-
 @ f8e6c643:03328ca9
2023-08-02 15:45:25
@ f8e6c643:03328ca9
2023-08-02 15:45:25Here’s the neat part, you don’t... \n...or rather, you can’t find rare satoshis. Rare satoshis don’t exist because individual satoshis don’t actually exist within the bitcoin network, only UTXOs. \n\n## But my wallet says I have satoshis.\nAnd the container of your food says it has calories. The bathroom scale says your body has lbs/kg. The tape measure says your floors have inches/cm. These are units of measure of a property of something, but they are not distinct individual units of the thing being measured. Calories measure energy. Scales measure mass. Rulers measure distance. These are properties of a thing, but not the thing itself. \n\nLikewise, satoshis (aka, sats) are a unit of measure for bitcoin UTXOs, which are the "things" that actually exist within the bitcoin network. A UTXO, or "unspent transaction output," can be very small, only a few hundred sats, or it can be very large, hundreds of millions or even billions of sats, but there are only UTXOs measured in sats and spendable by their corresponding private keys. There are no satoshis sitting in storage in bitcoin wallets and nodes. \n\n## If that's true, then why is Bitcoin Magazine selling "rare satoshis"?\nThey are salesmen in search of profit, and not all salesmen are honest. The product they are selling misrepresents the truth. Put simply, Bitcoin Magazine is lying about what they are selling. \n\nWhat they are actually selling is a UTXO measured in some amount of sats that can be cryptographically linked to another UTXO from the past that no longer exists. Why doesn't it exist? Because a UTXO is, by definition, "unspent." Once you spend one UTXO, new UTXOs are created and mined into a new block.\n\n## So I can't buy one of Hal Finney's satoshis?\nUnfortunately, no, you cannot. At best you could pay someone like Bitcoin Magazine to spend one of their UTXOs to a new UTXO at an address you control. It is up to you to decide if the cryptographic link to previous entries in the ledger has any added value or meaning beyond the sats-denominated value of the UTXO.\n\nIt would be a little bit like if I had a dollar bill, and I went to the bank and deposited it into your account, and then the bank destroyed that physical bill and replaced it with a new one when you came in to withdraw it. While you would now possess access to the $1 of value, you would not have the dollar bill that I deposited. In fact, it no longer exists, even though there is proof on the bank's ledger of the transfer of value from me to you.\n\n## Ok, so what? I can do what i want with my money.\nYes, you can. That is the freedom afforded to you by bitcoin. You are free to trade your sats for a lesser amount of sats. It's just my opinion that you ought to at least understand that that's all you're doing. \n\n🌽 🤙
-
 @ 20986fb8:cdac21b3
2023-07-29 06:45:23
@ 20986fb8:cdac21b3
2023-07-29 06:45:23YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.\n\nAs an incentive, participants can earn up to 100,000 SATs.\n\nRound 2 will be from 27th to 30th July\n\n### How to participate:\n1. Pick one or multiple Updates below, test it (them)\n2. Write your feedback and opinion (pros and cons are all welcomed)\n3. Post your article on Nostr via YakiHonne.com\n4. Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne\n5. Share the link to our group: http://t.me/YakiHonne_Daily_Featured\n5. Be Zapped!\n\n### Requirements:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion\n5. The top 10 posts will be zapped during each round.\n6. The evaluation will based on the article's depth, completeness, and constructiveness. \n7. Contact us for additional zaps if bugs are found.\n\n\n\n\n### Updates to be tested in Round 2:\n1. Comments: re-implemented and comments can be deleted\n\n2. NIP-25 supporting: users now can upvote and downvote\n\n3. Zap stats: Zaps sent and Zaps received can be seen from users profiles\n\n4. “login with an extension” button: now it is grayed out rather than invisible\n\n5. Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme\n\n6. Tags: click on the tags in the article to view the content under the tag\n\n7. Share: sharing posts with one click\n\n8. NIP-05: verify your profile\n\n\n\n### If you missed Round 1, the updates below could be tested as additions:\n\n1. Comment function: more user-friendly\n\n2. Stats area: clearly displays the interactive status of each article\n\n3. Following function: generated-key users can also be followed\n\n4. Curation function: easily add or remove articles from an existing curation\n\n5. Tags: search and browse articles with the tags\n\n6. Home feed scrolling pagination: optimized data fetching and faster loading time\n\n7. Article editing preview: preview the final version of the article while writing in MarkDown\n\nDon't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n
-
 @ 20986fb8:cdac21b3
2023-07-29 06:44:43
@ 20986fb8:cdac21b3
2023-07-29 06:44:43A long-term Nostr Creation Grant, with a 17,500,000 SATs funding pool\n\n\nRound 3 starts on 22 July till 5 Aug!\n\nCreating for You and Your Fans through Nostr and ZAP.\n\nNostr is a simple, open and censorship-resistant protocol, the number of users has been growing, and more and more users use zap to tip content. Nostr's growth over the past six months is amazing, which is a great encouragement for all nostrians. This is also a great encouragement for content creators. Earn SATs by posting your creations on nostr, allowing your readers to encourage better content creation while tipping your creations.\n\n\n
 \n
\n \n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n
\n\n\n\n\nZaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.\n\n\n\n\n \n\n\n\n\n
\n\n\n\n\n \n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n
\n\n\n\n\nOn the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems. \n\n\n\n\nTo this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!\n\n\n\n\n### What You Will Get From Your First 10 Posts in each round:\n1. 500 SATs, if you post on Relays through other clients\n2. 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne\n3. 2000 SATs, for posting your own past articles on Relays through YakiHonne.com\n4. 3000 SATs, for posting your new original on Relays through YakiHonne.com\n\n\n\n\n### Zap Rules:\n1. No malicious speech such as discrimination, attack, incitement, etc.\n2. No Spam/Scam, not fully AI-generated article\n3. No directly copy & paste from other posts on Relays\n4. Spread positive content like your knowledge/experience/insight/ideas, etc.\n\n\n\n\n### How to Get Zap:\n1. Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured\n2. Share your post in the group\n3. Make sure your LN address is in your profile\n4. Based on the rules above, we will ZAP your post directly within 2 days\n\n\n\n\nJoin our group for more queries: https://t.me/YakiHonne_Daily_Featured\n\n\n---\n### About YakiHonne: \n\nYakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.\nTry YakiHonne.com Now!\n\n#### Follow us\n\n- Telegram: http://t.me/YakiHonne_Daily_Featured\n- Twitter: @YakiHonne\n- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q\n\n\n\n\n\n\n -
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:03
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:03📝 Summary: Alice and Luke Dashjr discuss the growth potential of blockchain and the limitations of storage per block. Alice believes that the current cost of hardware makes it feasible to handle the growth, while Luke argues that storage is not the main issue and efforts are being made to optimize space requirements for individual nodes.
👥 Authors: • GamedevAlice ( nostr:npub18zra06q690wae9ty6sxxwf3jdcxuan2n4dq0ldynjddzz894jqesvhlw24 ) • Luke Dashjr ( nostr:npub1tfk373zg9dnmtvxnpnq7s2dkdgj37rwfj3yrwld7830qltmv8qps8rfq0n )
📅 Messages Date: 2023-08-02
✉️ Message Count: 2
📚 Total Characters in Messages: 51185
Messages Summaries
✉️ Message by GamedevAlice on 02/08/2023: The growth potential of the blockchain is limited by the amount of storage that can be added per block. However, the current cost of hardware makes it feasible to handle the growth. Efforts are also being made to optimize storage requirements.
✉️ Message by Luke Dashjr on 02/08/2023: Storage is not the issue with block sizes, and there are efforts to optimize how much space is needed by individual nodes.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 57fe4c4a:c3a0271f
2023-08-02 22:15:36
@ 57fe4c4a:c3a0271f
2023-08-02 22:15:36📝 Summary: The annual specification meeting in NYC discussed package relay, commitment transactions, and zero fee commitments. The Wolf team was thanked for organizing the LN Summit, with technical observations on package relay and minimum relay fees. A proposal was made to use a tapscript branch for unilateral closes and MuSig2 for mutual closes. Unconditional fees were suggested as a simple monetary solution. Carla thanked everyone for participating and acknowledged the hosts and note provider. Clara suggested making attackers pay for resources used to turn them into a profit center, but implementing fees based on HTLC holding time poses challenges.
👥 Authors: • Clara Shikhelman ( nostr:npub1uyhgpz5nsfnvdlcqm3erjsdjasd9pdeaejeetwtkvumm6mp3ujlqxt9vwk ) • Carla Kirk-Cohen ( nostr:npub17xugd458km0nm8edu8u2efuqmxzft3tmu92j3tyc0fa4gxdk9mkqmanw36 ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l ) • Anthony Towns ( nostr:npub17rld56k4365lfphyd8u8kwuejey5xcazdxptserx03wc4jc9g24stx9l2h ) • Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date Range: 2023-07-19 to 2023-07-31
✉️ Message Count: 6
📚 Total Characters in Messages: 173328
Messages Summaries
✉️ Message by Carla Kirk-Cohen on 19/07/2023: The text is a summary of the annual specification meeting held in NYC. It includes discussions on package relay, commitment transactions, and zero fee commitments.
✉️ Message by Antoine Riard on 20/07/2023: The sender thanks the Wolf team for organizing the LN Summit and hopes they become the YC of Bitcoin. Technical observations on package relay and minimum relay fees are discussed.
✉️ Message by ZmnSCPxj on 24/07/2023: A proposal was made to use a tapscript branch for unilateral closes and only sign with MuSig2 on mutual closes. Nonces can be stored in volatile RAM and mutual closes can be restarted on reconnection. Unconditional fees are suggested as a simple monetary solution for pricing.
✉️ Message by Antoine Riard on 26/07/2023: Proposal to use a tapscript branch instead of MuSig2 signing for unilateral closes in the Lightning Network. Discusses dynamic fees and Bitcoin as a universal clock.
✉️ Message by Anthony Towns on 26/07/2023: Carla thanks everyone for their participation in the meeting and acknowledges Wolf for hosting in NYC and Michael Levin for providing notes.
✉️ Message by Clara Shikhelman on 31/07/2023: A different approach to dealing with attacks on the network is to scale up capacity and make attackers pay for the resources they use, turning them into a profit center. This could be done through fees for message spam and holding funds. However, there are challenges in implementing fees based on the time an HTLC is held. The suggested fees are low, so hourly precision should be sufficient.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 57fe4c4a:c3a0271f
2023-08-02 16:02:44
@ 57fe4c4a:c3a0271f
2023-08-02 16:02:44👥 Authors: Einherjar ( nostr:npub18qg05c75rheuges4vdgtfqmcx543k3nmq63d9w4hzt7m2g6rqa3suy8sxf )
📅 Messages Date: 2023-08-02
✉️ Message Count: 1
📚 Total Characters in Messages: 1866
Messages Summaries
✉️ Message by Einherjar on 02/08/2023: Proposal to price space in the UTXO set raises concerns about UTXO management, doxing, and privacy issues. Pricing UTXOs may eliminate spam but offend users.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ d36a437b:4480d6a5
2023-08-04 10:10:55
@ d36a437b:4480d6a5
2023-08-04 10:10:55导论 在康德哲学中我们的行动不仅仅是受到感官经验和外部因素的驱动,还涉及到我们内在的理性和意志。自由意志使我们能够根据道德原则和理性的指导来选择和行动,而不是被感官欲望或外在条件所束缚。
自由意志使我们能够对我们的行为负责,并承担后果。康德认为,通过自由意志的行动,我们成为道德的主体,可以根据普遍适用的道德律法来判断和行动,而不仅仅是受到个人欲望或外界因素的驱动。
然而,康德也指出,自由意志并不意味着完全自由地做出任何选择。他认为自由意志有其限制和约束,需要在道德律法的指引下行动。 自由意志的真正价值在于我们能够根据道德原则做出自主的决策和行动,而不是纯粹地追求个人欲望或外在利益。
康德的自由意志观念与他对伦理学和道德认识的理解密切相关。他认为,自由意志是个体道德责任的基础,我们的行动应该根据普遍适用的道德原则来决策,并为我们的行为负责。
Part i 权力与自由意志
综上所述,完全无底线且不理性的自由早在康德就被批判了并且被认为是错误的理念
言论自由可以被视为康德自由意志的一个重要应用领域。言论自由是指个体表达思想、意见和信仰的权利,不受政府或其他机构的干预或压制。这个权利是公民社会和民主制度的基石,也是知识交流和进步的关键。
康德的自由意志观点强调个体的独立性和自主性,以及对道德准则的遵循。言论自由可以被视为个体运用自由意志的一种方式,通过言辞表达自己的思想和见解。言论自由使个体能够参与公共讨论和辩论,促进知识的共享和社会的进步。 自由意志应当在道德行为中的限制。自由不是放任任意行为的纵容,而是在理性和普遍准则的指引下进行选择。
言论自由使个体能够独立思考、形成独立的意见,并表达这些意见而不受外部干预或压制。言论自由为个体提供了一个平台,在其中展示他们的自主性和独立思考的能力,也是人权的基本体现,也是人之所以为人而不是被硬件(肉体)与软件(思想)所限制的“机器”
Part ii 马克思主义中的言论自由
马老师作为后来者对前者的补充与批判必然更加的全面
根据马克思的历史辩证法,上一个时代的真理必然在下一个时代所呈现,马克思对于自由意志,言论自由的看法与康德完全不同
马克思主义的角度来看,个体的自由意志受到社会、经济和阶级关系的制约。个体的行为和意识是在特定历史时期和社会环境下形成的。然而,在特定条件下,个体仍然具有一定的选择权和自主性,可以通过集体行动来争取自身权益和解放。
从阶级利益意识形态去分析,马克思主义认为在资本主义社会中,社会中存在阶级斗争,并且不同阶级拥有不同的阶级利益,统治阶级(资产阶级)掌握了经济和政治权力,并通过控制媒体、教育等手段来塑造和宣传符合其利益的意识形态。因此,言论自由在资本主义社会中常常受到限制,被用于服务统治阶级的利益。
从思想压迫与言论管控角度来说,资本主义社会存在着对劳动者的压迫和剥削。这种压迫不仅体现在经济方面,还包括思想和意识形态上的控制。统治阶级通过掌控话语权和言论管制,限制了被压迫阶级对自己状况的认识和声音的表达。言论自由的受限导致被压迫阶级难以真实地表达自己的需求和反抗。
从解放与革命来说,言论自由是解放与革命的一大工具,是被压迫阶级争取解放的重要工具之一;通过言论自由,被压迫阶级能够表达自己的不满、观点和组织起来参与革命运动。
马克思主义认为,建立共产主义社会后,将会有一个无产阶级专政的阶段。在这个阶段,对统治阶级的反抗将受到限制,以确保无产阶级的权力稳定。然而,马克思认为,在这种情况下,言论自由仍然可以存在,并且将为广大群众提供更多发声和参与决策的机会,所以自由并非与资本主义统治相绑定
结论
不论是以阶级,经济,社会还是哲学,我们都得出了一个结论,就是无产者,人民,社会,世界需要言论自由,并且是理性,以道德为准则的言论自由,这是一个理想的社会样态
自由不是以私有财产为权力代表的权力关系,也不是以私有财产为原则组建的社会,家庭。而是以伦理道德为底线自由原则与人权
以资产阶级法权为基础支撑的国家不过是资产阶级商议内部事务的委员会罢,与工人没有任何干系
致谢
作者:Bill Charles 感谢DAOrayaki对本文章的创作支持
-
 @ 82b30d30:40c6c003
2023-07-22 08:31:22
@ 82b30d30:40c6c003
2023-07-22 08:31:22[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
-
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41"Who do you say that I am?"
In Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.
- Who they tell us they are.
- Who others say about them.
- What we observe for ourselves.
Putting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.
With this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way?
The default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.
This falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.
I don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like... * Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover. * Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading. * Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed. * Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon. * Have a full pet-names override.
I think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.
A note on anonymity
Real world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety.
If you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ 2448a66f:838296c9
2023-08-04 09:02:34
@ 2448a66f:838296c9
2023-08-04 09:02:34หากมองที่โครงสร้างทางชีวภาพของมนุษย์ มนุษย์สามารถย่อยน้ำตาลแล็กโทสในนมได้ถึงแค่อายุ 2 ขวบ หลังจากนั้นความสามารถในการย่อยน้ำตาลนี้จะลดลง ซึ่งอนุมานได้ว่าในทางธรรมชาติแล้ว มนุษย์ไม่ควรดื่มนมอีกแล้ว หลังจากอายุ 2 ขวบ (แม่จะหยุดผลิตน้ำนมโดยธรรมชาติหลักจากคลอดบุตรแล้ว 1-2 ปีเช่นกัน)
ในปัจจุบัน มีคน 2 กลุ่ม 1. กลุ่มที่สามารถดื่มนมได้ปกติ พบมากในกลุ่มผู้คนแถบตอนเหนือและตอนกลางของทวีปยุโรป
- กลุ่มที่มีอาการผิดปกติหลังจากดื่มนม เกิดจากร่างกายไม่สามารถผลิตเอนไซม์ แล็กเทสได้อย่างเพียงพอ ในการย่อยแล็กโทสในนม ซึ่งกลุ่มนี้มักจะมีอาการ ท้องอืด ท้องเสีย ปวดท้อง พบมากในกลุ่มผู้คนในทวีปแอฟริกา เอเชีย และอเมริกาใต้
https://media.primal.net/uploads/1/e9/04/1e90454e3fce2a0558c626a722a8f298e7753dbcfb907e6e56e724a654e8965f.jpg
แล้วมนุษย์เริ่มกินนมจากสัตว์ตอนไหน ดื่มทำไม? ข้อมูลทางประวัติศาสตร์ที่ค้นพบในปัจจุบัน ยังบอกไม่ได้ว่าจุดเริ่มต้นของการดื่มนมจากสัตว์อื่นของมนุษย์ มันเริ่มขึ้นตั้งแต่ยุคสมัยไหน ไม่มีหลักฐานที่บ่งชี้แน่ชัด เพียงแต่เราคาดการณ์ได้จากหลักฐานที่ค้นพบว่า ++มันน่าจะเริ่มขึ้นเมื่อหลายพันปีก่อน++ จากการค้นพบไขมันนมในภาชนะโบราณ หรือ การค้นพบกลุ่มกระดูกฝูงสัตว์ให้นมเพศเมีย
แต่มันก็บอกไม่ได้ว่า ทำไมมนุษย์ถึงเริ่มดื่มนมจากสัตว์ ทั้งๆที่ย่อยมันไม่ได้ อะไรเป็นจุดเริ่มต้นของเรื่องนี้ มีเหตุผลอย่างอื่นนอกจากเพื่อการเอาตัวรอดอีกหรือไม่?
ซึ่งในปัจจุบันก็ยังคงมีการถกเถียงกันว่า มนุษย์ควรดื่มนมจากสัตว์ไหม? อยู่ตลอด และแน่นอนว่าทั้ง 2 แนวคิด ต่างมีจุดยืนที่เข้มข้นเป็นของตัวเอง
ฝั่งที่มีความเห็นว่า ++"มนุษย์ดื่มนมจากสัตว์ได้"++ เพราะการค้นพบการดื่มนม มันมาจากการวิวัฒนาการเอาตัวรอดของมนุษย์ และปัจจุบันมนุษย์บางกลุ่ม ก็ไม่ได้มีปัญหากับการย่อยแล็กโทสแล้ว (เกิดจากการวิวัฒนาการของยีนส์)
ในขณะที่อีกฝั่งก็มีความเห็นว่า ++"มนุษย์ไม่ควรดื่มนมจากสัตว์"++ มนุษย์ควรหยุดกินนมตั้งแต่หย่านมแม่แล้ว เพราะร่างกายเรามันหยุดย่อยแล็กโทสไปแล้วตามธรรมชาติ
ส่วนความคิดเห็นของเราในฐานะคนที่มีภาวะย่อยแล็กโทสบกพร่อง การดื่มนมจากสัตว์ควรเป็นแค่ทางเลือก ไม่ควรเป็นคำแนะนำสุขภาพ (คำแนะนำแบบควรดื่มนมอย่างน้อย 1-2 แก้วต่อวัน) เพราะสำหรับบางคน การดื่มนมตามคำแนะนำสุขภาพ ส่งผลเสียมากกว่าผลดี
อีกทั้งสารอาหารที่มีในนมจากสัตว์ สามารถหาทดแทนได้จากแหล่งอื่น เช่น แคลเซียม สามารถหาได้ในปลาตัวเล็ก ผักใบเขียว วิตามิน D มีให้คุณฟรีๆในแสงแดด หรือถ้าหากอยากให้กระดูกแข็งแรง การเคลื่อนไหวร่างกาย การออกกำลังกายช่วยเพิ่มมวลกระดูก ลดภาวะกระดูกพรุนได้
https://media.primal.net/uploads/d/13/a9/d13a949e5a275bb0df8e317a7b8eb3d66c1180e5f6d6b7e70f89217e8ee866b9.webp
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.\n\nIsto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.\n\nhttps://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico\n\nSegue artigo na íntegra. 👇\n\n\nSem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.\n\nCom a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.\n\nHá algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.\n\nLamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.\n\nNo entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.\n\nPela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.\n\nInfelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.\n\nComo a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.\n\nEm virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.\n\nComo são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.\n\nPartindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).\n\nPara a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.\n\nDe fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.\n\nSem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.\n\nVocê também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.\n\nSabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.\n\nTanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.\n\nMas vamos analisar cada um desses tópicos separadamente para entender isso melhor.\n\nRacismo\n\nQuando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.\n\nAproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.\n\nDiversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.\n\nNa Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.\n\nSe estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.\n\nA verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.\n\nE é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.\n\nAbsolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.\n\nA integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.\n\nOu seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.\n\nA discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.\n\nPara citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.\n\nO exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.\n\nIndo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.\n\nA verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.\n\nFascismo\n\nQuando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.\n\nMas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.\n\nEm um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.\n\nPortanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.\n\nÉ claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?\n\nAs leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.\n\nEssa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.\n\nExistem duas fortes razões para isso:\n\nA primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.\n\nAlém do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.\n\nOutra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.\n\nPortanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.\n\nSe você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.\n\nEm primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.\n\nMachismo\n\nMuitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.\n\nApesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.\n\nComo sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.\n\nO liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.\n\nTão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.\n\nA verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.\n\nO que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.\n\nO nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?\n\nHomofobia\n\nQuando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.\n\nA Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.\n\nSegue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:\n\n“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)\n\n“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)\n\n“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)\n\nSe você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.\n\nPortanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.\n\nInfelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.\n\nDefinitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.\n\nQualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.\n\nUma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.\n\nComo se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.\n\nEvidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.\n\nAfinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?\n\nHomossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.\n\nDiscriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.\n\nConclusão\n\nA militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.\n\nNós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.\n\nQuanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.\n\nA história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.\n\nPois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 75da9402:77a65b5c
2023-07-17 17:48:42
@ 75da9402:77a65b5c
2023-07-17 17:48:42
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ 57fe4c4a:c3a0271f
2023-08-02 16:02:43
@ 57fe4c4a:c3a0271f
2023-08-02 16:02:43📝 Summary: The author argues that implementing a first seen safe rule would avoid negative impacts on merchants and users who accept unconfirmed transactions. However, the validity of this claim is questioned as no evidence of actual merchants accepting unconfirmed payments is found. Daniel Lipshitz disputes this conclusion, providing evidence of Coinspaid's use of 0-conf and offering to connect with the CEO for confirmation. He also mentions Changelly's confirmation of GAP600 as a service provider. The request for concrete examples of merchants relying on unconfirmed transactions remains unanswered. Lipshitz disputes the recipient's assessment of their dishonesty, providing evidence to support their claims and challenging the recipient to provide concrete examples. GAP600's research is based on monitoring transactions and network activity, not specific hashing pools or client engagement. Coinpaid's root addresses can be validated using tools like Chainanlysis, and Max at Coinpaid can confirm GAP600's use. Changelly may not have implemented GAP600's service across all its offerings.
👥 Authors: • Daniel Lipshitz ( nostr:npub1t97ak5ltnq0v72nv4jssnhw0fr09axwqvc20623jfdnvrajae7nqufg2yy ) • Peter Todd ( nostr:npub1m230cem2yh3mtdzkg32qhj73uytgkyg5ylxsu083n3tpjnajxx4qqa2np2 )
📅 Messages Date Range: 2023-08-01 to 2023-08-02
✉️ Message Count: 5
📚 Total Characters in Messages: 21371
Messages Summaries
✉️ Message by Peter Todd on 01/08/2023: The author argues that implementing a first seen safe rule would avoid negative impacts on merchants and users who accept unconfirmed transactions. However, the author questions the validity of the claim, as they could not find any evidence of actual merchants accepting unconfirmed payments.
✉️ Message by Daniel Lipshitz on 01/08/2023: The author claims that the research is not thorough and reaches an incorrect conclusion. They provide evidence of Coinspaid's use of 0-conf and offer to connect with the CEO for confirmation. They also mention speaking to Changelly for confirmation of GAP600 as a service provider. The author questions the need for full RBF and requests contacts of mining pools that have adopted it.
✉️ Message by Peter Todd on 02/08/2023: Daniel Lipshitz argues that the research is flawed and reaches an incorrect conclusion. He provides evidence of Coinspaid's use of 0-conf and offers to connect with Max, the CEO, for confirmation. He also mentions Changelly's offer to confirm GAP600 as a service provider. However, the request for concrete examples of merchants relying on unconfirmed transactions remains unanswered.
✉️ Message by Daniel Lipshitz on 02/08/2023: The sender disputes the recipient's assessment of their dishonesty, stating that it is based on baseless assumptions and lacks commercial experience. They provide evidence to support their claims and challenge the recipient to provide concrete examples.
✉️ Message by Daniel Lipshitz on 02/08/2023: GAP600's research is based on monitoring transactions and network activity. They do not assess specific hashing pools or engage with clients for their names and applications. Coinpaid's root addresses can be validated using tools like Chainanlysis. It is possible to reach out to Max at Coinpaid to confirm GAP600's use. Changelly may not have implemented GAP600's service across all its offerings.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ f4db5270:3c74e0d0
2023-07-23 09:10:31
@ f4db5270:3c74e0d0
2023-07-23 09:10:31 \n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Alba a Spotorno" (2023)\n44x32cm, oil on chalkboard\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n
-
 @ 57fe4c4a:c3a0271f
2023-08-02 10:19:21
@ 57fe4c4a:c3a0271f
2023-08-02 10:19:21👥 Authors: Keagan McClelland ( nostr:npub1f2nxequ09nz44775vv6lkffq2plzqvrqramnk29eddmwcc9z7jys8ms289 )
📅 Messages Date: 2023-08-02
✉️ Message Count: 1
📚 Total Characters in Messages: 15187
Messages Summaries
✉️ Message by Keagan McClelland on 02/08/2023: There is a debate about whether to price space in the UTXO set to determine if transactions are spam. This could offend some Bitcoin users.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 28246aee:62b108ad
2023-08-02 02:27:20
@ 28246aee:62b108ad
2023-08-02 02:27:20This post was originally published on https://tftc.io by Marty Bent.
Japan bonds (JGBs, corporates, etc) have come under tremendous pressure since the BOJ's mild tweak to yield curve control.
Group just clocked the worst 2-day slump in at least 23 years pic.twitter.com/lhkxN2BHJj
— David Ingles (@DavidInglesTV) July 31, 2023
As everyone and their mother seems to be mentally prepping for a soft landing, it seems that things are starting to go terribly awry in the world of sovereign debt. Late last week the Bank of Japan made a surprise policy change and didn't put a confident foot forward when changing the range within which they plan to employ yield curve control. Since the policy change JGBs have experienced their worst two-day slump in at least 23 years and the yen has weakened significantly against the dollar. Reaching 142.5 earlier today. In layman's terms, markets are signsling that the little confidence they had left in the Bank of Japan's ability to maintain the monetary system was just destroyed with this spastic move. This move follows their abrupt policy change around Christmas of last year, which spooked markets at the time.
In a world that runs on a hyper-connected and intertwined financial system where everything everywhere needs to be in place for everything to function properly, the Bank of Japan, the JGB market, and the yen are the canary in the coal mine that signal turbulance on the horizon. And if we pan over to the US, things aren't looking so hot on the sovereign debt side of things either.
Earlier today, Fitch downgraded the US governments sovereign debt rating to AA+ from AAA. Joining S&P which downgraded to AA+ in 2011. Leaving the US with no AAA rating to point at while declaring that it has iron clad credit. While we've learned to be wary of credit ratings coming from these ratings agencies due to their abject negligence and pandering during the lead up to the 2008 finacial crisis, it is safe to say that the US debt situation is becoming impossible to ignore. These agencies tend to be very generous with their ratings. If they're downgrading the US government, you know things have to be pretty bad. Likely much worse than a AA+ status. Just look at how much debt Treasury is looking to take out to finish out their pillaging of the American people in 2023.
The Treasury's new guidance today is that they want borrow
::checks notes::
$1.85 trillion during the second half of this year. pic.twitter.com/zIYTB38oDe
— Lyn Alden (@LynAldenContact) July 31, 2023
If my back-of-the-napkin math is in the right ballpark, we're about to increase the national debt by ~10% this year. Utter insanity. And don't look now, but oil prices have been creeping higher and look like they are about to break out. Especially when you consider the inventory draws we've seen recently.
WTI first consecutive closes over the 40-week MA since July 2022. pic.twitter.com/oGLXTy2lQL
— Larry Tentarelli, Blue Chip Daily (@LMT978) July 31, 2023
Your Uncle Marty thinks the inflation problem is still pervasive, but it will begin to become even more obvious as it will be forced to be recognized by CPI prints because of energy costs rising. Let's hope this superconducter stuff is legit.
I don't think there's anything more attractive on the planet than bitcoin hovering between $28,500 and $31,000. The tremors are beginning to rumble louder and louder, the central banks have lost control of their monetary systems and the governments have absolutely no ability to stop themselves from binging on debt, which makes for a pretty precarious situation. It's not shocking that they want you focused on aliens, climate change, and the latest round of Trump indictments. They have completely lost control of the money behind the scenes.
Final thought...
Headed to the Big Apple tomorrow. Come check out the mining mert up at PubKey tomorrow night if you're in town.

You have your place to buy Bitcoin, but have you tried River? It’s where all the Bitcoiners are now going. See why at River.com/TFTC

Sleep soundly at night knowing your bitcoin are secured by multisig.


This rag was delivered to you via Ghost. If you are thinking about starting a newsletter or website and are looking for the most robust and sovereign option you should check out Ghost. For sovereign payments connect your Ghost site to Scrib.
-
 @ f4db5270:3c74e0d0
2023-07-22 16:32:18
@ f4db5270:3c74e0d0
2023-07-22 16:32:18 \n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Ponti sotto la pioggia" (2023)\n40x60cm, oil on panel canvas\n\n(Available)\n\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n\n-----------\n\n\nThe beginning...\n\n
\n\n\n-----------\n\n\nThe beginning...\n\n \n\n\n-----------\n\nThe original photo\n\n
\n\n\n-----------\n\nThe original photo\n\n
-
 @ f4db5270:3c74e0d0
2023-07-22 16:28:30
@ f4db5270:3c74e0d0
2023-07-22 16:28:30 \n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n
\n\n# "Sunset at Playa Hermosa, Uvita" (2023)\n40x30cm, oil on panel canvas\n\n(Available)**\n\n-----------\n\n\nHere a moment work in progress...\n\n \n\n-----------\n\n\nThe beginning...\n\n
\n\n-----------\n\n\nThe beginning...\n\n \n\n-----------\n\n\nThe original photo\n
\n\n-----------\n\n\nThe original photo\n
-
 @ 97c70a44:ad98e322
2023-06-29 15:33:30
@ 97c70a44:ad98e322
2023-06-29 15:33:30First, a product announcement.\n\nCoracle now supports connection multiplexing, which can reduce bandwidth usage by over 90% depending on how many relays you use. It's opt-in for now, but you can set it up by going to Settings and entering
wss://multiplextr.coracle.socialas your "Multiplextr URL".\n\nYou can check out the source code and self-host the library using this link. If you're a dev and want to add client support for multiplextr, the library I built to support this use case might be of use.\n\nNow, on to your regularly scheduled blog post.\n\n \n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n
\n\nThe above announcement isn't irrelevant to what I want to talk about in this post, which is (broadly) the question of "how can Nostr remain decentralized and still support advanced functionality?"\n\nThis is probably the most common question articulated among devs and enthusiasts - is search centralizing? What about recommendation engines? COUNT? Analytics? The answer is yes, and responses range from "it'll be fine" to "nostr is already captured".\n\nFor my part, I'm not sure if this problem can be solved. Already we have a browser wars dynamic emerging among clients, and business models based on proprietary services and advertising have been publicly considered. For the record, I don't think conventional business models are necessarily bad. The world works this way for a reason and Nostr isn't going to change that by default.\n\nNevertheless, I want to see a new internet emerge where my attention belongs to me, and I'm not beholden to massive companies who don't give a rip about me. As a result, much of the work I've put into Coracle hasn't gone into fun features, but into things I think will help realize the vision of Nostr. This gives me FOMO as I watch others' progress, but if I don't stay focused on my vision for Nostr, what am I even doing?\n\nI should be clear that this is not a judgment on the motivations of others, building for fun and profit is just as legitimate as building to idealistically realize the best of all Nostrs. However, I would say that it is every developer's duty to keep in mind that what we're trying to accomplish here is not a web2 clone.\n\n# Two, and only two options\n\nWith all that said, let's get into the meat of the problem. There's a false dichotomy floating around out there that we have two options for adding server-side functionality to the nostr ecosystem. Option 1: pack all required functionality into relays, eliminating the "dumb relay" model, and making it extremely difficult to run a relay. Option 2: keep relays dumb and the protocol minimal, allowing indexers, search engines, and recommendation services (which I'll collectively call "extensions" here) to profit by solving advanced use cases.\n\nBoth alternatives are obviously deficient. Relays need to be something hobbyists can run; requiring relays to fold in a recommendation engine or search index makes that much harder, and for every feature required, proprietary solutions will be able to build a bigger moat.\n\nOn the other hand, proprietary extensions will not bother to interoperate. This will result in an app-store-like landscape of competing extensions, which will redirect developer and user attention away from relays to extensions. If nostr is to succeed, relays must remain an important first-class concept. Aggregators and indexers that gloss over the differences between relays destroy much of the value an individual relay has to offer.\n\nIn either case, some components of the network will become too sophisticated for a layman to deploy. The only alternative is for a few professionals to take up the slack and grow their service as a business. But I think there's a way to squeeze between the horns of the dilemma.\n\n# It's all about routing\n\nIt seems to me that most people prefer the "extension" model of scaling functionality of Nostr as a pragmatic, market-driven alternative to the impossibility of requiring all relays to support all possible features. And I agree, the folks developing and operating more sophisticated tools should be compensated for their hard work.\n\nThe real problem with this approach is that not that extensions are competitive and specialized, but that they obscure the importance of relays by becoming gatekeepers for data by providing additional functionality. If a client or user has to select a search engine and ask it to return results for a given relay, they have given that search engine control over their results, when their trust really should be placed in the relay itself.\n\n(I will say as an aside, that there are scenarios when the gatekeeper approach does make sense, like when a user wants to "bring his own algorithm". But this should be something a user can opt-in to, not a default requirement for accessing the underlying protocol.)\n\nHere's my proposal: instead of requiring users to trust some non-standard extension to make decisions for them, flip the script and make relays the gatekeepers instead. With this approach, the addition of a single feature can open the door for relays to support any extension at no additional cost.\n\nOne of the most exciting aspects of Nostr is the redundancy relays provide. With Nostr, you don't need to trust a single entity to store your data for you! Why should you trust a single gatekeeper to route you to that data? Relays don't need to provide search or recommendations or indexing functionality directly, they can simply send you to a third-party extension they deem trustworthy.\n\nThis approach allows extensions to piggy-back on the trust already endowed in relays by end users. By allowing relays that are already aligned with end users to broker connections with extensions, they form a circuit breaker for delegated trust. This is more convenient for end users, and makes it easier to switch extensions if needed, since relay operators are more likely to have their finger on the pulse than end users.\n\nIt also enables cleaner business relationships. Instead of asking clients to create custom integrations with particular extensions leading to vendor lock-in, an extension provider can implement a common interface and sell to relays instead by offering to index their particular data set.\n\nWith this model, relays have the flexibility to either provide their own advanced functionality or delegate it to someone else, reducing the functionality gap that would otherwise emerge with thick relays without removing the ability for extension service providers to run a business, all the while keeping users and clients focused on interacting with relay operators rather than non-standard extensions.\n\n# Making it happen\n\nThe difficulty with this of course is that add-on services need to be identifiable based on functionality, and they must be interoperable. This means that their functionality must be described by some protocol (whether the core Nostr protocol or an addition to it), rather than by proprietary extensions. There will be extensions that are too complex or special-purpose to fit into this model, or for whom interoperability doesn't matter. That's ok. But for the rest, the work of specifying extensions will pay off in the long run.\n\nThis routing layer might take a variety of forms - I've already proposed an addition to to NIP 11 for service recommendations. Clients would look up what add-ons their relays recommend, then follow those recommendations to find a service that supports their requirements.\n\nIt also occurs to me having written my multiplexer relay this week (and here we come full circle) that it would be trivially easy for relays to proxy certain types of requests. So for example, a relay might fulfill REQs itself, but pass SEARCH requests on to a third-party extension and relay the result to the end user.\n\nIn either case though, a well-behaved client could get all the functionality desired, for all of the data required, without compomising the brilliant trust model fiatjaf came up with.\n\n# Conclusion\n\nI think this is a very important problem to solve, and I think relay-sponsored extension recommendations/routing is a very good way to do it. So, please comment with criticisms! And if you agree with me, and want to see something like this become the standard, comment on my pull request.\n -
 @ 2d5b6404:d4b500b0
2023-07-08 00:56:26
@ 2d5b6404:d4b500b0
2023-07-08 00:56:26nostr streamからzap streamにタイトルも変更し大幅なアップデートがされました。 今までは自分でcloudflare streamに月額課金してマニュアル設定しなければなりませんでしたが、zap streamとOBSを紐づけてSATS(21 sats/min)を支払うだけで簡単にlive配信を開始することができるようになりました。
必要なものは3つだけです。zap streamとalby(アルビー)とOBSです。
はじめにzap streamにログインするためalbyのアカウント作成が必要になります。別の記事でalbyの登録方法をまとめたのでそちらを参考にしてみてください。
→primalが作成したalby(アルビー)の使い方ショート動画
OBSに関しては多くの解説動画がでていますのでそちらを参考に設定してみてください。 ぼくが参考にした動画です。→ https://youtu.be/ZQjsPJpMLiQ
最後にzap streamとOBSを紐づけるだけです。 zap streamのページを開いてalbyでログインします。 ログインしたら右上のアイコンの横のStreamを押します。

Stream Providers
API.ZAP.STREAM
Stream Url
rtmp://in.zap.stream/liveをコピーして、OBSの設定→配信のサーバーの欄に貼り付けます。
Stream Key
・・・・・・・・・をコピーして、OBSの設定→配信のストリームキーに貼り付けます。

次にBalanceのTOPUPを押してSATSを支払います。21 sats/min 1分21satsなので1時間だと1260satsを先に支払います。長時間配信する場合は多めに入金しておきましょう。
あとはEdit Streamでタイトルやサムネイルを設定してSAVEします。 アダルトコンテンツの場合NSFW Contentにチェックをいれてください。

zap streamとOBSの設定が完了したら、OBSで配信開始すれば勝手にzap streamでlive配信が開始されます。
以上がzap streamでlive配信する方法です。
ライブコーディングやゲーム配信をしているユーザーがすでにいますのでVtuderの方などどんどん配信してみてください。
-
 @ b3590d02:0f2b1ae4
2023-07-06 18:44:20
@ b3590d02:0f2b1ae4
2023-07-06 18:44:20Verification: tweet
Badge implications:
- an account that joined Twitter in 2010 or earlier
- an account with fewer than 10,000 followers
Twitter user tweetious profile information:
- Joined in 2008
- Follower count: 699
- Following count: 529
-
 @ 97c70a44:ad98e322
2023-06-26 19:17:23
@ 97c70a44:ad98e322
2023-06-26 19:17:23Metadata Leakage\n\nIt's a well-known fact that Nostr's NIP 04 DMs leak metadata. This seems like an obvious flaw, and has been pointed out as such many times. After all, if anyone can see who you're messaging and how frequently, what time of the day, how large your messages are, who else is mentioned, and correlate multiple separate conversations with one another, how private are your communications really?\n\nA common retort repeated among those who "get" Nostr (myself included) is "it's not a bug, it's a feature". This hearkens back to the early days of the internet, when internet security was less than an afterthought, and social platforms throve on various permutations of the anonymous confessions-type app. How interesting to be able to flex to your friends about whom you're DMing and how often! Most conversations don't really need to be private anyway, so we might as well gamify them. Nostr is nothing if not fun.\n\nIn all seriousness though, metadata leakage is a problem. In one sense, Nostr's DMs are a huge improvement over legacy direct messages (the platform can no longer rat you out to the FBI), but they are also a massive step backward (literally anyone can rat you out to the FBI). I'm completely confident we'll be able to solve this issue for DMs, but solving it for other data types within Nostr might pose a bigger problem.\n\n# Social Content\n\nA use case for Nostr I've had on my mind these last few months is web-of-trust reviews and recommendations. The same sybil attack that allows bots to threaten social networks has also been used as a marketing tool for unscrupulous sellers. NPS surveys, purchased reviews, and platform complicity have destroyed the credibility of product reviews online, just like keyword-stuffed content has ruined Google's search results.\n\nProof-of-work would do nothing to defend against this attack, because the problem is not volume, it's false credibility. The correct tool to employ against false credibility is web-of-trust — verifiable trustworthiness relative to the end user's own social graph.\n\nThis is a huge opportunity for Nostr, and one I'm very excited about. Imagine you want to know whether the vibro-recombinant-shake-faker (VRSF) will result in visible abs in under 6 days. Well, it has over 4 thousand 5-star reviews on Amazon, and all the 1-star reviews are riddled with typos and non sequiturs. So it must work, and make you smarter into the deal! Well, sadly no, visible abs are actually a lie sold to you by "big gym".\n\nNow imagine you could find your three friends who fell for this gyp and ask them what they thought — you might just end up with a lower average rating, and you'd certainly have a higher level of certainty that the VRSF is not worth the vibra-foam it's molded from.\n\nThis same query could be performed for any product, service, or cultural experience. And you wouldn't be limited to asking for opinions from your entire social graph, it would be easy to curate a list of epicureans to help you choose a restaurant, or trusted bookworms to help you decide what to read next.\n\nCurrently, big tech is unable to pull this off, because Facebook won't share its social graph with Google, and Google won't share its business data with Facebook. But if an open database of people and businesses exists on Nostr, anyone can re-combine these silos in new and interesting ways.\n\n# Notes and other Spies\n\nSo that's the pitch, but let's consider the downsides.\n\nAn open social graph coupled with recommendations means that not only can you ask what your friends think about a given product, you can ask:\n\n- What a given person's friends think about a product\n- What kind of person likes a given product\n- How products and people cluster\n\nThat last one in particular is interesting, since it means you could find reasonable answers to some interesting questions:\n\n- Does a given region have fertility problems?\n- What are the political leanings of a given group?\n- How effective was a particular advertisement with a given group?\n\nThis is the kind of social experiment that has historically earned Facebook so much heat. Democratizing this data does not prevent its correlation from being a violation of personal privacy, especially since it will be computationally expensive to do sophisticated analysis on it — and the results of that analysis can be kept private. And to be clear, this is a problem well beyond the combination of social information and public reviews. This is just one example of many similar things that could go wrong with an open database of user behavior.\n\nNot to put too fine a point on it, we are at risk of handing the surveillance panopticon over to our would-be overlords on a silver platter. Just as walled gardens have managed us in the past to sway political opinion or pump the bags of Big X, an open, interoperable content graph will make building a repressive administrative state almost too easy.\n\n# Let's not give up just yet\n\nSo what can we do about it? I want a ratings system based on my social graph, but not at the expense of our collective privacy. We need to keep this threat in mind as we build out Nostr to address novel use cases. Zero-knowledge proofs might be relevant here, or we might be able to get by with a simple re-configuration of data custody.\n\nIn the future users might publish to a small number of relays they trust not to relay their data, similar to @fiatjaf's NIP-29 chat proposal. These relays might then support a more sophisticated query interface so that they can answer questions without revealing too much information. One interesting thing about this approach is that it might push relays towards the PWN model BlueSky uses.\n\nNot all data needs to be treated the same way either, which would give us flexibility when implementing these heuristics. Just as a note might be either broadcast or sent to a single person or group, certain reviews or other activity might only be revealed to people who authenticate themselves in some way.\n\nLike so many other questions with Nostr, this requires our concentrated attention. If all we're doing is building a convenient system for Klaus Schwab to make sure we ate our breakfast bugs, what are we even doing?\n\n
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr\n\n以下是使您的 Nostr 之旅更顺畅的几个步骤 \n\n---\n_本指南适用于: \n 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7\n 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs \n 俄语 \n\n--- \n你好,Nostrich同胞!\n\nNostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。 \n\n## 👋欢迎 \n\n由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz -- \n
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。 \n\n--- \n\n## 🤙玩得开心 \nNostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 \n这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: \nnostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu \n_名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们_ \n\n---\n ## ⚡️ 启用 Zaps \nZaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ \n查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: \n即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤: \n\n0 为您的移动设备下载 Wallet of Santoshi[^1](可能是比特币和闪电网络新手的最佳选择)[^2]\n1 点击“接收” \n2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。 \n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
\n3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。  \n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
\n\n--- \n\n## 📫 获取 Nostr 地址\nNostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: \n🔍 帮助您使您的帐户易于发现和分享 \n✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org  它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。\n\n--- \n要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。 \n\n--- \n\n## 🙇♀️ 学习基础知识 \n\n在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容 \n \n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n
\n_上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。_ \n\n--- \n## 🤝 建立连接 \n与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 \n在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: \n 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 \n 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。 \n * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。\n  \n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
\n--- \n## 🗺️探索 \n上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。  \n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:
\n查看有趣且有用的 Nostr 项目列表: \n https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费) \n https://nostrcheck.me/ – Nostr 地址、媒体上传、中继 \n https://nostr.build/ – 上传和管理媒体(以及更多) \n https://nostr.band/ – Nostr 网络和用户信息 \n https://zaplife.lol/ – zapping统计 \n https://nostrit.com/ – 定时发送帖子\n https://nostrnests.com/ – Twitter 空间 2.0\n https://nostryfied.online/ - 备份您的 Nostr 信息 \n https://www.wavman.app/ Nostr 音乐播放器 --- \n## 📻 中继\n熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。 \n\n## 📱 手机上的 Nostr \n在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile \n \n感谢阅读,我们在兔子洞的另一边见\nnostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 \n \n_发现这篇文章有价值吗_\n_Zap_⚡ 21ideas@getalby.com \n关注:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/\n\n \n\n[^1]:还有更多支持闪电地址的钱包,您可以自由选择您喜欢的 \n[^2]:不要忘记返回钱包并备份你的账户\n[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标\n\n\n译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边\n\n_Zap⚡ spang@getalby.com \n关注:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv\n\n\n\n\n\n -
 @ d266da53:7224d834
2023-08-04 08:39:38
@ d266da53:7224d834
2023-08-04 08:39:38Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.

The Internet of Things (IoT) has emerged as a transformative technology, connecting billions of devices and revolutionising industries across the globe. In parallel, smart contracts, powered by blockchain technology, have gained traction as an innovative means of automating and securing digital agreements. When these two disruptive technologies converge, the potential for synergy and transformative impact becomes evident. In this article, we explore how smart contracts could revolutionise the Internet of Things, enhancing security, efficiency, and trust in the interconnected world.
What is the Internet of Things (IoT) and what are the real-world benefits?
IoT refers to a network of physical objects, devices, vehicles, appliances, and other items embedded with sensors, software, and connectivity capabilities that enable them to collect and exchange data over the internet. These “things” can range from everyday objects like thermostats, refrigerators, and wearable devices to complex industrial machinery, smart cities infrastructure, and even autonomous vehicles.
Equipped with sensors and actuators, IoT devices help to gather data from their surroundings and potentially even interact with their environment. They can communicate with each other, exchange data with cloud-based systems, and potentially make autonomous decisions based on the information they receive. This interconnected network of devices creates a vast ecosystem where data flows and interactions occur, enabling a wide range of applications and services.
The primary goal of IoT is to enable the seamless integration between the physical and digital world, unlocking numerous opportunities for efficiency, automation, and innovation. By collecting and analysing data from various sources, IoT provides valuable insights, helping to make informed decisions and automate processes to enhance productivity, optimise resource utilisation, improve safety, and provide new services and experiences.
The proliferation of IoT has transformed numerous industries, including healthcare, agriculture, manufacturing, transportation, energy, and smart cities. In healthcare, for example, IoT devices can monitor patients’ vital signs, track medication adherence, and enable remote diagnostics, enhancing the quality of care and empowering patients to take a more proactive role in managing their health. In agriculture, IoT sensors can monitor soil moisture, weather conditions, and crop health, enabling farmers to optimise irrigation, reduce waste, and improve yields.
How can blockchain technology and smart contracts enhance IoT?
The seamless integration of IoT and blockchain technologies offer numerous potential benefits, particularly in scenarios where vast amounts of data collected from IoT devices need to be stored and accessed in the public domain. Meanwhile, smart contracts can eliminate the need for intermediaries, central authorities, and manual intervention, helping to streamline processes and increase operational efficiency. Here are three examples describing the potential impact blockchain technology and smart contracts could have on three incredibly important global sectors.

Example #1 — IoT-Based Supply Chain Tracking
In this scenario, let’s say a company manufactures organic coffee beans and wants to provide verifiable information about the product’s origin, ensuring transparency and trust for consumers.
- IoT Devices: The company installs IoT devices (e.g., RFID tags, GPS trackers) on each bag of coffee beans during the production process. These devices record data such as the location, temperature, humidity, and other relevant parameters at different stages of the supply chain.
- Data Storage on the Blockchain: The data collected by IoT devices is stored on a public blockchain. Each bag of coffee beans is associated with a unique identifier (e.g., a barcode) that acts as its digital twin on the blockchain, referred to as an NFT.
- Smart Contracts: Smart contracts are deployed on the blockchain to automate various aspects of the supply chain process. For instance, a smart contract could be programmed to trigger certain actions when specific conditions are met, such as recording the location and timestamp when a bag of coffee beans reaches a particular checkpoint, like a warehouse or a shipment hub.
- Transparency and Verification: Consumers and other stakeholders can access the blockchain to verify the entire journey of a bag of coffee beans, from its origin to the final destination. The immutable nature of the blockchain ensures that the data cannot be tampered with, providing transparent and auditable information about the product’s supply chain history.
- Supply Chain Efficiency: With the data being transparently recorded on the blockchain, all parties involved in the supply chain, including the manufacturer, distributors, retailers, and consumers, have access to real-time information. This transparency reduces the likelihood of disputes, delays, or fraudulent activities, leading to a more efficient and trustworthy supply chain.
- Quality Assurance: The data collected by IoT devices can help monitor environmental conditions during transportation and storage. If the temperature or humidity exceeds predefined thresholds, the smart contract could trigger an alert, allowing the company to take immediate action to preserve the product’s quality.
- Automated Payments and Incentives: Smart contracts can automate payment processes between different parties in the supply chain. For example, when a bag of coffee beans reaches its destination, the smart contract can automatically release the payment to the distributor, streamlining the payment process and reducing administrative overhead.
In summary, combining IoT, blockchain, and smart contracts in the supply chain management of organic coffee beans enables transparency, trust, and efficiency throughout the entire process. Consumers can access verifiable information about the product’s origin, quality, and handling, leading to increased trust in the brand. The automated and secure nature of smart contracts reduces the need for intermediaries and manual interventions, making the supply chain more streamlined and cost-effective. Overall, this example illustrates how blockchain and smart contracts enhance the IoT ecosystem, transforming supply chain management and positively impacting businesses and consumers alike.

Example #2 — IoT-Based Energy Management in a Smart City
In this scenario, we’ll explore how blockchain and smart contracts can help manage energy consumption in a smart city, optimising resources and enhancing sustainability.
- IoT Devices: In a smart city, various IoT devices are deployed throughout the infrastructure, including smart meters, sensors, and actuators. These devices collect real-time data on energy consumption, electricity generation (e.g., solar panels), weather conditions, traffic patterns, and other relevant information.
- Data Storage on the Blockchain: The data collected by IoT devices is stored on a private or public blockchain, depending on the level of required transparency and privacy. Each device or data source has its unique identifier and cryptographic signature to ensure data integrity and prevent tampering.
- Smart Contracts: Smart contracts are used to manage energy-related processes in the smart city. For instance, a smart contract could be created to automatically adjust street lighting levels based on the detected traffic patterns and weather conditions. Additionally, a smart contract could optimise the usage of renewable energy sources based on real-time electricity generation data and demand.
- Decentralised Energy Grid: The smart contracts on the blockchain enable the creation of a decentralised energy grid, where energy transactions can occur peer-to-peer between energy producers and consumers. Prosumers (those who produce and consume energy) can sell excess energy to others directly through the blockchain, without the need for intermediaries.
- Energy Efficiency: With real-time data collected from IoT devices and processed by smart contracts, the city’s energy management system can automatically optimise energy consumption. For example, smart contracts can adjust heating, cooling, and lighting systems in public buildings based on occupancy, weather conditions, and energy availability, reducing wastage and promoting energy efficiency.
- Demand Response: The IoT devices and smart contracts can enable a demand-response mechanism. When the energy grid faces peak demand periods, smart contracts can automatically adjust the energy consumption of certain non-essential systems to balance the load and prevent blackouts or energy shortages.
- Incentives for Sustainable Practices: Through the blockchain and smart contracts, the city can implement incentive programs to encourage sustainable energy practices. For instance, residents or businesses that actively participate in energy conservation or generate renewable energy may receive tokens or other rewards on the blockchain, fostering a culture of sustainability.
In summary, applying blockchain and smart contracts to IoT-based energy management in a smart city offers numerous benefits. It allows for a transparent, decentralised, and automated energy management system that optimises energy consumption, reduces waste, and promotes the use of renewable energy sources. The secure and immutable nature of the blockchain ensures data integrity, while smart contracts enable real-time decision-making and automation. By fostering a more sustainable and efficient energy ecosystem, this use case contributes to building smarter, greener, and more resilient cities for the future.

Example #3 — IoT-Based Healthcare Data Management
In this scenario, we’ll examine how blockchain and smart contracts can address the challenges of securely managing and sharing patient data among different healthcare providers, ensuring privacy, and promoting interoperability.
- IoT Medical Devices: In a healthcare setting, IoT medical devices are utilised to monitor patients’ vital signs, collect health data, and track medical conditions. These devices can include wearable health trackers, smart implants, and remote monitoring devices.
- Data Storage on the Blockchain: The health data collected by IoT devices is stored on a private blockchain network with controlled access. Each patient’s medical data is encrypted and linked to their unique digital identity on the blockchain.
- Smart Contracts for Data Access and Consent: Smart contracts are utilised to manage data access and patient consent. Patients can specify which healthcare providers or researchers can access their medical data through predefined smart contracts. The smart contracts enforce data access permissions and ensure that data is only accessible to authorised parties with patient consent.
- Interoperability: The use of a blockchain-based system enables interoperability between different healthcare providers and institutions. As patient data is stored in a standardised and secure format on the blockchain, authorised healthcare providers can access and share relevant data seamlessly, even if they use different electronic health record (EHR) systems.
- Patient-Centric Data Control: Blockchain and smart contracts empower patients to have greater control over their health data. Patients can easily grant or revoke access to their medical information, ensuring that sensitive data remains secure and shared only with those they trust.
- Auditability and Data Integrity: The immutable nature of the blockchain ensures that all data transactions and changes to patient records are recorded transparently. This audit trail fosters data integrity, reducing the risk of unauthorised modifications or data breaches.
- Research and Analytics: Researchers can securely access aggregated and anonymised health data for medical research and population health analytics. Smart contracts can govern data-sharing agreements between healthcare institutions and researchers, ensuring compliance with privacy regulations and ethical considerations.
- Telemedicine and Remote Monitoring: IoT devices can facilitate telemedicine and remote patient monitoring, where patients’ health data is transmitted securely to healthcare providers through the blockchain. Smart contracts can automate remote monitoring protocols and alert healthcare professionals in case of emergencies or abnormal conditions.
In summary, implementing blockchain and smart contracts in an IoT-based healthcare data management system offers significant advantages. It ensures patient data security, privacy, and control while promoting interoperability and data sharing among healthcare providers. The decentralised and immutable nature of the blockchain enhances data integrity and transparency, making it a valuable tool for improving healthcare delivery, medical research, and patient outcomes. By fostering a patient-centric approach to data management, this use case enhances the overall efficiency and effectiveness of the healthcare system.

How does blockchain data storage compare to traditional cloud storage?
Commonly referred to as the “Big Data of Things” the IoT space is anticipated to generate a staggering 73.1 zettabytes (ZB) of data — for context, a single zettabyte (ZB) is equal to one trillion gigabytes (GB). Big data is a valuable resource for businesses, researchers, and organisations alike, providing insights, trends, and patterns that can drive decision-making, innovation, and efficiency improvements.
Rising significantly in popularity during the 2010’s, cloud storage solutions from the likes of Google and Amazon have made a significant impact on IoT data storage, providing scalable, real-time access and analytics capabilities. However, the downside of cloud storage lies in its centralised nature, where data is stored and managed by third-party providers, making it susceptible to potential security breaches, data loss, and privacy concerns. Furthermore, cloud computing lacks the programmability of blockchain technology, offering automated rule-based interactions and conditional data access. These are the key benefits of using blockchain technology over traditional cloud-based storage:
- Decentralisation and Security: Blockchain’s decentralised nature ensures that data is distributed across a network of nodes, reducing the risk of single points of failure and making it more resistant to hacking or data breaches. This enhances the security and integrity of IoT data, safeguarding it from unauthorised access and tampering.
- Immutability: Data stored on a blockchain is immutable, meaning it cannot be altered or deleted once it is recorded. This feature ensures data integrity and creates a transparent and auditable trail of all data changes, providing reliable and trustworthy data history.
- Trust and Transparency: Blockchain operates on a consensus mechanism, where multiple nodes agree on the validity of transactions and data. This consensus fosters trust among participants, as all parties can verify data without relying on a central authority, ensuring transparent and accountable data sharing.
- Data Ownership and Control: In a blockchain network, data ownership and control lie with the users who hold cryptographic keys to access and manage their data. This user-centric approach enhances data privacy, giving individuals more control over their personal information, reducing dependence on third-party providers.
- Elimination of Centralised Authority: Unlike cloud storage solutions that rely on centralised servers and administrators, blockchain eliminates the need for a single central authority, reducing the risk of data abuse or manipulation by a single entity.
- Smart Contracts and Automation: Smart contracts can facilitate automated and trustless interactions based on predefined conditions. This allows for seamless and secure data sharing, automated transactions, and the execution of predefined rules without the need for intermediaries.
- Resilience and Disaster Recovery: The distributed nature of blockchain data storage ensures that even if some nodes fail or leave the network, the data remains available and operational, enhancing resilience and disaster recovery capabilities.
- Data Interoperability: Blockchain can facilitate data interoperability, enabling seamless data exchange between different IoT devices, platforms, and applications, fostering collaboration and integration across diverse systems.

How is IoT data stored on the blockchain?
IoT data collection can typically be integrated with a blockchain in one of two ways:
- Data can be directly embedded in smart contracts
- Data can be stored off-chain and the blockchain stores references (e.g., hashes) to the data
Prior to adding any data to the blockchain, it undergoes validation to ensure its accuracy, authenticity, and adherence to predefined rules or consensus mechanisms. The validated IoT data is then stored on the blockchain as transactions. Each transaction represents a batch of data and is added to a block, forming a chain of blocks, hence the name “blockchain”. Once data is stored on the blockchain, it becomes immutable and transparent. It cannot be altered or deleted, and its entire history is recorded, making it auditable and tamper-resistant.
Smart contracts are created to manage data access and data sharing permissions. These contracts define rules for accessing specific data sets, ensuring that only authorised parties can retrieve relevant data. External parties, such as other devices, applications, or organisations, can interact with the smart contract to request access to specific IoT data. The smart contract validates the request and executes predefined conditions to verify the legitimacy of the data access request. If the request is valid, the smart contract grants access to the requested data, either by providing the data directly from the blockchain or by referring to off-chain data sources. In cases where data privacy is crucial, the smart contract may use encryption mechanisms to secure the data during transmission and access.
Where cloud storage is typically charged on a subscription basis, determined by the amount of data stored, blockchain storage is done on a pay-as-you-go basis. Each time data is recorded on the blockchain, transaction fees are applicable. Further fees may be applicable when that data is later accessed through a smart contract. It is therefore important to select a blockchain network that is optimised for the intended application. Choosing a network that is interoperable with other networks is also vital, as the blockchain industry is very much in its infancy and official global standards have not yet been established. Choosing a network such as Electroneum, with extremely low transaction fees (several orders of magnitude cheaper than Ethereum) along with its compatibility with the Ethereum Virtual Machine (EVM) could be a good choice for your requirements. More on this in the next section.

The importance of standards in blockchain for IoT expansion
Technology standards enable different devices and technologies to communicate seamlessly with one another, eliminating fragmentation and proprietary lock-ins. Standards help to establish best practices for safety and security, whilst also allowing for easy substitution and scalability. This, in practice, helps to facilitate greater market access and global trade, whilst driving collaboration, research, and development for innovation and industry advancement.
Across the IoT sector today, wireless communication standards such as Wi-Fi and Bluetooth have played a crucial role in facilitating its significant growth, which in 2021 had exceeded 11 billion devices, and by 2023 is projected to reach almost 30 billion. Where Wi-Fi provides high-speed wireless connectivity, enabling IoT devices to connect to the internet and communicate with other devices, cloud platforms, and applications, Bluetooth offers short-range wireless communication, making it ideal for connecting IoT devices in close proximity, such as wearable devices, smart home devices, and personal sensors. Together, these standards have provided the foundation for scalable, interconnected IoT ecosystems.
As blockchain technology and smart contracts continue to evolve and find widespread adoption, similar standards will be needed. So far, the Ethereum Virtual Machine (EVM) has played a pivotal role in setting some key global standards for smart contracts. It introduced the Solidity programming language, which aims to foster a common coding standard, whilst EVM’s gas mechanism and fee standards ensure fairness and efficiency in contract execution. It has also fostered the development of tools, libraries, and frameworks for smart contract development, while the EIP process provides developers with a unified way of proposing improvements to the technology.
With the release of Project Aurelius later this year, Electroneum is aligning its well-established blockchain network with the standards set out by EVM, allowing external developers to build on top of the network for the very first time and establishing interoperability with other EVM-compatible blockchains, such as Ethereum, Ripple, Binance Smart Chain, Polygon, Avalanche, Cardano, amongst others. More importantly, however, Electroneum is introducing significantly lower EVM interaction fees that are a number of orders of magnitude cheaper than Ethereum’s, providing a more affordable way to build and deploy smart contracts within IoT environments.
How can an IoT manufacturer move to blockchain data storage?
The convergence of blockchain technology and smart contracts with the IoT presents a transformative potential for various industries, and as these technologies continue to evolve and gain broader adoption, their impact on today’s trillion-dollar IoT market can be transformational, unlocking new opportunities for efficiency, security, and innovation. If you work in IoT and would like to discuss any thoughts or ideas, be sure to reach out to us at: opportunities@electroneum.com
By:ETN-Network Link:https://medium.com/@ETN-Network/how-could-blockchain-technology-and-smart-contracts-impact-the-1-trillion-iot-market-8a78a6980219
-
 @ 97c70a44:ad98e322
2023-06-01 13:46:54
@ 97c70a44:ad98e322
2023-06-01 13:46:54I think I cracked the code on private groups.\n\nInstead of relying on relays to implement access control as in this PR, we could combine the Gift Wrap proposal with @PABLOF7z's nsec bunker to create private groups with easy administration and moderation!\n\nGift wrap fixes DM metadata leakage by using a temporary private key to send a DM to a recipient. The recipient decrypts the wrapper to find a regular nostr event inside. This could be another kind 4 as in the proposal, or anything else. Which means you can send kind 1's or anything else in a wrapped event.\n\nNow suppose you had a pubkey that you wanted to represent a group instead of a person. Put its nsec in a (modified) nsec bunker, and now you can allow other people than yourself to request signatures. A shared private key! Anyone who has access to this nsec bunker could also de-crypt any gift wrapped note sent to it. Relay-free read access control!\n\nThere are lots of ways you could manage this access list, but I think a compelling one would be to create a NIP 51 list (public or private!) of group members and set up the nsec bunker to authenticate using that list. Boom, dynamic member lists!\n\nYou could also create a NIP 51 list for admins, and pre-configure which event kinds each list is allowed to post using the group's nsec. So maybe members could only publish wrapped kind-1's, but admins could publish wrapped kind-0's (you can now zap a group!), kind 9's for moderation, updated member and moderator lists, normal kind 1's for public information about the group, etc.\n\nGift wrap would support:\n\n- Leak-free DMs\n- Fully private groups\n- Public-read groups (nsec bunker would allow for admin, but everyone would publish regular instead of wrapped events).\n- Organizations and other shared accounts, with role-based authorization (list/kind mappings)!\n\nOf course, no clients currently support this kind of thing, but support would not be hard to add, and it creates an entirely new set of affordances with two very simple applications of the core protocol.\n\nThere are a few drawbacks I can think of, of course. Gift wrap makes it harder to search notes by tag. You could:\n\n- Leave all tags off (other than for DM recipient as in the proposal)\n- Selectively keep tags that aren't revealing of identity\n- Encrypt tag values. When a client wants to query a tag, it must encrypt the value using the same pubkey and include that in the filter. This, I think, is ok for the group use case above.\n\nThere are also a number of proposals in the works to fix NIP 04 DMs which are apparently broken from a cryptographic standpoint, so implementing this should probably wait until that stuff is sorted out. But it should be possible however that ends up materializing.\n\nSo am I nuts? Or is this a galaxy brain solution?
-
 @ 32e18276:5c68e245
2023-06-01 04:17:00
@ 32e18276:5c68e245
2023-06-01 04:17:00Double-entry accounting is a tried and true method for tracking the flow of money using a principle from physics: the conservation of energy. If we account for all the inflows and outflows of money, then we know that we can build an accurate picture of all of the money we've made and spent.\n\nBitcoin is particularly good at accounting in this sense, since transaction inflows and outflows are checked by code, with the latest state of the ledger stored in the UTXO set.\n\nWhat about lightning? Every transaction is not stored on the blockchain, so we need same way to account for all the incoming and outgoing lightning transactions. Luckily for us, core-lightning (CLN) comes with a plugin that describes these transactions in detail!\n\nFor every transaction, CLN stores the amount credited and debited from your node: routed payments, invoices, etc. To access this, you just need to run the
lightning-cli bkpr-listaccounteventscommand:\n\n\nlightning-cli bkpr-listaccountevents | jq -cr '.events[] | [.type,.tag,.credit_msat,.debit_msat,.timestamp,.description] | @tsv' > events.txt\n\n\nThis will save a tab-separated file with some basic information about each credit and debit event on your node.\n\n\nchannel invoice 232000000 0 1662187126 Havana\nchannel invoice 2050000 0 1662242391 coinos voucher\nchannel invoice 0 1002203 1662463949 lightningpicturebot\nchannel invoice 300000 0 1663110636 [["text/plain","jb55's lightning address"],["text/identifier","jb55@sendsats.lol"]]\nchannel invoice 0 102626 1663483583 Mile high lightning club \n\n\nNow here's comes the cool part, we can take this data and build a ledger-cli file. ledger is a very powerful command-line accounting tool built on a plaintext transaction format. Using the tab-separated file we got from CLN, we can build a ledger file with a chart-of-accounts that we can use for detailed reporting. To do this, I wrote a script for convertingbkptreports to ledger:\n\nhttp://git.jb55.com/cln-ledger\n\nThe ledger file looks like so:\n\n\n2023-05-31 f10074c748917a2ecd8c5ffb5c3067114e2677fa6152d5b5fd89c0aec7fd81c5\n expenses:zap:1971 1971000 msat\n assets:cln -1971000 msat\n\n2023-05-31 damus donations\n income:lnurl:damus@sendsats.lol -111000 msat\n assets:cln 111000 msat\n\n2023-05-31 Zap\n income:zap:event:f8dd1e7eafa18add4aa8ff78c63f17bdb2fab3ade44f8980f094bdf3fb72d512 -10000000 msat\n assets:cln 10000000 msat\n\n\nEach transaction has multiple postings which track the flow of money from one account to another. Once we have this file we can quickly build reports:\n\n## Balance report\n\nHere's the command for "account balance report since 2023-05 in CAD"\n\n$ ledger -b 2023-05-01 -S amount -X CAD -f cln.ledger bal\n\n\n CAD5290 assets:cln\n CAD2202 expenses\n CAD525 routed\n CAD1677 unknown\nCAD-7492 income\n CAD-587 unknown\n CAD-526 routed\nCAD-1515 lnurl\n CAD-614 jb55@sendsats.lol\n CAD-1 tipjar\n CAD-537 damus@sendsats.lol\n CAD-364 gpt3@sendsats.lol\nCAD-4012 merch\nCAD-2571 tshirt\nCAD-1441 hat\n CAD-852 zap\n CAD-847 event\n CAD-66 30e763a1206774753da01ba4ce95852a37841e1a1777076ba82e068f6730b75d\n CAD-60 f9cda1d7b6792e5320a52909dcd98d20e7f95003de7a813fa18aa8c43ea66710\n CAD-49 5ae0087aa6245365a6d357befa9a59b587c01cf30bd8580cd4f79dc67fc30aef\n CAD-43 a4d44469dd3db920257e0bca0b6ee063dfbf6622514a55e2d222f321744a2a0e\n ...\n------------\n 0\n\n\nAs we can see it shows a breakdown of all the sats we've earned (in this case converted to fiat). We can have a higher-level summary using the depth argument:\n\n$ ledger -M -S amount -X sat -f cln.ledger bal\n\n\n sat14694904 assets:cln\n sat6116712 expenses\n sat1457926 routed\n sat4658786 unknown\nsat-20811616 income\n sat-1630529 unknown\n sat-1461610 routed\n sat-4207647 lnurl\nsat-11144666 merch\n sat-2367164 zap\n------------\n 0\n\n\nAs we can see we made 14 million sats this month, not bad! The number at the bottom balances to zero which means we've properly accounted for all income and expenses.\n\n## Daily Damus Donation Earnings\n\nTo support damus, some users have turned on a feature that sends zaps to support damus development. This simply sends a payment to the damus@sendsats.lol lightning address. Since we record these we can build a daily report of damus donations:\n\n$ ledger -D -V -f cln.ledger reg damus\n\n\n23-May-15 - 23-May-15 ..damus@sendsats.lol CAD-46 CAD-46\n23-May-16 - 23-May-16 ..damus@sendsats.lol CAD-73 CAD-120\n23-May-17 - 23-May-17 ..damus@sendsats.lol CAD-41 CAD-161\n23-May-18 - 23-May-18 ..damus@sendsats.lol CAD-37 CAD-197\n23-May-19 - 23-May-19 ..damus@sendsats.lol CAD-35 CAD-233\n23-May-20 - 23-May-20 ..damus@sendsats.lol CAD-28 CAD-261\n23-May-21 - 23-May-21 ..damus@sendsats.lol CAD-19 CAD-280\n23-May-22 - 23-May-22 ..damus@sendsats.lol CAD-29 CAD-309\n23-May-23 - 23-May-23 ..damus@sendsats.lol CAD-19 CAD-328\n23-May-24 - 23-May-24 ..damus@sendsats.lol CAD-25 CAD-353\n23-May-25 - 23-May-25 ..damus@sendsats.lol CAD-36 CAD-390\n23-May-26 - 23-May-26 ..damus@sendsats.lol CAD-37 CAD-426\n23-May-27 - 23-May-27 ..damus@sendsats.lol CAD-25 CAD-451\n23-May-28 - 23-May-28 ..damus@sendsats.lol CAD-25 CAD-476\n23-May-29 - 23-May-29 ..damus@sendsats.lol CAD-12 CAD-488\n23-May-30 - 23-May-30 ..damus@sendsats.lol CAD-29 CAD-517\n23-May-31 - 23-May-31 ..damus@sendsats.lol CAD-21 CAD-537\n\n\nNot making bank or anything but this covered the relay server costs this month!\n\nHopefully ya'll found this useful, feel free to fork the script and try it out! -
 @ 76c71aae:3e29cafa
2023-05-30 21:59:50
@ 76c71aae:3e29cafa
2023-05-30 21:59:50Joining a new digital community can be an exhilarating and empowering experience. This has been observed on numerous occasions when people join new platforms such as Nostr, BlueSky, Farcaster, Post.news, Tribel, and many others, as well as older social media platforms such as blogs, Usenet, LiveJournal, Xanga, AOL, Flickr, Facebook, Instagram, and TikTok.
Initially, these spaces create an idealistic environment where individuals are eager to connect, share, and participate in a virtual gathering that resembles a festival. However, it is worth examining what it is about these new social spaces that generates such a euphoric atmosphere, and whether it is feasible to sustain this utopian sentiment as communities expand and develop.
The Magic of Connection:
Joining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.
Utopias Form Where They Shouldn’t Exist:
The concept of "Paradise Built in Hell" becomes evident during natural and economic disasters. I personally witnessed this idea during Argentina's economic crisis in the early 2000s. Despite the difficulties, people came together and collaborated in new ways to support each other, as the collapsing economy demanded it. This same phenomenon is observed following earthquakes and other natural disasters, where people often speak of those days with a magical, almost reverential tone.
Rebecca Solnit argues that "Disaster is when the shackles of conventional belief and role fall away and the possibilities open up; people rise to the occasion or sink to the level of their fears and prejudices." In these challenging moments, we see the true nature of humanity: our ability to show compassion, resilience, and unity in the face of adversity.
Social Media and All Digital Spaces Have Physical Analogues:
The similarities between digital and physical communities are rooted in the fact that each has its own distinct set of unspoken rules and social norms. Just as we know to be quiet in a library, loud at a concert, social at a cocktail party, and anti-social on the subway, we also understand the unique dynamics of different digital platforms. Twitter resembles a bustling dive bar, Instagram an art gallery, TikTok an amusement park hall of mirrors, and Facebook a community hall rented for a retirement party. Every new digital space has its analogues in the physical world because human interaction remains consistent, even if the medium differs. As we navigate the ever-changing landscape of digital communities, we are reminded of our innate ability to adapt, connect, and thrive in the face of adversity. This adaptability empowers us to form new connections and rediscover the power of community, whether in the digital or physical realm.
The Small Community Paradox:
To maintain the utopian atmosphere of new digital communities, one effective approach is to keep them small or create numerous smaller sub-communities. In these sub-communities, people can engage in the social labor of connection and conflict resolution.
It is important to note, however, that this approach may conflict with the network effect principle. This principle states that each new member joining the community increases its overall value for all participants. As communities grow and the network effect takes hold, the utopian feeling may often fade, giving way to sub-tribes and conflict.
Nevertheless, with a confident approach, the community can adapt and navigate these challenges to foster a positive environment for all members.
The Fleeting Nature of Utopia:
The fleeting utopian sensation experienced within new digital communities is inevitable. Although it is not the design or coding of platforms such as BlueSky, Nostr, Mastodon, or Scuttlebutt that generates this feeling of euphoria, it is instead the human dynamics of joining something novel and building a community that cultivates this enchanting ambiance. Hakim Bey's concept of Temporary Autonomous Zones (TAZs) endorses this notion, demonstrating how short-lived spaces of freedom and interaction can emerge within established social structures. As communities expand and progress, the real challenge lies in sustaining the initial energy and sense of connection that made them so desirable in the first place.
Parallel to Protests and Uprisings:
This utopian sentiment is not limited to digital communities; it is also present during times of revolution, protests, and uprisings. There is a profoundly human element to the sense of love, connection, solidarity, and community that arises during these moments.
The most impactful moments of my life have been when I participated in protests that were met with repression. These protests ranged from tree-sits to protect old-growth redwoods in the forests where I grew up, to large convergences of the anti-globalization and anti-war movements, to Occupy's reclamation of public spaces, and to recent Black Lives Matter protests. All of these protests were scenes of anguish, repression, and, in some cases, violence, especially from the police. However, they were also places where I experienced the most love, connection, humanity, and common purpose. We were all individuals, together, living and breathing solidarity.
Cultivating and Sustaining Utopian Energy:
To preserve the utopian essence of new digital communities as they grow, one approach is to foster a culture of empathy, connection, and inclusiveness from the very beginning. Prioritizing these values and actively engaging in conflict resolution can help communities maintain that special feeling.
Another way to preserve the utopian essence of digital communities is to focus on building tools for the construction and maintenance of these digital public spaces. Unlike corporate social media platforms that only provide an illusion of public space while actually being privately owned, like a shopping mall, we need to create spaces that are community-controlled and collectively owned as a commons with confidence.
Understanding the Commons:
The concept of the commons offers a compelling alternative to traditional models of state or private ownership. Elinor Ostrom, the first woman to win the Nobel Prize in Economics, conducted extensive research on this topic, and her findings are truly remarkable. Through her work, she proved that commons can be effectively managed and maintained, debunking the misguided belief that these resources are doomed to fail and end in tragedy.
Designing for Digital Commons:
To design digital commons, we must prioritize transparency, decentralization, and participatory governance. By empowering users to make decisions about the direction and rules of their digital communities, we ensure that the spaces remain truly public and that the needs and desires of the community are at the forefront.
Open-source technology and decentralized protocols can play a vital role in the development of these digital commons. By allowing users to maintain control over their data and ensuring that no single entity has a monopoly over the platform, we create an environment that fosters collaboration, creativity, and innovation.
The Characteristics of a Well-Functioning Digital Commons:
- Clearly defined boundaries: Members and their rights are easily identifiable, and access to the shared digital resources is well-regulated.
- Proportional equivalence between benefits and costs: Users contribute to the commons according to their capabilities, and benefits are distributed fairly among members.
- Collective decision-making: Users have a say in shaping the rules and policies that govern their digital communities, promoting a sense of ownership and accountability.
- Monitoring: Transparent systems are in place to track the usage and management of shared resources, ensuring that members adhere to established rules.
- Graduated sanctions: Penalties for rule violations are proportional and escalate based on the severity and frequency of the transgressions.
- Conflict resolution mechanisms: Efficient and fair processes are in place to address disputes among members, promoting harmony and trust within the community.
- Minimal recognition of rights to organize: Users have the autonomy to self-organize and make decisions about their digital commons without excessive interference from external authorities.
- Nested enterprises: Digital commons are organized into multiple, interconnected layers of governance, with smaller communities operating within the context of larger ones, fostering collaboration and coordination.
By incorporating these principles into the design of digital commons, we can create spaces that are robust, sustainable, and equitable. This, in turn, fosters innovation, collaboration, and genuine community engagement.
Developing Community-Driven Tools:
To create and maintain digital public spaces, we need tools that empower communities to effectively manage their digital commons. These tools should facilitate communication, conflict resolution, and decision-making while promoting inclusiveness, empathy, and shared values. By empowering communities to shape their digital spaces and collaboratively resolve issues, we can help preserve the utopian essence that initially attracted people to these platforms.
Adapting to Growth and Change:
As digital communities continue to grow, it's crucial to acknowledge that their needs and challenges will inevitably change over time. To maintain a utopian atmosphere, we must be willing to adapt and consistently improve the tools and processes that sustain these digital public spaces. By promoting continuous feedback and collaboration among community members, we can ensure that the platform remains responsive to the needs of its users, fostering an environment of connection and belonging with conviction.
Conclusion:
Joining a new digital community can be a thrilling experience, but maintaining that sense of euphoria as the community grows can be difficult. To achieve this, we must design and construct digital commons that prioritize community control, collective ownership, and participatory governance. With the appropriate tools and a dedication to adapting to the evolving needs of the community, we can create spaces that continue to foster the magic of connection even as they transform. In doing so, we can nurture and sustain the utopian energy that makes these digital spaces so unique.
Post Script:
Since the completion of this essay, Bluesky has evolved from its initial utopian stage to a phase grappling with context, norms, and scalability. With an increasing user base, the once agreed-upon behavioral norms began to crumble. The initial playfulness, while staying within the community's value constraints, took a disturbing turn when individuals started posting racist and homophobic content. The situation deteriorated rapidly, escalating to the point of issuing death threats. Inspired by the "Nazi bar" parable, the community demanded urgent action to outline acceptable behavior and remove those who couldn't comply.
Bluesky, currently hosted on a single server, possesses the capability to enforce a unified set of community guidelines and terms of service. The creators of Bluesky, much like any other social media platform's developers, aimed for a laissez-faire approach. However, they eventually had to revise the terms of service and ban the trolls. This action was chaotic and resulted in significant loss of trust and goodwill.
Additionally, this did not aid the community in establishing governance for the burgeoning social media commons. Protocols such as Bluesky, Nostr, DSNP, Scuttlebutt, Farcaster, and Lens are not designed to operate in isolation. Among these, only ActivityPub and Mastodon have successfully implemented a model to manage abuse and community moderation at scale. Nonetheless, potential solutions are under development. I've personally contributed to proposals for specifications, codes, and norms on Nostr and know that Bluesky's team is making similar strides.
It is essential that the user community actively participate in this process. The Design Justice movement provides a valuable blueprint and strategies for achieving this. By applying principles of co-design and design justice, we can collaboratively build solutions. The stakes are too high to leave this endeavor to a small group of technologists alone.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ deba271e:36005655
2023-05-06 18:50:59
@ deba271e:36005655
2023-05-06 18:50:59(This is a repost from my original article for Stacker News)\n\nIs some specific website, like Twitter, bringing you joy or is it bringing you the opposite? Do you have a hard time stopping? Here's a quick tutorial recommended by 9 out 10 dentists. \n\nFirst rule: Never run random bash scripts you find online without reading the scripts yourself! \n\n---\n\n## Blocking with /etc/hosts\nIf you understand the first rule, then read, copypaste and run following script in your terminal. \n\nOn Linux or MacOS\n
shell\nsudo bash -c "cat >> /etc/hosts << EOF\n\n0.0.0.0 twitter.com\n0.0.0.0 reddit.com\nEOF\n"\n\nAnd that's it. This should apply the rule immediately. \nIf you want to check how does your/etc/hostslook like, then just runnano /etc/hosts.\n\nOn Windows\nbatch\necho 0.0.0.0 twitter.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\necho 0.0.0.0 reddit.com >> %WINDIR%\\System32\\Drivers\\Etc\\Hosts\n\n\n--- \n\n## Blocking with pi-hole\nEven better option is if you have pi-hole set up on your network to proxy all your DNS requests. If you didn't know pi-hole is also available on Umbrel or Citadel.\n\nSimple steps:\n1. Sign in to your your pi-hole admin interface, e.g. https://pi.hole/admin/index.php\n2. Navigate to Blacklist\n3. Addtwitter.comin the Domain input box and click on Add to Blacklist\n4. You are all set. -
 @ c9dccd5f:dce00d9a
2023-05-02 07:16:55
@ c9dccd5f:dce00d9a
2023-05-02 07:16:55Every fundamental particle carries an intrinsic angular momentum, which we call 'spin'. It is important to remember that this is an intrinsic quantum mechanical property of particles. There is no such thing as a spinning sphere in the classical sense. Nevertheless, the image of a spinning sphere is often a good analogue to understand what is going on.\n\n## Helicity\n\nThe helicity of a particle is the projection of its spin vector onto its linear momentum. In the spinning analogy, it is the relation of its spin direction to its direction of motion. The particle helicity is called either right-handed or left-handed. We say that the particle has right-handed helicity if the spin is aligned with the direction of motion, and left-handed helicity if the spin and motion have opposite orientations. In the spinning analogy, we can immediately understand where the names come from and what they mean. We look at your hands, make a fist and spread the thumbs. The thumbs indicate the direction of motion and the curled fingers indicate the direction of spin. We point our thumbs in the direction of motion and compare the fingers with the direction of spinning we see: If they are in the same direction as the right hand, we call it right-handed helicity, and conversely.\n\nSince massless particles (e.g. photons) travel at the speed of light, we will never find a reference frame in which this particle is at rest, i.e. we cannot find a rest frame. Therefore, the helicity will never change, since the spin is fixed and the direction of motion is the same in all reference frames.\n\nOn the other hand, massive particles travel at a speed less than that of light, so in principle we can find a rest frame. In fact, we can even find a reference frame in which the particle appears to be moving in the opposite direction. Yet the spin of a particle never changes. This leads to the fact that for massive particles the helicity can change because the direction of motion can be reversed, resulting in the opposite helicity. Note that this is not possible for massless particles, because we cannot move faster than them. \n\nThus we see that the mass of a particle tells us whether the helicity of a particle is an intrinsic property of the particle. For a massless particle, the helicity is fixed in all reference frames, whereas for a massive particle this is not the case, because different observers can infer different helicities for the same particle. \n\nAs physicists, we like to find fundamental properties of a particle. We therefore ask whether there is a related property to helicity that is intrinsic to particles. We call this fundamental property chirality.\n\n## Chirality\n\nChirality and helicity are closely related. Just as we say a particle has right-handed or left-handed helicity, we say a particle has right-handed or left-handed chirality. Sometimes we can drop the '-handed' and just say right-/left-helicity or right-/left-chirality. For massless particles, helicity and chirality are the same thing, so a right-chiral particle will also have right-helicity. For massive particles, however, helicity and chirality are different. A massive particle has a certain chirality but can have both helicity states, e.g. a right-chiral particle can have right or left helicity depending on the frame of reference. \n\nChirality is an abstract concept that refers to a fundamental intrinsic quantum mechanical property of a particle. However, a useful and nice visualisation can be made by looking at our hands. We hold our hand in front of us. The left and right hands are mirror images of each other. No matter how we rotate, flip or move one hand, it will never look exactly like the other hand. Our hands have different chirality.\n\nIn physics, particles with different chirality can be considered as completely different particles. It refers to how a particle's quantum mechanical wave function behaves under rotation. The quantum wave functions of left- and right-chiral particles behave differently under rotation.\n\nThe measurable physical effect of a particle's chirality can be seen in the theory of the weak interaction. The weak interaction only affects left-chiral particles and not right-chiral ones. As a result, neutrinos, which are weakly interacting particles, are only observed in left-handed chiral states.\n\n---\n\n_I hope this post has helped you understand the concept of helicity and chirality in physics. If anything is still unclear, or if an explanation could be improved to make it easier to understand, please comment or write to me. I am happy to answer. I'm looking forward to your feedback. PV_ 🤙\n\n---\n\n
v0 @ 785591; v1 @ 785712: fixed typos and added a missing sentence; v2 @ 787922: slight changes to the layout -
 @ 957966b6:2d4fe6b7
2023-08-02 01:55:36
@ 957966b6:2d4fe6b7
2023-08-02 01:55:36Paul, called to be an apostle of Jesus Christ through the will of God, and our brother Sosthenes, to the assembly of God which is at Corinth—those who are sanctified in Christ Jesus, called saints, with all who call on the name of our Lord Jesus Christ in every place, both theirs and ours: Grace to you and peace from God our Father and the Lord Jesus Christ.
I always thank my God concerning you for the grace of God which was given you in Christ Jesus, that in everything you were enriched in him, in all speech and all knowledge— even as the testimony of Christ was confirmed in you— so that you come behind in no gift, waiting for the revelation of our Lord Jesus Christ, who will also confirm you until the end, blameless in the day of our Lord Jesus Christ. God is faithful, through whom you were called into the fellowship of his Son, Jesus Christ our Lord.
Now I beg you, brothers, through the name of our Lord, Jesus Christ, that you all speak the same thing, and that there be no divisions among you, but that you be perfected together in the same mind and in the same judgment. For it has been reported to me concerning you, my brothers, by those who are from Chloe’s household, that there are contentions among you. Now I mean this, that each one of you says, “I follow Paul,” “I follow Apollos,” “I follow Cephas,” and, “I follow Christ.” Is Christ divided? Was Paul crucified for you? Or were you baptized into the name of Paul? I thank God that I baptized none of you except Crispus and Gaius, so that no one should say that I had baptized you into my own name. (I also baptized the household of Stephanas; besides them, I don’t know whether I baptized any other.) For Christ sent me not to baptize, but to preach the Good News—not in wisdom of words, so that the cross of Christ wouldn’t be made void. For the word of the cross is foolishness to those who are dying, but to us who are being saved it is the power of God. For it is written,
“I will destroy the wisdom of the wise.
I will bring the discernment of the discerning to nothing.”
Where is the wise? Where is the scribe? Where is the debater of this age? Hasn’t God made foolish the wisdom of this world? For seeing that in the wisdom of God, the world through its wisdom didn’t know God, it was God’s good pleasure through the foolishness of the preaching to save those who believe. For Jews ask for signs, Greeks seek after wisdom, but we preach Christ crucified, a stumbling block to Jews and foolishness to Greeks, but to those who are called, both Jews and Greeks, Christ is the power of God and the wisdom of God; because the foolishness of God is wiser than men, and the weakness of God is stronger than men.
For you see your calling, brothers, that not many are wise according to the flesh, not many mighty, and not many noble; but God chose the foolish things of the world that he might put to shame those who are wise. God chose the weak things of the world that he might put to shame the things that are strong. God chose the lowly things of the world, and the things that are despised, and the things that don’t exist, that he might bring to nothing the things that exist, that no flesh should boast before God. Because of him, you are in Christ Jesus, who was made to us wisdom from God, and righteousness and sanctification, and redemption, that, as it is written, “He who boasts, let him boast in the Lord.”
When I came to you, brothers, I didn’t come with excellence of speech or of wisdom, proclaiming to you the testimony of God. For I determined not to know anything among you except Jesus Christ and him crucified. I was with you in weakness, in fear, and in much trembling. My speech and my preaching were not in persuasive words of human wisdom, but in demonstration of the Spirit and of power, that your faith wouldn’t stand in the wisdom of men, but in the power of God.
We speak wisdom, however, among those who are full grown, yet a wisdom not of this world nor of the rulers of this world who are coming to nothing. But we speak God’s wisdom in a mystery, the wisdom that has been hidden, which God foreordained before the worlds for our glory, which none of the rulers of this world has known. For had they known it, they wouldn’t have crucified the Lord of glory. But as it is written,
“Things which an eye didn’t see, and an ear didn’t hear,
which didn’t enter into the heart of man,
these God has prepared for those who love him.”
But to us, God revealed them through the Spirit. For the Spirit searches all things, yes, the deep things of God. For who among men knows the things of a man except the spirit of the man which is in him? Even so, no one knows the things of God except God’s Spirit. But we received not the spirit of the world, but the Spirit which is from God, that we might know the things that were freely given to us by God. We also speak these things, not in words which man’s wisdom teaches but which the Holy Spirit teaches, comparing spiritual things with spiritual things. Now the natural man doesn’t receive the things of God’s Spirit, for they are foolishness to him; and he can’t know them, because they are spiritually discerned. But he who is spiritual discerns all things, and he himself is to be judged by no one. “For who has known the mind of the Lord that he should instruct him?” But we have Christ’s mind.
Brothers, I couldn’t speak to you as to spiritual, but as to fleshly, as to babies in Christ. I fed you with milk, not with solid food, for you weren’t yet ready. Indeed, you aren’t ready even now, for you are still fleshly. For insofar as there is jealousy, strife, and factions among you, aren’t you fleshly, and don’t you walk in the ways of men? For when one says, “I follow Paul,” and another, “I follow Apollos,” aren’t you fleshly?
Who then is Apollos, and who is Paul, but servants through whom you believed, and each as the Lord gave to him? I planted. Apollos watered. But God gave the increase. So then neither he who plants is anything, nor he who waters, but God who gives the increase. Now he who plants and he who waters are the same, but each will receive his own reward according to his own labor. For we are God’s fellow workers. You are God’s farming, God’s building.
According to the grace of God which was given to me, as a wise master builder I laid a foundation, and another builds on it. But let each man be careful how he builds on it. For no one can lay any other foundation than that which has been laid, which is Jesus Christ. But if anyone builds on the foundation with gold, silver, costly stones, wood, hay, or straw, each man’s work will be revealed. For the Day will declare it, because it is revealed in fire; and the fire itself will test what sort of work each man’s work is. If any man’s work remains which he built on it, he will receive a reward. If any man’s work is burned, he will suffer loss, but he himself will be saved, but as through fire.
Don’t you know that you are God’s temple and that God’s Spirit lives in you? If anyone destroys God’s temple, God will destroy him; for God’s temple is holy, which you are.
Let no one deceive himself. If anyone thinks that he is wise among you in this world, let him become a fool that he may become wise. For the wisdom of this world is foolishness with God. For it is written, “He has taken the wise in their craftiness.” And again, “The Lord knows the reasoning of the wise, that it is worthless.” Therefore let no one boast in men. For all things are yours, whether Paul, or Apollos, or Cephas, or the world, or life, or death, or things present, or things to come. All are yours, and you are Christ’s, and Christ is God’s.
So let a man think of us as Christ’s servants and stewards of God’s mysteries. Here, moreover, it is required of stewards that they be found faithful. But with me it is a very small thing that I should be judged by you, or by a human court. Yes, I don’t even judge my own self. For I know nothing against myself. Yet I am not justified by this, but he who judges me is the Lord. Therefore judge nothing before the time, until the Lord comes, who will both bring to light the hidden things of darkness and reveal the counsels of the hearts. Then each man will get his praise from God.
Now these things, brothers, I have in a figure transferred to myself and Apollos for your sakes, that in us you might learn not to think beyond the things which are written, that none of you be puffed up against one another. For who makes you different? And what do you have that you didn’t receive? But if you did receive it, why do you boast as if you had not received it?
You are already filled. You have already become rich. You have come to reign without us. Yes, and I wish that you did reign, that we also might reign with you! For I think that God has displayed us, the apostles, last of all, like men sentenced to death. For we are made a spectacle to the world, both to angels and men. We are fools for Christ’s sake, but you are wise in Christ. We are weak, but you are strong. You have honor, but we have dishonor. Even to this present hour we hunger, thirst, are naked, are beaten, and have no certain dwelling place. We toil, working with our own hands. When people curse us, we bless. Being persecuted, we endure. Being defamed, we entreat. We are made as the filth of the world, the dirt wiped off by all, even until now.
I don’t write these things to shame you, but to admonish you as my beloved children. For though you have ten thousand tutors in Christ, you don’t have many fathers. For in Christ Jesus, I became your father through the Good News. I beg you therefore, be imitators of me. Because of this I have sent Timothy to you, who is my beloved and faithful child in the Lord, who will remind you of my ways which are in Christ, even as I teach everywhere in every assembly. Now some are puffed up, as though I were not coming to you. But I will come to you shortly, if the Lord is willing. And I will know, not the word of those who are puffed up, but the power. For God’s Kingdom is not in word, but in power. What do you want? Shall I come to you with a rod, or in love and a spirit of gentleness?
It is actually reported that there is sexual immorality among you, and such sexual immorality as is not even named among the Gentiles, that one has his father’s wife. You are arrogant, and didn’t mourn instead, that he who had done this deed might be removed from among you. For I most certainly, as being absent in body but present in spirit, have already, as though I were present, judged him who has done this thing. In the name of our Lord Jesus Christ, when you are gathered together with my spirit with the power of our Lord Jesus Christ, you are to deliver such a one to Satan for the destruction of the flesh, that the spirit may be saved in the day of the Lord Jesus.
Your boasting is not good. Don’t you know that a little yeast leavens the whole lump? Purge out the old yeast, that you may be a new lump, even as you are unleavened. For indeed Christ, our Passover, has been sacrificed in our place. Therefore let’s keep the feast, not with old yeast, neither with the yeast of malice and wickedness, but with the unleavened bread of sincerity and truth.
I wrote to you in my letter to have no company with sexual sinners; yet not at all meaning with the sexual sinners of this world, or with the covetous and extortionists, or with idolaters, for then you would have to leave the world. But as it is, I wrote to you not to associate with anyone who is called a brother who is a sexual sinner, or covetous, or an idolater, or a slanderer, or a drunkard, or an extortionist. Don’t even eat with such a person. For what do I have to do with also judging those who are outside? Don’t you judge those who are within? But those who are outside, God judges. “Put away the wicked man from among yourselves.”
Dare any of you, having a matter against his neighbor, go to law before the unrighteous, and not before the saints? Don’t you know that the saints will judge the world? And if the world is judged by you, are you unworthy to judge the smallest matters? Don’t you know that we will judge angels? How much more, things that pertain to this life? If then you have to judge things pertaining to this life, do you set them to judge who are of no account in the assembly? I say this to move you to shame. Isn’t there even one wise man among you who would be able to decide between his brothers? But brother goes to law with brother, and that before unbelievers! Therefore it is already altogether a defect in you that you have lawsuits one with another. Why not rather be wronged? Why not rather be defrauded? No, but you yourselves do wrong and defraud, and that against your brothers.
Or don’t you know that the unrighteous will not inherit God’s Kingdom? Don’t be deceived. Neither the sexually immoral, nor idolaters, nor adulterers, nor male prostitutes, nor homosexuals, nor thieves, nor covetous, nor drunkards, nor slanderers, nor extortionists, will inherit God’s Kingdom. Some of you were such, but you were washed. You were sanctified. You were justified in the name of the Lord Jesus, and in the Spirit of our God.
“All things are lawful for me,” but not all things are expedient. “All things are lawful for me,” but I will not be brought under the power of anything. “Foods for the belly, and the belly for foods,” but God will bring to nothing both it and them. But the body is not for sexual immorality, but for the Lord, and the Lord for the body. Now God raised up the Lord, and will also raise us up by his power. Don’t you know that your bodies are members of Christ? Shall I then take the members of Christ and make them members of a prostitute? May it never be! Or don’t you know that he who is joined to a prostitute is one body? For, “The two”, he says, “will become one flesh.” But he who is joined to the Lord is one spirit. Flee sexual immorality! “Every sin that a man does is outside the body,” but he who commits sexual immorality sins against his own body. Or don’t you know that your body is a temple of the Holy Spirit who is in you, whom you have from God? You are not your own, for you were bought with a price. Therefore glorify God in your body and in your spirit, which are God’s.
Now concerning the things about which you wrote to me: it is good for a man not to touch a woman. But, because of sexual immoralities, let each man have his own wife, and let each woman have her own husband. Let the husband give his wife the affection owed her, and likewise also the wife her husband. The wife doesn’t have authority over her own body, but the husband does. Likewise also the husband doesn’t have authority over his own body, but the wife does. Don’t deprive one another, unless it is by consent for a season, that you may give yourselves to fasting and prayer, and may be together again, that Satan doesn’t tempt you because of your lack of self-control.
But this I say by way of concession, not of commandment. Yet I wish that all men were like me. However, each man has his own gift from God, one of this kind, and another of that kind. But I say to the unmarried and to widows, it is good for them if they remain even as I am. But if they don’t have self-control, let them marry. For it’s better to marry than to burn with passion. But to the married I command—not I, but the Lord—that the wife not leave her husband (but if she departs, let her remain unmarried, or else be reconciled to her husband), and that the husband not leave his wife.
But to the rest I—not the Lord—say, if any brother has an unbelieving wife, and she is content to live with him, let him not leave her. The woman who has an unbelieving husband, and he is content to live with her, let her not leave her husband. For the unbelieving husband is sanctified in the wife, and the unbelieving wife is sanctified in the husband. Otherwise your children would be unclean, but now they are holy. Yet if the unbeliever departs, let there be separation. The brother or the sister is not under bondage in such cases, but God has called us in peace. For how do you know, wife, whether you will save your husband? Or how do you know, husband, whether you will save your wife?
Only, as the Lord has distributed to each man, as God has called each, so let him walk. So I command in all the assemblies.
Was anyone called having been circumcised? Let him not become uncircumcised. Has anyone been called in uncircumcision? Let him not be circumcised. Circumcision is nothing, and uncircumcision is nothing, but what matters is keeping God’s commandments. Let each man stay in that calling in which he was called. Were you called being a bondservant? Don’t let that bother you, but if you get an opportunity to become free, use it. For he who was called in the Lord being a bondservant is the Lord’s free man. Likewise he who was called being free is Christ’s bondservant. You were bought with a price. Don’t become bondservants of men. Brothers, let each man, in whatever condition he was called, stay in that condition with God.
Now concerning virgins, I have no commandment from the Lord, but I give my judgment as one who has obtained mercy from the Lord to be trustworthy. Therefore I think that because of the distress that is on us, it’s good for a man to remain as he is. Are you bound to a wife? Don’t seek to be freed. Are you free from a wife? Don’t seek a wife. But if you marry, you have not sinned. If a virgin marries, she has not sinned. Yet such will have oppression in the flesh, and I want to spare you. But I say this, brothers: the time is short. From now on, both those who have wives may be as though they had none; and those who weep, as though they didn’t weep; and those who rejoice, as though they didn’t rejoice; and those who buy, as though they didn’t possess; and those who use the world, as not using it to the fullest. For the mode of this world passes away.
But I desire to have you to be free from cares. He who is unmarried is concerned for the things of the Lord, how he may please the Lord; but he who is married is concerned about the things of the world, how he may please his wife. There is also a difference between a wife and a virgin. The unmarried woman cares about the things of the Lord, that she may be holy both in body and in spirit. But she who is married cares about the things of the world—how she may please her husband. This I say for your own benefit, not that I may ensnare you, but for that which is appropriate, and that you may attend to the Lord without distraction.
But if any man thinks that he is behaving inappropriately toward his virgin, if she is past the flower of her age, and if need so requires, let him do what he desires. He doesn’t sin. Let them marry. But he who stands steadfast in his heart, having no urgency, but has power over his own will, and has determined in his own heart to keep his own virgin, does well. So then both he who gives his own virgin in marriage does well, and he who doesn’t give her in marriage does better.
A wife is bound by law for as long as her husband lives; but if the husband is dead, she is free to be married to whomever she desires, only in the Lord. But she is happier if she stays as she is, in my judgment, and I think that I also have God’s Spirit.
Now concerning things sacrificed to idols: We know that we all have knowledge. Knowledge puffs up, but love builds up. But if anyone thinks that he knows anything, he doesn’t yet know as he ought to know. But anyone who loves God is known by him.
Therefore concerning the eating of things sacrificed to idols, we know that no idol is anything in the world, and that there is no other God but one. For though there are things that are called “gods”, whether in the heavens or on earth—as there are many “gods” and many “lords”— yet to us there is one God, the Father, of whom are all things, and we for him; and one Lord, Jesus Christ, through whom are all things, and we live through him.
However, that knowledge isn’t in all men. But some, with consciousness of an idol until now, eat as of a thing sacrificed to an idol, and their conscience, being weak, is defiled. But food will not commend us to God. For neither, if we don’t eat are we the worse, nor if we eat are we the better. But be careful that by no means does this liberty of yours become a stumbling block to the weak. For if a man sees you who have knowledge sitting in an idol’s temple, won’t his conscience, if he is weak, be emboldened to eat things sacrificed to idols? And through your knowledge, he who is weak perishes, the brother for whose sake Christ died. Thus, sinning against the brothers, and wounding their conscience when it is weak, you sin against Christ. Therefore, if food causes my brother to stumble, I will eat no meat forever more, that I don’t cause my brother to stumble.
Am I not free? Am I not an apostle? Haven’t I seen Jesus Christ, our Lord? Aren’t you my work in the Lord? If to others I am not an apostle, yet at least I am to you; for you are the seal of my apostleship in the Lord.
My defense to those who examine me is this: Have we no right to eat and to drink? Have we no right to take along a wife who is a believer, even as the rest of the apostles, and the brothers of the Lord, and Cephas? Or have only Barnabas and I no right to not work? What soldier ever serves at his own expense? Who plants a vineyard, and doesn’t eat of its fruit? Or who feeds a flock, and doesn’t drink from the flock’s milk?
Do I speak these things according to the ways of men? Or doesn’t the law also say the same thing? For it is written in the law of Moses, “You shall not muzzle an ox while it treads out the grain.” Is it for the oxen that God cares, or does he say it assuredly for our sake? Yes, it was written for our sake, because he who plows ought to plow in hope, and he who threshes in hope should partake of his hope. If we sowed to you spiritual things, is it a great thing if we reap your fleshly things? If others partake of this right over you, don’t we yet more?
Nevertheless we didn’t use this right, but we bear all things, that we may cause no hindrance to the Good News of Christ. Don’t you know that those who serve around sacred things eat from the things of the temple, and those who wait on the altar have their portion with the altar? Even so the Lord ordained that those who proclaim the Good News should live from the Good News.
But I have used none of these things, and I don’t write these things that it may be done so in my case; for I would rather die, than that anyone should make my boasting void. For if I preach the Good News, I have nothing to boast about, for necessity is laid on me; but woe is to me if I don’t preach the Good News. For if I do this of my own will, I have a reward. But if not of my own will, I have a stewardship entrusted to me. What then is my reward? That when I preach the Good News, I may present the Good News of Christ without charge, so as not to abuse my authority in the Good News.
For though I was free from all, I brought myself under bondage to all, that I might gain the more. To the Jews I became as a Jew, that I might gain Jews; to those who are under the law, as under the law, that I might gain those who are under the law; to those who are without law, as without law (not being without law toward God, but under law toward Christ), that I might win those who are without law. To the weak I became as weak, that I might gain the weak. I have become all things to all men, that I may by all means save some. Now I do this for the sake of the Good News, that I may be a joint partaker of it. Don’t you know that those who run in a race all run, but one receives the prize? Run like that, so that you may win. Every man who strives in the games exercises self-control in all things. Now they do it to receive a corruptible crown, but we an incorruptible. I therefore run like that, not aimlessly. I fight like that, not beating the air, but I beat my body and bring it into submission, lest by any means, after I have preached to others, I myself should be disqualified.
Now I would not have you ignorant, brothers, that our fathers were all under the cloud, and all passed through the sea; and were all baptized into Moses in the cloud and in the sea; and all ate the same spiritual food; and all drank the same spiritual drink. For they drank of a spiritual rock that followed them, and the rock was Christ. However with most of them, God was not well pleased, for they were overthrown in the wilderness.
Now these things were our examples, to the intent we should not lust after evil things as they also lusted. Don’t be idolaters, as some of them were. As it is written, “The people sat down to eat and drink, and rose up to play.” Let’s not commit sexual immorality, as some of them committed, and in one day twenty-three thousand fell. Let’s not test Christ, as some of them tested, and perished by the serpents. Don’t grumble, as some of them also grumbled, and perished by the destroyer. Now all these things happened to them by way of example, and they were written for our admonition, on whom the ends of the ages have come. Therefore let him who thinks he stands be careful that he doesn’t fall.
No temptation has taken you except what is common to man. God is faithful, who will not allow you to be tempted above what you are able, but will with the temptation also make the way of escape, that you may be able to endure it.
Therefore, my beloved, flee from idolatry. I speak as to wise men. Judge what I say. The cup of blessing which we bless, isn’t it a sharing of the blood of Christ? The bread which we break, isn’t it a sharing of the body of Christ? Because there is one loaf of bread, we, who are many, are one body; for we all partake of the one loaf of bread. Consider Israel according to the flesh. Don’t those who eat the sacrifices participate in the altar?
What am I saying then? That a thing sacrificed to idols is anything, or that an idol is anything? But I say that the things which the Gentiles sacrifice, they sacrifice to demons and not to God, and I don’t desire that you would have fellowship with demons. You can’t both drink the cup of the Lord and the cup of demons. You can’t both partake of the table of the Lord and of the table of demons. Or do we provoke the Lord to jealousy? Are we stronger than he?
“All things are lawful for me,” but not all things are profitable. “All things are lawful for me,” but not all things build up. Let no one seek his own, but each one his neighbor’s good. Whatever is sold in the butcher shop, eat, asking no question for the sake of conscience, for “the earth is the Lord’s, and its fullness.” But if one of those who don’t believe invites you to a meal, and you are inclined to go, eat whatever is set before you, asking no questions for the sake of conscience. But if anyone says to you, “This was offered to idols,” don’t eat it for the sake of the one who told you, and for the sake of conscience. For “the earth is the Lord’s, with all its fullness.” Conscience, I say, not your own, but the other’s conscience. For why is my liberty judged by another conscience? If I partake with thankfulness, why am I denounced for something I give thanks for?
Whether therefore you eat or drink, or whatever you do, do all to the glory of God. Give no occasion for stumbling, whether to Jews, to Greeks, or to the assembly of God; even as I also please all men in all things, not seeking my own profit, but the profit of the many, that they may be saved.
Be imitators of me, even as I also am of Christ.
Now I praise you, brothers, that you remember me in all things, and hold firm the traditions, even as I delivered them to you. But I would have you know that the head of every man is Christ, and the head of the woman is man, and the head of Christ is God. Every man praying or prophesying, having his head covered, dishonors his head. But every woman praying or prophesying with her head uncovered dishonors her head. For it is one and the same thing as if she were shaved. For if a woman is not covered, let her hair also be cut off. But if it is shameful for a woman to have her hair cut off or be shaved, let her be covered. For a man indeed ought not to have his head covered, because he is the image and glory of God, but the woman is the glory of the man. For man is not from woman, but woman from man; for man wasn’t created for the woman, but woman for the man. For this cause the woman ought to have authority over her own head, because of the angels.
Nevertheless, neither is the woman independent of the man, nor the man independent of the woman, in the Lord. For as woman came from man, so a man also comes through a woman; but all things are from God. Judge for yourselves. Is it appropriate that a woman pray to God unveiled? Doesn’t even nature itself teach you that if a man has long hair, it is a dishonor to him? But if a woman has long hair, it is a glory to her, for her hair is given to her for a covering. But if any man seems to be contentious, we have no such custom, neither do God’s assemblies.
But in giving you this command I don’t praise you, because you come together not for the better but for the worse. For first of all, when you come together in the assembly, I hear that divisions exist among you, and I partly believe it. For there also must be factions among you, that those who are approved may be revealed among you. When therefore you assemble yourselves together, it is not the Lord’s supper that you eat. For in your eating each one takes his own supper first. One is hungry, and another is drunken. What, don’t you have houses to eat and to drink in? Or do you despise God’s assembly and put them to shame who don’t have enough? What shall I tell you? Shall I praise you? In this I don’t praise you.
For I received from the Lord that which also I delivered to you, that the Lord Jesus on the night in which he was betrayed took bread. When he had given thanks, he broke it and said, “Take, eat. This is my body, which is broken for you. Do this in memory of me.” In the same way he also took the cup after supper, saying, “This cup is the new covenant in my blood. Do this, as often as you drink, in memory of me.” For as often as you eat this bread and drink this cup, you proclaim the Lord’s death until he comes.
Therefore whoever eats this bread or drinks the Lord’s cup in a way unworthy of the Lord will be guilty of the body and the blood of the Lord. But let a man examine himself, and so let him eat of the bread and drink of the cup. For he who eats and drinks in an unworthy way eats and drinks judgment to himself if he doesn’t discern the Lord’s body. For this cause many among you are weak and sickly, and not a few sleep. For if we discerned ourselves, we wouldn’t be judged. But when we are judged, we are disciplined by the Lord, that we may not be condemned with the world. Therefore, my brothers, when you come together to eat, wait for one another. But if anyone is hungry, let him eat at home, lest your coming together be for judgment. The rest I will set in order whenever I come.
Now concerning spiritual things, brothers, I don’t want you to be ignorant. You know that when you were heathen, you were led away to those mute idols, however you might be led. Therefore I make known to you that no man speaking by God’s Spirit says, “Jesus is accursed.” No one can say, “Jesus is Lord,” but by the Holy Spirit.
Now there are various kinds of gifts, but the same Spirit. There are various kinds of service, and the same Lord. There are various kinds of workings, but the same God who works all things in all. But to each one is given the manifestation of the Spirit for the profit of all. For to one is given through the Spirit the word of wisdom, and to another the word of knowledge according to the same Spirit, to another faith by the same Spirit, and to another gifts of healings by the same Spirit, and to another workings of miracles, and to another prophecy, and to another discerning of spirits, to another different kinds of languages, and to another the interpretation of languages. But the one and the same Spirit produces all of these, distributing to each one separately as he desires.
For as the body is one and has many members, and all the members of the body, being many, are one body; so also is Christ. For in one Spirit we were all baptized into one body, whether Jews or Greeks, whether bond or free; and were all given to drink into one Spirit.
For the body is not one member, but many. If the foot would say, “Because I’m not the hand, I’m not part of the body,” it is not therefore not part of the body. If the ear would say, “Because I’m not the eye, I’m not part of the body,” it’s not therefore not part of the body. If the whole body were an eye, where would the hearing be? If the whole were hearing, where would the smelling be? But now God has set the members, each one of them, in the body, just as he desired. If they were all one member, where would the body be? But now they are many members, but one body. The eye can’t tell the hand, “I have no need for you,” or again the head to the feet, “I have no need for you.” No, much rather, those members of the body which seem to be weaker are necessary. Those parts of the body which we think to be less honorable, on those we bestow more abundant honor; and our unpresentable parts have more abundant modesty, while our presentable parts have no such need. But God composed the body together, giving more abundant honor to the inferior part, that there should be no division in the body, but that the members should have the same care for one another. When one member suffers, all the members suffer with it. When one member is honored, all the members rejoice with it.
Now you are the body of Christ, and members individually. God has set some in the assembly: first apostles, second prophets, third teachers, then miracle workers, then gifts of healings, helps, governments, and various kinds of languages. Are all apostles? Are all prophets? Are all teachers? Are all miracle workers? Do all have gifts of healings? Do all speak with various languages? Do all interpret? But earnestly desire the best gifts. Moreover, I show a most excellent way to you.
If I speak with the languages of men and of angels, but don’t have love, I have become sounding brass or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge, and if I have all faith, so as to remove mountains, but don’t have love, I am nothing. If I give away all my goods to feed the poor, and if I give my body to be burned, but don’t have love, it profits me nothing.
Love is patient and is kind. Love doesn’t envy. Love doesn’t brag, is not proud, doesn’t behave itself inappropriately, doesn’t seek its own way, is not provoked, takes no account of evil; doesn’t rejoice in unrighteousness, but rejoices with the truth; bears all things, believes all things, hopes all things, and endures all things.
Love never fails. But where there are prophecies, they will be done away with. Where there are various languages, they will cease. Where there is knowledge, it will be done away with. For we know in part and we prophesy in part; but when that which is complete has come, then that which is partial will be done away with. When I was a child, I spoke as a child, I felt as a child, I thought as a child. Now that I have become a man, I have put away childish things. For now we see in a mirror, dimly, but then face to face. Now I know in part, but then I will know fully, even as I was also fully known. But now faith, hope, and love remain—these three. The greatest of these is love.
Follow after love and earnestly desire spiritual gifts, but especially that you may prophesy. For he who speaks in another language speaks not to men, but to God, for no one understands, but in the Spirit he speaks mysteries. But he who prophesies speaks to men for their edification, exhortation, and consolation. He who speaks in another language edifies himself, but he who prophesies edifies the assembly. Now I desire to have you all speak with other languages, but even more that you would prophesy. For he is greater who prophesies than he who speaks with other languages, unless he interprets, that the assembly may be built up.
But now, brothers, if I come to you speaking with other languages, what would I profit you unless I speak to you either by way of revelation, or of knowledge, or of prophesying, or of teaching? Even lifeless things that make a sound, whether pipe or harp, if they didn’t give a distinction in the sounds, how would it be known what is piped or harped? For if the trumpet gave an uncertain sound, who would prepare himself for war? So also you, unless you uttered by the tongue words easy to understand, how would it be known what is spoken? For you would be speaking into the air. There are, it may be, so many kinds of languages in the world, and none of them is without meaning. If then I don’t know the meaning of the language, I would be to him who speaks a foreigner, and he who speaks would be a foreigner to me. So also you, since you are zealous for spiritual gifts, seek that you may abound to the building up of the assembly.
Therefore let him who speaks in another language pray that he may interpret. For if I pray in another language, my spirit prays, but my understanding is unfruitful.
What should I do? I will pray with the spirit, and I will pray with the understanding also. I will sing with the spirit, and I will sing with the understanding also. Otherwise, if you bless with the spirit, how will he who fills the place of the unlearned say the “Amen” at your giving of thanks, seeing he doesn’t know what you say? For you most certainly give thanks well, but the other person is not built up. I thank my God, I speak with other languages more than you all. However, in the assembly I would rather speak five words with my understanding, that I might instruct others also, than ten thousand words in another language.
Brothers, don’t be children in thoughts, yet in malice be babies, but in thoughts be mature. In the law it is written, “By men of strange languages and by the lips of strangers I will speak to this people. They won’t even listen to me that way, says the Lord.” Therefore other languages are for a sign, not to those who believe, but to the unbelieving; but prophesying is for a sign, not to the unbelieving, but to those who believe. If therefore the whole assembly is assembled together and all speak with other languages, and unlearned or unbelieving people come in, won’t they say that you are crazy? But if all prophesy, and someone unbelieving or unlearned comes in, he is reproved by all, and he is judged by all. And thus the secrets of his heart are revealed. So he will fall down on his face and worship God, declaring that God is among you indeed.
What is it then, brothers? When you come together, each one of you has a psalm, has a teaching, has a revelation, has another language, or has an interpretation. Let all things be done to build each other up. If any man speaks in another language, let there be two, or at the most three, and in turn; and let one interpret. But if there is no interpreter, let him keep silent in the assembly, and let him speak to himself and to God. Let two or three of the prophets speak, and let the others discern. But if a revelation is made to another sitting by, let the first keep silent. For you all can prophesy one by one, that all may learn and all may be exhorted. The spirits of the prophets are subject to the prophets, for God is not a God of confusion but of peace, as in all the assemblies of the saints. Let the wives be quiet in the assemblies, for it has not been permitted for them to be talking except in submission, as the law also says, if they desire to learn anything. “Let them ask their own husbands at home, for it is shameful for a wife to be talking in the assembly.” What!? Was it from you that the word of God went out? Or did it come to you alone?
If any man thinks himself to be a prophet or spiritual, let him recognize the things which I write to you, that they are the commandment of the Lord. But if anyone is ignorant, let him be ignorant.
Therefore, brothers, desire earnestly to prophesy, and don’t forbid speaking with other languages. Let all things be done decently and in order.
Now I declare to you, brothers, the Good News which I preached to you, which also you received, in which you also stand, by which also you are saved, if you hold firmly the word which I preached to you—unless you believed in vain.
For I delivered to you first of all that which I also received: that Christ died for our sins according to the Scriptures, that he was buried, that he was raised on the third day according to the Scriptures, and that he appeared to Cephas, then to the twelve. Then he appeared to over five hundred brothers at once, most of whom remain until now, but some have also fallen asleep. Then he appeared to James, then to all the apostles, and last of all, as to the child born at the wrong time, he appeared to me also. For I am the least of the apostles, who is not worthy to be called an apostle, because I persecuted the assembly of God. But by the grace of God I am what I am. His grace which was given to me was not futile, but I worked more than all of them; yet not I, but the grace of God which was with me. Whether then it is I or they, so we preach, and so you believed.
Now if Christ is preached, that he has been raised from the dead, how do some among you say that there is no resurrection of the dead? But if there is no resurrection of the dead, neither has Christ been raised. If Christ has not been raised, then our preaching is in vain and your faith also is in vain. Yes, we are also found false witnesses of God, because we testified about God that he raised up Christ, whom he didn’t raise up if it is true that the dead are not raised. For if the dead aren’t raised, neither has Christ been raised. If Christ has not been raised, your faith is vain; you are still in your sins. Then they also who are fallen asleep in Christ have perished. If we have only hoped in Christ in this life, we are of all men most pitiable.
But now Christ has been raised from the dead. He became the first fruit of those who are asleep. For since death came by man, the resurrection of the dead also came by man. For as in Adam all die, so also in Christ all will be made alive. But each in his own order: Christ the first fruits, then those who are Christ’s at his coming. Then the end comes, when he will deliver up the Kingdom to God the Father, when he will have abolished all rule and all authority and power. For he must reign until he has put all his enemies under his feet. The last enemy that will be abolished is death. For, “He put all things in subjection under his feet.” But when he says, “All things are put in subjection”, it is evident that he is excepted who subjected all things to him. When all things have been subjected to him, then the Son will also himself be subjected to him who subjected all things to him, that God may be all in all.
Or else what will they do who are baptized for the dead? If the dead aren’t raised at all, why then are they baptized for the dead? Why do we also stand in jeopardy every hour? I affirm, by the boasting in you which I have in Christ Jesus our Lord, I die daily. If I fought with animals at Ephesus for human purposes, what does it profit me? If the dead are not raised, then “let’s eat and drink, for tomorrow we die.” Don’t be deceived! “Evil companionships corrupt good morals.” Wake up righteously and don’t sin, for some have no knowledge of God. I say this to your shame.
But someone will say, “How are the dead raised?” and, “With what kind of body do they come?” You foolish one, that which you yourself sow is not made alive unless it dies. That which you sow, you don’t sow the body that will be, but a bare grain, maybe of wheat, or of some other kind. But God gives it a body even as it pleased him, and to each seed a body of its own. All flesh is not the same flesh, but there is one flesh of men, another flesh of animals, another of fish, and another of birds. There are also celestial bodies and terrestrial bodies; but the glory of the celestial differs from that of the terrestrial. There is one glory of the sun, another glory of the moon, and another glory of the stars; for one star differs from another star in glory.
So also is the resurrection of the dead. The body is sown perishable; it is raised imperishable. It is sown in dishonor; it is raised in glory. It is sown in weakness; it is raised in power. It is sown a natural body; it is raised a spiritual body. There is a natural body and there is also a spiritual body.
So also it is written, “The first man Adam became a living soul.” The last Adam became a life-giving spirit. However, that which is spiritual isn’t first, but that which is natural, then that which is spiritual. The first man is of the earth, made of dust. The second man is the Lord from heaven. As is the one made of dust, such are those who are also made of dust; and as is the heavenly, such are they also that are heavenly. As we have borne the image of those made of dust, let’s also bear the image of the heavenly. Now I say this, brothers, that flesh and blood can’t inherit God’s Kingdom; neither does the perishable inherit imperishable.
Behold, I tell you a mystery. We will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet. For the trumpet will sound and the dead will be raised incorruptible, and we will be changed. For this perishable body must become imperishable, and this mortal must put on immortality. But when this perishable body will have become imperishable, and this mortal will have put on immortality, then what is written will happen: “Death is swallowed up in victory.”
“Death, where is your sting?
Hades, where is your victory?”
The sting of death is sin, and the power of sin is the law. But thanks be to God, who gives us the victory through our Lord Jesus Christ. Therefore, my beloved brothers, be steadfast, immovable, always abounding in the Lord’s work, because you know that your labor is not in vain in the Lord.
Now concerning the collection for the saints: as I commanded the assemblies of Galatia, you do likewise. On the first day of every week, let each one of you save as he may prosper, that no collections are made when I come. When I arrive, I will send whoever you approve with letters to carry your gracious gift to Jerusalem. If it is appropriate for me to go also, they will go with me.
I will come to you when I have passed through Macedonia, for I am passing through Macedonia. But with you it may be that I will stay with you, or even winter with you, that you may send me on my journey wherever I go. For I do not wish to see you now in passing, but I hope to stay a while with you, if the Lord permits. But I will stay at Ephesus until Pentecost, for a great and effective door has opened to me, and there are many adversaries.
Now if Timothy comes, see that he is with you without fear, for he does the work of the Lord, as I also do. Therefore let no one despise him. But set him forward on his journey in peace, that he may come to me; for I expect him with the brothers.
Now concerning Apollos the brother, I strongly urged him to come to you with the brothers, but it was not at all his desire to come now; but he will come when he has an opportunity.
Watch! Stand firm in the faith! Be courageous! Be strong! Let all that you do be done in love.
Now I beg you, brothers—you know the house of Stephanas, that it is the first fruits of Achaia, and that they have set themselves to serve the saints— that you also be in subjection to such, and to everyone who helps in the work and labors. I rejoice at the coming of Stephanas, Fortunatus, and Achaicus; for that which was lacking on your part, they supplied. For they refreshed my spirit and yours. Therefore acknowledge those who are like that.
The assemblies of Asia greet you. Aquila and Priscilla greet you warmly in the Lord, together with the assembly that is in their house. All the brothers greet you. Greet one another with a holy kiss.
This greeting is by me, Paul, with my own hand. If any man doesn’t love the Lord Jesus Christ, let him be cursed. Come, Lord! The grace of the Lord Jesus Christ be with you. My love to all of you in Christ Jesus. Amen.
The World English Bible is in the Public Domain. That means that it is not copyrighted. However, "World English Bible" is a Trademark of eBible.org.
-
 @ 5e5fc143:393d5a2c
2023-04-15 17:18:11
@ 5e5fc143:393d5a2c
2023-04-15 17:18:11\nJust revisiting some quick tips for #newbies #pow #public #blockchain users only.\n\nif you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.\n\nHot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process\n\nCold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts\nPaper wallets are best n cheapest form of cold wallet that can used once n thrown away.\n\n#Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/\n\n\n
 \n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n
\n\nAny thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.\n\nBeginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet\n\nAlmost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value\n\nYou can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !\n\nAlways delete hot wallet to test practice restoration before sending any large refunds to it to be safe. \n\nLarge funds are always best to keep in self custody node wallets rare n occasional use\n\nFinal word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲\n\nThat’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️\n\n\nSome Cold wallet nostr posts\nnostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2\nnostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw\nnostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q\n\nsome nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option\nnostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8\nrelated blog post \nnostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87\n\n -
 @ d266da53:7224d834
2023-08-04 08:35:01
@ d266da53:7224d834
2023-08-04 08:35:01Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.
 Cosmos was once the king of interoperability thanks to its revolutionary Tendermint consensus mechanism and Inter-Blockchain Communication (IBC) standard. However, several years after its release, the Cosmos ecosystem has grown without needing the ATOM token. Let’s analyze the value proposition of ATOM, its newfound competitor Ethereum, and if the Cosmos ecosystem has a chance of ever taking off.
Cosmos was once the king of interoperability thanks to its revolutionary Tendermint consensus mechanism and Inter-Blockchain Communication (IBC) standard. However, several years after its release, the Cosmos ecosystem has grown without needing the ATOM token. Let’s analyze the value proposition of ATOM, its newfound competitor Ethereum, and if the Cosmos ecosystem has a chance of ever taking off.Cosmos was founded in 2016 by Jae Kwon and Ethan Buchman. They were part of the Tendermint team, which developed a software development kit that provides the core functionality of a blockchain, such as consensus and networking. The Cosmos SDK utilized Tendermint to create a modular framework that allows developers to build their blockchains with custom features and applications without starting from scratch. The SDK’s standardization also enables cross-chain communication through the Inter-Blockchain Communication (IBC) protocol, which allows different blockchains to transfer tokens and data with each other.
 Initially, the value proposition for the Cosmos blockchain and its ATOM token was that it would be the hub in a hub-and-spoke blockchain model. Whenever a Cosmos SDK or IBC-enabled chain, called a Zone, transferred tokens to another Zone, they would use Cosmos as the bridge and pay fees in ATOM. At first glance, this proposition made a lot of sense, as it would allow Cosmos to be the secure bridge between the Zones and collect value in that manner.
Initially, the value proposition for the Cosmos blockchain and its ATOM token was that it would be the hub in a hub-and-spoke blockchain model. Whenever a Cosmos SDK or IBC-enabled chain, called a Zone, transferred tokens to another Zone, they would use Cosmos as the bridge and pay fees in ATOM. At first glance, this proposition made a lot of sense, as it would allow Cosmos to be the secure bridge between the Zones and collect value in that manner. Unfortunately, as the number of Cosmos SDK-based chains grew, the hype and value of ATOM did not follow. Some prominent projects like Binance Chain, Crypto.com, and the now-infamous Terra were built using Cosmos and Tendermint technology and dwarfed ATOM in market capitalization. Binance did not even bother integrating with the IBC and instead used Tendermint solely as the consensus mechanism. The growth of these chains had little-to-no effect on Cosmos. Yet other Zones, including Kava, Band Protocol, Evmos, and Injective, joined the ecosystem, and there was still hope for Cosmos to succeed.
Unfortunately, as the number of Cosmos SDK-based chains grew, the hype and value of ATOM did not follow. Some prominent projects like Binance Chain, Crypto.com, and the now-infamous Terra were built using Cosmos and Tendermint technology and dwarfed ATOM in market capitalization. Binance did not even bother integrating with the IBC and instead used Tendermint solely as the consensus mechanism. The growth of these chains had little-to-no effect on Cosmos. Yet other Zones, including Kava, Band Protocol, Evmos, and Injective, joined the ecosystem, and there was still hope for Cosmos to succeed.When the Osmosis Zone was released in 2021, it was initially meant to be the decentralized exchange of the IBC. Naturally, this brought a lot of liquidity and volume to the chain, quickly becoming the de facto hub of activity in the Cosmos ecosystem. Since there was no strict requirement for bridging using Cosmos, Osmosis promptly became the hub of the ecosystem and inspired the idea of Zones simply bridging to other Zones instead of going through a hub. This realization created the staus quo we see today, where Cosmos, the project that made the majority of the technology, does not receive any benefits from the plethora of chains using it.
 In an attempt to regain a value proposition in its ecosystem, ATOM 2.0 was announced in late 2022. The main feature of these new tokenomics is the creation of InterChain Security, meaning that new projects can “rent” security from ATOM by paying in the chain’s native token. This allows new projects not to worry about building a decentralized network, as they can rely on the time-tested network of ATOM validators while still having the sovereignty of their own chain.
In an attempt to regain a value proposition in its ecosystem, ATOM 2.0 was announced in late 2022. The main feature of these new tokenomics is the creation of InterChain Security, meaning that new projects can “rent” security from ATOM by paying in the chain’s native token. This allows new projects not to worry about building a decentralized network, as they can rely on the time-tested network of ATOM validators while still having the sovereignty of their own chain. Though this idea is exciting and novel, it has a massive new competitor: Ethereum. Indeed, the once-monolithic smart contract protocol has increasingly become more of a data availability layer than a compute engine, as Layer 2s execute computations off-chain and store the associated data on Ethereum. Even Solana, a competitor to Ethereum, announced plans to use it as their data availability layer to improve interoperability between the two chains and take advantage of the Ethereum network and security effects. This trend and the ability to easily create Layer 3s using Optimism and Arbitrum’s tooling directly challenge Cosmos’ ICS plans.
Though this idea is exciting and novel, it has a massive new competitor: Ethereum. Indeed, the once-monolithic smart contract protocol has increasingly become more of a data availability layer than a compute engine, as Layer 2s execute computations off-chain and store the associated data on Ethereum. Even Solana, a competitor to Ethereum, announced plans to use it as their data availability layer to improve interoperability between the two chains and take advantage of the Ethereum network and security effects. This trend and the ability to easily create Layer 3s using Optimism and Arbitrum’s tooling directly challenge Cosmos’ ICS plans.The future of Cosmos has never looked more uncertain. Even though Tendermind and IBC are revolutionary technologies that are the backbone of billions of dollars in blockchain value, Cosmos’ initial tokenomics failed to capitalize on its creation. The proliferation of ICS could bring more value back to Cosmos, yet many app-chains will likely choose Ethereum due to its significantly larger user base and liquidity potential. Though this is not financial advice and is merely for education, it makes much more sense to hold Cosmos than to buy it. On the other hand, for those who believe in the potential of ICS and the value of IBC, this could be a great buying opportunity for ATOM and other Cosmos ecosystem chains.
By:Lincoln Murr Link:https://bitpushnews.medium.com/is-cosmos-a-dying-blockchain-a0c308af0dac
-
 @ 5ada3677:7c21c9db
2023-08-01 17:44:41
@ 5ada3677:7c21c9db
2023-08-01 17:44:41 小男生一身衣服配色,完全是教科書級別的。腳上一雙飛躍跑鞋。
小男生一身衣服配色,完全是教科書級別的。腳上一雙飛躍跑鞋。Bilbao跟很多歐洲城市一樣,禮拜天全城閉門打烊,除了一部分餐館之外。開始時候覺得有點不習慣,似乎頗不方便,買瓶牛奶都休想的樣子。漸漸覺得如此真好,好在非常清靜,整座城市安安靜靜,街頭幾乎沒有人,每週一次如此的清靜,太好了。另一個好,是禮拜天大家都在家裡了,古老而溫暖,多麼好。


對面房子的老爺叔,每個禮拜天的清晨,開著燦爛輝煌的歌劇詠嘆調,拿著雪白的大毛巾擦玻璃窗。因為街上太靜了,他的詠嘆調清清楚楚地隔街傳過來,我坐在陽台上飲碧螺春,真是天籟一般。此地有南美移民的女傭,上門幫忙打理家務,頗普遍,這位鄰居老爺叔親力親為,包子說,是我學習的好榜樣。
另一側的鄰居也是老爺叔,中午搬出午餐在陽台上吃,一個人有滋有味飲湯,是番茄冷湯吧我猜的,西班牙人的可以喝的色拉,然後還有一份外國報紙,厚厚的週末版,在桌上。報紙是西班牙的、還是外國的,一眼就分出來了。Bilbao小城,滿街的書報亭,天天都買得到紐/約/時/報和金融/時/報。上海是五星酒店也覓不到外/國/報紙的。


禮拜天,清晨晃去老城吃個早餐,順手買些麵包回家,老城裡比較多老而好的麵包舖子。
老城裡遊客散落,德國人荷蘭人,大多是一家人出來過暑假,父母帶兩三個孩子,或者退休老夫妻,基本是如此配置。
走兩步,結果沒有進麵包舖、也沒有進早餐小館子,而是先進了舊書店。舊書店裡鋪了滿地的老地毯,音樂很對頭,鬆軟宜人,濃濃的。這家店裡很多1850年左右的植物畫和動物畫,精得不得了,一頁一頁,看了個飽。還有銅版畫,更精,揀了兩幅。
角落裡翻到一冊美食指南之類的,1995年出版的,有趣的是,書的舊主人,真的拿著這冊書,當聖經一樣去覓美食,書裡留著很多筆記、剪報、菜單、發票,蹲在角落裡,默默翻了一遍,非常有味道,雖然我完全看不懂西班牙文。


去買麵包,小麵包舖頗多,最好的那間,走過去的時候,已經"今日售罄明日請早",當時還沒到中午12點。只好掉頭換一間,問包子去哪間,包子說,看看本地老太太去哪間、我們跟著去。結果跟著本地老太太,進了一家1983年的麵包舖子,買到很稱心的法棍,40年半老之店,生意興隆,需要稍稍排一點隊。




隨便一間咖啡館小酒吧,1850年的
這個禮拜天,在家聽了很多包子的音樂,從非洲馬里人的音樂、非洲尼日利亞的音樂,到土耳其音樂、古巴音樂,還在安達魯西亞的電台上,聽了久久的佛萊明戈音樂,無伴奏的佛萊明戈詠唱,絕美絕贊,跟信天游有很多異曲同工。我把網址留在下面,希望各位也能enjoy。
這個禮拜天,洗了床單、燉了桃膠,學著做了兩道巴斯克料理,讀完了一本中文書茨威格的《昨日的世界》和一本英文書《Basque Country》。
安靜的禮拜天。

 買了麵包出來,剛好遇見工人們在搬運麵粉
買了麵包出來,剛好遇見工人們在搬運麵粉佛萊明戈音樂在這裡


夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs -
 @ 35a8f9c0:351dae66
2023-08-04 07:36:31
@ 35a8f9c0:351dae66
2023-08-04 07:36:31test
-
 @ ba680951:ec182a0e
2023-08-01 16:47:58
@ ba680951:ec182a0e
2023-08-01 16:47:58FOMCの最新のミーティング
米国連邦公開市場委員会(FOMC)の最新のミーティングで、金利が0.25ポイント上昇しました。市場はこの結果を予期していました。
金利の動向
昨日、米国の金利を決定するFOMCのもう一つのミーティングが開催されました。市場は利上げを既に予想しており、下のグラフからわかるように、最も可能性の高いのは0.25ポイントの利上げで、これにより金利が年率5.25%から5.50%の範囲になると見られていました。
次に何が起こるのか?
経済活動のデータは引き続き強いままであり、雇用の増加、失業率の低下、インフレ率が目標を上回るなど、6月に公表されたデータではCore CPIが4.8%となっています。昨日のスピーチで、アメリカの中央銀行の議長であるジェローム・パウエルは、FEDが次回のFOMCの決定を予測する立場にないことを強調しました。全ては経済データの動向次第です。
Conclusion
それでも、一つは明らかです。もしCore CPIが高水準であれば、つまり、インフレが明らかに緩和の兆しを見せない場合、金利が再び上昇する可能性が高いです。これは、市場が金利の上昇を織り込み始める可能性があるため、これらのデータの公表日(8月10日)に価格に影響を与える可能性があります。
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0\n\nThe web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".\n\nThe first version added hyperlinks to existing browser technology. Bundled together were:\n\n- HTTP and the first server\n- the first web browser, which was also an editor\n- HTML which was based on SGML\n\nImportantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.\n\nWeb 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.\n\nHTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.\n\n
 \n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n
\n\n\n## Web 2.0\n\nAs the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.\n\nWithout editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates. \n\nThis system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.\n\nWith the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.\n\n\n\n## Web 3.0\n\nWeb 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.\n\nThe was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.\n\nBerners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"\n\nThe full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.\n\nA note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:\n\nhttps://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html\n\n
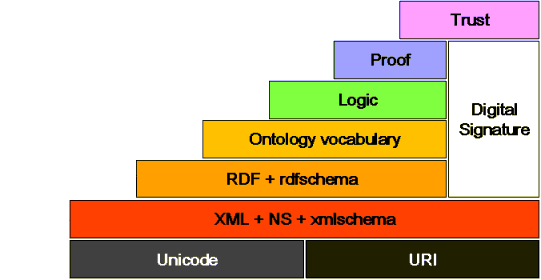 \n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n
\n\n## Towards Web 4.0\n\nThe first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:\n\nhttps://lists.w3.org/Archives/Public/public-rww/2021May/0006.html\n\nA significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.\n\nThese two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.\n\n \n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n
\n\n## Web 5.0\n\nWhat web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.\n\nOne guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.\n\nA note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.\n\nIMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.\n\n \n\nOpinions are the views of the author
\n\nOpinions are the views of the author -
 @ 49edd28f:90fb6d51
2021-11-07 16:58:53
@ 49edd28f:90fb6d51
2021-11-07 16:58:53We Went Back #1\n\n\n\nhttps://www.youtube.com/watch?v=sxj1H86J88U
-
 @ 7f5c2b4e:a818d75d
2023-08-04 07:25:45
@ 7f5c2b4e:a818d75d
2023-08-04 07:25:45この記事は nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0 によって、日本語訳されました。
この記事は以下の言語でもご覧になれます:
- 英語:nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6
- フランス語:nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- 中国語:nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme thanks to nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- スウェーデン語:nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 thanks to nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- スペイン語:nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- オランダ語:nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx thanks to nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- アラビア語:nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s thanks to nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- ドイツ語:nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz thanks to nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- ロシア語:nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x by nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
こんにちは、親愛なるノストリッチさん!
Nostrは全く新しいムーブメントです。はじめの一歩をよりスムーズに、より豊かにするためのいくつかの手順をご紹介しましょう。
👋 ようこそ
これを読んでいるあなたは、すでにモバイルアプリをダウンロードしてNostrに参加しているはずです (例:Damus, Amethyst, Plebstr)。もしくは以下のウェブクライアントかもしれません (例:snort.social, Nostrgram, Iris)。初心者の方であれば、選んだアプリに合った手順に従うことが重要です。ただし、最低限必要な手順はどのアプリにおいても基本は同じですので、ベーシック以上のことを知る必要はありません(もちろん、知りたければトライしてみましょう)。もしあなたが、この記事を偶然見つけて、まだNostr【アカウント】を取得していない場合は、以下のリンクをご覧ください:いちばん簡単なステップリスト by nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.
🤙 楽しもう
Nostrは、人々が確実につながれ、意見を聞いてもらえ、そして、その過程を楽しむことができるように設計されています。これが重要なのです(もちろん、自由の戦士や内部告発者のためのツールであるなど、深刻な使用例もたくさんありますが、それは別の記事で書くことにしましょう)。ですから、何か難しい感じることがあれば、経験豊富なノストリッチたちに声をかけてください。私たちは歓迎します。Nostrでの交流は決して難しいものではありませんが、従来のプラットフォームと比べるといくつか特殊な点があります(でも何も心配することはありません)。
非公式 Nostrアンバサダーリストはこちら:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
リストに掲載されたすべてのノストリッチには、Nostrアンバサダー バッジが授与されていますので、簡単に彼らを見つけることができ、また、フォローすることができます。
⚡️ ザップしよう
Zap(ザップ)は、Nostrに参加したら最初に気づく違いの1つです。ザップはNostrユーザーが即座に価値を送ることを可能にし、便利で楽しいコンテンツの作成をサポートします。これはビットコインとライトニングネットワークによって実現しました。これらの分散型決済プロトコルにより、従来のソーシャルメディアプラットフォームで誰かの投稿に「いいね!」をするのと同じくらい簡単に、satoshi / sats(ビットコインネットワークの最小単位)を即座に送ることができます。私たちはこのモデルをValue-4-Value(バリューフォーバリュー)と呼んでいて、この究極のマネタイズモデルについての詳細は以下をご覧ください:https://dergigi.com/value/
おすすめ記事 by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 では【ザップとは何か?】詳しく書かれてます。
あなたがコンテンツクリエイターでないとしても、ザップを有効にすべきです - 人々はあなたの投稿のいくつかに価値を見いだし、あなたにsatoshiを送りたいと思うかもしれません。Nostrで価値を受け取る最も簡単な方法は、以下の2ステップです:
- Wallet of Satoshiをダウンロードする - ビットコインとライトニングを、スマホで初めて使うなら、おそらくベストチョイスのはずです[^1] なお、他にもたくさんのウォレットがありますので、ご自分に合ったものをお選びください。また、ウォレットはバックアップを必ずお忘れなく。
- 【Receive / 受信】をタップする。
- 画面に表示されているライトニングアドレス(メールアドレスのように見える文字列)をタップして、クリップボードにコピーします。

- コピーしたアドレスをNostrクライアント内にある、対応箇所に貼り付けます(対応箇所には【Bitcoin Lightning Address / ビットコイン・ライトニングアドレス】や、【LN Address / LNアドレス】などのような記載があり、使用しているアプリによって異なります)。

📫 Nostrアドレスを取得しよう
Nostrのアドレスは、Nostrの諸先輩たちによってしばしば【NIP-05 identifier / NIP-05識別子】と呼ばれているもので、電子メールのように見え:
🔍 アカウントの発見と共有を簡単にします ✔️ あなたが人間であることの証明に役立ちます
以下がNostrのアドレスの例です:Tony@nostr.21ideas.org
 Nostrアドレスがあれば、どのNostrアプリであろうが、対応するユーザーを簡単に見つけることができます。
Nostrアドレスがあれば、どのNostrアプリであろうが、対応するユーザーを簡単に見つけることができます。
Nostrアドレスを取得するには、次のような無料サービスを利用できますNostr Check (by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) または有料サービスですがNostr Plebs (by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424) もおすすめです。どちらも異なる特典を提供していて、どちらを選ぶかはあなた次第です。また、Nostrアドレスを取得するもう1つの方法は、ブラウザの拡張機能を活用することです。この方法の詳細はこちらをご覧ください。
🙇♀️ 基本を知ろう
Nostrは、従来のソーシャル・プラットフォームとは大きく異なるため、基本的なことを理解しておくことは、あなたのような新しいユーザーにとって有益です。誤解しないでほしいのは、プログラミング言語やプロトコルの技術的な詳細を学べと言っているのではありません。私が言いたいのは、NostrとTwitter / Medium / Redditの違いを理解し、より大きな視野を持つことはとてもためになるということです。例えば、パスワードやログイン機能はなく、代わりに秘密鍵と公開鍵が使われています。でも、難しくはありません。Nostrを理解するのに役立つ膨大なリソースがありますのでご安心を。このきちんと整理されたランディングページ by nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 には、💜とともにあなたが知るべきすべての情報が載っています。
 これらのリソースが提供する情報は、あなたのNostrキー(つまりあなたのアカウント)を保護するのにも役立ちます。
これらのリソースが提供する情報は、あなたのNostrキー(つまりあなたのアカウント)を保護するのにも役立ちます。
🤝 つながろう
優秀な [^3] 人たちとつながる能力こそが、Nostrを特別なものにしています。ここでは誰もが話を聞いてもらうことができ、誰も排除されることはありません。Nostrで面白い人を見つける簡単な方法はいくつかあります:
- ツイッターでフォローしている人を探す:https://www.nostr.directory/はそのための素晴らしいツールです。
- 信頼できる人がフォローしている人をフォローする:同じ興味を持つ人のプロフィールを見て、その人がフォローしている人のリストをチェックし、その人とつながろう。

- グローバルフィードを見てみる:すべてのNostrクライアント(Nostrアプリ)には、すべてのNostrユーザーの投稿を集約したグローバルフィードに切り替えるタブがあります。興味のある人をただフォローしてみましょう(我慢してください - グローバルフィードでは大量のスパムを見ることになるかもしれません)。

- ハッシュタグ # を活用しよう:ハッシュタグは好きなトピックに集中するのに最適な方法です。気になる # ハッシュタグをタップするだけで、そのトピックに関連する投稿がさらに表示されます。また、使っているアプリでハッシュタグを検索することもできます。発見力を高めるために、あなたが投稿する際も、ハッシュタグを使うことをお忘れなく。
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg スクリーンショット https://nostrgraph.net/ ダッシュボード by nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj
🗺️ 探検しよう
ご紹介した5つのステップは、あなたの経験を大幅に向上させる素晴らしいスタートになったはずです。ですが、もっと新しい発見をサポートし、楽しむためのさらに多くのツールがあります!NostrはTwitterの代用品ではなく、その可能性は無限大です。

楽しくて便利なNostrプロジェクト・リストをご覧ください:
- https://nostrapps.com/ Nostrアプリ・リスト
- https://nostrplebs.com/ – NIP-05の取得とその他のNostr特典 (有料)
- https://nostrcheck.me/ – Nostrアドレス、メディアアップロード、リレー
- https://nostr.build/ – メディアアップロード管理 (などなど)
- https://nostr.band/ – Nostrネットワークとユーザー情報
- https://zaplife.lol/ – ザップ統計
- https://nostrit.com/ – 予約投稿
- https://nostrnests.com/ – Twitterスペース 2.0
- https://nostryfied.online/ - Nostr投稿のバックアップ
- https://www.wavman.app/ - Nostrミュージックプレイヤー
📻 リレー
Nostrに慣れたら、Nostrリレーに関するクイックガイドをぜひご覧ください:https://lnshort.it/nostr-relays 最初のうちは特に心配するようなテーマではありませんが、あとになればなるほど、間違いなく重要なテーマとなります。
📱 モバイル版Nostr
スマホでも、スムーズなNostr体験ができます。このガイドでは、スマートフォンでNostrウェブアプリケーションにシームレスにログイン、投稿、ザップなどを行う方法を説明します:https://lnshort.it/nostr-mobile
読んでくれてありがとう、そしてラビットホールの向こう側でお会いしましょう
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
[^1]: 忘れずにチェックしよう
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 04:46:45
@ 9ecbb0e7:06ab7c09
2023-08-04 04:46:45Vilma Alarcón, una mujer cubana residente en Estados Unidos, se convirtió en víctima de una estafa cuando trató de conseguir un patrocinador para que sus familiares en la Isla ingresaran al país norteño a través del parole humanitario, informó Univisión.
La desafortunada situación involucró a un individuo que se identificó como abogado migratorio en redes sociales y prometió ayudarla a conseguir a dicha persona, cuya responsabilidad es solventar los gastos de alimentación, atención médica y vivienda de los beneficiarios.

Según los detalles proporcionados por la afectada, entregó exactamente 7.800 dólares al presunto letrado, quien le cobró 1.500 USD por persona y aseguró que habría un segundo pago después de la supuesta aprobación del parole. Sin embargo, tras realizar la última entrega de dinero, el estafador desapareció sin dejar rastro.
La comunicación entre la mujer y el defraudador se llevó a cabo a través de mensajes privados en Instagram y WhatsApp; mientras que los pagos se realizaron mediante la plataforma Zelle, bajo el pretexto de que los recibirían los supuestos patrocinadores.

Desde el inicio del programa de parole humanitario en enero, varias personas han sido afectadas por diferentes formas de estafa, todas bajo la falsa promesa de agilizar el proceso y obtener patrocinadores ficticios.
Para evitar caer en este tipo de engaños, el abogado de inmigración José Guerrero advirtió, a través de una entrevista con dicho medio, que ningún profesional legal ofrece un patrocinador a sus clientes, ya que esto es responsabilidad del interesado.
Además, resaltó que pagar a alguien para ser patrocinador es un fraude, y que se debe estar alerta ante la solicitud de transferencias a cuentas personales o sistemas de pago alternativos.
El programa de parole humanitario ha sido una opción para que miles de cubanos, haitianos, nicaragüenses y venezolanos ingresen de manera legal y segura a EEUU.
Según los datos oficiales, casi 160 mil personas han llegado al país hasta finales de junio. A pesar de su éxito, el programa está en litigio en un tribunal federal de Texas debido a una demanda de 20 estados republicanos para eliminarlo.
-
 @ d266da53:7224d834
2023-08-03 09:27:53
@ d266da53:7224d834
2023-08-03 09:27:53Metis is a strong player as a Layer 2 (L2) solution provider based on Ethereum. The MetisDAO Foundation already offers a platform for many types of businesses to embed blockchain services into their products. For 2023, Metis plans to improve its services as an L2 platform to reduce transaction confirmation and finalization times through the release of a novel Hybrid Rollup service.
To this end, we describe the state of the art in the L2 space and present, from a zero-knowledge (ZK) engineering point of view, various technical challenges ranging from suggested optimizations for dramatic performance improvements to theoretical ideas for new cryptographic protocols. In particular, we present zkMIPS, an approach to using the MIPS instruction set as the programming language for ZK rollups in an architecture that can take advantage of both ZK and Optimistic rollups.
Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.
1. Introduction
It is well-known that Ethereum has a scalability issue (the blockchain trilemma), which turns out to be a major bottleneck when the network needs to process thousands of transactions per second, e.g. Decentralized Finance (DeFi). One possible solution is to delegate complex computations to an off-chain solution, called Layer 2 (L2).
Amongst many possible ways to implement an L2 solution, Metis adopted the rollup paradigm: it processes a batch of transactions at a time and later posts the process results to layer 1 (L1), where a smart contract verifies and approves these operations.
Currently, one of the most common frameworks to design a rollup is the Optimistic approach. In an Optimistic rollup, a batch of transactions is received and, unless any of them is contested and proven invalid by vigilant third parties, the transactions are considered valid after some period of time (typically 7–14 days).
A more recent rollup framework, zero-knowledge (ZK) rollups, submits transactions for ap-proval using state of art Zero-Knowledge protocols. This approach results in a much faster approval cycle with very strong security guarantees, but it adds significant complexity to con-trolling proof size, prover, and verifier times. Nevertheless, Metis believes in the potential of this methodology, and it is committed to investing time, effort, and resources to pursue and implement these ideas.
In this document, we describe the state of the art in the L2 space and present, from a ZK engineering point of view, various technical challenges ranging from suggested optimizations for dramatic performance improvements, to theoretical ideas for new cryptographic protocols.
2. Background
2.1 Preliminary notions
For clarity and to avoid potential ambiguities, we informally define the following notions as used in this paper.
MIPS
MIPS stands for Microprocessor without Interlocked Pipelined Stages, a decades-old and stable processor architecture. Several MIPS instruction sets have been standardized; for concreteness, we refer to the instruction set specified in [1].
Layer 1
Layer 1 (L1) refers to the Ethereum Mainnet, which is the blockchain that Metis uses as its consensus-achieving mechanism.
Layer 2
Layer 2 (L2) is a separate blockchain administered by an independent entity (possibly in a distributed manner). This L2 blockchain communicates periodically with L1, stores information (such as transaction data) on L1, and sends additional evidence (such as ZK proofs) in order to prove to L1 that the transactions are processed correctly. At L1, these functionalities are implemented through smart contracts.
The purpose of this architecture is to gain efficiency and transaction throughput and reduce gas costs while taking advantage of the property of L1 as a distributed, irrefutable ledger. Metis also administers an L2 blockchain, called Andromeda.
Layer 3
The term Layer 3 refers to any program running over L2 data, or to independent programs that help maintain L2 functioning properly. The main reason to add an L3 over an L2 blockchain is to improve performance, moving some computations to an independent system with fewer blockchain limitations. Eventually, since L3 uses a different trust model than L2, the computations it performs should be verified by L1/L2 in the same way L2 computations are verified by L1.
ZK Proofs of Verifiable Computation
In this document, Zero Knowledge Proofs are used to implement Verifiable Computation be-tween a prover and a verifier. The prover performs some (possibly lengthy) computation that validates some results published on the blockchain (L1 or L2) and produces additional in-formation to assist the verifier in the audit of these results, i.e. establishing its correctness. Subsequently, the verifier generates a random string and performs checks which allow him to convince himself that the result published is indeed correct.
Optimistic rollups
An Optimistic rollups considers transactions correct until proven otherwise. In this scenario, the otherwise proof is an investigation process triggered when users claim there is fraud in the transaction. We call this claim a challenge and the users who can trigger it the challengers. If a transaction is not challenged, then it is considered correct at the end of the challenge period (typically a few days).
ZK rollups
A Zero-Knowledge (ZK) rollup uses Zero Knowledge Proof techniques to create proof of va-lidity for transactions. The use of ZK proofs can reduce withdrawal time (the time that the network/L1 needs to finalize a transaction) from days to hours and allow the validity of the transactions submitted to L2 to be proved without revealing additional, potentially sensitive information. This is achieved by having L2 provide cryptographic validity proof before updating the blockchain state of L1. The verification process in a ZK rollup is more secure and faster than in Optimistic rollups. However, it is more difficult to implement.
Comparing the Optimistic and ZK rollups
There exist two types of time measurements to compare the rollup paradigms:
Confirmation time — This is the time it takes for the front-end, which is a decentralized appli-cation (dApp), to interact with L2 and L1, and to register transactions correctly.
Finalization time — This is the time it takes for the back-end (the L1 or L2 blockchain, depend-ing on the context) responsible for registering the finality (correctness) of the transaction.
In comparison to ZK rollups, Optimistic rollups take less confirmation time to consider transactions as valid (it happens as soon as the sequencer submits transaction data to L1). However, they take more finalization time to consider transactions as faulty (it happens only after the challenge process has been triggered and concluded), whereas ZK rollups only need to wait for a prover to generate proof and a verifier to reject it.
For a detailed comparison between the two, see [2].
zkSNARKs and zkSTARKs
Even though many Zero-Knowledge protocols for proving the validity of specific statements have been developed over the last 40 years of research, only recently we have seen efficient protocols for generic computations, such as Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zkSNARK) and Zero-Knowledge Scalable Transparent Argument of Knowledge (zkSTARK). ZK rollups can be implemented using any of these ZK techniques and, in both cases, proofs can be generated off-chain and posted on-chain so anyone can verify them.
zkSNARKs were implemented for the first time by the ZCash team. Although its proofs are small and no security issues have been identified in this technique so far, it requires a trusted setup ceremony before running the protocol, and, due to its underlying cryptographic assumptions, it is not quantum-safe. zkSTARKs were first implemented by the StarkWare team. Its proof sizes are not small compared to proof sizes from SNARKs, but they can be generated and verified faster, and also they are immune to quantum attacks.
In addition, for our purposes, the salient feature of the original STARK paper is the possibility of modeling a computation as a processor with a finite instruction set, as we explain below.
FRI
Techniques such as SNARKs and STARKs transform a computation to some specific polynomial which must be of a low degree. The Fast Reed-Solomon Interactive Oracle Proof (FRI) is a protocol that shows a polynomial is close to another polynomial of low degree, and it is applied to STARK polynomials in the verification of their low degrees.
3. Current Software Architecture
Our proposed architecture, zkMIPS (see next section), is inspired on the Cannon project by the Optimism team, which implements a method for investigating a disputed transaction between the Sequencer and the L1 rollup Validator. This investigation process is executed during a period called the dispute period, and includes verifying L2 Merkle roots generated by Sequencer and L2 rollup Validator.
Cannon also implements a MIPS interpreter on L1 in the form of a smart contract with about 400 lines of code. This interpreter receives two different sets of EVM opcodes from the L2 rollup Validator, the Sequencer, and converts both into MIPS opcodes. In addition, it converts data stored in Ethereum memory into MIPS data memory. In the last step, the MIPS interpreter sends both sets of opcodes and data to the Shell Executor.
Cannon uses a minimally modified subset of go-ethereum (Geth) compiled to MIPS called Minigeth, in which the consensus protocol, the RPC, and the database have been replaced by a Pre-image Oracle. On L2, there are four software components: Minigeth, a Pre-image Oracle, a Sequencer, and an L2 rollup Validator.
Figure 1 illustrates how L2 components communicate between themselves and with L1:
- Sequencer submits transactions and generated commitments for a specific block.
- L2 Validator fetches the submitted commitments.
- Validator creates a new set of commitments and verifies the fetched commitments match the generated ones. Note that during this process both commitments are submitted to MiniGeth.
- MiniGeth checks whether MIPS Memory has instructions related to that block.
- If MiniGeth does not find them in MIPS Memory, then it uses Pre-image Oracle. Pre-image Oracle accepts a block or transaction hash from MiniGeth.
- Pre-image Oracle fetches the pre-image of that block or transaction from the EVM state.
- Pre-image Oracle passes the result to MIPS Interpreter.
 Figure 1: The interaction of L1 blockchain and L2 Rollup with Cannon.
Figure 1: The interaction of L1 blockchain and L2 Rollup with Cannon.- MIPS Interpreter converts the EVM opcodes to MIPS opcodes and stores them in MIPS Memory.
- Validator sends the result of its decision to Challenger.
- If L1 Validator does not agree with the process result, Challenger Smart Contract submits the two commitments to Validator and lets it make the decision for the next step to slash Sequencer. Also, Validator can make a decision whether cancel the batch completely or remove the faulty transactions from the batch and re-do the verification process.
Shell Executor on L1 receives MIPS opcodes and data from L2 to find out whether there is any disagreement between the two instruction sets. In case of a disagreement between the rollup Validator and L2 Sequencer, it returns the line number of the EVM instruction in which the disagreement has happened and declares the Merkle root (which is submitted by Sequencer) as invalid. For getting more information on a particular block (e.g., access to an EVM state to obtain the block header), Shell Executor calls Pre-Image Oracle, which receives the hash of a block and returns the block header. Hence, Shell Executor can traverse the previous block until finding the block which contains the disputed instruction. Thus, Pre-Image Oracle replaces the usage of the database for this on-chain interpreter, eliminating the necessity to maintain a database in Cannon’s VM (MiniGeth).
4. Challenges
4.1 Challenge: Applying MIPS
In L2 solutions, there is some underlying computation C that needs to be verified by L1 before inserting L2’s processing results back into L1. To do this, C needs to be transformed into an equivalent polynomial for STARK. We distinguish between two important possible representations of C.
Boolean and algebraic circuits — A computation C can always be represented as an algebraic circuit, which in turn can be converted to a Boolean circuit. Several methods have been developed to create a SNARK proof from one of these two representations, even though creating a circuit can be a time-consuming task. For an example, see [3].
Finite instruction set— Imagine you have a processor which is able to execute a finite set of instructions and a program that reflects the computation C in this instruction set. Note that each program instruction will change the processor’s overall state from some well-defined current state to the next. This sequence of states is called the (execution) trace, and it can be used in STARKs to help prove there is a valid sequence of states for C.
Important questions concerning the second representation are: what exactly should be the specifications of a processor to emulate this instruction set? How many registers does it have? Which instructions are allowed? Etc. There are many choices possible, which strongly depend on the context where the ZK Proof has to run, among other factors.
StarkWare chose to define a new language called CAIRO, which stays close to their Algebraic Intermediate Representation (AIR). This leads to efficient protocols but requires programmers to adjust to this language. Instead, we propose a different approach, using an already estab-lished language, as we explain in the next section.
Problem. As already explained, in an Optimistic rollup, a challenger contests a proof by demonstrating an error in the execution of the program that executes a transaction, whereas in a ZK rollup, a prover receives a MIPS program as input that executes a transaction and uses the program’s logic to generate a zkSTARK/zkSNARK proof for its correctness.
We expect that both approaches, Optimistic and ZK, can coexist and be unified, a concept we call a hybrid rollup. We will explain the advantages of such a rollup technique combination in Section 4.5. It seems natural to use the same instruction set as input for both types of rollups. But then, the question is which intermediary instruction set is more appropriate.
Solution. Since we need to verify the source code that validates Ethereum (Layer 1) trans-actions, the EVM instruction set seems to be the logical choice. However, the complexity of interpreting EVM code requires a lot of work to write a prover that compiles its logic to ZK proofs. It only gets worse if we consider the large size of the instruction set as well as the frequent updates in the set of EVM opcodes [4].
Therefore, we intend to use the MIPS instruction set due to its well-known stability and its simple opcodes. This choice will also allow us to take advantage of incorporating Cannon into our system, which implements a method to challenge a transaction using a subset of MIPS.
An additional advantage of developing ZK circuits based on MIPS programs is that we do not have to worry about the EVM-based ZK types like ZK Type 1, 2, 3, or 4, as mentioned in [5]. This way, we obtain much more flexibility in developing ZK circuits and implementing formal or push-button verifications to make our circuits bug-free and safe from all types of attacks.
Challenge 1. Use the MIPS instruction set as the instruction set for ZK rollups and apply it to the ZK-proof system design.
4.2 Challenge: Fractal scaling
Problem.A naive implementation of the functionalities described in the previous section would lower TPS, so these components could be partially implemented outside Layer 2 with-out reducing the system’s reliability. Adding a Layer 3 solution to the architecture improves scalability, and also will not reduce the decentralization and security of the system. However, adding L3 to the architecture has its own challenges.
Solution. One possible approach to address this challenge is following a recursive proof generation method, known as Fractal Scaling. This helps to balance security, scalability, and decentralization since the proof generation process is done on machines to which attackers do not have access, whereas integrity is preserved because all off-chain computations can still be verified on-chain.
More specifically, zkSTARK proofs can be created in Layer 3 to help Layer 1 verify whether Ethereum L1 state roots were correctly computed from the execution of a transactions batch in L2. These proofs can be sent to L1 through call data at a lower cost since it could contain one proof for thousands of transactions united in one batch. Hence it is expected that Fractal Scaling will save gas and improve the TPS of the system.
In the zkMIPS solution, both the STARK and SNARK approaches are used. First, the Se-quencer on L2 generates multiple batches in which each batch has a hash value pointing to the next batch. On L3, there are several provers that process the received batches in parallel and generate one STARK-based proof for each transaction inside a batch. Then, by applying SNARK-based proof recursion and aggregation techniques, the prover combines the generated STARK-based proofs and will create one proof per batch. Finally, again all the SNARK-based proofs for batches will be combined using a recursive proof technique and will be returned to L1’s verifier smart contract.
Challenge 2. Although the required architecture with the capability of running smart contracts on L2 and bridging contracts on L1 is available, still high cost of the on-chain storage on L1, as well as the off-chain storage on L3, are challenges that should be investigated.
4.3 Challenge: Provider unavailability
Problem. In the case of unexpected shutting down or crashing of the proof generation process, new provers or Sequencers are unable to continue the process as they cannot track the previous prover’s pending work. Therefore, new provers will lose the state of processing accomplished by the previous prover who got crashed. If we lose this information then a new prover or Sequencer needs to start the process from the beginning, therefore increasing the time and cost spent for the total proof generation process and inflating the processing transaction fee.
Solution. One possible solution is to periodically create checkpoints for transaction summaries and other details necessary to rebuild a current state by some other prover using L3 offline storage. This storage keeps the checkpoint until a generated proof is submitted by a prover and reduces costs as it is not required to post transaction state details to L1.
In case of unexpected crashing scenarios, whenever a new rollup provider gets back online it can fetch the checkpoint from storage and continue the proof generation process.
Challenge 3. Designing a system to store the checkpoints during the ZK process is challenging. Also, finding the optimal value for the time interval to update the checkpoints should be investigated.
4.4 Challenge: Polynomial commitment schemes and proof size
For efficiency reasons, almost all zkSNARK and zkSTARK protocols rely heavily on some commitment scheme for the polynomials involved. A natural way to classify these schemes is according to their underlying cryptographic assumption:
- Hash-based, e.g. using Merkle trees (as in FRI)
- Discrete Log-based, e.g. over elliptic curves (as in BulletProof)
- Pairing-based, i.e. using pairings as well as elliptic curve discrete log (as in KZG)
- Hidden-order based, i.e. using a group whose order is known to nobody (such as in RSA and class groups)
These commitment schemes can be compared according to different criteria, e.g. proof size, prover time, verifier time, setup assumption, post-quantum resilience, etc. See [6] for an overview.
We intend to study which commitment scheme will be most suitable for our context, in which proof size concerns us the most. More precisely, KZG or Bulletproof (BP) could be used as zkSTARK’s polynomial commitment scheme instead of Merkle trees. We emphasize that this approach could, in theory, reduce the complexity of crucial parts of proof size from O(log2(d)) to O(log(d)) or O(1) (to BP and KZG-based zkSTARKs), and parts of prover time from O(log2(d)) to O(d) or O(1) (idem), where d represents the degree of modeled polynomials.
However, the feasibility of changing a polynomial commitment scheme has to be properly analyzed, so we cannot guarantee these performance improvements as real complexity depends on variables that are not yet considered here.
The benchmarks for our preliminary zkMIPS implementation using libSTARK[7] are presented in Figure 2. The results were generated for different values of the blow-up factor β, a STARK approach variable typically defined as a power of 2. As the name suggests, the blow-up factor blows the evaluation domain over which FRI polynomials are evaluated. Therefore, for a higher
β, the prover takes longer to generate the proofs, but soundness can be achieved more easily, causing proof size and verification to decrease. This relation can be observed in the benchmark results.
Challenge 4. Investigate how an appropriate choice of a polynomial commitment scheme will reduce the proof size and how to integrate the proposed protocol with other protocols in the applied ZK rollup scheme.
4.5 Challenge: Hybrid Rollups and various transaction types
Problem. The high cost of ZK rollups discourages some users from requesting the ZK rollup type of service, while the high withdrawal time of Optimistic rollups might be a bigger disad-vantage to other users. As we know there is a trade-off between these two rollup techniques. We intend to use both techniques in parallel. Our approach is to implement Optimistic and ZK rollup services at the same time to satisfy all types of users. The question that should be addressed is how to combine these rollups in one architecture.
Solution. By applying the Bedrock architecture as implemented in the Cannon project developed by the Optimism team[8], we can combine both Optimistic and ZK rollups. Applying this architecture requires several design choices, such as transaction types and execution time
 Figure 2: Benchmarks for preliminary zkMIPS implementation
Figure 2: Benchmarks for preliminary zkMIPS implementationparameters, in order to optimize the system’s confirmation and finalization times. The proposed hybrid solution will allow users to choose between Optimistic and ZK rollup services seamlessly.
We envision a system with different Transaction Categories. Each category would have its own configurable mechanism to automatically decide whether its transactions should be validated via Optimistic or ZK rollups if the user chooses to. Moreover, the soundness level (how hard it is to get a faulty transaction to be accepted as correct in ZK rollups), as well as the policy (such as defining the challenger’s reward in an Optimistic rollup) would be configurable. As a result, each transaction category would have different latency, depending on the configuration.
In this setup, hybrid rollups face several challenges. For example, the validity of ZK rolled-up transactions depends on previously Optimistic rolled-up transactions. Thus, how to properly implement this categorization is a question that still deserves considerable thought.
Challenge 5. How can Optimistic and ZK rollups accomplish transaction approval in one unified architecture? Also, how to identify independent transaction batches that allow having a transactions batch finalized before the previous one?
4.6 Challenge: Alternative recursive ZK architectures
One way to overcome the issue of large ZK proofs and prover times is to change how parties communicate in these protocols and what the communication between themselves represents. For instance, instead of verifying on-chain a proof (generated off-chain) for the validity of a transaction, one could design an additional ZK protocol to verify off-chain that same proof and use this off-chain verification to generate a second, smaller, proof to be verified on-chain.
The motivation behind this idea is that even though verifying a proof π for a computation C is faster than running C, sometimes it is not fast enough. Therefore, we could create a proof π⋆ for the correctness of π (the target computation is now the verification of π itself). For this reason, we use the adjective “Meta” to refer to this new proof, as well as to the prover P ⋆ that generates it and verifier V ⋆ that verifies it. This scheme is illustrated in Figure 3.
Of course, π⋆ is intrinsically related to π and the validity of one of these proofs must imply the validity of the other by design. The difference between them, however, is the introduction
 Figure 3: Meta ZK Proof
Figure 3: Meta ZK Proofof a new level of abstraction, where the validity of computation is replaced by the verification of this validity. On this new level, since proofs being verified are often produced by the same algorithm P , we can take advantage of their similarities to group many verifications into one meta-proof, achieving even better results. This optimized scheme is illustrated in Figure 4.
 Figure 4: Meta ZK Proof for multiple ZK Proofs
Figure 4: Meta ZK Proof for multiple ZK ProofsA similar idea has already been notably implemented by Coda/Mina[9] and Plonky2[10]. These projects use a framework known as Recursive ZK Proofs, which consists of grouping recursively many statements into one, and then proving only this final statement, as illustrated in Figure 5.
 Figure 5: Recursive ZK Proof
Figure 5: Recursive ZK ProofEven though Recursive and Meta ZK Proofs are similar in many aspects, we intend to employ Meta ZK Proofs because we believe there are many opportunities for optimization when verifying multiple ZK Proofs for different transactions at the same time. Furthermore, the generation of a ZK Proof reduces the full execution of computations to their verifications, which tends to be much faster and equally valid. Therefore Meta ZK Proofs can achieve the same soundness as the proofs they are reducing, but with significantly lower complexity.
Challenge 6. Explore alternative recursive ZK architectures.
4.7 Challenge: Security concerns
Formal Verification methods are mathematically precise techniques that analyze the specifi-cation, development, and verification of systems and protocols. Creating a formally verified implementation of a probabilistic proof system or protocol is challenging. However, the result-ing guarantees avoid security vulnerabilities in the designed protocol/system.
In a future version of zkMIPS, we will apply Formal Verification methods to realize the following improvements and prevent attacks on the ZK scheme and verifiers:
- To improve security, we intend to apply formal verification methods to the ZK proof generation protocol. We will experiment with both the State exploration and the Proof based approaches. State exploration can be useful for detecting common vulnerabilities such as reentrancy attacks, integer overflows, and unauthorized access. Proof-based can be useful for detecting subtle logic errors and security vulnerabilities that may be difficult to detect using state exploration, and also provide a high degree of confidence in the correctness and security of the contract. We use proof assistants such as Coq, Isabelle, and the K framework.
- In addition, to find ZK program vulnerabilities, we are following the Formal Specifications method using the Why3 platform which verifies programs developed in Rust.
- To improve the security of written codes in Solidity, we will be using the Satisfiability Modulo Theories (SMT) Checker application and the Horn-solving technique, or similar tools and techniques if they become available.
- To analyze the gas amount consumed by smart contracts, we will be using tools such as Oyente and Slither.
Challenge 7. Investigate the security of the designed protocol/system using formal verification methods. This investigation will analyze the provided solution from a technical perspective and assess its feasibility.
4.8 Challenge: Commitment schemes based on other assumptions
There exist little-known bit commitment schemes which use the Subset Sum problem as an underlying assumption and seem as efficient as Discrete Log schemes, but the known ones have similar construction and properties, allowing protocol designers to easily replace these schemes. The main advantage of applying a Subset Sum scheme to ZK protocols is that it makes them automatically quantum-resistant, with the addition of having similar Discrete Log schemes’ performance. However, this efficiency in terms of proof size, prover time, and verifier time needs thorough analysis (in particular, when applied to committing to polynomials).
Challenge 8. Investigate the applicability of commitment schemes based on Subset Sum in the context zkSNARKs/zkSTARKs.
4.9 Challenge: Implementation concerns
zkMIPS will accept as input MIPS assembly instructions from any type of application or system including IoT devices, L2 chains using Cannon Optimism, and Cloud APIs. It will output ZK proofs that can be verified on the Ethereum L1 chain. Hence, zkMIPS can be used as a generic ZK proof system in any centralized or decentralized application.
We have started implementing zkMIPS using the FRI protocol following an interactive model. Our current zkMIPS deployment accepts MIPS assembly instructions, parses them into stream format, and loads them into RAM Memory. The result is called a RAM Program, which is converted into Binary Algebraic Intermediate Representation (BAIR) constraints. The result is passed on to the FRI protocol which ensures the complexity of linear proof and the complexity of logarithmic verification (i.e., Low Degree Testing).
In our implementation we were faced with the following main issues:
- The proof size is linear in the size of the computation trace, even after the reduction of witness size. This increases storage costs on the prover side.
- The final verifier needs to interact with the prover continuously until the proof is gen-erated. Hence, the verifier process had to be on an untrusted machine. This is again challenging because L1 cannot rely on an untrusted machine to update its state.
Challenge 9. zkMIPS uses existing software libraries written in several languages. Ensuring the development, integration, optimization, reliability, and security of the final product constitutes a challenging endeavor.
5. Collaboration
Metis invites bright industry experts, researchers, and leaders who are interested to collaborate on the zkMIPS project. This invitation is not limited to the research and implementations mentioned in this document; Metis embraces other innovative ideas to improve the proposed hybrid rollup solutions in this document.
Notes
[1]https://inst.eecs.berkeley.edu/~cs61c/resources/MIPS_help.html
[2]https://vitalik.ca/general/2021/01/05/rollup.html
[3]https://vitalik.ca/general/2016/12/10/qap.html
[4]https://kelvinfichter.com/pages/thoughts/hybrid-rollups/
[5]https://vitalik.ca/general/2022/08/04/zkevm.html
[6]https://docs.google.com/presentation/d/1YJX_MgWjhsFHiubHoCMb5F27rtN9AcxgaKMswGFf8I4
[7]https://github.com/elibensasson/libSTARK
[8]https://github.com/ethereum-optimism/cannon/wiki/Cannon-High-Level-Overview
[9]https://minaprotocol.com/wp-content/uploads/technicalWhitepaper.pdf
[10]https://github.com/mir-protocol/plonky2/blob/main/plonky2/plonky2.pdf
By:MetisDAO Link:https://metisdao.medium.com/zkmips-and-other-research-challenges-for-layer-2-9097c661facb
-
 @ 3bf0c63f:aefa459d
2020-10-23 12:55:00
@ 3bf0c63f:aefa459d
2020-10-23 12:55:00\n# Parallel Chains\n\nWe want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).\n\nOn the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.\n\nIt's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.\n\nLuckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.\n\n## How does it work\n\nWith the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.\n\nThen you create a long sequence of transactions (sufficient to last for many many years), each with annLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".\n\nWith the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.\n\nThen you combine it withRBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.\n\n## See also\n\n- Drivechain\n\n[^eltoo]: The same thing used in Eltoo.\n -
 @ 96aea8a4:8606d449
2023-08-04 02:30:57
@ 96aea8a4:8606d449
2023-08-04 02:30:57The Bor Report... Day 0
If you've ever read The Mezzanine by Nicholson Baker then it's possible the aperiodic letters in my Back Office Report will resonate with you.
I'm treating these letters as a sort of journaling/social experiment. My thoughts, on a page, in no particular order. All for an unspecified amount of time. Burn after reading if you so desire.
This platform along with the Daumus app is the perfect place to inscribe my thoughts. It's written in stone. If I say something inaccurate I sincerely hope my readers call me out. And dare I try and make a prediction, there will be proof and I won’t be able to back pedal like Jim Cramer does every day of his career..
Okay let's begin...
Let’s start with the boring… Dow Jones 35,215.89 | S&P500 4,501.89 | Nasdaq 13,959.72 | Russell 1,961.40 | VIX 15.92 | GBTC 19.30
Keep in mind I’m writing this well after the close of the market. My 2022 LEAPs have well expired worthless, and my sentiment WAS overall very bad. My outlook on the market was completely negative up until I became bullish about half way through 2023. A good friend of mine purchased around 30k in CDs. I’m happy for him, a sound investment. And much more size than I was use to. But to me it felt a lot like peak hysteria. The bond fad had already hit the news headline and was starting to fade. I remember thinking, “great.. now bonds are exciting.. that’s when you know it’s bad.” But it wasn’t until a few months after that when first hand I saw someone act on it. Sure the major hedge fund managers were buying bonds but who in my circle actually cared about safe money. Nobody had enough for it to matter in the first place.
I always thought things usually get worse before they get better. That seems universally true. But how long is worse. That’s what was/is tough to decide. The economy is in shambles in many ways, but healthy in others. Was a year of red ticks enough, two years? Who really knew. The more I heard people in my circle actually purchasing things like CDs and bonds the more I was intrigued… was this it? Are the tides changing, is peak hysteria in the rear view mirror? No idea..
I decided to stop by a coin store on the way home. Sometime I end up with way too much time on my hands.. It was after my shift at corpo and I was meeting up with family for dinner. It was too early to drive home, but too early to drive to the dinner spot. My work, as you can guess, right in the middle. There was a coin jeweler just down the road so I thought screw it why not. The local guy, great guy by the way, had no gold coins. None at all. Said someone just came in and bought the whole place out. Didn’t believe him at first but after looking around he really was out of gold. I had been in here a few years ago and although the price of gold was steady there certainly was supply. He said, “I’ve got silver bullion left”. I said I didn’t want any..
Called a few other local places. I wasn’t going to actually buy any gold coins, but I was curious. Just about everywhere I called was out of gold. The theme Peak Hysteria was really starting to set in.
Although the market was closed I yearned for exposure. An option contract on the S&P. Maybe a call on something in tech. Just some exposure to the market of some sort so I don’t miss the shifting of tides..
I’ve realized as I’m writing this I’m using a mixture of present thought, and thoughts/experiences from weeks/months before. Incredibly confusing for the reader, but I frankly don’t care. I’ve set my foot down on starting the Bor Report and I won’t go another day without publishing something. I don’t want to get hung up on every detail. I want to put stream of thought to paper. Maybe someone will appreciate it. Or maybe I’ll look back and be extremely embarrassed. I frankly do not.. care.
I’ll leave you with a quote, so that you can think about me until the next time I publish something. Because it’s not everyday that I want to debate engineering disasters, argue about municipal funding projects, or simply harp on bond purchasers. But those days do seem to make up a majority of my life. There’s something blissful to me about the very nature of a boring topic. Maybe in a way it resembles the liminal style of some of my favorite artwork. I would argue that some of the most complicated and interesting things of this modern world can seem boring at face value. Or maybe I’m just boring.
"Warning: Everything saved will be lost." - Wii notification
Taken from the what is the most unintentionally profound thing you've heard thread.
Till next time,
The Boring Report
-
 @ 5df413d4:2add4f5b
2023-08-01 16:20:28
@ 5df413d4:2add4f5b
2023-08-01 16:20:28June 2018. Shanghai.
Cruising down the Shanghai East-West Expressway, riding shotgun in my friend’s BMW M3. The car is silly Americana. Captain America decals adorn the exterior, while the interior is Iron Man red and gold. Several large stuffed animals crowd the back seat — Peppa Pig, Winnie the Pooh (both inexplicable, irreverent quasi anti-government memes in China). All the while, Black Panther and Darth Vader bobbleheads nod along atop the dashboard. For many in China, and Shanghai particularly, personal vehicles are the medium for coded expressions that would be too garish or sensitive if made more publicly.
https://i.nostrimg.com/f29c7dde5549edc1eed5a5223a60b40605bd1c622b6bab747b13a5b7fa598d44/file.jpeg (Pictured: The ideal yuppie bachelor car in Shanghai. You may not like it but this is what peak achievement looks like.)
Outside a hazy, spring night fog colors the city like something out of a Simon Stålenhag painting. The neon-lit Bladerunner tetris set of Shanghai office complexes blurs by just beyond the tinted glass as we cut lanes at speed. Kids See Ghosts blasts loudly on the sound system. We hit the Julu Road (巨鹿路) junction, where the city’s two main expressways meet in a loping tangle of concrete and asphalt. And like clockwork, all connections go out — cell, bluetooth, radio — the car goes silent.
This always happens at this spot. I ask my friend about this. He thinks the police are running a high-end signal jammer at this location to prevent people from flying drones over the junction - which he learned at the cost of one of his own high-end DJI models...Perhaps triggered by the state’s technical show of force, a serious change comes over him for a moment. He glances over, "It's all bullshit, you know," pointing up to the dark sky beyond the windshield, "They have to keep the lights on. They have to convince us that the control everything. If they fail, we will just eat them." “Let the ducks roast,” he says to himself after a contemplative pause, his eyes trailing off into the far distance.
But moment passes quickly. A few moments after we pass through the junction, all signals and service reappear, stronger than before. Kid Cudi’s blaring “I feel freeeeeeeeeeeeee” bursts onto the car’s speakers at full volume. Political talk ceases and the entire thing immediately becomes a long forgotten memory.
In any case, it’s Friday. The bars are open, the clubs are calling, and we’re coming in HOT. That’s what matters. Today was a good day in Shanghai.
An Introduction to Life On Mars
Where to start? Folks in the US who have only known me as a bitcoiner often ask, “But how could you live in China?” I always chuckle at this question. Not least because its usually almost visibility dipping with the asker's absurd and exaggerated fantasies about China as a cartoonish 1984-style brutalist dystopia. That said, it is a question that I have given much thought to myself, especially now as a bitcoiner with all the many ways bitcoin has changed my views on things.
And this brings me to a series of far deeper questions — What is authoritarianism, really? Can it ever be benevolent? And how does one become attenuated to it to such an extent as to no longer notice it, if they ever noticed it at all?
https://i.nostrimg.com/2182fd6d38b9eeee65d0400b2659a5be500508cb6ccec34717d2e0a2e19ae878/file.jpeg (What people picture when they ask me about China)
https://i.nostrimg.com/0b565a702191eca5e37a769d80197f9644d61e968315dbfc76f96b660af750a0/file.jpg (This is the same location as the picture above. Today, most days the reality is more like this)
The best way to explore this is to just answer the very first question directly. I very much could live in China because it was RAAAD. I had a great time there and I enjoyed almost every minute of it. In many entirely non-dystopian ways being there was like living in the future or a vision of what it might be like if we (the US) hadn’t forgotten how to have nice things — High-speed rail available at every street corner! Bristling skyscrapers erected in mere days! Wifi bandwidth so cheap and abundant it jumps right out of the stream straight into your frying pan! Gold nuggets for everyone! Everything, now with 30% MORE BEEF!
The thing is, my life in China was good. At that time, the cold, collectivist CCP machinery was fully invested in delivering a jubilee of comforts and diversions to even the relative urban “haves.” Additionally, I came to China as a very well educated, very well paid American with an existing foundation in Mandarin, shuttled in under the wide auspices of a deeply connected global consulting firm. With such well-earned badges of globalist statism, I was afforded a ticket to freely mingle with China’s largely Western-educated, upwardly-mobile urban economic elite. In fact, this was a thing that was rather encouraged…
All this being the case, it is no surprise that I had such a “good” experience. It was always supposed to be that way. Irrespective of the deeper reality, nothing was ever actually supposed to feel authoritarian for me during my time in China. These conditions similarly held true for my particular class of Chinese friends (except that there were certain cultural obligations and political allegiances that it was understood could be called up in full at any moments’ notice).
As an African American, I must admit that in more than a few ways it was possible for me to feel much freer in China than in the United States. I certainly didn’t ever have to worry about being shot in the back by some speed-freak neighborhood watchman or unhinged police officer. And I slowly adjusted to not having to keep my head on a swivel if I heard loud popping sounds in a mall or crowded venue.
No, the Chinese police never bothered me. No, no shadowy state security agents ever interrogated me for my “suspicious” Americanism. No, women didn’t clutch their purse when I walked by (in the States I’ve had this happen midday, while I was wearing full business attire…). People were either ambivalent or genuinely curious to speak with me. In essence, I experienced the joys of simply being left alone by the system. Something like what I image most White Americans experience in the US. So reader, you might already know this, but I can confirm, it was GREAT!
https://i.nostrimg.com/cbdee50436016ab0554830b97b07c72510305752efce8ce6b28c42d7bb5dd1e1/file.jpeg (NGL, China had me out here feeling like this for a hot minute)
Super-Capitalism Is That You?
And beyond my direct personal experience, there were other observations that may seem counterintuitive. For instance, at street level, there was a kind of vivacious, raw free market-ism unlike anything you can find in the West. An ever changing flurry of ramshackle stalls and street vendors. Don’t like the sweet cherries this shop has or the owner has a bad attitude? Then leave! There’s literally 7 other sellers of the same thing on this block alone. And it was like that for most food and daily household consumer products. I could observe market price discovery for goods fluctuating daily, in real-time, sometimes even by the hour.
When I lived above a particularly boisterous commercial street I once saw someone lease a storefront for six days, fill it with heavy traditional Chinese household furniture which I was told “had gotten lost from the factory.” They blew through the inventory starting with signs advertising 20% off on day one, which progressed to 95% off in their final 12 hours of operation. They sold everything so thoroughly that I suspect they probably even sold some stuff that didn’t belong to them like the fixtures that were already in the space when they moved in.
And then, not even two weeks later, 11 days later, the exact same location was reopened as a hotpot restaurant — everything, and I mean everything, had been redone, the floors, the walls, the installation of restaurant equipment, everything. The food was delicious, but I struggled to believe that the health or fire safety inspector had approved any of it, nor that they had real permits for anything they were doing.
Were there laws and regulations on the books ostensibly to control such wildcat commercial activity? Sure, but 天高皇帝远 heaven is high and the emperor is far away, as they say. Now understand that, at street level at least, this was happening everywhere across a city of 26 million people, and then again everywhere across a country of 1.4 billion people.
https://i.nostrimg.com/bf516da1ba165f3a4d1a0694345980e43516d381b002b4e81aac49d7fdae8b6f/file.jpg (Chinese street vendors: a nigh uncontrollable wild force)
By all indications, both felt and seen, people appeared to be fully free to do business and make money while wading in the warm waters of technological modernity. Perhaps they didn’t talk about politics, but that hardly seemed to matter and no one really seemed to care.
It was easy for me to come away feeling that China was a nation of laws rather than enforcement. Maoist austerity might be signaled outwardly but inside its an open, high-octane laissez-faire free-for-all. Conversely, my own cultural history in the US suggested a place of enforcement over law. Signaling egalitarian and meritocratic piety but running on an engine of apartheid justice system, state asset forfeiture, imminent domain, and mass poisoning from Iran-Contra to Seed Oils and OxyContin.
Irrespective of the deeper reality, nothing was ever actually supposed to feel authoritarian for me during my time in China.
So what of it then? Am I here to suggest that China is some Garden of Earthly Delights while Western ideals are a brazen sham? Not so, not so. Rather, my experience brings the realization that in an authoritarian system, it all depends on who you are. And further, that such divisions are central to the maintenance of authoritarian power. I find deep relevance in this, particularly in enabling us to more fully recognize authoritarianism wherever it exists — in China, in the US, or anywhere else. Let me share another story to illustrate.
September 2018. Xinjiang Provence.
https://i.nostrimg.com/808dc51f3c58a37443539992c47448192cc7d05830212268e9279dae7ae7213d/file.jpg
Kashgar, Xinjiang Province. Dust and white heat. I am on a corporate boondoggle in the desert. A plus-one at a rival consulting firm’s Greater China Summit. Like Neo-liberal Wise Men, we galavant around on silk-laden camel-back, we visit the Potemkin village to congratulate ourselves on how well the local ethnics are living, we enjoy a Khan’s Kurultai of exotic roasted meats, red carpets in the sands, Oxbridge 30-under-30 Bedouins on the dunes — you could all but see the Harkonnen spice harvesters out in the distance…
https://i.nostrimg.com/41f41910466f29fd00461a0eb6014853f2af7e4bae8417b7b3068bd18213991a/file.jpg
And the whole time, we are all participating in a collective act of not-seeing the obvious police state all around us. Heavy roll gates, tire spikes, ID checks, mirrored undercarriage sweeps, and vehicle searches for the locals at every nexus of critical infrastructure — gas stations, hospitals, hotels, shopping centers. High-tech police convoys, armed foot patrols, and absurdities like bamboo-thin teenage paramilitary security guards in loose-fitting fatigues and fake Yeezys disinterestedly half-watching the public square while scrolling TikTok (called Douyin 抖音 there) on counterfeit iPhones behind their riot shields.
https://i.nostrimg.com/0af34ab4f7e3fb423ded79a2ebfab4d315d7dcba0a1b42bec19300549eaaedac/file.jpg
Out on the sands, I overhear a firm partner, a Westerner, marveling at the scale of the event wondering at what location could outdo this next year. I interject to suggest Pyongyang. He is not amused, but I certainly am. Later, just when I’m thinking I might be the only one noticing any of this, a tall Indian firm partner, a man built like rugby player, sensing that I was a company outsider (and therefor could potentially give honest answers) asks me what I think of “all of this” in a tone that immediately betrays his meaning.
“In China, I assume that wherever you can most see and feel the hand, is wherever the grip is also most tenuous,” I say. He nods in furrowed-browed approval and we leave it at that. A few months later, perhaps, the New York Times would chronicle this wild corporate exhibitionism in an absolute tear-down piece deeply critical of that firm’s (and all consulting firms) aiding and abetting of authoritarian regimes around the world...
https://i.nostrimg.com/15e19c76f0772161c1617359bcd123051840a5180bd1afe93e9737d308311156/file.jpg
In any case, the lamb roast is firing up and the evening’s next round of festivities are about begin. That’s what matters. Today was a good day in Kashgar
⚠️TRADE OFFER⚠️
This is how the machine works. Nothing is free. There was a near explicit trade being made. Those of us from the favored classes would ignore overhanded oppression of the disfavored out-groups and the sharper appendages of machine would ignore us in return.
https://i.nostrimg.com/a09827c69a55f04f8471abd3d4994615e7da59e07abb19f6868adae254081ba7/file.jpg
Nestled snuggly in the pleasure garden of this CCP-approved social, economic, and educational elitism, wealthy Chinese and visiting Western globalists are supposed to come away believing that what others decry as harsh authoritarianism is in fact, quite benevolent, benign, enjoyable even. From there, it requires only the tiniest of logical jumps for them to assume that their experience is most representative of the greater whole in China, because surely this must be so, right?
From such a vantage then, it becomes all befuddled monocle popping, trembly-handed tea spilling, and frazzled, indigent top-hat ruffling while looking out on any dissenting and oppressed people and wondering “Why are they so loud?”
Incentivized by the plush velour “benefits of membership” in Chinese statism, it is easy to come to view protesting voices, those struggling for justice and freedom, as dunce-hat complainers, salty haters, red-faced and tear-strewn Wojaks, or simply spiteful, back-bitting losers whose problems with the system would evaporate in short order if they just learned to follow the rules, better themselves, and fix their aberrant cultures...
And well done then! This is what the authoritarian system wants, fundamentally NEEDS— to estrange you, through a compromise of comforts, from moral rightness and to replace that with the false rightness of naked self-interest on one hand, and the threat to absolute violence on the other. O, what machines we have made!
In China, those close enough to the system to experience it as a warm embrace rather than an icy dagger are supposed to understand that it is the Uyghurs struggling against mass detention and cultural erasure who are in the wrong. Similarly, for those thusly appointed in the US, it is supposed to be all but self-evident that the same goes for African Americans struggling against mass incarceration and open-air summary executions by uniformed agents of the state.
To the authoritarian all such trouble-making peoples need to be corralled, controlled, and if required, crushed — but in the short run, they need your help to do it. It will always be done in the name of some manner of “social harmony” their doublespeak for the ossification of the status quo and the authoritarian’s power along with it.
In this world, the in-group, the favored classes, whoever they may be, by whatever lines such distinctions are drawn — class, race, sex, religion, ethnicity, sexual orientation — are led to believe they are safe as the authoritarian’s well-loved and much needed allies. But in the end, in the long run, it is the biggest rugpull of all. In such a system, all are Santiago’s sheep, to be meat for the slaughter in times of need.
So how does it feel, Western Anon? What people does our system eat to ensure that you may be comfortably overfed?
And so we become attenuated to such things in so much as we are benefiting from them. Or least, we believe that we are benefiting from them. In our age of the hungry ghost nation-state, it is so very easy to look past the true nature of the thing, or even to buy into it and to project it, when it is not YOU being targeted.
But understand. This is no benevolence. That you are not being targeted — for now, today — is an active, calculated, and entirely self-interested decision on the part of the authoritarian power structure. It is nothing that can be counted on. And whether you realize it or not, it is a decision that is reassessed at every interaction. If nothing else, the pandemic has shown us all this in the starkest relief.
https://i.nostrimg.com/6749febaeb20f102847e5867ad439fa96659bc33d21a795489b40b9baee755e2/file.jpg
If you are allowed to persist in a state where you may believe that all is well, that the thing is benevolent and here to help you, it is only because it is more useful to the animal for you to remain asleep. Understand this, and ask your self — why?
And what is authoritarianism then? Fundamentally, I’ve come to understand authoritarianism as something like the grand political end-point of force. The might-equals-right heuristic at civilization scale. It is the ever-present implicit threat that going against some Big Man’s arbitrary diktat will result in violence, be its physical, economic, social or otherwise, being levied against you to bring you to heel. It is that mindless power which flows from the barrel of a gun…when you have the gun and others do not. It is the system of rulers unbounded from rules.
What We Must Fight
As bitcoiners, this is what we fight. In all its forms, wherever it exists. We must recognize that ALL authoritarian systems and their operators, irrespective of any apparent, surface level ideological conflicts, are in fact like brothers, arms interlocked, in the maintenance of global authoritarianism itself. The principle struggle of the new century is the people against their own governments the world over, rather than the peoples of one nation or group against those of another nation or group. Though do not put it past our current political helmsmen (and women!) to try to steer us all in that dismal direction as a means for distraction that serves their self-preservation.
Bitcoin provides a potentially very powerful tool to the people in this epochal struggle. Bitcoin enshrines a new self-evident and inalienable right — the right of every individual to be an economic actor on a fair monetary protocol. At scale, this moderates the state’s capacity to perpetrate financial violence against both the individual and the collective. With bitcoin, no one is illegal. The protocol imposes no requirements and demands no allegiances, all may transact freely, always.
Value, once obtained in bitcoin, if held securely, cannot be seized. Nor can it be stolen through the occult dark arts of currency debasement. With bitcoin the individual is empowered — able to passively opt out of a predatory financial system, able to move their wealth across borders without restriction, able to actively resist an unjust government free from the threat of total definancialization — and all are welcome.
But bitcoin is just a tool, and just one of many. Fundamentally, the people are the movement and the movement is the change. We must never forget this. We must be both active and steadfast in building the futures we want to live in. Bitcoin is just a tool, but if we use it, perhaps we can one day have freedom — without anyone's authoritarian "characteristics" this time, but perhaps still with 30% more beef.
~Moon
As always thanks for reading, I hope you enjoyed! In case you missed them, be sure to check out Journey Into Bitcoin 01, 02, and 03. Always more to come soon!
Follow me on twitter: Michaelyouknow
Postscript
In the spirit of inter/multi-disciplinary bitconery, here are a few top notch recommendations that to me are related to elements in this piece.
Music: Something In The Way of Things (In Town), The Roots; Bulls on Parade, Rage Against the Machine; Who Will Survive in America, Kanye West
Movies: Four Hours in My Lai (1989)
Readings: City of Silence, Ma Boyang; Guantánamo’s Darkest Secret, The New Yorker
Use The Tools
Liberate your education:
libgen.is — Most books today exist on the internet, for free
Archive Today — Information wants to be free. Too much of it today sits behind absurdly extractive paywalls. (Bitcoin lightning payments can resolve this for both content users and producers)
Liberate you food: The Beef Initiative — Trade real, honest money for real, honest food
Liberate your security: DEFCAD— May you never need them but always know what tools are there
-
 @ 1c6b3be3:73f0ae6f
2023-08-01 10:25:57
@ 1c6b3be3:73f0ae6f
2023-08-01 10:25:57StableArtMaker est un bot innovant qui vous permet de créer des images à partir de plusieurs modèles de Stable Diffusion, Midjourney et des QR codes artistiques. Il est conçu pour être utilisé sur Nostr.
Comment ça marche ?
Le bot peut être utilisé dans le feed public ou en DM. Dans le feed public, il faut mentionner le bot et utiliser un des mots clefs documentés plus bas (exemple:
nostr:npub102ca8pnhy26vh2akepgr4vleyew65nuzug5val3sycslfe0wruwqzezyfp imagine a plane). En DM, il faut simplement utiliser le mot clef.Commandes
Voici les commandes que vous pouvez utiliser avec StableArtMaker :
help: Affiche une aide simplifiée.imagine: Demande au bot de créer une image.upscale: Choisit l'image à agrandir parmi les 4 images proposées par Midjourney.qr: Demande au bot de créer un qr code artistique.models: Affiche les modèles stable diffusion disponibles.deposit: Crédite votre compte.balance: Affiche la balance de votre compte.
Utilisation de la commande
imagineLa commande
imaginepeut être utilisée de trois façons en DM ou en public :-
imagine la description de mon image: Crée une image sur le modèle standard stable diffusion. Cette commande est utilisable en mode gratuit et payant.
-
imagine modèle la description de mon image: Permet de préciser le modèle de diffusion proposée par https://sinkin.ai. Cette commande est utilisable en mode payant.
-
imagine mj la description de mon image: Génère une image à l'aide de Midjourney. Cette commande est réservée aux utilisateurs payants.
Utilisation de midjourney
L'utilisation de Midjourney est réservée aux utilisateurs payants. Son utilisation se fait en deux étapes, il faut d'abord utiliser la commande
imagine mj la description de mon image. Le bot vous proposera 4 images ainsi qu'ungeneration id(exemple:generation id: 1135849470823780352).
Pour choisir la troisième image, il suffit de répondre au bot avec
upscale 1135849470823780352 3.
Utilisation de la commande
qrLa commande
qrpeut produire des QR codes pour des adresses Internet (URL) et n'importe quelle chaine de caractère. Les adresses Internet sont réduites automatiquement afin de produire un meilleur rendu. Plus la chaine de caractère est longue et moins le rendu sera beau.Voici un exemple d'utilisation de la commande
qr:qr https://decouvebitcoin.fr/ an orange rabit with red eyes looking at the camera, cynical, dramatic pose, intricate, highly detailed, detailed face, smooth, sharp focus, environmental light, rim light, artgerm, artstation, art by greg rutkowski, ilya kuvshinov, rossdraws, fantasy illustration
Modèle économique
Le bot dispose d'une gratuité limitée en nombre d'utilisation. Chaque génération coûte 100 satoshis. Le mode payant permet de débloquer certaines fonctionnalités décrites plus haut. Le paiement passe par lightning network.
Limitations et recommandations
Midjourney applique une politique restrictive sur l'utilisation de son service. Le prompt utilisateur peut être refusé et l'accès au service peut être restreint.
Les images générées par un modèle stable diffusion n'ont pas cette limitation cependant, les images sont hébergées par mes soins et peuvent être supprimées postérieurement. Je vous conseille de récupérer localement vos images. Gardez en tête que StableArtMaker n'est pas un service d'hébergement d'image.
StableArtMaker s'appuie sur des services de générations d'images (sinkin, gooey, midjourney) payants. La gratuité proposée est là pour vous donner une idée de la qualité des images produites. N'en abusez pas :)
Ce bot est créé avec amour par nostr:npub1r34nhc6nqswancymk452f2frgn3ypvu77h4njr67n6ppyuls4ehs44gv0h.
-
 @ 00000001:a21169a7
2023-08-01 10:03:57
@ 00000001:a21169a7
2023-08-01 10:03:57Edward Weston, initially recognized as a prominent pictorialist, played a crucial role in the evolution of photographic art during the 20th century. His trajectory marked a notable transition towards a new conception of the medium, leaving behind pictorialism to become one of the leading exponents of Group f/64 and elitist photography.

A distinctive feature of Weston's work was his relentless pursuit of maximum sharpness and tonal range in his images. This aspiration was evident in all his works, from his stunning landscapes to his innovative still lifes. Herein lay his genius: the ability to capture the purest essence of his subjects with a precision and clarity hitherto considered unattainable.

Weston pioneered the technique of previsualizing the final result in photography. This involved imagining and planning the final appearance of the image even before shooting the camera. To achieve this, he developed what became known as the Zone System, a method that allowed to control and modify the brightness of an image in a very precise way.

In his photographs, Weston often decontextualized his subjects, employing neutral backgrounds to further enhance the intrinsic identity of the object. This technique led to the creation of some of his most iconic images, in which each object becomes an autonomous entity, freed from the distractions and influence of its surroundings.
In addition to his extraordinary technical ability, Weston's capacity to infuse a sense of "radiation" into his images contributed greatly to his enduring influence. Through his refined technique, Weston created images so powerful and emotive that they impressed the viewer, eliciting an emotional and visceral response.
Weston also took his vision and technique beyond his studio. On his travels to post-revolutionary Mexico, he joined a revolutionary movement and published his work in their magazine. This experience not only broadened his artistic perspective but also left an indelible mark on his corpus of work, adding a new level of depth and context to his photographic approach.

In summary, Edward Weston exemplifies the evolution of photographic art in the 20th century. His transition from pictorialism to modern and elitist photography, his constant search for sharpness and tonal range, his innovative decontextualization of objects, and his radiant technique, all contributed to his enduring legacy. His influence is felt not only in the generations of photographers who followed him, but also in anyone who appreciates the ability of photography to transform the ordinary into extraordinary.
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 01:14:26
@ 9ecbb0e7:06ab7c09
2023-08-04 01:14:26La localidad de San Francisco, en el municipio Palma Soriano, Santiago de Cuba, se encuentra de luto ante la pérdida de dos adolescentes, identificadas como Yuleidis Sánchez Escalante, de 13 años, y Claudia Escalante Carmenate, de 16 años. Según diferentes reportes en redes sociales, las menores murieron ahogadas en una poza del río Aterrizaje.
Aris Arias Batalla, responsable de Operaciones y Socorro/Seguridad Acuática de Santiago de Cuba, informó ayer miércoles que las jóvenes fallecieron a causa de ahogamiento por sumersión en un área no certificada de baño, que carecía de salvavidas.
El internauta identificado como Jeissy Borrell Gámez detalló que cuando las dos muchachas comenzaron a tener problemas para salir del agua, sus amigos presentes en el lugar trataron de rescatarlas, pero al final no pudieron evitar la tragedia.

Este lamentable suceso ha causado una enorme tristeza en la familia a la que pertenecían ambas jóvenes. Además, también se encuentran conmocionados amigos y vecinos de las dos víctimas.
Ante esta situación, Arias Batalla recordó a los residentes en la oriental provincia la importancia de seguir las indicaciones de las autoridades y respetar las prohibiciones en sitios no designados para el baño. Enfatizó que la mejor opción para disfrutar del agua de manera segura es acudir a las áreas de baños públicos, certificadas y con salvavidas.

“Es responsabilidad y obligación de cada familia el cuidado y protección de bañistas y más de niños o adolescentes. Los salvavidas velan por cientos a la vez y, a pesar de sus charlas, advertencias, llamados de atención, no respetan sus indicaciones y prohibiciones”, agregó el socorrista.
Finalmente, reiteró sus condolencias para las familias de las jóvenes víctimas: “Que Diosito y los ángeles las custodien y protejan por siempre en el Reino del Señor”.
-
 @ 00000001:a21169a7
2023-07-29 19:50:18
@ 00000001:a21169a7
2023-07-29 19:50:18August Sander (1876-1964), a prominent figure in documentary photography, played a pivotal role in challenging and resisting Nazi ideology through his work during the difficult years preceding and following Adolf Hitler's rise to power in Germany.
Sander's most famous project, "People of the 20th Century," stands as a testament to this silent resistance. This monumental body of work, portraying a broad cross-section of German society, presented a bold challenge to the Nazi notion of a "superior race".
Sander's strategy was to humanize all the people he photographed, regardless of their social status or race. His approach was neither to glorify nor denigrate, but simply to portray people as they were, a vision that was in stark contrast with the Nazis' racial ideology.
Furthermore, Sander sought to dismantle the Nazis' rigid racial and social categories. In "People of the 20th Century," the range of subjects is impressively broad: aristocrats, peasants, artists, manual workers, women, men, Jews, non-Jews. By juxtaposing these different categories, Sander underscored the diversity and complexity of German society, thus challenging the Nazi notion of a "pure race".
Despite the resistance he faced, Sander's courage never wavered. His photographs were confiscated and destroyed by the Nazis, and his book "Face of Our Time" was banned in 1936. Yet, Sander persisted, and while he was forced to switch his focus to landscape photography to avoid further confrontations, he continued to document his time's Germany until his death in 1964.
Sander's resistance to Nazi ideology was not frontal or violent, but subversive and silent. His camera became his weapon, and his photographs, his resistance. By capturing his subjects' humanity, he demonstrated that diversity, far from being a threat, is a source of richness and vitality in a society.
August Sander's work remains a powerful tool for understanding the social and political context of Germany in the first half of the 20th century. At the same time, his work continues to be a reminder of the importance of preserving and respecting human dignity, regardless of race, religion, or social status. In this sense, Sander's photography not only documents the reality of his era but also offers a powerful critique of Nazi ideology and a more inclusive and humanitarian vision of society.
-
 @ 5df413d4:2add4f5b
2023-08-01 16:20:12
@ 5df413d4:2add4f5b
2023-08-01 16:20:12October 2013. New York City.
Visiting. I am shopping downtown and my card is declined. I try it again. DECLINED. I find an ATM around the corner. DECLINED. I call the bank’s fraud department. They say they can’t help me. I find the nearest branch. They say they can’t help me.
Puzzled, I think hard — I had just deposited a sizable check (signing bonus from the consulting firm that would be my post-MBA employer) into my account…could this be the issue? I hop on the subway for the long slog up to Morningside Heights, to return to the branch where I made the deposit the day before. Arriving at the branch, where yesterday they happily received my check, I am now greeted with suspicion and hostility.
“Thank you for your loyalty and congratulations on your new job” was replaced with an interrogation by the branch Asst. Mgr. — “Why did you have the check?,” “ How did you get the check?,” “Who gave you the check?…” After about 20 minutes of this, they tell me that my check is“bad.” And because of this, the money will not deposited and my account will be frozen until further notice. No further explanation is given. My protests are ignored.
At 5pm, the Asst. Mgr. goes on her 1-hour “lunch break” and I’m told that the branch manager, who I can see playing on in his phone through the glass walls of his office, is “in very important meetings” for the rest of the day. The branch closes at 6pm.
I am forced to leave, dejected and confused, the situation wholly unresolved. I have traveled cross-country to New York City to deposit my signing bonus only to find myself stranded in the Metropolis, completely cut off from my finances, and all but directly accused of check fraud by my bank.
Thank goodness I was raised to I always travel with a bit cash…
Gatekeeping Is An Act Of Love
I did not have a term for it then, other than perhaps wacky-mustache cartoon villainy on the part of the bank. However, I now understand that what I experienced in that moment in 2013 was definancialization.
The bank, being the omnipotent gatekeeper standing between me and my money, decided to demonstrate that it was not, actually, my money. Rather, insomuch as it was in their custody, it was their money that they just let me believe was mine for the sake of some vague social convenience.
https://i.nostrimg.com/7317a37b9682c425b9d151675cf2999cbda50a841e5f56fd13586739f361e20b/file.jpg
Without an iota of exaggeration, this bank had, literally, a direct record of every single relevant financial datapoint on my person. I am certain that there was no better body of data indicating the near statistical impossibility of me attempting check fraud than the bank’s own customer file on me — a 3LA case file couldn't have done better...
Further, this being the location serving the Columbia University community, customers showing up with large checks from marque consulting firms was undoubtedly both commonplace and frequent. And yet, for reasons unknown, I was interrogated and had my account frozen, including money completely unrelated to the check deposit. To this day, as far as I can tell, this was all because someone, somewhere inside the bank decided that they didn’t believe that I could or should have a check of such as amount from such a company.
https://i.nostrimg.com/4b080c135288e7dfc34429f93cc9699c81fa4ca02948ac2bf0602366384abbb7/file.jpg
Things were ultimately resolved the next day. But only after I showed up at opening and sat outside of the branch manager’s office for several hours. Once it was clear that I wasn't going anywhere they finally, begrudgingly decided to take a second look at my situation.
It was around the same time that an inexplicable attitudinal reversal swept though the branch and it was back to all smiles and “Thank you for your loyalty…” My account was unfrozen. They even fast tracked the entire check amount into my account, on a Friday afternoon no less — something they previously said would take 7+ business days. It was all just damage control.
I assume this was because they got internal word back that my check, was, in fact, real — making their little interrogation game woefully unnecessary, if not outright discriminatory. And because a cursory glance at my customer file suggested that I might be just the type of person with the professional reach and savvy to pursue some type of legal/media action in response. Simply put, it now behooved them to play nice.
During this entire saga, it was their schizophrenic whiplashing of behaviors that I found most bizarre and offensive. They were the Judge, Jury, and Enforcer over my finances. They had the latitude to behave with impunity — and they knew it. There was, of course, never any recognition from that bank that something objectively wrong, deeply strange, or even just wildly inconvenient had happened. I was simply left to wonder, “Why?”
https://i.nostrimg.com/c850ae09b942775a2eab07d3883005bdda2402a363633f134497ac01610fc58f/file.jpg
A Slow Burning Thing
Understandably, the experience left me with a deep mistrust of banks that was both specific and personal — as opposed to the general African American cultural-historical mistrust, or the popular, populist Occupy/99%/MAGA zeitgeist mistrust of the day — though it certainly helped with both of those too.
Stranded in the metropolis, completely cut off from my primary finances — all but directly accused of check fraud by my bank.
I felt that I was completely trapped. The most I could do was change banks, simply swapping one capricious Bridge Troll for another. I saw no alternatives, and so I believed there were none.
Instead, this experience marked the opening act of what I now look back on as a long, headfirst slide into financial nihilism. At the time, I was operating under the naive and Talented 10th and elitist belief that my education and corporate credentials would shield me for these kinds of “misunderstandings.” Not so, not so.
With this illusion shattered, my shock and anger manifested as a period of high-octane, consumerist mania. If access to my money rested on the benevolent grace of the bank, I was better off converting it into things that could not be so easily taken or withheld — clothes, meals, travel, experiences, collectables,— and so I did. I spent money just to prove that I could — as though it would somehow cause harm to the vain gods of retail banking who had wronged me.
https://i.nostrimg.com/787fe778cad4e400129745ed907db57a328ba8e8da2ec32b693284264acf6fbe/file.webp (BEHOLD! Blowing several thousand dollars on clothes to prove that “no one could tell me what to do with MY money!” That said, I was FLY AF at business school that Fall...)
My desire to save in the banking system took a massive hit. Over time, this morphed into lazy ambivalence, if not total disregard, for the habit altogether. Rather than extinguishing debts, or building up savings, I would go on to burn through the entirety of my bonus and almost all of my excess income during my years in consulting with absolute gusto.
https://i.nostrimg.com/ed2a117e9338301fdba38bbb0c84aa26540175ec74a6da738d05bb16355073d4/file.jpg
Widening the scope, there were certainly other contributing factors to the chaotic state of my finances in the years that followed — gambling, chief among them (but those are stories to be explored later). Regardless, this was a pivotal moment in hardening a destructive “IDGAF” / “nothing matters” approach to personal cash management that would stay with me for a long time.
Missing Bitcoin
Reflecting back, this was easily my biggest “bitcoin miss” — a situation where present bitcoiners imagine how fabulously wealthy we might be if we had just understood bitcoin back then. Bitcoin certainly did exist in October 2013. In fact, it was sitting around 200 USD per coin and would hit 1000 USD a month later.
But alas, I had not even heard about bitcoin yet. And even if I had, my reaction to my bank’s malfeasance probably would have been aping into bitcoin on Mt Gox only to be obliterated by an even more devastating loss when that exchange collapsed in February of 2014. Truly, I shudder to think what that might have done to my psyche at the time.
So I “missed” bitcoin and my financial disillusionment would continue on. And It wasn’t just the situation with the bank, it was everything. Even long after I had shaken off my initial rage at being temporarily unbanked, I still chose not save. Though I couldn’t fully articulate it, I felt the act of saving to be pointless in the face of the ever-ascending price tags of the trappings of “responsible” Boomerist adulthood.
Homeownership, a “respectable” (re: large and expensive) wedding ceremony, and the cost of raising even one child through to college all seemed laughable financial fantasies to me — even if, on my earnings, this should not have necessarily been the case. Once I had accepted these things as impossible, my mind made them real…
And while there are plenty of criticisms that can be lobbed my way — after all, my personal financial mismanagement during this time was just that, personal— the recognition of personal responsibility does not erase the truth about the regressive behavioral incentives that our present distorted money system imposes on people.
Such is the nature of financial nihilism — why should I sacrifice to save or plan for things that I did not believe were achievable? I could see myself living the carefree, mobile, and high-cashflow consulting lifestyle perpetually in the now but I could not see how even that would afford any type of stable, rooted future afterwards. In that state, living high on the hog, nestled snuggly in rented comforts, was the end unto itself.
https://i.nostrimg.com/15b36a2297e115d9863e4263d5973e6ac7db349a5c01131b20b7e8cc713142a0/file.webp
How's Your Trading Going, King?
For many American Millennials, adult life has been an endless mad scramble to surf the Kali Yuga as the world careens from one mind-melting and testicle/ovary-shattering calamity to the next. 9/11, Byzantine wars in the desert, financial collapse, The Great Recession, global pandemic—each of these events obliterating whatever meager economic gains we might have made in the interim.
https://i.nostrimg.com/737258af9667eedd9faf8b3dd1eb3a029aa76aaf84373e1b131272a7d79eebfb/file.jpg
And, of course, the answer to each of these “once in a century” events has been to create ever more money to keep the music going. In parallel, every cash-rich Boomer with two brain cells, a generous pension, and the assurance of comfortable social security has raced to the exits to get out of dollars and into stocks and real-estate. Layer on an explosion of loose credit and a self-referential flywheel emerges — and it becomes easy, convenient actually, to believe that these two asset classes “alway go up.”
Such has been the experience of Millennials, Gen Z, and anyone counting themselves in the dwindling middle class — from 2002–2022 median home price has increased from 182,000 USD to over 450,000 USD, while median salary has only increased from 42,000 USD to 54,000 USD during the same period. Being the people, who as a group, command the lowest income and own the least homes or corporate equities, we have been forced to sit by, watching in numb, glass-eyed stupor as this asset inflation — and now just regular ol’ price inflation — rockets ever-skywards.
For those lacking the excess capital for property and stock investments, this dynamic is a regressive tax that favors immediate consumption to maximize declining purchasing power over savings, resulting in extreme financial fragility. And for those fortunate enough to afford significant investments, they are still incentivized to chase evermore speculative investments (which are often just toxic malinvestments themselves) and/or to join an increasingly parasitic rentier class just to beat inflation.
This is how FOMOing into objectively absurd “stonks” like Peloton or Zoom gets to be hailed as “making your money work for you!” How extractive landlordism (i.e. allocating newly created money to yourself via preferential loans, using that money to collectively drive up home prices, and then turning around to bleed rents out of the very people for whom your previous actions have made homeownership cost-prohibitive) becomes lauded as “F.I.R.E — Financial Independence, Retire Early!” And why blowing all your income on Cheesecake Factory, vape pens, and vacationing Tulum on credit is cool because of that one time Drake said “You Only Live Once!”
Despite whatever appearances to the contrary may be, people, generally speaking, are not stupid. Most people simply react to incentives. Many “irrational” human social behaviors are, at least minimally rational responses to irrational or perverse incentives — it is Charlie Munger’s “If you have a dumb incentive system, you get dumb outcomes” at scale.
Though I couldn’t fully articulate it, I felt the act of saving to be pointless…
Given this, we should all understand that our society’s present fetish towards speculation, rent-seeking, and over-consumption on debt are the more rational choices when money — the money that most of us have to work for — can be freely and infinitely created out of thin air and saving is perpetually debased. If the only expected return on the activity of saving is reduced future purchasing power, it should be no wonder that so few in our society engage in it. Perversely, in most cases today, one would have to be "stupid" to save...
https://i.nostrimg.com/8f266ac8fd7b13dd5888a3a85984f670ce9f29aca834199f9efba8ee6cd39352/file.webp
And note, I do not mean to disparage stock or property investment as a rule. There is a role for them in any healthy economy. However that role is certainly not to be a proxy for stable money. Yet this is how both are presently being leveraged in our economy, our society, and in our minds.
The rush into housing and stocks is simply a function of people seeking to trade infinite fiat or things that they believe are more scarce or will generate returns. This creates an artificial “monetary premium” in these assets — a portion of price existing only because the asset is being used as a substitute for money. And this momentary premium has now become wholly confused with the “real value” of the asset just as “saving” and “investment” have taken on interchangeable meaning for the average person.
Consider now if technological advancements enabled a new, truly scarce, infinitely divisible, uninflatable, permissionless global money to emerge organically from zero…
Eventually the very same people running up home prices and stock valuations would realize that there is no shortage of land and housing can always be build upwards, that stocks can always be diluted, and that control over either can be rescinded by decree — as we learned from Robinhood/Gamestop and renter (but not mortgage) forgiveness in 2021. And when this realization does happen, if such a new truly scarce, infinitely divisible, uninflatable, permissionless global money does exist, that is where they will turn…
The Long Way Home
In all, I would take 8 long years before I finally came to a deeper understanding of bitcoin — the meantime was spent floating through the hazy morass of working extremely hard and making “good” money but never really getting ahead. At absolute best I was treading water and at worse I was just sinking more slowly than some of those with whom I might be compared…Understanding bitcoin has completely changed all of this for me. Bitcoin fixes this.
First, bitcoin makes definancialization much more difficult. Gone is the worry that the bank, because I violate someone’s preconceived notions of who should or should not not have money, would be successful in an endeavor to cut me off from access to / control over my stored wealth. Bitcoin, unlike money in the bank, or even homes & property, cannot be seized or frozen by writ by a hostile actor — whether company or state or fellow man.
Second, bitcoin restores the act and objective of saving. As a saver, bitcoin allows me to project wealth into the future with full confidence against debasement. I can rest assured that any amount of bitcoin I own will always be x/21,000,000 of whatever total value humanity has decided to store in bitcoin. Shielded from the grift of monetary manipulation, I am freed to think and act longer term and I am unbound from pressures to speculate, gamble, rent-seek or worse, simply to avoid falling behind.
Finally, bitcoin provides a deep wellspring of renewed hope for the future. Grand or utopian as it may sound, I can certainly say that the statement rings true for myself and many other bitcoiners I know. Its not that bitcoin magically solves all of our problems, rather it is that bitcoin demands a fundamental change in worldview. Once we are freed to store wealth securely for the future, we come to a fuller realization that it is the more fragile things in life, the things that get discounted by the demands of the fiat rat race — family, community, relationships, reputation, ethics, stewardship, truth — are most important. Buttressed by the benefits that bitcoin provides, we feel energized to set about pursuing, building, repairing, and protecting these things. And we can more easily see that most other things simply don’t actually matter.
They say that bitcoin passes you twice. First as a party boat, then as a lifeboat.
https://i.nostrimg.com/e94a68ddf9338b829a7390086d73ec3b5b4b7a313fb3a932a15a79dd06926609/file.webp
A Fire In The Master's House Is Set
Finally, in closing, I’d like to provide the real life, stunning conclusion of what happened with the bank, or at least the branch, from my story.
A few months later, I received a middle of the night call from a lawyer friend in New York with whom I had discussed the situation. I pick up the line and the first words out of his mouth are “Where are you right now?” Once I assured him that I was not in New York, nor had I been in months, he shares — I shit you not — “That branch. Where you had that problem. Well, it all but BURNED TO THE GROUND...”
https://i.nostrimg.com/52d0421791887f8b6ecabecd9caf0fca1715e64bfd8aa5d0ac9feabc6b60a8d6/file.jpg
In fact, it was a 6-alarm fire, of some still apparently unexplained origin, that raged for nearly 30 hours, gutting the building completely from top to bottom. Thankfully, there were no serious injuries and the fire didn’t cause any major damage to the adjacent apartments or businesses. But man, what a way to go out! I feel like there’s a lesson in here somewhere, but I couldn’t tell you what it is...
https://i.nostrimg.com/4200d23b9494f7402f5e974bee3ee16bc90d095744bb181abfd36c52e4898366/file.jpg
In case you missed them, be sure to check out Journey Into Bitcoin 01 and 02. As always thank you for your time to read and engage. More on the way!
Postscript
In the spirit of inter/multi-disciplinary bitconery, here are a few top notch recommendations that, to me, relate to elements in this piece.
Books: The Alchemist, Paulo Coelho; The Fiat Standard, Saifedean Ammous
Music: Liberation, Outkast; Poetic Justice, Kendrick Lamar; New Millennium Homes, Rage Against The Machine
USE THE TOOLS: I believe that every person with exposure to bitcoin should have a fundamental minimum skillset that includes the ability to manage 1) self-custody and 2) buying/selling bitcoin permissionlessly. Here are some helpful resources:
Robosats: P2P bitcoin exchange using Lightning over TOR (pro-tip, use gift cards as your method of exchange for maximum privacy)
Bisq: P2P bitcoin exchange over TOR desktop app
A Final Though
It is dangerous and naive to assume that centralized exchanges and banks will always be there to allow retail users to buy and sell bitcoin. If and as the prevailing government-corporate power structure feels threatened by bitcoin, this may change.
Governments may shut down or seize bitcoin from centralized exchanges, and banks may block consumer transactions that they believe are related to bitcoin under the guise of “consumer protection.”.
Bitcoin is often a tool that you don’t know you need, UNTIL YOU NEED IT. But when you do need it, you REALLY need it and you better hope you can get your hand on some. The same can be doubly said for holding bitcoin in self-custody and knowing how to buy/sell bitcoin permissionlessly. USE THE TOOLS.
-
 @ 00000001:a21169a7
2023-07-29 19:42:42
@ 00000001:a21169a7
2023-07-29 19:42:42
If for Henri Cartier-Bresson the essence of photography was the decisive moment, for William Klein the defining factor is commitment. This assertion, made by Raphaëlle Stopin, curator of the 'William Klein. Manifesto' exhibition, couldn't be more accurate. At 91 years old and with multiple facets to his name - photographer, painter, filmmaker, publicist, writer, and activist - Klein has left an indelible mark on the landscape of art and photography with his irreverent commitment and radical approach.
Born in New York in 1928, Klein transformed mid-20th-century photography, creating an aesthetic language that evokes the rawness and emotions of a post-war society still to be rebuilt. Through his lens, we see a vibrant, dirty, mestizo, and ever-evolving New York. His unconventional approach, which mixed with the subjects he portrayed, broke with the standards of photography of his time, resulting in images that the white, Anglo-Saxon elite of the era found distasteful. However, his honest and committed vision ended up paving a new path in photography.
Klein began his creative journey in painting, where he already displayed a unique, free, and transgressive language. His entry into the world of photography happened fortuitously, by photographing his own paintings, and it was in 1956 when his vision exploded onto the scene, with the publication of 'Life is Good & Good for You in New York: Trance Witness Revels'. This work, the fruit of his immersion in the wild side of New York life, became a revolutionary manifesto that subverted the traditional principles of photography.
Klein's photographs were never just images. They were bold statements of freedom and experimentation, going against the conventions of his time. It was with his legendary book about New York that he became a disruptive figure in photography. Despite being published in France, Italy, and Japan, this book took 40 years to be published in the United States, a fact that evidences the rejection his raw and uninhibited gaze of the city caused.
But Klein was never content with just being a photographer. His enormous cultural baggage, inspired by figures such as Masaccio, Piero della Francesca, and the Bauhaus, propelled him to explore other forms of expression. In his work, we see the fusion of photography with painting, the 'painted contacts', where he applies paint to contact sheets with large brushes, creating a fusion of disciplines that is surprisingly innovative and evocative.
Today, at 91 years old, Klein continues to work, reinventing himself and reinterpreting his archive. Although his pace has changed, his commitment to his art and his language has not diminished. His legacy endures, and his influence continues to be visible in contemporary photography.
Is Klein a Leonardo of photography? Perhaps it's not an exact comparison. But, just like Da Vinci, Klein has shown a diversity of interests and skills that rivals any Renaissance polymath's. And, unlike Da Vinci, Klein is indisputably wilder and more committed.
In summary, William Klein is a visionary, a provocateur, and an iconoclast, whose work remains a source of inspiration and a challenge to today's artists and photographers. With his committed, free, and innovative gaze, Klein has demonstrated that photography, like any form of art, should always be an act of commitment and revolution.
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 01:05:50
@ 9ecbb0e7:06ab7c09
2023-08-04 01:05:50La madre cubana Yanetzy Luis Ruiz, acompañada por sus tres hijos pequeños, se plantó frente a la sede provincial del Partido Comunista de Cuba (PCC) en la ciudad de Santa Clara para exigir una vivienda digna donde residir. La noticia fue denunciada por el opositor cubano Librado Linares, secretario general del Movimiento Cubano Reflexión.
El caso ha llamado la atención debido a la valiente acción que tomó la ciudadana para hacer visible la difícil realidad que enfrentan muchas familias en la Isla. Según Linares, la mujer ya había sido trasladada previamente a un albergue, pero decidió regresar a la sede para continuar con su demanda.
El opositor destacó que la situación de Yanetzy y su familia no es un caso aislado, sino que refleja los graves problemas que no reciben una solución concreta por parte del régimen, cuyas inversiones se centran en la construcción de hoteles para el turismo extranjero.

Al publicarse la imagen de la madre en Twitter, un usuario compartió la idea de que todos los cubanos en tal necesidad requieren unirse para causar un impacto en el gobierno. “Cuando se le sumen todos los necesitados, a reclamar derechos es cuando se resolverán el problema. Por eso llevamos 64 años de miseria hambruna y represión, protestan dos, mientras los demás observan, esperando como buitres a recoger la carroña”, mencionó.
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ 5df413d4:2add4f5b
2023-08-01 16:20:01
@ 5df413d4:2add4f5b
2023-08-01 16:20:01December 2017. Shanghai.
It is mid-December 2017. In Shanghai. And I have just fallen victim to a crypto rug-pull scam.
A few days prior, I had been recruited into an “enthusiasts” WeChat group (WeChat is China’s premier social app, think FB + IG + CashApp, all in one, and then in Mandarin) for a Chinese crypto token. A friendly-faced Laowai (China’s half endearing, half slur for foreigners, particularly, white foreigners) had approached me at Cages Bar — a uniquely Chinese oddity of a place, a sprawling “American Sports” themed bar complex and a haunt for lost Westerners of all sorts — to share the good news.
This new friend, managed to sell me that this token would be the Honest-to-God FUTURE of supply-chain traceability. And what luck! Through meeting him, I was to join a group of favored insiders, privy to pre-market information on this earth-shaking new technology. Even luckier was that I was joining this group mere days before the project’s “biggest announcement ever” which was sure to send prices “to the moon.” It all sounded so very exciting!
Fast forward three days. The announcement has just dropped, token prices are moving quickly and parabolically to the upside across exchanges. Except for Binance. Where all of us in the group had our tokens. Inexplicably, Binance goes down at the EXACT moment when this news is released — “Due to recent increase in user growth, Binance will be preforming a system upgrade shortly after 2017/12/18 10:00 AM (UTC).
The upgrade will take approximately 20 minute” their message reads. Simultaneously, on another exchange, a whale (massive token holder, capable of single-handedly moving the market) liquidates several million dollars worth of tokens. By the time Binance is up and running again, the token is on a similarly parabolic price collapse. Never to recover.
I can confidently say that it is by such magic, one may turn several thousand dollars into several tens of dollars in mere days, or perhaps even just minutes!
Welcome to Shanghai! Welcome to Crypto!…I guess…
The School of Rug-pull Fundamentals
Here, I received a foundational lesson in the mechanism of “crypto." Specifically, rug-pull scam 101 - by which nefarious but convincing crypto marketeers target technologically ignorant retail “investors” to be the exit liquidity for the project founders and earliest backers.
The WeChat “enthusiast” group I had joined was nothing but a pump and dump shop. The group members, rather than being privileged insiders were full-on dupes - serving as both free marketing hype and the exit dumping ground for the project founders. Peer-pressure, social proof, and faux camaraderie were applied by the truckload to induce us to promote the token and to bring in others, yet when the time came, we all found ourselves locked out of the party by forces seemingly far above and well beyond our comprehension. And this is when the real insiders exited.
https://i.nostrimg.com/a91530006a6070b14fcc935e4c88db7640f27b92df86e5f7ad1b015978265d06/file.jpg
However, on that brisk Shanghai winter evening in 2017, I knew none of this. I was the worst, or rather the best kind of mark — the kind with enough broad educational and professional achievements as to be very self-assured in their own intelligence while also being completely oblivious to their area-specific ignorance and inexperience - particularly on this "new" technology, called "the blockchain."
That I was possessing of such qualifications should surprise no one who has ever worked with management consultants. At the time, I was one — bright-eyed and bushy tailed, newly minted on a full-time international assignment to China. In reality though, the depth of the information asymmetry arrayed against me in this situation was tantamount to me having negative information while fully believing that I was some kind of anointed insider. What fun!
So how did I get here? Well...
Borderless
I landed in Shanghai in January of 2017, a stranger in a strange land. My arrival in Shanghai uncovered an interesting problem. A few months in, I realized that all of my money was sitting in RMB, in a Chinese bank account, yet I still had financial obligations in the United States, dominated in USD, along with a fast-dwindling USD account balance to support these obligations...
It was at this time that I discovered that the process to transfer money outside of China was arcane - requiring at least two months of planning, several trips to the Chinese tax authority, reams of paperwork, AND support from an internationally accredited employer. In short, a bureaucratic dog-and-pony show replete with unnecessary but entirely purposeful friction and obfuscation. But such is the squarely anti-free market Great Game of big-power nation capital controls.
It was this problem that spurred my first contact with bitcoin. I was searching for the best and most efficient way to transfer money to myself across borders. This eventually brought me to various articles and YouTube videos about bitcoin. From there, I got a Coinbase account (which worked in the China at the time), linked my bank account, and figured out LocalBitcoins - through which I could buy bitcoin peer-to-peer in RMB, and then transfer that bitcoin back into USD.
FUN FACT: While bitcoin had already been “banned” by the Chinese government several times by 2017, it was still legal to trade p2p. Also the largest RMB-for-bitcoin sellers on LocalBitcoins all appeared to be Africans. And I mean to the tune of thousands of bitcoin moved volumes. It would seem that perhaps large Chinese bitcoin holders may have been using Africans as plausible deniability frontmen to move in and out of large sums of bitcoin over Chinese social payment rails. The More You Know!
https://i.nostrimg.com/d97d6f67fb3db44d0fd38cc36059156c2cf7f07ea3de3fbec3902b9741c2603e/file.jpg
And just like that, I managed to Forrest Gump my way right into one of the most relevant, important, revolutionary — and in the West, overlooked — use cases for bitcoin - making money borderless, facilitating international value transfer in a way that completely obviates the rent-seeking artifice of arbitrary financial controls. But for all of that, I still couldn't see it. I was happy with what bitcoin did for me in that moment, but I failed to see any larger implications - I thought of it a novel, but certainly not anything ground-breaking. Further, my trust in the system was still too strong - believing on some deep level that the banks, both Chinese and US, truly wanted to help me but where beholden to cumbersome processes and regulations imposed on them from above.
Even in this very first exposure to bitcoin, it addressed a real and pressing problem for me and dramatically improved freedom of access and utility of my money - allowing me to transfer money back my USD bank account on-demand. I had a problem. Bitcoin fixed it. And all of the villagers rejoiced! …Or they would have if that had been the end of it. But as fate would have it, my first brush with bitcoin also coincided with the breakout of the wild 2017 bitcoin & crypto bull market run.
Initially, I just bought a bit of bitcoin to solve a problem and thought little of it. But when the bitcoin price started to take off (aka Number Go Up, or “NgU” in internet parlance), I had to take another look. But this time, I would be caught in the balmy, Icarian up-currents of tech speculation and good old fashioned get-rich-quick greed. But, me — I was in it for the technology, of course...
https://i.nostrimg.com/323487be17ae780a21f52519c995569f1794df55b02c796d666fa24147f37990/file.jpg
All My New Friends
And so, I began to research bitcoin and then "crypto" more deeply. In so doing, I “learned” that while bitcoin was “the father of all cryptos,” it was actually “old” technology. Bitcoin was slow, environmentally wasteful, limited in capability, and destined to be overtaken by newer, “better,” cryptocurrency technologies such as Ethereum or XRP. Knowing no better, I accepted these silly falsehoods, convincing myself that bitcoin’s core value was simply its tenure. Being more established, bitcoin was just a marginally less volatile asset in a sea of horrendously volatile, and otherwise interchangeable, crypto tokens.
But there was opportunity here too, I sensed. The real innovation in the space, I believed, would ultimately be led by other projects. That being the case, my incentive then was to “study the space and place calculated bets" (an MBA euphemism for wild-eyed speculation). Why hold onto Bitcoin’s AOL, when Ethereum is clearly going to be crypto’s Google? With any new technology, the first mover is always overtaken by a more innovative copy-cat, right?? RIGHT???
Moreover, I was desperately in need of Western friends. And knowing I’d find them in droves wherever there was speculative money to be had, I dived headlong into the Shanghai “crypto scene.” On the standard “Hero’s Journey” this is where a mysterious but benevolent, Gandalf-like mentor would have appeared to shepherd me through the peaks, valleys, and pitfalls of this new space. Obviously, this is not what happened. Instead, over freeium beers in the vaunted Millennial Chic common areas of so many Shanghai WeWork offices, I would meet some of the most colorful characters of my time in China...
A whip-smart but spectacularly sketchy Baltic fellow of significant, though indeterminate means who argued that any blockchain project that managed to successfully prevent supply chain malfeasance who see the project founders dismembered by some Eastern European mafia. Only half-jokingly, he suggested, at his direction.
A Middle Eastern “precious metals trader” who I later ascertained was probably more akin to a conflict minerals smuggler looking to use excitement and ignorance around “traceability on the blockchain” to wash his wares.
A South Asian “crypto-entrepreneur” who claimed to have a method, leveraging "blockchain technology," to swap large sums of physically delivered Chinese cash (think suitcases full of red bills) into infrastructure investment projects in Myanmar.
Several personally modest but obviously wealthy South American scions riding out political instability in their home countries while funneling money into ICOs (Initial Coin Offerings - crypto's answer to IPOs) with reckless abandon.
An American who shared, unsolicited, his pre-China 3LA (Three Letter Agency) background at first meeting, though I suspect he may have been telling a dangerous and stupid lie.
An obvious sex-kompromat honey-pot Chinese couple who described themselves as “crypto-observes” and who were, at a minimum, actually gathering intelligence for something. Fit and flirty in a way suggestive of some kind of open-door polyamory, and a little too fluent in English. Seemingly at every event and always hugged up onto any Westerner that seemed to be gaining influence in the space.
And finally the long tail of Moonboys (idiot gamblers who fashion themselves tech/investment mavens), minor conmen, “cross-border currency arbitrage” consultants, LBH (Loser Back Home) English teachers, broke college students, and an ever shifting menagerie of hypemen-simps riding the coattails of Shanghai's laowai crypto-influencer of the week.
It was in this fast-moving and footloose “Anything goes and we’re all gunna get rich AF!” environment that the December supply-chain token “opportunity” appeared to me. And of course, dazzled by fantasies of instant and meteoric crypto wealth, I went for it and I got burned right along with all the other Lambo-chasing chumps.
I was the worst, or rather the best kind of mark — the kind with enough broad educational and professional achievements as to be very self-assured in their own intelligence while also being completely oblivious to their area-specific ignorance and inexperience.
But in retrospect it could have been far worse. I could have put more money into the rug-pull or it could have been a straight-up wallet draining scam. And while I still had miles to go and years of learning ahead of me before fully eschewing “shitcoining” (the act of buying non-bitcoin crypto tokens in a state of deeply degenerative and highly speculative mania), this experience did, thankfully, give me the frame of reference to avoid further, similar insider malfeasance going forward…for the most part...
https://i.nostrimg.com/4e999806bd57e4e57c710234b2970597cb8aec37c9b5afa57d175e6e5bbc0c8e/file.jpg
Do Cryptos Dream of Electric Stupidity?
The silver lining here was that the speculative extremes and clearly questionable mental acuity of some of my new “crypto friends” gave me pause and cautioned me to anchor, relatively speaking anyways, to rationality and search for truth, as my consultant training so demanded. Though, I cannot in say good faith that this was intended in an entirely ethical or altruistic way at the time... After all, the fundamental role of a management consultant is to understand the truth more deeply than others so that you may choose when to best reveal or obscure it for social, political, and or economic gain — especially when you've assessed that you significantly outclass those around you intellectually.
That said, being an American (and so legally barred for participating in many ICOs) and a rare résumé on the scene, I came to be viewed - hilariously - as something of “the adult in the room,” to some. I would even eventually even sit down with a few founders to advise on their well-intentioned but deeply flawed and over-engineered crypto projects...
As I rode the 2017 bull-market wave up and then back down again (and where greed intervened to prevent me from selling the top, or even at a relative top), my perspective on the space matured.
Why couldn’t anyone articulate what actual, real-world problem their project was solving?
Why were so many projects’ assumptions around token usage (and therefore value) based on artificial needs that the project protocol itself created, or worse, inexplicably bizarre misunderstandings of incentive-driven human behavior?
Even the most lucid and well-presented project I encountered was still predicated on several other paradigm shattering technologies coming to the fore. They may as well have ended their pitch with “And as you can see here — when SkyNet, teleportation, Replicator, and Lightsaber technology all reach ubiquitous global scale (and we project this happening by Q3 2021 ± 3 mo) our protocol will be poised to capture MAXIMUM value, etc etc…”
The entire space came to resemble an unironically earnest masterclass in absurdity. Because that is, ultimately, what it was. And so, I developed expertise in tearing crypto white papers apart over their gibbering technical Esperanto and nonsense logic, ideally, in front of as many people as possible.
I made no attempt to hide my annoyance at every new project’s “graphic salad” or “Flying Spaghetti Monster” tech stack representation, alway a meaningless clownshow of sleek-designed neon-pastel toned boxes, cylinders, arrows, and lines indicating some much "obvious value."
https://i.nostrimg.com/89115440530a88c59e8358e3f8fbf95369f0e1490591455a2565da0f55d43606/file.jpg
I came to regard every crypto project as, at absolute best, a solution looking for a problem. A viewpoint that still holds to this day. No “cryptocurrency expert” I’ve spoken with, no matter how well-educated or well-meaning, has ever been able to articulate to me how a given “blockchain” solution solves any real (non-speculative, non-gambling, non-financial crimes based) problem better than existing solutions, imperfect as those may be.
Anything goes and we’re all gunna get rich AF!
But most of all, I was perturbed because we had very much not gone “to the moon.” If anything, my crypto holdings seemed to be, boldly, charting a path for the Marianas Trench, perhaps an equally ambitious though categorically different feat.
This disillusionment with “crypto” though healthy in retrospect, unfortunately also spawned an apathy towards bitcoin, what would ultimately become a long pause that significantly slowed my bitcoin understanding.
If there was any mentor in this situation, it was the market itself, all cruel vagaries, malicious intent, and so many rows of glistening, blood-stained teeth. As the long 2018–2019 crypto winter set in, defeated and financially depleted, I, like so many others, assumed (rightly) that crypto was a scam and (wrongly) that bitcoin was “dead.” I resolved myself to let go of all expectations so that I might be pleasantly surprised if the bitcoin price ever, for some unfathomable reason, did recover.
How could I have known how many unfathomable things would transpire both in the world and in my own life by the time that this would actually come to pass…
比特币死了!比特币万岁!(Bitcoin is dead! Long live Bitcoin!)
Thanks so much for reading Part 02 of my story! I look forward to any comments or feedback, it brightens my day and inspires me to keep writing! And in case you missed it, you can read Journey Into Bitcoin 01 here.
Postscript
In the spirit of inter/multi-disciplinary bitconery, here are a few top notch recommendations that to me are related to elements in this piece.
Music: Can’t Con an Honest John, The Streets; Dip, Young Fathers; Everything Is Recorded, Everything Is Recorded
Movies: No Man’s Land (2013), Shang-Chi (2021), The Message (2009)
If you’re ever in Shanghai: Sober Company (fine dining, 4 bars concepts at venue, 1 is hidden), Speak Low (Shanghai’s original speakeasy), The Odd Couple (East Meets West Pac-Man Bar)
-
 @ 00000001:a21169a7
2023-07-29 08:32:13
@ 00000001:a21169a7
2023-07-29 08:32:13Robert Frank, born on November 9, 1924, in Zurich, Switzerland, was the child of Rosa (Zucker) and Hermann Frank, of Jewish origin. Though his family managed to remain safe during the Second World War in Switzerland, the looming threat of Nazism informed his understanding of oppression, invariably seeping into his subsequent work. Frank was drawn to photography partly as a means to escape from his business-oriented family and home. He was mentored by various photographers and graphic designers before he crafted his first handmade book of photographs, "40 Photos," in 1946. At the age of 23, Frank migrated to the United States, seeking to broaden his photographic horizon. He found employment in New York as a fashion photographer for Harper's Bazaar. However, the rigidity and artifice of fashion photography failed to satiate his creative yearning. He soon quit his job and embarked on journeys through South America and Europe, creating a second handmade book of photographs taken in Peru.
Upon returning to the United States in 1950, Frank began to experience a transformation in his photographic perspective. Influenced by his disillusionment with the frantic pace of American life and its emphasis on money, he began to perceive America as a place often desolate and lonely. This vision is reflected in his subsequent photography.

The aesthetic context of the subjective photography of the 1950s, which Frank adopted, was marked by a paradigm shift in how photography was understood and practiced. It involved a move away from the apparent objectivity and neutrality that characterized documentary and journalistic photography, to adopt a more personal and subjective approach. Images ceased to be seen simply as faithful representations of reality to become the photographer's personal interpretations.

In this context, Robert Frank stood out for his direct, unadorned style. His photographs did not aim to beautify or idealize reality, but to capture it as it is, with all its imperfections and contradictions. For Frank, the camera was a tool to explore and question society, rather than merely documenting it. His most emblematic work, "The Americans," first published in Paris in 1958, is a chronicle of his journey through 48 states of the United States. The book, composed of 83 images selected from 28,000 shots, offers an unconventional and critical view of American life. Through his images, Frank portrays a society marked by racial and class inequality, loneliness, and helplessness. The images in "The Americans" are often dark, blurry, and off-kilter, contributing to a sense of unease and instability. Robert Frank continued to work intensely throughout his career. Here is a list of some of his most representative works, ordered by year:
- 1946: Published his first handmade book of photographs, "40 Photos."
- 1947: Moved to the United States and began working for Harper's Bazaar.
- 1950: Participated in the group exhibition "51 American Photographers" at the MoMA and published his second book of photographs from his journey through Peru.
- 1955: Received a Guggenheim Fellowship to travel and photograph the United States, a project that would result in "The Americans."
- 1958: Published "The Americans" in Paris.
- 1959: "The Americans" was published in the United States.
- 1961: Had his first solo exhibition at the Art Institute of Chicago.
- 1962: Exhibited at the Museum of Modern Art in New York.
- 1983: The French magazine "Les Cahiers de la photographie" devoted two special issues to his work.
- 2008: A new edition of "The Americans" was published to commemorate the 50th anniversary of its first publication.
- 2009: The exhibition "Looking In: Robert Frank's The Americans" was shown at the National Gallery of Art in Washington D.C., the San Francisco Museum of Modern Art, and the Metropolitan Museum of Art in New York.
Robert Frank's influence on contemporary photography is undeniable. His subjective and critical vision opened new pathways for understanding and practicing photography, shifting it away from conventionalism and closer to a more artistic and personal conception.
-
 @ 7f4f672a:c184579e
2023-08-03 20:45:04
@ 7f4f672a:c184579e
2023-08-03 20:45:04“Write on Obsidian and publish directly to Nostr.” A sentence that makes no sense to most people. I made a plugin for those who do 😅 Check it out my plugin on Github for download. It'll be available in the community plugins downloads section soon (in review now)! For anyone else who’s curious, WTF am I talking about? #obsidian #nostr
Nostr represents the future of how we will communicate and distribute the written word: decentralised, free, independent, incorruptible. @fiatjaf created it in 2020 and it’s been growing since, offering a new hope for content creators tied up by Big Tech and their walled gardens
On Nostr you own your social experience. Keep followers, posts, likes, and replies across platforms. Some people won’t care, but for creators - this is key! People use Nostr clients to see and post stuff - WTF’s a Nostr client ? 🤔
Clients are websites/apps that connect to the Nostr network. Think of them like different doors to the same room – your content and followers stay the same, whichever door you choose.🚪🚪 I’m not going to link a client here because Elon owns this door and could close it on me.
He also owns the room. On Nostr, nobody owns the room, you can just build or use doors to enter it. It’s the very early days. But lot’s of people, including @jack (who introduced me to it, thanks Jack) are excited! Which leads me to Part 2 of this spiel - Obsidian?
Obsidian is an amazing markdown editor, note organiser, and idea synthesiser: the perfect tool for writers. It’s free to download & use here : https://obsidian.md/
You can use it to take notes, write, blog, make shopping lists, or conduct research! Whatever! It’s easy and clever (check out note linking). Your notes are your own and easily portable - again, you’re not tied up in a room! Also, 1000’s of free community plugins make it great!
Long story short - Obsidian and Nostr are a match made in heaven. For writers - I hope this plugin can help you publish seamlessly, and open up a new world. I plan to use it myself to write & publish more. That’s proving harder than the software 😅 Now where’s my pen..
-
 @ b49df4b0:588be5df
2023-08-03 19:49:47
@ b49df4b0:588be5df
2023-08-03 19:49:47Note: originally published on my personal blog (testing Habla).
While looking for a nice local 2023 calendar, I was recently lucky to learn about the Oregon Natural Desert Association (ONDA). Their mission is to protect, defend and restore Oregon’s high desert for current and future generations.
Deserts are something. At first look, nothing seems to happen in a desert, but if you take the time to look and listen carefully, you’ll soon realize a lot is going on. Plus, there are many types of deserts, and no definition fits them all.
I love hiking in the desert or just driving through it. I enjoy stopping at the side of a road that barely anybody transit, stepping out of the car, getting a little away from it, and observing my surroundings in complete silence. But I’ll admit, I also fear it a bit. It’s not my natural environment, and I don’t know much about it yet; I feel vulnerable and am not always comfortable spending long periods in it. I need more exposure and a lot of learning to become more and more at ease.
Going back to ONDA, I purchased their calendar and it’s hanging on the kitchen wall, the first page waiting for January to be turned. I also learned several ways to help them, some involving projects on the terrain. Will that be how I better know the desert and become friends with it? I’ll have to think about that!
-
 @ 5df413d4:2add4f5b
2023-08-01 16:19:47
@ 5df413d4:2add4f5b
2023-08-01 16:19:47April 2021. Honolulu.
It is early evening now. In a few minutes, the sun will set over Ala Moana beach, a short distance west of where I am. My apartment, on the 11th floor, overlooks the Ala Wai canal at the corner of McCully — always traffic, always sound. My balcony’s sliding doors and jalousie windows are open, a salty breeze filters in as the low sun casts a golden glow over the south face of the Ko’olau Mountains in the distance and the city of Honolulu in the fore.
But for me, in this moment...I am hunched over my laptop, intently focused on the open brokerage page in front of me. I press “Confirm,” instantly selling all of the stock in my personal investment account. When the money clears into my bank account, I convert it all into bitcoin and then move it into cold storage.
Today, I have become a bitcoiner.
Origins
This was my personal “Bitcoin Moment.” The moment when I realized that, even with the most conservative outlook, there is basically no other “investment” that I could make that will deliver anything close to the returns I expect from bitcoin over the next 20–30+ years. Embracing this understanding, this was my moment of stepping over the threshold, remorselessly going "all-in." Selling off assets (stock) that almost everyone — from my most educated and accomplished friends, to my mother, to the random Spring Breaker from Jacksonville stumbling down the Waikiki strip — would (and at different points, did) tell me to hold, in order to increase exposure to bitcoin - which they felt was unacceptably risky, if not an outright scam.
Today, my views have evolved even further from that moment. I no longer think of bitcoin as an investment, because bitcoin is not an investment. Bitcoin is money. Full stop. And therefore, the act of holding bitcoin is saving. I no longer think in terms of USD returns on bitcoin, as this implies an intention to sell. Instead, I now think in terms of value capture, purchasing power per satoshi (the smallest unit of a bitcoin — as there are 100 pennies to a dollar, there are 100M satoshis to 1 bitcoin). In my present view, that dollars, or euros, or yuan — all of which are functionally infinite — can be traded for bitcoin, which is absolutely finite, is simply a lucky quirk of happenstance. The great fortunate of randomly coming into an understanding of bitcoin at time when the market misunderstanding of this new money is still so gross that anyone would willingly part with bitcoin in exchange for government currency.
But let me not get ahead of myself. My present bullishness on bitcoin is not what's important here — my feelings about bitcoin will be examined in stride throughout the writings to come. Rather, what I am interested in here is the journey, “how the heck did I arrive at my 'Bitcoin Moment' in the first place?”
This is the question that has captured my mind and now inspires me to write, to examine my own long and meandering path to "becoming a bitcoiner." For instance, I mark my bitcoiner awakening as April 2021 — but then again, maybe that’s not entirely right — did I actually become a bitcoiner in that moment, or had I already been one in many core ways (perhaps even in ways that I did not realize) and I just came to the discovery of this pre-existing personal truth? Was it an act of becoming OR, rather an act of committing to being a bitcoiner? And then what does it even mean, to be a bitcoiner? Is this even an appropriate question to ask?
I no longer think of bitcoin as an investment, I think of it as savings
Attempting to answer, or at a minimum, engage with, these questions has kicked off an experiment of deep introspection, an exercise of peeling back the onion, and untangling the thread of my own life up to this point. It has required self-reflection on foundational lessons from childhood, deconstruction of habits of mind from my education and upbringing, examinations of professional experiences and group associations, questions of identity, specifically being an African American in a global world, insights from far-flung travel both abroad and here at home (the US), and rumination on so many near misses — when I could have “gotten” bitcoin much earlier had it existed then or had my views on things been juuust so slightly different.
Clubhouse Bitcoining
While not the starting point of my engagement with bitcoin, I can say unequivocally that catching ‘The Clubhouse Moment” from Jan 2021 onward, was a particularly formative experience.
For future reader's Clubhouse is/was a VoIP group chat mobile app. A literal chat room, seemingly bringing the entire internet full circle from text-only chat rooms of the dial-up AOL days. Clubhouse launched in the deepest point of the US COVID pandemic/hysteria an scaled an break-neck speed, filling the wailing void of lost human interaction in everyone's totally collapsed and locked-down social lives.
Through Clubhouse, I was able to first observe, then engage with, and finally join one of the most varied, talented, resourceful, deeply interesting, and utterly strange groups of people I’ve ever had the great fortune to associate with — bitcoiners. Intelligent to the point of wild arrogance, studied to the point of oddness, traveled to the point of weird suspicion, insightful to the point of deep disquiet, convicted to the point of cultish religiosity, accomplished to the point of well-warranted disbelief, honest to the point of seeming bizarre, edge to the point of being fringe.
I do not mean any of the above as harsh criticism or insult, in fact quite the opposite. On the 9-box Alignment System chart, bitcoiners are the Chaotic Column...and usually the “Chaotic Good”. If there were a Bitcoiner’s Mantra, it would be something like “Do no harm…unless they deserve it.” With bitcoiners you find a paradoxical union of unique, even freakish individual strangeness, with equally strange (as compared to “normal society” or "normieland" as we say), yet broadly shared positive ethical standards that makes distributed, and even anonymous, trust possible between counterparties — both economically and, increasingly, socially. In all, I’d assess that everyone I’ve encountered who really “gets” bitcoin is 3–5 standard deviations out from the norm on some characteristic or another…again, usually, in a good way.
Oh, What a Time to Be Alive
To me, this is a pattern that is simply too fascinating to ignore. To have any real understanding of bitcoin today, even as bitcoin is already more than 14 years old, is incredibly strange in its own right. That so many who have acquired this still extremely niche understanding should also be so abnormal as to be outstanding suggests to me that the two may be connected in some way. I truly believe that future society will look back and deem that to have gained clear-headed understanding of bitcoin pre-mass adoption (or “hyperbitcoinization”), is to be deserving of study. I certainly believe this — right now, today. That said, having neither the means nor the general inclination to travel into the Escheresque mouth of madness that would be required of a broad psychographic study of present day bitcoiners, what I can contribute, however, is an open examination of my own story. My Journey into Bitcoin.
Every bitcoiner, like Batman or The Joker, has an “origin story.” It is such a common trope in the community that many bitcoin conferences will have a panel dedicated entirely to 4 or 5 people sharing their origin stories while simultaneously riffing new insights off of each other in real time. If you are a bitcoiner already, consider yourself very, very lucky. It doesn’t matter if you became a bitcoiner in 2010, 2017, 2021, or 10 minutes ago. We are incredibly early, and it takes an almost magical, borderline metaphysical series of events in life to have come to a grounded understanding of bitcoin where we are today. If you understand bitcoin today, you’ve been through a giant plinko game where everything had to go exactly right, to place you out on the extreme tail. This is why it is not totally unreasonable and not entirely unhinged when many bitcoiners say “bitcoin found me, not the other way around.” I, for one, absolutely feel this way.
That so many who have acquired this still extremely niche understanding should also be so abnormal as to be outstanding suggests to me that the two may be connected in some way
Bitcoiners constantly say that the most important thing one must do over the next 10–20 years is simply “hodling” (i.e. acquiring bitcoin, holding in secure self custody, and not selling). However, I believe its must more than that. If we intend to hold our bitcoin successfully over the long-term, it becomes critically important to understand how and why we each, individually, got here to be in this conversation now. Self-discovery, self-awareness, self-confidence, and the resulting self-actualization are essential input to self-sovereignty. And individual self-sovereignty is the foundation for the sovereign families and sovereign communities that we must set about creating if we want bitcoin, and far more pressingly, the very concept to individual rights and freedoms to mean anything against the very real threat of an ever-more atomized and digitally-enclosed future.
How can we build if we don’t understand, and when necessary, repair and strengthen, our own foundations?
So now, inspired but the likes of Cryptograffti and Brekkie von Bitcoin, artists who share the process of their art with BT (Bitcoin Twitter), I hope to make my exercise of writing an open experience. I look forward to comments and feedback from other bitcoiners or anyone interested enough to read and engage, bitcoiner or not. Most of all, I hope the examination of my story may inspire others to share their stories and to engage with their own self-discovery more deeply through the lens of how bitcoin, and the bitcoin community, has impacted their lives.
Thank you for making it this far, I am truly humbled. This is only the beginning. More to come soon!
Postscript
In the spirit of inter/multi-disciplinary bitconery, here a few top notch recommendations that are on my mind. Would love to hear some of yours!
Music: Plantasy, Resavior; Esc(Holding Back), Model Man; Darling, Esbe
Books: The 7th Property, Eric Yakes; The Paper Menagerie, Ken Liu; The Alchemist, Coelho
If you’re ever in Honolulu: Ho’omaluhia Botanical Garden, Valley of the Temples, Tane Vegan Izakaya, The Blind Ox, Lanikai Beach
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:33:21
@ 57fe4c4a:c3a0271f
2023-08-03 17:33:21👥 Authors: Anthony Towns ( nostr:npub17rld56k4365lfphyd8u8kwuejey5xcazdxptserx03wc4jc9g24stx9l2h )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 5833
Messages Summaries
✉️ Message by Anthony Towns on 03/08/2023: The author clarifies their intention to encourage research on monetary-based denial-of-service deterrence and provides a rough proof-of-work as an approach to explore. They also discuss the challenges of implementing fees based on the time an HTLC is held.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 5ada3677:7c21c9db
2023-08-01 15:53:06
@ 5ada3677:7c21c9db
2023-08-01 15:53:06差不多每天赴一座古城,中世紀古城,daytrip,日帰り,當天來回的小旅行。為每一座古城長噓短嘆驚艷不已,這是我半輩子裡,去了最多古城的一段日子,不能更過癮,不能更感慨。
如此一日復一日地逛古城,考驗腳力,更考驗腦力。營養太豐富,真真來不及消化,用力行走,用力看很多書和影像惡補自己。
這些城,查查資料,在wikipedia上,前世今生大多一頁都沒有寫滿,中文資料常常只有幾行字。靠包子查西班牙文的資料,翻譯給我一些。
古一點的,相當於我們的宋朝;近一點的,相當於我們的明朝。




Bergara,貝爾格拉,人口15000僅僅。下車往城中走,正是中午休息時間,行人寥寥。迎面過來一枚中年男,看見我,很愉快地站下來,眉飛色舞朝我說了一大段。我文盲的苦,只能微微笑過去。包子走過來,才聽明白,人家問我,你們覺得,我們足球隊裡的日本球員,久保建英,踢得好不好?
原來如此,是把我們母子當成日本人了。我們聊了幾句足球,西班牙北方的巴斯克人最熱愛的運動之一。英超二十支球隊,裡面倒有三個主教練是巴斯克人,根據去年的資料。
巴斯克人的真誠友好,幾乎是舉世聞名的,包子說選擇此地居住,這個也是很重要的原因。某年夏天,他走朝聖之路,路過Bilbao,看見地鐵裡,上來一輛嬰兒車,人人伸手幫忙的樣子,一下子印象深刻得不得了。這些天我們在古城內外晃,也看到老人搭車沒有零錢,馬上有老阿姨挺身而出幫忙買車票請老人安心坐車。
 一家心理醫生
一家心理醫生 當年的科學院
當年的科學院 修道院的門
修道院的門
回來講Bergara。
走十分鐘,到古城中心,然後就寸步難行了,一步一景,壯麗得脖子都酸了,舉著手機長噓短嘆啊啊啊,城中教堂的大鐘敲得噹噹的。
此地有一座至今美好的科學院,電燈泡裡用到的鎢絲,是此地的科學家發現的。
一座至今活著的修道院,十五世紀的,沉靜穩重,芬芳如夏日玫瑰。灰衣白巾的修女嬤嬤,於烈日裡飄過。西班牙一些女孩子,受到好的教育,至今是通過修道院系統。



看完古城中心,我們爬一點山坡,半山腰上古樹參天的園子裡,躺下來,體會「人閒桂花落」以及「鳥鳴山更幽」。
很奇怪,常常在歐洲的景致裡,想起唐詩和宋詞。









 如此小城,海報水平很高,商標水平很高。
如此小城,海報水平很高,商標水平很高。夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24 -
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:04
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:04👥 Authors: GamedevAlice ( nostr:npub18zra06q690wae9ty6sxxwf3jdcxuan2n4dq0ldynjddzz894jqesvhlw24 )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 13392
Messages Summaries
✉️ Message by GamedevAlice on 03/08/2023: The author realizes that storage is not the main issue, but rather the time it takes to sync the blockchain. UTreeXO is a promising solution.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 000003a2:e3b014e6
2023-08-01 11:51:35
@ 000003a2:e3b014e6
2023-08-01 11:51:35NDK noob question.
I'm trying to keep an indefinite subscription on the server side.
The issue here is that, slowly after receiving an eose, I'm being disconnected from the relay pool (pool stats show 0 connected relays).
Tried reconnecting on pool relay:disconnect (using ndk.connect() and ndk.pool.connect()) but it doesn't seem to be working.
Kinda running out of ideas on what's causing this. Perhaps I'm misunderstanding/missing something? Any tips on what I should look at/what to debug to find the issue?
Sharing the code below.
create ndk instance
const ndk = new NDK({ explicitRelayUrls: EXPLICIT_RELAYS, cacheAdapter: redisAdapter });connect to relaysndk.connect(2100) .then(() => { console.log(`Connected to relays`); });create subscriptionsubscribe({ kinds: [1, 30023], '#t': [Config.HASHTAG], since: Date.now() / 1000 - 45 * 60, }, { closeOnEose: false, cacheUsage: NDKSubscriptionCacheUsage.PARALLEL, groupable: false});subscribe function
``` const subscribe = ( filter: NDKFilter, opts: NDKSubscriptionOptions ) => {
const sub = ndk.subscribe(filter, opts); sub.on('event', onEvent); sub.on('eose', () => onEose); sub.on('close', () => onClose);}; ```
asknostr #ndkdevkit #nostrdevs
-
 @ 32dc4f25:f95ddcce
2023-07-27 11:56:04
@ 32dc4f25:f95ddcce
2023-07-27 11:56:04In Nostr, "smart clients and dumb servers" refers to a communication model or architecture where the clients (smart clients) have higher logic capability and autonomy, while the servers (dumb servers) have lower logic capability and passive execution.
Welcome read more of my articles form decentralized long content platform-- yakihonne.com
Smart clients refer to client applications or devices that possess higher intelligence and processing power. They can make autonomous decisions and perform specific tasks, including handling business logic, processing data, communicating, and coordinating interactions with other services. In Nostr, smart clients play an active role, responsible for controlling the communication flow, processing data and protocols, and executing necessary business logic.
Dumb servers, on the other hand, refer to servers with lower intelligence and passive execution capability. They are designed to perform basic data storage and transmission functions without handling complex business logic or decision-making. In Nostr, dumb servers act as passive recipients, receiving and transmitting data based on instructions from smart clients but not participating in active decision-making or coordination.
The concept of smart clients and dumb servers in Nostr aims to achieve a distributed and decentralized communication model. Smart clients take charge of managing the communication flow and business logic, reducing reliance on centralized servers and the risk of single points of failure. At the same time, the passive execution capability of dumb servers makes the system more scalable and flexible, allowing more services and nodes to join the communication network.
In summary, the smart clients and dumb servers model in Nostr provides a flexible, scalable, and decentralized communication architecture by decentralizing decision-making and logic to the clients and restricting servers to basic data storage and transmission functions.
Smart clients and dumb servers are the core idea in microservices
The tech development space is dominated by mantras — sayings that make sense in context but are repeated away from their original source. These expressions may carry meaning for the initiated but are often seen as complicated jargon to others. One such concept is “smart endpoints and dumb pipes.” Accredited to Martin Fowler, the idea is helpful to consider when designing microservices architectures.
The basic premise of “smart endpoints and dumb pipes” is that microservices should carry their own communication logic (the “endpoints”), and the carrier superstructure that transmits these messages (the “pipes”) should have as light a structure as possible. Why is this so? What’s the justification, and what’s the background upon which this conversation on pipes and endpoints exists?
Below, we’ll attempt to clarify what the saying means. We’ll look at where it came from, how it applies to microservice development, and see why it’s a helpful expression for modern software architects to understand.
The Problem of the Monolith
We’ve talked at length about both monoliths and microservices, but it bears significant importance to this discussion, so we will again define them.
Understanding Monolith
The traditional approach to development is often referred to by a singular term — the monolith. Monolithic development adopts a centralized data storage and response. A holdover from the era of mainframes and clients, the basic idea is to create a vertical stack wherein everything is located and guided by a single, all-powerful system. This non-distributed approach meant that everything existed in one body. Software applications were self-contained and non-modular, with requests being handled by a singular entity.
Often, these solutions were purpose-built, with many organizations utilizing a monolith due to their startup phases being singularly focused. This resulted in APIs that were non-modular, specific in intent and purpose to the point of rejecting extensibility and scalability in favor of stability and a functional response.
There are some strengths to this kind of approach. First, it’s often cheaper to engage with at the start. Building something to do one thing — and only one thing — is often more affordable than building a system that allows for many things. In such a monolithic approach, the service is a one-to-one relationship — the server owns the data, how it’s transmitted, and how it’s serviced, making a clear communication pathway.
Unfortunately, this means that monoliths are heavily siloed, lacking a malleable underlying codebase. Alterations or replacements carry an enormous cost in both time and resources. This can result in a sort of code paralysis just due to the sheer weight of the system. It can also result in a high cost to develop, maintain, and run. As a monolith grows larger, it remains constrained to its original design, incurring ever-growing expenses to add new components. This results in late-stage development that carries massive deployment burdens and slower release schedules.
Understanding Microservices
Microservices were designed to solve this problem. In essence, the microservice paradigm represents a sea change from isolated singular monoliths to a collection of smaller, single-purpose services that work in concert. With each service doing a specific thing, the idea is that those services would then work together to facilitate the core function.
This shift from non-distributed to distributed, from centralized to decentralized, delivers significant benefits. First, the system becomes much more scalable. An application can slot in new services or change existing ones without adverse end-user experience changes. Iteration does not freeze new development, as you’re changing a small part of the greater subset. You can compare this to changing clothes — if your entire outfit was all sewn together, as in a monolith, you would be unable to change your jacket or put on a hat without a huge effort. A microservice allows you to, metaphorically speaking, change hats or jackets at will. This is possible because the individual parts are only connected by necessity, not enforcement.
This also means microservices do not carry with them the problem of siloing. With components architected as microservices, the overall system can change, mold itself, and adapt to circumstances without affecting any other part. Business logic can be represented on the node with the closest affinity to its function, rather than being centralized into a singular node of control.
This system does introduce additional complexity, as we’ll cover below, yet the benefits are so substantial that many software architects have adopted it whole-heartedly.
The Solution: Smart or Dumb Pipes?
While microservices fix many of the issues of the monolith, some unique problems arise. Microservices don’t isolate everything into a single vertical silo, which is great — systems can be spread across multiple nodes and instances, creating a lot of variability in resource location. This also, unfortunately, creates some communication complexity. Think about it this way — imagine you are trying to do a group project, but instead of everyone sitting at the same conference table, you are all several miles apart. This would introduce significant communication barriers, even while introducing more extensibility and scalability to your group.
Microservices face this exact problem when it comes to facilitating inter-microservice communication. How do you solve that communication problem? There are really only two options: either you create smart pipes, or you create smart endpoints.
You could solve the microservices communication problem by creating smart pipes, and many implementations have employed this solution. An excellent example of this type, the Enterprise Service Bus, allows for the logic and processing governing communication to be placed in a singular system, a facilitation center, to make communication stable and efficient. However, the problem with doing this is that you’ve created a vertical system of centralization — while the entities doing the work are decentralized, all communication is centralized to this ESB, resulting in a sort of quasi-monolithic approach.
While an ESB is not itself bad — and to put a finer point, not necessarily a monolithic approach — taking it too far can certainly lead to a lot of the same issues incurred with a monolithic strategy.
Smart Endpoints and Dumb Pipes
A great solution is to go the other way. Instead of making your pipes smart, make your endpoints smart! In this system, you’re shifting the paradigm away from the idea of a communications bus and closer towards self-sufficient nodes. In essence, you are taking that business logic, communication logic, and general governance away from the communication node and are instead placing it firmly in the entities doing the talking.
The core idea of “smart endpoints and dumb pipes” is that the microservices, when designed correctly, don’t need a bus to govern this communication. The services themselves can govern the logical breakout of communication without going through an intermediary. If the User Service needs to talk to the Authentication Service, for instance, all the logic for how that works can be held by those entities — including a third entity may increase governance and control, but it may be antithesis to the microservice solution.
Martin Fowler’s coined this concept in his commentary on microservices. In it, he stated as thus:
“The microservice community favours an alternative approach: smart endpoints and dumb pipes. Applications built from microservices aim to be as decoupled and as cohesive as possible – they own their own domain logic and act more as filters in the classical Unix sense – receiving a request, applying logic as appropriate and producing a response. These are choreographed using simple RESTish protocols rather than complex protocols such as WS-Choreography or BPEL or orchestration by a central tool.”
To be clear, this doesn’t mean that no logic is located within the communication systems. The point is where the bulk of that logic resides. It’s one thing to have the “pipes” holding onto basic logic for managing asynchronous communication. Still, it’s a whole secondary thing to have them hold the complete logic for all communication and governance internally. Not only is it highly inefficient, but it may also be ineffective in actually facilitating communication. Lightweight logic systems can, in fact, be useful. Again, from the same commentary from Martin Fowler:
“The second approach in common use is messaging over a lightweight message bus. The infrastructure chosen is typically dumb (dumb as in acts as a message router only) – simple implementations such as RabbitMQ or ZeroMQ don’t do much more than provide a reliable asynchronous fabric – the smarts still live in the endpoints that are producing and consuming messages; in the services.”
This is really a solution that is more concerned with removing blockers than demanding a particular approach. The beauty of microservices lies in the freedom to adapt and change for different circumstances — adopting the concept of “smart endpoints and dumb pipes” simply allows that change and adaptation to be more fluid and independent of the communication controls and protocols more typical of centralized systems.
Conclusion
The best way to think about “smart endpoints and dumb pipes” is to think about where the logic exists. When you create dumb endpoints and smart pipes, you depend on the pipes for everything. You depend on the pipes to know where the data is coming from, where it’s going, and how it should be transmitted. You have centralized all communication power into a system of organization and governance. That’s not necessarily a bad thing in all cases — in secure data situations, you may very well need such a system — but it’s only truly appropriate in a handful of situations.
“Smart endpoints and dumb pipes” is an inversion of this principle. The microservices know what they’re doing, and if that’s true, why should you need to control their communication? If you’ve built out a robust microservice ecosystem, then you should be able to let them communicate over a system that is minimally controlling, with minimal logic built-in for core functions.
What do you think about this concept? Let us know below!
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ 629eb027:c6466988
2023-08-01 11:30:31
@ 629eb027:c6466988
2023-08-01 11:30:31Elon's lawyer Alex Spiro sent a letter to Mark Zuckerberg threatening legal action, claiming that Meta hired former Twitter employees to create a clone.
This isn't surprising, as Facebook's Moto has always been 'Why Innovate When You Can Imitate'
Unlike great tech innovators, Meta literally just takes others’ ideas and repackages them.
It is no secret that Meta has a copycat culture, and we know this because a US House Judiciary Committee probe in 2020 revealed emails from April 2012 with Facebook employees stating “copying is faster than innovating,”
Zuckerberg was asked by the Judiciary Committee whether "Facebook ever threatened to clone the products of another company while also trying to acquire that company?”
He responded "not that I recall" (please don't laugh)
Remember when @ElonMusk was mocked for Twitter Blue, then a few months later Instagram copied the strategy? Old habits die hard.
A QUICK GUIDE TO EXAMPLES OF FACEBOOK'S COPYCAT FAILS:
1) Facebook Check In deals - started in 2011 and closed after 4 months. This was a copy of Groupon and LivingSocial.
2) Facebook Gifts - started in September 2012 and closed after 1 year. This was a copy of the gifting app Karma.
3) Facebook acquired Parse in 2013 but had to shut it down. It was doing well before Facebook bought it
4) Facebook Credits - Users said it was too confusing. Credits were used by many companies like Disney Dining Credits.
5) Facebook Messages with email - this was touted as a "Gmail killer" but it was dropped as it was not popular.
6) Facebook Places - This was similar to Foursquare. In September 2011 it was shut down due to privacy concerns.
7) Facebook Stories - This was a failed copy of Pinterest and Snapchat.
8) Facebook Slingshot - This was a Snapchat imitation that launched in 2014, but it was scrapped in 2015.
9) Facebook Poke - This was probably the first Snapchat feature imitation, launched in December 2012 but pulled in 2014.
MY THOUGHTS:
Firstly, I hope Twitter proceed with their lawsuit as someone needs to stand-up to Meta's vulture-like approach to business: Acquiring competitors or destroying them by copying their product.
But at the same time, I do NOT think Meta is a threat to Twitter.
Twitter and Meta are FUNDAMENTALLY DIFFERENT
It's not about functionality, it's about each platform's stance on FREE SPEECH.
Both platforms can co-exist, they are NOT mutually exclusive.
The same way Twitter is shifting to 'X', the 'everything app', Meta is expanding so they compete with Twitter. I expect both ecosystems to exist a decade from now, with similar apps, but VERY DIFFERENT EXPERIENCES.
This difference makes it impossible for each to copy the other. Twitter will always be the Free Speech Town Hall and no other platform can take away that crown. Certainly not Meta.
So you simply need to ask yourself: How important is Free Speech to you?
META vs TWITTER, who comes out on top?


-
 @ ba680951:ec182a0e
2023-08-01 09:48:26
@ ba680951:ec182a0e
2023-08-01 09:48:26タイトル: フォートナイトで勝つための楽しく爆笑必至のコツ
はじめに: バトルロイヤル型ゲームである「フォートナイト」で一番になるためのコツが知りたいですか? それなら、あなたは運命のブログに辿り着きました! この記事では、誰もが笑顔になるようなコツを紹介します。なんといっても、ゲームは楽しむためにあるのですから!
-
エイリアンを友達にする: ゲーム中に出くわしたエイリアンを友達にしてみてはいかがでしょうか? お互いにハイタッチをして手を繋ぐ、なんてことも可能です。勝つための強力な味方が増えるだけでなく、笑顔が絶えないプレイができるでしょう。
-
ダンスで敵を惑わせる: 突然踊り始めることで敵を惑わせることができます。あなたがダンスパーティーを開始すれば、敵は驚き、一瞬戸惑うことでしょう。その隙に反撃するのです!
-
ピクニックを開く: ビルドモードでテーブルと椅子を作り、ピクニックを開くのも楽しい方法です。敵があなたに近づいてきたら、一緒にピクニックを楽しむように誘ってみてください。もちろん、この間に仲間が攻撃するのです。
-
ラマに乗る: ゲーム内で見つけたラマに乗って移動するのも一つの手です。これにより、あなたは敵のサプライズ攻撃から身を守ることができます。また、ラマに乗る姿は見ていて笑えるでしょう。
まとめ: フォートナイトでの勝つためのコツは無数にありますが、何より大切なのは楽しみながらプレイすることです。それが最大のコツかもしれませんね。あなたが楽しめば、必ず結果もついてくるはずです。では、バトルフィールドでお会いしましょう!
-
-
 @ 180a6d42:36cf5693
2023-07-11 15:56:07
@ 180a6d42:36cf5693
2023-07-11 15:56:07
This mini-guide aims to help you choose between a selection of Bitcoin lightning network (LN) wallets with an additional focus on working toward becoming unruggable through self-custody. No need to overthink, self-custody means: writing down and safely storing 12/24 words (aka 'seedphrase') offline, on paper/metal.
TL;DR. use WoS/LN.tips (transact📱) x Phoenix (save📱, self-custodial)
LN wallets (a selection)
Self-custodial LN wallets:
a. Phoenix app (📱, acts as a LN node*)
b. Breez (📱, acts as a LN node*)
c. Muun (📱, acts as a LN node*)
d. Zeus (📱, LN url)**
Custodial (by default) LN wallets:
a. Alby (browser extension, LN url)**
b. LN.tips (Telegram bot, LN url)**
c. Wallet of Satoshi (📱, LN url, use fresh email to sign-up)
d. ZBD (📱💻, LN url, kyc-free up to 500k sats)
sats= satoshi's (fractions of a bitcoin, e.g. 21.000 sats is 0.00021 BTC) LN url = Lightning address to add to your Nostr account to enable >receiving< Zaps
uses e.g. a big company LN node or submarine swaps *lightning node remote control apps: can also connect to self-hosted LN node
So to be clear, you have lightning wallets that act as (a) a wallet, (b) a self-custodial lightning wallet AND a lightning node on your phone, (c) a lightning node remote control app (if you run and self-host a LN node on a dedicated device).
Why choose custodial? It is only a temporary solution showing the power of LN where channels are already established and robust, is my conclusion. Be aware that there are major security/privacy trade-offs when using custodial wallets. However, if you're someone who's new to Nostr and/or bitcoin, and you e.g. want to enable receiving Zaps, it's obvious you play around with a custodial one with a smaller amount of sats first (let's say, up to ~ 21k sats/ 50$). I don't think it's realistic to expect someone new to this network to magically and instantly know how to spin up a LN node and manage channels. This is something that takes time to learn.
Unless you only use self-custodial LN wallets, it is advised to have your sats divided on more than one custodial wallet in case one of the hosted LN nodes temporarily goes down (not often) and you still want to transact at that moment.
Why choose self-custodial? When you're looking to learn more and/or if you plan to send/receive more substantial amounts of sats (e.g. for business) then you're ultimately going to want to learn to run a self-hosted node, preferably through Tor. Find trustworthy tutorials here.
A self-hosted node allows you to save on transaction fees; truly be in control of your bitcoin; and, protect yourself wrt third-party privacy violations. Know that you'll have to invest some time in learning and money in gear/gadgets in order to run your own (LN) node (~$200-$400).
What other choices do I have? If you're not ready to run a LN node just yet, you can also choose to go for one of the self-custodial wallets listed that act as a LN node on your mobile (e.g. Phoenix). The transaction fees are a bit higher than with custodial wallets but this is related to the wallet acting as a lightning node on your phone (e.g. with Phoenix you have to top-up the wallet with a minimum of 10.000 sats initially of which 3000 sats will be deducted in order to have the system open up lightning channels for you). A small price to pay for not having to have to run your own, self-hosted Bitcoin Lightning Node and managing it. Know that running your own lightning node has similar costs.
Tip: You can now deposit funds to self-custody on Lightning with Phoenix wallet for less than 500 sats when conditions are optimal* (compared to the previous 3000 sat/1%). They also made the LN<->onchain swaps trustless.
Summary
Here's a recommended Bitcoin wallet setup focussed on self-custody without having to have to run your own, self-hosted Bitcoin LN node:
Transacting bitcoin LN/L2 (active📱): Wallet of Satoshi and LN.tips
only use temporary, small amount of sats; custodial, but supports LN url
↕
Saving bitcoin, LN/L2 (passive📱): Phoenix wallet
self-custodial, easy, can swap LN↔on-chain, supports Tor
watch and learn: https://youtu.be/cbtAmevYpdM?t=223
↕
Saving bitcoin, Layer 1 aka on-chain (passive💻):
deep, air-gapped, cold storage (e.g. Seedsigner, Coldcard)
For a more extensive LN wallets comparison guide outside the scope of only Nostr, click here (would not recommend if you're new to all this; can be overwhelming).
Link to this blog: https://lnshort.it/lnwalletguidenostr
Find me on Nostr: matata@nostrplebs.com
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:03
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:03👥 Authors: josibake ( nostr:npub1lc8fsuj6ffha9xjpq7l9cfn0ylhfw6jm4gyjfudpvet7yvxpv5gq83p9xr )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 23880
Messages Summaries
✉️ Message by josibake on 03/08/2023: The BIP for Silent Payments has undergone several revisions, including changes to key sizes and a versioning scheme for addresses. Bitcoin Core implementation has been updated.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 7f5c2b4e:a818d75d
2023-07-11 13:05:57
@ 7f5c2b4e:a818d75d
2023-07-11 13:05:57The Problem
Key delegation has been a hot topic in the Nostr community for ages now. Even though Nostr is a new protocol, things are moving so fast that it feels like it's been years since it was launched. If you think about it in terms of regular social media, it's easy to see why this feature is so important. It's like being able to give someone the keys to your house but still being the one who's in charge. A good example of this is how nsecBunker is helping nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka run a shared Nostr account. But that's just one use case. There are a lot more possibilities, and we're going to discuss some of them in this post.
Legacy solutions
The centralized nature of many platforms simplifies the problem of key management. Social media platforms like Facebook Business Manager, Twitter Business, and LinkedIn Pages offer built-in tools for delegating roles to team members without divulging original login credentials. Third-party platforms like Hootsuite, Buffer, and Sprout Social further streamline this process, enabling management of multiple accounts, scheduling posts, and assigning roles, all without compromising the security of original credentials.
For more technical solutions there are services like Amazon Key Management Service (KMS). KMS helps generate, control, and manage cryptographic keys used for data encryption. With KMS, you can create Customer Master Keys (CMKs), define usage policies, and set up automatic yearly rotation. When data is encrypted, KMS generates a data key, encrypts it with the CMK, and provides you with both plaintext and encrypted versions of the data key. The plaintext key is used for data encryption, then discarded, leaving only the encrypted data key. To decrypt, the encrypted data key is sent back to KMS, which decrypts it into plaintext, given the necessary permissions. This system is employed by many businesses and media outlets to ensure secure access and compliance.
However, while these traditional systems are robust, they leave the end-user dependent on the service provider, who retains the ability to revoke access at their discretion. And this is precisely the problem Nostr is trying to fix.
The Nostr Way
The First Attempt
The first attempt that received serious attention in this direction was NIP-26. It introduced a new 'delegation' tag that enables events to be delegated and signed by other keypairs. This proposal is meant to abstract the use of 'root' keypairs when interacting with clients, with the idea that a user could generate new keypairs for each client they wish to use and authorize those keypairs to generate events on behalf of their root public key, where the root keypair is stored in cold storage.
However, NIP-26 has been critiqued for its implications on key management. Arguably, the best explanation of the corresponding problems was layed out by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 in his "Why I don't like NIP-26 as a solution for key management" post here. Initially, NIP-26 was praised for its optional nature. However, as NIP-26 began to be seen as a universal solution for key management on Nostr, it started to raise concerns. The concept entailed users generating a secure, offline key to sign delegation tags for each Nostr app, potentially rotating them periodically. This approach would make these keys "faceless entities" only identifiable by their master key, significantly changing the user experience and expectations from NIP-26.
This shift in approach would effectively render NIP-26 mandatory for usability, turning it from an optional enhancement to a necessary implementation for clients. This would remove the flexibility of choice and potentially complicate the protocol. Furthermore, while NIP-26 could provide some solutions in the realm of key management, it's not seen as a comprehensive solution. It's suggested that a multitude of key management methods could be more effective, maintaining the optional nature and possibly presenting a more elegant solution. There's an argument that if a mandatory key delegation method is indeed necessary for Nostr, an alternative design might be more optimized and easier to implement than NIP-26.
The Promising Alternative
NIP-26, while a noteworthy attempt, seemed to diverge from the core philosophy of Nostr. This discrepancy highlighted the need for an alternative solution that would respect this foundational principle and avoid precipitating Nostr down a slippery slope of mandatory adherence.
This is where nsecBunker, introduced by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft, provides a compelling proposition. As the name suggests, nsecBunker enables users to establish and self-host their own bunker allowing them to manage Nostr keys. This Bunker can communicate with the user interface on your device, facilitating the creation of target keys, sharing them with corresponding Nostr users, and offering granular control over their interactions with the protocol.
Crucially, the implementation of nsecBunker does not necessitate significant changes in the builds of existing clients, preserving the opt-in nature of Nostr. Beyond adhering to Nostr's core principles, nsecBunker also holds potential to enhance user experiences and provide improved functionality, aspects I will elaborate on shortly.
How Does This Work?
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft elaborates on the core concept behind nsecBunker:
nostr:note1uxjpstcw5ldxrlfzqvqs3nqqpvyumajz4r5elmaf8ffmjyu342qqwsn0yd
At a high level, this model bears similarities to the traditional Amazon KMS approach, albeit with certain distinct nuances. For a deep dive into the technical intricacies of this model, I recommend checking out nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft's work-in-progress SECURITY-MODEL.md on GitHub.
To put it simply, nsecBunker is a daemon that facilitates remote event signing. It operates with two types of keys: user keys and nsecBunker keys. The bunker key interacts with the admin UI and only communicates with the pre-defined (admin)
npub. Notably, this key doesn't store sensitive information or hold specific power -- it poses no threat to key material even if compromised.The user key, on the other hand, is used for signing purposes. These keys are encrypted with a passphrase following the same approach as LND. This passphrase is mandatory every time nsecBunker is initiated, and losing it equates to losing access to the keys.
During setup, the administrator pre-approves a key (or a set of keys) for communication with the nsecBunker. The administrator(s) then create target keys to distribute to the intended users. These users can interact with the Nostr infrastructure without ever accessing the private keys of the account they're using. Let's walk through the process of setting up a Bunker.
Running nsecBunker
Paid Subscription
The easiest way to run nsecBunker is to purchase a paid subscription. The process is very easy and intuitive and, thanks to Lightning Network, it does not require you to share any sensitive data, such as IDs or bank card details. Scan a lightning invoice and get access to your own bunker in seconds:
- Navigate to https://app.nsecbunker.com/ and press “Buy one here”:

- Click “Next”

- Paste your public key (or a few keys) you’d like to be in control of the target keys. The keys you’ll specify will be able to grant full or granular permission to target keys which, in turn, will be able to post on behalf of the admin account. The admin key will be able to, but have to be the same key that you’ll be signing as later on. This means that you will be able to create a target key to interact with Nostr and have it look like your account is the one that is logging in / posting / liking / etc., or a totally separate target key, which will be like a child account of yours, and won’t be linked to you for the outside world.

- Specify how many users you’d like to be able to sign Nostr events with the Bunker you are creating. The number of end users directly affects the yearly fee rate.

- Pay the lightning invoice

- That’s it – your keys management fortress is ready to be utilized.

Here's a quick demo on setting up and using your nsecBunker by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft:
Alternatively, if you are confident in your tech skills, you can build your own nsecBunker. It’s an open source project, meaning that anyone can spin up their own version.
Docker setup
To quickly install nsecBunker via Docker run:
``` docker run -d --name nsecbunkerd pablof7z/nsecbunkerd start --admin
```
nsecBunker will give you a connection string like:
``` bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com
```
Visit https://app.nsecbunker.com/ to administrate your nsecBunker remotely. For details see the GitHub repository here.
Setting up your Connection
After procuring the string, navigate to https://app.nsecbunker.com/. Log in using your preferred NIP-07 browser extension. Ensure the Nostr account (nsec) you're using is the same one that is designated as the administrator. The bunker is designed in such a way that it will not reply or even recognize if anyone other than the administrator
npubis trying to communicate with it.
Input the connection string into the required field and hit 'Login'.
As you can see, I left my connection string visible in the screenshot above. This is to showcase that it doesn't require protection and is simply a way of connecting to your bunker. The security model here relies on your
npubbeing the only entity with an administrative account.You'll land on the following screen:
https://nostr.build/p/nb10013.png
Click the "Keys'' tab. If you see a "Loading" message under the "Keys" title, simply refresh the page, and you should see the "No keys created yet" message.
If after clicking the "Keys" tab button you do not see the "No keys created yet" message, that means there is some problem with the setup. It could be the mismatch of the pubs or the bunker could be offline.
You are now set to create and manage target keys (the npubs you will be able to share).
Creating a Key
Click on "Add Key". This will reveal a pop-up prompting for information necessary to create a new target access key.
https://nostr.build/p/nb10015.png
The Key name is self-explanatory: it helps distinguish your target keys.
The need to fill up the Nsec field depends on how you plan to use nsecBunker. If you leave the 'Nsec' field empty, a new Nostr account will be created. This lets you manage how the target key owner interacts with Nostr. But if you already have an account and want to give someone else access, you can do that by entering the private key for that account into the bunker. It's a similar result, but uses an existing account instead of creating a new one.
The Passphrase is crucial for encrypting your keys and securing communications. Every time your bunker restarts you will need a passphrase to enter the admin panel. Treat it with the same caution you'd exercise with your private key - without it, access to your managed keys is lost.
With these steps completed, you can now share the public key with the owner of the target account.
Activating the Target Account
To start posting with a target key, users should visit https://coracle.social/ and click the "Advanced Login" button, followed by "Log in with Nsec Bunker".
https://nostr.build/i/c493ee745080ad4fd58a5c796792cadb491a0f194adc478bc7735399fb386c04.png
Enter the
npubor a token received from the Bunker administrator.https://nostr.build/i/7106719c873683c21a970662ecf3ebf95149b774efd0f36b8c1efcc16c8dbb99.png
The standard account setup process applies here (in case of a new account), but stay in touch with the Bunker administrator, as they must approve all new interactions.
The nsecBunker Admin UI displays the authorization request for 30 seconds, implying the need for synchronous coordination with the person requesting permission.
While tokens do not require any authorization (more on this below), if you first log in to https://coracle.social/ with the
npub, the administrator will receive an authorization request...https://nostr.build/p/nb10017.png
...and will be prompted to name this session.
https://nostr.build/p/nb10018.png
Each subsequent interaction will also generate a request in the admin UI. You can either authorize interactions by event kind - Always allow - or bulk-authorize all future interactions - Always allow signing all kinds - (yet to be enabled).
The "Always allow" feature signifies that the administrator is required to authorize each event type just a single time. For instance, if a user wishes to post a note, which is kind 1 event, the administrator's authorization is needed only once for this specific event type. Subsequently, the user can post additional notes without requiring further permissions. Please be aware that as the tool progresses, the precision of access permissions will be further refined.
https://nostr.build/p/nb10019.png
Introduction of Policies (see below) streamlines the system by allowing the issuance of an authorization token for the receiver, making administrators' lives much easier.
That's it. The target account owner can now interact with Nostr users without ever touching private keys. See the note below, which was posted by a co-author of nostr:npub10eezfnlq4ad2lyf3478na8f5las4l7guuf55vs8378lwtk87hd7slf6zka, who does not have access to the Herald's private key:
nostr:note1hmz72mg8d2hegpj0npungypqsv3wqtffjq3q3duwmk5zcha860uqnx0mx0
For the video tutorial on setting up the nsecBunker check out this video by Pablo:
If you opt for the "Always allow all kinds" option, the setup process will only need to be performed once. Target account owners can then interact with other Nostr users without further assistance. However, if the managed account owner logs out of Coracle and logs back in, the setup process needs to be repeated for security reasons.
Tokens
Tokens allow you to issue permissions to users, which they apply to an npub of their choosing without requiring interactivity. Creating tokens is super simple:
- Head over to the Keys tab;
- Click on the Tokens button;
https://nostr.build/i/c190e60cb125dd418f7db649678b1f083b314df3bf898caecff59291b0e6a85f.png
- Click Add Token
https://nostr.build/i/be1c2d723d7f9e4c0849634cdeed037e3b3f0e0db728eafac270edd392097234.png
-
Fill up required fields
-
Client name is required for your own reference
- Policy lets you choose which rights you'd like to grant to the token holder
- Set an expiry date if you'd like
- Hit Create Token
https://nostr.build/i/a046336915eba2bd6748188e86aa6eb3d387fb7d0dc48dc8645772f1fdd5cfc1.png
Policies
The latest update to nsecBunker has introduced the "Policies" tab, a feature that enhances the authorization process and gives administrators more detailed control over permissions. This addition enables the creation of access tokens to distribute to account holders. Each token can be customized to permit certain event types, set an expiration date for the token holder's privileges, and even define the number of times user's interactions can be authorized.
To leverage this new feature, navigate to the "Policies" tab and select "New Policy":
https://nostr.build/p/nb10298.png
Give your new policy a name and a short description...
https://nostr.build/p/nb10299.png
-
The "Method" dropdown menu provides a way to refine the assigned permissions. While the default "Sign Event" option will suit most users, if you want to restrict the user to only engage with Direct Messages or the Highlighter, select the appropriate option. For instance, using the "Encrypt" method provides the user with permissions to send Direct Messages (DMs) and to generate Highlighter events, such as private notes. Conversely, the "Decrypt" option enables the user to access and read Direct Messages and other encrypted data that is specifically intended for the private key owner.
-
Within the "Permission" menu, you have the flexibility to either permit all actions or, as demonstrated in the above screenshot, restrict the user to only publishing long-form posts. This functionality could be beneficial, for instance, if you are delegating your blogging responsibilities and prefer the copywriter to not have access to other areas of your account.
-
The "Usage count" setting allows you to control the number of interactions the target account can perform.
Select "Add Policy" followed by "Save Policy". As illustrated below, your chosen settings will generate various types of access tokens, each with distinct rights and descriptions. The token at the top of the screenshot, for example, restricts the holder to only publishing long-form posts, while the token at the bottom grants the holder full access:
https://nostr.build/p/nb10300.png
Navigate to the "Keys" tab and select the key to which you wish to assign rights, as outlined by the policy you created. Note that you'll need to unlock the key first by pressing the corresponding button and entering your nsecBunker passphrase. Click on "Tokens"
https://nostr.build/p/nb10301.png
Select the policy you wish to assign to the key and, if desired, set an expiration time:
https://nostr.build/p/nb10302.png
Click on "Create Token". A token, which takes the form of a Nostr public key, will be generated. You can now share this token with the intended user:
https://nostr.build/p/nb10303.png
For a live demonstration of this feature, check out Pablo's video:
Use Cases
"The possibilities of nsec bunker are endless." - nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
The pace of development in the Nostr ecosystem is impressive. Just a day after the release of nsecBunker, nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft integrated Bunker support into another one of his creations - the Highlighter.
nostr:note1u8x403llme28vpnsz83las60rgfuw2ht9hcf5tsscl3lnfgdlvkqu3096n
You can find out more about this super efficient productivity tool in my earlier guide here: nostr:naddr1qqxnzd3cxg6rxdfkxyerzv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28mg64kz. As the Highlighter was recently redesigned, my guide needs some updates, but it's still a great resource to understand what Highlighter is and how it functions.
The revamped Highlighter is loaded with new features, such as Lists, Highlights, Private Notes, and of course, the nsecBunker login option. With this feature, you can log into the app without ever disclosing your private key to either the app or the NIP-07 extension provider.
The integration of Highlighter with nsecBunker paves the way to nostr applications that work seamlessly with browsers that don't have a NIP-07 extension, as is the case in most cases on mobile, massively lowering the adoption of Nostr among a general, less tech-savvy, audience.
To use this feature, click on "Sign in" instead of logging in with your browser extension...
https://nostr.build/p/nb10150.png
...and enter the
npubyou got with the nsecBunker:https://nostr.build/p/nb10154.png
As the administrator approves your connection you get logged in. The process here is identical to the one I described for Coracle.
https://nostr.build/p/nb10155.png
Take note, with the introduction of Policies, the Highlighter - fully integrated with nsecBunker - also supports the fine-tuning of corresponding permissions:
https://nostr.build/p/nb10304.png
Highlighter showcases just one of many use cases of nsecBunker. Here are some more, but keep in mind that I'm only giving you a brief overview of the tool's potential:
-
Separate Accounts for Different Use Cases: nsecBunker enhances your security model by allowing you to retain your private key while using different Nostr clients.
-
Collective Social Media Account Management: nsecBunker can be used by journalist teams or companies to collectively run social media accounts, increasing user awareness of their products or services.
-
Child Control: Parents can utilize nsecBunker to set up accounts for their children, ensuring they adhere to family practices.
-
Burner Accounts: nsecBunker enables you to create specific accounts for specific use cases, all under your control.
-
Corporate Accounts: Businesses can generate keys for their employees, allotting rights specific to their positions.
However, the applications of nsecBunker are not limited to these. For example, one exciting possibility that emerged shortly after nsecBunker's release was the potential solution to creating private groups within the Nostr community. As nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn astutely observed, the possibilities with nsecBunker are indeed endless. Have a look at his long form post here: nostr:naddr1qqwkzttswfhhqmmnv9kz6en0wgkhqunfweshgefdvaex7atswvq3jamnwvaz7tmjv4kxz7fwdehhxarjd93kstnvv9hxgqgewaehxw309ac82unpwe5kgcfwdehhxarj9ekxzmnyqy2hwumn8ghj7mn0wd68ytnfdehhxarp9e3kxqg4waehxw309ahx7um5wghx66tvda6jumr0dsq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqyg8wumn8ghj7mn0wd68ytnhd9hx2qtxwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tmwwp6kyvfsv9mh56mwdfnn2u34d3sk5mnjx5engvecdejxx7t209kxwutnwfh8yar3x4nhyue58y6hvdpjw93nvcthwd4rgdtewvmn7cnjdaskgcmpwd6r6arjw4jsz9nhwden5te0vf5hgcm0d9hx2u3wwdhkx6tpdsq35amnwvaz7tmjv4kxz7fwdaexzmn8v4cxjmrv9ejx2asprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksz8rhwden5te0w4hxjan9wfek2tnwdaehgunfvd5zumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdaksz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyv8wumn8ghj7un9d3shjtnwdaehgunpw35jucm0d5pzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqvzqqqr4guzz40fz
Supported clients
Here's a list of Nostr clients supporting nsecBunker (keep in mind that new clients are actively adding support of this tool, so the list may not always be extensive, feel free to leave comments if you see that some clients are missing):
Note that every client that offers you to login with a so-called "NIP-46" supports nsecBunker login.
Nostr = Everything × Freedom
Harnessing the unparalleled power of the most advanced currency humanity has ever seen, Nostr is an open and censorship-resistant protocol that promotes freedom of expression and allows you to stay anonymous. Its very foundation is rooted in open-source principles, making the collective knowledge and experience gathered through its development accessible to all. The protocol itself, along with most Nostr applications, are open-source. This allows anyone to contribute, adapt, or even build upon existing developments to create something uniquely their own. This is where the true power of censorship-resistant, open-source software resides - it's unstoppable.
Legacy systems, bound by their proprietary constraints, simply cannot compete with the collective intellectual power of what began as a cypherpunk movement and has now blossomed into a vibrant community of dedicated individuals. These individuals are committed to bettering the world, rather than merely filling their pockets with others' hard-earned money. Together, we are paving the way towards a future where freedom of speech and self-sovereignty are the norm, and the fruits of our labor contribute to societal progress. This collective effort fosters the creation of tools that empower us to build better, move faster, and grow stronger. More on this in my post here: nostr:naddr1qqxnzd3cxs6rxv3hxsensv3nqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z78gua.
We invite you to join this peaceful revolution. Participate in the growth of permissionless protocols, contribute to open-source software, and share your ideas to further enhance this vibrant ecosystem. Together, we are not just evolving technology - we are shaping a more open, inclusive, and equitable future.
Like what nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is building? Make sure to support him!
-
Pablo's Nostr account: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
Pablo's site: https://pablof7z.com/
-
 @ c45af590:0dd0563b
2023-08-03 16:16:16
@ c45af590:0dd0563b
2023-08-03 16:16:16We are implementing a version of 2-of-2 Schnorr Musig2 for statechains where the server (party 1 in the 2-of-2) will be fully 'blinded' - in that it can hold a private key that is required to generate an aggregate signature on an aggregate public key, but that it does not learn either: 1) The aggregate public key 2) The aggregate signature and 3) The message (m) being signed.
In the model of blinded statechains, the security rests on the statechain server being trusted to report the NUMBER of partial signatures it has generated for a particular key (as opposed to being trusted to enforce rules on WHAT it has signed in the unblinded case) and the full set of signatures generated being verified client side https://github.com/commerceblock/mercury/blob/master/doc/merc_blind.md#blinding-considerations
Given the 2-of-2 musig2 protocol operates as follows (in the following description, private keys (field elements) are denoted using lower case letters, and elliptic curve points as uppercase letters. G is the generator point and point multiplication denoted as X = xG and point addition as A = G + G):
Party 1 generates private key x1 and public key X1 = x1G. Party 2 generates private key x2 and public key X2 = x2G. The set of pubkeys is L = {X1,X2}. The key aggregation coefficient is KeyAggCoef(L,X) = H(L,X). The shared (aggregate) public key X = a1X1 + a2X2 where a1 = KeyAggCoef(L,X1) and a2 = KeyAggCoef(L,X2).
To sign a message m, party 1 generates nonce r1 and R1 = r1G. Party 2 generates nonce r2 and R2 = r2G. These are aggregated into R = R1 + R2.
Party 1 then computes 'challenge' c = H(X||R||m) and s1 = c.a1.x1 + r1 Party 2 then computes 'challenge' c = H(X||R||m) and s2 = c.a2.x2 + r2
The final signature is then (R,s1+s2).
In the case of blinding this for party 1:
To prevent party 1 from learning of either the full public key or final signature seems straightforward, if party 1 doesn't not need to independently compute and verify c = H(X||R||m) (as they are blinded from the message in any case).
1) Key aggregation is performed only by party 2. Party 1 just sends X1 to party 2. 2) Nonce aggregation is performed only by party 2. Party 1 just sends R1 to party 2. 3) Party 2 computes c = H(X||R||m) and sends it to party 1 in order to compute s1 = c.a1.x1 + r1
Party 1 never learns the final value of (R,s1+s2) or m.
Any comments on this or potential issues would be appreciated.
Tom
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:57:38
@ 9ecbb0e7:06ab7c09
2023-08-03 15:57:38Con indignación y decepción, el cubano Salvador Lester Camejo relata su amarga experiencia en el famoso bar-restaurant El Don Ávila (La Espada), propiedad de la empresa estatal Palmarés, en Ciego de Ávila.
De acuerdo con el testimonio publicado en su perfil de Facebook, fue discriminado en su propia ciudad por el solo hecho de ser cubano y no generar ingresos en dólares, lo cual inmediatamente lo hace ser un “ciudadano de segunda”.
“Realmente ya es indignante que en el propio país de uno lo discriminen por el simple hecho de ser cubano, no ganar los dólares del ‘enemigo’ y por ende no tener preferencias en centros que brindan servicios al turismo”, explica Lester Camejo.

La historia comenzó cuando el ciudadano le pide un café al dependiente, y este le contesta que, por orden de la dirección de la empresa de Palmares, cuando están a la espera de un grupo de turistas no puede haber dentro ningún nacional.
Ante esta discriminación, el cubano optó por abandonar el lugar y dirigirse a un local privado cercano al parque, donde pudo disfrutar de un excelente café de importación (Café La Llave) sin sentirse avergonzado de ser cubano. No obstante, en este establecimiento el café estaba igual de caro. Lester Camejo reconoce que “tristemente” tomarse un simple café en la calle ya no está “al alcance de todos”.
“Por mí desde ya pueden cerrar el Don Ávila porque nunca más iré cuando tenga la posibilidad de hacerlo. ¡Que esperen a sus añorados turistas! Por mi parte, mi dinero no lo tocarán más, a la dirección de Palmares, u otra entidad que haya tenido que ver con esta estúpida y humillante aberración que no se les olvide que Cuba es de todos los cubanos y que nada dura para siempre”, concluyó el avileño.
Este lamentable episodio ha generado gran controversia y otras denuncias de comportamientos similares por parte de empresas estatales. “A mí me pasó en el Museo del Ron (cadena Caracol), en Varadero. Estaba vacío (literal), voy al bar y pido un trago y la ‘bar-woman’ me dice que no podía despacharme porque esperaban a ‘un grupo’”, contó Lupe Pérez.
“Esa es la gran y triste realidad de nosotros los cubanos, desterrados en nuestra propia tierra que nos vio nacer. Pero no leas la prensa, no oigas una emisora radial, para ellos el cubano es el que más libertad de expresión tiene y el que mejor dieta nutriente come. La realidad es que la población está muerta de hambre y necesidad. Quien con 1.678 al mes que es la media de un jubilado puede subsistir”, comentó Cándido Mariano.
-
 @ 9ecbb0e7:06ab7c09
2023-08-01 03:57:51
@ 9ecbb0e7:06ab7c09
2023-08-01 03:57:51El celular de Daysuris Vásquez, exesposa de Nicolás Petro, bajo arresto desde el sábado por un escándalo de corrupción que ya salpica a varios políticos nacionales vinculados a su padre, el presidente Gustavo Petro, es la principal fuente de evidencias contra el acusado.
De acuerdo con un reporte de la revista colombiana Semana, el dispositivo se convirtió en una prueba contundente contra Nicolás Petro, pues su esposa registró en él desde intercambios de mensajería hasta audios y videos que podrían convertirse en pruebas durante el proceso.
El teléfono habría estado en manos de la Fiscalía de Colombia durante más de dos meses, después que las denuncias de la mujer dieran inicio al escándalo.
Según Semana, "en el aparato está el rastro de todo lo que hizo Nicolás Petro por lo menos durante 2021, 2022 y parte de 2023. Su exesposa guardó con sigilo la prueba y hoy las más de 1.600 páginas de chats, las notas de voz y los videos son el eje principal del expediente contra el hijo mayor del presidente Gustavo Petro".
En numerosos chats, indica el reporte, quedó registrada la vida de pareja de Vásquez y Petro, así como el tejido de un entramado de acuerdos a la sombra que se produjeron durante la campaña política del actual presidente.
Entre las evidencias estaría el negocio para la compra de una casa por 1.600 millones de pesos colombianos, suma que, según la exesposa, provino del conocido en el expediente del caso como "Hombre Marlboro", un excapo que pagó cárcel extraditado en Estados Unidos por narcotráfico, y del hijo de un controvertido empresario conocido como "El Turco" Hilsaca.
Se suma a lo anterior chats donde constan las citas de Nicolás Petro con casi todos los ministros del gabinete del Gobierno de su padre, así como un diálogo suyo con el entonces ministro del interior, Alfonso Prada.
También asegura Semana que el hijo mayor del presidente colombiano habría recibido una camioneta de alta gama de parte de contratistas en plena campaña presidencial, algo que estaría registrado en los chats.
Aparte de lo anterior, existirían videos. En uno de ellos, Vásquez discute con su exesposo y él le reclama una suma de dinero, que según el testimonio de Day, sería el que recibió Nicolás para la campaña presidencial de su padre, del que se habría apropiado 600 millones de pesos aproximadamente.
Vásquez habría colaborado con la Fiscalía desde el primer momento del escándalo y su testimonio está judicializado y es, junto con el teléfono, el eje de los cargos contra Nicolás Petro. La mujer también está detenida y espera la decisión de los jueces.
Nicolás Petro es investigado por los presuntos delitos de lavado de activos y enriquecimiento ilícito. El escándalo ha salpicado al menos a 17 personas, entre políticos, financistas oscuros y funcionarios del Gobierno colombiano.
-
 @ 7f5c2b4e:a818d75d
2023-07-05 13:45:17
@ 7f5c2b4e:a818d75d
2023-07-05 13:45:17This FAQ is also available in Spanish: nostr:naddr1qqx9zat994jhxttgv93xccgpr9mhxue69uhhyetvv9ujumn0wd68y6trdqhxcctwvsq3jamnwvaz7tmsw4exzanfv3sjumn0wd68ytnvv9hxgqg4waehxw309ahx7um5wghxjmn0wd6xztnrvvq32amnwvaz7tmwdaehgu3wd45kcmm49ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgcnqcth0f4ku6n8x4er2mrpdfh8ydfnxsensmnyvduk57tvvachxunwwf68zdt8wfengwf4wc6ryutrxeshwum2xs6hjueh8a38ymmpv33kzum58468yat9qyt8wumn8ghj7cnfw33k76twv4ezuum0vd5kzmqprfmhxue69uhhyetvv9ujummjv9hxwetsd9kxctnyv4mqzxnhwden5te0wfjkccte9ehx7um5wfcxcetzwvhxxmmdqyw8wumn8ghj7atwd9mx2unnv5hxummnw3exjcmg9ekxzmnyqyw8wumn8ghj7mn0wd68ytndw46xjmnewaskcmr9wshxxmmdqy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgcwaehxw309aex2mrp0yhxummnw3exzarf9e3k7mgzypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq823crwnvag thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
What is Habla News?
Habla is a Nostr-based platform that allows you to create and manage long-form posts. You could compare it to Medium, yet Habla is so much more than that. Habla is superior to traditional blogging platforms because it is built on top of Nostr. It is interoperable with a plethora of other Nostr apps, which makes the user experience seamless and more engaging. Moreover, thanks to the Lightning Network, your input – if found valuable by the readers – can and will be instantly rewarded with the best money humanity has ever witnessed: bitcoin.
What is Nostr?
Nostr is a new way to communicate online that provides a ton of benefits for its users. It is free for everyone; you do not require an ID or any other third party verification to start connecting, mingling with like-minded people, and growing the community around you. Nostr is often mistaken for a social media platform, but it is much more than that. We encourage you to check out the Nostr resources gathered here to realize the potential magnitude of this tool.
How do I sign into Habla?
To start writing on Habla, simply create an Habla/Nostr account and log in. Follow these few simple steps to register, start sharing value, and receive value back.
How do I earn with Habla?
Habla allows you to receive value directly from your readers. No bank account or ID is required. Simply connect your Lightning address to your Habla / Nostr account and receive funds directly to your wallet – no third parties, no waiting for withdrawals, no sweat. Follow these simple steps to do so.
Why is posting on Habla different?
The Nostr protocol is super lightweight, which introduces some peculiarities into how the Nostr-based apps must behave. We won't go into technical details, but the most obvious difference you will notice as a content creator is that you'll have to use a different and, possibly, unusual format of text while composing your posts. But fear not; Habla provides tools that make this process easy and intuitive. Here's a quick video by nostr:npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t explaining the basics of posting with Habla (the guide was made prior to the redesign, yet remains useful):
https://nostr.build/p/nb9474.mp4
Habla (and many other Nostr apps) uses the well-established format, which is called Markdown. It has been around for almost a decade now and is supported by most apps you use every day. The reason you might not have heard about Markdown is because traditional apps usually hide it from the user, and we are working on doing so as well. You can find out more about Markdown here.
Where is my content stored?
Traditional blogging platforms store your content on their own servers. It is a convenient and (used to be) solid approach, but it bears critical risks. Leaving the fruits of your labor with a single party means they have full control over your content. Nostr fixes this. Every time you post something, your content is broadcast to numerous relays for further storage and redistribution. If any relay operator blocks your post or refuses to redistribute it, your readers can turn to other relays and access your content (do not worry if this sounds complicated; everything happens under the hood). This ensures you never get silenced. That said, Habla does not run its own relay; we've decided to concentrate on what we do best – build an intuitive, efficient, and easy-to-use blogging platform that rewards – and leave the content storage and distribution to the pros in that field.
How do I post?
Habla provides all the necessary tools to produce rich posts that stand out. Prepare your article, format your text with the help of designated tools, add media, and preview the results prior to publishing. All you need is at your fingertips, and the platform is only getting better and friendlier day by day.
Who can read my posts on Habla?
Anyone on the Internet can read your posts. However, if your readers would like to interact with your work – be it by following you / commenting / giving value back – they should create a Nostr account. We encourage you to onboard your followers to grow a thriving community and reach new heights. This quick guide will help you and your peers get started.
This FAQ is a work in progress, and it will evolve as both Habla and Nostr develop into even more powerful tools. Please provide feedback so that I can make it better.
-
 @ 32dc4f25:f95ddcce
2023-06-30 02:52:42
@ 32dc4f25:f95ddcce
2023-06-30 02:52:42Nostr, short for “Notes and other stuff transmitted through relays,” is a new communication protocol developed in 2021 by Lightning Network developer fiatjaf, which evolved out of LNBits developer Ben Arc’s attempt at a fully-decentralized marketplace called Diagon Alley. As opposed to other communication solutions, which mostly function via dumb clients and smart servers, Nostr offers smart clients and dumb servers, which heightens censorship resistance for users.
In Nostr, all data is stored locally with users and merely distributed via relays, rather than stored on central servers, such as via Twitter. In the case of social media, Nostr increases censorship resistance, as users are enabled to fully own their own content and profiles. In light of recent controversies around Twitter’s censorship policies, users began migrating toward the federated communications solution Mastodon. However, in Mastodon, ownership over content and profiles lies with those running the Mastodon servers users signed up with. While federations such as Mastodon offer more censorship resistance than centralized servers — as users are able to simply sign up to another server when censored — criticism has arisen around potential censorship on Mastodon through server owners.
In December 2022, the Nostr community received a 14 BTC grant from Twitter Founder Jack Dorsey, which brought unprecedented attention to the protocol. As applications built on Nostr evolved, the mobile client Damus jumped to number one in social networking on the iOS app store in China, resulting in its ban. In an apparent effort to contain the #MarchOffTwitter, Twitter CEO Elon Musk shortly banned the publication of Nostr-related content, along with bans on other third-party platforms such as Instagram, but to no avail.
While Nostr is by no means a privacy protocol, it could bring potential improvements to Bitcoin privacy.

A Nostr public key shared via Twitter, 2022
While Nostr is not a privacy protocol per se — among other issues, clients by default leak users’ IP addresses to relays — the Nostr protocol could bring improvements to Bitcoin privacy.
Improving Privacy And Scalability Of BIP47
BIP47 is a Bitcoin Improvement Proposal to create reusable payment codes while protecting the privacy of users for recurring payments. Without BIP47, users need to tediously generate new addresses by hand to avoid address reuse. When a user reuses an address for transactions, the user enables anyone watching the blockchain to easily cluster all transactions belonging to the address reused and form a graph of the user’s payment history and net worth. The prevention of address reuse is therefore a privacy best practice in Bitcoin and already implemented in many Bitcoin wallets by default. However, when a user aims to establish recurring payments with another party, such as in a merchant-customer relationship, a frequent generation of new addresses can be inconvenient.
With BIP47, a customer can generate a set of addresses to use for payments for the merchant. If a customer purchases products monthly, the merchant would need to send the customer an address each month. With BIP47, the customer creates a dedicated payment code for the merchant, which functions similarly to an extended public key. This allows the customer to automatically generate new addresses for the merchant, instead of the merchant needing to create addresses for the customer.
BIP47 makes use of notification addresses, which are monitored by HD wallets for outputs. In a notification transaction, the merchant sends the customer a blinded public key and chain code via the OP_RETURN field, together with a shared secret to keep the shared addresses private on the public blockchain. This exchange creates several issues due to the architecture of the Bitcoin network. The first two are economic: A notification transaction consists of 80 bytes, which can become expensive for users when fees on the Bitcoin network are high. Notification transactions, in addition, create unsendable outputs, which bloat the UTXO set over time. This increases the computing load on Bitcoin nodes who, at the time*, need to store the entire UTXO set, meaning every Bitcoin output that has not been used as a new input to ensure the validity of transactions.
A notification transaction creates so-called toxic change. When a user receives change from a notification transaction and spends the change to a third party, anyone watching the blockchain is able to correlate the user’s recurring payments to their non-recurring payments, even when addresses are not reused. A notification address also only exists once for each wallet. If a merchant wanted to establish recurring payments with 10 customers, anyone watching the blockchain is able to gain insight into the merchant’s customer base, as all 10 customers would need to create notification transactions for the merchant to the same notification address.
Instead of using notification transactions to exchange payment codes between merchants and customers, payment codes could be exchanged via Nostr. As opposed to other communication methods, Nostr is suitable for the exchange of BIP47 payment codes as no central authority exists to potentially censor the exchange of messages. At the same time, all direct messages on Nostr are encrypted by default, eliminating the need to compute shared secrets. By making use of BIP47 via Nostr, users can avoid the creation of UTXO set bloat via unspendable outputs and eliminate the correlation of recurring versus non-recurring payments as well as the publication of customer bases through the avoidance of toxic change and the re-use of notification addresses.
*Note: Storing the entire current UTXO set for Bitcoin nodes may potentially be eliminated in the future via the implementation of UTreeXO, which shifts the burden of proving that a transaction spends a valid UTXO to the owner of the UTXO, reducing the storage requirements from gigabytes to kilobytes.
Nostr Pay-To-EndPoint
In Bitcoin, blockchain analysis services operate the heuristic of “common input ownership” to map transactions to identities. Within this heuristic, a transaction containing different public keys used as inputs is classified as belonging to one person. Due to its UTXO-based architecture, through which inputs and outputs of transactions are linked, the Bitcoin protocol is also prone to subset sum analysis. In subset sum analysis, adversaries are able to calculate the probability of inputs and outputs belonging to the same entity, even when different public keys are used as inputs to one transaction. For example, if a transaction has inputs of 1, 4, 7, 23 and 6, and outputs of 5 and 36, it can be deduced that input 1 and 4 and inputs 7, 23 and 6 belong to the same entity.
 Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021
Source: “Knowledge Discovery In Cryptocurrency Transactions: A Survey” by Xia Fan Lu and Xin-Jiang Jang, 2021Pay-to-EndPoint (P2EP) is a privacy-preserving reinvention of Satoshi Nakamoto’s Pay-to-IP (P2IP) coded into the original Bitcoin client. One form of a P2EP transaction are PayJoins, which are transactions designed to break the common input ownership heuristic. In a PayJoin transaction, both the sender and the receiver contribute inputs to a transaction to break the common input heuristic. With PayJoins, users exchange information about what UTXOs will be used as inputs via any communication channel, such as a Tor Onion, which functions as the end point, to construct a partially-signed bitcoin transaction (PSBT). Once both parties have agreed to the terms and signed the transaction, a PayJoin transaction looks just like any other Bitcoin transaction on chain. Because involved parties act as both sender and receiver, a PayJoin transaction breaks the common ownership heuristic as well as subset sum analysis: parties may contribute inputs of 3 and 5, while the transaction generates outputs of 6 and 2.
 *Source: “Pay To EndPoint” by Adam Fiscor, 2018 *
*Source: “Pay To EndPoint” by Adam Fiscor, 2018 *The problem: PayJoin transactions are complicated to coordinate, as participants have to be online at the same time when using a clearnet domain or Tor Onion endpoints. If a user initiates a P2EP transaction and, for example, closes their computer or otherwise disturbs network connectivity, the transaction cannot be communicated. In Nostr, communication is asynchronous: users fetch information from relays once network connectivity is restored. By using Nostr keys instead of Tor Onions as endpoints for P2EP transactions, P2EP transactions could be coordinated more easily.
Another implementation of P2EP is the much-debated LNURL. With LNURL, instead of tediously needing to generate new invoices for each transaction, users are able to receive a static endpoint pointing at a web server to automatically generate new invoices. However, because web servers are reliant on the global Domain Name Service (DNS), users of LNURL inevitably reveal their identity to the hosting provider, as well as their IP address to payees if no proper precautions are taken. Wide adoption of LNURL would therefore be a detriment to the pseudonymity of the Lightning Network. Instead of using a web server as the endpoint for LNURL, users could use Nostr keys as endpoints for LNURL transactions to conceal their identities.
Nostr For CoinJoins
While a PayJoin is great to break the common ownership heuristic as well as subset sum analysis, PayJoins are unable to offer privacy to both sender and receiver toward the cooperating party. PayJoins are essentially two-party CoinJoins, limited to two participants — this means that both sender and receiver are aware of their own inputs and outputs, leaving the inputs and outputs of their partner identifiable. Unless a PayJoin is facilitated with CoinJoined transactions, users risk revealing their wallet balances as well as past and future transactions to their PayJoin partners.
In anonymous-amount credential systems such as Wasabi Wallet’s protocol for CoinJoin coordination, WabiSabi, Nostr keys can function as communication endpoints for the coordination of a CoinJoin transaction. This enables the sender and receiver of a CoinJoin transaction to exchange the credentials needed to participate in CoinJoin rounds, essentially enabling a form of discreet payments within a CoinJoin. With the use of Nostr keys as endpoints in CoinJoins, cooperating parties remain unaware of their counterparties’ balances and transactions by hiding in the crowd. At the same time, using Nostr keys as endpoints for CoinJoin transactions helps PayJoin users save on fees by facilitating payments directly within the CoinJoin, rather than CoinJoining to facilitate the payment after.
Another use for Nostr in CoinJoins lies in the discovery of coordinators. While most CoinJoin coordinators run behind Tor to obscure the identity of CoinJoin participants, users are currently unable to easily discover new coordinators to join with the exception of JoinMarket, a CoinJoin marketplace targeted toward more advanced CoinJoin users. While CoinJoin users are able to add custom coordinators to Wasabi Wallet — a trivial task as easy as exchanging a URL in the backend — no way exists to automate the process of updating coordinators due to the lack of a platform for publication. Instead, to discover new coordinators, users must search social media and forums, such as Reddit or Twitter, to add coordinators manually. However, the publication of a coordinator service via social media or forums may pose a risk to coordination providers depending on the policies applied to the service, as certain pages may easily be shut down.
If Tor is an anonymous remailer, meaning a protocol facilitating the anonymous forwarding and receiving of messages between peers, Nostr can function as an anonymous bulletin board. CoinJoin coordinators can publish their services via a Nostr event type, and CoinJoin wallets can be enabled to automatically pull from those relays to display within their clients. The broadcasting of coordinator servers via Nostr, such as facilitated via BTCPay’ Servers CoinJoin plugin and proposed in the Lightning-enabled CoinJoin software Vortex, can eliminate the need to manually search for and add CoinJoin coordinators in CoinJoin clients, helping to further decentralize the CoinJoin coordination landscape.
Circumventing IP Requirements With NOSTR
As touched upon previously, the Nostr protocol was originally conceptualized to realize a fully-decentralized marketplace called Diagon Alley. As the Nostr protocol evolved, Diagon Alley became the LNbits extension NostrMarkets: a Nostr-native marketplace which enables merchants and customers to run and interact with online shops via relays. In NostrMarkets, customers can subscribe to a merchant's public key to fetch products from relays instead of accessing a merchant’s site via a webshop. This increases the censorship resistance of online shops, as merchants are not dependent on seizable websites — rather, a merchant’s shop is hosted with all relays the shop sets up to communicate with. Even if the merchant's server were to be seized, its shop could easily be set up at a different location, as all products are stored with relays on the Nostr network. NostrMarkets handles order and payment coordination via encrypted Nostr direct messages, while payments are facilitated through the Lightning Network.
In addition to its censorship resistance, the LNbits extension NostrMarkets enables fully-anonymous marketplaces. Instead of exposing a merchant’s IP to the whole world, both merchants and customers only reveal their IPs to the relays they connect to, which can easily be mitigated by running a client or shop behind Tor. As an upside to fully running a shop behind Tor, which makes a shop only accessible via the Tor browser and .onion web pages, NostrMarkets can run in any web browser or smartphone, improving the user experience of privacy-preserving, client-server communications. Because payments are negotiated via encrypted Nostr direct messages and facilitated via the Lightning Network, payments in NostrMarkets remain comparatively private as long as the shop’s Lightning node runs behind Tor, as a payment coordination direct message is indistinguishable from other direct messages in Nostr.
Another way to circumvent the requirement of IP addresses in server client communication is NOSTREST. REST, short for “representational state transfer,” is part of the software architecture of the world wide web, used to facilitate communication between servers and clients via GET, POST, PUT, DELETE and PATCH requests. But, when a client sends a REST request to a server, IP addresses are revealed, potentially revealing personally-identifiable information. On GitHub, escapee proposed a REST API bridge built on Nostr, called NOSTREST. By using Nostr keys without identification headers, both users and server operators do not need to know the IP addresses of their counterparts. A NOSTREST implementation can therefore improve the privacy of Bitcoin applications using REST as servers do not need the clients’ IP addresses.
One such example could be the running of custodial Chaumian e-cash mints, a form of anonymous-amount credential systems. In an e-cash mint, the mint operator does not know the balances or value exchanged by its users. However, due to the current architecture of REST, it does learn the user’s IP address unless running behind Tor by default, such as in the e-cash system Cashu. But implementing and managing Tor support is tedious. With the NOSTREST bridge, projects can easily preserve the privacy of their users. By running an e-cash mint behind Tor using NOSTREST to communicate between server and clients, communication can be facilitated asynchronously, while both server operator and user only learn each other’s public keys, eliminating the risk of identification via IP.
*The original author of this article is L0la L33tz. It was initially published in Bitcoin Magazine. Original article link: https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy
*
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:54:49
@ 9ecbb0e7:06ab7c09
2023-08-03 15:54:49El subsecretario interino del Departamento de Seguridad Nacional (DHS, por sus siglas en inglés) de Estados Unidos, Blas Nuñez-Neto, admitió en una entrevista exclusiva con el periodista cubano Mario J. Pentón que a lo largo de los más de siete meses del proceso de parole humanitario se han cometido fraudes.
“Hemos rechazado la entrada de personas que cometen fraude en el proceso de parole humanitario. También hemos negado las aplicaciones antes que las personas se suban a los aviones”, confirmó el funcionario de la administración demócrata de Joe Biden.
Como ejemplo de las irregularidades detectadas por el DHS, Nuñez-Neto dijo que están “investigando patrocinadores que cobran por sus servicios o desde otra manera están involucrados en el crimen (…) Así que es algo que lo tomamos muy muy en serio”. Adicionalmente, alertó que los culpables se enfrentan a graves consecuencias por mentir al gobierno de EEUU y extorsionar a las personas.
En este sentido, el subsecretario animó a las personas que tienen información acerca de los fraudes que por favor los reporten a las autoridades. En el portal web del DHS hay información para enviar los reportes por diferentes medios de contacto, donde se les asegura el anonimato a quienes colaboren con denuncias.
De acuerdo con Mario J. Pentón, hay historias de beneficiarios del parole que los han regresado a Cuba desde el aeropuerto de Miami por haber pagado para que los patrocinaran. Obviamente, también hay rumores sobre funcionarios corruptos que están en puestos que les permiten acelerar los procesos de parole, pero sobre ese tema Nuñez-Neto no habló con Pentón, ya que se le había acabado el tiempo asignado.
Según el Servicio de Ciudadanía e Inmigración de EEUU (USCIS), proteger la integridad del proceso de inmigración es una prioridad para el gobierno. “Una de las maneras en que protegemos el sistema de inmigración es simplificándole a usted el proceso para reportar el fraude y abuso de inmigración a través de nuestro formulario de sospechas de fraude en línea”, refiere el portal web.
El proceso de otorgamiento del parole, para ciudadanos de Cuba, Nicaragua, Haití y Venezuela, es discrecional y sin límite de tiempo determinado para su procesamiento. USCIS tiene el compromiso de otorgar hasta 30.000 visas humanitarias al mes para estas cuatro nacionalidades.
Al cierre de junio pasado, unos 8.500 ciudadanos cubanos fueron beneficiados con visas humanitarias para ingresar a EEUU. El 92% de ese grupo, aproximadamente 7.800 cubanos, logró ingresar al territorio estadounidense, ya que algunos decidieron esperar para resolver asuntos personales antes de emigrar definitivamente.
-
 @ 1b0706e7:ec11b9b3
2023-08-01 03:01:44
@ 1b0706e7:ec11b9b3
2023-08-01 03:01:44
Starbucks
Saturday August 12, 2023
10:00 a.m -12:00 p.m. 371 Alessandro Blvd, Riverside, CA 92508
Starbucks
Saturday August 26, 2023
10:00 a.m -12:00 p.m. 371 Alessandro Blvd, Riverside, CA 92508
Want to suggest a Meetup? DM's are open and Elon can't stop them.
-
 @ 20986fb8:cdac21b3
2023-08-03 15:51:06
@ 20986fb8:cdac21b3
2023-08-03 15:51:06YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Round 3 will be from 3rd to 7th Aug
How to participate:
- Pick one or multiple Updates below, test it (them)
- Write your feedback and opinion (pros and cons are all welcomed)
- Don't forget to add taggs 'YakiHonne-updates' and 'YakiHonne' to your article
- Post your article on Nostr via YakiHonne.com
- Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our group: http://t.me/YakiHonne_Daily_Featured
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped during each round.
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
Updates to be tested in Round 3:
- Reporting: NIP-56 supported, users now have the ability to report undesired long-form content within the platform.
- Zaps: confirmation prompt to notify the sender that the transaction successfully completed; Zaps stat icon now function same as the original zapping button, so that users can intuitively fast acces to it.
- NIP-05 support: users now have the ability to add their NIP-05 to their profile settings and view other users identifiers across the platform.
- Images upload: all across yakihonne client now have the option to either paste a url image or instantly upload images within yakihonne server (instant uploads for the write article section is coming soon); not restricted to 1MB anymore, use wisely and avoid large images.
- Back-to-Top button: on the home feed page(right-bottom corner) for a quicker navigation.
- Welcome to feedback your suggestions and bugs reporting.
If you missed Round 1 & 2, the updates below could be tested as additions:
Round 2:
-
Comments: re-implemented and comments can be deleted
-
NIP-25 supporting: users now can upvote and downvote
-
Zap stats: Zaps sent and Zaps received can be seen from users profiles
-
“login with an extension” button: now it is grayed out rather than invisible
-
Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme
-
Tags: click on the tags in the article to view the content under the tag
-
Share: sharing posts with one click
-
NIP-05: verify your profile
Round 1:
-
Comment function: more user-friendly
-
Stats area: clearly displays the interactive status of each article
-
Following function: generated-key users can also be followed
-
Curation function: easily add or remove articles from an existing curation
-
Tags: search and browse articles with the tags
-
Home feed scrolling pagination: optimized data fetching and faster loading time
-
Article editing preview: preview the final version of the article while writing in MarkDown
Don't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 37c4e186:7de9109b
2023-08-01 01:34:49
@ 37c4e186:7de9109b
2023-08-01 01:34:49Bitcoin: The Sacrifice of the Ego
by Leopoldo Moreno de la Cova nostr:npub1m2x6mucaxs84d8njq5zrte3ksv7p83ppsqud3a84zww7rfw0hsysrq7v3j
Translated from the original Spanish by nostr:npub1xlzwrphhxppeyjw0prlw0dvpsmx2a8jd6yhnt06clx6zvl0fzzdsgce7w0
"In the world of Bitcoin there is a saying: 'stay humble and stack sats', which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency"
Satoshi Nakamoto is a venerated name in the world of cryptocurrency. He is the creator of Bitcoin, the first decentralized digital currency in the world, and responsible for initiating a revolution in the financial industry. Given the importance of his creation, it is surprising that he has never taken credit, and to this day, the identity of Satoshi continues to be a secret. The anonymity of Satoshi is perhaps the most underrated quality of this quasi-mythological figure, being the best exemplification of the sacrifice of the ego, and something that I consider that we should go into more deeply.
The ego is a powerful force that drives human behavior. It is the sense of self-esteem or self-importance of a person, and often it manifests in the necessity for recognition or credit. However, when we become too attached to our ego, it can lead to arrogance, narcissism, and a distorted view of reality. In contrast, sacrificing the ego requires humility, disinterest, and a disposition to put the needs of others above one's own.
Instead of seeking recognition for his creation, Satoshi decided to remain in the background and to allow his invention to speak for itself. This decision was not motivated by fear or insecurity, but rather by a deep understanding of the potential impact of his creation. Satoshi was conscious that Bitcoin had the potential to transform the financial industry, enabling people to control their own money, converting them into sovereign individuals, independent from corrupt governments, partisian monetary policies, or exhaustive control. He understood that his creation was greater than any single person, including himself.
Upon remaining anonymous, he avoided any potential conflict of interest that could arise because of personal or financial gains, and in its place, he created a decentralized, transparent, and secure system, based on the economic theories of the Austrian school and distancing itself from Keynesian economic policies.
The legend of Satoshi Nakamoto transcends the technological and financial spheres; already his influence has inspired a new generation of entrepreneurs and developers. His focus on decentralization and transparency has been the basis for innovative projects in diverse sectors, such as governance, intellectual property, and data protection. The philosophy behind Bitcoin, which seeks to empower people and democratize access to financial resources, has generated a paradigm shift in the way that we think of money and value. As we advance towards a digital future, the enduring impact of Satoshi and his vision continues to be a lighthouse of inspiration for those who seek to challenge the established system and to construct a more equitable world.
In the world of Bitcoin there is a saying: "stay humble and stack sats", which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency. Using Bitcoin as a store of value has provided an effective strategy for building long-term wealth and resisting the volatility of the market during the last 14 years. Humility has kept us focused on the final objective of the preservation of wealth, meanwhile constant saving/stacking permits us to take advantage of market opportunities and to build a solid base for the future. From my point of view, Satoshi reminds us that the success of decntralized digital money is not about getting rich quickly but rather about the creation of wealth in a constant and responsible fashion, with a focus on preserving property rights and personal liberty.
Through analyzing all of this in detail, perhaps we should not be surprised that something has been created that safeguards property rights, freedom, and privacy like nothing that has been seen in the world before. Satoshi decided to unlink his creation from his identity.
The story of Satoshi Nakamoto is the story of our age. Prometheus brought fire to humanity. Satoshi brought us Bitcoin.
Leopoldo Moreno de la Cova is an economist.
-
 @ 75bf2353:e1bfa895
2023-07-31 21:59:22
@ 75bf2353:e1bfa895
2023-07-31 21:59:22The Easy Way To Self Custody of Bitcoin
 TODO: [TOC]
TODO: [TOC]Note: This is a work in progress. **
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:50:13
@ 9ecbb0e7:06ab7c09
2023-08-03 15:50:13Los cubanos solo podrán sacar 5.000 pesos (CUP) en efectivo de sus cuentas bancarias, según las regulaciones establecidas por la Resolución 11/2023 del Banco Central de Cuba (BCC) que fueron publicadas el 2 de agosto en la Gaceta Oficial Extraordinaria No. 55.
El límite forma parte del corralito bancario que fue anunciado ante la escasez de efectivo provocada por los altos niveles de inflación en la que está inmersa la economía nacional. El mal manejo de las finanzas públicas con erróneas políticas monetarias, sobre todo a partir del establecimiento del mal llamado “ordenamiento económico” han traído estas consecuencias.
Las normativas de la Resolución 11/2023 afectan a múltiples “sujetos”. Ellos son: empresas estatales, organizaciones superiores de dirección empresarial, unidades presupuestadas; cooperativas no agropecuarias; cooperativas agropecuarias; productores agropecuarios; agricultores individuales; pescadores comerciales; micro, pequeñas y medianas empresas; proyectos de desarrollo local; trabajadores por cuenta propia; artistas y creadores; las modalidades de inversión extranjera y las formas asociativas creadas al amparo de la Ley de Asociaciones.
La opción que queda para efectuar acciones de cobro y pago que superen los 5.000 CUP es “mediante los instrumentos de pagos y títulos de crédito”. El BCC priorizará que estas operaciones “se ejecuten por los canales electrónicos de pago”.
Sin embargo, la acreditación de los pagos no se verá reflejada directamente en las cuentas corrientes de los “actores económicos”. Tendrá un retardo debido a las limitaciones tecnológicas del banco y en caso de caer fin de semana o días feriados se demorará más.
“Los ingresos en efectivo en pesos cubanos que reciban los sujetos de esta Resolución, como regla, son depositados en su cuenta corriente, a más tardar al siguiente día hábil bancario a la fecha de su recepción; en el caso de las formas de gestión no estatal, el depósito se realiza en la cuenta reconocida con propósitos fiscales”, refiere el artículo 11.1 de la mencionada Resolución.
Otras regulaciones del BCC
En Banco Central permitirá por los próximos seis meses que las entidades que no tengan a todos sus trabajadores o pensionados bancarizados puedan hacer extracciones de efectivo para el pago de salarios, subsidios y otras prestaciones de la seguridad social y prestaciones a estudiantes. Para ello deben hacerlo como máximo, con tres días hábiles de antelación a la fecha establecida para el pago. Asimismo, ordena restituir ese dinero al banco en caso de pasar siete días sin que los beneficiarios hayan reclamado su pago.
El ministro presidente del BCC, Joaquín Alonso Vázquez, faculta a los “presidentes de bancos o la persona en quien estos deleguen por escrito” para que suspendan “los servicios bancarios o el cierre de la cuenta” a clientes que incumplan con las regulaciones antes mencionadas.
-
 @ f866d5b1:c526b32f
2023-08-03 14:02:05
@ f866d5b1:c526b32f
2023-08-03 14:02:05หลังจากมีบริษัทเอกชนหลายแห่งที่ทำแพลตฟอร์มขายหวยออนไลน์ ในประเทศไทย ปัจจุบัน สำนักงานสลากกินแบ่งรัฐบาล ก็ได้ทำแพลตฟอร์ม Digital Lottery ของตัวเองออกมาให้บริการประชาชนเช่นกัน โดยเริ่มงวดแรกในงวด วันที่ 2 พฤษภาคม 2565 ที่ผ่านมา
ส่วนหวยแบบ n3 จะเริ่มประมาณปี พ.ศ. 2567 ส่วนหวยแบบ l6 จะเริ่มประมาณเดือนกันยายน พ.ศ. 2566
การทำแพลตฟอร์มขายหวยออนไลน์ รวมถึงออกรูปแบบสลากใหม่อย่าง n3 และ l6 ของกองสลากกินแบ่งรัฐบาล ไม่สามารถแก้ปัญหาหวยแพงได้ ปัญหาจริง ๆ ของ ลอตเตอรี่ในไทย คือ รูปแบบการจ่ายเงินรางวัล ที่หากขายสลากไม่หมด จำนวนเงินรางวัลจะถูกลดทอนตามสัดส่วนการขายได้
n3 & l6 ความหวังใหม่แก้ปัญหาหวยแพง
ล่าสุด สำนักงานสลากกินแบ่ง ก็ได้ออกหวยรูปแบบใหม่เพื่อมาแข่งกับหวยใต้ดินที่คนไทยชื่นชอบ และแก้ปัญหาการขายสลากกินแบ่งเกินราคา ด้วยสลากแบบ n3 และ l6
โดยสลากแบบ l6 จะเหมือนกับสลากกินแบ่งแบบเดิมแต่นำไปจำหน่ายแบบออนไลน์ ส่วนหวยแบบ n3 จะคล้ายกับการเล่นหวยใต้ดิน ที่มีให้ลุ้นรางวัล 2 ตัวตรง/ 3 ตัวตรง/ 3 ตัวโต๊ด
แต่เงินรางวัลของหวยแบบ n3 ไม่จูงใจนักเสี่ยงโชคให้ออกมาจากวงการหวยใต้ดินแน่นอน เพราะรูปแบบเงินรางวัลที่แตกต่างจากหวยใต้ดิน
โดยหวยใต้ดินกำหนดเงินรางวัลแน่นอน สามารถรู้แน่ชัดว่าซื้อหวยไป 1 บาท หากถูกรางวัลจะได้รับเงินกลับมาเท่าไหร่
แต่หวยแบบ n3 จะจ่ายรางวัล โดยนำเงินที่ขายได้ทั้งหมด มาปันส่วนตามอัตราที่สำนักงานสลากกินแบ่งรัฐบาลกำหนดไว้แล้ว ดังนี้
แนวทางการใช้เงินจากการขายสลาก n3
| สัดส่วน| วัตถุประสงค์การใช้เงิน | | --- | --- | | 60% | นำไปแบ่งเป็นเงินรางวัล | | ไม่น้อยกว่า 23% | นำส่งเป็นรายได้แผ่นดิน| | ไม่เกินกว่า 17% | ใช้เป็นค่าบริหารจัดการ |
กติกาการจ่ายเงินรางวัลสลากแบบ n3
| ประเภท | สัดส่วนเงินรางวัล | | --- | --- | | 3 ตัวตรง | 30% | | 3 ตัวโต๊ด | 30% | | 2 ตัวตรง | 39% | | รางวัลพิเศษ | 1% |
จะเห็นว่าหากมีการซื้อหวย n3 ทั้งหมด 1,000 ล้านบาท จะนำมาเป็นเงินรางวัลแค่ 600 ล้านบาท โดยแบ่งรางวัลเป็น 3 ตัวตรง 180 ล้านบาท/ 3 ตัวโต๊ด 180 ล้านบาท/ 2 ตัวตรง 234 ล้านบาท/ รางวัลพิเศษ 6 ล้านบาท
ดังนั้น หากเลขเด็ด เลขดัง ที่ถูกรางวัลในงวดนั้น แต่มีจำนวนคนซื้อเยอะมาก ๆ จะทำให้แต่ละคนได้รับเงินรางวัลน้อยลงตามไปด้วย
ด้วยสาเหตุข้างต้น จึงทำให้หวยแบบ n3 ไม่จูงใจให้คนไทยที่นิยมการเสี่ยงโชคเลิกเล่นหวยใต้ดิน แต่จะยิ่งส่งเสริมให้ใช้จ่ายเพื่อบริโภคการเสี่ยงโชคมากขึ้น เพราะมีสินค้าให้เสี่ยงโชคเพิ่มมากขึ้นเสียด้วยซ้ำ
ห้าเสือกองสลาก คือผู้ร้ายจริงหรือ?
จริง ๆ แล้ว ยี่ปั๊ว ที่รับซื้อหวยรัฐบาลยกชุด คือผู้รับภาระที่กวาดซื้อหวยจนหมดแผง ทำให้ไม่มีปัญหาว่า รางวัลที่ 1 ในแต่ละงวดแตกต่างกัน เลขไม่เด่นไม่ดัง อย่าง 00 หรือพวกเลข 0 นำหน้า ส่วนใหญ่คนจะไม่ชอบซื้อทำให้คนที่ได้โควต้าที่ไปเดินสายขายกันเอง ขายไม่หมดจมทุนกำไรหด
การที่ ผู้ขายปลีกที่ได้ โควต้าจากกองสลาก เอาไปขายให้ ยี่ปั๊ว จึงไม่ใช่เรื่องแปลกแต่อย่างใดในทางเศรษฐศาสตร์ เพราะถ้าเอาไปเดินเร่หรือตั้งแผงขายเอง มันขายไม่หมด ถึงขายหมดก็เหนื่อยแรง สู้เอาเงินชัวร์ ๆ จากยี่ปั๊ว มากินมาใช้แบบสบาย ๆ ดีกว่า
ทำอย่างไรถึงจะแก้ปัญหาหวยแพงแบบถาวร
การแก้ปัญหาหวยแพงในประเทศไทยอย่างแท้จริง ไม่ใช่การทำหวยออนไลน์ แต่ต้องปรับกติกาในการได้รับรางวัลที่ใช้อยู่ในปัจจุบัน ที่ระบุหลังสลากว่า “ถ้าสลากจำหน่ายไม่หมด เงินรางวัลหนึ่ง ๆ ต้องลดลงตามสัดส่วน” เพราะการทำช่องทางให้ซื้อขายได้สะดวก มันไม่ได้แก้ปัญหาเลขไม่มงคลที่ไม่ต้องการซื้อ ทำให้ผู้ขายหวยต้องรับภาระจมทุนจากการขายสลากไม่หมดในแต่ละงวดนั่นเอง
-
 @ 75bf2353:e1bfa895
2023-07-31 21:56:11
@ 75bf2353:e1bfa895
2023-07-31 21:56:11
Why TF do we need this book?
Most bitcoin books come in two categories.
1) Bitcoin is the best investment since sliced gold. 2) Bitcoin philosophy
As far as I know, there is not a book that teaches the average person how to take self-custody of their bitcoin. There are many guides, webpages, and YouTube videos, but they are kind of fragmented and require you to take many detours down the rabbit hole. This book is for people who have embroiled themselves in bitcoin. Maybe they read the Bitcoin Standard or the Progressive Case for Bitcoin and have decided they need some bitcoin. They think bitcoin is energy, digital gold, Venice, "the blockchain," proof-of-work, and 12 magic words you memorize and say to retrieve all of your wealth like Wingaudiam Levinosa in Harry Potter.

There are no more bitcoin books to be written. This is not a bitcoin book. It is a compilation of many different tools I have found and used since I got into bitcon. This book will not have any charts. It will not mention the price of bitcoin. The only model is tick-tock-next block. The world will never have 21 million bitcoin. This book will teach you how to control a small fraction of that amount. As long as you can write down 24 words and a passphrase and can store them safely, you will be able to store your bitcoin. You will have your Cold Card memorize your words.
This book will not teach you:
"How much will I get if I invest $100 in Bitcoin? "When Moon?" "How much does it cost to buy one Bitcoin?"
This book will not teach you how to lend your bitcoin or give it to someone else for interest." This is anti-Block-Fi. This book will not teach you how to buy bitcoin from a regulated exchange. Regulated exchanges are some of the most dangerous ways to store your bitcoin. The worst way to store bitcoin is in someone else's wallet. The bitcoin you hold in someone else's wallet is someone else's bitcoin. **This is not a book about other people's bitcoin. This is not about Blackrock's bitcoin, Coinbase's bitcoin, or Strike's bitcoin. This is about your bitcoin. Your bitcoin is your responsibility. ** If you lose your seeds, nothing in this book can help you. ** If you write your passphrase down wrong, you will hodl forever. This book will teach you how to double-check your wallets and do it as easily as possible while having bitcoin IOUs for as little time and as private as we reasonably can expect our privacy to be.
I went to my first bitcoin conference in November of 2020, in the midst of the FTX scam being revealed in real time. FTX was the most regulated of the regulated exchanges. They still stole their customers bitcoin. I didn't speak to anyone at the conference who would admit they kept their bitcoin on FTX, but many people said they kept it on a bitcoin-only exchange. This exchange regularly informs their customers that they need to withdraw. They make it very easy. Yet so many people trust the exchanges more than they trust themselves.
I found this surprising because the second line in the bitcoin white paper is very clear about this.
https://highlighter.com/e/note19r76y6vz7x8rtza8z08zn5htwu94v4mm77vtmqny7lnrhncul0sqsvw5e3
Satoshi Nakamoto said this in February 2009 on the Peer2Peer Foundation:
https://highlighter.com/e/note1dv8gue4e25za3d5p2ej4krcp7kaykfpfpggn6lk393c7zjdacp3s9855l5
note1dv8gue4e25za3d5p2ej4krcp7kaykfpfpggn6lk393c7zjdacp3s9855l5
I decided to write this book for these people to show them they do not need to trust themselves. They can trust the math instead. They can ditch their bitcoin IOUs for real UTXOs. What's a UTXO? an unspent bitcoin transaction output. That's just a fancy way of saying saving bitcoin or stacking sats.
This book is not a 100% trustless way to store bitcoin. That would be the hard way, but I do believe this is possible to achieve, especially if you only use bitcoin on the main chain, but that is beyond the scope of this book. I intend to teach you how to use your bitcoin. If you don't have any bitcoin, don't worry. I will teach you how to get some using bitcoin the way it was meant to be, **peer2peer. **
When you buy bitcoin peer2peer, you know you own bitcoin as soon as it gets to your wallet. This will protect you from exchanges that are regulated by a corrupt financial system that knows how to regulate fractional reserve banks that blow up but has no idea how cryptography works. For this reason, many bitcoiners have fallen victim to scams they thought were safe becauuse of financial regulation that keeps them as safe as the credit ratings of sub-prime mortgages, which means not very safe at all. There are many examples of regulated and unregulated exchanges and lending platforms that were hacked, rehypoticated, or just plain stolen. This book intends to teach you how to protect yourself from unscrupulous exchanges that look legit because of regulation, but are actually rug-pull technology such as:
-FTX -Celcius -Block-Fi -Mt. Gox
-
 @ c5fb6ecc:e58c38bb
2023-05-12 00:59:58
@ c5fb6ecc:e58c38bb
2023-05-12 00:59:58https://ln.tips is a great wallet. It's an extremely easy to use, custodial Lightning wallet for the masses. Each telegram account has it's own
@ln.tipsLN Address, but sometimes you want to use your own domain.In this guide I will teach you how to setup LN Address redirection with your own domain using Cloudflare's Redirection Rules.
Prerequisites
- A Web Domain that's has Cloudflare setup on it.
- https://ln.tips setup and ready to go.
- Using ln.tips is optional. This guide will work with any other custodial wallet that provides you with an LN Address will work too.
Setup
Getting your destructured LN Address
ln.tips
Since ln.tips provides two LN addresses to everybody, you have two options. 1. Use your Telegram username LN address (Not Recommended) 1. This isn't recommended because anyone can see your Telegram username with this method and use it to message you. It's the best choice for anonymity from other users. 2. ex:
nym@ln.tips2. Use your anonymous LN address (Recommended) 1. This is recommended because the address is random, nobody can look this up back to your Telegram account. 2. Can be obtained by running/advancedto the bot, and finding it under "Anonymous Lightning address" 3. ex:0x84e6b3ea699ab309@ln.tipsWhat option you pick doesn't matter to your next step, you're going to want to take the username portion of the address (everything before the @, like an email address) add
https://ln.tips/.well-known/lnurlp/<username>username goes at the end.The final url should look something like
https://ln.tips/.well-known/lnurlp/0x84e6b3ea699ab309(depending on the method you chose)Other platforms
Custodial Wallets that provide you with a Lightning address work similarly to this. Apps like Wallet of Satoshi provide you with a completely random address when you sign up, so a Wallet of Satoshi destructured address would look like:
https://walletofsatoshi.com/.well-known/lnurlp/LawyerCicanery69Setting up Cloudflare Redirects
Assuming that you have Cloudflare hooked up and ready to go, you're going to want to follow a few steps. 1. Open your site on the panel 2. On the sidebar, click the dropdown arrow next to Rules 3. Click "Redirect Rules" 4. Press the button that says "Create Rule" 5. Configure your new rule 1. Give it a name. ex: "lnaddr" 2. Configure the first condition 1. Set "Field" to
URI Path2. Set "Operator" tostarts with3. Set "Value" to/.well-known/lnurlp/3. Configure the "then" 1. Set "Type" toStatic2. Set "URL" to your destructured Lightning address from earlier 3. Set "Status Code" to3074. Check "Preserve query string" 6. Click SaveAll done! Now whenever someone goes to pay your new Lightning address, it should automatically redirect to your custodial wallet. Have fun!
-
 @ 83d999a1:46171d19
2023-08-03 13:56:27
@ 83d999a1:46171d19
2023-08-03 13:56:27We are building something cool that maybe you'll be interested in.
What is this? An announcement of an announcement (AoA for short)?
Well. Yes.
But bear with us.
We are doing an AoA because we haven't figured out all the details yet, (e.g. the name of what we're doing)
But here is what we do know:
- 2 months of focused building in #madeira.
- 21 builders with a record of shipping things in the #lightning/#nostr space
- working individually or in teams to make progress towards advancing freedom tech
- nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft will be physically (and spiritually) there to help bounce ideas off
- Funding (likely) available to all teams
Dates? Jan 8th - March 1st.
How to be a part of it? Details to follow very soon™️
But in the mean time, if you're stoked, DM us at nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5.
-
 @ 2b61985e:f4cebdc3
2023-08-03 10:16:24
@ 2b61985e:f4cebdc3
2023-08-03 10:16:24How the singularity of life will win
Previously published on Substack Jul 14, 2022
In a world where the masters that should never be are going batshit insane wanting to chip and control everyone it can often seem that we’re in for a bleak future.
Going back a few decades those who remember how things were can easily point to myriads of tech based things that have become way more stressful, are seemingly impossible to avoid, keep manipulating our mindstreams and in aggregate seem to change our very being.
But I want you to consider all of this from another perspective. Unless some AI bot is reading this (go away please!) you are a complex being that can navigate a LOT of unknowns, to adapt, interpret and find new ways of managing it all.
We have very good abilities when it comes to pattern recognition, taking in and calculating enormous amounts of organic data and in general find a way through even what looks like its all new, invincible and too much to handle for an individual.
The basic mistake, often subconscious, is to regard new technology and ways of interacting as brand new, something that we have no natural ability to handle. But what lies behind all tech, what drives all interaction on social media, and what will be included even in AI or whatever the tech obsessed engineers can come up with?
In my opinion there is nothing new under the sun when it comes to this basis, it will be the same mix of delusions and hangups we have had to wrangle with since sentience arose. Likewise anything with real good motivation and wisdom behind it will be beneficial, especially once enough of us catch on to the basis of it all being very human motivations.
I’ve been in media tech since 89 when I saw the previous democratic media revolution unfolding with DTP self publishing, and got in early on anything from website development to open source development, cloud computing, crypto and whatever “new” has been popping up. This enabled me to predict a few things like these:
Wondering aloud in 92 why not all phones were mobile when my own draggable one came in at 8 kg and a radio operators license
Almost scaring off old friends in 98 predicting that online dating would be huge
Predicting that all businesses will need smart, integrated online tools of all types to survive in 2005
Seeing that online ID with biometrics would be the BIG thing forward in 2018
Things like working on Amazon AWS since 2010 and seeing how the brutal and seemingly magic capabilities were just metastasizing into something very scary also come with some predictions, but these are far harder to formulate.
The single most important prediction now in 2022 is actually quite optimistic: despite all the capabilities of manipulation and control that converge into a demonic Beast Machine it will all fail to completely subjugate and subvert us humans.
Why? The short answer is that complexity can be handled by sentience/mind itself and especially in distributed networks of separate but connected actors.
The opposite which always is about central control will ultimately fail in the end regardless of capacity since those who do keep that central control will fall prey to the ever present delusions and obscurations.
Those jockeying for central control will end up the same way as the Chinese emperors of old when they hunted for longevity and even eternal life on this planet.
It turned out that eating mercury was not a good idea for longevity, yes this is what they did!
It will be interesting to see how the technocrats bring themselves down this time, and that is what navigating this “new jungle” is about.
So that is why this is Ways Through Wilderness, life will happen as always :-)
-
 @ 57fe4c4a:c3a0271f
2023-07-31 20:54:42
@ 57fe4c4a:c3a0271f
2023-07-31 20:54:42👥 Authors: Davidson Souza ( nostr:npub16qce8d6wvrrarl6pdaf285qaee27pyvumxwdm9x34y227z5uytks9n4zky )
📅 Messages Date: 2023-07-31
✉️ Message Count: 1
📚 Total Characters in Messages: 2209
Messages Summaries
✉️ Message by Davidson Souza on 31/07/2023: Davidson is excited to share
libfloresta, a project he has been developing, with the Bitcoin devs mailing list.libflorestais a compact and simple Bitcoin full node with integrated watch-only wallet and Electrum Server. It is designed for low-power devices and can run virtually anywhere. The project is in an early stage but is already being used on signet. Davidson is usinglibbitcoinconsensusand plans to uselibbitcoinkernelin the future to minimize misimplementations. He thanks Vinteum for supporting his work.Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 2b61985e:f4cebdc3
2023-08-03 10:06:54
@ 2b61985e:f4cebdc3
2023-08-03 10:06:54How the singularity of life will win
Previously published on Substack Jul 14, 2022
In a world where the masters that should never be are going batshit insane wanting to chip and control everyone it can often seem that we’re in for a bleak future.
Going back a few decades those who remember how things were can easily point to myriads of tech based things that have become way more stressful, are seemingly impossible to avoid, keep manipulating our mindstreams and in aggregate seem to change our very being.
But I want you to consider all of this from another perspective. Unless some AI bot is reading this (go away please!) you are a complex being that can navigate a LOT of unknowns, to adapt, interpret and find new ways of managing it all.
We have very good abilities when it comes to pattern recognition, taking in and calculating enormous amounts of organic data and in general find a way through even what looks like its all new, invincible and too much to handle for an individual.
The basic mistake, often subconscious, is to regard new technology and ways of interacting as brand new, something that we have no natural ability to handle. But what lies behind all tech, what drives all interaction on social media, and what will be included even in AI or whatever the tech obsessed engineers can come up with?
In my opinion there is nothing new under the sun when it comes to this basis, it will be the same mix of delusions and hangups we have had to wrangle with since sentience arose. Likewise anything with real good motivation and wisdom behind it will be beneficial, especially once enough of us catch on to the basis of it all being very human motivations.
I’ve been in media tech since 89 when I saw the previous democratic media revolution unfolding with DTP self publishing, and got in early on anything from website development to open source development, cloud computing, crypto and whatever “new” has been popping up. This enabled me to predict a few things like these:
Wondering aloud in 92 why not all phones were mobile when my own draggable one came in at 8 kg and a radio operators license Almost scaring off old friends in 98 predicting that online dating would be huge Predicting that all businesses will need smart, integrated online tools of all types to survive in 2005 Seeing that online ID with biometrics would be the BIG thing forward in 2018Things like working on Amazon AWS since 2010 and seeing how the brutal and seemingly magic capabilities were just metastasizing into something very scary also come with some predictions, but these are far harder to formulate.
The single most important prediction now in 2022 is actually quite optimistic: despite all the capabilities of manipulation and control that converge into a demonic Beast Machine it will all fail to completely subjugate and subvert us humans.
Why? The short answer is that complexity can be handled by sentience/mind itself and especially in distributed networks of separate but connected actors.
The opposite which always is about central control will ultimately fail in the end regardless of capacity since those who do keep that central control will fall prey to the ever present delusions and obscurations.
Those jockeying for central control will end up the same way as the Chinese emperors of old when they hunted for longevity and even eternal life on this planet.
It turned out that eating mercury was not a good idea for longevity, yes this is what they did!
It will be interesting to see how the technocrats bring themselves down this time, and that is what navigating this “new jungle” is about.
So that is why this is Ways Through Wilderness, life will happen as always :-)
-
 @ d5b41074:156978f1
2023-05-07 21:38:01
@ d5b41074:156978f1
2023-05-07 21:38:01Hyper-Nostr: Bringing P2P to relays
People suggested me to write a detailed post blog about my project, explaining how to use it, what it is, what to expect, and how it works. This post is the attempt of doing that.
What is it?
Hyper-Nostr is a decentralized nostr relay. It is a distributed relay, where everyone can have its own local node. Then, they behave as a single relay, sending and keeping the events on the network.
Right now, to use it you need to have
npm, which requiresnodejs. I may add plain executables on the future. You install it asnpm install -g hyper-nostrand then you can start your own node ashyper-nostr [<port> [<topics>...]]. Last step is to add the relay on your client asws://localhost:[port]/[topic]for each topic you want to have on that client. I am still working on havingwssinstead ofws, but looks like clients accept the connection because it is onlocalhost. UPDATE: you can use some reverse proxy to havewss. I personally use caddy so I can docaddy reverse-proxy --to localhost:3000.Right, the topics. The topic is how we find each other, to send the events and have an unified database. Think of it as the address of the hyper-nostr relay, or a specific instance of it.
Having all configured, you can now expect it to work just as a standard relay: it will receive events that was send to these, you will be able to send and receive events, and it will save the events on it.
How it even works?
This project is Powered by Holepunch.
The connections and event streamings happen on Hyperswarm, Autobase linearized the underlying files, and uses a Hyperbeedee database (loosely based on MongoDB).
The hyperswarm and cores management was highly abstracted thanks to Hyper SDK.
Want to know more? Okay, lemme try to explain: - Hyper SDK creates a unified swarm instance that is used by the entirety of the relay; - Each topic creates two underlying hypercores: one that is the same for everyone in the topic, used to connect the peers, and the other is local, for your own local database; - Then, the discovery core has two extensions: the event broadcasting extension, to relay to the connected users the real-time events, and the syncing extension, to share the local databases to the peers; - Then, with the help of Autobase, all the local databases are linearized, giving an unified database shared across all peers. - With that, it is as if every peer has the same database when querying, and every peer receives the broadcasted events on real-time too (filtering by the subscriptions, as specified on NIP-01).
What to expect? (or, what are these logs)
The first message the relay prints is
your key is <key>. This key is the hyperswarm public key, which for now I am doing nothing with it, but maybe in the future I will implement private relays that you connect specific peers on it. Still thinking on it.If you have passed initial topics, they will log here too. When you see
listening on <port>, the relay is now open to receive websocket connections (aka it is ready for your client to connect).During the database indexing it generates a warning of
(node:<PID>) MaxListenersExceededWarning: Possible EventEmitter memory leak detected. 11 append listeners added to [LinearizedCoreSession]. Use emitter.setMaxListeners() to increase limit (Usenode --trace-warnings ...to show where the warning was created). This warning is expected, dont panic.To each websocket connection, the relay will also log 2 messages:
ws connection startedandws connection stablished. They were first there to detect silent crashes during the topic initialization, that happens between these two logs if it didnt happen yet.To each topic initialized, it logs
swarm hyper-nostr-<topic> created with hyper!. The prefix is to mitigate the risk of topic crashing on the hyperswarm.Finally, there is one last thing to expect: peers connections. It logs a count of peers on topics on each connection, in the format of
<count> peers on <topic>!every time the connections update.What do you think? Do you liked this project?
Consider sharing your thoughts with me, I would love to know. Do you think the explanation was superficial? What could I have explained better? Do you have some suggestion for the project?
Consider supporting me, I have no formal job currently, and I am spending a lot of time and energy on this project.
-
 @ 57fe4c4a:c3a0271f
2023-07-31 16:02:14
@ 57fe4c4a:c3a0271f
2023-07-31 16:02:14👥 Authors: Hugo L ( nostr:npub1hc79sstpx7ws6jjaqlsnraseayhjua3q2dgp9cjxjxwex6n4lydqslgpzr )
📅 Messages Date: 2023-07-31
✉️ Message Count: 1
📚 Total Characters in Messages: 13682
Messages Summaries
✉️ Message by Hugo L on 31/07/2023: Transactions on the network should not be judged, and it would be better if we couldn't distinguish between different types. Resources should go to the highest bidder, based on supply and demand. The growth of the blockchain is not caused by inscriptions, but by the limit on storage per block.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 57fe4c4a:c3a0271f
2023-07-31 16:02:13
@ 57fe4c4a:c3a0271f
2023-07-31 16:02:13👥 Authors: Daniel Lipshitz ( nostr:npub1t97ak5ltnq0v72nv4jssnhw0fr09axwqvc20623jfdnvrajae7nqufg2yy )
📅 Messages Date: 2023-07-31
✉️ Message Count: 1
📚 Total Characters in Messages: 1853
Messages Summaries
✉️ Message by Daniel Lipshitz on 31/07/2023: The implementation of full Replace-by-Fee (RBF) could negatively impact merchants and users who rely on 0-conf transactions. GAP600 has seen strong usage of their service and believes the adoption of RBF will change their business.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ a1367061:a337453f
2023-08-03 09:58:43
@ a1367061:a337453f
2023-08-03 09:58:43appena arrivato
-
 @ 0c9b1e9f:3f6db0e0
2023-05-06 01:08:43
@ 0c9b1e9f:3f6db0e0
2023-05-06 01:08:43[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 46fcbe30:6bd8ce4d
2023-04-22 18:36:28
@ 46fcbe30:6bd8ce4d
2023-04-22 18:36:28Due to a bug you might have to scroll down a LOT to find the main content.
With more than 4000 products listed, it's time to extract some numbers.
The following is a breakdown of how many products fall into each verdict and meta-verdict:
| Meta / Verdict | ok | stale obsolete
defunct discontinued | Comment | | --- | --- | --- | --- | | fewusers | 194 | 1229 | Once stale or obsolete, these products have little chance to ever make an impact in the Bitcoin ecosystem. We don't look deeper into these. We started tracking them just in case. Only few were defunct when we first added them. | | custodial | 671 | 310 | This is what the bulk of Bitcoiners use apparently. The most popular mobile Bitcoin "wallets" are custodial (or the rather similar no-send-receive). | | wip | 202 | 639 | For some products we do archaeology and assign verdicts even after they are defunct but that's rather low priority. 202 to go ... for now. | | nosource | 235 | 151 | Most of these are defending their closed-source-ness with prevention of fake copy apps. Either way, nobody can check if they are playing by the rules. | | nowallet | 146 | 119 | Products that look like they might be wallets get looked into and we keep them around to not look into these again and again. Should we hide them somehow? | | nobtc | 105 | 69 | We currently don't analyze products that don't also manage BTC. | | nosendreceive | 84 | 30 | MercadoPago and PayPal have more than 100 million users each - and usually users cannot cash their bitcoins in or out to a self-custodial wallet. | | vapor | 77 | 2 | Most of these are hardware products. | | noita | 32 | 12 | "no interface to authorize a transaction" - No screen. No buttons. Mostly NFC tags that can sign transactions to avoid leaking the key but they sign whatever. | | ftbfs | 19 | 22 | "failed to build from source" - these products share source but we failed to build them in the latest version. | | unreleased | 34 | 6 | Mostly hardware products that were announced and maybe even do a pre-sale already but haven't delivered yet. Once defunct, these are the "vapor ware". | | fake | 4 | 34 | Luckily most of these are available only for a short time after being classified as "fake" but some blatant fakes survive longer than others. | | nonverifiable | 20 | 16 | These are self-custodial, share code and many are working on reproducibility. We track these closely. | | diy | 18 | 13 | Mostly hardware products. When you do it yourself, it is on you to be transparent. | | prefilled | 12 | 11 | Yep. These exist. And people use them. When funds move, it might have been the provider or the client. Both have plausible deniability. | | plainkey | 13 | 7 | These are mostly NFC tags in varying form factors that surrender the private keys to a companion app to do whatever with them. | | obfuscated | 8 | 9 | If we had more resources, we probably would find more products for this verdict. | | reproducible | 9 | 2 | Few verdicts contain fewer products than this - most transparent - verdict. But there is a backlog of hardware wallet projects and later desktop wallets but the latter is a hard problem to solve. | | sealed-plainkey | 6 | 3 | A verdict exclusive to bearer tokens. | | sealed-noita | 3 | 0 | A verdict exclusive to bearer tokens and until some open source "secure element" comes around, the top verdict there. | -
 @ 4d444439:7ed2458b
2023-08-03 09:26:27
@ 4d444439:7ed2458b
2023-08-03 09:26:27The quantum effects of physics are at the atomic and subatomic level, brought to us courtesy of quantum mechanics, and hold the key to major advances — quantum leaps — in computing, communication, measurement, and sensing, known collectively as quantum information science. This informal paper is not intended for physicists, but for computer scientists, software developers, and other non-physicists who wish to become involved with quantum information science, particularly quantum computing, and have a need (or desire) to know something about the underlying physics, particularly enough to understand what makes quantum information science tick, but nowhere near as much as a physicist or hard-core quantum engineer might need.
We need a lot more computing power to tackle much larger and much more complex computing challenges in the decades ahead. Ditto for communication, measurement, and sensing. That’s where quantum effects come in. Quantum information science is the broad umbrella for the theory, science, engineering, technology, infrastructure, and applications related to exploiting quantum effects (quantum mechanics) in the areas of computing, communication, and measurement and sensing.
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
This informal paper will focus primarily on quantum effects alone and how they enable quantum information science, but won’t delve deeply into the various areas of quantum information science itself, such as quantum computing and quantum communication. For a broad summary of quantum information science overall, see:
This informal paper was created from material which was originally in that paper but extracted to become a standalone paper and expanded somewhat.
Here are the topics covered in the remainder of this paper:
- What’s so special about quantum information science?
- What is quantum?
- Quantum mechanics
- Quantum physics
- Quantum chemistry
- Quantum computational chemistry
- Quantum biology
- Quantum field theory
- Quantum theory
- Quantum system
- Isolated quantum system
- Quantum effects
- Quantum resource
- Quantum state
- Wave function
- Linear algebra
- Quantum information
- Quantum bit — qubit
- Stationary, flying, and shuttling qubits
- Measurement / observation
- Observable
- Quantum phenomena
- Macroscopic quantum phenomena
Here are the quantum effects that will be described by this paper — not in any great detail, but simply to give the more casual reader a flavor of what quantum effects are all about:
- Discrete
- Quanta
- Particle and wave duality
- Probabilistic
- Uncertainty
- Superposition
- Schrödinger’s cat
- Cat state
- Entanglement
- Spooky action at a distance
- Bell’s theorem and Bell’s inequality
- Bell states
- Phase
- Interference
- Wave function
- Density matrix or density operator
- Probability amplitude
- Unitarity principle
- Basis state
- Computational basis state
- Quantum state
- State vector
- Collapse of wave function on measurement
- Measurement
- No-cloning theorem
- Hamiltonian
- Schrödinger’s equation
- Time evolution
- Fermi-Dirac statistics
- Bose-Einstein statistics
- Fermions
- Bosons
- Pauli exclusion principle
- Spin
- Integer spin
- Half-spin or half-integer spin or spin 1/2
- Spin up and spin down
- Cooper pairs
- Superconductivity and superfluidity
- Tunneling
- Josephson effect
- Quantum hall effect
- Macroscopic quantum effects
- Zero-point energy and vacuum fluctuations
What’s so special about quantum information science?
There are three key advantages of quantum information science over classical methods:
- Quantum computing offers much greater performance than classical computing through quantum parallelism which offers an exponential speedup — evaluating many (all) possibilities in parallel, in a single calculation.
- Quantum communication offers inherent security through quantum entanglement — also known as spooky action at a distance, in contrast to security as a problematic afterthought for classical communication and networking.
- Quantum metrology and quantum sensing offer much greater accuracy and precision for measurements of physical quantities and detection of objects.
All of these advantages are made possible by the magic of quantum effects enabled by quantum mechanics.
What is quantum?
Quantum is essentially a reference to quantum mechanics, which concerns itself with atomic and subatomic particles, their energy, their motion, and their interaction.
Larger accumulations of atoms and molecules behave in more of a statistical or aggregate manner, where the quantum mechanical properties (quantum effects) get averaged away. Quantum information science and its subfields focus at the quantum mechanical level where the special features of quantum mechanics (quantum effects) are visible and can be exploited and manipulated.
Quantum mechanics
Quantum mechanics is the field of physics which is the theoretical foundation of quantum information science. This paper won’t delve deeply into the concepts of quantum mechanics — see the Wikipedia Quantum mechanics article for more detail.
Feel free to read all my articles on the anti-censorship long content platform yakihonne.com.
The key elements of quantum mechanics are what are known as quantum effects, summarized below.
Quantum physics
Quantum physics is sometimes used merely as a synonym for quantum mechanics, but technically quantum physics is the application to the principles of quantum mechanics to the many areas of physics at the subatomic, atomic, and molecular level, including the behavior of particles and waves in magnetic and electrical fields.
Quantum chemistry
Quantum chemistry is the application of quantum mechanics to chemistry, particularly for the behavior of electrons, including excited atoms, molecules, and chemical reactions.
Applying classical computing to quantum chemistry is referred to as computational chemistry.
Quantum computational chemistry
Applying quantum computing to quantum chemistry is referred to as quantum computational chemistry (and here).
Quantum biology
Quantum biology is the application of quantum mechanics to biology, particularly for the behavior of electrons in complex, organic molecules, such as how organic molecules form, how they can change, how they can decompose, and even how they can fold.
Quantum field theory
Quantum field theory is the part of quantum mechanics concerned with subatomic particles and their interactions, but it is not necessary to dive down to that level of detail to comprehend quantum information science. For more information, see the Wikipedia Quantum field theory article.
Quantum theory
Quantum theory is not technically a proper term. Used loosely, it commonly refers to quantum mechanics or possibly simply to quantum effects.
Quantum system
A quantum system, or more properly an isolated quantum system, is a particle or wave, or collection of particles and waves, which can be analyzed for its quantum effects as if it were a single, discrete object.
Isolated quantum system
Technically, any quantum system is an isolated quantum system. The emphasis is on the fact that the particles and waves within the system can be analyzed and modeled in isolation, without concern for particles and waves outside of the system. That’s the theory. In practice, no system is truly isolated (except maybe the entire universe as a whole), but the assumption of isolation dramatically simplifies understanding, modeling, and computation of the system. Without the concept of an isolated quantum system, the modeling and mathematics would be too complex to be tractable (workable.)
Each qubit of a quantum computer or a quantum communication network is an isolated quantum system, except when it is entangled with other qubits, in which case the entangled qubits collectively constitute a larger isolated quantum system.
Quantum effects
Quantum mechanics — and hence all of quantum information science and its subfields — is based on quantum effects.
A quantum effect is any phenomenon which cannot be fully explained by classical mechanics — quantum mechanics is required.
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
Some quantum effects cannot be directly observed or measured, but can sometimes be indirectly inferred or at least have some ultimate effect on the results of manipulating a quantum system.
Quantum effects and their properties include:
- Discrete rather than continuous values for physical quantities.
- Quanta for discrete values. The unit for discrete values. Technically, quantum is a singular unit and quanta is the plural of quantum (just as with data and datum.)
- Particle and wave duality. Particles have wave properties and behavior, and waves have particle properties and behavior. For example, a photon can act as a particle as well as a wave, and an electron can act as a wave as well as a particle.
- Probabilistic rather than strictly deterministic behavior.
- Uncertainty of exact value or measurement. More than just uncertainty of any measurement, there is uncertainty in the actual value of any property, as a fundamental principle of quantum mechanics. A given property of a given quantum system may have a range of values, even before the property is measured. For example, a particle or wave can be at two — or more — positions at the same moment of time.
- Superposition of states — a quantum system can be in two quantum states at the same time. See spin up and spin down.
- Schrödinger’s cat — a thought experiment which demonstrates superposition — the cat can be both alive and dead at the same time.
- Cat state — alternate name for superposition of two quantum states. A tribute to Schrödinger’s cat.
- Entanglement — the same quantum state can exist at two physically separated locations at the same time.
- Spooky action at a distance — popular reference to entanglement.
- Bell’s theorem and Bell’s inequality — quantum mechanics cannot be explained simply by adding “hidden variables” to classical mechanics.
- Bell states — the various combinations of quantum states for two entangled particles. The quantum states of the two particles are correlated — they may be identical quantum states, but they don’t have to be identical. Measuring the state of one particle will allow the observer to infer the state of the other particle. This is useful for both quantum computing and quantum communication.
- Phase — the complex or imaginary part of the probability amplitude of a quantum state. The notion of cyclical or periodic behavior or a fraction of a single cycle of a wave or circle. Measured either in radians (two pi radians in a circle or cycle) or a fraction between 0.0 and 1.0, where 1.0 corresponds to a full, single cycle or circle (two pi radians.)
- Interference — cancellation or reinforcement of the complex or imaginary part of the probability amplitude of two quantum states (phases). Useful for quantum computing — it enables quantum parallelism. Not to be confused with environmental interference which disrupts the operation of a quantum system.
- Wave function is used to fully describe the state of a particle or wave (technically, an isolated quantum system) based on the probabilities of superposed and entangled states. The sum of the basis states of the quantum system, each weighted by its probability amplitude. Linear algebra is the notation used to express a wave function.
- Density matrix or density operator — an alternative to the wave function for describing the quantum state of a quantum system.
- Probability amplitude — a complex number with both real and imaginary parts which represents the likelihood of the quantum system being in a particular state, a basis state. Square it and then take the square root to get the probability for a particular basis state. The imaginary part of the probability amplitude is also referred to as its phase.
- Unitarity principle — the probabilities (square root of the square of the probability amplitude) of all possible states of a quantum system must sum to 1.0 by definition.
- Basis state — the actual numeric value of a single quantum state, comparable to a binary 0 or 1.
- Computational basis state — the combined basis states of a collection of qubits. A collection of strings of 0’s and 1’s, each string having a probability amplitude as its weight in the wave function. Essentially each string is an n-bit binary value.
- Quantum state — the state of an isolated quantum system described by its wave function. Alternatively, a single basis state.
- State vector — a single-column matrix describing the state of a quantum system, where each row represents a computational basis state and the value in the row represents the probability amplitude for that computational basis state. For a single qubit there would be two rows, for two qubits there would be four rows, and for k qubits there would be 2^k rows. Commonly referred to as a ket, the right hand side of bra-ket notation.
- Collapse of wave function on measurement — the probabilities of superposed states will influence but not completely determine the observed value. Measurement always causes the wave function of a quantum system to collapse — permanently.
- Measurement — the process of observing a quantum system. By definition, measurement causes collapse of the wave function, and will always produce a single basis state (0 or 1) or computational basis state (string of 0’s and 1’s) regardless of any superposition or entanglement which may be defined by the wave function of the quantum system.
- No-cloning theorem — quantum information (quantum state) cannot be copied — attempting to read (measure or observe) quantum state causes it (its wave function) to collapse to a discrete, non-quantum state.
- Hamiltonian — an equation which expresses the energy of a quantum system.
- Schrödinger’s equation — describes the evolution of the quantum state of a quantum system over time in terms of its Hamiltonian and wave function.
- Time evolution — how the quantum state of a quantum system incrementally evolves over time based on its Hamiltonian and wave function. See Schrödinger’s equation.
- Fermi-Dirac statistics — rules for fermions which require them to obey or follow the Pauli exclusion principle.
- Bose-Einstein statistics — rules for bosons which allow them to violate (not follow) the Pauli exclusion principle. Sometimes referred to as BES.
- Fermions — elementary particles, such as electrons, and atoms which obey Fermi-Dirac statistics, including the Pauli exclusion principle. Fermions have half-spin (half-integer spin or spin 1/2) by definition. Fermions can collide, bounce apart, or form composite particles, even molecules.
- Bosons — elementary particles, such as photons, and some atoms under special circumstances, which obey or follow Bose-Einstein statistics, which permits them to violate (not follow) the Pauli exclusion principle. Bosons have integer-spin by definition. Bosons can pass right through each other, or even occupy the same position, without interacting.
- Pauli exclusion principle — no two fermions, particles with half-spin, such as electrons and most atoms, can occupy the same quantum state (e.g., position) at the same time. In contrast, bosons, such as photons and pairs of fermions in special circumstances, can occupy the same quantum state (e.g., position) at the same time.
- Spin — the angular momentum, much like a spinning gyroscope, of an elementary particle or an atom.
- Integer spin — the form of angular momentum of bosons which allows them to violate the Pauli exclusion principle. Bosons obey or follow Bose-Einstein statistics, which allow them to occupy the same quantum state (e.g., position.)
- Half-spin or half-integer spin or spin 1/2 — the form of angular momentum of fermions which requires them to obey or follow the Pauli exclusion principle, preventing them from occupying the same quantum state (e.g., position.)
- Spin up and spin down — spin of a particle can have a direction of spin, which is the direction of the vector representing the angular momentum, and up and down are the direction of the axis of rotation, based on using the right-hand rule, where curled fingers represent the direction of spin and the pointing thumb represents the axis of rotation, pointing either up or down as the thumb points. Spin up and spin down can be used to represent two basis states for both quantum computing and quantum communication. Spin up and down for a particle can in fact be superposed, so that a particle (e.g., qubit) is in a linear combination of both spin up and spin down, corresponding to a linear combination of a 0 and a 1.
- Cooper pairs — electrons can pair up at ultracold temperatures (near absolute zero), so that the pair acts as a single boson rather than as a pair of fermions since the half-spin of each of the two fermions add up to be the integer spin of a boson. This allows the pair to violate the Pauli exclusion principle, enabling superconductivity.
- Superconductivity and superfluidity — the phenomenon of zero resistance, for electrical conduction and mechanical flow respectively, which occurs at ultracold temperatures (near absolute zero), allowing pairs of fermions, such as electrons and helium atoms, to pair up, which transforms the half-spin of each fermion into integral spin for the pair, allowing the pair to act as a boson, which no longer must obey the Pauli exclusion principle, so that the pairs can now occupy the same position, which is permitted for bosons which obey Bose-Einstein statistics, but is not possible for fermions alone, which must obey Fermi-Dirac statistics.
- Tunneling — the ability of a subatomic particle or wave such as an electron to appear to be able to move through a solid barrier as if it weren’t there. In actuality, quantum mechanics dictates that a particle or wave has a probability to be at any given location, so that a particle or wave can have a probability of being at either side of the barrier at a given moment, allowing the particle or wave to appear to skip over or through the barrier in the next moment. An example would be electrons and a Josephson junction used in a superconducting transmon qubit.
- Josephson effect — tunneling of Cooper pairs of electrons through an insulating barrier. Used to implement Josephson junctions, such as for superconducting transmon qubits. Also has applications for quantum sensing and quantum measurement.
- Quantum hall effect — quantized conductance (flow of current or electrons) induced by a magnetic field at very low temperatures. Useful for precise measurements.
- Macroscopic quantum effects — quantum effects which can be observed at the macroscopic scale — above the level of the atomic, subatomic, and molecular scale, such as superconductivity, superfluidity, and the quantum hall effect.
- Zero-point energy and vacuum fluctuations — uncertainty means that even a vacuum is not at absolutely zero energy. A vacuum fluctuates within the range of minimum uncertainty. Although an application to quantum information science is not clear at present, specialized hardware can be used to allow a classical computer to measure the fluctuating zero-point energy of a vacuum to generate true random numbers — which cannot be calculated by a strict Turing machine alone.
- Creation and annihilation operators — primarily to facilitate quantum mechanical modeling of many-particle systems.
Quantum resource
A quantum resource is any quantum effect which has some utility in quantum information science, such as for computation in quantum computing or representing quantum information in quantum communication.
It’s an odd term, but sometimes you see it used. Oddly, a qubit would not technically be considered a quantum resource, but superposition, entanglement, and interference would. See the list of quantum effects above.
Quantum state
Quantum state is the unit of quantum information.
A particle or wave — referred to as an isolated quantum system — has a quantum state for each physical quality which can be observed.
- The quantum state is described by a wave function.
- The individual possible states are known as basis states. Such as a 0 and a 1.
- Each basis state in a wave function occurs with some probability.
- A basis state can also have a complex or imaginary component, known as a phase, which is periodic or cyclical. This is exploited in quantum computing to enable quantum parallelism using interference of the phase of a potentially large number of quantum states.
- The probability and phase are combined into a single, complex value, called the probability amplitude, where the probability is the square root of the absolute value (or modulus) of the complex number.
- The basis states and their probability amplitudes are combined to form the wave function.
- If the probability of a basis state is other than 0.0 or 1.0, the two basis states are superposed.
- The quantum states of two separate particles or waves — two isolated quantum systems — can be shared or entangled.
The concept of quantum state applies across all subfields of quantum information science, not just quantum computing and quantum communication.
See the preceding section on quantum effects for more detail.
Wave function
Each qubit or collection of entangled qubits has a quantum state which is described by a wave function using linear algebra to detail each of the basis states and its probability amplitude.
Linear algebra
Linear algebra is the notation used to express a wave function in terms of basis states and probability amplitudes. It’s complex math (figuratively and literally), and not for the faint of heart.
Quantum information
Classical information (a sequence or collection of bits) is represented as quantum information in the form of a quantum state, one quantum state for each classical bit.
Quantum state is the unit of quantum information.
To be clear, quantum information can represent more than just a 0 or 1 classical bit. Since it is a quantum state, it may include a superposition of both a 0 and a 1. The probabilities of 0 and 1 may differ (but they have to add up to 1.0). The probability can include a phase component, and a quantum state may be entangled or shared between two or more separate, otherwise-isolated quantum systems (particles or waves.)
The concept of quantum information applies across all subfields of quantum information science, not just quantum computing and quantum communication.
Quantum bit — qubit
A quantum bit or qubit is the unit of storage and manipulation of quantum information (quantum states).
Qubits are used for both quantum computing and quantum communication.
Despite popular misconceptions, a qubit is not the quantum equivalent of classical information or the classical bit. Rather, a qubit is a device for storing and manipulating quantum information, not the quantum information itself, which is represented as the quantum state of the device. In classical computing and classical communication a bit is the abstract information, not the physical representation.
A bit is either a 0 or a 1, regardless of whether that 0 or 1 is represented as a voltage level, a magnetic field, a photon, or a punched hole.
Quantum information is a 0 or a 1 or a linear combination of a 0 and a 1, regardless of the technology used to implement the qubit device which holds and manipulates that quantum information (quantum state.)
Stationary, flying, and shuttling qubits
For quantum computing, generally a qubit is a stationary qubit, which is a hardware device which stores and manipulates quantum information. It is stationary, meaning that the device does not move.
For quantum communication, a qubit is a flying qubit, typically a photon which gains its utility or ability to communicate by being moveable to a remote location while it is in an entangled state with another qubit at a different and possibly very distant location.
A trapped-ion quantum computer may use shuttling to move a qubit — an ion or atom with a net charge — a short distance so that it is easier to manipulate and measure the quantum state of the qubit, and to store more qubits than can be directly controlled or measured directly.
Measurement / observation
Quantum state is not directly observable or directly measurable using normal, non-quantum methods, devices, or instruments. We can indeed measure any quantum information we want, but measuring a quantum state has the effect of collapsing the wave function of that quantum state, eliminating the truly quantum-ness of the state (e.g., superposition, entanglement, and interference or phase), leaving the quantum information in a purely classical state, such as the 0 and 1 of classical information.
These aspects of measurement apply across all of the subfields of quantum information science — quantum computing, quantum communication, and quantum metrology and sensing.
Observable
Any quantum effect which can be observed or measured is referred to as an observable.
Generally, the quantum state is the quantum effect which is the observable.
Quantum phenomena
Quantum phenomenon is a vague term which is loosely a synonym for quantum effect, or any phenomenon in which a quantum effect is observable in some way, including macroscopic quantum phenomena.
Macroscopic quantum phenomena
A macroscopic quantum phenomenon is any phenomenon above the level of the atomic, subatomic, and molecular level in which a quantum effect is observable in some way.
Prime examples are superconductivity, superfluidity, and the quantum hall effect.
Additional phenomena to consider
I need to dive deeper into these phenomena to figure out how they might be integrated here, especially with regard to quantum information science:
- The quantum hypothesis — in general. Historical role in transitioning from the classical world to the quantum world.
- Momentum, angular momentum, orbital momentum.
- Pure state, mixed state, density matrix, density operator.
- Wave packets.
- Nuclear magnetic resonance (NMR). Some early efforts in quantum computing relied on NMR.
- Nuclear electric resonance.
- Gravity. Nominally lies in the realm of General Relativity rather than quantum mechanics, but… who knows for sure. Can a quantum computer be used to accurately simulate or model gravity and gravitational effects, including effects on time and space? Clearly quantum metrology relates to gravity and gravity waves in some way.
- Add Helicity (spin, angular momentum), Chirality (handedness), polarization, and detail on creation and annihilation operators (primarily to facilitate quantum mechanical modeling of many-particle systems.)
- Harmonics.
- Localization vs. spooky action at a distance.
- Nuclear electric resonance.
- Is friction a quantum effect?
- Avalanche and threshold effects as quantum effects?
- Correlated quantum matter and quantum materials.
- What exactly is quantum theory — vs. quantum effects, quantum mechanics, and quantum physics?
- Mention hidden variables.
- Mention Hilbert space.
- Nonlocality, Bell’s theorem, nonlocal correlations.
- Contextuality — Kochen–Specker (KS) theorem, also known as the Bell–Kochen–Specker theorem.
- Add Penrose microtubules and consciousness.
- Quantum logic clock.
- AMO physics — atomic, molecular, and optical — matter-matter and light-matter interactions at the scale of no more than a relatively few atoms.
- Are phase transitions a quantum effect — macroscopic in aggregate, but specific effect at the atomic or molecular level, and could they be used for quantum information science?
- Quantum correlations.
- CHSH inequality.
- Interaction-free detection.
- Ghost imaging.
- Thermodynamics, quantum thermodynamics.
- Quantum dot.
- Position, navigation, and timing (PNT). More of an application of quantum effects.
Quantum 2.0 or should it be called Quantum 4.0?
Some people are now touting current quantum technologies — including quantum computing — as Quantum 2.0. I’d beg to differ.
I would classify Quantum 1.0 as the original work on quanta by Planck, Einstein, and Bohr — and others.
I would classify Quantum 2.0 as applying quantum mechanics to physics for practical applications, including the transistor, laser, superconductivity, and superfluidity.
I would classify Quantum 3.0 as the early efforts at quantum computing, quantum communication, quantum sensing, and quantum metrology — all fairly primitive and not really ready for practical application.
I would classify Quantum 4.0 as the next generation of quantum information science, including more advanced quantum computing architectures and programming models, quantum communication, quantum networking, quantum sensing, and quantum metrology — progressing towards practical applications.
And maybe Quantum 5.0 would be widespread adoption of quantum technologies, including quantum computers capable of achieving dramatic quantum advantage for production-scale practical real-world applications, and maybe even deployment of quantum networking — distributed quantum computing with quantum state transported between quantum computers separated by significant physical distances.
Alternative titles
I had difficulty deciding on a good title for this informal paper. These alternatives would have been equally good titles:
- Quantum effects
- Quantum effects for quantum computing
- Quantum effects for quantum information science
- What are quantum effects?
- Superficial introduction to quantum effects for non-physicists
- What are quantum effects and how do they relate to quantum computing?
- What are quantum effects and how do they relate to quantum information science?
- Quantum effects — The magic sauce which enables quantum information science
- Quantum effects — The magic sauce which enables quantum computing
- What are Quantum effects and how do they enable quantum information science?
Conclusions
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
Quantum effects enable the capabilities of quantum computing, quantum communication, and quantum sensing and measurement.
For more information about those capabilities and a broad summary of quantum information science overall, see: What Is Quantum Information Science?
By:Jack Krupansky Link:https://jackkrupansky.medium.com/what-are-quantum-effects-and-how-do-they-enable-quantum-information-science-75981368d059
-
 @ 3f770d65:7a745b24
2023-07-31 12:53:38
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-
 @ 6e468422:15deee93
2023-04-04 13:23:19
@ 6e468422:15deee93
2023-04-04 13:23:19Not too long ago, I tried to paint a picture of what a vision for a value-enabled web could look like. Now, only a couple of months later, all this stuff is being built. On nostr, and on lightning. Orange and purple, a match made in heaven.
It goes without saying that I'm beyond delighted. What a time to be alive!
nostr
Here's the thing that nostr got right, and it's the same thing that Bitcoin got right: information is easy to spread and hard to stifle.[^fn-stifle] Information can be copied quickly and perfectly, which is, I believe, the underlying reason for its desire to be free.
[^fn-stifle]: That's a Satoshi quote, of course: "Bitcoin's solution is to use a peer-to-peer network to check for double-spending. In a nutshell, the network works like a distributed timestamp server, stamping the first transaction to spend a coin. It takes advantage of the nature of information being easy to spread but hard to stifle."
Easy to spread, hard to stifle. That's the base reality of the nature of information. As always, the smart thing is to work with nature, not against it.[^1] That's what's beautiful about the orange coin and the purple ostrich: both manage to work with the peculiarities of information, not against them. Both realize that information can and should be copied, as it can be perfectly read and easily spread, always. Both understand that resistance to censorship comes from writing to many places, making the cost of deletion prohibitive.
Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
Eric Hughes, A Cypherpunk's Manifesto
Nostr is quickly establishing itself as a base layer for information exchange, one that is identity-native and value-enabled. It is distinctly different from systems that came before it, just like Bitcoin is distinctly different from monies that came before it.
As of today, the focus of nostr is mostly on short text notes, the so-called "type 1" events more commonly known as tweets.[^fn-kinds] However, as you should be aware by now, nostr is way more than just an alternative to twitter. It is a new paradigm. Change the note kind from
1to30023and you don't have an alternative to Twitter, but a replacement for Medium, Substack, and all the other long-form platforms. I believe that special-purpose clients that focus on certain content types will emerge over time, just like we have seen the emergence of special-purpose platforms in the Web 2.0 era. This time, however, the network effects are cumulative, not separate. A new paradigm.Let me now turn to one such special-purpose client, a nostr-based reading app.
[^fn-kinds]: Refer to the various NIPs to discover the multitude of event kinds defined by the protocol.
Reading
I'm constantly surprised that, even though most people do read a lot online, very few people seem to have a reading workflow or reading tools.
Why that is is anyone's guess, but maybe the added value of such tools is not readily apparent. You can just read the stuff right there, on the ad-ridden, dead-ugly site, right? Why should you sign up for another site, use another app, or bind yourself to another closed platform?
That's a fair point, but the success of Medium and Substack shows that there is an appetite for clean reading and writing, as well as providing avenues for authors to get paid for their writing (and a willingness of readers to support said authors, just because).
The problem is, of course, that all of these platforms are platforms, which is to say, walled gardens that imprison readers and writers alike. Worse than that: they are fiat platforms, which means that permissionless value-flows are not only absent from their DNA, they are outright impossible.[^2]
Nostr fixes this.

The beauty of nostr is that it is not a platform. It's a protocol, which means that you don't have to sign up for it---you can create an identity yourself. You don't have to ask for permission; you just do, without having to rely on the benevolence of whatever dictator is in charge of the platform right now.
Nostr is not a platform, and yet, powerful tools and services can be built and monetized on top of it. This is good for users, good for service providers, and good for the network(s) at large. Win-win-win.
So what am I talking about, exactly? How can nostr improve everyone's reading (and writing) experience?
Allow me to paint a (rough) picture of what I have in mind. Nostr already supports private and public bookmarks, so let's start from there.
Imagine a special-purpose client that scans all your bookmarks for long-form content.[^fn-urls] Everything that you marked to be read later is shown in an orderly fashion, which is to say searchable, sortable, filterable, and displayed without distractions. Voilà, you have yourself a reading app. That's, in essence, how Pocket, Readwise, and other reading apps work. But all these apps are walled gardens without much interoperability and without direct monetization.
[^fn-urls]: In the nostr world long-form content is simply markdown as defined in NIP-23, but it could also be a link to an article or PDF, which in turn could get converted into markdown and posted as an event to a special relay.
Bitcoin fixes the direct monetization part.[^fn-v4v] Nostr fixes the interoperability part.
[^fn-v4v]: ...because Bitcoin makes V4V practical. (Paywalls are not the way.)
Alright, we got ourselves a boring reading app. Great. Now, imagine that users are able to highlight passages. These highlights, just like bookmarks now, could be private or public. When shared publicly, something interesting emerges: an overlay on existing content, a lens on the written Web. In other words: swarm highlights.
Imagine a visual overlay of all public highlights, automatically shining a light on what the swarm of readers found most useful, insightful, funny, etc.
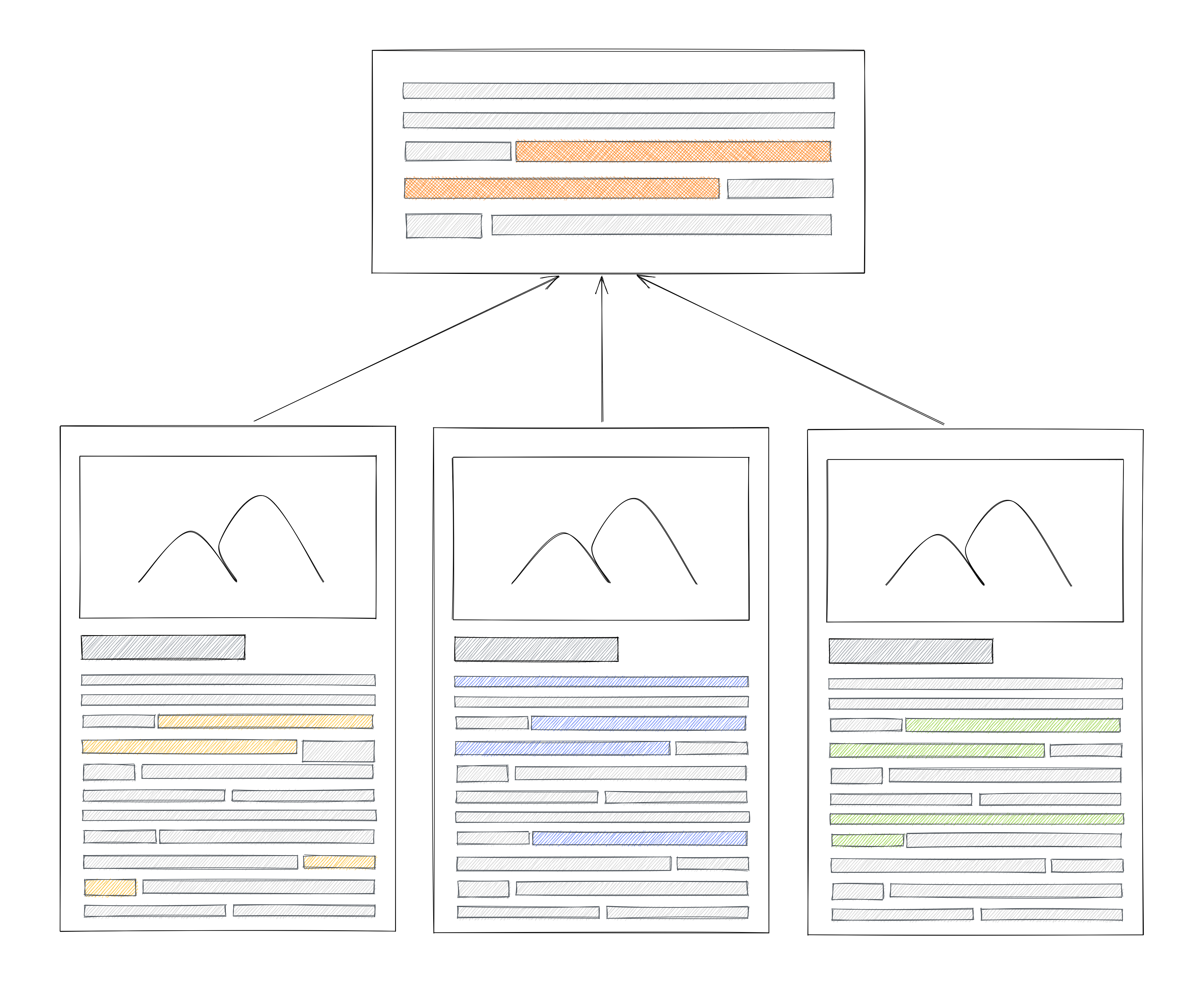
Further, imagine the possibility of sharing these highlights as a "type 1" event with one click, automatically tagging the highlighter(s)---as well as the author, of course---so that eventual sat-flows can be split and forwarded automatically.
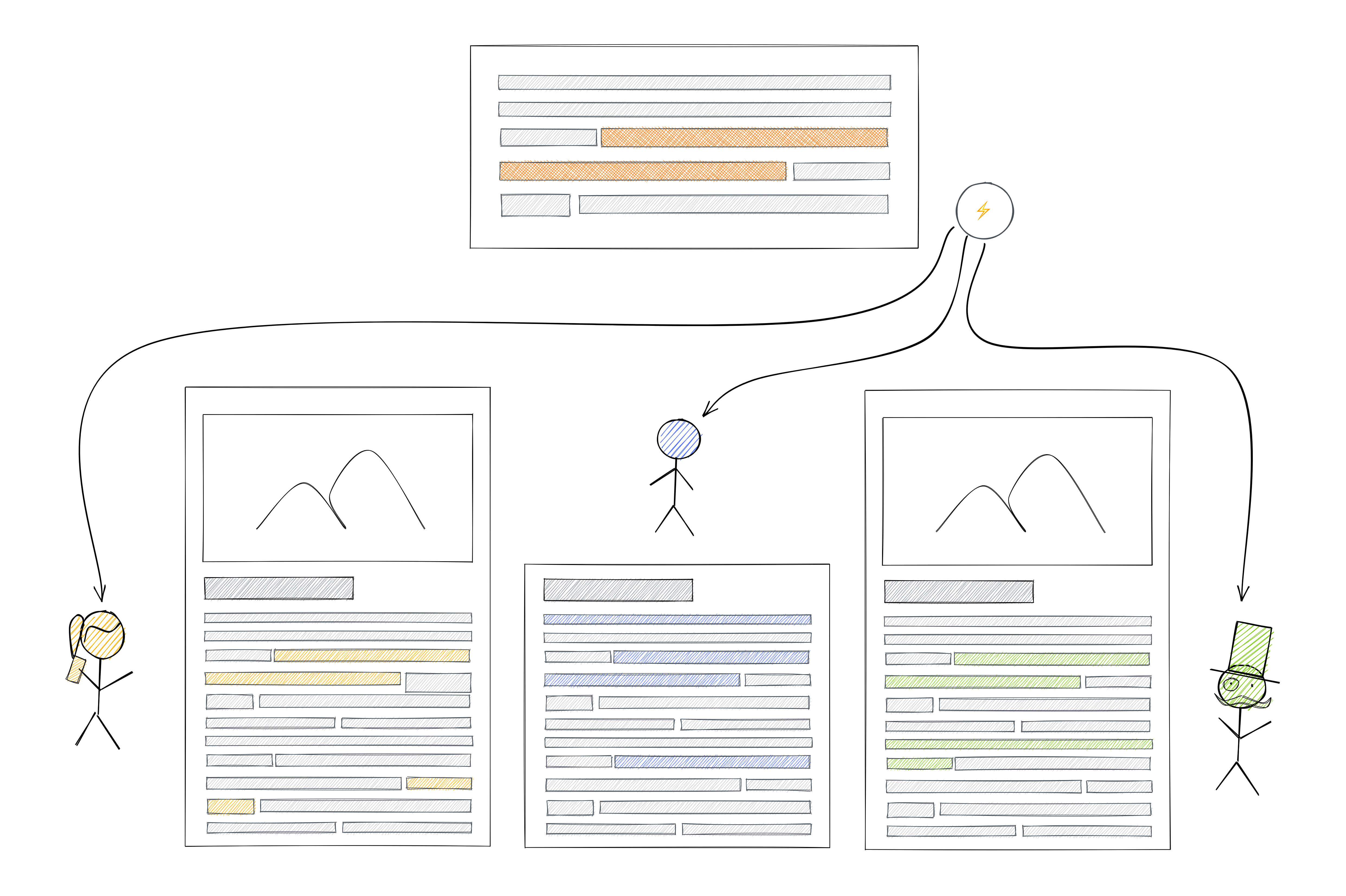
Voilà, you have a system that allows for value to flow back to those who provide it, be it authors, editors, curators, or readers that willingly slog through the information jungle to share and highlight the best stuff (which is a form of curation, of course).
Zaps make nostr a defacto address book[^fn-pp] of payment information, which is to say lightning addresses, as of now. Thanks to nostr wallet connect (among other developments), sending sats ~~will soon be~~ is already as frictionless as leaving a like.
[^fn-pp]: The Yellow Pages are dead, long live The Purple Pages!
Value-for-value and participatory payment flows are something that traditional reading apps desperately lack, be it Pocket, Instapaper, Readwise, or the simple reading mode that is part of every browser.
A neat side-effect of a more structured way to share passages of text is that it enables semi-structured discussions around said passages---which could be another useful overlay inside special-purpose clients, providing context and further insights.[^5]
Further, imagine the option of seamlessly switching from text-on-screen to text-to-speech, allowing the user to stream sats if desired, as Podcasting 2.0 clients already do.[^3]
Imagine user-built curations of the best articles of the week, bundled neatly for your reading pleasure, incentivized by a small value split that allows the curator to participate in the flow of sats.
You get the idea.
I'm sure that the various implementation details will be hashed out, but as I see it, 90% of the stuff is already there. Maybe we'll need another NIP or two, but I don't see a reason why this can't be built---and, more importantly: I don't see a reason why it wouldn't be sustainable for everyone involved.
Most puzzle pieces are already there, and the rest of them can probably be implemented by custom event types. From the point of view of nostr, most everything is an event: bookmarks are events, highlights are events, marking something as read is an event, and sharing an excerpt or a highlight is an event. Public actions are out in the open, private actions are encrypted, the data is not in a silo, and everyone wins. Especially the users, those who are at the edge of the network and usually lose out on the value generated.
In this case, the reading case, the users are mostly "consumers" of content. What changes from the producing perspective, the perspective of the writer?
Writing
Back to the one thing that nostr got right: information is easy to spread but hard to stifle. In addition to that, digital information can be copied perfectly, which is why it shouldn't matter where stuff is published in the first place.
Allow me to repeat this point in all caps, for emphasis: IT SHOULD NOT MATTER WHERE INFORMATION IS PUBLISHED, and, maybe even more importantly, it shouldn't matter if it is published in a hundred different places at once.[^fn-torrents]
What matters is trust and accuracy, which is to say, digital signatures and reputation. To translate this to nostr speak: because every event is signed by default, as long as you trust the person behind the signature, it doesn't matter from which relay the information is fetched.
This is already true (or mostly true) on the regular web. Whether you read the internet archive version of an article or the version that is published by an online magazine, the version on the author's website, or the version read by some guy that has read more about Bitcoin than anyone else you know[^fn-guy]---it's all the same, essentially. What matters is the information itself.
[^fn-guy]: There is only one such guy, as we all know, and it's this Guy: nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev
Practically speaking, the source of truth in a hypernostrized world is---you guessed it---an event. An event signed by the author, which allows for the information to be wrapped in a tamper-proof manner, which in turn allows the information to spread far and wide---without it being hosted in one place.
The first clients that focus on long-form content already exist, and I expect more clients to pop up over time.[^4] As mentioned before, one could easily imagine prism-like value splits seamlessly integrated into these clients, splitting zaps automatically to compensate writers, editors, proofreaders, and illustrators in a V4V fashion. Further, one could imagine various compute-intensive services built into these special-purpose clients, such as GPT Ghostwriters, or writing aids such as Grammarly and the like. All these services could be seamlessly paid for in sats, without the requirement of any sign-ups or the gathering of any user data. That's the beauty of money proper.
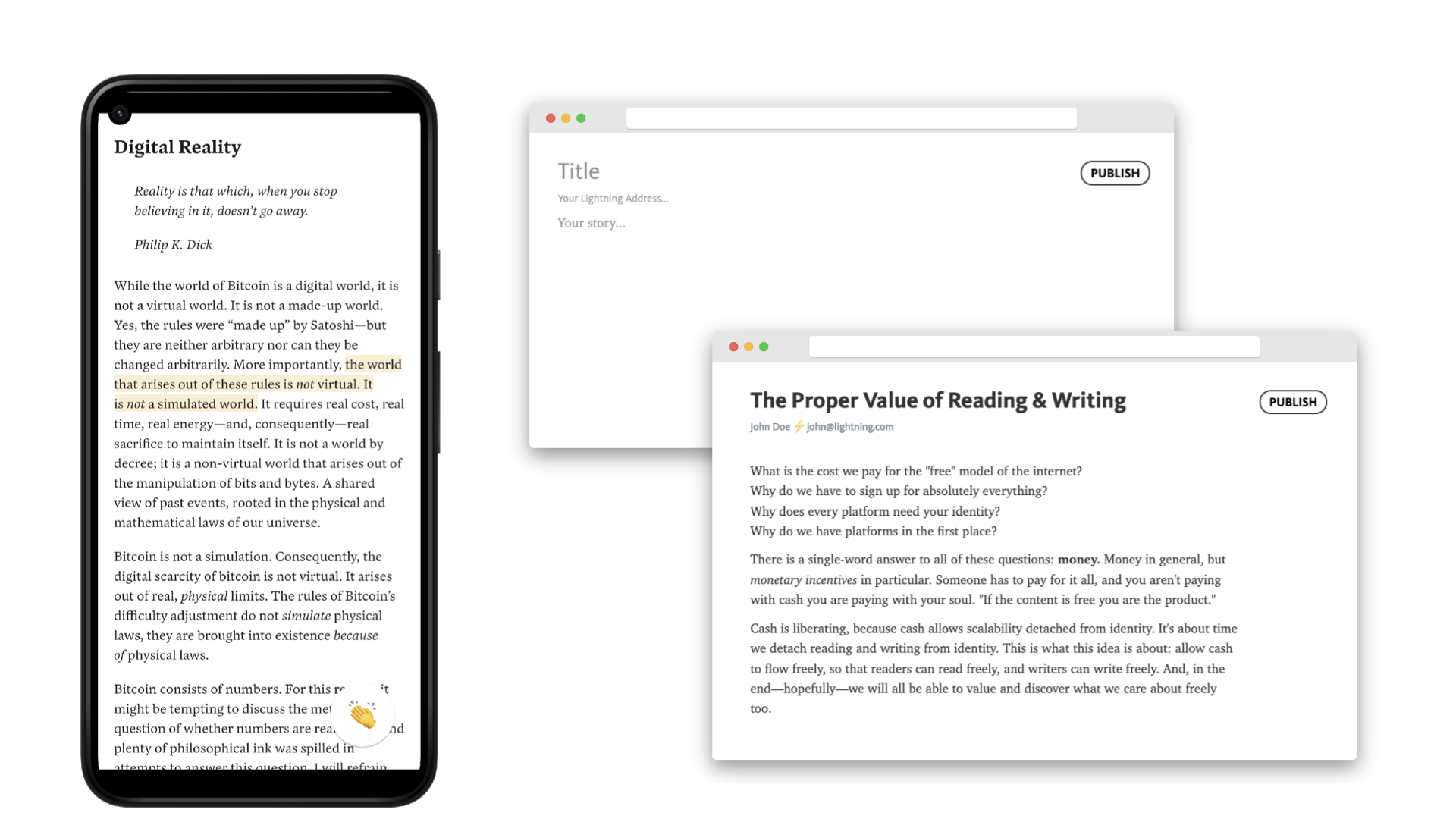
Plagiarism is one issue that needs to be dealt with, of course. Humans are greedy, and some humans are assholes. Neither bitcoin nor nostr fixes this. However, while plagiarism detection is not necessarily trivial, it is also not impossible, especially if most texts are published on nostr first. Nostr-based publishing tools allow for OpenTimestamp attestations thanks to NIP-03, which in turn allows for plagiarism detection based on "first seen" lookups.
That's just one way to deal with the problem, of course. In any case, I'm confident that we'll figure it out.
Value
I believe that in the open ~~attention~~ information economy we find ourselves in, value will mostly derive from effective curation, dissemination, and transmission of information, not the exclusive ownership of it.
Although it is still early days, the statistics around Podcasting 2.0 and nostr zaps clearly show that (a) people are willing to monetarily reward content they care about, and (b) the willingness to send sats increases as friction decreases.
The ingenious thing about boostagrams and zaps is that they are direct and visible, which is to say, public and interactive. They are neither regular transactions nor simple donations---they are something else entirely. An unforgable value signal, a special form of gratitude and appreciation.
Contrast that with a link to Paypal or Patreon: impersonal, slow, indirect, and friction-laden. It's the opposite of a super-charged interaction.
While today's information jungle increasingly presents itself in the form of (short) videos and (long-form) audio, I believe that we will see a renaissance of the written word, especially if we manage to move away from an economy built around attention, towards an economy built upon value and insight.
The orange future now has a purple hue, and I believe that it will be as bright as ever. We just have a lot of building to do.
Further Reading
NIPs and Resources
- Nostr Resources
- value4value.info
- nips.be
- NIP-23: Long-form content
- NIP-57: Event-specific zap markers
- NIP-47: Nostr Wallet Connect
- NIP-03: OpenTimestamps attestations for events
Originally published on dergigi.com
[^1]: Paywalls work against this nature, which is why I consider them misguided at best and incredibly retarded at worst.
[^2]: Fiat doesn't work for the value-enabled web, as fiat rails can never be open and permissionless. Digital fiat is never money. It is---and always will be---credit.
[^3]: Whether the recipient is a text-to-speech service provider or a human narrator doesn't even matter too much, sats will flow just the same.
[^4]: BlogStack and Habla being two of them.
[^5]: Use a URI as the discussion base (instead of a highlight), and you got yourself a Disqus in purple feathers!
[^fn-torrents]: That's what torrents got right, and ipfs for that matter.
-
 @ 57fe4c4a:c3a0271f
2023-07-30 22:54:53
@ 57fe4c4a:c3a0271f
2023-07-30 22:54:53👥 Authors: Carla Kirk-Cohen ( nostr:npub17xugd458km0nm8edu8u2efuqmxzft3tmu92j3tyc0fa4gxdk9mkqmanw36 )
📅 Messages Date: 2023-07-27
✉️ Message Count: 1
📚 Total Characters in Messages: 698
Messages Summaries
✉️ Message by Carla Kirk-Cohen on 27/07/2023: Transcripts of specification meetings held every other Monday are now available at https://btctranscripts.com/lightning-specification, thanks to Gurwinder at Chaincode.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 7f4f672a:c184579e
2023-08-03 08:59:56
@ 7f4f672a:c184579e
2023-08-03 08:59:5622nd of July, 2023. 08:07 am
What are public goods?
Public good are things which benefit everyone, which are publically owned. They can be accessed by everyone , they give value to everyone, and anyones use of the good does not reduce it's value or availability to others.
Examples ; the local park, clean air, beaches (non-private), local infratructure (not tolled)
ChatGPT: 1. Non-excludability: This means that once a good is produced, no one can be excluded from using it. It's available for everyone, regardless of whether they pay for it or not. For example, think about a public park. Once it's there, anyone can enjoy it, regardless of whether they contributed to its maintenance or creation.
- Non-rivalry: This means that one person's use of the good doesn't reduce its availability for others. Again, consider the public park. If one person is using the park, it doesn't prevent others from also using it.
Four Types of Goods: There are four categories of goods in economics, based on whether the goods are excludable and/or rivalrous in consumption.
- Private goods: Private goods are excludable and rival. Examples of private goods include food, clothes, and flowers. There are usually limited quantities of these goods, and owners or sellers can prevent other individuals from enjoying their benefits. Because of their relative scarcity, many private goods are exchanged for payment.
- Common goods: Common goods are non-excludable and rival. Because of these traits, common goods are easily over-consumed, leading to a phenomenon called “tragedy of the commons. ” In this situation, people withdraw resources to secure short-term gains without regard for the long-term consequences. A classic example of a common good are fish stocks in international waters. No one is excluded from fishing, but as people withdraw fish without limits being imposed, the stocks for later fishermen are depleted.
- Club goods: Club goods are excludable but non-rival. This type of good often requires a “membership” payment in order to enjoy the benefits of the goods. Non-payers can be prevented from access to the goods. Cable television is a classic example. It requires a monthly fee, but is non-rival after the payment.
- Public goods: Public goods are non-excludable and non-rival. Individuals cannot be effectively excluded from using them, and use by one individual does not reduce the good’s availability to others. Examples of public goods include the air we breathe, public parks, and street lights. Public goods may give rise to the “free rider problem. ” A free-rider is a person who receives the benefit of a good without paying for it. This may lead to the under-provision of certain goods or services.
The funding of public goods by Quadratic funding is an interesting topic.
References
Retroactive Public Goods https://medium.com/ethereum-optimism/retroactive-public-goods-funding-33c9b7d00f0c
https://socialsci.libretexts.org/Bookshelves/Economics/Economics_%28Boundless%29/8%3A_Market_Failure%3A_Public_Goods_and_Common_Resources/8.1%3A_Public_Goods
economics #explorethis
-
 @ 57fe4c4a:c3a0271f
2023-07-30 22:54:53
@ 57fe4c4a:c3a0271f
2023-07-30 22:54:53📝 Summary: The convo discusses the concept of multipath keysend, which allows for splitting payments into multiple parts. This adds complexity to keysend but can be useful in certain situations. ZmnSCPxj proposes a multipath payment protocol called "keysend" that enables this functionality. The protocol allows the receiver to claim the payment once all parts have arrived.
👥 Authors: • Olaoluwa Osuntokun ( nostr:npub19helcfnqgk2jrwzjex2aflq6jwfc8zd9uzzkwlgwhve7lykv23mq5zkvn4 ) • Thomas HUET ( nostr:npub1tcwr7j30p5q4sypnsw4arca9s2433s7wdcpt2z2sk7pkqfsntjds0pu5xp ) • Matt Morehouse ( nostr:npub1zgyy2j829vn4zuvhkgza7qe37knzdls4kuwt2k8cehwpjxn9duwqv5j4mf ) • Matt Corallo ( nostr:npub1e46n428mcyfwznl7nlsf6d3s7rhlwm9x3cmkuqzt3emmdpadmkaqqjxmcu ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l )
📅 Messages Date Range: 2023-07-27 to 2023-07-29
✉️ Message Count: 5
📚 Total Characters in Messages: 13928
Messages Summaries
✉️ Message by ZmnSCPxj on 27/07/2023: A scheme for creating a
keysendprotocol that allows for multipath payments is proposed, where the receiver can claim the payment once all parts have arrived.✉️ Message by Thomas HUET on 28/07/2023: The motivation for multipath keysend is to allow for splitting payments into multiple parts, ensuring the receiver can only claim the payment once all parts have arrived. This adds complexity to keysend, but may be useful for certain use cases.
✉️ Message by Matt Morehouse on 28/07/2023: ZmnSCPxj proposes a scheme for a multipath payment protocol called "keysend" that allows for splitting payments into multiple parts.
✉️ Message by Olaoluwa Osuntokun on 29/07/2023: The email discusses a scheme for creating a multipath payment protocol using keysend, allowing the receiver to claim the payment once all parts have arrived.
✉️ Message by Matt Corallo on 29/07/2023: The author suggests implementing a multipath payment protocol for keysend, allowing the receiver to claim the payment once all parts have arrived.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ f296e355:c28d00bc
2023-08-03 08:31:44
@ f296e355:c28d00bc
2023-08-03 08:31:44The history of codes and cryptography is a fascinating topic that spans thousands of years and involves many different methods and technologies. I have wanted to write on this topic for quite some time now but couldn’t complete it due to other projects at hand. Many people on individual basis and even companies use cryptographic techniques for various reasons from protecting sensitive data and preventing espionage to enabling the creation and exchange of cryptocurrency and other digital assets. But many people have little to no idea about the evolution of codes and cryptographic systems. In this piece, we shall briefly overview some of the main phases and milestones in the development of cryptology, the science of making and breaking codes.
 Photo by cottonbro studio from Pexels
Photo by cottonbro studio from PexelsFeel free to read all my articles on the anti-censorship long content platform yakihonne
Ancient Ciphers and Early Encryption Techniques
Ancient ciphers and early encryption techniques are methods of transforming messages or information in such a way that only authorized parties can access them. They usually involve replacing or rearranging the letters or symbols of the original message with a secret key or algorithm. Here are some examples of ancient ciphers and early encryption techniques:
The Caesar Shift Cipher
The Caesar cipher, employed by Julius Caesar and his army during the 1st century BC, served as a means to encrypt military and official messages. Operating as a simple substitution cipher, it involved replacing each letter in the message with another letter positioned a fixed number of places away in the alphabet. For instance, with a shift of 3, ‘A’ would be substituted with ‘D’, ‘B’ with ‘E’, and so forth. The key for this cipher represented the number of positions to shift, encompassing values ranging from 1 to 25. To decipher the message, the recipient needed knowledge of the key to revert the letters to their original positions. However, the Caesar cipher was susceptible to frequency analysis, a method involving the tabulation of letter occurrences in the ciphertext and comparing them against the expected frequencies in the language, thus rendering it relatively easy to break.
The Scytale Cipher
The Spartans and other ancient Greeks utilized a cipher during the 7th century BC for the encryption of military and political messages. This particular cipher operated as a transposition cipher, whereby the arrangement of letters in the message was altered based on a concealed pattern. The pattern, in this case, was determined through the utilization of a cylindrical rod known as a scytale. To encrypt the message, the sender would encircle a strip of parchment or leather around the scytale and proceed to inscribe the message along its length. Subsequently, the strip would be unwrapped and dispatched to the intended recipient. For decryption, the recipient would require a scytale possessing an identical diameter to rewrap the strip around it and decipher the concealed message. This cipher’s security was compromised, as its vulnerability lay in attempting various diameters of rods until the message became intelligible, rendering it relatively easy to break.
The Steganography
Steganography, distinct from a cipher, represents a technique employed to conceal messages in plain sight by disguising them as something else. Its origins can be traced back to ancient times, and it has found utility across a range of endeavors encompassing espionage, propaganda, and art. Several examples of steganography include inscribing a message on a shaved head, allowing the hair to regrow and obscure the hidden text, utilizing invisible ink or microdots to convey information, and embedding messages within different mediums, such as texts, images, audio, or video files. If executed adeptly, steganography can prove challenging to detect; nevertheless, it can be exposed through meticulous scrutiny or by subjecting the medium to careful examination or analysis.
The Renaissance and Early Modern Cryptography
The Renaissance and early modern period witnessed a flourishing of cryptography as a result of political, religious, and scientific developments. Cryptography became more sophisticated, diverse, and widespread, as well as more subject to cryptanalysis and code-breaking. Here are some aspects and examples of cryptography in this era:
The rise of diplomatic cryptography
During the Renaissance, a notable transformation occurred in the realm of diplomacy, paving the way for the establishment of a modern system characterized by permanent embassies, the formulation of international law, and multilateral negotiations among autonomous states. Given the crucial need for secure communication between ambassadors and their respective home governments, as well as among allies and adversaries, the significance of cryptography as an indispensable tool for diplomats became apparent. Cryptography served a dual purpose, enabling diplomats to safeguard their confidential information while simultaneously providing a means to engage in covert intelligence gathering, influencing public sentiment, and monitoring their rivals’ activities. As diplomatic relations evolved, cryptography emerged as an essential component in the arsenal of tools employed by diplomats to navigate the intricate web of international affairs during the Renaissance.
Here’re a few examples of diplomatic cryptography are:
- The Vigenère cipher, a polyalphabetic substitution cipher that was considered unbreakable for centuries. It was invented by Giovan Battista Bellaso in 1553 and improved by Blaise de Vigenère in 1586. It was widely used by European diplomats until the 19th century.
- The Babington Plot, a conspiracy to assassinate Queen Elizabeth I of England and replace her with Mary, Queen of Scots in 1586. The plot was exposed by Sir Francis Walsingham, Elizabeth’s spymaster, who intercepted and deciphered the letters between the plotters using a nomenclator, a combination of symbols and code words.
- The Great Cipher, a complex substitution cipher that was used by the kings of France from Louis XIV to Louis XVI. It was invented by Antoine and Bonaventure Rossignol in 1645 and remained unsolved until 1890.
 One component of a customary nomenclator employed during the era of Louis XIV, 1690. Wikimedia Commons Public Domain Image.
One component of a customary nomenclator employed during the era of Louis XIV, 1690. Wikimedia Commons Public Domain Image.The role of cryptography in religion and science during the Renaissance
Within the backdrop of the Renaissance, a period characterized by profound intellectual and societal transformations, religious conflicts like the Protestant Reformation and the Catholic Counter-Reformation took center stage. Simultaneously, the era bore witness to groundbreaking scientific advancements and methodologies, including the revolutionary Copernican heliocentric model and the Baconian induction. In the middle of these developments, cryptography emerged as a significant factor influencing both religious and scientific domains. Cryptography served as a means to express dissent, preserve orthodoxy, and facilitate the clandestine transmission of knowledge. Furthermore, it became a subject of scholarly inquiry and experimentation for esteemed scholars and natural philosophers of the time. Cryptography thus acquired a dual role, influencing and being influenced by the intellectual currents that shaped the Renaissance era.
Some examples of cryptography in religion and science are:
- The Trithemius cipher, a progressive polyalphabetic substitution cipher that was invented by Johannes Trithemius, a German abbot and occultist, in 1508. It was disguised as a book on magic called Steganographia, which claimed to teach how to communicate with angels using hidden messages in texts.
- The Baconian cipher, a biliteral substitution cipher that was devised by Francis Bacon, an English philosopher and scientist, in 1605. It used two different typefaces or fonts to encode messages within other texts. Bacon also proposed a method of hiding messages in musical notes or knots.
- The Newtonian cipher, a numerical substitution cipher that was used by Isaac Newton, an English physicist and mathematician, to encrypt his private notes on alchemy and theology. He assigned numbers to the letters of the alphabet according to their order or frequency and wrote them in groups of five.
Photo by K. Mitch Hodge on Unsplash
The Enigma Machine and World War II
The Enigma machine and World War II are closely related, as the Enigma was a cipher machine used by Nazi Germany to encrypt and decrypt messages for military and diplomatic purposes. The Enigma was considered to be very secure and reliable, but it was eventually broken by the Allies, who used the intelligence gained from reading the German messages to gain an advantage in the war.
The Enigma machine
The Enigma machine, conceived by German engineer Arthur Scherbius in 1918 and patented in 1923, emerged as a remarkable electro-mechanical apparatus consisting of several components. Comprising a keyboard, lampboard, plugboard, and a set of rotors, it enabled the encryption and decryption of messages.
Photo by Christian Lendl on Unsplash
Users would input plaintext or ciphertext through the keyboard, and the corresponding encrypted or decrypted letters would be displayed on the lampboard. The plugboard facilitated additional permutations of letters, while the rotors, altered with each keystroke, modified the electrical connections between the keyboard and lampboard. The Enigma machine boasted an extensive array of potential settings, rendering the key challenging to guess or crack via brute-force methods. These settings involved the selection and order of rotors, initial rotor positions, and the plugboard configuration. To maintain security, these settings were altered daily or even more frequently, using secret key lists that were distributed to operators in advance. Although initially intended for commercial purposes, the Enigma machine swiftly gained traction among various military and government entities worldwide, most notably the Nazi regime in Germany, who employed it extensively before and during World War II.
World War II
World War II, a global conflict spanning from 1939 to 1945, witnessed the engagement of two opposing alliances: the Axis powers and the Allied powers. The devastating war led to vast casualties, widespread destruction, and profound socio-political transformations.
Cryptography played a pivotal role during this period as both sides employed various encryption and decryption techniques to secure their communications and gather intelligence on their adversaries.
Among these methods, the Enigma machine held paramount importance for Nazi Germany, serving as a device to encode critical messages across all branches of the German military. The initial breakthrough in cracking the Enigma code came in 1932 when Polish mathematicians developed techniques and machines to decipher it. They subsequently shared their achievements with British and French intelligence prior to the outbreak of the war. In 1939, Britain established the clandestine code-breaking unit Ultra at Bletchley Park, led by mathematician Alan Turing and a team of experts. Building upon the Polish methods, they refined decryption processes and devised new machines, such as the Bombe, to decipher Enigma messages on a larger scale. The successful decryption of the Enigma code provided the Allies with a pivotal advantage in numerous battles and campaigns, including the Battle of Britain, the Battle of the Atlantic, and the pivotal D-Day invasion. It also allowed for vigilant monitoring of German movements, plans, and intentions. Estimates from historians suggest that the breaking of the Enigma code potentially shortened the war by two to four years, resulting in the preservation of millions of lives.
Photo by Mauro Sbicego on Unsplash
The Digital Age and Public-Key Cryptography
The digital age and public-key cryptography are interrelated, as the advent of digital technologies and the internet created new challenges and opportunities for cryptography.
Public-key cryptography, aka asymmetric cryptography, is a cryptographic field that employs a pair of interconnected keys, namely a public key and a private key, for the purpose of encrypting and decrypting messages.
Public-key cryptography revolutionized the field by allowing secure communication between parties who have no prior knowledge or trust of each other, using mathematical techniques such as asymmetric encryption and digital signatures.
The digital age
The digital age is the period of history characterized by the widespread use of digital technologies, such as computers, the internet, mobile devices, and social media. The digital age began in the late 20th century and continues to the present day. This age has brought many benefits and challenges for cryptography. On one hand, it has enabled faster, cheaper, and more accessible encryption and decryption of data, as well as new applications and domains for cryptography, such as e-commerce, online banking, cloud computing, cryptocurrency, and blockchain.
On the other hand, it has also increased the risks and threats of cyberattacks, hacking, surveillance, identity theft, and data breaches. It has also increased the demand and complexity of cryptography. As more data is generated, stored, transmitted, and processed online, there is a greater need for protecting its confidentiality, integrity, authenticity, and availability. As more users and devices are connected to the internet, there is a greater challenge for distributing and managing cryptographic keys securely.
Public-key cryptography
Public-key cryptography was invented in 1976 by Whitfield Diffie and Martin Hellman in their seminal paper “New Directions in Cryptography”. They proposed a method of key exchange that allowed two parties to establish a shared secret key over an insecure channel without any prior communication or trust. This method is known as the Diffie-Hellman key exchange.
This type of cryptography that uses pairs of related keys:
a public key that can be openly distributed without compromising security, and
a private key that should be kept under secrecy by the owner of the key
The keys are generated with cryptographic algorithms based on mathematical problems called one-way functions, which are easy to compute in one direction but hard to reverse.
Public-key cryptography has two main functions: encryption and digital signatures. Encryption is the process of transforming a message into an unreadable form using a key. Digital signatures are the process of creating a unique code that can verify the identity of the sender and the integrity of the message using a key. Anyone with a public key can encrypt a message for a specific recipient who has the corresponding private key. The decryption of the message can only be performed by the intended recipient using their private key.
Consider this example, Alice can send Bob an encrypted message using Bob’s public key that only Bob can decrypt with his private key. In public-key digital signatures, anyone with a private key can sign a message with their private key to create a signature. The authenticity of the signature and its association with the signer can be verified by anyone possessing the corresponding public key and confirming if it matches the message. For example, Alice can sign a message with her private key to create a signature that Bob can verify with Alice’s public key.
This type of cryptography was further developed by Ronald Rivest, Adi Shamir, and Leonard Adleman in 1977 when they created the RSA algorithm, which is one of the most widely used public-key encryption and digital signature schemes today. RSA stands for Rivest-Shamir-Adleman, the initials of its inventors.
 Ronald Rivest, Adi Shamir, & Leonard Adleman, 1977. Photographed by: Unknown. Source: National Cryptographic Foundation
Ronald Rivest, Adi Shamir, & Leonard Adleman, 1977. Photographed by: Unknown. Source: National Cryptographic FoundationQuantum Cryptography: A New Era of Encryption
A new era of encryption phrase that describes the use of quantum physics to create and secure cryptographic systems that are theoretically immune to conventional attacks.
Quantum cryptography exploits the properties of quantum mechanics, such as superposition, entanglement, and uncertainty, to perform tasks that are impossible or infeasible with classical cryptography.
Quantum key distribution
Quantum key distribution (QKD) stands as the most extensively explored and implemented approach within the realm of quantum cryptography. Serving as a technique, QKD enables two parties, commonly referred to as Alice and Bob, to establish a shared secret key over an insecure communication channel, including fiber-optic cables or free space, devoid of any prior communication or established trust. QKD capitalizes on the principle that quantum states, such as photons, cannot be replicated or measured without perturbation. Thus, any potential eavesdropper, often denoted as Eve, who endeavors to intercept or tamper with the quantum signals will inevitably introduce errors or irregularities, which can be detected by Alice and Bob. Through the implementation of suitable protocols and error correction techniques, Alice and Bob can generate a key that boasts provable security and randomness. This key can subsequently be utilized for encrypting and decrypting messages using conventional symmetric-key algorithms like AES or DES.
The notable advantage of QKD lies in its ability to securely distribute keys, addressing a prominent vulnerability within classical cryptography. Additionally, QKD facilitates the frequent updating of keys, thereby amplifying the security and freshness of the encryption process. The conceptualization of QKD originated from independent proposals by Stephen Wiesner in 1970 and Charles Bennett and Gilles Brassard in 1984. The first experimental demonstration of QKD occurred in 1990, conducted by Bennett and John Smolin. Since then, QKD has been further developed and tested across diverse settings, including metropolitan networks, satellite links, and underwater channels.
 Stephen Wiesner, 1988. Public Domain Image. Wikimedia Commons.
Stephen Wiesner, 1988. Public Domain Image. Wikimedia Commons.Quantum-resistant cryptography
Quantum-resistant cryptography, also known as post-quantum cryptography or quantum-proof cryptography, is a branch of classical cryptography that aims to create encryption methods that cannot be broken by quantum computers. Quantum computers are hypothetical machines that can exploit quantum phenomena to perform certain computations faster than classical computers.
QRC is motivated by the fact that some of the most widely used public-key algorithms, such as RSA and ECC, are based on mathematical problems that are hard to solve with classical computers but easy to solve with quantum computers. For example, Shor’s algorithm is a quantum algorithm that can factor large numbers efficiently, which would break RSA encryption. Similarly, Grover’s algorithm is a quantum algorithm that can search unsorted databases faster than classical algorithms, which would reduce the security of symmetric-key algorithms. The objective is to develop novel public-key algorithms that rely on mathematical problems posing challenges for both classical and quantum computers in terms of solving them. Some of the candidates for quantum-resistant cryptography are based on lattice problems, code problems, multivariate problems, hash-based problems, or supersingular elliptic curve problems. These algorithms are currently being evaluated and standardized by various organizations, such as NIST and ETSI.
Cryptography has evolved from simple manual methods to complex mechanized and digital systems, driven by the needs and demands of communication, security, and privacy. It has also played a very crucial role in many historical events (the Babington plot, for example), such as wars, revolutions, and discoveries, as well as in many modern applications, such as e-commerce, online banking, and cryptocurrency. It’s not only a practical tool, but also a scientific and mathematical discipline that explores the limits and possibilities of information theory, computation, and quantum physics. It is constantly changing and most certainly evolving, as new threats and opportunities emerge in the digital age.
By:Sunny Labh Link:https://www.cantorsparadise.com/the-history-of-codes-and-cryptography-from-caesar-cipher-to-quantum-encryption-262992255320
