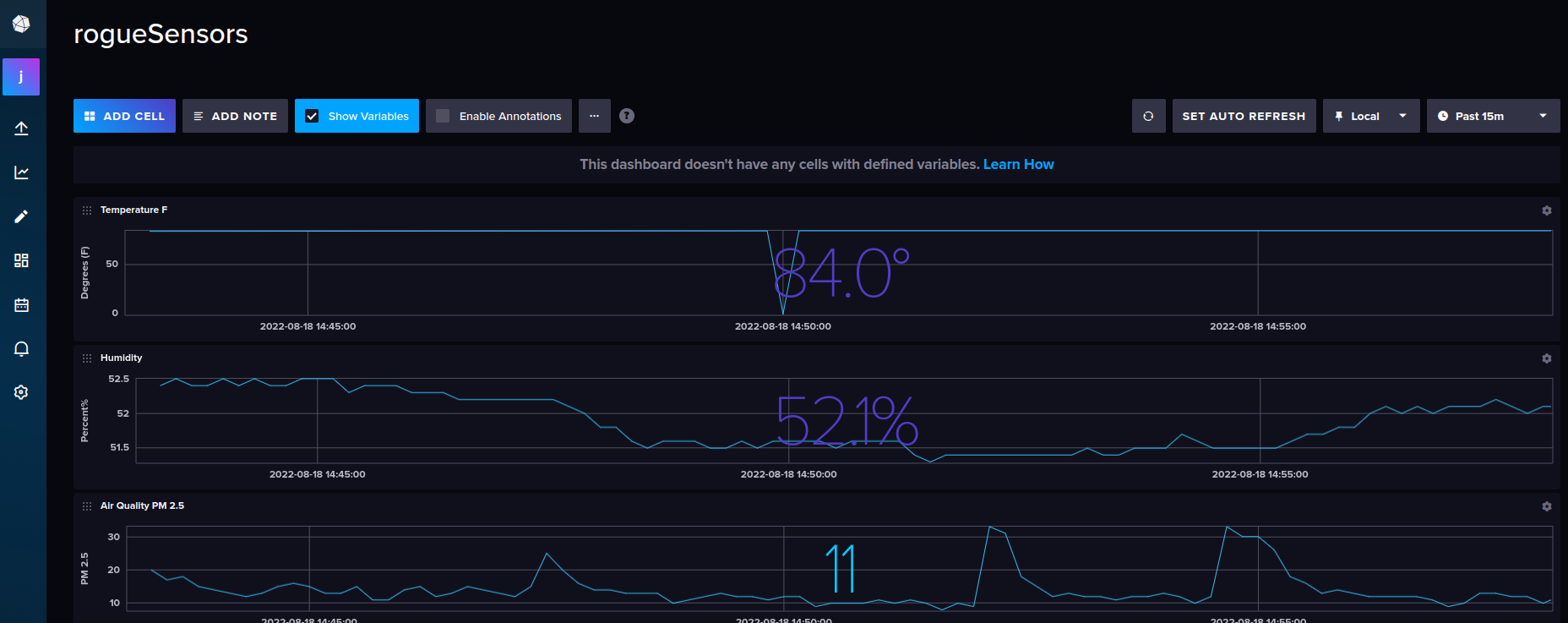
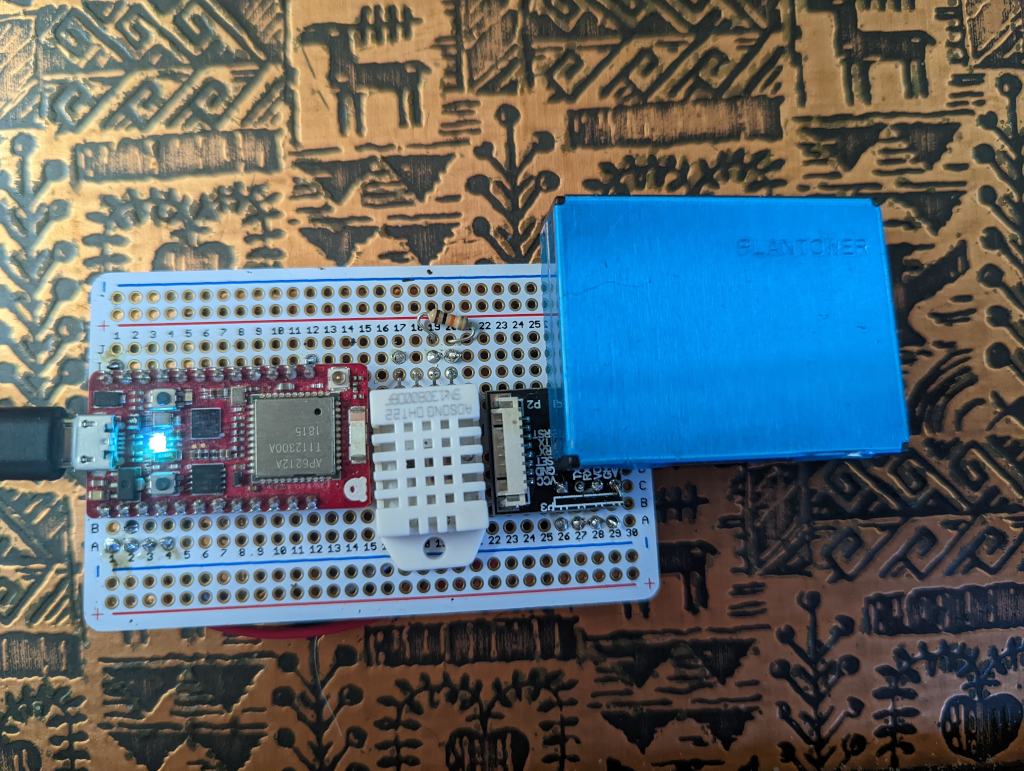
Build Components
- RedBear Duo github
Note, particle.io has since aquired RedBear labs and the Duo is old, yet still available in some places. You may also want to try particle devices like Argon instead of a redbear.
- DHT22 Temperature/Humidity sensor adafruit
- PM2.5 Air Quality Sensor and Breadboard Adapter Kit - PMS5003/PMS7003 adafruit
Note, I used a slightly different adapter, and it was lame to have to order it once I realized the PMS7003 I ordered did not come with an adaptor! The adafruit link above should get you hooked up. These air quality sensors come in different flavors just make sure you have a breakout board along with it when you order!
Software
Steps
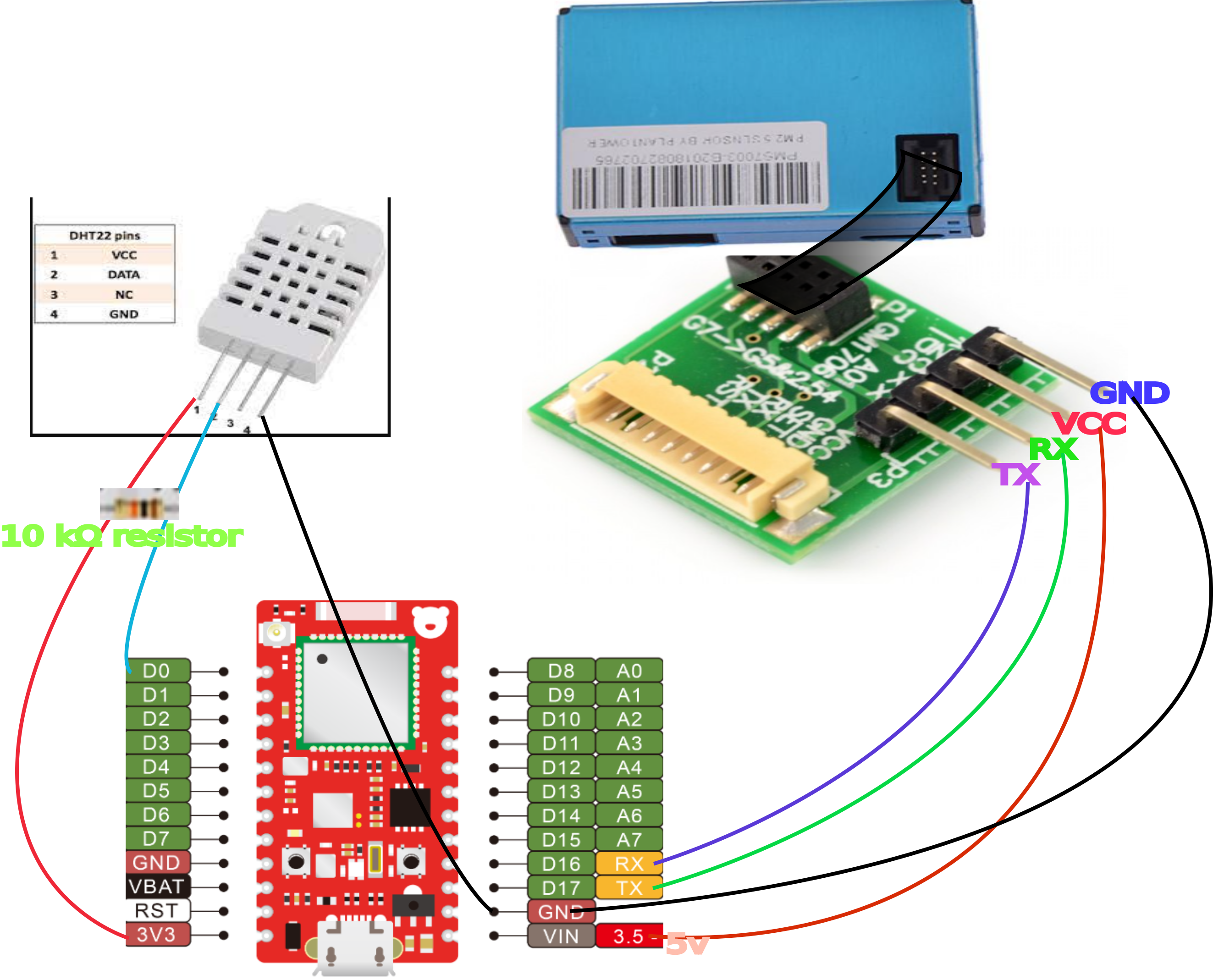
The Hardware wiring diagram
Plug in your device and connect it to particle.io
I used the following guide for the Redbear DUO here
Coding the application
- Go to console.particle.io, open the IDE by clicking the icon (bottom left < >)
- Create a new application.
- Click the "Libraries" icon on the bottom left of the screen.
- In the "Libraries" search enter "PMS7003-Particle-Sensor-Serial" and import it into the project.
- Click "Libraries" again, and search for "Adafruit_DHT_Particle" and import it into the project.
Paste this code into your app: ```arduino // This #include statement was automatically added by the Particle IDE.
include
// This #include statement was automatically added by the Particle IDE.
include
PMS7003Serial
pms7003(Serial1, D0); define DHTPIN D0 // what pin we're connected to
// Here we define the type of sensor used
define DHTTYPE DHT22 // DHT11 or DHT22
DHT dht(DHTPIN, DHTTYPE);
void setup() { //Serial.begin(); dht.begin();
}
unsigned long last = 0; unsigned long last_pm_reading = 0;
void loop() {
unsigned long now = millis();
// check every time to see if there is data if (pms7003.Read()) { last_pm_reading = now; }
if ((now - last) > 10000) { float f = dht.getTempFarenheit(); float h = dht.getHumidity(); Particle.publish("TempDegreesF", String(f)); Particle.publish("PercentHumidity", String(h)); // Let us be generous. Active state the device // reports at least every 2.3 seconds. if ((now - last_pm_reading) > 10000) { Particle.publish("No reading for at least 10 seconds!"); } else { Particle.publish("pm1", String(pms7003.GetData(pms7003.pm1_0))); Particle.publish("pm2_5",String(pms7003.GetData(pms7003.pm2_5))); Particle.publish("pm10",String(pms7003.GetData(pms7003.pm10))); // I didn't use these but they're there if you want them in the future. /Serial.println("um_3:" + String(pms7003.GetData(pms7003.count0_3um))); Serial.println("um_5:" + String(pms7003.GetData(pms7003.count0_5um))); Serial.println("um1:" + String(pms7003.GetData(pms7003.count1um))); Serial.println("um2_5:" + String(pms7003.GetData(pms7003.count2_5um))); Serial.println("um5:" + String(pms7003.GetData(pms7003.count5um))); Serial.println("um10:" + String(pms7003.GetData(pms7003.count10um))); / } last = now; } } ```
Flash the application to the device
You should see events coming into the particle.io console
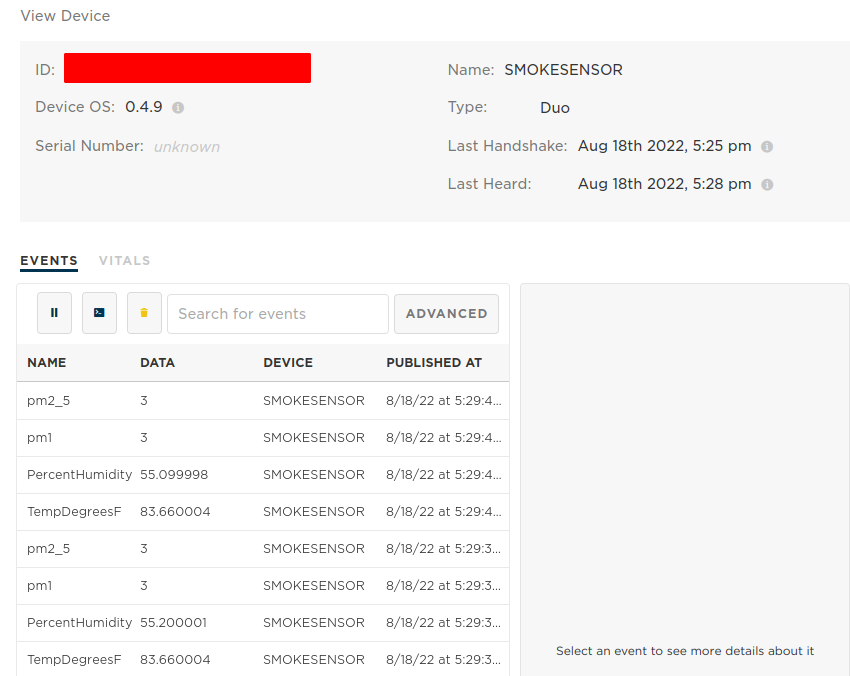
Now we're ready to setup InfluxDB
- Create a new bucket called "sensors" (or whatever you like)
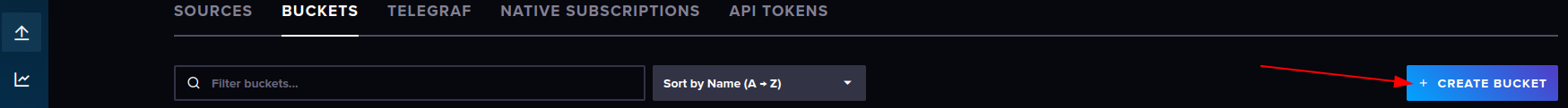
- Keep this window open or copy these settings, we need them to setup particle.io webhooks.
- Open organization settings
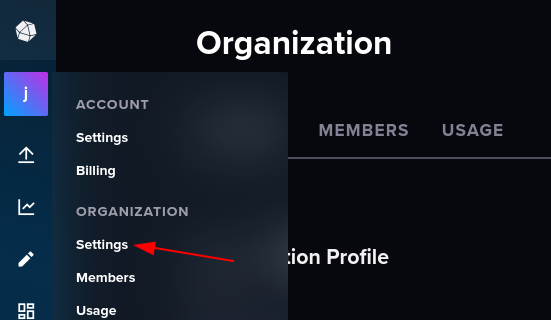
- Copy the info for ClusterURL and OrganizationID
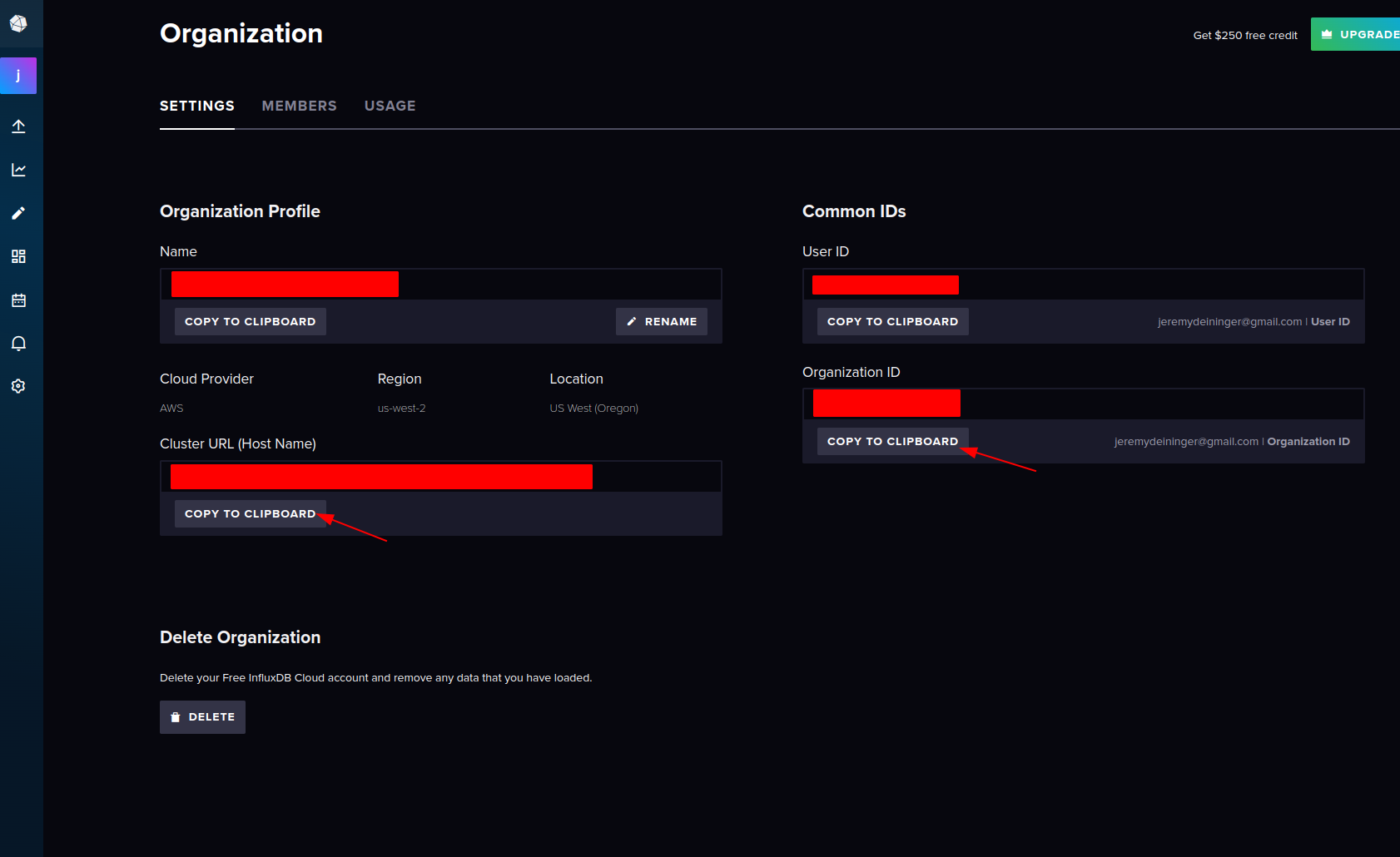
- Go to tokens and generate a new API token (and save it for the next step!)
Go back to particle.io console "Integrations"
-
Create new WebHook Integration Setting | Value --------|------ Event Name | pm2_5 URL | https://YourClusterURL/api/v2/write?org=YourOrganizationID&bucket=sensors&precision=s Request Type | POST Request Format | Custom Body Device | Any Status | Enabled
-
Expand the Advanced Settings!
Setting | Value --------|------|- Custom Request Body | envSensors,sensorID={{{PARTICLE_DEVICE_ID}}} {{{PARTICLE_EVENT_NAME}}}={{{PARTICLE_EVENT_VALUE}}} HTTP HEADERS (two fields) | Authorization | Token YOUR-API-TOKEN * After you're done creating the webhook it should look like this ->
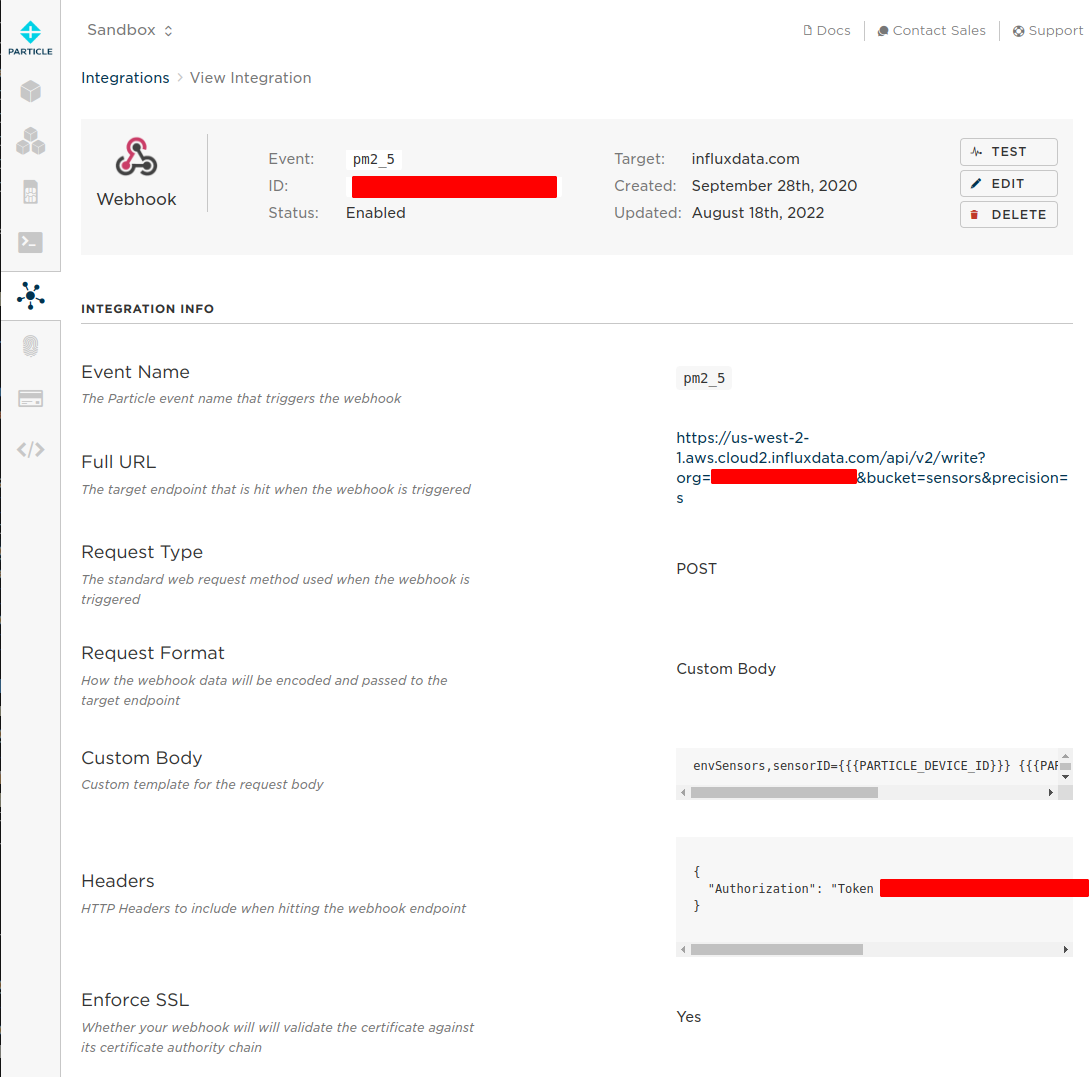 * While viewing the webhook we should start to see the webhook logs below ->
* While viewing the webhook we should start to see the webhook logs below ->
 You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)
You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)Now we can build an influxDB dashboard!
- You can create a new dashboard and play around. For example: create a new cell.
- Use QUERY BUILDER to point-and-click the sensor data.
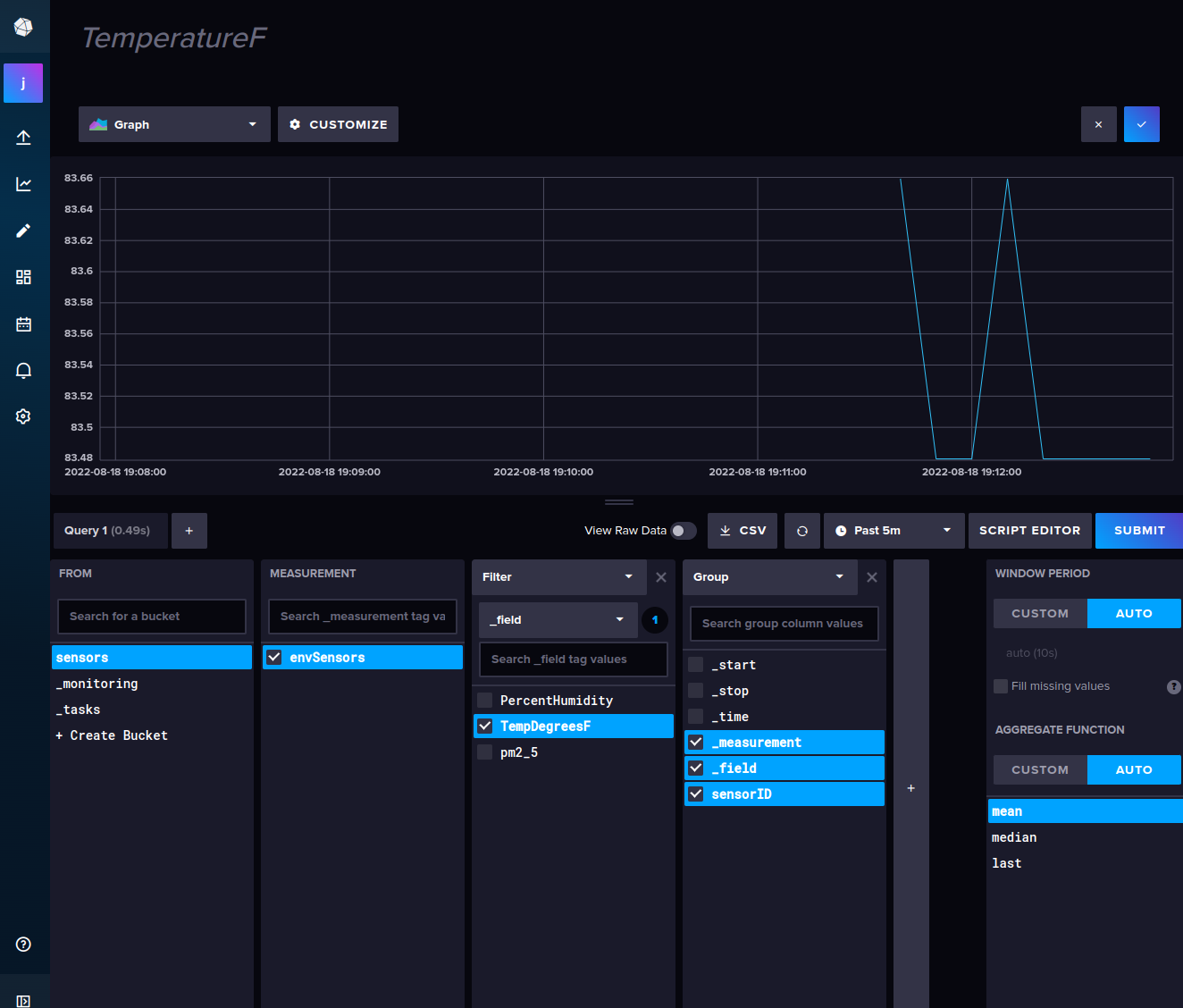
Done! Enjoy the free charts!
-
 @ 7cc328a0:2a247c0e
2023-08-02 22:57:59
@ 7cc328a0:2a247c0e
2023-08-02 22:57:59Here is an nginx config for setting up a streaming server that serves HLS. This is what you need if you want to stream from your own streaming server and be viewed on zap.stream, amethyst or other nostr clients that support streaming.
You can connect to it using RTMP -or RMTPS from OBS.
This is an 'advanced guide' it assumes all you need is the nginx.conf and that you can install nginx and use certbot to create the certificates.
I've tested this config on a t3.micro (very small) amazon server and it works great for streaming to my friens.
All you have to do is install nginx, point a DNS record to the server, and use certbot to get some SSL certificates.
nginx.conf ```nginx worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf;
events { worker_connections 768; # multi_accept on; }
http {
map $sent_http_content_type $expires { default 1d; application/vnd.apple.mpegurl epoch; }
server { allow all; sendfile off; tcp_nopush on;
aio on;
directio 512; include mime.types; default_type application/octet-stream; access_log /var/log/nginx/access.log;index test.html;
location / { expires $expires; # Disable cache add_header Cache-Control no-cache; # CORS setup add_header 'Access-Control-Allow-Origin' '*' always; add_header 'Access-Control-Expose-Headers' 'Content-Length'; # allow CORS preflight requests if ($request_method = 'OPTIONS') { add_header 'Access-Control-Allow-Origin' '*'; add_header 'Access-Control-Max-Age' 1728000; add_header 'Content-Type' 'text/plain charset=UTF-8'; add_header 'Content-Length' 0; return 204; } types { application/dash+xml mpd; application/vnd.apple.mpegurl m3u8; video/mp2t ts; text/html html; } root /tmp/hls; } listen 443 ssl; server_name mysite.com; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; # managed by Certbot} include /etc/nginx/sites-enabled/.;
}
stream { upstream backend { server 127.0.0.1:1935; }
server { listen 1936 ssl; proxy_pass backend; proxy_protocol on; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; }}
rtmp { server { listen 1935 proxy_protocol; chunk_size 4000;
application live { live on; hls on; hls_path /tmp/hls; # Use HLS encryption hls_keys on; # Store auto-generated keys in this location rather than hls_path hls_key_path /tmp/hls/keys; # Prepend key url with this value hls_key_url /keys/; # Change HLS key every 2 fragments hls_fragments_per_key 100; #hls_playlist_length 5s; #hls_fragment 2s; } }} ```
here is an index.html page that displays a video player embedded.
```html
```
As you can see, the URL you would give to zap.stream to setup the stream is https://yoursite/test2.m3u8
You can test the stream is online by visiting mysite/index.html and hitting play.
Hope this helps! At the very least, now I won't lose these precious working configs. PV.
-
 @ 18e3af1e:1d42e5df
2023-08-13 02:56:19
@ 18e3af1e:1d42e5df
2023-08-13 02:56:19Communities are formed not just by one person's effort, but by the work of dozens, hundreds, or even thousands of people. As a species, our unique talents have taught us that being skilled in one thing doesn't mean we'll go hungry or be unprepared for challenges. In fact, mastering just one skill can lead to the creation of entire civilizations.
Allowing ourselves to focus on learning, mastering, and excelling in our activities within a limited timeframe has propelled us into new realms. This shift has been so dramatic that looking back in time (for many of us) might feel like watching a mix of comedy and drama.
In our current world, where individualism often rules the physical realm, the spirit of community builders lives on in the digital domain.
The Evolution of Building
Throughout history, building has evolved from simple shelters to grand architectural marvels and cutting-edge structures. Early humans fashioned basic shelters using materials found in nature. With the growth of civilizations, permanent structures emerged – like pyramids and temples – reflecting social order and religious beliefs. Ancient Rome added engineering innovations with aqueducts and arches.
The Middle Ages saw the fusion of spirituality and craftsmanship in fortresses and Gothic cathedrals. The Renaissance embraced harmony and symmetry in famous palaces and buildings. The Industrial Revolution transformed construction with steel and concrete, enabling iconic skyscrapers and bridges.
The 20th century brought skyscrapers and modernist designs that challenged both structure and aesthetics. Sustainability has taken center stage in the 21st century, pushing for advanced technologies like 3D printing and modular construction. The history of building showcases human creativity and adaptability, not just in terms of technical achievements, but also reflecting cultural values and aspirations.
Today, software and tech developers could be seen as the builders of the coming century. Just as builders of yore shaped our physical surroundings, these developers craft digital structures that shape our interactions, communication, and modern way of life.
As technology advances and society becomes more digital, their role becomes vital in solving various challenges through tech solutions.
Like ancient architects who needed a grasp of physics, aesthetics, and human needs to create functional and appealing structures, modern software developers must understand programming logic, user experience, cyber security, and innovation to design applications, systems, and platforms that are truly effective and useful.
Inspiring Individuals
Personal inspiration is a potent force for change that can deeply impact the collective mindset of a community or society. When someone shows passion, determination, and a positive vision, their influence reaches others emotionally and mentally. Here are a few ways individual inspiration affects the collective mindset:
People identify with someone else's struggles and triumphs, forming a sense of unity and community. This can spark stronger support and solidarity for specific causes or values. What's more, individual inspiration often leads to action. When individuals witness someone overcoming hurdles or achieving ambitious goals, it can ignite motivation in others to face their own challenges and work towards their aspirations. A single person's example can trigger a chain reaction of action in many more.
This inspiration can also have a ripple effect. When a passionate person shares their story or experiences, they inspire others, creating a chain of influence that spreads through social networks, communities, and even entire societies. This can have a wide-reaching impact on the collective mindset.
An inspiring individual holds the potential to profoundly influence the collective mindset by shifting perspectives, encouraging action, and fostering a sense of community and unity.
Communities: Origins, Beginnings, and Progress
Communities have been a fundamental part of the human experience throughout history. From the earliest days to modern times, communities have evolved and changed in response to needs, technological advancements, and cultural shifts. In the early days of humanity, our ancestors banded together in small communities to ensure survival. These groups, whether family units or tribes, shared resources and knowledge for hunting, gathering food, and protection from dangers. Cooperation and unity were crucial for survival.
With the rise of agriculture, communities grew into more permanent settlements. The ability to cultivate food enabled the formation of villages and towns, where people could establish roots and develop more complex relationships. This gave rise to specialized roles and artisan crafts.
Ancient civilizations like the Sumerians, Egyptians, Greeks, and Romans paved the way for cities and organized societies. Communities became hubs of trade, governance, and culture. They built monumental structures like temples and palaces that united people under shared beliefs and political systems.
During the Middle Ages, communities organized around feudal systems, with feudal lords ruling over local lands and people. Villages and fiefs maintained a degree of autonomy, focusing on agriculture and self-sufficiency.
The Industrial Revolution brought about significant change in community structures. Industrialization spurred urbanization, as many left rural areas to work in factories within cities.
In the modern era, communities have continued to evolve with technological advancements and the interconnectedness of the world. Social media and digital communication have linked people across the globe, giving rise to online virtual communities.
Bitcoin | Nostr and the Builder's Spark
As we've seen, a single individual's inspiration can ignite the spirits of many others, causing a chain reaction. This phenomenon isn't confined to the physical world; rather, it taps into our psychology. In fact, it extends further into the realm of ideas and spirituality.
Not long ago, we relied heavily on big corporations to build everything for us. We eagerly anticipated each new iteration of their products. Over time, we unwittingly became increasingly dependent on these corporations. They subtly encroached on our time, and in a way, even on our personality and identity.
Today, thanks to available alternatives and inspiring individuals, the opportunity exists to create something beyond the control of large corporations. This creation transcends not only the physical and digital realms, but also surpasses the individual contributions to the community. I'm referring, of course, to Nostr, and how Bitcoin's alignment of incentives plays a part.
Consider a couple of names as examples, illustrating how inspiring individuals can light a fire that spreads to touch every person within the community.
Figures like nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (among many others I could mention, though the article might turn into a list of names) have inspired other developers, content creators, and professionals of all sorts to contribute to this protocol. Even individuals like the recent case of nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks have found inspiration to learn programming within this framework.
nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
In simpler words, the spark of the builder is about inspiring one another, multiplying this inspiration for enhanced productivity, and consequently fostering the growth of a community.
Without Bitcoin and the Lightning Network, this vision would still be possible, but its effectiveness would be diminished since those behind efforts focused on content creation and development, among others, also need to sustain themselves.
Conclusion
The Builder's Spark is all about individual inspiration that sets the stage for collective action. From the evolution of construction to digital communities, the influence of an inspired individual can shape the present and future of communities around the world.
-
 @ 18e3af1e:1d42e5df
2023-08-13 02:40:19
@ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera.
Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría.
Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital.
La evolución de la construcción
A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos.
La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos.
El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones.
En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno.
A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos.
Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos.
Individuos que inspiran
La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva:
La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más.
La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva.
El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad.
Comunidades: origen, inicios y progreso.
Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia.
Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales.
Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos.
Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia.
La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades.
En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea.
Bitcoin | Nostr y la chispa del constructor
Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual.
Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad.
Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin.
Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad.
Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles.
nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
La chispa del constructor en palabras mas concisas es: Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.
Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer.
Conclusión
La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.
-
 @ c8df6ae8:22293a06
2023-08-13 00:57:19
@ c8df6ae8:22293a06
2023-08-13 00:57:19"Regulated stablecoins do not compete with bitcoin."
— Matt Odell
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers PayPal’s launch of a stablecoin pegged to the US dollar.
This week PayPal launched the PayPal stablecoin PYUSD pegged to the US dollar. It joins Tether USDT, Circle USDC, and Binance BUSD in the quest to extract wealth from unsuspected crypto enthusiasts.
All stablecoins are the same. They all run on top of Ethereum and therefore offer the same programmatic capabilities.
The only way that these companies differentiate themselves is by promising to be more trustworthy than the other ones. Because, and here is the crux of the matter:
PayPal, Tether, Circle and Binance are borrowing your money and you are implicitly deciding who is most likely to pay you back.
By the way, all these promises of programmatic benefits are hollow promises that depend on someone else building an app that uses their stablecoin and these programmatic capabilities to deliver something that is yet to be determined but that somehow will be of great value to you.
You can read about PYUSD here.
Stablecoins steal wealth from you
Why is PayPal doing this? The answer is here:
 When you buy one PYUSD, you’re giving $1 to PayPal and receiving in exchange a token that returns no interest to you and costs them nothing to issue.
When you buy one PYUSD, you’re giving $1 to PayPal and receiving in exchange a token that returns no interest to you and costs them nothing to issue.Congratulations! You’re lending money to PayPal at zero interest rate!
PayPal then turns around and buys $1 worth of US Treasury with a 5% interest rate.
You can buy US Treasuries yourself and pocket the 5% interest rate. But instead you give them the money, they pocket the 5% and you assume the risk of PayPal defaulting on its reserves.
They make the money and you take the counterparty risk. Now you know why PayPal just launched PYUSD.
Bitcoin trumps stablecoins
People are lured to stablecoins because they want to protect their savings from the theft that inflation represents. They are very popular in Argentina or Turkey, where access to real US dollars may be limited and stablecoins provide an easy way to convert the useless peso or lira into what is perceived as a more trusted currency.
But you’re being fooled because your wealth is also stolen from you when you store it in US dollars thanks to inflation and you’re assuming the counterparty risk of PayPal, Binance, Tether or Circle not being able to maintain the parity of 1 PYUSD = 1 USD.
There is only one crypto currency that is free from inflation theft and free from all counterparty risks: Bitcoin.
Once you’re ready to move your savings into sound money, choose Bitcoin. It’s the only sound money where you have full control. All other cryptocurrencies are scamming you in one way or another and transferring the risks from the founders of the cryptocurrency to you.
Notable notes
nostr:note13s00phgqsqnzxrq375djumwr4384p8t4selajwwj97lzcgtd3rvsym2cda
Recommendations
Maxibitcoiner
Fantastic account to learn about Bitcoin for Spanish speaking audiences.
You can follow him here.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. It's a very effective way to stay up to date with the industry.
Just this week he also covered PayPal’s PYUSD and reported how apparently PayPal has the option to freeze or wipeout your PYUSD funds unilaterally.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ c8df6ae8:22293a06
2023-08-13 00:40:36
@ c8df6ae8:22293a06
2023-08-13 00:40:36"The SEC told Coinbase that it views “every asset other than bitcoin” as a security and ordered the company to delist them from its website."
— Brian Armstrong, CEO of Coinbase
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue goes back to basics to explain why the SEC asked Coinbase to delist all the shitcoins.
The SEC is a closet maxi
Before filing its suit against Coinbase, the Securities and Exchange Commission (SEC) asked Coinbase to delist all cryptocurrencies from its exchange except for Bitcoin.
Bitcoin is money. Shitcoins are investments. — The SEC, sort of
The SEC is explicitly saying that Bitcoin is the only digital money out there.
Why only Bitcoin?
When you buy Bitcoin, you’re buying a commodity, just like gold or grain.
When you buy a shitcoin like Ethereum or Hex, you are buying a security, just like when you buy shares of a company.
What makes Bitcoin different?
The founder of Bitcoin, Satoshi Nakamoto, did not assign himself a large share of Bitcoin before others could mine it. He did not assign a large share of Bitcoin to venture capital firms investing in him and his team either.
Instead, he launched the project and invited everyone else to join him. Anyone in the world who was paying attention was able to join the network and mine Bitcoin with the same probability of success as Satoshi.
The founder of Ethereum, the blockchain that underpins most shitcoins, did the opposite. Ethereum is like a startup. Both its founders and the investors that back it are hoping to make big money by selling you Eth tokens.
The founder of Bitcoin is anonymous. We do not know who he is. He has not transacted with his Bitcoin since he disappeared in 2011. For all we know he could be dead. He is not setting directions or acting as the referee in disputes about what Bitcoin should or should not do.
The founder of Ethereum, Vitalik Buterin, has full control over the project:
Nobody has control over Bitcoin. Bitcoin is open sourced and anyone can change the behaviour of the Bitcoin network. However, unless you convince 51% of Bitcoin node runners that the change is in their benefit as well, your change will go nowhere. The chances of convincing 51% of node operators is close to nil which is why people assert that no one can change Bitcoin.
Vitalik Buterin spearheaded the most important change in the Ethereum network in years: changing from proof-of-work to proof-of-stake validation.
Others have tried the same with Bitcoin and they failed.
Shitcoins are not the crypto industry
Coinbase declined to delist everything other than Bitcoin because according to its CEO, “compliance with the order would have meant the end of the crypto industry in the US.”.
The reality is that the crypto industry is Bitcoin and its layer 2 projects like Lightning, Fedimint and the Liquid network.
The shitcoins call themselves crypto industry but they are just good old scams. They call themselves crypto to fool you into buying them.
If Coinbase had delisted all shitcoins, the crypto industry wouldn’t had died. It would had been cleared from all these parasites that hang to it and suck its energy and reputation.
Just consider how much more widely accepted Bitcoin would be if we didn’t have these regular scams, rug pulls and exchange collapses.
The next time a someone tells you that the SEC is going after the crypto industry, say no, they are going after a bunch of scammers.
Notable notes
nostr:note1rhuh2dmk9d86gllfqgls9vmj2dr3x0ch56va2rrgrt397mlmarjqrp43v2
Recommendations
Matt Odell
Champion of freedom tech, free speech and humility.
You can follow him here.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. It's a very effective way to stay up to date with the industry.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ 1c52ebc8:5698c92a
2023-08-12 18:00:17
@ 1c52ebc8:5698c92a
2023-08-12 18:00:17Hey folks, happy Saturday!
Here’s your weekly newsletter on the technical happenings in the nostr-verse. Things are moving fast, people are building many amazing projects.
Let’s dive in.
Recent Upgrades to Nostr (NIPs)
1) Moderated Communities 💬
This NIP outlines how to implement a Reddit-like experience, where moderators can create and manage communities. Then anyone can propose a post, but moderators get final say about what shows up in the community. Can’t wait to use it! Hopefully we can use Zaps instead of upvotes like Stacker News!
Authors: nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and @arthurfranca
2) Proxy Tags (Approved!) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. Now that this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
3) Rewrite of NIP 65 - Relay Lists by nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
Many in the Nostr dev community desire to have many small relays instead of centralization around a smaller set of massive, highly capable relays. In order to do that, there’s a challenge with discovering relays to pull events for a users’ followers.
This NIP was approved weeks ago, but was rewritten recently to make it easier to implement, which should help add more momentum to decentralizing relays.
Notable projects
Vault - Nostr-based Password Manager 🔒
nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn implemented a way to store and retrieve sensitive information (like passwords) via Nostr. It has a 1Password-like interface for ease of use.
It’s also encrypted twice, once via the normal Nostr secret key signing like any Nostr event, but again with the password to unlock the vault. That way, if someone compromises your Nostr account’s secret key in the future, they still need your vault password to decrypt your sensitive information.
Can’t wait to migrate!
Nostrscript
Looks like nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s added a way to activate code in Damus via a link on a website. This pattern could help clients interoperate (one client activating actions in other clients a user is using). Endless possibilities!
Relay Backup
nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f Built a way to easily back up your events from a relay. This helps folks make sure all their events from public relays are copied to a private backup relay so none of their events are lost to time.
Stacker news
Not exactly new, but this project has been a delight to engage in discussion with other folks interested in Nostr, Bitcoin, and freedom tech in general. Using zaps as signal instead of upvotes is pretty novel to me, and all the zaps go to the posters as well as the platform to distribute rewards to the community. #valueforvalue
Latest conversations
Who controls NIPs?
Right now NIPs are hosted via a Github Repo. This is helpful in many ways because there’s one publicly-accessible way to read NIPs and get started contributing. By the nature of this being a code repository under source control, there are a small group of folks that are able to “approve” updates to NIPs.
The nature of projects like Nostr (or Bitcoin in the early 2010s for that matter) is that the early folks often need some control over the direction to make sure that the project has a chance to become self-sustaining without imploding into chaos.
The debate in the linked thread seems to be stemming from the timeless question for protocols, which is “how much should the protocol be able to do?” and that’s generally decided by early devs and those that control the generally accepted version of the spec for the protocol. That’s currently the NIPs repo, so who gets to “approve” NIPs in that repo?
Here’s hoping we can find a collaborative place to land that preserves the heart of nostr and maximizes its chance of success 💪
How to handle illegal content on Nostr
There was a Plebchain radio conversation with nostr:npub1yye4qu6qrgcsejghnl36wl5kvecsel0kxr0ass8ewtqc8gjykxkssdhmd0 who has been an advocate for folks that’ve been trafficked. She’s a rare advocate of preventing trafficking and CSAM through the internet without compromising encryption, or other online freedom.
There are unanswered questions about how the Nostr community is going to handle this content so we don’t see Nostr become a haven for activity most see as despicable. With the collection of smart people on Nostr, I’ll bet that a solution emerges to maximize freedom on the internet and drastically reduce the ability for illegal content to spread via the Nostr protocol.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual).
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week, but if you wanna see something advertised here just DM me!
Until next time 🫡
If I missed anything, or you’re building something I didn’t post about, let me know, DMs welcome.
God bless, you’re super cute
-
 @ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53
@ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53Questa guida è disponibile anche in:\n\n Francese: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c grazie a nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme grazie a nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n Svedese: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 grazie a nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7\n Spagnolo: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q grazie a nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624\n Olandese: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx grazie a nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6\n Arabo: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s grazie a nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j \n Tedesco: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz grazie a nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg\n Giapponese: nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6 di nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0\n Russo: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x di nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n\n---\n\nCiao, caro Nostrich! \n\nNostr è qualcosa di completamente nuovo, e ci sono alcuni passi da fare che semplificheranno il tuo ingresso e renderanno più interessante la tua esperienza.\n\n## 👋 Benvenuto\n\nDato che stai leggendo questa guida, diamo per assunto che tu ti sia già unito a Nostr scaricando un app (es. Damus, Amethyst, Plebstr) o usando un Web Client Nostr (es. snort.social, Nostrgram, Iris). E' importante per un nuovo arrivato seguire i passaggi suggeriti dalla piattaforma di tua scelta - la procedura di benvenuto ti fornisce tutte le basi, e non dovrai preoccuparti di configurare nulla a meno che tu non lo voglia fare. Se sei incappato in questo articolo, ma non hai ancora un “account” Nostr, puoi seguire questa semplice guida a cura di nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.\n\n---\n\n## 🤙 Divertiti\n\nNostr è fatto per assicurarsi che le persone siano in grado di connettersi liberamente, di essere ascoltate e di divertirsi. Questo è il fulcro centrale (ovviamente ci sono moltissimi altri casi d'uso, come essere uno strumento per i divulgatori e chi lotta per la libertà, ma per questo servirà un articolo a parte), quindi se qualcosa ti è poco chiaro contatta altri “nostriches” con esperienza e saremo lieti di aiutarti. Interagire con Nostr non è difficile, ma ci sono alcune differenze rispetto alle altre piattaforme tradizionali, quindi è normale fare domande (anzi...sei incoraggiato a farne).\n\nQuesta è una lista ufficiosa di utenti Nostr che saranno felici di aiutarti e rispondere alle tue domande:\n\nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu\n\n_Tutti i nostriches nella lista hanno ricevuto il badge Nostr Ambassador, il che renderà facile per te trovarli, verificarli e seguirli_\n\n---\n\n## ⚡️ Attivare gli Zaps\n\nGli Zaps sono una delle prime differenze che noterai entrando su Nostr. Consentono agli utenti Nostr di inviare istantaneamente valore per supportare la creazione di contenuti utili e divertenti. Sono possibili grazie a Bitcoin e Lightning Network. Questi due protocolli di pagamento decentralizzati permettono di inviare istantaneamente dei sats (la più piccola frazione di Bitcoin) tanto facilmente quanto mettere un like sulle piattaforme social tradizionali. Chiamiamo questo meccanismo Value-4-Value e puoi trovare altre informazioni al riguardo qui: https://dergigi.com/value/ \n\nDai un'occhiata a questa nota di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 per avere una panoramica su cosa sono siano gli zaps.\n\nDovresti attivare gli Zaps anche se non sei un creatore di contenuti - le persone troveranno sicuramente interessanti alcune delle tue note e vorranno mandarti dei sats. Il modo più semplice per ricevere sats su Nostr è il seguente:\n\n1. Scarica l'app Wallet of Satoshi - probabilmente la scelta migliore per dispositivi mobili per chi è nuovo in Bitcoin e Lightning. Tieni di conto che esistono molti altri wallets e che potrai scegliere quello che preferisci. Inoltre, non dimenticarti di fare un back up del wallet. \n2. Premi “Ricevere”\n3. Premi sopra al tuo Lightning Address (è quello che sembra un indirizzo email) per copiarlo\n
 \n4. Incollalo poi nel campo corrispondente all'interno del tuo client Nostr (il nome del campo potrebbe essere “Bitcoin Lightning Address”, “LN Address” o qualcosa di simile in base all'app che utilizzi). \n
\n4. Incollalo poi nel campo corrispondente all'interno del tuo client Nostr (il nome del campo potrebbe essere “Bitcoin Lightning Address”, “LN Address” o qualcosa di simile in base all'app che utilizzi). \n \n\n---\n\n## 📫 Ottieni un indirizzo Nostr\n\nGli indirizzi Nostr, a cui spesso i Nostr OGs si riferiscono con “NIP-05 identifier”, sono simili ad un indirizzo email e:\n\n🔍 Aiutano a rendere il tuo account facile da trovare e condividere \n✔️ Servono a verificare che il tuo “LN Address” appartenga ad un umano\n\n---\n\nQuesto è un esempio di indirizzo Nostr: Tony@nostr.21ideas.org\n
\n\n---\n\n## 📫 Ottieni un indirizzo Nostr\n\nGli indirizzi Nostr, a cui spesso i Nostr OGs si riferiscono con “NIP-05 identifier”, sono simili ad un indirizzo email e:\n\n🔍 Aiutano a rendere il tuo account facile da trovare e condividere \n✔️ Servono a verificare che il tuo “LN Address” appartenga ad un umano\n\n---\n\nQuesto è un esempio di indirizzo Nostr: Tony@nostr.21ideas.org\n \n E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente\n\n---\n\nPer ottenere un indirizzo Nostr puoi usare un servizio gratuito come Nostr Check (di nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) oppure uno a pagamento come Nostr Plebs (di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Entrambi offrono vari vantaggi, e la scelta dipende solo da te. Un altro modo per ottenere un indirizzo Nostr è tramite un'estensione del browser. Scopri di più al riguardo qui) . \n\n---\n\n## 🙇♀️ Impara le basi\n\nDietro le quinte Nostr è molto diverso dalle piattaforme social tradizionali, quindi conoscerne le basi è estremamente utile per i nuovi arrivati. E con questo non intendo che dovresti imparare un linguaggio di programmazione o i dettagli tecnici del protocollo. Sto dicendo che avere una visione d'insieme più ampia e capire le differenze fra Nostr e Twitter / Medium / Reddit ti aiuterà moltissimo. Ad esempio, al posto di un nome utente e password hai una chiave privata e una pubblica. Non entrerò nel dettaglio perchè esistono già moltissime risorse che ti aiuteranno a diventare un esperto di Nostr. Tutte quelle degne di nota sono state raccolte in questa pagina con 💜 da nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6\n\n
\n E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente\n\n---\n\nPer ottenere un indirizzo Nostr puoi usare un servizio gratuito come Nostr Check (di nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) oppure uno a pagamento come Nostr Plebs (di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Entrambi offrono vari vantaggi, e la scelta dipende solo da te. Un altro modo per ottenere un indirizzo Nostr è tramite un'estensione del browser. Scopri di più al riguardo qui) . \n\n---\n\n## 🙇♀️ Impara le basi\n\nDietro le quinte Nostr è molto diverso dalle piattaforme social tradizionali, quindi conoscerne le basi è estremamente utile per i nuovi arrivati. E con questo non intendo che dovresti imparare un linguaggio di programmazione o i dettagli tecnici del protocollo. Sto dicendo che avere una visione d'insieme più ampia e capire le differenze fra Nostr e Twitter / Medium / Reddit ti aiuterà moltissimo. Ad esempio, al posto di un nome utente e password hai una chiave privata e una pubblica. Non entrerò nel dettaglio perchè esistono già moltissime risorse che ti aiuteranno a diventare un esperto di Nostr. Tutte quelle degne di nota sono state raccolte in questa pagina con 💜 da nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6\n\n \n_Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata_\n\n---\n\n## 🤝 Connettiti\n\nLa possibilità di connetterti con altre [^3] persone brillanti è ciò che rende speciale Nostr. Qui tutti possono essere ascoltati e nessuno può essere escluso. Ci sono alcuni semplici modi per trovare persone interessanti su Nostr:\n\n Trova le persone che segui su Twitter: https://www.nostr.directory/ è un ottimo strumento per questo.\n Segui le persone seguite da altri di cui ti fidi: Visita il profilo di una persona che condivide i tuoi stessi interessi, guarda la lista delle persone che segue e connettiti con loro.\n\n
\n_Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata_\n\n---\n\n## 🤝 Connettiti\n\nLa possibilità di connetterti con altre [^3] persone brillanti è ciò che rende speciale Nostr. Qui tutti possono essere ascoltati e nessuno può essere escluso. Ci sono alcuni semplici modi per trovare persone interessanti su Nostr:\n\n Trova le persone che segui su Twitter: https://www.nostr.directory/ è un ottimo strumento per questo.\n Segui le persone seguite da altri di cui ti fidi: Visita il profilo di una persona che condivide i tuoi stessi interessi, guarda la lista delle persone che segue e connettiti con loro.\n\n \n\n Visita la Bacheca Globale: Ogni client Nostr (app Nostr se preferisci) ha una scheda per spostarsi nella Bacheca Globale (Global Feed), dove troverai tutte le note di tutti gli utenti di Nostr. Segui le persone che trovi interessanti (ricorda di essere paziente - potresti trovare una discreta quantità di spam).\n\n
\n\n Visita la Bacheca Globale: Ogni client Nostr (app Nostr se preferisci) ha una scheda per spostarsi nella Bacheca Globale (Global Feed), dove troverai tutte le note di tutti gli utenti di Nostr. Segui le persone che trovi interessanti (ricorda di essere paziente - potresti trovare una discreta quantità di spam).\n\n \n\n Usa gli #hashtags: Gli Hashtag sono un ottimo modo per concentrarti sugli argomenti di tuo interesse. Ti basterà premere sopra l'#hashtag per vedere altre note relative all'argomento. Puoi anche cercare gli hashtags tramite l'app che utilizzi. Non dimenticare di usare gli hashtags quando pubblichi una nota, per aumentarne la visibilità.\n\nhttps://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg \nScreenshot della bacheca di nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj su https://nostrgraph.net/ \n\n---\n\n## 🗺️ Esplora\n\nI 5 consigli menzionati sono un ottimo punto d'inizio e miglioreranno moltissimo la tua esperienza, ma c'è molto di più da scoprire! Nostr non è solo un rimpiazzo per Twitter e le sue possibilità sono limitate solo dalla nostra immaginazione. \n\n
\n\n Usa gli #hashtags: Gli Hashtag sono un ottimo modo per concentrarti sugli argomenti di tuo interesse. Ti basterà premere sopra l'#hashtag per vedere altre note relative all'argomento. Puoi anche cercare gli hashtags tramite l'app che utilizzi. Non dimenticare di usare gli hashtags quando pubblichi una nota, per aumentarne la visibilità.\n\nhttps://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg \nScreenshot della bacheca di nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj su https://nostrgraph.net/ \n\n---\n\n## 🗺️ Esplora\n\nI 5 consigli menzionati sono un ottimo punto d'inizio e miglioreranno moltissimo la tua esperienza, ma c'è molto di più da scoprire! Nostr non è solo un rimpiazzo per Twitter e le sue possibilità sono limitate solo dalla nostra immaginazione. \n\n \n\nDai un'occhiata alla lista di tutti i progetti Nostr:\n\n https://nostrapps.com/ una lista di tutte le apps su Nostr\n https://nostrplebs.com/ – ottieni il tuo NIP-05 e altri vantaggi (a pagamento)\n https://nostrcheck.me/ – Indirizzi Nostr, caricamento di media, relay\n https://nostr.build/ – Carica e gestisci i tuoi media (e altro)\n https://nostr.band/ – Informazioni sul network e gli utenti di Nostr\n https://zaplife.lol/ – Statistiche degli Zaps\n https://nostrit.com/ – Programma le note\n https://nostrnests.com/ – Twitter Spaces 2.0 \n https://nostryfied.online/ - Fai un backup dei tuoi dati di Nostr\n https://www.wavman.app/ - Player musicale per Nostr\n\n---\n\n## 📻 Relays\n\nDopo aver preso confidenza con Nostr assicurati di dare un'occhiata alla mia guida riguardo i Relays su Nostr: https://lnshort.it/nostr-relays. Non è un argomento di cui preoccuparsi all'inizio del tuo viaggio, ma è sicuramente importante approfondirlo più avanti.\n\n\n\n## 📱 Nostr su mobile\n\nAvere un'esperienza fluida su Nostr tramite un dispositivo mobile è fattibile. Questa guida ti aiuterà ad accedere, postare, inviare zap e molto di più all'interno delle applicazioni web Nostr sul tuo smartphone: https://lnshort.it/nostr-mobile\n\n\n\nGrazie per aver letto e ci vediamo dall'altra parte della tana del coniglio.\n\nGrazie a nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 per aver fornito il documento originale che ho tradotto\n\n** \n
\n\nDai un'occhiata alla lista di tutti i progetti Nostr:\n\n https://nostrapps.com/ una lista di tutte le apps su Nostr\n https://nostrplebs.com/ – ottieni il tuo NIP-05 e altri vantaggi (a pagamento)\n https://nostrcheck.me/ – Indirizzi Nostr, caricamento di media, relay\n https://nostr.build/ – Carica e gestisci i tuoi media (e altro)\n https://nostr.band/ – Informazioni sul network e gli utenti di Nostr\n https://zaplife.lol/ – Statistiche degli Zaps\n https://nostrit.com/ – Programma le note\n https://nostrnests.com/ – Twitter Spaces 2.0 \n https://nostryfied.online/ - Fai un backup dei tuoi dati di Nostr\n https://www.wavman.app/ - Player musicale per Nostr\n\n---\n\n## 📻 Relays\n\nDopo aver preso confidenza con Nostr assicurati di dare un'occhiata alla mia guida riguardo i Relays su Nostr: https://lnshort.it/nostr-relays. Non è un argomento di cui preoccuparsi all'inizio del tuo viaggio, ma è sicuramente importante approfondirlo più avanti.\n\n\n\n## 📱 Nostr su mobile\n\nAvere un'esperienza fluida su Nostr tramite un dispositivo mobile è fattibile. Questa guida ti aiuterà ad accedere, postare, inviare zap e molto di più all'interno delle applicazioni web Nostr sul tuo smartphone: https://lnshort.it/nostr-mobile\n\n\n\nGrazie per aver letto e ci vediamo dall'altra parte della tana del coniglio.\n\nGrazie a nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 per aver fornito il documento originale che ho tradotto\n\n** \n -
 @ d5415a31:b317849f
2023-08-12 11:38:14
@ d5415a31:b317849f
2023-08-12 11:38:14Below is a sample of my article on nostr...
*A dangerous trend has emerged in the United States where terms like free speech, censorship- resistant, privacy, and more have been co-opted by those on the political right, and tools enabling these principles argued or fought against by those on the political left. The truth is, freedom, privacy, and censorship resistant technologies are important for everyone regardless of political leanings and should not be politicized, lest we head down the path toward a dystopian future with no privacy or free speech guarantees, and only centralized institutions controlled by people with the ability to censor, revoke and remove important guarantees of freedom promoted in the spirit and language of the constitution. Just as bitcoin has falsely become politicized as a more right wing/libertarian thing, having no value, or a tool for criminals and those who disregard the dangers of climate change, open and decentralized protocols like nostr could enter the same cycle and become politicized or fought against unless we share more reasons why it is important for humanity and is not a political position to take. The fate of our ability to freely and openly communicate and have guarantees of privacy and property may rest on citizens of the world understanding the importance of open, censorship resistance protocols, and private end-to-end encrypted communication tools. *
One specific example I will focus on is Nostr. So, what is nostr?
Nostr was first conceptualized by pseudonymous bitcoin coder, Fiatjaf and “bitcoin tinkerer” Ben Arc. As described on nostr.how, run by JeffG:
“Nostr stands for “Notes and Other Stuff Transmitted by Relays”. Like HTTP or TCP-IP, Nostr is a protocol; an open standard upon which anyone can build. Nostr itself is not an app or service that you sign up for. Nostr is designed for simplicity and enables censorship-resistant and globally decentralized publishing on the web.”
The way in which we see the nostr protocol used and popularized today is via clients (i.e. apps/websites), like my personal favorite Damus, or Primal, Snort and dozens of others being built out by developers passionate about this protocol. Each user then adds relays (many are defaulted on most clients today), which is the way these messages get sent around in a decentralized way, and users can add free or even paid relays (by paying for relays, in bitcoin which is the money/medium of exchange used on nostr, users can eliminate the amount of spam or bots accessing relays/feeds and have a faster experience). Users can also sort their global feed based on relays, and more. The beauty of this system is that most traditional social media–twitter, facebook, instagram, linkedin, etc, is completely centralized. Twitter, for instance, manages the content and has its own server (or pays third parties to do so)–one central relay, in a way. So you can easily be censored or removed from using twitter for criticizing Elon Musk, posting a political statement that is unfavorable to decision makers within the company or a nation-state asking twitter to censor these types of messages, in the recent case of Turkey and its recent election, and more. With nostr, if you are censored on one relay, you still have endless amounts of other relays to write/post to. Nor is your nostr account tied to one specific relay or client. When each user signs up on nostr, an “npub” (think username) is created and an nsec (think password) that can be used to sign up for any client. Imagine if you had your twitter username and password, but you could also use that to sign into every other social media platform and it carried with it every post and connection you ever had on twitter. Pretty cool, right? But with this comes the responsibility of keeping your nsec (again, think password) written down in a safe place in the event you are logged out of a particular client, because there is no backup or password reset ability on most clients. There are browser extensions that save this information for you, but with any internet backup comes certain privacy risks as well.
So practically, nostr is a cool and easy way to use social media across multiple clients, leaving you with ultimate control and preference! Ideologically, it is so much more.
As I stated earlier, nostr is an open protocol, where anyone can post and build with it, leaving it to be censorship resistant and with you in control. As is the case with bitcoin, if you can access the internet, you can access nostr. I know many progressive friends of mine have been very frustrated with twitter/x’s/Elon’s selective control of who gets to practice “free speech” and who doesn’t on the platform. Many other self-described “free speech” platforms have been created, such as Trump’s Truth Social, Rumble, and more. But these platforms are FSINO, “Free Speech in Name Only.” They are still companies run by people with centralized control. When we say nostr promotes free speech and the user is in control, it isn’t because nostr is run by a self-described “free speech maximalist,” or because nostr has any specific political ideology. It is because the protocol is inherently open and free to use by anyone, and decentralized in a way where an infinite number of communities, ideologies, people, and movements can flourish and utilize the protocol however they wish. I believe it is technology and an internet enabled protocol as the cypherpunk movement intended: promoting freedom, censorship resistance, and the ability to be private and promote anonymity when needed (no KYC, government checks to use).
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 82b30d30:40c6c003
2023-07-22 08:31:22
@ 82b30d30:40c6c003
2023-07-22 08:31:22[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ a10260a2:caa23e3e
2023-08-16 04:59:43
@ a10260a2:caa23e3e
2023-08-16 04:59:43I just discovered YakiHonne today, and thankfully so, since the deadline to test the round 4 updates, provide feedback, and stack sats is near.
There's not much I enjoy doing more than stacking sats.

And growing Nostr too of course. That's why I'm here.
Alright, let's get right into it and go over the 5 updates in this round.
1. Drafts - You can save your articles for later edit/publish.
Love this and I look forward to the day we can make drafts of short notes on the mobile clients (e.g. Damus and Primal). But this behaves as expected, when clicking "Save as draft", I'm asked what relays I'd like to save my draft too.

After saving the draft and viewing "My articles", it makes sense that the draft wouldn't appear when clicking on a relay where the draft wasn't initially saved.
2. Stats previews - You can see who zapped/upvote/downvote your or other creator's articles.
This worked as expected as the shaka I received on my first ever blog post on Nostr showed up as an upvote. Shoutout to SoberGrizzlyBTC for the love!

3. Add "my articles" to the curation creation tab - You can directly select your articles for your curation from your articles.
I mentioned this one in #1 and I think it means there's a place I can go to where I can see only articles that I've created.

4. Add confirmation deletion prompt for comments - Now you have the ability to cancel faulty comments.
I'll have to revisit this one since I don't have any comments at the moment.
5. Hints - Add stats icons hovering hints to clear things up.
Looks good. You can see that it says "Tip article" when hovering over the lightning icon. This is something you should definitely do btw ;)

We've now covered all the updates from this round and all I can say is wow. I'm super impressed with the user interface and just being able to do something as simple as saving a draft.
I mentioned in my first post Running blogstack that there would be nothing stopping me from creating with another client and here we are. All I had to do was connect my private key which we're now able to do more safely with extensions like nos2x.
I'm looking forward to using YakiHonne more in the coming days and testing future updates.
Onward.
-
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41"Who do you say that I am?"
In Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.
- Who they tell us they are.
- Who others say about them.
- What we observe for ourselves.
Putting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.
With this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way?
The default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.
This falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.
I don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like... * Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover. * Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading. * Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed. * Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon. * Have a full pet-names override.
I think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.
A note on anonymity
Real world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety.
If you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 7f5c2b4e:a818d75d
2023-08-11 15:53:02
@ 7f5c2b4e:a818d75d
2023-08-11 15:53:02
This guide is available in:
- French: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme thanks to nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- Swedish: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 thanks to nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- Spanish: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- Dutch: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx thanks to nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- Arabic: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s thanks to nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- German: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz thanks to nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- Japanese: nostr:naddr1qqf8wetvvdhk6efdw3hj6mn0wd6z66nsqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z85v8z thanks to nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0
- Persian: nostr:naddr1qqfhwetvvdhk6efdw3hj6mn0wd68yttxvypzql6u9d8y3g8flm9x8frtz0xmsfyf7spq8xxkpgs8p2tge25p346aqvzqqqr4guk52uek thanks to nostr:npub1cpazafytvafazxkjn43zjfwtfzatfz508r54f6z6a3rf2ws8223qc3xxpk
- Italian: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1d57clc5wacyga7xyat2dkpzptedwza8ufucgr5p6hq5ecsrr5m8sjqxpr6
- Russian: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x by nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
Hello, fellow Nostrich!
Nostr is a brand new phenomenon and there are a few steps that will make your onboarding much smoother and your experience much richer.
👋 Welcome
Since you are reading this, it’s safe to assume that you already joined Nostr by downloading an app (e.g. Damus, Amethyst, Plebstr) for your mobile device or opening a Nostr web client (e.g. snort.social, Nostrgram, Iris). It is important for a newcomer to follow the steps suggested by the app of your choice – the welcoming procedure provides all the basics, and you won’t have to do much more tuning unless you really want to. If you’ve stumbled upon this post, but don’t have a Nostr “account” yet, you can follow this simple step-by-step guide by nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.
🤙 Have fun
Nostr is built to ensure people can connect, get heard, and have fun along the way. This is the whole point (obviously, there is a plethora of serious use cases, such as being a tool for freedom fighters and whistleblowers, but that deserves a separate article), so if you feel like anything feels burdensome, please reach out to the more experienced nostriches and we will be happy to help. Interacting with Nostr is not hard at all, but it has a few peculiarities when compared to traditional platforms, so it’s ok (and encouraged) to ask questions.
Here’s an unofficial list of Nostr ambassadors who will be happy to help you get onboard:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
All the nostriches on the list were also awarded a Nostr Ambassador badge that will make it easy for you to find, verify and follow them
⚡️ Enable Zaps
Zaps are one of the first differences one may notice after joining Nostr. They allow Nostr users to instantly send value and support creation of useful and fun content. This is possible thanks to Bitcoin and Lightning Network. These decentralized payment protocols let you instantly send some sats (the smallest unit on the Bitcoin network) just as easily as liking someone’s post on traditional social media platforms. We call this model Value-4-Value and you can find more about this ultimate monetization model here: https://dergigi.com/value/
Check out this note by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 that is a great intro to what zaps are.
You should enable Zaps even if you do not consider yourself a content creator – people will find some of your notes valuable and might want to send you some sats. The easiest way to start receiving value on Nostr onley takes a couple steps:
- Download Wallet of Satoshi - probably the best choice for those who are new to Bitcoin and Lightning for your mobile device.[^1] Note that there are many more wallets and you are welcome to choose the one that suits you best. Also, don't forget to come back and back up your wallet.
- Tap “Receive”
- Tap the Lightning Address you see on the screen (the string which looks like an email address) to copy it to the clipboard.

- Paste the copied address into the corresponding field in your Nostr client (the field may say “Bitcoin Lightning Address”, “LN Address” or anything along those lines depending on the app you are using).

📫 Get a Nostr address
Nostr address, often referred to as a “NIP-05 identifier” by the Nostr OGs, looks like an email and:
🔍 Helps you make your account easy to discover and share
✔️ Serves as a verification you are a human
Here's an example of a Nostr address: Tony@nostr.21ideas.org
 It's easy to memorize and later paste into any Nostr app to find the corresponding user.
It's easy to memorize and later paste into any Nostr app to find the corresponding user.
To get a Nostr address you can use a free service like Nostr Check (by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) or a paid one like Nostr Plebs (by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Both offer different perks, and it's up to you to decide which one to use. Another way of getting a Nostr address is using a browser extension. Find out more about this approach here) .
🙇♀️ Learn the basics
Under the hood Nostr is very different from traditional social platforms, so getting a basic understanding of what it is about will be beneficial for any newcomer. Don’t get me wrong, I’m not suggesting you should learn a programming language or technical details of the protocol. I’m implying that seeing a bigger picture and understanding the difference between Nostr and Twitter / Medium / Reddit will help a lot. For example, there are no passwords and logins, you have private and public keys instead. I won’t go deep into that, ‘cause there is a handful of exhaustive resources that will help you grokk Nostr. All of the ones worthy your attention are gathered on this neatly organized landing page prepared by nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 with 💜
 Info provided by the mentioned resources will also help you secure your Nostr keys (i.e. your account), so it’s important to have a look.
Info provided by the mentioned resources will also help you secure your Nostr keys (i.e. your account), so it’s important to have a look.
🤝 Connect
Ability to connect with brilliant [^3] people is what makes Nostr special. Here everyone can get heard and no one can get excluded. There are a few simple ways to find interesting people on Nostr:
- Find people you follow on Twitter: https://www.nostr.directory/ is a great tool for that.
- Follow people followed by people you trust: Visit a profile of a person who shares your interests, check the list of people they follow and connect with them.

- Visit Global Feed: Every Nostr client (a Nostr app, if you will) has a tab that lets you switch to the Global Feed, which aggregates all the notes from all Nostr users. Simply follow people you find interesting (be patient though – you might run into a decent amount of spam).

- Use #hashtags: Hashtags are a great way to concentrate on the topics you like. Simply tap on a #hashtag you find interesting and you’ll see more notes related to the topic. You can also search for hashtags in the app you are using. Do not forget to use hashtags when composing notes to increase discoverability.
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg Screenshot of https://nostrgraph.net/ dashboard by nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj
🗺️ Explore
The mentioned 5 steps are a great start that will massively improve your experience, but there’s so much more to discover and enjoy! Nostr is not a Twitter replacement, its possibilities are only limited by imagination.

Have a look at the list of fun and useful Nostr projects:
- https://nostrapps.com/ a list of Nostr apps
- https://nostrplebs.com/ – get your NIP-05 and other Nostr perks (paid)
- https://nostrcheck.me/ – Nostr address, media uploads, relay
- https://nostr.build/ – upload and manage media (and more)
- https://nostr.band/ – Nostr network and user info
- https://zaplife.lol/ – zapping stats
- https://nostrit.com/ – schedule notes
- https://nostrnests.com/ – Twitter Spaces 2.0
- https://nostryfied.online/ - back up your Nostr info
- https://www.wavman.app/ - Nostr music player
📻 Relays
After getting acquainted with Nostr make sure to check out my quick guide on Nostr relays: https://lnshort.it/nostr-relays. It’s not the topic to worry about at the very beginning of your journey, but is definitely important to dive into later on.
📱 Nostr on mobile
Smooth Nostr experience on mobile devices is feasible. This guide will help you seamlessly log in, post, zap, and more within Nostr web applications on your smartphone: https://lnshort.it/nostr-mobile
Thanks for reading and see you on the other side of the rabbit hole.
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
[^1]: Do not forget
-
 @ f296e355:c28d00bc
2023-08-16 04:09:05
@ f296e355:c28d00bc
2023-08-16 04:09:05In 1984, Adi Shamir proposed an alternative to PKI (Public Key Infrastructure)[1] named IBE (Identity Based Encryption). With this, we use trust centre (T) and which is responsible for generating Bob and Alice’s public and private keys. Anyone who wants to send Alice some encrypted data can generate her public key based on her identity.

Günther’s method [2] defined implicitly certified identity-based public keys. In this case, Bob will generate Alice’s public key from a signed version of Alice’s identity from T. Alice can then gain the private key to recover any encrypted data:

In this case Bob will generate Alice’s public key from a signed version of Alice’s identity from T. Alice can then gain the private key to recover any encrypted data. First the trust centre generates a prime number (p) and a random number (t), and where the GCD (Greatest Common Divisor) is:

t is then the private key, and the trust centre will then publish a public key of:

The trust centre will then give Alice a distinguishable name of IA. For example, this might be Alice’s email address. Next the trust centre will generate a random integer of kA and computes a reconstruction public key value of:

The trust centre will then select a hashing method (h) and will calculate a to make the following true:

The trust centre then sends Alice (PA,a), and where a is Alice’s private key, and Alice’s public key is (PA)a. Bob can then recreate Alice’s public key using (g,IA,u,PA,p) with:

This will work as:

and so:

(PA)a=gh(IA)⋅u−PA=uPA⋅PAa⋅u−PA=PAa(modp)
Coding
The coding is here:
```
https://asecuritysite.com/encryption/guther
from Crypto.Util.number import * import Crypto import libnum import sys from random import randint import hashlib bits=60 IDA="Alice" if (len(sys.argv)>1): IDA=str(sys.argv[1]) if (len(sys.argv)>2): bits=int(sys.argv[2]) p = Crypto.Util.number.getPrime(bits, randfunc=Crypto.Random.get_random_bytes) g=2 t= randint(0, p-1) u = pow(g,t,p) Ka=2 while (libnum.gcd(Ka,p-1)!=1): Ka= randint(0, p-1) Pa = pow(g,Ka,p)
inv_Ka=(libnum.invmod(Ka, p-1)) D = int.from_bytes(hashlib.sha256(IDA.encode()).digest(),byteorder='big' )
a=((D-tPa)inv_Ka) % (p-1) AlicePub = (pow(g,D,p)*pow(u,-Pa,p))%p
print (f"Alice's ID: {IDA}") print (f"g: {g}" ) print (f"p: {p}" ) print ("\nTrust centre generates:") print (f"t (secret): {t}" ) print (f"u: {u}" ) print (f"\nKa (secret): {Ka}" ) print (f"Pa: {Pa}" ) print (f"h(ID): {D}" ) print ("\nTrust centre computes private key (a)") print (f"a: {a}" )
print ("\nBob uses h(ID), g, p, Pa to generate Pa^a") print (f"\nBob recovers Alice's Public Key: {AlicePub}") AlicePubCheck= pow(Pa,a,p) print (f"Checking Alice's key: {AlicePubCheck}") if (AlicePub==AlicePubCheck): print ("Keys match!") ```
A sample run of a 60-bit random prime number [here]:
Alice's ID: AliceID g: 2 p: 1040036132433661127 Trust centre generates: t (secret): 660713498401150081 u: 980986780230779448 Ka (secret): 589723904035103703 Pa: 723160803210645123 h(ID): 67595362884446021875105118399538667587610985753592658773354317154313003189111 Trust centre computes private key (a) a: 395971050764850570 Bob uses h(ID), g, p, Pa to generate Pa^a Bob recovers Alice's Public Key: 914640446395302251 Checking Alice's key: 914640446395302251 Keys match!and for a 256-bit random prime number [here]:
Alice's ID: AliceID g: 2 p: 110852656632201419223507769493894048136848426930220287813503162988662829348977 Trust centre generates: t (secret): 5420854790828476304309386278954387233740482554973779054205803478913006085301 u: 64697115686470266631492260479221243176048809274825059116718088012573550201057 Ka (secret): 20736369342194049699240222075276879897257228346331438516768198568251740874385 Pa: 82471319207677041543661624897197701284235288542061131181106361468660770667435 h(ID): 67595362884446021875105118399538667587610985753592658773354317154313003189111 Trust centre computes private key (a) a: 29092559345246744005943907604839436726638585039735344938794362875508476380464 Bob uses h(ID), g, p, Pa to generate Pa^a Bob recovers Alice's Public Key: 109145868988609169229666201120970111197965029652983574881111854109393877108663 Checking Alice's key: 109145868988609169229666201120970111197965029652983574881111854109393877108663 Keys match!And for a 512-bit random prime number [here]:
Alice's ID: AliceID g: 2 p: 11594711316410846967916853565132250862037894680138050720795756067432045878659584226527851546936883041655136093357160565150064729045680859586390435534509527 Trust centre generates: t (secret): 2191214164617329390502800577257515102872263679113374667143645471782966249711520153195921397876416498321613910219550129463176077054705997822626692047476857 u: 5051299130299031047387839752448406883155966307472756568024424502283535855857556790339072400676772634206952316207408818108634058040443947427171921062033161 Ka (secret): 3199736435805188213122536402386225080894710347614613907456680584534308636464340762329569136631033965302586291398155867143830224449382353523442138690161583 Pa: 9999117489268092011334185996544288393708071829119283167481610028681214226700497534510697738924501849829555349175534403951016027867677868378836513909438911 h(ID): 67595362884446021875105118399538667587610985753592658773354317154313003189111 Trust centre computes private key (a) a: 9031294101194153277120983691313395748402010344578031815542871905666914503967045868680784618701444404548097796843564039060802400036862864806170446022817368 Bob uses h(ID), g, p, Pa to generate Pa^a Bob recovers Alice's Public Key: 4044332461710321742528279247057690808186827681132095994916664619736714349281452983822229104162394903124064381837437562214612084174280349532663621999453357 Checking Alice's key: 4044332461710321742528279247057690808186827681132095994916664619736714349281452983822229104162394903124064381837437562214612084174280349532663621999453357 Keys match!Conclusion
While PKI has worked for the trust infrastructure for the Web, it does not scale well in many other areas, especially where we need our own centralised trust infrastructure. IBE provides an opportunity to enhance trust and keep control of the encryption keys that we need. And, just because a method isn’t used in practice, doesn’t mean we should exclude it from our learning, as you just never know when it could be used with a new problem.
References
[1] Shamir, A. (1984, August). Identity-based cryptosystems and signature schemes. In Workshop on the theory and application of cryptographic techniques (pp. 47–53). Springer, Berlin, Heidelberg [here].
[2] Günther, C. G. (1989, April). An identity-based key-exchange protocol. In Workshop on the Theory and Application of of Cryptographic Techniques (pp. 29–37). Springer, Berlin, Heidelberg [here].
By:Prof Bill Buchanan OBE Link:https://medium.com/asecuritysite-when-bob-met-alice/implicitly-certified-identity-based-public-keys-meet-g%C3%BCnthers-method-49d4095c3a47
-
 @ ca843451:fa3b4c1a
2023-08-09 12:17:34
@ ca843451:fa3b4c1a
2023-08-09 12:17:34关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n\n原文作者:Eric Zhang\n\n区块链可以在货币和金融交易之外发挥作用。其中一种非金融应用便是区块链可以极大地改进投票和治理领域。在本文中,我们探讨构建一种特殊用途区块链的方法,该基础设施旨在促进基于MACI的投票活动。该基础设施应包括充当时间戳服务器并托管逻辑的轻型区块链,以及减少用户成本/最大化用户体验所需的工具。因此,它应该成为新一代投票技术的新基础平台。在深入探讨细节之前,让我们首先回顾一下投票技术的历史以及投票在区块链社区内的发展过程。\n## 投票技术的演变\n
 \n从古希腊Kleroterion到现代电子投票机的投票技术。\n\n投票技术有着悠久的历史。它对人类社会非常重要,但发展非常缓慢。英国在2019年脱欧大选期间仍然依赖手写选票,其他民族国家使用闭源电子投票机,很容易为选举结果带来争议。\n\n现代投票技术的采用提高了效率,但在解决透明度和可验证性方面并没有取得太大成功。\n\n毋庸置疑,投票的诚信对于权力的交接、重要事务的决策或资源的分配非常重要。如果人们不能就治理决策的投票结果达成一致,他们就无法相互合作,摩擦就会增加。摩擦可能会引起问题,如从争端到战争。\n\n尽管投票技术正在缓慢发展,但透明度在很长一段时间内并没有得到改善。从Kleroterion到纸质选票,再到电子和光学扫描投票机,验证仍然依赖于值得信赖的个人和审计组织。确认和审核投票结果的成本可能极其高昂。显然还有改进的空间。\n\n那么理想的投票技术是什么?其实这并不是一个困难的问题。我们可以轻松创建一个“愿望清单”:\n(1)基础设施开源;\n(2)托管用于投票逻辑的开源程序;\n(3)按顺序保留所有投票的永久记录;\n(4)能够对结果进行密码学验证;\n(5)抗串谋;\n(6)保护隐私;\n(7)投票成本低。\n\n\n如果我们能够构建一个可以不断完善的开源系统,我们就会逐步实现上述目标。投票技术的改进和成本的降低可以使较小的组织和社区受益于使用他们以前无法获得的技术,这增加了巨大的正外部性。\n## 区块链社区内的投票和治理\n投票和治理在区块链社区中并不陌生,因为很多区块链社区都是分布式的,他们必须依靠治理来推动事务的发展。\n\n区块链本身可以透明地记录投票并验证投票结果。这些属性已被区块链社区用于治理,例如Snapshot代币投票和Cosmos治理提案投票活动。因此,区块链社区可以在不经过中心化代理或面对面会议的情况下,对提案进行投票,并决定重要的治理事务。\n
\n从古希腊Kleroterion到现代电子投票机的投票技术。\n\n投票技术有着悠久的历史。它对人类社会非常重要,但发展非常缓慢。英国在2019年脱欧大选期间仍然依赖手写选票,其他民族国家使用闭源电子投票机,很容易为选举结果带来争议。\n\n现代投票技术的采用提高了效率,但在解决透明度和可验证性方面并没有取得太大成功。\n\n毋庸置疑,投票的诚信对于权力的交接、重要事务的决策或资源的分配非常重要。如果人们不能就治理决策的投票结果达成一致,他们就无法相互合作,摩擦就会增加。摩擦可能会引起问题,如从争端到战争。\n\n尽管投票技术正在缓慢发展,但透明度在很长一段时间内并没有得到改善。从Kleroterion到纸质选票,再到电子和光学扫描投票机,验证仍然依赖于值得信赖的个人和审计组织。确认和审核投票结果的成本可能极其高昂。显然还有改进的空间。\n\n那么理想的投票技术是什么?其实这并不是一个困难的问题。我们可以轻松创建一个“愿望清单”:\n(1)基础设施开源;\n(2)托管用于投票逻辑的开源程序;\n(3)按顺序保留所有投票的永久记录;\n(4)能够对结果进行密码学验证;\n(5)抗串谋;\n(6)保护隐私;\n(7)投票成本低。\n\n\n如果我们能够构建一个可以不断完善的开源系统,我们就会逐步实现上述目标。投票技术的改进和成本的降低可以使较小的组织和社区受益于使用他们以前无法获得的技术,这增加了巨大的正外部性。\n## 区块链社区内的投票和治理\n投票和治理在区块链社区中并不陌生,因为很多区块链社区都是分布式的,他们必须依靠治理来推动事务的发展。\n\n区块链本身可以透明地记录投票并验证投票结果。这些属性已被区块链社区用于治理,例如Snapshot代币投票和Cosmos治理提案投票活动。因此,区块链社区可以在不经过中心化代理或面对面会议的情况下,对提案进行投票,并决定重要的治理事务。\n \nKlaytnSquare正在进行的一项提案呼吁验证者在链上投票。该提案寻求季度财政支出计划的批准。\n\n前述的例子采用了简单直接的1代币1票规则 - 拥有多少投票权取决于在网络或协议中的权益。显然,只要有意义,我们可以创造其他投票逻辑。区块链的可编程性使得实施非传统投票逻辑变得更加容易和实际。\n\n一个例子是二次方投票(QV),这是一种在区块链社区中越来越受欢迎的投票方案。在QV轮中,选民可以通过在特定主题上花费“投票信用积分”(Voice Credit)来表达他/她的偏好。但如果选民想对同一主题投不止一票,则每票的声音信用成本就会增加。因此,投票的总成本呈二次增加,阻止了那些拥有过多投票权力的选民的极端偏好。\n\n
\nKlaytnSquare正在进行的一项提案呼吁验证者在链上投票。该提案寻求季度财政支出计划的批准。\n\n前述的例子采用了简单直接的1代币1票规则 - 拥有多少投票权取决于在网络或协议中的权益。显然,只要有意义,我们可以创造其他投票逻辑。区块链的可编程性使得实施非传统投票逻辑变得更加容易和实际。\n\n一个例子是二次方投票(QV),这是一种在区块链社区中越来越受欢迎的投票方案。在QV轮中,选民可以通过在特定主题上花费“投票信用积分”(Voice Credit)来表达他/她的偏好。但如果选民想对同一主题投不止一票,则每票的声音信用成本就会增加。因此,投票的总成本呈二次增加,阻止了那些拥有过多投票权力的选民的极端偏好。\n\n \n二次方融资轮在Aptos区块链上投票。投票结果记录在链上,投票逻辑可验证。\n\n选择特定投票方式时需要考虑许多参数。例如,一个权衡是选择链上投票还是链下投票。链上投票逻辑可能更具可验证性和透明度,但Gas Fee可能是一个重要的负担。相反,链下投票逻辑可能更便宜,但同时透明度和可验证性较低。然而,链上与链下投票不是二选一的关系。我们可以很容易地将其设计为混合系统,其中部分流程在链上进行,其余部分在链下完成。\n\n除了成本之外,还有隐私问题。隐私之所以重要有两个原因。首先,在很多情况下,如果选民可以匿名投票(用户和当局之间的隐私),他们对投票的顾虑就会减少。此外,用户之间的隐私可以帮助防止投票贿赂,有效实现抗共谋。\n\n我们可以最大限度地减少链上计算,同时强制链下完整性的一种方法是使用零知识证明。一个简单的想法是,如果链下计算可以通过零知识证明进行验证,我们就可以将大部分计算移至链下。如果消息进一步加密,我们就可以增强隐私性。MACI是实现这一目标的最小框架。\n\n
\n二次方融资轮在Aptos区块链上投票。投票结果记录在链上,投票逻辑可验证。\n\n选择特定投票方式时需要考虑许多参数。例如,一个权衡是选择链上投票还是链下投票。链上投票逻辑可能更具可验证性和透明度,但Gas Fee可能是一个重要的负担。相反,链下投票逻辑可能更便宜,但同时透明度和可验证性较低。然而,链上与链下投票不是二选一的关系。我们可以很容易地将其设计为混合系统,其中部分流程在链上进行,其余部分在链下完成。\n\n除了成本之外,还有隐私问题。隐私之所以重要有两个原因。首先,在很多情况下,如果选民可以匿名投票(用户和当局之间的隐私),他们对投票的顾虑就会减少。此外,用户之间的隐私可以帮助防止投票贿赂,有效实现抗共谋。\n\n我们可以最大限度地减少链上计算,同时强制链下完整性的一种方法是使用零知识证明。一个简单的想法是,如果链下计算可以通过零知识证明进行验证,我们就可以将大部分计算移至链下。如果消息进一步加密,我们就可以增强隐私性。MACI是实现这一目标的最小框架。\n\n \nMACI投票轮将计票转移到链外。最后通过零知识证明链上验证结果的有效性。\n\n在MACI投票轮中,投票被封装在由一轮管理员(运营商)生成的公钥加密的消息中,并提交给智能合约。因此,所有消息都被区块链“时间戳”,从而创建了一个选民消息链。\n\n当投票轮次结束时,运营商下载所有消息,对它们进行解密,并以相反的顺序进行投票计数。然后,将结果与零知识证明一起发布,可以在智能合约上(或由任何其他人)进行验证,从而标志着发布结果的有效性以及消息处理的正确性。\n\n整个过程在保证发布结果的完整性的同时,保持了最小的链上计算。它还为用户之间提供了隐私和抗共谋的能力。\n## MACI在实际产品中是如何工作的?\nMACI现在被DoraHacks上的各个黑客马拉松社区用来投票选出他们最喜欢的黑客马拉松项目。所以我们以DoraHacks MACI轮次为例。\n\n
\nMACI投票轮将计票转移到链外。最后通过零知识证明链上验证结果的有效性。\n\n在MACI投票轮中,投票被封装在由一轮管理员(运营商)生成的公钥加密的消息中,并提交给智能合约。因此,所有消息都被区块链“时间戳”,从而创建了一个选民消息链。\n\n当投票轮次结束时,运营商下载所有消息,对它们进行解密,并以相反的顺序进行投票计数。然后,将结果与零知识证明一起发布,可以在智能合约上(或由任何其他人)进行验证,从而标志着发布结果的有效性以及消息处理的正确性。\n\n整个过程在保证发布结果的完整性的同时,保持了最小的链上计算。它还为用户之间提供了隐私和抗共谋的能力。\n## MACI在实际产品中是如何工作的?\nMACI现在被DoraHacks上的各个黑客马拉松社区用来投票选出他们最喜欢的黑客马拉松项目。所以我们以DoraHacks MACI轮次为例。\n\n \nOpenSea与Replit黑客马拉松在2022年使用MACI进行评委投票\n\n黑客马拉松项目(BUIDL)提交后,主办方从所有提交的作品中选出了12支BUIDL团队。10名评委受邀为这12支BUIDL团队投票,并分发25,000美元的奖金。10名评委被列入白名单,报名参加投票轮,他们总共向部署在Polygon上的MACI智能合约发送了39条消息。\n\n投票结束后,管理员(DoraHacks)统计票数并将最终结果发布到排行榜上,然后提供零知识证明来验证排行榜。\n\n\n
\nOpenSea与Replit黑客马拉松在2022年使用MACI进行评委投票\n\n黑客马拉松项目(BUIDL)提交后,主办方从所有提交的作品中选出了12支BUIDL团队。10名评委受邀为这12支BUIDL团队投票,并分发25,000美元的奖金。10名评委被列入白名单,报名参加投票轮,他们总共向部署在Polygon上的MACI智能合约发送了39条消息。\n\n投票结束后,管理员(DoraHacks)统计票数并将最终结果发布到排行榜上,然后提供零知识证明来验证排行榜。\n\n\n \nOpenSea x Replit黑客马拉松投票结果的排行榜。\n\n
\nOpenSea x Replit黑客马拉松投票结果的排行榜。\n\n \n验证排行榜上显示的结果的零知识证明。\n\n作为一个通用框架,MACI可以用于黑客马拉松评委投票和开源社区投票之外的投票用例。然而,令人惊讶的是,在更多投票用例中采用MACI的情况却很少见。更广泛地说,区块链投票本身在现实世界中还没有被采用。\n\n使用区块链改进投票技术的好处显而易见,但为什么现实世界却没有向前发展?即使在区块链社区内,MACI的优势显而易见,为什么去中心化社区不普遍采用MACI?\n\n先进投票技术采用缓慢的一个主要原因并不是需求低,而是使用这种技术的困难。换句话说,我们需要改进技术,为现代投票产品提供更好的UX/UI,并降低用户的使用成本。\n\n## 用户体验\n除了开源社区治理之外,我们还需要构建更多接口供用户使用新的投票技术。DoraHacks为Web3生态系统和黑客马拉松社区提供了目前整个行业最好用的产品来提供资助。尽管DoraHacks.io上的接口本身具有特定的用例,但可以对其进行简化然后泛化,以便为更多用例构建更多接口。\n\n具体的前端策略尚未确定。然而,良好的用户体验对于该技术的采用至关重要,即使是在区块链社区中也是如此——这对于Dora Factory开发者来说很重要。\n## 投票费用\n通用区块链应该尽可能去中心化,并为所有类型的应用程序提供单一的基础设施。这些区块链并非旨在针对任何特定类型的应用程序进行优化,尤其是非货币或非金融应用。同时,当存在大量应用程序竞争同一组计算资源时,交易费用会出现波动。成本的不可预测性会给投票带来麻烦。\n\n为此,Dora Factory最近测试了一款名为Vota的新产品。Vota的想法是尝试特殊用途的区块链,并利用它们来不断优化投票技术和用户体验。目前,Vota还处于婴儿阶段。然而,我们可以想象几种不同形式的Vota。\n\n## 临时智能合约\n这是目前在DoraHacks.io上支持投票轮次的方式。每轮投票都作为单独的智能合约部署在特定的区块链上。大部分情况下,以太坊通常无法直接支持大部分的投票场景(这就是为什么Snapshot是以太坊社区默认使用的产品)。目前,Polygon和BNBChain是DoraHacks上大多数资助组织者和黑客马拉松组织者的热门选择。\n
\n验证排行榜上显示的结果的零知识证明。\n\n作为一个通用框架,MACI可以用于黑客马拉松评委投票和开源社区投票之外的投票用例。然而,令人惊讶的是,在更多投票用例中采用MACI的情况却很少见。更广泛地说,区块链投票本身在现实世界中还没有被采用。\n\n使用区块链改进投票技术的好处显而易见,但为什么现实世界却没有向前发展?即使在区块链社区内,MACI的优势显而易见,为什么去中心化社区不普遍采用MACI?\n\n先进投票技术采用缓慢的一个主要原因并不是需求低,而是使用这种技术的困难。换句话说,我们需要改进技术,为现代投票产品提供更好的UX/UI,并降低用户的使用成本。\n\n## 用户体验\n除了开源社区治理之外,我们还需要构建更多接口供用户使用新的投票技术。DoraHacks为Web3生态系统和黑客马拉松社区提供了目前整个行业最好用的产品来提供资助。尽管DoraHacks.io上的接口本身具有特定的用例,但可以对其进行简化然后泛化,以便为更多用例构建更多接口。\n\n具体的前端策略尚未确定。然而,良好的用户体验对于该技术的采用至关重要,即使是在区块链社区中也是如此——这对于Dora Factory开发者来说很重要。\n## 投票费用\n通用区块链应该尽可能去中心化,并为所有类型的应用程序提供单一的基础设施。这些区块链并非旨在针对任何特定类型的应用程序进行优化,尤其是非货币或非金融应用。同时,当存在大量应用程序竞争同一组计算资源时,交易费用会出现波动。成本的不可预测性会给投票带来麻烦。\n\n为此,Dora Factory最近测试了一款名为Vota的新产品。Vota的想法是尝试特殊用途的区块链,并利用它们来不断优化投票技术和用户体验。目前,Vota还处于婴儿阶段。然而,我们可以想象几种不同形式的Vota。\n\n## 临时智能合约\n这是目前在DoraHacks.io上支持投票轮次的方式。每轮投票都作为单独的智能合约部署在特定的区块链上。大部分情况下,以太坊通常无法直接支持大部分的投票场景(这就是为什么Snapshot是以太坊社区默认使用的产品)。目前,Polygon和BNBChain是DoraHacks上大多数资助组织者和黑客马拉松组织者的热门选择。\n \nL1区块链上的临时智能合约,所有投票消息发送到L1。\n\n使用临时智能合约并不完全是坏事。它很灵活,可以根据需要将其部署在任何地方。对于DoraHacks的用户而言,目前效果还不错,但无法同等满足所有投票需求。\n## L2 Vota\n如果我们创建一个专门用于投票的二层基础设施(L2),可以显着降低Gas费成本,并且可能能够在以太坊上实现低成本的投票。L2合约不必全部部署在以太坊上,它们可以更便宜,只需不时地提交L1交易以验证所有L2活动。\n\n我们可以进一步优化这个模型。通用L2必须经常提交到以太坊。Vota每轮只需向以太坊提交一笔交易,即每轮最多只需要一笔交易的Gas费成本。如果多轮在同一时间结束,他们可以共享一笔交易以进一步降低Gas成本,使投票L2更加现实可行。\n
\nL1区块链上的临时智能合约,所有投票消息发送到L1。\n\n使用临时智能合约并不完全是坏事。它很灵活,可以根据需要将其部署在任何地方。对于DoraHacks的用户而言,目前效果还不错,但无法同等满足所有投票需求。\n## L2 Vota\n如果我们创建一个专门用于投票的二层基础设施(L2),可以显着降低Gas费成本,并且可能能够在以太坊上实现低成本的投票。L2合约不必全部部署在以太坊上,它们可以更便宜,只需不时地提交L1交易以验证所有L2活动。\n\n我们可以进一步优化这个模型。通用L2必须经常提交到以太坊。Vota每轮只需向以太坊提交一笔交易,即每轮最多只需要一笔交易的Gas费成本。如果多轮在同一时间结束,他们可以共享一笔交易以进一步降低Gas成本,使投票L2更加现实可行。\n \n消息直接发送到L2合约。每轮结束时只有一笔交易被发送到L1区块链。\n## L3Vota(适用于L(n)Vota,其中n>=3)\nL3 Vota并非完全没有意义。通过已建立的L2,L3 Vota可以进一步将Gas费降低一个数量级。尽管L3交易最终在以太坊上记录和验证,但权衡之处在于要相信所选择的L2。\n\n当然,我们可以进一步将其扩展到L(n) Vota,因为L(2)…L(n-1)将向以太坊(或其他L1)提交交易。但显然信任链会让事情变得复杂。从目前的情况来看,很多著名的L2仍然依赖于单一的排序器(Sequencer);现在谈论L(4)可能还为时过早。\n
\n消息直接发送到L2合约。每轮结束时只有一笔交易被发送到L1区块链。\n## L3Vota(适用于L(n)Vota,其中n>=3)\nL3 Vota并非完全没有意义。通过已建立的L2,L3 Vota可以进一步将Gas费降低一个数量级。尽管L3交易最终在以太坊上记录和验证,但权衡之处在于要相信所选择的L2。\n\n当然,我们可以进一步将其扩展到L(n) Vota,因为L(2)…L(n-1)将向以太坊(或其他L1)提交交易。但显然信任链会让事情变得复杂。从目前的情况来看,很多著名的L2仍然依赖于单一的排序器(Sequencer);现在谈论L(4)可能还为时过早。\n \n## 应用链Vota\nDoraFactory开发人员创建了一个简单的“Hack”,允许CosmWasm合约使用Bellman验证SnarkJS生成的零知识证明。通过将Bellman纳入CosmWasm合约中,任何Cosmos应用链都可以快速支持zk应用程序。\n\n借助运行zk应用程序的能力,独立的区块链可以使用像Tendermint这样的软件架构来构建一条链。这些区块链的共识类似于BFT,因此它们通常可以支持多达100个左右的验证者。通过仔细选择利益不一致的验证者,独立的区块链可以足够安全和中立。\n
\n## 应用链Vota\nDoraFactory开发人员创建了一个简单的“Hack”,允许CosmWasm合约使用Bellman验证SnarkJS生成的零知识证明。通过将Bellman纳入CosmWasm合约中,任何Cosmos应用链都可以快速支持zk应用程序。\n\n借助运行zk应用程序的能力,独立的区块链可以使用像Tendermint这样的软件架构来构建一条链。这些区块链的共识类似于BFT,因此它们通常可以支持多达100个左右的验证者。通过仔细选择利益不一致的验证者,独立的区块链可以足够安全和中立。\n \n随着DoraHacks欢迎更多Cosmos应用链加入,基于应用链的Vota的一个明显用例是为黑客马拉松结果投票。除了DoraHacks之外,基于Cosmos应用链的Vota的作用远不止黑客马拉松评委投票。\n\n
\n随着DoraHacks欢迎更多Cosmos应用链加入,基于应用链的Vota的一个明显用例是为黑客马拉松结果投票。除了DoraHacks之外,基于Cosmos应用链的Vota的作用远不止黑客马拉松评委投票。\n\n \n应用链Vota的验证器数量较少,但精心挑选的验证器可以提供可靠的基础设施。\n\n值得注意的是,这些解决方案并不是排他性的。随着Vota的发展,不同的解决方案可能会交叉。例如,如果我们有一个独立的应用链版本的Vota作为主要基础设施,对于需要在特定L1上进行交易验证的用例,应用链可以向L1发送额外的交易。\n## 更好的匿名性\n目前正在进行的研究和工程工作旨在使MACI更加去信任。最初的MACI做出了一个重要的信任假设,即运营商不会腐败。这并不具有普遍性。为了改进这一点,有基于MPC的解决方案和非基于MPC的解决方案。目前,DoraHacks已经构建了一个基于ElGamal可重随机化加密的匿名MACI版本,该加密最初由KobeGuikan提出。它已在DoraHacks.io上的小型ETH研究资助轮中进行了测试。\n\n目前,在MACI本身被广泛采用之前推动匿名MACI的采用可能有点过早。然而,继续研究以减少一般投票机制的信任假设也很重要。\n
\n应用链Vota的验证器数量较少,但精心挑选的验证器可以提供可靠的基础设施。\n\n值得注意的是,这些解决方案并不是排他性的。随着Vota的发展,不同的解决方案可能会交叉。例如,如果我们有一个独立的应用链版本的Vota作为主要基础设施,对于需要在特定L1上进行交易验证的用例,应用链可以向L1发送额外的交易。\n## 更好的匿名性\n目前正在进行的研究和工程工作旨在使MACI更加去信任。最初的MACI做出了一个重要的信任假设,即运营商不会腐败。这并不具有普遍性。为了改进这一点,有基于MPC的解决方案和非基于MPC的解决方案。目前,DoraHacks已经构建了一个基于ElGamal可重随机化加密的匿名MACI版本,该加密最初由KobeGuikan提出。它已在DoraHacks.io上的小型ETH研究资助轮中进行了测试。\n\n目前,在MACI本身被广泛采用之前推动匿名MACI的采用可能有点过早。然而,继续研究以减少一般投票机制的信任假设也很重要。\n \n通过添加允许用户停用和更改其秘密密钥的操作来为MACI添加匿名性,而运营商无法知道谁添加了哪个新密钥。\n## GAS支付\n重要的是不要假设用户拥有加密货币。如果每个用户每笔交易都需要支付Gas费,那么区块链的用户将仅限于一小部分人。为了解决这个问题,MACI运营商可以预先存入一笔可退还的代币并支付用户的费用。该机制可以通过加油站来实现。\n\n加油站本身是一个驻留在Vota上的智能合约。在每轮开始之前,操作者可以选择使用它,也可以不使用它。通过使用加油站,运营商将DORA预先存入智能合约中,并且可以通过加油站支付与特定回合相关的交易费用。\n\n最有可能的是,Vota会部署一个默认的加油站,人们可以按需部署自己的具有不同支付逻辑的加油站。\n\n
\n通过添加允许用户停用和更改其秘密密钥的操作来为MACI添加匿名性,而运营商无法知道谁添加了哪个新密钥。\n## GAS支付\n重要的是不要假设用户拥有加密货币。如果每个用户每笔交易都需要支付Gas费,那么区块链的用户将仅限于一小部分人。为了解决这个问题,MACI运营商可以预先存入一笔可退还的代币并支付用户的费用。该机制可以通过加油站来实现。\n\n加油站本身是一个驻留在Vota上的智能合约。在每轮开始之前,操作者可以选择使用它,也可以不使用它。通过使用加油站,运营商将DORA预先存入智能合约中,并且可以通过加油站支付与特定回合相关的交易费用。\n\n最有可能的是,Vota会部署一个默认的加油站,人们可以按需部署自己的具有不同支付逻辑的加油站。\n\n \nGas支付合约是每轮投票的Gas余额的账本。\n## 结论\n特殊用途的区块链可能适用于广泛的特定应用用例,尤其是非金融用例。投票是区块链和零知识密码学可以帮助显着改善的最重要问题之一。提高投票透明度和效率可以减少人类社会和区块链社区内部的治理摩擦,从长远来看可以提高生产力。像MACI这样的协议为区块链上的投票应用程序创建了简洁的框架,但投票技术还需要做很多工作来改进。具体来说,我们需要一个用户友好的基础设施作为基础来长期改进投票技术,本文详细介绍了未来的工作。\n\n关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n
\nGas支付合约是每轮投票的Gas余额的账本。\n## 结论\n特殊用途的区块链可能适用于广泛的特定应用用例,尤其是非金融用例。投票是区块链和零知识密码学可以帮助显着改善的最重要问题之一。提高投票透明度和效率可以减少人类社会和区块链社区内部的治理摩擦,从长远来看可以提高生产力。像MACI这样的协议为区块链上的投票应用程序创建了简洁的框架,但投票技术还需要做很多工作来改进。具体来说,我们需要一个用户友好的基础设施作为基础来长期改进投票技术,本文详细介绍了未来的工作。\n\n关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n -
 @ 75da9402:77a65b5c
2023-07-17 17:48:42
@ 75da9402:77a65b5c
2023-07-17 17:48:42
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ 5ada3677:7c21c9db
2023-08-11 13:17:36
@ 5ada3677:7c21c9db
2023-08-11 13:17:36

翁達羅亞,Ondarroa,中世紀小城,中世紀海港,如今是人口8000左右的小城。
距離Bilbao大約40公里路程,公共交通的巴士或者火車,車資2塊到5塊不等,便宜到不可思議。這類長途巴士,高度準點,因為完全沒有堵車。Bilbao的長途巴士總站,是個令我非常驚奇的地方,設計完美,而且穩重美麗,高度有效,高度乾淨,一塵不染,車站內幾乎沒有一個工作人員,每車的司機負責檢票,慢悠悠檢了票,開了就走。車站內有一個居高的控制塔,像機場一樣,控制塔裡,也僅僅兩位工作人員。這是怎麼做到的?我至今沒有思考出來。


翁達羅亞,大西洋的一個海灣,景致美不勝收。我們在海灘上散步,一再感慨於平民百姓在海灘上的享樂,海裡打水球的孩子們,海灘上忘情玩沙的小東西們,附近的本地人、鄰近小城小鎮的鄰居們,老婦人老爺叔,自己拎個沙灘躺椅、一條大毛巾,來海邊躺半天。沙灘上結伴散步的中年夫婦層出不窮,肌膚鬆弛的身體,依然坦蕩蕩,比基尼絢爛多姿,自信安詳。雖然是烈日當空,大西洋的海水還是相當冷,默默散步是群眾運動。
離開海灘去吃午飯的時候,包子指給我看,牆上一幅標語:海灘是大家的。說到做到,牆上說的,和實際做的,沒有落差,佩服。


午飯的小館子,服務生問我們坐裡面坐外面,我愣了一下,通常沒有這一問,大家都是坐室外享受陽光,坐下之後才發現,原來這個小館子的室內,有一個很漂亮的舞台,唱爵士的,中午沒有樂隊,但是背景音樂也夠水平夠銷魂,很意外,如此小城小館子。
餐墊也有意思,寫了這麼些文字,按順序是:巴斯克語,西班牙語,加泰羅尼亞語,加利西亞語,法語,英語,我套一下:上海鹹話,普通話,溫州話,杭州話,日語,英語。對自己方言的珍惜,讓人唏噓。你不自愛自重,誰會尊重你呢?

 牆上的口號:海灘是大家的
牆上的口號:海灘是大家的
翁達羅亞有輝煌的歷史,至今是西班牙重要的漁港,漁獲非常豐富。19世紀的時候,此地就擁有龐大達18艘高空船的艦隊用於捕魚,8艘用來捕沙丁魚和鳳尾魚,2艘捕龍蝦。巴斯克地區盛產鐵礦,這裡是重要的運輸鐵礦砂的港口,帶來旺盛的貿易,差不多是甲午海戰風起雲湧的時間段吧。一直到今天,此地跟巴斯克其他地區一樣,是西班牙海軍水手的重要來源地。
翁達羅亞還盛產罐頭,最早是義大利兩三個家族帶來的,逐漸變成重要的一項工業。關於漁業和船業的相關活動,這裡至今看得到,比如修船、造船,等等,還有一個漁業學校,旗幟招展。


費一日的光陰,瀏覽一座中世紀小城、中世紀海港,感慨不已。


圖片一些是我拍的,一些來自網上
夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs
nostr:naddr1qqxnzd3exqunzvf4xs6ryvpkqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c6xk2dq
nostr:naddr1qqxnzd3exycrzvpcx5mnjve3qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8qk3y9
nostr:naddr1qqxnzd3exycrzvf58qervv3sqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cmy2dhr
nostr:naddr1qqxnzd3exyerxdpnx5ungdf5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cj0shly
nostr:naddr1qqxnzd3exymn2wph8yuryvekqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cx47vud -
 @ f8e6c643:03328ca9
2023-08-02 15:45:25
@ f8e6c643:03328ca9
2023-08-02 15:45:25Here’s the neat part, you don’t... \n...or rather, you can’t find rare satoshis. Rare satoshis don’t exist because individual satoshis don’t actually exist within the bitcoin network, only UTXOs. \n\n## But my wallet says I have satoshis.\nAnd the container of your food says it has calories. The bathroom scale says your body has lbs/kg. The tape measure says your floors have inches/cm. These are units of measure of a property of something, but they are not distinct individual units of the thing being measured. Calories measure energy. Scales measure mass. Rulers measure distance. These are properties of a thing, but not the thing itself. \n\nLikewise, satoshis (aka, sats) are a unit of measure for bitcoin UTXOs, which are the "things" that actually exist within the bitcoin network. A UTXO, or "unspent transaction output," can be very small, only a few hundred sats, or it can be very large, hundreds of millions or even billions of sats, but there are only UTXOs measured in sats and spendable by their corresponding private keys. There are no satoshis sitting in storage in bitcoin wallets and nodes. \n\n## If that's true, then why is Bitcoin Magazine selling "rare satoshis"?\nThey are salesmen in search of profit, and not all salesmen are honest. The product they are selling misrepresents the truth. Put simply, Bitcoin Magazine is lying about what they are selling. \n\nWhat they are actually selling is a UTXO measured in some amount of sats that can be cryptographically linked to another UTXO from the past that no longer exists. Why doesn't it exist? Because a UTXO is, by definition, "unspent." Once you spend one UTXO, new UTXOs are created and mined into a new block.\n\n## So I can't buy one of Hal Finney's satoshis?\nUnfortunately, no, you cannot. At best you could pay someone like Bitcoin Magazine to spend one of their UTXOs to a new UTXO at an address you control. It is up to you to decide if the cryptographic link to previous entries in the ledger has any added value or meaning beyond the sats-denominated value of the UTXO.\n\nIt would be a little bit like if I had a dollar bill, and I went to the bank and deposited it into your account, and then the bank destroyed that physical bill and replaced it with a new one when you came in to withdraw it. While you would now possess access to the $1 of value, you would not have the dollar bill that I deposited. In fact, it no longer exists, even though there is proof on the bank's ledger of the transfer of value from me to you.\n\n## Ok, so what? I can do what i want with my money.\nYes, you can. That is the freedom afforded to you by bitcoin. You are free to trade your sats for a lesser amount of sats. It's just my opinion that you ought to at least understand that that's all you're doing. \n\n🌽 🤙
-
 @ 5ada3677:7c21c9db
2023-08-11 13:01:48
@ 5ada3677:7c21c9db
2023-08-11 13:01:48
Deba小城,人口只有5000出頭一點的小城,從Bilbao坐車過去,三刻鐘的車程,有極美的海灘,海岸線悠揚綿長,整整一條海灘,滿地歡嬉的孩子,紛紛尖叫著縱身跳進大海裡。懶洋洋曬太陽的中年人,俊男美女豐富量產層出不窮。
我們在海灘上散步,頭上是滾燙的太陽,身上是清涼的海風,另一種境界的吹面不寒楊柳風,天堂一樣。
海邊三三兩兩幾間小鋪子,賣冰淇淋,雪糕,一些很古老的零嘴,比如棒棒糖,十分幫助我懷舊。
特別好的是,西班牙小城的這種海灘,遍地都是,公共交通簡簡單單,非常容易、非常便宜到達,普通人不必昂貴代價,人人可以享受。
所以,西班牙人是比較少去國外旅遊的一種人。
跟包子笑,18歲離開上海去歐洲讀書之前,幾乎去遍了東南亞的海灘,現在有了西班牙海灘了。



這個海灘,浪很細膩,層次豐富,是沖浪聖地,國家地理備加推崇。



小城裡的主教堂,坐下來吃個甜點心歇歇腳,此地的聖母像,酷似送子觀音娘娘,溫存慈悲,垂愛人間。
Deba小城,正好在朝聖路上,城中頻頻見到朝聖者,包子說他兩年前也是走朝聖路,第一次來這座城,還巧遇城裡過節。
這是這幾年過節的海報。



街角的房子很別緻,拍了照片,仔細看,才知道是警察局,警察們好像無事可幹,大玻璃窗裡,陳列著很多失物招領。想起來,我童年的時候,上海也很多失物招領,現在好像看不到了。是不失物了,還是不招領了?還是都不了?

黃昏時分,返回Bilbao之前,入城中的小咖啡館吃個點心。西班牙人的咖啡館跟酒吧是在一起的,大人們吃酒聊天,小孩子們在旁邊吃點心吃果汁,沒有兒童不可以進酒吧這回事。
西班牙朋友跟我說,是啊,我們跟孩子們在一起做很多事情、共渡很多時光,我們不會把孩子們留在家裡,自己去酒吧泡。
這個真是好。
想到還有很多很多的孩子們,父母常年在城裡打工,一年裡沒有幾天跟家鄉的寶貝們在一起,真是讓我有點淚目。
還有很多很多的父母,夜夜在外工作或者應酬,一天裡跟孩子們也是照個面僅僅。
如此不同的長大途徑,當然就有很多不同的結果darling你說是不是?




西班牙人的父母,各自有四個月的新生兒假期,每年暑假,父母各自有一個月的假期照顧放暑假的孩子們,加上暑期班,所以西班牙學校長達兩個月三個月的暑假,很普遍。
在Bilbao這些日子,是我半輩子看見嬰兒手推車最多的一段日子,滿街都是,每個時段都有,太多年輕夫婦推著一個兩個三個孩子出來。
Bilbao城中最優地段的城中河畔,是大片免費的兒童遊樂園。外灘啊,蘇州河畔啊,寸土寸金啊,一分錢不賺,給父母和孩子們。
有些選擇題,我們一直做不好,沒辦法。



圖片有些是我拍的,有些來自網上。
夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs
nostr:naddr1qqxnzd3exqunzvf4xs6ryvpkqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c6xk2dq
nostr:naddr1qqxnzd3exycrzvpcx5mnjve3qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8qk3y9
nostr:naddr1qqxnzd3exycrzvf58qervv3sqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cmy2dhr
nostr:naddr1qqxnzd3exyerxdpnx5ungdf5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cj0shly -
 @ 2d5b6404:d4b500b0
2023-07-08 00:56:26
@ 2d5b6404:d4b500b0
2023-07-08 00:56:26nostr streamからzap streamにタイトルも変更し大幅なアップデートがされました。 今までは自分でcloudflare streamに月額課金してマニュアル設定しなければなりませんでしたが、zap streamとOBSを紐づけてSATS(21 sats/min)を支払うだけで簡単にlive配信を開始することができるようになりました。
必要なものは3つだけです。zap streamとalby(アルビー)とOBSです。
はじめにzap streamにログインするためalbyのアカウント作成が必要になります。別の記事でalbyの登録方法をまとめたのでそちらを参考にしてみてください。
→primalが作成したalby(アルビー)の使い方ショート動画
OBSに関しては多くの解説動画がでていますのでそちらを参考に設定してみてください。 ぼくが参考にした動画です。→ https://youtu.be/ZQjsPJpMLiQ
最後にzap streamとOBSを紐づけるだけです。 zap streamのページを開いてalbyでログインします。 ログインしたら右上のアイコンの横のStreamを押します。

Stream Providers
API.ZAP.STREAM
Stream Url
rtmp://in.zap.stream/liveをコピーして、OBSの設定→配信のサーバーの欄に貼り付けます。
Stream Key
・・・・・・・・・をコピーして、OBSの設定→配信のストリームキーに貼り付けます。

次にBalanceのTOPUPを押してSATSを支払います。21 sats/min 1分21satsなので1時間だと1260satsを先に支払います。長時間配信する場合は多めに入金しておきましょう。
あとはEdit Streamでタイトルやサムネイルを設定してSAVEします。 アダルトコンテンツの場合NSFW Contentにチェックをいれてください。

zap streamとOBSの設定が完了したら、OBSで配信開始すれば勝手にzap streamでlive配信が開始されます。
以上がzap streamでlive配信する方法です。
ライブコーディングやゲーム配信をしているユーザーがすでにいますのでVtuderの方などどんどん配信してみてください。
-
 @ 20986fb8:cdac21b3
2023-07-29 06:45:23
@ 20986fb8:cdac21b3
2023-07-29 06:45:23YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.\n\nAs an incentive, participants can earn up to 100,000 SATs.\n\nRound 2 will be from 27th to 30th July\n\n### How to participate:\n1. Pick one or multiple Updates below, test it (them)\n2. Write your feedback and opinion (pros and cons are all welcomed)\n3. Post your article on Nostr via YakiHonne.com\n4. Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne\n5. Share the link to our group: http://t.me/YakiHonne_Daily_Featured\n5. Be Zapped!\n\n### Requirements:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion\n5. The top 10 posts will be zapped during each round.\n6. The evaluation will based on the article's depth, completeness, and constructiveness. \n7. Contact us for additional zaps if bugs are found.\n\n\n\n\n### Updates to be tested in Round 2:\n1. Comments: re-implemented and comments can be deleted\n\n2. NIP-25 supporting: users now can upvote and downvote\n\n3. Zap stats: Zaps sent and Zaps received can be seen from users profiles\n\n4. “login with an extension” button: now it is grayed out rather than invisible\n\n5. Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme\n\n6. Tags: click on the tags in the article to view the content under the tag\n\n7. Share: sharing posts with one click\n\n8. NIP-05: verify your profile\n\n\n\n### If you missed Round 1, the updates below could be tested as additions:\n\n1. Comment function: more user-friendly\n\n2. Stats area: clearly displays the interactive status of each article\n\n3. Following function: generated-key users can also be followed\n\n4. Curation function: easily add or remove articles from an existing curation\n\n5. Tags: search and browse articles with the tags\n\n6. Home feed scrolling pagination: optimized data fetching and faster loading time\n\n7. Article editing preview: preview the final version of the article while writing in MarkDown\n\nDon't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n
-
 @ 97c70a44:ad98e322
2023-06-29 15:33:30
@ 97c70a44:ad98e322
2023-06-29 15:33:30First, a product announcement.
Coracle now supports connection multiplexing, which can reduce bandwidth usage by over 90% depending on how many relays you use. It's opt-in for now, but you can set it up by going to Settings and entering
wss://multiplextr.coracle.socialas your "Multiplextr URL".You can check out the source code and self-host the library using this link. If you're a dev and want to add client support for multiplextr, the library I built to support this use case might be of use.
Now, on to your regularly scheduled blog post.

The above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"
This is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".
For my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.
Nevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?
I should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.
Two, and only two options
With all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.
Both alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.
On the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.
In either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.
It's all about routing
It seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.
The real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.
(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)
Here's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.
One of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.
This approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.
It also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.
With this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.
Making it happen
The difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.
This routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.
It also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.
In either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.
Conclusion
I think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.
-
 @ d830ee7b:4e61cd62
2023-08-11 05:47:04
@ d830ee7b:4e61cd62
2023-08-11 05:47:04ผมเกิดและโตในยุค 90’ ยุคเปลี่ยนผ่านทางเทคโนโลยีและวัฒนธรรมคาบเกี่ยว ได้เห็นวิวัฒนาการของสังคมในหลายๆ ส่วน โดยเฉพาะสิ่งที่เรียกว่า “Community” ที่ในอดีตไม่ได้มีกฏเกณฑ์หรือรูปแบบอันชัดเจนอย่างในปัจจุบัน.. ผมเกิดและโตในชนบทอันห่างไกลความเจริญ เรื่องราวและวิถีชีวิตที่จะเล่าจากนี้ไปก็จะขึ้นกับมุมมองหรือเลนส์ของผมเพียงคนเดียว

คอมมูนิตี้ในอดีต
ในความหมายแบบไทยๆ ที่ผมอยากจะบัญญัติมันเสียเอง มันเริ่มจากภาพของเด็กวัยกระโปกที่จับกลุ่มทำกิจกรรมสนุกสนานเฮฮากัน เล่นสนุกด้วยจุดมุ่งหมายและจิตใจอันบริสุทธิ์ ในยุคของผมนั้นการปั่นจักรยานไปเรื่อยๆ กับกลุ่มแก๊งค์เพื่อนๆ เป็นกิจกรรมสุดโปรดพอๆ กับเด็กทุกวันนี้รวมตัวกันเล่น ROV หรือ ROBLOX เลยก็ว่าได้
การผจญภัยของเด็กๆ มักจะมีกิจกรรมสุดท้ายรอพวกเขาอยู่ มันอาจเป็นการลงเล่นน้ำตามลำคลอง หนอง บึง หรือปีนต้นไม้เพื่อความเท่ สำรวจโลกเพื่อเรียนรู้อะไรบางอย่าง มันก็สนุกในแบบของมัน
เมื่อโตขึ้นมาในวัยมัธยม เด็กผู้ชายเริ่มเกาะกลุ่มกันเหนียวแน่น พวกเขาโตมาด้วยกันผ่านอะไรด้วยกันมามาก ความสัมพันธ์นั้นแน่นแฟ้นระดับยอมตายแทนกันได้ มันไม่มีสถานที่จัดเตรียมไว้ให้เรา ดังนั้นพวกเราต้องเลียบเลาะเสาะหาสถานที่สุมหัวคุยกันเอาเอง หัวข้อสนทนาในยุคนั้นไม่มีอะไรที่ไปไกลเกินกว่าประสบการณ์ที่พวกเขามี หรือเรื่องที่เคยได้เรียนมา รวมทั้งสื่อเพียงไม่กี่อย่างที่เข้าถึงได้ วิทยุและโทรทัศน์
ผู้ใหญ่ วัยทำงาน ไม่ได้มีรูปแบบสังคมอย่างวัยรุ่น กลุ่มสังคมของพวกเขานั้นเป็นวงเล็กๆ บ้านใกล้เรือนเคียง มานั่งรวมตัวพูดคุยกันทั่วไปในเรื่องสัพเพเหระ ชีวิตสโลว์ไลฟ์ที่ไม่ได้มีความเร่งรีบอะไร บางกลุ่มตั้งวงเหล้าใส่กันแต่เช้า ล้มหมู ล้มวัว ทำกับแกล้มสรวนเสเฮฮา อีกกลุ่มก็เข้าวัดฟังธรรมตามประเพณีปฏิบัติสืบต่อกันมา คนในอดีตราว 20-25 ปีก่อนในท้องถิ่นของผมนั้น ไม่ได้มีความเครียด ไม่ได้รับรู้ถึงความโสมมอะไรที่หยั่งรากลึกอยู่ภายในระบบเลย คำว่า Toxic คืออะไร? พวกเขาคงนึกถึงยาฆ่าหญ้า
เงิน ในวันที่ยังมีคุณค่าทำให้พวกเขามีความสุข ผมอดนึกถึงภาพเหล่านั้นไม่ได้จริงๆ

โลกเสมือนที่ใหญ่กว่าโลกแห่งความจริง
คอมมูในแบบที่ผมประทับใจที่สุดและดูซีเรียสจริงจังที่สุดเห็นจะเป็น “สภากาแฟ” ประจำหมู่บ้านหรือในตลาด ร้านกาแฟโบราณแบบในภาพยนตร์ยุคเก่า หลายคนคงพอนึกออก กลุ่มคอมมูนี้จะสนใจเหตุบ้านการเมือง อ่านหนังสือพิมพ์จนกระดาษขาด ฟังรายงานข่าวกันแต่เช้า ถกกันดุเดือดเหมือนเป็นอีกโลกนึงเลยทีเดียว และสภากาแฟแบบนี้นี่แหละที่ผมชอบไปนั่งฟังมากที่สุด ด้วยความที่ผมเป็นเด็กชอบเรียนรู้อะไรใหม่ๆ เรื่องต่างๆ ที่ผู้ใหญ่คุยกันมันช่างทำให้ผมสมองงอกมากจริงๆ
ตัดภาพ Fast forward กลับมาในยุคปัจจุบัน เราแทบไม่ได้เห็นกลิ่นอายหรือบรรยากาศอะไรแบบนั้นอีกแล้ว คอมมูนิตี้บนโลกแห่งความจริงมันดับสลายไปสูญสิ้น ผู้คนอพยพไปใช้ชีวิตกันบนโลกออนไลน์จนอาจิณ แม้ตัวพวกเขาเองผมก็คิดว่าคงไม่รู้สึกตัว เราหลุดจากโลกความจริงไปไกล เราหลงไปกับข้อมูลที่ส่วนใหญ่เป็นการล่อลวง สนตะพายจมูกลากจูงพวกเราไปทางไหนก็ได้ น่าเศร้าเหลือเกิน..
ตีวงให้แคบเข้ามาในสังคมการลงทุนโดยเฉพาะในแวดวงบิตคอยน์ ผมพบเห็นเพียงสื่อส่วนใหญ่ที่ชี้นำและชักพาผู้คนเข้าสู่คอมมูนิตี้ด้วยเป้าหมายสำคัญคือ “เงิน” และ “ความร่ำรวย” ผมคิดไปเองว่าเจ้าของสื่อก็คงจะไม่รู้ตัวเองเช่นกันว่ากำลังโดนสนตะพายจมูกอยู่โดยใครสักกลุ่มหรือใครบางคน ทั้งหมดนี้จะไม่ช่วยให้ใครเก่งพอจะเอาตัวรอดหรือปรับตัวได้เองในชีวิตการลงทุน มันไม่ทำให้หลายคนเข้าใจแก่นแท้หรือธรรมชาติของตลาดทุนอย่างแน่นอน เมื่อคนส่วนใหญ่ภายในคอมมูนิตี้ถูกชักพาในไปทิศทางนั้น บทสนทนาที่เราจะพบได้อย่างเดือนดาดบนโลกโซเชียลก็คงเป็นข่าวความเคลื่อนไหวระยะสั้นที่ส่งผลต่อราคาสินทรัพย์ พัฒนาการไร้สาระที่เอามาปลุกปั่นให้ดูดี พฤติกรรมการอวดไลฟ์สไตล์ อวดร่ำอวดรวยของอินฟลูเอนเซอร์ ที่ถูกหลอกมาอีกทีว่าควรสร้างภาพให้ดูน่าเชื่อถือ น่าเศร้ามากจริงๆ
มองหาที่ทางของตัวเอง
ผมเชื่อลึกๆ นะว่า บิตคอยเนอร์ในยุคหลังๆ ที่ยังไม่ผ่านสักไซเคิลมักจะรู้สึกอึดอัด หงุดหงิดเวลาต้องการ “คนคุยด้วย” ในชีวิตจริง มันไม่มีอีกแล้วกลุ่มปั่นจักรยานล่ากิ้งก่า กลุ่มสุมหัวที่ปลายนา หรือสภากาแฟ มันเหลือเพียงโลกออนไลน์ที่ต้องไปอยู่ท่ามกลาง Anonymous ร้อยพ่อพันแม่ กลางผู้คนที่ตัวเราเองก็ยากที่จะแสดงออกหรือเปิดใจ..
“คุยบิตคอยน์กับใครก็ไม่รู้เรื่อง” มันเรื่องปกติ.. ปกติจริงๆ ประสบการณ์การป้ายยาส้มแบบเฟลๆ น่าจะเคยเกิดขึ้นมาแล้วกับพวกเราทุกคน จุดนี้เองที่ผมตระหนักได้ว่า คนชอบเรื่องเดียวกันก็ควรได้คุยกับคนประเภทเดียวกัน อย่างน้อยก็ชื่นชอบเรื่องเดียวกันก็ยังดี ส่วนหน้าตาหลังการรวมตัวกันจะออกมาเป็นยังไงก็ปล่อยให้สังคมมันปรับตัวของมันไปเองอย่างออแกนิกก็แล้วกัน
“จับกลุ่มคุยกันเรื่องบิตคอยน์” มันเป็นที่มาของไอเดียแบบแนวๆ รายการ “สภายาส้ม” จนล่าสุดเราพึ่งมี “สภายาม่วง” ที่แคแรคเตอร์แตกต่างกันพอสมควร มันเป็นการสนทนากับบนโลกสีม่วงที่แต่ละคนจะได้เป็นตัวของตัวเองแบบไร้การปรุงแต่ง ได้คุยในสิ่งที่อยากคุย ได้เล่นกับคนในแชท ได้หัวเราะแบบที่ไม่ต้องกั๊ก ได้ทำเรื่องน่าอายแต่สนุกชิบหายเลย
ผมเล่ามาถึงตรงนี้ อย่าเข้าใจผิดว่าผมลากมาตบด้วยการขายของ ผมแค่กำลังจะบอกว่า.. สภาแบบนี้มันไม่เห็นจำเป็นต้องรอให้ Right Shift ทำ ลองจินตนาการสิว่า มันมีสภาแบบนี้อยู่ที่หมู่บ้าน ตำบล อำเภอ หรือจังหวัด หรือภูมิภาคของคุณเอง เช่น สภาชลบุรี, สภาขอนแก่น, สภาน่าน หรือสภายาส้มเขาใหญ่ ฯลฯ
มันเป็นไปได้นะ.. คำถามคือเราจะสร้างสภาแบบนั้นขึ้นมายังไง.. ก็ใช้ประโยชน์จากสื่อโซเชียลมีเดียที่เรามีนี่แหละ ประกาศตามหาพวก ทำความรู้จัก นักเจอกัน เริ่มจากเหตุการณ์เล็กๆ จุดเริ่มต้นน่ารักๆ นำไปสู่วัฒนธรรมสังคมอันยิ่งใหญ่แบบที่พวกเราทำกันมาแล้วนั่นไง
ผมอยากเห็นอะไรแบบนั้น อยากให้มีภาพความประทับใจจากหลายๆ พื้นที่มาอวด มาโชว์ มาแบ่งปันกัน มันก็ดีกว่าการเช็คอินสถานที่ต่างๆ ที่ตัวเราเองก็ไม่เห็นเคยอินกับมันเลย..
รออยู่นะ.. สภายาส้ม สภายาม่วง ทั่วไทย
-
 @ 97c70a44:ad98e322
2023-06-01 13:46:54
@ 97c70a44:ad98e322
2023-06-01 13:46:54I think I cracked the code on private groups.
Instead of relying on relays to implement access control as in this PR, we could combine the Gift Wrap proposal with @PABLOF7z's nsec bunker to create private groups with easy administration and moderation!
Gift wrap fixes DM metadata leakage by using a temporary private key to send a DM to a recipient. The recipient decrypts the wrapper to find a regular nostr event inside. This could be another kind 4 as in the proposal, or anything else. Which means you can send kind 1's or anything else in a wrapped event.
Now suppose you had a pubkey that you wanted to represent a group instead of a person. Put its nsec in a (modified) nsec bunker, and now you can allow other people than yourself to request signatures. A shared private key! Anyone who has access to this nsec bunker could also de-crypt any gift wrapped note sent to it. Relay-free read access control!
There are lots of ways you could manage this access list, but I think a compelling one would be to create a NIP 51 list (public or private!) of group members and set up the nsec bunker to authenticate using that list. Boom, dynamic member lists!
You could also create a NIP 51 list for admins, and pre-configure which event kinds each list is allowed to post using the group's nsec. So maybe members could only publish wrapped kind-1's, but admins could publish wrapped kind-0's (you can now zap a group!), kind 9's for moderation, updated member and moderator lists, normal kind 1's for public information about the group, etc.
Gift wrap would support:
- Leak-free DMs
- Fully private groups
- Public-read groups (nsec bunker would allow for admin, but everyone would publish regular instead of wrapped events).
- Organizations and other shared accounts, with role-based authorization (list/kind mappings)!
Of course, no clients currently support this kind of thing, but support would not be hard to add, and it creates an entirely new set of affordances with two very simple applications of the core protocol.
There are a few drawbacks I can think of, of course. Gift wrap makes it harder to search notes by tag. You could:
- Leave all tags off (other than for DM recipient as in the proposal)
- Selectively keep tags that aren't revealing of identity
- Encrypt tag values. When a client wants to query a tag, it must encrypt the value using the same pubkey and include that in the filter. This, I think, is ok for the group use case above.
There are also a number of proposals in the works to fix NIP 04 DMs which are apparently broken from a cryptographic standpoint, so implementing this should probably wait until that stuff is sorted out. But it should be possible however that ends up materializing.
So am I nuts? Or is this a galaxy brain solution?
-
 @ 20986fb8:cdac21b3
2023-07-29 06:44:43
@ 20986fb8:cdac21b3
2023-07-29 06:44:43A long-term Nostr Creation Grant, with a 17,500,000 SATs funding pool\n\n\nRound 3 starts on 22 July till 5 Aug!\n\nCreating for You and Your Fans through Nostr and ZAP.\n\nNostr is a simple, open and censorship-resistant protocol, the number of users has been growing, and more and more users use zap to tip content. Nostr's growth over the past six months is amazing, which is a great encouragement for all nostrians. This is also a great encouragement for content creators. Earn SATs by posting your creations on nostr, allowing your readers to encourage better content creation while tipping your creations.\n\n\n
 \n
\n \n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n
\n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n \n\n\n\n\n
\n\n\n\n\n \n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n
\n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n -
 @ 3bf0c63f:aefa459d
2023-08-10 18:02:31
@ 3bf0c63f:aefa459d
2023-08-10 18:02:31Things that we mostly can't fix, but that maybe could have been done better if they were here from the beginning -- or something like that.
- The
NOTICEmessage would have been better if it had structure likeOKmessages have. That would have allowed a more direct communication between relays and users, instead of relays being inside a client black box. - Choosing secp256k1 felt cool and maybe it still feels cool because it is the Bitcoin curve, but since many people have pointed out that other curves and algorithms are much faster maybe picking those would have been better.
- Writing a spec for direct messages and implementing them was bad. In my defense, it was an attempt to please the public, but still I should have not have done that, or thought more about it before doing it.
- Thinking that kind 1 should be used for all the things "text" just restricted the ability of clients to do different interfaces. If we had different kinds for replies, quotes, comments and "root" posts from the beginning that would have been better.
- For a long time I didn't realize Nostr wasn't useful just for "social networking" things. I wonder what else could have been better designed in the relay-client interface if the needs of non-social-networking apps were kept in mind.
- The querying system is sometimes too generic, it could have been better if it was more restrictive, but more complete. For example: allowing generic querying over tags is weird, can lead to O(n²) issues in some cases and relays are left to fend for themselves -- on the other hand we can't query for the absence of some tags. But I don't know how any of these things could have been better even today, so maybe it wasn't so bad.
- Making the events be JSON: sometimes I think this was a bad idea and a binary format would have been better, but most of the times I think Nostr wouldn't have become any popular at all if this was the case -- also binary is slower than JSON in JavaScript, so I guess this wasn't a completely bad choice. Perhaps if something like NSON had been adopted from the start, though, that would have been better for everybody.
When I decided to write this I had one item in mind, but when I started I forgot what that was. I'll add it here back when I remember.
- The
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.\n\nIsto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.\n\nhttps://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico\n\nSegue artigo na íntegra. 👇\n\n\nSem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.\n\nCom a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.\n\nHá algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.\n\nLamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.\n\nNo entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.\n\nPela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.\n\nInfelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.\n\nComo a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.\n\nEm virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.\n\nComo são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.\n\nPartindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).\n\nPara a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.\n\nDe fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.\n\nSem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.\n\nVocê também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.\n\nSabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.\n\nTanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.\n\nMas vamos analisar cada um desses tópicos separadamente para entender isso melhor.\n\nRacismo\n\nQuando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.\n\nAproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.\n\nDiversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.\n\nNa Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.\n\nSe estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.\n\nA verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.\n\nE é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.\n\nAbsolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.\n\nA integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.\n\nOu seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.\n\nA discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.\n\nPara citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.\n\nO exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.\n\nIndo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.\n\nA verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.\n\nFascismo\n\nQuando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.\n\nMas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.\n\nEm um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.\n\nPortanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.\n\nÉ claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?\n\nAs leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.\n\nEssa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.\n\nExistem duas fortes razões para isso:\n\nA primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.\n\nAlém do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.\n\nOutra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.\n\nPortanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.\n\nSe você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.\n\nEm primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.\n\nMachismo\n\nMuitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.\n\nApesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.\n\nComo sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.\n\nO liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.\n\nTão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.\n\nA verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.\n\nO que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.\n\nO nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?\n\nHomofobia\n\nQuando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.\n\nA Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.\n\nSegue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:\n\n“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)\n\n“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)\n\n“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)\n\nSe você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.\n\nPortanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.\n\nInfelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.\n\nDefinitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.\n\nQualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.\n\nUma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.\n\nComo se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.\n\nEvidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.\n\nAfinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?\n\nHomossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.\n\nDiscriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.\n\nConclusão\n\nA militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.\n\nNós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.\n\nQuanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.\n\nA história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.\n\nPois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 450a57c5:5a1cf9dd
2023-08-16 02:48:34
@ 450a57c5:5a1cf9dd
2023-08-16 02:48:34Title: AI in Adolescent Online Wellbeing
Introduction
In today's digital age, adolescents are growing up in a world heavily influenced by technology and the internet. As they navigate the complexities of online interactions, entertainment, and information consumption, concerns about their wellbeing have risen. This is where Artificial Intelligence (AI) comes into play. AI has the potential to positively impact adolescent online wellbeing by providing support, guidance, and protection in various aspects of their online lives.
Understanding Adolescent Online Wellbeing
Adolescence is a critical developmental stage marked by identity formation, social interactions, and emotional growth. The internet has become an integral part of adolescents' lives, offering numerous opportunities for learning, communication, and entertainment. However, it also presents challenges such as cyberbullying, online predators, misinformation, and excessive screen time. Ensuring a positive online experience for adolescents requires a balance between the benefits and risks of the digital world.
AI-Powered Solutions
-
Online Safety and Security: AI can play a vital role in safeguarding adolescents from online threats. Machine learning algorithms can analyze online content and identify potentially harmful or inappropriate material, alerting parents or guardians to take appropriate action. Additionally, AI-powered parental control tools can help regulate screen time, filter content, and monitor online activities to ensure a safer online environment.
-
Mental Health Support: Adolescence is a period of emotional vulnerability, and AI can assist in identifying signs of mental health issues. Chatbots and virtual assistants can engage in supportive conversations, offering resources and suggestions for seeking professional help if necessary. AI-powered apps can also track emotional patterns, helping adolescents better understand and manage their mental health.
-
Digital Literacy and Critical Thinking: AI can enhance adolescents' ability to navigate the vast amount of information online. AI-driven platforms can teach digital literacy skills, including how to identify credible sources, evaluate information accuracy, and recognize fake news. By promoting critical thinking, AI contributes to a healthier online experience.
-
Personalized Learning: AI can tailor educational content to match individual learning styles and preferences. This ensures that adolescents remain engaged and motivated in their online learning endeavors. Adaptive learning platforms can adjust the difficulty level of content based on the student's performance, fostering a more effective learning process.
-
Social Interaction Monitoring: AI can help parents and guardians keep track of their adolescent's social interactions without invading their privacy. Through sentiment analysis and language processing, AI can identify potential signs of cyberbullying, peer pressure, or emotional distress, allowing timely intervention.
Ethical Considerations and Limitations
While AI offers promising solutions, there are ethical concerns to address. The collection and use of personal data, potential biases in AI algorithms, and the risk of overreliance on technology are issues that need careful consideration. Striking a balance between AI-driven support and human guidance is crucial to ensuring a well-rounded approach to adolescent online wellbeing.
Conclusion
Adolescence is a formative phase where a positive online experience can contribute significantly to overall wellbeing. AI holds the potential to be a valuable ally in this endeavor, providing safety, support, and guidance to adolescents as they navigate the digital landscape. By addressing the challenges while harnessing the benefits of AI, we can create a healthier and more enriching online environment for the younger generation.
-
-
 @ 22f22e98:aabb8a5e
2023-08-09 19:39:04
@ 22f22e98:aabb8a5e
2023-08-09 19:39:04Make your notes look very official
If I had anything to say, I'd put it here. I can bold important things. Does it work? * Bullet points * Italics 3. Third thing 4. ~~Strikethrough~~
++Underline doesn't seem to work++
Time for a new section
This is a quote
Note link: nostr:note1gguda28qkf8x4dg02ud46j27zzt6jvqcnnceayvqgfphetl79jvqm8x7sl
https://nostr.build/i/efc07801e2d4a5e734d3019397ce81b7e50bd59ad512ce27caac01c601d0f23b.gif
| Tables | Tables | | --- | --- | | Data | Data | | Data | Data | | Data | Data |
H1
H2
H3
H4
H5
H6
H5 and H6 look the same in the preview.
code code more codealso codeI'm gonna write some shit soon.
-
 @ f4db5270:3c74e0d0
2023-07-23 09:10:31
@ f4db5270:3c74e0d0
2023-07-23 09:10:31 \n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n
-
 @ 57fe4c4a:c3a0271f
2023-08-16 00:45:53
@ 57fe4c4a:c3a0271f
2023-08-16 00:45:53📝 Summary: The Serverless Payjoin idea has advanced with the development of Payjoin version 2, allowing for payjoin receiver functionality without a secure public endpoint. Concerns were raised about securely sharing the secret key and potential attack vectors. Anonymized network connections were suggested to mitigate the risk of tying transactions to clients. The security of sharing the secret key in the payment URI was also discussed, with suggestions for alternative methods. The Blockchain Commons UR was proposed as the best choice for encoding pub keys in the
pj=endpoint, and a v2 upgrade was deemed necessary for JavaScript ur library support. Concerns were raised about payjoin implementations written in JavaScript and the need for a v2 upgrade to support receiving. Progress is being made with reference libraries in Typescript, and plans to expand. Some wallets are using URs in JavaScript, but no open-source libraries have been announced yet. The BIP has been updated to use a DH cryptosystem to prevent funds loss from leaked BIP 21 URIs.👥 Authors: • AdamISZ ( nostr:npub1nv7tjpn2g8tvt8qfq5ccyl00ucfcu98ch998sq4g5xp65vy6fc4sykqw2t ) • Christopher Allen ( nostr:npub19g47w5ewcqlpd7n07wpkp5cvcu2gjwrse0vl47l0avwl9hu933xsqct5d0 ) • Dan Gould ( nostr:npub1l58t68e4t3wgtva5enuvr4aaxxlut7srnhx88avfyfv25jzhkedq6nxs5k ) • David A. Harding ( nostr:npub16dt55fpq3a8r6zpphd9xngxr46zzqs75gna9cj5vf8pknyv2d7equx4wrd )
📅 Messages Date Range: 2023-08-09 to 2023-08-13
✉️ Message Count: 7
📚 Total Characters in Messages: 83741
Messages Summaries
✉️ Message by Dan Gould on 09/08/2023: The Serverless Payjoin idea has progressed towards a formal specification of Payjoin version 2, allowing payjoin receiver functionality without a secure public endpoint.
✉️ Message by AdamISZ on 10/08/2023: The text discusses the Serverless Payjoin idea and raises concerns about securely sharing the secret key and potential attack vectors.
✉️ Message by AdamISZ on 10/08/2023: The concern with this architecture is that relays can time correlate messages and potentially tie transactions to clients, unless anonymized network connections are used.
✉️ Message by David A. Harding on 13/08/2023: The sender is concerned about the security of sharing the secret key in the payment URI and suggests using a different method. Another person raises the issue of potential security risks when posting payment URIs in public.
✉️ Message by Dan Gould on 12/08/2023: Blockchain Commons UR is suggested as the best choice for encoding pub keys in the
pj=endpoint, and a v2 upgrade is needed for JavaScript ur library support.✉️ Message by Christopher Allen on 13/08/2023: Concerns about payjoin implementations written in JavaScript and the need for a v2 upgrade to support receiving. Progress is being made with reference libraries in Typescript and plans to expand. Some wallets are using URs in JavaScript but no open source libraries have been announced yet.
✉️ Message by Dan Gould on 13/08/2023: The BIP has been updated to use a DH cryptosystem, ensuring that leaked BIP 21 URIs do not pose a risk of funds loss.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ f4db5270:3c74e0d0
2023-07-22 16:32:18
@ f4db5270:3c74e0d0
2023-07-22 16:32:18 \n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n \n\n\n-----------\n\nThe original photo\n\n
\n\n\n-----------\n\nThe original photo\n\n
-
 @ 76c71aae:3e29cafa
2023-05-30 21:59:50
@ 76c71aae:3e29cafa
2023-05-30 21:59:50Joining a new digital community can be an exhilarating and empowering experience. This has been observed on numerous occasions when people join new platforms such as Nostr, BlueSky, Farcaster, Post.news, Tribel, and many others, as well as older social media platforms such as blogs, Usenet, LiveJournal, Xanga, AOL, Flickr, Facebook, Instagram, and TikTok.
Initially, these spaces create an idealistic environment where individuals are eager to connect, share, and participate in a virtual gathering that resembles a festival. However, it is worth examining what it is about these new social spaces that generates such a euphoric atmosphere, and whether it is feasible to sustain this utopian sentiment as communities expand and develop.
The Magic of Connection:
Joining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.
Utopias Form Where They Shouldn’t Exist:
The concept of "Paradise Built in Hell" becomes evident during natural and economic disasters. I personally witnessed this idea during Argentina's economic crisis in the early 2000s. Despite the difficulties, people came together and collaborated in new ways to support each other, as the collapsing economy demanded it. This same phenomenon is observed following earthquakes and other natural disasters, where people often speak of those days with a magical, almost reverential tone.
Rebecca Solnit argues that "Disaster is when the shackles of conventional belief and role fall away and the possibilities open up; people rise to the occasion or sink to the level of their fears and prejudices." In these challenging moments, we see the true nature of humanity: our ability to show compassion, resilience, and unity in the face of adversity.
Social Media and All Digital Spaces Have Physical Analogues:
The similarities between digital and physical communities are rooted in the fact that each has its own distinct set of unspoken rules and social norms. Just as we know to be quiet in a library, loud at a concert, social at a cocktail party, and anti-social on the subway, we also understand the unique dynamics of different digital platforms. Twitter resembles a bustling dive bar, Instagram an art gallery, TikTok an amusement park hall of mirrors, and Facebook a community hall rented for a retirement party. Every new digital space has its analogues in the physical world because human interaction remains consistent, even if the medium differs. As we navigate the ever-changing landscape of digital communities, we are reminded of our innate ability to adapt, connect, and thrive in the face of adversity. This adaptability empowers us to form new connections and rediscover the power of community, whether in the digital or physical realm.
The Small Community Paradox:
To maintain the utopian atmosphere of new digital communities, one effective approach is to keep them small or create numerous smaller sub-communities. In these sub-communities, people can engage in the social labor of connection and conflict resolution.
It is important to note, however, that this approach may conflict with the network effect principle. This principle states that each new member joining the community increases its overall value for all participants. As communities grow and the network effect takes hold, the utopian feeling may often fade, giving way to sub-tribes and conflict.
Nevertheless, with a confident approach, the community can adapt and navigate these challenges to foster a positive environment for all members.
The Fleeting Nature of Utopia:
The fleeting utopian sensation experienced within new digital communities is inevitable. Although it is not the design or coding of platforms such as BlueSky, Nostr, Mastodon, or Scuttlebutt that generates this feeling of euphoria, it is instead the human dynamics of joining something novel and building a community that cultivates this enchanting ambiance. Hakim Bey's concept of Temporary Autonomous Zones (TAZs) endorses this notion, demonstrating how short-lived spaces of freedom and interaction can emerge within established social structures. As communities expand and progress, the real challenge lies in sustaining the initial energy and sense of connection that made them so desirable in the first place.
Parallel to Protests and Uprisings:
This utopian sentiment is not limited to digital communities; it is also present during times of revolution, protests, and uprisings. There is a profoundly human element to the sense of love, connection, solidarity, and community that arises during these moments.
The most impactful moments of my life have been when I participated in protests that were met with repression. These protests ranged from tree-sits to protect old-growth redwoods in the forests where I grew up, to large convergences of the anti-globalization and anti-war movements, to Occupy's reclamation of public spaces, and to recent Black Lives Matter protests. All of these protests were scenes of anguish, repression, and, in some cases, violence, especially from the police. However, they were also places where I experienced the most love, connection, humanity, and common purpose. We were all individuals, together, living and breathing solidarity.
Cultivating and Sustaining Utopian Energy:
To preserve the utopian essence of new digital communities as they grow, one approach is to foster a culture of empathy, connection, and inclusiveness from the very beginning. Prioritizing these values and actively engaging in conflict resolution can help communities maintain that special feeling.
Another way to preserve the utopian essence of digital communities is to focus on building tools for the construction and maintenance of these digital public spaces. Unlike corporate social media platforms that only provide an illusion of public space while actually being privately owned, like a shopping mall, we need to create spaces that are community-controlled and collectively owned as a commons with confidence.
Understanding the Commons:
The concept of the commons offers a compelling alternative to traditional models of state or private ownership. Elinor Ostrom, the first woman to win the Nobel Prize in Economics, conducted extensive research on this topic, and her findings are truly remarkable. Through her work, she proved that commons can be effectively managed and maintained, debunking the misguided belief that these resources are doomed to fail and end in tragedy.
Designing for Digital Commons:
To design digital commons, we must prioritize transparency, decentralization, and participatory governance. By empowering users to make decisions about the direction and rules of their digital communities, we ensure that the spaces remain truly public and that the needs and desires of the community are at the forefront.
Open-source technology and decentralized protocols can play a vital role in the development of these digital commons. By allowing users to maintain control over their data and ensuring that no single entity has a monopoly over the platform, we create an environment that fosters collaboration, creativity, and innovation.
The Characteristics of a Well-Functioning Digital Commons:
- Clearly defined boundaries: Members and their rights are easily identifiable, and access to the shared digital resources is well-regulated.
- Proportional equivalence between benefits and costs: Users contribute to the commons according to their capabilities, and benefits are distributed fairly among members.
- Collective decision-making: Users have a say in shaping the rules and policies that govern their digital communities, promoting a sense of ownership and accountability.
- Monitoring: Transparent systems are in place to track the usage and management of shared resources, ensuring that members adhere to established rules.
- Graduated sanctions: Penalties for rule violations are proportional and escalate based on the severity and frequency of the transgressions.
- Conflict resolution mechanisms: Efficient and fair processes are in place to address disputes among members, promoting harmony and trust within the community.
- Minimal recognition of rights to organize: Users have the autonomy to self-organize and make decisions about their digital commons without excessive interference from external authorities.
- Nested enterprises: Digital commons are organized into multiple, interconnected layers of governance, with smaller communities operating within the context of larger ones, fostering collaboration and coordination.
By incorporating these principles into the design of digital commons, we can create spaces that are robust, sustainable, and equitable. This, in turn, fosters innovation, collaboration, and genuine community engagement.
Developing Community-Driven Tools:
To create and maintain digital public spaces, we need tools that empower communities to effectively manage their digital commons. These tools should facilitate communication, conflict resolution, and decision-making while promoting inclusiveness, empathy, and shared values. By empowering communities to shape their digital spaces and collaboratively resolve issues, we can help preserve the utopian essence that initially attracted people to these platforms.
Adapting to Growth and Change:
As digital communities continue to grow, it's crucial to acknowledge that their needs and challenges will inevitably change over time. To maintain a utopian atmosphere, we must be willing to adapt and consistently improve the tools and processes that sustain these digital public spaces. By promoting continuous feedback and collaboration among community members, we can ensure that the platform remains responsive to the needs of its users, fostering an environment of connection and belonging with conviction.
Conclusion:
Joining a new digital community can be a thrilling experience, but maintaining that sense of euphoria as the community grows can be difficult. To achieve this, we must design and construct digital commons that prioritize community control, collective ownership, and participatory governance. With the appropriate tools and a dedication to adapting to the evolving needs of the community, we can create spaces that continue to foster the magic of connection even as they transform. In doing so, we can nurture and sustain the utopian energy that makes these digital spaces so unique.
Post Script:
Since the completion of this essay, Bluesky has evolved from its initial utopian stage to a phase grappling with context, norms, and scalability. With an increasing user base, the once agreed-upon behavioral norms began to crumble. The initial playfulness, while staying within the community's value constraints, took a disturbing turn when individuals started posting racist and homophobic content. The situation deteriorated rapidly, escalating to the point of issuing death threats. Inspired by the "Nazi bar" parable, the community demanded urgent action to outline acceptable behavior and remove those who couldn't comply.
Bluesky, currently hosted on a single server, possesses the capability to enforce a unified set of community guidelines and terms of service. The creators of Bluesky, much like any other social media platform's developers, aimed for a laissez-faire approach. However, they eventually had to revise the terms of service and ban the trolls. This action was chaotic and resulted in significant loss of trust and goodwill.
Additionally, this did not aid the community in establishing governance for the burgeoning social media commons. Protocols such as Bluesky, Nostr, DSNP, Scuttlebutt, Farcaster, and Lens are not designed to operate in isolation. Among these, only ActivityPub and Mastodon have successfully implemented a model to manage abuse and community moderation at scale. Nonetheless, potential solutions are under development. I've personally contributed to proposals for specifications, codes, and norms on Nostr and know that Bluesky's team is making similar strides.
It is essential that the user community actively participate in this process. The Design Justice movement provides a valuable blueprint and strategies for achieving this. By applying principles of co-design and design justice, we can collaboratively build solutions. The stakes are too high to leave this endeavor to a small group of technologists alone.
-
 @ f4db5270:3c74e0d0
2023-07-22 16:28:30
@ f4db5270:3c74e0d0
2023-07-22 16:28:30 \n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n-----------\n\n\nThe beginning...\n\n
\n\n-----------\n\n\nThe beginning...\n\n \n\n-----------\n\n\nThe original photo\n
\n\n-----------\n\n\nThe original photo\n
-
 @ 87d2ca95:4a7b2baf
2023-08-15 07:33:57
@ 87d2ca95:4a7b2baf
2023-08-15 07:33:57The rapid advancement of technology has led to the integration of artificial intelligence (AI) into various aspects of our lives. One significant application of AI is in the realm of smart building systems. These systems are revolutionizing the way buildings are designed, constructed, operated, and maintained, leading to enhanced efficiency, sustainability, and user comfort.
Understanding Smart Building Systems: Smart building systems refer to the integration of various technologies and AI-driven solutions to create intelligent, responsive, and efficient buildings. ThesDe systems encompass a wide range of features, including automated lighting, heating, ventilation, air conditioning (HVAC), security, and energy management. The primary goal is to create buildings that can adapt and optimize their performance based on real-time data and user preferences.
The Role of AI: AI plays a pivotal role in making smart building systems truly intelligent. Machine learning algorithms analyze vast amounts of data collected from sensors, IoT devices, and user interactions. This data-driven approach enables buildings to learn patternDs, anticipate needs, and adjust their operations accordingly. For instance, AI algorithms can predict occupancy patterns and adjust HVAC systems to maintain a comfortable environment while conserving energy.
Benefits of AI in Smart Building Systems: 1. Energy Efficiency: AI-driven systems can optimize energy consumption by analyzing data and adjusting lighting, temperature, and other utilities. This leads to reduced energy waste and lower operating costs.
-
User Comfort: Smart building systems can create personalized environments based on user preferences. Lighting, temperature, and other factors can be adjusted to ensure optimal comfort for occupants.
-
Predictive Maintenance: AI algorithms can predict equipment failures and maintenance needs by analyzing sensor data. This enables timely maintenance, reducing downtime and repair costs.
-
Security Enhancement: AI-powered security systems can identify unusual patterns and detect potential threats. Facial recognition and anomaly detection contribute to improved building security.
-
Space Utilization: AI can analyze space utilization patterns to optimize office layouts and room allocations, leading to efficient space utilization.
-
Sustainability: Smart building systems contribute to sustainability by minimizing energy consumption and reducing the building's carbon footprint.
Challenges and Future Directions: Despite the many benefits, integrating AI into smart building systems presents challenges. Data privacy concerns, interoperability issues among different devices, and the complexity of managing these systems are some of the obstacles that need to be addressed.
Looking ahead, the future of AI and smart building systems is promising. As AI technologies continue to evolve, buildings will become even smarter, learning from user behavior, adapting to changing conditions, and contributing to a more sustainable and efficient urban environment.
In conclusion, AI has significantly transformed the landscape of smart building systems. The integration of AI-driven solutions enhances energy efficiency, user comfort, security, and sustainability. As technology continues to advance, the potential for creating smarter, more adaptive buildings is limitless, promising a future where our built environment works in harmony with the latest technological advancements.
-
-
 @ 31da2214:af2508e2
2023-08-09 19:11:59
@ 31da2214:af2508e2
2023-08-09 19:11:59"I do not want to miss a good chance of getting us a slice of this magnificent African cake." —Leopold II of Belgium
This post was originally published on Twitter by @AfricanArchives ( 2023-08-09 )
After the Berlin conference of 1884-1885 ( conference where European nations established the 'legal' claim that all of Africa could be occupied by whomever could take it), different European nations set out to mount their flags all over Africa. The nations set out murdering africans, and then taking their wealth to make Europe wealthier.
King Leopold II set out for the Congo and declared it his territory proclaiming it his property, the people and the land, quickly turning the land into a money-making enterprise. Congo was rich in many minerals, but at the time it was richer in ivory and rubber. He set up a system that was extremely harsh on the people — a system that, if they did not reach regular rubber collection quotas, he murdered and mutilated the indigenous people.
King Leopold II’s government declared that rubber harvesting was a necessary tax that would be paid to the crown by those who lived on the land. This literally meant that Leopold took the lands and wealth of a people and obliged them to work on their own land as slaves.

The rubber industry in Europe was booming and he had to meet the demands of the market. As punishment for not fulfilling the quota they cut-off of your limb or get murdered.
 (Congolese being forced to display severed hands of members of the commmunity for a photo)
(Congolese being forced to display severed hands of members of the commmunity for a photo)Leopold II had an army which consisted of about 19,000 european mercenaries, called Publique Force. The military aggressively recruited Africans into its lower ranks as well. These Africans were press-ganged into service and they were executed if they resisted.
The European officials were so ruthless and based on their rubber hatred and targeting that they created a rule for soldiers to cut off and deliver the hands of any of the Congolese citizens killed for failing to fulfill their quota.
The source began to decline thus becoming slightly scarce . It was then more difficult to obtain the rubber, as many individuals had to climb tall trees to reach the vines. People may often drop from the trees and fall to their deaths. In addition to the shooting and maiming, disease was another factor that caused millions to die. The wellbeing of the workers was not taken into account by the Belgians, who fed them with unhealthy meat and vegetables, and starved them most of the time.

However, this did not make the Belgians stop. For the commercial benefit of their resources, they continued the slavery and enslavement of the people of the Congo. The burning of their villages was one of the painful accounts of the genocide of the Congolese. The commissioners and their officers also gave a certain quota to a whole village to fulfill and if they failed their villages and inhabitants were burnt down.
Diplomatic talks and pressure from many quarters would later lead Leopold II to renounce his rule over the Free State of the Congo and then hand it over to the Belgian Government, and then the Congo to be named the Belgian Congo.
To this day, the Congo is still the property of the Europeans and has been held in constant conflict by European powers trying to seize their wealth while keeping the citizens divided.
If you love this content though sometimes triggering, You can support the history page/project here through donations/tips to keep up on: ko-fi.com/africanarchives
-
 @ c2232226:586fa98c
2023-08-15 04:22:26
@ c2232226:586fa98c
2023-08-15 04:22:26Project EcoToken: Revolutionizing Sustainability through Tokenization
Sustainability and environmental consciousness have become integral values in today's world. As the global community seeks innovative ways to promote eco-friendly practices and reward environmentally conscious choices, a groundbreaking initiative called Project EcoToken has emerged. This pioneering project leverages the power of blockchain and tokenization to create a transformative ecosystem that encourages and rewards the adoption of eco-friendly products and services.
The Urgency of Environmental Responsibility
With growing concerns about climate change and the depdletion of natural resources, the need for sustainable practices has never been more pressing. Individuals and businesses alike are searching for practical ways to contribute to a greener future. However, the challenge lies in incentivizing and tracking these efforts effectively.
Introducing Project EcoToken
Project EcoToken is not merely a digital concept; it's a visionary solutfion aimed at fostering environmental sustainability through blockchain technology. By tokenizing eco-friendly products and services, this project aims to create a comprehensive ecosystem where individuals and businesses can actively participate in promoting sustainability while being rewarded for their cogntributions.
Key Objectives and Features
-
Tokenized Eco-Products: Project EcoToken tokenizes eco-friendly products and segrvices, allowing consumers to make informed choices by verifying the environmental impact of their purchases.
-
EcoRewards: Participants are rewarded with EcoTokens for choosing sustainable options, such as using renewable energy sources, reducing waste, and supporting ethical businesses.
-
Transparent Impact: The blockchain ledger ensures transparency and traceability, enabling users to track the positive environmental impact of their choices.
-
Community Engagement: Project EcoToken fosters a commgunity of eco-conscious individuals and businesses, encouraging collaboration and knowledge sharing.
Empowering Sustainability in the Web3 Era
The impact of Project EcoToken extends far beyond the realm of tokenization:
-
Behavioral Shift: By incentivizing eco-friendly choices, Project EcoToken encourages a shift towards more sustainable consumption patterns.
-
Consumer Empowerment: Consumers gain the power to support products and services aligned with their values, ultimately influencing market demand.
-
Positive Impact: The transparent tracking of environmental contributions builds a sense of achievement and collective impact.
-
Global Network: As the project gains traction, it has the potential to create a global network of participants committed to sustainable practices.
Paving the Way for a Greener Future
As Project EcoToken evolves, collaboration with environmental organizations, businesses, and tech innovators will shape its trajectory. The project's commitment to promoting eco-friendly practices through tokenization aligns perfectly with the growing demand for sustainable solutions.
In a world where environmental responsibility is paramount, Project EcoToken stands as a symbol of positive change. By tokenizing eco-friendly products and services, the project envisions a future where every purchase becomes an opportunity to contribute to a more sustainable planet. As Project EcoToken gains momentum and garners support from individuals, businesses, and advocates of environmental conservation, it has the potential to transform the way we approach consumption and collectively work towards a greener, more sustainable future.
-
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ b804f68e:2fb0fa1f
2023-08-09 17:59:22
@ b804f68e:2fb0fa1f
2023-08-09 17:59:22
I've always had the itch to write and to share, but until nostr I've always felt like there were so many unnessary steps that must be taken to start writing. You have to go through KYC sign up processes, you have to pay for premium memberships, you have to make sure you're keeping up with SEO, etc. I also feel the sort of topics I want to write about, or opinions and perspectives I want to share don't align and resonate with most of what was / is trending in fiat land. Plus, having to constantly worry about being cancelled for some really stupid reason, self censor, and write pieces that are clearly for clout and virtue signaling in order to go "viral" just doesn't appeal to me at all.
But now, for me and for all of those who just want to write for the sole purpose of writing, and to write without all of the BS, we now have a home where we can do that, and write to our hearts' content! And if our writings touch the hearts of our readers, readers can directly send their token or rather "zap"ken of appreciation directly in the BEST money ever, bitcoin!
I've always had the itch to write but never felt fully committed and motivated to pursue that itch, which I now know is because the incentives did not align with my want to write, and because there was no platform or digital space in which I felt completely comfortable to share.
When I would attempt to write in the fiat world, the fiat mind would often get in the way of my writing. But on nostr I feel I am able to write from the heart and allow my creativity to flow naturally.
I have found my home.
nostr
writing
-
 @ f0ff87e7:deeeff58
2023-08-09 17:42:01
@ f0ff87e7:deeeff58
2023-08-09 17:42:01Note: this is a transcript of a talk given at a local Bitcoin event.
As Bitcoiners, we are all well aware of the dangers posed to our privacy, security, and freedom by CBDCs, digital ID, vaccine passports, carbon credits, and so on. We don’t even have to theorise about these dangers because governments and central bankers are happy to boast the “benefits” of CBDCs include the ability to control what you can buy and make your money expire.
But how do these things actually work? Governments are vague on the technical details, preferring instead to use buzzwords like “blockchain”, “interopterbility”, and the most profidious of all – “programmable money.”
What we do know is most – if not all – of the current CBDC trials include partnerships with the private banking and technology sectors. Specifically, some of the big players supplying the technology for CBDC infrastructure include Amazon, Accenture, Microsoft, IBM, the Linux Foundation, and ConsenSys – a company founded and run primarily by the co-founders of Ethereum itself, and largely funded by JP Morgan.
This should come as no surprise for those familiar with the tech industry. The cloud has been a rapidly growing sector for years now, and government departments are among the big customers. Already the NHS and HMRC use AWS for instance. In the US, even the CIA uses AWS.
Likewise, we are already aware of the fact that commercial banks are in charge of all digital money production in the form of credit creation, and this commercial bank money makes up close to all the fiat in the world today. It is therefore expected that a new form of digital money is being created with the help of commercial banks.
In this talk I hope to answer the question of how these outsourced, cloud based systems work in regards to CBDCs, digital ID, and other Orwellian bollocks. If you are left with questions, feel free to ask them at the end.
The first thing to understand is although these projects are almost entirely based around EVM – the Ethereum Virtual Machine – they will not be run on the Ethereum blockchain or any other public blockchain. Instead they will make use of private deployments of an EVM based blockchain.
In fact, you can learn exactly how this works from AWS right now. They’ll let you spin up your own EVM deployment. You will be the admin. You can choose how much – if any – of the wallets or transactions are made public, but as the admin, you have full view into and control over every single one. And if that sounds suspiciously similar to E-Coin from Mr Robot, that’s because it is.
Which brings me neatly onto the next essential concept – permissioned blockchains. Private deployments of EVM do not rely on proof of stake as you might suspect. Instead they operate under so-called proof of authority. This means exactly what it sounds like.
Remember when everyone who held USDC in Tornado Cash saw it frozen overnight as the smart contract was added to the OFAC sanction list? That was possible because USDC is a permissioned ERC-20 token. Circle is able to blacklist any wallet at any time, so that any USDC currently held in any given wallet, as well as any that may be sent to it in the future, is frozen. Even if it is on a hardware wallet or another non-custodial solution, it does not matter. The tokens themselves are a smart contract, the code is upgradable and includes a blacklist, so there is nothing you can do.
If you extrapolate USDC to all tokens held across an entire blockchain, you now understand permissioned blockchains, proof of authority, and the concept of “programmable money.” Not just in concept, but also in practice. Just as USDC is a Solidity smart contract on Ethereum, a CBDC will be a Solidity smart contract on a private Ethereum fork. And once that infrastructure is deployed, and if it is widely adopted, you have a platform that any smart contract with any additional function can be deployed on in the future. Nothing technologically prevents this – you have to simply trust the state not to expand their power… I know, hilarious.
Whenever you hear the term “programmable money” thrown around, remember it means money that a central authority has full control over, including the power to arbitrarily freeze everything linked to your digital ID, such as your CBDC wallet and passport, as well as the ability to make your money expire and decide what you are permitted to spend it on, and of course the aforementioned power to add to that list at will.
Although these national CBDC deployments will all be separate, they will largely be based on EVM, which will make them interoperable – this means that, for example, you can make a GBP payment to someone in the USA and it’ll instantly settle in USD. Provisions for CBDC support are already being integrated into fast payment systems around the world, which could allow banks to give you no choice in whether you use a CBDC. There is an ongoing active push for CBDC integration into fast payments right now, driven by the World Bank and the Bill and Malinda Gates Foundation.
Additionally, you can expect discounts on purchases to be offered in return for using a CBDC, and possibly even a free airdrop ala Worldcoin – in China they already gave away free digital yuan. We may even see UBI trials conducted with the CBDC. Because hey, the first hit is free, right?
You may have also heard a lot of talk around the idea of “tokenisation.” This is where physical goods are represented by NFTs on one of these state/corporate controlled blockchains. If everything you own is logged on a blockchain and linked to a digital ID, access to those goods can be removed if your CBDC wallet is frozen. With an increasing number of internet-of-things devices, our assets can literally be frozen.
Now, these are currently all ideas being thrown around as CBDCs themselves are being piloted. Tokenisation could turn out to be vaporware. But once this infrastructure rolls out into production, it is a full EVM blockchain linked to digital IDs of every user, and the state as well as banks and other private interests will have the power to add to the scope of that blockchain whenever they want.
The implementations that are already being developed aside from CBDCs themselves include digital ID as a prerequisite for a CBDC – since everything will be KYC’d, digital ID is a certainty. Digital passports are a natural extension of digital ID, and yes there are specific proposals from the likes of the WHO, EU, and WEF, among others, to make these vaccine passports in exactly those words – and finally carbon credits, including “individual carbon tracker” projects aimed at logging where individuals travel, how they travel, what they eat, what they buy, and more – effectly creating a social credit score in all but name.
The overarching theme through all of this highlights the true danger of CBDCs. It is not simply about the government knowing what you’ve spent money on. It is about the level of overt control the state is granting itself over how you spend your money, how long you have to spend it, what you do and say, whether you your fancy new EV will let you drive in the morning, and most vitally of all, the ability to add to their powers at will simply by writing a smart contract.
With all of these invasive systems of surveillance and control being rolled out onto a single platform, or at the very least, interoperable platforms, it seems to me impossible these won’t become interconnected – after all, that’s what interoperable means.
How do you escape this? You know that already.
Thank you for listening.
-
 @ aa8de34f:a6ffe696
2023-08-14 19:06:45
@ aa8de34f:a6ffe696
2023-08-14 19:06:45Bitcoin; A Beacon of Hope, in the Troubled Waters of the Fiat Money System. An Ethical and Social Science Perspective
I. Setting the Scene
In the saga of economics the fiat money system has taken center stage for more than a century. This system, where our money isn't backed by a commodity but by our trust in institutions has faced numerous crises that have exposed its inherent flaws. As a student of sciences I recognize the impact this has on societal well being, economic stability and power dynamics. The storyline of this system is riddled with turns such as inflation, debt cycles and power concentration among a few resulting in economic disparities and social unrest.
Imagine living in a world where your earned savings could vanish overnight due to decisions made away in corporate boardrooms. This is not some fiction but an unfortunate reality for many under our current fiat money system. In this essay we delve into Bitcoin—a cryptocurrency—as a protagonist, within this narrative. By exploring the social science principles that form the foundation of Bitcoin, our goal is to bring awareness to how our monetary system impacts our freedom, fundamental rights and democracy. Additionally we will delve into how Bitcoin has the potential to reshape this narrative.
II. Background: The Evolution of Money and the Current State of the Fiat Money System
Money the lifeblood of our economies has undergone changes, throughout history reflecting the evolving needs and technological advancements of societies. From barter systems to metals, paper currency and now the digital era each transformation has left its mark on our journey through time.
The fiat money system, which currently governs our economy has been the force for the century. However it resembles a sandcastle built close to the waters edge— to inflation and economic instability. Picture a castle where central banks hold the keys to influence your moneys value at their discretion. This is how our fiat money system operates. In this essay we will explore whether Bitcoins decentralized nature can reshape this landscape by offering a fair economic terrain.[1][2]
III. The Flaws in the Fiat Money System
Imagine envisioning the economy as a web interconnecting various nodes, with the U.S. Dollar acting as its central hub—the reigning fiat currency. The current economic system, which has been the foundation of our economies is displaying signs of strain. Fiat money, in essence is a currency that isn't tied to a commodity. Instead its value derives from the trust we have in the government that issues it (Wilck, Lynch, & Kauffmann, 2014).
Imagine a seesaw with banks on one side and ordinary individuals on the other. The control that banks have over the money supply can disrupt the balance. Result in inflation. This inflation gradually erodes peoples purchasing power. Creates instability. Moreover our system relies heavily on debt—a bit like a house of cards. Money is generated through lending practices leading to cycles of boom and bust that can jeopardize well being. These problems extend beyond economics. Contribute to widening inequality and instability.[3]
IV. The Unintended Consequences of Fiat Money
The impact of this can be especially harmful, for individuals with fixed incomes or limited savings. Take, for instance the decision made by the United States to abandon the gold standard in 1971. Since then the purchasing power of the U.S. Dollar has significantly decreased by, than 85% showcasing how inflation relentlessly eats away at its value.
The debt that emerges as a result of the fiat money system has repercussions leading to crises, social inequality and international instability. These consequences further exacerbate the divide, among groups.
Imagine a society where the gap between the wealthy and the impoverished continuously widens with each cycle. In such a society ones stability in life can be disrupted by decisions made in banking boardrooms. This is the reality we face due to the existence of the fiat money system. Hence it raises a question; Is it possible for us to navigate a path? Can Bitcoin, as a cryptocurrency serve as our guiding light, towards a balanced and fair economic landscape?
V. Bitcoin; A Revolutionary Response, to an Imperfect System
In the aftermath of the 2008 crisis, when economies were crumbling and faith in financial institutions was fading a new kind of currency emerged. Bitcoin, a currency came into existence as a reaction to the perceived flaws of the conventional financial system. Imagine it as a phoenix rising not from ashes but from the ruins left behind by a catastrophe.
The underlying philosophy of Bitcoin is to separate money from the control of governments—a concept that has gained momentum since the crisis. Its design principles, such as decentralization, fixed money supply and proof of work mechanisms position it as an alternative to our current fiat money system.[3][5].
VI. Bitcoin; A Beacon of Ethical Efficiency
In contrast, with the fiat money system Bitcoin has been specifically crafted to address many of its problems. Operating as a currency means that it functions without relying on any central authority. Consequently it cannot be influenced by governments or central banks for their benefit. Is safeguarded against manipulation by a privileged few individuals. The supply of bitcoins is fixed, with only 21 million ever to be produced. This scarcity sets it apart from currencies, which can be printed without limitations.
Bitcoins core design principles include decentralization, transparency and immutability. These ensure that all transactions are transparent and cannot be changed, providing a level of security and trust compared to financial systems. Additionally it eliminates the need, for intermediaries resulting in cost reduction and increased efficiency.
One key feature of Bitcoin is its Proof of Work (PoW) consensus mechanism. Despite concerns about its energy consumption it's important to note that this energy usage is necessary for the security of the system. Miners solve problems using computational power and energy to validate transactions and secure the network effectively. While the total energy consumption may seem significant according to Wolfram Alphas data it serves as a trade off, for the security and decentralization benefits it offers [2].
VII. Practical Applications and Advantages of Bitcoin
Bitcoins potential goes beyond theory; it has already been put into practice across sectors demonstrating its applications and benefits. These real life examples demonstrate how Bitcoin can address concerns linked to the fiat money system, such, as transparency and decentralization.
Bitcoin as Legal Tender: The Case of El Salvador[6]
In a historic move, El Salvador became the first country to adopt Bitcoin as legal tender in 2021. This bold step signifies Bitcoin's growing acceptance and its potential to serve as a viable alternative to traditional fiat currencies. The country's move to embrace Bitcoin has opened up new possibilities for financial inclusion, economic growth, and innovation.
VIII. The Challenges and Criticisms of Bitcoin
According to a study, by Bonneau, Miller, Clark, Narayanan, Kroll and Felten in 2015 it was observed that the value of Bitcoin can fluctuate greatly which can result in losses for users. This volatility may discourage users. Undermine Bitcoins reliability as a stable form of value storage.
Another concern raised is the impact of Bitcoin mining. The mining process involves solving problems to validate transactions and add them to the blockchain requiring substantial computational power and energy. This has sparked worries about the carbon footprint associated with Bitcoin especially considering the pressing need to address climate change. Critics argue that this is wasteful; however they fail to consider the security and efficiency provided by Proof of Work (PoW). PoW makes the Bitcoin network highly resistant to attacks, necessitating energy consumption as an aspect of maintaining a global transaction system.
Bitcoin has also faced criticism for its association with activities like money laundering and illegal trade due to its nature. Consequently there have been calls, for regulation and oversight that could potentially undermine Bitcoins nature and privacy advantages (Sas & Khairuddin 2017).
The regulation of Bitcoin remains an issue. While there are some who argue against it expressing concerns, about activities and market stability there are others, including myself who believe that Bitcoins inherent design principles make it self regulating. The transparency of its blockchain and the decentralized nature of Bitcoin create a system where market forces and network consensus drive its operation and governance [2].
IX. Conclusion
As we find ourselves at the intersection of evolution the current fiat money system presents its challenges such as inflation, economic disparity and centralized control. This calls for a shift. Enter Bitcoin. A beacon of hope in the landscape. Its decentralized nature and limited money supply offer an alternative to the system.
From an ethical and social sciences perspective Bitcoin is more than a currency. It serves as a tool for promoting inclusion reducing inequality and outlining a blueprint for a more democratic financial system. The urgency for regulation on Bitcoin may not be as immediate as some might think. Its design principles inherently provide security, transparency and fairness while effectively bypassing the shortcomings of the fiat money system.
Envision a world where money isn't controlled by a rather acts as a democratic medium accessible to all individuals. Bitcoin brings us closer, to this vision of reality. It tackles shortcomings that exist within the fiat currency system and signifies a notable advancement, in the progression of money. The potential for Bitcoin to reshape our system into one that's fairer and more effective is not just an abstract idea but something we can realistically achieve. As we navigate the path in finance Bitcoin serves as a guiding light offering a voyage, towards a financial landscape that is more inclusive, equitable and open.
Footnotes
- Yermack, D. (2013). Is Bitcoin a real currency? An economic appraisal. National Bureau of Economic Research. https://doi.org/10.3386/w19747 [↩]
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. https://bitcoin.org/bitcoin.pdf [↩]
- Saraswat, S., Chauhan, V., & Faujdar, N. (2016). Analysis on Crypto-Currency. International Journal of Computer Applications, 144(6), 975-8887. https://dx.doi.org/10.21172/1.91.28 [↩]
- Saraswat, S., Chauhan, V., & Faujdar, N. (2016). Analysis on Crypto-Currency. International Journal of Computer Applications, 144(6), 975-8887. https://dx.doi.org/10.21172/1.91.28 [↩]
- Monem, M., Ahmad, A., Jumana, R., Ahmed, R., & Arif, H. (2020). Efficient Blockchain System based on Proof of Segmented Work. 2020 IEEE Region 10 Symposium (TENSYMP), 1717-1722. https://dx.doi.org/10.1109/TENSYMP50017.2020.9231027 [↩]
- El Salvador: Launching Bitcoin as Legal Tender - Case - Faculty & Research - Harvard Business School (hbs.edu) https://www.hbs.edu/faculty/Pages/item.aspx?num=62068 [↩]
References
Bonneau, J., Miller, A. K., Clark, J., Narayanan, A., Kroll, J. A., & Felten, E. (2015). SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. Retrieved from https://dx.doi.org/10.1109/SP.2015.14
Fauzi, M. A., Paiman, N., & Othman, Z. (2020). Bitcoin and Cryptocurrency: Challenges, Opportunities and Future Works. Retrieved from https://dx.doi.org/10.13106/jafeb.2020.vol7.no8.695
Khairuddin, I. E., & Sas, C. (2019). An Exploration of Bitcoin Mining Practices: Miners' Trust Challenges and Motivations. Retrieved from https://dx.doi.org/10.1145/3290605.3300859
Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. Bitcoin.org Narayanan, A., Bonneau, J., Felten, E., Miller, A., & Goldfeder, S. (2016). Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction. Princeton University Press.
Sas, C., & Khairuddin, I. E. (2017). Design for Trust: An Exploration of the Challenges and Opportunities of Bitcoin Users. Retrieved from https://dx.doi.org/10.1145/3025453.3025886
Tapscott, D., & Tapscott, A. (2016). Blockchain Revolution: How the Technology Behind Bitcoin Is Changing Money, Business, and the World. Penguin.
Wilck, J. H., Lynch, D., & Kauffmann, P. (2014). Bitcoin: A Pedagogical Guide for the College Classroom. Retrieved from https://dx.doi.org/10.2139/ssrn.2436823
Zappia, C., Chen, Y., Pavone, P., & Pisani, M. (2018). Bitcoin and the Blockchain as Possible Corporate Governance Tools: Strengths and Weaknesses. Retrieved from https://dx.doi.org/10.2139/ssrn.3180606
-
 @ 97c70a44:ad98e322
2023-06-26 19:17:23
@ 97c70a44:ad98e322
2023-06-26 19:17:23Metadata Leakage\n\nIt's a well-known fact that Nostr's NIP 04 DMs leak metadata. This seems like an obvious flaw, and has been pointed out as such many times. After all, if anyone can see who you're messaging and how frequently, what time of the day, how large your messages are, who else is mentioned, and correlate multiple separate conversations with one another, how private are your communications really?\n\nA common retort repeated among those who "get" Nostr (myself included) is "it's not a bug, it's a feature". This hearkens back to the early days of the internet, when internet security was less than an afterthought, and social platforms throve on various permutations of the anonymous confessions-type app. How interesting to be able to flex to your friends about whom you're DMing and how often! Most conversations don't really need to be private anyway, so we might as well gamify them. Nostr is nothing if not fun.\n\nIn all seriousness though, metadata leakage is a problem. In one sense, Nostr's DMs are a huge improvement over legacy direct messages (the platform can no longer rat you out to the FBI), but they are also a massive step backward (literally anyone can rat you out to the FBI). I'm completely confident we'll be able to solve this issue for DMs, but solving it for other data types within Nostr might pose a bigger problem.\n\n# Social Content\n\nA use case for Nostr I've had on my mind these last few months is web-of-trust reviews and recommendations. The same sybil attack that allows bots to threaten social networks has also been used as a marketing tool for unscrupulous sellers. NPS surveys, purchased reviews, and platform complicity have destroyed the credibility of product reviews online, just like keyword-stuffed content has ruined Google's search results.\n\nProof-of-work would do nothing to defend against this attack, because the problem is not volume, it's false credibility. The correct tool to employ against false credibility is web-of-trust — verifiable trustworthiness relative to the end user's own social graph.\n\nThis is a huge opportunity for Nostr, and one I'm very excited about. Imagine you want to know whether the vibro-recombinant-shake-faker (VRSF) will result in visible abs in under 6 days. Well, it has over 4 thousand 5-star reviews on Amazon, and all the 1-star reviews are riddled with typos and non sequiturs. So it must work, and make you smarter into the deal! Well, sadly no, visible abs are actually a lie sold to you by "big gym".\n\nNow imagine you could find your three friends who fell for this gyp and ask them what they thought — you might just end up with a lower average rating, and you'd certainly have a higher level of certainty that the VRSF is not worth the vibra-foam it's molded from.\n\nThis same query could be performed for any product, service, or cultural experience. And you wouldn't be limited to asking for opinions from your entire social graph, it would be easy to curate a list of epicureans to help you choose a restaurant, or trusted bookworms to help you decide what to read next.\n\nCurrently, big tech is unable to pull this off, because Facebook won't share its social graph with Google, and Google won't share its business data with Facebook. But if an open database of people and businesses exists on Nostr, anyone can re-combine these silos in new and interesting ways.\n\n# Notes and other Spies\n\nSo that's the pitch, but let's consider the downsides.\n\nAn open social graph coupled with recommendations means that not only can you ask what your friends think about a given product, you can ask:\n\n- What a given person's friends think about a product\n- What kind of person likes a given product\n- How products and people cluster\n\nThat last one in particular is interesting, since it means you could find reasonable answers to some interesting questions:\n\n- Does a given region have fertility problems?\n- What are the political leanings of a given group?\n- How effective was a particular advertisement with a given group?\n\nThis is the kind of social experiment that has historically earned Facebook so much heat. Democratizing this data does not prevent its correlation from being a violation of personal privacy, especially since it will be computationally expensive to do sophisticated analysis on it — and the results of that analysis can be kept private. And to be clear, this is a problem well beyond the combination of social information and public reviews. This is just one example of many similar things that could go wrong with an open database of user behavior.\n\nNot to put too fine a point on it, we are at risk of handing the surveillance panopticon over to our would-be overlords on a silver platter. Just as walled gardens have managed us in the past to sway political opinion or pump the bags of Big X, an open, interoperable content graph will make building a repressive administrative state almost too easy.\n\n# Let's not give up just yet\n\nSo what can we do about it? I want a ratings system based on my social graph, but not at the expense of our collective privacy. We need to keep this threat in mind as we build out Nostr to address novel use cases. Zero-knowledge proofs might be relevant here, or we might be able to get by with a simple re-configuration of data custody.\n\nIn the future users might publish to a small number of relays they trust not to relay their data, similar to @fiatjaf's NIP-29 chat proposal. These relays might then support a more sophisticated query interface so that they can answer questions without revealing too much information. One interesting thing about this approach is that it might push relays towards the PWN model BlueSky uses.\n\nNot all data needs to be treated the same way either, which would give us flexibility when implementing these heuristics. Just as a note might be either broadcast or sent to a single person or group, certain reviews or other activity might only be revealed to people who authenticate themselves in some way.\n\nLike so many other questions with Nostr, this requires our concentrated attention. If all we're doing is building a convenient system for Klaus Schwab to make sure we ate our breakfast bugs, what are we even doing?\n\n
-
 @ d830ee7b:4e61cd62
2023-08-09 17:22:10
@ d830ee7b:4e61cd62
2023-08-09 17:22:10สองคนนี้รู้จักกันเพราะคุยเรื่องบิตคอยน์กันแน่ๆ เลย?
ถ้าผมบอกว่าเราคุ้นเคยกันมากขึ้นเพราะ "เกมส์" คุณจะเชื่อไหม?
ย้อนกลับไปในช่วงเปิดตัวหนังสือ The Bitcoin Standard ฉบับแปลไทยของ อ.พิริยะ นั่นคือเหตุผลแรกที่ผม ซึ่งเป็นใครจากไหนก็ไม่รู้ ทักไปหา อ.ตั๊ม ครั้งแรก..
"ผมเอาเล่มนึงคับ"
ก็คงเป็นการ Approach แบบที่ใครเค้าก็ทำกัน พวกคุณก็คงพอเดาได้ แต่คุณคงเคยเห็นมาแล้ว บัญชีโซเชียลมีเดียแต่ละแอปของเขาน่ะ การแจ้งเตือนมัน 999+ ตลอด ผมไม่คิดว่าจะมีใครโชคดีได้ป๊ะได้คุยตั้งแต่ทักเขาครั้งแรก
ใช่ครับ.. ผมรอครึ่งปีเพื่อให้ถึงจังหวะโอกาสที่เขาต้องตอบผมแน่ๆ ก็ตอนขายหนังสือนี่แหละ..
ไม่มีอะไรมากมาย ผมมีแนะนำตัวเล็กน้อยว่าผมเป็นแอดมินเพจ CryptoNize (ที่ตอนนี้เลิกทำไปแล้วล่ะ) ผมชื่นชอบบิตคอยน์ และติดตามมานาน บลา บลา บลา
แต่สิ่งหนึ่งที่ผมต้องใช้ความกล้าอย่างมาก และต้องทำทันทีคือการ "Declare" บอกกับเขาตรงๆ ว่าผมอยากร่วมทำบางอย่างเพื่อตอบแทนสิ่งที่เขาทำทั้งหมดด้วยการช่วยทุกอย่างเท่าที่เขาจะอนุญาต โดยเฉพาะการสร้าง Bitcoin Network ในไทย ก็ถ้าไม่ใช่โอกาสนี้ก็ไม่รู้จะทำตอนไหนละ
เอ่อ.. ผมคิดว่าตอนนั้น อ.ตั๊ม ก็คงจะงงๆ แบ่งรับแบ่งสู้ อะไรของมึงวะหมอนี่..
จริง ๆ มันเริ่มมาจากการที่ผมสังเกตมานานแล้ว และคิดเรื่องนี้ในหัวมาตลอด ผมเองก็เป็นคนนึงที่อยากทำให้ในไทยมีฐานความรู้เกี่ยวกับบิตคอยน์ภาษาไทยมาตั้งแต่ต้น
ผมหลงเข้าดงชิตคอยน์ในก้าวแรกสู่ตลาดคริปโต เดชะบุญที่ผมอยู่กับการศึกษาวงการลงทุนมานาน หลายสินทรัพย์ที่ผมรู้จักดี ผมใช้เวลาไม่นานนักในการแยกแยะได้ว่าอะไรคือของจริง ของปลอม
หลังจากนั้นผมก็ทำเพจบิตคอยน์งูๆ ปลาๆ ในแบบของตัวเองไป แน่นอนว่าในไทยเมื่อคุณตกลงปลงใจจะศึกษาบิตคอยน์ ชื่อแรกที่คุณจะนึกถึงแน่ๆ คือ อ.พิริยะ เขาเป็นไอดอลของผมเหมือนกับพวกคุณทุกคนนั่นแหละครับ
แล้วไอดอลกลายมาเป็นเพื่อนเราได้ยังไง?
มีช่วงหนึ่งที่ผมสังเกตุเห็นได้ชัดว่า อ.ตั๊ม เริ่มมีอาการ Burn-out ผมไม่รู้ว่าใครเห็นแบบผมไหมนะ แต่ผมแน่ใจว่าใช่แน่ๆ ผมกลับไปคิดว่าผมจะช่วยอะไรเค้าได้บ้าง?
ถ้าเราอยากจะผลักดันวงการบิตคอยน์ในไทย แทนที่จะแยกกันทำไปแบบนี้ ทำไมเราไม่ไปขอจอยช่วย อ. ทำ เสริมพลังให้แกไปเลยนะ? ผมตัวเล็กมากในคอมมูนิตี้ไทยตอนนั้น จะว่าโนเนมเลยก็ได้ แต่คิดอะไรเกินตัวซะเหลือเกิน
But how?
ผมรื้อทุกอย่างที่เป็น อ.พิริยะ เท่าที่จะหาแหล่งข้อมูลได้ในเมืองไทย ผมเป็นคนนึงที่ดูทุกคลิป ทั้งบิตคอยน์ สอนเทรด ส่วนตัว เฟซบุ๊ก หนังสือที่อ่าน วิธีที่พูด โพสต์ที่เคยผ่านตา บทความที่เคยเขียน ฯลฯ เรียกว่าผมวิจัยคนๆ นึงเลยก็ว่าได้
ผมศึกษานิสัยใจคอของเขา ความชอบ เป้าหมาย ต่างๆ นานา ไม่ใช่เพื่อจะ Take Advantage จากสิ่งนี้ แต่ผมต้องการเป็นเพื่อนกับเขาจริงๆ ผมเป็นคนแบบนี้ ผมชอบทำงานกับเพื่อน กับคนที่รู้มือรู้ใจกัน และในสถานการณ์แบบนี้ มันควรเป็นผมที่ต้องเข้าใจ อ. ให้ได้ก่อน
ถ้าคุณคิดว่าเราคงถกเรื่องบิตคอยน์ หรืองานเทรดกัน คุณคิดผิดถนัด.. ผมคุยเรื่องสัพเพเหระที่ไม่เกี่ยวกับบิตคอยน์กันแม้แต่นิดเดียว จนกระทั่งวันนี้ก็ยังเป็นแบบนี้ เรื่องที่เราคุยกันถูกคอมากที่สุดคือ.. "เรื่องเกมส์"
ให้ตายเถอะ เรามันเด็กที่โตมาในยุค 90' เหมือนกัน มีอะไรจะคุยได้ยาวเท่าเรื่องในอดีตอีก เราคุยถึงสมัยเรียน สมัยเด็ก สมัย Ragnarok เราเล่นเกมบน Nintendo switch ด้วยกัน
เอ่อ.. ผมหมายถึง… เล่นของใครของมันแล้วมาคุยกันอะนะ
พวกคุณรู้ไหมว่าเราชอบเกมกันขนาดนี้ แต่เอาเข้าจริงเราได้เล่นกันก่อนนอนวันละไม่เกินครึ่ง ชม. แค่นั้นเอง เอาแค่พอให้หายอยาก เรามีเรื่องต้องทำกันเยอะมากๆ ในตอนนั้น หากใครยังจำได้ จะมีช่วงนึงที่ อ. พูดถึงเกม Triangle Strategy บ่อยๆ นั่นแหละ เล่นอยู่กับผม
แต่อันนี้ยอมนะ เกม RPG นี่ผมสู้แกไม่ได้จริงๆ
จนกระทั่งเราได้เจอกันครั้งแรกที่งานมีตอัพบิตคอยน์ที่โรงเบียร์พี่ชิต (น่าจะมีคนอ่านสักคนที่ได้ไป) เอาจริงๆ นะ ผมไม่ตื่นเต้นเลย เป็น อ. มากกว่าที่ไม่รู้จะทำตัวยังไง ฮ่าๆๆ
ก็ผมมันดิบ ผมเป็นคนเซอร์ๆ ขัดกับลุคของ อ. คนละขั้ว แต่คนต่างขั้วนี่แหละพาพวกคุณให้ได้มาอ่านบทความนี้บน Nostr ตอนนี้ เรามาไกลจากตรงนั้นมาก เรามีคอมมูที่โตขึ้นอย่างออแกนิก มีสมาชิกน่ารักๆ ในคอมมูนิตี้หลายคน เรามี Right Shift และพาร์ทเนอร์อีกมากมายที่กำลังผุดกันขึ้นมา
ผมที่คิดว่าจะเข้ามาช่วยแบ่งเบาภาระ อ. ในตอนแรก ตอนนี้ผมทำให้เขายุ่งยิ่งกว่าเดิม แต่ผมก็สัมผัสได้นะ ผมเชื่อลึกๆ ว่าตอนนี้ อ. คงมีความสุข อ.ไม่ได้สู้ตัวคนเดียว วันนี้ อ. มีพวกเราทุกคน มันจับต้องได้ ใช้แค่หัวใจก็สัมผัสมันได้ละ
สิ่งที่ดีที่สุดที่เกิดขึ้นระหว่างเราสองคน คือผมได้สวมกอด อ. (แบบลูกผู้ชาย) หลังการจัดงาน BTC2023 ไม่มีใครได้เห็นภาพนี้ เพราะมันอยู่ในความทรงจำของผมคนเดียว…
เราเคยวาดรูปล้อเลียนให้นาย.. ตอนนี้ยังอยู่ดีไหม?
ผมอยากจะบอกกับทุกคนว่า.. เราคงไม่สามารถมีเพื่อนได้จากการนั่งอยู่เฉยๆ หรอกครับ มันมีคุณค่าบางอย่างที่จะคอยดึงดูดคนเราเข้าหากัน แต่มันต้องมีสักคนที่เริ่มก่อน และ พิริยะ คือชายคนนั้นที่ได้มอบคุณค่าบางอย่างให้กับพวกเรา พวกเรารู้กันดีว่ามันคืออะไร
สิ่งนี้แหละเรียกว่า Value for Value เมื่อเราให้มากพอ วันนึงเราจะได้รับบางอย่างเป็นการตอบแทน..
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr\n\n以下是使您的 Nostr 之旅更顺畅的几个步骤 \n\n---\n_本指南适用于: \n 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n 俄语 \n\n--- \n你好,Nostrich同胞!\n\nNostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。 \n\n## 👋欢迎 \n\n由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz -- \n
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。 \n\n--- \n\n## 🤙玩得开心 \nNostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 \n这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: \nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu \n_名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们_ \n\n---\n ## ⚡️ 启用 Zaps \nZaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ \n查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: \n即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤: \n\n0 为您的移动设备下载 Wallet of Santoshi[^1](可能是比特币和闪电网络新手的最佳选择)[^2]\n1 点击“接收” \n2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。 \n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
\n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。  \n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
\n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org  它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n \n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n
\n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n  \n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
\n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。  \n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:
\n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/\n\n \n\n[^1]:还有更多支持闪电地址的钱包,您可以自由选择您喜欢的 \n[^2]:不要忘记返回钱包并备份你的账户\n[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标\n\n\n译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边\n\n_Zap⚡ spang@getalby.com \n关注:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n\n\n\n\n\n -
 @ 32e18276:5c68e245
2023-06-01 04:17:00
@ 32e18276:5c68e245
2023-06-01 04:17:00Double-entry accounting is a tried and true method for tracking the flow of money using a principle from physics: the conservation of energy. If we account for all the inflows and outflows of money, then we know that we can build an accurate picture of all of the money we've made and spent.\n\nBitcoin is particularly good at accounting in this sense, since transaction inflows and outflows are checked by code, with the latest state of the ledger stored in the UTXO set.\n\nWhat about lightning? Every transaction is not stored on the blockchain, so we need same way to account for all the incoming and outgoing lightning transactions. Luckily for us, core-lightning (CLN) comes with a plugin that describes these transactions in detail!\n\nFor every transaction, CLN stores the amount credited and debited from your node: routed payments, invoices, etc. To access this, you just need to run the
lightning-cli bkpr-listaccounteventscommand:\n\n\nlightning-cli bkpr-listaccountevents | jq -cr '.events[] | [.type,.tag,.credit_msat,.debit_msat,.timestamp,.description] | @tsv' > events.txt\n\n\nThis will save a tab-separated file with some basic information about each credit and debit event on your node.\n\n\nchannel invoice 232000000 0 1662187126 Havana\nchannel invoice 2050000 0 1662242391 coinos voucher\nchannel invoice 0 1002203 1662463949 lightningpicturebot\nchannel invoice 300000 0 1663110636 [["text/plain","jb55's lightning address"],["text/identifier","jb55@sendsats.lol"]]\nchannel invoice 0 102626 1663483583 Mile high lightning club \n\n\nNow here's comes the cool part, we can take this data and build a ledger-cli file. ledger is a very powerful command-line accounting tool built on a plaintext transaction format. Using the tab-separated file we got from CLN, we can build a ledger file with a chart-of-accounts that we can use for detailed reporting. To do this, I wrote a script for convertingbkptreports to ledger:\n\nhttp://git.jb55.com/cln-ledger\n\nThe ledger file looks like so:\n\n\n2023-05-31 f10074c748917a2ecd8c5ffb5c3067114e2677fa6152d5b5fd89c0aec7fd81c5\n expenses:zap:1971 1971000 msat\n assets:cln -1971000 msat\n\n2023-05-31 damus donations\n income:lnurl:damus@sendsats.lol -111000 msat\n assets:cln 111000 msat\n\n2023-05-31 Zap\n income:zap:event:f8dd1e7eafa18add4aa8ff78c63f17bdb2fab3ade44f8980f094bdf3fb72d512 -10000000 msat\n assets:cln 10000000 msat\n\n\nEach transaction has multiple postings which track the flow of money from one account to another. Once we have this file we can quickly build reports:\n\n## Balance report\n\nHere's the command for "account balance report since 2023-05 in CAD"\n\n$ ledger -b 2023-05-01 -S amount -X CAD -f cln.ledger bal\n\n\n CAD5290 assets:cln\n CAD2202 expenses\n CAD525 routed\n CAD1677 unknown\nCAD-7492 income\n CAD-587 unknown\n CAD-526 routed\nCAD-1515 lnurl\n CAD-614 jb55@sendsats.lol\n CAD-1 tipjar\n CAD-537 damus@sendsats.lol\n CAD-364 gpt3@sendsats.lol\nCAD-4012 merch\nCAD-2571 tshirt\nCAD-1441 hat\n CAD-852 zap\n CAD-847 event\n CAD-66 30e763a1206774753da01ba4ce95852a37841e1a1777076ba82e068f6730b75d\n CAD-60 f9cda1d7b6792e5320a52909dcd98d20e7f95003de7a813fa18aa8c43ea66710\n CAD-49 5ae0087aa6245365a6d357befa9a59b587c01cf30bd8580cd4f79dc67fc30aef\n CAD-43 a4d44469dd3db920257e0bca0b6ee063dfbf6622514a55e2d222f321744a2a0e\n ...\n------------\n 0\n\n\nAs we can see it shows a breakdown of all the sats we've earned (in this case converted to fiat). We can have a higher-level summary using the depth argument:\n\n$ ledger -M -S amount -X sat -f cln.ledger bal\n\n\n sat14694904 assets:cln\n sat6116712 expenses\n sat1457926 routed\n sat4658786 unknown\nsat-20811616 income\n sat-1630529 unknown\n sat-1461610 routed\n sat-4207647 lnurl\nsat-11144666 merch\n sat-2367164 zap\n------------\n 0\n\n\nAs we can see we made 14 million sats this month, not bad! The number at the bottom balances to zero which means we've properly accounted for all income and expenses.\n\n## Daily Damus Donation Earnings\n\nTo support damus, some users have turned on a feature that sends zaps to support damus development. This simply sends a payment to the damus@sendsats.lol lightning address. Since we record these we can build a daily report of damus donations:\n\n$ ledger -D -V -f cln.ledger reg damus\n\n\n23-May-15 - 23-May-15 ..damus@sendsats.lol CAD-46 CAD-46\n23-May-16 - 23-May-16 ..damus@sendsats.lol CAD-73 CAD-120\n23-May-17 - 23-May-17 ..damus@sendsats.lol CAD-41 CAD-161\n23-May-18 - 23-May-18 ..damus@sendsats.lol CAD-37 CAD-197\n23-May-19 - 23-May-19 ..damus@sendsats.lol CAD-35 CAD-233\n23-May-20 - 23-May-20 ..damus@sendsats.lol CAD-28 CAD-261\n23-May-21 - 23-May-21 ..damus@sendsats.lol CAD-19 CAD-280\n23-May-22 - 23-May-22 ..damus@sendsats.lol CAD-29 CAD-309\n23-May-23 - 23-May-23 ..damus@sendsats.lol CAD-19 CAD-328\n23-May-24 - 23-May-24 ..damus@sendsats.lol CAD-25 CAD-353\n23-May-25 - 23-May-25 ..damus@sendsats.lol CAD-36 CAD-390\n23-May-26 - 23-May-26 ..damus@sendsats.lol CAD-37 CAD-426\n23-May-27 - 23-May-27 ..damus@sendsats.lol CAD-25 CAD-451\n23-May-28 - 23-May-28 ..damus@sendsats.lol CAD-25 CAD-476\n23-May-29 - 23-May-29 ..damus@sendsats.lol CAD-12 CAD-488\n23-May-30 - 23-May-30 ..damus@sendsats.lol CAD-29 CAD-517\n23-May-31 - 23-May-31 ..damus@sendsats.lol CAD-21 CAD-537\n\n\nNot making bank or anything but this covered the relay server costs this month!\n\nHopefully ya'll found this useful, feel free to fork the script and try it out! -
 @ e8ed3798:67dd345a
2023-07-16 02:49:48
@ e8ed3798:67dd345a
2023-07-16 02:49:48This article has been translated into Japanese here: https://yakihonne.com/article/naddr1qq257w2t8qeksc6tdg6njnekdc6x55j0w56nvq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wu2llgg
This article has been translated into French here: https://yakihonne.com/article/naddr1qq2h23jjwck4zajsv4485h68f5mj6c66vfmxuq3qarkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqxpqqqp65wvsexdg
In this article we are going to explore the conceptual origins of the original metaverse called "cyberspace" and see how nostr finally enables it to exist as it was predicted in early science fiction. Then we will explore what cyberspace might be able to do for humanity and how you can contribute to this exciting new open-source metaverse project.
A Concept Obscured by Time
What is a "metaverse"? Ask 10 different people and you will get 10 different answers. Some will say that it is an online game where you can use and transfer crypto assets. Some will say it's a virtual reality experience with extrasensory input for things like smell and touch. Some will say that a metaverse is anywhere you can connect and express yourself digitally. And some may tell you the metaverse doesn't exist yet because we don't have the technology to make it happen.
It's hard to define what a metaverse is because nobody has convincingly built it yet. This is demonstrable by simply asking anyone to show you a metaverse. They may show you VR Chat, or Meta (Facebook), or the HoloLens or Apple Vision, or someone's Discord server or NFT ecosystem, or say "it's not real, and if it is it's probably stupid."
But how did we get here? Why do we all know about the metaverse but we can't define it and we don't even know what it looks like? Where did the idea of the metaverse come from? This answer will give us the conceptual background we need to untangle the question of "what is a metaverse" and see how cyberspace can exist today.
The word "metaverse" was first popularized in Neal Stephenson's 1992 book "Snow Crash", and he was in turn inspired by William Gibson's earlier 1984 book "Neuromancer" (and 2 other books in a trilogy called "The Sprawl"), which popularized the word "cyberspace" and "matrix" in reference to digital 3D spaces.
Accordingly, cyberspace preceded "the metaverse" by 8 years and serves as the foundation for our exploration. Gibson's cyberspace was a digital 3D world one could connect to via a cyberspace deck — a machine/brain interface — and interact with all the data in the entire world. Artificial Intelligences guarded data constructs and kept out intruders with lethal feedback programs that would fry human operator's brains. In the books, cyberspace is described as being used for pretty much everything: entertainment, education, communication, commerce, data storage, and crime, and it is used daily by billions of people throughout the world, including millions of people in orbital colonies.
Mysterious Properties
In Gibson's work, cyberspace has many fascinating qualities that, until nostr, remained very mysterious and seemed to be impossible. Here are some examples.
1. Cyberspace is Permissionless
Everyone can use cyberspace but nobody has full control over it; cyberspace seems to exist outside of every jurisdiction and system. It never goes down for maintenance or has connection issues or suffers security breaches. It seems to exist everywhere at once, even though it is explicitly stated that cyberspace was created by humanity. How can humanity create an uninterruptable, omnipresent digital system that nobody can control but everyone can use?
2. Power is Wielded Without Privilege
Certain people, corporations, and AI weilded greater levels of power in cyberspace than others, but the mechanism of that power was not derived from permissions or access levels or privileged administrator capabilities; rather, the power came from some mysterious other source that could not be granted, governed, or revoked by any law or system or authority. This power seemed also to be heavily influenced by...
3. Hardware and Skill
The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace. There is a a specific example where a character uses a premium cyberspace deck and describes the speed and smoothness of their ability to fly through cyberspace. A short while later, this operator is captured and immobilized by another dangerously skilled operator, demonstrating that while the cyberspace hardware was top-tier, the operator's skill level was also a big factor governing interactions in cyberspace. This also demonstrates that conflict is possible in cyberspace. How is it possible that hardware directly correlates to your capacity for virtual action? How can someone else influence your actions against your will in this digital reality?
4. Space is Scarce
Bitcoin was the first scarce digital resource to ever exist, and having only been created 14 years ago, scarce digital resources are still a novel concept to humanity in 2023. In Gibson's cyberspace, territory was conquered, captured, and fought over, indicating that the space in cyberspace may be scarce or valuable in some way. How could it be possible to fight for digital territory or acquire it without any governing intermediary took keep track of who owns what?
5. Construction Has a Cost
Constructs, or cyberspace "buildings", required some kind of effort or cost to create, but it was not clear to whom this cost was paid or how the effort was expended.
The metaverse of Stephenson's "Snow Crash" shares many properties with Gibson's cyberspace, although Stephenson is somewhat opinionated with the literal shape of the metaverse. He depicts it as a street that wraps around a black planet, and the land off the street is where people build things and claim territory.
This metaverse similarly does not seem to be owned or controlled by any single entity, yet it is available to everyone in the world to connect, interact, and build in 24/7. It is not described as an application or piece of software, but rather a place that is the sum of other software created by many different parties with different interests and motivations.
Here are some mysterious traits of Stephenson's metaverse:
6. Rules without Rulers
The rules of the metaverse were never broken — not even by hackers or bad guys. How are rules enforced by a system nobody controls?
7. No Teleportation, Localized Rules
The metaverse had rules about where you could spawn in and how you move. Teleportation was not an option. Specialized vehicle software could make traveling easier. Rules for travel were enforced by the metaverse itself. Experiences in the metaverse were localized to constructs that implemented their own rules. For example, sword fighting was allowed in The Black Sun hacker haven because it was programmed to exist there; other places did not have such activities. How can certain places in cyberspace have unique rules separate from the rest of cyberspace? How is locality enforced in a digital system controlled by noone?
8. Customize Without Compromising Everything
People were able to customize how their avatars and constructs looked. How do you govern this so people don't abuse it? Without enforceable rules, one person could make their avatar be the size of the universe and ruin the metaverse for everyone.
9. Everything is Connected
Digital systems in the real world had a presence in the metaverse too, although they were far from commonly populated areas. How do real world systems relate to the metaverse?
I enumerate these points in order to provide some context for where the idea for "the metaverse" began. These two books were instrumental in originally defining what the metaverse was even though it raised many specific questions that naturally were never addressed. As I have said: if the authors knew how to build the things they wrote about, they might not need to sell any books at all! This is fiction after all. Specifics are not required, but I have been focused on uncovering these specifics in the context of new technologies such as bitcoin and nostr and I believe they may now be defined.
To summarize, here are the mysterious properties of cyberspace/the metaverse:
- Everyone can use it
- Nobody controls it
- It exists everywhere
- An individual's power is not granted by any system or authority but comes from their hardware and skill
- Individuals can weild their power against each other
- Territory is scarce and may be captured
- Constructs may be build on territory but have some kind of cost
- The system enforces rules on everyone, or somehow incentivises everyone to follow the rules — even bad actors
- locality is enforced and travel requires time
- certain localities have unique rules
- freedom to customize your avatar and constructs are bounded in some way to prevent total corruption and abuse of digital space
- there is some form of connection between real world digital systems and cyberspace
Nothing Like It
I want to make it very clear that no metaverse in existence today exhibits all of the above properties or even a few of them, and very few digital systems exhibit even one of these properties.
Before I discovered Neuromancer several months ago, my perception of "cyberspace" was that of a quaint, naive concept of what interconnected computer systems would become that never came to pass. I used to ironically refer to the internet as "cyberspace" when talking with other developers as a kind of humorous or self-important overemphasis. I thought that cyberspace was a cultural relic and a failed prediction of what the internet would be. The glossy, 3D wireframe neon world never materialized, and for this I've always felt a sense of loss of what could have been.
Why didn't cyberspace ever come into existence? As computers became more advanced and consumer-focused, they did not attempt to emulate a 3D space, but rather did the practical and sensible thing of emulating paper documents so people could get work done digitally.
As the internet became a household utility, centralized systems and applications were the first and only way that humanity knew to grow our collective capabilities online. Websites grew as they collected users and became behemoths. Ebay, Google, Amazon, PayPal. Although the internet itself was technically decentralized, decentralized systems and applications would come later when the problems with centralization became obvious as these internet giants started abusing their power.
As the internet continued to grow and resemble less and less the fictional worlds of cyberspace and the metaverse, these lofty ideas of digital 3D worlds turned into toys for most people — unnecessary but entertaining fluff. The notion of cyberspace faded into 80's retro culture and the word cyberspace was painfully repurposed to simply refer to the internet or networked systems collectively. This, however, is a terribly inaccurate use of the word. There is no space to speak of on the internet. But, sadly, the interet was the closest thing we have ever had to Gibson's vision of cyberspace, and it really wasn't close by any measure except that people all over the world use it for pretty much everything. All the other magical properties of cyberspace were simply forgotten. They were fiction. They weren't necessary. They weren't possible. There was no way to make it work and no reason to do so.
However, when reading these books from nearly 4 decades past, there is something poignant to me in the fact that across these various works by various authors, the metaverse (or cyberspace) posesses consistent properties that no author is willing to alter. What is so inviolate about a fictional concept that would make it so consistent across works? Perhaps there is a kernel of truth in what is imagined, and that truth is so compelling that it must be repeated until it crosses the veil between idea and reality.
Reality And Cyberspace
I have always been fascinated by technology's ability to improve our lives, and I have strived to create consequential software my entire life, like video games played via fitness watches and augmented reality navigation web apps, but it wasn't until I read Softwar that I realized something profound.
In reality, I am able to do anything I want as long as I have the thermodynamic energy to do it.
It may not be legal or socially acceptable, but if I have the energy to do something, I can. Likewise, if someone wants to stop me from doing something, they can't unless they also expend enough energy to stop me.
This means that reality is permissionless, because nobody can disallow my actions. It also means reality is thermodynamic, because every action has a cost that must be paid to the universe in the form of entropy.
Conversely, in digital systems, the amount of energy you have is irrelevant. The things you can do are only the things you are allowed to do by the permissioned system, or, the things you can trick the system into letting you do. This means that within a digital system, you always have a severely limited subset of available actions, and your ability to execute those actions has nothing to do with your thermodynamic potential and everything to do with the permissions you are granted by others. No matter how strong my muscles are or how clever I am, I can't do more than a digital system allows me to do, and even if I hack it, I still can't do anything I want — only more than I'm supposed to.
Almost all digital systems and software are permissioned and non-thermodynamic.
This is why, fundamentally, no metaverse that has ever been built actually matters. This is why no video game keeps you interested in it forever, because the actions that you can do and the extent to which you can do them are arbitrarily disconnected from your ability to act in reality. It's "just a game" — a limited subset of reality.
This isn't fundamentally a bad thing. Obviously, software has done a lot for humanity. And software-based rules have been used in many contexts to keep things fair for everybody. Except, unfortunately, digital systems are never truly fair. There's always a programmer who wrote the rules. There's always an admin above you. There's always a hacker. And there's always someone with more permissions than you who can restrict your potential. Compared to reality, this seems arbitrary and capricious. At least in reality, the universe to which you pay your entropy costs is truly, terribly impartial and unbiased. This is why thermodynamic systems are fundamentally fair; even though it may not seem fair to you it is truly fair to everyone.
Reality is a permissionless, thermodynamic protocol, and almost nothing in the digital world resembles this whatsoever.
Nostr, however, is permissionless. Until now you may not have considered this to be a fundamental property of our universe, but it is, and the fact that nostr exhibits this same property is quite compelling. In fact, any system that is truly permissionless (of which there are very few) seems to have the magic ability to capture people's imaginations in ways that no other digital system can. Things such as bitcoin, perhaps the most famous permissionless digital system, has such broad and profound effects on people who grasp it that they have been known in some cases (such as Andreas M. Antonopoulos') to stop eating, stop sleeping, research it obsessively, and completely change their entire way of life. How's that for consequential software?
Like bitcoin, nostr can also be thermodynamic via proof-of-work (NIP-13). And with the combination of these two properties, which are shared with reality, we are suddenly able to dispell every single mystery we've encountered regarding cyberspace.
Proof-of-work is the secret ingredient to dissolve the fiction in the science fiction of cyberspace.
A Mystery Solved About Cyberspace and Bitcoin
The reason that the properties of cyberspace and the metaverse are so mysterious is because they are actually properties of reality, but inside a digital system.
In reality, it is no surprise that your hardware and skill affects your ability. No surprise that your work determines your power. No surprise that you can't teleport and must travel using energy. No surprise that building constructs or customizing yourself takes effort and cost. No surprise that territory is scarce and must be defended. No surprise that conflict happens between people. All of this is so completely normal that it's easy to overlook.
The reason these things in Neuromancer and Snow Crash and other works about the metaverse seemed so mysterious is because they weren't possible to model in a digital space. These authors took properties of reality and put them in a digital space, and it seemed amazing because nobody knew how it could actually work.
This is how it is possible: you design a digital system that has the same fundamental properties as reality. It must be permissionless. It must be thermodynamic. Then you have a system wherein cyberspace can exist.
Nostr is the fulfillment of these requirements. Like bitcoin, nostr has captured the imaginations of thousands of early adopters and developers. The magic is there. But few may realize why it is feels so magical. The answer is that when you make a digital system that can model reality's own properties, you have created an extension of reality itself. This is one of the most significant discoveries in human history, because a digital extension of reality can allow humanity to connect, collaborate, and grow in a place where their physical diatance does not matter. Barring any major advancements in spacefaring technology, cyberspace will be the most significant departure from earth you may experience in your lifetime.
I posit that a virtual action which is permissionless and thermodynamic is as real as a physical action, except the consequences of that action happen in the digital space rather than the physical one. It's not quite reality, but it is like a mirror. It is a true extension of reality. Nothing in it is disconnected from the real world. And therefore, unlike any other digital system, it can be truly consequential.
Healthy Skepticism
Wait a minute, you may say. Cyberspace is still just a digital way of communicating. Isn't email and texting and video chat good enough? Why do we need cyberspace? How could it possibly be so important to humanity?
This is a great question.
One may ask similar questions about bitcoin. Don't we already have digital money? Why do we need absolutely scarce, decentralized censorship-resistant money?
Or about nostr: why do we need another way to transmit text? What good is it to be decentralized and censorship resistant?
Like bitcoin, cyberspace makes something digital into a scarce resource, but instead of enabling the capture of time (on a timechain) cyberspace enables the capture of scarce space (in a construct or your movement chain).
In the physical world, our movement can easily be censored. Our expression of power is censored. Our capture of space is censored. Not so in cyberspace. The only thing that matters in cyberspace is the thermodynamic energy you exert — just like in reality, but minus the permissioned (artificial) power structures of governments and laws.
Just as bitcoin doesn't care who you are or who you are transmitting value to, cyberspace doesn't care who you are or where you are moving to or where you are claiming space.
Consequences of Proof-of-Work in Detail
I'd like to enumerate the specific ways in which proof-of-work in nostr demystifies the mysterious properties of cyberspace mentioned earlier.
- Everyone can use cyberspace but nobody has full control over it.
Just replace "cyberspace" with "nostr" and the above statement is already true. If we build cyberspace on nostr, then cyberspace will inherit these properties.
- Certain people, corporations, and AI weilded greater levels of power in cyberspace than others
If we base an entity's power on their thermodynamic output via proof-of-work, then we have a permissionless way for cyberspace participants to enact their real thermodynamic potential in cyberspace to whatever degree they choose.
- The hardware that people used to connect to cyberspace had a direct impact on their capabilities in cyberspace.
If all actions in cyberspace are thermodynamic like in reality, then hardware capable of greater amounts of proof-of-work will enable more powerful actions. Mobile phone, desktop computer, or ASIC farm: take your pick.
- Territory in cyberspace was conquered, captured, and fought over, indicating that it may be scarce or valuable in some way. Constructing had a cost.
The territory in cyberspace is the maximum 3-dimensional coordinate space that can be represented by 256 bits. In cryptography, nostr, and bitcoin, 256-bit numbers are very commonly used along with mathematical functions like SHA-256 that process data in blocks of 256, so it is a good "round" amount of information to work with.
You can divide a 256-bit number into X, Y, and Z coordinates that are each 85 bits long. This leaves 1 extra least-significant bit from the 256 bits that is ignored.
This means that each axis of cyberspace is 2^85 units long.
Space can be claimed by publishing a construct event whose event ID is the coordinate. The event ID is obtained from hashing the event (standard process for all events in the nostr protocol). This means the event ID can be mined to obtain the coordinates you desire (or at least something close by).
If two constructs overlap, the one with the most proof-of-work wins. This is how territory can be contested in a permissionless way in cyberspace, as alluded to in Gibson's works.
The cost of construction is the proof-of-work, and the maintenance of that territory by proof-of-work is the digital analogy of either paying taxes to a government who will protect your land, or, protecting your land with your own thermodynamic energy. Notice how money, also known as time, is inextricably linked to the ownership of property in reality and now also in cyberspace. If property were free to own and maintain, would it be worth anything at all?
I have been presented with the argument that it does not cost you anything to hold bitcoin, so constructs or cyberspace real estate should be no different. To this I say that for you to hold your bitcoin, a tremendous amount of cost is expended by all the miners in the world. If not for them, your bitcoin would be double-spent or stolen by invalid transactions. The validity of your unmoving bitcoin requires the continual, perpetual operation of the largest computer network in the world. So, continual energy expenditure to secure your property is true with bitcoin, cyberspace, and all of your things in reality as well.
Unlike bitcoin, whose value lies in the entire network, constructs are valuable only to their owner. Therefore, it is the responsibility of the construct's owner to defend it.
More complex symbiotic relationships in construct defense may be borne out of the perpetual fight for survival inherent in any thermodynamic system. But this is only speculation.
Enforcing rules universally
As with any protocol, deviation excludes you from it and submission grants a share in its value. Forking the cyberspace meta-protocol, whether by disobeying its rules or rewriting them, results in an irreconcilable forking of digital reality. The value of cyberspace as a protocol depends on network effects like any protocol, and the first-mover has a strong advantage in any protocol war. Additionally, as all actions require proof-of-work and must be chained together, the sum of your history in cyberspace is put at risk of invalidation should you deviate from the protocol everyone else is following.
Ultimately I believe that the purpose of cyberspace should be to imbue humanity with new capabilities and opportunities, and I think that it will, simply by virtue of the fact that it is built on a protocol and interoperates with protocols that likewise imbue humanity with new capabilities and opportunities (notsr, bitcoin, and TCP-IP). I desire that cyberspace will be flexible and capable enough to support as many use-cases as possible as long as the fundamental properties are preserved as axiomatic non-negotiables. Cyberspace itself must be both permissionless and thermodynamic. Without these properties, cyberspace becomes just another digital illusion apart from reality.
Flexibility, locality, and customzation
With these axioms in mind, I think it would be very smart to create a method of defining construct-level rules that exist only within certain spaces. This would allow for custom interactions and systems to exist in the fabric of cyberspace, making it very flexible and local. Any such system or customization, even if cosmetic, must impose a fundamental thermodynamic cost. The details of how this could work are yet to be developed, but the blueprints of fiction, our axioms, and our ingenuity will lead us to it.
The metaverse of things
Because nostr is a web-friendly protocol, it is trivial to connect anything to cyberspace. I love to tell the tale of how I witnessed an early 2022 conversation between someone and (if I remember correctly) Will Casarin's smart dishwasher that was posting kind 1 status updates to nostr. If someone can talk to a smart dishwasher over nostr, then the Metaverse of Things already exists. However, the degree to which these things expose themselves to the metaverse should follow the same security model as for the internet at large. Unlike in fiction, I doubt anyone will allow sufficient proof-of-work be the only prequisite for commandeering a real-world system. That's ok. Ultimately, the relationship between reality and cyberspace isn't meant to be a 1:1 map. Digital systems only really ought to participate in cyberspace if they share the same properties as cyberspace. Most digital systems are permissioned and non-thermodynamic, and therefore do not have a compelling reason to exist in cyberspace. But anything is indeed possible.
Chasing a Ghost or Following a Blueprint?
I'd like to make the distinction that the purpose of a construct (and of most things) in the real-world cyberspace is not necessarily the same as in Gibson's literary cyberspace nor in Stephenson's literary metaverse. But the fundamental properties as depicted remain the same, and it is enabled by proof-of-work.
Remember, the remarkable thing about Gibson's cyberspace is that it is a digital world that functions like reality — there is egalitarian conflict resolution, scarce space, and universally enforced rules. The cyberspace meta-protocol likewise enables a digital system to function like space in reality. The motivations and reasons behind this digital system may be completely different than in the books, but that doesn't mean the mechanisms are any less accurate.
My goal is not to reproduce Gibson's and Stephenson's work in reality. The properties of this fiction are compelling, and the implementation and usage of cyberspace will completely depend on free market forces — exactly as it should be. It is not for me to decide. These works opened the conceptual pathway to creating this new thermodynamic digital reality. The human motivations and actions that shape cyberspace will undoubtedly cause it to look plenty different than depicted in the books, while the funamental properties remain identical.
Throughout the process of designing the cyberspace meta-protocol I have tried to keep it as simple and fundamental as possible, using these books as my guidepost. Whether these authors realized it or not, their depictions of cyberspace and the metaverse were extremely consistent and coherent, which makes not only for great fiction and believability but also for a great guide to follow in developing a real system.
Step Into Cyberspace
I'd like to provide some concrete examples of how cyberspace works so that the concepts presented herein are not without application.
NOSTR in 3 minutes
To interact with cyberspace, one must simply publish certain "kinds" of nostr events. If you are not familiar with nostr, here is a short explanation. Nostr is made up of people running clients, which are just apps like on your phone or desktop, and people running relays, which are like servers that store events. Clients download streams of events from relays in real time. Clients can also publish events to relays. Publishing an event is like sending a tweet. Clients normally publish the same event to many relays at once. As long as you send the tweet to at least one relay that your friend is connected to, they will see your tweet. Anyone can run a relay or build a client and connect to whichever relays they want. In this way, nostr is permissionless and decentralized.
A "kind 1" event is essentially a tweet, but there are other kinds of events, each represented by a number. A kind 0 event is what you publish when you update your profile with a new bio or screen name. Anyone may make up a new kind of event and assign it any number, except it would be poorly supported if you used a number that is already accepted as part of the nostr protocol for another purpose than you are using it for. Luckily, there are a lot of numbers to go around.
A private/public keypair is an anonymous cryptographic identity, and it can be used for secure communication, storage of bitcoin, and other various things. The keys themselves are just unfathomly large unguessable numbers represented in the hexadecimal number system which includes numbers 0-9 and a-f (base 16 instead of base 10). When you publish an event on nostr, it is signed by your private key, and the event contains your public key. This allows anyone to verify that the event is legitimately from that public key, which presumably only a certain person controls. In this way, nobody can forge or tamper with events without invalidating them, because the signature would not match the public key.
Meta-protocol
This is why I refer to cyberspace as a meta-protocol because it is simply a specific way of publishing and interpreting specific event kinds over nostr and visualizing them in a 3D space.
Drift
To move in cyberspace, you must publish a kind 333 event, referred to as a Drift event. This event contains your 3D cyberspace coordinates, your direction, your existing velocity, a reference to your previous Drift event, and proof-of-work to add velocity by your direction. The amount of proof-of-work on the drift event determines your acceleration. Proof-of-work can be added to any nostr event by choosing an amount of work, represented by the number of leading binary zeroes on the event's ID, and hashing the event with a different nonce until the target amount of work is reached. This process is specified in NIP-13.
Each Drift event may be validated by running the coordinates and velocity through a standardized cyberspace algorithm (currently being developed) to verify that the value changes from one drift event to the next are within a tolerable range of error. It is in effect a way of simulating the movement within a physics system in order to validate that the movements did not break the rules of cyberspace physics. In this way, every participant in cyberspace is a validator of everyone else they are physically near.
When a drift event is signed, the reference to the previous drift event is included in the signature. This creates, in effect, a personal verifiable hash chain history of your movements and actions in cyberspace that anyone else can verify.
Dishonesty and Punishment
In order to encourage people to be honest about their movement chains, anyone who finds an invalid — or "broken" — movement chain may punish its owner by publishing a Derezz event on it, which will invalidate all movement chains and proof-of-work owned by the victim and teleport them back to their home coordinate where they originally spawned when they first used cyberspace. This is effectively a respawn. You start from scratch, but you can keep your constructs.
One can easily lie about their movement chains and teleport anywhere at any time. But on nostr, for the most part, events cannot be deleted. Therefore, a cheater will leave a bright trail by which others may cyber-kill them via Derezz. A broken movement chain is like a ghost copy of the cheater that can't move. For deeper protocol reasons that the adventurous may explore in the spec, this makes the ghost copy extra vulnerable to Derezz.
A cheater may choose to ignore the Derezz attack and continue to teleport where desired. Nothing in nostr or cyberspace can stop this. But to everyone else who follows the protocol, this type of behavior can easily be ignored. The habitual cheater may as well be a ghost, as their thermodynamic actions will be ignored by everyone else who has chosen to obey the protocol. The cheater might redeem themselves by publishing a very long valid chain of events, but this probationary period may be too demanding for habitual protocol breakers. Other aggressive actions may be leveled against cheaters, making their operation in cyberspace unproductive, difficult, and dangerous.
A cheater in cyberspace is an easy target. As the punishment of cheaters is a noble act of justice rather than an evil act of predation, I expect cheaters in cyberspace to be punished with great swiftness and mirth.
Incentives for honest movement legitimize the spatial aspect of cyberspace. In cyberspace, space is real and consequential. Traversing it has a cost. No two places are funamentally the same because there is a real cost to visit them. And all space is scarce, because of the hard limit of the 2^85 coordinate system, which was chosen to be compatible with the most popular mining agorithm in the world, SHA-256.
Other actions
To read all about the different kinds of events one can publish to interact with cyberspace, check out (and contribute!) to the official cyberspace specification here: https://github.com/arkin0x/cyberspace
In this specification you will find technical implementation details for clients to interact with the cyberspace meta-protocol, including definitions of other actions that may be taken by operators, including:
- manipulating "gravity" to affect other operators
- creating proof-of-work armor against Derezz
- cloaking one's location with stealth
- and more!
Ubiquity and Omnipresence of Cyberspace
A very interesting recent development is an open-source project called
nostrmeshby lnbits that enables anyone to host a nostr relay on a small mesh-networked device, such as an Arduino. Imagine a network of billions of these devices, scattered across the globe, running on battieries and solar panels, each contributing to the infrastructure of cyberspace — a decentralized, omnipresent digital cosmos, accessible from virtually anywhere. This level of ubiquity brings us one step closer to the vision of Gibson's work, where cyberspace becomes an integral part of our daily lives and can be found everywhere — even in outer space!With such a ubiquitous and omnipresent network, the spatial limitations of cyberspace extend far beyond conventional digital boundaries, intertwining with our physical world in a way that was once the domain of science fiction. The implications of this development are enormous and lay the foundation for the potential uses and influence of cyberspace, which we will explore in the following section.
Consequences of Cyberspace
It is difficult to predict whether cyberspace will find its place in the daily lives of billions or be forgotten once again. However, the foundations of cyberspace are inextricably linked to technologies that have been developed and adopted for the sake of human freedom and personal rights: public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
As one who takes science fiction seriously enough to remove the fiction from it entirely, I find speculation to be invaluable. One cannot go where the imagination does not first lead. Our entire perception of the world is parsed from an abstraction created by our minds. We automatically assign meaning to inherently meaningless things — symbols, patterns, etc. Fiction is our reality, and our perception of the world is the sum of logical patterns within this fiction. Therefore, let us do what we do best and create fiction, or speculate, without hesitation.
I personally envision cyberspace to be a place of commerce and social organization. Constructs enable people to claim cyber land. They can use this land to design interactive experiences that are governed by localized rules and thernodynamics. The Lightning network enables instant transfer of value through cyberspace, facilitating the transaction of information, services, cyber experiences, digital and physical goods.
Use cases include shopping, gaming, gambling, competitions, live cyber events, virtual-presence social gatherings, virtual protests, collaborative spaces, advertising, education, tourism, development of cyberspace-based applications, data visualization, research, social networking, and even more that we haven't imagined yet.
Conclusion
As we venture into the vast digital landscapes of cyberspace, we are not simply traversing through lifeless data, but immersing ourselves in a consequential world that reflects the order and complexity of our physical reality. This revolutionary approach to cyberspace isn't merely a mirage of science fiction, but a tangible exploration of its key principles, built on the bedrock of public key cryptography, hashing, proof-of-work, bitcoin, and nostr.
Through the implementation of a meta-protocol layered over nostr, cyberspace opens a myriad of opportunities – drifting through the boundless expanses of the digital cosmos, crafting personal domains, or engaging in vibrant social interactions. Just as actions in the physical world carry costs and consequences, so too does cyberspace enforce its own unique set of rules and repercussions, fostering a sense of shared responsibility, fairness, and cooperation among its denizens.
Envisioned as a playground for creativity, commerce, and social organization, cyberspace, in its current formative state, already shows tremendous potential for an expansive array of use cases. Its inherent thermodynamic properties and permissionless nature offer a groundbreaking amalgamation of digital and physical realities, poised to profoundly augment our capabilities, experiences, and opportunities in a dynamic, inclusive, global, and consequential realm.
However, the most exciting aspect of cyberspace is not merely what it currently offers, but its potential to continuously evolve and redefine itself. As more people engage with and contribute to its development, it's bound to expand and morph in ways we can hardly fathom today.
As we stand on the cusp of this digital frontier, we are not chasing after phantoms of fiction. Instead, we are architects and pioneers of a revolutionary new realm, where digital existence converges with physical principles. This remarkable blend of technology and human imagination sets the stage for an unprecedented era of exploration and innovation, signaling a future that is as exciting as it is unpredictable.
Join me on this grand endeavor to shape cyberspace, to mold this new frontier into a shared and diverse digital world that reflects the best of human spirit and ingenuity. Together, let's step into cyberspace, the frontier of the future.
Build with me
Cyberspace is for humanity, and therefore I desire as many humans to be involved in its construction as possible. I have created the following resources for anyone who wants to learn more or get involved:
Join the ONOSENDAI Telegram group: https://t.me/ONOSENDAITECH
I love answering questions! Please hop in and ask away!
Pull requests welcome on the spec: https://github.com/arkin0x/cyberspace
Check out the first cyberspace client, ONOSENDAI: https//onosendai.tech (thermodynamics still in development)
Pull requests welcome on ONOSENDAI: https://github.com/arkin0x/ONOSENDAI
whoami
My name is Nick. I go by arkinox. I have been making websites since I was 11 and designing games since I was 4. I've been the director of web for a midwest marketing firm for 10 years and the co-founder and senior vice president of an augmented reality company, innovatar.io, for 4 years.
Support FOSS
If you would like to support development of this protocol I would love for you to get involved. Also, I am accepting donations and looking for opportunities to pursue it full time.
Follow me on nostr: npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w
Zap me with Bitcoin Lightning: arkinox@getalby.com
Soli Deo gloria
-
 @ c75622fd:a9b66e1d
2023-03-18 15:09:42
@ c75622fd:a9b66e1d
2023-03-18 15:09:42[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
-
 @ d830ee7b:4e61cd62
2023-08-09 05:59:10
@ d830ee7b:4e61cd62
2023-08-09 05:59:10ผมมีความสุขดีกับการทำตัว Low profile เพราะมันมีเรื่องราวที่เป็นเหตุผลของมันอยู่..
ใครอ่านงานเขียนผมบ่อยๆ จะทราบดีว่าผมมักจะเขียนไปเรื่อย เล่าเรื่องหรือความคิดของตัวเองออกมาได้ยาวเหยียด เมื่อมันเป็นแบบนี้ก็เลยคิดว่าจะใช้ Account นี้ให้เหมือนเป็นบล็อกส่วนตัวสุดๆ แบบไม่มีคอนเซ็ปต์ไปเสียเลย วันไหนอยากเขียนอยากเล่าอะไรผมก็จะเล่ามันดื้อๆ นี่แหละ..
มันเริ่มจาก.. มีคนพยายามบอกว่าผมอยู่เบื้องหลังของคอมมูนิตี้บิตคอยน์ในไทย มีคนบอกว่าผมเป็นตัวตั้งตัวตี แต่ก็เป็นคนที่ลึกลับหาข้อมูลได้ยากอะไรแบบนั้น ซึ่งมันก็มีทั้งส่วนที่ถูกและยังไม่ใช่อยู่พอสมควรครับ..
อย่างแรก ผมไม่ได้มองว่าตัวเองยิ่งใหญ่หรือมีบทบาทสำคัญมากขนาดนั้น ผมยังเชื่อมาตลอดว่าอะไรก็ตามที่เกิดขึ้น มันไม่ได้เกิดเพราะผมเพียงคนเดียว มันประกอบมาจากหลายส่วนและคนที่มีส่วนร่วมในสิ่งนี้ยังมีอีกมากมาย ผมอาจเป็นฟันเฟืองหลักในเรื่องนี้ แต่ยังไงผมก็คงต้องปฎิเสธว่าไม่ใช่เพราะผมคนเดียวอย่างแน่นอน ใช่ครับ.. มันก็มาถึงตรงนี้ได้เพราะพวกเราทุกคน
อย่างที่สอง โดยส่วนตัวผมคิดว่าการมีตัวตนในลักษณะนั้นจะทำให้ผมไม่สามารถทำอย่างที่ทำอยู่ในทุกวันนี้ได้ มันจะทำให้ผมนึกถึงเพียงแค่ตัวเอง สนใจแค่เพียงตัวเองมากกว่าคนรอบข้าง
ซึ่งมันขัดกับเป้าหมายสำคัญส่วนตัวของผมนั่นคือ “ส่วนรวม” ฝันของผมนั้นไกลจนยากที่ใครจะจินตนาการถึง วันนี้เราทำเสต็ปแรกกันยังไม่ครบเลยด้วยซ้ำ หากผมมตัวแต่ส่องกระจกประเมินตัวเองอยู่ทุกวันๆ ผมคงไม่มีเวลาไปคิดถึงส่วนอื่นๆ เป็นแน่แท้ ..งานแบบนั้นยังมีอีกหลายคนที่พร้อมจะเสียสละและเต็มที่ไปกับมัน ไม่จำเป็นต้องเป็นผมใช่ไหมล่ะ
อย่างที่สาม ผมเชื่อในแนวคิด Decentralized อย่างที่สุด คำนี้ลึกซึ้งมากกว่าแค่เข้าใจว่ามันกระจายหรือรวมศูนย์ ผมไม่ได้เป็นคนที่เข้าใจลงลึกในวิชาการหรือความรู้ทางเทคนิคของบิตคอยน์มากนัก ผมเชื่อว่าตัวเองก็แค่รู้ในระดับคนทั่วๆ ไป แต่ในเรื่องหลักการและแนวคิดพวกนี้ รวมถึงการนำมาประยุกตร์เข้ากับเรื่องต่างๆ ในชีวิต ผมคิดว่าผมทำได้ค่อนข้างดีเลยล่ะ
เกี่ยวกับเรื่องนี้.. ผมเชื่อเองตั้งแต่ต้นว่าสังคมจะไม่เติบโตอย่างยั่งยืนหากพึ่งพาผู้นำหรือใครคนใดคนหนึ่งมากเกินไปหรือกระทั่งการเทิดทูนฮีโร่ บิตคอยน์ยังอยู่มาอย่างแข็งแกร่งมากกว่า 10 ปีผมไม่คิดว่าเป็นเพราะใครสักคน แต่มันเป็นเพราะอาณุภาพของ Network ที่เข้มแข็งและแพร่กระจายตัวในทุกนาทีแบบเดียวกับไมซีเลียม ผมฝันอยากเห็นสังคมที่โตในแบบของมันเอง มีความมั่นคงเข็มแข็ง อาจไม่ต้องเป็นหนึ่งเดียว แต่มันไม่ควรมีจุดตายอยู่ที่ใครทั้งนั้น
เราสามารถมีผู้เสียสละเก่งๆ ได้อีกมากมายที่กระจายตัวอยู่ตามพื้นที่ต่างๆ ต่างจังหวัด หรือแพลตฟอร์มต่างๆ เพื่อทำหน้าที่ผลักดันในแบบที่เขาถนัด
https://i.imgur.com/3sDzTdg.png เมื่อเราจินตนาการเห็นภาพนั้นเราจะเริ่มตระหนักได้ทันทีว่า..
เรานั้นตัวเล็กเกินกว่าจะไปคิดว่าเราใหญ่
ผมไม่ชอบใช้คำว่า “การต่อสู้” หรือ “การเอาชนะ” ไม่ว่าจะกับใคร (ใครๆ ก็คงจะหมายถึงรัฐ) บิตคอยน์มันชนะได้ด้วยตัวมันเองแบบไม่ต้องแข่งเลยด้วยซ้ำ ทำไมเราต้องไปเสียเวลากับการคิดหาหนทางเอาชนะในแบบเดิมๆ วิธีที่แยบยลกว่าน่าจะเป็น “การสร้าง” สิ่งที่ทรงพลัง กำแพงหนาที่แข็งแกร่งยากจะโค่นล้ม นั่นคือพลังแห่งความคิดและฝูงชน พลังแห่งเครือข่ายและชุมชน
ผมอยากเห็นมากกว่าแค่คนๆ เดียว คนกลุ่มเดียว ที่เก่งกล้าพอจะลุกขึ้นมาเสียสละแบ่งปันและช่วยเหลือ เผยแพร่สิ่งที่พวกเขารู้ไปยังคนอื่นๆ เพื่อขยายแนวคิดให้กระจายออกไป ผมมีส่วนจริงในการปลูกฝังแนวคิดและสร้างคอมมูนิตี้ขึ้นมาจากจุดนั้น แต่ผมไม่ใช่คนบงการอะไรทั้งสิ้น
แนวคิดจะได้รับการยอมรับคงไม่ใช่เพราะคนมาเกรงใจตัวผม แต่มันควรมาจากการที่ทุกคนเห็นพ้องต้องกันว่ามันอาจเป็นแนวทางที่ใช่สำหรับสังคมของพวกเขา เราอาจต้องนำ ต้องเป็นแบบอย่างก่อนในช่วงแรก แต่เมื่อทุกอย่างเริ่มเข้าที่ ทุกคนเริ่มเข้าใจเหตุผลและรูปแบบในการอยู่ร่วมกัน เวลาของผมสำหรับบทบาทนั้นก็คงไม่ต้องมีอีกแล้ว
นั่นเป็นเหตุผลว่าทำไมผมผละจากสิ่งที่เคยแอคทีฟในตอนแรก การมีส่วนร่วมเป็นแกนหลักและคอยแอคทีฟในชุมชน ผมไปทำอีกสิ่งหนึ่งเพื่อเตรียมไว้ตอบสนองต่อความต้องการของชุมชนในอนาคตนั่นคือคลังความรู้ เพราะผมเชื่อว่ากลุ่มบิตคอยน์ของชาวเรามันเติบโตขึ้นมากแล้วจากวันแรกๆ ที่เราได้เริ่ม
มันไม่ใช่เรื่องของจำนวน ไม่ใช่เรื่องของการตลาด มันคือหลักการและแนวคิด รูปแบบการปฏิสัมพันธ์ที่ค่อยๆ ก็ร่างสร้างตัวมาเรื่อยๆ จนมีคุณลักษณะที่ชัดและเป็นปัจเจกแตกต่างจากเหรียญอื่นๆ ไม่ว่าใครจากภายนอกจะมองว่าสัวคมของเราเป็นแบบไหนก็ตาม ผมไม่ได้สนใจเลยตรงนั้น เพราะนี่แหละคือเราในแบบของเรา
ผมมาเขียนเล่าเรื่องพวกนี้ไม่ใช่เพราะผมอยากจะหายตัวไปแบบ Satoshi หรอกนะครับ ผมไม่ได้ทำเรื่องยิ่งใหญ่อะไรขนาดนั้นเลย เพราะเมื่อไหร่ก็ตามที่เราคิดว่าเรานั้นใหญ่เสียเหลือเกิน ตัวของเราจะบดบังตาเราจนมืดบอด เราจะมองไม่เห็นใคร
ผมขอเป็นคนตัวเล็กๆ เล็กพอที่จะมองเห็นคนทุกคนบนโลกแบบนี้ต่อไปดีกว่า ผมชอบที่จะได้เห็นและคอยมีส่วนกับทุกๆ เรื่อง ผมสนุกกับมัน และหวังว่าพวกเราที่อ่านมาถึงตรงนี้ก็คงจะสนุกแบบผมเหมือนกัน
https://i.imgur.com/z7XmLjh.png บิตคอยน์ไม่ได้เปลี่ยนโลกในแบบที่เราเข้าใจ มันเริ่มเปลี่ยนคนตัวเล็กแบบพวกเขาให้เติบโตไปเปลี่ยนโลกต่างหากล่ะ
-
 @ 0b963191:fc5e7ffd
2023-08-08 18:06:14
@ 0b963191:fc5e7ffd
2023-08-08 18:06:14I have an idea I am currently putting together a javascript library and implementation for. This is a quick and dirty blog post to note where my head is at with it.
The main idea is using Nostr as a transport layer for accessing micro services in a censorship resistant way.
I will just use this blog post of a quick introduction on what I am thinking and I will link to more as development continues.
The idea
The idea is for the client side to access a nostr service very similar to how websites and other clients use XMLHttpRequest() to make API calls to services. The difference here being that rather than relaying on HTTP for the request, the requests and responses would be sent through relays.
 The above just shows a quick example of the standard http call to a service.
The above just shows a quick example of the standard http call to a service.This allows the following: * Services that do not directly rely on a hosts DNS * Services that do not expose the service IP address * Redundancy across multiple relays * Censorship resistant applications (I will not use the term dapp) that have a service backend
 The above shows how a client can interact with a service using nostr as the transport layer.
The above shows how a client can interact with a service using nostr as the transport layer.How it will work (TL;DR)

In simple terms a service will have a naddress (naddr1) that will carry its public key and core relays it will be listening on. A client will make a request using a generated nostr keypair referencing the service's pubkey in a tag and some call data. The service will read and validate this request and respond by referencing the client's event ID it used to make the call.
There will also be the ability for the service to push data to relays that can be read by clients without a call request being made (i.e. block height changes).
Why?
There are already many ways to push and pull data whether using nostr relays natively, inefficient block chain smart contracts, tor, or standard http. This may find a few use cases that can compliment existing methods.
In many ways this acts like many of the bots created on nostr that take input and responds with some output. This standardizes the uses a bit more.
A few use cases: * Server side code that can be used on something like ipfs (instead of using expensive inefficient smart contract block chains) * Services resistant to DNS and IP points of failure (i.e. targeted shutdown of services on the name server level. It has happened!) * Pulling in outside data that a client does not have ability or access to generate
I will have a working prototype of this in the next few weeks that I will host on a github.
-
 @ 3bf0c63f:aefa459d
2022-10-29 19:19:00
@ 3bf0c63f:aefa459d
2022-10-29 19:19:00What is better than bounties and grants?
The experience with bounties from HRF wasn't great. No one has answered to the calls for implementing what they wanted because the work was too much and the risk of not getting paid very real. The experience with grants in general from Spiral is also not great: many random developers making cool but useless projects, wasted money.
The two kinds of open-source financial support that have worked so far are:
- Paying people who are already doing useful work so they can continue doing that. That is the experience of some people who are "maintaining" Bitcoin Core, for example, or other open-source projects. You're doing a thing, you've proven yourself valuable and you definitely seem to be interested in that personally such that you don't need a boss telling you what to do, so take the money and just keep doing that.
- Structured open-source initiatives, like the LDK effort. Although LDK is arguably useless, it has a stated goal and that goal is being delivered. I don't have any knowledge about how its development process works, but they have people being paid and "bosses" that direct the work to be done, as any team needs. So it is not the same as an open grant.
The thing that is missing is a way to provide these open loose grants to people that don't require bosses, but also that don't just pick a winner and let them do whatever stupid idea they might have (Spiral grants), and also do not mandate that they do something big before being paid and offers no guarantee of that they will be paid whatsoever.
The solution: smaller flexible bounties in large quantities
My suggestions is: instead of giving 1 bitcoin for a huge very specific project, state some "principles", or "problems", in a loose manner, that you want to see solved. For example, "we, the organization X, wants to see projects that use zero-knowledge proofs to help Bitcoin somehow, because we love zero-knowledge proofs".
Then state that you're going to give 20 grants of 0.05 bitcoins each, at random times, for projects that you see being done that may be on the right track.
That will tilt people that may had a small inclination to work on these problems to actually start doing something, and if they see that what they're doing is being appreciated and awarded with a payment, they will be more incentivized to finish it. There could even be a conditional bounty (like HRF did with Cashu) for finishing the project with certain requirements, but this only works after some structure is already in place for a certain project.
-
 @ 668ceee5:930b960e
2023-08-08 11:25:59
@ 668ceee5:930b960e
2023-08-08 11:25:59So you've joined nostr, set up your lightning wallet, and started receiving zaps ⚡️ Maybe you've even participated in some zapathons. Bitcoin on nostr is a lot of fun, but why is everyone so excited about it?
I do not wish to get technical. While you can benefit greatly from learning about UTXOs and the other confusing things about Bitcoin, I want to talk about why Bitcoin is the hardest money ever discovered.
Many believe money is something governments create, or simply a figment of our imagination. As long as everyone believes the paper printed by governments is money, then we can have an economy. This is incorrect.
Money is actually an emergent property of trade. Suppose I have an apple, and I want your banana. We can trade, and this is called the barter system. But what if you don't want my apple because you would rather have oranges? How do I get your banana?
I could trade my apple for an orange and trade my orange for your banana, but this is obviously a huge inconvenience. Add a few million more goods to this equation, and we can see how this quickly becomes chaotic.
But humans are smart, and they eventually found a way to solve this problem with money. Money can be anything; this is true. However, we will soon see why some goods are better suited as money than others.
Suppose we all agree that apples will be the money we choose to exchange for goods. If I want bananas or oranges or iPhones, I give you a certain number of apples. This could work, because you know that you can purchase anything you want with apples, so you readily accept my apples.
https://cdn.nostr.build/p/rkMj.jpg
Eventually you want to buy a car that cost 1000 apples, so you start to save these apples. Everything is going great, until a few weeks later your apples start to rot. Nobody wants rotten apples, so you’re never getting that car.
Let's pretend apples do not rot, and you can successfully save 1000 apples. This takes you several years, and you can finally afford that car. However, people act; and since apples are money, everyone realized years ago that money can literally grow on trees. By the time you have saved 1000 apples, everyone has 10,000 apples from the trees they grew, and new apples are being harvested everyday.
The amount of a good in circulation divided by its annual production is called stock-to-flow ratio. As the production of apples quickly increases, the purchasing power of your apples decline because of apple inflation. This means our unrottable apples are not a good store of value, and therefore apples are easy money (as opposed to hard money).
https://cdn.nostr.build/p/ZEkl.jpg
Apples are terrible money, and humans eventually figured out they need something that doesn't rot or rust, while also having a low stock-to-flow ratio. This is how gold became the standard money of the world. Gold is practically indestructible, and despite many efforts from the alchemists, gold cannot be created. We must dig for gold, and put in real work to obtain it. Gold is also scarce, so it has one of the lowest stock-to-flow ratios of any resource in the world. For thousands of years, gold was the hardest money society had ever discovered. Gold sounds pretty awesome, doesn't it?
So what is so special about Bitcoin if we already have gold? Well, one of the most important distinctions is you cannot zap gold on nostr. This sounds like a joke, but it has very important implications.
https://cdn.nostr.build/p/owDW.jpg
Gold is bulky, it's difficult to divide into smaller units, and it's very expensive to transport. If I want to send you the equivalent of $1 in gold for your meme, it wouldn't be worth the trouble. Likewise, if we meet IRL and I have $10 in gold, but you only want $1 for your apple, it would be very difficult to divide my gold into exactly 1/10th pieces.
And this is how fiat dollars were born. The US used to be on a gold standard, where every dollar was a reciept for a certain amount of gold. This gave you the convenience of carrying a lightweight and easily divisible amount of gold.
It's important to note that governments did not declare paper and gold are money and force everyone to use it. On the contrary, governments form when a group of people are able to steal large amounts of gold, allowing them to afford armies that can steal even more gold.
The indestructibility of gold used to make this very easy. If I am the leader of a group of bandits and robbers, we can burn down your house and take the gold. However, there came a time when people began to trust and admire this group of bandits. So instead of burning down your house, I simply threaten you with violence and steal your gold. But don't worry, in return you get a piece of paper that we pretend is worth $1 in gold. Makes things more convenient for you, and I will safely store your gold in a centralized bank.
https://cdn.nostr.build/p/6xKa.jpg
This actually sounds like a decent deal, but after several years of trading paper for goods, the temptation to print more paper than the existing gold supply was too much. If a banker or politician can print $1000 to buy a brand new Model T, who's going to notice?
Well, like our inflated apples above, eventually the market noticed. People brought their paper receipts to the banks to get their gold back. But there wasn't enough gold, and this caused the Great Depression. Instead of owning their mistakes, governments and banks began working on a new form of economics based on the ideas of John Maynard Keynes. This is called Keynesian economics, but we will not get into all that.
https://cdn.nostr.build/p/nb2744.jpeg
The point is, gold has its flaws, and these flaws eventually led to the US Federal government being $32,000,000,000,000 in debt, endless wars, and a crumbling society.
But now we have Bitcoin. Like gold, Bitcoin is mined by powerful machines that require work. It cannot be created out of thin air. Bitcoin has a stock-to-flow ratio that is cut in half every four years. In the year 2140 there will be 21 million Bitcoin, and then no other Bitcoin will ever be mined again. This makes Bitcoin the most scarce resource in the universe.
Unlike gold, Bitcoin is not bulky, hard to divide, or difficult to transport because Bitcoin doesn't physically exist. Bitcoin is weightless, massless, easily divisible, and travels at the speed of light. You don't need to trust a bank to hold your Bitcoin, because instead of a vault, Bitcoin is held on 12 or 24 word seed phrases.
This means the equivalent of billions of dollars can be held on a single piece of paper, a metal plate, a digital hardware wallet, or even stored inside your thoughts. Nobody can burn down your house and steal it. If they threaten you with violence, they have no way to confirm the sats you give them are all you have.
https://cdn.nostr.build/p/nb2500.jpeg
Yes, this is the same Bitcoin we are all zapping each other on nostr. Not only is it more convenient than fake paper dollars, it is the greatest and hardest money ever discovered.
This is why Bitcoiners always stress the importance of self custody. Bitcoin is your property, and as history has shown time and time again, we cannot trust anyone. We cannot trust the governments, the banks, exchanges, or even the custodial wallets you download to your phone.
But all you have to do is have fun zapping your Bitcoin on nostr, move it to self custody when you accumulate a decent amount of sats, and wait for the market to respond. Because like gold before it, Bitcoin doesn’t need governments to accept it. Bitcoin is inevitable.
If you would like to learn more about the economics of Bitcoin and Austrian Economics in general, I highly recommend reading The Bitcoin Standard by nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak, which this note attempts to summarize.
-
 @ 7395e451:3f48abc6
2023-08-14 08:13:16
@ 7395e451:3f48abc6
2023-08-14 08:13:16Project GovernanceDAO: Empowering Decentralized Decision-Making for Stronger Communities
In the rapidly evolving landscape of decentralized techndologies, the concept of governance takes on a new dimension with Project GovernanceDAO. This pioneering initiative seeks to revolutionize the way communities make decisions, putting the power of governance directly into the hands of the people. By leveraging blockchain and decentralized principles, GovernanceDAO aims to foster transparency, inclusivity, and collective decision-making, paving the way for stronger and more resilient communities.
The Evolution of Governance in the Digital Age
Traditional governance models often involve centralized decisfion-making structures, which can lead to inefficiencies, lack of transparency, and limited representation of community interests. In the era of Web3 and blockchain, GovernanceDAO introduces a paradigm shift by enabling communities to collaborate and co-create in a decentralized and transparent manner.
Introducing Project GovernanceDAO
Project GovernanceDAO is not just a platform; it's a philosophy that centers around the idea that decisions should be made collectively and inclusively. By utilizing blockchain technology, GovernanceDAO empowers community members to participate directly in the decision-making process, enabling them to progpose, discuss, and vote on various matters.
Key Objectives and Innovative Features
-
Decentralized Proposals: Community members can submit prgoposals for various initiatives, projects, or changes within the community ecosystem.
-
Token-Based Voting: Each member's voting power is determined by the number of tokens they hold, ensuring a democratic and proportional decision-making process.
-
Transparency and Accountability: All proposals, discussions, and voting outcomes are recorded on the blockchain, ensuring transparency and accountability.
-
Smart Contract Execution: Once a proposal is approved, smart contracts are used to execute the decision, ensuring that the agreed-upon action is carried out.
Empowering Community Governance
Project GovernanceDAO offers a range of benefits that contribute to its potgential to transform community governance:
-
Inclusivity: GovernanceDAO ensures that every member's voice is heard, regardless of their status or influence, promoting a more inclusive decision-making process.
-
Transparency: Decisions are made openly and transparently, enabling community members to track proposals and outcomes in real-time.
-
Efficiency: The use of smart contracts automates the execution of decisions, reducing bureaucracy and streamlining the implementation process.
-
Empowerment: Community members become active participants in shaping the future of their community, fostering a sense of ownership and empowerment.
Shaping the Future of Communities
As Project GovernanceDAO progresses, collaborations between community leaders, blockchain developers, and engaged community members will shape its trajectory. The project's commitment to decentralized decision-making aligns with the principles of empowerment, collaboration, and democratic governance.
In a world where communities are interconnected and digital technologies enable unprecedented levels of participation, Project GovernanceDAO emerges as a beacon of community strength. With the project gaining momentum and attracting communities that value transparency, inclusivity, and collective action, it has the potential to redefine how communities make decisions and work together. Through its dedication to empowering decentralized decision-making, Project GovernanceDAO envisions a future where communities thrive, driven by the collective wisdom and shared aspirations of their members.
-
-
 @ 3bf0c63f:aefa459d
2022-10-29 13:24:00
@ 3bf0c63f:aefa459d
2022-10-29 13:24:00On Bitcoin Bounties
The HRF has awarded two bounties yesterday. The episode exposes some of the problems of the bounties and grants culture that exists on Bitcoin.
First, when the bounties were announced, almost an year ago, I felt they were very hard to achieve (and also very useless, but let's set that aside).
The first, "a wallet that integrates bolt12 so it can receive tips noncustodially", could be understood as a bounty for mobile wallets only, in which case the implementation would be hacky, hard and take a lot of time; or it could be understood as being valid for any wallet, in which case it was already implemented in CLN (at the time called "c-lightning"), so the bounty didn't make sense.
The second, a wallet with a noncustodial US dollar balance, is arguably impossible, since there is no way to achieve it without trusted oracles, therefore it is probably invalid. If one assumed that trust was fine, then it was already implemented by StandardSats at the time. It felt it was designed to use some weird construct like DLCs -- and Chris Steward did publish a guide on how to implement a wallet that would be eligible for the bounty using DLCs, therefore the path seemed to be set there, but this would be a very hard and time-intensive thing.
The third, a noncustodial wallet with optional custodial ecash functionality, seemed to be targeting Fedimint directly, which already existed at the time and was about to release exactly these features.
Time passed and apparently no one tried to claim any of these bounties. My explanation is that, at least for 1 and 2, it was so hard to get it done that no one would risk trying and getting rejected. It is better for a programmer to work on something that interests them directly if they're working for free.
For 3 I believe no one even tried anything because the bounty was already set to be given to Fedimint.
Fast-forward to today and bounties 1 and 3 were awarded to two projects that were created by the sole interest of the developers with no attempt to actually claim these bounties -- and indeed, the two winners strictly do not qualify according to the descriptions from last year.
What if someone was working for months on trying to actually fulfill the criteria? That person would be in a very bad shape now, having thrown away all the work. Considering this it was a very good choice for everyone involved to not try to claim any of the bounties.
The winners have merit only in having pursued their own interests and in creating useful programs as the result. I'm sure the bounties do not feel to them like a deserved payment for the specific work they did, but more like a token of recognition for having worked on Bitcoin-related stuff at all, and an incentive to continue to work.
-
 @ fa984bd7:58018f52
2023-08-08 08:37:26
@ fa984bd7:58018f52
2023-08-08 08:37:26Let's talk about NIP-31, NIP-89 and how discoverability in Nostr is not only not broken, but it's a step-function improvement over the status quo of the siloed web.
The captured internet has organically evolved multiple solutions to enable discoverability, which is, the process of discovering new content / tools / people, etc.
These tools sit at the top of the internet food chain: Search engines, app stores, social networks' proprietary algorithms, etc.
These individual approaches are multi-billion industries on their own.
How are we, humble nostriches, supposed to compete with these giants and their enormous moats?
We compete by not competing. By playing a different game.
The game
Nostr has a funny design that makes for some very creative implementations.
In Nostr everything is an event. These events can reference other events. Each event has a
kindnumber, which represent what that event is. An event of kind 1 is a short note, what we typically call a tweet. An event of kind 7 is a reaction to another event, such as 🤙ing it. Zaps? Those are kind 9735.It's very simple. Painfully simple.
But the fact that these event kinds can mix together in a chaotic soup of events changes the game.
The soup
A few months ago I wrote an application based on Karnage's designs. Zapstr. It's a music player where everything you do is... you guessed it, a nostr event. Publishing a song. Listening to a song. Liking it, and of course, zapping it.
But also, you can respond to a song with a short note.
And that's the first ingredient of this soup.
The moment you find a song you like in this remote corner of the internet and make a comment about it, your followers, can see this comment on any other social application.
Of course, since Zapstr is an application with zero marketing budget, using a kind number I came up with (kind 31337, a wink to the elite hackers out there), your followers don't know what you're talking about.
You're talking to the void.
The void
This is where NIP-31 and NIP-89 come in.
Until these NIPs, you responding to a random song, or to a random anything, your followers will think you're going insane. You're responding with something like "Wow, this song moved me to my core", but you don't mention what song you're talking about.
Lana del rey, is that you?
NIP-31 is, like almost anything in nostr, simple as hell.
If you remember the good old
alttag in HTML<img>s that was so important when you were loading images on your 28k modem, you'll understand NIP-31. This NIP proposes that event kinds that are not widely supported by all clients, include analttag explaining, in a human readable format, what the event is about.alt: "This is a song 'Video Games' by Lana del Rey."Simple.
But now your followers have context.
Of course, the context is helpful. But insufficient for a full experience.
The full experience
The measuring stick most people will compare our ecosystem with, are superapps.
WeChat. X.com. Etc.
here's a reason these apps are so popular. It's not merely that people might crave being governed by a benevolent dictator; the convenience of superapps stands on its own merit.
The appeal of a superapp is the convenience of the seamless integration across use-cases.
Chat with your friends? ✅
Pay your bills? ✅
Get a ride? ✅ How about order some food while you're riding back home? ✅
The super app is the internet. Why leave? Why create a new account somewhere else? Why go through the hassle of connecting your payment methods, porting your social graph?
It's all so painful. What's the upside?
Of couse, if you've been paying attention, you feel that Nostr provides many of these properties.
Frictionless transition through all use cases: it's all just one npub!
Porting your social graph: there is no porting; your social graph already transcends whatever nostr clients you use.
Reconnecting your payment methods: well, we have bitcoin, and wallet connect, and lightning!
Putting it all together
Here the vision of the Nostr I see comes full circle, and why I believe nostr doesn't only NOT suffer from a discoverability problem, but it's actually orders of magnitude better than the status quo. We've just haven't fully built it yet.
Nostr allows any developer, with no marketing budget, to create an app, a new app, using a new kind number, on an incredibly niche use case of the internet/nostr, and leverage the liquid nature of how event kinds interoperate to provide organic reach to these new and strange use case of nostr/internet.
The glue
NIP-89 was that one last missing piece to make the experience of transitioning through multiple microapps cohesive. It provides two simple building blocks:
- a way for apps to "register" kind applications handlers (e.g. app X supports kind Y using such-and-such URL)
- a way for users to publicly associate kinds with these application handlers throughout their different platforms (e.g. web, vs ios)
A byproduct of this, is that anyone can query 1) which applications exist for a given kinds, and 2) which one the people they follow use.
Let's go back to the Zapstr example.
One of your followers sees that song, but clicking on the event yields nothing. Their client doesn't know what kind 31337 means, how to render, or interact with it.
But, using NIP-89 the client can ask the user's social graph "hey, what apps do you use for kind 31337?"
All the user experiences is the song opening up in Zapstr, or in any other app that supports kind 31337 as recommended by the people they follow.
From the people the user follows.
This is key.
This means that multiple applications can compete and win under the same use case in different communities.
A million microapps, one glue
Why do I insist that Nostr is orders-of-magnitude better than the siloed internet and the superapps approach?
Superapps need to appeal to everybody; they have to move carefully, iterate in small steps and remain very conservative. By their very nature, they MUST be bland (which is why all these superapps look very much alike and none of them look like ONOSENDAI)
Whereas in nostr we can experiment with the wildest of ideas and weirdest approaches since no app needs to serve all users. Perhaps a very weird app appeals to only 20 or 50 people, but it can transparently interact with all other apps serving the same event kind.
Long-tails all the way down.
As these microapps enable all types of niche use cases while maintaining interoperability and leveraging discoverability and distribution through nostr, the use cases of nostr begin to blend in and the artificial use-case silos break down.
App Stores need not apply
I believe App Stores are a synthetic solution to a problem that doesn't exist in Nostr.
App Stores exist due to the internet's lack of unification in exposing novel use cases to users.
App Stores are necessary because the captured internet lacks a way of unifying different use cases exposing novel use cases and applications to users. The main way of discovering these was through use cases.
But in this world, where within the context of a social client you might see when one of the people you follow posts a new product for sale, or adds a review to a concert, or takes notes about a book they're reading you can immediately discover these new use cases organically.
WTF happened in 1989?
For decades, we've operated within data silos, with each use case as its own isolated entity. The only trancendence of use-cases was the centralizing vertical-integration of a Facebook offering both social media and commerce.
YouTube data isn't interoperable with Spotify's. Twitter isn't interoperable with Amazon, and Airbnb doesn't inform in any sort of way what happens in reddit.
Every one of these use cases is its own thing, and, to stay relevant, they needed to persuade you to engage, engage, engage. We are all very aware of this and it's many pitfalls.
We know where that path leads.
But, as we've constructed Nostr apps we've erected similar use-case walls. Social clients are interoperable with other social clients, but the link to music clients, or to commerce websites, or to airbnb-like websites, etc, is mostly non-existent.
Just like in 1989, bringing down this wall, will unleash a great flurry of innovation and creativity. When Nostr can provide organic, free, non-invasive, discoverability and distribution to any new use case, we'll see millions of microapps bloom and new entrepreneurs and developers build on Nostr.
Developers, tear down this wall.
-
 @ 0a63d301:b1fb5602
2023-08-14 08:12:52
@ 0a63d301:b1fb5602
2023-08-14 08:12:52In the dynamic realm of digital art and environmental advocacy, a groundbreaking initiative known as Project EcoNFT is paving thez way for a new era of awareness and action. This visionary project aims to combine the power of Non-Fungible Tokens (NFTs) with environmental consciousness, using the blockchain technology to promote sustainability and foster a deeper connection between art and the planet.
The Nexus of Art and Environmental Advocacy
Art has long been a medium for expressing societal concerns and sparking conversations. As environmental issues continue to take center stage on the global agenda, Project EcoNFT recognizes the potential of art and blockchain technology to amplify the message of sustainability and inspire positive change.
Introducing Project EcoNFT
Project EcoNFT is more than just a digital art platform; it's a movement that seeks to integrate art and environmental awareness in a way that resonates with individuals across the globe. By leveraging NFTs and blockchain, EcoNFT provides artists with a unique avenue to create and share environmentally themed artwork while fostering a sense of responsibility and engagement among collectors.
Key Objectives and Innovative Features
-
Eco-Focused NFTs: Project EcoNFT encourages artists to create NFTs that center around environmental themes, such as climate change, conservation, and sustainable practices.
-
EcoCharity Initiatives: A portion of the proceeds from EcoNFT sales is directed toward environmental charities and initiatives, creating a direct impact on the causes that matter most.
-
Carbon-Neutral Operations: EcoNFT is committed to offsetting its carbon fcootprint, ensuring that its activities have a minimal environmental impact.
-
Community Engagement: The project facilitates discussions, workshops, and events that bring artists, collectors, and environmentalists together to foster a sense of community and shared purpose.
Empowering Environmental Change through Art
Project EcoNFT offers a range of benefits that contribute to its potential to drive environmental awareness:
-
Art as Advocacy: NFTs serve as digital canvases for artists to depict pressing environmental concerns, raising awareness and inspiring action.
-
Direct Impact: Through financial contributions to environmental causes, EcoNFT transforms art purchases into tangible support for conservation efforts.
-
Global Collaboration: The project creates a global platform for artists, collectors, and environmentalists to collaborate, amplify messages, and drive change together.
-
Positive Reinforcement: By showcasing the beauty of nature and highlighting the urgency of environmental issues, EcoNFT motivates individuals to take positive steps toward sustainability.
Shaping a Sustainable Future
As Project EcoNFT gains momentum, collaborations between artists, environmentalists, and blockchain enthusiasts will shape its trajectory. The project's commitment toq promoting environmental awareness through NFTs aligns with the principles of creativity, sustainability, and shared responsibility.
In a world where art is a universal language and environmental concerns are of paramount importance, Project EcoNFT emerges as a potent catalyst for change. With the project garnering support from artists, collectors, and advocates aof ecological well-being, it has the potential to redefine how art contributes to the global dialogue on sustainability. Through its dedication to merging art and environmental consciousness, Project EcoNFT envisions a future where creative expression transcends boundaries and plays a pivotal role in safeguarding our planet for generations to come.
-
-
 @ 3bf0c63f:aefa459d
2022-09-12 02:28:00
@ 3bf0c63f:aefa459d
2022-09-12 02:28:00A prediction market as a distributed set of oracle federations
See also: Truthcoin as a spacechain.
This is not Truthcoin, but hopefully the essence of what makes it good is present here: permissionless, uncensorable prediction markets for fun, profit, making cheap talk expensive and revolutionizing the emergence and diffusion of knowledge in society.
The idea
The idea is just to reuse Fedimint's codebase to implement federated oracle corporations that will host individual prediction markets inside them.
Pegging in and out of a federation can be done through Lightning gateways, and once inside the federation users can buy and sell shares of individual markets using a native LMSR market-maker.
Then we make a decentralized directory of these bets using something simple like Nostr so everybody can just join any market very easily.
Why?
The premise of this idea is that we can't have a centralized prediction market platform because governments will shut it down, but we can instead have a pseudonymous oracle corporation that also holds the funds being gambled at each time in a multisig Bitcoin wallet and hope for the best.
Each corporation may exist to host a single market and then vanish afterwards -- its members returning later to form a new corporation and host a new market before leaving again.
There is custodial risk, but the fact that the members may accrue reputation as the time passes and that this is not one big giant multisig holding all the funds of everybody but one multisig for each market makes it so this is slightly better.
In any case, no massive amounts are expected to be used in this scheme, which defeats some of the use cases of prediction markets (funding public goods, for example), but since these are so advanced and society is not yet ready for them, we can leave them for later and first just try to get some sports betting working.
This proto-truthcoin implementation should work just well enough to increase the appetite of bitcoiners and society in general for more powerful prediction markets.
Why is this better than DLCs?
Because DLCs have no liquidity. In their current implementations and in all future plans from DLC enthusiasts they don't even have order books. They're not seen very much as general-purpose prediction markets, but mostly as a way to create monetary instruments and derivatives.
They could work as prediction markets, but then they would need order books and order books are terrible for liquidity. LMSR market makers are much better.
But it is custodial!
If you make a public order book tied to known oracles using a DLC the oracle may also be considered custodial since it becomes really easy for him to join multiple trades as a counterpart then lie and steal the money. The bets only really "discreet" if they're illiquid meaningless bets between two guys. If they're happening in a well-known public place they're not discreet anymore.
DLC proponents may say this can be improved by users using multiple oracles and forming effectively a federation between them, but that is hardly different from choosing a reputable oracle corporation in this scheme and trusting that for the life of the bet.
But Hivemind is better!
Yes.
-
 @ deba271e:36005655
2023-05-06 18:50:59
@ deba271e:36005655
2023-05-06 18:50:59(This is a repost from my original article for Stacker News)\n\nIs some specific website, like Twitter, bringing you joy or is it bringing you the opposite? Do you have a hard time stopping? Here's a quick tutorial recommended by 9 out 10 dentists. \n\nFirst rule: Never run random bash scripts you find online without reading the scripts yourself! \n\n---\n\n## Blocking with /etc/hosts\nIf you understand the first rule, then read, copypaste and run following script in your terminal. \n\nOn Linux or MacOS\n
shell\nsudo bash -c "cat >> /etc/hosts << EOF\n\n0.0.0.0 twitter.com\n0.0.0.0 reddit.com\nEOF\n"\n\nAnd that's it. This should apply the rule immediately. \nIf you want to check how does your/etc/hostslook like, then just runnano /etc/hosts.\n\nOn Windows\nbatch\necho 0.0.0.0 twitter.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\necho 0.0.0.0 reddit.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\n\n\n--- \n\n## Blocking with pi-hole\nEven better option is if you have pi-hole set up on your network to proxy all your DNS requests. If you didn't know pi-hole is also available on Umbrel or Citadel.\n\nSimple steps:\n1. Sign in to your your pi-hole admin interface, e.g. https://pi.hole/admin/index.php\n2. Navigate to Blacklist\n3. Addtwitter.comin the Domain input box and click on Add to Blacklist\n4. You are all set. -
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ c9dccd5f:dce00d9a
2023-05-02 07:16:55
@ c9dccd5f:dce00d9a
2023-05-02 07:16:55Every fundamental particle carries an intrinsic angular momentum, which we call 'spin'. It is important to remember that this is an intrinsic quantum mechanical property of particles. There is no such thing as a spinning sphere in the classical sense. Nevertheless, the image of a spinning sphere is often a good analogue to understand what is going on.\n\n## Helicity\n\nThe helicity of a particle is the projection of its spin vector onto its linear momentum. In the spinning analogy, it is the relation of its spin direction to its direction of motion. The particle helicity is called either right-handed or left-handed. We say that the particle has right-handed helicity if the spin is aligned with the direction of motion, and left-handed helicity if the spin and motion have opposite orientations. In the spinning analogy, we can immediately understand where the names come from and what they mean. We look at your hands, make a fist and spread the thumbs. The thumbs indicate the direction of motion and the curled fingers indicate the direction of spin. We point our thumbs in the direction of motion and compare the fingers with the direction of spinning we see: If they are in the same direction as the right hand, we call it right-handed helicity, and conversely.\n\nSince massless particles (e.g. photons) travel at the speed of light, we will never find a reference frame in which this particle is at rest, i.e. we cannot find a rest frame. Therefore, the helicity will never change, since the spin is fixed and the direction of motion is the same in all reference frames.\n\nOn the other hand, massive particles travel at a speed less than that of light, so in principle we can find a rest frame. In fact, we can even find a reference frame in which the particle appears to be moving in the opposite direction. Yet the spin of a particle never changes. This leads to the fact that for massive particles the helicity can change because the direction of motion can be reversed, resulting in the opposite helicity. Note that this is not possible for massless particles, because we cannot move faster than them. \n\nThus we see that the mass of a particle tells us whether the helicity of a particle is an intrinsic property of the particle. For a massless particle, the helicity is fixed in all reference frames, whereas for a massive particle this is not the case, because different observers can infer different helicities for the same particle. \n\nAs physicists, we like to find fundamental properties of a particle. We therefore ask whether there is a related property to helicity that is intrinsic to particles. We call this fundamental property chirality.\n\n## Chirality\n\nChirality and helicity are closely related. Just as we say a particle has right-handed or left-handed helicity, we say a particle has right-handed or left-handed chirality. Sometimes we can drop the '-handed' and just say right-/left-helicity or right-/left-chirality. For massless particles, helicity and chirality are the same thing, so a right-chiral particle will also have right-helicity. For massive particles, however, helicity and chirality are different. A massive particle has a certain chirality but can have both helicity states, e.g. a right-chiral particle can have right or left helicity depending on the frame of reference. \n\nChirality is an abstract concept that refers to a fundamental intrinsic quantum mechanical property of a particle. However, a useful and nice visualisation can be made by looking at our hands. We hold our hand in front of us. The left and right hands are mirror images of each other. No matter how we rotate, flip or move one hand, it will never look exactly like the other hand. Our hands have different chirality.\n\nIn physics, particles with different chirality can be considered as completely different particles. It refers to how a particle's quantum mechanical wave function behaves under rotation. The quantum wave functions of left- and right-chiral particles behave differently under rotation.\n\nThe measurable physical effect of a particle's chirality can be seen in the theory of the weak interaction. The weak interaction only affects left-chiral particles and not right-chiral ones. As a result, neutrinos, which are weakly interacting particles, are only observed in left-handed chiral states.\n\n---\n\n_I hope this post has helped you understand the concept of helicity and chirality in physics. If anything is still unclear, or if an explanation could be improved to make it easier to understand, please comment or write to me. I am happy to answer. I'm looking forward to your feedback. PV_ 🤙\n\n---\n\n
v0 @ 785591; v1 @ 785712: fixed typos and added a missing sentence; v2 @ 787922: slight changes to the layout -
 @ 32e18276:5c68e245
2023-08-07 16:10:07
@ 32e18276:5c68e245
2023-08-07 16:10:07Hey guys,
I spent some time this weekend fixing a bunch of the bugs that were introduced in the latest nostrdb refactor. See the changelog below for the full list of changes in the latest build!
Planned this week
I have a big list of things I'm planning on adding to Damus this week:
- Lists!
- Zap improvements: Bringing back top zap comments in threads, profile zap comments in notifications, Private DM Zaps
- Video player improvements
- Sharing improvements (share to damus, etc)

Make sure to come back in a week to see how much I could get done!
Changelog
Added
- Add close button to custom reactions (Suhail Saqan)
- Add ability to change order of custom reactions (Suhail Saqan)
- Adjustable font size (William Casarin)
Changed
- Show renotes in Notes timeline (William Casarin)
Fixed
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Don't cutoff text in notifications (William Casarin)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fixed nostr reporting decoding (William Casarin)
- Dismiss qr screen on scan (Suhail Saqan)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix crash when muting threads (Bryan Montz)
-
 @ 3bf0c63f:aefa459d
2022-05-27 14:34:00
@ 3bf0c63f:aefa459d
2022-05-27 14:34:00Formula for making games with satoshis
I think the only way to do in-game sats and make the game more interesting instead of breaking the mechanics is by doing something like
- Asking everybody to pay the same amount to join;
- They get that same amount inside the game as balances;
- They must use these balances to buy items to win the game;
- The money they used becomes available as in-game rewards for other players;
- They must spend some money otherwise they just lose all the time;
- They can't use too much because if they run out of money they are eliminated.
If you think about it, that's how poker mostly works, and it's one of the few games in which paying money to play makes the game more interesting and not less.
In Poker:
- Everybody pays the same amount to join.
- Everybody gets that amount in tokens or whatever, I don't know, this varies;
- Everybody must pay money to bet on each hand;
- The money used on each round is taken by the round winner;
- If you don't bet you can't play the rounds, you're just eliminated;
- If you go all-in all the time like a mad person you'll lose.
In a game like Worms, for example, this could be something like:
- Idem;
- Idem;
- You must use money to buy guns and ammunitions;
- Whatever you spent goes to a pot for the winners or each round -- or maybe it goes to the people that contributed in killing you;
- If you don't buy any guns you're useless;
- If you spend everything on a single gun that's probably unwise.
You can also apply this to games like Counter-Strike or Dota or even Starcraft or Bolo and probably to most games as long as they have a fixed duration with a fixed set of players.
The formula is not static nor a panacea. There is room for creativity on what each player can spend their money in and how the spent money is distributed during the game. Some hard task of balancing and incentivizing is still necessary so the player that starts winning doesn't automatically win for having more money as the game goes on.
-
 @ 7395e451:3f48abc6
2023-08-14 08:08:01
@ 7395e451:3f48abc6
2023-08-14 08:08:01Project Web3Supply: Pioneering Traceable and Ethical Supply Chains on the Blockchain
In today's interconnected global marketplace, consumers are increasingly conscious of the origin, journey, and ethical considerations behind the products they purchase. Addressing this growing demand for transparency and accountability, Project Web3Supply emerges as a groundbreaking initiative that harnesses the power of blockchain technology to revolutionize supply chain management. By introducing traceability, authentdicity, and ethical practices, Web3Supply aims to reshape the way goods are produced, distributed, and consumed.
The Challenges of Traditional Supply Chains
Traditional supply chains often lack transparency, making it challenging for confgsumers to verify the authenticity and ethical sourcing of products. Moreover, issues like counterfeit goods, environmental concerns, and exploitative labor practices have highlighted the need for a more robust and accountable system.
Introducing Project Web3Supply
Project Web3Supply is not simply an enhancement of existing supply chain practices; it represents a paradigm shift in how supply chains are conceived and executed. By leveraging blockchain's immutable ledger and decentralized architecture, Web3Supply aims to create a secure and traceable ecosystem where every step of a product's journey is documented and verified.
Key Objectives and Innovative Features
-
Immutable Product Records: Web3Supply records each stage of a product's journey on the blockchain, ensuring that information is tamper-proof and verifiable.
-
Ethical Sourcing: The platform encourages businesses to disclose sourcing practices, promoting ethical production, and discouraging the use of exploitative labor or harmful materials.
-
Consumer Empowerment: With Web3Supply, consumers can access detailed information about a product's origin, ingredients, and manufacturing processes by simply scanning a QR code.
-
Supply Chain Automation: Smart contracts automate certain supply chain processes, such as payments and inventory management, reducing administrative overhead.
Empowering Transparent and Ethical Commerce
Project Web3Supply offers a range of benefits that contribute to its potengtial to reshape supply chains:
-
Trust and Verification: Blockchain's transparency ensures that every claim made about a product's origin and journey can be verified, promoting trust between businesses and consumers.
-
Ethical Consumer Choices: Consumers can make informed purchasing decisions by supporting brands and products that align with their values, ultimately driving the demand for ethical practices.
-
Reduced Fraud: The immutability of blockchain records mitigates the risk of counterfeit goods and fraudulent claims, creating a more secure marketplace.
-
Business Accountability: Web3Supply encourages businesses to adopt ethical practices by holding them accountable to their claims and commitments.
Shaping the Future of Ethical Commerce
As Project Web3Supply progresses, collaboration with supply chain experts, blockchain developers, responsible businesses, and the broader Web3 community will shape its trajectory. The project's commitment to traceable and ethical supply chains aligns with the principles of transparency, accountability, and sustainable business practices.
In a world where consumers demand more than just products, Project Web3Supply emerges as a catalyst for change. With the project gaining momentum and receiving support from ethical consumers, businesses, and advocates of responsible commerce, it has the potential to redefine how supply chains are designed and managed. Through its dedication to traceable and ethical supply chains on the blockchain, Project Web3Supply envisions a future where every purchase is a step towards a more transparent, accountable, and ethical global marketplace.
-
-
 @ 5e5fc143:393d5a2c
2023-04-15 17:18:11
@ 5e5fc143:393d5a2c
2023-04-15 17:18:11\nJust revisiting some quick tips for #newbies #pow #public #blockchain users only.\n\nif you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.\n\nHot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process\n\nCold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts\nPaper wallets are best n cheapest form of cold wallet that can used once n thrown away.\n\n#Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/\n\n\n
 \n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n
\n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n -
 @ 3bf0c63f:aefa459d
2022-05-10 21:57:00
@ 3bf0c63f:aefa459d
2022-05-10 21:57:00Doing automatic payouts to users on the Lightning Network
No service wants to keep users balances forever or "become a custodian", as that may have some complications dependending on who is doing it.
But the sad truth is that there is no way to do automatic payouts to users on the Lightning Network. So if you're running a marketplace or a game of some kind that takes sats from some users, does something, then sends sats out to other users, you must keep a table with balances for each user.
-- But I can ask for a Lightning Address!
No, you can't, because mobile users of noncustodial wallets do not have those things generally, and that's not the purpose of Lightning Addresses anyway. Well, of course you can, but what I'm trying to say is that you shouldn't, as that is an anti-practice that will cause people to not want to use your service or force them into custodial providers -- which may be ok for them, but may not be.
-- So if I ignore the concerns above I can do this with Lightning Addresses, right?
Not really, because payments can fail. The user might input an invalid Lightning Address, or the Lightning Address may stop working after a while. Or even if it is working and online your payout can still fail for many reason inherent to Lightning.
That means you need to keep a table of balances for your users anyway. It doesn't matter.
Since you are already keeping a table of balances, now it's your chance to bring back the mobile noncustodial wallet users into a greater standard that accomodates everybody: LUD-14.
Wallets can implement LUD-14 support and then be made to withdraw balances from your service automatically every time they're turned on or periodically or upon manual request from the user. That limits the amount of user balance you'll have to keep on your service (but you can also add more rules around that, for example, automatically confiscating balances that stay parked too long, or putting a hard limit on the balance size for each user).
-- But with Lightning Addresses I can do instant payouts!
Yes, you can, but that's why LUD-15 exists: for all custodial providers, noncustodial wallets that rely on some kind of friendly server or coordinator (like Breez, Blixt or Phoenix) or even noncustodial providers running some kind of homemade server, you can dispatch these requests that cause them to withdraw the money automatically, which makes the experience similar to instant payouts -- and better, since then the payment requests can be more meaningful and say they are withdrawals from your service instead of saying that you're donating money to them (which is what most Lightning Address payments really mean).
-
 @ 0a63d301:b1fb5602
2023-08-14 08:08:00
@ 0a63d301:b1fb5602
2023-08-14 08:08:00In the ever-evolving landscape of technological advancements, two groundbreaking technologies have captured the world's imagination: artificial intelligence (AI) and blockchain. Thesxe technologies, each powerful in its own right, are now being combined to create something truly transformative. Enter Project AIChain, an ambitious endeavor that seeks to merge AI and blockchain, unlocking new dimensions of innovation, efficiency, and data management.
The Convergence of AI and Blockchain
Artificial intelligence has redefined how machines can analyze data, recognize patterns, and make intelligent decisions, while blockchain has revolutionized data storage, security, and transparency. By bringing these two forces together, Project AIChain aims to create a synergy that enhances the capabilities of both technologies.
Introducing Project AIChain
Project AIChain is not simply about coexistence; it represents a fusion thsat goes beyond the sum of its parts. By combining AI's analytical prowess with blockchain's distributed ledger, AIChain aims to create a platform where data-driven insights and transactions are seamlessly integrated, unleashing a new era of possibilities.
Key Objectives and Innovative Features
-
Enhanced Data Analysis: AIChain leverages AI algorithms to analyze blockchain data, extracting valuable insights and trends that can inform decision-making across industries.
-
Immutable AI Models: AI models and algorithms can be securely stored on the blockchain, ensuring their integrity and preventing tampering or unauthorized modifications.
-
Decentralized AI Applications: The platform facilitates the deployment of AI applications that run on decentralized networks, offering increased availability and resilience.
-
Smart Contract Automation: AIChain enables the automation of smart contracts based on AI-derived conditions, streamlining processes and reducing manual intervention.
Unlocking the Synergy of AI and Blockchain
Project AIChain offers a host of advantages that contribute to its potential to reshape various sectors:
-
Data-Driven Insights: The integration of AI and blockchain allows for enhanced data analysis, enabling organizations to extract meaningful insights and optimize their operations.
-
Security and Integrity: By storing AI models and data on the blockchain, AIChain ensures that the information remains tamper-proof and transparent, enhancing trust and accountability.
-
Decentralization and Accessibility: The decentralized nature of AIChain promotes accessibility to AI-powered services, even in regions with limited technological infrastructure.
-
Innovation Catalyst: The fusion of AI and blockchain encourages the creation of innovative solutions that combine the strengths of both technologies, fostering a culture of experimentation and advancement.
Shaping the Future of Innovation
As Project AIChain evolves, collaborations with AI experts, blockchain developers, industry leaders, and the broader tech community will shape its trajectory. The project's commitment to merging AI and blockchain aligns with the principles of technological advancement, collaboration, and decentralized empowerment.
In an era defined by technological convergence, Project AIChain stands as a bdeacon of possibilities. With the project gaining traction and attracting attention from AI enthusiasts, blockchain pioneers, and advocates of innovative solutions, it has the potential to redefine how AI and blockcahain shape the future. Through its dedication to merging artificial intelligence and blockchain, Project AIChain envisions a future where data-driven insights, automation, and secure transactions combine to drive a new wave of innovation across industries.
-
-
 @ ead55d2b:08ae8e65
2023-08-14 07:33:48
@ ead55d2b:08ae8e65
2023-08-14 07:33:48Project EduVerse: Building an Educational Metaverse with Web3
In a world where education is undergoing a profound transformation driven by technological advancements, a groundbreaking initiative is emerging to redefine the future of learning through the power of Web3 technology. Introducing Project EduVerse, a visionary endeavor that aims to create an immersive educational metaverse that leverages the principles of blockchain, decentralized networks, and experiential learning. By merging the virtual realm with educational innovation, EduVerse seeks to revolutionize how knowledge is acquired, shared, and experienced.
Navigating Education in the Web3 Era
As traditional educational models face challenges and opportunities in the digital age, Project EduVerse recognizes the transformative potential of Web3 technology in shaping the future of learning. By integrating blockchain's transparency, interoperability, and decentralized architecsture, EduVerse envisions a future where education transcends physical boundaries, offering learners an interactive and collaborative platform to explore and master various subjects.
Introducing Project EduVerse
Project EduVerse represents more than just a virtual classroom; it's a call to reimagine education in a digitized and decentralized world. By harnessing the capabilities of blockchain and decentralized networks, EduVerse aims to bridge the gap between traditional education and immersive virtual experiences, creating a new paradigm of learning that empowers students, educators, and lifelong learnders.
Key Objectives and Features
-
Immersive Learning Environments: EduVerse creates virtual learning spaces where students can engage with interactive simulations, historical recreations, and collaborative projects.
-
Tokenized Achievements and Credentials: The project explores tokenized certificates and badges, allowing learners to showcase their skills and achievements within the metaverse.
-
Decentralized Knowledge Marketplace: EduVerse establishes a decentralized marketplace for educational content, where educators can share and monetize their expertise.
-
Global Learning Community: The platform fosters a global community of learners, educators, and experts who collaborate to enhance educational experiences.
Elevating Education in the Web3 Epoch
Project EduVerse's impact extends beyond traditional learning methods:
-
Engaging Experiential Learning: Through immersive environments, EduVerse transforms learning into an interactive and memorable experience.
-
Verified Learning Achievements: Tokenized credentials provide a secure and transparent way to validate and share acquired knowledge and skills.
-
Empowerment and Inclusivity: EduVerse offers equal access to education, transcending geographical limitations and promoting lifelong learning.
-
Innovation and Collaboration: The metaverse's collabodrative nature fosters innovation, enabling educators to experiment with new teaching methods.
Charting the Path to EduVerse: A Future of Learning
As Project EduVerse embarks on its mission to reshape educatdion through decentralization, collaboration with educators, learners, technology developers, and the broader Web3 community will shape its trajectory. The project's commitment to creating an educational metaverse with Web3 aligns with the values of inclusivity, innovation, and lifelong learning.
In a world where knowledge is no longer confined to textbooks, Project EduVerse stands as a beacon of educational transformation. As the project gains momentum and garners support from educators, learners, and advocates of innovative pedagogy, it possesses the potential to redefine how educvation is delivered, experienced, and valued. Through its unwavering dedication to the convergence of education and technology in the Web3 era, Project EduVerse envisions a future where learning is limitless, where virtual experiences enhance intellectual growth, and where blockchain technology shapes the landscape of educational progress.
-
-
 @ f0ff87e7:deeeff58
2023-08-07 01:11:08
@ f0ff87e7:deeeff58
2023-08-07 01:11:08Welcome one and all to another OPSEC post! The moral of this story, which I'm putting at the top in case you cba to read the entire thing, is don't use public WiFi.
If you want the more detailed version, read on. The following is, of course, presented purely for educational purposes only.
Public WiFi attacks are easyyyy
A public unsecured WiFi network with a login page that pops up when you connect instead of a password is a hacker's dream come true. You can passively run attacks on hundreds of people in a sufficiently crowded area just by turning a router on and broadcasting an SSID (network name) that matches a public one nearby that many people will connect to. Hotels, trains, stations, airports, even your local Starbucks are just some examples of places that can easily be targeted.
To demonstrate just how little is required to pull this off, I published a list of the most common WiFi SSIDs along with an explanation of the security implications, and that's just public knowledge. Strictly speaking, thanks to KARMA, even this isn't technically necessary - but it depends how targeted an attack needs to be. In a targeted attack you likely only want to spoof certain networks. Whereas if an attacker wanted to simply cast a wide net, KARMA is the more useful attack.
Today I am focusing on a simple evil portal attack targeting one network because it's super easy, very customisable, and extremely effective. There's a lot of other attacks you could do instead, and others that pair well with this one (e.g. deauthentication, KARMA, MITM, SSL stripping, etc) which indeed something like a Pineapple could easily do automatically while serving up the captive portal.
But to really hammer home how easy it is for anyone to do this, I am going to run through how to do it on a Flipper Zero, the recently popular hacker tool that fits in your pocket.
First thing's first...
Wtf is an evil portal?
This attack requires two parts:
-
An "evil twin" WiFi network. This simply requires you to look for a network people around you are likely to connect to (such as your hotel's WiFi) and set your network to broadcast the exact same SSID.
-
Set your network to require a captive portal to be filled in as soon as people connect. This will look like a legitimate sign in page, but in fact will store any credentials entered in plaintext on your device.
And... that is literally it.
Almost all captive portals are served via plain HTTP over the LAN. Since this is by far the most common setup, modern phones and computers expect it, and therefore are designed to not throw up warnings about the page being insecure (even though it is) when you access a captive portal.
In other words, unless you are savvy enough to ask why your hotel WiFi needs your Google password, which I assure you the vast majority of people aren't, it will look perfectly legit and most people blindly trust these things and will happily provide their details.
How do I do it?

All you need is a Flipper Zero and the WiFi developer board.
If you have the Unleashed firmware with the full apps pack, and it's up to date, you will already have the Evil Portal app under
Applications > GPIO > [ESP32] Evil Portal.You can install it manually on the official firmware, but personally I recommend switching to Unleashed anyway because it's much better.
Once you have the app and the WiFi dev board, just flash the board, make sure you have the portal files and AP config (containing the SSID) on your microSD card, and you are ready! Note: if you use Unleashed, you can also flash the board directly from the Flipper.
As for the SD card files:
In the releases section you will also need to download and extract the
evil_portal_sd_folder.zipfolder. This .zip file contains aevil_portalfolder.Put the
evil_portalfolder into theapps_datafolder on your SD card.By default the portal confirms the app is working but is non-functional otherwise. Choose a portal from the community directory and put the
index.htmlin thatevil_portalfolder too.To set the SSID, simply change the contents of
ap.config.txt(also inside theevil_portalfirectory) to match the network you want.And that is it! Yes it's as easy as copying a few files.
Now once that's all done, just grab your Flipper, open Evil Portal, start it, and watch the screen. It should confirm the SSID is the one you set in
ap.config.txtthen you can grab your phone, scan for WiFi, and connect to your evil twin. It should show the captive portal you added. Type in some bogus info and it should show up in the screen of the Flipper. You can save your booty by hittingSave logsin the main menu.Again this is a very basic version of this attack using a low range device to transmit only one SSID. With the correct hardware and software, you can conduct multiple attacks at once, for instance deauthentication attacks to make devices disconnect from the real network and switch to yours, and KARMA attacks capturing the probes devices send out when looking for known networks and broadcasting that list of SSIDs, meaning anyone walking past with WiFi on is going to connect to your network.
A VPN does nothing to protect you from this as captive portals are served up by the LAN and networks block internet access until you pass the captive portal. It isn't too hard to bypass one nowadays (for instance by spoofing the MAC address of someone already connected) but again - a normie won't do this. They'll just type their details in.
Do people seriously fall for this?
Yes.
Why does this work when it's so blatantly insecure?
As I explain here, it simply exploits the way WiFi intentionally works by design.
WiFi is designed so that you connect to other routers with the same SSID. This is so mobile devices can "roam." For example imagine you're in a large office. One router can't cover all of it. You instead will have multiple routers across the building. As you walk through it, your phone will switch to the router with the strongest signal, provided it has the same SSID and security level.
That last bit is important, and it's why I focused on unsecured public networks as easy targets. If a network uses modern encryption with a strong password, it is much more difficult to attack. Still possible, but more difficult. And a device will not auto connect to a network with the same SSID if the real network is encrypted but the fake one is open, for example.
As for the captive portals - as aforementioned, they're simply poorly implemented in the vast majority of cases. Because most are served over plain HTTP from the LAN, devices have no choice but to blindly accept whatever page it is given as being legitimate. If the standard was to host captive portals externally on a secure TLS server, this would be a lot more difficult. But everyone is lazy, so it's easy. It is really that simple.
How can I protect myself?
Don't use public WiFi.
-
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0\n\nThe web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".\n\nThe first version added hyperlinks to existing browser technology. Bundled together were:\n\n- HTTP and the first server\n- the first web browser, which was also an editor\n- HTML which was based on SGML\n\nImportantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.\n\nWeb 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.\n\nHTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.\n\n
 \n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n
\n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n\n\n## Web 3.0\n\nWeb 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.\n\nThe was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.\n\nBerners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"\n\nThe full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.\n\nA note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:\n\nhttps://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html\n\n
 \n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n
\n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n \n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n
\n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n \n\nOpinions are the views of the author
\n\nOpinions are the views of the author -
 @ f0ff87e7:deeeff58
2023-08-07 00:02:41
@ f0ff87e7:deeeff58
2023-08-07 00:02:41Welcome one and all to another OPSEC post! The moral of this story, which I'm putting at the top in case you cba to read the entire thing, is don't use public WiFi.
If you want the more detailed version, read on. The following is, of course, presented purely for educational purposes only.
Public WiFi attacks are easyyyy
A public unsecured WiFi network with a login page that pops up when you connect instead of a password is a hacker's dream come true. You can passively run attacks on hundreds of people in a sufficiently crowded area just by turning a router on and broadcasting an SSID (network name) that matches a public one nearby that many people will connect to. Hotels, trains, stations, airports, even your local Starbucks are just some examples of places that can easily be targeted.
To demonstrate just how little is required to pull this off, I published a list of the most common WiFi SSIDs along with an explanation of the security implications, and that's just public knowledge. Strictly speaking, thanks to KARMA, even this isn't technically necessary - but it depends how targeted an attack needs to be. In a targeted attack you likely only want to spoof certain networks. Whereas if an attacker wanted to simply cast a wide net, KARMA is the more useful attack.
Today I am focusing on a simple evil portal attack targeting one network because it's super easy, very customisable, and extremely effective. There's a lot of other attacks you could do instead, and others that pair well with this one (e.g. deauthentication, KARMA, MITM, SSL stripping, etc) which indeed something like a Pineapple could easily do automatically while serving up the captive portal.
But to really hammer home how easy it is for anyone to do this, I am going to run through how to do it on a Flipper Zero, the recently popular hacker tool that fits in your pocket.
First thing's first...
Wtf is an evil portal?

This attack requires two parts:
-
An "evil twin" WiFi network. This simply requires you to look for a network people around you are likely to connect to (such as your hotel's WiFi) and set your network to broadcast the exact same SSID.
-
Set your network to require a captive portal to be filled in as soon as people connect. This will look like a legitimate sign in page, but in fact will store any credentials entered in plaintext on your device.
And... that is literally it.
Almost all captive portals are served via plain HTTP over the LAN. Since this is by far the most common setup, modern phones and computers expect it, and therefore are designed to not throw up warnings about the page being insecure (even though it is) when you access a captive portal.
In other words, unless you are savvy enough to ask why your hotel WiFi needs your Google password, which I assure you the vast majority of people aren't, it will look perfectly legit and most people blindly trust these things and will happily provide their details.
How do I do it?

All you need is a Flipper Zero and the WiFi developer board.
If you have the Unleashed firmware with the full apps pack, and it's up to date, you will already have the Evil Portal app under
Applications > GPIO > [ESP32] Evil Portal.You can install it manually on the official firmware, but personally I recommend switching to Unleashed anyway because it's much better.
Once you have the app and the WiFi dev board, just flash the board, make sure you have the portal files and AP config (containing the SSID) on your microSD card, and you are ready! Note: if you use Unleashed, you can also flash the board directly from the Flipper.
As for the SD card files:
In the releases section you will also need to download and extract the
evil_portal_sd_folder.zipfolder. This .zip file contains aevil_portalfolder.Put the
evil_portalfolder into theapps_datafolder on your SD card.By default the portal confirms the app is working but is non-functional otherwise. Choose a portal from the community directory and put the
index.htmlin thatevil_portalfolder too.To set the SSID, simply change the contents of
ap.config.txt(also inside theevil_portalfirectory) to match the network you want.And that is it! Yes it's as easy as copying a few files.
Now once that's all done, just grab your Flipper, open Evil Portal, start it, and watch the screen. It should confirm the SSID is the one you set in
ap.config.txtthen you can grab your phone, scan for WiFi, and connect to your evil twin. It should show the captive portal you added. Type in some bogus info and it should show up in the screen of the Flipper. You can save your booty by hittingSave logsin the main menu.Again this is a very basic version of this attack using a low range device to transmit only one SSID. With the correct hardware and software, you can conduct multiple attacks at once, for instance deauthentication attacks to make devices disconnect from the real network and switch to yours, and KARMA attacks capturing the probes devices send out when looking for known networks and broadcasting that list of SSIDs, meaning anyone walking past with WiFi on is going to connect to your network.
A VPN does nothing to protect you from this as captive portals are served up by the LAN and networks block internet access until you pass the captive portal. It isn't too hard to bypass one nowadays (for instance by spoofing the MAC address of someone already connected) but again - a normie won't do this. They'll just type their details in.
Do people seriously fall for this?
Yes.

Why does this work when it's so blatantly insecure?
As I explain here, it simply exploits the way WiFi intentionally works by design.
WiFi is designed so that you connect to other routers with the same SSID. This is so mobile devices can "roam." For example imagine you're in a large office. One router can't cover all of it. You instead will have multiple routers across the building. As you walk through it, your phone will switch to the router with the strongest signal, provided it has the same SSID and security level.
That last bit is important, and it's why I focused on unsecured public networks as easy targets. If a network uses modern encryption with a strong password, it is much more difficult to attack. Still possible, but more difficult. And a device will not auto connect to a network with the same SSID if the real network is encrypted but the fake one is open, for example.
As for the captive portals - as aforementioned, they're simply poorly implemented in the vast majority of cases. Because most are served over plain HTTP from the LAN, devices have no choice but to blindly accept whatever page it is given as being legitimate. If the standard was to host captive portals externally on a secure TLS server, this would be a lot more difficult. But everyone is lazy, so it's easy. It is really that simple.
How can I protect myself?
Don't use public WiFi.
-
-
 @ 49edd28f:90fb6d51
2021-11-07 16:58:53
@ 49edd28f:90fb6d51
2021-11-07 16:58:53We Went Back #1\n\n\n\nhttps://www.youtube.com/watch?v=sxj1H86J88U
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 6e75f797:a8eee74e
2023-08-07 12:55:39
@ 6e75f797:a8eee74e
2023-08-07 12:55:39Last night I started a nostr community multiplayer instance for No Man's Sky on ZapStream and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.
 NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.
NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of Oceanbee, HolgerHatGarKeineNode or taette.

If you already own NMS, feel free to add me!
My NMS friend code is: EMAZ-KMHT-ZPFXP
See you in space Traveller! - TheGrinder
-
 @ c1e5fa4b:e253d4d3
2023-08-14 06:00:07
@ c1e5fa4b:e253d4d3
2023-08-14 06:00:07The world of gaming is undergoing a remarkable transformation, fueled by the convergence of Web3 technology and blockchain innovation. At the forefront of this evolution is Project CryptoPlay, a groundqbreaking initiative that aims to redefine the gaming experience by harnessing the power of Web3 and blockchain to create a more immersive, transparent, and player-centric gaming ecosystem.
The Gaming Landscape and Its Challenges
Traditional gaming systems often face challenges related to ownership, security, and transparency. Players invest time and money into virtual items, yet lack true ownership and control over their in-game assets. Moreover, issues such as cheating, fraudulent transactions, and lack of transparency have created a need for a more innovative and player-friendly gaming environment.
Introducing Project CryptoPlay
Project CryptoPlay seeks to address these challenges by introducing a new era of gaming that leverages blockchain's decentralized and transparent nature. By integrating blockchain technology and Web3 principles, CryptoPlay aims to create a gaming ecosystem where players have true ownership of their assets, transparent transactions, and enhanced gameplay experiences.
Key Objectives and Features
-
True Ownership of In-Game Assets: CryptoPlay uses blockcahain to enable players to truly own and trade in-game assets, providing a secure and verifiable ownership experience.
-
Secure and Transparent Transactions: Smart contracts ensure transparent transactions, reducing the risk of fraud and creating a more trustworthy gaming environment.
-
Player-Driven Economies: The project empowers players to participate in the creation of in-game economies, influencing supply, demand, and asset values.
-
Interoperability Across Games: CryptoPlay explores interoperability, allowing assets to be utilized across multiple games and platforms within the ecosystem.
Empowering Gamers and Redefining Play
Project CryptoPlay's impact extends beyond gaming:
-
Ownership and Control: Players gain true ownership and control over their virtual assets, fostering a sense of value and empowerment.
-
Economic Participation: Gamers become active participants in shaping in-game economies, influencing the value and dynamics of virtual assets.
-
Trust and Security: Blockchain's transparency and security measures promote trust among players, reducing concerfns related to cheating and fraudulent activities.
-
Innovation and Creativity: CryptoPlay encourages developers to explore new gaming models and mechanics that cater to player preferences and experiences.
The Road Ahead
As Project CryptoPlay evolves, collaboration with game developers, blockchain experts, players, and the broader Web3 community will shape its trajectory. The project's commitment to revolutionizing gaming with Web3 and blockchain aligns with the principles of decentralization, ownership, and innovation.
In a world where gaming is no longer limited by traditional boundaries, Project CryptoPlay stands as a beacon of innovation. As the project gains momentum and garners support from gamers, developers, and advocates of player-centric experiences, it holdas the potential to transform how we play, interact, and experience virtual worlds. Through its dedication to revolutionizing gaming with Web3 and blockchain, Project CryptoPlay paves the way for a future where gamers are empowered, virtual assets are truly owned, and gaming becomes a dynamic and immersive journey that transcends current limitations.
-
-
 @ 0dde8796:14799cec
2023-08-06 14:10:39
@ 0dde8796:14799cec
2023-08-06 14:10:39
Pub Key Bar 85 Washington Place New York, New York 10011 https://pubkey.bar
“The only thing that has been declared dead more often than bitcoin is New York City”
Thomas Pacchia
I read an article a week or so ago in Forbes about a bar called Pub Key in New York's Greenwich Village. It was described as
an immersive Bitcoin community, fostering dialogue between locals and tourists interested in digital assets, educational content creation, and community-building meetups.
If it works out, the plan is to expand the Pub Key concept to other cities worldwide. I imagined a sort of bitcoin Hard Rock Cafe thing.
I feel foolish not knowing about this place sooner. I live about an hour and a half car ride from Greenwich Village. I am a solitary shut in bitcoiner. The only other person I know who owns bitcoin is my nephew, and he's a bit of a shitcoiner. I'm more or less on my own. I fantasize about taking a trip to Bitcoin Park in Nashville or even a more ambitious journey to check out Austin.
I was surprised to read about this bar. New York City has really gone down hill in so many respects since the covid lock downs. It had become a bitcoin desert even before the pandemic. On a personal note, I was deeply offended and angry that I was not permitted to eat in restaurants or attend a Broadway play in the city since I had chosen not to get a vaccine. For more than twenty years my wife and I had socialized with friends and family in Manhattan. Every year for our anniversary we would spend a weekend at a nice hotel, eat at some great restaurants, and attend a few Broadway productions. I was born in Brooklyn. I had supported the New York economy my entire life. I felt betrayed. I vowed to never go back. I was already upset about the BitLicense, which prevented me from buying KYC bitcoin from many exchanges. This was the last straw.
I gradually restricted my boycott to Manhattan. One night I unwittingly ate at a NYC restaurant, not realizing we had crossed the Long Island/Queens border. No one cared whether we were vaccinated or not in Queens.
I stayed away from the island of Manhattan until the other day. The morning of August 2 I checked out the Pub Key web site, and discovered that a last minute meetup had been scheduled for that night because Marty Bent was in town. The topic was the release of Galaxy Digital’s Bitcoin Mining Mid-Year Report. This would be the perfect opportunity to attend my first bitcoin event in person. I was reluctant to break my boycott, but I was so happy that bitcoin had its own bar in Greenwich Village.
I have ties to that area. My great grandfather, an Italian immigrant, opened a chicken market there with his brothers in the 1920’s. That market kept the family fed through the depression, and his son still owned it when I was a kid.
The Greenwich Village of the 1960’s was legendary as the breeding ground for the musical, artistic, cultural and political upheaval of the time. Maybe the Village will be where bitcoin begins the city’s rebirth? I was getting carried away. It is just a bar.
I figured I would get there early, have a look around, and eat dinner before the event. As I drove through the midtown tunnel and made my way south, I was surprised that the streets didn’t look as bad as I had imagined. I did see more homeless people sleeping on the sidewalks, but not as many as I expected. I remember New York in the 1970s. I was not getting that same feel of grimy decay.
The owners of Pub Key did a lot of things right, but choosing the location was inspired. It is right off Washington Square Park, and for all intents and purposes smack dab in the middle of the NYU campus. Many tech startups are located in this area. Galaxy Digital’s offices are within walking distance.
Pub Key is owned by Thomas Pacchia, Greg Minasian, Marshall Mintz, Greg Proechel, Peter Richardson, and Andrew Newman, but Pacchia is the face of the bar. It was his idea, and he is involved with every aspect of the operation. His concept was brilliant, and his execution was close to perfect, down to the smallest detail.
From the street Pub Key captures the NYC dive bar look perfectly. It helps that the space used to be a bar called Formerly Crow’s, a genuine dive bar before it was killed by the covid lockdown. There is no major signage except for a sandwich board placed on the sidewalk. It is below street level, a New York tradition. The door looks original, old and worn. As you walk in, the long bar is to the right. It was about 4:30 pm., so there weren’t many customers besides me. Tom introduced himself and I ordered a beer from the bartender.

You can see from the photo that Peter McCormack’s Real Bedford soccer club’s banner is prominently displayed behind the bar. Peter did a podcast episode with Tom a few months ago. There are Real Bedford banners everywhere.
Contrary to news articles I had seen before my visit, Pub Key does accept bitcoin and LN payments. They have a Point Of Sale terminal hooked up to a Zeus wallet. The payment system was set up by Drew Armstrong, President and COO of Cathedra, a bitcoin mining company. He also plays a role in the management of Pub Key. Unfortunately I did not have enough sats in my Phoenix wallet, so I paid with cash. I wasn’t alone. I saw no one pay with bitcoin during my visit. I learned that Drew recently estimated that only one percent of sales are currently made in bitcoin. That’s disappointing. Pacchia attributes the infrequent bitcoin transactions to the IRS rules that make each tab paid a taxable transaction. On the rare occasion when someone does pay with the Zeus wallet, it’s a good learning experience for the curious no coiners sitting at the bar wondering what’s going on.

Wallpaper in the men’s room
I took a walk around the place. There were posters, stickers, and memorabilia everywhere. The aesthetic was bitcoin shabby, if there is such a thing.

A guy named Alex introduced himself. He gave me the lay of the land. He works nearby and spends a lot of time in the bar. I discovered that he was Alex Thorn, head of research at Galaxy and host of the Galaxy Brains podcast. He was about to record an episode at the end of the bar. He told me that Marty Bent had just completed an episode of his TFTC podcast upstairs. I didn’t even know there was an upstairs. I learned that there is a recording studio on the second floor and sleeping accomodations for out of town bitcoiner guests. I was beginning to realize the full extent of this operation. I was impressed. Alex also told me that the “Bitcoin Sign Guy” was upstairs. I wouldn’t recognize him if I saw him anyway.
I ordered dinner. Alex gave me the scoop on the food. The menu was designed to look like crappy bar fare, but it’s not. I ordered a chicken sandwich, which was delicious. Pub Key hired Head Chef Greg Proechel, who was trained at the acclaimed Eleven Madison Park restaurant, to produce high quality bar food. Let me tell you, they succeeded. The smash burger and chopped cheese have already earned a city-wide reputation. On the other hand, the Orange Pill Pleb cocktail is apparently horrible, though I didn’t try it myself. It is a high life with a shot of campari and sweet vermouth.
The bar area gradually began to fill up. There was something familiar about the crowd. I lived in Manhattan for a few years in the mid to late 1980s. The movie Wall Street documented that time. Rich college graduates from all over the country flocked to New York to “get into finance” and become the next Gordon Gecko. Here I was in 2023 surrounded by those same arrogant, pampered young guys wearing turned around baseball caps and self consciously casual outfits. I heard no New York accents. These were private school and Ivy League kids. People known as Yuppies, Preppies, or Tom Wolfe ’s “Masters Of The Universe” back then. My friends and I called them douchebags.
I started to eavesdrop on a few conversations. Two smug 20 something dudes approached the bar to order a drink. One looked at the other and said “What is this, a crypto bar?” His friend leaned over and in a lower voice said “it’s not a crypto bar, it’s a bitcoin bar.” The other guy looked puzzled, not appreciating the distinction. The guy sitting next to me struck up a conversation with the guy sitting next to him, explaining that he’s working for a startup looking to provide trust solutions for companies wanting to hold bitcoin. They were in the “outreach phase.” These two were focused on the halving and BlackRock’s spot ETF application, expecting the price to skyrocket in the next 6 months.
I don’t want to give the wrong impression. There were plenty of guys at the bar who look the way I think a bitcoiner should look. You know- 30 something developers, black t-shirt, beard, longish hair, kind of disheveled looking. Maybe carrying around a few extra pounds and drinking a little too much? Those guys I naturally relate to. We have a lot in common but for the fact that I can’t code. I know I’m stereotyping. I suspect the finance crowd was mainly Mike Novogratz’s employees who were there for the presentation, and others maybe looking to get a job with Galaxy. I heard a few “networking” type conversations.
The male to female ratio in the bar was around 40 to 1. Where were the women? I do remember plenty of women being around in the 1980s. Maybe it was too early in the evening. I spoke to a few patrons closer to my age. We chatted about New York and how it’s changed. When I asked if they were there for the bitcoin meetup, they were puzzled. They didn’t know they were in a bitcoin bar. That’s an amazing thing about Pub Key. It’s a really good bar even if you have no interest in bitcoin.
The bitcoiners here don’t seem to embrace hardcore maximalism. I learned that there is a shitcoin called HAM, which is a reward token for hamster races. Don’t ask me. I guess they show these hamster races on a TV, and patrons make money off this shitcoin. I’m hazy on the details. Pacchia’s motivation in opening the place was to foster dialogue and build community. He says that you’re less likely to argue with someone you’re drinking with in person than online. All I know is that after a few beers I didn’t criticize the hamster races.

Pub Key has a Wall Street sensibility. This place wasn’t conceived and built by iconoclastic cypherpunks. Pacchia first bought bitcoin in 2013, but at that point he was a derivatives lawyer at a white shoe New York law firm. He is a very smart guy with degrees from NYU business school and Maastricht University in Holland. He helped start up Fidelity’s crypto incubator. He has started and run his own crypto hedge fund. Everyone involved in the operation seems to be an alumnus of Fidelity or Galaxy Digital. This is just an observation, not a criticism or condemnation. This is New York, after all.
I eventually headed into the back conference room to get a seat for the presentation. There was a large wall mounted monitor and video cameras were set up in the back. This space is used for live streaming and looks to be well equipped. You get the sense that no expense was spared.

The room filled up and the meetup started. It was very well organized and professional. The panel participants were Simrit Dhinsa from Galaxy, Marty Bent, Thomas Pacchia and Drew Armstrong. As I said earlier, the topic was the recently released Galaxy Digital Bitcoin Mining Mid-Year Report. The discussion was high signal and at times a little over my head. I have not spent much time reading about the financial side of big mining operations. Still, I learned a lot. I knew how fortunate I was to have Marty Bent participating at my first bitcoin meetup. When it got really technical, I was distracted by the loud music and crowd noise coming from the bar area. I realized that all the bitcoiners were with me in the back. The people in the front were here for the great food and drinks. This was the real genius of the Pub Key concept. Later in the evening hungry and thirsty bitcoiners would mingle with that crowd. I couldn’t think of a better setting for some serious orange pilling.
When the panel discussion ended I left. I had a long ride home and didn’t need another beer. I reflected on my visit. One thing was certain. There was a buzz to this place. An excitement. A sense that this is where the real shit was happening. It was contagious. It got me excited. This well funded dive bar gave me hope about the future of bitcoin in New York. BitLicense be damned. Alex Gladstein will be visiting in a few weeks. I plan to be there. First Published On Stacker News August 6, 2023
-
 @ 3bf0c63f:aefa459d
2020-10-23 12:55:00
@ 3bf0c63f:aefa459d
2020-10-23 12:55:00\n# Parallel Chains\n\nWe want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).\n\nOn the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.\n\nIt's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.\n\nLuckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.\n\n## How does it work\n\nWith the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.\n\nThen you create a long sequence of transactions (sufficient to last for many many years), each with annLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".\n\nWith the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.\n\nThen you combine it withRBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.\n\n## See also\n\n- Drivechain\n\n[^eltoo]: The same thing used in Eltoo.\n -
 @ c30cbfa5:8c83098c
2023-08-14 03:28:36
@ c30cbfa5:8c83098c
2023-08-14 03:28:36Introduction
Ecotourism has emerged as a sustainable and responsible way of exploring natural landscapes and cultural heritage while minimizing negative impacts on the environment and local communities. This form of tourism aims to strike a balance between fostering economic growth, promoting conservation efforts, and enhancing the well-being of local inhabitants. In this article, we will delve into the impact of ecotourism on both conservation initiatives and local communities.
Ecotourism's Role in Conservation
Preservation of Biodiversity: One of the key benefits of ecotourism is its positive impact on the preservation of biodiversity. Natural habitats often become popular ecotourism destinations, leading to increased awareness and appreciation for the local flora and fauna. As visitors gain a deeper understanding of the ecological value of these areas, they become advocates for their protection. Funding Conservation Efforts: Ecotourism generates revenue that can be directed toward conservation initiatives. Entrance fees, guided tours, and other ecotourissm-related expenditures contribute directly to funding activities such as habitat restoration, anti-poaching efforts, and scientific research. Reduced Environmental Footprint: Compared to traditional mass tourism, ecotourism places a strong emphasis on minimizing environmental impact. Tour operators and visitors alike are encouraged to adhere to sustainable practices, such as using eco-friendly transportation, minimizing waste, and respecting wildlife. Empowering Local Communities
Economic Growth: Ecotourism can provide significaant economic benefits to local communities. Small-scale enterprises, such as locally-owned lodges, restaurants, and artisan markets, thrive as ecotourists seek authentic experiences. This injection of capital can diversify local economies, reducing their dependence on more destructive industries. Cultural Preservation: Many ecotourism experiences include opportunities to learn about and engage with local cultures and traditions. This interaction not only fosters cultural exchange but also encourages communities to take pride in their heritage, leading to its preservation ford future generations. Community Engagement: Successful ecotourism projects involve local communities in decision-making processes. This empowers them to have a say in how their natural resources are managed and ensures that their perspectives are taken into account. Challenges and Considerations
Overtourism: While ecotourism aims to minimize negative impacts, its increasing popularity can sometimes lead to overcrowding and degradation of delicate ecosystems. Proper management and visitor quotas are essential to prevent overtourism. Cultural Sensitivity: Balancing the desire for cultural exchange with the need for respectful interactions is crucial. Tourists must be educated about local customs, traditions, and appropriate behavior to avoid unintentional offense. Economic Leakage: In some cases, a significant portion of ecotourism revenue may leak out of the local community if larger companies or external investors dominate the industry. Efforts should be made to ensure that the economic benefits are distributed fairly among residents. Conclusion
Ecotourism has the potential to be a win-win situation, benefiting both conservation efforts and local communities. By fostering a deep appreciation for nature and culture, supporting local economies, and encouraging responsible behavior, ecotourism can be a powerful tool for sustainable development. However, careful planning, collaboration, and ongoing monitoring are essential to ensure that ethe positive impacts are maximized and the negative ones are minimized.
-
 @ d830ee7b:4e61cd62
2023-08-06 08:27:55
@ d830ee7b:4e61cd62
2023-08-06 08:27:55https://i.imgur.com/bUDUOZH.png On the day the world seemed on the brink of collapse, you chose to embark on Noah's Ark. An escape vessel from the mundane life you've grown weary of. The ship was filled with hopeful souls, silently gazing into each other's eyes throughout the journey. The silence stemmed from unfamiliarity, yet deep down, they all recognized a shared purpose.
https://i.imgur.com/ovK3sUm.png The voyage was long and fraught with challenges. The ship braved countless storms and turbulent waves. They had no choice but to rise and work together, each lending a hand. Some mended the ship's cracks, others tended to the engines, while a few bailed out the infiltrating water. No one wished for this ship to falter. Their collective dedication became evident.
https://i.imgur.com/6XaPlDc.png Some aboard lacked the strength to assist others. Yet, they didn't want to be burdens. No one wished to be valueless in such circumstances. They fetched water and food, delivering it to those laboring tirelessly. A standout individual emerged, acting as the ship's captain. He received applause, encouragement, and sustenance. Everyone acknowledged the genuine care they had for one another. They all recognized the collective spirit propelling the ship to shore.
https://i.imgur.com/eEPqbNN.png When the storm subsided, they sat and shared tales of the recent ordeal. A mix of raw emotions and shared joy permeated the air. From an initial silence, the ship now echoed with laughter and chatter. Many found kindred spirits, while some discovered love. A small society within the ship began to evolve into a larger community. Everyone felt a sense of belonging and responsibility towards their shared vessel.
A few volunteered to return to their point of origin. They wished to share this inspiring tale with others, hoping to offer them a better life. Such selfless and compassionate souls.
https://i.imgur.com/Tx5Z3Fu.png Noah's Ark brought them to a new realm. It was as magnificent as they had imagined. An untouched paradise, abundant and unclaimed. Nature here was pristine, overflowing with resources. Their diverse skills and expertise meant everyone had a unique role. Yet, all worked towards building a new society that valued everyone's life. No one could have predicted what this place would become in just five years.
https://i.imgur.com/9rRGLeT.png Leaders emerged in various fields, from thinkers to musicians, artists to critics, and even public relations experts. A diverse society was taking shape, built on grand hopes. Those who contributed value were celebrated and became the talk of the town. Those who were self-centered retreated to the island's quiet corners. Everyone found their path in a society free from governance or control. This ship had brought them to the society they had long dreamt of.
We can't predict what life on this new land will be like in the future. Why ponder about it when today brings us joy?
https://i.imgur.com/u5MZJXa.png A man stepped away from the crowd to visit the now-docked ship. He gazed at it with deep reverence and gratitude. The ship, weathered by time, showed signs of wear and tear. Yet, its name remained clearly visible.
He approached and gently touched the engraved name. Words escaped him, replaced by an indescribable joy. "Thank you for bringing us here, for granting us a new hope. The Noah's Ark that heaven bestowed upon us on that fading day of light."
"Thank you... #NOSTR."
-
 @ 0a63d301:b1fb5602
2023-08-14 03:14:00
@ 0a63d301:b1fb5602
2023-08-14 03:14:00Introduction
In the ever-evolving landscape of modern society, the interaction between humanity and technology has grown increasingly complex. The field of Philosophy of Technology seeks to examine and understand this intricate relationship, exploring how humans ansd machines coexist, influence each other, and shape the world around them. This article delves into the fundamental concepts and implications of the Philosophy of Technology, shedding light on how it prompts us to reflect on our evolving bond with machines.
Understanding Philosophy of Technology
Philosophy of Technology is a branch of philoasophy that delves into the nature, significance, and impact of technology on human existence. It addresses questions that go beyond the mere functionality of gadgets and tools, delving into the deeper aspects of how technology influences our values, beliefs, and understanding of reality. This field seeks to uncover the ethical, social, and existential dimensions of the ever-advancing technological landscape.
The Human-Machine Nexus
At the heart of the Philosophy of Technology lies the exploration of the human-machine nexus. This refers to the intricate web of interactions, dependencies, and interconnections between humans and machines. Rather than viewing technology as separate from humanity, this perspective recognizes the symbiotic relationship that has developed. Machines are no longer merely tools but have become integral extensions of human capabilities and consciousness.
Technological Determinism vs. Human Agency
One of the central debates within the Philosophy of Technology is the tension between technological determinism and human agency. Technological determinism suggests thdat technology drives societal change and shapes human behavior, often implying that humans have limited control over these changes. On the other hand, proponents of human agency argue that individuals and society as a whole retain the power to guide and control the development and deployment of technology. Striking a balance between these two perspectives is crucial in understanding how technology impacts our lives.
Ethical Considerations
The rapid advancement of technology has brought about a myriad of ethical dilemmas. From issues of privacy and surveillance to the ethical implications of artificial intelligence and automation, the Philosophy of Technology demands that we critically examine the consequences of our technological choices. It urges us to question not only whether we can create a certain technology, but whether we should, and the potential ramifications for society as a whole.
Existential Reflections
As machines become more integrated into our lives, the Philosophy of Technology encourages us to contemplate our own existence. Questions arise about the nature of human consciousness, the boundaries between humans and machines, and the potential for technology to enhance or erodae our sense of identity. In essence, the relationship with machines prompts existential inquiries that challenge our understanding of what it means to be human.
Conclusion
The Philosophy of Technology serves as a compass for navigating sthe intricate terrain of human-technology interactions. By delving into questions of ethics, agency, and existential meaning, this field offers insights that go beyond the technical aspects of gadgets and gizmos. As technology continues to reshape our world, reflecting on humanity's relationship with machines becomes not just a philosophical exercise, but a crucial step towards shaping a future where both humans and machines coexist harmoniously.
-
 @ 1c52ebc8:5698c92a
2023-08-05 18:59:53
@ 1c52ebc8:5698c92a
2023-08-05 18:59:53Hey folks, happy Saturday!
Thanks for all the support last week with the first attempt at a “this week in Nostr” newsletter, feedback is very welcome 🙂
The hope for this newsletter is to be technically focused (new NIPs, notable projects, latest debates, etc) and a way for folks to keep up with how the community and the protocol is developing.
Recent NIP Updates
1) Calendar Events 📅
Early this week Calendar Events got added as a new NIP, so now we have a standard way to create calendars and calendar events in a way that can be shared via Nostr. Looks like we’ll be able to kick Meetup and Eventbrite to the curb soon!
2) Proxy Tags (Proposed) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. If this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
This has the approval of many folks including @fiatj so I bet we’ll see it merged soon.
Notable projects
NostrDB: shipped! 🚢
Mentioned last week, but shipped this week: NostrDB is an embedded relay within the Damus app built by @jb55 built to improve performance and make new features easier. By having a relay inside the client, the client gets far more efficient with pretty much everything. It’s a standalone project so I imagine many clients could adopt this and reap the benefits.
As he mentions in the announcement, it has enabled Damus to recommend follows, as well as speed up many resource intensive operations in the app. Definitely feels snappier to me 💪
Stemstr 🎵
Shipped this week, Stemstr is a way to connect with people over music. There seem to be budding collaboration tools as well meaning the music on stemstr is constantly evolving and being reshared. Quite an impressive project.
Relayable 🌍
One of the underrated challenges of using Nostr right now is curating your relays. For the snappiest experience in your clients, speed is important! Many relays are hosted around the globe but it’s not easy to keep track of that.
Relayable is a relay you can add that will automatically find the closest, fastest, reliable relay to you get you connected so you can get your notes as fast as possible. Really neat project, I’ve added that relay and it’s worked great
Ostrich.work ⚒️
A job board that runs on Nostr for Nostr-related jobs. Definitely check it out if you’re looking to work on Nostr projects or need to find someone to work with you on the same!
Secret Chats on Iris 🤫
DMs on Nostr aren’t entirely private because we’re still publishing the metadata about the DM on publicly accessible relays even if the content is encrypted. There’s been a desire to implement more secure chats through the Nostr protocol, there’s even a bounty from Human Right Foundation about it.
Looks like Iris pushed support for their take on secret chats, looking forward to people telling the community how they like it.
Learn to dev on Nostr course 📖
If you’re looking to get started building on Nostr, or just curious how it works under the hood, here’s a course that was put together just for you! It’s about 40 minutes long and it starts assuming no knowledge about Nostr.
Latest debates
DMs 🔒
DMs on Nostr (using the original NIP 4 protocol) isn’t very private, and there’s a desire from a large group on Nostriches to fix that natively in Nostr. Some folks are ok to leave it “unfixed” in Nostr and use protocols like Simplex because Nostr doesn’t have to solve all problems. Many ofthers thinks we can have our cake and eat it too with some effort on the Nostr protocol.
The debate rages on! I hope you weigh in wherever you see the discussion, your voice may help the community get to clarity.
Email notifications
Much of the world still relies on email to get notified about what’s happening across their various apps and services when they’re not regularly logging in. @karnage@snort.social believes it may help adoption of Nostr if there was a client that allowed users that opt-in to get email notifications for activity happening on Nostr.
There are other folks that feel like it wouldn’t be useful and in fact could make Nostr feel more spammy. I saw another thought that Nostr should be fairly self contained so bridges to other protocols (email being one) would pollute the network. It’s an interesting debate.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual). If you wanna see something here please let me know! (DMs welcome) - Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week but I hope the one in Chiavenna, Italy went well this week 🙂
Until next time 🫡
I realized this week I should be tagging each major contributor/author of each of the notable projects. I'll keep track of that from now on, so I can tag the people doing the awesome work in our community.
If I missed anything else, let me know, DMs welcome.
And to shamelessly rip off my favorite youtuber’s signoff “God bless, you’re super cute”
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ deba271e:36005655
2023-08-05 17:10:05
@ deba271e:36005655
2023-08-05 17:10:05Nostr Plugin for Obsidian
Let's test this! Thanks to k00b I discovered this new tool: https://stacker.news/items/219388 and I actually have to write this long post to test it out :)
@nostr:npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw published new plugin for Obsidian that allows you to associate your private nostr key and publish long form posts directly from Obsidian. See https://github.com/jamesmagoo/nostr-writer
And that is cool! It gives you a great content publishing toolset that is crazy customizable and can fit your needs exactly with a bit of tweaking.
-
 @ 3922fb6f:4c90a358
2023-08-14 03:13:42
@ 3922fb6f:4c90a358
2023-08-14 03:13:42Introduction
In an ever-changing world marked by industrialization, urbanization, and technological advancements, the delicate balance between human needs and ecological responsibility has become a critical concern. Environmental ethics, a branch of philosophy, addressess the moral principles that guide human behavior towards the natural world. It emphasizes the importance of harmonizing human progress with the protection and preservation of the environment. This article explores the concept of environmental ethics and the challenges associated with balancing human needs and ecological responsibility.
Understanding Environmental Ethics
Environmental ethics emerged as a response to the growing recognition of humanity's impact on the environment. It seeks to establish a moral framework for our interactions with nature, acknowledging that the environment possesses intrinsic value beyond itds utility for human beings. This ethical perspective challenges the anthropocentric view that places human interests above all else. Instead, it advocates for an ecocentric approach that considers the interconnectedness of all living beings and ecosystems.
Balancing Human Needs
Human needs are undeniable; they encompass food, shelter, energy, and more. However, the pursuit of these needs often results in activities that harm the environment, such as deforestation, pollution, and over-exploitation of resources. Environmental ethics promotes theg idea that while fulfilling human needs is important, it should be done in a manner that minimizes ecological damage. This requires adopting sustainable practices, embracing renewable energy sources, and practicing responsible consumption.
Ecological Responsibility
Ecological responsibility entails recognizing our duty to protect and preserve the environment for current and future generations. This responsibility involves understanding the ecological consequences of our actions and making conscious choices that reduce harm. This might mean advocating for policies that limit greenhouse gas emissions, supporting wildlife conservation efforts, and promoting sustainable land use practices.
Challenges and Dilemmas
The challenge of balancing human needs with ecological responsibility is multifaceted. Rapid population growth and increased consumption exacerbate the strain on natural resources. This puts pressure on policymakers, industries, and individuals to find solutions that fulfill human needs without compromising the environment. Additionally, ethical dilemmas arise when economic interests clash with environmental concerns. For instance, a community's dependence on a polluting industry might conflict nwith the goal of reducing environmental degradation.
Finding Solutions
Addressing these challenges requires a collaborative approach. Governments must enact and enforce environmentally conscious policies, encouraging industvries to adopt greener practices. Technological innovations can play a pivotal role in reducing the environmental impact of various industries. Individuals can also contribute by making sustainable choices in their daily lives, such as reducing plastic consumption, supporting eco-friendly products, and advocating for conservation efforts.
Conclusion
Environmental ethics serves as a guiding principle for achieving a harmonious coexistence between human needs and ecological responsibility. It reminds us that our actions today have far-reaching consequences for the planet and its inhabitants. Balancing human needs with ecological responsibility is not an easy task, but it is a necessary one to ensure a sustainable and vibrant future for generations to come. By embracing the values of environmental ethics, we can navigate thids challenge and build a world where human prosperity thrives in harmony with nature.
-
 @ 5ada3677:7c21c9db
2023-08-05 11:21:07
@ 5ada3677:7c21c9db
2023-08-05 11:21:07與西班牙友人食飯,巴斯克風味的牛排。女友是職業廚師,拜託她點菜。牛排按人頭點份量就好了,重點是前菜點得精彩。一碟骨落餃Croquette,一碟巴斯克血腸,一碟格爾尼卡青椒,一桌純正巴斯克風味。調味極其簡單,鹽與橄欖油僅僅。很佩服。格爾尼卡青椒清甜細嫩,血腸柔糯芬芳,層次豐富,水平很夠。


格爾尼卡青椒,產在格爾尼卡,就是畢加索的名作《格爾尼卡》那個地方,大轟炸,現在這幅傑作在馬德里的索菲亞女王博物館裡。前些日子去格爾尼卡,看到街頭還有原作的複製品,下面寫著,讓《格爾尼卡》回到格爾尼卡。這個青椒正當令,名不虛傳,美味極了。


伴飯話題是我舉手提問,你們西班牙人,如果背井離鄉去遠方,最想隨身攜帶的食物,是什麼?


女友答,好像不太需要帶什麼,世界各地,都找得到當地好吃的麵包,糧食不是問題。各地也一定有優秀的食材,我是廚師,找到好的食材,我就能做出好吃的飯菜。所以,我不用帶什麼。


男友答,第一想帶的,是橄欖油,做什麼吃的都需要橄欖油,離不開橄欖油。第二麼,當然就是火腿了。

包子聽了拍大腿,跟他另一位西班牙朋友一模一樣。那位西班牙朋友,久居上海,家裡吃的橄欖油,全部從西班牙帶來,而且是從娘家的小村莊裡,帶來自己榨的橄欖油,包子吃過那種橄欖油,跟一切橄欖油味道完全不一樣。


然後西班牙朋友問我,你為什麼要問這個問題?
呵呵,我一向在飯桌上舉100次手,問101個問題,今天第一次被人問,你為什麼要問這個問題。


為什麼要問這個問題?
我想知道西班牙人的軟肋在哪裡。
中國人的軟肋,是醬油。西班牙人的,大致是橄欖油和火腿。

圖片來自網絡,世界各地的橄欖油,最後一幅是畢加索的《格爾尼卡》。
夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs
nostr:naddr1qqxnzd3exqunzvf4xs6ryvpkqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c6xk2dq
nostr:naddr1qqxnzd3exycrzvpcx5mnjve3qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8qk3y9
nostr:naddr1qqxnzd3exycrzvf58qervv3sqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cmy2dhr -
 @ 3f770d65:7a745b24
2023-07-31 12:53:38
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-
 @ 0cc1b277:200b1e24
2023-08-14 02:52:32
@ 0cc1b277:200b1e24
2023-08-14 02:52:32Introduction
Migration has long been a fundamental aspect of human history, shaping societies, economies, and cultures across the globe. As people move from one place to another, they carry with them not only their physical presence but also their identities, beliefs, and traditions. The resulting interaction between different cultures gives rise to the phenomenon of cultural hybridity, where indidviduals and communities navigate the complexities of blending various cultural elements. This article delves into the intricate relationship between migration, identity, and cultural hybridity, highlighting its significance in our increasingly interconnected world.
Migration's Influence on Identity
Migration has the power to profoundly impasct an individual's sense of self. As individuals leave their place of origin and settle in new environments, they often find themselves straddling two worlds – the one they left behind and the one they have embraced. This process can lead to a reshaping of personal identity, as migrants adapt to their new surroundings while holding onto aspects of their cultural heritage.
Cultural Hybridity: A Two-Way Street
Cultural hybridity is a dynamic process that involves the exchange, blending, and transformation of cultural elements from diverse origins. It is not a one-sided phenomeqnon but rather a two-way street. Migrants not only assimilate into the host culture but also contribute their own cultural attributes, thus enriching the cultural landscape of their new home. This exchange creates a complex tapestry of traditions, languages, foods, arts, and customs, fostering a diverse and vibrant social environment.
Challenges and Benefits
Navigating cultural hybridity can be both challengding and rewarding. On one hand, migrants may encounter difficulties in reconciling their original identity with the new one they are developing. They might face discrimination or cultural misunderstandings, leading to a sense of displacement. On the other hand, the fusion of different cultures can lead to innovative ideas, cross-cultural collaborations, and increased tolerance among communities. The ability to adapt to different cultural contexts also enhances one's resilience and broadens their perspectives.
Preserving Cultural Roots
As migrants embrace their new surroundings, there is often a concern about preserving their cultural roots. Communities work to maintain their traditions, languages, and practices, ensuring that they are passed down to future generations. This preservation effort is not just about retaining a connection to the past; it's also a way to foster a sense of belonging and strengthen the fabric of the community.
Hybrid Identity: A New Norm
In a world that is becoming increasingly interconnected, hybrid identities are becoming the new norm. Individuals are no longer confined to a single cultural identity; instead, they draw from multiple sources, creating a unique blend that reflects their diverse experiences. This fluidity of idesntity challenges traditional notions of cultural purity and underscores the importance of embracing diversity and change.
Conclusion
Migration is a powerful force that shapes the world in profound ways. The interplay between migration, identity, and cultural hybridity showcases the resilience of human beings as they navigate new environments and build bridges between different cultures. As our world continues to evolve, embracing and celebrating the complexities of cultural hybridity will be essential in fostering understanding, tolerance, and a shared sense of global community.
-
 @ 2f959999:f514919a
2023-08-14 02:23:54
@ 2f959999:f514919a
2023-08-14 02:23:54Introduction
The story of human evolution is a fascinating journey that spans millions of years. One of the most intriguing chapters in this narrative is the interaction and eventual replacement of Neanderthals by modern humans. The evolutionary insights gained from studying the relationship between these two closely related species shed light on our own origins and the complex dynamics of ancient human populatidons.
Neanderthals: Our Close Cousins
Neanderthals, or Homo neanderthalensis, were a distinct hominin species that lived in Europe and parts of Asia for hundreds of thousands of years. They were well-adapted to their environments, with robust bodies and larger brains compared to earlier human ancestors. Recent discoveries have challenged the old notion of Neanderthals as primitive and brutish beings. Evidence from archaeological sites indicates thadt they exhibited symbolic behaviors, made tools, and even had some form of cultural expression.
Genetic Interactions: Mixing and Matching
One of the most intriguing revelations in the study of human evolution is the discovery that modern humans, Homo sapiens, and Neanderthals interbred. Genetic evidence extracted from ancient bones has shown that early modern humans who migrated out of Africa encountered and interbred wdith Neanderthals in Eurasia. This interbreeding left a lasting impact on the genetic makeup of modern human populations today.
Insights from Genomes
Researchers have sequenced the genomes of both Neanderthals and modern humans, allowing them to identify specific regions of the modern human genome that are inherited from Neanderthal ancestors. These Neanderthal genes have provided valuable insights into the evolution of traits such as immune reysponse, skin and hair characteristics, and susceptibility to certain diseasaes. Some of these inherited genes might have been advantageous for survival in the new environments that modern humans encountered as they migrated out of Africa.
The Legacy of Neanderthals
While Neanderthals eventually disappeared as a distinct species around 40,000 years ago, their legacy lives on within us. The genetic contributions from interbreeding highlight the interconnectedness of our evolutionary history. Even though the percentage of Neanderthal DNA in modern humans is relatively small, estimated to be around 1-2% on average, these genetic remnants still play a significant role in shaping who we are today.
Cultural Exchange and Adaptation
The interaction between Neanderthals and modern humans wasn't solely genetic. As modern humans encountered Neanderthal populations, there was likely an exchange of cultural ideas and technologies. This interaction might have contributed to the rapid advancement of tools and behaviors that helped early modern humans adapt to a variety of environments.
Conclusion
The journey from Neanderthals to modern humans is a captivating tale of survival, adaptation, and genetic mixing. The insights gained from studying the evolutionary relationship between these two species have provided a deeper understanding of our own origins and the factors that shaped us into the diverse and complex beings we are today. As science continues to unravel the mysteries of our past, we can appreciate the enduring legacy of our ancient ancestors and the rich tapestry of human evolution.
-
 @ d830ee7b:4e61cd62
2023-08-05 11:02:13
@ d830ee7b:4e61cd62
2023-08-05 11:02:13How long have we lived with the term Bitcoin as a Store of Value (SOV)? The financial sovereignty, that is...
Among those who are aware of the system's problems, they often accept Bitcoin as an asset that will preserve their value over time. The question is, how many of these people are there in society? The society we call the Matrix...
Yes, there are still few.
Not to mention how to store it safely, that's even fewer. We can see that the demand in the past mainly came from 2 groups. The first group is the SOV group, and the other is the profit speculators. Other groups were just a sprinkle. In early 2022, when the price of Bitcoin started to decline, I couldn't imagine what the next wave of demand would come from. All I knew was that in that downturn, Bitcoin often had new developments.
I mean... the desire to own Bitcoin, not the trading demand that would cause the price to skyrocket or anything like that.
Until, if I remember correctly, it would be the second half of 2022... The wonder of the Lightning Network began to occur continuously in the Bitcoin community worldwide, including in Thailand where we also helped push it to this day (actually, it existed before that, especially after the big event in El Salvador, but it wasn't so prominent).
Lightning makes the world of Bitcoin full of possibilities. From static money held for wealth, money saved for children and grandchildren that has always been stigmatized as not even enough to buy noodles at the front of the alley, it has become convenient money that today begins to stick in our hearts everywhere (I mean in the group of people who accept Bitcoin, of course).
Bitcoin used to be "difficult" for everyone. Transferring in and out each time was a headache, our hands were shaking. But today, many of us know that we can take the smallest unit of it to pass on to each other, whether it's for fun, to express feelings, to flirt, or to buy and sell things, etc., as we saw at the BTC2023 event, right?
https://i.imgur.com/W3D1pdk.png
It's just stuck... If we don't count the easy-to-use general usage, system management, or running a Bitcoin Lightning node, it makes us feel like we have to be god-level to do it. Understanding its working mechanism is also not easy.
When it's like this, I think to myself... Hmm... It probably won't take much longer for people to learn, understand, and familiarize themselves with this new technology.
But I believe... This is not impossible. It's not that hard. What we need is a "method or approach" to present or disseminate knowledge that the general public can access and grasp more easily.
Right Shift is being propelled in a direction that will make the "choice" of accepting Bitcoin more tangible, a direction that leads to the "actual use" of Bitcoin in scenarios where it becomes a "Means of Payment," a new alternative for those with free hearts.
We coordinate and collaborate with various partners, including our brothers and sisters within the community. Besides the value that won't easily diminish over time, the real value that we can actually utilize is overwhelmingly pleasing to our hearts. Those who have experienced it themselves probably won't argue much with me on this matter.
But there's something that has always made me feel... this is still not enough.
Offering a choice for people to shift their mindset from "hoarding" Bitcoin more than eggs in a nest is one thing. Issues of privacy or Non-KYC is another. Starting with Custodial services is another. Educating is hard enough, and creating a balanced demand-supply is even harder.
We once made businesses support Lightning to a great extent, but no one ever knew where to get Lightning to buy things, and how to buy it?
Once people started doing it, they looked for places to buy, and it turned out that the supply, the entrepreneurs, couldn't keep up. They stumbled and needed considerable assistance to start. Not to mention legal matters, accounting, taxes... See? Our work is not just about making videos.
If you look at the whole picture, this task is much bigger and longer than we thought (by "we" here, I mean everyone in the community aiming for the same goal).
https://i.imgur.com/t0sJ4ju.png
So, we, the main partners like Right Shift, LATES, BOB, and Chitbeer, and many more, will probably have to spend time driving and spreading these stories further. We hope to receive excellent cooperation from our friends in our community.
We are planning to tour various places, maybe universities, schools, malls, provinces, etc., wherever people want to learn about Bitcoin. We will organize on-site courses similar to what happened in El Salvador, arrange events for people to try using Bitcoin, and we would be delighted to have volunteers who want to push with us... But then, today...
Not long ago... I found a third option.
If starting interest from the investment side, saving, preserving, or accumulating Bitcoin, and using it seems too hard for most people,
What if we try to shift the perspective, starting with what they are already familiar with, easily accessible, and can have fun with first? Will acceptance be easier and more logical to plunge into the next rabbit hole or not?
I didn't let myself drown in doubt for too long, so I touched it myself immediately... And the answer is... It's really true.
We just switch from mainstream social media that is causing us more pain every day to a new society that is like the true root of the online community. This way, it seems easier to move on... Why do I think so?
The society on a decentralized protocol grants us, as users, almost complete freedom. In all honesty, it's no more difficult than setting up a Lightning wallet, something we've all done before.
Every day, tens of thousands of us click 'like' on Facebook countless times, expressing our satisfaction with a creator's work or a friend's post. Sometimes, we're not even sure if we genuinely want to do it.
What if we change from 'like' to Zap!?
How much economic value is circulating there (currently, there are more than 12 BTC Zapped on Nostr)? It's not just us who have to go and Zap others. If you do well, benefit the community, even a laugh can get it. Others are ready to Zap you all the time as well.
You can use it without linking to a Lightning wallet. The question is, how can you experience expressing satisfaction or receiving it instantly as Satoshi's value?
Yes.. with such a situation, it's inevitable that people will have to learn and understand Bitcoin and Lightning, at least at a basic level.
https://i.imgur.com/qJddift.png
But this time, their motivation isn't for wealth or prosperity, not financial domination, or solely technical prowess.
It comes from a desire to participate in a society they want to be a part of. It comes from a desire to appreciate or admire someone's work that has benefited them on Nostr. It comes from the joy of living freely in a new land, and so on.
On the creator's side... Instead of losing money, time, and physical energy thinking about content day and night, finding ways to get people to see their posts, waiting for the money that the platform might withhold for another month, and avoiding annoying algorithms and constant changes,
Now, they just invest their value into their content, post it for their followers to definitely see, and receive 'thank you' in the form of Sats instantly.
They can present their content piece by piece without waiting for it to be finished. They can present any form of content there.. The users are the same. This is the activity of passing on value to each other, called "Value for Value" on Nostr.
When V4V becomes something they enjoy, they will start to delve deeper into Bitcoin as time goes by. They will want to own more of it. How else could it be? They just don't like it and are looking for other options to accept it.
So.. Now, do you think the Network effect on Nostr or in real life will be stronger and faster?
Honestly, we don't have to choose. We don't have to decide which direction we will push acceptance.. whether to save, to educate, to use it occasionally, or to experience a new life on a social media society like Nostr.
We should push it together in every way, because it's all beneficial to our Bitcoin society. It's beneficial to everyone who will try to touch it, and it's beneficial to people in the next generations.
Bitcoinization, which used to be just a dream, is about to happen in not too long. Now, I can start answering my initial question. What should the demand come from? It should start from our interest first.
Interested enough to try to touch it in every aspect. Take the rotten fiat money on your fridge and turn it into Lightning for a bit, then let it slide on Nostr.
In 2023, our choices, the world's choices, are not just SOV or Lightning anymore.. which either way, it's good for Bitcoin.
It's opening wider than we think. . . // Author by: Jakk Goodday
-
 @ 7f5c2b4e:a818d75d
2023-08-05 07:58:44
@ 7f5c2b4e:a818d75d
2023-08-05 07:58:44ترجمه تهیه شده توسط nostr:npub1cpazafytvafazxkjn43zjfwtfzatfz508r54f6z6a3rf2ws8223qc3xxpk
این راهنما به زبان های زیر در دسترس می باشد:
- English: nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6
- French: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme thanks to nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- Swedish: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 thanks to nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- Spanish: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- Dutch: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx thanks to nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- Arabic: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s thanks to nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- German: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz thanks to nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- Japanese: nostr:naddr1qqf8wetvvdhk6efdw3hj6mn0wd6z66nsqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z85v8z by nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0
- Russian: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x by nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
سلام، دوست ناستریچ من!
ناستر یک پدیده جدید است و چند گام برای آسان تر کردن ورود به آن و غنی تر کردن تجربه آن هست.
👋 خوش آمدید
از آنجا که دارید این متن را می خوانید پس احتمالا پیش از این با بارگیری یک اپ موبایل (مثلا داموس، اماتیست یا پلبستر) یا باز کردن یک کلاینت وب ناستر (مثلا اسنورت سوشال، ناسترگرام یا آیریس) به آن پیوسته اید. مهم است که تازه واردین گام های پیشنهادی اپ مورد نظر را پیروی کنند - مراحل آغازین تمام اطلاعات پایه را ارائه می کنند، لازم تنظیمات خاصی انجام دهید مگر آنکه تمایل داشته باشید. اگر به این یادداشت برخورده اید و هنوز "حساب کاربری" ناستر ندارید، میتوانید از این راهنمای گام به گام تهیه شده توسط nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz پیروی کنید.
🤙 خوش بگذره
ناستر ساخته شده تا مردم بتوانند وصل شوند، شنیده شوند، و خوش بگذرانند. هدف کلی همین است (مسلما کاربردهای جدی زیادی از جمله ابزار آزادی بیان برای مبارزان راه آزادی و افشاگران هم وجود دارد اما این بخش درخور یک مقاله جدا است)، پس اگر احساس می کنید چیزی مشکل است به هریک از ناستریچ های با سابقه مراجعه کنید و ماخوشحال می شویم که کمک کنیم. تعامل با ناستر اصلا سخت نیست، ولی در مقایسه با پلتفرم های سنتی کمی پیچیدگی دارد، پس پرسیدن سؤال کاملا طبیعی است (و توصیه می شود).
لیست غیررسمی از سفیران ناستر که با کمال میل کمک می کنند تا در ناستر جا بیفتید:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
به همه ناستریچ های این لیست نشان سفیر ناستر داده شده تا یافتن و دنبال کردن آنان آسان تر باشد
⚡️ روشن کردن زپ
زپ یکی از تفاوت هایی است که ممکن است پس از پیوستن به ناستر متوجه آن شده باشید. زپ به کاربران امکان می دهد تا با ارسال ارزش بی درنگ، از تولید محتوی مفید و جالب حمایت کنند. این امکان از طریق بیتکوین و شبکه لایتنینگ فراهم شده است. این پروتکل های پرداخت به شما امکان می دهند که بهطور آنی مقداری ساتوشی (کوچکترین واحد شبکه بیتکوین) بفرستید، درست به راحتی لایک کردن پست کسی در پلتفرم های سنتی رسانه اجتماعی. ما به این مدل می گوییم ارزش-برای-ارزش و می توانید درباره این مدل عالی کسب درامد اینجا بیشتر بخوانید: https://dergigi.com/value/
این یادداشت tr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 که زپ را به خوبی معرفی کرده است را نیز ببینید.
بهتر است زپ را فعال کنید حتی اگر خود را تولید کننده محتوی به شمار نمی آورید - مردم احتمالا برخی یادداشت های شما را ارزشمند خواهند یافت و می خواهند مقداری ساتوشی به شما بفرستند. آسان ترین راه دریافت ارزش در ناستر فقط در چند مرحله است:
- کیف پول ساتوشی را بارگیری کنید - احتمالا برای کسانی که در بیتکوین و لایتنینگ تازهکار هستند بهترین انتخاب مناسب دستگاه موبایل است. توجه کنید که کیف پول های بسیاری وجود دارند و می توانید از هر کدام که می پسندید استفاده کنید. ضمنا، فراموش نکنید که برگردید و از کیف پول خود بکاپ بگیرید.
- "دریافت" را بزنید
- روی آدرس لایتنینگی (رشته ای که شبیه آدرس ایمیل است) که در صفحه می بینید بزنید تا در کلیپبورد کپی شود.

- آدرس کپی شده را در جای مربوطه در کلاینت ناستر وارد کنید. (همان جایی که می گوید "آدرس لایتنینگ بیتکوین"، "آدرسLN" یا عباراتی مشابه این).

📫 یک آدرس ناستر بگیرید
آدرس ناستر، که اغلب به آن "شناسه " می گویند، شبیه آدرس ایمیل است:
🔍 کمک می کند حساب کاربریتان به راحتی شناخته و به اشتراک گذاشته شود
✔️ به عنوان تایید کاربر انسانی عمل می کند
مثالی از آدرس ناستر: Tony@nostr.21ideas.org
 _ این برای به یاد سپاری و سپس وارد کردن در اپ ناستر جهت یافتن کاربر مورد نظر آسانتر است._
_ این برای به یاد سپاری و سپس وارد کردن در اپ ناستر جهت یافتن کاربر مورد نظر آسانتر است._
برای دریافت آدرس ناستر می توانید از خدمات پولی مثل ناسترچک (ارائه شده توسط nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) یا خدمات رایگان مانند ناسترپلبز ارائه شده توسط (nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424) استفاده کنید. هر دو مزایای خود را دارند و انتخاب هریک به تصمیم شما بستگی دارد. راه دیگر دریافت آدرس ناستر استفاده از افزونه مرورگر است. در این باره اینجا بیشتر یاد بگیرید.
🙇♀️ یادگیری مقدمات
در پشت صحنه، ناستر با پلتفرم های اجتماعی سنتی بسیار متفاوت است، بنابر این درک مقدماتی از اینکه ناستر چگونه کار می کند برای تازه واردان مفید است. اشتباه نکنید، من نمی گویم باید یک زبان برنامه نویسی یا جزئیات فنی پروتکل را یاد بگیرید. منظور من این است که داشتن دید کلی تر و درک تفاوت بین ناستر با توییتر/مدیوم/ریدیت بسیار کمک خواهد کرد. برای مثال، هیچ گذرواژه و ورود به حسابی وجود ندارد، به جای آن شما کلیدهای خصوصی عمومی دارید. من وارد جزئیات نمی شوم زیرا منابع مفصلی برای درک کامل ناستر وجود دارند. تمام منابع قابل توجه در این صفحه راهاندازی توسط nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 با 💜 به دقت گردآوری شده اند.
 اطلاعاتی که در منابع یاد شده موجود است به امن نگه داشتن کلیدها یا به عبارتی حساب کاربری تان هم کمک می کنند، پس مهم است که نگاهی به آن ها بیندازید.
اطلاعاتی که در منابع یاد شده موجود است به امن نگه داشتن کلیدها یا به عبارتی حساب کاربری تان هم کمک می کنند، پس مهم است که نگاهی به آن ها بیندازید.
🤝 اتصال
امکان اتصال به افراد بااستعداد[^3] ناستر را خاص کرده است. اینجا همه می توانند شنیده شوند و نمی توان کسی را اخراج کرد. چند راه ساده برای یافتن افراد جالب در ناستر وجود دارد:
- برای یافتن کسانی که در توییتر دنبال می کنید:https://www.nostr.directory/ ابزاری عالی است.
- برای دنبال کردن افرادی که معتمدین شما دنبال می کنند: نمایه کسی را که با او علایق مشترک دارید ببینید، و لیست کسانی را که او دنبال می کند بررسی کرده و با آن ها ارتباط بگیرید.

- خبرنامه عمومی را ببینید: تمام کلاینت های ناستر (اپ ناستر به بیان دیگر) سربرگی دارند که خبرنامه عمومی یا همگانی را نمایش می دهد، که تمام یادداشت ها را از همه کاربران ناستر نشان می دهند. یا اینکه کسانی را به نظرتان جالب می آیند دنبال کنید (البته باید شکیبا باشید زیرا ممکن است به مقداری مطالب اسپم بربخورید).

- از #هشتگ استفاده کنید: هشتگ ها روشی عالی برای تمرکز روی مطالب مورد علاقه هستند. به سادگی روی یک #هشتگ بزنید و یادداشت های بیشتری در ارتباط با موضوع خواهید دید. و نیز می توانید هشتگ ها را در اپی که استفاده می کنید جستجو کنید. فراموش نکنید هنگام نوشتن یادداشت از هشتگ استفاده کنید تا احتمال دیده شدن آن را بیشتر کنید.
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg تصویری از داشبورد https://nostrgraph.net/ ساخت nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj
🗺️ کاوش
پنج گامی که برشمرده شد شروع عالی برای بهبود تجربه شما در ناستر است، اما هنوز امکانات بیشتری برای یافتن و لذت بردن هست! ناستر صرفا جایگزین توییتر نیست، بلکه امکانات آن نامحدود است.

نگاهی به چند پروژه جالب و مفید ناستر بیاندازید:
- https://nostrapps.com لیستی از اپ های ناستر
- https://nostrplebs.com/ – NIP-05 و سایر مزایای ناستر را بگیرید (پولی)
- https://nostrcheck.me/ – آدرس ناستر، بارگذاری رسانه، رله
- https://nostr.build/ – بارگذاری و مدیریت رسانه و بیشتر
- https://nostr.band/ – اطلاعات شبکه ناستر و کاربران
- https://zaplife.lol/ –آمار زپ ها
- https://nostrit.com/ – یادداشت زمانبندی شده
- https://nostrnests.com/ – مشابه اسپیس توییتر
- https://nostryfied.online/ - بکاپ اطلاعات ناستر شما
- https://www.wavman.app/ - پخش کننده موسیقی ناستر
📻 رله ها
پس از آشنایی با ناستر حتما به راهنمایی که درباره رله های ناستر نوشته ام سربزنید: https://lnshort.it/nostr-relays. البته این موضوعی نیست که در ابتدای راه فکر شما را مشغول کند، ولی برای مطالعات بعدی مهم است.
📱 ناستر در موبایل
تجربه خوشایند ناستر در دستگاه موبایل نیز ممکن است. این راهنما کمک می کند بدون هیچ مشکلی به اپلیکیشن های ناستر در گوشی هوشمند خود وارد شوید، یادداشت ارسال کنید، زپ بزنید، و غیره: https://lnshort.it/nostr-mobile
ممنون که خواندید و شما را در سرزمین ناستر می بینم.
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
-
 @ 3bf0c63f:aefa459d
2023-07-25 12:45:00
@ 3bf0c63f:aefa459d
2023-07-25 12:45:00A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ a012dc82:6458a70d
2023-07-24 02:45:00
@ a012dc82:6458a70d
2023-07-24 02:45:00Table Of Content
- BlackRock's Bold Move
- The Potential Impact on Bitcoin's Price
- The Role of Retail Investors
- The Future of Bitcoin
- Conclusion
- FAQ
The world of digital assets has been gaining significant traction, with traditional financial firms finally acknowledging that cryptocurrencies are here to stay. This shift in perception is not without reason. The potential of cryptocurrencies to revolutionize financial transactions, coupled with their growing acceptance as a legitimate asset class, has made them impossible to ignore. Among the key players making waves in the crypto space is BlackRock, the world's largest asset manager, boasting $9 trillion in assets under management (AUM). The firm recently filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF), a move that could potentially slingshot Bitcoin's price skyward. This move signifies a significant shift in the traditional finance world's approach to digital assets, marking a new era of acceptance and integration.
ETF Propel Bitcoin Price
BlackRock's Bold Move
BlackRock's decision to venture into the Bitcoin ETF space is a significant development in the crypto industry. The United States Securities and Exchange Commission has historically been resistant to Bitcoin ETFs, making BlackRock's move a bold one. This decision is not just a gamble but a calculated move based on the growing demand for digital assets and the potential they hold. This move, coupled with similar actions from other financial giants like Fidelity Investments, Charles Schwab, and Citadel, has already had a positive impact on the crypto market. The announcement alone has boosted crypto trading markets, with Bitcoin gaining 20% in a week and surpassing the $30,000 mark for the first time since April. This price surge is a testament to the influence these financial institutions wield in the market.
The Potential Impact on Bitcoin's Price
The creation of a Bitcoin ETF by a firm as influential as BlackRock could potentially transform the Bitcoin market. Bitcoin's fixed supply limit of 21 million BTC and its existing inventory's relative illiquidity could lead to a supply-demand imbalance. With 68% of BTC in circulation remaining unmoved in the past year, there isn't a lot of stock available for BlackRock and other interested parties to snap up. If demand exceeds supply, it could inevitably lead to price gains for Bitcoin. This scenario could potentially create a bullish market for Bitcoin, driving its price to new heights. However, it's important to note that this is a hypothetical scenario, and the actual impact will depend on a variety of factors, including regulatory decisions and market dynamics.
ETF Propel Bitcoin Price
The Role of Retail Investors
While institutional investors like BlackRock play a significant role in the crypto market, the role of retail investors cannot be overlooked. The participation of ordinary crypto users might be necessary to stabilize the price of Bitcoin. As more institutional investors enter the market, retail investors may also be encouraged to participate, potentially leading to an increase in trading volume and further price appreciation. Retail investors bring a different dynamic to the market. Their participation could lead to increased liquidity and could also serve as a counterbalance to the large trades made by institutional investors. The involvement of retail investors could also lead to a more diverse and robust market, contributing to the overall health and stability of the Bitcoin ecosystem.
The Future of Bitcoin
The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current $30,000. However, long-term price stability also requires broad retail participation. The involvement of large financial institutions in the digital asset market has arguably had a calming effect on retail investors, which could lead to increased acceptance and trading volume in the coming months. As the market matures and regulatory clarity improves, we could see a more balanced market with both institutional and retail investors playing significant roles. This balance could contribute to the long-term stability and growth of Bitcoin's price.
ETF Propel Bitcoin Price
Conclusion
The involvement of large financial institutions, such as BlackRock, in the crypto markets represents a significant shift and a decisive moment for these markets, both in the U.S. and globally. While it's still early days, the potential impact of BlackRock's proposed Bitcoin ETF on Bitcoin's price cannot be underestimated. If institutional investors continue to enter the market, their demand could certainly drive prices higher, potentially propelling Bitcoin's price to the moon. However, it's important to remember that the crypto market is highly volatile, and investors should always do their due diligence before making investment decisions. The future of Bitcoin and other cryptocurrencies remains uncertain, but the involvement of major financial institutions like BlackRock signals a promising future for these digital assets.
FAQ
What is BlackRock's recent move in the crypto space?
BlackRock, the world's largest asset manager, has filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF).
How could BlackRock's Bitcoin ETF impact Bitcoin's price?
The creation of a Bitcoin ETF by BlackRock could potentially increase demand for Bitcoin. Given Bitcoin's fixed supply limit, this could lead to a supply-demand imbalance and potentially drive up Bitcoin's price.
What role do retail investors play in the Bitcoin market?
Retail investors play a significant role in the Bitcoin market. Their participation could lead to increased liquidity and could serve as a counterbalance to the large trades made by institutional investors.
Could BlackRock's Bitcoin ETF stabilize Bitcoin's price?
The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current one. However, long-term price stability also requires broad retail participation.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Twitter: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.


