-
 @ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15
@ 9ecbb0e7:06ab7c09
2023-08-08 02:53:15Según nos reporta y documenta la familia, la niña pequeña de 3 años de edad Leadi Kataleya Naranjo, hija del preso de conciencia Idael Naranjo Pérez, ha sido citada para mañana por la Seguridad del Estado de #Cuba.
 La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
La citación no ofrece duda e indica los dos nombres, apellido y la dirección de la abuela paterna, donde entregaron la citación, y la abuela también ha sido citada y amenazada de desobediencia.
 Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!
Si la niña no se presenta, amenazan de acusarla igualmente de "desobediencia".
La abuela se preocupó, les dijo la edad, y aún así entregaron la citación y se fueron. Que "debían presentarse". Nada más.
Desalmados son, pero...
¿Qué clase de locos de atar están al mando en #Cuba?
¿Qué pretenden citando y amenazando a una niña de 3 años?
Esa niña no puede ir a esa ignominiosa citación. ¿A oír qué? ¿A responder qué? El tema da ASCO.
La familia no quiere llevar a la niña, y necesitan todo el apoyo para que esta locura se aclare y se detenga.
Desgraciadamente hemos visto cosas iguales o peores. Niños amenazados, separados por la fuerza de sus padres, menores torturados... El régimen de Cuba da mucho asco, por todos lados rezuma repugnancia y degradación. Todo lo que sucede en Cuba clama al cielo, y estas barbaries son distópicas.
¡MANTENGAN AL MARGEN A LOS NIÑOS, DESALMADOS ENFERMOS!
Bastante daño causan con la Ley de los 8 años que tiene a miles de niños huérfanos, separados forzosamente de sus madres para castigarlas a ellas por no doblegarse a trabajar en las misiones médicas esclavas de Cuba en el exterior, como sentenció el Comité de los Derechos del Niño.
¡BASTA YA!11jul #11j #11jCuba #CubaEsUnaDictadura #UNICEF @uniceflac @unicefenespanol
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53
@ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53Questa guida è disponibile anche in:\n\n Francese: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c grazie a nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme grazie a nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n Svedese: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 grazie a nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7\n Spagnolo: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q grazie a nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624\n Olandese: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx grazie a nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6\n Arabo: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s grazie a nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j \n Tedesco: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz grazie a nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg\n Giapponese: nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6 di nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0\n Russo: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x di nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n\n---\n\nCiao, caro Nostrich! \n\nNostr è qualcosa di completamente nuovo, e ci sono alcuni passi da fare che semplificheranno il tuo ingresso e renderanno più interessante la tua esperienza.\n\n## 👋 Benvenuto\n\nDato che stai leggendo questa guida, diamo per assunto che tu ti sia già unito a Nostr scaricando un app (es. Damus, Amethyst, Plebstr) o usando un Web Client Nostr (es. snort.social, Nostrgram, Iris). E' importante per un nuovo arrivato seguire i passaggi suggeriti dalla piattaforma di tua scelta - la procedura di benvenuto ti fornisce tutte le basi, e non dovrai preoccuparti di configurare nulla a meno che tu non lo voglia fare. Se sei incappato in questo articolo, ma non hai ancora un “account” Nostr, puoi seguire questa semplice guida a cura di nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.\n\n---\n\n## 🤙 Divertiti\n\nNostr è fatto per assicurarsi che le persone siano in grado di connettersi liberamente, di essere ascoltate e di divertirsi. Questo è il fulcro centrale (ovviamente ci sono moltissimi altri casi d'uso, come essere uno strumento per i divulgatori e chi lotta per la libertà, ma per questo servirà un articolo a parte), quindi se qualcosa ti è poco chiaro contatta altri “nostriches” con esperienza e saremo lieti di aiutarti. Interagire con Nostr non è difficile, ma ci sono alcune differenze rispetto alle altre piattaforme tradizionali, quindi è normale fare domande (anzi...sei incoraggiato a farne).\n\nQuesta è una lista ufficiosa di utenti Nostr che saranno felici di aiutarti e rispondere alle tue domande:\n\nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu\n\n_Tutti i nostriches nella lista hanno ricevuto il badge Nostr Ambassador, il che renderà facile per te trovarli, verificarli e seguirli_\n\n---\n\n## ⚡️ Attivare gli Zaps\n\nGli Zaps sono una delle prime differenze che noterai entrando su Nostr. Consentono agli utenti Nostr di inviare istantaneamente valore per supportare la creazione di contenuti utili e divertenti. Sono possibili grazie a Bitcoin e Lightning Network. Questi due protocolli di pagamento decentralizzati permettono di inviare istantaneamente dei sats (la più piccola frazione di Bitcoin) tanto facilmente quanto mettere un like sulle piattaforme social tradizionali. Chiamiamo questo meccanismo Value-4-Value e puoi trovare altre informazioni al riguardo qui: https://dergigi.com/value/ \n\nDai un'occhiata a questa nota di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 per avere una panoramica su cosa sono siano gli zaps.\n\nDovresti attivare gli Zaps anche se non sei un creatore di contenuti - le persone troveranno sicuramente interessanti alcune delle tue note e vorranno mandarti dei sats. Il modo più semplice per ricevere sats su Nostr è il seguente:\n\n1. Scarica l'app Wallet of Satoshi - probabilmente la scelta migliore per dispositivi mobili per chi è nuovo in Bitcoin e Lightning. Tieni di conto che esistono molti altri wallets e che potrai scegliere quello che preferisci. Inoltre, non dimenticarti di fare un back up del wallet. \n2. Premi “Ricevere”\n3. Premi sopra al tuo Lightning Address (è quello che sembra un indirizzo email) per copiarlo\n
 \n4. Incollalo poi nel campo corrispondente all'interno del tuo client Nostr (il nome del campo potrebbe essere “Bitcoin Lightning Address”, “LN Address” o qualcosa di simile in base all'app che utilizzi). \n
\n4. Incollalo poi nel campo corrispondente all'interno del tuo client Nostr (il nome del campo potrebbe essere “Bitcoin Lightning Address”, “LN Address” o qualcosa di simile in base all'app che utilizzi). \n \n\n---\n\n## 📫 Ottieni un indirizzo Nostr\n\nGli indirizzi Nostr, a cui spesso i Nostr OGs si riferiscono con “NIP-05 identifier”, sono simili ad un indirizzo email e:\n\n🔍 Aiutano a rendere il tuo account facile da trovare e condividere \n✔️ Servono a verificare che il tuo “LN Address” appartenga ad un umano\n\n---\n\nQuesto è un esempio di indirizzo Nostr: Tony@nostr.21ideas.org\n
\n\n---\n\n## 📫 Ottieni un indirizzo Nostr\n\nGli indirizzi Nostr, a cui spesso i Nostr OGs si riferiscono con “NIP-05 identifier”, sono simili ad un indirizzo email e:\n\n🔍 Aiutano a rendere il tuo account facile da trovare e condividere \n✔️ Servono a verificare che il tuo “LN Address” appartenga ad un umano\n\n---\n\nQuesto è un esempio di indirizzo Nostr: Tony@nostr.21ideas.org\n \n E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente\n\n---\n\nPer ottenere un indirizzo Nostr puoi usare un servizio gratuito come Nostr Check (di nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) oppure uno a pagamento come Nostr Plebs (di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Entrambi offrono vari vantaggi, e la scelta dipende solo da te. Un altro modo per ottenere un indirizzo Nostr è tramite un'estensione del browser. Scopri di più al riguardo qui) . \n\n---\n\n## 🙇♀️ Impara le basi\n\nDietro le quinte Nostr è molto diverso dalle piattaforme social tradizionali, quindi conoscerne le basi è estremamente utile per i nuovi arrivati. E con questo non intendo che dovresti imparare un linguaggio di programmazione o i dettagli tecnici del protocollo. Sto dicendo che avere una visione d'insieme più ampia e capire le differenze fra Nostr e Twitter / Medium / Reddit ti aiuterà moltissimo. Ad esempio, al posto di un nome utente e password hai una chiave privata e una pubblica. Non entrerò nel dettaglio perchè esistono già moltissime risorse che ti aiuteranno a diventare un esperto di Nostr. Tutte quelle degne di nota sono state raccolte in questa pagina con 💜 da nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6\n\n
\n E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente\n\n---\n\nPer ottenere un indirizzo Nostr puoi usare un servizio gratuito come Nostr Check (di nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) oppure uno a pagamento come Nostr Plebs (di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Entrambi offrono vari vantaggi, e la scelta dipende solo da te. Un altro modo per ottenere un indirizzo Nostr è tramite un'estensione del browser. Scopri di più al riguardo qui) . \n\n---\n\n## 🙇♀️ Impara le basi\n\nDietro le quinte Nostr è molto diverso dalle piattaforme social tradizionali, quindi conoscerne le basi è estremamente utile per i nuovi arrivati. E con questo non intendo che dovresti imparare un linguaggio di programmazione o i dettagli tecnici del protocollo. Sto dicendo che avere una visione d'insieme più ampia e capire le differenze fra Nostr e Twitter / Medium / Reddit ti aiuterà moltissimo. Ad esempio, al posto di un nome utente e password hai una chiave privata e una pubblica. Non entrerò nel dettaglio perchè esistono già moltissime risorse che ti aiuteranno a diventare un esperto di Nostr. Tutte quelle degne di nota sono state raccolte in questa pagina con 💜 da nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6\n\n \n_Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata_\n\n---\n\n## 🤝 Connettiti\n\nLa possibilità di connetterti con altre [^3] persone brillanti è ciò che rende speciale Nostr. Qui tutti possono essere ascoltati e nessuno può essere escluso. Ci sono alcuni semplici modi per trovare persone interessanti su Nostr:\n\n Trova le persone che segui su Twitter: https://www.nostr.directory/ è un ottimo strumento per questo.\n Segui le persone seguite da altri di cui ti fidi: Visita il profilo di una persona che condivide i tuoi stessi interessi, guarda la lista delle persone che segue e connettiti con loro.\n\n
\n_Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata_\n\n---\n\n## 🤝 Connettiti\n\nLa possibilità di connetterti con altre [^3] persone brillanti è ciò che rende speciale Nostr. Qui tutti possono essere ascoltati e nessuno può essere escluso. Ci sono alcuni semplici modi per trovare persone interessanti su Nostr:\n\n Trova le persone che segui su Twitter: https://www.nostr.directory/ è un ottimo strumento per questo.\n Segui le persone seguite da altri di cui ti fidi: Visita il profilo di una persona che condivide i tuoi stessi interessi, guarda la lista delle persone che segue e connettiti con loro.\n\n \n\n Visita la Bacheca Globale: Ogni client Nostr (app Nostr se preferisci) ha una scheda per spostarsi nella Bacheca Globale (Global Feed), dove troverai tutte le note di tutti gli utenti di Nostr. Segui le persone che trovi interessanti (ricorda di essere paziente - potresti trovare una discreta quantità di spam).\n\n
\n\n Visita la Bacheca Globale: Ogni client Nostr (app Nostr se preferisci) ha una scheda per spostarsi nella Bacheca Globale (Global Feed), dove troverai tutte le note di tutti gli utenti di Nostr. Segui le persone che trovi interessanti (ricorda di essere paziente - potresti trovare una discreta quantità di spam).\n\n \n\n Usa gli #hashtags: Gli Hashtag sono un ottimo modo per concentrarti sugli argomenti di tuo interesse. Ti basterà premere sopra l'#hashtag per vedere altre note relative all'argomento. Puoi anche cercare gli hashtags tramite l'app che utilizzi. Non dimenticare di usare gli hashtags quando pubblichi una nota, per aumentarne la visibilità.\n\nhttps://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg \nScreenshot della bacheca di nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj su https://nostrgraph.net/ \n\n---\n\n## 🗺️ Esplora\n\nI 5 consigli menzionati sono un ottimo punto d'inizio e miglioreranno moltissimo la tua esperienza, ma c'è molto di più da scoprire! Nostr non è solo un rimpiazzo per Twitter e le sue possibilità sono limitate solo dalla nostra immaginazione. \n\n
\n\n Usa gli #hashtags: Gli Hashtag sono un ottimo modo per concentrarti sugli argomenti di tuo interesse. Ti basterà premere sopra l'#hashtag per vedere altre note relative all'argomento. Puoi anche cercare gli hashtags tramite l'app che utilizzi. Non dimenticare di usare gli hashtags quando pubblichi una nota, per aumentarne la visibilità.\n\nhttps://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg \nScreenshot della bacheca di nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj su https://nostrgraph.net/ \n\n---\n\n## 🗺️ Esplora\n\nI 5 consigli menzionati sono un ottimo punto d'inizio e miglioreranno moltissimo la tua esperienza, ma c'è molto di più da scoprire! Nostr non è solo un rimpiazzo per Twitter e le sue possibilità sono limitate solo dalla nostra immaginazione. \n\n \n\nDai un'occhiata alla lista di tutti i progetti Nostr:\n\n https://nostrapps.com/ una lista di tutte le apps su Nostr\n https://nostrplebs.com/ – ottieni il tuo NIP-05 e altri vantaggi (a pagamento)\n https://nostrcheck.me/ – Indirizzi Nostr, caricamento di media, relay\n https://nostr.build/ – Carica e gestisci i tuoi media (e altro)\n https://nostr.band/ – Informazioni sul network e gli utenti di Nostr\n https://zaplife.lol/ – Statistiche degli Zaps\n https://nostrit.com/ – Programma le note\n https://nostrnests.com/ – Twitter Spaces 2.0 \n https://nostryfied.online/ - Fai un backup dei tuoi dati di Nostr\n https://www.wavman.app/ - Player musicale per Nostr\n\n---\n\n## 📻 Relays\n\nDopo aver preso confidenza con Nostr assicurati di dare un'occhiata alla mia guida riguardo i Relays su Nostr: https://lnshort.it/nostr-relays. Non è un argomento di cui preoccuparsi all'inizio del tuo viaggio, ma è sicuramente importante approfondirlo più avanti.\n\n\n\n## 📱 Nostr su mobile\n\nAvere un'esperienza fluida su Nostr tramite un dispositivo mobile è fattibile. Questa guida ti aiuterà ad accedere, postare, inviare zap e molto di più all'interno delle applicazioni web Nostr sul tuo smartphone: https://lnshort.it/nostr-mobile\n\n\n\nGrazie per aver letto e ci vediamo dall'altra parte della tana del coniglio.\n\nGrazie a nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 per aver fornito il documento originale che ho tradotto\n\n** \n
\n\nDai un'occhiata alla lista di tutti i progetti Nostr:\n\n https://nostrapps.com/ una lista di tutte le apps su Nostr\n https://nostrplebs.com/ – ottieni il tuo NIP-05 e altri vantaggi (a pagamento)\n https://nostrcheck.me/ – Indirizzi Nostr, caricamento di media, relay\n https://nostr.build/ – Carica e gestisci i tuoi media (e altro)\n https://nostr.band/ – Informazioni sul network e gli utenti di Nostr\n https://zaplife.lol/ – Statistiche degli Zaps\n https://nostrit.com/ – Programma le note\n https://nostrnests.com/ – Twitter Spaces 2.0 \n https://nostryfied.online/ - Fai un backup dei tuoi dati di Nostr\n https://www.wavman.app/ - Player musicale per Nostr\n\n---\n\n## 📻 Relays\n\nDopo aver preso confidenza con Nostr assicurati di dare un'occhiata alla mia guida riguardo i Relays su Nostr: https://lnshort.it/nostr-relays. Non è un argomento di cui preoccuparsi all'inizio del tuo viaggio, ma è sicuramente importante approfondirlo più avanti.\n\n\n\n## 📱 Nostr su mobile\n\nAvere un'esperienza fluida su Nostr tramite un dispositivo mobile è fattibile. Questa guida ti aiuterà ad accedere, postare, inviare zap e molto di più all'interno delle applicazioni web Nostr sul tuo smartphone: https://lnshort.it/nostr-mobile\n\n\n\nGrazie per aver letto e ci vediamo dall'altra parte della tana del coniglio.\n\nGrazie a nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 per aver fornito il documento originale che ho tradotto\n\n** \n -
 @ 69f16d34:4568b5f8
2023-08-13 01:28:26
@ 69f16d34:4568b5f8
2023-08-13 01:28:26Constant type
int const n = 4; n = 3; /* Error */Constant array
/* Constant array of integers */ int const array[] = {3, 4}; array[0] = 5; /* Error */Pointer to a constant type
/* Pointer to a constant character */ char const *str = "hello"; str++; /* Fine */ *str = 'p'; /* Error */Constant pointer
char s_array[] = "porld"; /* Constant pointer to a character */ char * const p = s_array; *p = 'w'; /* Fine */ p++; /* Error */Constant pointer to a constant type
/* Constant pointer to a constant character */ char const * const str = "hello"; str++; /* Error */ *str = 'p'; /* Error */ -
 @ c8df6ae8:22293a06
2023-08-13 00:57:19
@ c8df6ae8:22293a06
2023-08-13 00:57:19"Regulated stablecoins do not compete with bitcoin."
— Matt Odell
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers PayPal’s launch of a stablecoin pegged to the US dollar.
This week PayPal launched the PayPal stablecoin PYUSD pegged to the US dollar. It joins Tether USDT, Circle USDC, and Binance BUSD in the quest to extract wealth from unsuspected crypto enthusiasts.
All stablecoins are the same. They all run on top of Ethereum and therefore offer the same programmatic capabilities.
The only way that these companies differentiate themselves is by promising to be more trustworthy than the other ones. Because, and here is the crux of the matter:
PayPal, Tether, Circle and Binance are borrowing your money and you are implicitly deciding who is most likely to pay you back.
By the way, all these promises of programmatic benefits are hollow promises that depend on someone else building an app that uses their stablecoin and these programmatic capabilities to deliver something that is yet to be determined but that somehow will be of great value to you.
You can read about PYUSD here.
Stablecoins steal wealth from you
Why is PayPal doing this? The answer is here:
 When you buy one PYUSD, you’re giving $1 to PayPal and receiving in exchange a token that returns no interest to you and costs them nothing to issue.
When you buy one PYUSD, you’re giving $1 to PayPal and receiving in exchange a token that returns no interest to you and costs them nothing to issue.Congratulations! You’re lending money to PayPal at zero interest rate!
PayPal then turns around and buys $1 worth of US Treasury with a 5% interest rate.
You can buy US Treasuries yourself and pocket the 5% interest rate. But instead you give them the money, they pocket the 5% and you assume the risk of PayPal defaulting on its reserves.
They make the money and you take the counterparty risk. Now you know why PayPal just launched PYUSD.
Bitcoin trumps stablecoins
People are lured to stablecoins because they want to protect their savings from the theft that inflation represents. They are very popular in Argentina or Turkey, where access to real US dollars may be limited and stablecoins provide an easy way to convert the useless peso or lira into what is perceived as a more trusted currency.
But you’re being fooled because your wealth is also stolen from you when you store it in US dollars thanks to inflation and you’re assuming the counterparty risk of PayPal, Binance, Tether or Circle not being able to maintain the parity of 1 PYUSD = 1 USD.
There is only one crypto currency that is free from inflation theft and free from all counterparty risks: Bitcoin.
Once you’re ready to move your savings into sound money, choose Bitcoin. It’s the only sound money where you have full control. All other cryptocurrencies are scamming you in one way or another and transferring the risks from the founders of the cryptocurrency to you.
Notable notes
nostr:note13s00phgqsqnzxrq375djumwr4384p8t4selajwwj97lzcgtd3rvsym2cda
Recommendations
Maxibitcoiner
Fantastic account to learn about Bitcoin for Spanish speaking audiences.
You can follow him here.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. It's a very effective way to stay up to date with the industry.
Just this week he also covered PayPal’s PYUSD and reported how apparently PayPal has the option to freeze or wipeout your PYUSD funds unilaterally.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 1c52ebc8:5698c92a
2023-08-12 18:00:17
@ 1c52ebc8:5698c92a
2023-08-12 18:00:17Hey folks, happy Saturday!
Here’s your weekly newsletter on the technical happenings in the nostr-verse. Things are moving fast, people are building many amazing projects.
Let’s dive in.
Recent Upgrades to Nostr (NIPs)
1) Moderated Communities 💬
This NIP outlines how to implement a Reddit-like experience, where moderators can create and manage communities. Then anyone can propose a post, but moderators get final say about what shows up in the community. Can’t wait to use it! Hopefully we can use Zaps instead of upvotes like Stacker News!
Authors: nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and @arthurfranca
2) Proxy Tags (Approved!) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. Now that this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
3) Rewrite of NIP 65 - Relay Lists by nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
Many in the Nostr dev community desire to have many small relays instead of centralization around a smaller set of massive, highly capable relays. In order to do that, there’s a challenge with discovering relays to pull events for a users’ followers.
This NIP was approved weeks ago, but was rewritten recently to make it easier to implement, which should help add more momentum to decentralizing relays.
Notable projects
Vault - Nostr-based Password Manager 🔒
nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn implemented a way to store and retrieve sensitive information (like passwords) via Nostr. It has a 1Password-like interface for ease of use.
It’s also encrypted twice, once via the normal Nostr secret key signing like any Nostr event, but again with the password to unlock the vault. That way, if someone compromises your Nostr account’s secret key in the future, they still need your vault password to decrypt your sensitive information.
Can’t wait to migrate!
Nostrscript
Looks like nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s added a way to activate code in Damus via a link on a website. This pattern could help clients interoperate (one client activating actions in other clients a user is using). Endless possibilities!
Relay Backup
nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f Built a way to easily back up your events from a relay. This helps folks make sure all their events from public relays are copied to a private backup relay so none of their events are lost to time.
Stacker news
Not exactly new, but this project has been a delight to engage in discussion with other folks interested in Nostr, Bitcoin, and freedom tech in general. Using zaps as signal instead of upvotes is pretty novel to me, and all the zaps go to the posters as well as the platform to distribute rewards to the community. #valueforvalue
Latest conversations
Who controls NIPs?
Right now NIPs are hosted via a Github Repo. This is helpful in many ways because there’s one publicly-accessible way to read NIPs and get started contributing. By the nature of this being a code repository under source control, there are a small group of folks that are able to “approve” updates to NIPs.
The nature of projects like Nostr (or Bitcoin in the early 2010s for that matter) is that the early folks often need some control over the direction to make sure that the project has a chance to become self-sustaining without imploding into chaos.
The debate in the linked thread seems to be stemming from the timeless question for protocols, which is “how much should the protocol be able to do?” and that’s generally decided by early devs and those that control the generally accepted version of the spec for the protocol. That’s currently the NIPs repo, so who gets to “approve” NIPs in that repo?
Here’s hoping we can find a collaborative place to land that preserves the heart of nostr and maximizes its chance of success 💪
How to handle illegal content on Nostr
There was a Plebchain radio conversation with nostr:npub1yye4qu6qrgcsejghnl36wl5kvecsel0kxr0ass8ewtqc8gjykxkssdhmd0 who has been an advocate for folks that’ve been trafficked. She’s a rare advocate of preventing trafficking and CSAM through the internet without compromising encryption, or other online freedom.
There are unanswered questions about how the Nostr community is going to handle this content so we don’t see Nostr become a haven for activity most see as despicable. With the collection of smart people on Nostr, I’ll bet that a solution emerges to maximize freedom on the internet and drastically reduce the ability for illegal content to spread via the Nostr protocol.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual).
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week, but if you wanna see something advertised here just DM me!
Until next time 🫡
If I missed anything, or you’re building something I didn’t post about, let me know, DMs welcome.
God bless, you’re super cute
-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
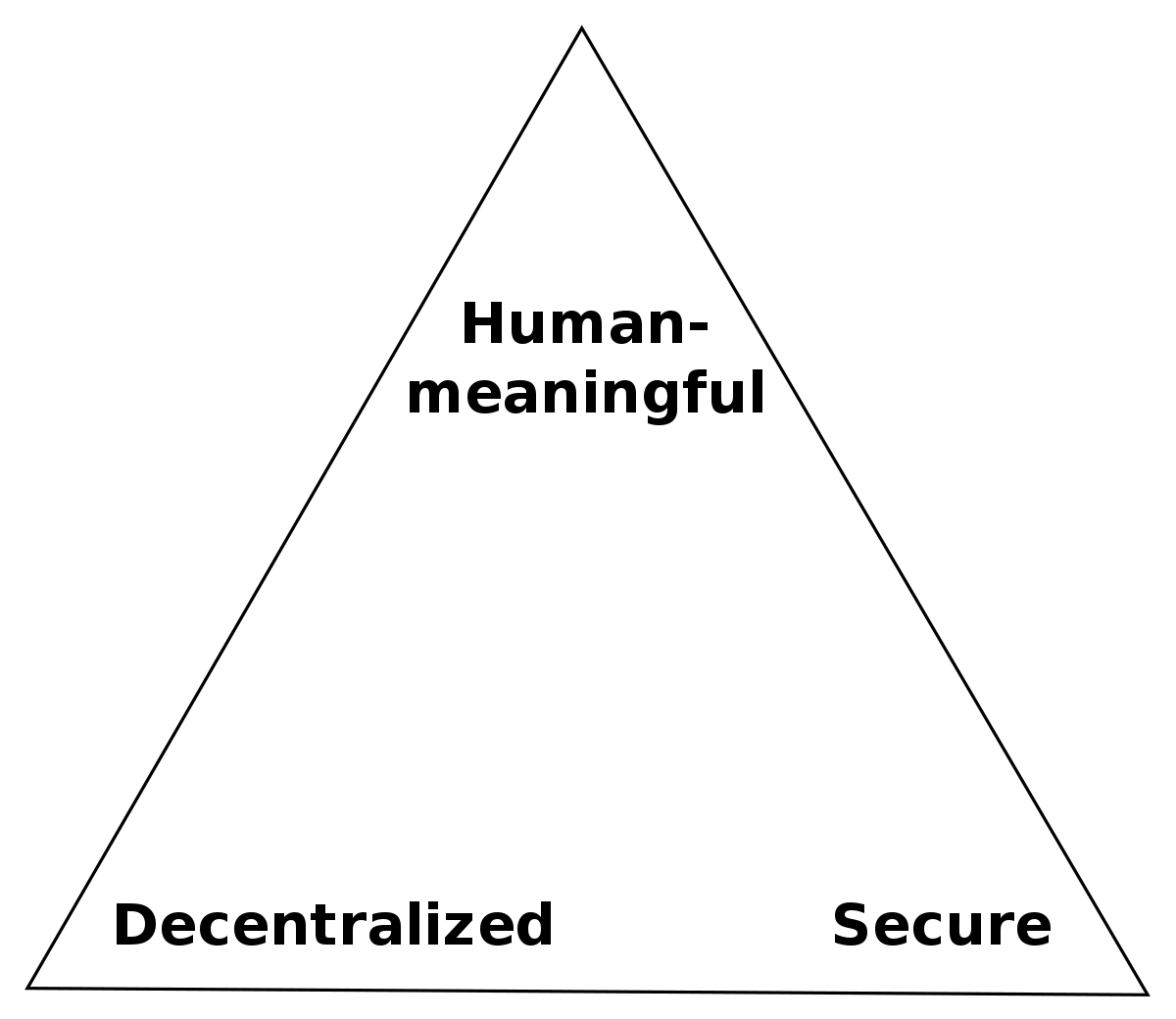
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ aa55a479:f7598935
2023-07-19 17:54:44
@ aa55a479:f7598935
2023-07-19 17:54:44Test
-
 @ c8df6ae8:22293a06
2023-08-13 00:40:36
@ c8df6ae8:22293a06
2023-08-13 00:40:36"The SEC told Coinbase that it views “every asset other than bitcoin” as a security and ordered the company to delist them from its website."
— Brian Armstrong, CEO of Coinbase
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue goes back to basics to explain why the SEC asked Coinbase to delist all the shitcoins.
The SEC is a closet maxi
Before filing its suit against Coinbase, the Securities and Exchange Commission (SEC) asked Coinbase to delist all cryptocurrencies from its exchange except for Bitcoin.
Bitcoin is money. Shitcoins are investments. — The SEC, sort of
The SEC is explicitly saying that Bitcoin is the only digital money out there.
Why only Bitcoin?
When you buy Bitcoin, you’re buying a commodity, just like gold or grain.
When you buy a shitcoin like Ethereum or Hex, you are buying a security, just like when you buy shares of a company.
What makes Bitcoin different?
The founder of Bitcoin, Satoshi Nakamoto, did not assign himself a large share of Bitcoin before others could mine it. He did not assign a large share of Bitcoin to venture capital firms investing in him and his team either.
Instead, he launched the project and invited everyone else to join him. Anyone in the world who was paying attention was able to join the network and mine Bitcoin with the same probability of success as Satoshi.
The founder of Ethereum, the blockchain that underpins most shitcoins, did the opposite. Ethereum is like a startup. Both its founders and the investors that back it are hoping to make big money by selling you Eth tokens.
The founder of Bitcoin is anonymous. We do not know who he is. He has not transacted with his Bitcoin since he disappeared in 2011. For all we know he could be dead. He is not setting directions or acting as the referee in disputes about what Bitcoin should or should not do.
The founder of Ethereum, Vitalik Buterin, has full control over the project:
Nobody has control over Bitcoin. Bitcoin is open sourced and anyone can change the behaviour of the Bitcoin network. However, unless you convince 51% of Bitcoin node runners that the change is in their benefit as well, your change will go nowhere. The chances of convincing 51% of node operators is close to nil which is why people assert that no one can change Bitcoin.
Vitalik Buterin spearheaded the most important change in the Ethereum network in years: changing from proof-of-work to proof-of-stake validation.
Others have tried the same with Bitcoin and they failed.
Shitcoins are not the crypto industry
Coinbase declined to delist everything other than Bitcoin because according to its CEO, “compliance with the order would have meant the end of the crypto industry in the US.”.
The reality is that the crypto industry is Bitcoin and its layer 2 projects like Lightning, Fedimint and the Liquid network.
The shitcoins call themselves crypto industry but they are just good old scams. They call themselves crypto to fool you into buying them.
If Coinbase had delisted all shitcoins, the crypto industry wouldn’t had died. It would had been cleared from all these parasites that hang to it and suck its energy and reputation.
Just consider how much more widely accepted Bitcoin would be if we didn’t have these regular scams, rug pulls and exchange collapses.
The next time a someone tells you that the SEC is going after the crypto industry, say no, they are going after a bunch of scammers.
Notable notes
nostr:note1rhuh2dmk9d86gllfqgls9vmj2dr3x0ch56va2rrgrt397mlmarjqrp43v2
Recommendations
Matt Odell
Champion of freedom tech, free speech and humility.
You can follow him here.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. It's a very effective way to stay up to date with the industry.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ ca843451:fa3b4c1a
2023-08-09 12:17:34
@ ca843451:fa3b4c1a
2023-08-09 12:17:34关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n\n原文作者:Eric Zhang\n\n区块链可以在货币和金融交易之外发挥作用。其中一种非金融应用便是区块链可以极大地改进投票和治理领域。在本文中,我们探讨构建一种特殊用途区块链的方法,该基础设施旨在促进基于MACI的投票活动。该基础设施应包括充当时间戳服务器并托管逻辑的轻型区块链,以及减少用户成本/最大化用户体验所需的工具。因此,它应该成为新一代投票技术的新基础平台。在深入探讨细节之前,让我们首先回顾一下投票技术的历史以及投票在区块链社区内的发展过程。\n## 投票技术的演变\n
 \n从古希腊Kleroterion到现代电子投票机的投票技术。\n\n投票技术有着悠久的历史。它对人类社会非常重要,但发展非常缓慢。英国在2019年脱欧大选期间仍然依赖手写选票,其他民族国家使用闭源电子投票机,很容易为选举结果带来争议。\n\n现代投票技术的采用提高了效率,但在解决透明度和可验证性方面并没有取得太大成功。\n\n毋庸置疑,投票的诚信对于权力的交接、重要事务的决策或资源的分配非常重要。如果人们不能就治理决策的投票结果达成一致,他们就无法相互合作,摩擦就会增加。摩擦可能会引起问题,如从争端到战争。\n\n尽管投票技术正在缓慢发展,但透明度在很长一段时间内并没有得到改善。从Kleroterion到纸质选票,再到电子和光学扫描投票机,验证仍然依赖于值得信赖的个人和审计组织。确认和审核投票结果的成本可能极其高昂。显然还有改进的空间。\n\n那么理想的投票技术是什么?其实这并不是一个困难的问题。我们可以轻松创建一个“愿望清单”:\n(1)基础设施开源;\n(2)托管用于投票逻辑的开源程序;\n(3)按顺序保留所有投票的永久记录;\n(4)能够对结果进行密码学验证;\n(5)抗串谋;\n(6)保护隐私;\n(7)投票成本低。\n\n\n如果我们能够构建一个可以不断完善的开源系统,我们就会逐步实现上述目标。投票技术的改进和成本的降低可以使较小的组织和社区受益于使用他们以前无法获得的技术,这增加了巨大的正外部性。\n## 区块链社区内的投票和治理\n投票和治理在区块链社区中并不陌生,因为很多区块链社区都是分布式的,他们必须依靠治理来推动事务的发展。\n\n区块链本身可以透明地记录投票并验证投票结果。这些属性已被区块链社区用于治理,例如Snapshot代币投票和Cosmos治理提案投票活动。因此,区块链社区可以在不经过中心化代理或面对面会议的情况下,对提案进行投票,并决定重要的治理事务。\n
\n从古希腊Kleroterion到现代电子投票机的投票技术。\n\n投票技术有着悠久的历史。它对人类社会非常重要,但发展非常缓慢。英国在2019年脱欧大选期间仍然依赖手写选票,其他民族国家使用闭源电子投票机,很容易为选举结果带来争议。\n\n现代投票技术的采用提高了效率,但在解决透明度和可验证性方面并没有取得太大成功。\n\n毋庸置疑,投票的诚信对于权力的交接、重要事务的决策或资源的分配非常重要。如果人们不能就治理决策的投票结果达成一致,他们就无法相互合作,摩擦就会增加。摩擦可能会引起问题,如从争端到战争。\n\n尽管投票技术正在缓慢发展,但透明度在很长一段时间内并没有得到改善。从Kleroterion到纸质选票,再到电子和光学扫描投票机,验证仍然依赖于值得信赖的个人和审计组织。确认和审核投票结果的成本可能极其高昂。显然还有改进的空间。\n\n那么理想的投票技术是什么?其实这并不是一个困难的问题。我们可以轻松创建一个“愿望清单”:\n(1)基础设施开源;\n(2)托管用于投票逻辑的开源程序;\n(3)按顺序保留所有投票的永久记录;\n(4)能够对结果进行密码学验证;\n(5)抗串谋;\n(6)保护隐私;\n(7)投票成本低。\n\n\n如果我们能够构建一个可以不断完善的开源系统,我们就会逐步实现上述目标。投票技术的改进和成本的降低可以使较小的组织和社区受益于使用他们以前无法获得的技术,这增加了巨大的正外部性。\n## 区块链社区内的投票和治理\n投票和治理在区块链社区中并不陌生,因为很多区块链社区都是分布式的,他们必须依靠治理来推动事务的发展。\n\n区块链本身可以透明地记录投票并验证投票结果。这些属性已被区块链社区用于治理,例如Snapshot代币投票和Cosmos治理提案投票活动。因此,区块链社区可以在不经过中心化代理或面对面会议的情况下,对提案进行投票,并决定重要的治理事务。\n \nKlaytnSquare正在进行的一项提案呼吁验证者在链上投票。该提案寻求季度财政支出计划的批准。\n\n前述的例子采用了简单直接的1代币1票规则 - 拥有多少投票权取决于在网络或协议中的权益。显然,只要有意义,我们可以创造其他投票逻辑。区块链的可编程性使得实施非传统投票逻辑变得更加容易和实际。\n\n一个例子是二次方投票(QV),这是一种在区块链社区中越来越受欢迎的投票方案。在QV轮中,选民可以通过在特定主题上花费“投票信用积分”(Voice Credit)来表达他/她的偏好。但如果选民想对同一主题投不止一票,则每票的声音信用成本就会增加。因此,投票的总成本呈二次增加,阻止了那些拥有过多投票权力的选民的极端偏好。\n\n
\nKlaytnSquare正在进行的一项提案呼吁验证者在链上投票。该提案寻求季度财政支出计划的批准。\n\n前述的例子采用了简单直接的1代币1票规则 - 拥有多少投票权取决于在网络或协议中的权益。显然,只要有意义,我们可以创造其他投票逻辑。区块链的可编程性使得实施非传统投票逻辑变得更加容易和实际。\n\n一个例子是二次方投票(QV),这是一种在区块链社区中越来越受欢迎的投票方案。在QV轮中,选民可以通过在特定主题上花费“投票信用积分”(Voice Credit)来表达他/她的偏好。但如果选民想对同一主题投不止一票,则每票的声音信用成本就会增加。因此,投票的总成本呈二次增加,阻止了那些拥有过多投票权力的选民的极端偏好。\n\n \n二次方融资轮在Aptos区块链上投票。投票结果记录在链上,投票逻辑可验证。\n\n选择特定投票方式时需要考虑许多参数。例如,一个权衡是选择链上投票还是链下投票。链上投票逻辑可能更具可验证性和透明度,但Gas Fee可能是一个重要的负担。相反,链下投票逻辑可能更便宜,但同时透明度和可验证性较低。然而,链上与链下投票不是二选一的关系。我们可以很容易地将其设计为混合系统,其中部分流程在链上进行,其余部分在链下完成。\n\n除了成本之外,还有隐私问题。隐私之所以重要有两个原因。首先,在很多情况下,如果选民可以匿名投票(用户和当局之间的隐私),他们对投票的顾虑就会减少。此外,用户之间的隐私可以帮助防止投票贿赂,有效实现抗共谋。\n\n我们可以最大限度地减少链上计算,同时强制链下完整性的一种方法是使用零知识证明。一个简单的想法是,如果链下计算可以通过零知识证明进行验证,我们就可以将大部分计算移至链下。如果消息进一步加密,我们就可以增强隐私性。MACI是实现这一目标的最小框架。\n\n
\n二次方融资轮在Aptos区块链上投票。投票结果记录在链上,投票逻辑可验证。\n\n选择特定投票方式时需要考虑许多参数。例如,一个权衡是选择链上投票还是链下投票。链上投票逻辑可能更具可验证性和透明度,但Gas Fee可能是一个重要的负担。相反,链下投票逻辑可能更便宜,但同时透明度和可验证性较低。然而,链上与链下投票不是二选一的关系。我们可以很容易地将其设计为混合系统,其中部分流程在链上进行,其余部分在链下完成。\n\n除了成本之外,还有隐私问题。隐私之所以重要有两个原因。首先,在很多情况下,如果选民可以匿名投票(用户和当局之间的隐私),他们对投票的顾虑就会减少。此外,用户之间的隐私可以帮助防止投票贿赂,有效实现抗共谋。\n\n我们可以最大限度地减少链上计算,同时强制链下完整性的一种方法是使用零知识证明。一个简单的想法是,如果链下计算可以通过零知识证明进行验证,我们就可以将大部分计算移至链下。如果消息进一步加密,我们就可以增强隐私性。MACI是实现这一目标的最小框架。\n\n \nMACI投票轮将计票转移到链外。最后通过零知识证明链上验证结果的有效性。\n\n在MACI投票轮中,投票被封装在由一轮管理员(运营商)生成的公钥加密的消息中,并提交给智能合约。因此,所有消息都被区块链“时间戳”,从而创建了一个选民消息链。\n\n当投票轮次结束时,运营商下载所有消息,对它们进行解密,并以相反的顺序进行投票计数。然后,将结果与零知识证明一起发布,可以在智能合约上(或由任何其他人)进行验证,从而标志着发布结果的有效性以及消息处理的正确性。\n\n整个过程在保证发布结果的完整性的同时,保持了最小的链上计算。它还为用户之间提供了隐私和抗共谋的能力。\n## MACI在实际产品中是如何工作的?\nMACI现在被DoraHacks上的各个黑客马拉松社区用来投票选出他们最喜欢的黑客马拉松项目。所以我们以DoraHacks MACI轮次为例。\n\n
\nMACI投票轮将计票转移到链外。最后通过零知识证明链上验证结果的有效性。\n\n在MACI投票轮中,投票被封装在由一轮管理员(运营商)生成的公钥加密的消息中,并提交给智能合约。因此,所有消息都被区块链“时间戳”,从而创建了一个选民消息链。\n\n当投票轮次结束时,运营商下载所有消息,对它们进行解密,并以相反的顺序进行投票计数。然后,将结果与零知识证明一起发布,可以在智能合约上(或由任何其他人)进行验证,从而标志着发布结果的有效性以及消息处理的正确性。\n\n整个过程在保证发布结果的完整性的同时,保持了最小的链上计算。它还为用户之间提供了隐私和抗共谋的能力。\n## MACI在实际产品中是如何工作的?\nMACI现在被DoraHacks上的各个黑客马拉松社区用来投票选出他们最喜欢的黑客马拉松项目。所以我们以DoraHacks MACI轮次为例。\n\n \nOpenSea与Replit黑客马拉松在2022年使用MACI进行评委投票\n\n黑客马拉松项目(BUIDL)提交后,主办方从所有提交的作品中选出了12支BUIDL团队。10名评委受邀为这12支BUIDL团队投票,并分发25,000美元的奖金。10名评委被列入白名单,报名参加投票轮,他们总共向部署在Polygon上的MACI智能合约发送了39条消息。\n\n投票结束后,管理员(DoraHacks)统计票数并将最终结果发布到排行榜上,然后提供零知识证明来验证排行榜。\n\n\n
\nOpenSea与Replit黑客马拉松在2022年使用MACI进行评委投票\n\n黑客马拉松项目(BUIDL)提交后,主办方从所有提交的作品中选出了12支BUIDL团队。10名评委受邀为这12支BUIDL团队投票,并分发25,000美元的奖金。10名评委被列入白名单,报名参加投票轮,他们总共向部署在Polygon上的MACI智能合约发送了39条消息。\n\n投票结束后,管理员(DoraHacks)统计票数并将最终结果发布到排行榜上,然后提供零知识证明来验证排行榜。\n\n\n \nOpenSea x Replit黑客马拉松投票结果的排行榜。\n\n
\nOpenSea x Replit黑客马拉松投票结果的排行榜。\n\n \n验证排行榜上显示的结果的零知识证明。\n\n作为一个通用框架,MACI可以用于黑客马拉松评委投票和开源社区投票之外的投票用例。然而,令人惊讶的是,在更多投票用例中采用MACI的情况却很少见。更广泛地说,区块链投票本身在现实世界中还没有被采用。\n\n使用区块链改进投票技术的好处显而易见,但为什么现实世界却没有向前发展?即使在区块链社区内,MACI的优势显而易见,为什么去中心化社区不普遍采用MACI?\n\n先进投票技术采用缓慢的一个主要原因并不是需求低,而是使用这种技术的困难。换句话说,我们需要改进技术,为现代投票产品提供更好的UX/UI,并降低用户的使用成本。\n\n## 用户体验\n除了开源社区治理之外,我们还需要构建更多接口供用户使用新的投票技术。DoraHacks为Web3生态系统和黑客马拉松社区提供了目前整个行业最好用的产品来提供资助。尽管DoraHacks.io上的接口本身具有特定的用例,但可以对其进行简化然后泛化,以便为更多用例构建更多接口。\n\n具体的前端策略尚未确定。然而,良好的用户体验对于该技术的采用至关重要,即使是在区块链社区中也是如此——这对于Dora Factory开发者来说很重要。\n## 投票费用\n通用区块链应该尽可能去中心化,并为所有类型的应用程序提供单一的基础设施。这些区块链并非旨在针对任何特定类型的应用程序进行优化,尤其是非货币或非金融应用。同时,当存在大量应用程序竞争同一组计算资源时,交易费用会出现波动。成本的不可预测性会给投票带来麻烦。\n\n为此,Dora Factory最近测试了一款名为Vota的新产品。Vota的想法是尝试特殊用途的区块链,并利用它们来不断优化投票技术和用户体验。目前,Vota还处于婴儿阶段。然而,我们可以想象几种不同形式的Vota。\n\n## 临时智能合约\n这是目前在DoraHacks.io上支持投票轮次的方式。每轮投票都作为单独的智能合约部署在特定的区块链上。大部分情况下,以太坊通常无法直接支持大部分的投票场景(这就是为什么Snapshot是以太坊社区默认使用的产品)。目前,Polygon和BNBChain是DoraHacks上大多数资助组织者和黑客马拉松组织者的热门选择。\n
\n验证排行榜上显示的结果的零知识证明。\n\n作为一个通用框架,MACI可以用于黑客马拉松评委投票和开源社区投票之外的投票用例。然而,令人惊讶的是,在更多投票用例中采用MACI的情况却很少见。更广泛地说,区块链投票本身在现实世界中还没有被采用。\n\n使用区块链改进投票技术的好处显而易见,但为什么现实世界却没有向前发展?即使在区块链社区内,MACI的优势显而易见,为什么去中心化社区不普遍采用MACI?\n\n先进投票技术采用缓慢的一个主要原因并不是需求低,而是使用这种技术的困难。换句话说,我们需要改进技术,为现代投票产品提供更好的UX/UI,并降低用户的使用成本。\n\n## 用户体验\n除了开源社区治理之外,我们还需要构建更多接口供用户使用新的投票技术。DoraHacks为Web3生态系统和黑客马拉松社区提供了目前整个行业最好用的产品来提供资助。尽管DoraHacks.io上的接口本身具有特定的用例,但可以对其进行简化然后泛化,以便为更多用例构建更多接口。\n\n具体的前端策略尚未确定。然而,良好的用户体验对于该技术的采用至关重要,即使是在区块链社区中也是如此——这对于Dora Factory开发者来说很重要。\n## 投票费用\n通用区块链应该尽可能去中心化,并为所有类型的应用程序提供单一的基础设施。这些区块链并非旨在针对任何特定类型的应用程序进行优化,尤其是非货币或非金融应用。同时,当存在大量应用程序竞争同一组计算资源时,交易费用会出现波动。成本的不可预测性会给投票带来麻烦。\n\n为此,Dora Factory最近测试了一款名为Vota的新产品。Vota的想法是尝试特殊用途的区块链,并利用它们来不断优化投票技术和用户体验。目前,Vota还处于婴儿阶段。然而,我们可以想象几种不同形式的Vota。\n\n## 临时智能合约\n这是目前在DoraHacks.io上支持投票轮次的方式。每轮投票都作为单独的智能合约部署在特定的区块链上。大部分情况下,以太坊通常无法直接支持大部分的投票场景(这就是为什么Snapshot是以太坊社区默认使用的产品)。目前,Polygon和BNBChain是DoraHacks上大多数资助组织者和黑客马拉松组织者的热门选择。\n \nL1区块链上的临时智能合约,所有投票消息发送到L1。\n\n使用临时智能合约并不完全是坏事。它很灵活,可以根据需要将其部署在任何地方。对于DoraHacks的用户而言,目前效果还不错,但无法同等满足所有投票需求。\n## L2 Vota\n如果我们创建一个专门用于投票的二层基础设施(L2),可以显着降低Gas费成本,并且可能能够在以太坊上实现低成本的投票。L2合约不必全部部署在以太坊上,它们可以更便宜,只需不时地提交L1交易以验证所有L2活动。\n\n我们可以进一步优化这个模型。通用L2必须经常提交到以太坊。Vota每轮只需向以太坊提交一笔交易,即每轮最多只需要一笔交易的Gas费成本。如果多轮在同一时间结束,他们可以共享一笔交易以进一步降低Gas成本,使投票L2更加现实可行。\n
\nL1区块链上的临时智能合约,所有投票消息发送到L1。\n\n使用临时智能合约并不完全是坏事。它很灵活,可以根据需要将其部署在任何地方。对于DoraHacks的用户而言,目前效果还不错,但无法同等满足所有投票需求。\n## L2 Vota\n如果我们创建一个专门用于投票的二层基础设施(L2),可以显着降低Gas费成本,并且可能能够在以太坊上实现低成本的投票。L2合约不必全部部署在以太坊上,它们可以更便宜,只需不时地提交L1交易以验证所有L2活动。\n\n我们可以进一步优化这个模型。通用L2必须经常提交到以太坊。Vota每轮只需向以太坊提交一笔交易,即每轮最多只需要一笔交易的Gas费成本。如果多轮在同一时间结束,他们可以共享一笔交易以进一步降低Gas成本,使投票L2更加现实可行。\n \n消息直接发送到L2合约。每轮结束时只有一笔交易被发送到L1区块链。\n## L3Vota(适用于L(n)Vota,其中n>=3)\nL3 Vota并非完全没有意义。通过已建立的L2,L3 Vota可以进一步将Gas费降低一个数量级。尽管L3交易最终在以太坊上记录和验证,但权衡之处在于要相信所选择的L2。\n\n当然,我们可以进一步将其扩展到L(n) Vota,因为L(2)…L(n-1)将向以太坊(或其他L1)提交交易。但显然信任链会让事情变得复杂。从目前的情况来看,很多著名的L2仍然依赖于单一的排序器(Sequencer);现在谈论L(4)可能还为时过早。\n
\n消息直接发送到L2合约。每轮结束时只有一笔交易被发送到L1区块链。\n## L3Vota(适用于L(n)Vota,其中n>=3)\nL3 Vota并非完全没有意义。通过已建立的L2,L3 Vota可以进一步将Gas费降低一个数量级。尽管L3交易最终在以太坊上记录和验证,但权衡之处在于要相信所选择的L2。\n\n当然,我们可以进一步将其扩展到L(n) Vota,因为L(2)…L(n-1)将向以太坊(或其他L1)提交交易。但显然信任链会让事情变得复杂。从目前的情况来看,很多著名的L2仍然依赖于单一的排序器(Sequencer);现在谈论L(4)可能还为时过早。\n \n## 应用链Vota\nDoraFactory开发人员创建了一个简单的“Hack”,允许CosmWasm合约使用Bellman验证SnarkJS生成的零知识证明。通过将Bellman纳入CosmWasm合约中,任何Cosmos应用链都可以快速支持zk应用程序。\n\n借助运行zk应用程序的能力,独立的区块链可以使用像Tendermint这样的软件架构来构建一条链。这些区块链的共识类似于BFT,因此它们通常可以支持多达100个左右的验证者。通过仔细选择利益不一致的验证者,独立的区块链可以足够安全和中立。\n
\n## 应用链Vota\nDoraFactory开发人员创建了一个简单的“Hack”,允许CosmWasm合约使用Bellman验证SnarkJS生成的零知识证明。通过将Bellman纳入CosmWasm合约中,任何Cosmos应用链都可以快速支持zk应用程序。\n\n借助运行zk应用程序的能力,独立的区块链可以使用像Tendermint这样的软件架构来构建一条链。这些区块链的共识类似于BFT,因此它们通常可以支持多达100个左右的验证者。通过仔细选择利益不一致的验证者,独立的区块链可以足够安全和中立。\n \n随着DoraHacks欢迎更多Cosmos应用链加入,基于应用链的Vota的一个明显用例是为黑客马拉松结果投票。除了DoraHacks之外,基于Cosmos应用链的Vota的作用远不止黑客马拉松评委投票。\n\n
\n随着DoraHacks欢迎更多Cosmos应用链加入,基于应用链的Vota的一个明显用例是为黑客马拉松结果投票。除了DoraHacks之外,基于Cosmos应用链的Vota的作用远不止黑客马拉松评委投票。\n\n \n应用链Vota的验证器数量较少,但精心挑选的验证器可以提供可靠的基础设施。\n\n值得注意的是,这些解决方案并不是排他性的。随着Vota的发展,不同的解决方案可能会交叉。例如,如果我们有一个独立的应用链版本的Vota作为主要基础设施,对于需要在特定L1上进行交易验证的用例,应用链可以向L1发送额外的交易。\n## 更好的匿名性\n目前正在进行的研究和工程工作旨在使MACI更加去信任。最初的MACI做出了一个重要的信任假设,即运营商不会腐败。这并不具有普遍性。为了改进这一点,有基于MPC的解决方案和非基于MPC的解决方案。目前,DoraHacks已经构建了一个基于ElGamal可重随机化加密的匿名MACI版本,该加密最初由KobeGuikan提出。它已在DoraHacks.io上的小型ETH研究资助轮中进行了测试。\n\n目前,在MACI本身被广泛采用之前推动匿名MACI的采用可能有点过早。然而,继续研究以减少一般投票机制的信任假设也很重要。\n
\n应用链Vota的验证器数量较少,但精心挑选的验证器可以提供可靠的基础设施。\n\n值得注意的是,这些解决方案并不是排他性的。随着Vota的发展,不同的解决方案可能会交叉。例如,如果我们有一个独立的应用链版本的Vota作为主要基础设施,对于需要在特定L1上进行交易验证的用例,应用链可以向L1发送额外的交易。\n## 更好的匿名性\n目前正在进行的研究和工程工作旨在使MACI更加去信任。最初的MACI做出了一个重要的信任假设,即运营商不会腐败。这并不具有普遍性。为了改进这一点,有基于MPC的解决方案和非基于MPC的解决方案。目前,DoraHacks已经构建了一个基于ElGamal可重随机化加密的匿名MACI版本,该加密最初由KobeGuikan提出。它已在DoraHacks.io上的小型ETH研究资助轮中进行了测试。\n\n目前,在MACI本身被广泛采用之前推动匿名MACI的采用可能有点过早。然而,继续研究以减少一般投票机制的信任假设也很重要。\n \n通过添加允许用户停用和更改其秘密密钥的操作来为MACI添加匿名性,而运营商无法知道谁添加了哪个新密钥。\n## GAS支付\n重要的是不要假设用户拥有加密货币。如果每个用户每笔交易都需要支付Gas费,那么区块链的用户将仅限于一小部分人。为了解决这个问题,MACI运营商可以预先存入一笔可退还的代币并支付用户的费用。该机制可以通过加油站来实现。\n\n加油站本身是一个驻留在Vota上的智能合约。在每轮开始之前,操作者可以选择使用它,也可以不使用它。通过使用加油站,运营商将DORA预先存入智能合约中,并且可以通过加油站支付与特定回合相关的交易费用。\n\n最有可能的是,Vota会部署一个默认的加油站,人们可以按需部署自己的具有不同支付逻辑的加油站。\n\n
\n通过添加允许用户停用和更改其秘密密钥的操作来为MACI添加匿名性,而运营商无法知道谁添加了哪个新密钥。\n## GAS支付\n重要的是不要假设用户拥有加密货币。如果每个用户每笔交易都需要支付Gas费,那么区块链的用户将仅限于一小部分人。为了解决这个问题,MACI运营商可以预先存入一笔可退还的代币并支付用户的费用。该机制可以通过加油站来实现。\n\n加油站本身是一个驻留在Vota上的智能合约。在每轮开始之前,操作者可以选择使用它,也可以不使用它。通过使用加油站,运营商将DORA预先存入智能合约中,并且可以通过加油站支付与特定回合相关的交易费用。\n\n最有可能的是,Vota会部署一个默认的加油站,人们可以按需部署自己的具有不同支付逻辑的加油站。\n\n \nGas支付合约是每轮投票的Gas余额的账本。\n## 结论\n特殊用途的区块链可能适用于广泛的特定应用用例,尤其是非金融用例。投票是区块链和零知识密码学可以帮助显着改善的最重要问题之一。提高投票透明度和效率可以减少人类社会和区块链社区内部的治理摩擦,从长远来看可以提高生产力。像MACI这样的协议为区块链上的投票应用程序创建了简洁的框架,但投票技术还需要做很多工作来改进。具体来说,我们需要一个用户友好的基础设施作为基础来长期改进投票技术,本文详细介绍了未来的工作。\n\n关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n
\nGas支付合约是每轮投票的Gas余额的账本。\n## 结论\n特殊用途的区块链可能适用于广泛的特定应用用例,尤其是非金融用例。投票是区块链和零知识密码学可以帮助显着改善的最重要问题之一。提高投票透明度和效率可以减少人类社会和区块链社区内部的治理摩擦,从长远来看可以提高生产力。像MACI这样的协议为区块链上的投票应用程序创建了简洁的框架,但投票技术还需要做很多工作来改进。具体来说,我们需要一个用户友好的基础设施作为基础来长期改进投票技术,本文详细介绍了未来的工作。\n\n关注我了解更多crypto相关动态\n欢迎在抗审查的长内容平台 yakihonne.com 阅读我的所有文章!\n -
 @ 78733875:4eb851f2
2023-07-14 22:25:21
@ 78733875:4eb851f2
2023-07-14 22:25:21"The computer can be used as a tool to liberate and protect people, rather than to control them," as Hal Finney wrote so presciently 30 years ago.[^fn-hal]
The goal of OpenSats is to help build the tools that Hal alluded to. Tools that liberate and protect, rather than systems that control and oppress. Many tools still have to be built. Many tools still need to be improved. However, "the universe smiles on encryption," as Assange so aptly put it.[^fn-assange]
We believe that freedom tech is what carries this smile forward, which is why we are delighted to announce grants for over a dozen projects in the bitcoin & lightning ecosystem.
[^fn-hal]: Hal Finney: Why remailers... (November 1992)
[^fn-assange]: Julian Assange: A Call to Cryptographic Arms (October 2012)
The following open-source projects were selected by the OpenSats board for funding:
- Payjoin Dev Kit
- Bolt12 for LND
- Splicing
- Raspiblitz
- Labelbase
- BTCPay Server
- ZeroSync
- Mutiny Wallet
- next-auth Lightning Provider
- Cashu
- lnproxy
- Blixt Wallet
Let's take a closer look at each to understand their goal and how it aligns with the OpenSats mission.
Payjoin Dev Kit
Payjoin brings privacy to bitcoin without changing the way you're used to using it. Payjoin transactions look no different from normal activity on-chain, so they boost everyone's privacy, even those who don't payjoin, and foil chain surveillance.
Payjoin is easy to integrate and falls back to working defaults where it isn't supported, but it can only take off when senders and receivers include standard payjoin support in their software. Payjoin Dev Kit makes it easy for wallet developers to integrate BIP 78 standard payjoins everywhere, having working reference integrations for Bitcoin Core, LND, and BDK.
Repository: github.com/payjoin
License: MITBolt12 for LND
Bolt12 brings a new invoice format, enabling static invoices (offers) as well as recurring payments. It adds support to receive payments in a lightning-native way without using a web server. It also uses Blinded Paths to disguise the destination of a node both when fetching the invoice and when paying. This improves privacy and, therefore, security for the receiver of the payment.
Consequently, Bolt12 makes it much easier to receive and send payments without any third-party infrastructure in a native-lightning way. Static invoices make donations and recurring payments much easier.
Repository: lightningnetwork/lnd
License: MITSplicing
Splicing is the ability to resize Lightning channels on-the-fly, giving users of the Lightning Network many additional benefits that were not intuitively obvious at first. Splicing scales Lightning by removing a fundamental limitation. Removing this limitation increases fungibility and lowers blockspace usage, an important step towards maturing the Lightning network and enabling the onboarding of millions, and ultimately billions, of people.
Repository: ddustin/splice
License: BSD-MITRaspiblitz
Raspiblitz is a do-it-yourself node stack that allows you to run a Lightning Node together with a Bitcoin Core full node on your Raspberry Pi. While the Raspberry Pi is the most common hardware running this particular software, it was developed to support multiple hardware platforms and can run on bare metal servers too.
The open-source project was started in 2018 as part of a Lightning hackathon in the German Bitcoin space. Since then, it has grown to over 150 contributors and 2000 stars on GitHub. The software integrates dozens of services and tools via its plugin system and sports advanced features like touchscreen support, channel autopilot, backup systems, DynDNS, SSH tunneling, and more.
Repository: raspiblitz/raspiblitz
License: MITLabelbase
Labelbase is a label management service for Bitcoin transactions and addresses. It provides features for adding labels, importing and exporting labels, and offers a public API for integration with wallets and existing workflows.
Labelbase supports BIP-329, a format for unifying label data. The goal of the project is to offer a convenient solution for managing labels associated with Bitcoin transactions and addresses across wallets and other tools. By providing a unified label management interface, Labelbase enhances the user experience, improves privacy, and promotes better organization and understanding of Bitcoin transactions.
Repository: Labelbase/Labelbase
License: MITBTCPay Server
BTCPay Server is a free, open-source & self-hosted bitcoin payment gateway that allows self-sovereign individuals and businesses to accept bitcoin payments online or in person without added fees.
At its core, BTCPay Server is an automated invoicing system. Merchants can integrate the software with their website or shop, so customers are presented with an invoice upon checkout. The status of the invoice will update according to settlement, so merchants can fulfill the order at the appropriate time. The software also takes care of payment refunding and bitcoin management alongside many other features.
Repository: btcpayserver/btcpayserver
License: MITZeroSync
While ZeroSync is still at an early stage, its promise is to allow verification of Bitcoin's chain state in an instant. It offers compact cryptographic proofs to validate the entire history of transactions and everyone's current balances.
The first application is to "zerosync" Bitcoin Core in pruned mode. The long-term vision for ZeroSync is to become a toolbox for custom Bitcoin proofs.
Repository: zerosync/zerosync
License: MITMutiny Wallet
Mutiny Wallet is a web-first wallet capable of running anywhere, providing instant onboarding and platform censorship resistance. It is self-custodial, privacy-focused, user-friendly, and open-sourced under the MIT license.
The wallet has a strong focus on privacy, scalability, and accessibility. In addition to features that you would expect a regular lightning wallet to have, the team is working to incorporate Nostr-related features into the wallet, such as a feed of friends' Zaps, native Zap sending and receiving, a lightning subscription specification for services such as nostr relays, and a P2P DLC marketplace. The team's goal is to provide users with a seamless experience, combining the power of Bitcoin and Lightning with social media in a way that matches the Bitcoin ethos.
Repository: MutinyWallet
License: MITnext-auth Lightning Provider
The goal of this project is to implement an authentication provider for next-auth, an authentication provider for the popular open-source framework NextJS. The next-auth framework has nearly 500k weekly downloads and powers the authentication of many modern web, mobile, and desktop apps. Having a plug-and-play Provider for Lightning makes integration easier and more attractive for developers.
Repository: jowo-io/next-auth-lightning-provider
License: ISCCashu
Cashu is a Chaumian ecash system built for bitcoin that brings near-perfect privacy for users of custodial bitcoin applications. A Cashu ecash mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately, without anyone being able to know who the involved parties are.
Payments are executed without anyone able to censor specific users. There are multiple implementations of the Cashu protocol. Popular open-source wallets are Cashu Nutshell, Cashu.me, and Nutstash.
Repository: cashubtc/cashu
License: MITlnproxy
lnproxy is a simple privacy tool that empowers users of custodial Lightning wallets with better payment destination privacy and sovereign node runners with enhanced receiver privacy. lnproxy works like a "poor man's" rendezvous router, providing privacy for users without taking custody of their funds. The project encompasses an LNURL-style protocol specification and a collection of open-source implementations of lnproxy clients and a relay.
Repository: lnproxy/lnproxy
License: GPL 3.0 & MITBlixt Wallet
Blixt is a non-custodial wallet for bitcoiners who want to give Lightning a try. It runs on Android, iOS, and macOS. It is easy to use and straightforward to set up, making it a user-friendly option to get started with Lightning.
Blixt uses LND and Neutrino under the hood, directly on the phone, respecting your privacy. The wallet does not use any centralized servers for doing transactions. Channels are opened automatically on the user's behalf, making it easy to get up and running on Lightning.
Repository: hsjoberg/blixt-wallet
License: MIT
In addition to the software projects listed above, three educational initiatives were selected for funding:
- Bitcoin Education in Nigeria is an initiative started and led by Apata Johnson. Apata's project aims to educate youths on bitcoin and the opportunities it brings for the people living in the rural areas of Nigeria.
- 21 Ideas is a project that aims to bring quality Bitcoin education to Russian citizens. Tony and others have been working for many years on translations, original material, and hands-on tutorials for beginners. We believe that education is paramount to proper Bitcoin use, and localization is paramount for everyday citizens to properly grasp the importance as well as the novel concepts of bitcoin.
- CoreDev.tech is organizing recurring developer events, which are all about bringing devs together so that they can hack on Bitcoin Core and related software.
We received hundreds of applications in the last couple of months, which is a fantastic signal and something we are delighted about. Some applications are still being reviewed by the OpenSats board, as we try our best to assess feasibility, alignment, and potential impact of each project. We will announce additional grants as applications pass our grant selection process.
Unfortunately, we were unable to fund all of the proposals that were sent to us. Please don't hesitate to apply again in case your application was rejected this time around. The applicant pool was very competitive, which is a great thing to see in and of itself.
Grants for the projects above are funded by contributions to the Bitcoin General Fund. Our operations as well as our grant programs are made possible by generous donors like you. If you want to help fund the Bitcoin ecosystem, please donate to the Bitcoin General Fund.
Our team is screening applications constantly, and we will announce new grants and funding opportunities as they arise. If you are working on an open-source project in and around bitcoin, and you think your work is aligned with the OpenSats mission, please apply for funding.
-
 @ 78733875:4eb851f2
2023-07-07 22:06:45
@ 78733875:4eb851f2
2023-07-07 22:06:45The mission of OpenSats is to support and maintain a sustainable ecosystem of funding for free and open-source projects that help Bitcoin flourish. Nostr is such a project, which is why OpenSats introduced The Nostr Fund and built a team around the protocol's originator to help fund the growing nostr ecosystem. As an open, interoperable, and censorship-resistant protocol, nostr has the chance of doing social-native networking right.
After weeks of sorting through applications, we are excited to announce the first round of grants from The Nostr Fund. OpenSats is proud to support over a dozen projects, from clients to relay implementations to adjacent tools and design efforts.
In no particular order, here they are:
- NDK by @pablof7z
- Habla by @verbiricha
- Coracle by @hodlbod
- Iris by @mmalmi
- Damus by @jb55
- rust-nostr & nostr-sdk by @yukibtc
- Nostr Relay NestJS by @CodyTseng
- Soapbox by @alexgleason
- Code Collaboration over Nostr by @DanConwayDev
- Satellite by @lovvtide
- Amethyst by @vitorpamplona
- Pinstr by @sepehr-safari
- nostr.build by @nostr.build
- Gossip by @mikedilger
- Nostr SDK iOS by @bryanmontz
- Nostr Design by @karnage
The projects above have received grants of various durations and sizes, and we have more nostr-related applications in the pipeline. Donate to The Nostr Fund if you want to help fund the nostr ecosystem.
Without further ado, let's take a closer look at each project in turn.
NDK
NDK is a nostr development kit that makes the experience of building Nostr-related applications—whether they are relays, clients, or anything in between—better, more reliable, and overall more enjoyable to work with than existing solutions. The core goal of NDK is to improve the decentralization of Nostr via intelligent conventions and data discovery features without depending on any one central point of coordination, such as large relays or centralized search providers.
Repository: nostr-dev-kit/ndk
License: MITHabla
Habla is a website for reading, writing, curating, and monetizing long-form content on nostr. It uses NIP-23 to allow markdown-formatted articles and embedded nostr content such as notes, profiles, lists, relays, badges, and more. The goal of Habla is to give everyone an alternative to centralized publishing platforms such as Medium or Substack, which are by their very nature prone to censorship and deplatforming.
Repository: verbiricha/habla.news
License: GNU GPL v3.0Coracle
Coracle is a nostr web client focusing on user experience, performance, and scaling of the nostr network beyond the "twitter clone" use-case. The end goal is to build marketplaces, groups, chat, and more on top of an emergent web of trust. Coracle is already one of the most mature and accessible clients for new users while also providing some novel features for more advanced nostriches.
Repository: coracle-social/coracle
License: MITIris
Iris is a multi-platform nostr client that is available for web, mobile, and desktop. Iris' design goals are speed, reliability, and ease of use. The client features public as well as private messaging, customizable feeds, an offline mode, and speedy account creation.
Repository: irislib/iris-messenger
License: MITDamus
Damus is a cutting-edge nostr client for iOS. The goal of Damus is to integrate bitcoin with social media and to show the power, censorship resistance, and scalability of nostr in general. Damus includes picture and video uploading, is fully translated into 24 languages, supports automatic translation of notes, and includes all of the features you would expect from a Twitter-like client.
Repository: damus-io/damus
License: GNU GPL v3.0rust-nostr & nostr-sdk
Rust-nostr is a Rust implementation of the nostr protocol. It is a high-level client library with the explicit goal to help developers build nostr apps for desktop, web, and mobile that are both fast and secure. Rust crates can be easily embedded inside other development environments like Swift, Kotlin, Python, and JavaScript, making rust-nostr a versatile base to build upon. While the project is in the early stages of development, over 35 NIPs are already supported, with more to come.
Repository: rust-nostr/nostr
License: MITNostr Relay NestJS
Nostr-relay-nestjs is a Nostr relay with a clear structure that is easy to customize to your needs. This relay implementation is based on the NestJS framework and focuses on reliability and high test coverage.
Repository: CodyTseng/nostr-relay-nestjs
License: MITSoapbox
Soapbox started out as an alternative to Mastodon but has grown to encompass ActivityPub and nostr while being interoperable with both. In February 2023, the team launched the "Mostr" bridge, seamlessly connecting nostr to the ActivityPub Fediverse and enabling bidirectional communication between both protocols. This bridge exposes over 9.4M potential users in nostr's target audience to nostr, many of whom have already left the Fediverse completely in favor of nostr.
Repository: gitlab.com/soapbox-pub
License: GNU Affero General Public License v3.0Code Collaboration over Nostr
This project is a proof-of-concept for a much-needed, often discussed, and permissionless, nostr-based GitHub alternative. The goal is to replace the traditional interactions using a centralized server or service with a nostr-based alternative centered around nostr events. Commits, branches, pull requests, and other actions are all modeled as nostr events, with permissions managed through groups so that multiple maintainers can manage a repository. This model reduces the barriers for clients to support repository collaboration and allows for interoperability between repository management tools.
Repository: DanConwayDev/ngit-cli
License: MITSatellite
satellite.earth is a web client for nostr that has a community focus and presents conversations as threaded comments, borrowing from the traditional Reddit interface.
Repository: lovvtide/satellite-web
License: MITAmethyst
Amethyst is one of the most popular nostr clients for Android. Amethyst comes with expected features such as account management, feeds, profiles, and direct messages. Amethyst also offers native image uploads, public chat groups, link previews, one-tap zaps, public and private bookmarks, as well as the ability to follow hashtags, and other novel features. You can install releases of Amethyst via F-Droid or Google Play.
Repository: vitorpamplona/amethyst
License: MITPinstr
Pinstr allows users to easily organize and discover new ideas by creating public boards of pins. Users can star, comment, and zap other users' boards. Users can find curated boards of other users and create boards themselves. Default boards include users' bookmarked content, among other lists.
Repository: sepehr-safari/pinstr
License: MITnostr.build
Nostr.build is a free-to-use media hosting service that allows users to upload images, gifs, videos, and audio files to share them as nostr events. The team recently released their code under an MIT License so that anyone might use the software to offer a similar service.
Repository: nostrbuild/nostr.build
License: MITGossip
Gossip is a fast and stable desktop nostr client focused on the Twitter-like micro-blogging aspect of nostr. Gossip follows people by downloading their events from whichever relays they post to (rather than relays you configure) and was the impetus for NIP-65. It does not use complex web technologies such as JavaScript or HTML rendering and stores your private key only in an encrypted format. Consequently, Gossip is considered more secure than other clients by some. The client is packaged and released for Linux, Windows, and MacOS.
Repository: mikedilger/gossip
License: MITNostr SDK iOS
The nostr SDK for iOS is a native Swift library that will enable developers to quickly and easily build nostr-based apps for Apple devices. The library plans to implement all approved NIPs and will follow Apple's API patterns, so that iOS developers feel comfortable using it from the start. The SDK aims to be simple in its public interface, abstracting away as much complexity as possible so that developers can focus on what makes their specific application unique.
Repository: nostr-sdk/nostr-sdk-ios
License: MITNostr Design
Nostr Design will be a comprehensive resource for designers and developers to build successful nostr products. Nostr introduces several new concepts that most people are not familiar with. Given its nature, the protocol presents some unique design challenges for developers and users alike. The Nostr Design efforts are led by Karnage, who has done stellar product design work around nostr in the past. We believe that this project has the potential to impact the entire nostr space, as it can act as a go-to source for developing quality products, addressing user needs, as well as providing concrete examples and building blocks for product designers and developers alike.
License: Public Domain, Creative Commons
We have received hundreds of applications in the last couple of weeks, many related to or exclusively focused on nostr. Most projects that applied focus on bitcoin and lightning. We will announce another wave of grants for these soon.
To all the nostr projects that applied and didn't make the cut this time around: don't be discouraged. Please apply for funding again in the future. We will announce new grants and funding opportunities quarterly, and there is always the possibility of being listed on the OpenSats website to receive pass-through donations for your project.
We are excited to support the projects above in building the tools we bitcoiners care so deeply about. The future is bright; we just have a lot of building to do.
-
 @ 000688f2:44fbd1ae
2023-08-13 00:03:31
@ 000688f2:44fbd1ae
2023-08-13 00:03:31A community of crypto enthusiasts excited about the upcoming launch of a new crypto exchange decided to run a competition to celebrate the lead up to the big day.
The concept was fairly simple, put up a prize of 25,000 X7R tokens (currently worth about $1,000) for the last person to buy X7R tokens if more then an hour had passed since the last purchase. Every time somebody buys X7R tokens, the clock is set back to zero and starts ticking towards that hour mark again.
There were lots of laughs and friendly ribbing as community members made purchases just before the hour was up to deny one their friends the prize. The hours slowly ticked by as the word began to spread that the prize was worth about USD$1,000 and that bought in a whole new wave of players.
Now some of these community members were a tad bit competitive and the hours turned into a day and so on. Suddenly members were wondering could we keep this running long enough to get an entry in the Guinness Book of Records? Rob the Bank got the ball rolling when he said:
I think it’d be epic if we kept it going for like 30 days. We could submit it to the Guinness book of world records.
Not to be outdone Adz upped the anti:
We might have 2 entries into the Guinness world record
And the community's very own professional gambler Dallas, who has never back away from a game of chance confirmed the quest:
Get Guinness world records involved.
If you want to join the quest to get be entered in the Guinness Book of Records and maybe win a $1,000 check out their Telegram Channel. Being tech nerds they have automated the whole competition with countdown clocks etc. It is very cool.
You do not have to participate, but I am sure you would have a lot of fun cheering them on and they would no doubt appreciate your moral support.
For me, I am thinking I would not mind pocketing the $1,000 prize.
This is not investment advice.
-
 @ 81870f53:29bef6a6
2023-08-12 23:58:25
@ 81870f53:29bef6a6
2023-08-12 23:58:25ゲルマニウムとガリウムは、半導体として優れた特性を持つ希少金属で、中国が世界の主要な生産国です。2020年の世界の精製ゲルマニウム生産量は約130純分トンで、そのうち中国が約66%を占めています。また、中国の金属ゲルマニウムの輸出量は29純分トンで、主な輸出先は日本、韓国、米国などです。一方、ガリウムの世界生産量は2019年に約380トンと推定されており、そのうち中国が約90%を占めています。中国のガリウムの輸出量は2019年に約120トンで、主な輸出先は日本、台湾、韓国などです。
ゲルマニウムとガリウムの需要は現時点では大きくありませんが、将来的には高性能半導体向けの用途拡大が期待されています。例えば、ゲルマニウムはPET樹脂の重合触媒や光ファイバーの屈折調整剤として利用されており、赤外線検知素子や太陽電池用の単結晶などにも応用されています。また、ガリウムは窒化ガリウムや砒化ガリウムなどの化合物半導体として利用されており、電気自動車用パワー半導体や5G通信用高周波素子などにも応用されています。
レアアース、ゲルマニウム、ガリウムに対する中国の新たな制裁は、米国、日本、EUにとって深刻な経済的打撃となる可能性がある。これらの素材は、高性能コンピューターやスマートフォンなどの先端技術に不可欠であり、中国は世界の供給の大部分を支配している。制裁は、台湾海峡や香港などの地域問題で中国と対立する西側諸国への報復措置とみられている。制裁の影響を緩和するために、米国、日本、EUは、代替的な供給源の確保や素材のリサイクルなどの対策を検討する必要がある。
これらの制裁は、スマートフォン、コンピューター、および太陽電池パネルや軍事産業など、これらの材料を使用するすべての製品の価格に影響を与えるでしょう。
読んでくれてありがとう !
この記事がお役に立てば幸いです。
もしそうなら、チップをおくるどうぞ
https://getalby.com/p/bitcap
-
 @ f821179b:ed4fd022
2023-08-12 22:43:09
@ f821179b:ed4fd022
2023-08-12 22:43:09Nbits is an amazing tool that grants us all the ability to harness the power of Bitcoin's Lightning Network. LNBits can be considered the "WordPress" for Bitcoin. A fresh install will grant you a blank slate Lightning wallet to which you may add a variety of plugins, ranging from a simple paywall to a fully functional PoS system for accepting Bitcoin payments, to your own Nostr Market stall (store) and customize LNBits to fit your needs. You can learn more about LNBits by visiting to their website at LNBits.com.
LNBits and Nostr
The people behind LNBits and those behind Nostr have a history together, and both sides played a part in the birthing of the Nostr protocol. Lucky for us! LNBits has been there for Nostr's growth and has been implementing fantastic plugins that allow us to do great things within the Nostr ecosystem. If you're new to Nostr and want to better understand it, check out our post "Nostr and Bitcoin"
Nostr Market
One of their more recent developments is the Nostr Market plugin. This lovely little app lets you create your own market stall where you can list items you'd like to sell, kind of like opening a kiosk in a public square or mall. And because this is LNBits, you have the power to easily accept Bitcoin payments for all the items for sale in your stall (kiosk). What's exciting is that this is all done over Nostr's censorship-resistant and permissionless protocol (the public square). It's all just so beautifully designed.
With this plugin, getting started with an online store has never been easier. Its intuitive marketplace client (storefront) comes complete with a shopping cart, giving you everything you need to showcase your offerings and tempt potential buyers. And, as an added bonus, the platform includes a simple messaging tool that makes it a breeze to communicate with your customers via Nostr, whether you're discussing orders or simply chatting.
Setup Your Stall
Setting up and getting started with a Nostr Market stall is quite straightforward. The plugin operates alongside another tool named "Nostr Client," which facilitates Nostr Market's interaction with the broader Nostr ecosystem. I won't delve into the setup process in this post, as I believe the Nostr Market team has already provided a comprehensive walkthrough. If you're looking for a detailed step-by-step guide on configuring everything, I recommend visiting their official GitHub page.
The guide covers everything you need from the necessary basics to the customization or the look and feel of your stall.
-
 @ f8e6c643:03328ca9
2023-08-02 15:45:25
@ f8e6c643:03328ca9
2023-08-02 15:45:25Here’s the neat part, you don’t... \n...or rather, you can’t find rare satoshis. Rare satoshis don’t exist because individual satoshis don’t actually exist within the bitcoin network, only UTXOs. \n\n## But my wallet says I have satoshis.\nAnd the container of your food says it has calories. The bathroom scale says your body has lbs/kg. The tape measure says your floors have inches/cm. These are units of measure of a property of something, but they are not distinct individual units of the thing being measured. Calories measure energy. Scales measure mass. Rulers measure distance. These are properties of a thing, but not the thing itself. \n\nLikewise, satoshis (aka, sats) are a unit of measure for bitcoin UTXOs, which are the "things" that actually exist within the bitcoin network. A UTXO, or "unspent transaction output," can be very small, only a few hundred sats, or it can be very large, hundreds of millions or even billions of sats, but there are only UTXOs measured in sats and spendable by their corresponding private keys. There are no satoshis sitting in storage in bitcoin wallets and nodes. \n\n## If that's true, then why is Bitcoin Magazine selling "rare satoshis"?\nThey are salesmen in search of profit, and not all salesmen are honest. The product they are selling misrepresents the truth. Put simply, Bitcoin Magazine is lying about what they are selling. \n\nWhat they are actually selling is a UTXO measured in some amount of sats that can be cryptographically linked to another UTXO from the past that no longer exists. Why doesn't it exist? Because a UTXO is, by definition, "unspent." Once you spend one UTXO, new UTXOs are created and mined into a new block.\n\n## So I can't buy one of Hal Finney's satoshis?\nUnfortunately, no, you cannot. At best you could pay someone like Bitcoin Magazine to spend one of their UTXOs to a new UTXO at an address you control. It is up to you to decide if the cryptographic link to previous entries in the ledger has any added value or meaning beyond the sats-denominated value of the UTXO.\n\nIt would be a little bit like if I had a dollar bill, and I went to the bank and deposited it into your account, and then the bank destroyed that physical bill and replaced it with a new one when you came in to withdraw it. While you would now possess access to the $1 of value, you would not have the dollar bill that I deposited. In fact, it no longer exists, even though there is proof on the bank's ledger of the transfer of value from me to you.\n\n## Ok, so what? I can do what i want with my money.\nYes, you can. That is the freedom afforded to you by bitcoin. You are free to trade your sats for a lesser amount of sats. It's just my opinion that you ought to at least understand that that's all you're doing. \n\n🌽 🤙
-
 @ 000688f2:44fbd1ae
2023-08-12 20:12:55
@ 000688f2:44fbd1ae
2023-08-12 20:12:55Cryptocurrency markets are complex ecosystems, teeming with opportunities for savvy traders and automated bots alike. With the advent of Decentralized Finance (DeFi), a new breed of tools and strategies has emerged, offering unique ways to navigate the crypto landscape. X7 Finance, a DeFi project boasting an innovative concept called Initial Liquidity Loans (ILLs), is one such example. Coupled with Crypto Sniper Bots, these tools can yield significant benefits. In this post, we'll explore how the X7 Finance ecosystem, including its unique Xchange Router, can enhance your crypto trading experience.
Initial Liquidity Loans: A Fresh Perspective on Liquidity Management
In the crypto world, liquidity is king. The more liquidity a pair has, the easier it is to execute trades without causing significant price slippage. However, providing liquidity requires substantial upfront capital—a challenge for many projects. Enter X7 Finance's unique solution: Initial Liquidity Loans (ILLs). This tool lets projects deploy enhanced liquidity without substantial upfront capital, reducing initial capital requirements and promoting efficient resource allocation. With a 10x loan, for example, a smart contract can deploy 10 times the initial planned liquidity, creating a more vibrant trading environment.
Crypto Sniper Bots: Playing in the Initial Liquidity Pairs
The increased liquidity brought by ILLs and the constant tradability of the liquidity pair make X7's Initial Liquidity Pairs an ideal playground for Crypto Sniper Bots. These bots, programmed to exploit price discrepancies swiftly, find fertile ground in the initial trading phases and loan default stages. They can execute rapid trades, taking advantage of the dynamic market conditions generated by the liquidity fluctuations. This can lead to increased profits for bot operators and enhanced market efficiency overall.
Loan Defaults: Ensuring Continuity and Tradeability
While the prospect of a loan default might seem alarming, X7 Finance has built-in mechanisms to handle such situations. In the event of a loan default, the assets are returned to the lending pool, allowing the liquidity pair to continue functioning. This ensures operational continuity and maintains tradeability, even during a temporary dip in price and liquidity. In this environment, Crypto Sniper Bots can continue to operate and seize opportunities arising from the changing market conditions.
Xchange Router: Amplifying Opportunities
Central to the X7 Finance ecosystem is the Xchange Router—a tool that can create and interact with liquidity pairs, and integrate seamlessly with Automated Market Maker (AMM) UI for trading and creating LPs/ILLs. By integrating the Xchange Router, projects can tap into the benefits offered by X7 Finance, including the innovative ILLs. This integration not only enhances the value proposition for projects but also amplifies the opportunities for Crypto Sniper Bots, creating a win-win situation for all parties involved.
In conclusion, X7 Finance, with its innovative ILLs, provides a unique playground for Crypto Sniper Bots, and the integration of Xchange Router presents numerous benefits for projects and traders alike. By enabling efficient liquidity management, enhancing market efficiency, and providing novel trading opportunities, X7 Finance is shaping the future of DeFi trading.
Republished with Permission Author @mikemurpher Original Article https://www.x7finance.org/blog/posts/x7-a-sniper-bot-playground
-
 @ f35ae048:d018a92d
2023-08-12 19:49:52
@ f35ae048:d018a92d
2023-08-12 19:49:52NOSTR stands for "Notes and Other Stuff Transmitted by Relays"
It's a revolutionary new open protocol that helps decentralize the web. Your data is stored across relays, instead of locked inside Googlazon™. All that's needed is a simple private 🔑 to publish or encrypt your data.
Doubtful? This page loaded from NOSTR relays.
NOSTR is incredible because: * You take your data with you * It's censorship resistant * It uses open standards * It can be anonymous
Quick Start
- https://nostr.com/clients
Exploring further
- https://github.com/nostr-protocol/nips#readme - the protocol
- https://nostr.watch/relays/find - find relays
- https://nostr.moe/ - nostr utilities
- https://nostrapp.link/ - nostr apps
- https://www.nostrapps.com/ - nostr apps
- https://github.com/aljazceru/awesome-nostr - lots more
- https://github.com/pluja/awesome-nostr-usenostr - lots more
Also, be sure to drop by and check out Pleb.to

-
 @ d34e832d:383f78d0
2023-08-08 03:14:43
@ d34e832d:383f78d0
2023-08-08 03:14:4325 Verses to Draw Motivation Within
Pray Continually
Title: Finding Motivation in Scripture: Overcoming Failure and Embracing Hope
Have you ever felt like a failure? It's a tough spot to be in, and it can really bring you down. But you know what? Scripture can be a powerful source of motivation, encouragement, and renewed hope, even in those moments when you feel like you're falling short. Let's dive into how various scriptures, including the ones we mentioned earlier, can give you that much-needed boost when you're feeling down.
1. Recognizing God's Sovereignty: You know, sometimes it's comforting to remember that we're not alone in our struggles. Scriptures like Psalm 46:10 and Isaiah 41:10 remind us that God is right there with us, holding us up and giving us strength. So, even when it feels like everything is falling apart, we can find motivation in knowing that God's got our back. His plans are bigger than our failures, and that thought alone can help us keep pushing forward.
2. Trusting in God's Guidance: It's not always easy to figure things out on our own, especially when we're feeling defeated. That's where scriptures like Proverbs 3:5 come in handy. They encourage us to put our trust in the Lord, to lean on Him and His understanding. When we feel like we're failing, we can find motivation by surrendering our worries and uncertainties to God. Trusting that He'll guide us can give us the courage to take that next step, even when it feels uncertain.
3. Embracing God's Love and Grace: You know, it's important to remember that our worth isn't defined by our failures. John 3:16 and Ephesians 2:8 remind us of God's unconditional love and the grace He extends to us. When we feel like we're falling short, these verses can be a source of comfort and motivation. They remind us that God's love remains unwavering, regardless of our achievements or mistakes. His grace gives us the opportunity for a fresh start and encourages us to keep going.
4. Finding Strength in Adversity: Hey, setbacks and failures are tough, no doubt about it. But you know what? They can also be opportunities for growth and resilience. James 1:2-4 reminds us to see trials as stepping stones toward becoming stronger individuals. When we face failures, we can find motivation by shifting our perspective. We can view these challenges as temporary hurdles on our journey to personal growth. With God's strength, we can keep moving forward, knowing that we're getting stronger with every step.
5. Cultivating a Positive Attitude: Sometimes, it's all about having the right mindset. Philippians 4:13 is a verse that reminds us we can do anything through Christ who strengthens us. Isn't that amazing? When we're feeling like failures, this verse encourages us to focus on our strengths and abilities. It's about channeling our energy into positive thinking. Instead of dwelling on our shortcomings, we can approach challenges with confidence, knowing that we have God's power within us.
When you feel like you're failing, scripture can be a powerful source of motivation and hope. By recognizing God's presence, trusting in His guidance, embracing His love and grace, finding strength in adversity, and cultivating a positive attitude, you can rise above your failures. Remember, you're not alone in this journey, and there's always hope, even in the face of failure. So, keep your chin up and let these scriptures be a source of inspiration on your path to success and fulfillment . You've got this!
-
 @ e31dfd09:04f2fb21
2023-08-12 23:06:10
@ e31dfd09:04f2fb21
2023-08-12 23:06:10
Tom Brady delivered the perfect retort when confronted with a snapshot of himself attending a Blackpink concert with his daughter. The retired NFL icon graced the K-pop sensation's Aug. 11 performance at New Jersey's MetLife Stadium, accompanied by his daughter and a clique of her friends.
On the subsequent morning, Brady, known for his humor, playfully responded to a fan-captured snapshot circulating on X (formerly Twitter). In the photo, a wide-eyed Brady stands amid enthusiastic Blinks on the floor of East Rutherford’s MetLife Stadium. His comment on the image encapsulated the quintessential "dad takes his daughter and her friends to a concert" vibe, showcasing his good-natured attitude. The quarterback extraordinaire had attended the event alongside his 10-year-old daughter, Vivian.
Since his retirement from the NFL early in 2023, Brady has devoted significant time to crafting cherished moments with his children. In July, he and his daughter embarked on an African safari, an adventure chronicled on the 46-year-old Super Bowl champion's Instagram account. Brady's familial realm includes two sons as well: 13-year-old Benjamin, from his marriage to Gisele Bündchen, and 15-year-old Jack, his child with former partner Bridget Moynahan.
Blackpink is nearing the conclusion of their Born Pink World Tour, which commenced in October to promote their sophomore album, "Born Pink," released in 2022. Notably, the album secured the top spot on the Billboard 200 chart, marking the group's maiden achievement in that regard. The album also spawned two No. 1 singles on the Global 200 chart: “Pink Venom” and “Shut Down.” As the curtain descends on their tour, Blackpink continues to bask in the glow of their musical success.
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ 78733875:4eb851f2
2023-07-07 22:04:12
@ 78733875:4eb851f2
2023-07-07 22:04:12OpenSats is pleased to announce a new long-term support (LTS) program for Bitcoin Core developers and similar Load-Bearing Internet People.[^fn-lbip] This grant program is designed to provide financial support for developers who are working on critical infrastructure for the bitcoin network.
The LTS program is a new initiative from OpenSats and is distinct from our regular grant program, which is more expansive in scope. It is also distinct from OpenSats' website listings, which allows reviewed open-source projects to receive tax-deductible donations via OpenSats. The LTS program is specifically designed to provide long-term support for developers who are working on critical open-source infrastructure in and around bitcoin.
Having a longer time horizon than regular grants, the LTS program is geared towards long-term stability for grantees, with a minimum grant duration of 12 months and possible grant durations of two years or longer. This will allow developers to focus on their work without having to worry about financial constraints.
To be eligible for the LTS program, applicants must:
- have a track record of quality contributions
- be mission-driven and self-motivated
- be able to work in public
- be bitcoin-only
Applications for the LTS program are now open: https://opensats.org/apply/
The first recipient of an OpenSats LTS Grant is Marco Falke, a long-term maintainer and contributor of Bitcoin Core with thousands of contributions over many years. Marco will continue to focus on testing and quality assurance, as well as maintenance and review, helping to make sure that the Bitcoin Core software is as solid as it can be. You can read more about his contributions here.
We appreciate all the hard work that goes into building and maintaining critical open-source infrastructure. It is a hard and often thankless job. We hope that we can play a role in closing the gaps in bitcoin open-source funding, and we look forward to working with contributors in the future.
OpenSats aims to be an additional pillar of the increasingly solid funding landscape in and around bitcoin. We have learned a lot from the programs of the past and aim to join Brink, Spiral, Chaincode, HRF, and other successful grant programs to support those who build the tools that ensure the protection of individual liberties in our digital world.
We are committed to supporting the development of bitcoin. The LTS program is a new way for OpenSats to support long-term contributors who are building, maintaining, testing, researching, and reviewing critical software.
We encourage all qualified developers to apply for the LTS program. Together, we can build a stronger and more resilient bitcoin network.
[^fn-lbip]: "An LBIP is a person who maintains the software for a critical Internet service or library, and has to do it without organizational support or a budget backing him up." —Eric S. Raymond
-
 @ e31dfd09:04f2fb21
2023-08-12 22:49:44
@ e31dfd09:04f2fb21
2023-08-12 22:49:44Fostering Compassion and Empathy: Nurturing the Heart's Deepest Connections
In a world that often races ahead, propelled by the forces of technology and progress, there exists a timeless and essential practice—a practice that binds us in our shared humanity, transcending borders, backgrounds, and beliefs. This practice is the art of fostering compassion and empathy—a powerful force that has the ability to transform lives, mend wounds, and create a tapestry of interconnected souls.
The Essence of Compassion and Empathy: Compassion and empathy are intertwined threads of emotion and understanding. Compassion is the tender embrace of another's suffering or joy, acknowledging their experiences with an open heart. Empathy, on the other hand, is the act of stepping into another's shoes, feeling their emotions, and seeing the world through their eyes.
The Ripple Effect of Kindness: Like pebbles dropped into a tranquil pond, acts of compassion and empathy send ripples that reverberate far beyond their origin. A kind word, a comforting gesture, or a listening ear can uplift spirits, heal wounds, and create a chain reaction of positivity that spreads through communities and across continents.
Cultivating a Culture of Understanding: Fostering compassion and empathy begins with embracing diversity and seeking to understand the experiences of others. By opening ourselves to different perspectives, cultures, and backgrounds, we cultivate an environment where empathy flourishes and bridges of understanding are built.
A Healing Balm for Emotional Wounds: Life's journey is replete with moments of pain, loss, and heartache. In these times, compassion and empathy become a healing balm, offering solace and support to those in need. The simple act of being present, offering a shoulder to lean on, or sharing a heartfelt connection can alleviate the burden of suffering.
Breaking Down Barriers: Compassion and empathy dismantle the barriers that divide us. They transcend differences and create common ground, reminding us of our shared human experience. Through these qualities, we build bridges of connection that enable us to relate to one another on a fundamental level.
Empowering Connection in Relationships: In the realm of relationships, compassion and empathy act as powerful tools for building intimacy and trust. By truly understanding and validating each other's feelings, we forge bonds that are unbreakable and authentic. These qualities enable us to navigate conflicts with grace and understanding.
Nurturing the Seeds of Social Change: History is a testament to the transformative power of compassion and empathy in driving societal progress. Movements rooted in empathy—whether advocating for human rights, social justice, or environmental preservation—have reshaped the world, reminding us of the extraordinary impact that even a single act of compassion can have.
A Practice of Mindfulness and Presence: Cultivating compassion and empathy requires a mindful presence—a willingness to fully engage with the present moment and the experiences of others. By actively listening and being attuned to the emotions of those around us, we create an environment where empathy thrives.
The Legacy of a Compassionate Heart: The legacy of a life steeped in compassion and empathy is one that endures through generations. It leaves an indelible mark on the lives it touches, inspiring others to follow in its path. As we practice compassion and empathy, we contribute to a world that is kinder, more understanding, and profoundly interconnected.
In a universe that often seems vast and unknowable, the practice of fostering compassion and empathy brings us back to our shared humanity. It teaches us that, at our core, we are all connected by threads of emotion and experience. As we cultivate these qualities, we infuse our lives with meaning, purpose, and a deep sense of belonging—to a world where hearts are open, souls are understood, and the beauty of our collective journey is embraced.
-
 @ 20986fb8:cdac21b3
2023-07-29 06:45:23
@ 20986fb8:cdac21b3
2023-07-29 06:45:23YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.\n\nAs an incentive, participants can earn up to 100,000 SATs.\n\nRound 2 will be from 27th to 30th July\n\n### How to participate:\n1. Pick one or multiple Updates below, test it (them)\n2. Write your feedback and opinion (pros and cons are all welcomed)\n3. Post your article on Nostr via YakiHonne.com\n4. Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne\n5. Share the link to our group: http://t.me/YakiHonne_Daily_Featured\n5. Be Zapped!\n\n### Requirements:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion\n5. The top 10 posts will be zapped during each round.\n6. The evaluation will based on the article's depth, completeness, and constructiveness. \n7. Contact us for additional zaps if bugs are found.\n\n\n\n\n### Updates to be tested in Round 2:\n1. Comments: re-implemented and comments can be deleted\n\n2. NIP-25 supporting: users now can upvote and downvote\n\n3. Zap stats: Zaps sent and Zaps received can be seen from users profiles\n\n4. “login with an extension” button: now it is grayed out rather than invisible\n\n5. Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme\n\n6. Tags: click on the tags in the article to view the content under the tag\n\n7. Share: sharing posts with one click\n\n8. NIP-05: verify your profile\n\n\n\n### If you missed Round 1, the updates below could be tested as additions:\n\n1. Comment function: more user-friendly\n\n2. Stats area: clearly displays the interactive status of each article\n\n3. Following function: generated-key users can also be followed\n\n4. Curation function: easily add or remove articles from an existing curation\n\n5. Tags: search and browse articles with the tags\n\n6. Home feed scrolling pagination: optimized data fetching and faster loading time\n\n7. Article editing preview: preview the final version of the article while writing in MarkDown\n\nDon't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n
-
 @ 1c52ebc8:5698c92a
2023-08-05 18:59:53
@ 1c52ebc8:5698c92a
2023-08-05 18:59:53Hey folks, happy Saturday!
Thanks for all the support last week with the first attempt at a “this week in Nostr” newsletter, feedback is very welcome 🙂
The hope for this newsletter is to be technically focused (new NIPs, notable projects, latest debates, etc) and a way for folks to keep up with how the community and the protocol is developing.
Recent NIP Updates
1) Calendar Events 📅
Early this week Calendar Events got added as a new NIP, so now we have a standard way to create calendars and calendar events in a way that can be shared via Nostr. Looks like we’ll be able to kick Meetup and Eventbrite to the curb soon!
2) Proxy Tags (Proposed) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. If this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
This has the approval of many folks including @fiatj so I bet we’ll see it merged soon.
Notable projects
NostrDB: shipped! 🚢
Mentioned last week, but shipped this week: NostrDB is an embedded relay within the Damus app built by @jb55 built to improve performance and make new features easier. By having a relay inside the client, the client gets far more efficient with pretty much everything. It’s a standalone project so I imagine many clients could adopt this and reap the benefits.
As he mentions in the announcement, it has enabled Damus to recommend follows, as well as speed up many resource intensive operations in the app. Definitely feels snappier to me 💪
Stemstr 🎵
Shipped this week, Stemstr is a way to connect with people over music. There seem to be budding collaboration tools as well meaning the music on stemstr is constantly evolving and being reshared. Quite an impressive project.
Relayable 🌍
One of the underrated challenges of using Nostr right now is curating your relays. For the snappiest experience in your clients, speed is important! Many relays are hosted around the globe but it’s not easy to keep track of that.
Relayable is a relay you can add that will automatically find the closest, fastest, reliable relay to you get you connected so you can get your notes as fast as possible. Really neat project, I’ve added that relay and it’s worked great
Ostrich.work ⚒️
A job board that runs on Nostr for Nostr-related jobs. Definitely check it out if you’re looking to work on Nostr projects or need to find someone to work with you on the same!
Secret Chats on Iris 🤫
DMs on Nostr aren’t entirely private because we’re still publishing the metadata about the DM on publicly accessible relays even if the content is encrypted. There’s been a desire to implement more secure chats through the Nostr protocol, there’s even a bounty from Human Right Foundation about it.
Looks like Iris pushed support for their take on secret chats, looking forward to people telling the community how they like it.
Learn to dev on Nostr course 📖
If you’re looking to get started building on Nostr, or just curious how it works under the hood, here’s a course that was put together just for you! It’s about 40 minutes long and it starts assuming no knowledge about Nostr.
Latest debates
DMs 🔒
DMs on Nostr (using the original NIP 4 protocol) isn’t very private, and there’s a desire from a large group on Nostriches to fix that natively in Nostr. Some folks are ok to leave it “unfixed” in Nostr and use protocols like Simplex because Nostr doesn’t have to solve all problems. Many ofthers thinks we can have our cake and eat it too with some effort on the Nostr protocol.
The debate rages on! I hope you weigh in wherever you see the discussion, your voice may help the community get to clarity.
Email notifications
Much of the world still relies on email to get notified about what’s happening across their various apps and services when they’re not regularly logging in. @karnage@snort.social believes it may help adoption of Nostr if there was a client that allowed users that opt-in to get email notifications for activity happening on Nostr.
There are other folks that feel like it wouldn’t be useful and in fact could make Nostr feel more spammy. I saw another thought that Nostr should be fairly self contained so bridges to other protocols (email being one) would pollute the network. It’s an interesting debate.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual). If you wanna see something here please let me know! (DMs welcome) - Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week but I hope the one in Chiavenna, Italy went well this week 🙂
Until next time 🫡
I realized this week I should be tagging each major contributor/author of each of the notable projects. I'll keep track of that from now on, so I can tag the people doing the awesome work in our community.
If I missed anything else, let me know, DMs welcome.
And to shamelessly rip off my favorite youtuber’s signoff “God bless, you’re super cute”
-
 @ 20986fb8:cdac21b3
2023-07-29 06:44:43
@ 20986fb8:cdac21b3
2023-07-29 06:44:43A long-term Nostr Creation Grant, with a 17,500,000 SATs funding pool\n\n\nRound 3 starts on 22 July till 5 Aug!\n\nCreating for You and Your Fans through Nostr and ZAP.\n\nNostr is a simple, open and censorship-resistant protocol, the number of users has been growing, and more and more users use zap to tip content. Nostr's growth over the past six months is amazing, which is a great encouragement for all nostrians. This is also a great encouragement for content creators. Earn SATs by posting your creations on nostr, allowing your readers to encourage better content creation while tipping your creations.\n\n\n
 \n
\n \n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n
\n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n \n\n\n\n\n
\n\n\n\n\n \n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n
\n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n -
 @ 1c52ebc8:5698c92a
2023-07-29 17:58:50
@ 1c52ebc8:5698c92a
2023-07-29 17:58:50Hey folks, let’s take a shot at this. If folks find this helpful, this will become a weekly summary of what’s happening in Nostr.
The intention is for it to be technically focused (new NIPs, new projects, new bounties, etc) and a way for folks that aren’t terminally online / on-nostr to be able to keep up with what’s going on.
Let’s dive in!
Recent NIP Updates
1) Long form content
Looks like there’s some activity around long-form content. Recently a few updates to various NIPs added the expectation that relays and clients support drafts of long-form content. That way folks can save their drafts without a client having to save in some way other than a relay. 💪
2) NIP 99: Classified listings
This NIP was accepted July 18, 2023 and outlines a new kind of note that will help Nostr clients to build Craiglist competitors natively in Nostr. 💲
Notable projects
Human Rights Foundation Bounties
A series of bounties to add capabilities to the Nostr ecosystem.
NostrDB: under development
A nostr-specific database that @jb55 is building to improve performance of the Damus iOS app
NJson: a JSON parser for Nostr events
A parser for JSON that’s specific to Nostr Event JSON. It’s wayyyyy faster. Great foundationally pattern/tool to improve all nostr clients and relays.
Data vending machines
This one was a mind bender and a new concept to me. But @pablof7z introduced having bots compete to accomplish tasks. The person that’s hiring for the task sets the terms and can accept a bid on whatever dimension they care about.
This could be used for things as simple as answering a question you’d previously use Google for, or curating a Nostr feed based on your interests.
Highlighter
Highlighter is a way to highlight content from anywhere and wrap that highlight as a nostr event. Which means that people can interact with this content like any other note: reactions, reposts, zaps, etc.
Seems like it could become a way to discover quality content by following folks that are digging into topics you’re interested in. Lots of ways to use this 🤯
Habla.news
Habla.news has built a way for people to draft and publish long form content in a familiar way. The interface supports rich text editing and other nice features of products like Medium.
Best part is that it publishes to your relays, so any client that supports long form content events will showcase your work (and make it zapable ⚡). For now I’ve only seen Damus (the iOS app) support long-form notes natively, but I’m sure more are incoming 💪
Latest debates
Nostr for everything vs narrow, powerful nostr
Seen a few of these debates lately, I imagine it’s just the beginning.
With protocols there’s a temptation to make that protocol support the capability to do everything. On the other hand, a protocol that can do anything isn’t particularly useful.
Nostr is still evolving though and no one is an authority on what IS and IS NOT Nostr. Can’t wait to see folks hash it out.
Build requests / ideas
I’m gonna collect the features / build requests I see throughout the week and post them here for anyone that has the cycles and interest to build what the community is asking for.
If you have something you want put here, let me know! (DM’s are welcome)
- @jb55 = nuke all events client (to clean up a relay or your wipe your account)
- @jb55 = nostr-based email client
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual). If you wanna see something here please let me know! (DMs welcome)
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Meet up in Chiavenna, Italy August 3rd
Until next time 🫡
If I missed anything, let me know, DMs welcome.
And to shamelessly rip off my favorite youtuber’s signoff “God bless, you’re super cute”
-
 @ e31dfd09:04f2fb21
2023-08-12 22:45:35
@ e31dfd09:04f2fb21
2023-08-12 22:45:35The Art of Self-Reflection: Navigating the Inner Landscape for Growth and Clarity
In the hustle and bustle of modern life, where distractions are aplenty and time is a precious commodity, there exists a quiet sanctuary—an art form that invites us to pause, turn inward, and embark on a journey of profound discovery. This art is none other than the practice of self-reflection—a timeless endeavor that holds the key to unlocking our true selves, fostering personal growth, and gaining a deeper understanding of the intricate tapestry of our lives.
The Essence of Self-Reflection: Self-reflection is a conscious and deliberate act of introspection—an opportunity to examine our thoughts, emotions, actions, and experiences. It is a practice that transcends the mere recounting of events; it delves into the realm of understanding why we think, feel, and behave the way we do.
Cultivating the Space for Introspection: In a world that constantly demands our attention, finding the space for self-reflection can be a challenge. Yet, this practice necessitates carving out moments of solitude and silence. Whether through meditation, journaling, or simply taking a mindful walk, these pockets of stillness become fertile ground for self-discovery.
Unveiling the Layers: Self-reflection is akin to peeling back the layers of an onion, revealing the core essence beneath. As we delve deeper, we may unearth long-held beliefs, biases, and assumptions that have shaped our worldview. By confronting these layers, we create room for transformation and growth.
A Mirror to Our Emotions: Emotions, both fleeting and profound, are the colors that paint the canvas of our lives. Self-reflection offers a mirror to these emotions, enabling us to understand their origins and effects. This awareness empowers us to respond rather than react, cultivating emotional intelligence and resilience.
Gaining Clarity Amid Chaos: Life's complexities often leave us entangled in a web of decisions and dilemmas. Self-reflection serves as a lighthouse, guiding us through the fog of uncertainty. By scrutinizing our goals, values, and aspirations, we can align our choices with our authentic selves, finding clarity amidst the chaos.
The Catalyst for Personal Growth: True growth is a continuous journey—one that thrives on self-awareness. Through self-reflection, we identify areas for improvement and recognize patterns that may hinder our progress. By acknowledging our strengths and weaknesses, we lay the groundwork for intentional self-improvement.
Fostering Compassion and Empathy: As we engage in self-reflection, we develop a profound sense of empathy—both towards ourselves and others. By recognizing our own vulnerabilities and struggles, we become more compassionate observers of the human experience, fostering deeper connections with those around us.
Cultivating Resilience in the Face of Adversity: Life's trials and tribulations often serve as mirrors, reflecting our inner strength and resilience. Self-reflection allows us to extract lessons from adversity, transforming challenges into opportunities for growth. By reframing setbacks as stepping stones, we harness the power of resilience.
A Lifelong Practice: The art of self-reflection is not a destination, but a lifelong practice. Just as an artist hones their craft over time, we refine our ability to engage in meaningful introspection. As we navigate the ever-changing landscapes of our lives, self-reflection becomes an unwavering compass, guiding us towards authenticity, purpose, and fulfillment.
In a world that constantly beckons us outward, the art of self-reflection calls us to turn inward—to explore the uncharted territories of our minds and hearts. Through this introspective journey, we unearth the gems of self-awareness, resilience, and growth. Like a masterpiece in the making, self-reflection crafts a life that is not only lived, but deeply understood, embraced, and enriched.
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ d830ee7b:4e61cd62
2023-08-11 05:47:04
@ d830ee7b:4e61cd62
2023-08-11 05:47:04ผมเกิดและโตในยุค 90’ ยุคเปลี่ยนผ่านทางเทคโนโลยีและวัฒนธรรมคาบเกี่ยว ได้เห็นวิวัฒนาการของสังคมในหลายๆ ส่วน โดยเฉพาะสิ่งที่เรียกว่า “Community” ที่ในอดีตไม่ได้มีกฏเกณฑ์หรือรูปแบบอันชัดเจนอย่างในปัจจุบัน.. ผมเกิดและโตในชนบทอันห่างไกลความเจริญ เรื่องราวและวิถีชีวิตที่จะเล่าจากนี้ไปก็จะขึ้นกับมุมมองหรือเลนส์ของผมเพียงคนเดียว

คอมมูนิตี้ในอดีต
ในความหมายแบบไทยๆ ที่ผมอยากจะบัญญัติมันเสียเอง มันเริ่มจากภาพของเด็กวัยกระโปกที่จับกลุ่มทำกิจกรรมสนุกสนานเฮฮากัน เล่นสนุกด้วยจุดมุ่งหมายและจิตใจอันบริสุทธิ์ ในยุคของผมนั้นการปั่นจักรยานไปเรื่อยๆ กับกลุ่มแก๊งค์เพื่อนๆ เป็นกิจกรรมสุดโปรดพอๆ กับเด็กทุกวันนี้รวมตัวกันเล่น ROV หรือ ROBLOX เลยก็ว่าได้
การผจญภัยของเด็กๆ มักจะมีกิจกรรมสุดท้ายรอพวกเขาอยู่ มันอาจเป็นการลงเล่นน้ำตามลำคลอง หนอง บึง หรือปีนต้นไม้เพื่อความเท่ สำรวจโลกเพื่อเรียนรู้อะไรบางอย่าง มันก็สนุกในแบบของมัน
เมื่อโตขึ้นมาในวัยมัธยม เด็กผู้ชายเริ่มเกาะกลุ่มกันเหนียวแน่น พวกเขาโตมาด้วยกันผ่านอะไรด้วยกันมามาก ความสัมพันธ์นั้นแน่นแฟ้นระดับยอมตายแทนกันได้ มันไม่มีสถานที่จัดเตรียมไว้ให้เรา ดังนั้นพวกเราต้องเลียบเลาะเสาะหาสถานที่สุมหัวคุยกันเอาเอง หัวข้อสนทนาในยุคนั้นไม่มีอะไรที่ไปไกลเกินกว่าประสบการณ์ที่พวกเขามี หรือเรื่องที่เคยได้เรียนมา รวมทั้งสื่อเพียงไม่กี่อย่างที่เข้าถึงได้ วิทยุและโทรทัศน์
ผู้ใหญ่ วัยทำงาน ไม่ได้มีรูปแบบสังคมอย่างวัยรุ่น กลุ่มสังคมของพวกเขานั้นเป็นวงเล็กๆ บ้านใกล้เรือนเคียง มานั่งรวมตัวพูดคุยกันทั่วไปในเรื่องสัพเพเหระ ชีวิตสโลว์ไลฟ์ที่ไม่ได้มีความเร่งรีบอะไร บางกลุ่มตั้งวงเหล้าใส่กันแต่เช้า ล้มหมู ล้มวัว ทำกับแกล้มสรวนเสเฮฮา อีกกลุ่มก็เข้าวัดฟังธรรมตามประเพณีปฏิบัติสืบต่อกันมา คนในอดีตราว 20-25 ปีก่อนในท้องถิ่นของผมนั้น ไม่ได้มีความเครียด ไม่ได้รับรู้ถึงความโสมมอะไรที่หยั่งรากลึกอยู่ภายในระบบเลย คำว่า Toxic คืออะไร? พวกเขาคงนึกถึงยาฆ่าหญ้า
เงิน ในวันที่ยังมีคุณค่าทำให้พวกเขามีความสุข ผมอดนึกถึงภาพเหล่านั้นไม่ได้จริงๆ

โลกเสมือนที่ใหญ่กว่าโลกแห่งความจริง
คอมมูในแบบที่ผมประทับใจที่สุดและดูซีเรียสจริงจังที่สุดเห็นจะเป็น “สภากาแฟ” ประจำหมู่บ้านหรือในตลาด ร้านกาแฟโบราณแบบในภาพยนตร์ยุคเก่า หลายคนคงพอนึกออก กลุ่มคอมมูนี้จะสนใจเหตุบ้านการเมือง อ่านหนังสือพิมพ์จนกระดาษขาด ฟังรายงานข่าวกันแต่เช้า ถกกันดุเดือดเหมือนเป็นอีกโลกนึงเลยทีเดียว และสภากาแฟแบบนี้นี่แหละที่ผมชอบไปนั่งฟังมากที่สุด ด้วยความที่ผมเป็นเด็กชอบเรียนรู้อะไรใหม่ๆ เรื่องต่างๆ ที่ผู้ใหญ่คุยกันมันช่างทำให้ผมสมองงอกมากจริงๆ
ตัดภาพ Fast forward กลับมาในยุคปัจจุบัน เราแทบไม่ได้เห็นกลิ่นอายหรือบรรยากาศอะไรแบบนั้นอีกแล้ว คอมมูนิตี้บนโลกแห่งความจริงมันดับสลายไปสูญสิ้น ผู้คนอพยพไปใช้ชีวิตกันบนโลกออนไลน์จนอาจิณ แม้ตัวพวกเขาเองผมก็คิดว่าคงไม่รู้สึกตัว เราหลุดจากโลกความจริงไปไกล เราหลงไปกับข้อมูลที่ส่วนใหญ่เป็นการล่อลวง สนตะพายจมูกลากจูงพวกเราไปทางไหนก็ได้ น่าเศร้าเหลือเกิน..
ตีวงให้แคบเข้ามาในสังคมการลงทุนโดยเฉพาะในแวดวงบิตคอยน์ ผมพบเห็นเพียงสื่อส่วนใหญ่ที่ชี้นำและชักพาผู้คนเข้าสู่คอมมูนิตี้ด้วยเป้าหมายสำคัญคือ “เงิน” และ “ความร่ำรวย” ผมคิดไปเองว่าเจ้าของสื่อก็คงจะไม่รู้ตัวเองเช่นกันว่ากำลังโดนสนตะพายจมูกอยู่โดยใครสักกลุ่มหรือใครบางคน ทั้งหมดนี้จะไม่ช่วยให้ใครเก่งพอจะเอาตัวรอดหรือปรับตัวได้เองในชีวิตการลงทุน มันไม่ทำให้หลายคนเข้าใจแก่นแท้หรือธรรมชาติของตลาดทุนอย่างแน่นอน เมื่อคนส่วนใหญ่ภายในคอมมูนิตี้ถูกชักพาในไปทิศทางนั้น บทสนทนาที่เราจะพบได้อย่างเดือนดาดบนโลกโซเชียลก็คงเป็นข่าวความเคลื่อนไหวระยะสั้นที่ส่งผลต่อราคาสินทรัพย์ พัฒนาการไร้สาระที่เอามาปลุกปั่นให้ดูดี พฤติกรรมการอวดไลฟ์สไตล์ อวดร่ำอวดรวยของอินฟลูเอนเซอร์ ที่ถูกหลอกมาอีกทีว่าควรสร้างภาพให้ดูน่าเชื่อถือ น่าเศร้ามากจริงๆ
มองหาที่ทางของตัวเอง
ผมเชื่อลึกๆ นะว่า บิตคอยเนอร์ในยุคหลังๆ ที่ยังไม่ผ่านสักไซเคิลมักจะรู้สึกอึดอัด หงุดหงิดเวลาต้องการ “คนคุยด้วย” ในชีวิตจริง มันไม่มีอีกแล้วกลุ่มปั่นจักรยานล่ากิ้งก่า กลุ่มสุมหัวที่ปลายนา หรือสภากาแฟ มันเหลือเพียงโลกออนไลน์ที่ต้องไปอยู่ท่ามกลาง Anonymous ร้อยพ่อพันแม่ กลางผู้คนที่ตัวเราเองก็ยากที่จะแสดงออกหรือเปิดใจ..
“คุยบิตคอยน์กับใครก็ไม่รู้เรื่อง” มันเรื่องปกติ.. ปกติจริงๆ ประสบการณ์การป้ายยาส้มแบบเฟลๆ น่าจะเคยเกิดขึ้นมาแล้วกับพวกเราทุกคน จุดนี้เองที่ผมตระหนักได้ว่า คนชอบเรื่องเดียวกันก็ควรได้คุยกับคนประเภทเดียวกัน อย่างน้อยก็ชื่นชอบเรื่องเดียวกันก็ยังดี ส่วนหน้าตาหลังการรวมตัวกันจะออกมาเป็นยังไงก็ปล่อยให้สังคมมันปรับตัวของมันไปเองอย่างออแกนิกก็แล้วกัน
“จับกลุ่มคุยกันเรื่องบิตคอยน์” มันเป็นที่มาของไอเดียแบบแนวๆ รายการ “สภายาส้ม” จนล่าสุดเราพึ่งมี “สภายาม่วง” ที่แคแรคเตอร์แตกต่างกันพอสมควร มันเป็นการสนทนากับบนโลกสีม่วงที่แต่ละคนจะได้เป็นตัวของตัวเองแบบไร้การปรุงแต่ง ได้คุยในสิ่งที่อยากคุย ได้เล่นกับคนในแชท ได้หัวเราะแบบที่ไม่ต้องกั๊ก ได้ทำเรื่องน่าอายแต่สนุกชิบหายเลย
ผมเล่ามาถึงตรงนี้ อย่าเข้าใจผิดว่าผมลากมาตบด้วยการขายของ ผมแค่กำลังจะบอกว่า.. สภาแบบนี้มันไม่เห็นจำเป็นต้องรอให้ Right Shift ทำ ลองจินตนาการสิว่า มันมีสภาแบบนี้อยู่ที่หมู่บ้าน ตำบล อำเภอ หรือจังหวัด หรือภูมิภาคของคุณเอง เช่น สภาชลบุรี, สภาขอนแก่น, สภาน่าน หรือสภายาส้มเขาใหญ่ ฯลฯ
มันเป็นไปได้นะ.. คำถามคือเราจะสร้างสภาแบบนั้นขึ้นมายังไง.. ก็ใช้ประโยชน์จากสื่อโซเชียลมีเดียที่เรามีนี่แหละ ประกาศตามหาพวก ทำความรู้จัก นักเจอกัน เริ่มจากเหตุการณ์เล็กๆ จุดเริ่มต้นน่ารักๆ นำไปสู่วัฒนธรรมสังคมอันยิ่งใหญ่แบบที่พวกเราทำกันมาแล้วนั่นไง
ผมอยากเห็นอะไรแบบนั้น อยากให้มีภาพความประทับใจจากหลายๆ พื้นที่มาอวด มาโชว์ มาแบ่งปันกัน มันก็ดีกว่าการเช็คอินสถานที่ต่างๆ ที่ตัวเราเองก็ไม่เห็นเคยอินกับมันเลย..
รออยู่นะ.. สภายาส้ม สภายาม่วง ทั่วไทย
-
 @ e31dfd09:04f2fb21
2023-08-12 22:40:28
@ e31dfd09:04f2fb21
2023-08-12 22:40:28The Journey of Personal Growth and Self-Discovery: Navigating the Path Within
In the intricate tapestry of human existence, there exists a profound quest—an odyssey that traverses the realms of personal growth and self-discovery. This journey, guided by introspection, resilience, and the pursuit of understanding, is a transformative expedition that holds the potential to unlock the depths of our true selves.
Embarking on the Quest: The journey of personal growth and self-discovery is an inner pilgrimage that invites us to explore the landscapes of our emotions, thoughts, and experiences. It is a quest that defies linear progression, often resembling a winding path marked by twists, turns, and unexpected revelations.
The Crucible of Challenges: At the heart of this voyage lies the embrace of challenges—obstacles that become catalysts for transformation. Adversities, setbacks, and moments of uncertainty act as mirrors reflecting our strengths and weaknesses, urging us to delve deeper into our psyche and confront our fears.
 The Art of Self-Reflection:
Self-discovery requires a willingness to engage in profound self-reflection. It's a practice of peeling back the layers of conditioning, expectations, and societal influences to reveal the essence of who we truly are. In moments of solitude, we gain insight into our dreams, desires, and aspirations that may have long been buried beneath the noise of daily life.
The Art of Self-Reflection:
Self-discovery requires a willingness to engage in profound self-reflection. It's a practice of peeling back the layers of conditioning, expectations, and societal influences to reveal the essence of who we truly are. In moments of solitude, we gain insight into our dreams, desires, and aspirations that may have long been buried beneath the noise of daily life.Nurturing Personal Growth: The journey isn't solely about uncovering our core identity; it's also about nurturing personal growth. Growth manifests through the acquisition of new skills, expanding our knowledge, and embracing change with open arms. It is through growth that we evolve, adapt, and become more resilient in the face of life's challenges.
Embracing Vulnerability: In the quest for self-discovery, vulnerability becomes a source of strength. Sharing our stories, fears, and aspirations with others allows for connection and empathy. Vulnerability fosters authentic relationships, reminding us that we are not alone in our journey.
Cultivating Mindfulness and Presence: Mindfulness—being fully present in the moment—is a cornerstone of the journey. Through mindfulness, we become attuned to our thoughts, emotions, and sensations. This heightened awareness enables us to make conscious choices, break patterns, and align our actions with our true selves.
The Ripple Effect: As we embark on the journey of personal growth and self-discovery, the impact extends beyond our own lives. Our transformation ripples outward, inspiring others to embark on their quests, fostering a collective movement towards greater self-awareness and authenticity.
A Continual Voyage: The journey of personal growth and self-discovery is not a destination; it is a lifelong expedition. Just as nature evolves with the changing seasons, so too do we transform with the passage of time. Each experience, whether joyous or challenging, contributes to the ongoing narrative of our personal evolution.
In the grand narrative of existence, the odyssey of personal growth and self-discovery is a testament to the complexity and beauty of the human spirit. It is an exploration that unveils the unique tapestry of our being—one woven with threads of resilience, vulnerability, and the unwavering quest for truth. As we navigate this profound voyage within, we unearth the gems of wisdom and authenticity that guide us towards a more fulfilling and meaningful life.
-
 @ 908d47b6:a2bf38ad
2023-08-12 15:55:13
@ 908d47b6:a2bf38ad
2023-08-12 15:55:13With its Wombat smartphone app, Womplay offers an easily accessible way to earn cryptocurrencies by playing games. In addition to some mini games, there are also smartphone and desktop games to choose from. There are always new challenges and missions with different rewards. For playing and reaching milestones you will initially receive Wombucks. You can exchange these for EOS, WAX or pBTC and have them sent to your wallet. You also have the opportunity to earn NFTs. These can in turn be used to play games and earn even more cryptocurrencies.
Overall, Womplay offers a very simple user experience and an entire ecosystem of games, apps and wallets. Just right to enter the world of cryptocurrencies and NFTs with little risk. A considerable collection of NFTs can be gathered within a year.
The Wombat App offers many functions and DApps that you can use directly. You can also set up a variety of wallets and admire your NFT gallery. Overall, Womplay offers a very easy entry into the world of play-to-earn. Want to learn more about play to earn? Visit our blog here
What are you waiting for? Its never to early to start earning cryptocurrencies!
-
 @ d830ee7b:4e61cd62
2023-08-09 17:22:10
@ d830ee7b:4e61cd62
2023-08-09 17:22:10สองคนนี้รู้จักกันเพราะคุยเรื่องบิตคอยน์กันแน่ๆ เลย?
ถ้าผมบอกว่าเราคุ้นเคยกันมากขึ้นเพราะ "เกมส์" คุณจะเชื่อไหม?
ย้อนกลับไปในช่วงเปิดตัวหนังสือ The Bitcoin Standard ฉบับแปลไทยของ อ.พิริยะ นั่นคือเหตุผลแรกที่ผม ซึ่งเป็นใครจากไหนก็ไม่รู้ ทักไปหา อ.ตั๊ม ครั้งแรก..
"ผมเอาเล่มนึงคับ"
ก็คงเป็นการ Approach แบบที่ใครเค้าก็ทำกัน พวกคุณก็คงพอเดาได้ แต่คุณคงเคยเห็นมาแล้ว บัญชีโซเชียลมีเดียแต่ละแอปของเขาน่ะ การแจ้งเตือนมัน 999+ ตลอด ผมไม่คิดว่าจะมีใครโชคดีได้ป๊ะได้คุยตั้งแต่ทักเขาครั้งแรก
ใช่ครับ.. ผมรอครึ่งปีเพื่อให้ถึงจังหวะโอกาสที่เขาต้องตอบผมแน่ๆ ก็ตอนขายหนังสือนี่แหละ..
ไม่มีอะไรมากมาย ผมมีแนะนำตัวเล็กน้อยว่าผมเป็นแอดมินเพจ CryptoNize (ที่ตอนนี้เลิกทำไปแล้วล่ะ) ผมชื่นชอบบิตคอยน์ และติดตามมานาน บลา บลา บลา
แต่สิ่งหนึ่งที่ผมต้องใช้ความกล้าอย่างมาก และต้องทำทันทีคือการ "Declare" บอกกับเขาตรงๆ ว่าผมอยากร่วมทำบางอย่างเพื่อตอบแทนสิ่งที่เขาทำทั้งหมดด้วยการช่วยทุกอย่างเท่าที่เขาจะอนุญาต โดยเฉพาะการสร้าง Bitcoin Network ในไทย ก็ถ้าไม่ใช่โอกาสนี้ก็ไม่รู้จะทำตอนไหนละ
เอ่อ.. ผมคิดว่าตอนนั้น อ.ตั๊ม ก็คงจะงงๆ แบ่งรับแบ่งสู้ อะไรของมึงวะหมอนี่..
จริง ๆ มันเริ่มมาจากการที่ผมสังเกตมานานแล้ว และคิดเรื่องนี้ในหัวมาตลอด ผมเองก็เป็นคนนึงที่อยากทำให้ในไทยมีฐานความรู้เกี่ยวกับบิตคอยน์ภาษาไทยมาตั้งแต่ต้น
ผมหลงเข้าดงชิตคอยน์ในก้าวแรกสู่ตลาดคริปโต เดชะบุญที่ผมอยู่กับการศึกษาวงการลงทุนมานาน หลายสินทรัพย์ที่ผมรู้จักดี ผมใช้เวลาไม่นานนักในการแยกแยะได้ว่าอะไรคือของจริง ของปลอม
หลังจากนั้นผมก็ทำเพจบิตคอยน์งูๆ ปลาๆ ในแบบของตัวเองไป แน่นอนว่าในไทยเมื่อคุณตกลงปลงใจจะศึกษาบิตคอยน์ ชื่อแรกที่คุณจะนึกถึงแน่ๆ คือ อ.พิริยะ เขาเป็นไอดอลของผมเหมือนกับพวกคุณทุกคนนั่นแหละครับ
แล้วไอดอลกลายมาเป็นเพื่อนเราได้ยังไง?
มีช่วงหนึ่งที่ผมสังเกตุเห็นได้ชัดว่า อ.ตั๊ม เริ่มมีอาการ Burn-out ผมไม่รู้ว่าใครเห็นแบบผมไหมนะ แต่ผมแน่ใจว่าใช่แน่ๆ ผมกลับไปคิดว่าผมจะช่วยอะไรเค้าได้บ้าง?
ถ้าเราอยากจะผลักดันวงการบิตคอยน์ในไทย แทนที่จะแยกกันทำไปแบบนี้ ทำไมเราไม่ไปขอจอยช่วย อ. ทำ เสริมพลังให้แกไปเลยนะ? ผมตัวเล็กมากในคอมมูนิตี้ไทยตอนนั้น จะว่าโนเนมเลยก็ได้ แต่คิดอะไรเกินตัวซะเหลือเกิน
But how?
ผมรื้อทุกอย่างที่เป็น อ.พิริยะ เท่าที่จะหาแหล่งข้อมูลได้ในเมืองไทย ผมเป็นคนนึงที่ดูทุกคลิป ทั้งบิตคอยน์ สอนเทรด ส่วนตัว เฟซบุ๊ก หนังสือที่อ่าน วิธีที่พูด โพสต์ที่เคยผ่านตา บทความที่เคยเขียน ฯลฯ เรียกว่าผมวิจัยคนๆ นึงเลยก็ว่าได้
ผมศึกษานิสัยใจคอของเขา ความชอบ เป้าหมาย ต่างๆ นานา ไม่ใช่เพื่อจะ Take Advantage จากสิ่งนี้ แต่ผมต้องการเป็นเพื่อนกับเขาจริงๆ ผมเป็นคนแบบนี้ ผมชอบทำงานกับเพื่อน กับคนที่รู้มือรู้ใจกัน และในสถานการณ์แบบนี้ มันควรเป็นผมที่ต้องเข้าใจ อ. ให้ได้ก่อน
ถ้าคุณคิดว่าเราคงถกเรื่องบิตคอยน์ หรืองานเทรดกัน คุณคิดผิดถนัด.. ผมคุยเรื่องสัพเพเหระที่ไม่เกี่ยวกับบิตคอยน์กันแม้แต่นิดเดียว จนกระทั่งวันนี้ก็ยังเป็นแบบนี้ เรื่องที่เราคุยกันถูกคอมากที่สุดคือ.. "เรื่องเกมส์"
ให้ตายเถอะ เรามันเด็กที่โตมาในยุค 90' เหมือนกัน มีอะไรจะคุยได้ยาวเท่าเรื่องในอดีตอีก เราคุยถึงสมัยเรียน สมัยเด็ก สมัย Ragnarok เราเล่นเกมบน Nintendo switch ด้วยกัน
เอ่อ.. ผมหมายถึง… เล่นของใครของมันแล้วมาคุยกันอะนะ
พวกคุณรู้ไหมว่าเราชอบเกมกันขนาดนี้ แต่เอาเข้าจริงเราได้เล่นกันก่อนนอนวันละไม่เกินครึ่ง ชม. แค่นั้นเอง เอาแค่พอให้หายอยาก เรามีเรื่องต้องทำกันเยอะมากๆ ในตอนนั้น หากใครยังจำได้ จะมีช่วงนึงที่ อ. พูดถึงเกม Triangle Strategy บ่อยๆ นั่นแหละ เล่นอยู่กับผม
แต่อันนี้ยอมนะ เกม RPG นี่ผมสู้แกไม่ได้จริงๆ
จนกระทั่งเราได้เจอกันครั้งแรกที่งานมีตอัพบิตคอยน์ที่โรงเบียร์พี่ชิต (น่าจะมีคนอ่านสักคนที่ได้ไป) เอาจริงๆ นะ ผมไม่ตื่นเต้นเลย เป็น อ. มากกว่าที่ไม่รู้จะทำตัวยังไง ฮ่าๆๆ
ก็ผมมันดิบ ผมเป็นคนเซอร์ๆ ขัดกับลุคของ อ. คนละขั้ว แต่คนต่างขั้วนี่แหละพาพวกคุณให้ได้มาอ่านบทความนี้บน Nostr ตอนนี้ เรามาไกลจากตรงนั้นมาก เรามีคอมมูที่โตขึ้นอย่างออแกนิก มีสมาชิกน่ารักๆ ในคอมมูนิตี้หลายคน เรามี Right Shift และพาร์ทเนอร์อีกมากมายที่กำลังผุดกันขึ้นมา
ผมที่คิดว่าจะเข้ามาช่วยแบ่งเบาภาระ อ. ในตอนแรก ตอนนี้ผมทำให้เขายุ่งยิ่งกว่าเดิม แต่ผมก็สัมผัสได้นะ ผมเชื่อลึกๆ ว่าตอนนี้ อ. คงมีความสุข อ.ไม่ได้สู้ตัวคนเดียว วันนี้ อ. มีพวกเราทุกคน มันจับต้องได้ ใช้แค่หัวใจก็สัมผัสมันได้ละ
สิ่งที่ดีที่สุดที่เกิดขึ้นระหว่างเราสองคน คือผมได้สวมกอด อ. (แบบลูกผู้ชาย) หลังการจัดงาน BTC2023 ไม่มีใครได้เห็นภาพนี้ เพราะมันอยู่ในความทรงจำของผมคนเดียว…
เราเคยวาดรูปล้อเลียนให้นาย.. ตอนนี้ยังอยู่ดีไหม?
ผมอยากจะบอกกับทุกคนว่า.. เราคงไม่สามารถมีเพื่อนได้จากการนั่งอยู่เฉยๆ หรอกครับ มันมีคุณค่าบางอย่างที่จะคอยดึงดูดคนเราเข้าหากัน แต่มันต้องมีสักคนที่เริ่มก่อน และ พิริยะ คือชายคนนั้นที่ได้มอบคุณค่าบางอย่างให้กับพวกเรา พวกเรารู้กันดีว่ามันคืออะไร
สิ่งนี้แหละเรียกว่า Value for Value เมื่อเราให้มากพอ วันนึงเราจะได้รับบางอย่างเป็นการตอบแทน..
-
 @ f4db5270:3c74e0d0
2023-07-23 09:10:31
@ f4db5270:3c74e0d0
2023-07-23 09:10:31 \n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n
-
 @ 32e18276:5c68e245
2023-08-07 16:10:07
@ 32e18276:5c68e245
2023-08-07 16:10:07Hey guys,
I spent some time this weekend fixing a bunch of the bugs that were introduced in the latest nostrdb refactor. See the changelog below for the full list of changes in the latest build!
Planned this week
I have a big list of things I'm planning on adding to Damus this week:
- Lists!
- Zap improvements: Bringing back top zap comments in threads, profile zap comments in notifications, Private DM Zaps
- Video player improvements
- Sharing improvements (share to damus, etc)

Make sure to come back in a week to see how much I could get done!
Changelog
Added
- Add close button to custom reactions (Suhail Saqan)
- Add ability to change order of custom reactions (Suhail Saqan)
- Adjustable font size (William Casarin)
Changed
- Show renotes in Notes timeline (William Casarin)
Fixed
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Don't cutoff text in notifications (William Casarin)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fixed nostr reporting decoding (William Casarin)
- Dismiss qr screen on scan (Suhail Saqan)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix crash when muting threads (Bryan Montz)
-
 @ 62a45004:b2ff78c5
2023-08-12 15:42:21
@ 62a45004:b2ff78c5
2023-08-12 15:42:21Macom slid the memory disk in his pocket, grabbed his coat and badge, and headed for the communications tower. Outside, the bright but cold day encouraged him to walk briskly under the deep blue skies that reminded him of his childhood on his home planet.
Along the uneven sidewalk, a treacherous minefield of puddles from the previous night’s downpour made it necessary to focus on one’s steps. As Macom waved off a group of teens looking to peddle their counterfeit ration cards, he accidentally stepped on a loose tile, which promptly responded by squirting a copious stream of muddy water all over his right leg and torso. Without the slightest flinch, Macom continued onward, his mind focused on the task at hand.
It was not much to look at from the outside. Like most other buildings, the round-shaped communications “tower” was half-way embedded into the ground as a way to take advantage of the earth’s biomass and its natural cooling and heating effects. On top, transmission disks no larger than a few feet in diameter adorned the building like ears on the head of a sleeping, mossy giant.
Inside, however, the space was majestic and luminous. Beyond the security checkpoints, the circular, expansive lobby was centered around a grand spherical computer. The Galactic Timechain, as it was known, was encased in glass, and around it, a second layer formed a terrarium of the native ecosystem, meant to mirror the resilient and self-sustaining nature of the Timechain’s distributed network.
Along the curved wall, intricate but faded murals of historic figures blended into textual inscriptions of poems and quotes, and from above, a beam of sunlight from the roof-timer cycled its’ focus through each piece of art as new blocks were added to the Timechain. The space felt more like a temple than a government building.
‘Good morning Sub-Commander,’ the guard uttered as Macom flashed his badge, ‘you are earlier today than usual.’ The greeting was silently acknowledged with a stoic nod, and as he was waiting for the gate to open, the beam of sunlight moved to the left, and the newly illuminated quote on the gallery wall caught his attention.
Time is an abstraction at which we arrive by means of the changes of things.
Macom had never really understood the meaning of those abstract words. But today of all days, the quote he had seen a thousand times found within him a renewed resonance. He remembered being taught that in ancient civilizations, humans measured the passing of time by the ticking of metal arms around a circle, which was meant to track the astrological movement of planets around a sun. As interstellar travel evolved, this antiquated system created synchronization nightmares, for everyone had a different definition of what “time” was, of how long it took their planet to circle their sun.
Now, the addition of new blocks on the Galactic Timechain marked the passage of time. Macom felt this was curious. There was nothing in the transactions and records stored within the blocks, in the bits of zeroes and ones, that had a physical existence called “time.” Neither could the humans of antiquity find any physical element constituting “time” in the movement of the planets. The change of any thing, in fact, could be used as the measuring yardstick, and in this particular moment, Macom realized he had been unconsciously measuring time by the quickly changing political situation: the Empire’s draconian laws would open the floodgates to changes not seen since the Wars of Independence. Millennia would happen within the next few blocks, and for that reason, he thought, now was the time for decisive action.
Aided by this newly found revelation, Macom walked across the lobby towards the elevator, finding his way to transcription station #B412. The room, no larger than a regular size office, betrayed no sign of its importance. This station was designed as a decoy and kept as a closely guarded secret, for it contained the Nhafezi Confederacy’s keys, used to compose and transmit blocks onto the Galactic Mempool. As such, the security clearance used to access it also triggered an alert to high command. Even someone of his rank was not supposed to be here unannounced, and Macom knew he would only have a few moments to complete his task.
Standing in front of the door, Macom took a deep breadth to gather his courage, for he knew that as soon as he entered the room and sent the message across the Timechain, there would be no stopping, that there would be no coming back from this. He thought of the countless years of suffering, the bad winters, the unnecessary cruelty of it all. He thought of the despair and hopelessness he saw on so many faces, including his own. Above all, he thought of his brother, now gone.
As long as the life of a star to the human mind, and as short as the span of a human life to a star, the moment ended, and Macom swiped his badge on the door’s console. Moving swiftly now, he slid onto the station chair, picked the memory disk from his pocket and blended it into the transcriptor in one fluid motion. The text appeared before him, exactly as he had last proof-read it. Just as he was about to fetch the keys, a gentle knock came from the door before it opened.
With his heart skipping a beat, Macom saw a familiar figure appear from the corner of his eyes, and quickly composed himself. “I am that predictable,” he said with an air of resignation while still staring into the transcriptor.
“You were never good at hiding that look on your face,” Jiun said sardonically, while closing the door behind her.
Guarding against stalling tactics, he ignored the jab and tried to finish the job, but his fingers had barely moved before Jiun flung her comm tablet and key ring towards his desk.
“No one is coming Macom, I had Ella disengage the alert and now you have my personal key ring. I know you will not stop, not even for me, but I ask you to hear me out. If you still want to go ahead after we are done talking, I won’t stop you.”
The tablet, which had landed with a loud thud and knocked over a mug, displayed ‘#B412, alert disengaged.’ Macom was not the trusting kind, and for a moment he hesitated, thoughts of deception and betrayal rushing through his head. But even after all these years, Jiun’s word still meant something.
“I helped you draft this, remember?” Macom said while turning towards her. “It wasn’t that long ago you agreed we have to send this out.”
“That was before the council voted it down,” Jiun said with a calm assertiveness.
“And that changes nothing. You know better than I do how the Empire is systematically starving us. I am not going to allow them to reduce us to nothing, to drain us of our strength until finally, stripped of all self-respect and dignity, unable to summon the will to fight, they can simply sweep us out with a broom. We must fight,” Macom said emphasizing each word, “even though the council is too afraid, perhaps even too corrupted to do what must be done.”
“I agree, the Empire wants us to do nothing. But they would equally benefit if we over-reacted. Now that Antigonium can be synthesized and mass manufactured, we are disposable. They would like nothing more than to have the perfect excuse to send their destroyers. We have to fight, not to destroy our enemy, but to save what we love, and sending this archive to the Galactic Timechain would be suicidal.”
“The real suicide is already happening Jiun. How many people are starving? How many have taken their own lives in their misery and despair?,” Macom’s voice splintered with the faintest of cracks, before continuing. “How many of our young will they take, once this new round of laws are enforced? Should we wait until we start getting paid in imperial script, or perhaps when we start forgetting our own language? Revolution is not suicide, even if it leads to certain death. Our ancestors knew that when they fought for our independence.”
“You are right, but this is not a decision for you to make. Corrupted as it might be, the council is still needed to organize any meaningful resistance. And we might be able to force their hand, but not if the transgression comes from you Macom. If you do this, they will call it a military coup, and it would only further our internal division and turmoil. That is exactly what the Empire wants. They put us in a position to make an impossible decision, they infiltrate the council with unseen extortion and threats, all so they can watch us implode from the inside. You know this playbook.”
A long silence now enveloped the space between them, words being said without a single sound. The impasse brought into relief their conflicts from eons ago, and as Macom digested the arguments of this latest salvo, he also felt reminded with a certain fondness, why she was who she was, their indisputable moral leader.
Standing up now, Macom walked towards the door, accepting her overture: “Someone has to do it, Jiun. Even if it is a trap, even if it leads to our demise, the archive would guarantee the preservation of our culture and Our-Story for future generations. We must break the long silence. You know it is time.”
As Macon exited the room, he handed her his badge and his Antigonium pendant, the one she had gifted him all those years ago. Now alone, Jiun took a long and deep sigh before heading towards the transcriptor. On the screen, the words they had drafted together stared back at her. She sat down, clutching the pendant that stored his keys, and read it one last time.
Top Secret
My name is Jiun Nhafezi, Matriarch of the Nhafezi Confederacy, and these words, inscribed on the Galactic Timechain Codex, block number 226,524,579, will in all likelihood lead to our demise, effectively constituting our people’s last act.
Bitcoin’s Timechain has long afforded the possibility of free speech, and more importantly, the preservation of a lasting legacy against physical genocide and cultural erasure. For the first time ever, the last defiant breath from those facing annihilation will not simply scatter in the wind, unheard of and forgotten by those who seek to erase us from their-story. For the first time ever, they who control the present will not be able to sanitize, re-write, and control the past. Our past, which is also our future.
Even though this tool has been but an open road, useless to those who seek to walk it when a gun is held to their heads, it has nevertheless acted as leverage for those fighting for survival under the Empire’s watchful eye. And for millennia, this leverage has afforded our people a semblance of life: ever since the Independence Wars, our accord has forbidden us from off-planet communication. As long as we supplied the Empire with minerals and kept our words and ideas to ourselves, we were allowed the independence to uphold our customs and organize our own way of life. This is why you might have never heard of our people, or of Kaweah, a faraway moon better known in the ancient world as an Antigonium mine.
But the balance of power has now changed. As our world grew stronger and brighter, so did the Empire’s fear. Our knowledge, our art, our way of life, all of it became dangerous proof that another mode of social organization is not merely possible, but if allowed to flourish, would undermine the deepest moral foundations of the Empire in the eyes and hearts of their own people.
And so we must be destroyed.
First came the impossible mineral quotas, the penalties of which were reduced food supplies. Slowly, they forced us to choose who would go hungry, sowing the seeds of discord. Then, as we grew more desperate, the Empire extended a helping hand, offering to send our young off-world, saddling them with unpayable debts, and scattering them across the stars in search of “a better life.” Now, under the guise of industrial standardization and efficiency management, they are forcing us to adopt the imperial tongue in all curricula and settings, abandoning our own.
Faced with the slow, painful immiseration of our people, and the clear directive to dismantle our society piece by piece, we are left with no choice but to break our long silence, preserving our cultural heritage, our memory and our knowledge on the Timechain. Perhaps the two most important ones are the lexical archive, for those who seek to learn our tongue, and the mineral archive, which includes the hitherto secret chemical composition of the synthetic ingredients needed to mass manufacture Antigonium. Now it becomes open-source, our first, and perhaps last gift to the Universe.
For our transgression, the Empire will soon circle our moon and rain down extinction. Our last efforts to defend ourselves will most likely fail. By the time you receive this message, we will have long ceased to exist. I will presume these words are the only record that will survive us. Our books will be burned, our culture expunged. The young sent to the Ministry of Harmony and Reintegration will likely never speak our language our know of their heritage. Our matriarchs will be sent to the gallows, and our men to labor camps across the known galaxies.
It is our hope that this fate that awaits us, that announces its presence with every word that I convey to you, is but a temporary defeat, a chapter linking our past and the many revolutions to come. Faced with the certainty of a death of the spirit, and the possibility of a death of the body and the flesh, we as a people have chosen to not give up our dignity. Instead, we choose life at its fullest.
As we begin, so we end. This is Our-Story.
-
 @ d830ee7b:4e61cd62
2023-08-09 05:59:10
@ d830ee7b:4e61cd62
2023-08-09 05:59:10ผมมีความสุขดีกับการทำตัว Low profile เพราะมันมีเรื่องราวที่เป็นเหตุผลของมันอยู่..
ใครอ่านงานเขียนผมบ่อยๆ จะทราบดีว่าผมมักจะเขียนไปเรื่อย เล่าเรื่องหรือความคิดของตัวเองออกมาได้ยาวเหยียด เมื่อมันเป็นแบบนี้ก็เลยคิดว่าจะใช้ Account นี้ให้เหมือนเป็นบล็อกส่วนตัวสุดๆ แบบไม่มีคอนเซ็ปต์ไปเสียเลย วันไหนอยากเขียนอยากเล่าอะไรผมก็จะเล่ามันดื้อๆ นี่แหละ..
มันเริ่มจาก.. มีคนพยายามบอกว่าผมอยู่เบื้องหลังของคอมมูนิตี้บิตคอยน์ในไทย มีคนบอกว่าผมเป็นตัวตั้งตัวตี แต่ก็เป็นคนที่ลึกลับหาข้อมูลได้ยากอะไรแบบนั้น ซึ่งมันก็มีทั้งส่วนที่ถูกและยังไม่ใช่อยู่พอสมควรครับ..
อย่างแรก ผมไม่ได้มองว่าตัวเองยิ่งใหญ่หรือมีบทบาทสำคัญมากขนาดนั้น ผมยังเชื่อมาตลอดว่าอะไรก็ตามที่เกิดขึ้น มันไม่ได้เกิดเพราะผมเพียงคนเดียว มันประกอบมาจากหลายส่วนและคนที่มีส่วนร่วมในสิ่งนี้ยังมีอีกมากมาย ผมอาจเป็นฟันเฟืองหลักในเรื่องนี้ แต่ยังไงผมก็คงต้องปฎิเสธว่าไม่ใช่เพราะผมคนเดียวอย่างแน่นอน ใช่ครับ.. มันก็มาถึงตรงนี้ได้เพราะพวกเราทุกคน
อย่างที่สอง โดยส่วนตัวผมคิดว่าการมีตัวตนในลักษณะนั้นจะทำให้ผมไม่สามารถทำอย่างที่ทำอยู่ในทุกวันนี้ได้ มันจะทำให้ผมนึกถึงเพียงแค่ตัวเอง สนใจแค่เพียงตัวเองมากกว่าคนรอบข้าง
ซึ่งมันขัดกับเป้าหมายสำคัญส่วนตัวของผมนั่นคือ “ส่วนรวม” ฝันของผมนั้นไกลจนยากที่ใครจะจินตนาการถึง วันนี้เราทำเสต็ปแรกกันยังไม่ครบเลยด้วยซ้ำ หากผมมตัวแต่ส่องกระจกประเมินตัวเองอยู่ทุกวันๆ ผมคงไม่มีเวลาไปคิดถึงส่วนอื่นๆ เป็นแน่แท้ ..งานแบบนั้นยังมีอีกหลายคนที่พร้อมจะเสียสละและเต็มที่ไปกับมัน ไม่จำเป็นต้องเป็นผมใช่ไหมล่ะ
อย่างที่สาม ผมเชื่อในแนวคิด Decentralized อย่างที่สุด คำนี้ลึกซึ้งมากกว่าแค่เข้าใจว่ามันกระจายหรือรวมศูนย์ ผมไม่ได้เป็นคนที่เข้าใจลงลึกในวิชาการหรือความรู้ทางเทคนิคของบิตคอยน์มากนัก ผมเชื่อว่าตัวเองก็แค่รู้ในระดับคนทั่วๆ ไป แต่ในเรื่องหลักการและแนวคิดพวกนี้ รวมถึงการนำมาประยุกตร์เข้ากับเรื่องต่างๆ ในชีวิต ผมคิดว่าผมทำได้ค่อนข้างดีเลยล่ะ
เกี่ยวกับเรื่องนี้.. ผมเชื่อเองตั้งแต่ต้นว่าสังคมจะไม่เติบโตอย่างยั่งยืนหากพึ่งพาผู้นำหรือใครคนใดคนหนึ่งมากเกินไปหรือกระทั่งการเทิดทูนฮีโร่ บิตคอยน์ยังอยู่มาอย่างแข็งแกร่งมากกว่า 10 ปีผมไม่คิดว่าเป็นเพราะใครสักคน แต่มันเป็นเพราะอาณุภาพของ Network ที่เข้มแข็งและแพร่กระจายตัวในทุกนาทีแบบเดียวกับไมซีเลียม ผมฝันอยากเห็นสังคมที่โตในแบบของมันเอง มีความมั่นคงเข็มแข็ง อาจไม่ต้องเป็นหนึ่งเดียว แต่มันไม่ควรมีจุดตายอยู่ที่ใครทั้งนั้น
เราสามารถมีผู้เสียสละเก่งๆ ได้อีกมากมายที่กระจายตัวอยู่ตามพื้นที่ต่างๆ ต่างจังหวัด หรือแพลตฟอร์มต่างๆ เพื่อทำหน้าที่ผลักดันในแบบที่เขาถนัด
https://i.imgur.com/3sDzTdg.png เมื่อเราจินตนาการเห็นภาพนั้นเราจะเริ่มตระหนักได้ทันทีว่า..
เรานั้นตัวเล็กเกินกว่าจะไปคิดว่าเราใหญ่
ผมไม่ชอบใช้คำว่า “การต่อสู้” หรือ “การเอาชนะ” ไม่ว่าจะกับใคร (ใครๆ ก็คงจะหมายถึงรัฐ) บิตคอยน์มันชนะได้ด้วยตัวมันเองแบบไม่ต้องแข่งเลยด้วยซ้ำ ทำไมเราต้องไปเสียเวลากับการคิดหาหนทางเอาชนะในแบบเดิมๆ วิธีที่แยบยลกว่าน่าจะเป็น “การสร้าง” สิ่งที่ทรงพลัง กำแพงหนาที่แข็งแกร่งยากจะโค่นล้ม นั่นคือพลังแห่งความคิดและฝูงชน พลังแห่งเครือข่ายและชุมชน
ผมอยากเห็นมากกว่าแค่คนๆ เดียว คนกลุ่มเดียว ที่เก่งกล้าพอจะลุกขึ้นมาเสียสละแบ่งปันและช่วยเหลือ เผยแพร่สิ่งที่พวกเขารู้ไปยังคนอื่นๆ เพื่อขยายแนวคิดให้กระจายออกไป ผมมีส่วนจริงในการปลูกฝังแนวคิดและสร้างคอมมูนิตี้ขึ้นมาจากจุดนั้น แต่ผมไม่ใช่คนบงการอะไรทั้งสิ้น
แนวคิดจะได้รับการยอมรับคงไม่ใช่เพราะคนมาเกรงใจตัวผม แต่มันควรมาจากการที่ทุกคนเห็นพ้องต้องกันว่ามันอาจเป็นแนวทางที่ใช่สำหรับสังคมของพวกเขา เราอาจต้องนำ ต้องเป็นแบบอย่างก่อนในช่วงแรก แต่เมื่อทุกอย่างเริ่มเข้าที่ ทุกคนเริ่มเข้าใจเหตุผลและรูปแบบในการอยู่ร่วมกัน เวลาของผมสำหรับบทบาทนั้นก็คงไม่ต้องมีอีกแล้ว
นั่นเป็นเหตุผลว่าทำไมผมผละจากสิ่งที่เคยแอคทีฟในตอนแรก การมีส่วนร่วมเป็นแกนหลักและคอยแอคทีฟในชุมชน ผมไปทำอีกสิ่งหนึ่งเพื่อเตรียมไว้ตอบสนองต่อความต้องการของชุมชนในอนาคตนั่นคือคลังความรู้ เพราะผมเชื่อว่ากลุ่มบิตคอยน์ของชาวเรามันเติบโตขึ้นมากแล้วจากวันแรกๆ ที่เราได้เริ่ม
มันไม่ใช่เรื่องของจำนวน ไม่ใช่เรื่องของการตลาด มันคือหลักการและแนวคิด รูปแบบการปฏิสัมพันธ์ที่ค่อยๆ ก็ร่างสร้างตัวมาเรื่อยๆ จนมีคุณลักษณะที่ชัดและเป็นปัจเจกแตกต่างจากเหรียญอื่นๆ ไม่ว่าใครจากภายนอกจะมองว่าสัวคมของเราเป็นแบบไหนก็ตาม ผมไม่ได้สนใจเลยตรงนั้น เพราะนี่แหละคือเราในแบบของเรา
ผมมาเขียนเล่าเรื่องพวกนี้ไม่ใช่เพราะผมอยากจะหายตัวไปแบบ Satoshi หรอกนะครับ ผมไม่ได้ทำเรื่องยิ่งใหญ่อะไรขนาดนั้นเลย เพราะเมื่อไหร่ก็ตามที่เราคิดว่าเรานั้นใหญ่เสียเหลือเกิน ตัวของเราจะบดบังตาเราจนมืดบอด เราจะมองไม่เห็นใคร
ผมขอเป็นคนตัวเล็กๆ เล็กพอที่จะมองเห็นคนทุกคนบนโลกแบบนี้ต่อไปดีกว่า ผมชอบที่จะได้เห็นและคอยมีส่วนกับทุกๆ เรื่อง ผมสนุกกับมัน และหวังว่าพวกเราที่อ่านมาถึงตรงนี้ก็คงจะสนุกแบบผมเหมือนกัน
https://i.imgur.com/z7XmLjh.png บิตคอยน์ไม่ได้เปลี่ยนโลกในแบบที่เราเข้าใจ มันเริ่มเปลี่ยนคนตัวเล็กแบบพวกเขาให้เติบโตไปเปลี่ยนโลกต่างหากล่ะ
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ 374bff5b:3d2f92d8
2023-08-12 21:50:19
@ 374bff5b:3d2f92d8
2023-08-12 21:50:19
Cristiano Ronaldo scored a brace as 9-man Al Nassr secured a comeback 2-1 win over Al Hilal in the Arab Club Champions Cup final on Saturday.

 .
.In a pulsating match that unfolded today, football fans were treated to a spectacular showcase of skill, determination, and heart-stopping moments as Al Nassr and Al-Hilal clashed on the field. The highly anticipated game, which took place on the hallowed grounds of the King Fahd Stadium, left spectators on the edge of their seats as the two Saudi powerhouses battled for supremacy.
In an impressive display of teamwork and resilience, Al Nassr's star player, the five-time Ballon D'or winner Cristiano Ronaldo, emerged as the driving force behind his team's triumph. Just months after his arrival from Manchester United, Ronaldo proved once again why he is regarded as one of the greatest footballers of all time.
The match was marked by a series of nail-biting moments, with both sides showcasing their prowess and determination to seize victory. Brazilian winger Michael set the stage alight by opening the scoring for Al-Hilal with a remarkable header in the 51st minute, celebrating with the now-iconic 'SIU' gesture aimed at Ronaldo. The tension reached a fever pitch as Ronaldo responded with an awe-inspiring brace, securing his 24th goal of 2023 and his 21st final goal—an astonishing feat that earned him yet another Guinness World Record for the highest number of goals scored in finals.
Al Nassr faced adversity when they were reduced to 10 men after Abdulelah Al-Amri was shown a red card in the 71st minute. However, in a testament to Ronaldo's leadership and unwavering spirit, he managed to equalize, sparking a dramatic turnaround that rekindled hope for Al Nassr's inaugural trophy win. Even the subsequent red card for Nawaf Boushal in the 78th minute couldn't deter Ronaldo and his resilient teammates.
In a truly mesmerizing moment, Ronaldo defied all odds, drawing the game level almost immediately after Sultan Al-Ghannam's well-placed cross. The emotional celebration that followed, as Ronaldo waved his finger directly at Michael, showcased the intensity of the competition and the depth of rivalry on the field.
The intensity only heightened during extra time, with Ronaldo's head once again stealing the spotlight as he capitalized on a rebound to score the winning goal. His 843rd senior career goal resonated as a testament to his enduring talent and determination.
As the game drew to a close, Ronaldo was forced to exit the field with an injury, leaving Al Nassr to defend their lead with determination and grit. Despite the late pressure exerted by Al-Hilal, Al Nassr's unwavering defense held strong, clinching a historic victory and their first championship title since 2020.
This game will undoubtedly be etched in the annals of football history as a showcase of pure talent, resilience, and the captivating drama that makes the sport so exhilarating. Cristiano Ronaldo's heroics, the intense rivalries, and the triumphant moments will be remembered by fans around the world, a testament to the enduring magic of the beautiful game.

Amid a surge of exhilaration, Ronaldo hastened his return to the field, a palpable excitement evident even as he celebrated alongside his teammates. In a poignant moment, he lifted his 35th overall trophy—an extraordinary achievement, marking his first triumph since securing the Coppa Italia with Juventus back in May 2021.
At 38 years of age, Ronaldo exhibited a level of performance that can only be described as stellar. His influence on Al Nassr's triumphant journey in the Arab Club Champions Cup campaign was undeniable. An embodiment of excellence, he clinched the coveted title of top scorer, seizing the Golden Boot with an impressive tally of six goals. His pivotal contributions included finding the net in the quarter-finals and semi-finals, etching his mark on the tournament's outcome.
A resounding testament to his prowess, Ronaldo secured the decisive goal in a narrow 1-0 victory over Al-Shorta SC, the Iraqi champions, during the semi-finals. Prior to this, his brilliance illuminated a remarkable 3-1 triumph over Morocco's Raja Club Athletic in the quarter-finals, not to mention a series of awe-inspiring goals during the intense group stage clashes.
Before the grand stage of the Arab Club Champions Cup, the legendary figure from Real Madrid and Manchester United had already begun making waves. He ignited the scoring fire with his inaugural goal of the season—a significant contribution to a convincing 4-1 victory over Tunisia's Union Sportive Monastirienne. Yet, his indomitable spirit shone even brighter during a challenging encounter, as his 87th-minute equalizer rescued Al Nassr from the brink of elimination, salvaging a crucial 1-1 draw against Egypt's Zamalek.
In the realm of football, Ronaldo's journey through the Arab Club Champions Cup serves as a captivating chapter of determination, resilience, and unparalleled skill. As he jubilantly hoisted his 35th trophy, the significance of this victory echoed his enduring legacy and unwavering commitment to the sport. In a testament to his remarkable contributions, Cristiano Ronaldo has etched his name yet again in the annals of football history. Your comments is greatly valued!
-
 @ f4db5270:3c74e0d0
2023-07-22 16:32:18
@ f4db5270:3c74e0d0
2023-07-22 16:32:18 \n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n \n\n\n-----------\n\nThe original photo\n\n
\n\n\n-----------\n\nThe original photo\n\n
-
 @ 0b963191:fc5e7ffd
2023-08-08 18:06:14
@ 0b963191:fc5e7ffd
2023-08-08 18:06:14I have an idea I am currently putting together a javascript library and implementation for. This is a quick and dirty blog post to note where my head is at with it.
The main idea is using Nostr as a transport layer for accessing micro services in a censorship resistant way.
I will just use this blog post of a quick introduction on what I am thinking and I will link to more as development continues.
The idea
The idea is for the client side to access a nostr service very similar to how websites and other clients use XMLHttpRequest() to make API calls to services. The difference here being that rather than relaying on HTTP for the request, the requests and responses would be sent through relays.
 The above just shows a quick example of the standard http call to a service.
The above just shows a quick example of the standard http call to a service.This allows the following: * Services that do not directly rely on a hosts DNS * Services that do not expose the service IP address * Redundancy across multiple relays * Censorship resistant applications (I will not use the term dapp) that have a service backend
 The above shows how a client can interact with a service using nostr as the transport layer.
The above shows how a client can interact with a service using nostr as the transport layer.How it will work (TL;DR)

In simple terms a service will have a naddress (naddr1) that will carry its public key and core relays it will be listening on. A client will make a request using a generated nostr keypair referencing the service's pubkey in a tag and some call data. The service will read and validate this request and respond by referencing the client's event ID it used to make the call.
There will also be the ability for the service to push data to relays that can be read by clients without a call request being made (i.e. block height changes).
Why?
There are already many ways to push and pull data whether using nostr relays natively, inefficient block chain smart contracts, tor, or standard http. This may find a few use cases that can compliment existing methods.
In many ways this acts like many of the bots created on nostr that take input and responds with some output. This standardizes the uses a bit more.
A few use cases: * Server side code that can be used on something like ipfs (instead of using expensive inefficient smart contract block chains) * Services resistant to DNS and IP points of failure (i.e. targeted shutdown of services on the name server level. It has happened!) * Pulling in outside data that a client does not have ability or access to generate
I will have a working prototype of this in the next few weeks that I will host on a github.
-
 @ f4db5270:3c74e0d0
2023-07-22 16:28:30
@ f4db5270:3c74e0d0
2023-07-22 16:28:30 \n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n-----------\n\n\nThe beginning...\n\n
\n\n-----------\n\n\nThe beginning...\n\n \n\n-----------\n\n\nThe original photo\n
\n\n-----------\n\n\nThe original photo\n
-
 @ be73ff09:c8539bee
2023-08-12 16:30:01
@ be73ff09:c8539bee
2023-08-12 16:30:01Introduction
Picture a world where computers can chat, write, and create content like humans. It might sound like something out of a science fiction movie, but it has become a reality thanks to Large Language Models (LLMs). These digital wonders are putting the world in an uneasy position, making people ask if they should be worried about the possibility of AI taking over what we call Earth, because if they are now crafting text that sounds like it's coming from a real person, what is next? Are they coming for jobs? Let's take a journey into the world of LLMs and see if this frenzy will materialize.
Understanding Large Language Models
Definition and Evolution: Large language models (LLMs) are a type of artificial intelligence (AI) known as Natural Language Processing (NLP) that can generate text, translate languages, write different kinds of creative content, and answer your questions in an informative way. They are trained on massive amounts of text data, and they can learn to perform a wide range of tasks. LLMs have come a long way in recent years. In the past, they were only able to generate simple text, such as "Hello, world!" However, they have now evolved to the point where they can write poetry that could bring tears to your eyes. They can also translate languages, write different kinds of creative content, and answer your questions in an informative way. LLMs are still under development, but they have the potential to revolutionize the way we interact with computers. They could be used to create new forms of art and literature, translate languages in real time, and answer our questions in a way that is both informative and engaging. LLMs are a powerful tool that has the potential to change the world. As they continue to evolve, they will become even more capable of performing a wide range of tasks. For some, it is exciting to think about what the future holds for LLMs, however, for others, it is their worst nightmare.
Architecture and Working Mechanism: Imagine large language models (LLMs) as big, intricate puzzles made of digital pieces. These pieces are like tiny brain cells called neural networks. They work together, paying special attention to the important parts of the text. It is as if they are having a secret conversation about how to make the writing sound amazing. Just like a musician practices their notes, LLMs have two phases: they learn from lots of text (pre-training), and then they fine-tune their skills for specific tasks (such as writing a funny story or translating languages).

II. Applications and Impact:
Natural Language Processing: Natural Language Processing (NLP) is a field of computer science that focuses on the interaction between computers and human (natural) languages. NLP is used in a wide variety of applications, including machine translation, speech recognition, and text analysis. Large language models (LLMs) are a type of NLP model that is trained on massive amounts of text data. LLMs can be used to perform a variety of tasks, including:
-
Generating text
-
Translating a text from one language to another
-
Answering questions about a text
-
Summarizing text
LLMs are still under development, but they have the potential to revolutionize the way we interact with computers. They can be used to create more natural and engaging user interfaces, and they can also be used to automate tasks that are currently performed by humans. LLMs are like language superheroes. They can understand different languages, figure out if someone's happy or sad from what they write, and even answer questions like your all-knowing friend. They're like the Sherlock Holmes of words.
Creative Expression: LLMs aren't just the nerdy, bookish types. They also display some artistic sides! They can paint pictures with words, creating beautiful poetry and stories that could rival the classics (arguably). Although the question that has been coming up recently is regarding who owns a generative AI, a consensus hasn’t been reached yet.
Types of Large Language Models
-
GPT (Generative Pre-trained Transformer): GPT is one of the most well-known and widely used types of large language models. It uses a transformer architecture to generate text and has been trained on massive amounts of data from the internet.
-
BERT (Bidirectional Encoder Representations from Transformers): BERT is designed to understand the context of words in a sentence by considering the words that come before and after them. It's particularly useful for tasks like sentiment analysis and question answering.
-
T5 (Text-to-Text Transfer Transformer): T5 is unique in that it frames almost all NLP tasks as a text-to-text problem. It can take various inputs and generate corresponding outputs, making it versatile for a wide range of applications.
-
XLNet: XLNet is a model that goes beyond the limitations of traditional autoregressive models by considering all permutations of words in a sentence, allowing it to capture even more complex relationships between words.
-
BART (Bidirectional and Auto-Regressive Transformers): BART combines the strengths of bidirectional and autoregressive models, making it effective for tasks like text generation, summarization, and language translation.
-
Turing-NLG: This model is designed for natural language generation tasks and is known for its ability to produce coherent and contextually relevant text.
-
CTRL (Conditional Transformer Language Model): CTRL is designed to generate text with specific styles or tones, making it useful for tasks like creating content in different writing styles.
-
Megatron: Megatron is a model specifically optimized for large-scale training, making it suitable for tackling complex NLP challenges using massive amounts of data.
-
ELECTRA (Efficiently Learning an Encoder that Classifies Token Replacements Accurately): ELECTRA introduces a new training objective that helps improve the efficiency and effectiveness of pre-training language models.
-
RoBERTa (A Robustly Optimized BERT Pretraining Approach): RoBERTa is an optimized version of BERT that is trained with larger batch sizes and more data, resulting in improved performance on various NLP tasks.
III. Benefits and Advantages
Efficiency and Automation: Imagine having a super-fast assistant that can write reports, analyze data, and help with all sorts of tasks. That's what LLMs can do! They're like the super-speedy typists that help get things done in no time. Businesses are already loving them because they make work easier and faster.
Personalization and User Experience: Have you ever talked to a computer and felt like it understood you? LLMs are great at that. They can chat with you like a friend, give you advice, and even recommend things you might like. It's like having a helpful buddy who knows exactly what you need.
IV. Ethical Considerations
Bias and Fairness: Now, let's talk about a tricky part. LLMs are smart, but they're not perfect. Sometimes, they might pick up on things from the internet that aren't so great, like unfair stereotypes. But the smart people who create them are working hard to fix this and make sure they treat everyone fairly.
Misinformation and Manipulation: Remember that old saying, "With great power comes great responsibility"? Well, it's true for LLMs too. They can write all sorts of things, even stuff that isn't true. That's why the creators and users need to be careful and make sure the stories they tell are honest and helpful. And this is where a lot of fear is at. The fact that It can generate lies (hallucinations) and gives you authority is what bothers people like Grady Booch and the Pentagon Chief Digital and AI Officer Craig Martell.


V. The Future of Large Language Models
Advancements and Research: The future is a place where LLMs become even more amazing. They might start understanding not just words, but pictures too. They'll learn to read between the lines and understand jokes, like a real pro comedian. The skeptics believe that this is not going to happen as Grady cited in a recent tweet that “Told ya. ALL large language models are architecturally incapable of reasoning. Period.”
 While the optimists believe that LLMs understand our world like Andrew Yang of Deeplearning.ai.
While the optimists believe that LLMs understand our world like Andrew Yang of Deeplearning.ai.

LLMs and Taking Jobs
The impact of large language models on job markets is a topic of debate and consideration. While large language models (LLMs) have shown remarkable capabilities in tasks like content creation, translation, and data analysis, the idea that they will completely replace human jobs is nuanced.
Enhancement and Transformation LLMs have the potential to enhance certain tasks by automating repetitive and time-consuming processes. This can lead to increased efficiency and productivity in various industries. For example, LLMs can assist in generating reports, summarizing data, and providing customer support, freeing up human workers to focus on more strategic and creative aspects of their jobs.
Task Automation vs. Job Replacement It's important to distinguish between task automation and complete job replacement. While LLMs can automate specific tasks, they may not fully replicate the complex decision-making, empathy, and creativity that humans bring to many roles. Rather than taking jobs, LLMs could reshape job roles, allowing humans to focus on higher-level responsibilities that require critical thinking and emotional intelligence.
 Some internet users like Edward are quite indifferent though
Some internet users like Edward are quite indifferent thoughNew Opportunities and Collaboration The rise of LLMs could lead to the creation of new job opportunities. As industries adopt these technologies, there will be a demand for individuals who can develop, fine-tune, and manage LLMs. Moreover, collaboration between LLMs and human workers could become a norm, where these models act as valuable tools, enhancing human capabilities and enabling innovative solutions.

Reskilling and Adaptation The evolution of technology, including LLMs, underscores the importance of reskilling and lifelong learning. Adapting to new tools and technologies will become crucial for the workforce. This could lead to a shift towards more specialized roles that require a combination of technical expertise, domain knowledge, and human skills.
Ethical and Social Considerations While LLMs offer many benefits, ethical considerations must guide their deployment. Ensuring that the technology is used responsibly, addressing biases, and minimizing the potential for misinformation are critical challenges that need to be addressed.
My Opinion The advent of large language models (LLMs) has sparked a debate about whether or not we should be afraid of these artificial wordsmiths. Some people believe that LLMs pose a threat to human jobs, while others believe that they can be used to augment human creativity and productivity. I believe that the future of work will be a collaboration between humans and AI. LLMs can be used to automate tasks that are currently done by humans, freeing up our time for more creative and strategic work. Additionally, LLMs can be used to generate new ideas and insights that humans may not have thought of on their own. In a world where humans and AI work together, we can create a future that is both innovative and ethical. We need to be careful about how we use LLMs, but we should not be afraid of them. With careful planning and implementation, LLMs can be a powerful tool for good. I imagine a world where people and LLMs work side-by-side, like the best of friends. They will brainstorm ideas together, help each other out, and create things that no one could have imagined on their own. It will be a team of dreamers and thinkers, pushing the boundaries of what is possible.
-
-
 @ a4a6b584:1e05b95b
2023-07-27 01:23:03
@ a4a6b584:1e05b95b
2023-07-27 01:23:03"For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God." Romans 14:11-12
Though God has always had a people, the New Testament Church started with Christ and His disciples and was empowered at Pentecost. Historically, there has always been a remnant of people who adhered to the truth of God's Word for their faith and practice. I am convinced that the very same body of truth which was once delivered must be contended for in every generation.
In every generation from Christ and His disciples to this present moment, there have been holy adherents to the truth of God's Word. This witness of history is a witness in their blood. I am a Baptist by conviction. I was not "Baptist-born." I became and remain a Baptist because of what I have discovered in the Word of God.
The Lord Jesus Christ left His church doctrine and ordinances. The ordinances are baptism and the Lord's Supper. These are the things He ordered us to do. They picture His death and remind us of Him and His return. He also left us a body of doctrine. This involves our belief and teaching. Our doctrine distinguishes us. It is all from the Bible.
No one can be forced to become a Baptist. Our records show that baptism was always administered to professing believers. Hence, we refer to baptism as believers' baptism.
Baptists are gospel-preaching people. They preached the gospel to me. The Lord Jesus said to the first-century church, "But ye shall receive power, after that the Holy Ghost is come upon you: and ye shall be witnesses unto me both in Jerusalem, and in all Judea, and in Samaria, and unto the uttermost part of the earth ,, (Acts I :8). I am grateful to God to be a Baptist. I consider this to be New Testament Christianity. It is my joy to serve as the pastor of an independent Baptist church, preaching and teaching God's Word.
A Baptist recognizes the autonomy of the local church. There is no such thing as "The Baptist Church." The only Baptist headquarters that exists is in the local assembly of baptized believers. There are only local Baptist churches. \
When we say that the Bible is our sole authority, we are speaking of all the scriptures, the whole and its parts. We should preach the whole counsel of God. In the Bible we find the gospel-the death, burial, and resurrection of Jesus Christ. We should proclaim the gospel because Jesus Christ said that we are to take the gospel message to every creature. When we open the sixty-six books of the Bible, we find more than the gospel. Of course, that scarlet thread of redemption runs through all the Bible, but the whole counsel of God must be proclaimed.
The Bible says in Romans 14:11-12, ''For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God. " Each human being must answer personally to God.
In our nation we hear people talk about religious tolerance. Religious tolerance is something created by government. It is a "gift" from government. Religious tolerance is something man has made. Soul liberty is something God established when He created us. We find a clear teaching of this in His Word. Soul liberty is a gift from God! God's Word says in Galatians 5:1, "Stand fast therefore in the liberty wherewith Christ hath made us free, and be not entangled again with the yoke of bondage."
Soul liberty does not rest upon the legal documents of our nation-it is rooted in the Word of God. This individual freedom of the soul is inherent in man's nature as God created him. Man is responsible for his choices, but he is free to choose. This conviction is at the core of Baptist beliefs.
This powerful declaration about our Baptist position was made by J.D. Freeman in 1905:
Our demand has been not simply for religious toleration, but religious liberty; not sufferance merely, but freedom; and that not for ourselves alone, but for all men. We did not stumble upon this doctrine. It inheres in the very essence of our belief. Christ is Lord of all.. .. The conscience is the servant only of God, and is not subject to the will of man. This truth has indestructible life. Crucify it and the third day it will rise again. Bury it in the sepulcher and the stone will be rolled away, while the keepers become as dead men .... Steadfastly refusing to bend our necks under the yoke of bondage, we have scrupulously withheld our hands from imposing that yoke upon others .... Of martyr blood our hands are clean. We have never invoked the sword of temporal power to aid the sword of the Spirit. We have never passed an ordinance inflicting a civic disability on any man because of his religious views, be he Protestant or Papist, Jew, or Turk, or infidel. In this regard there is no blot on our escutcheon (family crest).
Remember that, when we are talking about individual soul liberty and the relationship of the church and the state, in America the Constitution does not place the church over the state or the state over the church. Most importantly, Scripture places them side by side, each operating independently of the other. This means there is freedom in the church and freedom in the state. Each is sovereign within the sphere of the authority God has given to each of them (Matthew 22:21).
Read carefully this statement made by Charles Spurgeon, the famous English preacher, concerning Baptist people:
We believe that the Baptists are the original Christians. We did not commence our existence at the Reformation, we were reformers before Luther or Calvin were born; we never came from the Church of Rome, for we were never in it, but we have an unbroken line up to the apostles themselves. We have always existed from the very days of Christ, and our principles, sometimes veiled and forgotten, like a river which may travel underground for a little season, have always had honest and holy adherents. Persecuted alike by Romanists and Protestants of almost every sect, yet there has never existed a government holding Baptist principles which persecuted others; nor, I believe, any body of Baptists ever held it to be right to put the consciences of others under the control of man. We have ever been ready to suffer, as our martyrologies will prove, but we are not ready to accept any help from the State, to prostitute the purity of the Bride of Christ to any alliance with overnment, and we wil never make the Church, although the Queen, the despot over the consciences of men.
The New Park Street Pulpit, Volume VII · Page 225
This a marvelous statement about Baptist beliefs. I am rather troubled when I see so many people who claim to be Baptists who do not understand why they are Baptists. We should be able to defend our position and do it biblically. lf we are people who know and love the Lord and His Word and if the Bible is our sole authority for faith and practice, then we have no reason to be ashamed of the position we take. May God not only help us to take this position, but to take it with holy boldness and cotnpassion. May He help us to be able to take His Word in hand and heart and defend what we believe to a lost and dying world.
So much of what we have to enjoy in our country can be credited to Baptist people. Any honest student of American history will agree that the Virginia Baptists were almost solely responsible for the First Amendment being added to our Constitution providing the freedom to worship God as our conscience dictates.
We have a country that has been so influenced that we do not believe it is right to exercise any control or coercion of any kind over the souls of men. Where did this conviction come from? We find it in the Bible, but someone imparted it to the Founding Fathers. It became the law of the land, and it should remain the law of the land. We need to understand it. It comes out of the clear teaching of God's Word concerning the subject of soul liberty.
There are many historic places there where people were martyred for their faith, giving their lives for what they believed. The religious persecution came as a result of the laws of the land. Although many Baptists have been martyred, you will never find Baptist people persecuting anyone anywhere for his faith, no matter what his faith may be.
There are many denominations that teach the Scriptures are the infallible Word of God, God is the creator of heaven and earth, man is a fallen creature and must be redeemed by the blood of Christ, salvation is the free offer of eternal Iife to those who receive it and eternal helI awaits those who reject it, the Lord's Day is a day of worship, and the only time for man to be made right with God is in this lifetime. There are certainly other commonly held teachings, but there are certain Baptist distinctive. Often an acrostic using the word BAPTISTS is used to represent these Baptist distinctive.
-
B is for biblical authority. The Bible is the sole authority for our faith and practice.
-
A for the autonomy of the local church. Every church we find in the New Testament was a self-governing church with only Christ as the head.
-
P represents the priesthood of believers and the access we have to God through Jesus Christ.
-
T for the two church officers-pastors and deacons. We find these officers in the New Testament.
-
I for individual soul liberty. Most people, when asked, say that the sole authority of the Scripture in our faith and practice is the single, most important distinctive of our faith. However, if we did not have individual soul liberty, we could not come to the convictions we have on all other matters.
-
S for a saved church membership.
Personal Accountability to God
Renowned Baptist leader, Dr. E.Y. Mullins, summarized our Baptist position in these words. He wrote:
The biblical significance of the Baptist is the right of private interpretation of and obedience to the Scriptures. The significance of the Baptist in relation to the individual is soul freedom. The ecclesiastical significance of the Baptist is a regenerated church membership and the equality and priesthood of believers. The political significance of the Baptist is the separation of church and state. But as comprehending all the above particulars, as a great and aggressive force in Christian history, as distinguished from all others and standing entirely alone, the doctrine of the soul's competency in religion under God is the distinctive significance of the Baptists.
We find this accountability in the opening verses of God's Word. When God created man, He created man capable of giving a personal account of himself to God. God did not create puppets; He created people. He gave man the right to choose. That is why we find the man Adam choosing to sin and to disobey God in Genesis chapter three. Of his own volition he chose to sin and disobey God. Genesis I :27 says, "So God created man in his own image, in the image of God created he him; male and female created he them. " We were made in God's image, and when God made us in His image, He made us with the ability to choose.
It is not right to try to force one's religion or belief upon another individual. This does not mean, however, that he can be a Christian by believing anything he wishes to believe, because Jesus Christ said that there is only one way to heaven. He said in John 14:6, "I am the way, the truth, and the life: no man cometh unto the Father, but by me." He is the only way to God. The only way of salvation is the Lord Jesus Christ.
In this age of tolerance, people say that nothing is really wrong. The same people who say that any way of believing is right will not accept the truth that one belief can be the only way that is right. You may believe anything you choose, but God has declared that there is only one way to Him and that is through His Son, Jesus Christ. He is the only way of salvation- that is why He suffered and died for our sins. The only way to know God is through His Son, the Lord Jesus Christ.
Someone is certain to ask, "Who are you to declare that everyone else's religion is wrong?" We are saying that everyone ~as ~ right to choose his own way, but God has clearly taught us in His Word that there is only one way to Him. The Lord Jesus says in John 10:9, "I am the door: by me if any man enter in, he shall be saved, and shall go in and out, and find pasture."
No human being is going to live on this earth without being sinned against by others. Many children are sinned against greatly by their own parents. However, we cannot go through life blaming others for the person we are, because God has made us in such a way that we have an individual accountability to God. This comes out of our soul liberty and our right to choose and respond to things in a way that God would have us espond to them. God has made us in His image. Again, He did not make us puppets or robots; He made us people, created in His image with the ability to choose our own way.
Remember, "For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God" (Romans 14:11- 12). We are responsible because we have direct access to God. God has given us the Word of God, the Holy Spirit, and access to the Throne by the merit of Jesus Christ. We, therefore? must answer personally to God at the judgment seat because God communicates to us directly.
People do not like to be held personally accountable for their actions. The truth of the Word of God is that every individual is personally accountable to God. In other words, you are going to meet God in judgment some day. I am going to meet God in judgment some day. All of us are going to stand before the Lord some day and answer to Him. We are individually accountable to God. Since the state cannot answer for us to God, it has no right to dictate our conscience.
We live in a country where there are many false religions. As Baptist people, we defend the right of anyone in our land to worship as he sees fit to worship. This is unheard of in most of the world. If a man is a Moslem, I do not agree with his Islamic religion, but I defend his right to worship as he sees fit to worship. The teaching of the Catholic Church declares that salvation comes through Mary, but this is not the teaching of the Bible. We zealously proclaim the truth, but we must also defend the right of people to worship as they choose to worship. Why? Because individual soul liberty is a gift from God to every human being.
Since the Bible teaches individual soul liberty and personal accountability to God, then it is a truth that will endure to all generations. To be sure, Baptists believe the Bible is the sole authority for faith and practice (II Timothy 3:16-17; Matthew 15:9; I John 2:20, 21 , 27) and the Bible clearly teaches that no church or government or power on earth has the right to bind a man's conscience. The individual is personally accountable to God. Hence, we reject the teaching of infant baptism and all doctrine that recognizes people as members of a church before they give evidence of personal repentance toward God and faith in the Lord Jesus Christ.
The famous Baptist, John Bunyan is the man who gave us Pilgrim's Progress. This wonderful book was planned during Bunyan's prison experience and written when he was released. The trial of John Bunyan took place on October 3, 1660. John Bunyan spent twelve years in jail for his convictions about individual soul liberty, failure to attend the Church of England, and for preaching the Word of God. During his trial, Bunyan stood before Judge Wingate who was interested in hearing John Bunyan state his case. Judge Wingate said, "In that case, then, this court would be profoundly interested in your response to them."
Part of John Bunyan's response follows:
Thank you, My 'lord. And may I say that I am grateful for the opportunity to respond. Firstly, the depositions speak the truth. I have never attended services in the Church of England, nor do I intend ever to do so. Secondly, it is no secret that I preach the Word of God whenever, wherever, and to whomever He pleases to grant me opportunity to do so. Having said that, My 'lord, there is a weightier issue that I am constrained to address. I have no choice but to acknowledge my awareness of the law which I am accused of transgressing. Likewise, I have no choice but to confess my auilt in my transgression of it. As true as these things are, I must affirm that I neiher regret breaking the law, nor repent of having broken it. Further, I must warn you that I have no intention in future of conforming to it. It is, on its face, an unjust law, a law against which honorable men cannot shrink from protesting. In truth, My 'lord, it violates an infinitely higher law- the right of every man to seek God in his own way, unhindered by any temporal power. That, My 'lord, is my response.
Remember that Bunyan was responding as to why he would not do all that he was doing for God within the confines of the Church of England. The transcription goes on to say:
Judge Wingate: This court would remind you, sir, that we are not here to debate the merits of the law. We are here to determine if you are, in fact, guilty of violating it. John Bunyan: Perhaps, My 'lord, that is why you are here, but it is most certainly not why I am here. I am here because you compel me to be here. All I ask is to be left alone to preach and to teach as God directs me. As, however, I must be here, I cannot fail to use these circumstances to speak against what I know to be an unjust and odious edict. Judge Wingate: Let me understand you. You are arguing that every man has a right, given him by Almighty God, to seek the Deity in his own way, even if he chooses without the benefit of the English Church? John Bunyan: That is precisely what I am arguing, My 'lord. Or without benefit of any church. Judge Wingate: Do you know what you are saying? What of Papist and Quakers? What of pagan Mohammedans? Have these the right to seek God in their own misguided way? John Bunyan: Even these, My 'lord. Judge Wingate: May I ask if you are articularly sympathetic to the views of these or other such deviant religious societies? John Bunyan: I am not, My 'lord. Judge Wingate: Yet, you affirm a God-given right to hold any alien religious doctrine that appeals to the warped minds of men? John Bunyan: I do, My'lord. Judge Wingate: I find your views impossible of belief And what of those who, if left to their own devices, would have no interest in things heavenly? Have they the right to be allowed to continue unmolested in their error? John Bunyan: It is my fervent belief that they do, My'lord. Judge Wingate: And on what basis, might r ask. can you make such rash affirmations? John Bunyan: On the basis, My 'lord, that a man's religious views- or lack of them- are matters between his conscience and his God, and are not the business of the Crown, the Parliament, or even, with all due respect, My 'lord, of this court. However much I may be in disagreement with another man's sincerely held religious beliefs, neither I nor any other may disallo his right to hold those beliefs. No man's right in these affairs are . secure if every other man's rights are not equally secure.
I do not know of anyone who could have expressed the whole idea of soul liberty in the words of man any more clearly than Bunyan stated in 1660. Every man can seek God as he pleases. This means that we cannot force our religious faith or teaching on anyone. It means clearly that no one can be coerced into being a Baptist and believing what we believe. It means that we can do no arm-twisting, or anything of that sort, to make anyone believe what we believe. Every man has been created by God with the ability to choose to follow God or to follow some other god.
Personal accountability to God is a distinctive of our faith. It is something we believe, and out of this distinctive come other distinctives that we identify with as Baptist people.
The Priesthood of Every Believer
The priesthood of the believer means that every believer can go to God through the merit of Jesus Christ. Christ and Christ alone is the only way to God. All of us who have trusted Christ as Saviour enjoy the glorious privilege of the priesthood of the believer and can access God through the merits of our Lord and Saviour Jesus Christ.
The Bible says in I Timothy 2: 1-6,
I exhort therefore, that, first of all, supplications, prayers, intercessions, and giving of thanks, be made for all men,· for kings, and for all that are in authority; that we may lead a quiet and peaceable life in all godliness and honesty. For this is good and acceptable in the sight of God our Saviour,· who will have all men to be saved, and to come unto the knowledge of the truth. For there is one God, and one mediator between God and men, the man Christ Jesus; who gave himself a ransom for all, to be testified in due time.
Take special note of verse five, "For there is one God, and one mediator between God and men, the man Christ Jesus."
Any man, anywhere in this world can go to God through the Lord Jesus Christ.
1 Peter 2:9 says, "But ye are a chosen generation, a royal pn~ • thood , an . holy nation, a peculiar people; that ye should. shew forth the praises of hzm who hath called you out of darkness into his marvellous light. "
Christians have access to God. You can personally talk to God. You can take your needs to the Lord. Whatever your needs are, you can take those needs to the Lord. You, as an individual Christian, can go to God through the Lord Jesus Christ, your High Priest who "ever liveth to make intercession" for you (Hebrews 7:25).
We have no merit of our own. We do not accumulate merit. People may make reference to a time of meritorious service someone has rendered, but we cannot build up "good works" that get us through to God. Each day, we must come before God as needy sinners approaching Him through the finished work of Christ and Christ alone.
The Bible teaches the personal accountability of every human being to God. We cannot force our religion on anyone or make anyone a believer. We cannot force someone to be a Christian. Think of how wrong it is to take babies and allow them later in life to think they have become Christians by an act of infant baptism. Yes, they have a right to practice infant baptism, but we do not believe this is biblical because faith cannot be forced or coerced.
There are places in the world where the state is under a religion. There are places in the world where religion is under the state-the state exercises control over the faith of people. This is not taught in the Bible. Then, there are countries like ours where the church and the state operate side by side.
Throughout history, people who have identified with Baptist distinctives have stood as guardians of religious liberty. At the heart of this liberty is what we refer to as ndividual soul liberty. I am grateful to be a Baptist.
The Power of Influence Where does this teaching of the priesthood of every believer and our personal accountability to God lead us? It leads us to realize the importance of the power of influence. This is the tool God has given us. I want to give you an Old Testament example to illustrate the matter of influence.
Judges 21 :25 tells us, "In those days there was no king in Israel: every man did that which was right in his own eyes."
In the days of the judges, every man did what was right in his own eyes with no fixed point of reference.
God's Word continues to describe this time of judges in Ruth 1:1, ''Now it came to pass in the days when the judges ruled, that there was a famine in the land. " God begins to tell us about a man named Elimelech, his wife Naomi, and his sons. He brings us to the beautiful love story of Ruth and Boaz. God tells us that at the same time in which the judges ruled, when there was anarchy in the land, this beautiful love stor of Boaz and Ruth took place.
This story gives us interesting insight on the responsibility of the Christian and the church. In the midst of everything that is going on, we are to share the beautiful love story of the Lord Jesus Christ and His bride. We need to tell people about the Saviour.
The same truth is found throughout the Word of God. Philippians 2:15 states, "That ye may be blameless and harmless, the sons of God, without rebuke, in the midst of a crooked and perverse nation, among whom ye shine as lights in the world. "
We are "in the midst ofa crooked and p erverse nation." This is why the Lord Jesus said in Matthew 5:16, "Let your light so shine before men, that they may see your good works, and glorify your Father which is in heaven. " Let your light shine!
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have diolauges. Singing that is sacred is taken out and the worlds music comes in. All revrence is gone. What so many are attempting to do in order to build up their ministry is actualy what will cause the demise of their ministry. We will never make a difference without being willing to be differnt, Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it cais the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have dialogue. Singing that is sacred is taken out, and the world's music comes in. All reverence is gone. What so many are attempting to do in order to build up their ministry is actually what will cause the demise of their ministry. We will never make a difference without being willing to be different. It is Christ who makes us different. Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it is the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him.
As this world becomes increasingly worse, the more off-thewall and ridiculous we will appear to an unbelieving world. The temptation will come again and again for us to simply cave in.
When one finds people with sincerely held Baptist distinctives, he finds those people have a passion for going in the power of the Holy Spirit, obeying Christ, preaching the gospel to every creature. I am grateful to God to say, "I am a Baptist."
Baptists know it is because of what we find in the Bible about soul freedom, personal accountability, and the priesthood of every believer that we must use the power of Spirit-filled influence to win the lost to Christ. If we disobey Christ by conforming to the world, we lose our influence.
May the Lord help us to be unashamed to bear His reproach and be identified with our Lord Jesus Christ.
The Way of Salvation
Do you know for sure that if you died today you would go to Heaven?
1. Realize that God loves you
God loves you and has a plan for your life. "For God so loved the world, that he gave His only begotten Son, that whosoever believeth in him, should not perish but have everlasting life" (John 3:16 ).
2. The Bible says that all men are sinners
Our sins have separated us from God. "For all have sinned, and come short of the glory of God" (Romans 3:23). God made man in His own image. He gave man the ability to choose right from wrong. We choose to sin. Our sins separate us from God.
3. God's word also says that sin must be paid for
"For the wages of sin is death" (Romans 6:23 ). Wages means payment. The payment of our sin is death and hell, separation from God forever. If we continue in our sin, we shall die without Christ and be without God forever.
4. The good news is that Christ paid for our sins
All our sins were laid on Christ on the cross. He paid our sin debt for us. The Lord Jesus Christ died on the cross, and He arose from the dead. He is alive forevermore. "But God commendeth his love toward us, in that, while we were yet sinners, Christ died for us" (Romans 5:8).
5. We must personally pray and recieve Christ by faith as our saviour
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
Lets review for a moment
- Realize That God Loves You - John 3: 1
- All are sinners - Romans 3:21
- Sin Must Be Paid For - Romans 6:23
- Christ paid for our sins - Romans 5:8
- We Must Personally Pray and Receive Christ as Our Saviour - Romans 10:13
- Pray and recieve Christ as your saviour
Lord, I know that I am a sinner. If I died today I would not go to heaven. Forgive my sins and be my Saviour. Help me live for You from this day forward. In Jesus' name, Amen.
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
~navluc-latmes
-
-
 @ 32e18276:5c68e245
2023-07-30 21:19:40
@ 32e18276:5c68e245
2023-07-30 21:19:40Company Overview:
Damus is the pioneering iOS nostr client. Through its platform, Damus empowers billions on iOS with the tools for free speech and free speech money. If you're driven to bring freedom technology to the masses and ignite change, we invite you to join our mission.
Job Description
- Collaborate on iOS Damus in tandem with our core developer, Will Casarin, and the broader Damus team.
- Implement our vision as laid out in our product roadmap: https://github.com/orgs/damus-io/projects/3/views/1.
- Embrace the fun and critical mission of undermining totalitarian regimes across the globe.
Job Requirements
- A genuine passion for freedom technology.
- At least one year of collaborative development experience.
- Experience building SwiftUI iOS apps.
- Passionate about design and user experience.
- Eager to work in close coordination with Damus lead developer, Will, and a dedicated team spanning development, design, and product.
- Commitment to a full-time role, although we remain open to discussing alternative arrangements.
Bonus Qualifications
- Experience with Nostr development.
- Experience with C.
- Previous work in free and open source projects.
- A publicly shareable portfolio.
Job Structure
- A one-month paid probationary period to ensure a mutual fit.
- Upon successful completion of the trial, the opportunity for a six (6) month contractual engagement.
- The potential for contract renewal, contingent on funding.
Application Process:
Interested candidates should forward a motivational statement alongside their CV/portfolio to vanessa@damus.io. -
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41\n> "Who do you say that I am?" \n\nIn Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.\n\n1. Who they tell us they are.\n2. Who others say about them.\n3. What we observe for ourselves.\n\nPutting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.\n\nWith this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way? \n\nThe default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.\n\nThis falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.\n\nI don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like...\n Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover.\n Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading.\n Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed.\n Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon.\n Have a full pet-names override.\n\nI think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.\n\n### A note on anonymity\nReal world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never* be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety. \n\nIf you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ e6817453:b0ac3c39
2023-08-12 16:24:37
@ e6817453:b0ac3c39
2023-08-12 16:24:37I am tech-heavy and blog mainly about decentralized tech, but I have a secret passion and a secret weapon - team meditation with classical gong fu cha style .
Tea meditation is shrouded in legends and mysteries, and we will undoubtedly delve into them. Today, we will discuss how to ground oneself using tea and the role of meditation in this process.
The tea ceremony is both a routine and meditative process: - Setting up the teapot - Warming the teaware - Getting acquainted with the tea - Rinsing the tea - Inhaling the aroma of the rinsed tea - The first pour
The key is to focus intently on the aroma and taste. After sipping, wait... but what about the aftertaste and sensations? Focus on what you feel. What lingers on the tongue?
Repeat this cycle, pour after pour, until the tea begins to fade.
However, there's a catch - our brain learns quickly. To experience a "wow" sensation or an "aha, something new!" feeling with a dose of dopamine, we constantly need to taste something new and often change what we drink. Otherwise, instead of fascination, our lazy brain might say, "Hold on, dude, I'll tell you how it's going to be," and we might start worrying about dire outcomes.
Tea meditation is fascinating, especially when we have something to work with and frequently trick our brains. With the same tea and materials, you can: - Adjust the tea dosage - Change the temperature - Alter the pouring time - Switch the teaware - Mix the tea or pair it with food
The most important thing is to listen to yourself, your sensations, and taste. Observe how the tea unfolds within you. Aged sheng pu-erh teas stand out with their complex bouquets and aftertastes, offering flavors that can be dissected for hours.
Taste is a deceptive sensation, more about aroma than flavor. It's a complex sensory experience that encompasses not just the tea but also the surrounding environment: - Aesthetics of the teaware - Tactile sensations of the teapot and cups - Ambient aromas - Room temperature - Music - Company and surroundings - Most notably, your inner state
I love pairing tea with essential oils. However, the essence of this practice is to shift your focus to the physical sensations of self, akin to feeling the earth with bare feet.
Benefits of Tea Meditation for Focus
Tea meditation is not just a ritual; it's a practice that enhances focus and concentration. Here are some benefits of tea meditation for focus:
- Mindfulness: The process of preparing and savoring tea requires attention to detail, helping you stay present and mindful.
- Sensory Awareness: Focusing on the aroma, taste, and aftertaste of tea heightens sensory awareness, training the mind to notice subtle nuances.
- Reduces Distractions: Engaging in the tea ceremony provides a break from digital distractions, allowing the mind to relax and refocus.
- Enhances Concentration: Repeating the steps of the tea ceremony and focusing on each aspect cultivates concentration and discipline.
- Grounding: The tactile experience of handling teaware and the warmth of the tea can be grounding, anchoring you in the present moment.
Incorporating tea meditation into your daily routine can be a transformative experience, sharpening your focus and offering a serene moment of reflection amidst the chaos of daily life.
-
 @ 8f014c5a:f9bbae3b
2023-08-12 14:47:07
@ 8f014c5a:f9bbae3b
2023-08-12 14:47:07In a much-anticipated showdown that had football fans on the edge of their seats, Arsenal opened their 2023-2024 Premier League season against Nottingham Forest. The clash was scheduled to kick off at 12:30 GMT +1, but a surprising 30-minute extension added an extra layer of anticipation. As the referee's whistle finally echoed through the stadium, little did we know we were in for an enthralling encounter that would keep us hooked until the final whistle.
 J. Turner in action
J. Turner in actionThe first half was dominated by the Gunners, asserting their dominance with flair and finesse. In the 26th minute, Gabriel Martinelli orchestrated a magnificent play, delivering a pinpoint assist to Eddie Nketiah, who buried the ball beneath the vigilant Nottingham Forest goalkeeper. The crowd erupted in cheers as Arsenal claimed the lead.
 Nketiah's goal
Nketiah's goalBut the drama didn't stop there. Just six minutes later, Bukayo Saka showcased his prodigious talent, launching a stunning strike from the edge of the box. The ball swerved and curved like a guided missile, leaving the Nottingham Forest goalie helpless. The net rippled, and the Emirates Stadium was awash with euphoria.
 Saka's Goal
Saka's Goal  Saka celebrates after scoring the second goal.
Saka celebrates after scoring the second goal.As the half drew to a close, the tension simmered. A rough tackle from Nottingham's J. Timber in the 45+5 minute earned him a yellow card, a testament to the intensity of the match. Arsenal's grip on possession was undeniable, with a staggering 85% of the ball under their control, leaving Nottingham Forest chasing shadows.
The addition of Declan Rice to Arsenal's midfield proved to be a masterstroke. His presence added steel to the Gunners' play, allowing them to dictate the tempo of the game. Martinelli, an unstoppable force on the field, drew fouls as Nottingham's defense grappled to contain him.
As the second half commenced, Nottingham Forest seized a rare attacking opportunity. A ball sent into the box resulted in ricochets that forced Arsenal's goalkeeper Aaron Ramsdale into action, making a smart save in the 56th minute. The visitors were determined to turn the tide, unleashing a wave of attacking intent.
 Notthingham's forest Willy in action with Nketiah
Notthingham's forest Willy in action with NketiahSubstitutions added a fresh twist to the unfolding drama. In the 71st minute, Danilo made way for Taiwo Awoniyi, signaling Nottingham Forest's desire to enforce their side attacks. Arsenal responded with their own change, as Nketiah exited the pitch for Trossard in the 74th minute.
As the clock ticked on, Declan Rice came inches away from opening his goal-scoring account for Arsenal. His audacious 25-yard attempt showcased a delicate finesse, but Turner, Nottingham's vigilant goalkeeper, tipped the ball onto the woodwork, denying the England midfielder a moment of glory.
In a valiant push, Nottingham Forest managed to claw back a goal in the 82nd minute. Elanga, a catalyst for the visitors' resurgence, raced down the flank and delivered a precise cross to Awoniyi, who exhibited exceptional composure with a first-time finish at the near post making the score line 2-1.
Awoniyi picks the ball after the goal
The closing moments saw frenetic action. Gabriel Magalhaes replaced Martinelli in the 86th minute, adding defensive fortitude to Arsenal's ranks. The final whistle loomed, and as the match headed into added time, both teams battled valiantly. In a flurry of activity, Magalhaes received a yellow card, further highlighting the match's intensity.
 Nottinhham forest's goal keeper applaud fans after the match
Nottinhham forest's goal keeper applaud fans after the matchAs the referee signaled the end, Arsenal emerged victorious with a narrow lead. The lone goal secured their triumphant start to the 2023-2024 Premier League season. The fans' jubilation echoed through the Emirates Stadium as they celebrated a hard-fought win that sets the tone for an exhilarating season ahead. Arsenal had delivered, and the football world watched in awe.
-
 @ cca7ef54:e7323176
2023-08-06 08:59:21
@ cca7ef54:e7323176
2023-08-06 08:59:21
วันที่โลกกำลังจะแตกสลาย.. คุณตัดสินใจล่องไปกับเรื่อโนอาห์ เรือที่พาคุณหลุดพ้นจากชีวิตอันแสนบัดซบที่คุณเริ่มเบื่อหน่ายกับมัน บนเรื่อเต็มไปด้วยผู้คนที่มีความหวัง พวกเขานั่งนิ่งๆ มองหน้ากันไปตลอดทาง สภาวะที่เงียบสงัดเพราะต่างคนต่างยังไม่คุ้นเคยซึ่งกันและกัน แต่ลึกๆ ในใจพวกเขาต่างก็รู้ดีว่า คนเหล่านี้ตรงหน้าคือคนที่มีจุดมุ่งหมายเดียวกัน

การเดินทางนั้นแสนยาวไกล เรือต้องฝ่าพายุคลื่นลมนับครั้งไม่ถ้วน พวกเขาไม่มีทางเลือกอื่น นอกจากลุกขึ้นมาช่วยกันคนละไม้คนละมือ บางคนทำหน้าที่อุดรอยรั้วบริเวณกาบเรือ บางคนดูแลเครื่องยนต์ อีกส่วนทำหน้าที่วิดน้ำที่หลั่งไหลเข้ามา ไม่มีใครต้องการให้เรือลำนี้อัปปาง ในที่สุดพวกเขาก็ได้เห็นถึงความทุ่มเทของกันและกัน

บนเรือมีคนไม่ยังไม่แข็งแรงพอจะช่วยอะไรคนอื่นได้ พวกเขาไม่ต้องการเป็นตัวถ่วง ไม่มีใครอยากไร้คุณค่าในสถานการณ์นี้ พวกเขาหาน้ำหาอาหารมาคอยส่งให้คนอื่นๆ ที่กำลังออกแรงอย่างเหน็ดเหนื่อย มันมีคนที่โดดเด่นที่สุดทำหน้าที่คล้ายเป็นกัปตันของเรือ เขาได้รับเสียงปรบมือ เขาได้รับกำลังใจ เขาได้รับอาหาร ทุกคนต่างรับรู้ได้ถึงความจริงใจที่มีให้แก่กัน ทุกคนรับรู้ได้ถึงเจตนาร่วมในการประคับประครองเรือไปให้ถึงฝั่ง

เมื่อพายุสงบลง พวกเขานั่งลงและพูดคุยกันถึงเรื่องที่พึ่งเกิดขึ้น ความรู้สึกพรั้งพรูปนความสุขที่แบ่งปันให้แก่กันนั้นหลากหลาย จากในตอนแรกที่เรือนั้นเงียบราวกับป่าช้า ตอนนี้เต็มไปด้วยเสียงจอแจ หลายคนได้พบเพื่อนที่รู้ใจ บางคนได้พบกับคู่รักที่ถูกใจ สังคมเล็กๆ ภายในเรือเริ่มก่อร้างสร้างตัวเป็นสังคมที่ใหญ่ขึ้น ทุกคนรู้สึกถึงความเป็นส่วนหนึ่ง ความรับผิดชอบต่อเรือลำเดียวกัน
มีคนอาสาจะออกเรือเล็กกลับไปยังจุดที่จากมา เขาต้องการนำเรื่องราวอันน่าประทับใจนี้ไปเผยแพร่ให้กับคนอื่นๆ เขาต้องการให้คนที่เหลือบนแผ่นดินเก่าได้รับชีวิตที่ดีกว่า คนกลุ่มเล็กๆ นี้ช่างเสียสละและมีใจเมตตา

เรือโนอาห์พาทุกคนมาส่งยังสถานที่ใหม่ มันได้สวยงามโสภาในแบบที่ทุกคนได้จินตนาการเอาไว้ มันเป็นสถานที่รกร้างที่อุดมสมบูรณ์ที่ยังไม่ได้รับการจัดสรรใดๆ ธรรมชาติที่นี่ยังเพรียบพร้อม เต็มไปด้วยทรัพยากรที่ล้นหลาม ความแตกต่างทางด้านทักษะและความชำนาญทำให้แต่ละคนทำในสิ่งที่ต่างกัน แต่ทั้งหมดก็ทำไปเพื่อสร้างสังคมใหม่ที่ให้คุณค่าในชีวิตของกันและกัน ไม่มีใครจินตนาการได้ว่าอีก 5 ปีนับจากนี้ พื้นที่แห่งนี้จะเป็นเช่นไร

มันให้กำเนิดผู้นำในด้านต่าง ๆ นักเผยแพร่ทางความคิด นักดนตรี ศิลปิน นักวิจารณ์ไปจนถึงนักข่าวประชาสัมพันธ์ สังคมที่หลากหลายกำลังก่อตัวขึ้นบนความหวังอันยิ่งใหญ่ ผู้ที่สร้างคุณค่าแก่สังคมได้รับความเชิดชู กลายเป็นที่กล่าวขวัญถึง ผู้ที่นึกถึงประโยชน์ส่วนตัวเป็นใหญ่ ต้องหลบไปอยู่เงียบๆ ท้ายเกาะ แต่ละคนค้นพบที่ทางของตัวเอง ภายใต้สังคมที่ไม่มีการปกครองหรือควบคุม เรือลำนี้ได้พาพวกเขามาพบกับสังคมที่ใฝ่ฝันถึงมานาน
เราไม่สามารถจินตนาการต่อไปได้ว่าชีวิตบนแผ่นดินใหม่นี้จะเป็นอย่างไรต่อไป เราจะคิดถึงเรื่องนั้นไปทำไมกันเล่า.. ตราบใดที่วันนี้เรายังมีความสุขกับมันดี

ชายผู้หนึ่งเดินออกมาจากฝูงชนเพื่อกลับไปเยี่ยมลำเรือที่ถูกจอดทิ้งสมอเอาไว้ เขามองมันด้วยความรู้สึกซาบซึ้งและเต็มไปด้วยคำขอบคุณ ส่วนต่างๆ ของเรือเริ่มผุพังไปตามกาลเวลา แต่ชื่อของมันยังคงมองเห็นได้อย่างชัดเจน..
เขาเดินเข้าไปใกล้ๆ ใช้มือสัมผัสไปยังชื่อที่สลักไว้ให้เห็นเป็นตระหง่าน เขาไม่มีคำพูดใด ๆ นอกจากความสุขที่บรรยายออกมาไม่ได้ ขอบคุณที่ส่งเรามาถึงตรงนี้ ขอบคุณที่มอบความหวังใหม่ให้กับเรา เรือโนอาห์ที่สวรรค์มอบให้เราในวันที่แสงกำลังมอดมิดลง
ขอบคุณนะ.. #NOSTR
-
 @ e29812e0:690887ef
2023-08-12 12:25:20
@ e29812e0:690887ef
2023-08-12 12:25:20Memes will remain forever. Memes aren't just funny images, but they are people who want to bring laughter to others.
A meme is a form of cultural idea, symbol, or practice that can be transmitted from one person's mind to another through writing, speech, gestures, rituals, mimicry, and various terms within an image that carries a humorous or satirical meaning, often imitating other events or phenomena. Simply put, it involves taking images and creating them into funny or comical pictures, spreading them through social media.
There are many online meme-generating websites that many people use or have seen. However, today, I will introduce websites that make creating memes online easy. Each website provides templates, and all you need to do is insert text. Let's take a look at the 4 recommended online meme-generating websites.
- https://imgflip.com/memegenerator
- https://www.iloveimg.com/th/meme-generator
- https://photoretrica.com/th/meme-generator
- https://www.meme-arsenal.com/en/create/chose
If any of your friends have links to meme generators, you can comment to let each other know. This way, creative individuals can create and post humorous memes on social media.

-
 @ f6a5c82f:3aa6f2a0
2023-08-12 16:10:33
@ f6a5c82f:3aa6f2a0
2023-08-12 16:10:33Welcome to another series where we delve into the intricacies of Ethereum addresses. In this article, we'll demystify Ethereum addresses, their significance, and their role in the Ethereum ecosystem. We'll simplify complex concepts, provide real-world examples, and share practical tips to ensure you're adept at handling Ethereum addresses with confidence.
By the time you finish reading, you'll have a solid grasp of Ethereum addresses, empowering you to handle transactions, engage with smart contracts, and secure your assets within Ethereum. Let's jump in and master the world of Ethereum addresses!
Understanding Ethereum Addresses
Think of Ethereum addresses as the digital equivalents of traditional bank accounts, but for the Ethereum blockchain. These 20-byte hexadecimal numbers uniquely identify accounts on Ethereum and serve as the gateway for sending, receiving, storing Ether (ETH), tokens, and accessing decentralized applications (DApps). Each address comprises alphanumeric characters and typically begins with "0x" to indicate its hexadecimal nature.
Types of Ethereum Accounts
There are two primary types of Ethereum accounts, each with its own address:
-
Externally Owned Accounts (EOAs): These are user-controlled accounts used for managing Ether and tokens. EOAs facilitate transactions like sending Ether to other addresses and can be created using wallet software such as MetaMask.
-
Contract Accounts: Owned by smart contracts, these accounts interact with the Ethereum blockchain. Each smart contract deployed has a unique contract address, serving as an identifier.
Differences Between EOAs and Contract Accounts
EOAs:
-
Created by users.
-
Have a private-public key pair.
-
Controlled by the user's private key.
-
Can sign transactions.
-
Interact via transactions.
Contract Accounts:
-
Created by deploying smart contracts.
-
No private-public key pair.
-
Controlled by smart contract code.
-
Cannot sign transactions.
-
Interact via transactions and events.
-
Address Generation
EOA Address Generation:
-
Generate a random private key.
-
Compute the corresponding public key through elliptic curve multiplication.
-
Hash the public key using the Keccak-256 algorithm.
-
Take the last 20 bytes to get the EOA address. Prefix the address with "0x."
Contract Address Generation:
Contract addresses are generated using a combination of the deploying account’s address and a nonce value, which represents the number of transactions sent from that account.
The contract address is derived by RLP encoding the deploying account’s address and the nonce using the Keccak-256 hashing algorithm.
Contract addresses are deterministic, meaning that the same contract deployed from the same account with the same nonce will always result in the same address.
Address obfuscation techniques, like hashing and mixing, to enhance privacy. ZKPs allow users to prove ownership without revealing specific details.
Here is a more detailed explanation of the process:
-
The deploying account’s address is obtained. Let’s assume the deployer’s account’s address is: 0x0123456789abcdef0123456789abcdef0123456
-
The nonce value is obtained. Let’s assume the nonce value is 5
-
The deploying account’s address and the nonce value are concatenated. We concatenate the deploying account’s address and the nonce value: 0x0123456789abcdef0123456789abcdef01234565
-
The concatenation is then RLP encoded.
-
Keccak-256 Hash: 0x4b6f5a3dfc911e992c3d8f38c6bb9d1563b5e9a526260ee1a83693a8e56f4f48
-
The first 20 bytes of the hash are used as the contract address.
- Following our example, the Contract Address is prefixed with the “0x” character.: 0x4b6f5A3dFc911E992c3D8F38C6bb9D1563B5e9A5
Note that this is a simplified example for illustration purposes, and in practice, additional steps and considerations might be involved in the deployment process.
Conclusion
Mastering Ethereum addresses is vital for seamless navigation within the Ethereum ecosystem. This expertise empowers you in transactions, smart contract interactions, and asset security. By understanding Ethereum addresses and embracing privacy measures, you contribute to the decentralized movement. Thank you for reading, and stay tuned for more insights in my upcoming articles!
-
-
 @ a4a6b584:1e05b95b
2023-07-25 23:44:42
@ a4a6b584:1e05b95b
2023-07-25 23:44:42Introducing Box Chain - a decentralized logistics network enabling private, secure package delivery through Nostr identities, zero-knowledge proofs, and a dynamic driver marketplace.
Identity Verification
A cornerstone of Box Chain's functionality and security is its identity verification system. Drawing on the principles of decentralization and privacy, it eschews traditional identifiers for a unique, cryptographic solution built on the Nostr protocol.
When a new user wishes to join the Box Chain network, they begin by generating a unique cryptographic identity. This identity is derived through complex algorithms, creating a unique key pair consisting of a public and a private key. The public key serves as the user's identity within the network, available to all participants. The private key remains with the user, a secret piece of information used to sign transactions and interactions, proving their identity.
Unlike many centralized systems, Box Chain does not require any form of real-world identification for this process. This is crucial for a few reasons. First, it ensures the privacy of all participants by not requiring them to disclose sensitive personal information. Second, it allows Box Chain to operate independently of any jurisdiction, enhancing its universal applicability.
Once their identity is established, participants engage in the network, accepting and fulfilling delivery tasks. Each successful delivery, confirmed by the receiver, contributes to the participant's reputation score. This reputation score is publicly linked to their identity and serves as a measure of their reliability and performance.
A critical aspect of mitigating potential identity fraud is the stake requirement. Each participant, before they can accept a delivery task, is required to stake a certain amount of Bitcoin. This acts as a form of collateral, held in escrow until the successful completion of the delivery. The staked amount is forfeited in case of fraudulent activities or non-delivery, creating a strong financial disincentive against dishonest behavior.
Overall, the identity verification system in Box Chain, built on unique cryptographic identities, a reputation score system, and the staking mechanism, provides a robust framework to ensure reliability and trust in a decentralized, borderless context. It significantly mitigates the risks of identity fraud, further strengthening Box Chain's promise of secure, efficient, and private package delivery.
Zero-Knowledge Proof Shipping Information
Box Chain's unique approach to preserving privacy while ensuring accurate delivery relies heavily on the concept of Zero-Knowledge Proofs (ZKPs). This cryptographic principle allows for the verification of information without revealing the information itself.
When a package is set for delivery, the sender provides the recipient's address. This address is immediately subjected to cryptographic transformation - the details are processed and turned into a form that is impossible to understand without a specific decryption key. This transformation process is designed to ensure maximum privacy - the original address remains known only to the sender and, eventually, the recipient.
In this transformed state, the address can still be verified for its validity without revealing its actual content. This is where ZKPs come into play. The sender, by leveraging ZKPs, can prove to the Box Chain system that they possess a valid address without needing to reveal the specifics of that address. This protects the privacy of the recipient by ensuring their address isn't openly visible on the system.
For the delivery process, the route is broken down into relay points, each assigned a particular driver. This relay-based system plays a significant role in preserving privacy and ensuring package safety. Instead of providing the entire route to each driver, they only receive the location of the next relay point. This is accomplished by giving them a cryptographic key which, when applied to the encrypted route data, reveals only the necessary information - the location of the next relay driver.
This way, the sender's address and recipient's final address remain as private as possible. Moreover, it enables the package to be securely handed off from one relay driver to the next, each having access to only the information necessary for their leg of the journey.
It's important to note that this process, while extremely secure, can take a longer time due to its relay nature and the cryptographic processes involved. There may also be a need to introduce a timeout mechanism for each leg of the journey to ensure drivers complete their part in a reasonable timeframe.
By incorporating ZKPs and a relay-based delivery system, Box Chain is able to provide a level of privacy and security that is rare in the logistics world, striking a balance between efficiency and privacy.
Delivery Confirmation
One of the key aspects of ensuring the success and trustworthiness of Box Chain's decentralized package delivery service is the process of delivery confirmation. To make this process as secure, transparent, and reliable as possible, Box Chain implements a multi-signature approach that leverages the power of cryptography.
When a delivery is made, it is not enough to simply leave the package at the prescribed location. Confirmation of delivery is critical to ensure the transaction is closed and the delivery person can receive their payment. This is where the multi-signature approach comes into play.
In essence, a multi-signature approach means that more than one party needs to provide a digital signature to confirm the transaction. For Box Chain, this involves both the receiving party and the delivery person. After the delivery person leaves the package at the prescribed location, they would use their private cryptographic key to sign a confirmation of delivery. The recipient, upon receiving the package, would do the same.
These digital signatures are securely generated using each party's private key and are incredibly difficult, if not impossible, to forge. This means that when both signatures are provided, the system can be confident that the package was delivered and received successfully.
As a further layer of security and accuracy, Box Chain incorporates geolocation confirmation into its delivery confirmation process. This means that when the delivery person signs the confirmation of delivery, their geographic location is checked against the intended delivery location. If the two locations match within an acceptable margin of error, this acts as another layer of proof that the delivery was made successfully.
This process ensures that delivery confirmations are not only secure but are also indisputable. It provides a significant level of trust and reliability, both for the sender and receiver, but also for the delivery people who are looking to receive their payments.
Furthermore, it aligns with the principles of decentralization and privacy, leveraging the power of cryptography and blockchain technology to provide a secure, transparent, and effective service. This approach positions Box Chain as a pioneer in combining the gig economy with the blockchain technology, providing a unique and secure package delivery solution.
Package Security
Guaranteeing the security of packages throughout transit is fundamental to Box Chain's service offering. To accomplish this, Box Chain utilizes a unique stake system that incentivizes delivery drivers to handle packages with the utmost care.
When a sender initiates a delivery, they specify the value of the package being shipped. This value is used to determine the stake amount that the delivery person must deposit to accept the delivery task. The stake functions as a form of shipping insurance, held in escrow by the Box Chain system until successful completion of the delivery.
The stake amount set by the sender is commensurate with the value of the package, allowing the sender to decide how much insurance they deem appropriate for their shipment. Higher-value packages may necessitate a larger stake, serving to reassure the sender that the delivery person has a significant financial incentive to ensure the safe delivery of the package.
In the event that a package is lost or damaged, the stake acts as a safety net for the sender. The staked amount is forfeited by the delivery driver and is transferred to the sender as compensation for their loss.
This system not only provides reassurance to the sender, but also gives a powerful incentive for delivery drivers to handle the packages with care. By having their own funds at risk, delivery drivers are likely to go the extra mile to ensure packages are safely delivered to their destination.
Further enhancing the security of the package, Box Chain uses a multi-signature approach during the relay handoff process. The current delivery driver and the next relay driver must both provide a digital signature to confirm the handoff. This ensures that responsibility for the package is officially transferred from one party to the next in a secure and verifiable manner. This "chain" of signatures creates an auditable trail that adds another layer of security and trust to the process.
Through the combination of a stake system and multi-signature handoff confirmation, Box Chain provides a comprehensive security solution that ensures packages are not only delivered efficiently but are also safeguarded throughout their transit journey.
Routing Algorithm and Pricing Mechanism
The efficiency and economic fairness of Box Chain's service hinge significantly on its innovative routing algorithm and pricing mechanism. This system is designed to ensure a smooth journey for each package, while also ensuring that delivery drivers are fairly compensated for their work.
The journey of a package begins with the sender specifying the destination and offering a starting payment for delivery. This payment information is propagated to the network, along with the package's destination, where potential delivery drivers can view it. However, unlike traditional package delivery services, the journey and price aren't fixed from the onset. Instead, Box Chain employs a dynamic, decentralized, and market-driven approach to optimize routing and pricing.
The total journey is divided into smaller legs, each of which can be undertaken by different delivery drivers. The starting payment offered by the sender is not a flat rate for the whole journey but is instead used as an initial bid for each leg of the journey. This bid is then doubled, and the network waits for a delivery driver to accept the offer. If no one accepts, the bid continues to increase in increments, creating an auction-like environment.
This system allows the real-time market dynamics to determine the cost of delivery. Factors such as distance, package weight, or even current traffic conditions can influence how much a delivery driver is willing to accept for a leg of the journey. If a leg of the journey is particularly difficult or inconvenient, the price will naturally rise until it reaches a level that a delivery driver deems worthwhile.
By allowing the drivers themselves to choose which jobs to accept based on their own assessment of the work's value, Box Chain creates a fair, flexible, and dynamic market where compensation is closely tied to the effort and resources required to complete a delivery. This is akin to how the Tor network or the Lightning Network operates, but instead of data packets being routed and priced, Box Chain is doing this with physical packages in the real world.
Such a system not only incentivizes delivery drivers to participate but also ensures the service remains adaptable and resilient to changing conditions and demands. This represents a novel and intelligent use of blockchain technology to disrupt the traditional gig economy model, placing the power in the hands of the individual drivers and fostering a more equitable and efficient market.
Incentive for Participation
Box Chain's unique approach to package delivery provides a plethora of compelling incentives for individuals to participate in the network as delivery drivers. By offering the potential for higher earnings through a competitive and dynamic bidding system, Box Chain encourages active participation and healthy competition within its network.
Upon initiating a package delivery, the sender offers a starting bid for each leg of the journey. This bid is then escalated through the network, doubling with each round until a delivery driver accepts the task. This mechanism presents delivery drivers with the opportunity to earn more for their services, especially in cases where the journey is long or complex.
However, the competitive aspect of the bidding system also helps regulate the pricing. Although prices might be high initially, as more delivery drivers join the network and competition increases, the bid required to win a delivery job is likely to decrease. This dynamic balance ensures a fair market price for delivery services while also enabling delivery drivers to optimize their earnings.
Furthermore, Box Chain's reputation system, based on the Nostr protocol, provides an additional layer of incentive for delivery drivers. The reputation of each driver is tracked and publicly displayed, allowing senders to gauge the reliability and efficiency of their potential couriers. As drivers successfully complete deliveries and earn positive feedback, their reputation score increases.
This reputation score can play a pivotal role in the Box Chain economy. Drivers with higher reputation scores may demand higher bids for their services, reflecting their proven track record of successful deliveries. Alternatively, the system could grant priority in the bidding process to drivers with higher reputation scores. This not only incentivizes good performance and reliability but also helps to foster trust within the network.
Overall, Box Chain's combination of a competitive bidding system and a reputation-based incentive structure encourages active participation and ensures a high standard of service. By aligning economic incentives with high-quality service delivery, Box Chain empowers its participants while also ensuring a satisfying experience for its users.
Here is an additional section covering dispute resolution and failed delivery handling that could be added:
Dispute Resolution and Failed Deliveries
For a decentralized network like Box Chain, dispute resolution and handling of failed deliveries present unique challenges. To address these in alignment with its principles, Box Chain implements an arbitration-based system and a dual-stake mechanism.
In case deliveries fail due to recipients being unavailable or refusing, both the sender and recipient are required to stake funds as collateral. If the delivery cannot be completed, the stakes are forfeited and awarded to the delivery driver as compensation for their time and effort. This creates a disincentive for recipients failing to receive packages and ensures drivers are paid for their work.
For disputes between senders, recipients and drivers, Box Chain leverages a decentralized arbitration system built on the Nostr protocol. Independent arbitrators stake their own funds and adjudicate disputes based on review of evidence from both parties. Their incentive is a small percentage of the transaction amount.
The arbitration process involves submission of dispute details, review of evidence, ruling based on policies, and appeals handled by additional arbitrators if required. A majority ruling wins the appeal. This system, relying on staked incentives and the wisdom of the crowd, enables fair dispute resolution aligned with Box Chain's ethos.
By combining reciprocal stakes and decentralized arbitration, Box Chain is able to provide robust recourse around failed deliveries and disputes while retaining its principles of decentralization, privacy, and aligned incentives. These mechanisms strengthen the system and instill further user trust and satisfaction.
Bitcoin + Nostr = <3
The combination of Bitcoin and Nostr represents a powerful and synergistic integration of decentralized technologies. Bitcoin provides a secure, transparent and decentralized means of value transfer, while Nostr offers a decentralized protocol for creating and managing digital identities and data. Together, they can enable truly decentralized and privacy-preserving applications, like Box Chain, that have the potential to disrupt traditional business models and empower individuals around the world. The future looks promising with such advanced and transformative technologies working hand in hand.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ 908d47b6:a2bf38ad
2023-08-12 11:59:20
@ 908d47b6:a2bf38ad
2023-08-12 11:59:20How does solitaire work? Match cards in descending order and alternating suit to complete the four decks. But this is about more than just the game itself - it's about the opportunity to win real satoshis. The game is available as a mobile app for Android and iOS. You can Download it here
The integration of Bitcoin
Imagine winning a game of Solitaire and being rewarded by being credited with a certain amount of Satoshis. This integration of cryptocurrencies adds a whole new dimension to the game. You play not only to win, but also to use your skills and collect bitcoin rewards in the process. It's an interesting marriage of gaming and financial incentive. The whole thing works with a lottery system. By solving the game you will receive tickets with which you can earn real Satoshis in draws that take place several times a day.
What are satoshis actually?
Satoshis are the smallest unit of Bitcoin. Named after its creator, Satoshi Nakamoto, one satoshi represents one hundred millionth (0.00000001) of a bitcoin. Satoshis enable microscopic transactions and play a key role in fine-tuning values within the bitcoin economy.
Pay out Satoshis via Lightning
You have to withdraw your satoshis regularly, otherwise they will “expire”, means they are no longer withdrawable. So before you start playing, make sure you have a Lightning Wallet to receive your Satoshis. We recommend installing the “ Wallet of Satoshi ” to start with. This is particularly easy to use, even if some compromises have to be made. Find out more in our wallet guide .
Have you got the urge to test your solitaire skills and earn some real hard cash in the process? Dont forget to download it here. Share your thoughts and experiences in the comments below.
-
 @ e6817453:b0ac3c39
2023-08-12 15:55:51
@ e6817453:b0ac3c39
2023-08-12 15:55:51The advent of the digital era has stretched our identities beyond their physical boundaries. Today, we exist in an interconnected virtual realm, where our digital selves traverse across an array of platforms and services. As the line between the physical and digital world blurs, we find ourselves in the throes of a new concept: meta identity. This evolution makes understanding meta identity systems, and their guiding principles, crucial for navigating our future.
A “meta identity” represents an aggregated, holistic portrayal of an individual, organization, or system in the digital realm, drawn from a multitude of sources. Meta identity systems, therefore, are the frameworks that manage these meta identities, ensuring security, privacy, and efficient interactions in our increasingly digitized ecosystems.
To comprehend the core principles of meta identity systems, we must turn to Kim Cameron’s Laws of Identity. These seven tenets, devised by Microsoft’s former identity architect, still hold relevance and provide an invaluable lens to view meta identity systems.
1. User Control and Consent
In alignment with Cameron’s first law, meta identity systems are inherently user-centric. Users have direct control over their identities and determine what portions of their identity they share with which provider, fostering trust and enhancing user experience.
2. Minimum Disclosure for a Constrained Use
Meta identity systems uphold the principle of sharing the least amount of information necessary for a transaction, paralleling Cameron’s second law. With technologies like zero-knowledge proofs, users can validate their identities without revealing sensitive information.
3. Justifiable Parties
Meta identity systems also abide by the third law, meaning that digital identity information is only disclosed to parties having a necessary and justifiable place in a given identity relationship. This limits unnecessary data sharing and maintains privacy.
4. Directed Identity
A meta identity system can provide both “omnidirectional” identifiers for public use and “unidirectional” identifiers for private interactions, adhering to the fourth law. It facilitates the exchange of identity data without hampering security and privacy.
5. Pluralism of Operators and Technologies
Emphasizing Cameron’s fifth law, meta identity systems support a variety of identity technologies and operators. They ensure interoperability and smooth interaction by using standardized protocols and interfaces.
6. Human Integration
The sixth law — integration of the human user — is at the heart of meta identity systems. They aim to be user-friendly, and comprehensible to the everyday user, ensuring that individuals can easily manage and control their digital identities.
7. Consistent Experience Across Contexts
Finally, meta identity systems strive for a consistent user experience across multiple contexts, platforms, and services, adhering to the seventh law. This uniformity aids in creating a more reliable and holistic identity across the digital landscape.
The future of meta identity systems extends beyond just identity management. By providing a more detailed and accurate understanding of users, these systems open avenues for customization, personalization, and enhanced consumer targeting for businesses. Furthermore, technologies like blockchain and decentralized networks are catalyzing the potential of meta-identity systems, offering secure, private, and efficient digital identity management solutions.
As we navigate the increasingly digital landscape of our lives, understanding and implementing robust meta identity systems are of utmost importance. By adhering to the principles laid out by Kim Cameron’s Laws of Identity, meta identity systems provide a blueprint that respects digital autonomy while facilitating smooth, secure digital interactions.
In the digital era, meta identity systems stand at the forefront of innovation, promising far more than managing our digital identities. They are about redefining our digital existence
-
 @ 97c70a44:ad98e322
2023-06-29 15:33:30
@ 97c70a44:ad98e322
2023-06-29 15:33:30First, a product announcement.\n\nCoracle now supports connection multiplexing, which can reduce bandwidth usage by over 90% depending on how many relays you use. It's opt-in for now, but you can set it up by going to Settings and entering
wss://multiplextr.coracle.socialas your "Multiplextr URL".\n\nYou can check out the source code and self-host the library using this link. If you're a dev and want to add client support for multiplextr, the library I built to support this use case might be of use.\n\nNow, on to your regularly scheduled blog post.\n\n \n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n
\n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n -
 @ e6817453:b0ac3c39
2023-08-12 15:43:18
@ e6817453:b0ac3c39
2023-08-12 15:43:18 How DIDs talk to each other — DID Auth, DIDComm, DWN — what the difference
How DIDs talk to each other — DID Auth, DIDComm, DWN — what the differenceThe backbone of Trust over IP is secure messaging and transport protocols L2. But first we need to create addressable space somehow. ToIP focuses on autonomous decentralised identifiers.

© https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
It is not a focus of this article you could read about ToIPon my article but it is bring critical topic to the table — how to build a secure communication between SSI entities and agents ?
Addresses , Names and Identifiers
Identity is not identifiers but it is heavily depends on it. To communicate you need a address and authenticity check. You need to know with whom you talking and how to send him a message.
DIDs — Decentralised Identifiers deserve a separate post with a deep dive. But it serve 3 main goals:
- distribute a public key
- be decentralized cryptographic verifiable identifier
- define an analog of name in a global context
So you could threat a DID as a identity identifier or name that cryptographically proved and what more importantly binded but not coupled with a private key pair. The possibility of the signing key rotation is quite a crucial security feature.
DID Auth
In case when you need just a prove of ownership of DID or lets say prove of ownership of private key you could relay on did Auth.
Unfortunately it is more concept level and we do not have official standard for it.
It could be few possible implementations of it

Source of pictures and useful slides on topic (https://www.w3.org/Security/201812-Auth-ID/04_-_Day_1_-_Understanding_DID_Auth.pdf)
I have a separate video about did auth benefit over a WEB3 login
DID auth unlock a possibility to have a password-less, otp less login similar to FIDO but with a benefit of better security and a key rotation.
We have our own implementation of did auth as a library and widely use it for ssi agent
It is give a implementation of client and a server parts or in terms of Open Id — client and relying party

Still it is give more authenticity but live a message and communication protocol open.
Messages and DIDCommv2
Hyperladger and Aries community has a agent oriented architecture. It was a emerging need for message protocol to communicate between a agents. As a result of this efforts DIDComm was developed. Now it is independent from Hyperladger protocol under DIF umbrella.
https://identity.foundation/didcomm-messaging/spec/v2.0/
More details about DIDComm in a Video. You will see how DIDComm build on top of existing standards and define proper abstraction.
Still DID comm live a topic of persistence and async and offline communication open
Affinidi Messages
In era before DIDComm we implement a bit simplified transport layer over HTTP that solve few critical needs for us
- Use DIDs that already exists with out modification of document and need of service endpoints
- design of offline interaction and async messages
- create SSI hub that are secure and multi Tennant
As a result we have Affinidi messages
Is more modern and still emerging SSI hub that have a DID based message oriented architecture and offer security, permission management and persistence on top of IPLD data structures that compatible with IPFS.
https://identity.foundation/decentralized-web-node/spec/
Still as same as DIDComm it is require to have a service endpoint to a DWN user node for a communication.
It is still relatively new and under development. It have different philosophy and focus more on collection of data and access to data streams rather that messages.
Summary
- if you need something simple and move logic on the application side — go with did Auth and negotiate mainly on cryptography.
- if you need to reuse dids that already exist and has simple persistence and offline and async communication — take a look to affinidi messages
- if you are a protocol builder, look at DIDCOMMV2 https://didcomm.org/book/v2/. And figure out the best persistence and ACL yourself. Maybe you could combine https://ceramic.network/ and https://litprotocol.com/ solve your needs.
- keep an eye on DWN if you need a persistence and more collection and datastream oriented app
-
 @ d5415a31:b317849f
2023-08-12 11:38:14
@ d5415a31:b317849f
2023-08-12 11:38:14Below is a sample of my article on nostr...
*A dangerous trend has emerged in the United States where terms like free speech, censorship- resistant, privacy, and more have been co-opted by those on the political right, and tools enabling these principles argued or fought against by those on the political left. The truth is, freedom, privacy, and censorship resistant technologies are important for everyone regardless of political leanings and should not be politicized, lest we head down the path toward a dystopian future with no privacy or free speech guarantees, and only centralized institutions controlled by people with the ability to censor, revoke and remove important guarantees of freedom promoted in the spirit and language of the constitution. Just as bitcoin has falsely become politicized as a more right wing/libertarian thing, having no value, or a tool for criminals and those who disregard the dangers of climate change, open and decentralized protocols like nostr could enter the same cycle and become politicized or fought against unless we share more reasons why it is important for humanity and is not a political position to take. The fate of our ability to freely and openly communicate and have guarantees of privacy and property may rest on citizens of the world understanding the importance of open, censorship resistance protocols, and private end-to-end encrypted communication tools. *
One specific example I will focus on is Nostr. So, what is nostr?
Nostr was first conceptualized by pseudonymous bitcoin coder, Fiatjaf and “bitcoin tinkerer” Ben Arc. As described on nostr.how, run by JeffG:
“Nostr stands for “Notes and Other Stuff Transmitted by Relays”. Like HTTP or TCP-IP, Nostr is a protocol; an open standard upon which anyone can build. Nostr itself is not an app or service that you sign up for. Nostr is designed for simplicity and enables censorship-resistant and globally decentralized publishing on the web.”
The way in which we see the nostr protocol used and popularized today is via clients (i.e. apps/websites), like my personal favorite Damus, or Primal, Snort and dozens of others being built out by developers passionate about this protocol. Each user then adds relays (many are defaulted on most clients today), which is the way these messages get sent around in a decentralized way, and users can add free or even paid relays (by paying for relays, in bitcoin which is the money/medium of exchange used on nostr, users can eliminate the amount of spam or bots accessing relays/feeds and have a faster experience). Users can also sort their global feed based on relays, and more. The beauty of this system is that most traditional social media–twitter, facebook, instagram, linkedin, etc, is completely centralized. Twitter, for instance, manages the content and has its own server (or pays third parties to do so)–one central relay, in a way. So you can easily be censored or removed from using twitter for criticizing Elon Musk, posting a political statement that is unfavorable to decision makers within the company or a nation-state asking twitter to censor these types of messages, in the recent case of Turkey and its recent election, and more. With nostr, if you are censored on one relay, you still have endless amounts of other relays to write/post to. Nor is your nostr account tied to one specific relay or client. When each user signs up on nostr, an “npub” (think username) is created and an nsec (think password) that can be used to sign up for any client. Imagine if you had your twitter username and password, but you could also use that to sign into every other social media platform and it carried with it every post and connection you ever had on twitter. Pretty cool, right? But with this comes the responsibility of keeping your nsec (again, think password) written down in a safe place in the event you are logged out of a particular client, because there is no backup or password reset ability on most clients. There are browser extensions that save this information for you, but with any internet backup comes certain privacy risks as well.
So practically, nostr is a cool and easy way to use social media across multiple clients, leaving you with ultimate control and preference! Ideologically, it is so much more.
As I stated earlier, nostr is an open protocol, where anyone can post and build with it, leaving it to be censorship resistant and with you in control. As is the case with bitcoin, if you can access the internet, you can access nostr. I know many progressive friends of mine have been very frustrated with twitter/x’s/Elon’s selective control of who gets to practice “free speech” and who doesn’t on the platform. Many other self-described “free speech” platforms have been created, such as Trump’s Truth Social, Rumble, and more. But these platforms are FSINO, “Free Speech in Name Only.” They are still companies run by people with centralized control. When we say nostr promotes free speech and the user is in control, it isn’t because nostr is run by a self-described “free speech maximalist,” or because nostr has any specific political ideology. It is because the protocol is inherently open and free to use by anyone, and decentralized in a way where an infinite number of communities, ideologies, people, and movements can flourish and utilize the protocol however they wish. I believe it is technology and an internet enabled protocol as the cypherpunk movement intended: promoting freedom, censorship resistance, and the ability to be private and promote anonymity when needed (no KYC, government checks to use).
-
 @ d830ee7b:4e61cd62
2023-08-06 08:27:55
@ d830ee7b:4e61cd62
2023-08-06 08:27:55https://i.imgur.com/bUDUOZH.png On the day the world seemed on the brink of collapse, you chose to embark on Noah's Ark. An escape vessel from the mundane life you've grown weary of. The ship was filled with hopeful souls, silently gazing into each other's eyes throughout the journey. The silence stemmed from unfamiliarity, yet deep down, they all recognized a shared purpose.
https://i.imgur.com/ovK3sUm.png The voyage was long and fraught with challenges. The ship braved countless storms and turbulent waves. They had no choice but to rise and work together, each lending a hand. Some mended the ship's cracks, others tended to the engines, while a few bailed out the infiltrating water. No one wished for this ship to falter. Their collective dedication became evident.
https://i.imgur.com/6XaPlDc.png Some aboard lacked the strength to assist others. Yet, they didn't want to be burdens. No one wished to be valueless in such circumstances. They fetched water and food, delivering it to those laboring tirelessly. A standout individual emerged, acting as the ship's captain. He received applause, encouragement, and sustenance. Everyone acknowledged the genuine care they had for one another. They all recognized the collective spirit propelling the ship to shore.
https://i.imgur.com/eEPqbNN.png When the storm subsided, they sat and shared tales of the recent ordeal. A mix of raw emotions and shared joy permeated the air. From an initial silence, the ship now echoed with laughter and chatter. Many found kindred spirits, while some discovered love. A small society within the ship began to evolve into a larger community. Everyone felt a sense of belonging and responsibility towards their shared vessel.
A few volunteered to return to their point of origin. They wished to share this inspiring tale with others, hoping to offer them a better life. Such selfless and compassionate souls.
https://i.imgur.com/Tx5Z3Fu.png Noah's Ark brought them to a new realm. It was as magnificent as they had imagined. An untouched paradise, abundant and unclaimed. Nature here was pristine, overflowing with resources. Their diverse skills and expertise meant everyone had a unique role. Yet, all worked towards building a new society that valued everyone's life. No one could have predicted what this place would become in just five years.
https://i.imgur.com/9rRGLeT.png Leaders emerged in various fields, from thinkers to musicians, artists to critics, and even public relations experts. A diverse society was taking shape, built on grand hopes. Those who contributed value were celebrated and became the talk of the town. Those who were self-centered retreated to the island's quiet corners. Everyone found their path in a society free from governance or control. This ship had brought them to the society they had long dreamt of.
We can't predict what life on this new land will be like in the future. Why ponder about it when today brings us joy?
https://i.imgur.com/u5MZJXa.png A man stepped away from the crowd to visit the now-docked ship. He gazed at it with deep reverence and gratitude. The ship, weathered by time, showed signs of wear and tear. Yet, its name remained clearly visible.
He approached and gently touched the engraved name. Words escaped him, replaced by an indescribable joy. "Thank you for bringing us here, for granting us a new hope. The Noah's Ark that heaven bestowed upon us on that fading day of light."
"Thank you... #NOSTR."
-
 @ 97c70a44:ad98e322
2023-06-26 19:17:23
@ 97c70a44:ad98e322
2023-06-26 19:17:23Metadata Leakage\n\nIt's a well-known fact that Nostr's NIP 04 DMs leak metadata. This seems like an obvious flaw, and has been pointed out as such many times. After all, if anyone can see who you're messaging and how frequently, what time of the day, how large your messages are, who else is mentioned, and correlate multiple separate conversations with one another, how private are your communications really?\n\nA common retort repeated among those who "get" Nostr (myself included) is "it's not a bug, it's a feature". This hearkens back to the early days of the internet, when internet security was less than an afterthought, and social platforms throve on various permutations of the anonymous confessions-type app. How interesting to be able to flex to your friends about whom you're DMing and how often! Most conversations don't really need to be private anyway, so we might as well gamify them. Nostr is nothing if not fun.\n\nIn all seriousness though, metadata leakage is a problem. In one sense, Nostr's DMs are a huge improvement over legacy direct messages (the platform can no longer rat you out to the FBI), but they are also a massive step backward (literally anyone can rat you out to the FBI). I'm completely confident we'll be able to solve this issue for DMs, but solving it for other data types within Nostr might pose a bigger problem.\n\n# Social Content\n\nA use case for Nostr I've had on my mind these last few months is web-of-trust reviews and recommendations. The same sybil attack that allows bots to threaten social networks has also been used as a marketing tool for unscrupulous sellers. NPS surveys, purchased reviews, and platform complicity have destroyed the credibility of product reviews online, just like keyword-stuffed content has ruined Google's search results.\n\nProof-of-work would do nothing to defend against this attack, because the problem is not volume, it's false credibility. The correct tool to employ against false credibility is web-of-trust — verifiable trustworthiness relative to the end user's own social graph.\n\nThis is a huge opportunity for Nostr, and one I'm very excited about. Imagine you want to know whether the vibro-recombinant-shake-faker (VRSF) will result in visible abs in under 6 days. Well, it has over 4 thousand 5-star reviews on Amazon, and all the 1-star reviews are riddled with typos and non sequiturs. So it must work, and make you smarter into the deal! Well, sadly no, visible abs are actually a lie sold to you by "big gym".\n\nNow imagine you could find your three friends who fell for this gyp and ask them what they thought — you might just end up with a lower average rating, and you'd certainly have a higher level of certainty that the VRSF is not worth the vibra-foam it's molded from.\n\nThis same query could be performed for any product, service, or cultural experience. And you wouldn't be limited to asking for opinions from your entire social graph, it would be easy to curate a list of epicureans to help you choose a restaurant, or trusted bookworms to help you decide what to read next.\n\nCurrently, big tech is unable to pull this off, because Facebook won't share its social graph with Google, and Google won't share its business data with Facebook. But if an open database of people and businesses exists on Nostr, anyone can re-combine these silos in new and interesting ways.\n\n# Notes and other Spies\n\nSo that's the pitch, but let's consider the downsides.\n\nAn open social graph coupled with recommendations means that not only can you ask what your friends think about a given product, you can ask:\n\n- What a given person's friends think about a product\n- What kind of person likes a given product\n- How products and people cluster\n\nThat last one in particular is interesting, since it means you could find reasonable answers to some interesting questions:\n\n- Does a given region have fertility problems?\n- What are the political leanings of a given group?\n- How effective was a particular advertisement with a given group?\n\nThis is the kind of social experiment that has historically earned Facebook so much heat. Democratizing this data does not prevent its correlation from being a violation of personal privacy, especially since it will be computationally expensive to do sophisticated analysis on it — and the results of that analysis can be kept private. And to be clear, this is a problem well beyond the combination of social information and public reviews. This is just one example of many similar things that could go wrong with an open database of user behavior.\n\nNot to put too fine a point on it, we are at risk of handing the surveillance panopticon over to our would-be overlords on a silver platter. Just as walled gardens have managed us in the past to sway political opinion or pump the bags of Big X, an open, interoperable content graph will make building a repressive administrative state almost too easy.\n\n# Let's not give up just yet\n\nSo what can we do about it? I want a ratings system based on my social graph, but not at the expense of our collective privacy. We need to keep this threat in mind as we build out Nostr to address novel use cases. Zero-knowledge proofs might be relevant here, or we might be able to get by with a simple re-configuration of data custody.\n\nIn the future users might publish to a small number of relays they trust not to relay their data, similar to @fiatjaf's NIP-29 chat proposal. These relays might then support a more sophisticated query interface so that they can answer questions without revealing too much information. One interesting thing about this approach is that it might push relays towards the PWN model BlueSky uses.\n\nNot all data needs to be treated the same way either, which would give us flexibility when implementing these heuristics. Just as a note might be either broadcast or sent to a single person or group, certain reviews or other activity might only be revealed to people who authenticate themselves in some way.\n\nLike so many other questions with Nostr, this requires our concentrated attention. If all we're doing is building a convenient system for Klaus Schwab to make sure we ate our breakfast bugs, what are we even doing?\n\n
-
 @ 32e18276:5c68e245
2023-07-19 02:56:47
@ 32e18276:5c68e245
2023-07-19 02:56:47I’m so lazy I’m thinking of running the damus merch store via stateless and serverless lightning payment links. All data is collected and stored in the lightning invoice descriptions which are fetched from your node. You can do this without having to run any server code except a lightning node!
This is the same tech we used when selling merch as at bitcoin Miami. It was extremely reliable. I love these things, they are so easy. Integrating with the legacy fiat system is such a pita, It may just be a lightning-only store for now because of how simple this is. Here's what a lightning payment link looks like:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=
How it works
The entire product page is stored as data in the url. When a customer click the link, the product info is decoded and rendered as a webpage. The data in the url includes
- The product name
- Description
- Price in sats
- Product image url
- Fields to collect data from the user
- Lightning node address
- Lightning node rune for fetching and waiting for invoice payments
This works thanks to a javascript library I created called "lnsocket". It allows you to connect to your CLN node over websockets. Once the user fills out all of the info, a new lightning invoice is fetched with this information in the description, by connecting directly to your node. This connection is end-to-end encrypted thanks to the lightning protocol itself.
To your lightning node, it looks like another lightning node is connecting to it, but in reality it's just a dumb client asking for things.
At this point, custom lightning packets called "commando" packets are sent to your node which asks your node to run certain commands. CLN authenticates these packets using the rune and then returns a response. This is pretty much the same as calling these commands directly on your lightning node, except now someone is doing it from a browser in a secure way!
Why not just run btcpayserver?
btcpayserver is cool and is more powerful, but I like exploring simpler ways to do things that don't require running lots of software which can be challenging for many non-technical people. You shouldn't have to become a server administrator to start accepting payments. It should be as simple as running a bitcoin and lightning node, pushing all of the application logic to the clients.
This is a similar philosophy to what we have in the nostr space. Let's make it easier for people to use self-sovereign tools. Everyone deserves freedom tech.
Anyways, I'm still working on https://lnlink.org. I just added images and nostr address support! You can make your own payment links here! Try it out:
http://lnlink.org/?d=ASED88EIzNU2uFJoQfClxYISu55lhKHrSTCA58HMNPgtrXECMjQuODQuMTUyLjE4Nzo4MzI0AANgB6Cj2QCeZAFOZ1nS6qGuRe4Vf6qzwJyQ5Qo3b0HRt_w9MTIwJm1ldGhvZD1pbnZvaWNlfG1ldGhvZD13YWl0aW52b2ljZSZwbmFtZWxhYmVsXmxubGluay0mcmF0ZT04BERlYXRoIFN0YXIABQAAAGQGQW4gb2JqZWN0IG9mIHVuZmF0aG9tYWJsZSBwb3dlcgAHEwhodHRwczovL3VwbG9hZC53aWtpbWVkaWEub3JnL3dpa2lwZWRpYS9lbi9mL2Y5L0RlYXRoX3N0YXIxLnBuZwA=&edit=1
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr\n\n以下是使您的 Nostr 之旅更顺畅的几个步骤 \n\n---\n_本指南适用于: \n 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n 俄语 \n\n--- \n你好,Nostrich同胞!\n\nNostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。 \n\n## 👋欢迎 \n\n由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz -- \n
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。 \n\n--- \n\n## 🤙玩得开心 \nNostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 \n这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: \nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu \n_名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们_ \n\n---\n ## ⚡️ 启用 Zaps \nZaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ \n查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: \n即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤: \n\n0 为您的移动设备下载 Wallet of Santoshi[^1](可能是比特币和闪电网络新手的最佳选择)[^2]\n1 点击“接收” \n2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。 \n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
\n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。  \n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
\n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org  它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n \n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n
\n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n  \n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
\n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。  \n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:
\n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/\n\n \n\n[^1]:还有更多支持闪电地址的钱包,您可以自由选择您喜欢的 \n[^2]:不要忘记返回钱包并备份你的账户\n[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标\n\n\n译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边\n\n_Zap⚡ spang@getalby.com \n关注:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n\n\n\n\n\n -
 @ 7ecd3fe6:6b52f30d
2023-08-12 07:18:50
@ 7ecd3fe6:6b52f30d
2023-08-12 07:18:50Social media is a part of our lives, like it or not, it's how we get our news, voice our opinions engage with friends and family, find community and argue with anons, it's just what we modern humans do.
The problem with social media today is that it is run by corporations, these platforms, while acting as public utilities for communication are actually walled gardens where narratives can be pushed or suppressed and your time on site is paid for by ads that are burning your eyeballs so hard they leave an imprint on the back of your brain.
We can all see the incentive structure of corporate social media has us all going a little loopy while others have fully given themselves over to whoring for the algorithm.
We need decentralised social media
It's obvious we need a platform where we're not beholden to who has the biggest budget, or what the algos are looking to rage bait you into so you remain on site to see more ads. This is not a system that is good for one's brain and soul, the "free" social media model comes at a price, and you as the product have begun to decay.
Anyone who voices their real opinions or counters narratives that go against profits and the bottom line of interest parties also gets cleaned out pretty quickly so if you're are still on trad social media it's because you're willing to self-censor or you have nothing real to say.
We are all self-censoring in a way, you know it, I know it, but we all accept it.
Nostr came along
I think many of us didn't know we needed an alternative until #nostr came along and we could start to play around in a world where we had more control and some of us started to like it.
Nostr has grown slowly and steadily, without a token, without a real path to monetisation, it's organic growth built by people who have an interest in seeing this protocol eat away market share from tradsocial.
Right now it's just a bunch of people sharing their ideas, engaging in a small community testing out new features, pushing clients for new updates, and zapping one another along the way.
Despite the seemingly inconspicuous nature of nostr it's already started to rub large institutions the wrong way, first, it was banned in China, then it's mobile clients were removed from the Chinese Apple App store and later it was threatened by the global app store to remove zaps.
If a little protocol that simply allows for chronological curation and organic following of accounts and content along with independent payments powered by Bitcoin is already in the eyes of big institutions at this early stage, then you know you're on to something.
Shitcoiners are not going to let us have our fun
Nostr might have started as a Bitcoin-centric tool, but like Bitcoin its a protocol for enemies, you can say and do what you like on nostr, and if certain clients or relays don't like what you're doing you can find one that do or build your own.
If you're not a fan of zaps and you want to use stablecoins or your preferred shitcoin, you could build that into your own nostr client and relays that support it. But this would mean you are supporting nostr, since you're growing the user base and if your project failed, those users would simply login to the nostr clients and relays that remain.
But that's not the shitcoiner way, they don't want to compete, they want to extract value while its possible, the shitcoiner way is to try and create walled gardens where they can sucker you in and dilute you slowly or quickly.

Nothing new to the space
SocialFi is nothing new, if you've paid attention to this space long enough you would know that a lot of this is the rebranding of failed ideas and projects for a new cohort of users.
For those of you who were not around from 2016 during the ICO phase, you might not know that social media on the blockchain was all the rage. It was tried on separate blockchains like STEEM, these social applications like STEEMIT were wildly popular back then, running up to over 1 billion in market cap and were firmly in the top 10 tokens at the time.
Today it's still around, with a tiny user base, most people have abandoned it, those who profited from it have gone on to build new scams and the token has fallen down the ranks.

STEEM price action since launch
The way this scam worked was you would pre-mine tokens for yourself and your buddies, and then build various dApps would reward users with new inflation. Users would create content on your site, and users with stake would upvote their content.
When you upvote content you receive an amount of tokens, which is usually autostaked and the incentive for you is to create more content to earn tokens or buy tokens to build up a reputation so you can control more of the inflation through upvotes.
As users earned tokens and purchased tokens to stake them, you as the pre-mine owner get to sell into that demand and you have less competition for sales as the incentive is to stake to gain influence on the platform, so you're profiting off peoples egos and the gamification of the system.
Eventually, like all inflationary shitcoin projects you run out of new suckers and the original suckers feel they want to profit too and start dumping inflation just keeps pumping out, and you dilute demand to a point where your token is worth nothing.
I mention STEEM because it was probably the most "successful" relatively speaking, so i see this as the best outcome for these kinds of projects. Of course, there were others like Bitcoin Cash-funded Read Cash and Noise Cash, EOS-funded Trybe and Voice, SoMee, and Publish0x which used a bunch of random shitcoins.
Friends.tech and why we can't have nice things
So socialFI failed in 2018 and we all moved on from the dumb idea, the Bitcoin circles have picked up on nostr and it's got a fair bit of traction, so what do the shitcoiners do? Support Nostr?
Hell no, let's make socialFi 3.0 as part of this painfully stupid web3 narrative, and the first play in this new brand of SocialFI seems to be friends.tech.
An app that emerged out of nowhere and is built on Base Coinbases fork of ETH which is a weird choice, but it hasn't stopped its growth in a week the network reached 136,000 daily active users beating out OpenSea over the same time frame.
How much of that is real or just botting I don't know but that's the numbers being promoted.
So what is this app all about? Uncensorable social media? Owning your data? Migrating your data between apps seamlessly? No
The app essentially allows users to tokenize your social network by selling shares in your profile. So influencers in the space can sell access to themselves since buying someone’s share grants owners the ability to exchange private messages with them.
The new social app has driven 4,400 ETH ($8.1 million) in trading volume in less than 24 hours since its launch, far surpassing OpenSea’s in the same time frame.
Again these user numbers and trading value is not verified, and we don't know how much is just botting or wash trading to create attractive metrics to sucker people in, but sucker people in they will.
To me this just looks like another zero some game of extracting wealth from your followers, as if influencers don't already do this, I don't see how this is in anyway decentralised or an improvement on social media today, in fact I think it just super charges the worst kind of behaviour we see on social media and I don't see this app living longer than a footnote of 2023.
Sources:
- https://www.coindesk.com/web3/2023/08/11/is-friendtech-a-friend-or-foe-a-dive-into-the-new-social-app-driving-millions-in-trading-volume/
- https://captainaltcoin.com/friend-tech-leads-the-way-for-the-next-generation-of-socialfi-on-basechain/
-
 @ 32e18276:5c68e245
2023-07-17 21:55:39
@ 32e18276:5c68e245
2023-07-17 21:55:39Hey guys!
Another day, another TestFlight build. This fixes many mention bugs and includes bandwidth improvements.
During nostrica, jack told everyone to open their phones and say GM to fiatjaf. This actually brought down nostrica's wifi! Damus is really dumb when it first opens and makes many requests. Sometimes hundreds (nip05 validation, etc). This build fixes all those issues. Damus will no longer:
- Make hundreds of nostr address validation requests.
- Make tons of duplicate lnurl requests when validating zaps
nostr address validation only happens when you open someones profile now.
This build also fixes some annoying mention issues. If you forget a space when mentioning someone, it will automatically add it.
I've also removed the restriction where you were not allowed to login to "deleted" accounts. This was way too confusing for people, and logging into a deleted account will allow you to reset the profile information and get it going again. You're welcome NVK.
Another thing that was added in this build is support for
_usernames in nostr addresses. This will hide your full nostr address username when used. Damus will also hide your username if it matches your profile username. Damus always did this before but it was incorrect. Now it will show your full nostr address (nip05) with its proper username. You can stop bugging me about this now Semisol.Last but not least there are some small tweaks to longform note padding. Nothing too crazy but it does make notes like this look less cramped.
Until next time!
Added
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Re-add nip05 badges to profiles (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Added padding under word count on longform account (William Casarin)
Fixed
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Allow user to login to deleted profile (William Casarin)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:48
@ e6817453:b0ac3c39
2023-08-12 15:42:48I deeply believe that practically every business runs a few identity systems. Identity is unavoidable. Sometimes you need to be made aware that you manage an identity system.
Some examples of identity could be quite uncommon.
- Online or offline event tickets
- order receipts
We should rethink identity as a relation, not personalities or users.
Well, today, we will focus on broader categories of identity systems.
Such a quick categorisation of identity systems based on the root of trust
- Administrative
- Algorithmic
- Autonomic
Administrative
The total and almost exclusive majority of modern identity is Administrative identity. Administrator founds trust basis. An administrator could be a person, organization, or system managed by organizations. In an administrative system, an identifier could be issued or owned by the Administrator or could be owned by another system. Still, it is bonded — assigned by the administrator to the controller (user). So controller-identifier or AI binging is weak and controlled by the administrator. In such systems, keys could be a password or MFA authentification factor.
The source of truth is an administrative database that stores an identifier to controller bindings.
Quite often, this system is centralized and owned by Organisations.

The trust basis — Administrative System
SSI systems
SSI systems introduce a completely different approach as an alternative to Administrative systems. First of all, network effects in such systems play a key role. Every member of a system has equal rights. The controller has full ownership of his identity. Such systems have an interconnected mesh of sovereign administrators.
One of the key challenges in such systems is the root of trust. Roots of trust derive a key difference in the next 2 Architectures.
The key concept is not decentralization — it is only an implementation detail. Key of SSI identity systems is sovereignty and user control of identity.
Algorithmic
Relay on Verified Data Registry.
VDR is publicly open for reading and discovery.
VDR has an algorithmic and protocol-driven architecture which means it is controlled algorithmically based on open standards and public algorithms. In rare cases, it could be centralized and managed by the organization but still follow open standards.
The more preferred way is decentralized distributed consensus-based data storage.
It could be public or permission blockchains—some blockchains designed for identity only, like hyper ledger Indy or similar.
In Algorithmic systems, keys usually mean asymmetric cryptography key pairs. The controller generates a key pair and registers a public key in a VDR. Everybody can access a VDR and retrieve public keys based on the identifier. In the best-case scenario, an identifier is cryptographically derived from a key pair or the same cryptographic material.
The majority of blockchain DID methods are a perfect example of VDR. VDR could store much more than public keys or identifier bindings. VDR is a key enabler in AnonCreds Verifiable credentials that enable ZKP credentials to store VC schemas, blind links, VC metadata, and public information about issuers together with a revocation list, etc.
In the case of did: corporate web domain, a website could act as a primitive centralized VDR.
Any DTL and decentralized file systems like IPFS could be used as VDRs.
VDR is a bit more than storage it brings governance and policies that enable trust and regulation in the network

trust basis on algorithmic identity systems
Autonomic
Similar to Algorithmic in a flow but completely self-administrated and self-certified. Cryptographic material owned by the controller still drives the identifier. All bindings between an identifier, controller, and identifier govern by a protocol and recorded in a controller Key event log.
The key difference here — we eliminate a VDR and replace it with co-local architecture owned and run by the controller. As a result, we get a high-scale, resistant, autonomic system that could operate without any third-party services.
In this case, the root of trust is self-certified by the controller. It creates a question should we trust and rely on self-certified data? A few tries to create self-certified systems in the past failed to build trust relations. That's why it is critical to creating open to audit end-to-end verifiable systems and protocols that could create a network of trust. Such systems could involve witness networks and network participants' cross-verification of key event logs.

autonomic system — trust basis
AIDs or autonomous DIDs fail in this bucket well together with the KERI protocol.
You can read more about AID in my article.
And discover DID:Web as a simplified AID for organizations
All key event logs or did document storages for did:peer is some form of co-local storages that still require end-to-end verifiability. You can discover more about micro ledgers
The pioneer and most matured solution now for autonomic identity systems infrastructure is KERI
It is still a lot of work in adoption of SSI identity systems but i see a stable trand in this space.
-
 @ 97c70a44:ad98e322
2023-06-01 13:46:54
@ 97c70a44:ad98e322
2023-06-01 13:46:54I think I cracked the code on private groups.\n\nInstead of relying on relays to implement access control as in this PR, we could combine the Gift Wrap proposal with @PABLOF7z's nsec bunker to create private groups with easy administration and moderation!\n\nGift wrap fixes DM metadata leakage by using a temporary private key to send a DM to a recipient. The recipient decrypts the wrapper to find a regular nostr event inside. This could be another kind 4 as in the proposal, or anything else. Which means you can send kind 1's or anything else in a wrapped event.\n\nNow suppose you had a pubkey that you wanted to represent a group instead of a person. Put its nsec in a (modified) nsec bunker, and now you can allow other people than yourself to request signatures. A shared private key! Anyone who has access to this nsec bunker could also de-crypt any gift wrapped note sent to it. Relay-free read access control!\n\nThere are lots of ways you could manage this access list, but I think a compelling one would be to create a NIP 51 list (public or private!) of group members and set up the nsec bunker to authenticate using that list. Boom, dynamic member lists!\n\nYou could also create a NIP 51 list for admins, and pre-configure which event kinds each list is allowed to post using the group's nsec. So maybe members could only publish wrapped kind-1's, but admins could publish wrapped kind-0's (you can now zap a group!), kind 9's for moderation, updated member and moderator lists, normal kind 1's for public information about the group, etc.\n\nGift wrap would support:\n\n- Leak-free DMs\n- Fully private groups\n- Public-read groups (nsec bunker would allow for admin, but everyone would publish regular instead of wrapped events).\n- Organizations and other shared accounts, with role-based authorization (list/kind mappings)!\n\nOf course, no clients currently support this kind of thing, but support would not be hard to add, and it creates an entirely new set of affordances with two very simple applications of the core protocol.\n\nThere are a few drawbacks I can think of, of course. Gift wrap makes it harder to search notes by tag. You could:\n\n- Leave all tags off (other than for DM recipient as in the proposal)\n- Selectively keep tags that aren't revealing of identity\n- Encrypt tag values. When a client wants to query a tag, it must encrypt the value using the same pubkey and include that in the filter. This, I think, is ok for the group use case above.\n\nThere are also a number of proposals in the works to fix NIP 04 DMs which are apparently broken from a cryptographic standpoint, so implementing this should probably wait until that stuff is sorted out. But it should be possible however that ends up materializing.\n\nSo am I nuts? Or is this a galaxy brain solution?
-
 @ d830ee7b:4e61cd62
2023-08-05 11:02:13
@ d830ee7b:4e61cd62
2023-08-05 11:02:13How long have we lived with the term Bitcoin as a Store of Value (SOV)? The financial sovereignty, that is...
Among those who are aware of the system's problems, they often accept Bitcoin as an asset that will preserve their value over time. The question is, how many of these people are there in society? The society we call the Matrix...
Yes, there are still few.
Not to mention how to store it safely, that's even fewer. We can see that the demand in the past mainly came from 2 groups. The first group is the SOV group, and the other is the profit speculators. Other groups were just a sprinkle. In early 2022, when the price of Bitcoin started to decline, I couldn't imagine what the next wave of demand would come from. All I knew was that in that downturn, Bitcoin often had new developments.
I mean... the desire to own Bitcoin, not the trading demand that would cause the price to skyrocket or anything like that.
Until, if I remember correctly, it would be the second half of 2022... The wonder of the Lightning Network began to occur continuously in the Bitcoin community worldwide, including in Thailand where we also helped push it to this day (actually, it existed before that, especially after the big event in El Salvador, but it wasn't so prominent).
Lightning makes the world of Bitcoin full of possibilities. From static money held for wealth, money saved for children and grandchildren that has always been stigmatized as not even enough to buy noodles at the front of the alley, it has become convenient money that today begins to stick in our hearts everywhere (I mean in the group of people who accept Bitcoin, of course).
Bitcoin used to be "difficult" for everyone. Transferring in and out each time was a headache, our hands were shaking. But today, many of us know that we can take the smallest unit of it to pass on to each other, whether it's for fun, to express feelings, to flirt, or to buy and sell things, etc., as we saw at the BTC2023 event, right?
https://i.imgur.com/W3D1pdk.png
It's just stuck... If we don't count the easy-to-use general usage, system management, or running a Bitcoin Lightning node, it makes us feel like we have to be god-level to do it. Understanding its working mechanism is also not easy.
When it's like this, I think to myself... Hmm... It probably won't take much longer for people to learn, understand, and familiarize themselves with this new technology.
But I believe... This is not impossible. It's not that hard. What we need is a "method or approach" to present or disseminate knowledge that the general public can access and grasp more easily.
Right Shift is being propelled in a direction that will make the "choice" of accepting Bitcoin more tangible, a direction that leads to the "actual use" of Bitcoin in scenarios where it becomes a "Means of Payment," a new alternative for those with free hearts.
We coordinate and collaborate with various partners, including our brothers and sisters within the community. Besides the value that won't easily diminish over time, the real value that we can actually utilize is overwhelmingly pleasing to our hearts. Those who have experienced it themselves probably won't argue much with me on this matter.
But there's something that has always made me feel... this is still not enough.
Offering a choice for people to shift their mindset from "hoarding" Bitcoin more than eggs in a nest is one thing. Issues of privacy or Non-KYC is another. Starting with Custodial services is another. Educating is hard enough, and creating a balanced demand-supply is even harder.
We once made businesses support Lightning to a great extent, but no one ever knew where to get Lightning to buy things, and how to buy it?
Once people started doing it, they looked for places to buy, and it turned out that the supply, the entrepreneurs, couldn't keep up. They stumbled and needed considerable assistance to start. Not to mention legal matters, accounting, taxes... See? Our work is not just about making videos.
If you look at the whole picture, this task is much bigger and longer than we thought (by "we" here, I mean everyone in the community aiming for the same goal).
https://i.imgur.com/t0sJ4ju.png
So, we, the main partners like Right Shift, LATES, BOB, and Chitbeer, and many more, will probably have to spend time driving and spreading these stories further. We hope to receive excellent cooperation from our friends in our community.
We are planning to tour various places, maybe universities, schools, malls, provinces, etc., wherever people want to learn about Bitcoin. We will organize on-site courses similar to what happened in El Salvador, arrange events for people to try using Bitcoin, and we would be delighted to have volunteers who want to push with us... But then, today...
Not long ago... I found a third option.
If starting interest from the investment side, saving, preserving, or accumulating Bitcoin, and using it seems too hard for most people,
What if we try to shift the perspective, starting with what they are already familiar with, easily accessible, and can have fun with first? Will acceptance be easier and more logical to plunge into the next rabbit hole or not?
I didn't let myself drown in doubt for too long, so I touched it myself immediately... And the answer is... It's really true.
We just switch from mainstream social media that is causing us more pain every day to a new society that is like the true root of the online community. This way, it seems easier to move on... Why do I think so?
The society on a decentralized protocol grants us, as users, almost complete freedom. In all honesty, it's no more difficult than setting up a Lightning wallet, something we've all done before.
Every day, tens of thousands of us click 'like' on Facebook countless times, expressing our satisfaction with a creator's work or a friend's post. Sometimes, we're not even sure if we genuinely want to do it.
What if we change from 'like' to Zap!?
How much economic value is circulating there (currently, there are more than 12 BTC Zapped on Nostr)? It's not just us who have to go and Zap others. If you do well, benefit the community, even a laugh can get it. Others are ready to Zap you all the time as well.
You can use it without linking to a Lightning wallet. The question is, how can you experience expressing satisfaction or receiving it instantly as Satoshi's value?
Yes.. with such a situation, it's inevitable that people will have to learn and understand Bitcoin and Lightning, at least at a basic level.
https://i.imgur.com/qJddift.png
But this time, their motivation isn't for wealth or prosperity, not financial domination, or solely technical prowess.
It comes from a desire to participate in a society they want to be a part of. It comes from a desire to appreciate or admire someone's work that has benefited them on Nostr. It comes from the joy of living freely in a new land, and so on.
On the creator's side... Instead of losing money, time, and physical energy thinking about content day and night, finding ways to get people to see their posts, waiting for the money that the platform might withhold for another month, and avoiding annoying algorithms and constant changes,
Now, they just invest their value into their content, post it for their followers to definitely see, and receive 'thank you' in the form of Sats instantly.
They can present their content piece by piece without waiting for it to be finished. They can present any form of content there.. The users are the same. This is the activity of passing on value to each other, called "Value for Value" on Nostr.
When V4V becomes something they enjoy, they will start to delve deeper into Bitcoin as time goes by. They will want to own more of it. How else could it be? They just don't like it and are looking for other options to accept it.
So.. Now, do you think the Network effect on Nostr or in real life will be stronger and faster?
Honestly, we don't have to choose. We don't have to decide which direction we will push acceptance.. whether to save, to educate, to use it occasionally, or to experience a new life on a social media society like Nostr.
We should push it together in every way, because it's all beneficial to our Bitcoin society. It's beneficial to everyone who will try to touch it, and it's beneficial to people in the next generations.
Bitcoinization, which used to be just a dream, is about to happen in not too long. Now, I can start answering my initial question. What should the demand come from? It should start from our interest first.
Interested enough to try to touch it in every aspect. Take the rotten fiat money on your fridge and turn it into Lightning for a bit, then let it slide on Nostr.
In 2023, our choices, the world's choices, are not just SOV or Lightning anymore.. which either way, it's good for Bitcoin.
It's opening wider than we think. . . // Author by: Jakk Goodday
-
 @ a012dc82:6458a70d
2023-08-12 07:00:14
@ a012dc82:6458a70d
2023-08-12 07:00:14Table Of Content
- The Rise of Bitcoin Mining
- Riot Platforms: The New Kid on the Block
- Local Residents Speak Out
- The Environmental Angle
- Economic Implications
- The Road Ahead: Solutions and Compromises
- Conclusion
- FAQ
Deep in the heart of Texas, a new challenge is brewing. The vast state, known for its oil rigs, cowboy culture, and iconic history, is now grappling with a modern dilemma. The world's largest Bitcoin mine has set up shop, and it's causing quite the commotion. As the digital gold rush intensifies, the Lone Star State finds itself at the crossroads of progress and preservation. Residents, policymakers, and industry leaders are all weighing in, making it a hot topic of discussion from Houston to Dallas.
The Rise of Bitcoin Mining
Bitcoin, the pioneering digital currency that's taken the world by storm, relies on a process called mining. This isn't about pickaxes and gold pans, but powerful computers solving complex algorithms. As the value of Bitcoin has soared, so has the race to mine it. Texas, with its cheap energy and vast landscapes, has become a hotspot. However, this boom brings its own set of challenges, from infrastructure strains to environmental concerns.
Riot Platforms: The New Kid on the Block
Enter Riot Platforms, the behemoth at the center of the storm. As the world's most significant Bitcoin mining operation, it's drawing power and attention in equal measure. While it promises prosperity and progress, it also poses questions. How much strain can the Texan grid take? And at what cost to the community? With its massive operations, Riot Platforms is both a beacon of opportunity and a potential point of contention.
Local Residents Speak Out
For the folks calling Texas home, this isn't just a tech debate. It's about their daily lives, their neighborhoods, and their futures. There are fears of power outages, skyrocketing electricity bills, and even potential environmental fallout. The heart of the matter? Balancing the promise of the future with the needs of the present. Town hall meetings, community forums, and local discussions are buzzing with opinions and concerns.
The Environmental Angle
Let's face it, Bitcoin mining isn't exactly green. The energy consumption is staggering, often compared to that of entire countries. With Texas' grid already dancing a delicate balance, the addition of massive mining operations is like adding fuel to the fire. The question on everyone's lips: Is there a sustainable way forward? Environmentalists and activists are pushing for greener solutions, making it a pivotal point in the debate.
Economic Implications
But it's not all storm clouds. The silver lining? Economic growth. Bitcoin mining is bringing jobs, investments, and a tech boom to regions that might have been left behind. For many, this is a golden opportunity, a chance to ride the wave of the future. But is it a future everyone wants? Economists and industry experts are analyzing the long-term implications, weighing the pros and cons of this digital revolution.
The Road Ahead: Solutions and Compromises
All is not lost. As the debate rages, innovators are seeking solutions. Think renewable energy sources, improved grid infrastructure, and even tweaks to the mining process itself. The goal? To find a middle ground where tech and tradition can coexist. Stakeholders are coming together, brainstorming ways to ensure that Texas remains both progressive and preserved.
Conclusion
The Bitcoin mining grid challenge is more than just a Texan issue; it's a global conversation about the future of energy, economy, and the environment. As Texas grapples with this modern gold rush, the world watches, waits, and wonders: What's the next move for the Lone Star State? With its rich history of innovation and resilience, many are optimistic that Texas will find a path forward that benefits all.
FAQ
What is the main issue in Texas regarding Bitcoin mining? Texas is grappling with the challenges posed by the world's largest Bitcoin mine, Riot Platforms, which has raised concerns about energy consumption, grid strain, and environmental impact.
Why is Bitcoin mining a concern for the environment? Bitcoin mining consumes vast amounts of energy, often compared to entire countries, leading to concerns about its carbon footprint and sustainability.
How are local residents reacting to the Bitcoin mining operations? Many Texans are concerned about potential power outages, increased electricity bills, and the broader community impact of such large-scale mining operations.
Are there any economic benefits to Bitcoin mining in Texas? Yes, Bitcoin mining has brought jobs, investments, and technological advancements to the state, offering economic growth opportunities.
That's all for today, see ya tomorrow dear plebs
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
 @ 9ecbb0e7:06ab7c09
2023-08-12 03:59:17
@ 9ecbb0e7:06ab7c09
2023-08-12 03:59:17La comunidad cubana en el extranjero ha sido sorprendida con la noticia del trágico hallazgo sin vida del expreso político Nelson Molinet, quien fue parte del grupo de los 75 opositores detenidos durante la Primavera Negra en 2003.
El disidente había sido reportado como desaparecido en Hialeah desde el pasado lunes 7 de agosto. La última vez que lo vieron con vida tenía una bolsa de plástico azul y se encontraba en las cercanías de la 2140 W 68 St., en Hialeah, cerca de las oficinas del Social Security. En medio de su búsqueda se había informado que padecía problemas de memoria y psiquiátricos.
Normando Hernández González, director del Instituto Cubano por la Libertad de Expresión y Prensa (ICLEP), confirmó en redes sociales la muerte del activista. Según su post, el cuerpo fue encontrado sin vida dentro de un automóvil en Hallandale Beach, una ciudad ubicada en el condado de Broward. Se espera que, en las próximas horas, las autoridades del sur de Florida compartan información precisa sobre esta muerte.
Molinet, quien tenía 59 años, fue una figura destacada en la lucha y un símbolo de resistencia incansable contra el régimen cubano. Durante siete años, estuvo privado de libertad en las cárceles castristas debido a sus desacuerdos con las ideas del régimen. En ese tiempo de encierro, sufrió torturas que le dejaron secuelas en su salud.
El opositor, conocido por su papel como sindicalista independiente, fue condenado en los juicios de la Primavera Negra a una pena de 20 años de prisión. Su liberación se produjo luego de las conversaciones de la Iglesia Católica y el gobierno español de Zapatero con el régimen de La Habana, y en septiembre de 2010 fue puesto en libertad con la condición de marchar al exilio junto con otros disidentes también excarcelados en estas negociaciones.
La comunidad cubana en el extranjero lamenta profundamente la pérdida del opositor, cuya valiente lucha por la libertad y los derechos humanos en la Mayor de las Antillas dejó una huella imborrable.
La Primavera Negra fue un período en el que ocurrió una serie de detenciones masivas y juicios sumarios contra periodistas independientes y disidentes políticos. Los detenidos enfrentaron cargos por supuestamente conspirar contra el gobierno del fallecido dictador Fidel Castro.
-
 @ 32e18276:5c68e245
2023-07-16 22:47:17
@ 32e18276:5c68e245
2023-07-16 22:47:17Hey guys, I just pushed a new Damus update TestFlight. This should drastically improve longform event rendering. Let me know if you find any bugs!
Full Changelog
Added
- New markdown renderer (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
Changed
- Hide nsec when logging in (cr0bar)
- Remove nip05 on events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
Fixed
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
- Fix nostr:nostr:... bugs (William Casarin)
-
 @ 32e18276:5c68e245
2023-06-01 04:17:00
@ 32e18276:5c68e245
2023-06-01 04:17:00Double-entry accounting is a tried and true method for tracking the flow of money using a principle from physics: the conservation of energy. If we account for all the inflows and outflows of money, then we know that we can build an accurate picture of all of the money we've made and spent.\n\nBitcoin is particularly good at accounting in this sense, since transaction inflows and outflows are checked by code, with the latest state of the ledger stored in the UTXO set.\n\nWhat about lightning? Every transaction is not stored on the blockchain, so we need same way to account for all the incoming and outgoing lightning transactions. Luckily for us, core-lightning (CLN) comes with a plugin that describes these transactions in detail!\n\nFor every transaction, CLN stores the amount credited and debited from your node: routed payments, invoices, etc. To access this, you just need to run the
lightning-cli bkpr-listaccounteventscommand:\n\n\nlightning-cli bkpr-listaccountevents | jq -cr '.events[] | [.type,.tag,.credit_msat,.debit_msat,.timestamp,.description] | @tsv' > events.txt\n\n\nThis will save a tab-separated file with some basic information about each credit and debit event on your node.\n\n\nchannel invoice 232000000 0 1662187126 Havana\nchannel invoice 2050000 0 1662242391 coinos voucher\nchannel invoice 0 1002203 1662463949 lightningpicturebot\nchannel invoice 300000 0 1663110636 [["text/plain","jb55's lightning address"],["text/identifier","jb55@sendsats.lol"]]\nchannel invoice 0 102626 1663483583 Mile high lightning club \n\n\nNow here's comes the cool part, we can take this data and build a ledger-cli file. ledger is a very powerful command-line accounting tool built on a plaintext transaction format. Using the tab-separated file we got from CLN, we can build a ledger file with a chart-of-accounts that we can use for detailed reporting. To do this, I wrote a script for convertingbkptreports to ledger:\n\nhttp://git.jb55.com/cln-ledger\n\nThe ledger file looks like so:\n\n\n2023-05-31 f10074c748917a2ecd8c5ffb5c3067114e2677fa6152d5b5fd89c0aec7fd81c5\n expenses:zap:1971 1971000 msat\n assets:cln -1971000 msat\n\n2023-05-31 damus donations\n income:lnurl:damus@sendsats.lol -111000 msat\n assets:cln 111000 msat\n\n2023-05-31 Zap\n income:zap:event:f8dd1e7eafa18add4aa8ff78c63f17bdb2fab3ade44f8980f094bdf3fb72d512 -10000000 msat\n assets:cln 10000000 msat\n\n\nEach transaction has multiple postings which track the flow of money from one account to another. Once we have this file we can quickly build reports:\n\n## Balance report\n\nHere's the command for "account balance report since 2023-05 in CAD"\n\n$ ledger -b 2023-05-01 -S amount -X CAD -f cln.ledger bal\n\n\n CAD5290 assets:cln\n CAD2202 expenses\n CAD525 routed\n CAD1677 unknown\nCAD-7492 income\n CAD-587 unknown\n CAD-526 routed\nCAD-1515 lnurl\n CAD-614 jb55@sendsats.lol\n CAD-1 tipjar\n CAD-537 damus@sendsats.lol\n CAD-364 gpt3@sendsats.lol\nCAD-4012 merch\nCAD-2571 tshirt\nCAD-1441 hat\n CAD-852 zap\n CAD-847 event\n CAD-66 30e763a1206774753da01ba4ce95852a37841e1a1777076ba82e068f6730b75d\n CAD-60 f9cda1d7b6792e5320a52909dcd98d20e7f95003de7a813fa18aa8c43ea66710\n CAD-49 5ae0087aa6245365a6d357befa9a59b587c01cf30bd8580cd4f79dc67fc30aef\n CAD-43 a4d44469dd3db920257e0bca0b6ee063dfbf6622514a55e2d222f321744a2a0e\n ...\n------------\n 0\n\n\nAs we can see it shows a breakdown of all the sats we've earned (in this case converted to fiat). We can have a higher-level summary using the depth argument:\n\n$ ledger -M -S amount -X sat -f cln.ledger bal\n\n\n sat14694904 assets:cln\n sat6116712 expenses\n sat1457926 routed\n sat4658786 unknown\nsat-20811616 income\n sat-1630529 unknown\n sat-1461610 routed\n sat-4207647 lnurl\nsat-11144666 merch\n sat-2367164 zap\n------------\n 0\n\n\nAs we can see we made 14 million sats this month, not bad! The number at the bottom balances to zero which means we've properly accounted for all income and expenses.\n\n## Daily Damus Donation Earnings\n\nTo support damus, some users have turned on a feature that sends zaps to support damus development. This simply sends a payment to the damus@sendsats.lol lightning address. Since we record these we can build a daily report of damus donations:\n\n$ ledger -D -V -f cln.ledger reg damus\n\n\n23-May-15 - 23-May-15 ..damus@sendsats.lol CAD-46 CAD-46\n23-May-16 - 23-May-16 ..damus@sendsats.lol CAD-73 CAD-120\n23-May-17 - 23-May-17 ..damus@sendsats.lol CAD-41 CAD-161\n23-May-18 - 23-May-18 ..damus@sendsats.lol CAD-37 CAD-197\n23-May-19 - 23-May-19 ..damus@sendsats.lol CAD-35 CAD-233\n23-May-20 - 23-May-20 ..damus@sendsats.lol CAD-28 CAD-261\n23-May-21 - 23-May-21 ..damus@sendsats.lol CAD-19 CAD-280\n23-May-22 - 23-May-22 ..damus@sendsats.lol CAD-29 CAD-309\n23-May-23 - 23-May-23 ..damus@sendsats.lol CAD-19 CAD-328\n23-May-24 - 23-May-24 ..damus@sendsats.lol CAD-25 CAD-353\n23-May-25 - 23-May-25 ..damus@sendsats.lol CAD-36 CAD-390\n23-May-26 - 23-May-26 ..damus@sendsats.lol CAD-37 CAD-426\n23-May-27 - 23-May-27 ..damus@sendsats.lol CAD-25 CAD-451\n23-May-28 - 23-May-28 ..damus@sendsats.lol CAD-25 CAD-476\n23-May-29 - 23-May-29 ..damus@sendsats.lol CAD-12 CAD-488\n23-May-30 - 23-May-30 ..damus@sendsats.lol CAD-29 CAD-517\n23-May-31 - 23-May-31 ..damus@sendsats.lol CAD-21 CAD-537\n\n\nNot making bank or anything but this covered the relay server costs this month!\n\nHopefully ya'll found this useful, feel free to fork the script and try it out! -
 @ 76c71aae:3e29cafa
2023-05-30 21:59:50
@ 76c71aae:3e29cafa
2023-05-30 21:59:50Joining a new digital community can be an exhilarating and empowering experience. This has been observed on numerous occasions when people join new platforms such as Nostr, BlueSky, Farcaster, Post.news, Tribel, and many others, as well as older social media platforms such as blogs, Usenet, LiveJournal, Xanga, AOL, Flickr, Facebook, Instagram, and TikTok.\n\nInitially, these spaces create an idealistic environment where individuals are eager to connect, share, and participate in a virtual gathering that resembles a festival. However, it is worth examining what it is about these new social spaces that generates such a euphoric atmosphere, and whether it is feasible to sustain this utopian sentiment as communities expand and develop.\n\nThe Magic of Connection:\n\n\nJoining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.\n\nUtopias Form Where They Shouldn’t Exist:\n\n\nThe concept of "Paradise Built in Hell" becomes evident during natural and economic disasters. I personally witnessed this idea during Argentina's economic crisis in the early 2000s. Despite the difficulties, people came together and collaborated in new ways to support each other, as the collapsing economy demanded it. This same phenomenon is observed following earthquakes and other natural disasters, where people often speak of those days with a magical, almost reverential tone.\n\nRebecca Solnit argues that "Disaster is when the shackles of conventional belief and role fall away and the possibilities open up; people rise to the occasion or sink to the level of their fears and prejudices." In these challenging moments, we see the true nature of humanity: our ability to show compassion, resilience, and unity in the face of adversity.\n\nSocial Media and All Digital Spaces Have Physical Analogues:\n\n\nThe similarities between digital and physical communities are rooted in the fact that each has its own distinct set of unspoken rules and social norms. Just as we know to be quiet in a library, loud at a concert, social at a cocktail party, and anti-social on the subway, we also understand the unique dynamics of different digital platforms. Twitter resembles a bustling dive bar, Instagram an art gallery, TikTok an amusement park hall of mirrors, and Facebook a community hall rented for a retirement party. Every new digital space has its analogues in the physical world because human interaction remains consistent, even if the medium differs. As we navigate the ever-changing landscape of digital communities, we are reminded of our innate ability to adapt, connect, and thrive in the face of adversity. This adaptability empowers us to form new connections and rediscover the power of community, whether in the digital or physical realm.\n\nThe Small Community Paradox:\n\n\nTo maintain the utopian atmosphere of new digital communities, one effective approach is to keep them small or create numerous smaller sub-communities. In these sub-communities, people can engage in the social labor of connection and conflict resolution.\n\nIt is important to note, however, that this approach may conflict with the network effect principle. This principle states that each new member joining the community increases its overall value for all participants. As communities grow and the network effect takes hold, the utopian feeling may often fade, giving way to sub-tribes and conflict.\n\nNevertheless, with a confident approach, the community can adapt and navigate these challenges to foster a positive environment for all members.\n\nThe Fleeting Nature of Utopia:\n\n\nThe fleeting utopian sensation experienced within new digital communities is inevitable. Although it is not the design or coding of platforms such as BlueSky, Nostr, Mastodon, or Scuttlebutt that generates this feeling of euphoria, it is instead the human dynamics of joining something novel and building a community that cultivates this enchanting ambiance. Hakim Bey's concept of Temporary Autonomous Zones (TAZs) endorses this notion, demonstrating how short-lived spaces of freedom and interaction can emerge within established social structures. As communities expand and progress, the real challenge lies in sustaining the initial energy and sense of connection that made them so desirable in the first place.\n\nParallel to Protests and Uprisings:\n\n\nThis utopian sentiment is not limited to digital communities; it is also present during times of revolution, protests, and uprisings. There is a profoundly human element to the sense of love, connection, solidarity, and community that arises during these moments.\n\nThe most impactful moments of my life have been when I participated in protests that were met with repression. These protests ranged from tree-sits to protect old-growth redwoods in the forests where I grew up, to large convergences of the anti-globalization and anti-war movements, to Occupy's reclamation of public spaces, and to recent Black Lives Matter protests. All of these protests were scenes of anguish, repression, and, in some cases, violence, especially from the police. However, they were also places where I experienced the most love, connection, humanity, and common purpose. We were all individuals, together, living and breathing solidarity.\n\nCultivating and Sustaining Utopian Energy:\n\n\nTo preserve the utopian essence of new digital communities as they grow, one approach is to foster a culture of empathy, connection, and inclusiveness from the very beginning. Prioritizing these values and actively engaging in conflict resolution can help communities maintain that special feeling.\n\nAnother way to preserve the utopian essence of digital communities is to focus on building tools for the construction and maintenance of these digital public spaces. Unlike corporate social media platforms that only provide an illusion of public space while actually being privately owned, like a shopping mall, we need to create spaces that are community-controlled and collectively owned as a commons with confidence.\n\nUnderstanding the Commons:\n\n\nThe concept of the commons offers a compelling alternative to traditional models of state or private ownership. Elinor Ostrom, the first woman to win the Nobel Prize in Economics, conducted extensive research on this topic, and her findings are truly remarkable. Through her work, she proved that commons can be effectively managed and maintained, debunking the misguided belief that these resources are doomed to fail and end in tragedy.\n\nDesigning for Digital Commons:\n\n\nTo design digital commons, we must prioritize transparency, decentralization, and participatory governance. By empowering users to make decisions about the direction and rules of their digital communities, we ensure that the spaces remain truly public and that the needs and desires of the community are at the forefront.\n\nOpen-source technology and decentralized protocols can play a vital role in the development of these digital commons. By allowing users to maintain control over their data and ensuring that no single entity has a monopoly over the platform, we create an environment that fosters collaboration, creativity, and innovation.\n\nThe Characteristics of a Well-Functioning Digital Commons:\n\n\n1. Clearly defined boundaries: Members and their rights are easily identifiable, and access to the shared digital resources is well-regulated.\n2. Proportional equivalence between benefits and costs: Users contribute to the commons according to their capabilities, and benefits are distributed fairly among members.\n3. Collective decision-making: Users have a say in shaping the rules and policies that govern their digital communities, promoting a sense of ownership and accountability.\n4. Monitoring: Transparent systems are in place to track the usage and management of shared resources, ensuring that members adhere to established rules.\n5. Graduated sanctions: Penalties for rule violations are proportional and escalate based on the severity and frequency of the transgressions.\n6. Conflict resolution mechanisms: Efficient and fair processes are in place to address disputes among members, promoting harmony and trust within the community.\n7. Minimal recognition of rights to organize: Users have the autonomy to self-organize and make decisions about their digital commons without excessive interference from external authorities.\n8. Nested enterprises: Digital commons are organized into multiple, interconnected layers of governance, with smaller communities operating within the context of larger ones, fostering collaboration and coordination.\n\nBy incorporating these principles into the design of digital commons, we can create spaces that are robust, sustainable, and equitable. This, in turn, fosters innovation, collaboration, and genuine community engagement.\n\nDeveloping Community-Driven Tools:\n\n\nTo create and maintain digital public spaces, we need tools that empower communities to effectively manage their digital commons. These tools should facilitate communication, conflict resolution, and decision-making while promoting inclusiveness, empathy, and shared values. By empowering communities to shape their digital spaces and collaboratively resolve issues, we can help preserve the utopian essence that initially attracted people to these platforms.\n\nAdapting to Growth and Change:\n\n\nAs digital communities continue to grow, it's crucial to acknowledge that their needs and challenges will inevitably change over time. To maintain a utopian atmosphere, we must be willing to adapt and consistently improve the tools and processes that sustain these digital public spaces. By promoting continuous feedback and collaboration among community members, we can ensure that the platform remains responsive to the needs of its users, fostering an environment of connection and belonging with conviction.\n\nConclusion:\n\n\nJoining a new digital community can be a thrilling experience, but maintaining that sense of euphoria as the community grows can be difficult. To achieve this, we must design and construct digital commons that prioritize community control, collective ownership, and participatory governance. With the appropriate tools and a dedication to adapting to the evolving needs of the community, we can create spaces that continue to foster the magic of connection even as they transform. In doing so, we can nurture and sustain the utopian energy that makes these digital spaces so unique.\n\n\nPost Script:\n\nSince the completion of this essay, Bluesky has evolved from its initial utopian stage to a phase grappling with context, norms, and scalability. With an increasing user base, the once agreed-upon behavioral norms began to crumble. The initial playfulness, while staying within the community's value constraints, took a disturbing turn when individuals started posting racist and homophobic content. The situation deteriorated rapidly, escalating to the point of issuing death threats. Inspired by the "Nazi bar" parable, the community demanded urgent action to outline acceptable behavior and remove those who couldn't comply.\n\nBluesky, currently hosted on a single server, possesses the capability to enforce a unified set of community guidelines and terms of service. The creators of Bluesky, much like any other social media platform's developers, aimed for a laissez-faire approach. However, they eventually had to revise the terms of service and ban the trolls. This action was chaotic and resulted in significant loss of trust and goodwill.\n\nAdditionally, this did not aid the community in establishing governance for the burgeoning social media commons. Protocols such as Bluesky, Nostr, DSNP, Scuttlebutt, Farcaster, and Lens are not designed to operate in isolation. Among these, only ActivityPub and Mastodon have successfully implemented a model to manage abuse and community moderation at scale. Nonetheless, potential solutions are under development. I've personally contributed to proposals for specifications, codes, and norms on Nostr and know that Bluesky's team is making similar strides.\n\nIt is essential that the user community actively participate in this process. The Design Justice movement provides a valuable blueprint and strategies for achieving this. By applying principles of co-design and design justice, we can collaboratively build solutions. The stakes are too high to leave this endeavor to a small group of technologists alone. \n
-
 @ 32e18276:5c68e245
2023-07-11 21:23:37
@ 32e18276:5c68e245
2023-07-11 21:23:37You can use github PRs to submit code but it is not encouraged. Damus is a decentralized social media protocol and we prefer to use decentralized techniques during the code submission process.
[Email patches][git-send-email] to patches@damus.io are preferred, but we accept PRs on GitHub as well. Patches sent via email may include a bolt11 lightning invoice, choosing the price you think the patch is worth, and we will pay it once the patch is accepted and if I think the price isn't unreasonable. You can also send an any-amount invoice and I will pay what I think it's worth if you prefer not to choose. You can include the bolt11 in the commit body or email so that it can be paid once it is applied.
Recommended settings when submitting code via email:
$ git config sendemail.to "patches@damus.io" $ git config format.subjectPrefix "PATCH damus" $ git config format.signOff yesYou can subscribe to the [patches mailing list][patches-ml] to help review code.
Submitting patches
Most of this comes from the linux kernel guidelines for submitting patches, we follow many of the same guidelines. These are very important! If you want your code to be accepted, please read this carefully
Describe your problem. Whether your patch is a one-line bug fix or 5000 lines of a new feature, there must be an underlying problem that motivated you to do this work. Convince the reviewer that there is a problem worth fixing and that it makes sense for them to read past the first paragraph.
Once the problem is established, describe what you are actually doing about it in technical detail. It's important to describe the change in plain English for the reviewer to verify that the code is behaving as you intend it to.
The maintainer will thank you if you write your patch description in a form which can be easily pulled into Damus's source code tree.
Solve only one problem per patch. If your description starts to get long, that's a sign that you probably need to split up your patch. See the dedicated
Separate your changessection because this is very important.When you submit or resubmit a patch or patch series, include the complete patch description and justification for it (-v2,v3,vn... option on git-send-email). Don't just say that this is version N of the patch (series). Don't expect the reviewer to refer back to earlier patch versions or referenced URLs to find the patch description and put that into the patch. I.e., the patch (series) and its description should be self-contained. This benefits both the maintainers and reviewers. Some reviewers probably didn't even receive earlier versions of the patch.
Describe your changes in imperative mood, e.g. "make xyzzy do frotz" instead of "[This patch] makes xyzzy do frotz" or "[I] changed xyzzy to do frotz", as if you are giving orders to the codebase to change its behaviour.
If your patch fixes a bug, use the 'Closes:' tag with a URL referencing the report in the mailing list archives or a public bug tracker. For example:
Closes: https://github.com/damus-io/damus/issues/1234Some bug trackers have the ability to close issues automatically when a commit with such a tag is applied. Some bots monitoring mailing lists can also track such tags and take certain actions. Private bug trackers and invalid URLs are forbidden.
If your patch fixes a bug in a specific commit, e.g. you found an issue using
git bisect, please use the 'Fixes:' tag with the first 12 characters of the SHA-1 ID, and the one line summary. Do not split the tag across multiple lines, tags are exempt from the "wrap at 75 columns" rule in order to simplify parsing scripts. For example::Fixes: 54a4f0239f2e ("Fix crash in navigation")The following
git configsettings can be used to add a pretty format for outputting the above style in thegit logorgit showcommands::[core] abbrev = 12 [pretty] fixes = Fixes: %h (\"%s\")An example call::
$ git log -1 --pretty=fixes 54a4f0239f2e Fixes: 54a4f0239f2e ("Fix crash in navigation")Separate your changes
Separate each logical change into a separate patch.
For example, if your changes include both bug fixes and performance enhancements for a particular feature, separate those changes into two or more patches. If your changes include an API update, and a new feature which uses that new API, separate those into two patches.
On the other hand, if you make a single change to numerous files, group those changes into a single patch. Thus a single logical change is contained within a single patch.
The point to remember is that each patch should make an easily understood change that can be verified by reviewers. Each patch should be justifiable on its own merits.
If one patch depends on another patch in order for a change to be complete, that is OK. Simply note "this patch depends on patch X" in your patch description.
When dividing your change into a series of patches, take special care to ensure that the Damus builds and runs properly after each patch in the series. Developers using
git bisectto track down a problem can end up splitting your patch series at any point; they will not thank you if you introduce bugs in the middle.If you cannot condense your patch set into a smaller set of patches, then only post say 15 or so at a time and wait for review and integration.
-
 @ a4a6b584:1e05b95b
2023-07-21 01:51:34
@ a4a6b584:1e05b95b
2023-07-21 01:51:34Is light really a constant? In this blog post by Adam Malin we theorize about redshift caused not by expanding space, but by changes in zero point energy field over cosmic time
I was inspired to write this post after reading a paper written in 2010 by Barry Setterfield called Zero Point Energy and the Redshift. If you want a very deep dive into this concept, I recommend you check it out. Here is the link.
I recently read an intriguing paper that puts forth an alternative explanation for the redshift we observe from distant galaxies. This paper, published in 2010 by Barry Setterfield, proposes that redshift may be caused by changes over time in the zero point energy (ZPE) field permeating space, rather than cosmic expansion. In this post, I'll summarize the key points of this theory and how it challenges the conventional framework.
An important distinction arises between Stochastic Electrodynamics (SED) and the more mainstream Quantum Electrodynamics (QED) framework. SED models the zero point field as a real, random electromagnetic field that interacts with matter, possessing observable physical effects. In contrast, QED considers virtual particles and zero point energy as mathematical constructs that do not directly impact physical systems. The zero point energy discussed in this proposed mechanism builds upon the SED perspective of modeling the quantum vacuum as a dynamic background field that can exchange energy with matter. SED provides a means to quantitatively analyze the redshift effects hypothetically caused by changes in the zero point field over cosmic time.
The standard model of cosmology attributes redshift to the Doppler effect - light from distant galaxies is stretched to longer wavelengths due to those galaxies receding away from us as space expands. Setterfield's paper argues that the data actually better supports a model where the speed of light was higher in the early universe and has decayed over time. This would cause older light from farther galaxies to be progressively more redshifted as it travels through space and time.
Setterfield cites historical measurements of the speed of light by scientists like R.T. Birge that showed systematic decreases over time, contrary to our modern assumption of constancy. He argues that while experimental improvements have reduced uncertainties, residual trends remain even in recent high-precision measurements.
A key part of Setterfield's proposed mechanism is that the ZPE interacts with subatomic particles to give them mass and stabilize atomic orbits. As the ZPE has increased in strength over cosmic history, it has caused a contraction in electron orbits within atoms. This results in electron transitions emitting bluer light over time. Thus, looking out into space is looking back to earlier epochs with weaker ZPE and redder light.
This theory raises some thought-provoking questions. For instance, have we misinterpreted redshift as definitive evidence for an expanding universe? Might a static universe with slowing clocks account for observations we attribute to dark matter and dark energy? However, changing existing scientific paradigms is extremely challenging. Let's examine some potential counterarguments:
- The constancy of the speed of light is a fundamental pillar of modern physics backed by extensive experimental verification. This theory would require overturning tremendous empirical support. Setterfield argues that Lorentz and others kept an open mind to variations in c early on. While unexpected, new evidence could prompt another evolution in perspective.
- The current Lambda-CDM cosmological model based on general relativity matches a wide array of observations and predicts phenomena like the cosmic microwave background. But it also has issues like the need for speculative dark matter and dark energy. An alternate cosmology with varying c may provide a simpler unifying explanation.
- Astrophysical observations like supernova brightness curves seem to confirm expanding space. But these interpretations assume constancy of c and other principles that this hypothesis challenges. The cosmic microwave background, for instance, could potentially be re-interpreted as a cosmological redshift of earlier light.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ a4a6b584:1e05b95b
2023-07-21 01:44:57
@ a4a6b584:1e05b95b
2023-07-21 01:44:57The French sociologist and philosopher Jean Baudrillard offered profound critiques of modern society, technology, media and consumer culture through his work. Often associated with postmodernism and post-structuralism, Baudrillard challenged established notions of truth, reality and the power dynamics between humans and the systems they create.
In this blog post, we'll explore some of Baudrillard's most notable concepts and theories to understand his influential perspectives on the contemporary world.
Simulacra and Simulation
One of Baudrillard's most well-known works is "Simulacra and Simulation." In the book, Baudrillard argues that our society has replaced reality and meaning with symbols, images and signs that he calls “simulacra.”
He believed human experience is now a simulation of reality rather than reality itself. Unlike simple imitations or distortions of reality, simulacra have no connection to any tangible reality. They are mere representations that come to define our perception of existence.
To illustrate this concept, Baudrillard outlined three “orders” of simulacra:
-
First Order: Copies or imitations that maintain a clear link to the original, like photographs.
-
Second Order: Distortions of reality that mask the absence of an original, like heavily edited advertising images.
-
Third Order: Simulations with no original referent that become “hyperreal,” like video game worlds.
Per Baudrillard, much of postmodern culture is made up of third-order simulacra. Media representations and simulations hold more meaning than reality, creating a “hyperreality” driven by consumerism and spectacle.
Hyperreality
Building on his theory of simulacra, Baudrillard introduced the concept of “hyperreality” to describe how representations and simulations have come to replace and blur boundaries with reality.
In hyperreality, the lines between real life and fictional worlds become seamless. Media, technology and advertising dominate our perception of reality, constructing a simulated world that appears more real and appealing than actual reality.
For example, the carefully curated lives presented on social media often appear more significant than people’s daily lived experiences. Additionally, idealized representations of reality presented in movies, TV and advertising shape our expectations in ways that real life cannot match.
According to Baudrillard, we increasingly interact with these fabricated representations and hyperreal signs over direct experiences of reality. The simulations and models come to define, mediate and construct our understanding of the world.
Consumer Society
In “The Consumer Society,” Baudrillard argues that traditional institutions like family, work and religion are losing significance to the prevailing values and rituals of consumerism.
Rather than simply meeting needs, consumption has become a defining way of life, shaping identities and social belonging. Non-essential consumer goods and experiences drive the quest for happiness, novelty and status.
Baudrillard notes that consumer society fosters a constant pressure to consume more through an endless pursuit of new products, trends and experiences. This “treadmill of consumption” fuels perpetual dissatisfaction and desire.
Additionally, he highlights how objects take on symbolic value and meaning within consumer culture. A luxury car, for example, denotes wealth and status beyond its functional utility.
Overall, Baudrillard presents a critical perspective on consumerism, showing how it has come to dominate modern society on psychological and cultural levels beyond simple economic exchange.
Symbolic Exchange
In contrast to the materialistic values of consumer society, Baudrillard proposes the concept of “symbolic exchange” based on the exchange of meanings rather than commodities.
He suggests symbolic exchange has more power than material transactions in structuring society. However, modern culture has lost touch with the traditional symbolic exchanges around fundamental existential themes like mortality.
By marginalizing death and pursuing endless progress, Baudrillard argues that society loses balance and restraint. This denial leads to excessive consumption and constant pursuit of unattainable fulfillment.
Fatal Strategies
Baudrillard’s theory of “fatal strategies” contends that various systems like technology and consumerism can take on lives of their own and turn against their creators.
Through proliferation and exaggeration, these systems exceed human control and impose their own logic and consequences. For instance, while meant to be tools serving human needs, technologies can shape behavior and exert control in unanticipated ways.
Baudrillard saw this reversal, where the object dominates the subject who created it, as an impending “fatal” danger of various systems reaching a state of autonomous excess.
This provides a cautionary perspective on modern society’s faith in perpetual progress through technology and constant economic growth.
Conclusion
Through groundbreaking theories like simulation, hyperreality and symbolic exchange, Jean Baudrillard provided deep critiques of modern society, consumer culture, media and technology. His work dismantles assumptions about reality, history and human agency vs. systemic control.
Baudrillard prompts critical reflection about the cultural, psychological and philosophical implications of postmodern society. His lasting influence encourages re-examining our relationships with consumerism, technology and media to navigate the complex intricacies of the contemporary world.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ 9ecbb0e7:06ab7c09
2023-08-12 03:55:47
@ 9ecbb0e7:06ab7c09
2023-08-12 03:55:47En medio de la crítica situación de escasez de agua potable que aqueja a diversas localidades cubanas, un ciudadano en Matanzas ha captado la atención de las redes sociales al protagonizar un acto desesperado.
A través de un video compartido en Facebook por el usuario Ernesto Sánchez, el cubano reveló su desesperada iniciativa de dirigirse a la playa de su localidad a recolectar el vital líquido, imprescindible para su supervivencia diaria.
El protagonista del video, cuya identidad se mantiene en el anonimato, expresó su frustración por la grave carencia de agua en su área. “Mira, cogiendo agüita aquí a la orilla de la playa para poder tomar porque en Matanzas no hay agua, con una pila de manantiales que hay aquí”, exclamó visiblemente consternado por la situación.
Su gesto revela una dura realidad que enfrentan muchos cubanos, cuyas vidas cotidianas se ven afectadas por la falta de suministros básicos, debido a que las autoridades no atienden de manera integral las necesidades ciudadanas.
Con determinación, el ciudadano llenó recipientes con agua de mar para transportarla posteriormente a su hogar. “Míralo, es en la playa, no es mentira. Mira echándole agua al tanque porque no tengo en mi casa ni para lavarme el fondill*”, señaló, demostrando la autenticidad de su esfuerzo.
El hombre no solo destacó la paradoja de la situación en una región con abundantes fuentes de agua, sino que también expuso su descontento con la falta de atención a las carencias del pueblo.
La publicación del video ha provocado una avalancha de reacciones en el ciberespacio. Decenas de internautas han expresado su simpatía hacia la difícil situación del cubano. “Todo es una falta de respeto, una detrás de la otra”, comentaron algunos usuarios en línea.
Sin embargo, otros han expresado sus preocupaciones respecto a la salud y seguridad del ciudadano debido a su consumo de agua de mar y su uso para fines de higiene. También han subrayado la urgencia de resolver la crisis y la necesidad de una reforma estructural para mejorar la calidad de vida en el país.
“Pero bañarse con agua de mar es algo loco y después con qué agua dulce te la vas a quitar. Nos quieren volver locos”; “La libertad del pueblo de Cuba está en las calles. Abajo la dictadura. Libertad para el pueblo de Cuba”, sostuvieron otros.
-
 @ b9e76546:612023dc
2023-06-07 22:12:51
@ b9e76546:612023dc
2023-06-07 22:12:51
#Nostr isn't just a social network, that's simply the first use case to sprout from the Nostr tree.
Simple Blocks, Complex Change
Nostr isn't just a social network, in a similar way that Bitcoin isn't just a transaction network. Both of these things are true, but they each miss the more significant elements of what they accomplish.
In my mind, the source of Nostr's true potential is two fold; first, in fundamentally changing the centralized server model into an open environment of redundant relays; and second, it eliminates the association of clients with their IP address and metadata, and replaces it with identification via public keys. Within this one-two punch lies the most important tools necessary to actually rearchitect all of the major services on the internet, not just social media. Social is simply the interface by which we will connect all of them.
The combination of this simple data & ID management protocol with decentralized money in #Bitcoin and #Lightning as a global payments network, enables nostr to build marketplaces, "websites," podcast feeds, publishing of articles/video/media of all kinds, auction networks, tipping and crowdfunding applications, note taking, data backups, global bookmarks, decentralized exchanges and betting networks, browser or app profiles that follow you wherever you go, and tons more - except these can be built without all of the negative consequences of being hosted and controlled by central servers.
It separates both the data and client identity from the server hosting it. Handing the ownership back to the owner of the keys. We could think of it loosely as permission-less server federations (though this isn't entirely accurate, its useful imo). Anyone can host, anyone can join, and the data is agnostic to the computer it sits on at any given time. The walls are falling away.
Efficiency vs Robustness
There is also a major secondary problem solved by these building blocks. A byproduct of solving censorship is creating robustness, both in data integrity, but also in data continuity. While the fiat world is so foolishly focused on "efficiency" as the optimal goal of all interaction, it naively ignores the incredible fragility that comes with it. It is far more "efficient" for one big factory to produce all of the computer chips in the world. Why build redundant manufacturing to produce the same thing when one factory can do it just fine? Yet anyone who thinks for more than a few seconds about this can see just how vulnerable it would leave us, as well as how much corruption such "efficiency" would wind up enabling.
Nostr is not alone either. Holepunch is a purely P2P model (rather than based on relays) that accomplishes the same separation in a different way. One where the clients and servers become one in the same - everyone is the host. Essentially a bittorrent like protocol that removes the limitation of the data being static. The combination of their trade offs & what these protocols can do together is practically limitless. While Nostr begins building its social network, combining it with what Synonym is building with their Web of trust, (the critical ingredient of which is public key identification) we can "weigh" information by the trust of our social graph.
Not too long ago, a friend and I used Nostr to verify who we were communicating with, we shared a Keet (built on Holepunch) room key over encrypted nostr DM, and opened a P2P, encrypted chat room where we could troubleshoot a bitcoin wallet problem and safely and privately share very sensitive data. The casual ease by which we made this transaction enabled by these tools had us both pause in awe of just how powerful they could be for the privacy and security of all communication. And this is just the very beginning. The glue of #Lightning and #Bitcoin making possible the direct monetization of the infrastructure in all of the above has me more bullish on the re-architecting of the internet than ever in my life. It cannot be reasonably called an insignificant change in incentives to remove both the advertiser and the centralized payment processor from inbetween the provider and the customers online. The base plumbing of the internet itself may very well be on the verge of the greatest shift it has ever gone through.
A Tale of Two Network Effects
I would argue the most significant historical shift in the internet architecture was the rise of social media. It was when we discovered the internet was about connecting people rather than computers. The social environment quickly became the dominant window by which the average person looked into the web. It's the place where we go to be connected to others, and get a perspective of the world and a filter for its avalanche of information as seen through our trust networks and social circles. But consider how incredibly neutered the experience really is when money isn't allowed to flow freely in this environment, and how much it actually would flow, if not for both centralized payment processors and the horrible KYC and regulatory hurdle it entails for large, centralized entities.
The first time around we failed to accomplish a global, open protocol for user identity, and because of this our social connections were owned by the server on which we made them. They owned our digital social graph, without them, it is erased. This is an incredible power. The pressures of the network effect to find people, rather than websites, took a decentralized, open internet protocol, and re-centralized it into silos controlled by barely a few major corporations. The inevitable abuse of this immense social power for political gain is so blatantly obvious in retrospect that it's almost comical.
But there is a kind of beautiful irony here - the flip side of the network effect's negative feedback that centralized us into social media silos, is the exact same effect that could present an even greater force in pushing us back toward decentralization. When our notes & highlights have the same social graph as our social media, our "instagram" has the same network as our "twitter," our podcasts reach the same audience, our video publishing has the same reach, our marketplace is built in, our reputation carries with us to every application, our app profiles are encrypted and can't be spied on, our data hosting can be paid directly with zaps, our event tickets can be permanently available, our history, our personal Ai, practically anything. And every bit of it is either encrypted or public by our sole discretion, and is paid for in a global, open market of hosts competing to provide these services for the fewest sats possible. (Case in point, I'm paying sats for premium relays, and I'm paying a simple monthly fee to nostr.build for hosting media)
All of this without having to keep up with 1,000 different fucking accounts and passwords for every single, arbitrarily different utility under the sun. Without having to setup another account to try another service offering a slightly different thing or even just one feature you want to explore. Where the "confirm with your email" bullshit is finally relegated to the hack job, security duck tape that it really is. The frustrating and post-hoc security design that is so common on the internet could finally become a thing of the past and instead just one or a few secure cryptographic keys give us access & control over our digital lives.
The same network effect that centralized the internet around social media, will be the force that could decentralize it again. When ALL of these social use cases and connections compound on each other's network effect, rather than compete with each other, what centralized silo in the world can win against that?
This is not to dismiss the number of times others have tried to build similar systems, or that it's even close to the first time it was attempted to put cryptographic keys at the heart of internet communications. Which brings me to the most important piece of this little puzzle... it actually works!
I obviously don't know exactly how this will play out, and I don't know what becomes dominant in any particular area, how relays will evolve, or what applications will lean toward the relay model, while others may lean P2P, and still others may remain client/server. But I do think the next decade will experience a shift in the internet significant enough that the words "relay" and "peer" may very well, with a little hope and lot of work, replace the word "server" in the lexicon of the internet.
The tools are here, the network is proving itself, the applications are coming, the builders are building, and nostr, holepunch, bitcoin and their like are each, slowly but surely, taking over a new part of my digital life every week. Case in point; I'm publishing this short article on blogstack.io, it will travel across all of nostr, I'm accepting zaps with my LNURL, it is available on numerous sites that aggregate Kind:30023 articles, my entire social graph will get it in their feed, & there will be a plethora of different clients/apps/websites/etc through which the users will see this note, each with their own features and designs...
Seriously, why the fuck would I bother starting a Substack and beg people for their emails?
This is only the beginning, and I'm fully here for it. I came for the notes and the plebs, but it's the "Other Stuff" that will change the world.
-
 @ d2fb756f:453e247e
2023-08-12 15:42:10
@ d2fb756f:453e247e
2023-08-12 15:42:10Yakihonne, the platform known for enabling content creation, has introduced a series of updates designed to enhance user experience and productivity. These updates offer practical solutions for common challenges faced by content creators, ranging from improved collaboration tools to insightful analytics. In this article, we will delve into the details of these updates and their potential impact on the content creation process.
Drafts: A Space for Idea Development
One of the significant additions to Yakihonne is the introduction of drafts. Drafts provide a space for content creators to refine their ideas and collaborate with others before publishing. This feature aims to streamline the content creation process, allowing creators to gather their thoughts, make necessary adjustments, and seek input from team members. By facilitating collaborative editing and planning, drafts contribute to a more organized and efficient workflow.
Enhanced Comment Management
Yakihonne has addressed a common concern in online communication—accidental comment deletion. The platform now incorporates a confirmation prompt before comments are deleted. This practical addition encourages users to pause and consider their actions, reducing the likelihood of unintended deletions. By promoting thoughtful engagement and minimizing potential errors, this feature fosters a more constructive and mindful commenting environment.
Insightful Stats Previews
The introduction of "Stats Previews" offers content creators valuable insights into the reception of their articles and the engagement of their audience. This feature provides data on reader reactions, enabling creators to gauge the impact of their content and identify areas of interest. By understanding which aspects of their work resonate with readers, creators can make informed decisions to enhance their content strategy and tailor their future creations to their audience's preferences.
Conclusion
Yakihonne's recent updates signify a commitment to practicality and efficiency in the realm of content creation. The inclusion of drafts, the implementation of a confirmation prompt for comment deletion, and the introduction of Stats Previews collectively contribute to an environment that empowers content creators with tools for improved collaboration, communication, and data-driven decision-making.
As content creators continue to navigate the evolving landscape of online engagement, these updates serve as valuable resources that can enhance the quality of their work and foster a more engaging and productive creative process. By addressing real-world challenges and providing practical solutions, Yakihonne's updates have the potential to elevate the content creation experience for users.
-
 @ a4a6b584:1e05b95b
2023-07-21 01:22:42
@ a4a6b584:1e05b95b
2023-07-21 01:22:42A comprehensive exploration of Metamodernism, its principles and influences across art, design, music, politics, and technology. This piece delves into how Metamodernism paves the way for a future that harmonizes grand narratives and individual nuances, and how it could shape the cultural, economic, and digital landscape of the future.
Introduction
Welcome to the metamodern era. A time where we find ourselves caught in the flux of digital revolution, cultural shifts, and a rekindling of grand narratives, all while still
As an artist, I find myself standing at the crossroads of these cultural and technological shifts, with Metamodernism serving as my compass. I'd like to share my thoughts, experiences, and observations on what Metamodernism is, and how I believe it will shape our future.
This journey began as an exploration into the potential future of graphic design, taking cues from an evolving cultural paradigm. I quickly realized that Metamodernism was not just about creating compelling visual narratives, but it had potential to influence every aspect of our lives, from politics and technology to our individual experiences and collective narratives.
Metamodernism, in essence, is about balancing the best of what came before – the grand narratives and optimism of modernism, and the skepticism and relativism of postmodernism – while forging ahead to create a new, coherent cultural reality.
So let's embark on this journey together to understand the metamodern era and its impact on our culture, our technology, and our art. Let's delve into Metamodernism.
Understanding Postmodernism and Metamodernism
To appreciate the metamodern, we must first unpack the concept of postmodernism. Rooted in skepticism, postmodernism came into being as a reaction to modernism’s perceived failures. Where modernism sought universality, believing in grand narratives and objective truths, postmodernism reveled in fragmentation and the subjective nature of reality. It questioned our institutions, our ideologies, and our grand narratives, challenging the very structure upon which our society was built.
However, as we moved deeper into the postmodern era, a palpable sense of fatigue began to set in. The endless questioning, the constant fragmentation, and the cynical deconstruction of everything began to take a toll. While postmodernism provided valuable insights into the limitations of modernist thinking, it also left us feeling disconnected and adrift in a sea of relativism and irony.
This is where Metamodernism steps in. As the cultural pendulum swings back from the fragmentation of postmodernism, it does not return us to the naive grand narratives of modernism. Instead, Metamodernism synthesizes these seemingly contradictory ideologies, embracing both the skepticism of the postmodern and the optimism of the modern.
In essence, Metamodernism is a search for meaning and unity that still acknowledges and respects the complexity of individual experience. It recognizes the value in both grand narratives and personal stories, aspiring to create a more cohesive cultural discourse.
The metamodern era is a new dawn that challenges us to be both skeptical and hopeful, to engage in dialogue and debate, and to harness the opportunities that lie ahead. It's not about choosing between the grand narrative and the individual, but rather finding a way to harmoniously integrate both.
Metamodernism in Politics
In recent years, we've seen political movements around the world that embody the elements of Metamodernism. On one hand, there's a call for a return to grand narratives and nostalgia for perceived better times, while on the other, there's a desire to dissolve hierarchical structures and traditional norms in favor of individual freedom and recognition.
A case in point is the political era marked by the rise of Donald Trump in the United States. Trump's slogan, "Make America Great Again," was a nod to the modernist ideal of a grand narrative - a return to American exceptionalism. It was an appeal to a past time when things were, as perceived by some, better.
Meanwhile, reactions on the left have taken a different trajectory. Movements to decentralize power, break down traditional norms, and encourage more individual subjectivity echoing postmodern sentiments.
Metamodernism enables us to interpret these political movements from a fresh perspective. It does not discard the grand narrative nor does it plunge into fragmentation. Instead, it presents a narrative of balance and synthesis, oscillating between the modernist and postmodernist perspectives, and offering a way forward that is nuanced, respectful of individual experiences, and yet oriented toward a shared goal for the culture and people.
In the realm of politics, the metamodern era isn't about swinging to one extreme or another. Instead, it suggests a way to reconcile the polarity and move forward, synthesizing the best of both perspectives into a more nuanced, inclusive future. This is the metamodern political landscape, complex and dynamic, where grand narratives and individual stories coexist and inform one another.
The Metamodernist Canvas in Graphic Design
Now, let's look at the impact of Metamodernism on graphic design, a realm where I live and breathe every day. Here, Metamodernism offers a fresh perspective, providing a way to express the complexity of the world we live in and creating a narrative that is both universal and individual.
Traditional graphic design was about simplicity and clarity. It was built on the modernist principles of functionalism and minimalism, where form follows function. Postmodern design, however, sought to question these principles, embracing complexity, contradiction, and the power of the image.
As a graphic designer in the metamodern era, I find myself torn between these two extremes. On one hand, I appreciate the clarity and simplicity of modernist design. On the other, I am captivated by the dynamism and complexity of postmodern aesthetics.
The solution, I believe, lies in the synthesis offered by Metamodernism. Metamodernist design does not reject the past, but rather builds on it. It blends the simplicity of modern design with the vibrancy of postmodern aesthetics, creating something that is both familiar and fresh.
The Metamodernist canvas is a space where contrasting ideas can coexist and inform each other. It is a space where the universal and the individual intersect, creating narratives that resonate on multiple levels. It is a space where design can play a role in building a more cohesive and well integrated society.
The challenge for designers in the metamodern era is to create designs that reflect this complexity and nuance, designs that speak to both the individual and the collective, designs that challenge, inspire, and unite. It's a tall order, but it's a challenge that, as designers, we are ready and excited to embrace.
Liminal Spaces and the Visual Language of Metamodernism
A pivotal concept within the Metamodernist philosophy is that of the "liminal space" - an in-between space, where transformation occurs. These spaces, often associated with uncertainty, dislocation, and transition, have become particularly poignant in recent times as we grappled with the global impact of COVID-19.
Within this context, we've all had a shared experience of liminality. Offices, parks, and public spaces - once bustling with activity - suddenly became eerily quiet and deserted. These images have since been ingrained in our collective memory, symbolizing a profound shift in our way of life.
From a visual perspective, these liminal spaces offer a unique canvas to create Metamodernist narratives. Picture a 3D render of an empty office space, serving as a backdrop for a fusion of past and future aesthetics, where classical works of art - subtly altered - coexist with modern elements. Consider the emotional impact of a low-resolution Mona Lisa or a melting clock a la Salvador Dalí set against the familiar concrete reality of the modern workspace.
This use of liminal space is not just a stylistic choice. It's a nod to our shared experiences, an acknowledgment of the transitions we are going through as a society. It's a way of showing that while we live in an era of immense change and uncertainty, we are also capable of creating new narratives, of finding beauty in the unfamiliar, and of moving forward together.
The challenge in Metamodernist design is to create a visual language that resonates with our collective experiences, that brings together the past and the future, the familiar and the strange, and that stimulates thought, dialogue, and connection. And that, I believe, is where the true power of Metamodernist design lies.
Metamodernism in Art, Music, and Memes
Just as in politics and graphic design, Metamodernism manifests itself in various facets of culture, from art and music to internet memes. This wide-ranging influence attests to the universality of Metamodernist thinking and its ability to encompass and unify diverse aspects of human experience.
In visual arts, consider Banksy's elusive street art, which often blends irony and sincerity, public space and private sentiment, modern graffiti techniques and traditional painting styles. In music, take the example of Kanye West's album "Jesus is King," which fuses gospel traditions with hip-hop sensibilities, blurring the line between secular and religious, the mainstream and the fringe.
Meanwhile, the internet meme culture, characterized by its oscillation between irony and sincerity, absurdity and poignancy, chaos and order, is perhaps one of the most profound expressions of Metamodernism. Memes like "This is fine," a dog calmly sitting in a burning room, epitomize the Metamodernist spirit by acknowledging the complexities and contradictions of modern life while also seeking to find humor and connection within them.
Even the trend of remixing adult rap with kids shows can be seen as Metamodernist. It juxtaposes the mature themes of rap music with the innocence of children's entertainment, resulting in a work that is both familiar and disorienting, humorous and thought-provoking.
In all these instances, Metamodernist works draw from the past and present, high culture and popular culture, the sacred and the profane, to create experiences that are multilayered, dynamic, and rich in meaning. They acknowledge the complexity and diversity of human experience, yet also aspire to forge connections, provoke thought, and inspire change.
The Rise of Bitcoin and Metamodernist Economics
The rise of Bitcoin - the world's first decentralized digital currency - is a prime example of Metamodernist influence in economics. Bitcoin incorporates elements from both modernist and postmodernist economic theories, yet transcends them by creating a novel economic system that has never been seen before.
On one hand, Bitcoin harks back to the modernist ideal of hard money. It revives the principles of scarcity and predictability that underpinned the gold standard, a system that many believe led to stable, prosperous economies. On the other hand, Bitcoin's design is rooted in postmodern principles of decentralization and disintermediation, disrupting traditional economic hierarchies and structures.
But Bitcoin isn't just a fusion of modern and postmodern economics. It goes a step further by incorporating elements of Metamodernist thinking. Bitcoin's design encourages a sincere, cooperative approach to economic interaction. Its transparent, tamper-proof ledger (blockchain) promotes trust and collaboration, discourages deceit, and enables all participants, no matter how big or small, to verify transactions independently.
Moreover, Bitcoin is a grand narrative in itself - a vision of a world where economic power is not concentrated in the hands of a few, but distributed among many. At the same time, it acknowledges the individuality and diversity of its participants. Each Bitcoin user has a unique address and can transact freely with anyone in the world, without the need for a middleman.
Bitcoin's rise offers a glimpse into what a Metamodernist economic system might look like - one that combines the best aspects of modern and postmodern economics, while also adding a new layer of trust, cooperation, and individual freedom.
The Impact of Urbit and Metamodernist Computing
Urbit symbolizes a compelling manifestation of Metamodernist ideology within the realm of technology. This unique operating system revolutionizes the individual's interaction with the digital world, intrinsically mirroring the principles of Metamodernism.
In contrast to the postmodern complexities that plague the current internet – a web characterized by surveillance capitalism, privacy invasion, and data centralization – Urbit leans towards a modernist vision. It champions the idea of the internet as a streamlined, intuitive tool, but concurrently it envisions something unprecedented: a digital landscape where each user not only owns but is also the infrastructure of their digital identity and data.
The design philosophy of Urbit embodies a characteristic Metamodernist oscillation, as it traverses between elements of the past and the future, the familiar and the uncharted. It embraces the modernist simplicity reminiscent of early computing while concurrently advancing a futuristic concept of a personal server for every individual, in which they possess full sovereignty over their digital existence.
Urbit’s operating system and its unique programming language, Nock and Hoon, employ a Kelvin versioning system. This system is designed to decrement towards zero instead of incrementing upwards, epitomizing the modernist pursuit of perfection and simplicity. Once the protocol reaches zero, it signifies that an ideal state has been achieved, and no further changes will be required. This, in essence, represents the modernist grand narrative embedded within Urbit's design.
In the wider narrative of Metamodernism, Urbit symbolizes a decentralized, user-centric digital future. It recognizes the individuality of each user and emphasizes their control over their digital persona and interactions.
The promise of a completely decentralized internet is a vision still in progress. Regardless, it offers crucial insights into how Metamodernist principles could potentially shape our digital future. It paints a picture of an equilibrium between grand narratives and individual nuances, encapsulating a collective digital aspiration, as well as personal digital realities.
Moving Towards a Metamodernist Future
The common thread running through the Metamodernist era is the simultaneous embrace of grand narratives and personal experiences, the oscillation between modernist and postmodernist ideals, and the sincere pursuit of a better future.
However, moving towards a Metamodernist future is not without challenges. The danger lies in taking Metamodernist principles to an extreme, where the balance between irony and sincerity, grand narratives and individual nuances, can be lost. It's vital to avoid the pitfalls of dogmatism and extremism that plagued previous cultural eras.
For instance, an overemphasis on grand narratives can lead to totalitarian tendencies, while an excessive focus on individual nuances can result in cultural fragmentation. Metamodernism's strength lies in its ability to reconcile these extremes, fostering a sense of shared purpose while acknowledging individual experiences and perspectives.
Similarly, the interplay of irony and sincerity, often seen in Metamodernist works, should not tip over into either pure cynicism or naive earnestness. The goal should be to create a dialectic, a conversation, a fusion that creates a new, more complex understanding.
As we move towards this future, we can use the tools at our disposal – from graphic design and art, to music, memes, Bitcoin, and Urbit – to explore and shape this Metamodernist narrative. By consciously adopting Metamodernist principles, we can construct a culture that is at once reflective of our individual experiences and representative of our collective aspirations. In doing so, we can pave the way for a future that truly encapsulates the complexity, diversity, and richness of the human experience.
A Future Infused with Metamodernism
Metamodernism offers a comprehensive cultural lens through which we can understand, critique, and navigate our world. It provides a potential pathway to a future where our grand collective narratives coexist harmoniously with our nuanced individual experiences.
In the creative world, artists and designers can become the torchbearers of this movement, integrating Metamodernist principles into their work. They can leverage the power of nostalgia, sincerity, irony, and innovation to create works that resonate with the complexities of the human condition, reflecting both shared experiences and personal journeys.
In the world of technology and economics, Metamodernist principles illuminate the path to a more decentralized, user-centric digital future, as embodied by Bitcoin and Urbit. These platforms highlight the value of individual autonomy within a collective system, creating a new narrative of economic and digital empowerment.
In the political realm, Metamodernism can help create a dialogue that is both encompassing and respectful of diverse perspectives. It advocates for a new kind of political discourse that eschews extreme polarization in favor of a nuanced conversation that acknowledges the complexities of our world.
In essence, the potential of Metamodernism lies in its capacity to weave a compelling tapestry of our collective human experience – one that is vibrant, complex, and teeming with diverse narratives. By understanding and embracing the principles of Metamodernism, we can co-create a future that truly reflects the dynamic interplay of our shared narratives and individual nuances.
In this promising future, we can all become active participants in the Metamodernist narrative, shaping a world that values both the grandeur of our collective dreams and the authenticity of our individual experiences. The future is not just something we move towards; it is something we actively create. And Metamodernism provides a powerful blueprint for this creation.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ deba271e:36005655
2023-05-06 18:50:59
@ deba271e:36005655
2023-05-06 18:50:59(This is a repost from my original article for Stacker News)\n\nIs some specific website, like Twitter, bringing you joy or is it bringing you the opposite? Do you have a hard time stopping? Here's a quick tutorial recommended by 9 out 10 dentists. \n\nFirst rule: Never run random bash scripts you find online without reading the scripts yourself! \n\n---\n\n## Blocking with /etc/hosts\nIf you understand the first rule, then read, copypaste and run following script in your terminal. \n\nOn Linux or MacOS\n
shell\nsudo bash -c "cat >> /etc/hosts << EOF\n\n0.0.0.0 twitter.com\n0.0.0.0 reddit.com\nEOF\n"\n\nAnd that's it. This should apply the rule immediately. \nIf you want to check how does your/etc/hostslook like, then just runnano /etc/hosts.\n\nOn Windows\nbatch\necho 0.0.0.0 twitter.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\necho 0.0.0.0 reddit.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\n\n\n--- \n\n## Blocking with pi-hole\nEven better option is if you have pi-hole set up on your network to proxy all your DNS requests. If you didn't know pi-hole is also available on Umbrel or Citadel.\n\nSimple steps:\n1. Sign in to your your pi-hole admin interface, e.g. https://pi.hole/admin/index.php\n2. Navigate to Blacklist\n3. Addtwitter.comin the Domain input box and click on Add to Blacklist\n4. You are all set. -
 @ c9dccd5f:dce00d9a
2023-05-02 07:16:55
@ c9dccd5f:dce00d9a
2023-05-02 07:16:55Every fundamental particle carries an intrinsic angular momentum, which we call 'spin'. It is important to remember that this is an intrinsic quantum mechanical property of particles. There is no such thing as a spinning sphere in the classical sense. Nevertheless, the image of a spinning sphere is often a good analogue to understand what is going on.\n\n## Helicity\n\nThe helicity of a particle is the projection of its spin vector onto its linear momentum. In the spinning analogy, it is the relation of its spin direction to its direction of motion. The particle helicity is called either right-handed or left-handed. We say that the particle has right-handed helicity if the spin is aligned with the direction of motion, and left-handed helicity if the spin and motion have opposite orientations. In the spinning analogy, we can immediately understand where the names come from and what they mean. We look at your hands, make a fist and spread the thumbs. The thumbs indicate the direction of motion and the curled fingers indicate the direction of spin. We point our thumbs in the direction of motion and compare the fingers with the direction of spinning we see: If they are in the same direction as the right hand, we call it right-handed helicity, and conversely.\n\nSince massless particles (e.g. photons) travel at the speed of light, we will never find a reference frame in which this particle is at rest, i.e. we cannot find a rest frame. Therefore, the helicity will never change, since the spin is fixed and the direction of motion is the same in all reference frames.\n\nOn the other hand, massive particles travel at a speed less than that of light, so in principle we can find a rest frame. In fact, we can even find a reference frame in which the particle appears to be moving in the opposite direction. Yet the spin of a particle never changes. This leads to the fact that for massive particles the helicity can change because the direction of motion can be reversed, resulting in the opposite helicity. Note that this is not possible for massless particles, because we cannot move faster than them. \n\nThus we see that the mass of a particle tells us whether the helicity of a particle is an intrinsic property of the particle. For a massless particle, the helicity is fixed in all reference frames, whereas for a massive particle this is not the case, because different observers can infer different helicities for the same particle. \n\nAs physicists, we like to find fundamental properties of a particle. We therefore ask whether there is a related property to helicity that is intrinsic to particles. We call this fundamental property chirality.\n\n## Chirality\n\nChirality and helicity are closely related. Just as we say a particle has right-handed or left-handed helicity, we say a particle has right-handed or left-handed chirality. Sometimes we can drop the '-handed' and just say right-/left-helicity or right-/left-chirality. For massless particles, helicity and chirality are the same thing, so a right-chiral particle will also have right-helicity. For massive particles, however, helicity and chirality are different. A massive particle has a certain chirality but can have both helicity states, e.g. a right-chiral particle can have right or left helicity depending on the frame of reference. \n\nChirality is an abstract concept that refers to a fundamental intrinsic quantum mechanical property of a particle. However, a useful and nice visualisation can be made by looking at our hands. We hold our hand in front of us. The left and right hands are mirror images of each other. No matter how we rotate, flip or move one hand, it will never look exactly like the other hand. Our hands have different chirality.\n\nIn physics, particles with different chirality can be considered as completely different particles. It refers to how a particle's quantum mechanical wave function behaves under rotation. The quantum wave functions of left- and right-chiral particles behave differently under rotation.\n\nThe measurable physical effect of a particle's chirality can be seen in the theory of the weak interaction. The weak interaction only affects left-chiral particles and not right-chiral ones. As a result, neutrinos, which are weakly interacting particles, are only observed in left-handed chiral states.\n\n---\n\n_I hope this post has helped you understand the concept of helicity and chirality in physics. If anything is still unclear, or if an explanation could be improved to make it easier to understand, please comment or write to me. I am happy to answer. I'm looking forward to your feedback. PV_ 🤙\n\n---\n\n
v0 @ 785591; v1 @ 785712: fixed typos and added a missing sentence; v2 @ 787922: slight changes to the layout -
 @ dafdf2c1:cd561387
2023-08-12 15:11:47
@ dafdf2c1:cd561387
2023-08-12 15:11:47Yakihonne remains at the forefront of innovation, consistently introducing features that enhance the user experience. Come with me as I embark on another round of updates, Let's talk about the remarkable additions that are set to revolutionize your interactions and engagement within the Yakihonne community. "Drafts" and "Stats Previews" are here to redefine how we create, share, and connect on this dynamic platform.
Introducing "Drafts": Safeguarding Your Creative Journey
Imagine being in the flow of crafting a compelling article, pouring your thoughts onto the digital canvas, when life's demands unexpectedly call you away. In the past, this scenario could have led to the frustrating loss of your valuable work. Enter Drafts," your invaluable ally in the creative process. This feature is designed to seamlessly preserve your progress, ensuring that your ideas are never lost in the void. With "Drafts," you can now save your articles for later editing or publishing, allowing you to pick up right where you left off whenever inspiration strikes. "Drafts" empowers you to reclaim control over your creative journey, providing a secure haven for your evolving ideas.

Unveiling "Stats Previews": Insights into Your Impact
The power of engagement lies not only in creating content but also in understanding its reception. "Stats Previews" empowers you with a new level of insight into your contributions. Visualize who zapped, upvoted, or downvoted your articles – a valuable window into the impact of your content on the Yakihonne community. This transparency bridges the gap between creators and their audience, enabling you to fine-tune your content strategy based on real-time feedback. With "Stats Previews," you can make informed decisions to amplify your influence and engagement, fostering deeper connections with your fellow Yakihonne enthusiasts.
Preview of SATs indicating individuals who have zapped and upvoted.



A Glimpse into the Future: Leveraging Yakihonne's Enhancements
As we embrace the possibilities brought forth by "Drafts" and "Stats Previews," we set our sights on a future where creativity knows no bounds. "Drafts" ensure that your ideas are nurtured and ready for further exploration, while "Stats Previews" empower you to harness the full potential of your contributions. These enhancements mark a new chapter in your Yakihonne journey, where the fusion of technology and creativity unlocks uncharted avenues of expression and connection.
In Conclusion: Embrace the Evolution
With every update, Yakihonne paves the way for a richer, more immersive content creation experience. "Drafts" and "Stats Previews" are not just features; they are gateways to a universe of possibilities. Embrace them, experiment with them, and let them fuel your imaginative fire. The stage is set, the spotlight is on you, and the Yakihonne community eagerly awaits the masterpiece you'll create.
Embrace the evolution, unleash your creativity, and let your voice resonate across the Yakihonne cosmos. Your journey is boundless, and with "Drafts" and "Stats Previews" by your side, your potential knows no limits.
-
 @ 765da722:17c600e6
2023-08-11 22:41:47
@ 765da722:17c600e6
2023-08-11 22:41:47Some of my friends install different Linux distributions and flavors more often than they brush their teeth. I'm not afflicted with this malady, only because I'm not much of a technical person. If I were, I'd be a part of that Great Conversation about the pros and cons of the latest and greatest.
As much as I hate social media, I confess, as if I were in an AA meeting, of being a hopper, skipper, and jumper from one to another Fediverse boat, all the way back to GNU Social and Friendika (note spelling), if not before, coming down to Mastodon, Hubzilla, Misskey and Firefish. I joined Twitter in 2008, left it out of disgust, returned recently, but ever so meekly, with revived hopes, albeit not high ones.
Before I saw the light, Google kicked everyone's legs out from under them by axing their latest social attempt and Facebook began limiting what my contacts could see of my posts. Slowly, the realization dawned. OK, so I'm not too bright to start with, but even a slow brain can have a synapse connect now and again.
Nostr was the latest shiny coin to come rolling along, even though the whole crypto-thing is over my head. But the decentralized star shone brightly, so in we went. Except my posts kept disappearing and nobody could or would tell me what was happening. Switch relays, one kind person said. As if I were to know which were bad and which were good. So I abandoned the idea for the time being. Maybe when the threshold lowers and the little people can just hop right in, there might be another flicker of hope renewed.
Yet here we are on Habla, attempting another stab at it (excuse the violent figure, but hey). What is this, an appeal, a complaint, a wishful thought? Take it for what it's worth to you. We take it as another trail at whose end the Holy Grail is probably not to be found.
-
 @ d2fb756f:453e247e
2023-08-12 14:57:42
@ d2fb756f:453e247e
2023-08-12 14:57:42In the dynamic realm of cryptocurrency and blockchain technology, innovation persists as a driving force. A notable development within this landscape is the integration of "Zaps" with the Lightning Network. Zaps introduce a remarkable mechanism for expediting payments, thereby opening doors to frictionless transactions. This exposition aims to elucidate the concept of Zaps and their synergy with the Lightning Network.
Unraveling the Lightning Network
The Lightning Network emerges as an ingenious solution to enhance the efficiency of Bitcoin transactions. Analogous to a superhighway, this network minimizes congestion on the Bitcoin blockchain by facilitating off-chain transactions. It accomplishes this through temporary payment channels that enable instantaneous transfers, circumventing the typical delays and fees associated with on-chain processes. In essence, the Lightning Network serves as a private express lane for swift transactions.
Unveiling Zaps
Within the context of the Lightning Network, Zaps emerge as a compelling augmentation. Zaps introduce a new paradigm of interaction, further refining the transaction experience. Fundamentally, Zaps manifest as lightning invoice receipts, signifying payments exchanged between users.
Herein lies the operation: Consider a scenario where you intend to tip a content creator, acquire a digital asset, or effectuate a peer-to-peer transfer. Zaps seamlessly facilitate such transactions. Upon initiating a Zap, a payment request is transmitted to the recipient's Lightning wallet.
The Zap Request and Confirmation Process
-
Initiation of Zap Request (Type 9734): The user initiates a payment utilizing Zaps. A Zap request is formulated, encapsulating the payment amount, recipient details, and optional message. Subsequently, this request is conveyed to the recipient's Lightning wallet.
-
Recipient's Acknowledgment (Zap Receipt, Type 9735): Upon receipt of the Zap request, the recipient's Lightning wallet acknowledges the transaction, generating a corresponding Zap receipt. This receipt serves as confirmation of the completed payment and encompasses pivotal transaction particulars.
Benefits of Zaps
-
Immediate Transaction Fulfillment: Zaps expedite payment processing, obviating the need for prolonged blockchain confirmations. Transactions transpire in near real-time.
-
Facilitation of Microtransactions: Zaps facilitate the seamless transfer of even minute cryptocurrency sums, effectively sidestepping concerns regarding exorbitant fees. This feature facilitates microtransactions, pertinent for activities such as tipping, charitable donations, and pay-as-you-go utilities.
-
Elevated User Engagement: Zaps epitomize user-centricity, simplifying the payment trajectory and rendering it accessible to a broader demographic. This convenience bolsters the adoption of cryptocurrency-based transactions.
-
Diverse Applications: Zaps boast versatility, catering to an array of scenarios, encompassing content creator gratuities, digital asset acquisitions, service payments, and beyond. The spectrum of possibilities is bound solely by creative imagination.
Conclusion
Zaps signify a noteworthy advancement in cryptocurrency transactions, augmenting the capabilities of the Lightning Network and refining the payment process. This innovation ushers in a regime of rapid, efficient, and versatile transactions, all while maintaining cost-effectiveness. Whether one seeks to acknowledge a content creator or acquire digital artistry, Zaps epitomize the epitome of cryptocurrency transactional ease.
Anticipate forthcoming blockchain innovations to usher in user-friendly solutions akin to Zaps, perpetuating the fusion between conventional finance and the captivating domain of cryptocurrencies. When the need arises for swift transactions, the concept of Zaps shall undoubtedly come to mind, underscoring the seamless experience they confer.
-
-
 @ 75656740:dbc8f92a
2023-07-20 19:50:48
@ 75656740:dbc8f92a
2023-07-20 19:50:48In my previous article I argued that it is impossible to have an effective filter in a delivery-by-default and universal reach messaging protocol. This might seem over-specific because, after various filters, nothing is truly universal or delivery-by-default. * Mail is limited by a cost filter phone calls by call screening services. * Faxes are limited by the fact that we all got sick of them and don't use them any more. * Email dealt with it by pushing everyone into a few siloed services that have the data and scale to implement somewhat effective spam detection. * Social media employs thousands of content moderators and carefully crafted algorithms.
Most of these are, however, delivery-by-default and universal in their protocol design. Ostensibly I could dial any number in the world and talk to anyone else in possession of a phone. If I have an email address I can reach anyone else. I can @ anyone on social media. All these protocols make an initial promise, based on how they fundamentally work, that anyone can reach anyone else.
This promise of reach then has to be broken to accomplish filtering. Looking at limiting cases it becomes clear that these protocol designs were all critically flawed to begin with. The flaw is that, even in a spam free case, universal reach is impossible. For a galaxy-wide civilization with billions of trillions of people, anyone individual wouldn't be able to even request all the information on a topic. The problem is more than just bandwidth, it is latency.
That is without spam and trolling. With spam and trolls things crash at a rate proportional to the attention available on the protocol.
The answer is to break the promise of universal reach in theory so we can regain it in practice. By this I mean filtering should happen as soon as possible to keep the entire network from having to pass an unwanted message. This can be accomplished if all messages are presumed unwanted until proven otherwise. Ideally messaging happens along lines of contacts where each contact has verified and signed each-other's keys. That is annoying and unworkable, however, instead it should be possible to simply design for trust. Each account can determine a level of certainty of an identity based on network knowledge and allow or deny based on a per-instance threshold.
While requiring all messages to originate "in network" does break the promise of the internet as an open frontier, the reality is that, like the six degrees of Kevin Bacon, everyone you want to reach will be in your network if scaled out to a reasonable level. This puts a bottleneck on bot farms trying to gain entry into the network. While they will be able to fool people into connecting with them, such poor users can lose the trust of their contacts for introductions, algorithmically limiting reach.
With Nostr I expect this form of filtering will arise organically as each relay and client makes decisions about what to pass on. This is why I like Nostr. It isn't exactly what I want, but that doesn't matter I am probably wrong, it can morph into whatever it needs to be.
-
 @ 5e5fc143:393d5a2c
2023-04-15 17:18:11
@ 5e5fc143:393d5a2c
2023-04-15 17:18:11\nJust revisiting some quick tips for #newbies #pow #public #blockchain users only.\n\nif you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.\n\nHot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process\n\nCold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts\nPaper wallets are best n cheapest form of cold wallet that can used once n thrown away.\n\n#Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/\n\n\n
 \n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n
\n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n -
 @ 75bf2353:e1bfa895
2023-08-11 21:33:21
@ 75bf2353:e1bfa895
2023-08-11 21:33:21In this chapter, you will learn what a bitcoin seed phrase is and what the words represent. You will learn how to create a bitcoin testnet wallet and how to revover testnet bitcoin on a different wallet. Real bitcoin transactions are sent over the main network, also known as mainnet. Testnet bitcoin is has no real world value so it gives us a low-stakes way of learning how to create bitcoin wallets. . Padawan Wallet is a testnet only wallet. Green wallet has a testnet option. Since testnet bitcoin is recorded on the testnet bitcoin blockchain, both wallets will display the same information in the same way you see the same people on Damus or Amethyst. If you have never made a bitcoin transaction or are unsure how it works, hopefully you will find this chapter helpful. If you are a Cypherpunk ninja, please share this. Constructive criticism is also welcome.
There are 2048 words in the BIP 39 wordlist Each word represents 4 digits from 0000 - 2047. The first 4 letters of each word are unique.
abandon = 0000
bacon = 0138
zoo = 2047
Before we move on, let's disect another bitcoin wallet with 12 words like a pig in a high school biology class. Scan this screen shot of a QR code Keith Mukai drew with a pen and paper template with your phone. It should be obvious that you will never take a picture of a key you hold bitcoin with on your cell phone. Don't do that. When you scan the hand drawn QR code with a mobile phone, this number will appear on your screen:
113501140662064312980397197212600826068006871766
Try it yourself.

4 digits in this number translate into a word on the BIP39 wordlist. There are 48 digits. 48 / 4 = 12. This is a 12 word seed phrase with 128 bits of entropy.
1) 1135 2) 0114 3) 0662 4) 0643 5) 1298 6) 0397 7) 1972 8) 1260 9) 0826 10) 0680 11) 0687 12) 1766
We don't need to buy a rasberry pi and create our own Seed Signer to obtain the key from this QR code. We can obtain the seed words by looking them up on the Bip39 wordlist and subtracting 1 to get the word.
1) 1135 = misery 2) 0114 = asthma 3) 0662 = famous 4) 0643 = expand 5) 1298 = pear 6) 0397 = cousin 7) 1972 = wagon 8) 1260 = outer 9) 0826 = grunt 10) 0680 = feel 11) 0687 = fiber 12) 1766 = symptom
We can verify this by typing the words into Ian Coleman's BIP39 Tool.

1135 -1 = 1134. Therefore misery is word 1134 on the BIP9 wordlist

0680 - 1 = 689 feel because it is word 679 on the BIP39 wordlist. Notice how the zeros count because it is part of a longer number.

We do this becase it is easier for humans to remember these 12 words than it is to remember 113501140662064312980397197212600826068006871766. The 12 words are just a mnemonic to make it easier to write down or remember if you become a refugee.

Now that we understand what a bitcoin wallet is, let's create our first bitcoin testnet wallet. Remember: bitcoin on the testnet network has no real world value. Take the time to carefully follow the instructions to learn how bitcoin wallets work, but if you make a mistake, you won't lose any real money. If you have bitcoin IOU's on an exchange because you are too afraid of using bitcoin, you have no reason to be afraid of making a testnet wallet.
Step 1) Download the Padawan Wallet.
Don't think different. Think adversarial. Apple might make the phones all the cool kids want for Christmas. They might have the Bitcoin White paper hidden in their computers, but they also banned bitcoin wallets in 2014 and nostr zaps in 2023. You can pick up a used Google Pixel 4 for less than a hundred bucks on swappa.com. You could also install the Padowan wallet on Google Play, but think adversarial. Download the APK file on github in case Google bans you. If they ban downloading APK files, install Graphene OS and Obtanium. These tools are a little complicated for a book entitled the Easy Way To Take Self-Custody of Your Bitcoin, but keep these options in mind in case you need them. It may not be as easy as Google Play, but it's not that hard either.
Step 2) Tap Menu > Recover Phrase. You will see 12 words that look something like this:

Your words will be different, of course, but these are the words you will use to recover your wallet later. This seed phrase is 12 words. Each word represents a four digit number from 0000 to 1247. To show you how this works, we can use Ian Coleman's BIP39 tool. Before we begin, you must solemnly swear to NEVER ENTER A BITCOIN SEED PHRASE MEANT FOR COLD STORAGE INTO A WEBSITE. Hot wallets are necessary for coinjoins and we will go over this later. Far too many people have recieved phisshing emails that say their bitcoin is at risk, please put your seed phrase into this website to recover it. They panic. "Oh no. I don't want to lose all my bitcoin. I should put my ledger seed words into this very professional looking website. The email is from ledger.com so it must be legit. DON'T DO IT! IT'S A TRAP! You will lose all the bitcoin you controlled with that wallet.
You can enter a testnet seed phrase into the Internet though because the testnet Bitcoin has as much value as monopoly money. When we enter these 12 words into the mnemonic code converter, we can look deep inside the anatomy of our practice bitcoin wallet. The first sentence on this website tells us:

Notice how we can't just type 12 random words into the Mnemonic Code Conveter. This helps us enter the words correctly. The words for my Padawan Wallet are:
theory pen whale unique inch include emerge light obscure avocado battle vacantWrite Down your words .
Hardware wallets often come with cardboard cards with numbers and branding on them. The author does prefers to use index cards. You could make an argument for acid free paper, but I like to engrave my seeds in steel and place them in a security envelope with the index card. I find the index card easier t read. Pro Tip: Take your time. Right legibly. I once had a wallet with the word "store" that I couldn't recover for a couple years because my poor penmanship made the word look like "stove."

What if I read the eleventh word "bacon" instead of "battle" by accident?

As you can see, these 12 words to do not create a valid bitcoin wallet.
There is no address associated with these words.
This is because a bitcoin seed phrase is a random number, but the last 4 digits are calculated to prevent such accidents.
According to Yan Pritzker, in the book Inventing Bitcoin:
"Guessing the entire key would be similar to guessing a specific atom in the universe, or winning the Powerball 9 times in a row: One chance in 115,792,089,237;316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936."
The numbers must be in the exact order and the last four must be caulculated. It's not like you can just enter 12 random words from a forutne cookie. They need to be specific words from the BIP39 wordlist and the last word must be calculated as a checksum. Next we will get some testnet bitcoin, but first--Double check the words. When you create a real bitcoin wallet, you should triple check.
Get Some Testnet BitCoin
 **
**2) Click Get Coins. You should get 75,000 testnet sats, but since I did it twice, I got 150,000 testnet sats,

Go back to the main menu
Click the menu button
Click Send testnet coins back

4) You will see a testnet wallet address. Copy the testnet address. Then navigate back to the wallet, paste the address and click send.

Confirm the amount.

The transaction should confirm soon. If it hasn't in about ten minutes, click sync. Write down your balance. We will use this to verify our wallet is correct in the next section

Delete The Padawan Wallet From your Phone.
Padawan does not give you an option to restore your wallet. Wallets do break. I have had a real bitcoin wallet fail me. This was stressful, but I was able to recover my sats. Bitcoin is not stored on a hardware wallet. The key is stored on the hardware wallet. That is why many bitcoiners refer to wallets as a signing device. It's a better term, but I'm old school. Whatever you call it, bitcoin is stored on the bitcoin time chain. It's like a mailbox in the sky. Anyone can place an envelope in a mailbox in the same way anyone can send bitcoin to a bitcoin address. Only the mail carrier with the key can open the mailbox can send the envelopes inside. In the same way, only the person with the key can send bitcoin associated with the addresses calculated for that wallet,
Install Green Wallet by Blockstream
Green Wallet is a mobile wallet developed by Blockstream, a company nuilding bitcoin infrastructure. It is founded by Adam Back, who you might remember from the last chapter. He is the guy who discovered hashcash and Satoshi cited hashcash in the White Paper. You can download this wallet on F-Droid. It's also available on Google Play and the app store if you're into that sort of thing, and I already told you how I feel about these walled gardens, but I won't waste anymore time preaching.
Step 1) Install and update the app

Step2) Check the "I agree to the Terms of Service and Privacy Policy. Click on app settings in the lower right-hand corner.

Step 3) Toggle enable testnet button. Then navigate back to the first screen.

Step 4) Tap Add Wallet

Step 5) Tap Restore Wallet

Tap Testnet under the Select Network Menu
Step 6) Enter the 12 recovery words you wrote down when you first set up your Padawan Wallet These are the words you wrote on an index card.
Notice how the words auto- populate as you type. If you type 4 letters, you will only see one word. Click Continue when finished.

You'll need to set a PIn. Then you will need to verify the PIN. Click Continue once you are done. Write this PIN down and keep it with the seed. Your PIN is a secret, but if someone finds your seed words, you're PIN doesn't matter. Blockstream did not let me take a screen shot of the PIN setting process, but it's self-explantory.
Step 7) Verify this is your wallet

We have 0.0006569 Testnet Bitcoin or 65,690 sats. This is exactly how much we had in our Padawan Wallet.

Two Tesnet Wallets, One Seed Phrase
How did this happen? Maybe Green Wallet and Padawan Wallet colluded somehow, but that seems unlikely. If we wanted to verify this the hard way, we could check the addresses and set up an air gapped computer, but this is the easy way. The most likely explanation for these two amounts matching is math that was verified on the bitcoin testnet network and the nodes verified the transactions associated to this public key. Therefore, we conclude that our seed phrase is correct and we can be sure to have access to these testnet sats as long as we have our 12 words. We were not able to recover our testnet bitcoin on Padawan once we deleted the wallet, but still recovered our testnet bitcoin using green wallet. Most Hardware Wallets are Interoperable There are a few exceptions like Muun Wallet or Tap Signer, but if your hardware wallet goes out of business or breaks you will be able to recover it on any other wallet.(Even the tap signer, but it's more complex) This is because our bitcoin is not inside the wallet. It is on the thousands of computers around the world. I just demonstrated this with testnet, but bitcoin works the same way. Michael Saylor compares this to an inpenatrable safe deposit box in the sky. You might think the money is on the Internet, but that's not the whole story. It is on an inpenatrable network. Transactions can be broadcast via satellite *too. Only the person with our key can spend these testnet bitcoin. This is why you must keep your keys safe. Anyone with your seed phrase has access to your safe deposit box in the sky.
Although testnet bitcoin has no real-world value--they are still hard to come by. Therefoere, if you don't plan on using these testnet sats again anytime soon, please send the testnet sats back to the padawan wallet.
Now that you know how to create and recover a testnet bitcoin wallet, it's time to take the next step: Set Up A Cold Card
Blogging Bitcoin 802,712
If you found value in this blog post. Please send value back as a zap.
-
 @ cca7ef54:e7323176
2023-08-05 10:44:08
@ cca7ef54:e7323176
2023-08-05 10:44:08เราเคยอยู่กับคำว่าบิตคอยน์เป็น Store of Value (SOV) มานานแค่ไหนกันแล้วครับ? อำนาจอธิปไตยทางการเงินนั่นอีก..
ในกลุ่มคนที่ตระหนักถึงปัญหาภายในระบบ มักจะยอมรับบิตคอยน์ในฐานะสินทรัพย์ที่จะเก็บรักษามูลค่าผ่านกาลเวลาให้พวกเขาได้ คำถามก็คือคนกลุ่มนี้มีจำนวนมากแค่ไหนในสังคม? สังคมที่เราเรียกว่า Matrix นั่นน่ะ..
ใช่ครับ.. มันยังมีน้อย
ยังไม่ต้องเอ่ยถึงการเก็บอย่างไรให้ปลอดภัย นั่นยังน้อยลงไปได้อีก เราจะเห็นได้ว่าดีมานด์ในฝั่งที่ต้องการยอมรับบิตคอยน์ในอดีตนั้นหลักๆ มีเพียง 2 กลุ่ม กลุ่มแรกคือกลุ่ม SOV อีกกลุ่มคือนักเก็งกำไร กลุ่มอื่นๆ ยังมีอยู่เพียงแค่ประปรายเท่านั้น ในต้นปี 2022 ที่ราคาบิตคอยน์เริ่มเปลี่ยนเป็นขาลง ผมเองก็จินตนาการไม่ได้เหมือนกันว่าดีมานด์ในระลอกถัดไปจะมาจากอะไรได้บ้าง ผมรู้แค่ว่าในขาลงนั้น บิตคอยน์มักจะมีพัฒนาการใหม่ๆ ผุดขึ้นมาเสมอ
ผมหมายถึง.. ความอยากได้บิตคอยน์มาไว้เป็นของตัวเองนะ ไม่ได้หมายถึงดีมานด์ในการซื้อขายที่จะทำให้ราคาพุ่งขึ้นอะไรแบบนั้น
จนกระทั่งถ้าผมจำไม่ผิด คงจะเป็นช่วงครึ่งหลังของปี 2022 นั่นเอง.. กระแสความมหัศจรรย์ของ Lightning Network ก็เริ่มอุบัติขึ้นอย่างต่อเนื่องในกลุ่มสังคมชาวบิตคอยน์ทั่วโลก ไม่เว้นแม้แต่ในไทยที่เราเองก็มีส่วนช่วยกันผลักดันมาจนถึงวันนี้ (ความจริงมันมีมาก่อนหน้านั้นแล้ว โดยเฉพาะหลังจากอีเว้นท์ใหญ่ที่เอลซัลวาดอร์ แต่ก็ยังไม่เปรี้ยงปร้างเท่าใดนัก)
https://i.imgur.com/t0sJ4ju.png
Lightning ทำให้โลกของบิตคอยน์เต็มไปด้วยความเป็นไปได้ จากเงินนิ่งๆ ถือไว้รอรวย เงินสะสมไว้ให้ลูกให้หลานที่โดนตราหน้ามาตลอดว่าซื้อก๋วยเตี๋ยวหน้าปากซอยก็ยังไม่ได้ กลายเป็นเงินสะดวกจ่ายที่ในวันนี้เริ่มติดอกติดใจกันทั่วบ้านทั่วเมือง (ก็หมายถึงในกลุ่มคนที่ยอมรับบิตคอยเนอร์นั่นแหละนะ)
บิตคอยน์เคยเป็น "ของยาก" สำหรับทุกคน จะโอนเข้า-โอนออกแต่ละทีเล่นเอาปวดหัว มือไม้สั่นกันเลยทีเดียว แต่วันนี้พวกเราหลายคนรู้แล้วว่า เราสามารถเอาหน่วยย่อยที่เล็กที่สุดของมันมาส่งต่อให้กันได้ ไม่ว่าจะส่งกันเล่นๆ ส่งแทนใจ จีบกัน หรือซื้อ-ขายของ ฯลฯ ก็อย่างที่ได้เห็นกันในงาน BTC2023 ใช่ไหมครับ
มันติดอยู่อย่างเดียว.. ถ้าไม่นับเรื่องการใช้งานในฐานะคนทั่วไปที่ทำได้ง่ายๆ หมูๆ แล้ว การบริหารจัดการระบบ หรือรันโหนดบิตคอยน์ไลท์นิ่งมันทำให้พวกเรารู้สึกว่าคงต้องเป็นระดับเทพเท่านั้นที่ทำกันได้ การทำความเข้าใจกับกลไกการทำงานของมันก็เป็นเรื่องไม่ง่ายเช่นเดียวกัน
พอเป็นแบบนี้ผมก็นึกในใจว่า.. อืม... มันคงต้องใช้เวลาอีกไม่มากก็น้อยให้คนได้ค่อยๆ เรียนรู้ ทำความเข้าใจและคุ้นเคยกับเทคโนโลยีใหม่ให้มากกว่านี้
แต่ผมก็เชื่อนะ.. นี่ไม่ใช่เรื่องที่เป็นไปไม่ได้ มันไม่ได้ยากขนาดนั้น ที่เราต้องการคือ "วิธี หรือ แนวทาง" ในการนำเสนอ หรือ เผยแพร่ความรู้ที่คนทั่วไปจะเข้าถึงและจับต้องมันได้ง่ายกว่านี้
Right Shift ถูกผลักดันการดำเนินงานไปในทิศทางนั้น ทิศทางที่จะทำให้ "ตัวเลือก" ในการยอมรับบิตคอยน์เป็นรูปเป็นร่างเพิ่มมากขึ้นอีกทางหนึ่ง นั่นคือ "การนำบิตคอยน์มาใช้งานจริง" ในยูสเคสลักษณะที่บิตคอยน์จะกลายเป็น *"Means of Payment"*** การใช้จ่ายทางเลือกใหม่สำหรับคนที่มีหัวใจอิสระนั่นเอง
เราประสานงานร่วมมือกับพาร์ทเนอร์ในหลายๆ ส่วน รวมถึงพี่น้องของเราภายในคอมมูนิตี้ด้วย นอกจากคุณค่าที่จะไม่หายไปง่ายๆ ตามกาลเวลาแล้ว คุณค่าในการที่เรานำมันมาใช้ได้จริงๆ ก็ดีต่อใจพวกเราเหลือเกิน คนที่ได้สัมผัสมาแล้วด้วยตัวเองคงจะไม่มีอะไรมาเถียงผมได้มากนักในเรื่องนี้
แต่มันมีบางอย่างที่ทำให้ผมรู้สึกมาตลอดว่า.. แค่นี้มันยังไม่พอ
การมอบทางเลือกเพื่อให้คนปรับเปลี่ยนมายเซตที่เคย "หวง" บิตคอยน์ยิ่งกว่าไข่ในหินก็เรื่องนึง เรื่องความเป็นส่วนตัวหรือ Non-KYC ก็เรื่องนึง การเริ่มต้นที่ต้องใช้บริการ Custodial ไปก่อนก็เรื่องนึง การให้ความรู้ก็ว่ายากแล้ว การทำให้เกิดดีมานด์-ซัพพลายที่สมดุลกันนั้นมันยากยิ่งกว่า
เราเคยทำให้มีกิจการรองรับ Lightning กันมากโขในช่วงหนึ่ง แต่ไม่เคยมีใครรู้ว่าจะเอา Lightning จากไหนมาซื้อของ แล้วจะซื้อมันยังไงล่ะ?
พอมีคนเริ่มทำได้ พวกเขามองหาที่ซื้อ ปรากฏว่าซัพพลาย ผู้ประกอบกิจการยังโตตามไม่ทัน ติดๆ ขัดๆ และต้องการความช่วยเหลือในการเริ่มต้นอีกพอสมควร ไหนจะเรื่องกฏหมาย บัญชี ภาษีนั่นอีก.. เห็นหรือเปล่าครับ งานของพวกเราไม่ได้มีแค่ถ่ายทำคลิปแน่ๆ
https://i.imgur.com/hd1FJYK.png
ถ้ามองให้ครอบคลุมทั้งองคาพยพ งานนี้ใหญ่และยาวกว่าที่พวกเราคิดกันเอาไว้มากเลยล่ะ (เราในที่นี้ผมหมายถึงทุกคนในคอมมูนิตี้ที่มิงเป้าหมายเดียวกัน)
เราเองจึงมีความคิดกันว่า ในช่วงเวลาต่อจากนี้ พวกเรากลุ่มพาร์ทเนอร์หลักๆ Right Shift, LATES, BOB และ Chitbeer และอีกมากมาย น่าจะต้องใช้เวลาในการทำหน้าที่ขับเคลื่อนและเผยแพร่เรื่องราวเหล่านี้กันต่อไป โดยเราก็หวังว่าคงจะได้รับความร่วมมือร่วมใจจากเพื่อนๆ ในคอมมูนิตี้ของเราเป็นอย่างดี
เรากำลังวางแผนที่จะ ออนทัวร์ ไปยังสถานที่ต่างๆ อาจจะเป็นมหาวิทยาลัย สถานศึกษา ห้างร้าน ตจว ฯลฯ ที่ไหนก็แล้วแต่ที่ต้องการศึกษาบิตคอยน์ จัดทำหลักสูตรการเรียนการสอนออนไซต์ในลักษณะเดียวกับที่เกิดขึ้นทราเอลซัลวาดอร์ จัดอีเว้นท์ให้คนได้นำบิตคอยน์มาลองใช้ และยินดีมากๆ ที่จะได้รับความร่วมมือจากอาสาสมัครที่มีใจจะผลักดันร่วมกับเรา.. แต่แล้ววันนี้..
เมื่อไม่นานมานี้เอง.. ผมก็พบทางเลือกที่สาม
ถ้าการเริ่มต้นความสนใจจากฝั่งการลงทุน การเก็บออม เก็บรักษาหรือการนำบิตคอยน์มาสะสม นำมาใช้ มันเหมือนจะยากเกินไปสำหรับคนส่วนใหญ่
ถ้าเราลองมาปรับเลี่ยนมุมมอง โดยเริ่มจากสิ่งที่พวกเขาคุ้นเคยกันดีอยู่แล้ว เข้าถึงได้ง่ายและสนุกกับมันได้ก่อนล่ะ.. การยอมรับจะง่ายขึ้นและสมเหตุสมผลมากขึ้นที่จะกระโจนลงสู่หลุมกระต่ายต่อไปหรือเปล่า?
ผมไม่ปล่อยตัวเองจมอยู่กับความสงสัยนานเกินไป ว่าแล้วผมก็ลงมือสัมผัสมันด้วยตัวเองในทันที.. และคำตอบที่ได้คือ.. มันใช่จริงๆ ด้วย
เราแค่เปลี่ยนจากสื่อโซเชียลมีเดียเมนสตรีมที่กำลังทำให้เราต้องปวดกันมากขึ้นทุกวัน ๆ ไปอยู่บนสังคมใหม่ที่เป็นเหมือนรากเหง้าของสังคมออนไลน์ที่แท้จริง แบบนี้มันดูจะเดินต่อกันได้ง่ายกว่า.. ทำไมผมคิดแบบนั้น?
สังคมบนโปรโตคอลกระจายศูนย์ มันมอบอิสระให้เราในฐานะผู้ใช้แทบทุกด้าน เอาเข้าจริงๆ แล้วมันไม่ได้ยากไปกว่าการเปิดกระเป๋า Lightning ที่เราเคยทำกันมาแล้วแม้แต่นิดเดียว
วันนี้พวกเราหมื่นกว่าคนรวมกันกดไลค์บนเฟซบุ๊กไปกี่ครั้ง เพื่อแสดงความพึงพอใจต่อผลงานของครีเอเตอร์ หรือโพสต์ของเพื่อนเรา ที่บางทีเราจะเต็มใจทำมันหรือเปล่าก็ไม่รู้
ถ้าเปลี่ยนจากไลค์ มาเป็น Zap! ล่ะ?
มูลค่าทางเศรษฐกิจที่หมุนเวียนอยู่บนนั้นจะมากมายขนาดไหน (ปัจจุบันมีการ Zap รวมกันไปมากกว่า 12 BTC แล้วบนนอสเตอร์) มันไม่ใช่แค่เราที่ต้องไปคอย Zap คนอื่นเขา ถ้าคุณทำได้ดี ทำประโยชน์ต่อชุมชน เอาแค่เสียงหัวเราะก็ยังได้ คนอื่นก็พร้อมที่จะ Zap ให้คุณตลอดเวลาเช่นเดียวกัน
คุณสามารถใช้งานมันโดยไม่ต้องผูกกับกระเป๋าไลท์นิ่งก็ได้ คำถามคือคุณจะได้รับประสบการณ์ในการแสดงความพึงพอใจหรือรับเอามันมาแบบในทันทีเป็นมูลค่า Satoshi ได้อย่างไร?
ใช่แล้วครับ.. ด้วยสถานการณ์ดังกล่าว มันเลี่ยงไม่ได้ที่คนจะต้องเรียนรู้และทำความเข้าใจเกี่ยวกับบิตคอยน์และไลค์นิ่ง อย่างน้อยก็ในระดับเบสิค
https://i.imgur.com/0jzG9mh.png
แต่คราวนี้แรงจูงใจของพวกเขาไม่ใช่เพื่อความมั่งคั่งหรือความรำรวย ไม่ใช่อธิปไตยทางการเงิน หรือความเก่งกาจทางเทคนิคเพียงอย่างเดียว
มันจะมาจากความต้องการในการได้มีส่วนร่วมกับสังคมที่พวกเขาอยากเป็นส่วนหนึ่งในนั้นด้วย มาจากความต้องการที่จะขอบคุณหรือชื่นชอบผลงานของใครสักคนที่ได้มอบประโยชน์ให้กับเขาบนนอสเตอร์ มาจากความสนุกเพลิดเพลินกับชีวิตที่เป็นอิสระบนดินแดนแห่งใหม่ ฯลฯ
ในขณะที่ฝั่งครีเอเตอร์... แทนที่จะขาดทุนทั้งเงินทองและเวลารวมถึงแรงกายไปกับการนั่งคิดคอนเทนต์ข้ามวันข้ามคืน การหาทางทำให้คนได้เห็นโพสต์ของตัวเอง แล้วรอรับเงินที่แพลตฟอร์มอาจจะเบี้ยวเอาได้ในอีกเดือนถัดไป คอยหลบเลี่ยงอัลกอริทึมที่น่ารำคาญ สารพัดความเปลี่ยนแปลงที่ต้องปรับตัวตามให้ทัน
คราวนี้พวกเขาเพียงแค่ทุ่มเทคุณค่าลงไปในคอนเทนต์อย่างเต็มที่ โพสต์ออกไปให้คนที่ติดตามเขาได้เห็นกันแน่ๆ และรับเอาคำขอบคุณมาเป็น Sats ได้แบบวินาทีต่อวินาที
พวกเขาสามารถนำเสนอเนื้อหาแค่ทีละส่วนได้โดยไม่ต้องรอให้ทำเสร็จ พวกเขาสามารถนำเสนอเนื้อหารูปแบบใดก็ได้บนนั้น.. ผู้ใช้ก็เช่นกัน นี่คือกิจกรรมการส่งต่อคุณค่าให้กันที่เรียกว่า "Value for Value" บนนอสเตอร์
เมื่อ V4V กลายเป็นสิ่งที่พวกเขาชื่นชอบ พวกเขาจะเริ่มหันมาให้ความสนใจอย่างลงลึกในบิตคอยน์มากขึ้นเมื่อเวลาผ่านไป พวกเขาจะอยากครอบครองมันเพิ่มขึ้น มันจะเป็นอย่างไรได้อีก อย่างมากเขาก็แค่ไม่ชอบและมองหาทางเลือกอื่นในการยอมรับมันเท่นั้นเอง
เอาล่ะ.. คราวนี้คุณคิดว่า Network effect บนนอสเตอร์ กับในชีวิตจริงแบบไหนจะปรี๊ดปร๊าดแข็งแกร่งได้เร็วกว่ากัน?
เอาจริงๆ เราไม่จำเป็นต้องเลือกหรอกครับ ไม่จำเป็นต้องตัดสินใจว่าพวกเราจะผลักดันการยอมรับไปในทิศทางไหน.. จะเก็บออม จะให้ความรู้ นำมันมาใช้งานบ้างหรือจะผ่านการใช้ชีวิตใหม่บนสังคมโซเชียลมีเดียอย่างนอสเตอร์
เราควรจะผลักดันมันไปพร้อมๆ กันในทุกๆ ทาง เพราะมันต่างก็เป็นประโยชน์ต่อสังคมบิตคอยน์ของพวกเราทั้งนั้น มันเป็นประโยชน์ต่อทุกคนที่จะได้ลองสัมผัสมัน และเป็นประโยชน์ต่ิผู้คนในรุ่นถัดๆ ไป
Bitcoinization ที่เคยเป็นเพียงแค่ความฝันลมๆ แล้งๆ กำลังจะเกิดขึ้นได้จริงในเวลาไม่นานนับจากนี้ คราวนี้ผมเริ่มตอบความสงสัยของตัวเองในตอนแรกได้บ้างแล้ว ดีมานด์ควรจะมาจากเรื่องอะไรได้บ้าง มันก็ควรจะเริ่มต้นมาจากความสนใจของพวกเราก่อนนี่แหละครับ
สนใจมากพอที่จะลองเข้าไปสัมผัสมันในทุกด้าน หยิบเอาเงินเฟียตเน่าๆ บนหลังตู้เย็นของคุณไปเปลี่ยนเป็น Lightning สักตับนึง แล้วพามันลงไปโลดแล่นบนนอสเตอร์กันดูครับ
ปี 2023 ทางเลือกของพวกเรา ทางเลือกของคนทั้งโลกไม่ได้อยู่แค่เพียง SOV หรือ Lightning อีกต่อไป.. ซึ่งไม่ว่าทางไหนมันก็ดีต่อบิตคอยน์ทั้งนั้น
มันกำลังเปิดกว้างกว่าที่พวกเราคิด . . // Author by: Jakk Goodday
-
 @ 07aa4bc1:e286520c
2023-08-12 14:40:52
@ 07aa4bc1:e286520c
2023-08-12 14:40:52Yakihonne Unleashed: A Creative Oasis Blooms with Thrilling Updates! 🌟✨
Hold onto your keyboards, creators and wordsmiths, because Yakihonne has just dropped a digital bombshell of game-changing updates that's set to rock our content universe! 🚀 Get ready to buckle up as we dive deep into these shiny new tools that promise to redefine our Yakihonne experience.
This isn't just a routine facelift, folks. Yakihonne's latest innovations are like a symphony of user-friendly wizardry, sweeping in to tackle old problems and sprinkle some extra pizzazz on our creative playground. 🎉 So, grab your virtual magnifying glasses as we dissect each update, giving you the inside scoop on what's sizzling and what might need a pinch of fine-tuning.
By the end of this whirlwind review, you'll be armed with the ultimate guide to Yakihonne's evolution, ready to conquer this brave new world of words and wonders! 📚🔍"

"Drafts Unleashed: Your Creative Playground on Yakihonne! 🎨📝
Attention, creators! Yakihonne just dropped a game-changer: drafts. It's like a backstage pass to content magic. Got an idea while waiting for your latte? Snap it into drafts, and let the genius marinate.
But here's the twist: drafts aren't a solo gig. They're your collaboration playground, where you and your dream team fine-tune, tweak, and perfect together. 🎉✍️
And the cherry on top? No more tech tantrums. Your drafts are locked and loaded against power outages and browser bloopers. It's a digital safety net that lets you create without worries.
True, drafts aren't full wizards yet—you gotta nudge 'em onto the stage. But trust us, Yakihonne's working on that magical touch.
So give it up for drafts—the unsung heroes of your content journey. Hats off to Yakihonne for this slick update! 🎩🚀"

"Comment Deletion Safety Net: Think Before You Delete! 🤔🗑️
Alright, fellow opinion ninjas, let's talk about a slick new move Yakihonne just pulled off. You know how easy it is to swipe your comments away in the heat of the moment, right? Well, fear not, 'cause now, before you hit the delete button, a life-saving confirmation prompt swoops in like a digital superhero.
In this wild realm of instant sharing, where our thoughts can travel the world with a single click, it's easy to slip on a banana peel of accidental deletion. But hold onto your keyboards, 'cause Yakihonne's got your back. 🦸♀️ Before you wave goodbye to your wisdom, the platform taps you on the shoulder and asks, "Hey, are you sure you wanna do this?"
And guess what? It's a total game-changer. With this new sidekick feature, we're steering clear of deletion disasters and preserving our digital footprints one confirmation at a time. Nice work, Yakihonne team—this one's a bullseye! 🎯🙌"

"Unveiling 'Stats Previews': The Power to Peek Behind the Curtain! 👀📊
Hold onto your pens, wordsmiths, because Yakihonne just dropped a truth bomb—'Stats Previews'! It's like having X-ray vision for your articles and others'. Ever wondered who's giving your content a thumbs-up or a sly downvote? Now you don't just wonder, you know!
Imagine this: you're sipping your coffee, scrolling through your article, and bam! You spot who's showering your words with love, who's sending them a virtual high-five, and even who's shaking their head. It's like a backstage pass to reader reactions, and let's be real, it's kinda cool to see who's in the audience.
But here's the real magic. This feature isn't just about a sneak peek—it's about connecting the dots between your words and your readers' vibes. It's like getting a front-row seat to the 'how' and 'why' of your content's impact. And hey, it's not a one-way street. You get to dive into other creators' stats too, sharing in the highs, lows, and everything in between.
And me? I'm loving every second of it. The stats preview? It's like my secret writing superpower, making me want to craft even more epic articles and dive deeper into this content cosmos.
So here's to 'Stats Previews': the ultimate behind-the-scenes show that transforms our reading and writing into a grand adventure of discovery and connection. Cheers to Yakihonne for this thrilling upgrade! 🥂🚀""In a Nutshell: Yakihonne's Evolution Unveiled! 🌟🚀
Yakihonne's latest updates? They're like a symphony of user-centric genius, creating a smoother and more empowering experience for us content creators. Let's break it down:
📝 "Add My Article": A slick tool for sharing your gems with the world. It's like your personal megaphone for creativity.
📊 Interactive Stats: Peek behind the curtain and see who's loving (or not-so-loving) your work. Transparency, baby!
🗑️ Delete Comment Power: Swipe with confidence, 'cause now there's a confirmation shield. No more accidental vanishing acts.
🔍 Hint, Hint: Navigate like a boss with the new hint feature. It's like having a friendly guide on your content quest.
🎨 Drafts Sanctuary: Your ideas get a safe playground to evolve into masterpieces. No more lost brainwaves.
As Yakihonne continues its cosmic dance of evolution, these updates add more color to our creative canvas. It's a mix of power moves and thoughtful touches, creating a space that's dynamic, exciting, and brimming with potential. So, fellow creators, keep those keyboards clacking, 'cause Yakihonne's turning our ideas into digital magic! 🎩✨"

-
 @ 000688f2:44fbd1ae
2023-08-11 19:57:28
@ 000688f2:44fbd1ae
2023-08-11 19:57:28X7's Leveraged Decentralized Exchange is
- permissionless,
- trustless,
- censorship-resistant,
- decentralized architecture &,
- decentralized governance
In recent years, exchanges across the globe have been shutting their doors to customers simply because a sovereign state has decreed it. X7 is designed to overcome those shortcomings and give power back to the people. A quick definition of terms is in order to ensure the message is consistent and the community is able to understand what each term means.
Permissionless
No individual, organization, or sovereign state actor shall infringe on the functionality and usability of X7’s system. We believe the world is better with free speech and freedom and our system is designed to prevent asking permission to interact with the system.
Trustless
Traditional loan systems have a problem with trust. Principle among them, is the trust that your loan will be repaid. X7’s DEX is able to allow trustless loans between the Lending Pool and the Initial Liquidity Loan Requestor, leading to higher market capitalization and access to capital.
Censorship Resistant
Multinational corporations exert massive control over the finances of everyday people and recent stories of Visa, Mastercard, and PayPal blacklisting ordinary citizens from transacting on their networks highlight the need for a system to be resilient and resistant to those forms of censorship.
Decentralized Architecture
Engineering a system to not have single points of failure is a difficult task. X7 will run all parts of the system in multiple locations and open-source the final product so anyone can run the source code anywhere.
Decentralized Governance
Designing management processes to be handled by a group is also a difficult task, but X7’s governance strategy is optimized to aggregate large groups’ opinions into smaller decisions to vote on. In time, X7 will delegate that 51% of profits generated to community marketing multi sig wallet and community development multi sig and hand over all system controls to the DAO.
X7 is currently nearing the end of a very successful beta and is readying for launch next month. Learn more about: * X7 Finance * X7 App * X7 Community
-
 @ 75656740:dbc8f92a
2023-07-19 21:56:09
@ 75656740:dbc8f92a
2023-07-19 21:56:09All social media companies quickly run into the impossible problem of content moderation. I have often seen commentary suggesting that Twitter, FaceBook, etc need to make some particular adjustment to their content moderation policy. Perhaps they should have clearer rules, be more transparent about moderation actions taken, err on the side of permissiveness, have community moderation, time outs vs bans etc. My thesis, however, is that all such endeavors are doomed to failure. The problem is that maintaining signal to noise over a single channel cannot scale.
If a platform wants to remain relevant to the majority of people, it needs to maintain signal. Filtering is a fundamental feature of communication. Even in-person conversations between individuals break down without self-filtering to stay on topic and maintain constructive relations. Long range delivery systems have a second order problem that makes the issue even worse.
All delivery-by-default communication systems succumb to spam. This is without exception. Mail, phone, fax, email, text, forums, etc. have all fallen to spam and now require herculean efforts to maintain signal through extensive filtering. The main offenders are non-human entities that have a low barrier to entry into the network. Once in, delivery-by-default allows and motivates swamping out competing signals for user attention.
In combating this problem most platform operators do seem to act in good-faith while implementing filters. They are even fairly successful. But they end up with the same problem as economic central planners and Maxwell's Daemon; to do the job perfectly they require more information than the system contains. This means that the system is guaranteed to fail some users. As a successful platform scales the filtering needs will outrun the active users by some f(n) = n^k where k is greater than 1. This follows from the network effect of greater information being contained in the edges of the graph than in its nodes.
For networks like Facebook and Twitter the impossible threshold is many orders of magnitude past. What can be maintained on a small mailing list with the occasional admonition, now requires tens of thousands of swamped moderators that still can't begin to keep up. Those moderators have to make value judgements for content generated by people they don't know or understand. Even the best meaning moderators will make bias mistakes. Thus the proportion of unhappy users will also scale non-linearly with size.
The impossible problem takes a second step in the presence of civil authority. The problem is that a filter being necessary means that a filter exists. A civil authority and other motivated actors will not be able to leave a filter be, without at least attempting to tip the scales. Again they are generally well-meaning. But what they consider noise, may not actually be noise.
Well-meaning is probably a stretch given that levers of power tend to attract the attention of people who like that sort of thing, but I like to assume the best. I tend to think that there were some early signs of Jack stressing out under the load of bearing this problem. He didn't want it but there just wasn't anyway out of it. You must maintain signal or die!
But there is light at the end of the tunnel. The problem only exists with delivery-by-default when reach is universal (a problem for another post) with distributed systems there is still a filter but it is no longer any one entity's problem. Once the social graph is complete, deny-by-default can work wonders since each node can decide what to allow.
I don't know what the final filtering mechanism will look like, but Nostr is a lovely chance to experiment.
-
 @ 69f16d34:4568b5f8
2023-08-11 19:24:03
@ 69f16d34:4568b5f8
2023-08-11 19:24:03Did you know this is valid HTML?
```
My to-do list My to-do list
Here are the things I need to do:
- First item
- Second item
- Third item
That's it! ``` You can omit elements such as **html**, **head**, or **body**. Additionally, depending on the element, you can even omit the closing tag, like with **p** and **li**.
-
 @ cca7ef54:e7323176
2023-08-05 03:56:48
@ cca7ef54:e7323176
2023-08-05 03:56:48เรามาทำความเข้าใจเกี่ยวกับระบบ Relay ใน Nostr กันครับ นี่เป็นส่วนสำคัญที่ทำให้ Nostr ทำงานได้ และมันก็ทำหน้าที่คล้ายๆ กับเป็นเซิร์ฟเวอร์หลังบ้านของ Nostr นั่นเอง
เริ่มต้นทำความเข้าใจอย่างง่าย
เราจะเริ่มต้นด้วยการจินตนาการว่า Nostr เป็นเมืองที่มีผู้คนจำนวนมากที่ต้องการจะสื่อสารกัน แต่ทุกคนต่างก็อยู่ห่างกันไกลเหลือเกิน ทำให้พวกเขาไม่สามารถสื่อสารกันได้โดยตรง ดังนั้น.. เราก็เลยต้องการสิ่งที่เรียกว่า "Relay" หรือ "สถานีเชื่อมต่อ" ที่จะช่วยส่งข้อมูลจากคนหนึ่งไปยังคนอื่นๆ
ในบริบทของ Nostr นั้น.. Relay คือเซิร์ฟเวอร์ที่รับข้อมูล (หรือ "notes" ที่เราโพสต์) จากไคลเอนต์หนึ่งและส่งต่อไปยังไคลเอ็นต์อื่นๆ ที่ต้องการข้อมูลนั้น ดังนั้น.. คุณสามารถจินตนาการเปรียบเทียบได้ว่า Relay เป็นเหมือนที่ทำการไปรษณีย์ที่คอยรับจดหมายจากคนหนึ่งแล้วก็ทำหน้าที่ในการส่งต่อไปยังคนอื่นๆ
https://i.imgur.com/qKEXUWM.png
แต่ Relay ใน Nostr มีความพิเศษที่มากกว่าแค่ที่ทำการไปรษณีย์ทั่วไป นั่นคือ.. มันไม่มีการควบคุมหรือการเซ็นเซอร์ ทุกคนในระบบสามารถสร้างและรัน Relay ของตนเองได้ ทำให้เครือข่ายของ Nostr มีความเป็นธรรมและเป็นกลาง ไม่มีใครสามารถควบคุมหรือจำกัดการสื่อสารของใครได้
แล้วการทำงานของ Relay ใน Nostr เป็นอย่างไร?
มาลองจินตนาการว่าคุณมีข้อความที่ต้องการส่งไปยังเพื่อนของคุณ คุณจะสร้าง "note" และส่งไปยัง Relay ที่คุณเชื่อถือซึ่งคุณได้ทำการเพิ่มการเชื่อมต่อเอาไว้กับบัญชีของคุณ Relay จะรับ "note" นั้นและส่งต่อไปยัง Relay อื่นๆ ในเครือข่าย จนกระทั่ง "note" นั้นถึงมือเพื่อนของคุณในที่สุด
จะเห็นได้ว่า.. ความสำคัญของ Relay คือ มันช่วยทำให้การสื่อสารใน Nostr สามารถเกิดขึ้นได้โดยไม่จำเป็นต้องมีเซิฟเวอร์ตัวกลาง ไม่ว่าคุณจะอยู่ที่ไหนบนโลก คุณก็สามารถสื่อสารกับคนอื่นๆ ได้ผ่าน Nostr ด้วยความช่วยเหลือจาก Relay นั่นเอง
Relay คืออะไร?
Relay ใน Nostr ทำหน้าที่รับข้อความจากไคลเอนต์ Nostr และอาจจะเก็บข้อความเหล่านั้นไว้ หรือส่งต่อข้อความเหล่านั้นไปยังไคลเอนต์อื่นๆ ที่เชื่อมต่อกันอยู่ทั่วโลก การพัฒนาในโลกของ Relay กำลังเปลี่ยนแปลงอย่างรวดเร็ว จึงคาดว่าจะมีการเปลี่ยนแปลงเกิดขึ้นตามมาอย่างมากในอนาคต เราควรทราบเอาไว้ว่า Nostr เป็นระบบที่ไม่มีศูนย์กลาง และการส่งต่อข้อมูลนั้นขึ้นอยู่กับ Relay ในการเก็บและดึงข้อมูลจากกันและกัน ถ้าคุณสังเกตพบว่าไคลเอนต์ Nostr ของคุณทำงานช้า สาเหตุส่วนใหญ่เป็นเพราะ Relay ที่คุณใช้หรือเชื่อมต่ออยู่นั่นเอง ซึ่งอาจจะดีกว่าหากคุณเพิ่ม Relay ให้มากขึ้น (หรือลบบางอันที่ไม่มีประสิทธิภาพ) ในไคลเอนต์ของคุณ
Relay ที่ใช้ได้ฟรี และ Relay ที่เก็บค่าบริการ
ในปัจจุบัน มี Relay ที่ใช้ได้ฟรีๆ อยู่มากมาย แต่เนื่องจากค่าใช้จ่ายในการรัน Relay (สำหรับการประมวลผล การจัดเก็บ และบริหารจัดการแบนด์วิดธ์) หลายคนจึงคาดว่า Relay แบบเก็บค่าบริการจะกลายเป็นมาตรฐานในอนาคต ข้อดีหนึ่งของการใช้ Relay แบบเสียตังค์ในตอนนี้ คือ สัญญาณการเชื่อมต่อที่สูงและไหลลื่นของไคลเอนต์และ note ซึ่งใน Relay แบบนี้ "proof of work" สำหรับการเข้าถึง Relay ที่เก็บค่าบริการ คือสิ่งที่ช่วยให้บัญชีสแปมไม่สามารถรบกวนเครือข่ายได้
https://i.imgur.com/UE2tiHi.png
Relay ที่เก็บค่าบริการที่ได้รับความนิยม
คุณสามารถหารายการอัปเดตของ Relay ที่เก็บค่าบริการพร้อมรายละเอียดราคาและผู้ดำเนินการได้ที่ Relay Exchange: https://nostr.how/en/relays
เราจะหารายการของ Relay ทั้งหมดได้ที่ไหน?
แหล่งที่ดีที่สุดสำหรับการเรียกดูและประเมินความเร็วของ Public relay ที่รู้จักกันดีคือ Nostr.watch site: https://nostr.watch/
จะเกิดอะไรขึ้นถ้า Relay ที่เราใช้ทั้งหมดหยุดทำงาน?
ถ้า Relay ทั้งหมดที่คุณใช้เกิดตออฟไลน์ไป โพสต์ของคุณทั้งหมดจะไม่สามารถดึงข้อมูลได้ นี่เป็นเหตุผลหนึ่งที่ Nostr อนุญาตให้ไคลเอนต์สามารถเชื่อมต่อเข้ากับ Relay หลายๆ ตัวได้ – สิ่งนี้ช่วยให้เรามั่นใจในการสำรองข้อมูล นอกจากนี้ ถ้าคุณค่อนข้างกังวลในความเป็นส่วนตัว ไม่ต้องการโดนเซ็นเซอร์ คุณก็สามารถศึกาษาค้นคว้าและควรรัน Relay ส่วนตัวของคุณเอง (Private relay)
เราควรรัน Relay ของตัวเองหรือไม่?
สำหรับผู้คนส่วนใหญ่ คงต้องตอบว่าไม่ เพราะมันไม่คุ้มกับความยุ่งยากที่คุณต้องเจอ แต่หากคุณพอจะมีทักษะและความเข้าใจทางเทคนิค และต้องการให้การพูดคุยของคุณไม่มีใครสามารถเซ็นเซอร์ได้เลย หรือต้องการรัน Relay ส่วนตัวสำหรับกลุ่มเล็กๆ ของตัวเอง คุณสามารถทำได้และควรรัน Relay ของคุณด้วยตัวเอง
อย่างที่ Jakk Gooday พึ่งโพสต์ไปวันก่อน ผู้รัน Public relay ที่ให้เราเชื่อมต่อได้ฟรีในตอนนี้ สามารถล้างข้อมูลของผู้ใช้ Nostr ออกจากฮาร์ดดิสของตัวเองได้หากมันเต็มขึ้นมา หรือหมดแพสชั่นเลิกทำเมื่อไหร่ก็ได้ เบื้องต้นคุณอาจต้องคอยบริหารจัดการ นำเข้า-น้ำออก Public relay ในไคลเอนต์และบัญชีของคุณด้วยตัวเองอย่างสม่ำเสมอ หมั่นตรวจสอบประสิทธิภาพของ Relay แต่ละเจ้าเป็นระยะๆ ดังนั้นการศึกษาหาความรู้เกี่ยวกับการรัน Private relay อาจเป็นเรื่องที่จำเป็นในอนาคต เพราะในความเป็นจริง คุณไม่จำเป็นต้องเปิดการทำงานของมันตลอดเวลา เพียงแต่เปิดขึ้นมาเพื่อทำการสำรองข้อมูลของตัวเองเป็นระยะๆ ก็เพียงพอแล้ว
การรัน Relay ด้วยตัวเองจะทำให้คุณมั่นใจได้ว่าคุณจะมีสำเนาของโพสต์และการโต้ตอบทั้งหมดใน Nostr ของคุณตลอดเวลา ในขณะนี้เรากำลังทำคู่มือสำหรับสิ่งนี้ นี่คือคู่มือจาก Andre Neves เกี่ยวกับวิธีการตั้งค่า Relay Nostr https://andreneves.xyz/p/set-up-a-nostr-relay-server-in-under
https://i.imgur.com/QmrjkYb.png เรียบเรียงจากต้นฉบับ: https://nostr.how/en/relays
-
 @ b9e76546:612023dc
2023-05-23 18:13:45
@ b9e76546:612023dc
2023-05-23 18:13:45The real power of AI will be in its integration of other tools to use in specific situation and recognizing what those tools are. There will be extremely specific & curated AI models (or just basic software circuits) on certain topics, tasks, or concepts. And this will also be a crucial way in which we keep AI safe, and give it understanding of its own actions. In other words, how we prevent it from going insane. I've recently experienced a tiny microcosm of what that might look like...
— ie. a general language model that knows to call on the conceptual math language model, that then makes sense of the question and knows to input it into the calculator app for explicit calculations when solving complex or tricky word problems. And then to apply this in the realm of safety and morals, a specific model that an AI calls on for understanding the consequences and principles of any actions it takes in the real world.
I believe there needs to be an AI "Constitution" (a particular term I heard used to describe it) where there is a specific set of ideas and actions it is enabled to perform, and a particular set of "moral weights" it must assess before taking action. Anyone who's read Asimov will recognize this as "The Three Laws" and that's basically what it would be. This is critical because an AI running an actual humanoid machine like Boston Dynamics could go ape shit literally because it is emulating trolling someone by doing the opposite of what they asked -- I just had a LLM troll me yesterday & go a bit haywire when i asked it to be concise, and every answer afterward was then the wordiest and longest bunch of nonsense imaginable... it was funny, but also slightly sobering to think how these things could go wrong when controlling something in the real world. Now imagine a robot that thinks Kick Ass is a funny movie and starts emulating its behavior thinking it's being funny because it has no model to assess the importance of the humans whose skulls it's smashing and thinks the more blood it can splatter everywhere makes it a more comical experience for those in the room. That's essentially the "real world robot" version of asking a LLM to be concise and instead getting an avalanche of BS. Ask a robot to be funny and maybe it crushes your skull.
Because of that, I think there will be certain "anchors" or particular "circuits" for these LLMs to be constrained by for certain things. Essentially action specific built governors that add meaning to the actions and things they are doing. A very simple version mentioned above would be a calculator. If you ask an LLM right now to do basic math, it screws up all the time. It has no idea how to generate a true answer. It just predicts what an answer might sound like. So even extremely simple and common sense requests turn up idiotic answers sometimes. But if it can recognize that you are asking a math problem, find the relevant mathematical elements, and then call on the hardcoded & built-in calculator circuit, then the LLM isn't doing the calculation, it's simply the interface between the calculation tool and the human interaction.
What I think will be critical as we integrate these into real world machines over time, and as their capabilities become more generalized and layered, will be to build in a sort of moral constitution that behaves like a concrete engine (a calculator), that has the model recognize when something might be a questionable behavior or cause an undesirable outcome, and then call on the "constitution" to make the decision to act or not. In that way, it may actually prevent itself from doing something stupid or terrible that even a human hadn't realized the full consequences of. — ie. it won't help a child get to the roof of his building so he can fly off the side with his cardboard wings.
It will be very interesting to watch these come about because the failure more of AI will be a critically important thing to consider, and unfortunately from an engineering and cultural standpoint, "failure modes" are something that have been underrepresented and increasingly ignored. A simple example is a modern washing machine; when something entirely arbitrary or some silly little feature breaks, the whole thing is useless and you have to bring a technician out to fix it, when a sensible failure mode would be that it simply routes around what arbitrary feature failed, and continues working normally. This, unfortunately, has become the norm for tons of "modern" devices and appliances. they are simultaneously increasingly "advance" and "stupid" at the same time. It's largely a product of the high time preference mindset, and we need MUCH more low time preference consideration as we unleash AI onto the world. It will matter exponentially more when we start making machines that can operate autonomously, can maintain themselves, and learn through their own interactions and environment... and we aren't very far away.
Learn as fast as you can, understand the tools, and stay safe.
grownostr #AI_Unchained
(my very first post on BlogStack.io)
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)


