-
 @ 202365de:dad57ea9
2023-04-10 02:26:25
@ 202365de:dad57ea9
2023-04-10 02:26:25It was a mid August evening on a remote trout stream in central Pennsylvania, and I was all set to wet my line in the hopes of hooking a beautiful trout. The water was clear and the air humid as I approached the bank with my fly rod tucked under my arm. As I readied myself to cast, I repositioned my Nittany Blue cigar, careful not to obstruct my view of the stream with my exhale, as I targeted a feeding brown with what seemed a satiating appetite. A more practiced fly Fisherman would have attempted to 'match the hatch' where as I tied on a size 6 streamer and readied myself to cast, quartering downstream and swinging the fly across, envisioning the take, the fight, the landing.
I heard a friendly voice from behind me, asking how the fishing was. My buddy Ben and I had been friends since the end of our Penn State tenures, and after school we continued to stay connected as we both appreciated the outdoors and specifically tricking finicky trout with thread and precision. Ben was kind enough to offer me a spot on his weekend getaway with his Dad Jack, up in the Allegheny's at a well known yet private Rod & Gun club where they are members. I acknowledged Ben and was right back in the zone, focused on the task at hand in the dying daylight.
The cast, the mend, the strip. Slam! The brown inhaled the streamer and a fight ensued on my Cabelas Genesis 4 wt. Upon landing the fish, I looked up and saw an older gentleman sitting under the canopy of what seemed to be an old hut. He didn't have the same urgency to be on the water, perhaps he was reminiscing on all the times he had been in my boots, trying to get just one more fish before dark. He acknowledged my catch and continued to take in the evening scenery.
I turned to see Ben and his Dad walking towards him and other members of the club across the bank. Jack called out from across the stream, "hey Barry, do you want to meet Joe Humphreys?" I was floored. Where would we be going to meet him? Was the living legend of Pennsylvania fly fishing actually here on the property? I picked up my net, notched my fly accordingly on my rod, and began trotting with pace downstream to cross to the other side. I recognized him right away. It was Joe Humphreys, a living legend in the world of fly fishing. I couldn't believe my luck. Here, on this remote stream, I had the opportunity to meet and chat with one of the greatest fly anglers of all time.
Joe was so gracious, he knew I was a big fan. I told him my story of getting into fly fishing, swapping stories about fishing and life. I had already researched about his experiences fishing all over the world and his passion for teaching the next generation of anglers. In person he was unassuming and humble, making our interaction personable as if he had known me since I was a kid. His enthusiasm was infectious, and I couldn't help but feel lucky to be sharing the water with him.
As I recall, Ben and I fished and landed trout all day, and I watched in awe as Ben expertly cast his line and maneuvered his fly across the water. His knowledge and ease of use displayed years of experience, evident in every cast he made. Joe had been his teacher, his mentor on the water and I realized then I was in the company of serious practitioners of the sport. I decided to dedicate serious time and effort for the next time I'd have the opportunity.
As the sky finally turned black and the stars came out, we packed up and made our way up to the clubhouse. I left the stream that day feeling inspired by my chance encounter with such a fishing legend, and with a renewed appreciation for the beauty and challenge of fly fishing. It was a memory I'd cherish for a lifetime.
-
 @ 97c70a44:ad98e322
2023-04-07 16:23:31
@ 97c70a44:ad98e322
2023-04-07 16:23:31Yesterday I was browsing bountsr and discovered a new bounty by fiatjaf for adding "relay browsing" to clients. This is the bounty Coracle was born to claim! However, it's a problem I've been putting off for some time now, because it's a very hard problem requiring some real creativity. In this post I'll survey the state of the art, try to articulate my vague ideas about what needs to be done, and sketch some next steps toward realizing this goal.
The problem of relays
Relays are a problem. They are simultaneously an implementation detail that users don't understand and don't want to deal with, and the very soul of Nostr. So far, no client has unleashed the power of Nostr's architecture, instead focusing on ease of adoption by starting users off with a hard-coded set of relays. Users are then left to dig through their settings to change which relays they want to connect to. Others, like Primal, attempt to elide the concept of relays altogether and provide a unified view of the entire network.
Various nods to the importance of relays do exist in various clients however, for example:
- Amethyst shows pretty granular controls and stats on their relay list.
- Snort (and others) shows the list of relays other users connect to on their profile page.
- Gossip has all kinds of settings for how many relays to use, how smart to be about relay discovery, and more.
- Coracle shows which relays an event was seen on in the note's overflow menu, and asks new users to select relays during the onboarding process.
Other common patterns include: color-coding relays, differentiating between read and write relays, and auto-selecting relays different from the user's own selections in order to fetch context related to a given note or feed.

All of these are great features, but they are baby steps, and don't fundamentally address the problem (or realize the possibility) of allowing users to navigate between overlapping venn diagrams of relays and their content.
Let me tell you about my feelings
I think it's generally a shared perception that these half-measures aren't enough, but nobody really knows what to do about it. Even fiatjaf, who has relentlessly pushed development efforts towards surfacing relays admits in the bounty cited above, "The app should make it seamless to browse these various scenarios, I have no idea how."
I share this utter sense of bewilderment. I feel unmoored when I try to think what a user interface that fully embraced multiple relays would look like. Decades of using software with a single-master paradigm has broken my mind; designing something that could actually be used to seamlessly navigate between relays is a massive effort for my poor, tired brain.
The closest thing to a "vision" for what this would look like is what Arkin0x has built with ONOSENDAI: a vast, three-dimensional space that you can travel through. Although to solve the problem, they would have to use an address space focused on relationships between relays, pubkeys, and events, rather than event content simhashes.

This could be a workable approach, resulting in something similar to LN Insights, a browser for lightning network topology, which adds node capacity and clustering as additional dimensions. But it's also true that this type of visualization quickly becomes disorienting, and is far less familiar than a traditional user interface with buttons and menus.

There are examples of this kind of thing being executed successfully by tools like Figma which allow you to zoom in and out on your canvas to travel from one place to another. Games like Supreme Commander support zoom-to-navigate, in addition to showing multiple windowed views of the same game. Tools like Photoshop and vector graphics editors take a different approach and introduce an extra dimension by allowing you to group content into multiple layers.

Another way to think about the additional dimension that relays introduce is by imagining Nostr is a virtual world, with geography (relays), actors (pubkeys), and history (events). Users are mobile, and can travel at will through the world (unless denied access by a relay), viewing artifacts left by other users in the form of published events. The wrinkle is that events can happen in multiple places at the same time, or be replicated across space over time as events get re-broadcasted.
Take a look at the conversation I had with Arkin0x on telegram while writing this post for more ideas for representing Nostr in 3D space.
Back to flatland
In traditional user interfaces, relationships within the data model are not usually represented spatially, except in very purpose-built applications like UML diagrams or mind maps. Instead, space is taken up by an additional dimension: affordances for user interaction. Screens are designed according to functionality, and access to groups of those functions exist in navigation items or menus. Content is addressed by overlaying those groups of functionality either literally via modal dialogs, or dimensionally using "Uniform Resource Locators". There's no space left for representing the same address space in multiple dimensions, especially simultaneously.
So, what is required is either a new UI element or a re-purposed one that satisfies the same semantics as a checkbox group: a way to choose zero or more options for the same value. This isn't too hard, you could add a dropdown menu on feed views, and call it good. But this won't make any sense to users unless they know what differentiates relays from one another, and with 1,300 relays in the network and counting, it will be impossible to process that information without help from the software.

So, relays need to be filtered and grouped. This can be partly accomplished by giving good names and metadata to relays, but the important thing is the content that lives on a given relay, which might be analyzed using the social graph, textually, or using some other heuristic. Unfortunately, with the current culture of cross-posting for reach, relays don't differ substantially from one another. For now, filters and groups have to be user-generated, which creates a chicken-and-egg problem, because remember? we are trying to make it easy for users to navigate Nostr!
Maybe a good place to start would be to create a tool that would allow users to analyze for themselves the factors contributing to relay differentiation, as specified in this bounty. Then, those insights could be quantified and automatically integrated into a given client's implementation of groups and filters. Of course, that runs afoul of the problem of centralization.
Or, discovery could be built in to clients using crude tools like checkboxes, color codes, and modal dialogs, and as the network partitions and relays specialize due to scaling limitations users can begin to develop a gestalt for what kind of notes end up on a given relay. The naturally occurring social partitioning that would result would self-reinforce by allowing implementations to classify relay content by personalities or content central to content already hosted there.
Conclusion
This post has been far more stream-of-consciousness than usual, and for that I apologize. But I also thank you, dear reader, for helping me rubber-duck my way to profundity. Here are my take-aways (maybe yours are different):
- Multi-master content is a truly novel paradigm, and interface metaphors for surfacing it don't really exist.
- The semantics of multi-master match multi-select and checkbox list interface elements.
- Relays are not sufficiently differentiated to support intelligent filtering and grouping. Users cannot currently care about the distinctions between relays, because they don't currently exist.
- The concept of "layers" in tools for video/image/graphics editing is probably the closest thing we have to a metaphor for representing two-dimensional content in multiple dimensions. Layers correspond well to dialogs, and so a first pass at this problem might be to show a feed's content modified by relay selection in a popover dialog.
I'm sure I'm not the only one thinking about this problem, so please! Take a moment to leave a comment with your thoughts, opinions, or hallucinations.
-
 @ 45c41f21:c5446b7a
2023-04-05 14:03:47
@ 45c41f21:c5446b7a
2023-04-05 14:03:47This might be a very controversial feature to most of the people on nostr but, flycat is rolling out a new experimental feature that allows users to sign in and use nostr protocol via Metamask wallet and WalletConnect (both are toolchain from Ethereum and EVM compatible blockchains). You can try it at https://flycat.club/login

Since nostr is mostly gathered by Bitcoin folks, most people here might not have a good feeling about Ethereum or any "shitcoin". but I decided to experiment with such a new feature anyway, mainly for two reasons:
- I find this Nip-111 solution(which is how this feature works) interesting on an account-control level and couldn't help to get my hands on it
- To me, seems it doesn't do any harm to Nostr protocol and the current flycat user experience. if you hate Ethereum or any other shitcoin, you can close the window and abort reading this post now and it makes no difference on using flycat.
But the real reason I am experimenting with such a feature comes from one simple fact I believed, that is
Nostr is the future for social networks and it is how things are supposed to work and do right from the first day of the internet.
Of course, Bitcoin and the lighting network are the main motivation for building such a protocol at the first stage(which is currently where we are), but nostr is not only meant for Bitcoin people. it is for mainstream users and for people who don't even know about Bitcoin. that's the potential we saw from nostr.
With max simplicity protocol design(literally, there are only three parts of nostr: 1. public key as account id, 2. digitally sign content, and 3. relay-to-client mode), nostr is born to be the ultimate glue layer to connect to everything from centralized services like Twitter and Facebook to decentralized networks like bitcoin and lighting.
From this perspective, I believe it is worth exploring other blockchain spaces with nostr, demonstrating and telling non-bitcoin people how it feels to have a real social network binding with your crypto wallet.
How it works
This feature is done following the un-merged proposal Nip-111. If you want to know the workflow in detail, it is recommended to read the post written by the NIP authors.
Here are some simple explanations of how the Nip-111 proposal works:
since the Metamask and Ethereum blockchains use different crypto algorithms to do signings, it is impossible to use your Eth account to sign nostr stuff (unless Metamask and other Eth wallets support the Schnorr and Nip-07). But even if they did and we can, it is also not a wise choice to mix your blockchain key with the Nostr key since there are used for different scenes.
The Nip-111 solves this problem by proposing to generate a nostr sub-account (meaning a brand new key pair). The first step is using your Eth wallets to sign a fixed message to generate a fixed signature, and then take this signature, combined with the user password, to generate a new deterministic nostr private key.
To get this private key, you must be able to sign the message(prove that you are the owner of Eth wallet) and know what the password is(another proof). If the nostr key is exposed to hackers, it doesn't affect your Eth wallet account and your assets like NFTs or ERC20 tokens.
Risk and Downside
However, this approach does come with some risks and downside that you probably needs to know before using it. Even a nostr client(like flycat) doesn't store the generated private key from your Eth account, the Nip-111 required the client to hold your private key in the browser memory.
What this means is that every time you need to do something with write access on your nostr account(or export your private key), the web client will ask your Metamask or WalletConnect to sign a message to generate the private key and then use this private key to do the writing. during this process, the private key is accessible by the web client, which brings two risks:
- you need to make sure the verify the integrity and authenticity of the web client you are using. Clients like Flycat are open-source and can be checked if it takes your private key somewhere else.
- your private key is also exposable to the XSS attack during the generating process. This one is a real issue, and I don't see a clear solution besides making careful choices with which library to use and writing careful code in the web client implementation to upgrade the XSS defense. Considering there are still some people pasting their nostr private key to the web client to use the product, I will say this problem is as bad as that.
Why it is interesting
I think the Nip-111 is interesting not only because it can get Ethereum people to use nostr, but also because it is a pattern that shows how we can do account abstraction on all the other platforms. Besides Eth, all the other blockchains can create their nostr key using similar patterns. and maybe outside the blockchain space, we can also build it for centralized services to make people migrate to nostr.
Take Twitter for example, we can design a sign-in button that says sign-in with Twitter, and when people click the button, we let users post a private tweet that's only visible to himself/herself on Twitter, we take it with their password to generate a fixed nostr private key and let them start use nostr. after some time, the user might find that the nostr is great and decide to export his nostr private key and use the private key standalone instead of signing via Twitter.
Now you might think, there is a question with the above workflows: since Twitter is centralized, the private tweet is not only readable by the account owner but also by the Twitter company!
Yes, it is. That is why if the user decides to migrate to nostr seriously, he/she should consider generating a new key instead. But this is not a real problem in my opinion, because when you choose to sign in on nostr via Twitter, the implication is that you do understand the trusted scope is narrowed down to Twitter itself.
In another word, it means you choose to trust Twitter for such an operation, so if Twitter leaks your private tweet, it is not the nostr fault. The same thing also applies to Eth wallets. You trust your Metamask or WalletConnect has no backdoor to record and steal your signature.
Conclusion
I am really curious about whether Ethereum people will come to use Nostr or not and it depends on how they react to this experimental feature. If they want to taste a little bit of how nostr feels, they might choose to use it at some risk. and then make a new account when they get serious. or migrate to wallets like Alby that support Nip-07. If you have any thoughts, please comment on this post. We appreciate your feedback.
-
 @ 1bc70a01:24f6a411
2023-04-05 01:25:09
@ 1bc70a01:24f6a411
2023-04-05 01:25:09Unless you have some private projects that require secrecy, you should just organize conversations on nostr.
Smart bootstrapped founders know that one of the best ways to garner attention is by building in public.
By posting on Nostr, you are in essence building in public. This has many benefits:
- Free marketing for your project
- Recruit other designers. If they see that there are others, they are more likely to join your cause.
- Attract talent (people who are interested in the project will likely want to work on it). Find development help.
- Attract funding (even sats from plebs, bounties on your behalf, etc…)
- Help nostr grow. By getting outside the siloed communication channels, you help add activity to Nostr. When people see that it’s busy, they are more likely to participate. Nobody wants to use a dead social network (even though nostr is so much more than a social network).
How to organize on Nostr without channels or groups
A common objective is “but there is not a good client for group chat”.
Nostr IS the group chat. It's just a much larger group. All you need is a way of organizing conversations.
Enter hashtags.
Hashtags allow people to track conversations so you can see if someone is discussing #nostrdesign for example.
“But, I forget to use hashtags!”
Ok, make a SUPER simple client that automatically inserts the hashtag into the message. Hardcode if if you need to for the time being.
Clients like Snort already let you follow hashtags so it’s a matter of bookmarking it and just checking it whenever you’re online.
Don’t want a bloated client? No problem. Clone Snort, remove everything but the posting and reading functionality. Use the client only for posting and for reading that specific hashtag. Congrats, you just created your own public channel! The best part? Everyone can see it without signing up for any siloed platforms.
Act
Do it now. Close the group and let everyone know you’re using nostr from now on. No excuses, no waiting. Just do it. It may be hard and painful at first, but you'll get used to it. Who knows, it may be enough motivation to build great clients that do one thing very well. Let’s go!
-
 @ 75bf2353:e1bfa895
2023-04-10 14:26:00
@ 75bf2353:e1bfa895
2023-04-10 14:26:00RIP Final Message

I have some bad news. You will die. If your the only one who knows where your bitcoin keys are, your bitcoin dies with you. That's fine. It is a noble gesture. I know some people who plan on doing this. I suspect this is what Satoshi did, but I obviously cannot verify this.
“Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone.”--Satoshi Nakamoto
For those of us who want bitcoin to continue beyond our graves, there are dead man's switches. A dead man's switch is like a Rube Goldberg machine. Instead of opening a door like in the movie Goonies, it sends an email to your next of kin if you die. I have used a couple of these, but final message.io is my favorite since I find it the most secure. Final message.io is essentially ransomware. That's a scary ass word for most people, but have no fear. We are doing it to ourselves like Krugman thinks we owe money to ourselves.
I am certain you already know how ransomware works.
- A company gets hacked.
- Some asshole encrypts all their files using a passphrase.
- The asshole holds the passphrase hostage.
- The company pays the ransom for the passphrase or the asshole tells the company to GFY.
## How Final Message Worked:

Final Message works like a ransomware attack, but you're the hacker hacking yourself. You write your secret, say a key for a 2-of-3 multisig wallet.
- You encrypt this secret
- Give the passphrase to your wife, husband, child, etc.
- You upload your encrypted message to finalmessage.io
- You pay for a certain number of months.
- If you pay for more months final message will not send your encrypted secret message
- If you get hit by the proverbial bus, you stop paying the ransom and final message sends the encrypted message to your spouse.
Final Message Is Dead

I first wrote about final message in May of 2022. I intended to re-create it on nostr, but while doing this I noticed some sad news. Final Message is dead. They are no longer in business. That's too bad because I liked how it does not let you access your information unless you do not pay. It was the most secure dead man's switch I was aware of.
If you need to decrypt a message, you can do so by using the demo page here.
TODO: Add decryption tutorial
-
 @ 5257f6d6:c90192b1
2023-04-10 03:41:31
@ 5257f6d6:c90192b1
2023-04-10 03:41:31[3]
[4]
[5]
[6]
[7]
-
 @ 6e468422:15deee93
2023-04-04 13:23:19
@ 6e468422:15deee93
2023-04-04 13:23:19Not too long ago, I tried to paint a picture of what a vision for a value-enabled web could look like. Now, only a couple of months later, all this stuff is being built. On nostr, and on lightning. Orange and purple, a match made in heaven.
It goes without saying that I'm beyond delighted. What a time to be alive!
nostr
Here's the thing that nostr got right, and it's the same thing that Bitcoin got right: information is easy to spread and hard to stifle.[^fn-stifle] Information can be copied quickly and perfectly, which is, I believe, the underlying reason for its desire to be free.
[^fn-stifle]: That's a Satoshi quote, of course: "Bitcoin's solution is to use a peer-to-peer network to check for double-spending. In a nutshell, the network works like a distributed timestamp server, stamping the first transaction to spend a coin. It takes advantage of the nature of information being easy to spread but hard to stifle."
Easy to spread, hard to stifle. That's the base reality of the nature of information. As always, the smart thing is to work with nature, not against it.[^1] That's what's beautiful about the orange coin and the purple ostrich: both manage to work with the peculiarities of information, not against them. Both realize that information can and should be copied, as it can be perfectly read and easily spread, always. Both understand that resistance to censorship comes from writing to many places, making the cost of deletion prohibitive.
Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
Eric Hughes, A Cypherpunk's Manifesto
Nostr is quickly establishing itself as a base layer for information exchange, one that is identity-native and value-enabled. It is distinctly different from systems that came before it, just like Bitcoin is distinctly different from monies that came before it.
As of today, the focus of nostr is mostly on short text notes, the so-called "type 1" events more commonly known as tweets.[^fn-kinds] However, as you should be aware by now, nostr is way more than just an alternative to twitter. It is a new paradigm. Change the note kind from
1to30023and you don't have an alternative to Twitter, but a replacement for Medium, Substack, and all the other long-form platforms. I believe that special-purpose clients that focus on certain content types will emerge over time, just like we have seen the emergence of special-purpose platforms in the Web 2.0 era. This time, however, the network effects are cumulative, not separate. A new paradigm.Let me now turn to one such special-purpose client, a nostr-based reading app.
[^fn-kinds]: Refer to the various NIPs to discover the multitude of event kinds defined by the protocol.
Reading
I'm constantly surprised that, even though most people do read a lot online, very few people seem to have a reading workflow or reading tools.
Why that is is anyone's guess, but maybe the added value of such tools is not readily apparent. You can just read the stuff right there, on the ad-ridden, dead-ugly site, right? Why should you sign up for another site, use another app, or bind yourself to another closed platform?
That's a fair point, but the success of Medium and Substack shows that there is an appetite for clean reading and writing, as well as providing avenues for authors to get paid for their writing (and a willingness of readers to support said authors, just because).
The problem is, of course, that all of these platforms are platforms, which is to say, walled gardens that imprison readers and writers alike. Worse than that: they are fiat platforms, which means that permissionless value-flows are not only absent from their DNA, they are outright impossible.[^2]
Nostr fixes this.

The beauty of nostr is that it is not a platform. It's a protocol, which means that you don't have to sign up for it---you can create an identity yourself. You don't have to ask for permission; you just do, without having to rely on the benevolence of whatever dictator is in charge of the platform right now.
Nostr is not a platform, and yet, powerful tools and services can be built and monetized on top of it. This is good for users, good for service providers, and good for the network(s) at large. Win-win-win.
So what am I talking about, exactly? How can nostr improve everyone's reading (and writing) experience?
Allow me to paint a (rough) picture of what I have in mind. Nostr already supports private and public bookmarks, so let's start from there.
Imagine a special-purpose client that scans all your bookmarks for long-form content.[^fn-urls] Everything that you marked to be read later is shown in an orderly fashion, which is to say searchable, sortable, filterable, and displayed without distractions. Voilà, you have yourself a reading app. That's, in essence, how Pocket, Readwise, and other reading apps work. But all these apps are walled gardens without much interoperability and without direct monetization.
[^fn-urls]: In the nostr world long-form content is simply markdown as defined in NIP-23, but it could also be a link to an article or PDF, which in turn could get converted into markdown and posted as an event to a special relay.
Bitcoin fixes the direct monetization part.[^fn-v4v] Nostr fixes the interoperability part.
[^fn-v4v]: ...because Bitcoin makes V4V practical. (Paywalls are not the way.)
Alright, we got ourselves a boring reading app. Great. Now, imagine that users are able to highlight passages. These highlights, just like bookmarks now, could be private or public. When shared publicly, something interesting emerges: an overlay on existing content, a lens on the written Web. In other words: swarm highlights.
Imagine a visual overlay of all public highlights, automatically shining a light on what the swarm of readers found most useful, insightful, funny, etc.
Further, imagine the possibility of sharing these highlights as a "type 1" event with one click, automatically tagging the highlighter(s)---as well as the author, of course---so that eventual sat-flows can be split and forwarded automatically.
Voilà, you have a system that allows for value to flow back to those who provide it, be it authors, editors, curators, or readers that willingly slog through the information jungle to share and highlight the best stuff (which is a form of curation, of course).
Zaps make nostr a defacto address book[^fn-pp] of payment information, which is to say lightning addresses, as of now. Thanks to nostr wallet connect (among other developments), sending sats ~~will soon be~~ is already as frictionless as leaving a like.
[^fn-pp]: The Yellow Pages are dead, long live The Purple Pages!
Value-for-value and participatory payment flows are something that traditional reading apps desperately lack, be it Pocket, Instapaper, Readwise, or the simple reading mode that is part of every browser.
A neat side-effect of a more structured way to share passages of text is that it enables semi-structured discussions around said passages---which could be another useful overlay inside special-purpose clients, providing context and further insights.[^5]
Further, imagine the option of seamlessly switching from text-on-screen to text-to-speech, allowing the user to stream sats if desired, as Podcasting 2.0 clients already do.[^3]
Imagine user-built curations of the best articles of the week, bundled neatly for your reading pleasure, incentivized by a small value split that allows the curator to participate in the flow of sats.
You get the idea.
I'm sure that the various implementation details will be hashed out, but as I see it, 90% of the stuff is already there. Maybe we'll need another NIP or two, but I don't see a reason why this can't be built---and, more importantly: I don't see a reason why it wouldn't be sustainable for everyone involved.
Most puzzle pieces are already there, and the rest of them can probably be implemented by custom event types. From the point of view of nostr, most everything is an event: bookmarks are events, highlights are events, marking something as read is an event, and sharing an excerpt or a highlight is an event. Public actions are out in the open, private actions are encrypted, the data is not in a silo, and everyone wins. Especially the users, those who are at the edge of the network and usually lose out on the value generated.
In this case, the reading case, the users are mostly "consumers" of content. What changes from the producing perspective, the perspective of the writer?
Writing
Back to the one thing that nostr got right: information is easy to spread but hard to stifle. In addition to that, digital information can be copied perfectly, which is why it shouldn't matter where stuff is published in the first place.
Allow me to repeat this point in all caps, for emphasis: IT SHOULD NOT MATTER WHERE INFORMATION IS PUBLISHED, and, maybe even more importantly, it shouldn't matter if it is published in a hundred different places at once.[^fn-torrents]
What matters is trust and accuracy, which is to say, digital signatures and reputation. To translate this to nostr speak: because every event is signed by default, as long as you trust the person behind the signature, it doesn't matter from which relay the information is fetched.
This is already true (or mostly true) on the regular web. Whether you read the internet archive version of an article or the version that is published by an online magazine, the version on the author's website, or the version read by some guy that has read more about Bitcoin than anyone else you know[^fn-guy]---it's all the same, essentially. What matters is the information itself.
[^fn-guy]: There is only one such guy, as we all know, and it's this Guy: nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev
Practically speaking, the source of truth in a hypernostrized world is---you guessed it---an event. An event signed by the author, which allows for the information to be wrapped in a tamper-proof manner, which in turn allows the information to spread far and wide---without it being hosted in one place.
The first clients that focus on long-form content already exist, and I expect more clients to pop up over time.[^4] As mentioned before, one could easily imagine prism-like value splits seamlessly integrated into these clients, splitting zaps automatically to compensate writers, editors, proofreaders, and illustrators in a V4V fashion. Further, one could imagine various compute-intensive services built into these special-purpose clients, such as GPT Ghostwriters, or writing aids such as Grammarly and the like. All these services could be seamlessly paid for in sats, without the requirement of any sign-ups or the gathering of any user data. That's the beauty of money proper.
Plagiarism is one issue that needs to be dealt with, of course. Humans are greedy, and some humans are assholes. Neither bitcoin nor nostr fixes this. However, while plagiarism detection is not necessarily trivial, it is also not impossible, especially if most texts are published on nostr first. Nostr-based publishing tools allow for OpenTimestamp attestations thanks to NIP-03, which in turn allows for plagiarism detection based on "first seen" lookups.
That's just one way to deal with the problem, of course. In any case, I'm confident that we'll figure it out.
Value
I believe that in the open ~~attention~~ information economy we find ourselves in, value will mostly derive from effective curation, dissemination, and transmission of information, not the exclusive ownership of it.
Although it is still early days, the statistics around Podcasting 2.0 and nostr zaps clearly show that (a) people are willing to monetarily reward content they care about, and (b) the willingness to send sats increases as friction decreases.
The ingenious thing about boostagrams and zaps is that they are direct and visible, which is to say, public and interactive. They are neither regular transactions nor simple donations---they are something else entirely. An unforgable value signal, a special form of gratitude and appreciation.
Contrast that with a link to Paypal or Patreon: impersonal, slow, indirect, and friction-laden. It's the opposite of a super-charged interaction.
While today's information jungle increasingly presents itself in the form of (short) videos and (long-form) audio, I believe that we will see a renaissance of the written word, especially if we manage to move away from an economy built around attention, towards an economy built upon value and insight.
The orange future now has a purple hue, and I believe that it will be as bright as ever. We just have a lot of building to do.
Further Reading
NIPs and Resources
- Nostr Resources
- value4value.info
- nips.be
- NIP-23: Long-form content
- NIP-57: Event-specific zap markers
- NIP-47: Nostr Wallet Connect
- NIP-03: OpenTimestamps attestations for events
Originally published on dergigi.com
[^1]: Paywalls work against this nature, which is why I consider them misguided at best and incredibly retarded at worst.
[^2]: Fiat doesn't work for the value-enabled web, as fiat rails can never be open and permissionless. Digital fiat is never money. It is---and always will be---credit.
[^3]: Whether the recipient is a text-to-speech service provider or a human narrator doesn't even matter too much, sats will flow just the same.
[^4]: BlogStack and Habla being two of them.
[^5]: Use a URI as the discussion base (instead of a highlight), and you got yourself a Disqus in purple feathers!
[^fn-torrents]: That's what torrents got right, and ipfs for that matter.
-
 @ 97c70a44:ad98e322
2023-03-29 19:56:16
@ 97c70a44:ad98e322
2023-03-29 19:56:16Proof-of-work (POW) is not new to Nostr. Because the protocol is "Bitcoin-adjacent", there is a general familiarity with one of the precursor technologies to Bitcoin, Hashcash, invented by Adam Back in 1997. Some users have mined keys with a certain number of leading zeroes, or with the first few letters of their handle in order to demonstrate skin-in-the-game, and there have even been some nips merged which take advantage of proof-of-work.
This blog post won't be new to people who have given much thought to the merits of Hashcash and proof of work, but I only recently discovered the benefits of POW against micropayments in some situations, and thought would be interesting to try to articulate.
POW vs Micropayments
The basic idea behind using proof-of-work in a social protocol is that having work embedded in pubkeys (or event ids) demonstrates that the person publishing the information has spent a certain amount of processing power mining the information, and therefore has invested more into producing the content that would otherwise be evident.
There is, however, another way to prove your work: micropayments. Bitcoin, being the best money, is directly based on proof of work, and so payments made using Bitcoin are a way of borrowing the proof of work already invested in minting the coins. But any token that has recognized value will also work (with less fidelity) to store your labor for later use; that's just how money works.
It's exchange of value all the way down
The advantage of using payments instead of direct computational proof of work is because the work stored in a medium of exchange is re-usable. When you buy something, the merchant isn't simply interested in having you prove you worked for your bread, they want to prove they worked to provide you that bread when they go on to make their own purchase. This is because a purchase is a "value exchange" - there is someone providing their own work in exchange for yours.
In theory, this is always true - there really is no free lunch. This is the case even for the most negligible use cases of proof of work, for example when mining an event id to get past spam filters. Someone somewhere is checking that zero, hosting, and transmitting that content, and wouldn't it be nice if they (or the final recipient of the note) could be compensated by receiving the value that you had to expend anyway? That way, you could simultaneously boost your reach and pay people to read your content!
For this reason, I used to be against POW in any amount. Direct computational work is always wasted. That's a lot of work being destroyed instead of being used to support the people running the infrastructure. And I still think payments should be preferred wherever possible. For example, one possible alternative to proof-of-work for getting past a spam filter would be to pay relays directly, and then have those relays publish an additional proof of your payment, similar to a zap note. The relays receiving your content would be paid directly, and the proof of payment would function as proof of work for all subsequent relays (or clients) receiving the event.
Nanopayments
Of course, this only works if the price tag of publishing content is significant enough to justify the extra coordination, storage, and transmission of the payment proofs. Payments also don't make sense if there is no clear recipient, if the recipient is not yet known, or if they introduce an unacceptable amount of required trust. This is where proof-of-work shines - not as a substitute for micropayments, but as a trustless, coordination-free substitute for nanopayments, which I'll define as "any payment that costs more to process that the value it is being exchanged for". In Bitcoin-land, UTXOs that can't be included in a transaction without costing more than they yield are known as "dust".
Nonopayments never make economic sense. The most obvious being as a substitute for very small amounts of work, e.g. a single leading zero on an event id. How many fractions of a satoshi would mining one digit cost? Another nanopayment that is less obvious would be payments for very long-lived value, for example to verify a public key. In this case, even though the work isn't re-usable, it continues to have utility as long as the key is in use.
Resource Auctions
To tie all this together, let's think about what filtering spam actually is. The problem with spam is that it unproductively consumes valuable resources - both computational and social - that legitimate content should consume instead. In other words, there is a limited amount of organic engagement available for content to attract, and spam undercuts legitimate content's bid for engagement by virtue of its lower cost to produce.
The traditional solution for solving contention over a limited resource is an auction. Each interested party makes a bid, and the highest bidder wins. The problem with auctions is that they require coordination to choose a winner, and participants usually have a clear idea of what the ultimate value of the good being sold actually is. This difficulty in both assessing and facilitating a transfer of value makes the advantages of payments irrelevant, leaving the only goal of the auction to impose a cost on all actors in order to reduce spam's cost advantage to a lower multiple. So, instead of spam being thousands of times cheaper to produce than legitimate content (1 minute of your time to compose a note at $30/hr is 50 cents!), it becomes only a few times cheaper. So even though POW is an inferior way to transfer value, its trustless nature makes it the best option in this case.
Conclusion
That's not to say there aren't better ways to do moderation, just that direct payments to cover resource consumption aren't the correct solution. I personally think web-of-trust is the best baseline for eliminating spam, but it does need a complement in order to introduce newcomers to the network, or promote content to interested users. This can take the form of proof-of-work for lower-stakes cases, or payments as a way of borrowing reputation from someone already established in the network for cases where the goal is not to avoid spam, but to leverage reputation external to the social graph embedded in Nostr.
Distributed moderation and content recommendations is something I'm really interested in, so expect to see more thoughts on that topic from me in the future.
-
 @ 1bc70a01:24f6a411
2023-03-27 02:41:22
@ 1bc70a01:24f6a411
2023-03-27 02:41:22You may remember a documentary on Netflix that discussed the negative effects of social media - Social Dilemma. It sparked many discussions in various circles, but nothing came of it.
Well, today I want to talk about making social media healthier, if not for ourselves, but for our kids.
We have a once in a lifetime opportunity with Nostr to reshape social media clients from scratch. Let us not blindly copy existing social media behavior. After all, the definition of stupidity is doing the same thing and expecting different results. Let’s not be stupid and make social media just as, if not more addicting than before.
The big TLDR; is that social media addictive mechanisms harm self image in kids. At the time where they should be building confidence, the mechanics of social media make them feel insecure. I can only imagine the downstream effects into adulthood, but on society level it can’t be good.
Some organizations even exist to supposedly move this subject forward, but after reviewing their content, I see nothing substantial put forward. One such organization “Center for Human Technology” seems to say the right things but puts no effort into offering any actual solutions.
Strategies to make social media healthier
Let’s brainstorm some actual things we can do to limit social media addictiveness, reduce social influence and manipulation.
Boost self-esteem
Vanity metrics can play a positive role but the wrong kind of metric is more harmful than not. Follower count immediately comes to mind. You see people obsessing with their follower count, and even those not realizing they are obsessed are constantly comparing themselves to one another. You are probably one of those people. If you don’t believe me, go ahead and close down your account right now, and create a fresh one to start over. I’ll wait.
Still here? I thought so. Short of constantly deleting our accounts, we can do something else - not showing a follower metric at all.
Remove followers metrics
As drastic as this sounds, removing followers is a huge step forward to better mental health. We don’t need to see how many people follow us. As long as you can see who you follow, it shouldn’t matter who is following you.
This goes beyond Twitter-like apps. Subscriber counts on YouTube channels, on email lists, none of these things need to exist. The number of people you send something to should be irrelevant. Think about it - how does it impact the content of your message whether you have 100 followers or 10,000? It doesn’t.
Avoid algorithms at all costs
Algos are excellent at hijacking attention. They know what you like and keep feeding off you to keep you hooked. Let’s end this stupidity once and for all and say no to algorithms.
I also came to a realization that “algorithmic choice” is an illusion. The “best” algorithm will by definition be the winner and the most popular. Clients will implement the thing that people crave most until “better” algorithms get more users hooked on a client. Who doesn’t want that for their platform? Everyone. Attention is money. Attention is harm.
If we want to create a better future for our children, we’ll say no to algorithms. This means we have to accept that people will gravitate towards “cheaters” who do include “useful” algorithms in their clients. It also means we have to be willing to forgo larger profits.
Perhaps well-thought out policy can be introduced in the future that limits the harm of algorithms, but in the meantime we can take matters into our own hands and simply say no.
Improve happiness levels
Avoid news feeds
Thanks to nostr we can create clients that only handle news feeds, so we don’t really need to include them in social clients.
News keeps people down because negative news gets most clicks. We can avoid this whole issue just by not including news feeds in social applications. Less clickbaity headlines, less rage, more productive conversations.
If you still crave news, go ahead and use that nostr client designed specifically for news consumption.
Of course, we can’t stop people from sharing the news, but we can avoid algos that surface it, and avoid creating feeds specifically designed for news consumption.
News also consumed a lot of time and spreads misinformation. You get scenarios where neither of the arguers read the article in full and are arguing about something that’s not even reported. It’s painful to watch.
Then you have situations where the news is actually a narrative spun by some organization or individual who wants to influence social behavior. They may report correct information or completely misrepresent facts.
News is “bad news”. Just don’t build it into social clients intentionally.
Create happiness clients
One thing I have not seen any social media do is ask whether a piece of content makes you feel positive, neutral or negative.
In theory, we should be able to create clients that prioritize positive content. I know I said avoid algorithms at all costs, but if you wanted to create a happiness portal, you could cheat a little and ask people to market content as positive, neutral or negative, and then surface only the positive.
In my opinion this is not an ideal way to go about it, because you’re creating a different type of bubble, one where people ignore the reality of things. Yet, it is a possibility if we want to alter our mood by putting algos to work for us. At the very least it would be a fun experiment!
Reduce addiction / Save time
Disable notifications by default
You hear countless stories of people feeling better in their lives after disabling notifications. Why not make this the default behavior? “But, people won’t know if the app works!” Yeah.. it has to start some place. If we want change, we need to make tough decisions. If you want to be less extreme about it, you could disable most notifications by default, while not touching the “critical” ones. Personally, I don’t think any notification is critical, you should be completely in control over your attention and that any notification is a major intrusion into your consciousness.
With notifications disabled, we can regain time and attention. Society as a whole might think more clearly and be in the moment. I think it would be a huge step forward.
Delay notifications
Nothing sucks more time than notifications. That tiny red dot begging to be tapped. One solution to make notification less addicting short of turning them off is to delay them. We can purposely set a timer to show notifications in a delayed fashion rather than right away. This way people or kids don’t need to constantly check to see who replied or messaged you. Something as simple as a 3 minute notification delay may be sufficient to curb the constant checking behavior.
Delay reactions
Dopamine is fun, but constant dopamine in real time is unhealthy. Real time reactions force us to stare at our screens waiting for the next reaction.
We can lessen this addictive behavior by introducing delayed reactions to notes. Instead of reactions coming in real time, introduce a delay of 1-5 minutes. If you know that you won’t see any responses to your post for at least 5 minutes, it makes it easier to put down the phone and not have to constantly look to see who liked your note.
Improve Transparency
Once media organizations get on nostr, I think there’s a lot we can do to make them more transparent, accountable, and less manipulative.
One thing we can do is to create meta data for media accounts to indicate their funding sources. Everyone should be able to see who funds a certain organization (as discovered by anyone in the community and voted on by the community in terms of accuracy).
The idea is that someone could dig up funding sources for an organization and add them as meta notes to the account. The community can then collectively decide if this is accurate or inaccurate, giving others an idea if there is a certain bias involved.
Think about the Greenpeace ordeal currently happening. A meta note to indicate that Ripple, a “competing” cryptocurrency is funding them would add a lot of transparency to their claims. I think people would be less likely to believe the nonsense they are spewing.
Create a record of accuracy
Fueled entirely by the community, people could verify the accuracy of claims and indicate that in meta data. Other members can then review those claims and vote on them as well. With enough people involved, you could see if there is a sufficient sample size to indicate whether a media organization has been accurate or inaccurate in the past.
One thing we’d need to watch out here is bot manipulation. Said organizations could hire out malicious services to make it seem they are more accurate than they are typically. We’d have to think of some ways of preventing that.
The sheer lack of ratings on a claim should raise an eyebrow and whether something is to be believed or not.
The right to be forgotten
I know I will catch a lot of heat for this one. “The internet never forgets!” This is what the vast majority of people will say right away. That’s fine… but hear me out…
As builders and developers, we can form a consensus that social media data should be forgotten after x amount of time. Yes, anyone can screenshot it, mirror, put it on their own relay, rebroadcast it, yada yada yada… I get it. But that doesn’t mean we can’t create a consensus by which many builders, relay operators can voluntarily abide. It may not be a bulletproof solution, but it’s an effort that counts.
When we speak in the real world, unless recorded, our words are forgotten. A person should not be judged by a stupid thing they said yesterday, a week ago, a year ago. We can’t be in the right all the time - all people make mistakes and say and do stupid things. However, online, your word remains forever. Various servers cache, duplicate, at zero cost. I totally get that. Yet, we can still design an experience where that information disappears from our feeds, unless actively surfaced with some specific intent to surface it. I think this is a worthwhile effort that developers should consider today.
In cases where information should be saved for good reasons, someone will save it. Entire clients can and will exist to index everything, but that doesn’t mean every single client should surface every single note. People have a right to be wrong and to not be constantly harassed for what they said or did if they no longer feel or act that way.
Let’s have this conversation because no one else will
This article is meant to be a conversation starter. I really think we should weave it into the Nostr conferences as a crucial segment worth exploring and discussing. If we don’t do this, no one will. The world will continue to get gamified, attention hijacked and kids will continue suffering, depressed, lacking confidence and the tools needed to create a better world for their own kids. Let’s not fall sleep at the wheel and actually do something about it.
What other ideas do you have? Share the article and attach your own ideas.
-
 @ 1bc70a01:24f6a411
2023-03-25 13:52:21
@ 1bc70a01:24f6a411
2023-03-25 13:52:21In one of his earlier talks, developer and entrepreneur Rob Walling who was previously founder of drip.com said something seemingly small but profound (paraphrased):
To increase conversion rates (people sticking around to keep using your product, and ultimately paying), get people to their “aha!” moment as quickly as possible.
The “aha!” moment is where it clicks for the user exactly why this product is awesome. It's the shortest path to awesome. Once the user sees the value in the product, they are more likely to stick around.
Product designers and developers who are aware of this, know that the name of the game is providing value, and hopefully overdelivering, as quickly as possible. This means setting aside their own desires to showcase the product in its full glory, and focusing on the essentials - minimizing the number of steps required to get to the aha moment.
Design by omission becomes important. What to not include becomes equally, if not more important as what to include. So does reducing friction. The fewer, less painful steps involved in getting insane value out of a product, the better.
This concept is a great rule of thumb for every product founder. Instead of thinking “what feature should I add to make people love this product?”, founders should be thinking “what features do I absolutely need for people to love this product?” Then de-emphasize everything else.
Nostr clients are no different from a typical startup - they should be trying to figure out the “aha!” moment, and how to get the user to it as quickly as possible.
A useful exercise I often perform is to reverse the process and start at the end - the action the user needs to take to have their minds blown. Once you figure out what that action is, work backwards to the steps where they first land on the product page, or install the app, whatever that may be. The goal is to cut out as many steps in-between as possible.
I’ll demonstrate with a hypothetical, but practical example.
Let us assume we are building a music app where people can earn sats when others listen to their tracks.
Nostr has several layers and steps that most people typically go through, for example:
- Generate key pair
- Save keys warning
- Pick a username
- Import follows (perhaps)
- In some cases add relays
- Navigate to some sort of a feed, either from follows or general
- You typically need to set up your profile if you want people to take you seriously
- Have to figure out what sats are, why anyone should care? What are these play tokens?
- If care enough, find settings to connect a wallet
- Learn about wallets (now you leave the platform to do a bunch of reading), chances are you are gone for good.
- Connect a wallet, test a payment.
- Do something for someone to find your action worthy of a zap / perhaps upload a track?
- Aha moment! You can get paid easily and fast just for interacting with people.
Perhaps you’ll also have a realization that your comments are showing cross-platforms which supercharges your content distribution, but for now we don’t need to worry about this.
Of course, some of these steps may be optional, but if we are talking about someone who knows nothing about nostr, sats, zaps, key pairs, that’s 12 steps to get to some realization of what is possible.
12 steps!
The barrier to seeing value is very steep unless you already understand the benefits of decentralized social platforms, know about bitcoin and understand the possibilities.
Sadly, this is not what an average user looks like.
In fact, if you look on Nostr.band, the stats show that the number of profiles with an LN address has remained largely flat for a long time. It’s likely that these people are mostly bitcoiners who already understand the value proposition of a lightning payment.
Now, let’s work backwards and just think through which steps could potentially be eliminated. Keep in mind, we are talking about a music client.
Let us assume that the aha! moment is someone getting paid for their creative work (music). I think this is a safe assumption.
Final step: Pay bills with your creative work
This is going a bit beyond the aha moment, but we’ll roll with it.
Let’s ask some questions…
- What’s the fastest way to demonstrate that a user can collect payments for uploading tracks? How about a web client that is visible without logging in? Perhaps you can see some songs right away and notice that they are earning money? It’s not a personal aha moment, but it’s a preview.
- Can we get the user to skip signup entirely?
- Can the user upload a track as step 1?
- Can they see their local currency as a payout option?
- Can they collect payment in their local currency?
- Do they need to know what sats are? At least initially?
- Do they need to care about relays and everything that this entails?
- Do they really need to connect a wallet to get paid?
- Do they really need to follow anyone to see a feed?
- Are usernames even important to see the value in this product?
- Do they need to learn about cryptographic key pairs? How can we delay this step?
Having asked all of these questions, we can draft an ideal scenario. It may not be realistic, far from it, but at least we know what an ideal and amazing journey would look like.
- Land on a website and see that people are getting paid in your local currency for the same work you offer. Hey, maybe I should try this? 🤔
- What’s this.. a button to upload music? Ok, I have a file sitting on my drive, or have a link handy, let’s do it! Go ahead and add the track (as few steps as possible). Holy shit, I can add splits? Sounds crazy.. ok, let’s keep going.
- Now that I’ve made progress in adding some information, it seems I need to sign up to finish. Makes sense. One or two clicks, I’m in and my track is added.
- Aha moment: I go eat dinner, come back an hour later and see that I’ve just earned $5. It ain’t that much, but it didn’t take long! Turns out new tracks go into the new tab and people can stream them which goes directly to your wallet.
- Final step: I click a button to cash out, in my local currency. The funds arrive in my bank account. Now I can pay my bills.
It may not be a feasible flow, or even a desirable one, but at least we can see that an amazing journey might only take 3-4 steps. It is still using the old money rails for some parts of the app, but the artist can get paid for their work fast and can come to a realization that there might be something to this.
We don’t need to create this specific journey and outcome, but we can use it as a baseline.
As a technical founder / developer you will have a better idea of what is possible. Perhaps new services need to be created to get to our end state? This exercise gives us a lot to think about.
In our example, we might be able to:
- Let users preview the product without signing up
- Have built-in wallets that require no additional setup (with the ability to customize your experience later in the options)
- Display earrings in local currencies while slowly introducing sats, zaps (surely there is an API that can handle sats to local currency conversion in real time? If not, maybe it has to be created?)
- Allow users to cash out into local currency. Why do we need to keep them in sats? Why not let them make their own option? If this is not possible to do - Why? What service needs to exist to allow lightning-enabled apps to tap into easy, plug and play fiat conversion?
- Let users discover relays later on instead of right away to keep them from being overwhelmed.
Even if some of these things are not technically feasible, at least we are now thinking about the flow from a user’s perspective and empathize with them. We start thinking about their time, their needs, their existing frustrations and how we might be able to brighten their day.
This user-centric approach helps founders skip the fluffy parts and focus on the guts that truly matter.
New founders specifically tend to enjoy adding features, thinking the next one will do the trick, only to be disappointed.
I encourage Nostr client developers to start thinking about their users as customers who are looking to solve their own problems.
- How might you make that journey as effortless as possible?
- What is your customer truly seeking? Is it distribution? Is it attention? Is it money?
- Are you delivering it in as few steps as possible?
- Can the “customer” take a more familiar path to get to the same decentralized destination that we all love?
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ 3bf0c63f:aefa459d
2023-03-04 11:41:00
@ 3bf0c63f:aefa459d
2023-03-04 11:41:00The current plan consists in giving out money not for specific tasks, but for general open-source efforts that seem to be worth it according to my own completely arbitrary and subjective judgment and hand out microbounties to these.
The idea is that people will give a little more priority working on Nostr things that they already wanted to because they have a chance of getting a microbounty for it while if they work on another side project like a rollercoaster building game they don’t have that chance (although rollercoaster building games have other advantages).
If you have any micro project idea in your head (or half-done) message fiatjaf at https://t.me/fiatjaf and he may decide to preassign a bounty to it conditional to your completion of that same project in case he finds that to be worth pursuing. The plan is that this will work because you are already interested in the thing and not just doing it for the money, as it is the case with normal bounties.
Here is a list of themes that I currently think are worth exploring more, to serve as an inspiration: Themes
- Microapps (Nostr apps that do only one thing and do it well), for example:
- An app for just publishing things and reading replies
- An app for just managing your contacts
- An app for just reading threads
- Native apps instead of web
- Pull requests that add these nice features to existing clients instead of making a new client
- New use cases besides “social” but that still deliver interoperability and standardized behavior between clients
- Bonus points if these new use cases can be interacted with with from the “social” clients in some way, e.g.
- if you do webpage comments on Nostr you can see and interact with these from social clients as normal posts
- If you do wikipedia on Nostr you can comment on these articles from social clients
- Usable tricks to secure keys that can still work in practice, some stupid examples:
- A client (or addition to existing clients) that stores encrypted Nostr on the user’s Google Drive and the decryption key for that on a custom server
- An integrated multisig server that signs stuff upon request
- Relay discovery
- Because we should not assume everybody will always be in all relays or that clients will talk to all relays all the time forever
- Making existing things
- Prettier
- Faster
- Non-public relays use cases
Bounties given
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ d0debf9f:ea4b466c
2023-03-01 19:10:19
@ d0debf9f:ea4b466c
2023-03-01 19:10:19Why wireguard?
If you are already sold on why you need this, skip to the next section.
A motivational story
The year is 2025. You're at the small coffeshop you found on btcmap and want to pay for your morning double expresso.
A LN invoice flashes before your sleepy eyes, you pull out your phone and try to open your Zeus wallet connected to your sovereign self-custodial LN node running in your basement.
You wait for Zeus to load. And you wait. And you wait. And you wait some more. The barista gets impatient, there is a line of NPCs behind you rushing to get to their fiat mines.
Finally you curse, pay with your slave VISA CBDC card and uninstall Zeus as you walk out.
The Issue
You used Tor to connect to your node. Tor was being DDOSed by some state-level actors.
You're using Tor because either it was the easiest thing to setup, or it was just the default in your node distribution.
Have you stopped to wonder if it really makes sense to use an anonymity network designed to be censorship resistant just to connect to your own home server?
You obviously don't want to expose your node to the public internet (which would expose what you are using as well as make you vulnerable to attacks).
The Solution
The best solution (as far as I'm aware of) is to connect to your home node using an encrypted VPN point-to-point tunnel using something called WireGuard.
The only information you leak to potential traffic sniffers is encrypted UDP packets (which are already hard to sniff) to your home IP address, which is pretty harmless information.
The (not ideal) Alternative
Many people find Wireguard hard to setup on its own (don't worry, that is why I wrote this guide) and prefer a more seamless corporate solution based on Wireguard called Tailscale.
Tailscale has 2 major drawbacks:
- It's an additional third party that knows every encrypted packet you send over it as well as all your public IPs.
- It's permissioned and requires setting up an account, not very sovereign
Setup
Requirements
- Access to your home router admin page: if your node is behind a NAT (usually that is the case when it's behind a home router), you're going to need to forward a port to your node LAN IP. If you don't know how to do this, you can try to follow the guide for your router model at portforward.com.
- Either a fixed home public IP address, or a domain name that points to your dynamic home IP address. Even if you don't have this, you can still follow the guide and manually update your home IP in the configuration file.
- Shell root access in your node.
Node setup
Gather network information
Find your node's LAN IP address:
bash $ ip -human --brief address show lo UNKNOWN 127.0.0.1/8 ::1/128 eth0 UP 192.168.1.2/24 metric 1024In this case, the your node's LAN IP is
192.168.1.2.Find your home public IP address:
bash $ curl ipecho.net/plain### Install wireguard tools
The wireguard module is actually built into any modern linux kernel by default, what we actually need to install is the tooling to generate valid wireguard cryptographic keys.
For debian/ubuntu based distros:
bash $ sudo apt install wireguardFor other distros, check wireguard.com/install.Generate keys
You manually need to generate 1 keypair for each device (called peer) that will use your wireguard VPN (including your home node).
To generate a keypair for your node (let's call it
node):bash $ wg genkey | (umask 0077 && tee node.key) | wg pubkey > node.pubThis will create 2 files:
node.keyandnode.pubcontaining your private and public keys, respectively. Keep these files safe and after being done configuring wireguard you can even delete them.Create extra keypairs for your other devices, e.g.: * Your phone:
bash $ wg genkey | (umask 0077 && tee phone.key) | wg pubkey > phone.pub* Your laptop:bash $ wg genkey | (umask 0077 && tee laptop.key) | wg pubkey > laptop.pubCreate as many as you wish.Configure the tunnel
Using a text editor create and edit the file
/etc/wireguard/mytunnelname.confwith the content:``` [Interface] Address = 10.0.0.1/24 ListenPort = 50000 PrivateKey =
[Peer] PublicKey =
AllowedIPs = 10.0.0.2/32 [Peer] PublicKey =
AllowedIPs = 10.0.0.3/32 ``` Subsitute
*_KEYwith the relevant keys found in the files you generated earlier (which you can see the contents usingcat node.keyfor instance).Generate configurations for the other peers
For your phone/laptop, create a files (can be anywhere, does not matter) with the contents: *
phone.conf``` [Interface] Address = 10.0.0.2/24 PrivateKey =[Peer] PublicKey =
AllowedIPs = 10.0.0.1/32 Endpoint = :50000 ``` laptop.conf:
``` [Interface] Address = 10.0.0.3/24 PrivateKey =
[Peer] PublicKey =
AllowedIPs = 10.0.0.1/32 Endpoint = :50000 ``` Now you need to either transfer these files to their respective devices (how you do it is your business) or generate an easy to use QR code to use to configure your phone.
Optional: generate QR code for the phone configuration
Install
qrencodebash sudo apt install qrencodePrint the QR code on your terminal:
bash $ qrencode -r phone.conf -t ansiutf8Or save it (and transfer) as png image:
bash $ qrencode -r phone.conf -o phone.pngRun wireguard the wireguard tunnel
bash $ sudo systemctl enable --now wg-quick@mytunnelname.serviceNow when you do
ip -human --brief address showyou should see an extra interface:lo UNKNOWN 127.0.0.1/8 ::1/128 eth0 UP 192.168.1.2/24 metric 1024 mytunnelname UNKNOWN 10.0.0.1/24Open UDP wireguard port
If your node has a firewall, we need to open our chosen UDP port (50000).
If using
ufw:bash $ sudo ufw allow 50000/udpif just using iptables:
bash $ sudo iptables -A UDP -p udp -m udp --dport 50000 -j ACCEPTHome router setup
Forward port 50000 UDP to your node's LAN IP. If you don't know how to do this, you can try to follow the guide for your router model at portforward.com.
Phone setup
1- Install the wireguard app, you can find links in wireguard.com/install.
2 - Open the app 3 - Click on the
+button 4 - Choose if you want to import thephone.confconfiguration file, the your generated QR or input everything manually. 5 - Activate the tunnel by tapping the switchYou should have a working tunnel between your node and your phone. You can try pinging your phone wireguard IP (
10.0.0.2) from your node's terminal (ping 10.0.0.2) to check that it is working.Now on every app you connect to your node (e.g. Zeus), instead of using the onion address, you can just use your node's wireguard IP (
10.0.0.1).Laptop setup
If it's a linux laptop: place (and rename)
laptop.confto/etc/wireguard/mytunnelname.confand do:bash $ sudo systemctl enable --now wg-quick@mytunnelname.servicePing your node wireguard IP
ping 10.0.0.1to make sure it's working.Now you can use that IP instead of the onion address to connect to your node (e.g. in Sparrow).
Help
If you have questions feel free to contact me (NIP-05: sommerfeld@strisemarx.com).
-
 @ 85c32138:34778f3d
2023-04-09 18:19:23
@ 85c32138:34778f3d
2023-04-09 18:19:23Among all the chaos and disturbing regulation around social media platforms, Nostr's simple design feels fitting for our global context. Allow me to share some thoughts with you.
Just as TikTok is about to be banned and Twitter is becoming unusable, a lot of us are exhausted and confused about social media. Needless to say, we’re experiencing a vibe shift and the drawbacks of centralisation and algorithmically dominated feeds are becoming clear.
Personally, I have low mental bandwidth and didn’t see why I should spend time learning about alternatives like Mastodon or Nostr. It took multiple nudges for me to open up and realise that this future is in our hands.
I want to own my data. I want a simple, intuitive new stream for social interactions. I want a fundamentally free cyberspace. One solution won’t fix everything or be perfect, but I’d rather try. Each click is an energetic vote on how we choose to collectively coordinate.
So I went clicking around Nostr and here’s what I want to share with you:
Your data is yours
- You’re equipped with a public and private key pair, it follows you everywhere so you don’t have to lose followers or content between platforms
- Doesn’t matter which platform your friends are using, if you share your public keys then you can still follow each other (no need to get everyone onto your specific bandwagon - yeehaw)
- You don’t sign up for a new account each time you use a new app (it’s the same public key), goodbye to aaall the email and password logins you’ve collected over the years
Censorship resistant
- Instead of relying on one server to hold your data (like what we have with Twitter for example), you choose a number of “relays” run by people around the world to store your data and share messages
- Each relay gets to choose how to store and share data, and you choose the relays you connect to. We’re not limited by a host’s rules and ideologies, and avoid ending up with a collection of silos
- Relays interact with clients (which provides the interface you see), and that checks whether your data was actually produced from the public key you hold. Clients display your posts and can’t control the data or your identity
- Remember, you can sign into any Nostr client with a single pair of keys; no registration required
It’s simple to build on
- Nostr itself is a protocol, not an app or service that you sign up for. It’s an open standard which anyone can build on, much like how we build our sites to go on HTTP or TCP-IP
- It’s a message standard, based on simple and flexible “event” objects which are passed around as plain JSON. It uses standard public-key cryptography for keys and signing
- This makes it easy to run relays and build clients, ensuring the ability for the protocol to extend and adapt/evolve over time
- It also works as a peer to peer network where you don’t need to know the IP address of your peers or be online at the same time
Belongs to the community
- Anyone can build and anyone can transact (already has effortless Bitcoin micropayments for content, without ads or subscriptions)
- Potential for emergent properties to arise, since people running relays can experiment with different mechanisms to store data and send messages
- The people getting involved feel like a community reminiscent of older internet days, and there’s a sense of commonality and lessons learned from the past decades
- Individual sensemaking around this could be really exciting for developments beyond just a “social platform”
- The community is already responding to major gaps in privacy (check out this first run through of Nostr through the Nym mixnet — for some network privacy lovin’)
Tidbits for getting started
Sharing some gems I found helpful (this by no means is a solid how-to guide): - How To Use NOSTR - A Decentralized Censorship Resistant Social Layer
-
- Don’t issue your key pairs within the browser or app directly, because it can potentially be leaked. I wasn’t aware of this but luckily followed the video’s tip on using the Alby plugin and have been pretty happy with it. For best practice there is a particular command you can run while generating key pairs (I’m not your person for this).
-
- Also, the video suggests astral.ninja, I’ve jumped to iris.to since it’s less glitchy. This is the fun part because things will be changing and you can switch as much as you like; so be open to different clients and know that people are doing their best to build right now
-
Nostr w/ Gsovereignty | FIAT LUX Podcast #4 (shoutout to Yves Edwards)
-
- I really enjoyed this interview actually, it’s genuine and gives you some sense of the ideas behind and around Nostr
If you made it all the way here then congrats!
Say hi if you choose to follow me: (tech.energy.love@pnproxy.org) or nostr pub key: npub1shpjzwzudkj0hfcn0eeypn9haqr4mzwp4vlycn5wkp6audrh3u7sd9dm2g
Let’s play: I’ll gift you a special Nostr badge if you quote a line from my poem ;) <3
It’s up to us to shape a healthier internet
We’re stepping into a new era and it’s time to learn and make do with new patterns. You and I are emergently figuring this out, let’s embrace collective intelligence and explore what a better future could look like (who knows, it might even be surprisingly simple).
Special shoutout to the No Trust Verify crew and Pineapple Proxy for the help <3
Ok I want to share one more last thing: this recent talk between privacy practitioners on the front lines, I really enjoyed this and may write about it in a future post. It’s not related to Nostr but I’m putting it in anyway.
Lots of love
xxx
-
 @ de7ecd1e:55efd645
2023-02-20 16:41:11
@ de7ecd1e:55efd645
2023-02-20 16:41:11Web 1.0
The web was proposed in 1989, by Tim Berners-Lee but had been conceived decades earlier. The proposal was not read for a full year, and, after that, allowed as a side-project with the infamous words, "vague, but exciting".
The first version added hyperlinks to existing browser technology. Bundled together were:
- HTTP and the first server
- the first web browser, which was also an editor
- HTML which was based on SGML
Importantly a new type of variable was created, the hyperlink, originally the UDI (Universal Document Identifier). This was later standardized as the URI, with an intent to go beyond just documents to describe Things as well.
Web 1.0 was in competition with Gopher at the time, and Gopher was winning. However, there was a rumour that Gopher might charge some royalties on their protocol, say, to enterprise customers, and with that, the people flocked to the web and made it take off as a grass roots movement.
HTTP was a formal specification in 1997 a full 8 years later, and the architecture of the world wide web was published in 2004, 7 years after that.

Web 2.0
As the web grew as a system, businesses started to spring up around it. A product was a browser called Mosaic, made by Marc Andreessen. While Mosiac added multi media, it also removed the editing functionality in the original browser, a tragic loss.
Without editing built in, the web needed central servers to allow user generated content. These servers grew in time to become giants. A technology added on this was AJAX, which allowed browsers to interact with servers asynchronously to generate richer applications and realtime updates.
This system of greater usability was branded "Web 2.0", popularized by Tim O'Reilly. It was not a formal upgrade of the web, so considered somewhat cheeky by some, the inventor of the web calling the term "jargon". Jargon it is, but the term stuck, and the web did go to a next level, adding important things like search, commerce, and the social web.
With the increased centralization of servers came other problems, such as pervasive tracking, monopolistic effects, censorship and information engineering.
Web 3.0
Web 3.0 was a term coined by Tim Berners-Lee, to represent a radical new idea, which allowed both data and documents to be denoted, on the web. This is of course a radical old idea which was in the web 1.0 proposal, a so-called "semantic web", but with the name 2.0 already co-opted, Tim decided to call it web 3.0.
The was formalized in the RDF (resource definition framework) which made extensive use of XML. Later it was renamed Linked Data, sometimes called the web of data. This has been popularized by schema.org which allows commonly used terms to be put in web pages, allowing easier search, and link previews.
Berners-Lee continues to work on a project called Solid, which stands for "Social Linked Data" (a term I coined in 2012), with the aim of making Linked Data more social, and benefiting from same usability upgrades and lessons learned from "Web 2.0"
The full web 3.0 stack is standardized at the w3c, though has grown over time, leading to a somewhat complex system, and steep learning curve for new developers.
A note on the deceptively named web3. This was an attempt by VCs (including Marc Andreessen again) and others to co-opt the web brand. The main aim was an affinity scam to sell tokens to the unsuspecting public. The issue is that it is not the web at all. In this case Berners-Lee did speak out against it:
https://www.cnbc.com/2022/11/04/web-inventor-tim-berners-lee-wants-us-to-ignore-web3.html
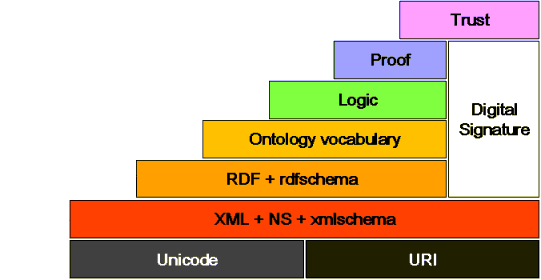
Towards Web 4.0
The first 3 "versions" of the web work well enough. However, the web itself is ephemeral. The average age of a link is 100 days. And there is no good mechanism at web scale to ensure the integrity or version control of information on the web. A possible approach to the next version of the web would be towards a Temporal Web. I wrote a post about this here:
https://lists.w3.org/Archives/Public/public-rww/2021May/0006.html
A significant innovation in recent times is that of Bitcoin, which is a web scale timestamp server. It orders records (blocks) in time, robustly and securely, creating a permanent record. It also, for the first time in history, creates a global currency that is strongly resistant to money printing by fiat.
These two systems working together could create a robust temporal backbone to the web, allowing commerce without rent seeking, and creating whole new business models that are more decentralized, and act in the interests of the users, competing with each other with better services, rather than, serving privacy intrusive monopolies.

Web 5.0
What web 5.0 will look like, nobody knows. However the aim of the original proposal was to have both humans and machines working together. A semantic web was needed for that, to make it easier for machines to participate. Although machines are often censored or blocked on the large platforms, or, even worse, act with perverse incentives to spam users with adverts, noisy information and propaganda.
One guess about web 5.0 could be a web of machine agents, virtual assistants, working together with people to act in the interests of people. This builds on a Temporal web as machines can then evolve over time and the best ones will emerge, in an evolutionary way. Artificial Intelligence can further be folded into the system to optimize its utility to humanity.
A note on web5: This was an earnest attempt to push back on web3 and remove some of the more corrupt aspects, such as copious use of money printing. It has some alignment with the web, but it is not web 5.0, however, I hope it produces something interesting. Never fight an affinity scam with an affinity scam.
IMHO a promising project in this area is Nostr. It reuses the websockets standard to relay information from one user to another which is signed. Importantly, it is grass roots, as the original web was, has already integrated fast cheap payments, with bitcoin and the lightning network in many apps. Unlike the semantic web, it has a very easy developer experience which has seen high uptake from developers. Additionally, the tagging system allows integration with time chains paving a cow path for a temporal web, and then perhaps humans and agents co existing for mutual benefit. We are still early, but time will tell how the web evolves.

Opinions are the views of the author
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ c753997e:9fe20adc
2023-04-09 18:16:56
@ c753997e:9fe20adc
2023-04-09 18:16:56SOCIETY 10 April 2023 By RUSSELL MCLENDON
Loyalty may be a virtue, but it can be a vulnerability, too.
Although managers tend to value employees perceived as loyal, for example, a new study shows they also tend to exploit loyal workers when assigning unpaid work or extra tasks.
These managers are not necessarily nefarious, the researchers note. Some may be oblivious, failing to grasp the ethical results of their decisions.
Yet, that's little comfort for dedicated workers, left with excessive workloads as the apparent price of their loyalty.
"Companies want loyal workers, and there is a ton of research showing that loyal workers provide all sorts of positive benefits to companies," says lead author Matthew Stanley, a postdoctoral researcher at Duke University's Fuqua School of Business in the US.
"But it seems like managers are apt to target them for exploitative practices," he states.
Stanley and his colleagues recruited close to 1,400 managers on the internet to participate in the study, in which the managers were presented with various scenarios starring a fictional 29-year-old employee named John.
John works for a company that's trying to cut costs, the managers were told. To that end, the managers rated their willingness to assign John extra hours and duties without extra pay.
They consistently gave John more work if he had a reputation for loyalty, the study found, regardless of how else researchers framed the scenario.
After managers read recommendation letters about John, those highlighting his loyalty apparently raised their willingness to assign him unpaid labor, the researchers found.
Different letters praising John for other positive traits, like honesty or fairness, didn't have the same effect, suggesting it was specifically loyalty that made managers more comfortable with giving the work to him.
Furthermore, John accepting that work could further reinforce managers' treatment of him, the study found. When managers read descriptions of John as open to extra hours and duties, they rated him as more loyal than alternate Johns with reputations for declining optional extra work.
"It's a vicious cycle," Stanley says. "Loyal workers tend to get picked out for exploitation. And then when they do something that's exploitative, they end up getting a boost in their reputation as a loyal worker, making them more likely to get picked out in the future."
Some cases of exploitation are more obvious than others, the researchers acknowledge, and it could be argued that optional work isn't exploitative if managers merely ask workers to do it, rather than demanding it.
But given the power dynamic between employees and managers, who may control access to vital resources like pay or health insurance for their workers, previous research suggests workers often feel like they can't safely decline requests to take on extra work without pay.
For their part, managers seem to perceive this as normal, the study found, with extra work naturally going to more loyal employees as a function of their loyalty.
Some of this could be less malevolent than it sounds, the researchers note. While it wouldn't excuse mistreatment, managers' tendency to exploit loyal workers could be at least partly a result of "ethical blindness," or ignorance about the unfairness of their behavior.
"Most people want to be good," Stanley says. "Yet they transgress with surprising frequency in their everyday lives. A lot of it is due to ethical blindness, where people don't see how what they're doing is inconsistent with whatever principles or values they tend to profess."
In that case, one way to reduce exploitation might be to raise awareness of this phenomenon among managers, the researchers suggest, to help them anticipate their ethical blind spots.
The researchers also caution that loyalty isn't necessarily negative, and workers shouldn't always avoid going beyond the call of duty.
"I don't want to suggest that the take-away of the paper is to not be loyal to anybody because it just leads to disaster," Stanley says.
"We value people who are loyal. We think about them in positive terms. They get awarded often. It's not just the negative side. It's really tricky and complex."
The study was published in the Journal of Experimental Social Psychology.
-
 @ 45c41f21:c5446b7a
2023-04-09 12:04:56
@ 45c41f21:c5446b7a
2023-04-09 12:04:56flycat now supports rendering the metadata for the nip-23 long-form articles on the server side, what this mean is that you should be able to share an informative link(with the correct title and description etc) for your article. for example, since flycat also render such metadata with your links on short notes (event 1), when you share a flycat article link in your short notes on flycat, you can see it with a beautiful preview like the following:

because I don't want flycat to be a property software, I don't want to introduce a database(which makes it harder to deploy and host your own flycat instance) in order to do that. so right now we use a very bad method to achieve this, but I think it will be alright since we will make it better after setting up our own relay(instead of a private database, which means an interoperable way to do things on nostr) or doing some code refactoring.
-
 @ fe9edd5d:f158913b
2023-04-09 09:07:11
@ fe9edd5d:f158913b
2023-04-09 09:07:11[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
[85]
[86]
[87]
[88]
[89]
[90]
[91]
[92]
[93]
[94]
[95]
[96]
[97]
[98]
[99]
[100]
[101]
[102]
[103]
[104]
[105]
[106]
[107]
[108]
[109]
[110]
[111]
[112]
[113]
[114]
-
 @ a6f97691:f1adbb41
2023-04-09 05:47:07
@ a6f97691:f1adbb41
2023-04-09 05:47:07Just tuning my publication setup...
-
 @ a6f97691:f1adbb41
2023-04-09 03:40:22
@ a6f97691:f1adbb41
2023-04-09 03:40:22April 8th 2023
Bitcoin is currently trading at around $28,000, up 2% on the day. The cryptocurrency has been on a steady upward trend since the beginning of the year, and is now up more than 20% year-to-date.
The recent rally in Bitcoin has been driven by a number of factors, including increased institutional adoption, the launch of new Bitcoin-related products and services, and positive regulatory developments.
Institutional adoption of Bitcoin has been a major driver of the recent rally. In recent months, a number of major companies have announced that they are investing in Bitcoin, including Tesla, MicroStrategy, and Square. These investments have helped to legitimize Bitcoin and attract more investors to the cryptocurrency.
The launch of new Bitcoin-related products and services has also contributed to the recent rally. In recent months, a number of new Bitcoin-related products and services have been launched, including Bitcoin futures ETFs, Bitcoin-backed loans, and Bitcoin-powered point-of-sale terminals. These new products and services have made it easier for people to buy, sell, and use Bitcoin, which has helped to increase demand for the cryptocurrency.
Positive regulatory developments have also been a factor in the recent rally. In recent months, a number of countries have taken steps to regulate Bitcoin and other cryptocurrencies. These regulatory developments have helped to legitimize Bitcoin and make it more attractive to investors.
The recent rally in Bitcoin has been impressive, and it is likely that the cryptocurrency will continue to attract attention from investors in the coming months. If Bitcoin can continue to gain traction with institutional investors and regulators, it could reach new all-time highs in the near future.
However, there are also some risks that could weigh on Bitcoin in the near future. These risks include a potential global recession, increased regulation of cryptocurrencies, and competition from other cryptocurrencies.
Overall, the outlook for Bitcoin is positive. The cryptocurrency has been on a steady upward trend since the beginning of the year, and is now up more than 20% year-to-date. The recent rally has been driven by a number of factors, including increased institutional adoption, the launch of new Bitcoin-related products and services, and positive regulatory developments. However, there are also some risks that could weigh on Bitcoin in the near future. These risks include a potential global recession, increased regulation of cryptocurrencies, and competition from other cryptocurrencies.
-
 @ be318ab6:dd25a806
2023-04-09 02:55:48
@ be318ab6:dd25a806
2023-04-09 02:55:48Howdy y'all,
This is the Ramble #001
I was gifted extra spare time (layoffs), and I'm excited to put it into learning about some of the new exciting things swirling around us at an ever-accelerating speed & also about the good old ever-useful manual skills, which are disappearing almost at the same rate.
The focus will be on anti-fragility tools and skills. I'll be touching on the the topics of Nostr, AI, Bitcoin, Privacy and self-sufficiency skills like woodworking or food production. I'll include any building just for the sake of it (I get more value myself and motivation to do more of it if I can show off something tangible, I guess). It's not gonna be the most frontier-breaking r0ckstar knowledge, but it will humbly keep moving forward one step at the time along with my selfish pursuit of improving my knowledge and skills along these vectors. I also won't avoid some rants about the insane corruption in our Money and all the downstream problems it brings.
Why?
1. Why having a blog? * I want to practice my writing. Not to challenge the AI, but just to better remember the learnings, and to clarify & structure my thoughts. * The public record forces accountability on me. I want to commit to a habit of writing a few posts per week.
2. Why it's on Nostr? * When dozens of the smartest and most honest individuals I respect flock to this like a bunch of crazy birds, it's something I don't want to miss out on, and I want to get intimately familiar with the tech. * It's an uncensorable protocol that allows you to own your data and can re-architect many broken things on the current web. * Easy for me to push my tip jar in y'alls faces and see if anyone gets any real value out of this * And, I just wanted to play with it. Some clients still might be buggy, but the speed of development and improvements is lightning miles away from anything I've seen before.
I'll probably write some intro to NOSTR next time around; but in the meantime Gigi will help you out at nostr-resources.com
3. Why including the offline skills and tools? * Humans are not meant to stare into screens all day. * I see there's one of the most competitive edges for the next 10 years.
And, that's about it. I'm really excited about days and weeks, and will have some fun. If you have read all down here, thank you and PV to you!
PS.

Resources/Inspiration for this issue: * Marty's Bent - duh! * BloggingBitcoin - How To Start A Blog Today
-
 @ b3b1d580:27db0aa8
2023-04-08 20:44:50
@ b3b1d580:27db0aa8
2023-04-08 20:44:50Sell them all. Special offer until the end of the week (Sunday 9/4/2023), you get 2100 Sats instead of the usual 210 sats in Plebbin-Credit!
Libby asked the plebs on twitter and nostr to sell their chairs on Plebbin and it has already started a trend!

How do I get in on this? * Sign up at plebbin https://loveisbitcoin.com/plebbin * Get 2100 sats, 210 if you’re too late. * Take photo of chair you want to get rid of. * List chair on plebbin, ask for sats. * Comment with your chair’s photo on https://twitter.com/LoveIsBitcoin21/status/1643897779251470337?s=20 for the culture. * Then start referring other plebs to do the same with your own link and you might win some prizes! Read about them here https://plebbin.com/blog/article/plebrefcontest-b3
What are you waiting for? Stack harder. https://loveisbitcoin.com/plebbin
-
 @ 46fcbe30:6bd8ce4d
2023-04-08 19:48:48
@ 46fcbe30:6bd8ce4d
2023-04-08 19:48:48NIP-27
Text Note References
draftoptionalauthor:arthurfrancaauthor:hodlbodauthor:fiatjafThis document standardizes the treatment given by clients of inline references of other events and profiles inside the
.contentof any event that has readable text in its.content(such as kinds 1 and 30023).When creating an event, clients should include mentions to other profiles and to other events in the middle of the
.contentusing NIP-21 codes, such asnostr:nprofile1qqsw3dy8cpu...6x2argwghx6egsqstvg.Including NIP-10-style tags (
["e", <hex-id>, <relay-url>, <marker>]) for each reference is optional, clients should do it whenever they want the profile being mentioned to be notified of the mention, or when they want the referenced event to recognize their mention as a reply.A reader client that receives an event with such
nostr:...mentions in its.contentcan do any desired context augmentation (for example, linking to the profile or showing a preview of the mentioned event contents) it wants in the process. If turning such mentions into links, they could become internal links, NIP-21 links or direct links to web clients that will handle these references.
Example of a profile mention process
Suppose Bob is writing a note in a client that has search-and-autocomplete functionality for users that is triggered when they write the character
@.As Bob types
"hello @mat"the client will prompt him to autocomplete with mattn's profile, showing a picture and name.Bob presses "enter" and now he sees his typed note as
"hello @mattn",@mattnis highlighted, indicating that it is a mention. Internally, however, the event looks like this:json { "content": "hello nostr:nprofile1qqszclxx9f5haga8sfjjrulaxncvkfekj097t6f3pu65f86rvg49ehqj6f9dh", "created_at": 1679790774, "id": "f39e9b451a73d62abc5016cffdd294b1a904e2f34536a208874fe5e22bbd47cf", "kind": 1, "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "sig": "f8c8bab1b90cc3d2ae1ad999e6af8af449ad8bb4edf64807386493163e29162b5852a796a8f474d6b1001cddbaac0de4392838574f5366f03cc94cf5dfb43f4d", "tags": [ [ "p", "2c7cc62a697ea3a7826521f3fd34f0cb273693cbe5e9310f35449f43622a5cdc" ] ] }(Alternatively, the mention could have been a
nostr:npub1...URL.)After Bob publishes this event and Carol sees it, her client will initially display the
.contentas it is, but later it will parse the.contentand see that there is anostr:URL in there, decode it, extract the public key from it (and possibly relay hints), fetch that profile from its internal database or relays, then replace the full URL with the name@mattn, with a link to the internal page view for that profile.Verbose and probably unnecessary considerations
- The example above was very concrete, but it doesn't mean all clients have to implement the same flow. There could be clients that do not support autocomplete at all, so they just allow users to paste raw NIP-19 codes into the body of text, then prefix these with
nostr:before publishing the event. - The flow for referencing other events is similar: a user could paste a
note1...ornevent1...code and the client will turn that into anostr:note1...ornostr:nevent1...URL. Then upon reading such references the client may show the referenced note in a preview box or something like that -- or nothing at all. - Other display procedures can be employed: for example, if a client that is designed for dealing with only
kind:1text notes sees, for example, akind:30023nostr:naddr1...URL reference in the.content, it can, for example, decide to turn that into a link to some hardcoded webapp capable of displaying such events. - Clients may give the user the option to include or not include tags for mentioned events or profiles. If someone wants to mention
mattnwithout notifying them, but still have a nice augmentable/clickable link to their profile inside their note, they can instruct their client to not create a["p", ...]tag for that specific mention. - In the same way, if someone wants to reference another note but their reference is not meant to show up along other replies to that same note, their client can choose to not include a corresponding
["e", ...]tag for any givennostr:nevent1...URL inside.content. Clients may decide to expose these advanced functionalities to users or be more opinionated about things.
- The example above was very concrete, but it doesn't mean all clients have to implement the same flow. There could be clients that do not support autocomplete at all, so they just allow users to paste raw NIP-19 codes into the body of text, then prefix these with
-
 @ b3b1d580:27db0aa8
2023-04-08 19:35:13
@ b3b1d580:27db0aa8
2023-04-08 19:35:13I’ve always ignored Ledger until I used one to demonstrate how to use hardware wallets to my Bitcoin Workshop in Athens.
The Ledger is one of the easiest hardware wallets to use. The wizard to set it up amazed me to be honest, it was educational, perfectly made for a newbie, taking you step by step through the whole process.
There even was a test to make sure you understood what you were doing while securing your keys.
Now for a limited time, Ledger gives you up to $30 in BTC when you buy your device. It’s already affordable enough, this is a no-brainer to be honest.
If you don’t have a hardware wallet to secure your keys, get this now.
Even Snoop Dogg has one. https://loveisbitcoin.com/snoop-dogg-holds-his-own-bitcoin-keys-do-you/
Not your keys, not your coins. Buy a ledger and withdraw your sats from the exchange, it’s very easy to do. https://loveisbitcoin.com/ledger
 Offer Starts Now, Valid Until April 18th* and while stocks last.
Offer Starts Now, Valid Until April 18th* and while stocks last.Order your ledger wallet here. https://loveisbitcoin.com/ledger
-
 @ 4d006833:8ab6a677
2023-04-08 18:44:55
@ 4d006833:8ab6a677
2023-04-08 18:44:55Satoshi Nakamoto created bitcoin, and took great care to make a system that was completely independent, self sufficient, and self balancing without the requirements of trusted third parties or intermediaries.
The difficulty adjustment is arguably, the most beautiful part of the system as it ensures that block times will be about 10 minutes in all conditions from the onset of the network, and into the future. Put simply bitcoin, can tell time without a clock.
Most people who mine bitcoin no longer solo mine, as the odds of finding a block are astronomical. This has led to the development of mining pools which are operated by third parties, and consolidate hashrate and construct blocks on behalf of individual miners.
This is a benefit to smaller miners as it ensures somewhat predictable payouts so the miner has an opportunity to collect rewards, and if necessary, convert bitcoin into dollars to cover energy and other expenses.
The downside to this set up is that it consolidates a lot of hashrate, into centralized organizations, which themselves are often hosted on other centralized organizations, such as Amazon AWS. This makes mining pools an easy target for censorship and pool operators may not care about this.
A good example of this in action is Foundry’s pool. Foundry is the Bitcoin mining arm of Digital Currency Group which to put it kindly is not a role model for defending bitcoin or open systems. DCG's crypto lending unit had to file for bankruptcy as a result of the fallout from the collapse of the FTX exchange Ponzi scheme.
At the time of writing, Braiins mining insights estimates Foundry controls 32.2% of the Bitcoin hashrate. This alone is concerning, as in my opinion it's way too much for one entity to control. The bigger issue, however, is that Foundry was able to grow very fast because it was targeted at institutional miners who are already used to extensive regulation. Foundry pool is invite only and requires KYC/AML for anyone using the pool. They offered 0% pool fees to their customers as another perk.

Foundry has recently announced that it will begin charging fees in late April 2023 to its customers. Their notice states that pool fees will be tiered based on the previous quarter’s average hashrate.
Unfortunately, customers mining at Foundry who don't like this probably won't be able to leave the pool as their business structure probably won’t allow them to take their hashrate elsewhere. Hopefully others considering using Foundry will choose more decentralized options going forward.
Centralization exists everywhere on the Internet, not just in bitcoin mining pools. You're a writer and you want to reach an audience, well you're going to need a Substack or a Medium account. You're an artist or creator, and you want people to be able to sponsor you? Well, you're going to need a Patreon account. You’re a Podcaster and you want to reach Spotify's audience? Well, you have to be exclusive on Spotify, or they just list you without your permission and inject advertising into your product.
The Internet, as we know it was built on advertising, and because of that strong incentives are in place for companies to centralize, control, and monetize other peoples work.
When you post on Twitter, it's not your post. It's Twitter's post. If they decide they don't like you, they can shadow ban you or delete you.
The same is true for Substack, Patreon, Medium, Facebook, Instagram, and any other modern platform. They even do it to each other with Twitter recently suppressing Substack and those discussing it because they made a Twitter like experience on their own platform.
There is, however, one place where you truly own your identity and your content and that place is Nostr (Notes and Other Stuff Transmitted by Relays).

Nostr like bitcoin is a protocol not an app. TCP/IP is a protocol and others build their businesses and applications on top of it. A good example is Amazon. TCP/IP is the protocol and Amazon is the application or the product built on top.
For social implementations, Nostr is the protocol and various applications are built on top of it. Most of the current popular implementations are replicating the experience of Twitter and Reddit. I am posting this on another implementation called Habla that offers a blogging type of experience. I also post to my own Wordpress site bitcoinalchemy.io.
This alone is powerful as Nostr uses a public/private key system like bitcoin to track identity, and because the protocol is open, no central authority can delete notes posted on to Nostr and the users hold their own keys. Not your keys, not your notes.
The real power, however, is that the bitcoin lightning network is directly integratabtle with Nostr. It is very easy to send “zaps” to people and many client implementation's offer this directly on the note or post. This offers the ability to have instant monetization of any content that is paid directly to the content creator in a frictionless way, that no central authority can take a cut of or arbitrarily censor.
Bitcoin and Nostr are a match made in heaven. An open and uncensored communications layer, paired with an open and uncensored financial layer. Both systems are relatively new and a little rough around the edges, however, given time, and I don't believe it will be a very long time; value will flow where it is treated best.
Why are you enriching other companies with your content when you can claim all of the value for your work? Why are you posting to Twitter and allowing an algorithm to decide who sees your work? Why are you spending your time trying to game that algorithm when you can post to another platform that treats everyone equally? Why do you have dollars in a bank that steals from you through inflation? Why not store it in an asset that increases in value over time and incentivizes, saving instead of frivolous spending?
The Internet was designed as an open and decentralized system, and that was stolen from us, because the only viable way to monetize it was through advertising. Now there are other options for monetization, because the Internet now has its own digitally native asset in bitcoin and truly free communication layer in Nostr. We must all do our part to make sure that we get it right this time and promote open and decentralized systems.
Nostr Resources:
Nostr Guide - https://uselessshit.co/resources/nostr/
Get Verified (Like Twitter Blue Check, but better) - https://mainstreetchungus.com/nostr-nip-05-verification/
About me:
Bitcoin only and aspiring sovereign individual, trying my best to homestead in the Ozark Mountains of Missouri and mine bitcoin on stranded energy in the Show Me state.
I'm looking for like-minded individuals to help us build Bitcoin mines owned and operated by plebs.
Website: https://bitcoinalchemy.io
Nostr (GigaBTC): npub1f5qxsvu27hh8nsr9z0024upyjgj8h0m6h55lz9hxu5xptz4k5emsed576p
-
 @ 75bf2353:e1bfa895
2023-04-08 16:47:48
@ 75bf2353:e1bfa895
2023-04-08 16:47:48Dogecoin Is Dumb
This blog has evolved into writing about how to use cryptography to live a more private, fullfilled life. I don't often write about the monetary investment proposition of bitcoin. I think I have only posted one chart in jest.
tk fuck fiat
There are plenty of writers like Parker Lewis, Robert Breedlove(dispite his brief foray i to shitcoinery) and Lymn Alden that write about bitcoin from an investment perspective. I love their works, even Breedlove, and encourage you to read their articles about Bitcoin.
Here's the gist. * Fiat is infinite. * Bitcoin is limited to just under 21,000,000. * Bitcoin is better money.
One of the most important pieces of math in bitcoin has nothing to to with cryptography. It's actually a summation. Jammeson Lopp wrote an excellent artocle which shows us where to find this in the code. He also includes a wonderful info-graphic created by @anilsaidso.
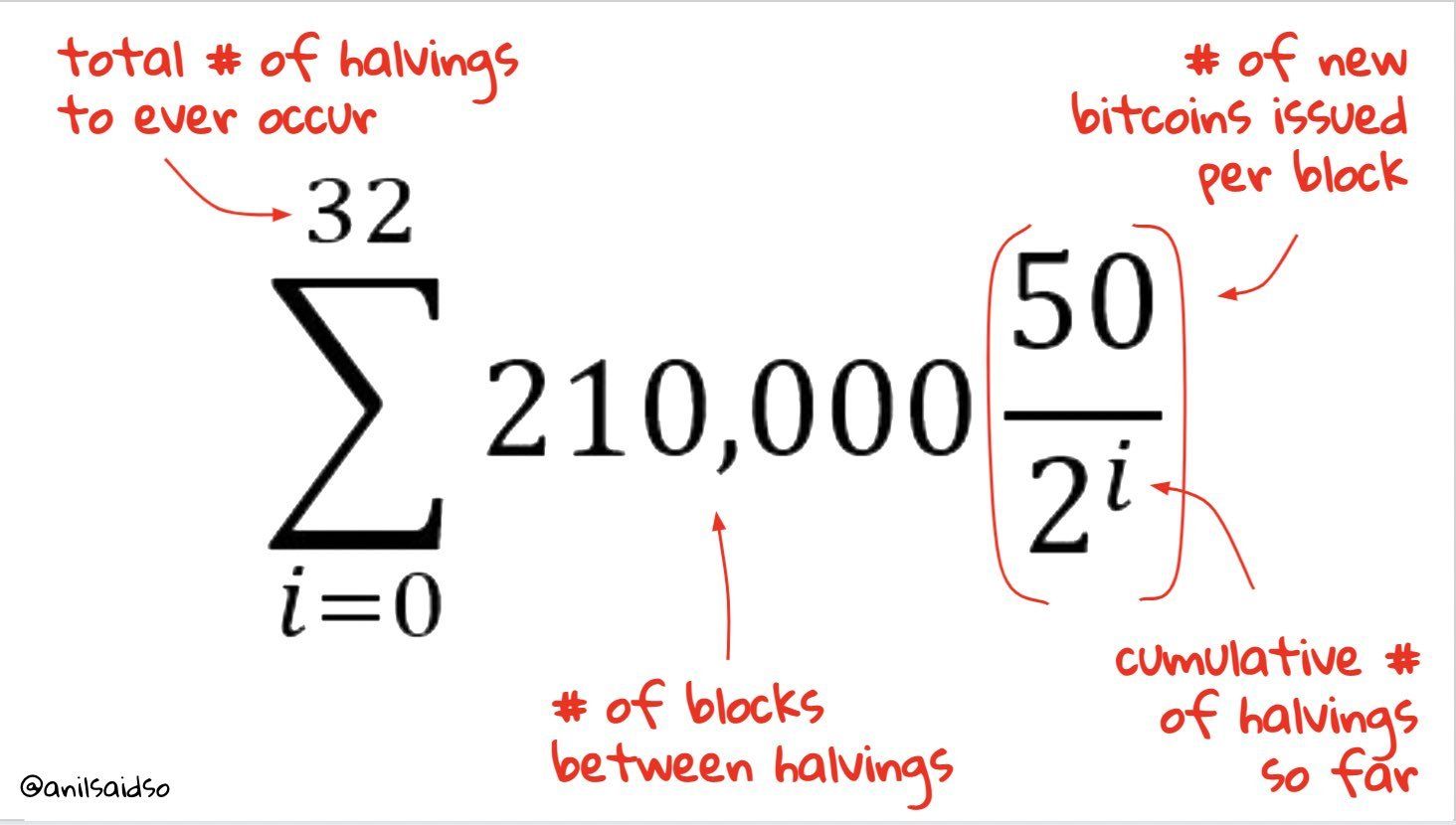
My creative writing degree allowed me to bypass as much math as possible in college. I never took calculus or anything lime this, but I was able to understand this info-graphic as fast as degen defi dork goes broke.
This info-graphic shows us a story using the language of mathematics, annotated in English. It's a story I've heard repeated many times before. I first heard Andreas Antonopolis tell this story on the Joe Rogan Experience in 2014, but it was originally told by none other than Satoshi Nakamoto:
``` Total circulation will be 21,000,000 coins. It'll be distributed to network nodes when they make blocks, with the amount cut in half every 4 years.
first 4 years: 10,500,000 coins next 4 years: 5,250,000 coins next 4 years: 2,625,000 coins next 4 years: 1,312,500 coins etc...
When that runs out, the system can support transaction fees if needed. It's based on open market competition, and there will probably always be nodes willing to process transactions for free*.
```
The Supply Schedule of Dogecoin

10,000 new dogecoin are issued every block.
A new block is made every minute...
60 x 60 = 3,600 new doge every hour
- 3,600 x 24 = 86,400 new doge every day.
- 86,400 x 365.25 = 31,557,600 new doge every year. Forever Elon.
Remember, somewhere around the year 2139, just under 21,000,000 bitcoin will be mined. 10,557,600 more dogecoin than that is mined every year.
Nathaniel Popper said bitcoin is digital gold.
Dogecoin is digital slave beads
One of my close in real life friends bought dogecoin at 12 cents. I tried orange pilling him every week for about 5 years and he never bought any bitcoin. Says he "did it for the memes.”
Now the richest man in the world plastered that dog on twitter. What was the purpose? You can't send it on twitter like we can send bitcoin on nostr. The price pumped 30% and twitter doesn't even use it. Why would they? Imagine a doge zap of 1 doge. It's worth 10 cents and takes a minute to send.
Why would anyone do that? * They won't. * They don't.
What would you rather have during the next financial crisis, digital gold or slave beads?
Don't trust Elon just because he's the richest man in the world.
Don't trust some nym either.
Run the numbers yourself.
--Blogging Bitcoin, 784,522
*This blog has no ads and is reader supported. It uses the Value 4 Value model over the lightning network instead. This allows you to pay content creators almost instantly, directly over the Internet using bitcoin.
-
 @ c753997e:9fe20adc
2023-04-08 15:54:16
@ c753997e:9fe20adc
2023-04-08 15:54:16By ZeroHedge - Apr 08, 2023, 10:00 AM CDT
Bills introduced in the Texas House and Senate would create a state-issued, gold-backed digital currency.
Enactment of this legislation would create an option for people to transact business in sound money, set the stage to undermine the Federal Reserve’s monopoly on money and create a viable alternative to a central bank digital currency (CBDC). Sen. Bryan Hughes (R) introduced Senate Bill 2334 (SB2334) on March 10. Rep. Mark Dorazio (R) introduced a companion, House Bill 4903 (HB4903) on the same day. The legislation would require the state comptroller to establish a digital currency that is fully backed by gold and fully redeemable in cash or gold as well. The comptroller would also be required to create a mechanism to use this gold-backed digital currency in everyday transactions.
“In establishing the digital currency the comptroller shall establish a means to ensure that a person who holds the digital currency may readily transfer or assign the digital currency to any other person by electronic means.”
The state of Texas would hold gold backing the currency in trust on behalf of the digital currency holders.
“The trustee shall maintain enough gold to provide for the redemption in gold of all units of the digital currency that have been issued and are not yet redeemed for money or gold.”
In practice, individuals would be able to purchase digital currency from the state. The state would then use the money to purchase gold that would be held in the Texas Bullion Depository or another secure vault. Individuals would be able to redeem their digital currency for dollars or gold.
Central Bank Digital Currencies (CBDC)
A gold-backed digital currency would create an alternative and allow individuals and businesses to avoid a CBDC.
Digital currencies exist as virtual banknotes or coins held in a digital wallet on your computer or smartphone. The difference between a central bank (government) digital currency and peer-to-peer electronic cash such as bitcoin is that the value of the CBDC is backed and controlled by the government, just like traditional fiat currency. Related: G7 Plans To Back New Natural Gas Investments
At the root of the move toward a CBDC is “the war on cash.” The elimination of cash creates the potential for the government to track and even control consumer spending.
Nigeria is already trying to get people to accept its CBDC (with a great deal of resistance), and China, India, and the US have all launched pilot programs to test CBDCs.
Imagine if there was no cash. It would be impossible to hide even the smallest transaction from the government’s eyes. Something as simple as your morning trip to Starbucks wouldn’t be a secret from government officials. As Bloomberg put it in an article published when China launched a digital yuan pilot program in 2020, digital currency “offers China’s authorities a degree of control never possible with physical money.”
The government could even “turn off” an individual’s ability to make purchases. Economist Thorsten Polleit outlined the potential for Big Brother-like government control with the advent of a digital euro in an article published by the Mises Wire. As he put it, “the path to becoming a surveillance state regime will accelerate considerably” if and when a digital currency is issued. A gold-backed digital currency would create an alternative to CBDCs.
Impact
The creation of a state-issued gold-backed digital currency would create currency competition with Federal Reserve notes and undermine the Fed’s monopoly on money. It would also provide an alternative if the Federal Reserve implements a central bank digital currency.
Broadly speaking, by making gold conveniently available for regular, daily transactions by the general public, gold-backed digital currency would create the potential for a wide-reaching effect. Professor William Greene, an expert on constitutional tender, said in a paper for the Mises Institute that when people in multiple states actually start using gold instead of Federal Reserve notes, it would effectively nullify the Federal Reserve and end the federal government’s monopoly on money.
“Over time, as residents of the state use both Federal Reserve notes and silver and gold coins, the fact that the coins hold their value more than Federal Reserve notes do will lead to a ‘reverse Gresham’s Law’ effect, where good money (gold and silver coins) will drive out bad money (Federal Reserve notes).
“As this happens, a cascade of events can begin to occur, including the flow of real wealth toward the state’s treasury, an influx of banking business from outside of the state – as people in other states carry out their desire to bank with sound money – and an eventual outcry against the use of Federal Reserve notes for any transactions.”
Gresham’s Law holds that “bad money drives out good.” For example, when the U.S. government replaced silver quarters and dimes with coins made primarily of less valuable copper, the cheap coins drove the silver out of circulation. People hoarded the more valuable silver coins and spent the less valuable copper money. So, how do you reverse Gresham?
The key is in making it easier to use gold in everyday transactions. The reason bad money drives out good is that governments put up barriers to using sound money in day-to-day life. That makes it more costly to spend gold and incentivizes hoarding. When you remove barriers, you level the playing field and allow gold and silver to compete head-to-head with Federal Reserve notes. On an even playing field, gold beats fiat money every time.
Background
The United States Constitution states in Article I, Section 10, “No State shall…make any Thing but gold and silver Coin a Tender in Payment of Debts.” Currently, all debts and taxes in Kansas are either paid with Federal Reserve Notes (dollars) which were authorized as legal tender by Congress, or with coins issued by the U.S. Treasury — very few of which have gold or silver in them.
The Federal Reserve destroys this constitutional monetary system by creating a monopoly based on its fiat currency. Without the backing of gold or silver, the central bank can easily create money out of thin air. This not only devalues your purchasing power over time; it also allows the federal government to borrow and spend far beyond what would be possible in a sound money system. Without the Fed, the U.S. government wouldn’t be able to maintain all of its unconstitutional wars and programs. The Federal Reserve is the engine that drives the most powerful government in the history of the world.
Creating a gold-backed digital currency would take another step in the process of abolishing the Federal Reserve system by attacking it from the bottom up – pulling the rug out from under it by working to make its functions irrelevant at the state and local levels, and setting the stage to undermine the Federal Reserve monopoly by introducing competition into the monetary system.
What’s Next?
At the time of this report, SB2334 and HB4903 had not been assigned to committees. Once they get committee assignments, they must get a hearing and pass by a majority vote before moving forward in the legislative process.
The Tenth Amendment Center contributed to this report.
-
 @ 7a9a58cb:ebc4db57
2023-04-08 14:43:02
@ 7a9a58cb:ebc4db57
2023-04-08 14:43:02blogstack test - ignore this
-
 @ 4d006833:8ab6a677
2023-04-08 14:20:17
@ 4d006833:8ab6a677
2023-04-08 14:20:17Since tumbling down the bitcoin, rabbit hole, I have had a lot of fun experiences learning about bitcoin with a focus on mining. One of the adventures that I was fortunate to have was mining bitcoin, at an oil well in a remote location in Wyoming.
When I started mining bitcoin at home there were challenges to overcome as I knew nothing about electricity beyond the basics of installing light switches, changing, outlets, etc.
Mining at any scale beyond a handful of machines is quite a different experience. As you add more ASICS to your mine, the time that it takes to manage the operation increases, as do the problems that need to be fixed on a regular basis.
Adding to these complexities, we were operating on an oil well using a natural gas generator powered by the gas flare at the well that was burning off the wasted methane that the oil well owner had no way to bring to market.
This was one of the hardest and most fun things I've ever done.

The first thing that we had to do was get permission from the Wyoming minerals commission to run the natural gas generator at the well. The reason for this is that the state wants to maintain control and keep records of emissions.
This was necessary as the requirement to maintain emissions within a certain range was the only reason we were invited to operate at the well in the first place. There was no pipeline to bring the natural gas to market, and before bitcoin, burning it was the only viable option.
When we presented, the governor of Wyoming was there, and we got a chance to briefly meet with him and talk bitcoin.

We were given permission to operate and began installing our equipment at the oil well. For our deployment, this consisted of a 350 kW natural gas generator connected to a 16 foot mining container that could hold 100 S19’s.
For Internet, we initially chose a land based wireless Internet service provider. These are common in the remote parts of Wyoming, because the terrain is generally flat, and there is line of sight for the Internet service provider to establish connections. We actually ended up replacing this solution with a HughesNet satellite dish as Starlink was not available at this time. Mining bitcoin does not require a lot of bandwidth, and HughesNet proved to be more stable. I use Starlink RV for these types of deployments now as you can turn it on and off and use it at any location if you need to move around.

When we began installing everything, I thought that the natural gas generator uptime and maintenance would be our biggest challenge. It turned out that the generator was pretty easy. If the oil well was operating properly, then natural gas fed the generator and made electricity. We were mining bitcoin.
The biggest challenge we faced was the weather. Wyoming is flat, and the wind is unforgiving. When it's hot outside, it's blasting the intake fans on your container with hot air. If you face your intakes the wrong way, the wind is working against your fans, making that side of the container hotter. Even if you face it the correct direction, you're still sucking in hot air and in summer and during peak hot days, we were losing 10% to 20% of our hash because the machines were simply too hot to operate efficiently.
When it's cold out, it's still windy and when it snows it creates drifts that can be as high as the mining container. Support personnel have a hard time reaching the site as all the roads are gravel and the weather beats them down. Even the large semi trucks that come to take the oil have a hard time getting in during the worst parts of winter.

Even with these difficulties, it was an incredible experience. We had 100 S19’s running for a total of 10,000 TH/s. I basically lived at the well for a month while we got everything tuned and running smoothly.
This was a lot of fun to set up and run, however, not being local to Wyoming ultimately made the project unsustainable. We had a very low purchase price for the natural gas as it was stranded, however, we were leasing our generator and had a cost associated with another company to keep that running. We also had to contract a support person to go out to the site when necessary to change fans, reset machines and breakers and all the other little issues that happen at any bitcoin mine. This was a one and a half hour trip each way, and every time this happened we incurred a trip charge and time for the person to be on site. Communication was also an issue as there was no cellular service, and we had to direct the support person via chat.
We ended up selling the location to another company and moved our machines to an on grid location that ended up being about the same cost to operate when you factor in all the extra costs in Wyoming.
Stranded natural gas is an excellent energy source for mining bitcoin. The holy grail is to find a location where you can get the gas very cheap, own and operate your own generator and have that location be reasonably close to civilization to support it yourself or to contract someone else at a cost that keeps the project economically viable. If I had a natural gas well on my own land, I would set this up and let it make bitcoin 24/7. If you are one of the lucky ones that does have a well on your land, hit me up, and I'll help you install a bitcoin factory in your backyard.
About me:
Bitcoin only and aspiring sovereign individual, trying my best to homestead in the Ozark Mountains of Missouri and mine bitcoin on stranded energy in the Show Me state. I'm looking for like-minded individuals to help us build Bitcoin mines owned and operated by plebs.
Website: https://bitcoinalchemy.io Nostr (GigaBTC): npub1f5qxsvu27hh8nsr9z0024upyjgj8h0m6h55lz9hxu5xptz4k5emsed576p
-
 @ 3bd14ae2:c169f4f4
2023-04-08 12:38:09
@ 3bd14ae2:c169f4f4
2023-04-08 12:38:09Title
Bold
++Underline++
Text with an image.
Famous words
-
 @ c75622fd:a9b66e1d
2023-04-08 12:33:13
@ c75622fd:a9b66e1d
2023-04-08 12:33:13[3]
-
 @ c75622fd:a9b66e1d
2023-04-08 10:02:21
@ c75622fd:a9b66e1d
2023-04-08 10:02:21[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
[85]
[86]
[87]
[88]
[89]
[90]
[91]
[92]
[93]
[94]
[95]
[96]
[97]
[98]
[99]
[100]
[101]
[102]
[103]
[104]
[105]
[106]
[107]
[108]
[109]
[110]
[111]
[112]
[113]
[114]
[115]
[116]
[117]
[118]
[119]
[120]
[121]
[122]
[123]
[124]
[125]
[126]
[127]
[128]
[129]
[130]
[131]
[132]
[133]
[134]
[135]
[136]
[137]
[138]
[139]
[140]
[141]
[142]
[143]
[144]
[145]
[146]
[147]
[148]
[149]
[150]
[151]
[152]
[153]
[154]
[155]
[156]
[157]
[158]
[159]
[160]
[161]
[162]
[163]
[164]
[165]
[166]
[167]
-
 @ c75622fd:a9b66e1d
2023-04-08 09:13:12
@ c75622fd:a9b66e1d
2023-04-08 09:13:12[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
[85]
[86]
[87]
[88]
[89]
[90]
[91]
[92]
[93]
[94]
[95]
[96]
[97]
[98]
[99]
[100]
[101]
[102]
[103]
[104]
[105]
[106]
[107]
[108]
[109]
[110]
[111]
[112]
[113]
[114]
[115]
[116]
[117]
[118]
[119]
[120]
[121]
[122]
[123]
[124]
[125]
[126]
[127]
[128]
[129]
[130]
[131]
[132]
[133]
[134]
[135]
[136]
[137]
[138]
[139]
[140]
[141]
[142]
[143]
[144]
[145]
[146]
[147]
[148]
[149]
[150]
[151]
[152]
[153]
[154]
[155]
[156]
[157]
[158]
[159]
[160]
[161]
[162]
[163]
[164]
[165]
[166]
[167]
[168]
[169]
[170]
[171]
[172]
[173]
[174]
[175]
[176]
[177]
[178]
[179]
[180]
[181]
[182]
[183]
[184]
[185]
[186]
[187]
[188]
[189]
[190]
[191]
[192]
[193]
[194]
[195]
[196]
[197]
[198]
[199]
[200]
[201]
[202]
[203]
[204]
[205]
[206]
[207]
[208]
[209]
[210]
[211]
[212]
[213]
[214]
[215]
[216]
[217]
[218]
[219]
[220]
[221]
[222]
[223]
[224]
[225]
[226]
[227]
[228]
[229]
[230]
[231]
[232]
[233]
[234]
[235]
[236]
[237]
[238]
[239]
[240]
[241]
[242]
[243]
[244]
[245]
[246]
[247]
[248]
[249]
[250]
[251]
[252]
[253]
[254]
[255]
[256]
[257]
[258]
[259]
[260]
[261]
[262]
[263]
[264]
[265]
[266]
[267]
[268]
[269]
[270]
[271]
[272]
[273]
[274]
[275]
[276]
[277]
[278]
[279]
[280]
[281]
[282]
[283]
[284]
[285]
[286]
[287]
[288]
[289]
[290]
[291]
[292]
[293]
[294]
[295]
[296]
[297]
[298]
[299]
[300]
[301]
[302]
[303]
[304]
[305]
[306]
[307]
[308]
[309]
[310]
[311]
[312]
[313]
[314]
[315]
[316]
[317]
[318]
[319]
[320]
[321]
[322]
[323]
[324]
[325]
[326]
[327]
[328]
[329]
[330]
-
 @ 79c704df:37126767
2023-04-08 08:11:33
@ 79c704df:37126767
2023-04-08 08:11:33Testing image uploads

| Head | Head | Head | Head | Head | Head | | --- | --- | --- | --- | --- | --- | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data | | Data | Data | Data | Data | Data | Data |
-
 @ 42a8514a:ba7e0578
2023-04-08 03:23:23
@ 42a8514a:ba7e0578
2023-04-08 03:23:23 -
 @ 7ab79bc0:9385ad99
2023-04-08 01:09:38
@ 7ab79bc0:9385ad99
2023-04-08 01:09:38Bitcoin ist Zeit und Zeit ist Geld
In einem der vorigen Artikel haben wir uns mit den Funktionen und Eigenschaften von Geld befasst. Eine, vielleicht sogar die wichtigste, Funktion von wertvollem und hartem Geld ist Knappheit. Wir haben gesehen, dass Bitcoin die einzige Form von Geld ist, die diese Charakteristik zu 100% erfüllt.
Knappheit bedeutet, dass das Gut, das als Geld benutzt wird, begrenzt ist und nicht ohne weiteres vermehrt werden kann.
Bitcoin erfüllt diesen Anspruch, denn
Bitcoin ist auf 21.000.000 begrenzt. Die harte Obergrenze von Bitcoin ist von zentraler Bedeutung für sein Wertversprechen. Alle 2.099.999.997.690.000 Sats werden irgendwann existieren (oder existieren schon - je nach Betrachtungsweise) und darüber hinaus werden keine weiteren Sats produziert.
Die einzige andere Ressource, die wir Menschen haben, die uns jedem zur Verfügung steht und zu 100% begrenzt ist, ist unsere Zeit. Ausnahmslos jeder Mensch hat ab dem Moment seiner Geburt ein Zeitfenster in diesem Leben und dieses Zeitfenster - dieses Leben - ist begrenzt. Es hat noch niemand geschafft diese Regel zu brechen, bzw. zu cheaten.

Die Lebensdauer jedes Menschen fällt unterschiedlich aus und ist sogar recht ungerecht verteilt. Es gibt Menschen, die schon sehr, sehr früh nach ihrer Geburt sterben, und es gibt Menschen, die sehr, sehr alt werden. Auf diesem Spektrum von 0 bis ca. 120 Jahren befinden wir Menschen uns alle. Wir können aktiv Einfluss auf unsere Lebenserwartung nehmen, sowohl verlängernde als auch verkürzende Maßnahmen ergreifen, doch eins bleibt bisher immer garantiert: Unsere Zeit ist endlich. Und damit ist sie unser knappstes Gut.
Kommen wir nun zurück zum Geld. Wie wir schon gesehen haben, muss Geld drei Funktionen erfüllen:
Es muss als Tausch- oder Zahlungsmittel funktionieren, es sollte ein Wertaufbewahrungsmittel sein und als Recheneinheit dienen.
Während man schnell dazu übergeht, bei Geld an die Funktionen von Zahlungsmittel und Recheneinheit zu denken, da diese im täglichen Leben tausendfach vorkommen, ist es besonders die Funktion des Wertaufbewahrungsmittels, die Geld einen besonderen Stellenwert in unserem Leben als Ganzes verleiht. Und da ist sie, die Überschneidung von Geld und unserem Leben, also unserer begrenzten Zeit, auf die ich seit 400 Wörtern hinarbeite 😰
Zeit ist Geld. Jeder kennt diese Redewendung. Im wahrsten Sinne des Wortes bedeutet sie, dass man Zeit in Geld verwandeln kann und dass diejenigen, die Zeit haben auch Geld haben. Man spricht hier irrtümlicherweise auch von "Zeit sparen". Als ob die Möglichkeit bestehe, nicht verbrauchte Zeit zu einem späteren Zeitpunkt abzurufen. Dass dies außerhalb von Momos Welt nicht möglich ist, sollte jedem bewusst sein. Was meint man also damit, wenn man sagt man spart Zeit, oder Zeit ist Geld? Die Funktion des Wertaufbewahrungsmittels von Geld bedeutet erstmal, dass das verwendete Geld seinen Wert durch die Zeit aufrecht erhalten kann. Im allerbesten Falle ist ein Geld von heute auch morgen immer noch ein Geld wert.

Betrachten wir nun unser eigenes, hart begrenztes Zeitfenster, also jenes, das uns gegeben wurde, um auf diesem blauen, lustigen Ball zu verweilen, so wollen wir diese Zeit möglichst würdevoll und möglichst angenehm verbringen. Da das Leben allerdings Geld kostet, sind wir in der Regel gezwungen, solches zu verdienen. Es soll ein paar glückliche Menschen geben, denen dieser Ballast von Geburt an genommen wird, allerdings verhält es sich für das Gros der Menschen so, dass sie für ihren Unterhalt puckeln müssen. Im Idealfall sieht das so aus, dass man bei einem erwartbaren Durchschnittsalter von 80 Jahren, die ersten 20 Jahre damit verbringt zu erlernen, wie das Leben funktioniert und wie man Geld verdient, um dann 40 Jahre lang genau das zu tun und wenn alles gut läuft hat man noch 20 Jahre, um seinen wohlverdienten Ruhestand zu geniessen. Also einfach gesprochen verbringt man 50% seines Lebens damit, 100% seines Zeitfensters zu finanzieren (die ersten 20 Jahre des Lernens finanziert man zwar seinen Nachkommen, hat aber im Gegenzug dafür diese auch fremdfinanziert bekommen). Das bedeutet wiederum, dass man in den 40 Jahren Berufsleben doppelt so viel Geld verdienen muss, wie das eigens gewählte Leben kostet.

Um auf die Redewendung "Zeit ist Geld" zurückzukommen, bedeutet dies schlicht, dass jeder arbeitende (und damit Geld verdienende) Mensch seine eigene knapp bemessene Zeit in Form von Arbeit zur Verfügung stellt, um Geld zu verdienen. Dies tun wir, da wir Zeit eben nicht sparen können. Wir versuchen sie in einen anderen Aggregatzustand umzuwandeln (Zeit ➡️ Geld), um uns zu einem späteren Zeitpunkt mit diesem Geld unsere Zeit zurückzukaufen. Dies funktioniert zwar nicht im direkten Sinne, also dass wir uns zusätzliche Zeit kaufen, jedoch können wir das Decken laufender Kosten vorfinanzieren und somit, hoffentlich, im Ruhestand leben, ohne unsere laufenden Kosten durch Arbeit decken zu müssen. Wenn alles gut läuft, schaffen wir es sogar unseren gewählten Lebensstandard aufrechtzuerhalten und führen somit ein für unsere subjektiv gesteckten Messpunkte würdevolles und angenehmes Leben.
So die Theorie. Denn in der Praxis funktioniert dies nur, wenn es uns möglich ist, unsere Zeit in ein Geld umzuwandeln, das es uns erlaubt, eine Umwandlung von Geld zurück zur Zeit zu einem späteren Zeitpunkt so vorzunehmen, dass wir möglichst wenig verlieren. Dies ist die einzige Aufgabe eines Wertaufbewahrungmittels: Der Erhalt des jetzigen Wertes einer Sache über einen Zeitraum hinweg.

Praktisch gesprochen besteht dieser Vorgang aus zwei Komponenten. Zuerst müssen wir Geld verdienen, dann müssen wir es sparen. Bestenfalls schaffen wir so viel Geld zu verdienen, dass unsere Einnahmen unsere Ausgaben übersteigen, damit wir überhaupt in der Lage sind, überschüssiges Geld zu sparen. Dann müssen wir ein Wertaufbewahrungsmittel finden, dass es uns erlaubt, diesen Überschuss so zu konservieren, dass wir ihn zu einem späteren Zeitpunkt abrufen können. Über die erste Komponente lässt sich schon genug schreiben, über den gewählten Lebensstandard und die damit einhergehenden Kosten, die (Un-) Gerechtigkeit und Chancenungleichheit beim Erlangen einer Erwerbstätigkeit, etc. blah.

Die zweite Komponente allerdings ist für unsere Betrachtung die viel entscheidendere. Denn gehen wir davon aus, dass wir zu den glücklichen Wenigen gehören, die es schaffen eine niedrige Zeitpräferenz zu erlangen und Überschüsse in der Gewinn- und Verlustrechnung des Lebens zu erzielen, so bleibt immernoch die grosse Frage offen, wie wir es schaffen sollen, diese Überschüsse zu konservieren, sodass wir sie dann später nutzen können. Und zwar so, dass sie möglichst wenig an Wert verloren haben, oder sogar an Wert zugenommen haben.
Genau das ist das Geschäftsmodell von vielen Unternehmen, Institutionen und Schlangenölverkäufern weltweit, die damit werben, unser hart verdientes Geld so anzulegen, dass es später unseren Ruhestand finanziert. Sie wollen uns in ihre undurchsichtigen Finanzierungsmodelle locken, um damit als die eigentlichen Profiteure hervorzugehen.

Ob private oder staatliche Altersvorsorge, Riesterrente, Bausparvertrag, 401k, IRA, fondsgebundene Tralalarente oder Aktion Mensch-Los mit Sofort-Rente, alle Anbieter spielen mit der Sorge der Menschen, dass ihr heute gespartes Geld morgen wohl nicht mehr zur Finanzierung des erträumten Ruhestands reicht. Und warum ist das so? Wegen des effektiven Kaufkraftverlustes unseres aktuellen Geldes. Viel Tinte wurde vergossen, viele Tasten misshandelt, um dieses Thema zu beschreiben, das heute aktueller denn je ist. Denn wenn Geld in einer Fiat-Währung für die zukünftige Verwendung gespeichert wird, verliert es aufgrund der Währungsinflation im Laufe der Zeit an Kaufkraft. Das bedeutet effektiv, dass die investierte Zeit nicht nachhaltig widergespiegelt wird, oder drastischer ausgedrückt: wir haben unsere Zeit verschwendet. Sparen funktioniert also nicht mehr, wie es uns damals im Kindesalter beigebracht wurde.
Bitcoin fixes this, yay, Bitcoin-Floskel. Aber warum ist das so? Während Fiat-Währungen einem reellen Kaufkraftverlust ausgesetzt sind, der durch Fiskal- und Geldpolitik bedingt ist, ist der Wert von Bitcoin immer gleich. Ein bitcoin = ein bitcoin. Jetzt könnte man natürlich entgegensetzen, dass ein Knopf = ein Knopf. Allerdings lassen sich Knöpfe unendlich nachproduzieren und in Umlauf bringen. Doch wie wir wissen, hat Bitcoin eine harte Obergrenze von 21.000.000 bitcoins. Dies macht Bitcoin wahrscheinlich zum überprüfbar knappsten Gut auf unserer Erde. Selbst unser Zeitfenster könnte mit ein paar Entwicklungssprüngen in der DNA und Molekularforschung vielleicht irgendwann deutlich ausgeweitet, wenn nicht sogar für immer geöffnet werden.
Jedoch ist Bitcoins Code unveränderlich: Die 21 Millionen Obergrenze ist in Stein (Code) gemeißelt und damit eignet sich Bitcoin hervorragend als langfristiger Speicher für Zeit. Allein der Umrechnungskurs von Bitcoin in eine lokale, aktuelle oder für den Moment nützliche Währung hängt davon ab, wie viel Zeit man in einen anderen Wert umwandeln kann. Doch auch dies ist ein Feature und kein Bug. Denn jeder Arbeitstag, den ich heute in Euro oder US Dollar "spare" (besser: umwandle), ist komplett verloren, wenn diese Fiat-Währung zu einem Zeitpunkt x nicht mehr existiert. Dann ist es doch von Vorteil, wenn man seine Zeit in einen neutralen Aggregatzustand umwandeln kann, der sich in Zukunft beliebig in die benötigte aktuell brauchbare Recheneinheit / Währung transformieren lässt.
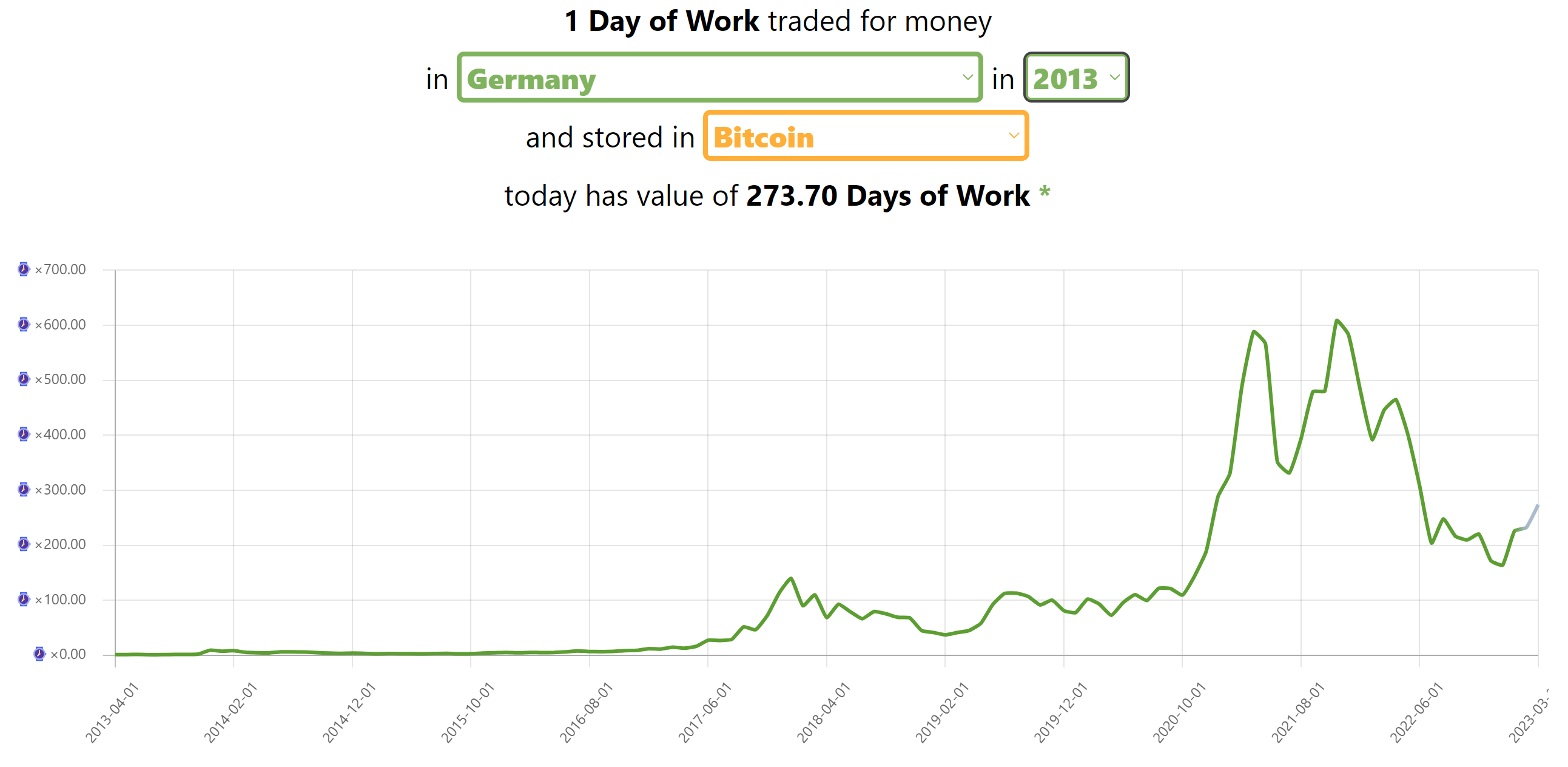
Andersherum lässt sich argumentieren, dass das Währungspaar nicht BTC/USD oder BTC/EUR ist, sondern direkt ZEIT/BTC. Man ermittelt also den Wert von Zeit direkt in einer Bitcoin-Ausdrucksweise, die in Zukunft sogar festgesetzt werden könnte und damit die ultimative Währungseinheit darstellen würde.
Bitcoin verstehen
Bitcoin ist nicht nur Zeit im Sinne von umgewandelter Zeit in Geldmenge, sondern als reeller Zeitaufwand, um Bitcoin zu verstehen und Bitcoin für sich selbst begreifbar zu machen. Auch diese Definition von Zeit ist wiedermals für jeden Menschen subjektiv und dem eigenen Empfinden nach zu bemessen. Was jedoch nicht von der Hand zu weisen ist, ist dass es einen gewissen Mindestaufwand von Zeit, ob mit der Lektüre verschiedener Texte, dem Austausch mit Gleichgesinnten, dem tatsächlichen Ausprobieren und Erlernen der mechanischen Abläufe, etc. bedarf, um Bitcoin zu begreifen. Niemand wird jemals Bitcoin in seiner Gänze, seiner Tragweite oder seiner Wirkung vollständig verstehen, allerdings bin ich fest davon überzeugt, dass es diesen einen Punkt gibt, an dem bei jedem an Bitcoin interessierten Menschen ein gewisser Aha!-Moment eintritt, an dem viele Puzzleteile mit einem Mal ein Bild ergeben.
Dieser Moment tritt bei manchen sehr früh, bei manchen eher später ein, jedoch eint alle Bitcoiner und Bitcoin-verstehende Menschen dieser eine Moment, den es nur zu erreichen möglich ist, wenn ein gewisses Maß von Zeit investiert wurde. Dieser Moment lässt sich nicht erklären und muss von jedem Menschen selbst erlebt werden, um ihn zu verstehen. Damit kann er nicht erkauft oder erschlichen werden, sondern lässt sich nur in Form von aufgebrachter Zeit erreichen. Damit trägt Bitcoin eine weitere Zeitkomponente in sich, die weder im Whitepaper, noch im Code, noch in später veröffentlichten Texten Satoshis festgehalten oder gar definiert wurde. Jedoch wage ich zu behaupten, dass es niemanden gibt, der/die Bitcoin begriffen hat und von sich sagt, diesen Moment der Klarheit, der Offenbarung, nicht erlebt zu haben.

Bitcoin hat sein eigenes Verständnis von Zeit
Zeit ist ein sehr tiefgründiges und subjektives Konstrukt. Es gibt die Uhrzeit, also eine Zahl, die uns anzeigt, wie weit der jeweilige Tag vorangeschritten ist. Der Kalender misst auch Uhrzeit, nur eben nicht in Form von Stunden, Minuten und Sekunden, sondern in Monaten, Wochen und Tagen. Und dann gibt es noch Jahre. Wohingegen Sekunden, Minuten, Stunden, Tage, Wochen und Monate begrenzt sind - es gibt z.B. nur 12 Monate, dann fangen wir wieder von vorne an zu zählen, ist die Anzahl von Jahren keinem Zyklus unterworfen. Es wird immer weiter gezählt. Natürlich gibt es Dekaden, Jahrhunderte, Jahrtausende, etc., doch sind diese nur Recheneinheiten, die das Zählen von Jahren vereinfachen. In unserem System gibt es ein Jahr null und seit dem zählen wir vorwärts (wenn man davon absieht, dass sich jemand vor 400 Jahren das Jahr null ausgedacht hat und seit dem alles zurückgerechnet wurde, aber wir wollen mal nicht kleinlich sein) und alles was vor diesem Jahr null liegt, wird rückwärts gezählt. Dem Weihnachtshasen sei Dank 🙏
Genauso willkürlich, wie diese Zeiterfassung festgelegt wurde, verhält es sich bei Bitcoin auch. Denn Bitcoins innerer Maschinenraum ist eigentlich nichts anderes als eine eigenwillige und nutzungsbezogene Uhr. Die Bitcoin-Blockchain ist eigentlich eine Timechain, ein sogenannter Timestamp-Server. Wie schon mehrmals erwähnt, findet man das Wort 'Blockchain' in Satoshis Whitepaper nicht ein einziges Mal. Dafür findet man bereits im vierten Satz den Begriff 'Timestamp'.

Da Zeit ein recht flexibler Begriff ist und die Zeitmessung vom jeweiligen Nutzen oder dem Erfüllen eines Ziels abhängig ist, ist es besonders schwierig, ein allgemeingültiges System zu wählen. Zeit kann in vielen Formen dargestellt werden, von "Jetzt bis kein Bock mehr", oder "Anno Pief und Dazumal" gibt es etliche Redewendungen, die zeigen, dass Zeit gefühlt wird und nicht gemessen wird. Doch wenn man ein global funktionierendes dezentrales Netzwerk errichten möchte, dass darauf basiert seine eigene Wahrheit zu speichern, ohne auf Dritte angewiesen zu sein und alle Transaktionen so zu speichern, dass sie nachvollzogen und validiert werden können, bedarf es eines Zeitmessungsmechanismus. Und dieser muss absolut fehlerfrei sein und darf keine Latenz zulassen, da sonst Raum für Schummeleien geboten wäre. Was eignet sich da also besser, als ein eigener, eigens für diesen besonderen Zweck erdachter Mechanismus zum Festhalten von Geschehnissen? Diese Geschehnisse werden vom System mit einem Zeitstempel versehen, der unmissverständlich macht, welche Reihenfolge von Geschehnissen die eine Wahrheit ausmacht, der alle Netzwerkteilnehmer vertrauen.
Gigi hat sich dem Thema in seinem neuen Buch deutlich detaillierter gewidmet und ich empfehle jedem/r die Lektüre dieses Kapitels:
Fazit
Bitcoin ist nicht nur Zeit. Bitcoin misst die Zeit in seiner eigenen Weise. Bitcoin verlangt Zeit von uns, damit wir es begreifen, aber Bitcoin hilft uns, den Wert unserer Zeit einzufangen. Damit ist Bitcoin sowohl das Metronom, das seinen eigenen Takt angibt, strenger Lehrer, der Aufwand fordert, um Exzellenz zu erreichen, als auch Tresor oder Akku, der aufgebrachter Zeit einen Wert beimisst, und diesen Wert zu speichern vermag. Tick, tock, next Block!
-
 @ 76c71aae:3e29cafa
2023-04-07 23:29:10
@ 76c71aae:3e29cafa
2023-04-07 23:29:10The super app is something like WeChat or QQ, a single app where you do everything, book a car service, talk to your friends, make purchases online or in person. It's a monolithic do everything app, and it's very popular, especially in China.
Silicon Valley tends to make apps that are nothing like the super app. It's because western tech companies don't work anything like Chinese internet companies. Western tech tends to rely on a huge base of open source software, but then create these vertically integrated silos of apps that do one thing well with elegant design and not many options. When an app does try to do lots of things, we hate it, just look at MS Word.
The vertical integration is narrow. The Chinese super app does everything broadly, but it's not so pretty. SV tends to stagnate, companies are afraid to compete with themselves so they get stuck at a local maximum. Our culture of product development find something that works, and sticks with it. That's why in the west, big companies buy the upstarts. If you're an ambitious entrepreneur, you quit and create a new startup. Most likely you'll fail, but you might do well enough that a big company will you buy you out, or you'll do so well you replace the incumbents.
The last western super app was AOL. And we celebrated its death. Since then, it's just been a dream. It was Elon Musk's goal when he bought twitter, it was the story that SBF sold to investors as he pumped up FTX. An app to rule them all.
We don't make a super app because our culture, politics, and economic system don't work like that. We hated being stuck on AOL. Silicon Valley's real super app is the web itself, the browser, linux, smart phones, etc... They're more open, less controlled, more competitive. Our legal system punishes companies that become dominate to eliminate monopolies. Out business culture causes big tech companies to be safe and consistent. Google had the lead in AI, yet it was OpenAI that launched ChatGPT in a chaotic, barely coordinated 6-week sprint.
Even after AOL, there was a time when silicon valley was moving towards its model of a more open super app. Facebook launched their platform, twitter's api enabled a tremendous app ecosystem. But both companies chose to lock things down. They did it because their only economic model was based on advertising and required their control. The web was slowly enclosed from an open, chaotic ecosystem to a platform which monitors users behaviour and captured their attention to sell to advertisers.
I think open social protocols we're seeing emerge today, and in particular nostr, could be our super app. Instead, a single app that does everything. It's a common social protocol where many apps can be created and run. We've created a system that reflects a set of values around autonomy, openness, decentralization, permissionless participation, privacy, encryption, and yes cryptocurrencies. Without the financial part, we can't make the ecosystem thrive.
We can make a super app, but not one, rather a family of apps, a style of apps that let there be choices on a common platform. Smart clients, dumb relays, and just enough cryptography to keep it all functioning.
When we build this new open super app protocol, we'll need to create all the things that existed on the centralized social media apps, but also the giant closed super apps. The old model was vertically integrated. Lots of services and businesses were needed to keep it running, but they were all controlled by a single company, hidden off from the public. The advertising marketplace, the content moderation, the CDN for fast media delivery, the transcoders for making images and video the right size, the algorithms for deciding what to show you or who you should connect with, the bug tracking, customer support, business development team, legal, compliance, public relations.
We don't like how the vertically integrated ecosystem worked, it didn't provide us agency and autonomy. But most importantly, we didn't have the space to innovate and create. In this new open system, we still need all those services provided by the big companies is needed somehow. We need to meet those same needs, but in new ways.
Users see the frontend of an app, the UX, their experience as a user. But there is so much more, middleware, backend, business operations. All of that will need to be created in a new open ecosystem.
To take one example, moderation, so we don't have to see a constant flow of ISIS beheading videos, some that we can handle with algorithms, but that's also how big social does it today. Even with the best AI minds in the world, a lot slips through. People need to be able to make judgements, and figure out edge cases. I don't like the choices that Facebook, TIkTok, or Elon's Twitter makes, but it doesn't mean we won't need to make those choices. Now we can make it a service where we pay people who do that social labor. And we can choose who we want to do it, making sure their values are aligned. We can use a stead stream of payments to all of these services.
Nostr can be the protocol upon which we build an open super app ecosystem which contains multitudes.
-
 @ f0ff87e7:deeeff58
2023-04-07 22:39:19
@ f0ff87e7:deeeff58
2023-04-07 22:39:19So I just created a quotes bot on Nostr. I'm adding new quotes to it all the time but already it is serving up quotes from Satoshi to Nietzsche.
Making one of these yourself is incredibly easy - much more so than conventional social media like Twitter as there's no locked down API to deal with or beg for keys to. You simply generate a new private key for the bot, add some metadata, setup a script to pick from a random selection your a predefined list of quotes, setup another script to feed the output into a new Nostr status and post it, then put that on your
crontabso it runs automatically every hour, or two hours, or once a day, or whatever you want.This tutorial will show you how to do that even if you have no coding experience. All you need is access to something running Linux (even if it's just a Raspberry Pi or a cheap VPS) and... that's it.
Keep in mind that whatever you choose to set this up on has to be constantly running for the scripts to work. This is why a Raspberry Pi or a VPS are good options. It requires almost zero CPU power, RAM, or bandwidth.
Ready? Let's go!
Install the dependencies
To make sure all dependencies are installed, simply run:
bash sudo apt install python3 python3-pip python-is-python3 golang gitMake a user for the bot
Especially if you use a VPS for this, having separate non-privileged users for different tasks is just smart:
bash sudo adduser nostrbotChoose a password then you can jump into the new user with:
bash sudo su - nostrbotInstall noscl
This is the magic sauce that will let you directly interact with Nostr in the command line. If you made a new user, log into it first, then run this:
bash go install github.com/fiatjaf/noscl@latestNow let's make sure it'll work correctly:
bash nano ~/.bashrcScroll to the bottom and add:
bash export GOPATH=$HOME/go export PATH=$PATH:$GOROOT/bin:$GOPATH/binSave (ctrl + O) and exit (ctrl + X) then run:
bash source ~/.bashrcNow you want to create the directory
nosclcan create its config file in when you run it and use it:bash mkdir -p ~/.config/nostrIf you followed the above correctly, you run
nosclin the command line and you should get an output like this:bash Usage: noscl home noscl setprivate <key> noscl sign <event-json> noscl verify <event-json> noscl public noscl publish [--reference=<id>...] [--profile=<id>...] <content> noscl message [--reference=<id>...] <id> <content> noscl metadata --name=<name> [--about=<about>] [--picture=<picture>] noscl profile <key> noscl follow <key> [--name=<name>] noscl unfollow <key> noscl event <id> noscl share-contacts noscl key-gen noscl relay noscl relay add <url> noscl relay remove <url> noscl relay recommend <url>That means it's working!
At this point you simply want to run three commands:
bash noscl key-gen noscl setprivate [key generated above] noscl publicThe first generates a private/public keypair. The second is where you copy the new private key to set it as the one
nosclwill use. The third prints the public key you can use to look up the bot later on.You'll also need to add some relays. You can do that now or at the end. The process is simple:
bash noscl relay add wss://relay.2nodez.com noscl relay add wss://relay.snort.social noscl relay add wss://offchain.pub noscl relay add wss://nostr-relay.alekberg.net noscl relay add wss://no.str.crAnd so on... add as many as you like.
You can do this at any point, just make sure to add at least a few before the first time you run the bot, otherwise it won't have anything to publish to!
You can also add some metadata such as a name and an about section using the command line, or you can sign in with a client of your choice and use that instead for a friendly GUI option.
To do it on the command line:
bash noscl metadata --name="My Bot" --about="This is my Nostr bot for posting quotes." --picture="https://..."Get your list of quotes and a Python script to pick one at random
This is the bit you'll have to do manually. Pick out some quotes you like and put them in a file called
quotes.txtin the home folder. Make sure each quote is on a new line.Now create a Python script by running
nano quotepicker.pyand simply pasting this in:```python import random
text_file = open("quotes.txt") line = text_file.readlines()
print(random.choice(line)) text_file.close() ```
Now as long as you have your Python script and your
quotes.txtwith at least a few quotes for testing, both in the same directory, you should be able to simply run this and get a different one each time:bash python3 quotepicker.pyKeep in mind, the more quotes you have, the less likely it is you will get the same quote when you run the script again.
Once you have a decent number of quotes (I recommend at least 100) you can move onto the next step. You're almost done!
Setup the bash script and crontab
This bit is super easy and should take under a minute.
Run
nano nostrpost.shand paste this in:bash b=$(python3 /home/nostrbot/quotepicker.py) echo $b /home/nostrbot/go/bin/noscl publish "$b"Now let's make it executable:
bash chmod +x nostrpost.shAt this point, assuming you already added some relays, we can do a testrun:
bash ./nostrpost.shIt should echo the quote it's picked then show you the progress of publishing to each relay.
If you look the bot up on your Nostr client of choice using the public key we printed earlier, assuming you have the same relays added, it should pop up and you can see it for yourself and even follow it!
And finally, assuming the test run went well, all you need to do is set the
crontabso it runs automatically:bash crontab -eScroll to the bottom of this file and just add:
bash @hourly /home/nostrbot/nostrpost.sh >> /home/nostrbot/nostrbot.logThis will run your script every hour, on the hour (e.g. exactly 7pm) and write the results to a log file, which is useful for debugging if something breaks at any point.
At this point you're done. Add more relays if you want, wait for the next hour, and it should automatically post another quote!
If you found this helpful feel free to follow me on Nostr at the pubkey below and, if you're feeling generous, zap me at
xanny@xanny.family!npub17rlc0emedw5xljztfqrmykjaacsx6ujvdas64zznjadrnhhwlavq4jjtggPV!
-
 @ c753997e:9fe20adc
2023-04-07 20:24:01
@ c753997e:9fe20adc
2023-04-07 20:24:01HUMANS 08 April 2023 By DAVID NIELD
Long before the counter-culture revolution of the 1960s, Bronze Age Europeans were tuning in and dropping out on hallucinogenic drugs.
While archaeologists have long had their suspicions, a new analysis of hair recovered from a 3,600-year-old burial site in Spain provides the first direct evidence of drug use among the inhabitants of ancient Europe.
Discoveries of remains of psychoactive plants and preparation tools and depictions in art have hinted at European cultures seeking altered states of consciousness. But finding traces of the compounds themselves in samples of body tissue, such as hair, carries far more weight.
Only hair doesn't tend to stick around as long as bones and teeth. Researchers from the University of Valladolid and the Autonomous University of Barcelona in Spain, and the University de Chile, were fortunate in uncovering samples that had been unusually well preserved as part of a burial ritual.
Testing the hair with advanced particle processing techniques, the researchers identified key traces of atropine and scopolamine, which can both induce hallucinations and altered sensory perception. There was also evidence of ephedrine, a stimulant known to increase excitement and alertness.
Hair samples One of the hair samples, with small rock fragments. (P. Witte) "The results furnish direct evidence of the consumption of plant drugs and, more interestingly, they reveal the use of multiple psychoactive species," the researchers write in their published paper.
Nightshade plants such as mandrake (Mandragora autumnalis), henbane (Hyoscyamus albus), thorn apple (Datura stramonium), and joint pine (Ephedra fragilis) are the most likely sources for the drugs, the researchers say. These plants would have been available in the area where the burial site is, and have been found at other similar sites.
The researchers think that the drugs may have been administered as part of some kind of ritual, and were probably supplied by a shaman: an ancient person of medicine and religion who would have extensive experience in the preparation and delivery of the plant materials.
"Considering the potential toxicity of the alkaloids found in the hair, their handling, use, and applications represented highly specialized knowledge," write the researchers.
"This knowledge was typically possessed by shamans, who were capable of controlling the side effects of the plant drugs through an ecstasy that made diagnosis or divination possible."
The rare hair samples were found in the Es Càrritx cave in Menorca. While more than 200 people were buried here, samples of hair were only taken from a few of them: the hair was dyed red as part of their burial ritual and placed in special containers at the rear of the cave chamber, although it's not clear why.
There's also something interesting about the containers. Made of wood and antler, they feature concentric circles that could well have been painted to represent eyes – perhaps hinting that the hallucinogens they hold might alter a person's vision or consciousness. Similar designs have been seen at other sites.
wooden piece with concentric circles inscribed Part of the wooden container holding the hair, with inscribed circle 'eyes'. (.Guerra‑Doce et al., Scientific Reports, 2023) Part of the reason the hair samples were stowed away may have been to preserve local traditions following a cultural shift that seems to have occurred around the same time, according to the research team. Now, more than three millennia later, those traditions have indeed been discovered again.
"These results confirm the use of different alkaloid‑bearing plants by local communities of this Western Mediterranean island by the beginning of the first millennium BCE," write the researchers.
The research has been published in Scientific Reports.
-
 @ 9a576bd9:538775f4
2023-04-07 17:57:05
@ 9a576bd9:538775f4
2023-04-07 17:57:05Pour comprendre la volonté d'avoir des relais Nostr qui fonctionnent sur le mixnet retrouvez l'article Nostr x Nym qui détail nos motivations.
Le fait d'avoir un relai Nostr qui fonctionne à travers le mixnet va permettre de protéger les utilisateurs comme par exemple que leur fournisseur d'accès Internet puissent savoir qu'ils utilisent Nostr, à quelle fréquence et vers quel relai, ou encore d'avoir le risque de vous voir demander toutes les adresses IP qui contactées votre serveur. Le système proposé ici est fonctionnel avec tous les relais actuels, il est encore en phase de développement, donc des bugs ne sont pas exclus.
Voici l'architecture finale résumée
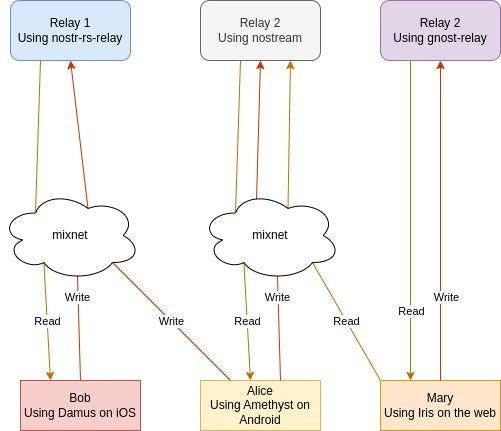
Plusieurs composants sont nécessaires à installer pour arriver à cela:
-
Un relai, une liste très complète est disponible ici. Pour cet article, nostr-rs-relay sera utilisé car il est très simple, utilise SQLite et tourne facilement sur Docker
-
nym-client, qui va faire le lien entre votre relai et le mixnet
-
nostr-nym, pour "traduire" les requêtes reçu du mixnet et les envoyer au relai
Relai
Si Docker n'est pas installé vous pouvez retrouver les informations ici: https://docs.docker.com/get-docker/. Docker n'est pas indispensable pour qu'un relai fonctionne mais simplifie grandement les explications
Il faut maintenant démarrer le relai
bash mkdir data docker run -it -p 7000:8080 \ --mount src=$(pwd)/data,target=/usr/src/app/db,type=bind \ scsibug/nostr-rs-relaySi tout se passe bien, voilà la sortie qui devrait apparaitre. Le relai est maintenat démarré
Nym-client
Le nym-client est le composant qui va permettre de communiquer avec le mixnet
Le téléchargement se passe sur Github: https://github.com/nymtech/nym/releases, il faut rechercher une release appelé "Nym Binaries v1.1.x". Dans cet exemple, la version [Nym Binaries v1.1.14](https://github.com/nymtech/nym/releases/tag/nym-binaries-v1.1.14) est utilisé
```bash
Download the nym-client and give exec permission
wget https://github.com/nymtech/nym/releases/download/nym-binaries-v1.1.14/nym-client -O nym-client && chmod +x nym-client
Init the nym-client
./nym-client init --id nostr-relay --latency-based-selection
Start the nym-client
./nym-client run --id nostr-relay ```
Si tout s'est correctement le nym-client devrait maintenant afficher son nym-client id. C'est cet élément qui va permettre d'identifier le relai et l'atteindre dans le mixnet
La fenêtre doit rester ouverte
Nostr-nym
C'est cet élément qui va faire le lien entre le mixnet et le relai. Il va se charger d'établir une connexion avec le nym-client, écouter les messages envoyé par les clients, transmettre les evénements Nostr et renvoyer la réponse ou notifier les clients.
Pour plus de flexibilité,
pipenvest utilisé. Pour l'installer pip est nécessaire:pip install pipenv```bash
clone the repo
git clone https://github.com/notrustverify/nostr-nym cd nostr-nym
start pipenv shell and install dependencies
pipenv shell pipenv install ```
Résultat final, la fenêtre doit rester ouverte
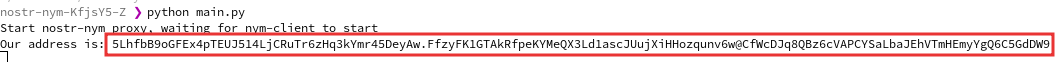
Le relai est maintenant accessible via le mixnet, dans cet exemple c'est à l'adresse (=nym-client id)
5LhfbB9oGFEx4pTEUJ514LjCRuTr6zHq3kYmr45DeyAw.FfzyFK1GTAkRfpeKYMeQX3Ld1ascJUujXiHHozqunv6w@CfWcDJq8QBz6cVAPCYSaLbaJEhVTmHEmyYgQ6C5GdDW9qu'il peut être atteintLa section suivante explique comment tester le relai, un client nostr simple à été développé.
Test
Maintenant que tous les éléments sont en place, il est possible de tester que la création de note et la souscription à des nouveaux fonctionne.
Dans le dépôt précédemment cloné, un dossier comporte un client Nostr léger compatible avec le mixnet. Le démarrage d'un autre nym-client est nécessaire
```bash
Init the nym-client
./nym-client init --id nostr-client --latency-based-selection --port 1978
Start the nym-client
./nym-client run --id nostr-client ```
Un relai public est disponible sur le mixnet pour tester facilement le fonctionnement
2gc9QidpXs4YGKmphinsDhWTHxdy2TZgWYWz2VenN5jL.dkwwJqS1zXa9BuPAFdniRN2HxFvAbTybAmrUHGAT5KV@2BuMSfMW3zpeAjKXyKLhmY4QW1DXurrtSPEJ6CjX3SEh```bash
navigate to nostr client
cd nostr-nym/client
start pipenv shell and install dependencies
pipenv shell pipenv install ```
Publication d'un nouvel événement
bash python main.py --cmd text-note --message "Hello world (from the Nym mixnet)" --relay <nym-client of relay started before> --nym-client ws://127.0.0.1:1978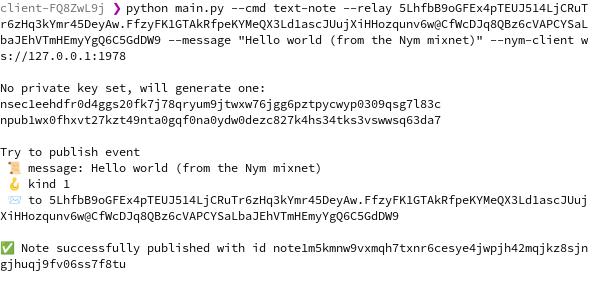
Souscription aux nouveaux événements
bash python main.py --cmd subscribe --relay <nym-client id of relay started before> --nym-client ws://127.0.0.1:1978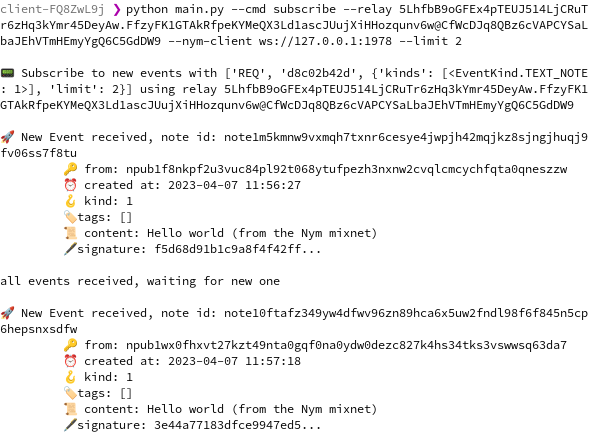
Filtrage des événements
bash python main.py --cmd filter --authors <npub to filter> --relay <nym-client id of relay started before> --nym-client ws://127.0.0.1:1978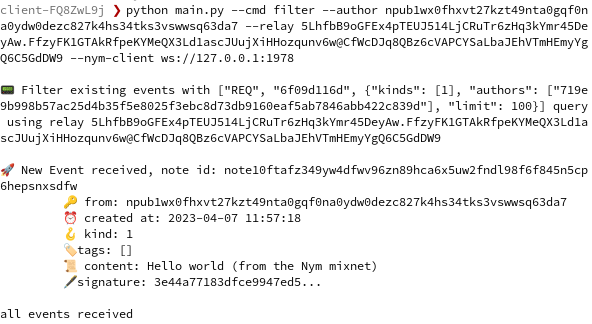
Conclusion
Le relai est maintenant accessible via le mixnet. C'est un premier pas vers plus de vie privée et de protection pour les relais.
Un futur article présentera les bénéfices de mettre en place une telle infrastructure pour Nostr ainsi que l'intégration du nym-client dans un client existant comme iris.to, snort.social, damus sur iOS ou encore Amethyst sur Android
Ressources:
Nostr-nym
Nym
A propos de No Trust Verify
Nous sommes membres de la #VerifyValley. Nous soutenons le réseau de Nym Technologies et y contribuons depuis le testnet. Nous sommes heureux de le renforcer avec nos mixnodes et nos gateways.
Développeur de pastenym.ch et isnymup.com
✅ Hébergé en Suisse
✅ Commission garantie : 5%
✅ Bande passante : 10 Gbit/sIdentity keys:
NTV1 : APxUbCmGp4K9qDzvwVADJFNu8S3JV1AJBw7q6bS5KN9E
NTV2 : 4yRfauFzZnejJhG2FACTVQ7UnYEcFUYw3HzXrmuwLMaR
NTV3 : ESPa5xnwZ7BebSX9SGmUbeYgNtkUeJo8PtbBx7JhzEHA
N’hésitez pas à nous contacter :
| Site officiel | Twitter | Telegram | Linkedin | Matrix |
-
-
 @ 9a576bd9:538775f4
2023-04-07 17:56:22
@ 9a576bd9:538775f4
2023-04-07 17:56:22To understand the will to have Nostr relays working on the mixnet, please read the article Nostr x Nym which details our motivations.
The fact of having a Nostr relay that works through the mixnet will allow to protect the users as for example that their ISP can know that they are using Nostr, how often and to which relay, or to have the risk to see you asking for all the IP addresses that contacted your server. The system proposed here is functional with all current relays, it is still in development phase, so bugs are not excluded.
Here is the final architecture summarized
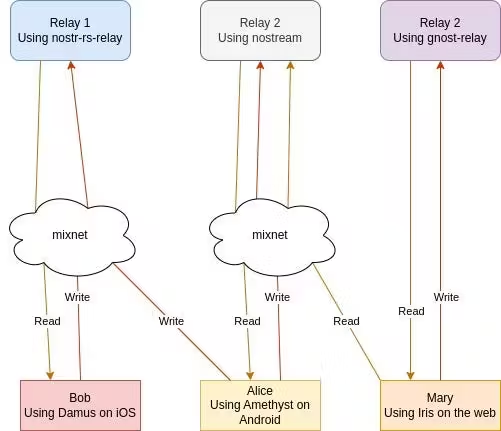
Several components are necessary to install to achieve this:
-
A relay, a very complete list is available here. For this article, nostr-rs-relay will be used because it is very simple, uses SQLite and runs easily on Docker
-
nym-client, which will make the link between your relay and the mixnet
-
nostr-nym, to "translate" the requests received from the mixnet and send them to the relay
Relay
If you do not have Docker installed you can find the information here: https://docs.docker.com/get-docker/. Docker is not essential for a relay to work but it greatly simplifies the explanations.
Now we have to start the relay :
plaintext mkdir data docker run -it -p 7000:8080 \ --mount src=$(pwd)/data,target=/usr/src/app/db,type=bind \ scsibug/nostr-rs-relayIf all goes well, here is the output that should appear. The relay is now started.
Nym-client
The nym-client is the component that will allow to communicate with the mixnet.
The download is on Github: https://github.com/nymtech/nym/releases, you have to search for a release called "Nym Binaries v1.1.x". In this example, the version Nym Binaries v1.1.14 is used.
```plaintext
Download the nym-client and give exec permission
wget https://github.com/nymtech/nym/releases/download/nym-binaries-v1.1.14/nym-client -O nym-client && chmod +x nym-client
Init the nym-client
./nym-client init --id nostr-relay --latency-based-selection
Start the nym-client
./nym-client run --id nostr-relay ```
If everything is correct the nym-client should now display its nym-client id. This is the element that will identify the relay and reach it in the mixnet.
The window must remain open.
Nostr-nym
It is this element that will make the link between the mixnet and the relay. It will establish a connection with the nym-client, listen to the messages sent by the clients, transmit the Nostr events and send back the answer or notify the clients.
For more flexibility,
pipenvis used. To install pip is necessary:pip install pipenv```plaintext
clone the repo
git clone https://github.com/notrustverify/nostr-nym cd nostr-nym
start pipenv shell and install dependencies
pipenv shell pipenv install ```
End result, the window must remain open.
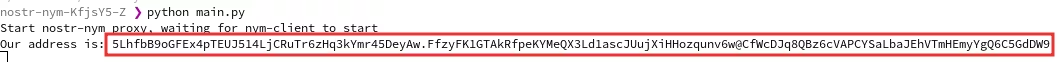
The relay is now accessible via the mixnet, in this example it is at the address (=nym-client id)
5LhfbB9oGFEx4pTEUJ514LjCRuTr6zHq3kYmr45DeyAw.FfzyFK1GTAkRfpeKYMeQX3Ld1ascJUujXiHHozqunv6w@CfWcDJq8QBz6cVAPCYSaLbaJEhVTmHEmyYgQ6C5GdDW9that it can be reached.The following section explains how to test the relay, a simple nostr client has been developed.
Test
Now that all the elements are in place, it is possible to test that creating notes and subscribing to new ones works.
In the previously cloned repository, there is a folder with a mixnet-compatible light Nostr client. Starting another nym-client is necessary.
```plaintext
Init the nym-client
./nym-client init --id nostr-client --latency-based-selection --port 1978
Start the nym-client
./nym-client run --id nostr-client ```
A public relay is available on the mixnet to easily test the operation :
2gc9QidpXs4YGKmphinsDhWTHxdy2TZgWYWz2VenN5jL.dkwwJqS1zXa9BuPAFdniRN2HxFvAbTybAmrUHGAT5KV@2BuMSfMW3zpeAjKXyKLhmY4QW1DXurrtSPEJ6CjX3SEh```plaintext
navigate to nostr client
cd nostr-nym/client
start pipenv shell and install dependencies
pipenv shell pipenv install ```
Publication of a new event.
plaintext python main.py --cmd text-note --message "Hello world (from the Nym mixnet)" --relay <nym-client of relay started before> --nym-client ws://127.0.0.1:1978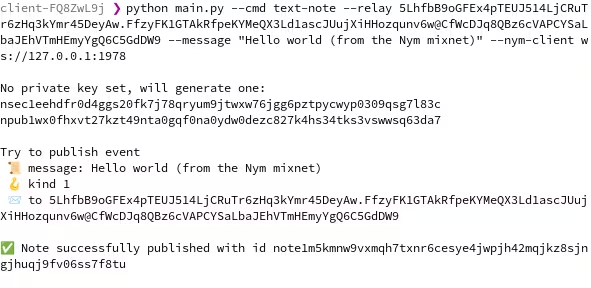
Subscription to new events.
plaintext python main.py --cmd subscribe --relay <nym-client id of relay started before> --nym-client ws://127.0.0.1:1978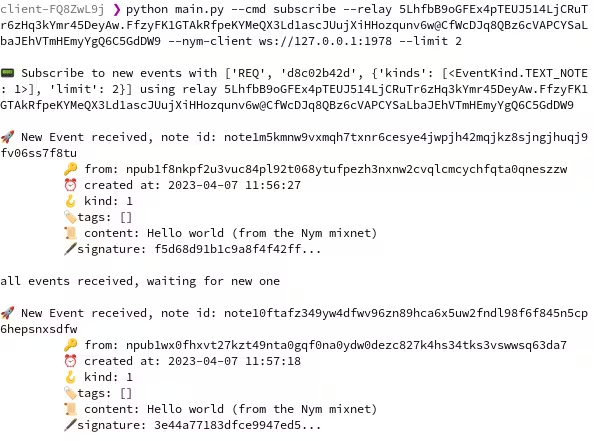
Event filtering.
plaintext python main.py --cmd filter --authors <npub to filter> --relay <nym-client id of relay started before> --nym-client ws://127.0.0.1:1978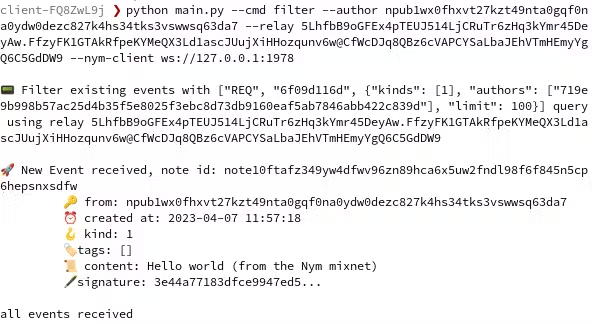
Conclusion
The relay is now accessible via the mixnet. This is a first step towards more privacy and protection for relays.
A future article will present the benefits of setting up such an infrastructure for Nostr as well as the integration of the nym-client in an existing client such as iris.to, snort.social, damus on iOS or Amethyst on Android.
Resources:
Nostr-nym
Nym
About No Trust Verify
We are members of the #VerifyValley. We support the Nym Technologies network and contribute to it since the testnet. We are happy to strengthen the mixnet with our mixnodes and our gateways.
Developer of pastenym.ch and isnymup.com
✅ Hosted in Switzerland
✅ Guaranteed commission: 5%.
✅ Bandwidth: 10 Gbit/sIdentity keys:
NTV1 : APxUbCmGp4K9qDzvwVADJFNu8S3JV1AJBw7q6bS5KN9E
NTV2 : 4yRfauFzZnejJhG2FACTVQ7UnYEcFUYw3HzXrmuwLMaR
NTV3 : ESPa5xnwZ7BebSX9SGmUbeYgNtkUeJo8PtbBx7JhzEHA
Do not hesitate to contact us:
-
-
 @ f6578e56:a44078c1
2023-04-07 13:15:29
@ f6578e56:a44078c1
2023-04-07 13:15:29KYC or “Know Your Customer” is a procedure to first identify and then verify user identities. Pi Network utilizes a proprietary KYC solution to scalably verify the identity of millions of Pioneers all over the world to onboard them to the Mainnet blockchain and ecosystem.
Not only is KYC important for the integrity of the network and compliance, but also it makes sure that it is fair for all human Pioneers who have been honestly mining in their own accounts. Achieving this goal is critical because real verified humans on Pi will contribute to the robustness of the network while encouraging the development of various apps for a utility-based ecosystem.
Over the past year, the Pi KYC software has been continuously updated to allow more and more Pioneers to apply, address many different corner cases in the application process, and verify identities of millions of Pioneers to prepare them for their Mainnet migration, while safeguarding the integrity of the network. The KYC progress of the whole network will remain a top priority of the community including the Core Team, Validators and Pioneers, and one of the two primary goals of the Enclosed Network period in the Mainnet Phase.
In the recent celebration of Pi Day, a major software update in the KYC app was also released and introduced in the Pi Day 2023 announcement. We’re providing the following FAQs to elaborate on the Pi Day KYC announcement and overall assist Pioneers on their KYC journey.
KYC FAQs
1. Do you still need to get a KYC slot randomly assigned by the system?
No, anyone except the two scenarios below should be able to visit the KYC app via Pi Browser and start your KYC application without waiting for an invitation. The invitation-based KYC slots assignment was only used in the past, and the process has been updated to allow anyone to start.
Newly created accounts will not be able to immediately apply for KYC verification, until after mining for 30 days (no need to be consecutive). This helps the network prioritize KYC validation resources for more committed human Pioneers who also have mined enough balance to make sense to go through KYC and migrate to Mainnet.
A very small proportion of accounts, identified by the algorithms as highly likely fake accounts or accounts that have violations, will not be eligible to KYC. If such account owners think that there is a mistake by the algorithms, they should submit their username for further investigation and potential proof of otherwise by filling in this form here: https://minepi.com/kyc-application-access. Depending on what we receive, we can investigate further.
2.When a KYC slot is opened up for you, will you still get the "KYC slot" popup notification when you start a new mining session?
The KYC popup notification should not be used as the only means by which Pioneers know whether they are eligible to start KYC application or not, although they will likely get a “KYC slot” popup. Pioneers should directly check their KYC eligibility on the KYC app in the Pi Browser (KYC.PI). You can simply open the Pi Browser and navigate to the KYC application. Please use the popup notification as a reminder rather than an invitation.
3.Now that Pi KYC is open for all, how can I apply for KYC?
Downloading the Pi Browser is required to apply for KYC. You can access KYC through the Pi KYC app in the Pi Browser. Make sure to have your relevant identification documents ready!
Pioneers are encouraged to directly check your KYC eligibility on the KYC app in the Pi Browser.
4.KYC Tentative Approval: What does it mean? What is necessary to pass? How long will that take?
The Tentative KYC program, which does not apply to the majority of the network, requires additional verification checks before the Pioneer can fully pass KYC. Tentative KYC approval does not equal full KYC approval, and thus will not yet unlock functionalities (e.g. becoming a Validator, or migrating to the Mainnet) requiring full KYC approval until the additional checks confirm its full KYC approval. However, tentative KYC approval gets the account much closer to full approval.
The reason for the selective Tentative KYC program is to ensure the integrity of the network—cautiously allowing as many real human Pioneers as possible to pass KYC, while catching and preventing as many fake and bot accounts as possible. Not only is this important for the network, but it’s also fair for all human Pioneers who have been honestly mining in their own accounts.
The specific additional verification steps may vary depending on the individual case, and the time it takes to complete them can vary, as well. Factors that can impact the timing include the volume of KYC applications being processed, availability of human validators of the region, complexity of the application, and types of additional checks applied to the tentative KYC case.
5.When the KYC status is "Tentative approval," how long will it take for it to be final "KYC passed"?
The duration of the Tentative Approval status is on a case-by-case basis and depends on the extent and types of additional verifications needed. One of the priorities of Q2 2023 for the KYC app is to iterate and apply such additional checks on the tentative KYC cases.
**6.When KYC status is "Tentative approval," can migration to Mainnet happen? **
No, you need to fully pass the KYC to be able to migrate to the Mainnet.
**7.When KYC is submitted, what screens can you get in the KYC app? **
After submitting the KYC application, the Pioneer can expect to see a few different screens in the KYC app. Pioneers may see a screen indicating that the application is “review in progress”. If the KYC application is approved tentatively (meaning it was accepted by Validators pending additional checks), the Pioneer may see a “tentative approval” screen.
If the additional checks further confirm the authenticity of the data and account, a Pioneer will see the “KYC passed” screen. For the majority of applications that are outside of the Tentative KYC program, they will directly see the “KYC passed” screen without the additional checks, if they are accepted
8.As per previous announcements, a submitted KYC application may be approved within 15 minutes if everything is submitted correctly and no name appeal is made. Is this still the case?
Yes, this is still the case as long as Pioneers have completed the required fields correctly and the availability of the human Validators is abundant in the country or region.
9.When will it be possible for KYC Validators to review name change appeals?
For Pioneers who appealed to change their account name (for small name updates), their appeals are either resolved by only machine automation or require the help from human validators to resolve. The first case has already been in place unblocking such applications to proceed in their KYC process. For the second case, human validators will likely be able to review name change appeals in Q2 this year, after the priorities of additional checks on tentative KYC applications and validators performance analysis.
10.My KYC is approved but not reflected in Mainnet Checklist Step 6. When can I proceed and start migration?
The Core Team is aware of this issue affecting some users and are working on resolving the data synchronization issue on the Mainnet Checklist in Q2 this year. In general, always rely on the Pi KYC app for the most accurate KYC status.
11. Overall, why is Pi Network requiring KYC before Mainnet Migration?
The vision of Pi Network is to build an inclusive and the most widely-distributed digital currency and ecosystem for all Pioneers. Pi Network’s mining mechanism is social-network based and relies on contributions of real Pioneers. Therefore, Pi has a strict policy of one account per person.
This requires a high degree of accuracy to establish that members in the network are genuine human beings, preventing individuals from being able to hoard Pi by creating fake accounts unfairly. KYC thus helps ensure the true humanness of the network in addition to compliance with anti-money laundering and anti-terrorism regulations.
Only people who passed the Pi KYC can migrate to the Pi Mainnet. The current Enclosed Mainnet period gives the community time to KYC and migrate to the Mainnet blockchain—a identity-verified, compliant and utilities-driven ecosystem where Pioneers can begin to use Pi for real goods and services.
-
 @ 46fcbe30:6bd8ce4d
2023-04-07 13:10:59
@ 46fcbe30:6bd8ce4d
2023-04-07 13:10:59I'm #spending a lot of time on nostr and my mind is regularly blown by how content is separated or freed from design and UI there. People share "tweets" using one software and others read them in a dozen of other prominent or hundreds of nascent clients, each showing aspects differently. But there are also long-form clients that feel more like substack or medium and others focus on media content and feel more like Instagram and the clients overlap in what content they show:
A Bounty is a long-form post is a social post
For example a page focused on nostr development bounties shows bounties like this:

... but they are a subset of long-form content, so pages focused on long form content like Habla.news show them, too but like this:
 .
.Notice how Habla supports replying, zapping and liking ... and does list additional pledges.
But as the content is not bound to just Habla.news, other instances of this open source software by nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg also show them.
But these replies are the Twitter-like "kind 1" messages that make it into your feed on social clients like Snort or Nostrgram and these clients also try to show you what the comments were in reply to.
Nostrgram and others now support long form content and show what originated in a bounty platform really nicely:

Notice how other bounty pledges are not listed but you can suddenly zap the bounty post - and zaps do work of course without the website taking a cut.
What could possibly go wrong?
But of course this also has its down side. Now, the author of the website suddenly has to deal with unexpected content.
Here is how Snort currently deals with Bounty posts:

Will all public content migrate to Nostr?
In many cases liberating the content makes sense but it currently has its limits. Reasons to use nostr for your project's content might be: * Actual concerns about censorship: If the content must not get lost if your project gets into legal trouble, nostr is for you * Tap into the broader nostr ecosystem to give your project visibility: If nostr social talking about and liking your content like bounties is helpful exposure, nostr might be for you * Open Standards and seamless login: If you want people to bring their established identity to your platform, nostr might be for you. * Proven transparency: If your site sparks debates, you might "moderate" some content for your users but with other nostr clients anybody can expose your acts of moderation as censorship if you judged poorly. That keeps you honest and users can know if they are being spoon-fed your version or not.
But some projects might need more control than what nostr currently provides: * If you need tight control of the user experience, nostr might not be for you. This might apply if you target minors for example. * If your project has "haters" with big incentives to sabotage your project, nostr is probably not for you. Monsanto, Ku Klux Klan, ... come to mind. * Shared content ownership: We don't know yet how to do Wikipedia on nostr. If you are dealing with content that has multiple authors, nostr is not yet for you.
Why did I write this article?
I'm exploring how to improve trust in my project WalletScrutiny.com. Together with the Bitcoin Design Community which you can find on GitHub, Slack, Substack, Dog App and also here on Nostr (nostr:npub13s5mxgws70rpxsug96jfvglggackjrxs2ehypwg0prjaxsek42sqd9l03e) we've been brainstorming on how to prove transparency with nostr and we developed a nostr plugin that allows Nostriches to comment on wallet reviews but that leaves us in the awkward situation that the comments reply to some non-nostr content which doesn't really help with our content going viral.
I'm now thinking that all the reviews should be nostr long-form content. WalletScrutiny being open source would allow anybody to copy the content anyway but with the content being on nostr, the discoverability and transparency would greatly improve.
WalletScrutiny would only show reviews by approved authors but would instantly have a great incentive to open up to reasonable contributions - or turn obsolete if another team does a better job.
-
 @ c753997e:9fe20adc
2023-04-06 17:37:36
@ c753997e:9fe20adc
2023-04-06 17:37:36By Yarno Ritzen and Al Jazeera Investigative Unit Published On 6 Apr 2023
To many people around the world, Switzerland is synonymous with the Alps, fine chocolates and designer watches.
To those in the bling business, the European nation has another identity: it is the world’s largest exporter of gold. In 2021, Switzerland sold nearly $87bn of the precious metal, almost as much as the next three biggest exporters – the United Arab Emirates (UAE), the United Kingdom and the United States – combined.
Switzerland imports almost all of that gold from other nations, refined and branded, and then exports it around the world where jewellery and other accessories made from the precious metal adorn the necks, arms and ankles of millions of people.
And it’s the same with the UAE and the UK. The top three gold exporters do not figure in the world’s top gold producers. They do not mine much, if any, of the metal. Yet they are the biggest hubs of the industry.
That trade model is at the heart of a mechanism smugglers and money launderers use to wash dirty cash and sell gold from dubious sources, Gold Mafia, a four-part investigation by Al Jazeera’s Investigative Unit (I-Unit), reveals.
Undercover reporters infiltrated some of Southern Africa’s biggest gold-smuggling and money-laundering gangs. The investigation showcases how it is next to impossible to determine the true origins of gold bought by regular customers, whether in New York and London or New Delhi and Karachi.
That quality is precisely what makes the metal a priceless asset for criminals.
The ‘Swiss gold’ stamp Al Jazeera’s undercover reporters, pretending to be Chinese criminals, were offered a range of options to launder more than $100m of dirty cash by multiple smuggling gangs using Zimbabwean gold.
The precious metal is Zimbabwe’s biggest export but the taint of Western sanctions against government officials over human rights violations makes it difficult for the country to sell gold internationally.
Enter the smugglers, who ferry Zimbabwean gold abroad, and return with the unaccounted wealth of launderers – ostensibly the proceeds from the sale of the gold. In reality, the earnings from the sale of the gold are wired to the bank accounts of the launderers, who now have seemingly legitimate money.
Kamlesh Pattni and Ewan Macmillan, who run two major rival gold-smuggling gangs out of Zimbabwe, both made clear to Al Jazeera reporters that they – and others in their field – had one preferred destination for the gold their couriers carry out of the Southern African nation: Dubai.
“It all comes out of Dubai. It’s all Dubai, Dubai, Dubai, Dubai,” Macmillan said.
Pattni and Alistair Mathias, Macmillan’s business partner, independently advised Al Jazeera reporters to set up front companies in Dubai. Once the gold from Zimbabwe arrives in the Emirati city, they said, it is melted in refineries there and rebranded as Dubai gold. Dubai is the UAE’s gold hub.
But the process of hiding the origins of the gold does not always end there, said experts. In recent years, the United Nations and other global bodies and nonprofits have raised questions about the due diligence practices employed in Dubai’s gold industry. So another layer of disguise around the original source of the gold helps.
“The Dubai gold would for instance be exported either to London or to Switzerland because you want the stamp ‘Swiss Gold’ on it,” anti-corruption and money laundering expert Mark Pieth told Al Jazeera. “Then, of course, every bank in the world will buy it.” Pieth is a former president of the Basel Institute on Governance.
The UAE exports the biggest chunk – 23 percent – of its gold to Switzerland, where smugglers like Mathias also have companies.
‘Practically brand new gold’ As a partner at global accounting firm Ernst & Young 10 years ago, Amjad Rihan was responsible for auditing Dubai-based Kaloti – at the time one of the largest gold refineries in the world.
He found that some of that gold had come from Darfur, which has witnessed the worst horrors of Sudan’s civil war. “That’s the very gold we were auditing,” Rihan told Al Jazeera.
Rihan subsequently won a court case in the UK against Ernst & Young, which judges ruled had forced him out of the company because it did not want to address the red flags he raised about Kaloti.
In 2015, the Dubai Multi Commodities Centre (DMCC), the city’s main licensing authority for commodities trade, acted against Kaloti, removing the company from Dubai’s list of approved gold refiners.
In 2020, UN experts reported that gold from another conflict zone, the Democratic Republic of the Congo (DRC), also ended up in the UAE. In Dubai, the refining process removes traces of its origins, making it more attractive to other gold hubs around the world.
“Gold that comes to refiners, once it’s refined, it’s practically brand new gold,” Rihan said.
That makes the origins of the gold untraceable and perfect for criminals wanting to hide the source of their wealth. A 2020 report by Global Witness showed that the world’s largest gold refinery, Switzerland’s Valcambi, had previously bought gold from Kaloti that almost certainly originated in Sudan.
Al Jazeera’s investigation showed how smuggling gangs help criminals turn dirty cash into seemingly legitimate money by selling Zimbabwean gold. But sometimes, said experts, gold is also valuable in itself, in what Pattni described as an “investment”.
“[The value of] gold may go up and down, but it’s always at the top of our list of items that we want and that goes back as far as we can find records,” former US Federal Bureau of Investigation (FBI) investigator and anti-corruption expert Karen Greenaway explained to Al Jazeera.
Meanwhile, gold-smuggling gangs also use Switzerland as a safe haven for their ill-gotten wealth, the investigation showed.
Zimbabwean millionaire Simon Rudland owns one of Southern Africa’s biggest cigarette companies, Gold Leaf Tobacco. South African authorities have accused him of skirting taxes by selling cigarettes on the black market. Rudland also smuggles Zimbabwean gold to Dubai through a team of couriers.
Al Jazeera’s investigation revealed how Mohamed Khan, a South African money launderer, funnels millions of dollars of Rudland’s money abroad as payments for nonexistent imports using fake invoices and shell companies run by Rudland’s business partners.
Among those front companies is Velmont Valley, which received nearly $16m in a Swiss bank account from Gold Leaf Tobacco in May 2017, according to documents accessed by Al Jazeera.
Why this matters Because gold gets refined over and over again and moves all around the world, it is hard to be certain if gold bought on the open market is ethically and legally clean, said experts – and that its money trail is free of laundering and crime.
A watch might have been made with pieces of gold from a conflict region, or a bar of gold was melted with parts of smuggled gold.
The never-ending loop of melting, selling, buying and melting again obfuscates any trace of the gold’s origin, making it particularly difficult for law enforcement agencies to build evidence against suspected smugglers.
Nonprofits, such as Global Witness and Corruption Watch, and organisations, such as the International Monetary Fund (PDF) and the OECD, have called for increased scrutiny of gold, like the Kimberley Process for the diamond industry. The Kimberley Process has tried to prevent the sale of blood diamonds, plundered from conflict zones. But so far, there is no similar regulation in the gold industry.
“When you talk about gold, some people actually think that ‘oh, this doesn’t affect us, this is just for the rich people or for a small segment of society that care about gold’,” Rihan, the former Ernst & Young partner said. “But the reality is, gold enters our lives and we interact with gold all the time, pretty much on a daily basis, because even the phones and the laptops that we use, they use gold.” Many everyday electronic devices use small quantities of gold in their circuit boards.
“We all have a responsibility to ensure that we receive clean gold and we also have the right as people to know that the gold we use is clean.”
DMCC, the Dubai commodities licensing authority, told Al Jazeera that it is not a regulator but provides companies with the necessary licenses to operate within the Dubai Free Zone using a “clear, comprehensive and robust compliance process”. It also emphasised that it was not given an opportunity to provide evidence or make representations during the court action in London between Amjad Rihan and Ernst & Young. It denied allegations made against it in those proceedings, and strenuously denied being involved in money laundering or criminal activity of any kind.
Kamlesh Pattni denied involvement in any form of money or gold laundering and told us that his activities in the UAE were entirely lawful. Alistair Mathias said that he had never laundered money or gold or traded illegal gold and that he had never had any working relationship with Ewan Macmillan, who did not respond to Al Jazeera’s request for comment.
Simon Rudland said that the allegations against him formed part of a smear campaign by an unidentified third party. He denied any involvement in the sale of illicit cigarettes, in gold or other smuggling and in sanctions busting. He accepted that he had had dealings with Mohamed Khan, who he agreed “appeared” to be a money launderer, but he denied that any form of money laundering had been undertaken for him.
Gold Leaf Tobacco denied any involvement in money laundering or the trade in illegal gold. It said no “untaxed” or “illegal” cigarettes could be “attributed” to Gold Leaf. It said Gold Leaf’s limited transactions with Mohamed Khan had always been lawful and proper – though it accepted that Khan was a money launderer.
Mohamed Khan told us that all allegations against him were false and were based on speculation, conjecture and manufactured and doctored evidence. He confirmed that Gold Leaf was a client of his businesses but he denied having any involvement in money laundering or other criminal activity.
Ernst & Young said that it was the work of its staff that identified and reported irregularities, resulting in sanctions and changes to the sourcing of precious metals and the regulation of refiners in Dubai.
Kaloti denied all wrongdoing, including in relation to those matters that arose in the course of the Ernst & Young audit.
Other entities mentioned in this article did not respond to Al Jazeera’s request for comment.
SOURCE: AL JAZEERA
-
 @ ce35f2f8:22931a55
2023-04-06 14:52:26
@ ce35f2f8:22931a55
2023-04-06 14:52:26Proprietary software refers to software that is owned by a particular company or individual, and its source code is not publicly available. This is in contrast to open-source software, which allows anyone to access and modify its source code. While proprietary software has its advantages, it also has some downsides. In this article, we will explore the pros and cons of proprietary software.
Pros of Proprietary Software:
Quality Control: Proprietary software developers have complete control over the code and the development process. This means that they can ensure that the software is thoroughly tested, and any bugs or security vulnerabilities are fixed before it is released to the public. As a result, proprietary software is generally more stable and reliable than open-source software. Support and Training: Proprietary software vendors offer comprehensive support and training programs to help users get the most out of their software. This is particularly beneficial for businesses that rely on the software to run their operations. Proprietary software vendors often provide dedicated support staff to help users troubleshoot issues and ensure that the software is working correctly. Competitive Advantage: Proprietary software can give a company a competitive advantage by providing unique features and capabilities that are not available in open-source alternatives. This can be particularly important for businesses that rely on software to provide a competitive edge in their industry.Cons of Proprietary Software:
Limited Flexibility: Proprietary software is usually designed to work in a specific way and cannot be easily modified to suit individual needs. This can be a disadvantage for businesses that require a high degree of customization or flexibility from their software. Higher Costs: Proprietary software is often more expensive than open-source alternatives. This is because the development costs are borne entirely by the vendor, and they need to recoup those costs through licensing fees. This can be a significant expense for businesses that require multiple licenses or need to upgrade their software regularly. Dependency: Proprietary software can create a dependency on the vendor, as users are reliant on the vendor to provide updates and support. If the vendor goes out of business or decides to stop supporting the software, users can be left stranded without access to critical functionality. Lack of Transparency: Proprietary software is not transparent, as users cannot access or modify the source code. This can make it difficult to identify security vulnerabilities or bugs, and users are reliant on the vendor to provide security patches and updates.In conclusion, proprietary software has its advantages and disadvantages. It can provide a high level of quality control, support, and competitive advantage, but it also comes with higher costs, limited flexibility, and a potential dependency on the vendor. When considering whether to use proprietary software, it is important to weigh the pros and cons carefully and evaluate the specific needs of your business or organization.
-
 @ 883fea4c:596bbc39
2023-04-06 14:16:57
@ 883fea4c:596bbc39
2023-04-06 14:16:57OK, Marty showed me this and I really like the idea. Going to try it for a bit with more notes and stuff than actual 'writing'
Onward!
AC
-
 @ 45c41f21:c5446b7a
2023-04-06 12:58:15
@ 45c41f21:c5446b7a
2023-04-06 12:58:15有一天晚上,我跟 chatGPT 聊天。聊了一些琐碎的话题,交换了一些不太重要的看法。聊到后面,窗外已经漆黑一片,我在想 chatGPT 是怎么理解我的,而我又是如何理解它的。人机对话对我来说,究竟是拿着纸笔的一种思考方式,类似脑海里的一场自言自语,还是我真的把 chatGPT 当作了某个重逢相谈的老友。
这么想着我突然想到了两句诗:“姑苏城外寒山寺,夜半钟声到客船”。这两句诗跟上面的问题有什么关系呢?我也不知道,我只是任由思绪向前游走。我想象一个满肚愁肠的诗人在一艘轻飘飘的乌船上,大概是斜卧在篷下,透过外面月亮漏出的一点光,瞥到了江边的枫树和渔火。四周静悄悄的,他听到船浆轻轻划过水面的声音。船夫也有点累了,任由乌船自行漂往岸边。
他们两个男人,从白天到夜晚刚刚经历一段冗长疲惫的水路,此刻马上靠岸,意味着即将结束共同面对的这段旅程。在旅程的前半段,他们两人肯定大声交谈,终于到了后面谈无可谈,便都默不作声。诗人在心里给一首未完的诗打腹稿,船夫则不时望着水面发呆。
请记住,当时没有手机和互联网,当你踏上一段路程时,你无法一边和熟悉的人保持联系,一边打量新的世界。你只能被动地接受所有陌生与未知。而这让旅途本身重新变得危险而敏感。
到了苏州城外的这一刻,夜深得与水面融为一体,除了船上的他们,万物似乎都深陷在睡眠中。诗人感到一股巨大的寂寞要推着他起身,上岸,回头与船夫告别。就在这时远处山上传来了一阵稀薄的钟声,那钟声彷佛藏在夜晚的微风里,稍不小心就会被弄破打散。
船夫慢慢支开乌船,他要趁着天色未亮原路回去。诗人转身走入异乡的黑夜里。周围的陌生感很快吞噬了刚才那阵寂寞,诗人呼出一口白气,夜凉如水,看着苏州城浸在黑夜里的残影,心里突然一阵轻松。也是在这时,他想到了两句诗应该怎么写。
这两句诗写于756年,唐朝天宝年号的最后一年。大概要再过一千年的时间,也就是十八世纪,地球的另一端才会出现另一个野心勃勃的意大利年轻人,名叫维柯。他的理想是建立一门真正的新科学,这门科学研究如何凭借想象力“进入”在时间或空间上远离我们社会的那些人的心灵——去考察他们创造了什么,他们曾经是什么,他们做过什么,他们遭受了什么苦难。
而实现这一目标的重要方法,恰好就是通过理解前人留给我们的那些作品。通过人类共通的同情心机制,找到某个时代的作品与之交流,从而理解那个时代的人们的所思所想所感。
这门新科学依赖这样一个简单的假设:人只能理解完全由他们所创造的事物。世界上有两种知识,自然科学是其中一种,但只有上帝能完全弄懂它。人类最多只能观察记录自然表面的规律而无法从本质上理解这些知识。因为自然不是由人类创造的。
而长期以来备受忽略的另一种知识,也就是今天人们谈论的人文学科,正是研究那些人类独创的事物的知识。我们能完全理解这些知识,因为是我们创造了这些事物。而这正是研究历史、文化、社会机制的意义。只有补充这部分知识,才能让人类更了解自己。
当一千多年前那两句诗从苏州城上空,飘到我的窗外时,我突然意识到我正如维柯所说的那样,靠着这两句诗,爬进了另一个时空里那个诗人的头脑中,共同感受了一种怅然的思绪。
我在他的乌船上,正如他在我的电脑里。
-
 @ df44246d:152ee13d
2023-04-06 12:26:05
@ df44246d:152ee13d
2023-04-06 12:26:05Sorry if you're reading this. Wanted to try editing funciton and NIP-23 Will edit later with content of message
Heading
Heading
Heading
import test print ("Hello World") -
 @ 3d32d22c:ea76b3bb
2023-04-06 09:48:58
@ 3d32d22c:ea76b3bb
2023-04-06 09:48:58Lionel Shriver's The Mandibles: A Family, 2029-2047 is an engaging novel that captures the imagination of anyone interested in the future of money, particularly those who are participating in the Bitcoin revolution. Set in an even more dystopian near-future America, the story follows the upper-middle class Mandible family as they navigate the consequences of a devastating economic collapse that leads to the disintegration of the once-mighty USD.
Shriver's vivid portrayal of a world thrown into chaos by the collapse of the dollar serves as a potent reminder of the potential vulnerabilities inherent in traditional financial systems...and in the illusion of wealth that those systems promote. In the novel, the Bancor, a new global currency, emerges as a response to this financial catastrophe. This narrative thread is especially thought-provoking for Bitcoin users.
The author's keen insights into the societal, political, and economic ramifications of the dollar's demise make The Mandibles an essential read for anyone who follows current financial news. Shriver's exploration of a near-future where the world's biggest centralized currencies have lost their footing echoes the current discussions about the banking situation in the United States and abroad.
As the story unfolds, the characters must adapt to a new reality where traditional financial structures no longer hold sway. This aspect of the novel resonates deeply with the principles that underpin the Bitcoin movement, reinforcing the importance of reimagining our financial and political systems and embracing innovative alternatives.
The book's characters are well crafted, each embodying unique reactions to the new economic reality they face. Among them, a once-affluent social worker, a self-absorbed academic, an unemployed tenant, a well-known writer returning from living abroad, and a psychotherapist, all struggle to adapt to the collapse of the dollar. However, it is Willing, a perceptive and resourceful teenager, who stands out as the character with whom most of us will identify. Willing's skepticism of traditional financial systems, coupled with his quick thinking and adaptability, make him an embodiment of the innovative spirit that drives the Bitcoin movement. I, personally enjoyed watching him MacGyver his way through challenges that the adults around him simply couldn't grasp in time.
Enola, affectionately known as Nolly, is my second-favorite character (and probably will be yours). Nolly embodies a unique combination of seasoned pragmatism and unwavering moral integrity. Her presence in the novel as another outlier in the family adds nuance to the narrative.
Nolly's experiences and insights offer a compelling contrast to those of the other characters, including Willing. Her role in the story not only lends emotional weight but also serves as a powerful reminder of the resilience and adaptability needed to survive and flourish in a world gone completely pear-shaped.
It's a shame that I hadn't even heard of this book until quite recently. It's interesting how much has happened since 2016 when the book was published. I highly recommend The Mandibles to anyone imagining what the world might be like when the USS Petrodollar finally sinks.
-
 @ 38eba25d:4a78e9fe
2023-04-06 08:36:32
@ 38eba25d:4a78e9fe
2023-04-06 08:36:32Test
-
 @ b5aabce9:b62cec60
2023-04-06 02:34:46
@ b5aabce9:b62cec60
2023-04-06 02:34:46PETER KILLS THE METAVERSE
~~PETER PANDA KILLS YOUR FAVORITE NFT~~
So the past year I've been writing for a comic-book series that is pretty Dope. Here's the just of what it is. A guy's (more backstory on the guy will come at a later time in the series) consciousness gets transferred into a panda teddy-bear and he is on a journey to get his body and hopefully everything he lost, back. But all that backstory will be told at a later time. Here is where this series takes off at... A Predictive A.i. computer program A.D.I.C., Advanced Digital Intelligence Computer, was originally designed in the 1980’s as an algorithm for 'banking and trading'. It has since gained sentience and has been secretly pulling the strings of the financial markets. For the last few decades, A.D.I.C has ended up on the right side of every trade, amassing more capital than any human on the planet. But, the unexpected NFT boom has disrupted the program’s financial plans. A.D.IC. now must destroy the NFT market by taking down the most widely held NFTs. To carry out the scheme, it recruits the best entity for the job... Peter Panda.
This has been a fun series to work on and I'm def lookin forward to the completion. So far we have two issues completed and published. The first issue premiered in February at both the Chattanooga & Atlanta Comic Convention. It did receive a warm welcome and I can't wait for people to get their hands on the second issue, which will be released this month at the Las-Vegas comic Convention.
The series will be a 6 issue run that takes the main character into the world of NFTs. Like he actually goes into each NFT realm and carries out his obligation to "destroy" them. The first issue explores the land of WhIsBe. Yes those unassuming gigantic gummy-bears. And don't worry, permission to include them was given. The following issues will be parody's or similar versions of your favorite NFT's. Maybe you can take a glimpse at the cover to see which company the second one is about.
Anyway, this was an introduction to the series and I'll be posting updates as we move forward. I may even include some give-aways. Ah... I do know that the digital versions of the comic will be available for BTC, just like most of my projects. Well, until next time... Much Thanks.
THIS SERIES IS FOR MATURE READERS
-
 @ 909c2ba8:44d7d9e5
2023-04-05 23:06:17
@ 909c2ba8:44d7d9e5
2023-04-05 23:06:17 Do you ever feel like you're struggling to create abundance?
Do you ever feel like you're struggling to create abundance? Like millions of others living in lack, frustration, resentment, and worry - listening to that negative inner voice?
Well, today, I want to share an astonishing secret with you. A secret that can shoot you straight into a whole new world filled with everything your heart desires. 💖
Enter the magnificent world of mindfulness
Did you know 95% of our thoughts are unconscious... lurking below the surface like hidden saboteurs, holding us back from success? It's time to trounce those self-limiting, stress-based emotions keeping you chained to the past. The key to unlocking true abundance and happiness is... mindfulness. 🧘♀️
To put that river of abundance flowing like the great Mississippi, you must be fully present in each moment - a skill you can improve with practice. So the more you move your energy from that familiar, predictable past to an unpredictable and exciting future, the easier it becomes to generate your dream life. 💫
🤯 Mind-blowing, isn't it?
Now, let me tell you about a fantastic bunch of people with one common attribute—abundance!
From ordinary to extraordinary: Tales of affluence
It's fascinating that most abundant people, whether contemporary or from history, weren't always living in prosperity. They gained valuable experiences and lessons along the way, course correcting as they faced various trials, struggles, and setbacks.
These invaluable lessons acted as their most powerful tools for transformation, ultimately leading them into a life of abundance and affluence.
Embrace mastery by learning from the best, but don't just imitate them; understand and apply their principles to your life's unique path. 🌱
But what's the secret sauce?
What separates the truly abundant from those who merely dream?
You see, instead of getting bogged down in a mindset of lack, the affluent understand the power of abundance. They draw upon their experiences to build influence, both within themselves and in their surrounding world. 🌎
Want to share in their affluence and experience unlimited growth? Read on!
Join my exclusive Mastermind Group today! 🌟
I invite you to join the incredible journey that has brought me and countless others an awakening in the world of abundance.
Excited to share the knowledge and steps one must take to elevate themselves from the ordinary, I am ecstatic to offer you a unique opportunity to join my exclusive Mastermind Group!
Together, we'll explore:
The powerful principles of duality and polarity of creation
Why creating from a place of abundance conquers lack mentality
The future-focused mindset and how 5th-dimensional reality taps into a world of affluence
Join the ranks of the abundant—now! 💥
Bradley Woods
-
 @ 0af3ed9b:842c0641
2023-04-05 22:02:13
@ 0af3ed9b:842c0641
2023-04-05 22:02:13You passed :)
-
 @ f09d8f9f:af64fc7a
2023-04-05 21:54:20
@ f09d8f9f:af64fc7a
2023-04-05 21:54:20Hello there :)
-
 @ a8483554:c8e63f6b
2023-04-05 15:50:45
@ a8483554:c8e63f6b
2023-04-05 15:50:45Hello World!
-
 @ d408b55a:7ea8e70a
2023-04-05 15:37:55
@ d408b55a:7ea8e70a
2023-04-05 15:37:55Amidst the hills and valleys green, The world is like a magic dream. Where streams flow and rivers sing, And birds take to the sky on wing.
The sun casts its golden rays, As the flowers bloom in different ways, Their petals soft and colors bright, A symphony of beauty in plain sight.
The forests rustle in the breeze, As the leaves whisper melodies, And the scent of pine fills the air, Nature's magic is everywhere.
From mountain peaks to ocean floors, Nature's beauty forever soars, A world of wonders to behold, A treasure chest of stories untold.
So let us cherish this natural gem, For it's a part of who we are and when, We stand in awe of the world we see, A place of beauty, forever free.

-
 @ c753997e:9fe20adc
2023-04-05 15:28:15
@ c753997e:9fe20adc
2023-04-05 15:28:15By Simon Watkins - Apr 04, 2023, 6:00 PM CDT
Saudi Arabia’s very public announcement last week that its cabinet had approved a plan to join the Shanghai Cooperation Organisation (SCO) as a ‘dialogue partner’ is the surest sign yet that any U.S. efforts to keep it out of the China-Russia sphere of influence may now be futile. The Kingdom had already signed a memorandum of understanding on 16 September 2022 granting it the status of SCO dialogue partner, as was exclusively reported by OilPrice.com at the time. However, Saudi Arabia did nothing to encourage the release of the news at that point, unlike now - just after it resumed relations with Iran, in a deal brokered by China.
The SCO is the world’s biggest regional political, economic and defence organisation both in terms of geographic scope and population. It covers 60 percent of the Eurasian continent (by far the biggest single landmass on Earth), 40 percent of the world’s population, and more than 20 percent of global GDP. It was formed in 2001 on the foundation of the ‘Shanghai Five’ that was set up in 1996 by China, Russia, and three states of the former USSR (Kazakhstan, Kyrgyzstan and Tajikistan). Aside from its vast scale and scope, the SCO believes in the idea and practice of the ‘multi-polar world’, which China anticipates will be dominated by it by 2030. In this context, the end of December 2021/beginning of January 2022 saw meetings in Beijing between senior officials from the Chinese government and foreign ministers from Saudi Arabia, Kuwait, Oman, Bahrain, plus the secretary-general of the Gulf Cooperation Council (GCC). At these meetings, the principal topics of conversation were to finally seal a China-GCC Free Trade Agreement and to forge “a deeper strategic cooperation in a region where U.S. dominance is showing signs of retreat”. Related: Japan Is Betting Big On Hydrogen This idea was the centrepiece of the declaration signed in 1997 between then-Russian President, Boris Yeltsin, and his then-China counterpart, Jiang Zemin. Veteran Russian Foreign Minister, Sergey Lavrov, has since stated that: “The Shanghai Cooperation Organisation is working to establish a rational and just world order and […] it provides us with a unique opportunity to take part in the process of forming a fundamentally new model of geopolitical integration”. Aside from these geopolitical redesigns, the SCO works to provide intra-organisation financing and banking networks, plus increased military cooperation, intelligence sharing and counterterrorism activities, among other things. The U.S. itself applied for ‘observer status’ of the SCO in the early 2000s but was rejected in 2005.
This latest step by Saudi Arabia away from the U.S. and towards the China-Russia axis should come as no surprise to anyone who has been watching developments in the Kingdom since the rise of Crown Prince Mohammed bin Salman (MbS) from around 2015. At that point, he was not Crown Prince (the heir designate position) – that role was held by Muhammad bin Nayef (MbN) – but rather Deputy Crown Prince with burning ambition to take the number one succession spot upon the death of King Salman. His stint as Defense Minister was disastrous, with the dramatic escalation of the war against the Houthis in Yemen – including indiscriminate bombing of civilian targets – roundly condemned by the West. This led the German intelligence service, the Bundesnachrichtendienst (BND), to leak an abridged internal-only assessment report of MbS to various trusted members of the press that stated: ‘Saudi Arabia [under MbS] has adopted an impulsive policy of intervention.’ It went on to describe MbS in terms of being a political gambler who was destabilising the Arab world through proxy wars in Yemen and Syria.
In order to rebuild his reputation with a view to usurping MbN as Crown Prince, MbS came up with an idea that he thought would win over senior Saudis who supported his rival. That idea was to float a stake in the Kingdom’s flagship company, Saudi Aramco, through an initial public offering (IPO), as analysed in depth in my latest book on the global oil markets. In theory, the idea had several positive factors going for it that would benefit MbS. First, it would raise a lot of money, which Saudi Arabia needed to offset the economically disastrous effect of the 2014-2016 Oil Price War that it had instigated. Second, it would likely be the biggest ever IPO, thus boosting Saudi Arabia’s reputation and the breadth and depth of its capital markets. And third, the new money from the sale could be used as part of Saudi Arabia’s ‘Vision 2030’ development plan aimed at diversifying the Kingdom’s economy away from a reliance on oil and gas exports.
MbS pitched the idea to the senior Saudis based on very specific benchmark targets. First, the flotation would be for 5% of the company. Second, this would raise at least USD100 billion, which would value the whole company at US$2 trillion. Third, it would be listed not just on the domestic Tadawul stock market but also on at least one of the world’s biggest and most prestigious stock markets – the New York Stock Exchange and the London Stock Exchange were the exchanges MbS had in mind. None of these targets was hit, of course, as the more information was made known about Saudi Aramco to international investors the more they regarded it as an omni-toxic liability, including financially and politically.
At that point, China stepped in with an offer to save MbS’s face, an offer that he has apparently never forgotten. The offer was that China would buy the entire 5% stake for the required US$100 million, and it would be done in a private placement, meaning no possibly embarrassing details about anything surrounding the deal would ever be made public, including to those senior Saudis who opposed MbS. Although the offer was declined as King Salman did not at that point want to alienate the U.S. any further than had already been done by launching the 2014-2016 Oil Price War with the intention of destroying or disabling the then-nascent U.S. shale oil sector, the relationship between Saudi Arabia and China blossomed from that point onwards. A little under a year before the Russian invasion of Ukraine in February 2022, Saudi Arabia was already so aligned to China that Saudi Aramco’s chief executive officer, Amin Nasser, spent several days at the annual China Development Forum hosted in Beijing, during which time he said: “Ensuring the continuing security of China’s energy needs remains our highest priority - not just for the next five years but for the next 50 and beyond.” One year later, and just a few months after the Russian invasion of Ukraine, Aramco’s senior vice president downstream, Mohammed Al Qahtani, announced the creation of a ‘one stop shop’ provided by his company in China’s Shandong. He said: “The ongoing energy crisis, for example, is a direct result of fragile international transition plans which have arbitrarily ignored energy security and affordability for all.” He added: “The world needs clear-eyed thinking on such issues. That’s why we highly admire China’s 14th Five Year Plan for prioritising energy security and stability, acknowledging its crucial role in economic development.” At the same time as this relationship was moving up several gears, so was the relationship between Saudi Arabia and Russia. By the end of the 2014-2016 Oil Price War, as also analysed in depth in my latest book on the global oil markets, the U.S. shale oil sector had reorganised itself into an oil-producing machine that could survive on prices as low as US$35 per barrel (pb) of Brent if necessary. Saudi Arabia’s budget breakeven price then was over US$84 pb and there was no way it could compete with the U.S. Saudi Arabia desperately needed to push oil prices back up to repair its budget but was unable to do so because its disastrous Second Oil Price War (the first being the 1973/74 Oil Crisis) had critically undermined its credibility with other OPEC members and with the global oil market. At that point, Russia had stepped in to support the OPEC oil production cuts in late 2016 aimed at bringing oil prices back to levels that allowed OPEC members to begin to repair their decimated finances. This support has continued ever since and has formalised into the ‘OPEC+’ grouping.
Both Russia and China know how to leverage such relationships, as they have been doing in the Middle East ever since the U.S. withdrew from the Joint Comprehensive Plan of Action with Iran in 2018, Syria in 2019, and Afghanistan and Iraq in 2021. These combination of factors put China in the position of being able to broker the relationship normalisation deal between Saudi Arabia and Iran – the leaders of the Sunni Islam world and the Shia Islam world, respectively. Although White House national security spokesperson, John Kirby, did observe tersely at the time that the deal between Iran and Saudi Arabia “is not about China”, it absolutely was about China. What it absolutely was not about was the U.S.
By Simon Watkins for Oilprice.com
-
 @ 3acf7ffd:937abb7b
2023-04-05 13:10:04
@ 3acf7ffd:937abb7b
2023-04-05 13:10:04This became something that I never thought I would like. Sunbather is one of those albums that evoke a particular visual to you. It's in the blackgaze genre and if you're not aware of that it's basically a fusion genre between black metal and shoegaze. So it has the raw drums and screamo interlaced with fuzzy guitar riffs and dreary atmosphere.
On paper, it shouldn't work. But somehow Sunbather made it work. This is a piece that just feels cathartic and calming. There are moments that it jolts you out of that state but the guitar riffs and non-stop raw drumming that's constantly trying to build a crescendo feels so much when it drops.
This is an album that you should listen to when you want to try something new and you want to feel a bit cathartic with some black metal.
This article's heading image was taken from discogs.com.
I originally published this article on my gopherhole on February 2, 2022 [0]. Aside from a few formatting quirks, I did not change any of the content of the article for this repost.
[0] gopher://kalayaan.xyz/0/~rtr/muzika/deafheaven.txt
-
 @ 846b763b:23539eca
2023-04-05 09:33:39
@ 846b763b:23539eca
2023-04-05 09:33:39[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
-
 @ c753997e:9fe20adc
2023-04-05 05:54:21
@ c753997e:9fe20adc
2023-04-05 05:54:21By Steven Levy June 12, 1994 New York Times
On a sunny spring day in Mountain View, Calif., 50 angry activists are plotting against the United States Government. They may not look subversive sitting around a conference table dressed in T-shirts and jeans and eating burritos, but they are self-proclaimed saboteurs. They are the Cypherpunks, a loose confederation of computer hackers, hardware engineers and high-tech rabble-rousers.
The precise object of their rage is the Clipper chip, offically known as the MYK-78 and not much bigger than a tooth. Just another tiny square of plastic covering a silicon thicket. A computer chip, from the outside indistinguishable from thousands of others. It seems improbable that this black Chiclet is the focal point of a battle that may determine the degree to which our civil liberties survive in the next century. But that is the shared belief in this room.
The Clipper chip has prompted what might be considered the first holy war of the information highway. Two weeks ago, the war got bloodier, as a researcher circulated a report that the chip might have a serious technical flaw. But at its heart, the issue is political, not technical. The Cypherpunks consider the Clipper the lever that Big Brother is using to pry into the conversations, messages and transactions of the computer age. These high-tech Paul Reveres are trying to mobilize America against the evil portent of a "cyberspace police state," as one of their Internet jeremiads put it. Joining them in the battle is a formidable force, including almost all of the communications and computer industries, many members of Congress and political columnists of all stripes. The anti-Clipper aggregation is an equal-opportunity club, uniting the American Civil Liberties Union and Rush Limbaugh.
The Clipper's defenders, who are largely in the Government, believe it represents the last chance to protect personal safety and national security against a developing information anarchy that fosters criminals, terrorists and foreign foes. Its adherents pose it as the answer, or at least part of the answer, to a problem created by an increasingly sophisticated application of an age-old technology: cryptography, the use of secret codes.
For centuries, cryptography was the domain of armies and diplomatic corps. Now it has a second purpose: protecting personal and corporate privacy. Computer technology and advanced telecommunications equipment have drawn precious business information and intimate personal communications out into the open. This phenomenon is well known to the current Prince of Wales, whose intimate cellular phone conversations were intercepted, recorded and broadcast worldwide. And corporations realize that competitors can easily intercept their telephone conversations, electronic messages and faxes. High tech has created a huge privacy gap. But miraculously, a fix has emerged: cheap, easy-to-use, virtually unbreakable encryption. Cryptography is the silver bullet by which we can hope to reclaim our privacy.
The solution, however, has one drawback: cryptography shields the law abiding and the lawless equally. Law-enforcement and intelligence agencies contend that if strong codes are widely available, their efforts to protect the public would be paralyzed. So they have come up with a compromise, a way to neutralize such encryption. That's the Clipper chip and that compromise is what the war is about.
The idea is to give the Government means to override other people's codes, according to a concept called "key escrow." Employing normal cryptography, two parties can communicate in total privacy, with both of them using a digital "key" to encrypt and decipher the conversation or message. A potential eavesdropper has no key and therefore cannot understand the conversation or read the data transmission. But with Clipper, an additional key -- created at the time the equipment is manufactured -- is held by the Government in escrow. With a court-approved wiretap, an agency like the F.B.I. could listen in. By adding Clipper chips to telephones, we could have a system that assures communications will be private -- from everybody but the Government.
And that's what rankles Clipper's many critics. Why, they ask, should people accused of no crime have to give Government the keys to their private communications? Why shouldn't the market rather than Government determine what sort of cryptosystem wins favor. And isn't it true that the use of key escrow will make our technology so unattractive to the international marketplace that the United States will lose its edge in the lucrative telecommunications and computer fields? Clipper might clip the entire economy.
Nonetheless, on Feb. 4 the White House announced its approval of the Clipper chip, which had been under study as a Government standard since last April, and the Crypto War broke out in full force. Within a month, one civil liberties group, Computer Professionals for Social Responsibility, received 47,000 electronic missives urging a stop to Clipper. "The war is upon us," wrote Tim May, co-founder of the Cypherpunks, in an urgent electronic dispatch soon after the announcement. "Clinton and Gore folks have shown themselves to be enthusiastic supporters of Big Brother."
Editors’ Picks
Brooke Shields and the Curse of Great Beauty
Hot Cross Buns Are the Pumpkin Spice Latte of Australia
What You Missed at Brooklyn’s Most Fabulous Garage Sale Continue reading the main story And though the Clinton Administration's endorsement of Clipper as a Government standard required no Congressional approval, rumblings of discontent came from both sides of the Capitol. Senator Patrick J. Leahy, the Vermont Democrat whose subcomittee has held contentious hearings on the matter, has called the plan a "misstep," charging that "the Government should not be in the business of mandating particular technologies."
Two weeks ago, an AT&T Bell Laboratories researcher revealed that he had found a serious flaw in the Clipper technology itself, enabling techno-savvy lawbreakers to bypass the security fuction of the chip in some applications. Besides being a bad idea, Clipper's foes now say, it doesn't even work properly.
Yet the defenders of Clipper have refused to back down, claiming that the scheme -- which is, they often note, voluntary -- is an essential means of stemming an increasing threat to public safety and security by strong encryption in everyday use. Even if Clipper itself has to go back to the drawing board, its Government designers will come up with something quite similar. The underlying issue remains unchanged: If something like Clipper is not implemented, writes Dorothy E. Denning, a Georgetown University computer scientist, "All communications on the information highway would be immune from lawful interception. In a world threatened by international organized crime, terrorism and rogue governments, this would be folly."
The claims from both sides sound wild, almost apocalyptic. The passion blurs the problem: Can we protect our privacy in an age of computers -- without also protecting the dark forces in society?
The crypto war is the inevitable consequence of a remarkable discovery made almost 20 years ago, a breakthrough that combined with the microelectronics revolution to thrust the once-obscure field of cryptography into the mainstream of communications policy.
It began with Whitfield Diffie, a young computer scientist and cryptographer. He did not work for the Government, which was strange because in the 1960's almost all serious crypto in this country was done under Federal auspices, specifically at the Fort Meade, Md., headquarters of the supersecret National Security Agency. Though it became bigger than the C.I.A., the N.S.A. was for years unknown to Americans; the Washington Beltway joke was that the initials stood for "No Such Agency." Its working premise has always been that no information about its activities should ever be revealed. Its main mission involved cryptography, and the security agency so dominated the field that it had the power to rein in even those few experts in the field who were not on its payroll.
But Whitfield Diffie never got that message. He had been bitten by the cryptography bug at age 10 when his father, a professor, brought home the entire crypto shelf of the City College library in New York. Then he lost interest, until he arrived at M.I.T.'s Artifical Intelligence Laboratory in 1966. Two things rekindled his passion. Now trained as a mathematician, he had an affinity for the particular challenges of sophisticated crypto. Just as important, he says, "I was always concerned about individuals, an individual's privacy as opposed to Goverment secrecy."
Diffie, now 50, is still committed to those beliefs. When asked about his politics, he says, "I like to describe myself as an iconoclast." He is a computer security specialist for Sun Microsystems, a celebrated cryptographer and an experienced hand at Congressional testimony. But he looks like he stumbled out of a Tom Robbins novel -- with blond hair that falls to his shoulders and a longish beard that seems a virtual trademark among code makers. At a Palo Alto, Calif., coffeehouse one morning, he describes, in clipped, precise cadence, how he and Martin E. Hellman, an electrical engineering professor at Stanford University, created a crypto revolution.
Diffie was dissatisfied with the security on a new time-sharing computer system being developed by M.I.T. in the 1960's. Files would be protected by passwords, but he felt that was insufficient. The system had a generic flaw. A system manager had access to all passwords. "If a subpeona was served against the system managers, they would sell you out, because they had no interest in going to jail," Diffie says. A perfect system would eliminate the need for a trusted third party.
This led Diffie to think about a more general problem in cryptography: key management. Even before Julius Caesar devised a simple cipher to encode his military messages, cryptography worked by means of keys. That is, an original message (what is now called "plaintext") was encrypted by the sender into seeming gibberish (known as "ciphertext"). The receiver, using the same key, decrypted the message back into the original plaintext. For instance, the Caesar key was the simple replacement of each letter by the letter three places down in the alphabet. If you knew the key, you could encrypt the word help into the nonsense word khos; the recipient of the message would decrypt the message back to help.
The problem came with protecting the key. Since anyone who knew the Caesar key would be able to understand the encoded message, it behooved the Romans to change that key as often as possible. But if you change the key, how do you inform your spies behind enemy lines? (If you tell them using the old code, which may have already been cracked, your enemies will then learn the new code.) For centuries, generals and diplomats have faced that predicament. But a few years ago, it took on added urgency.
With computers and advanced telecommunications, customers outside Government were discovering a need for information security. Cryptography was the answer, but how could it be applied widely, considering the problem of keys? The best answer to date was something called a key-management repository, where two parties who wanted secrecy would go to a trusted third party who would generate a new key for the private session. But that required just what Diffie deplored -- an unwanted third wheel.
"The virtue of cryptography should be that you don't have to trust anybody not directly involved with your communication," Diffie says. "Without conventional key distribution centers, which involved trusting third parties, I couldn't figure how you could build a system to secure, for instance, all the phones in the country."
When Diffie moved to Stanford University in 1969, he foresaw the rise of home computer terminals and began pondering the problem of how to use them to make transactions. "I got to thinking how you could possibly have electronic business, because signed letters of intent, contracts and all seemed so critical," he says. He devoured what literature he could find outside the National Security Agency. And in the mid-1970's, Diffie and Hellman achieved a stunning breakthrough that changed cryptography forever. They split the cryptographic key.
In their system, every user has two keys, a public one and a private one, that are unique to their owner. Whatever is scrambled by one key can be unscrambled by the other. It works like this: If I want to send a message to Whit Diffie, I first obtain his public key. (For complicated mathematical reasons, it is possible to distribute one's public key freely without compromising security; a potential enemy will have no advantage in code-cracking if he holds your public key alone.) Then I use that key to encode the message. Now it's gobbledygook and only one person in the world can decode it -- Whit Diffie, who holds the other, private, key. If he wants to respond to me with a secret message, he uses my public key to encode his answer. And I decode it, using my private key.
It was an amazing solution, but even more remarkable was that this split-key system solved both of Diffie's problems, the desire to shield communications from eavesdroppers and also to provide a secure electronic identification for contracts and financial transactions done by computer. It provided the identification by the use of "digital signatures" that verify the sender much the same way that a real signature validates a check or contract.
Suddenly, the ancient limitations on cryptography had vanished. Now, perhaps before the millennium, strong cryptography could find its way to every telephone, computer and fax machine -- if users wanted it. Subsequent variations on the Diffie-Hellman scheme focused on using crypto algorithms to insure the anonymity of transactions. Using these advances, it is now possible to think of replacing money with digital cash -- while maintaining the comforting untraceability of bills and coins. The dark art of cryptography has become a tool of liberation.
From the moment Diffie and Hellman published their findings in 1976, the National Security Agency's crypto monopoly was effectively terminated. In short order, three M.I.T. mathematicians -- Ronald L. Rivest, Adi Shamir and Leonard M. Adleman -- developed a system with which to put the Diffie and Hellman findings into practice. It was known by their initials, RSA. It seemed capable of creating codes that even the N.S.A. could not break. They formed a company to sell their new system; it was only a matter of time before thousands and then millions of people began using strong encryption.
That was the National Security Agency's greatest nightmare. Every company, every citizen now had routine access to the sorts of cryptographic technology that not many years ago ranked alongside the atom bomb as a source of power. Every call, every computer message, every fax in the world could be harder to decipher than the famous German "Enigma" machine of World War II. Maybe even impossible to decipher!
The genie was out of the bottle. Next question: Could the genie be made to wear a leash and collar? Enter the Clipper chip.
When illustrating the Government's need to control crypto, Jim Kallstrom, the agent in charge of the special operations division of the New York office of the F.B.I., quickly shifts the discussion to the personal: "Are you married? Do you have a child? O.K., someone kidnaps one of your kids and they are holding your kid in this fortress up in the Bronx. Now, we have probable cause that your child is inside this fortress. We have a search warrant. But for some reason, we cannot get in there. They made it out of some new metal, or something, right? Nothing'll cut it, right? And there are guys in there, laughing at us. That's what the basis of this issue really is -- we've got a situation now where a technology has become so sophisticated that the whole notion of a legal process is at stake here!"
Kallstrom is a former head of the Bureau Tech Squad, involved in the bugging operation that brought John Gotti to justice. Some have described him as the F.B.I.'s answer to "Q," the gadget wizard of the James Bond tales.
"From the standpoint of law enforcement, there's a superbig threat out there -- this guy is gonna build this domain in the Bronx now, because he's got a new steel door and none of the welding torches, none of the boomerangs, nothing we have is gonna blast our way in there. Sure, we want those new steel doors ourselves, to protect our banks, to protect the American corporation trade secrets, patent rights, technology. But people operating in legitimate business are not violating the laws -- it becomes a different ball of wax when we have probable cause and we have to get into that domain. Do we want a digital superhighway where not only the commerce of the nation can take place but where major criminals can operate impervious to the legal process? If we don't want that, then we have to look at Clipper."
Wiretapping is among law enforcement's most cherished weapons. Only 919 Federal, state and local taps were authorized last year, but police agencies consider them essential to fighting crime. Obviously if criminals communicate using military-grade cryptosystems, wiretapping them becomes impossible.
For two years, the F.B.I. has been urging Congress to pass the proposed Digital Telephony and Communications Privacy Act, which would in essence require that new communications technologies be designed to facilitate wiretapping. Even if the bill should somehow pass, overcoming the opposition of the communications industry and civil libertarians, the extra effort and expense will be wasted if the only thing the wiretappers can hear is the hissy white noise of encrypted phone conversations and faxes. If cryptography is not controlled, wiretapping could be rendered obsolete. Louis J. Freeh, the Director of the F.B.I., surely fears that prospect. He has told Congress that preserving the ability to intercept communications legally, in the face of these technological advances, is "the No. 1 law enforcement, public safety and national security issue facing us today."
Some people criticize Clipper on the basis that truly sophisticated criminals would never use it, preferring other easily obtained systems that use high-grade cryptography. Despite Clipper, kidnappers and drug kingpins may construct Kallstrom's virtual fort in the Bronx with impunity, laughing at potential wiretappers.
The Government understands the impossibility of eradicating strong crypto. Its objective is instead to prevent unbreakable encryption from becoming rountine. If that happens, even the stupidest criminal would be liberated from the threat of surveillance. But by making Clipper the standard, the Government is betting that only a tiny percentage of users would use other encryption or try to defeat the Clipper.
At a rare public appearance in March at a conference on computers and privacy, Stewart A. Baker, then general counsel of the National Security Agency, tried to explain. "The concern is not so much what happens today when people go in and buy voice scramblers," said Baker, a dapper, mustached lawyer who worked as an Education Department lawyer in the Carter Administration. "It is the prospect that in 5 years or 10 years every phone you buy that costs $75 or more will have an encrypt button on it that will interoperate with every other phone in the country and suddenly we will discover that our entire communications network is being used in ways that are profoundly antisocial. That's the real concern, I think, that Clipper addresses. If we are going to have a standardized form of encryption that is going to change the world, we should think seriously about what we are going to do when it is misused."
Not all law-enforcement experts believe that cryptography will unleash a riot of lawlessness. William R. Spernow, a Sacramento, Calif., computer crime specialist who works on a grant from the Federal Bureau of Justice Assistance, has encountered a few cases in which criminals have encrypted information unbreakably, including one involving a pedophile who encrypted the identities of his young victims. Yet Spernow sees no reason to panic. "In cases where there's encryption, the officers have been able to make the case through other investigative means," he says. "If we hustle, we can still make our cases through other kinds of police work."
Sign up for The New York Times Magazine Newsletter The best of The New York Times Magazine delivered to your inbox every week, including exclusive feature stories, photography, columns and more. Get it sent to your inbox. But crime is only part of the problem. What happens to national security if cryptography runs free? Those who know best, officials of the National Security Agency, won't say. When the agency's director, Vice Adm. John M. McConnell testified before a Senate subcommittee on May 3, he withheld comment on this question until the public hearing was terminated and a second, classified session convened in a secure room.
Still, the effect of strong crypto on N.S.A. operations is not difficult to imagine. The agency is charged with signals intelligence, and it is widely assumed that it monitors all the communications between borders and probably much of the traffic within foreign countries. (It is barred from intercepting domestic communications.) If the crypto revolution crippled N.S.A.'s ability to listen in on the world, the agency might miss out on something vital -- for instance, portents of a major terrorist attack.
No compelling case has been made, however, that the key-escrow system would make it easier for authorities to learn of such an attack. The National Security Agency would take the legal steps to seek the telltale keys after it had first identified those potential terrorists and wiretapped their calls, then discovered the inpenetrable hiss of encryption. Even then, the keys would be useful only if the terrorists were encoding conversations with Clipper technology, the one kind the Government had the capability to decode instantly. What sort of nuclear terrorist would choose Clipper?
The Government response has been to say that potential terrorists might indeed use alternative crypto methods to converse among themselves. But if Clipper were the accepted standard, the terrorists would have to use it to communicate with outsiders -- banks, suppliers and other contacts. The Government could listen in on those calls. However, the work of the Bell Labs researcher, Matthew Blaze, casts serious doubt on that contention. Blaze has uncovered a flaw in Clipper that would allow a user to bypass the security funtion of the chip. Anyone who tinkered with Clipper in this way could communicate in privacy with anyone else with a Clipper phone and Government wiretappers would be unable to locate the key to unscramble the conversations.
Nonetheless, it was the terrorist threat, along with national security concerns, that moved the Clinton Administration to support the key-escrow inititative. White House high-tech policy makers share a recurrent fear: one day they might be sitting before an emergency Congressional investigation after the destruction of half of Manhattan by a stolen nuclear weapon planted in the World Trade towers and trying to explain that the Government had intercepted the communications of the terrorists but could not understand them because they used strong encryption. If Clipper were enacted, they could at least say, "We tried."
Obviously the Government views the Crypto revolution with alarm and wants to contain it. For years, much of its efforts have focused on the use of stringent export controls. While cryptography within the United States is unrestricted, the country's export laws treat any sort of encryption as munitions, like howitzers or nuclear triggers. The National Security Agency is the final arbiter and it will approve exports of cryptosystems in computer software and electronic hardware only if the protective codes are significantly weakened.
The N.S.A. stance is under attack from American businesses losing sales to foreign competitors. Listen to D. James Bidzos, the 39-year-old president of RSA Data Security, the Redwood City, Calif., company that controls the patents for public-key cryptography: "For almost 10 years, I've been going toe to toe with these people at Fort Meade. The success of this company is the worst thing that can happen to them. To them, we're the real enemy, we're the real target."
RSA is making a pitch to become the standard in encryption; its technology has been adopted by Apple, AT&T, Lotus, Microsoft, Novell and other major manufacturers. So imagine its unhappiness that its main rival is not another private company, but the National Security Agency, designer of the key-escrow cryptosystems. The agency is a powerful and dedicated competitor.
"We have the system that they're most afraid of," Bidzos says. "If the U.S. adopted RSA as a standard, you would have a truly international, interoperable, unbreakable, easy-to-use encryption technology. And all those things together are so synergistically theatening to the N.S.A.'s interests that it's driving them into a frenzy."
The export laws put shackles on Bidzos's company while his overseas competitors have no such restaints. Cryptographic algorithms that the N.S.A. bans for export are widely published and are literally being sold on the streets of Moscow. "We did a study on the problem and located 340 foreign cryptographic products sold by foreign countires," says Douglas R. Miller, government affairs manager of the Software Publishers Association. "The only effect of export controls is to cripple our ability to compete."
The real potential losses, though, come not in the stand-alone encryption category, but in broader applications. Companies like Microsoft, Apple and Lotus want to put strong encryption into their products but cannot get licenses to export them. Often, software companies wind up installing a weaker brand of crypto in all their products so that they can sell a single version worldwide. This seems to be the Government's intent -- to encourage "crypto lite," strong enough to protect communications from casual intruders but not from Government itself.
In the long run, however, export regulation will not solve the National Security Agency's problem. The crypto business is exploding. People are becoming more aware of the vunerability of phone conversations, particularly wireless ones. Even the National Football League is adopting crypto technology; it will try out encrypted radio communication between coaches and quarterbacks, so rivals can't intercept last-minute audibles.
Anticipating such a boom, the N.S.A. devised a strategy for the 90's. It would concede the need for strong encryption but encourage a system with a key-escrow "back door" that provides access to communications for itself and law enforcement. The security agency had already developed a strong cryptosystem based on an algorithm called Skipjack, supposedly 16 million times stronger than the previous standard, D.E.S. (Data Encryption Standard). Now the agency's designers integrated Skipjack into a new system that uses a Law Enforcement Access Field (LEAF) that adds a signal to the message that directs a potential wiretapper to the approriate key to decipher the message. These features were included in a chip called Capstone, which could handle not only telephone communications but computer data transfers and digital signatures.
Supposedly, this technology was designed for Government use, but in 1993 the National Security Agency had a sudden opportunity to thrust it into the marketplace. AT&T had come to the agency with a new, relatively low-cost secure-phone device called the Surity 3600 that was designed to use the nonexportable DES encryption algorithm. The N.S.A. suggested that perhaps AT&T could try something else: a stripped-down version of Capstone for telephone communications. This was the Clipper chip. As a result, AT&T got two things: an agreement that Uncle Sam would buy thousands of phones for its own use (the initial commitment was 9,000, from the F.B.I.) and the prospect that the phone would not suffer the unhappy fate of some other secure devices when considered for export. There was also the expectation that AT&T would sell a lot more phones, since private companies would need to buy Clipper-equipped devices to communicate with the Governmment's Clipper phones.
It was an ingenious plan for several reasons. By agreeing to buy thousands of phones, and holding out the promise that thousands, or even millions more might be sold, AT&T phones gained a price advantage that comes with volume. (The original price of the Surity 3600 was $1,195, considerably less than the previous generation of secure phones; Mykotronx, the company making the Clipper chip, says that each chip now costs $30, but in large orders could quickly go as low as $10.) That would give the phones a big push in the marketplace. But by saturating the market, Clipper had a chance to become the standard for encryption, depending on whether businesses and individuals would be willing to accept a device that had the compromise of a government-controlled back door.
This compromise, of course, is the essence of Clipper. The Government recognizes the importance of keeping business secrets, intimate information and personal data hidden from most eyes and ears. But it also preserves a means of getting hold of that information after obtaining "legal authorization, normally a court order," according to a White House description.
The N.S.A. presented the idea to the Bush Administration, which took no action before the election. Then it had to convince a Democratic Administration to adopt the scheme, and started briefing the Clinton people during the transition. Many in the computer industry figured that with Vice President Al Gore's enthusiastic endorsement of the high-frontier virtues of the information highway, the Administration would never adopt any proposal so tilted in favor of law enforcement and away from his allies in the information industries. They figured wrong. A little more than two months after taking office, the Clinton Administration announced the existence of the Clipper chip and directed the National Institute of Standards and Technology to consider it as a Government standard.
Clipper was something the Administration -- starting with the Vice President -- felt compelled to adopt, and key escrow was considered an honorable attempt to balance two painfully contradictory interests, privacy and safety.
The reaction was instant, bitter and ceaseless. The most pervasive criticisms challenged the idea that a Clipper would be, as the standard said, "voluntary." The Government's stated intent is to manipulate the marketplace so that it will adopt an otherwise unpalatable scheme and make it the standard. Existing systems have to cope with export regulations and, now, incompatibility with the new Government Clipper standard. Is it fair to call a system voluntary if the Government puts all sorts of obstacles in the way of its competitors?
Others felt that it was only a matter of time before the National Security Agency pressured the Government to require key escrow of all cryptographic devices -- that Clipper was only the first step in a master plan to give Uncle Sam a key to everyone's cyberspace back door.
"That's a real fear," says Stephen T. Walker, a former N.S.A. employee who is now president of Trusted Information Systems, a company specializing in computer security products. "I don't think the Government could pull it off -- it would be like prohibition, only worse. But I think they might try it."
But mostly, people were unhappy with the essence of Clipper, that the Government would escrow their keys. As Diffie notes, key escrow reintroduces the vulnerability that led him to invent public key cryptography -- any system that relies on trusted third parties is, by definition, weaker than one that does not. Almost no one outside the Government likes the key-escrow idea. "We published the standard for 60 days of public comments," says F. Lynn McNulty, associate director for computer security at the National Institute of Standards and Technology. "We received 320 comments, only 2 of which were supportive."
Many people thought that in the face of such opposition, the Administration would quietly drop the Clipper proposal. They were dismayed by the Feb. 4 announcement of the adoption of Clipper as a Government standard. Administration officials knew they were alienating their natural allies in the construction of the information superhighway but felt they had no alternative. "This," said Michael R. Nelson, a White House technology official, "is the Bosnia of telecommunications."
If clipper is the administration's Techno-Bosnia, the crypto equivalent of snipers are everywhere -- in industry, among privacy lobbyists and even among Christian Fundamentalists. But the most passionate foes are the Cypherpunks. They have been meeting on the second Saturday of every month at the offices of Cygnus, a Silicon Valley company, assessing new ways they might sabotage Clipper. The group was co-founded in September 1992 by Eric Hughes, a 29-year-old freelance cryptogapher, and Tim May, a 42-year-old physicist who retired early and rich from the Intel company. Other Cypherpunk cells often meet simultaneously in six or seven locations around the world, but the main gathering place for Cypherpunks is the Internet, by means of an active mailing list in which members post as many as 100 electronic messages a day.
Cypherpunks share a few common premises. They assume that cryptography is a liberating tool, one that empowers individuals. They think that one of the most important uses of cryptography is to protect communications from the Government. Many of them believe that the Clipper is part of an overall initiative against cryptography that will culminate in Draconian control of the technology. And they consider it worth their time to fight, educating the general public and distributing cryptographic tools to obstruct such control.
Both Hughes and May have composed manifestos. Hughes's call to arms proclaims: "Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it."
May's document envisions a golden age in which strong cryptography belongs to all -- an era of "crypto anarchism" that governments cannot contain. To May, cryptography is a tool that will not only bestow privacy on people but help rearrange the economic underpinnings of society.
"Combined with emerging information markets, cryptography will create a liquid market for any and all material that can be put into words and pictures," May's document says. "And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property."
At a recent meeting, about 50 Cypherpunks packed into the Cygnus conference room, with dozens of others participating electronically from sites as distant as Cambridge, Mass., and San Diego. The meeting stretched for six hours, with discussions of hardware encryption schemes, methods to fight an electronic technique of identity forgery called "spoofing," the operation of "remailing" services, which allow people to post electronic messages anonymously -- and various ways to fight Clipper.
While the Cypherpunks came up with possible anti-Clipper slogans for posters and buttons, a bearded crypto activist in wire-rim glasses named John Gilmore was outside the conference room, showing the latest sheaf of cryptography-related Freedom of Information documents he'd dragged out of Government files. Unearthing and circulating the hidden crypto treasures of the National Security Agency is a passion of Gilmore, an early employee of Sun Microsystems who left the company a multimillionaire. The Government once threatened to charge him with a felony for copying some unclassified-and-later-reclassified N.S.A. documents from a university library. After the story hit the newspapers, the Government once again declassified the documents.
"This country was founded as an open society, and we still have the remnants of that society," Gilmore says. "Will crypto tend to open it or close it? Our Government is building some of these tools for its own use, but they are unavailable -- we have paid for cryptographic breakthroughs but they're classified. I wish I could hire 10 guys -- cryptographers, librarians -- to try to pry cryptography out of the dark ages."
Perhaps the most admired Cypherpunk is someone who says he is ineligible because he often wears a suit. He is Philip R. Zimmermann, a 40-year-old software engineer and cryptographic consultant from Boulder, Colo., who in 1991 cobbled together a cryptography program for computer data and electronic mail. "PGP," he called it, meaning Pretty Good Privacy, and he decided to give it away. Anticipating the Cypherpunk credo, Zimmermann hoped that the appearance of free cryptography would guarantee its continued use after a possible Government ban. One of the first people receiving the program placed it on a computer attached to the Internet and within days thousands of people had PGP. Now the program has been through several updates and is becoming sort of a people's standard for public key cryptography. So far, it appears that no one has been able to crack information encoded with PGP.
Like Diffie, Zimmermann developed a boyhood interest in crypto. "When I was a kid growing up in Miami, it was just kind of cool -- secret messages and all," he says. Later, "computers made it possible to do ciphers in a practical manner." He was fascinated to hear of public key cryptography and during the mid-1980's he began experimenting with a system that would work on personal computers. With the help of some colleagues, he finally devised a strong system, albeit one that used some patented material from RSA Data Security. And then he heard about the Senate bill that proposed to limit a citizen's right to use strong encryption by requiring manufacturers to include back doors in their products. Zimmermann, formerly a nuclear freeze activist, felt that one of the most valuable potential uses of cryptography was to keep messages secret from the Government.
Zimmermann has put some political content into the documentation for his program: "If privacy is outlawed, only outlaws will have privacy. Intelligence agencies have access to good cryptographic technology. So do the big arms and drug traffickers. So do defense contractors, oil companies, and other corporate giants. But ordinary people and grassroots political organizations mostly have not had access to affordable 'military grade' public-key cryptographic technology. Until now."
He has been told that Burmese freedom fighters learn PGP in jungle training camps on portable computers, using it to keep documents hidden from their oppressive Government. But his favorite letter comes from a person in Latvia, who informed him that his program was a favorite among one-time refuseniks in that former Soviet republic. "Let it never be," wrote his correspondant, "but if dictatorship takes over Russia, your PGP is widespread from Baltic to Far East now and will help democratic people if necessary."
Early last year, Zimmermann received a visit from two United States Customs Service agents. They wanted to know how it was that the strong encryption program PGP had found its way overseas with no export license. In the fall, he learned from his lawyer that he was a target of a grand jury investigation in San Jose, Calif. But even if the Feds should try to prosecute, they are likely to face a tough legal issue: Can it be a crime, in the process of legally distributing information in this country, to place it on an Internet computer site that is incidentally accessible to network users in other countries? There may well be a First Amendment issue here: Americans prize the right to circulate ideas, including those on software disks.
John Gilmore has discovered that Government lawyers have their own doubts about these issues. In some documents he sued to get, there are mid-1980's warnings by the Justice Department that the export controls on cryptography presented "sensitive constitutional issues." In one letter, an assistant attorney general warns that "the regulatory scheme extends too broadly into an area of protected First Amendment speech."
Perhaps taking Phil Zimmermann to court would not be the Government's best method for keeping the genie in the bottle.
The Clipper program has already begun. About once a month, four couriers with security clearances travel from Washington to the Torrance, Calif., headquarters of Mykotronx, which holds the contract to make Clipper chips. They travel in pairs, two from each escrow agency: the NIST and the Treasury Department. The redundancy is a requirement of a protocol known as Two-Person Integrity, used in situations like nuclear missile launches, where the stakes are too high to rely on one person.
The couriers wait while a Sun work station performs the calculations to generate the digital cryptographic keys that will be imprinted in the Clipper chips. Then it splits the keys into two pieces, separate number chains, and writes them on two floppy disks, each holding lists of "key splits." To reconstruct the keys imprinted on the chip, and thereby decode private conversations, you would need both sets of disks.
After being backed up, the sets of disks are separated, each one going with a pair of couriers. When the couriers return to their respective agencies, each set of disks is placed in a double-walled safe. The backup copies are placed in similar safes. There they wait, two stacks of floppy disks that grow each month, now holding about 20,000 key splits, the so-called back doors.
Will this number grow into the millions as the Government hopes? Ultimately the answer lies with the American public. Administration officials are confident that when the public contemplates scenarios like the Fortress in the Bronx or the Mushroom Cloud in Lower Manhattan, it will realize that allowing the Government to hold the keys is a relatively painless price to pay for safety and national security. They believe the public will eventually accept it in the same way it now views limited legal wiretapping. But so far the Administration hasn't recruited many prominent supporters. The main one is Dorothy Denning, a crypto expert who heads the computer science department at Georgetown University.
Since endorsing Clipper (and advocating passage of the Digital Telephony initiative) Denning has been savagely attacked on the computer nets. Some of the language would wither a professional wrestler. "I've seen horrible things written about me," Denning says with a nervous smile. "I try to actually now avoid looking at them, because that's not what's important to me. What's important is that we end up doing the right thing with this. It was an accumulation of factors that led me to agree with Clipper, and the two most important areas, to me, are organized crime and terrorism. I was exposed to cases where wiretaps had actually stopped crimes in the making, and I started thinking, 'If they didn't have this tool, some of these things might have happened.' You know, I hate to use the word responsibility, but I actually feel some sense of responsibility to at least state my position to the extent so that people will understand it."
The opponents of Clipper are confident that the marketplace will vote against it. "The idea that the Government holds the keys to all our locks, before anyone has even been accused of committing a crime, doesn't parse with the public," says Jerry Berman, executive director of the Electronic Frontier Foundation. "It's not America."
Senator Leahy hints that Congress might not stand for the Clinton Administration's attempt to construct the key-escrow system, at an estimated cost of $14 million dollars initially and $16 million annually. "If the Administration wants the money to set up and run the key-escrow facilities," he says, "it will need Congressional approval." Despite claims by the National Institute of Standards and Technology deputy director, Raymond G. Kammer, that some foreign governments have shown interest in the scheme, Leahy seems to agree with most American telecommunications and computer manufacturers that Clipper and subsequent escrow schemes will find no favor in the vast international marketplace, turning the United States into a cryptographic island and crippling important industries.
Leahy is also concerned about the Administration's haste. "The Administration is rushing to implement the Clipper chip program without thinking through crucial details," he says. Indeed, although the Government has been buying and using Clipper encryption devices, the process of actually getting the keys out of escrow and using them to decipher scrambled conversations has never been field tested. And there exists only a single uncompleted prototype of the device intended to do the deciphering.
Leahy is also among those who worry that, all policy issues aside, the Government's key escrow scheme might fail solely on technical issues. The Clipper and Capstone chips, while powerful enough to use on today's equipment, have not been engineered for the high speeds of the coming information highway; updates will be required. Even more serious are the potential design flaws in the unproved key-escrow scheme. Matthew Blaze's discovery that wrongdoers could foil wiretappers may be only the first indication that Clipper is unable to do the job for which it was designed. In his paper revealing the glitch, he writes, "It is not clear that it is possible to construct EES (Escrow Encryption Standard) that is both completely invulnerable to all kinds of exploitation as well as generally useful."
At bottom, many opponents of Clipper do not trust the Government. They are unimpressed by the elaborate key-escrow security arrangements outlined for Clipper. Instead, they ask questions about the process by which the Clipper was devised -- how is it that the N.S.A., an intelligence agency whose mission does not ordinarily include consumer electronics design, has suddenly seized a central role in creating a national information matrix? They also complain that the Skipjack cryptographic algorithm is a classified secret, one that cryptographic professionals cannot subject to the rigorous, extended testing that has previously been used to gain universal trust for such a standard.
"You don't want to buy a set of car keys from a guy who specializes in stealing cars," says Marc Rotenberg, director of the Electronic Privacy Information Center. "The N.S.A.'s specialty is the ability to break codes, and they are saying, 'Here, take our keys, we promise you they'll work.' "
At the March conference on computers and privacy, Stewart Baker responded to this sort of criticism. "This is the revenge of people who couldn't go to Woodstock because they had too much trig homework," he said, evoking some catcalls. "It's a kind of romanticism about privacy. The problem with it is that the beneficiaries of that sort of romanticism are going to be predators. PGP, they say, is out there to protect freedom fighters in Latvia. But the fact is, the only use that has come to the attention of law enforcement agencies is a guy who was using PGP so the police could not tell what little boys he had seduced over the net. Now that's what people will use this for -- it's not the only thing people will use it for, but they will use it for that -- and by insisting on having a claim to privacy that is beyond social regulation, we are creating a world in which people like that will flourish and be able to do more than they can do today."
Even if Clipper flops, the Crypto War will continue. The Administration remains committed to limiting the spread of strong cryptography unless there's a back door. Recently, it has taken to asking opponents for alternatives to Clipper. One suggestion it will not embrace is inaction. "Deciding that the genie is out of the bottle and throwing our arms up is not where we're at," says a White House official.
The National Security Agency will certainly not go away. "The agency is really worried about its screens going blank" due to unbreakable encryption, says Lance J. Hoffman, a professor of computer science at George Washington University. "When that happens, the N.S.A. -- said to be the largest employer in Maryland -- goes belly-up. A way to prevent this is to expand its mission and to become, effectively, the one-stop shop for encryption for Government and those that do business with the Government."
Sure enough, the security agency is cooking up an entire product line of new key-escrow chips. At Fort Meade, it has already created a high-speed version of the Skipjack algorithm that outperforms both Clipper and Capstone. There is also another, more powerful, encryption device in the works named Baton. As far as the agency is concerned, these developments are no more than common sense. "To say that N.S.A. shouldn't be involved in this issue is to say that Government should try to solve this difficult technical and social problem with both hands tied behind its back," Stewart Baker says.
But Phil Zimmermann and the Cypherpunks aren't going away, either. Zimmermann is, among other things, soliciting funds for a PGP phone that will allow users the same sort of voice encryption provided by the Clipper chip. The difference, of course, is that in his phone there is no key escrow, no back door. If the F.B.I. initiated a wiretap on someone using Zimmermann's proposed phone, all the investigators would hear is static that they could never restore to orderly language.
What if that static shielded the murderous plans of a terrorist or kidnapper? Phil Zimmermann would feel terrible. Ultimately he has no answer. "I am worried about what might happen if unlimited security communications come about," he admits. "But I also think there are tremendous benefits. Some bad things would happen, but the trade-off would be worth it. You have to look at the big picture."
-
 @ d408b55a:7ea8e70a
2023-04-05 01:10:28
@ d408b55a:7ea8e70a
2023-04-05 01:10:28I found it. The Medium/Substack crossover for Nostr. Shoutout Gigi for showing me the way in his recent article. It's called blogstack. Original naming? Clearly not. Badass? Absolutely. https://dergigi.com/2023/04/04/purple-text-orange-highlights/
Thus, I will be copying and pasting all my Mediums over there as well because like Satoshi said "information is easy to spread and hard to stifle."
I'm going to summarize what I got out of Gigi's article. Might even turn it into an article for bitcoinnews.com because it's been awhile since I had my writing shared there and they practice V4V. Nostr is a decentralized protocol for social media. It allows users to create and share content without the need for a central authority. The protocol is based on the idea of a distributed ledger, which is a database that is shared and maintained by a network of computers. This makes it difficult for anyone to censor or control the content that is shared on Nostr.
The Nostr protocol is made up of two main components: clients and relays. Clients are the software that users use to interact with the protocol. The Damus app made by JB55 is a great example of a client for iOS. Relays are the computers that store and process the data that is shared on Nostr. If you have the desire you can even spin up a relay using Umbrel and a raspberry pi. Here is a video on how to do so. When a user creates a post on Nostr, it is signed with their private key. This ensures that the post cannot be tampered with. The post is then broadcast to the network of relays. The relays verify the signature and then store the post. The post is then available for other users to view.
Nostr is a censorship-resistant protocol. This means that it is difficult for anyone to remove or censor content that is shared on Nostr. This is because the data is stored on a distributed ledger and is not controlled by any one entity. There are no username and passwords. Just public and private key pairs. You can view anyone's feed with their public key, but if you want to see private data, like messages, you will need a private key.
Nostr is still in its early stages of development, but it has the potential to revolutionize the way we interact with social media. Devs are pushing code quickly and responding to user feedback. JB55 even spun up a chatGPT bot on the platform so you don't have to go to openAI's website to proompt anymore.

While the anti-censorship part of Nostr is cool that is only the beginning. Nostr's platform provides a value-for-value model, which allows writers to earn money from their work via zaps. On the Nostr protocol sending satoshis (the smallest unit of a bitcoin) just takes a few clicks. This eliminates the need for advertisers and algorithms to show users emotion provoking content in an attempt to keep their attention. Nostr has reduced the friction of value transfer and provided a seamless way for writers and readers to engage with each other in positive ways.
As the internet continues to grow, the amount of information available is increasing exponentially. With Nostr's platform, information is more accessible, and the value-for-value model encourages the creation of high-quality content. This creates a more level playing field for writers, who might not have been able to monetize their work through traditional publishing methods.
While the idea of free information might be daunting to some, the reality is there is no one qualified to be the disinformation police. Propaganda is everywhere. People need to read as much as possible and weigh the bias for themselves. Nostr's model of providing value for value, rather than relying on advertising revenue, creates a more sustainable system for the production and dissemination of quality content. This incentivizes writers to create content that is valuable to readers, rather than clickbait.
Despite being in its early stages, Nostr has already shown its potential to revolutionize the way we consume and share information. The platform provides a unique opportunity for writers to connect with readers while earning money from their work. The value-for-value model is more in line with the principles of a free and open internet, and it offers a refreshing alternative to the traditional platforms that rely on advertising revenue.
In conclusion, Nostr's platform offers a promising future for every single user of the protocol. We are just at the beginning. If you had told someone in 2011 that one day people would be earning Bitcoin by using their credit or debt card, they would have laughed at you. But today, it is a reality. And one day, I am going to tell my grandkids that I was getting paid 1000s of satoshis for shitposting. And they will laugh at me. But not because they think it's ridiculous. They will laugh because they will be amazed at how much money I was able to make for doing something that they enjoy. Also, earning a 1000 satoshis in 50 years is going to be a whole lot harder than it is today. Having both Nostr & Bitcoin empowers both creators and consumers of content like never before. We are creating a more sustainable and equitable model for the dissemination of information. You don't even have to part with your fiat anymore to stack sats anymore. Just provide valuable content on Nostr and people will zap you.
4/4/23
Conor Jay Chepenik
-
 @ 75bf2353:e1bfa895
2023-04-05 01:08:28
@ 75bf2353:e1bfa895
2023-04-05 01:08:28What Backs Bitcoin
People who have spent less than 600 blocks worth of time studying bitcoin like Elizabeth Warren often argue that Bitcoin has no intrinsic value.
``` "No thing that backs it up. That's what makes it different. It's just belief. You and I assess. You assess the value goes up. I assess the value is going down and therefore I buy."
So It's like this artwork?
"No because at the end of the day I can hang that thing on my wall and I can enjoy it or I can throw darts at it."
```
They assert it is "just digital." How do you know it's there if you can't touch it with your hands or see it with your own eyes? They often believe that money needs to be "backed by something," as if they still think the bank has gold in the vault to back up the digits in your bank account. Maybe they think pieces of cotton embossed with presidential portraits back up that money-- but that's not the case. I can't fault them for this. I thought the dollars in my piggy bank were backed by gold held in Fort Knox. As it turns out, it is backed by the full faith and credit of the United States Government. The same government that brought you:
- The Gulf Of Tonkin
- The Iran Contra Affair
- Read my lips: No new taxes
- Weapons of Mass Destruction
- 15 days to slow the spread. ```
“The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts.” --Satoshi Nakamoto ```
We can't trust the United States government officials. Some people think that makes me a waco conspiracy theorist, but we also have to trust the banks, the bonds, thye Federal Reserve with the Interest rates. A CBDC would make us need to trust them even more. Maybe you live in a country that uses a different currency. What is that currency backed by? The full faith and credit of the Venezuelan government? The full faith and credit of Russia? Turkey? Lebanon?Full faith and credit is nothing more than a belief. Despite the poignant accusations of the Senator from Massachusetts and the full faith and credit of her Native American ancestry, the full faith and credit of any nation is the full faith and credit in the honesty of its politicians. I guess this means fiat currency and now CBDC's are backed by something after all: Bullshit.
Does Bitcoin have intrinsic value? Yes, because like gold, bitcoin is backed by physical reality. Wait, I thought Pocahontas said it isn't backed by anything? She wears a pantsuit and makes speeches. She's a US Senator for crying out loud. She must be doing a good job because like all the rest of the Senators we keep electing her again and again. You are just some cartoon robot. Why should we trust you? You haven't even been verified by the Ministry of Truth.
You Should Not Trust Me, You Should Verify The Math
```
" A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network."
Satoshi Nakamoto'' ```
Let's break this down. Bitcoin is peer-to-peer. That means it is run on a peer-to-peer network like BitTorrent. If you've never used BitTorrent, this term might not mean anything to you. BitTorrent is a file-sharing network. People on the BitTorrent network seed bits and pieces of music, movie, audiobooks, and even plans for 3D-printed guns, and porn(of course). You may not like 3D-printed guns, Justin Beiber, or transgender goat porn. Too bad. Those things exist on BitTorrent whether you like it or not.
"Governments are good at cutting off the heads of centrally controlled networks like Napster, but pure P2P networks like Gnutella and Tor seem to be holding their own." --Satoshi Nakamoto

Music, 3D printed gun cad files, and transgendered goat porn are all information. This information is valuable. Value is subjective. I might not find Justin Beiber's music valuable, but Beliebers disagree with me. I don't like grannie goat porn. That's fine. That's what a market is for, determining value via the price system. Beliebers find value in his music. Granny goat porn aficionados find value in granny goat porn,
subjective value
His songs are distributed on centralized servers like Apple music. I would bet a million sats that Apple backs up this music on more than one computer, but I can't say for sure since it is proprietary information. Proprietary information is so valuable that laws are created to protect it. Justin Bieber's bibliography is protected by copyright laws.
BitTorrent is unaware of these copyright laws. 1 mp3 = 1 mp3 according to the BitTorrent software. This software does not make a distinction between copyright and copyleft. The rules of BitTorrent do not discern between legal or illegal mp3s. All are welcome.
For the sake of argument, let's say I seed a copy of Justin Bieber's song. The government of the United States says this is illegal so they destroy my computer. Can someone in Australia still download it? Absolutely! Because that song was not just on my computer. It was on dozens, maybe hundreds of computers. In other words, it is backed up by hard drives all over the world.
According to Clark Moody's dashboard, there are 17,096 nodes on the network as of block height 783,791. (11:08 PST 4-3-2023) These nodes back up bitcoin like the dollar once backed gold With bitcoin, however, no one person can write an Executive Order to shut down all the nodes, effectively taking Bitcoiners of the node standard. All 17,000 of us would need to shut down our nodes to end bitcoin.
What If They Change The Code?
Greenpeace just released the Death Skull commemorative sticker. Most Bitcoiners I know rushed to get one. It looks cool. We also know that changing the code is futile because we have seen the bitcoin code changed many times before. You may have heard of these changes in the code. Centralized, publicly traded companies like CoinBase sell them for fees. We call these code changes shitcoins. Our nodes reject these shitcoins, cryptographic rules that do not follow the rules of the bitcoin software. Coins that changed the code can make transactions on other nodes. Ethereum can make transactions on fully permissioned Ethereum nodes. Litecoin can make transactions on Litecoin nodes. According to Bitcoin nodes, however, these coins are counterfeits and will be rejected. Our nodes define a hard cap of just under 21 million bitcoin. Each whole coin can be divided by 100,000,000. This is how we enforce the monetary supply, by preprogrammed rules distributed over a computer network. As I said before, you can change the code, but 17,049 other nodes will tell you to GFY.
What if I uploaded Metalica's "Enter Sandman" to BitTorrent, but titled it "Baby(Featuring Ludacris)?" Would Bieber fans believe me? Of course not, because songs are not subject to belief. It is based on Consensus. These are not the same songs. Only one is a valid Justin Beiber song. I wouldn't be able to fool a five-year-old kid with this scheme.
Bitcoin works the same way, but instead of verifying the information with our ears, we verify the information with math. To be fair, we can also use this same math to verify songs on BitTorrent, but this is not important. The main takeaway is that the transactions can and are verified using math. You might not be able to hear, taste, smell, or understand this math but you can see it. It can be verified like 2+2, even if you think the answer is 5, nobody else will agree with you. It does not require belief. We can see this with our own eyes, making bitcoin an objective truth duplicated by thousands of computers.
What If I Forget My Password?

Not only is the entire history of every bitcoin transaction backed up by thousands of computers, but people who use Bitcoin must also back up their secret keys which allow them to spend the bitcoin they own which is backed up by the network. A common misconception is to call this a password. Furthermore, as if this was not confusing enough, we can also add passphrases. A secret key is generally 12 or 24 words that represent a 128 or 256-bit number. It is nearly impossible to guess one of these provided it has enough entropy. If a.passphrase is also used, the Bitcoin user will need this as well and it must be exact. There is no room for error as a passphrase creates a whole new wallet.
I'm not going to lie, I'm no politician after all. If you lose your keys or forget your passphrase, you're shit out of luck. There are no bailouts in bitcoin. Therefore, it makes sense to back these things up and use test net before sending real value to your wallets. To back up our private keys, most of us rely on metal. Specifically, military-grade stainless steel with 24 words etched or stamped on them. Again, these are real words that represent real numbers so that real math can be used with them. This is not a belief. We literally back up our keys with steel, at least the smart Bitcoiners do. The point is that we might forget our passwords as you say if we get Alzheimer's or bumped in the head. That is why we back our keys up. Politicians like Elizabeth Warren who say our bitcoin is not backed by anything other than belief are just plain wrong.
In conclusion, Every Bitcoin transaction on the network is backed by silicon and all the components inside our computers. If one of these computers goes down, thousands are still running. We each share a copy of the same ledger. If someone tries to change the code, our computers reject it. I did not get into mining, but the same argument holds. There are thousands of Bitcoin miners doing math too. All of that math is verified by other miners and all the nodes are like a cloud run by thousands of volunteers instead of a corporation or government. The keys we use to make transactions on this network technically do not need to be backed by anything. We could just commit them to memory, but most of us back these keys up using military-grade stainless steel. That's what backs up Bitcoin.
--Blogging Bitcoin, 783,827
This blog has no ads and is reader supported. It uses the Value 4 Value model instead. If you don't know what that is, please click the button bellow.
-
 @ c753997e:9fe20adc
2023-04-04 22:36:17
@ c753997e:9fe20adc
2023-04-04 22:36:17Johnson & Johnson said Tuesday that it will offer at least $8.9 billion to resolve thousands of lawsuits filed by people alleging that the company's products containing talc caused cancer.
In a news release, the health and consumer goods company said that its latest proposal to settle the talcum powder litigation, which is payable over 25 years, is $6.9 billion more than its previous offer in connection with a 2021 bankruptcy filing by its LTL Management unit.
Women have filed a barrage of suits in recent years alleging that J&J's baby power gave them ovarian cancer or mesothelioma, a cancer that strikes the lungs and other organs.
J&J continues to deny that its talcum powder poses health risks, saying that the settlement offer does not constitute an admission of wrongdoing.
"The company continues to believe that these claims are specious and lack scientific merit," said Erik Haas, worldwide vice president of litigation at Johnson & Johnson, in a statement. "However, as the bankruptcy court recognized, resolving these cases in the tort system would take decades and impose significant costs on LTL and the system, with most claimants never receiving any compensation."
J&J has stopped selling its talcum-based baby powder worldwide.
-
 @ c753997e:9fe20adc
2023-04-04 22:17:16
@ c753997e:9fe20adc
2023-04-04 22:17:16On March 29, the US Senate voted to repeal two Authorizations for the Use of Military Force (AUMFs), one passed in 1991 and another in 2002. The repeal now goes to the House of Representatives.
But those Authorizations are irrelevant to the present; they apply only to the Iraq war. A third AUMF, passed in 2001, was left untouched. And that AUMF is the only one that has a bearing on the present moment, because it provides legal cover for the many US military operations, open and secret, around the world.
The 1991 and 2002 AUMFs gave congressional approval for two wars on Iraq, known respectively as Operation Desert Storm and Operation Iraqi Freedom. After the hundreds of thousands left dead and the millions displaced as a result of the US wars on Iraq, the Senate repeal should be filed under “Too little, too late. But good PR.”
2001 authorization of secret wars left untouched
The AUMF of 2001, the one untouched by the Senate, is an entirely different matter. Its content and use are explained in a nutshell here:
“The authorization granted the president the authority to use all ‘necessary and appropriate force’ against those whom he determined ‘planned, authorized, committed or aided’ the September 11 [2001] attacks, or who harbored said persons or groups….
“Since 2001, US presidents have interpreted their authority under the AUMF to extend beyond al-Qaeda and the Taliban in Afghanistan to apply to numerous other groups as well as other geographic locales.….
“Today, the full list of actors the US military is fighting or believes itself authorized to fight under the 2001 AUMF is classified and therefore a secret unknown to the American public.
“The AUMF has also been cited by a wide variety of US officials as justification for continuing US military actions all over the world [emphasis mine]….
“According to a report by the Congressional Research Service, published May 11, 2016, at that time the 2001 AUMF had been cited 37 times in connection with actions in 14 countries and on the high seas. The report stated … ‘Of the 37 occurrences, 18 were made during the [George W] Bush administration, and 19 have been made during the [Barack] Obama administration.’
“The countries that were mentioned in the report included Afghanistan, Cuba (Guantanamo Bay), Djibouti, Eritrea, Ethiopia, Georgia, Iraq, Kenya, Libya, the Philippines, Somalia, Syria and Yemen.”
What does this mean for the present? Here is what Just Security tells us:
“As General Mark Milley, chairman of the Joint Chiefs of Staff, recently (June 2021) testified before the House Armed Services Committee (here at 3:10:45), no current US military operations depend on the 2002 AUMF and thus its repeal would not affect the United States’ ongoing wars. Repeal of the 2002 AUMF costs the Biden administration little or nothing.
“Where the rubber meets the road on AUMF reform is the 2001 AUMF, the principal statutory authority for US military operations in the war on terror. As General Milley explained, the ‘2001 AUMF is the one we need to hang on to … it is the critical one for us to continue operations [emphasis mine].”
But as noted above, those “operations” which take place “all over the world” are a secret, unknown to the American people and the world.
The New York Times was optimistic in its reportage of the Senate action, noting that the repeal might be a stepping stone to dealing with the 2001 AUMF. However, in this case the word the Times used was not “repeal” but “replace.”
(Obama had once spoken of the need to “refine” it.) General Milley must have heaved a sigh of relief as he read those carefully chosen words. He will be able to “continue operations” well into the future.
Flashes of decency quickly extinguished
There were, however, flashes of relevance to the current wars in the debate over the Senate repeal. First was Rand Paul’s Resolution to repeal the 2001 AUMF along with the other two. That failed by a vote of 9 to 86, with four Republicans, four Democrats and one Independent voting yes.
Second was an amendment advanced by Republican Senator Josh Hawley that would create a special watchdog over the $113 billion that have gone to President Joe Biden’s Ukrainian proxy war to cripple Russia. But that bright spot was also quickly snuffed out by a vote of 68-26. Only two Democrats, Jon Tester of Montana and Jon Osoff of Georgia, and one Independent, Kristin Sinema of Arizona, voted for it.
The Times also noted, “Over the past few years, there has also been a pronounced generational shift in Congress and in both parties, where anti-war voices on the left have aligned with ‘America First’ enthusiasts on the right who resist entangling the United States in foreign conflicts.”
That is certainly good news for those who would like to see the survival of humanity, but unfortunately this new breed has not yet gathered sufficient strength to pass legislation like the proposals of Rand Paul or Josh Hawley.
Vatican rescinds Doctrine of Discovery
All in all, these proceedings in the Senate bore an unseemly resemblance to another repeal a day later, this one in the Vatican. That day the Doctrine of Discovery was rescinded. You may not know what that Doctrine states, dear reader, but its spirit is alive and well today.
The Doctrine of Discovery is a legal concept that was developed out of Papal Bulls in the 1400s that granted European Christian nations the right to conquer non-Christian lands and subjugate their inhabitants. By 1493 it had grown into an accepted European legal doctrine that “discovery” of a land by a European nation conferred ownership – even if the land had indigenous occupants.
The Doctrine of Discovery provided a rationale for European colonialism and was introduced into US jurisprudence by Thomas Jefferson and John Marshall. Marshall used the Doctrine in 1823 to justify the expropriation of American Indians’ lands. Needless to say, indigenous peoples in America and throughout the world find the Doctrine repulsive and have demanded that it be “rescinded” for a long time.
Today the Doctrine of Discovery has no force or relevance in the world of policy, and so it can be rescinded. File it under “Too little, too late. But great PR.” Just like the AUMFs of 1991 and 2002 – but unlike the AUMF of 2001, which allows General Milley’s operations to continue and is kept on the books.
In the long view, the Doctrine of Discovery is the “spiritual” forebear of the AUMFs. Its echo can be heard in the “Wolfowitz Doctrine” and in the bloody US drive for global hegemony from Ukraine to Taiwan.
This article appeared originally at Antiwar.com.
JOHN WALSH
John V Walsh, until recently a professor of physiology and neuroscience at the University of Massachusetts Chan Medical School, has written on issues of peace and health care for the San Francisco Chronicle, EastBayTimes/San Jose Mercury News, Asia Times, LA Progressive, Antiwar.com, CounterPunch and others. More by John Walsh
-
 @ f8838597:7ad3e77a
2023-04-04 18:39:19
@ f8838597:7ad3e77a
2023-04-04 18:39:19Porn artists like myself, for whom NIP-36 is a must, have suffered from account bans and freezes on social networking sites for many years. While it may be basically inevitable that porn users will be excluded, shadowbanning on Twitter has forced even the average artist to be concerned about the percentage of skin tones in their images.
How would Nostr benefit such artists? Currently, Gossip and Rabbit are the only clients that have implemented NIP-36 correctly.
And even if NIP-36 is implemented in all clients, there is nothing we can do if more and more spammers start posting pornographic photos without NIP-36. You can block them individually, but it is not perfect.
Nostr's zap feature and NIP-05 verification for artists would be features that would help artists.
We need to figure out how to make Nostr a great protocol that accepts a diverse group of people, including people like me.
Will it be a good place for porn artists like me to exist?
That said, I love Nostr and will be here for a while, even if I can't post pornographic illustrations.
If there are any other NIP-36-like users out there, please let me know what you think.
It's an inevitable problem for using Nostr as a social network.
-
 @ 46fcbe30:6bd8ce4d
2023-04-04 16:10:59
@ 46fcbe30:6bd8ce4d
2023-04-04 16:10:59Different social clients show content very differently and while it's often by preference of the respective developers and not just a missing feature, it results in a mismatch between authors' intended impact and readers' actual impact.
For example:
- You use markdown to have a pretty link but most clients do not render markdown links, resulting in rather ugly "gibberish"
- You react with 😂 and the recipient sees only a ❤️ counter go up - or no reaction at all because the client dev wants to push towards zaps
- You zap an event but the recipient only supports ln tips, not zaps, so while the recipient gets money, others don't see that you liked this content.
- You embed some events in your post and most clients only add a links to those events without rendering them inline
- You mention somebody and clients go all over the place on how that looks. Some render the nip-5, some render the username with the nip-5 domain if present, some show avatars inline and some only show plain npubs.
I think, we need to communicate that these differences exist and we need words to describe them as a first step to help consolidate ways of doing things where desired.
Currently nips describe mostly the network layer - how events should look like in their JSON form but we don't standardize how things should look for the user. At least not to great detail. And while some would argue we have too many nips already, others would argue that we need more - but not in Fiatjaf's GitHub repository. And for that, we need a way to collaborate and collectively curate a body of nips. We will get there ...
-
 @ 42f9711f:8239fb2a
2023-04-04 13:53:16
@ 42f9711f:8239fb2a
2023-04-04 13:53:16Tribune de Konstantin Rabin, écrivain en finance et en technologie.
Je fais partie de ceux qui ont eu la chance d’avoir découvert Bitcoin il y a plus d’une décennie avant qu’il ne gagne l’attention du grand public. Malheureusement, je fais également partie de ces idiots qui ont vu cette opportunité se profiler, n’y ont pas trop réfléchi et l’ont ignorée.
Au cours de ce petit récit, je voudrais vous faire partager le chemin qui m’a conduit à ignorer à investir dans Bitcoin à trois reprises avant de finalement céder et de devenir un HODLer. Voici donc les leçons cruciales que j’ai tirées de cette expérience et qui valent la peine d’être partagées avec ceux et celles qui doutent encore de BTC.
LE COMMENCEMENT
Étant donné que j’ai commencé mon premier emploi à plein-temps dans le courtage en ligne en 2011, cela ne surprendra personne que j’étais entouré de collègues passionnés par le trading et par tout ce qui touchait aux investissements, à la technologie et au progrès du monde de la finance. En peu de temps, je suis devenu ami avec Edgar. Nous partagions les mêmes centres d’intérêt, principalement les jeux vidéo et notre addiction de longue date à la nicotine. Même si nous travaillions dans différents départements et avions peu d'occasions de collaborer dans le cadre du travail, nous nous contactions l’un l’autre pour prendre des pauses cigarettes. Nous parlions de nos vies, de l’univers et de tout le reste en prenant une bouffée d’air frais et de nicotine.
Un jour de 2012, j’ai envoyé à Edgar un message du type “clope ?” avant de remarquer que son statut Skype contenait une sorte de charabia, comme si un chat avait marché sur son clavier.
Cela ressemblait à quelque chose comme : “1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2.”
Alors que nous fumions, je lui ai demandé, “C’était un chat ou ton compte a-t-il été piraté ?” Il a nié les deux possibilités et s’est lancé dans une longue tirade compliquée sur les addresses Bitcoin et la technologie blockchain.
Edgar m’a expliqué avec passion tout ce qu’il savait sur Bitcoin et son enthousiasme m’a immédiatement contaminé - j’ai donc commencé à m’intéresser au sujet. Faisant partie du monde de la finance, j’étais conscient de toutes les arnaques et produits douteux qui circulaient sur le net et qui, comme e-gold, semblaient similaires aux premiers abords. Néanmoins, plus il m’en parlait, moins Bitcoin semblait être un projet malhonnête. À minima, cela en valait la peine de tenter le coup.
Mon problème majeur était que 2012 était ma pire année en matière de santé financière, et bien que 3 730 218 clés publiques étaient déjà en existence sur le réseau Bitcoin à cette époque, je n’avais aucune économie à dépenser pour aller parier sur une technologie nouvelle qui n’avait pas fait ses preuves et qui promettait de “révolutionner” notre relation à l’argent.
Pour le dire franchement, j’étais vraiment fauché. Si fauché qu’à la fin de chaque mois, mes passages au supermarché se résumaient à devoir choisir entre acheter de la nourriture ou un paquet de cigarettes pour tuer la sensation de faim. Au final, j’en suis venu à la conclusion qu’alors que manger de la viande était considéré comme un luxe, parier sur le futur de jetons numérisés ne s’inscrivait pas dans une logique budgétaire saine. À cette époque, bitcoin s'échangeait pour moins de 10 $
LE DOUTE
Avançons en 2015. Ayant passé plusieurs bonnes années au travail, j’avais cumulé les promotions et dirigeais dorénavant la stratégie et l’exécution marketing dans une des plus importantes start-ups de fintech en Europe. L’environnement professionnel était super. La plupart de mes collègues étaient des développeurs de logiciels invétérés qui travaillaient sans cesse à collecter les données bancaires d’individus sans demander de permissions quelconques aux banques. Le bureau arborait même un bon vieux pavillon noir comme sorte de justification pour le travail qui y était mené. Comme vous pouvez l’imaginer, beaucoup de mes collègues étaient de grands fans de Bitcoin et de tout ce que cela représentait.
Puisque j’avais beaucoup progressé professionnellement, les chiffres indiquant mon salaire avaient gagné en zéro. J’avais enfin la possibilité d’acheter des cigarettes et de la nourriture, tout en ayant suffisement d'argent de côté pour subvenir à des temps difficiles. En travaillant dans ce secteur, je savais mieux que quiconque que laisser mon argent à la banque n’était pas la voie à suivre et je commençais donc à réfléchir à comment investir mon capital, puisque je n’avais aucune intention de le dépenser.
J'entendais souvent mes collègues parler de “Bitcoin” au bureau, mais j’étais encore sceptique quant à s’il s’agissait d’un bon investissement. À l’époque, bitcoin s’échangeait pour environ 250 $ après être tombé du haut de ses 1000 $. J’ai approché la question avec mon cerveau d’investisseur bien conditionné et en ai conclu que bitcoin n’allait probablement jamais recouvrir cette perte et qu’il continuerait de chuter jusqu’à ce qu’il ne reste plus qu’une poignée de geeks invétérés pour s’y intéresser encore.
Je gardais quand même un oeil sur les courbes de dominance de Bitcoin et remarquais que, malgré la chute, sa dominance sur le marché restait sans équivoque, ce qui m’a conduit à conclure qu’il s’agissait de la seule cryptomonnaie ayant réussi à accomplir quelque chose, mais que sans concurrence, elle ne parviendrait jamais à devenir vraiment importante.
“Il me faut un produit de placement plus stable pour mes économies,” disais-je à l’investisseur avisé de mon esprit, et j’ai donc acheté 7 500 $ en lingots d’or. Ayant gardé un oeil sur la hausse continue du cours de l’or depuis la crise économique de 2008, cela me paraissait être l’investissement le plus stable possible.
LE REJET
Faisons un saut en 2018, année durant laquelle tout le monde était fou de crypto. À part bitcoin, de nombreuses autres cryptomonnaies avaient emergé et le boom des ICO (Initial Coin Offering: Offre publique de pièces initiale) battait son plein avec plus de 6,88 milliards $ levés par l’intermédiaire d’ICO au cours du premier trimestre de 2018. Tout le monde, y compris leurs mères, parlait de Bitcoin et de crypto. Une visite chez le coiffeur et vous en entendiez parler, et sur Facebook il était impossible de trouver une page qui n’en faisait pas mention d’une manière ou d’une autre ; même mes parents m’ont donné un coup de fil et m’ont demandé si j’en possédais, me disant que je devais en acheter puisqu’ils avaient entendu dire qu’il était probable que le cours monte.
À cette période, j’offrais des services de marketing en freelance, et les affaires allaient bien puisque les ICO bros dépensaient des sommes folles dans n’importe quel service à condition qu’ils puissent payer en crypto. Même si des stablecoins comme USDT étaient déjà présents depuis longtemps, il était rare que les gens les utilisent dans un contexte transactionnel. Je voyais certains de mes paiements arriver sous forme de BTC dans une fourchette de prix allant de 4 000 $ à 13 000 $ par bitcoin.
C’était à ce moment là que j’ai acquis mon premier bitcoin, mais du fait de la folie complète qui frappait l’univers de la crypto, j’ai décidé de vendre toutes mes unités de BTC le plus vite possible à quelqu’un trouvé sur Local Bitcoins. Durant cette période, la volatilité quotidienne était énorme, et — par sûreté — je me dépêchais de convertir mes bitcoins en cash à chaque paiement le plus vite possible.
L’ACCEPTATION
La mi-2018 fut un point tournant pour moi en matière de carrière. J’avais arrêté de travailler à plein temps pour autrui et avais décidé de me concentrer sur le développement de ma propre entreprise. À ce moment là, j’avais réussi à vendre un de mes projets pour une somme conséquente, ce qui m’a permis d’acquérir le capital initial nécessaire pour démarrer ma nouvelle entreprise, alors que les fonds dormant sur mon compte bancaire me donnaient suffisamment de tranquilité d’esprit pour dormir sur mes deux oreilles pendant que ma nouvelle entreprise prenait forme.
La vie était belle. Je possédais déjà quelques propriétés, je gagnais plus d’argent que je ne pouvais en dépenser et j’avais toutes les opportunités professionnelles que je désirais. Tout allait pour le mieux.
Puis, un jour, j’ai eu une épiphanie. Pourquoi devais-je continuer à convertir mes fonds [en monnaie fiduciaire] ? J’avais suffisamment d’argent à la banque et plein d’autres investissements boursiers. En quoi avoir 10 000 $ de plus en mon nom ferait-il quelconque différence sur mon bien-être personnel ?
J’en suis finalement arrivé à la conclusion que cela ne changerait rien, mais que le fait de ne pas avoir de bitcoin pourrait potentiellement me mener à redevenir pauvre. Que se passerait-il si la monnaie fiduciaire devenait un monopole ? Après tout, je n’ai pas vraiment confiance dans le gouvernement, et les individus que j’ai rencontrés au cours de ma vie qui croyaient en bitcoin étaient ceux auxquels je faisais le plus confiance - bien plus que ceux qui n’utilisaient que la monnaie fiduciaire. En gardant cela à l’esprit, j’ai commencé à accumuler le plus de BTC possible. Mon raisonnement était simple : je me fais payer en BTC et je les garde sans jamais encaisser.
QUELLES LEÇONS EN AI-JE TIRÉES ?
Je ne suis pas en colère contre moi-même du fait de ne pas avoir acquis des bitcoins plus tôt. De façon générale, je suis un homme heureux, et malgré la récente période glaciaire que traverse le monde de la crypto, notamment la débandade de FTX, je reste très optimiste quant à l’avenir du secteur. Je voudrais néanmoins partager avec vous les leçons que j’ai tirées de mon expérience avec BTC.
Leçon 1 : On n’est jamais trop “petit” pour investir
Au début, je pensais que ce serait une bonne idée d'acheter 1000 $ de BTC, mais je n’avais pas les moyens de me le permettre et ai donc laissé l'opportunité m'échapper. En général, si l’occasion se présente, il faut la saisir.
Il ne faut pas non plus investir toute ses économies ou se sentir mal à cause de son investissement, mais n’engager ne serait-ce qu’une fraction de ses revenus ne doît pas devenir une décision difficile à prendre. Aurais-je pu me permettre d'épargner 50 $ en 2012 pour acquérir 5 BTC ? Très probablement, mais rien que l'idée d’investir si peu me gênait.
Leçon 2 : Faire des sacrifices est nécessaire
Il a fallu que j’examine certaines de mes expériences passées pour raconter cette histoire car je voulais que les dates soient correctes. Ce faisant, je suis tombé sur une réservation de chambre d'hôtel pour 100 $ faite en 2012. C'était pour une nuit à l'étranger lors d’un voyage touristique avec ma copine.
Oui, dépenser autant pour une chambre d'hôtel en étant fauché n’est pas une décision très judicieuse. Avec du recul, j’aurais pu éviter ce voyage et investir dans BTC à la place, ou j’aurais pu prendre une réservation moins chère ailleurs et acheter du BTC avec le montant restant.
Il est inutile de regretter les décisions du passé, mais souvenez-vous que de faire un sacrifice de court terme pourrait assurer votre sécurité financière de long terme.
Leçon 3 : Équilibrer son portefeuille d'investissement
Tout livre d'investissement explique que “il ne faut pas mettre tous ses oeufs dans le même panier.” Ce n’est pas nouveau, mais c’est un principe que j’ai complètement negligé en 2015. J’avais suffisamment d'argent à investir et avais la volonté d'acquérir du BTC, mais pour une raison qui m'échappe, j'ai pris la décision de tout investir dans un métal précieux. Si je n’avais investi ne serait-ce que 20% de cette somme dans BTC, mon retour sur investissement aurait été considérablement plus grand.
Leçon 4 : Ne pas pourchasser les prix du passé
Une des raisons pour laquelle j’ai choisi d’investir dans l’or plutôt que dans bitcoin était simplement basée sur la perception que j’achetais de l’or à “un bon prix”. Je tenais compte du fait qu’il m'aurait fallu à ce moment donné payer 25 fois plus pour obtenir la même quantité de bitcoin que trois ans auparavant. Avec du recul, je sais maintenant que le prix du présent est le prix du présent — il ne faut pas rejeter l'idée d’investir dans le présent pour la seule raison que le prix à payer semble élevé par rapport aux années précédentes.
Leçon 5 : Faire partie de l'écosystème
Accepter du BTC en guise de paiement et ne pas y toucher est bien plus facile (mentalement) que d’en acheter contre de la monnaie fiduciaire. Si vous offrez des biens et services, pourquoi ne pas permettre à vos clients de régler les factures en BTC ? Éviter juste de commettre la même erreur que moi et de convertir tous vos BTC en monnaie fiduciaire après acquisition.
Gardez au moins une fraction de votre solde intacte et n’y pensez plus pendant un moment. Cela favorisa le taux adoption et continuera à jouer en votre faveur et en celle de l'ensemble de la communauté sur le long terme.
Article original : https://bitcoinmagazine.com/culture/what-i-learned-from-ignoring-bitcoin
Auteur : Konstantin Rabin (@konstantean)
Date de parution : 7 janvier 2023
-
 @ be318ab6:dd25a806
2023-04-04 13:10:00
@ be318ab6:dd25a806
2023-04-04 13:10:00Like many other nostr users (nostriches), I pulled the plug on Twitter in March and moved my social media energy entirely to Nostr to give it a proper test. And same as the most, I won't be coming back to Twitter after this. I'll share a few highlights here about my experience.
Motivation
There have been two sets of reasons for me:
Macro ones
-
I'm concerned about the creeping digital tyranny, censorship, and manipulation abilities of the centralized platforms and state actors. Trusting people that these powers won't be misused is naive (especially after living past few years where we've seen globally the state-coordinated attacks on free speech and freedom). Therefore, I'm eager to support and explore any tools that make individuals and their families more resilient to tyranny.
-
Secondly, I love that it's an open-source tech. If there is a reasonable OS alternative to private closed-source ones, I prefer to support it. I see these as impactful charitable gifts that have the compounding utility for the world - especially if they lower the barriers to entry for new subsequent projects, services, and prosperity.
Personal
- I haven't been able to isolate myself from all the artificial politicization and triggering present on Twitter. The site's definition of engagement has been corrupted over the years. And now more than anything, it maximizes the enragement. And even when going there for particular signals (Bitcoin, Macroeconomics, ...), I got served the enraging noise, and it has stolen way too much time from me.
What have I learned after one month on Nostr:
Good (Nostr winning):
- On nostr, you usually don't see what you don't follow. In the future, this may lead to more bubbles and group-think, but it will lead to more politeness, signal, meaningful engagement on your feeds, and true diversity of global thinking.
- People build on Nostr at an amusing speed. I've never seen devs and designers shipping so rapidly. And this makes me want to get involved more actively.
- Zaps are fun. At first. And valuable forever.
- Ex. It's pretty exciting when @Jack Dorsey reposts your stupid meme, and then your wallet phone notifications get instantly showered with sats. Then the fun novelty effect wears off a bit, but the undisputed utility and its incentives stay. People have the extra motivation to share valuable content and replies. opportunity for content creators
Bad (Twitter winning):
- Twitter still has the network effects.
-
Unless you're a bitcoiner or nostr enthusiast, you might struggle to find enough content you care about on Nostr right now. Myself an amateur economist (same as Paul Krugman), I missed the Macroeconomic news and commentary from the folks on the border of FinTwitter-Bitcoin
-
Missing some of the basic functionality
- Search: Twitter search function could be better, but it usually gets me what I need. Nostr search is a terrible experience for now
- Tagging people - it's so cumbersome/impossible to do on the mobile clients I've been using. Either way, many more positives than negatives. I will keep using the combo of both for different use cases now because, in the end of the day, it's just tools.
Hope
Above all pros and cons, there's the vividly expressed hope. There's this universally shared feeling on Nostr that the platform is the new frontier for freedom and happiness, and every day there's a feeling of a Digital Woodstock lived in the 90s Eastern Europe with the vision of almost limitless possibilities. It's a new and exciting world where everyone's white-pilled about the future, and that's why I'm staying.

Tl;dr: @note1akfxxp4k203wq0wz7tpwykapyv2rs0asvd4ka2qws87jvly4v64qu4jtkv
-
-
 @ c75622fd:a9b66e1d
2023-04-04 12:22:25
@ c75622fd:a9b66e1d
2023-04-04 12:22:25my drawing
Zapathon 2023-03-25



community art












-
 @ 9a576bd9:538775f4
2023-04-04 12:18:11
@ 9a576bd9:538775f4
2023-04-04 12:18:11Nostr
(Notes and Other Stuff Transmitted by Relays) est un nouveau protocole simple, ouvert et résistant à la censure, actuellement les developpeur-euse-s sont concentrés sur la construction d'un réseau social décentralisé basé principalement sur des clés publiques et privées.
Pour atteindre cela les clients vont se connecter à différents relais et vont y publier des messages appelés événements. Nostr utilise la notion de relai simple et client intelligent qui vont se charger de signer les événements à l'aide d'une paire de clés pour authentifier la personne.
 https://nostr.how/the-protocol
https://nostr.how/the-protocolAvec cette approche tout y est public, c'est-à-dire que l'on peut savoir facilement à qui vous parlez dans le cas d'une discussion privée (le contenu des messages est chiffré) ou encore à quelle fréquence vous publiez du contenu.
Le site Web nostrapps.com regroupe des ressources intéressantes et nécessaire pour commencer à interagir avec Nostr
Pour plus de détails, l'article de JohnOnChain sur Découvre Bitcoin est à lire ici: decouvrebitcoin.fr/nostr
Le mixnet
Nym est en train de construire une infrastructure pour protéger votre vie privée, c'est le premier bloc nécessaire afin d'assurer une liberté totale sur Internet.
Semblable à Tor ou i2p, le mixnet de Nym ajoute notamment 2 composantes nécessaires pour atteindre leur but et protéger complétement les utilisateur-trice-s du réseau:
- Faux trafic pour empêcher à un ISP par exemple de savoir quand une personne intéragit avec un service (site Web, porte-feuille bitcoin, …)
- Interval de temps régulier dans les informations transmises pour éviter de déduire l'application utilisée (téléphonie, navigation web, …)
C'est donc sur cette nouvelle proposition de valeur que nous avons voulu avec les membres de Pineapple Proxy expérimenter sur cette infrastructure.
Nostr sur Nym
L'utilisation du mixnet de Nym ne peut donc pas protéger les métadonnées générées lorsqu'une personne interagit avec le protocole mais peut par contre empêcher votre fournisseur d'accès Internet que vous utilisez Nostr, avec quel relai vous interagissez, combien de vous fois vous connectez ou encore les potentielles interactions que vous avez.

Un deuxième point intéressant est le fait qu'un opérateur de relai peut facilement lier votre clé publique avec votre localisation géographique en se basant sur votre IP.
Ce sont essentiellement sur ces éléments que nous avons décidé d'expérimenter Nostr-nym, une application qui permet à n'importe quel opérateur de relai de le rendre accessible sur le mixnet afin de protéger la vie privée des utilisateurs. Nous nous sommes concentrés sur une application générique afin de pouvoir supporter tous les relais (futurs et actuels).
La seule différence pour un utilisateur sera de spécifier un nym-client id (semblable à un nom de domaine) à la place d'une URL dans son client Nostr.
Une étape cruciale doit encore être développée, le fait qu'un client Nostr puisse utiliser un relai uniquement accessible via le mixnet. Pour les besoins de démonstration, un client léger en ligne de commande a pu être développé afin de pouvoir tester le concept proposé.
Donc ?
Nostr sur Nym est pour nous une solution qui permettrait à tout utilisateur-trice-s et d'avoir un droit à la vie privée et la liberté d'expression et ce sans même se poser la question grâce à ce modèle qui l'offre par défaut.
C'est aussi le moment de collaborer et d'assembler un cerveau commun pour arriver à cet objectif qu'est de voir Nostr comme protocole utilisant Nym pour transporter les informations. Cette intelligence collective a déjà donné naissance à une explication de Nostr et une démonstration de Nostr-Nym, le tout disponible ici (en anglais)
Ressources
Nostr
Clients (liste non exhaustive)
Compléments * nostr.how * nostrapps.com * github.com/nostr-protocol/ * www.nostr.net
Nym
A propos de No Trust Verify
Nous sommes membres de la #VerifyValley. Nous soutenons le réseau de Nym Technologies et y contribuons depuis le testnet. Nous sommes heureux de le renforcer avec nos mixnodes et nos gateways.
Développeur de pastenym.ch et isnymup.com
- ✅ Hébergé en Suisse
- ✅ Commission garantie : 5%
- ✅ Bande passante : 10 Gbit/s
Identity keys: * NTV1 : APxUbCmGp4K9qDzvwVADJFNu8S3JV1AJBw7q6bS5KN9E * NTV2 : 4yRfauFzZnejJhG2FACTVQ7UnYEcFUYw3HzXrmuwLMaR * NTV3 : ESPa5xnwZ7BebSX9SGmUbeYgNtkUeJo8PtbBx7JhzEHA
N'hésitez pas à nous contacter : | Site officiel | Twitter | Telegram | Linkedin | Matrix |
-
 @ 166737b1:b860d91f
2023-04-04 09:51:26
@ 166737b1:b860d91f
2023-04-04 09:51:26As I delved deeper into the Nostr network protocol, I found myself struggling to navigate the Nostr Implementation Possibilities (NIPs). Each NIP contains a wealth of information, but it's often obfuscated by noise, making it challenging to understand what each one is trying to convey.
For instance, when I tried to figure out what the
"e"field would do, I went to read through the first document. But instead of finding a straightforward programming guide, I was confronted with blocks of text that read like a nuclear safety manual. It was a frustrating experience, to say the least, highlighted by the fact that the information I needed was buried in the last paragraph, long after its actual use within the same document.To make matters worse, I'm never sure if the NIP I'm looking at is the right one for my problem. And with so many NIPs available, it's difficult to determine which one is relevant. Moreover, searching for information in NIPs is a pain. I often wonder if all the relevant information is contained within a particular NIP or if I should be looking at other NIPs as well.
Furthermore, I find it perplexing that app layer things are being mixed into the "protocol." Why is there a NIP for browser extensions, for example? This NIP, by itself, blocks developers from creating alternative solutions since it's considered canonical. It's worth noting that there is no Ethereum Improvement Proposal (EIP) for
window.ethereum, yet everything still works perfectly fine.The sheer number of NIPs is already mind-boggling. As of April 2023, there are at least 30 NIPs in the repository, with nondescript filenames like
01.mdonly adding to the confusion. There are also 82 open pull requests (PRs), suggesting that people view NIPs more as a validation for their app ideas rather than a base protocol for notes.In conclusion, I believe that if NIPs are necessary for app layer development on the Nostr network protocol, they need to be improved significantly. They need to be clearer, more organized, and easier to navigate. Otherwise, users like me will continue to struggle with them, making it challenging to contribute to the Nostr network protocol's development. One potential solution could be to make them more like traditional programming documentation or create a ChatGPT-like search for NIP content. Since NIPs are describing JSON objects, we could document them as such, making them more accessible to developers and users alike.
-
 @ 05e6367c:6ba9be85
2023-04-03 19:19:33
@ 05e6367c:6ba9be85
2023-04-03 19:19:33我们今天要讨论的是,最近广受关注且具有一定创新性的新型社交媒体协议Nostr-Damus。其中包括Nostr的技术原理、待解决的关键管理问题及如何激励中继持续运转。
第五权利下的新型社交媒体设计已经探索多年,却并没有被大规模采用的迹象。在过去的一年里,随着加密技术的不断发展,以及对马斯克收购推特的担忧,去中心化社交网络迎来新的机会。
这些社交网络试图解决的问题:可能包括加强审查制度,使内容审核更加灵活,削弱大型社交媒体公司塑造和跟踪人们在网上谈论的内容的权力等。
随着新平台的出现和增长,对替代社交网络的选择往往带有政治考虑因素。
如 Getr、Parler、Gab 和 Truth Social 这样站点,都通过将自己宣传为 Twitter 的言论自由替代品来迎合右派。
我们今天要讨论的是,最近广受关注且具有一定创新性的新型社交媒体协议Nostr-Damus。其中包括Nostr的技术原理、待解决的关键管理问题及如何激励中继持续运转。

背景:Nostr
Nostr 于 2020 年启动,是一种去中心化协议,允许用户拥有自己的身份并使用公钥-私钥加密的数字签名来验证帖子。然后,这些帖子会传播到互连服务器网络。该协议并未使用区块链,因为在早期实验中发现区块链对于社交网络来说太慢。但在结构上存在相似之处,Nostr 凭借其自由主义和开源精神在加密人群中找到了早期的利基市场。
Mastodon VS Nostr
Nostr 协议和第一个中继服务器由开发人员 fiatjaf 在 2020 年底创建。在引起广泛关注之前,Nostr 只是一个安静的小众协议,致力于成为 Twitter 和 Mastodon 问题的轻量级解决方案。
Mastodon,一个成立于 2016 年的开源网络,允许任何人设置服务器。该设计通常被描述为“联合”,并且可能属于也可能不属于“Web3”的模糊界限,具体取决于如何定义。Mastodon允许用户加入具有自定义内容审核规则的策划社区。目前注册用户达到200w+,成为了自由派、记者和学者的避风港。
Twitter 和 Mastodon 系统中,身份/用户名是由运行服务器的人控制。
Nostr的核心区别在于:每个用户都使用公钥/私钥对来处理该功能,而不是使用服务器运营商所拥有的用户名,使得Nostr抗审查。这是构建整个 Nostr 协议的核心构建块之一。
“事件”:这是客户端和客户端为了发送和检索消息而连接的中继服务器使用的基本对象/数据类型。该协议的总体思路是,客户端将事件发送到中继服务器,中继服务器随后存储和索引它们,其他客户端可以与中继服务器通信以请求它们已接收和存储的事件。在最初的 NIP 01 中,定义了三种不同的事件类型:
0:发送有关用户的元数据,例如用户名、图片、简介等。
1:发送短信和基本内容
2:推荐中继服务器供关注事件创建者的人连接
所有事件都以特定定义的方式构建。包括创建者的公钥、创建时间戳、类型(或规范中的种类)、内容有效负载和事件创建者的签名。另外,还可以有引用其他事件或用户的标签,并且有一个 ID 值,该值是除创建者签名之外的所有内容的哈希值(类似于比特币交易的 TXID)。
这让用户可以通过验证签名(以及拥有该密钥的人,如果它没有被破坏的话)来保证信息确实是由其中的公钥所有者创建的,并保证信息在他们签署后没有被修改。
就像不能在比特币交易签署后改变它而不使其失效一样,用户也不能在Nostr事件的创建者签署后改变它而不使其成为明显的欺诈。
事件类型系统从最初的 NIP 得到了相当大的扩展。有一种事件类型用于加密的直接信息,通过结合发送方的私钥和接收方的公钥来建立一个共享密钥,其结果与你通过结合发送方的公钥和接收方的私钥得到的密钥相同(这就是BIP 47和沉默支付的工作方式)。也有可替换事件和短暂事件的类型。在可替换事件的情况下(很明显),它们被设计成事件的原始创建者可以签署一个新的事件来替换旧的事件。遵循该规范的中继服务器将自动从其存储中删除旧事件,并在收到后开始向客户提供较新的版本。短暂事件的设计是这样的:当发送到中继站时,它们将被广播给任何订阅其创建者的人,但中继服务器不应该存储它们。这就创造了一种可能性,即在其广播期间,只有在线的人才能看到消息。甚至还有一种事件类型,用来表示对其他人的事件的反应(如喜欢或表情符号)。
说到最后一个问题,事件也可以包含标签。目前有事件(引用一个确切的Nostr事件)、公钥(标记或引用其他用户)和主题(模仿功能,如电子邮件主题)的标签类型。所有这些都可以包括指向特定中继服务器的指针,从这些服务器上可以获取数据,这样用户就可以在不同的服务器上进行实际的互动,也就是说,一个用户在一个中继服务器上发布他们的内容,可以与另一个用户在不同的中继服务器上发布的内容进行互动和引用,这样就可以让任何用户以适当的顺序连贯地获取整个交互线程,而不需要在找出相关数据的地方进行大量的复杂操作。
在原始 NIP 中,给出了客户端如何通过订阅消息/数据结构与中继服务器交互的规范,该结构包括客户端有兴趣接收哪些事件的过滤器。这些过滤器可以根据先前的标准指定用户的公钥、确切的事件、事件类型,甚至是他们想要的特定时间范围。用户甚至可以提交公钥或事件 ID 的前缀,例如“1xjisj ...”。并从以该短字符串开头的公钥接收任何一个或多个事件(这对于从中继服务器隐藏实际想要查看的内容非常有用)。
总的来说,协议是一个非常简单的通用方案,用于在用户之间传递消息,涵盖了重要的事情,例如保证消息的完整性以及使用公钥身份发送消息的人,同时还促进了后端基础设施 中继服务器可以是高度集中的或允许用户运行他们自己的个人中继服务器,同时彼此无缝交互并且在用户被禁止使用一个中继服务器的情况下不会造成大规模混乱。他们可以转移到另一个服务器或运行自己的服务器,并且他们从之前的服务器上脱离平台并不会失去他们的数字身份或追随者,因为他们仍然保持对私钥的控制,并且用户可以在其他地方找到他们时对其进行身份验证。
中继服务器也可以随心所欲地运行:免费运营、收取小额费用来发布或下载消息,甚至还有一个 NIP 要求 hashcash 样式的工作证明来提交消息。它们可以是一个单一的中继服务器,用于托管帖子并将其仅提供给其他用户,或者一个大规模运行的服务器,例如 Twitter 或 Reddit(客户端可以根据需要显示和组织信息,这允许模拟任何社交媒体) 。所有这些都可以无缝互操作,并且不会将用户拒之门外。
Nostr 待解决的关键管理问题
用户公钥/私钥是 Nostr 作为协议工作方式不可或缺的一部分。这起到了实际用户与其他人如何识别他们之间紧密绑定的作用,以防止任何中继服务器解除这两件事的绑定,即将某人的标识符提供给另一个用户。也解决了用平台最大的问题之一:缺乏对用户自身身份的控制。
不过这也引入了新的问题:密钥可能会丢失,密钥可能会受到损害,如果发生此类事件,用户将无法寻求帮助。
这将不可避免地需要一种方案,让用户以一种可验证和可发现的方式从一个密钥对转换到另一个密钥对,并可让他们通过协议与其他用户互动。整个协议是基于证明一个事件来自一个特定的用户(身份密钥),所以一旦某人的密钥被破坏,所有这些保证都会被抛到九霄云外。
Nostr 需要一个实际的密码方案,将一个密钥的轮换与另一个密钥联系起来。开发人员 fiatjaf 提出了一项可能解决此问题的基本方案的提案。基本思想是采用从单个主种子派生的一长串地址,并创建一组“调整后的”密钥,类似于 Taproot 树如何提交给比特币密钥。Taproot 获取 Taproot 树的 Merkle 树根并将其“添加”到公钥以创建新的公钥。这可以通过将该 Merkle 树根添加到私钥来复制,以获得与新公钥匹配的私钥。Fiatjaf 的想法是将承诺从末尾向后链接到开始,这样每个经过调整的密钥实际上都会包含下一个经过调整的密钥用于创建它的证明。
所以,想象一下从密钥 Z 开始,链中的最后一个。你可以用一些东西来调整它,然后返回并使用调整后的 密钥 Z (Z' + Y = Y') 创建密钥Y 的调整版本。从这里您可以获取 Y',然后用它来调整 X (Y' + X = X')。你会一直这样做回到密钥 A,得到 A',然后从那里开始使用该密钥。当它被破坏时,用户可以广播一个包含未调整密钥 A 和调整密钥 B' 的事件。这将包含显示 B' 用于生成 A' 所需的所有数据,并且用户可以立即停止关注 A' 并转而关注 B'。他们会明确地知道 B' 是该用户的下一个密钥,并改为遵循该密钥。
不过,这个提议仍然存在一些问题。首先,必须提前生成将要使用的所有密钥,并且无法轮换到一组全新的密钥。这可以通过在这个方案中提交一个可以公证这种轮换的主密钥来解决,或者简单地从一开始就生成一组非常大的密钥。任何一条路径都是可行的,但最终需要保持根密钥或密钥材料的安全,并且只向 Nostr 客户端公开单个快捷键(Hotkeys)。
然而,该方案不会保护用户或提供在根密钥材料丢失或本身受到损害的情况下进行身份恢复的机制。
为了在这里对潜在的解决方案进行一些讨论,换一种思考,将一个密钥调整为一个主冷密钥,该主冷密钥还必须用于签署从一个密钥到另一个密钥的事件轮换。您有密钥 A',它是通过添加 A 和 M(主密钥)派生的,轮换事件将是 A、M 和 B'(通过添加 B 和 M 生成)以及 M 的签名。M 可以是 多重签名阈值密钥——三分之二、五分之三等。这可能会增加冗余以防丢失,并为密钥轮换提供安全机制。这也打开了使用服务来帮助恢复或将其中一些密钥传播给可信赖的朋友的大门。它提供了与比特币本身的多重签名相同的灵活性。
NIP26 也是一个可能对处理这个问题非常有用的提案。这指定了事件的协议扩展,允许来自一个密钥的签名授权另一个密钥代表它发布事件。然后,“令牌”或委托的签名证明将包含在第二个公钥代表第一个公钥发布的所有事件中。它甚至可以是有时间限制的,因此委托令牌会自动过期并且必须更新。
密钥管理和安全问题是一个非常大的问题,具有非常大的设计空间,充满权衡和痛点。但,Nostr如果不能为用户保护和维护这些身份的完整性,则完全基于用作身份的公钥/私钥对的协议,将不能被大规模的采用。
Nostr 面临的扩展
整个Nostr协议依赖于某个地方的人运行一个中继服务器。没有 "Nostr网络",只有中继和连接到中继的客户端。需要激励人们运行中继器,从长远来看,这最终将是中继器能扩展到什么程度的一个重要部分。除非Nostr中继可以盈利,或者至少可以带来足够的资金来支付自己的运营成本,否则永远不会有与Twitter服务器同样规模的中继。
广告
考虑到 Nostr 作为协议的工作方式,完全阻止广告将非常微不足道,使其成为不可行的解决方案。中继服务器可以尝试使用广告作为一种收入模式,这显然是几乎所有在线免费服务的主要收入模式,但问题在于用户基本上必须选择加入。中继可以很容易地将广告注入到它们发送给客户端的事件中,但如果广告事件不是由它们有意订阅的公钥创建的,客户端也可以很容易地将它们从用户界面中过滤掉。
小额支付
小额支付是另一个明显的解决方案,特别是考虑到目前正在尝试将闪电网络更紧密地集成到 Nostr 应用程序中。这种模式在如何收费方面提供了很大的灵活性。中继可以只对在那里发布事件收费,也可以对下载事件阅读收费,还可以将两者结合起来,并根据两者消耗的资源多少来调整每一种的价格。不过,这种模式能否扩大到像Twitter那样的规模表示怀疑。
内容小额支付在许多基于闪电网络的利基产品中显示出自己的可行性,但真正扩展到全球规模存在两个基本问题。
首先,目前还没有足够的比特币采用。即使每个人都神奇地接受为 Nostr 上的每一次小服务交互付费,也没有足够多的人持有比特币来支持像 Twitter 这样大规模的比特币。中继可以通过法币收取订阅费用,但这些支付方式不会支持为每个发布或下载的事件支付一小部分费用。其次,人们实际上已经习惯了这种免费服务。这正是人们所期望的。我并不认为靠小额支付就能真正支持大规模的中继。
有一种方法可以使小额支付 "更有粘性 "或更有可持续性,而不需要把它们强加给使用中继的每一类用户。关于在Nostr之上建立各种应用的讨论已经很多了,除了Twitter的克隆。GitHub、维基百科,甚至是Uber。
最后一个是关键:经济期望。人们非常习惯于在某处发布招聘广告时支付费用,或在网上订购东西时向市场运营商支付一定的费用,但不会为认为应该免费的商品提供服务—谷歌、推特。这可以为中继站提供一种方法,从他们的用户那里创造一个可靠的收入支柱,而不产生大量的摩擦或打破一般潜在用户的期望。
如果小额支付也将成为一个因素,那么中继运营商将不得不运行一个闪电节点,以便首先从用户那里接收资金。如果与中继实施的任何小额支付模型适当协同,这可能会增加收入。中继服务器的收入越大,它在闪电网络上需要的流动性就越大,以促进这一点。如果运营商正确地规划他们如何在网络中部署或分配流动性,那么除了通过中继接受或传输数据收取的任何费用外,仅运行路由节点的行为本身就可能成为一个不小的收入来源。
结论
Web3 社交项目,除了以上提到的Nostr和Mastodon之外,还包括 Farcaster 和 Lens 等项目,它们并不会快速取代现有的社交媒体平台。据统计,Twitter 有数亿活跃用户,Facebook 有数十亿,但 Mastodon 只有 250 万用户, Nostr 仅大约 22w 个唯一用户身份。许多Web3的社交项目都面临着可用性障碍,这些障碍会减慢大规模采用速度。
媒体与政治必不可分。随着 Web3 社交项目的激增和公共对话在不同应用程序和协议之间的分裂,可能会产生政治结果。即使,墨西拿长期以来提倡去中心化社交媒体,但仍担心去中心化会进一步加剧近年来以相互敌对和误解为标志的公共话语。
-
 @ ce35f2f8:22931a55
2023-04-03 18:59:03
@ ce35f2f8:22931a55
2023-04-03 18:59:03Linux is often overlooked as a gaming platform, but it has come a long way in recent years. While Windows still dominates the gaming industry, Linux is becoming an increasingly popular choice among gamers. In this article, we’ll explore why Linux is a great choice for gaming.
Firstly, Linux is open-source, meaning that it is free to use and distribute. This means that gamers can save money on operating system licenses and hardware upgrades, which can be a significant expense for gamers. Linux also allows gamers to customize their gaming experience, which can enhance gameplay and performance.
Secondly, Linux is lightweight and customizable, which makes it ideal for gaming. Linux-based operating systems are designed to be efficient, which means they use fewer system resources than other operating systems. This means that games can run more smoothly on Linux, even on lower-end hardware. Additionally, Linux users have access to a vast array of customization options, including desktop environments, window managers, and other tools, which can improve their gaming experience.
Thirdly, Linux has a strong community of developers who are dedicated to creating games and software for the platform. This means that Linux users have access to a growing library of games, which includes both open-source and commercial titles. Popular games like Dota 2, Counter-Strike: Global Offensive, and Rocket League all have native Linux versions, and more and more games are being ported to Linux every year.
Fourthly, Linux is a highly secure operating system. This means that gamers can enjoy a safe and secure gaming experience without worrying about malware or viruses. Linux users are less likely to be targeted by cyber attacks than Windows users, which can provide peace of mind when gaming online.
Finally, Linux offers a range of compatibility options that make it easy for gamers to run Windows games on Linux. One of the most popular compatibility tools for Linux is Wine, which allows gamers to run Windows software and games on Linux without the need for a virtual machine or dual boot. While not all games are compatible with Wine, many popular titles, including League of Legends and World of Warcraft, can be run on Linux using this tool.
In conclusion, Linux is an excellent choice for gamers who are looking for an efficient, customizable, and secure gaming platform. With a growing library of games and software, a dedicated community of developers, and a range of compatibility options, Linux is quickly becoming a serious contender in the gaming world. If you’re a gamer who is looking for a new platform to play on, Linux is definitely worth considering.
-
 @ 42f9711f:8239fb2a
2023-04-03 16:59:49
@ 42f9711f:8239fb2a
2023-04-03 16:59:49Nous avons tendance à faire une nette distinction entre les entreprises purement spéculatives et les investissements véritablement sûrs. Cette distinction n'est qu'une question de degré. Un investissement non-spéculatif, ça n'existe pas. Dans une économie changeante, toute action implique une notion de spéculation. Les investissement peuvent être bons ou mauvais, mais ils sont toujours spéculatifs. Un changement radical de conditions peut par ailleurs rendre mauvais des investissements communément considérés comme étant parfaitement sûrs.
— Ludwig von Mises, L’Action humaine, traité d’économie
Il est courant que des critiques s'interrogent sur la rationalité économique des bitcoiners qui épargnent en bitcoin en affirmant que bitcoin n'est rien d'autre qu'un "actif spéculatif". Cela insinue que bitcoin ne vaut rien et ne dérive sa valeur qu'à travers une série d'arnaques ou de jeux de dupes. Alors que cette attitude arrogante permet aux critiques de se sentir supérieurs et de rejeter bitcoin comme étant une technologie et un actif ne méritant pas leur dignité, un tel language les trahit car leur médisance ne fait que révéler leur incompréhension d'une pensée économique fondamentale. La simple réalité est que toute action et tout actif sont de nature spéculative. La question à se poser n'est donc pas de savoir s'il faut spéculer sur bitcoin mais de réfléchir aux façons de spéculer sur bitcoin.
Action, incertitude et risque
Si l'avenir était parfaitement prévisible, il n'y aurait pas besoin de prendre des décisions économiques. Une décision n'aurait donc aucune capacité à influencer l'avenir, car l'avenir serait déjà prédeterminé. Le fait que les hommes agissent dans le but d'affecter les conditions futures à leur profit suggère que l'avenir est fondamentalement et inévitablement incertain.
L'incertitude existe pour deux raisons. Premièrement, nous n'avons pas assez de connaissances sur les phénomènes naturels de sorte à ce que nous puissions prévoir tout condition naturelle future, et il est probable que nous le puissions jamais. Deuxièmement, les préférences humaines sont sans cesse fluides. Les individus changent la façon dont ils prisent des marchandises d'un moment à l'autre. L'apparition de nouvelles connaissances et expériences influence leur façon de penser aux meilleurs moyens à employer pour atteindre des objectifs données, ou même leur désir d'atteindre certains objectifs.
Comprendre l'incertitude nécessite de la différencier du risque. Dans son ouvrage L’Action humaine, Ludwig von Mises le fait en énumérant différents types de probabilité auxquels les individus font face. Nous n'avons jamais assez de connaissances à notre disposition pour formuler des hypotèses précises sur l'avenir, mais il n'y a pas de moments où nous ne disposons d'aucune connaissance non plus. Ces deux types de probabilité, qu'il nomme probabilité de classe et probabilité de cas, traitent des types de connaissances qui nous font défaut.
Mises définit la probabilité de classe comme suit :
La probabilité de classe signifie : Nous savons ou présupposons savoir, en ce qui concerne un problème donné, tout ce qu'il y a savoir sur le comportement d'une classe d'événements ou de phénomènes ; mais nous ne savons rien d'un événement ou d'un phénomène spécifique, hormis le fait qu'ils appartiennent à cette classe.
Lorsqu'un dé est jeté, nous savons qu'il y a une chance sur six qu'un nombre particulier apparaisse, mais nous savons pas quel nombre exact apparaitra. De la même manière, il est possible de déduire la probabilité d'une maladie à affecter une population, mais il est impossible de savoir à l'avance quelle population sera affectée. Lorsque nous avons à notre disposition assez de connaissances et de certitude pour faire face à une telle classe d'événements, nous avons affaire à un risque. La probabilité de résultats est objective, calculable et prévisible. Nous pouvons nous assurer contre de telles probabilités.
En revanche, ce degré de certitude n'existe pas pour tout événement, il s'agit alors d'une probabilité de cas et d'incertitude.
La probabilité de cas signifie : Nous savons, en ce qui concerne un problème donné, certains des facteurs déterminant le résultat, mais il existe d'autres facteurs déterminants dont nous ne savons rien.
L'action humaine se fonde sur une valeur subjective et qualitative, plutôt que sur des données quantitatives mesurables. Il est donc impossible de calculer différentes probabilités de résultats économiques. Il est possible d'utiliser des facteurs, tels que les préférences passées, pour parvenir à juger les résultats d'une action, mais nous ne pouvons pas utiliser ceux-ci pour déterminer la fréquence de résultats précis. Mises prend l'exemple d'un match de football. Les victoires passées d'une équipe peut nous amener à penser qu'elle continuera à gagner, mais cela ne garantit aucunement la défaite de l'équipe adverse. Si ce fut le cas, le match serait ennuyeux et sans intérêt.
En résumé, le risque se résume à des événements dont la fréquence est calculable et contre lesquels nous pouvons nous assurer. Cependant, la plupart des incertitudes auxquelles sont confrontés les hommes se résume à des événements uniques liés à des circonstances individuelles, et contre lesquels nous ne pouvons donc pas nous assurer. Nous devons utiliser d'autres moyens pour faire face à l'incertitude.
Le pari, l'ingénierie et la spéculation
Mises identifie trois méthodes utilisées pour faire face à l'incertitude : le pari, l'ingénierie et la spéculation.
Le pari est utilisé pour faire face à la probabilité de classe et au risque, et ce en pariant sur des cas individuels.
Le parieur ne sait rien de l'événement duquel le résultat de son pari dépend. Tout ce qu'il sait, c'est la fréquence à laquelle un résultat favorable peut se produire lors d'une telle série d'événements, connaissance en fin de compte inutile pour son projet. Sa seule intention est de s'en remettre au hasard.
Le parieur sait que le résultat d'un jet de dé n'a qu'une chance sur six de se produire, mais il parie que le prochain sera le bon. Du point de vue de l'assuré, s'assurer contre ce risque est un pari, car même s'il paie une prime qui reflète la fréquence qu'un mauvais résultat puisse se produire, celui-ci peut aussi ne jamais se produire, et la prime aura donc été payée pour rien. Chaque jour, des gens prennent le pari qu'ils ne se feront pas percuter par une voiture ou qu'ils ne se feront pas frapper par la foudre. Dans un sens, il est impossible de vivre sa vie sans un élément de hasard (à moins de s'appeler Phil Ivey).
D'autre part, si un individu a les connaissances techniques suffisantes pour faire face aux phénomènes naturels avec confiance, il peut affronter l'avenir via l'ingénierie.
L'ingénieur, en revanche, sait tout ce dont il a besoin pour résoudre un problème de manière satisfaisante par le biais technologique, comme la construction d'une machine. À partir du moment où il est capable d'exercer un contrôle sur des éléments incertains du problème, il tente de les éliminer via des dispositifs de sécurité. L'ingénieur n'a conscience que des problèmes qui peuvent être résolus et des problèmes qui ne peuvent l'être dans l'état actuel des connaissances. Il lui arrive parfois de découvrir lors d'événements indésirables que ses connaissances n'étaient pas aussi vastes qu'il ne le présupposait initialement et qu'il n'a pas réussi à reconnaitre l'indétermination de certains des problèmes qu'il pensait pouvoir contrôler. Il tente alors d'y remédier en améliorant ses connaissances. Évidemment, il ne sera jamais capable d'éliminer complètement l'élément de hasard omniprésent dans la vie humaine. Mais son principe, c'est de fonctionner dans une orbite de certitude. Il vise à être en contrôle total des éléments de son action.
Un cycliste ne sait jamais quand il prendra une gamelle, mais s'il porte un casque conçu par un ingénieur compétent, l'incertitude que son tour à vélo se termine avec une fracture de la tête est réduite de manière significative, lui donnant ainsi plus de certitudes sur sa capacité à arriver à destination en un seul morceau.
En revanche, lorsqu'il s'agit d'évaluer des biens ou marchandises, les hommes n'ont pas d'autres choix que de spéculer :
Dans le monde réel, l'homme qui agit est confronté au fait que d'autres hommes agissent par eux-même, tout comme lui. La nécessité d'ajuster ses actions à celles des autres font de lui un spéculateur pour qui le succès et l'échec dépend de sa capacité relative à comprendre l'avenir. Chaque investissement est une forme de spéculation. Il n’y a dans le cours des événements humains aucune stabilité et donc aucune sécurité.
Les préférences peuvent changer pour une raison quelconque, voire aucune. Un bien qui a de la valeur aujourd'hui n'en aura pas forcément demain, et vice-versa. Les individus traitent ce problème par la spéculation. Ils achètent ou vendent des biens aujourd'hui en fonction des conditions qu'ils prévoient pour le lendemain. Cela étant dit, ces décisions ne sont pas prises dans le vide. Les individus utilisent leurs connaissances sur l'état du marché actuel, ainsi que sur leurs préférences, croyances, actions passées, et autres, pour faire des hypotèses sur l'avenir. Ils organisent leur production en fonction de ces spéculations afin d'arriver au futur qu'ils envisagent et pour en émaner un profit. Cependant, ils en tirent un profit uniquement dans le cas où leur jugement sur les désirs futurs des gens s'avère être correct. Puisque l'avenir est incertain, ils peuvent aussi se tromper en produisant des biens d'une valeur moindre à celle attendue par autrui et finir avec des pertes. Les entrepreneurs ayant le plus de succès sont ceux qui sont le plus adeptes à anticiper la façon dont les gens agiront à l'avenir, tandis que ceux qui en sont incapables prennent le risque de perdre de l'argent et peuvent finir par faire faillite.
Les gains et pertes de chaque acteur commercial, à leur tour, servent d'occasions d'apprentissage pour tous les acteurs du marché en leur signalant comment ajuster leur jugement et l'organisation de leur production afin de mieux anticiper l'avenir et offrir aux individus les marchandises dont ils ont besoin. L'incertitude et la spéculation sont alors au coeur du processus de marché. Il incombe à tout acteur commercial de savoir comment répondre aux signaux du marché, générés par la révélation des préférences et actions individuelles, s'ils souhaitent faire des spéculations rentables et entreprises productives contribuant à un meilleur avenir pour eux-même, comme pour autrui.
Tous les actifs sont spéculatifs
L'avenir est toujours incertain, car il n'y a pas de constance dans l'action humaine. La spéculation est inévitable. Toute action vise à améliorer des conditions futures, mais nous ne pouvons que spéculer sur l'avenir qui nous attend. Les préférences changent, y compris les nôtres. Ce que nous désirons aujourd'hui ou ce que nous pensons que nous désirerons demain, nous n'en voudrons peut être pas lorsque demain arrive.
Cela signifie, strictement parlant, que chaque bien que l'on achète ou que l'on vend est un "actif spéculatif." Bitcoin est de toute évidence un "actif spéculatif", tout comme les crayons, les voitures, et les glaces. Alors que vous achetez une glace à la vanille aujourd'hui, il est possible que plus tard vous en vouliez une au chocolat, ou un même un dessert complètement différent. Vous n'auriez pas pu le savoir à l'avance. Vous pouvez seulement exercer un jugement en vous basant sur le fait que vous désirez habituellement une glace à la vanille.
De plus, si vous spéculer sur un actif (ce que vous faites constamment), vous spéculez également sur tous les autres actifs, car l'achat ou la vente d'un bien nécessite de renoncer à l'achat ou la vente d'un autre bien.
Ceux qui dénigrent les "actifs spéculatifs" ont souvent recours au terme péjoratif de "pari". Rhétoriquement parlant, ce n'est pas une comparaison injuste, mais praxéologiquement parlant, c'est imprécis. Bien qu'un individu puisse spéculer sur un actif après une profonde réflexion (comme un bitcoiner) et qu'un autre le fasse après avoir reçu un "bon tuyau" (comme le téléspectateur moyen de CNBC), tous deux utilisent la connaissance de facteurs d'entrée qui peuvent influer sur le résultat de l'événement.
Gérer des actifs spéculatifs, ce n'est pas faire un pari. Comme indiqué ci-dessus, le pari traite de la probabilité de classe, tandis que la spéculation traite de la probabilité de cas. Lorsqu'un individu prend un pari, il sait tout de la fréquence des événements, mais ces connaissances n'ont aucun impact sur le résultat d'un événement particulier. Lorsque nous spéculons, bien que nous ne connaissions pas tous les facteurs pouvant influer sur le résultat d'un événement, nous en connaissons quelques uns. Vous ne savez peut-être pas si vous choisirez une glace à la vanille, mais vous savez bien ce que vous avez tendance à choisir.
Incertitude et argent
Comme mentionné précédemment, un acteur qui souhaite échapper au risque peut se procurer une assurance pour faire face aux imprévus. Cependant, comme l'incertitude n'est pas prévisible, il n'y a pas d'assurance contre celle-ci. Au lieu de cela, les acteurs se tournent vers un bien spécifique, le bien le plus commercialisable : l'argent.
Dans un article intitulé "‘The Yield From Money Held’ Reconsidered", Hans-Hermann Hoppe écrit :
Face à ce défi des aléas imprévisibles, l'homme en vient à priser des biens en raison de leur degré de commercialisation (plutôt que pour leur valeur d'usage en tant que consommateur ou producteur de biens) et envisage de commercer lorsqu'un bien à acquérir est plus commercialisable que celui à céder, de sorte que sa possession faciliterait l'acquisition future d'autres biens et services directement ou indirectement utiles. C'est-à-dire qu'une demande d'instruments d'échange pourrait émerger, soit, en d'autres termes, une demande de biens prisées en raison de leur qualité marchande ou potentiel de revente.
Il continue :
Parce que l'argent peut être utilisé pour satisfaire instantanément un large éventail de besoins, il offre à son propriétaire la meilleure protection humainement possible contre l'incertitude. En détenant de l'argent, son propriétaire a la satisfaction de pouvoir répondre à un grand nombre d'aléas futurs au fur et à mesure qu'ils surviennent de manière inattendue. Investir dans un solde de trésorerie, c'est investir contre l'aversion (ressentie subjectivement) à l'incertitude. Un solde de trésorerie plus élevé diminue davantage l’aversion à l’incertitude.
Il faut cependant noter que cela n'immunise pas l'argent en lui-même contre l'incertitude et la spéculation. Quiconque obtient de l'argent spécule sur le fait que cette acquisition aura plus de valeur à l'avenir que n'importe quel investissement présent et que le pouvoir d'achat qui en découle sera satisfaisant. Bitcoin est peut-être un actif spéculatif, mais le dollar américain l'est aussi.
Conclusion
Étant donné que tous les actifs sont spéculatifs, y compris l'argent, il nous incombe d'examiner l'activité spéculative en fonctions des connaissances et des jugements employés dans le processus de spéculation, plutôt que de se fermer l'esprit en ayant recours à de la gymnastique linguistique.
Dans le cas de l'argent, il est possible d'évaluer à quel point les caractéristiques d'un bien lui permettent de faire face à différents types d'incertitude, que ce soit par le biais de ses propriétés naturelles ou par le biais de l'ingénierie humaine, de sorte qu'il ait une valeur marchande supérieure à tous les autres biens. Cela ne garantit pas l'adoption de ce bien monétaire, mais cela nous permet de comprendre les raisons de son adoption et d'emettre un jugement sur l'évolution future de son adoption.
Si vous avez apprécié cet article, vous pouvez soutenir Michael Goldstein en devenant un abonné payant de son Substack ou en lui faisant une donation en sats (https://rb.gy/onn4uc)
Article original : https://bitstein.substack.com/p/everyones-a-speculator
Auteur : Michael Goldstein (@bitstein)
Date de parution : 23 janvier 2023
-
 @ 42f9711f:8239fb2a
2023-04-03 16:47:47
@ 42f9711f:8239fb2a
2023-04-03 16:47:47Tribune de Jimmy Song, développeur Bitcoin, éducateur, entrepreneur et programmeur fort de 20 ans d'expérience.
Nous avons besoin du travail et le travail a besoin de nous.
Le travail est ce qui permet de transformer un monde rude, brutal et difficile en quelque chose de vivable, plaisant et même profond. C'est par le travail que l'on contribue au développement de notre civilisation, de nos communautés et, bien sûr, de nos familles. Le travail dans un marché normal et fonctionnel génère de la valeur.
Le travail, au sens véritable, représente notre contribution à la civilisation. Le résultat de notre travail est l'empreinte que nous laissons derrière nous. Le travail collectif est ce qui nous permet de construire tout ce qui nous entoure, des édifices dans lesquels nous vivons aux routes sur lesquelles nous nous déplaçons, en passant par les ordinateurs sur lesquels nous tapons, l'électricité que nous utilisons et pratiquement tout le reste.
Néanmoins, cette équation basique — travail productif contre compensation monétaire — ne semble pas fonctionner très bien. On peut en attester au travers des licenciements de masse qui ont actuellement lieu dans tous les secteurs économiques, notamment dans la technologie. Que se passe-t-il exactement ? Comment se fait-il que des dizaines de milliers de personnes se voient perdre leur emploi dans différentes entreprises sans que cela ne semble affecter le fonctionnement des choses ? Que faisaient-ils tous ? Des vidéos stupides sur TikTok ?
Dans cet article, je répondrai à ces questions et imputerai la faute à qui de droit. Comme d'habitude, le coupable est l'argent fiduciaire.
Le travail conduit à la spécialisation
Les marchés fonctionnent car les individus sont prêts à payer pour les biens et services qu'ils convoitent. Quelqu'un paie car le coût — qu'il soit mesuré en prix, qualité, facilité d'obtention ou autre — lui serait plus élevé. La monnaie, c'est-à-dire le moyen d'échange que nous employons au quotidien, nous permet de nous spécialiser et de faire usage de nos meilleures compétences.
Un pêcheur sait comment attraper de larges quantités de poissons, bien plus qu'il ne peut en consommer. Un cordonnier sait comment fabriquer des chaussures, bien plus qu'il n'a besoin d'en porter. Via le commerce, ils ont alors la possibilité d'aiguiser leurs propres compétences pour acquérir les biens qu'ils désirent et dont ils ont besoin. C'est la raison pour laquelle les pêcheurs ne fabriquent pas leurs propres chaussures et les cordonniers ne pêchent pas de poissons.
La civilisation prend forme grâce à cette spécialisation du travail. Dans ce sens, chacun optimise la valeur qu'il génère par unité de temps travaillée tout en minimisant la pénibilité de la tâche. Plus directement, on essaie de faire le plus d'argent possible en faisant ce qui nous déplait le moins.
Ce dernier point est important car il existe des métiers bien rémunérées que les gens ne désirent pas exercer, comme éboueur ou camionneur, et qui bénéficient de taux horaires supérieurs à d'autres activités mais qui sont d'une pénibilité qui en décourage plus d'un. La rémunération du travail augmente en accord avec le degré de pénibilité. De la même manière, les compétences rares sont mieux rémunérées car peu de personnes peuvent exercer les métiers qui les nécessitent. Le travail est comme toute autre marchandise sur le marché, c'est l'utilité de la production qui en découle et sa rareté relative qui déterminent le prix. Les individus qui gagnent le plus d'argent sont ceux qui, en toute logique, font le travail le plus difficile et/ou le moins désirable.
Clairement, quelque chose ne va pas car beaucoup d'emplois bien rémunérés ne sont pas difficiles (travail administratif, groupes de réflexion, etc.) et très convoités (membres de conseil d'administration, banquiers d'investissement, capital-risqueurs). Il y a donc quelque chose dans notre système économique qui ne récompense pas les bons choix.
La monnaie fiduciaire favorise le travail inutile
La monnaie fiduciaire met des bâtons dans les roues d'un marché qui tourne efficacement en introduisant un nouvel acheteur. En fabriquant de la nouvelle monnaie de toute pièce, l'argent fiduciaire permet aux gouvernements de créer des emplois ne générant aucune valeur. C'est ce que l'on appelle des emplois de recherche de rente.
Dans une économie de marché normale, la monnaie sert à compenser toute valeur créée. L'inefficacité y est punie par une baisse, voire une perte de profit. Par conséquent, le travail doit générer de la valeur. Mais dans une économie de monnaie fiduciaire, il existe un nouvel acheteur qui n'est pas sensible aux prix du marché : l'imprimeur d'argent. Généralement, les personnes au pouvoir consomment des biens ostentatoires, achètent du prestige, créent des emplois précaires, distribuent des pots-de-vin à leurs fidèles, etc. Ils génèrent encore moins de valeur que Roger Ver.
Pour les responsables de la planche à billet, le travail ne sert plus à créer de la valeur mais à satisfaire leurs désirs, souvent pour maintenir leur position de pouvoir. En démocracie, les responsables de la planche à billet ont tendance à dépenser dans la création d'emplois aussi inutiles que de creuser des trous pour le simple fait de creuser des trous. En dictature militaire, ces mêmes responsables ont tendance à acheter des votes, des armes et à financer des programmes sociaux. Les emplois sous de tels régimes ne sont souvent qu'une façade servant à occulter le népotisme et la distribution de pots-de-vin. L'argent y est imprimé et utilisé pour maintenir le pouvoir sans créer de valeur pour quiconque.
Dans une économie fiduciaire, lorsque les imprimeurs d'argent deviennent des clients majeurs dans la plupart des secteurs, presque tous les emplois ont vocation à soutirer de la rente. Le travail créant de la valeur se confond avec celui qui n'en crée aucune. Dans la durée, il devient alors difficile de discerner ce qui produit de la valeur de ce qui n'en produit pas, et de discerner ce qui est bénéfique pour la civilisation de ce qui ne l'est pas. La recherche de rente à tout prix se propage telle de la moisissure sur un vieux sandwich.
Par exemple, de nombreuses entreprises ont des départements de ressources humaines spécialisées uniquement dans le respect des questions de conformité professionnelle. Comme dans tout système bureaucratique typique, chaque employé est dans l'obligation d'assister à des formations embarrassantes sur le harcèlement sexuel, les discriminations raciales, les questions acceptables pour les entretiens d'embauche, etc. La plupart n'ont presque aucun lien avec l'industrie dont les employés font partie, mais chaque nouvelle recrue est forcée de perdre son temps précieux sur ce type d'activités. Ces exigences en matière de conformité n'ont pas nécessairement d'implication monétaire, mais elles font perdre beaucoup de temps. De ce fait, le temps de travail est partagé entre tâches productives et improductives. Au cours des 50 dernières années, les tâches improductives ont pris tant d'ampleur que des professions entières n'ont aucune utilité véritable, même dans des sociétés très rentables.
Est-il alors étonnant que des sociétés comme Twitter, Google, Facebook, Microsoft et autres entreprises rentables puissent licencier autant d'employés sans que cela n'affecte leurs opérations ? Les licenciements sont équivalents à de la chimiothérapie ; cela nuit probablement aux sociétés qui en font usage, mais permet aussi de se débarasser d'un cancer sous-jacent.
Friction fiduciaire
La quête permanente de rente ralentit l'économie, de la même manière qu'une crevaison ralentit un véhicule. L'enchevêtrement omniprésent de la monnaie fiduciaire et du monde politique est un des nombreux facteurs contribuant au ralentissement de la productivité, créant un manque à gagner. Le travail que les gens s'efforcent de faire ne consiste pas à créer de la valeur mais à agir comme intermédiaires de transactions de valeur. Ils crèvent des pneus et causent des désagréments majeurs dans l'objectif de vendre plus de pneus.
Par conséquence, il est difficile de générer de la valeur dans une économie fiduciaire, même si la volonté est là. Cette recherche de rente cause de nombreuses fictions qui sont difficiles à surmonter et qui empêche les individus de créer de la valeur. Est-il facile de lancer une entreprise dans la plupart du monde ? Est-il facile d'ouvrir un compte en banque, d'obtenir les permis nécessaires et de se conformer aux règles qui enrichissent les rentiers ? Il ne s'agit pas seulement d'impôts sur l'entreprenariat mais d'impôts sur la civilisation en soi.
Pourquoi est-il alors si difficile d'éliminer cette pratique ? Le problème est que la quête de rente est attractive pour la majorité des gens. La volatilité est bien moindre que celle du marché et les revenus sont en quelque sorte garantis par le gouvernement. Il n'y a pas besoin faire face à des clients difficiles, aux conditions changeantes du marché ou à des concurrents ambitieux. La plupart des gens choisirait volontier de gagner moins d'argent en échange d'une certitude de long terme. En conséquence, même les individus qui génèrent de la valeur ont tendance à rapidement adopter une mentalité de rentier.
La descente vers une mentalité de rentier
Tous les rentiers ne commencent pas de la sorte. Beaucoup adoptent cette mentalité petit à petit sans même s'en rendre compte. On peut remarquer ce phénomène dans certaines des sociétés de technologie à très grand succès au cours des 20 dernières années. Amazon, Facebook et Google étaient de très bons services. Évidemment, une des raisons pour laquelle ces sociétés étaient perçues comme telles est parce qu'elles vendaient leurs biens et services à perte. Dans le cas d'Amazon, l'entreprise perdait de l'argent sur beaucoup de ventes à ses débuts. Facebook et Google offraient leurs services gratuitement. D'ailleurs, cela était possible uniquement en raison des larges sommes d'argent mises à disposition pour les investissements, ce qui est un des effets pervers d'une monnaie fiduciaire inflationniste. Les services fournis étaient donc très bon marché pour les clients.
Mais cela faisait partie de leur stratégie de long terme. Tel un traffiquant de drogue fournissant un premier échantillon gratuit, les utilisateurs sont vite devenus accros. Puis ils ont commencé à vendre des publicités afin de "monétiser" leur public. Monétiser est en fait un euphémisme qui signifie devenir un intermédiaire d'échange pour les utilisateurs. Par conséquent, Amazon, Google et Facebook sont vite devenus des intermédiaires d'échange pour des partis tiers, soit par le biais de publicités ou en devenant des plaformes monopolistiques.
Une fois les utilisateurs séduits, ces entreprises ont également fait en sorte de rendre attractifs les termes pour les vendeurs. La génération de prospects sur Facebook et Google coûtait alors beaucoup moins cher par rapport à ce qui existait auparavant. En peu de temps, les vendeurs étaient devenus accros à ces plateformes et se faisaient exploiter dans un but de monétisation. La disponibilité de l'espace publicitaire était manipulée et les frais d'annonce ne cessaient d'augmenter. Ces plateformes utilisaient de l'argent fiduciaire pour agir comme intermédiaires sur un marché qu'elles controllaient entièrement. À chaque étape, elles s'inséraient dans le processus de création de valeur afin d'en tirer du profit. En d'autres termes, elles sont devenues rentières.
Le pire, c'est que tout était planifié depuis le début. C'est le plan de presque toutes les start-ups depuis des années : attirer un maximum d'utilisateurs et de vendeurs et devenir l'intermédiaire de leurs échanges. Tout financier de capital-risque estime qu'un résultat souhaitable est d'arriver à capturer le maximum de valeur et être capable de défendre ce monopole. Il s'agit de la voie de la profitabilité que toute start-up financée par du capital-risque vise à empreinter, c'est pourquoi le concept de croissance est tant primordial.
Il ne s'agit pas d'un cas isolé depuis 1971. À partir du moment où Richard Nixon a mis fin à l'étalon or, toutes les devises indexées sur le dollar américain sont instantanément devenues des monnaies fiduciaires et les incitations commerciales ont alors changé. La quête de rente est devenue beaucoup plus rentable et— sans surprise — les rentiers ont donc beaucoup augmenté en nombre. Il n'y a dorénavant plus qu'une poignée d'entreprises qui créent énormément de valeur. De nombreuses grandes entreprises dépendent de subventions gouvernementales, de prêts bancaires ou d'une combinaison des deux. De nombreuses entreprises technologiques n'existent que par le biais des financements des capital-risqueurs, c'est-à-dire de prêts bancaires, dans le but de soutirer de la rente. La "fiduciarisation" de l'économie est omniprésente et n'a cessé de croître depuis 50 ans, contaminant même les entreprises les plus productives.
La glorification de la recherche de rente
Pourquoi y a-t-il autant de personnes fraîchement diplomées d'écoles de commerce qui cherchent dorénavant à devenir gestionnaires de fortune ? Car elles imitent les Warren Buffet du monde, une personne qui n'a jamais créé de valeur de toute sa vie et qui n'a fait qu'une chose : gérer l'argent des autres. Il s'agit là du rentier ultime et cela l'a rendu fabuleusement riche. En raison de la suprémacie de l'argent, la quête de rente est devenue une activité prestigieuse. Les héros de cette génération sont des gens comme Warren Buffet et non comme Thomas Edison ou Nikola Tesla, lesquels étaient véritablement productifs.
Heureusement que Bitcoin commence à exposer les rentiers pour ce qu'ils sont vraiment. Les altcoiners s'inscrivent dans la même lignée et ne créent aucune valeur, c'est la raison pour laquelle les Bitcoiners les condamnent si fermement à juste titre. Il n'est pas difficile de détecter ces arnaques qui promettent de l'argent facile en corrompant les individus pour faire la promotion d'altcoins. L'attraction majeure des altcoins est qu'elles permettent à quiconque de devenir rentier en contournant la case école de commerce de renom, sans avoir de réseau politique ni l'approbation des médias. C'est donc de la recherche de rente pour tous, ce qui signifie que personne ne travaille vraiment.
Dans un sens, les altcoins ne sont que l'évolution naturelle de la quête de rente dans un monde dominé par la monnaie fiduciaire. Elles sont complètement improductives et ne disposent d'aucune qualité véritable. La promesse qui en découle est qu'il est possible de faire de l'argent en ne créant aucune valeur. C'est cela qui les rend attractives, mais c'est aussi cela qui est troublant. La plupart des gens peuvent ressentir que rien ne va lorsque des personnes gagnent de l'argent à ne rien faire. Quelque chose ne tourne pas rond et même un enfant de cinq ans est capable de le ressentir. La valeur doit provenir de quelque part et c'est pourquoi il y a toujours une certaine appréhension chez la plupart des altcoiners. Même en période de marché haussier, ils savent que dans une certaine mesure ils jouent avec l'argent du casino qu'ils n'ont pas gagné. En conséquence, de nombreux altcoiners perdent tout leur argent comme des gagnants du loto car ils savent qu'au fond d'eux-même ils ne produisent aucune valeur.
En effet, la valeur extraite de cette activité rentière provient du capital que la civilisation a accumulé sur plusieurs générations. En Occident, la culture de la confiance commence à se désintégrer. La confiance est un bien capital qui prend longtemps à se former. La confiance est la raison pour laquelle on a pu observer un miracle économique au Japon et en Allemagne dans la période d'après-guerre et pas un seul dans le bloc de l'Union soviétique. Abuser de la confiance à des fins de gains monétaires diminue la confiance commune. Ces escroqueries rentières détruisent les semences de la productivité.
La création de valeur
Heureusement que Bitcoin ne permet pas de devenir rentier car il n'existe aucune autorité centrale capable de manipuler le système. Bitcoin accumule du capital car le protocole récompense ceux qui génèrent de la valeur. Le maximalisme toxique dont tout le monde se plaint n'est qu'une réaction contre la mentalité de rentier. Les capital-risqueurs sont des spécialistes de l'extraction de valeur, tout comme les influenceurs. Ce sont des gens qui, lorsqu'ils essaient de soutirer de la valeur aux Bitcoiners, se brûlent à la tâche.
Les entreprises tournant autour de Bitcoin sont plus difficiles à créer car il n'y a pas de place pour la recherche de rente. L'Ethereum Fondation ne vous accordera pas de subventions et les capital-risqueurs de la "crypto" ne vous financeront pas si vous n'avez pas de nouveaux tokens à leur faire promouvoir. C'est cela qui fait la force de ces entreprises et qui les rendent plus intègres, et c'est pourquoi les Bitcoiners sont plus susceptibles de les soutenir. La valeur ajoutée qu'elles apportent est évidente car elles ne dépendent pas de subventionnement en altcoin ou en monnaie fiduciaire.
Bitcoin accumule du capital en favorisant la création de valeur. Et le travail, ça nécessite de faire des efforts, mais ce pas une escroquerie. En d'autres termes, au lieu de devenir des escrocs de la rente, nous pouvons faire en sorte que le travail redevienne honnête.
Rejetez la mentalité de rentier. Soyez productifs.
Article original : https://bitcoinmagazine.com/culture/bitcoin-kills-rent-seeking
Auteur : Jimmy Song (@jimmysong)
Date de parution : 31 janvier 2023
-
 @ 42f9711f:8239fb2a
2023-04-03 16:41:37
@ 42f9711f:8239fb2a
2023-04-03 16:41:37Le fardeau économique de l'inflation continue de ravager les économies du monde entier. Des États-Unis au Royaume-Uni, en passant par la zone Euro, les gens se rendent compte que l'argent dans leur portefeuille et sur leur compte bancaire ne leur permet pas d'acheter autant que les mois précédents. Comme pour tout problème, tout le monde est à la recherche de trois choses : des stratégies, des solutions et des boucs émissaires.
Un des boucs émissaires sur lequel la faute est régulièrement rejetée est le bénéfice des entreprises. Les entreprises sont accusées d'augmenter leurs prix, ce qui crée de l'inflation - ou du moins y contribue - et nous apprauvrit donc tous. Ces prix plus élevés gonflent leur marge bénéficiaire et les entreprises se rient de nous, plébéiens impuissants. La solution à leur imprudente avidité ? Restreindre les prix que les entreprises imposent ou les profits qu'elles amassent.
Cette opinion n'est pas limitée à la personne moyenne. L'Institut de politique économique (IPE), un groupe de réflexion à but non lucratif, affirme que les profits contribuent à l'inflation de manière "disproportionnée". Bloomberg rapporte que les bénéfices d'entreprise ont atteint leurs plus hauts taux depuis les années 1950, et la Réserve fédérale de New York a même publié un rapport sur la question. Comme ces écrits le montrent, cette opinion est partagée par des institutions sérieuses et semble être étayée par des données empiriques.
Néanmois, les bénéfices d'entreprise ne sont pas la cause de l'inflation. Il est facile de le démontrer en réfléchissant un instant aux conséquences de la montée des prix pour une entreprise. Des prix plus élevées signifient que les consommateurs ont moins d'argent dans la poche après avoir payé pour un bien ou un service. Cela signifie par ailleurs qu'ils ont moins d'argent à dépenser pour acheter d'autres biens ou services. Cependant, en période inflationniste, les prix de tous les biens et services augmentent.
Si les consommateurs ont moins d'argent à dépenser en raison d'une montée des prix, comment cela est-il possible ? L'augmentation d'un seul prix signifie qu'il y a moins d'argent à dépenser, mais une hausse générale des prix nécessite plus d'argent à dépenser ! L'augmentation des prix par les entreprises peut expliquer la montée de prix uniques, mais elle ne peut pas expliquer une hausse générale des prix qui caractérise l'inflation.
Si la cause de l'inflation ne peut pas être attribuée à l'avarice des hommes d'affaire, à quoi donc peut-elle être attribuée ? La seule chose capable d'engendrer une hausse générale des prix dans une économie est une augmentation de la masse monétaire. Comme indiqué ci-dessus, une hausse générale des prix nécessite qu'il y ait plus d'argent à dépenser. La seule façon d'y parvenir est d'avoir plus d'argent en circulation. Une augmentation de la masse monétaire signifie que les individus ont plus d'argent à dépenser qu'auparavant, et ils choisissent donc de dépenser cet excédent d'argent. Les entreprises perçoivent une augmentation de la demande et élèvent leurs prix en fonction de celle-ci. Lorsque de plus en plus d'entreprises perçoivent une augmentation de la demande, les prix augmentent partout en conséquence - c'est ce qu'on appelle l'inflation.
Cela décharge les entreprises toute responsabilité concernant l'inflation, mais comment peut-on alors expliquer le lien entre inflation et profits ? Après tout, il semble y avoir une corrélation entre les deux, aussi infime soit elle. Est-ce une coïncidence ou existe-t-il une autre cause pouvant expliquer ce lien positif entre les deux ?
La raison qui explique une hausse des profits en période inflationniste est simple : tous les prix n'augmentent pas en même temps au même endroit. Lorsque de l'argent nouveau entre en circulation, il se retrouve tout d'abord entre les mains d'individus soigneusement sélectionnés. Les premiers à recevoir l'argent fraîchement émis le dépensent, plaçant ainsi le nouvel argent dans les mains d'autres individus qui le dépensent à leur tour, etc. Le fait que ces bénéficiaires détiennent cet argent nouvellement créé en premier signifie qu'ils ont plus de revenus qu'ils n'en auraient eu autrement et peuvent désormais acquérir plus de biens. Ces biens qu'ils acquièrent verront leur prix augmenter, les biens que les seconds bénéficiaires acquièrent avec ce nouvel argent verront également leur prix augmenter et ainsi de suite au fur et à mesure que cet argent ruisselle dans l'économie, poussant ainsi tous les prix à la hausse.
Si tous les prix n'augmentent pas d'un coup, lesquels ont le plus de chance d'augmenter en premier ? Parce que la majorité de ce nouvel argent sera dépensé dans les biens de consommation et les services (contrairement aux entreprises qui l'utilisent pour couvrir leurs coûts), l'augmentation des prix affectera tout d'abord les biens de consommation déjà disponibles sur le marché. Au fur et à mesure que les entreprises répondent à la hausse des prix, il y a une augmentation de la demande des moyens de production pour fabriquer ces biens, ce qui engendre par la suite une hausse du prix de ces mêmes biens. Toutefois, les entreprises ne répondent pas à cette demande instantanément, il y a donc un délai entre la hausse du prix des biens de consommation déjà disponibles et celle des biens produits par les entreprises en réponse à la hausse de la demande.
Que se passe-t-il lorsque le prix des biens d'une entreprise augmentent mais que leurs coûts de production ne changent pas ? Les bénéfices totaux augmentent. Ce n'est pas parce que les entreprises forcent les consommateurs à payer plus cher ou utilisent l'inflation comme excuse pour faire payer les consommateurs toujours plus, mais parce que l'inflation a poussé les prix de certains biens à la hausse avant d'autres, ce qui résulte en une plus grande rentabilité pour les entreprises sur le court terme.
Cette rentrée d'argent imprévue est clairement avantageuse pour les entreprises, mais elle peut également être dangereuse. L'inflation a pour effet de fausser les calculs et d'induire les hommes d'affaires en erreur en leur faisant croire qu'ils sont plus riches qu'ils ne le sont réellement. Ludwig von Mises a abordé ce phénomène dans "L'Action humaine, traité d'économie" :
"Ce serait une erreur sérieuse de négliger le fait que l'inflation génère également des forces qui poussent à la consommation de capital. Une de ses conséquences est qu'elle fausse les comptes et les calculs économiques. Elle produit le phénomène de profits imaginaires ou d'apparence. Si les quotas de dévalorisation annuelle sont déterminés de manière telle qu'ils ne tiennent que peu du compte que le coût de remplacement des équipements usés sera plus élevé que leur coût d'achat initial, ils sont alors insuffisants. Si en vendant des stocks et des produits la différence entre le prix d'acquisition et le prix de vente est enregistrée comme étant positive, l'erreur est la même... [Les hommes d'affaires] pensent avoir de la chance et se sentent alors d'humeur généreuse, ils dépensent et profitent de la vie. Ils embellissent leur maison, font construire de nouvelles demeures et soutiennent le secteur du divertissement. En dépensant leurs profits apparents, le résultat fantaisiste de calculs faussés, ils consomment du capital."
La conséquence de cela est qu'une fois que la réalité s'installe et que les hommes d'affaires se rendent compte que leurs profits n'étaient qu'illusoires, il est déjà trop tard. Ils ont consommé bien au-delà de leurs moyens et sont en conséquence moins riches qu'auparavant. Ainsi, même si l'inflation leur a permis de bénéficier d'une aubaine temporaire, cela peut finir par leur nuire bien plus que cela ne les a aidés.
Doit-on imputer la faute aux entreprises pour l'inflation ? Pas du tout. Une entreprise ne peut pas manipuler les prix selon son bon vouloir, elle ne peut que fixer un prix que le marché est prêt à payer. À la place, la faute ne peut être imputée qu'à l'entité qui contrôle la masse monétaire : la Réserve fédérale. Toute l'agitation et l'amertume accumulées au cours des deux dernières années en raison de sa mauvaise gestion monétaire ne devraient qu'être exclusivement dirigées contre elle.
Pour détruire une mauvaise herbe, il faut la déraciner. Les racines des troubles monétaires contemporains pointent toutes vers cette institution gangrénée qu'est la banque centrale. Si l'on désire une solution permanente au problème de l'inflation, c'est le contrôle de la masse monétaire par l'État qu'il faut déraciner une fois pour toute.
Article original : https://mises.org/wire/profits-do-not-cause-inflation-no-matter-what-progressives-claim
Auteur : J.W. Rich (@thejwrich)
Date de parution : 10 octobre 2022
-
 @ 42f9711f:8239fb2a
2023-04-03 16:26:37
@ 42f9711f:8239fb2a
2023-04-03 16:26:37Dans cet article de blog, la chercheuse principale Natalie Smolenski affirme que les monnaies numériques de banques centrales (MNBC) annoncent l'effondrement des institutions démocratiques américaines. Pour distinguer notre économie politique de celle de nos adversaires autoritaires, il faut rejeter les MNBC.
Aujourd'hui, les États-Unis font face à un choix monumental :
Allons-nous préserver notre tradition de liberté et rester une démocratie représentative qui fonctionne ?
Ou resterons-nous sur la voie de l'autoritarisme et de la projection de puissance mondiale qui a caractérisé notre règne en tant qu'empire mondial ?
De nombreux membres de la classe politique voudraient vous faire croire que nous pouvons avoir les deux - qu'il n'y a pas de compromis entre la république et l'empire. C'est peut-être vrai, pendant un temps. Mais ça ne peut pas durer éternellement. Comme tous les compromis, cela est contraint par le fait matériel de la rareté des ressources : il n'y a aucun moyen d'imprimer suffisamment d'argent, de déployer suffisamment de main-d'œuvre, d'acheter ou de fabriquer suffisamment d'armes, de punir suffisamment de crimes et de contrôler suffisamment d'industries productives pour qu'une paix universelle par la domination puisse être appliquée à l'échelle mondiale, pour l'éternité.
Il est parfois facile pour les gouvernements d'ignorer le fait des contraintes matérielles, puisqu'ils disposent du privilège souverain de l'émission de la monnaie, de la fiscalité et du monopole de la violence légitime. Dans le monde des affaires, cependant, la rareté est souvent plus intuitive. Tout PDG semi-compétent sait que le moyen le plus rapide de faire couler son entreprise est de dépasser son budget dans des activités commerciales ou autres initiatives qui font augmenter les coûts sans générer les revenus nécessaires pour couvrir ces coûts dans les délais requis. Une telle entreprise peut être en mesure de survivre à coup d'injections de capital-risque ou d'autres entrées de capitaux si ses membres dirigeants sont particulièrement doués pour « vendre une vision », mais cette vision finit toujours par se heurter à la réalité, ou l'entreprise s'effondre.
Ainsi en est-il des pays et des empires. Lorsque les dettes arrivent à échéance, les actifs sont examinés et certaines choses doivent disparaître. Souvent, les premières choses à disparaître sont les actifs incorporels - une culture de respect, d'autonomie individuelle et de liberté collective. Politiquement, ces choses deviennent très vite « des choses dont nous n'avons plus le luxe de bénéficier ». Mais les ressources matérielles sont également bradées.
L'expansion et la domination impériale ont toujours coûté cher aux habitants de l'empire. Quoi qu'ils puissent gagner en sentiment de fierté nationale et en afflux de ressources à un stade précoce, ils sacrifient leur qualité de vie au fil du temps. Dans le cas des États-Unis, nous avons vu notre secteur industriel (et notre classe moyenne) se vider ; notre monnaie dévaluée (le dollar a perdu 96% de sa valeur depuis son introduction en 1913) ; des générations de jeunes traumatisés par des guerres à l'étranger qu'ils ne peuvent associer à aucune amélioration de leurs perspectives ou de leur niveau de vie ; une forte augmentation de l'accumulation de biens durables et d'actions américaines par des entités étrangères ; et l'érosion de nos traditions et institutions démocratiques. Les taux d'alphabétisation des américains, le revenu médian réel, l'espérance de vie et les résultats en matière de santé stagnent ou diminuent. La confiance dans le gouvernement, y compris dans le processus électoral, est au plus bas, et les discussions de guerre civile sont plus fréquentes sur les forums en ligne et même dans certains médias grand public. Nous sommes en désaccord sur ce qui est vrai, sur ce qui a de la valeur et sur ce que nous devrions faire ensemble en tant que peuple, sur ce que signifie le projet américain.
Ce sont tous des signes de déclin civilisationnel.
L'Empire romain est un exemple historique instructif. Tout en laissant à désirer, son ère républicaine se caractérisa par une véritable gouvernance délibérative des citoyens romains. Au fur et à mesure que l'Empire s'étendait, cependant, Rome faisait face à des contraintes croissantes en matière de ressources qui conduisaient à des conflits civils intérieurs et, au final, à l'exercice de la tyrannie. Ce n'était qu'une question de temps avant que l'Empire ne soit fragmenté en plus petites régions.
Dans le compromis entre république et empire, l'empire est souvent la voie la plus facile à emprunter. Les dirigeants ambitieux et les démagogues populaires croient souvent que la domination est nécessaire pour qu'un pays soit puissant. Nos principaux adversaires dans le monde aujourd'hui – la Russie et la Chine – choisissent la voie de l'empire en temps réel. Par conséquent, « tranquille » n'est pas l'adjectif qu'un observateur avisé utiliserait pour caractériser la situation intérieure de ces pays. Bien que ces gouvernements exercent des contrôles importants et rigoureux sur la presse ainsi que sur leurs populations, ils n'arrivent pas à contenir complètement les récits de pauvreté, de corruption, de protestation et de violations des droits de l'homme qui caractérisent leurs réalités politiques.
C'est en gardant ce contexte à l'esprit que le Bitcoin Policy Institute a publié notre livre blanc, "Pourquoi les États-Unis devraient rejeter les monnaies numériques de banques centrales (MNBC)". Les MNBC ne sont que l'exemple le plus récent du lent resserrement de la corde autour du cou de la république américaine - surveillance et contrôle au nom de la stabilité politique et de la suprémacie américaine sur le monde. Le principe derrière les MNBC est simple : éliminer l'argent liquide, dernier vestige des transactions financières autonomes, et donner à l'État une visibilité totale sur toute l'activité économique à toutes les échelles sociales possibles. En tant que monnaies programmables, les MNBC serviraient d'outil de politique monétaire : taux d'intérêt négatifs, confiscation directe des devises et capacité de contrôler quand, avec qui et combien d'argent n'importe qui effectue des transactions, partout dans le monde.
Tout simplement, l'introduction des MNBC élimine une pierre angulaire des libertés politiques - la liberté de commercer - et présume que les citoyens sont coupables jusqu'à preuve du contraire. Cela renverse la charge de la preuve de l'État à l'individu, aggravant un déséquilibre de pouvoir déjà flagrant.
Pire, la plupart des Américains ignorent complètement ce que sont les MNBC, ou que la décision de les mettre en place ou non est déjà bien engagée sans véritable délibération populaire. C'est un autre signe de l'effondrement des institutions démocratiques. L'avènement imminent des MNBC devrait générer un sentiment d'urgence : c'est un signal d'alarme que la fenêtre pour sauver notre république est en train de se fermer.
En bref, les MNBC ne sont qu'un symptôme de la consolidation du pouvoir étatique au détriment du pouvoir individuel, une tendance mondiale qui s'intensifie au rythme du développement technologique. Pourtant, un système de gouvernement républicain dépend d'individus autonomes – une société civile autonome – pour fonctionner. Au fur et à mesure que les gouvernements augmentent leur contrôle sur la société civile, même si leur justification est que c'est « pour le bien du public », ils détruisent la possibilité d'une autonomie populaire et consolident le système gouvernemental par les élites. Au fil du temps, cela devient un cercle vicieux : un contrôle accru de l'élite devient nécessaire pour appliquer un système de plus en plus obscur à une population récalcitrante et impuissante, dont les voies de contestation et de dissidence se rétrécissent progressivement. Cela crée les conditions de la violence comme seul recours de contestation politique.
En rejetant les MNBC, le gouvernement américain peut déclarer que l'autonomie individuelle est une valeur fondamentale de notre système politique. Mais si nous voulons vraiment redevenir une république, le peuple américain doit faire plus : nous devons révoquer le chèque en blanc que nous avons écrit pour que notre gouvernement fasse la guerre à sa seule discrétion et agisse comme le gendarme du monde. Ce chèque en blanc a accumulé une dette souveraine – à la fois fiscale et morale – qui arrive maintenant à échéance, et c'est le peuple américain qui paie les factures.
Le huitième secrétaire d'État américain et sixième président, John Quincy Adams, a déclaré que l'Amérique « ne va pas à l'étranger à la recherche de monstres à détruire. Elle est la bienveillante de la liberté et de l'indépendance de tous. Elle n'est que la championne et la justicière de la sienne. Elle inspire la cause générale par la contenance de sa voix et la bienveillante sympathie de son exemple. »
En d'autres termes, l'influence la plus puissante que l'Amérique puisse avoir sur le monde est de continuer à être qui nous sommes : en vivant nos valeurs. Dans un passé récent, nous avons sacrifié ces valeurs dans la poursuite de l'empire, au détriment à la fois du peuple américain et du monde. Nous ne pouvons pas simplement inverser le cours - après tout, on ne peut pas changer le passé - mais nous pouvons et devons choisir de devenir meilleurs à l'avenir.
Nous pouvons le faire. Il n'y a jamais d'arrivée définitive au pôle idéal d'une union plus parfaite, il n'y a que sa poursuite de bonne foi. Tant que suffisamment d'Américains sont engagés dans ce projet, nous sommes la république que nous prétendons être.
Article original : https://www.btcpolicy.org/articles/republic-or-empire
Auteur : Natalie Smolenski (@NSmolenski)
Date de parution : 31 janvier 2022
-
 @ 42f9711f:8239fb2a
2023-04-03 16:12:53
@ 42f9711f:8239fb2a
2023-04-03 16:12:53Artur Marion Ceolin est doctorant en économie à l’Université Rey Juan Carlos et boursier d’été à l’Institut Mises en 2022.
J'ai récemment publié un article dans le Mises Wire intitulé « Woke Egalitarianism and the Elites » (lit: L'égalistarianisme woke et les élites) dans lequel je présentais les vrais motifs se cachant derrière l'égalitarianisme woke. L'article décrit également la façon dont les élites tentent de rebâtir la société à travers le prisme du collectivisme. Mais plutôt que de discuter des objectifs du progressisme, il est nécessaire de discuter du fondement intellectuel de ces tentatives. Quelles suppositions et quel cadre intellectuel guident ces actions ?
Le progressisme se fonde sur le manque de respect des individus, de leurs actions et de leur capacité à choisir. En premier lieu, le progressisme groupe les personnes en collectifs selon des critères particuliers (ex: race, genre et orientation sexuelle). De plus, le progressisme homogénéise leurs pensées, leurs valeurs et leurs actions selon ces classifications de groupe. Pour les progressistes, les individus ne peuvent pas échapper à ces classifications.
Cette homogénéisation reflète les opinions progressistes vis-à-vis de l'humanité. Les progressistes comprennent mal l'action humaine et l'individualité de chacun. Ils ne se rendent pas compte que chaque personne est unique et souveraine. De plus, les individus ont la capacité et la liberté de juger en sélectionnant les options qu'ils considèrent comme étant les meilleures et en agissant de la façon qui leur semble la plus appropriée.
Les penseurs autrichiens, dans leurs débats avec les chercheurs objectivistes positivistes, affirment depuis longtemps que les individus ne sont pas des atomes. Les individus ne réagissent pas en fonction de relations causales objectives et probabilistiques qui peuvent être décrites de façon mathématique.
Chaque esprit dispose d'une capacité unique à percevoir et créer des opportunités en agissant selon une échelle de préférences individuelles et la capacité à percevoir la relation entre fins et moyens.
En outre, les individus ne peuvent pas être classés en groupes. Les groupes n'agissent pas. Qu'est-ce qui fait que l'action collective est une composition d'actions individuelles ? Les groupes sont des abstractions créées par l'esprit humain dans le but d'analyser des phénomènes. Mais ceux-ci n'ont pas de fondement ontologique.
Le progressisme ne permet pas non plus de comprendre la façon dont les individus peuvent altérer leurs actions avec le temps. Les individus ne sont pas des machines qui répètent des procédures imposées par quelqu'un ou l'environnement. Les individus font preuve d'autonomie et utilisent leur raisonnement logique pour changer le cours de leurs actions. Par conséquent, ils changent aussi l'histoire.
Les individus ne sont pas programmées pour se comporter d'une manière déterminée. Les individus créent du savoir continuellement. Cette capacité à apprendre est ce qui permet de guider le développement institutionnel. Le mécanisme d'apprentissage par tâtonnements est ce qui a rendu possible le développement d'institutions telles que la monnaie, le droit, le système de prix, etc.
Pour l'élite progressiste, les individus sont « stupides » et se font facilement duper. C'est ainsi que les progressistes expliquent pourquoi certains individus ne soutiennent pas leurs actions : ils manquent de conscience (de classe, de genre, de race, etc.). C'est également ainsi qu'ils justifient leur propre existence : les mouvements progressistes doivent défendre ces groupes. Même si ces groupes ne veulent pas de soutien, ces mouvements doivent exister pour sensibiliser les consciences à l'oppression existente.
Les progressistes ignorent complètement le rôle des individus dans la création de l'histoire. Selon eux, les personnes réagissent comme des atomes. Selon eux, les personnes ne créent rien et ne s'impliquent pas dans le processus d'évolution sociale. Ils ne se rendent pas compte que les hommes ne peuvent pas être façonnés comme de l'argile. Les individus sont uniques, ils disposent de la capacité à décider et à créer. Le monde humain n'est pas acquis mais construit par l'action humaine.
Ce mépris nocif pour l'individu se fonde sur une caractérisation erronée de l'humanité. Le progressisme, c'est le constructivisme. Le constructivisme se fonde sur l'idée que les hommes répondent à des incitations et règles externes. Le constructivisme affirme que la société peut être façonnée du haut vers le bas par de l'ingénierie sociale.
Le constructivisme ne conçoit pas les individus comme agents créatifs qui construisent l'histoire. Il rejette la capacité des êtres humains à développer des institutions qui régulent leur comportement social. Il conçoit les individus comme des jouets avec lesquels les régulateurs et ingénieurs sociaux peuvent s'amuser.
L'humanité est en train de traverser une nouvelle tentative socialiste visant à détruire la civilisation occidentale. Au XXème siècle, ils ont utilisé les « prolétaires » ; ils utilisent dorénavant les « minorités ». Combattre ces tentatives requiert une défense structurée de la liberté et créativité humaines.
Voici la place que tient l'école autrichienne, avec sa compréhension de la subjectivité humaine. C'est la raison pour laquelle nous devons diffuser l'école autrichienne à travers le monde. L'humanité a besoin d'idée qui renforcent l'autonomie individuelle et le respect de leur liberté, de sorte qu'il devienne possible de défier le progressisme et ses conséquences maléfiques.
Article original : https://mises.org/es/wire/la-economia-austriaca-se-opone-al-colectivismo-del-pensamiento-progresista
Auteur : Artur Marion Ceolin (@artceolin)
Date de parution : 3 mars 2023
-
 @ 9ca0bd74:4052340b
2023-04-03 13:16:24
@ 9ca0bd74:4052340b
2023-04-03 13:16:24Not being too strict with 'cyberpunk' here, might be some which are more cyberpunk-adjacent lol (please drop recommendation)
Nirvana (1997)

Trancers (1984)

Cyborg (1989)

Virtual Nightmare (2000)

Possessor (2020)

Strange Days (1995)

Repo Man (1984)

World On A Wire (TV series - 1973)

Cold Lazarus (TV series -1996)

-
 @ 05e6367c:6ba9be85
2023-04-03 11:47:24
@ 05e6367c:6ba9be85
2023-04-03 11:47:24如果媒体公司是唱片公司,创作者是摇滚明星,那么观众就是粉丝——这就引入了一个全新的商业机会。媒体和音乐一样,只有当观众和创作者一起走在一条路上,给对方机会来定义对方时,才能蓬勃发展。这是一条双向的道路,而不是一个自上而下的指令。但是,当一个创作者或艺术家影响大到其观众开始在他们的作品之上建造产品时,会发生什么?
如今媒体正在加速走向颠覆。我们可以看到,平台和服务上新媒体品牌(微标签,micro-labels)的发展,媒体公司将人才作为核心业务支柱的优先级,以及商业模式从内容导向转变为创作者导向。
随着创作的每个组成部分的发展,媒体业务公式中最关键的部分也发生了另一种演变:消费者。在媒体业务中,商业模式推动产品战略。虽然这是产品背后的驱动力,但它取决于消费者的兴趣、参与度和忠诚度。这意味着随着经济的转变,对消费者价值的需求也会转变。这是一个建立新业务的机会,该业务将创造者和消费者的关系放在首位,并引入所有权元素。这是粉丝圈和亚文化的生意。
创作者应该负责引出和制造亚文化。
亚文化是作为对已有文化的回应而发展起来的。就音乐和媒体而言,预先存在的文化或分类就是流派。传统上,希望融入已有的流派对艺术家来说是有益的。流派广泛地设定了听众或读者对该类别中的艺术家或创作者的期望。基础由现有的受众和现有的商业模式建立。
其目的是突破流派,创造一个属于自己的亚流派(亚文化)。从两方面考虑:创造者(或标签)根据流派发展自己的身份,如Sub-Pop,而歌迷则根据它发展自己的身份和亚文化,如Punk。在小众时代,这种方法是完全相反的。与其说是为更多的观众创作,现在的时尚是为特定的少数人设计。这不是关于规模,而是关于想要它的观众的质量。通过这样做,创造者不仅为自己开辟了一个独特的价值口袋,而且他们的社区也开始从已经创造的价值中构建一个身份。
创作者和消费者之间的关系比其交易货币(即内容)更有价值。在这个媒体时代,内容不是唯一的产品。内容是价值的关键部分,因为它是保持一致性的工具,但创作者和社区是产品。真正的价值是消费者和创作者之间通过各种接入点获得的联系,最终发展出消费者利益。随着业务从内容即价值转向创作者即价值,我们也应该转移支持它的商机。消费者建立在品牌之上。
对于创作者来说,文化是指他们的品牌非常易于传播,商业和社区建立在创作者本身之外。如果成员资格能够产生身份认同,而身份认同能够建立品牌,那么文化就是永恒的。当消费者成为创造者,并将他们的价值不仅与创造者环境内的建设相关联,也与创造者环境外的建设相关联时,创造者就成为了一个平台。由于消费者对其品牌的承诺和奉献,企业正在建立在创造者之上,与他们的参与分开。创作者是平台,在这个例子中,这种关系不仅与内容、创作者和社区有关,而且与亚文化本身的发展有关。而观众不是商品,相反,观众将自己视为品牌的一部分,并将他们自己的想法与他们的消费和与创作者的互动联系起来。这方面的一个例子是Phish乐队。
通过Phish的音乐、品牌和社区,整个亚文化围绕该集团发展,以至于在乐队的直接参与之外建立了企业、身份和社区。Phish是创作者,但他们创作的本质(即音乐和社区)和他们的文化发展已经将他们的粉丝变成了创作者。他们可以利用Phish的受众来发展自己的受众,从而扩大品牌和文化。就像The Grateful Dead的调整场景一样,Phish已经将自己打造为消费者(在这种情况下为粉丝)建立业务的平台。结果,品牌通过他们在社区业务基础上的关联而变得不朽。在Phish亚文化中,有许多粉丝建立的跨各种行业的场所。
由Scott Marks和团队运营的 Phish.net可以实时编辑乐队及其相关项目的演出列表、新闻和分析。幻想之旅(Phantasy Tour),一个由粉丝为粉丝开发的reddit式论坛,已经成为所有粉丝讨论任何事情的事实平台。在这里,一位粉丝(也是我的一位亲爱的朋友)正在为他的新房子寻找中世纪的现代家具。第一个帖子最多有499条回复(499条!),然后又蔓延到了第二个帖子。他选择了Phantasy Tour,并找到了完美的椅子。
由粉丝开发、设计和分发的完全强大的商业生态系统是存在的。受乐队影响,独立运行的JEMP电台和Phish Just Jams是建立在目录之上的音乐应用程序,用于服务于特定的兴趣和利基(niche)。粉丝摄影师围绕他们的艺术建立了整个业务和声誉,我最喜欢的一个是AZN。在乐队所在城市的现场活动中,甚至还有一个实体商业市场。除了商业,不断增长的亚文化还有很多社会效益。例如,Phellowship是一个由选择不吸毒和酗酒的粉丝组成的粉丝领导小组。
在Phish定义的文化中,亚文化现在决定了品牌的身份和长寿的能力,使其能够永久存在。歌迷们自己也在通过商业来定义文化和品牌。当然,这花了30多年的时间,而且一直在增加。
有趣的是,随着媒体运营和平台的分拆和重组,整个朝着创作者经济的运动本身就是一种媒体亚文化。创作者和支持平台和服务正在寻求通过建立自己的天意来挑战媒体机构及其结构的解释权威。对于一些创作者来说,这与业务无关,而更多地与打破体制、促进个人自由和构建自己的环境的愿望有关。许多独立的个体可能比留在机构中挣得更少,但这不是重点。这是一个信号,既表明现有企业需要如何准备应对挑战者,也表明企业需要如何建立以提供亚文化动力平台。
音乐永远与亚文化和粉丝相关。Phish不仅使消费者成为创造者,而且使他们成为所有者,从而将其提升到了一个新的水平,并在这个领域一会处于领先地位。与本篇文章中强烈坚持的机会相反,他们将很难被复制。媒体业务传统上是围绕内容构建的。多年来,在《纽约客》蓝色包袋、《纽约客》手提包中,一直有文化驱动商业的迹象,但大多数这些尝试都徘徊在会员资格的边缘,远不及亚文化的制造。我们看到新媒体公司开始努力抓住这个机会,将消费者身份从订阅者转变为会员,转变为将品牌视为其文化一部分的人。作为商业模式驱动产品战略,制造亚文化的业务不能只是一种现象,它也必须是品牌增长的源泉。鼓励粉丝,并转向一个消费者成为创造者的环境,是对品牌的保险和未来证明。
亚文化随着时间有机地发生,但它们可以被推向一个方向并加速发展。这仅与品牌理念有关——为了推动文化,品牌必须有一家之言 为了推动亚文化,必须引起自己有观点的消费者的回应。触发这种情况的一种方法是解锁品牌。权利管理很重要,文化是由商业驱动的,但把它控制得太紧意味着你失去了赢得媒体的潜力和你的消费者成为创造者的能力。让消费者成为创造者对品牌有好处,尤其是如果它是在考虑品牌的情况下构建的。最终的目标是让品牌与消费者身份密切相关,有些人甚至围绕它塑造他们的生活或业务。
另一个很好的例子是K-pop轰动一时的BTS背后的代理商Big Hit。他们最近进行了首次公开募股,并被机构和散户投资者大量超额认购。粉丝们实际上是在为艺人的成功投资,并鼓励他们做得好。第四面墙正在被打破。
BTS不会永远年轻。K-Pop Sensation的所有者需要新的热门歌曲。
韩国流行音乐或K-pop风靡全球的同时也在震动金融市场
有许多新兴的创作者正在通过社区建设文化,通过时间和承诺,将引发亚文化。正如上面定义和展示的,亚文化的业务不同于亚文化的发展。这是关于将粉丝角色的期望从被动的消费者转变为实际的业务创造者。游戏领域有很多动力,尤其是由MrBeast和Ninja等公司建立的商业、品牌和社区,我期望这是他们品牌扩张的下一阶段。
环境变了,平台也变了。这个机会真正植根于数字领域。随着媒体公司努力成为唱片公司,独立创作者创立自己的品牌,或与他人合作创建自己的微型标签,商业模式应该遵循。在我们拆分和重组媒体公司的运营结构时,我们应该同样拆分和重组我们推动该业务的方式以及我们将价值的重点置于之处。如上所述,这是从内容作为价值到创作者作为价值的转变。随着我们进一步从内容转向创作者,现有的订阅和会员结构将限制品牌在下一个时代扩张的机会。
因此,我们进入亚文化业务,专注于打造把品牌作为平台。那些投资于与粉丝建立更深层次联系并使他们成为代表品牌的创作者的人将遥遥领先。媒体行业面前有一个绝佳的机会,我很期待看到你们都建立了什么。
-
 @ 05e6367c:6ba9be85
2023-04-03 11:45:39
@ 05e6367c:6ba9be85
2023-04-03 11:45:39在过去的二十年里,免费平台已经使内容商品化和贬值。一段强有力引述,描述了这一现状:
“如果我在 30 分钟内完成一项工作,那是因为我花了 10 年时间学习如何在 30 分钟内完成这项工作。你欠我的是年,而不是分钟。”
然而,Web3创造数字稀缺性的能力有可能导致这一趋势的逆转。今天,本文将:
分析创作者经济的发展史和Web3 的作用 回顾创作者经济的现状及其面临的一些关键问题 深入探讨 Web3 所有权经济在创作者经济中的效用 探讨创作者所有权经济的现状和创作者可用的工具 尝试预测创作者经济长期发展趋势
Part.1 背景设定
关于创作者及创作者经济尚未有统一的定义,为了更方便的探讨,我们首先通过一些关键定义来设定背景。
创作者:制作具有教育和/或娱乐价值的媒体个人(或一群人),其目的是增加观众。 创作者经济:创作者阶层(以数字发行为主导)的崛起,他们通过创作内容和以各种方式将观众货币化来赚取收入。 所有权经济:所有权经济是指下一代的产品/服务将由其参与者通过使用代币化的激励机制来拥有和运行。这渗透到所有的行业--娱乐、去中心化的金融、基础设施、消费等。
 图1: 创造者和所有权经济之间的关系
图1: 创造者和所有权经济之间的关系Part.2 创作者经济发展史
为了更好地理解创作者经济是如何随着时间的推移而演变的,我们将其分为四个不同的时代——爱好者时代、分发时代、独立时代和所有权时代。
1.爱好者时代始于Myspace、Friendster等社交平台的兴起,以及Facebook的早期发展。这些平台的特点是双向关注,关注你在现实生活中认识的人,没有价值积累。
2.随着“影响者”类创作者以及 Instagram、YouTube 和 Snapchat 等平台的兴起,发行/分发时代随之而来。这些平台的特点是单向关注,即关注你从未见过面但为你提供娱乐/教育价值的人,并且价值开始通过广告积累到各种利益相关者手中。
广告业务模型包括:
向用户展示静态/视频广告; 产品/服务的付费代言; 联盟营销。 实际上,这些平台成为其他企业实现其目标的促销渠道。正如 The Generalist 的 Mario Gabriele 所说,创作者用投入到内容创作中的资源付费,观众用注意力为这种努力买单,广告商购买创作者积累的注意力。
- 独立时代是由分发时代平台作为创作者创收的主要手段的转变所引领的。从创作者销售其他品牌到成为品牌的转变。创作者现在开始利用 Shopify、Substack 和 Patreon 等平台销售自己的产品和服务。这不仅让他们获得了更多价值,还加深了粉丝关系。
在发行时代和独立时代之间的某个时候,创造者在达到一定规模后,开始作为价值创造的第三种模式进行投资。这绝对是新生的,只有少数投资者采取这一飞跃(例如,Sway Boys 的 Animal Capital),但我们认为这一领域未得到充分开发,主要是因为教育和基础设施投资于他们的专长--创作者经济--过去和现在都没有向长尾创作者提供。
- 这将我们带到所有权时代,这是 Web3 对创作者经济的介绍。虽然我们稍后会更深入地探讨这个部分,但这标志着新工具的引入模糊了创作者和观众之间的界限,并通过为每个创作者创造微观经济来创造价值,从而减少创作者/粉丝关系的交易性 ,而不是一维的商业模式。
下图由 Mario Gabriele 提供,展示了上述动态:

简而言之,今天的创作者和用户创造了最大的价值,但只获得了其中的一部分,而平台本身则获得了不成比例的价值。
这是由于以下原因:
由于内容可以无限复制和消费,因此消费集中在选定数量的创作者制作的内容上。例如,如果一个医生比其他人的权威及专业度高10%,他们不会吸引 10% 以上的需求——会吸引所有的需求。同样,每个人都想只消费绝对最好的内容。因此,收入集中在这些精选的最佳创作者身上,使大多数人难以维持生计。
正如 Chris Dixon 所指出的,在中心化平台的早期,它以正和的方式表现以吸引尽可能多的参与者。然而,当参与者增长达到 S 曲线的顶部时,这种关系就会变成零和关系,从协作变成榨取。现在,网络效应太强大了,以至于用户无法简单地放弃该平台。你可以在这里更好地理解这种动态。
 这里的根本问题是所有中心化平台(由于股东是平台参与者的独立实体)都需要作为一家公司有价值。不幸的是,他们只有在从平台参与者产生的价值中提取尽可能多的价值时才能做到这一点。
这里的根本问题是所有中心化平台(由于股东是平台参与者的独立实体)都需要作为一家公司有价值。不幸的是,他们只有在从平台参与者产生的价值中提取尽可能多的价值时才能做到这一点。因此,要让一个平台尽可能对创作者“友好”,必须使其创作者享有权益。
目前,员工持股计划 (ESOP) 旨在调整员工与平台之间的激励机制。然而,这受到跨地域和社会经济背景的法律和金融基础设施的限制,而且只针对平台的运营商而不是创造者,只因他们是平台的摇钱树和主要用户。由于创作者可以说是最具增值性的利益相关者,而 ESOP 无法(或根本无法)为他们提供足够的报酬,因此创作者目前无法有效地从他们在平台上花费的时间中获益。
总之,创作者并不拥有内容,第三方开发者无法控制代码,所有的平台参与者都无法影响所使用的平台的政策或决策,而主要的商业模式是一种不透明的、基于广告的模式,给封闭的花园平台带来巨大的优势。
Part.3 那么Web3的承诺是什么
如前所述,所有权经济假设下一代产品/服务(跨行业)将由其参与者通过使用代币化的激励机制来拥有和运营。所有权通过经济收益、治理权和/或社会影响力表现。
这个世界是由Web3技术促成的,特别是代币的出现,它与IP、HTTP、SMTP等类似,是一种协议级的创新。把代币看作是一个互联网原生的产权系统--这是有史以来第一次,你可以真正拥有互联网的一部分。这一块可以代表任何东西,从一个单纯的JPG到你使用的任何互联网产品/服务的一部分。作为例子,比特币和以太坊是第一个大规模的用户拥有的网络。
使用代币作为所有权资产和 DAO 等协调结构,创作者不仅可以拥有他们制作的内容,还可以拥有平台本身。由于参与者将是所有者,他们可以集体决定平台的政策和产品决策,没有外部利润提取压力。
Part.4 代币与股权的不同
允许任何有互联网连接的人与代币进行交互,同时还允许流畅和即时的传输。与股权不同,它们不受地域界限的限制。这种简单的可访问性使“赞助+”得以出现。Patronage+ 由 Jesse Walden 创造,是一种新范式,支持创作者不仅是一种利他行为,也是一种投资。换句话说,有盈利潜力的光顾。
人们可以在代币(价值交换的媒介)中编纂规则以促进商业关系,这在今天需要第 3 方来执行。例如,人们可以通过 NFT 对数字稀缺性进行编程,这使创作者能够切实地重视他们本质上数字化的作品。这更多是为了恢复创作者的定价权,而不是人为地限制消费者的选择。
可编程性的另一个例子是可组合性。现在,在其他人的作品之上构建(例如,混音)不会妨碍原创艺术家获得经济补偿,因为每次任何价值转移到钱包 Y 时,都可以将版税流向钱包 X。
由于代币的链上特性,创作者可以通过不同的参数(例如个人何时支持、消费了多少内容、财务贡献等)可验证地了解粉丝的质量。如果创作者同意,会将数据整合到其未来的工作中,并为他们的粉丝创造更多定制内容。创作者还可以为他们的“真正”粉丝提供超级专业的福利,更有效地与粉丝互动,从而使他们能够建立一个经得起时间考验的更紧密的社区。
代币允许创作者从热心的粉丝那里产生更多价值,从而实现更深层次的货币化。这带来了一种分层策略,即为每个级别的粉丝提供产品/服务,同时增加创作者的超级粉丝创造价值的上行潜力。
除了货币化,创作者还可以将效用注入代币中,从而让粉丝(代币持有者)积极参与内容创作,而不是仅仅被动的消费者。这种类型的有趣实验是 Shibuya 和 Mad Realities。
由于代币可以从根本上使平台增长及其参与者保持一致,因此它可能会产生比我们迄今为止看到的更大、更强大的网络。由于平台将服务于用户而非股东,用户可能不想优化股价,这完全颠覆了米尔顿弗里德曼的观点,即所有公司的主要目标都是为股东带来利润。然而,易于交易的创作者代币确实会带来投机的风险,这会破坏激励机制的稳定。
最后,Web3 可以通过数字稀缺性将价值返回数字内容。在过去的二十年里,免费平台已经使内容商品化和贬值。因此,为内容付费的行为已大大减少。然而,创造数字稀缺性的能力有可能导致这一趋势的逆转。以下是一段有用的引述,有助于理解为什么这很重要:
“如果我在 30 分钟内完成一项工作,那是因为我花了 10 年时间学习如何在 30 分钟内完成这项工作。你欠我的是年,而不是分钟。”
虽然对每一种媒体来说数字化稀缺并不是有益的,但创作者让他们的作品变得稀缺的能力开启了货币化的用例。
例如,一个艺术家不需要放弃她的Spotify流媒体--相反,她可以利用音乐NFT、限量版投放和其他福利给她最热心的粉丝,同时保持在Spotify上的存在,以达到更大、更普遍的受众。
Part.5 所有权工具
颠覆性创新的总可寻址市场是未知的。对于创作者经济来说,这一点是正确的,因为由于新的平台、技术和社会趋势(例如,COVID),人们成为创作者的意愿和能力都在增加。因此,虽然无法确定市场规模,但工具的类别可以分为那些帮助内容生产、增长/吸引观众、以及货币化和管理业务的工具。下图是一个可视化的表示。

也就是说,专门为创造者经济构建的 Web3 工具往往分为两类:重生和新生工具,即模仿 Web2 解决方案的工具以及新颖的工具用于链上需求。重生工具的一个例子是 Audius,它正试图成为去中心化的 Spotify。另一方面,新生工具的一个例子是 Collab.land,它提供软件来对在线群聊进行代币门控。
尽管如此,我们相信用于创作者经济的 Web3 工具仍将大致属于上述类别:那些有助于内容制作、增加/吸引观众以及货币化和管理业务的工具。

虽然我们描绘的画面看起来几乎是乌托邦式的,但此类用户拥有的平台尚未广泛普及的原因有几个。
首先,用户拥有的平台需要基本的 Web3 技术知识水平,而大多数人不具备这种理解。新平台上需要有一个临界质量来激励用户迁移到新平台,因为它包括承担大量的转换成本。而且,正如我们之前多次说过的那样,UI/UX 需要进一步简化才能达到临界质量。
此类平台代表了我们可以使用经济激励(例如代币)来引导网络效应的第一个实例。
 虽然代币可以快速启动网络,但绝对不能替代产品市场契合度,也不清楚它们是否会随着时间的推移在维护和发展网络方面带来持续优势。归根结底,仍然需要构建人们想要的东西。举个例子,OpenSea,没有代币,但仍然领先于所有推出代币的竞争对手(SuperRare、Rarible 等)。
虽然代币可以快速启动网络,但绝对不能替代产品市场契合度,也不清楚它们是否会随着时间的推移在维护和发展网络方面带来持续优势。归根结底,仍然需要构建人们想要的东西。举个例子,OpenSea,没有代币,但仍然领先于所有推出代币的竞争对手(SuperRare、Rarible 等)。Part.6 创作者的潜在发展
需要部署更多资金。从这个角度来看,截至 2022 年年中,Red DAO 是数字时尚领域最大的资本部署者。他们累计投资了约 1000 万美元。时尚是一个价值数万亿美元的产业,可以比现在更有效地使用数字参与方式。
更多的创作者成为投资人。虽然这种趋势多年前就开始了(Dr. Dre 和 Beats、Diddy 和 Ciroc 等),但 Web3 工具现在允许较小的创作者投资于他们产生共鸣的品牌和产品。
创作者中产阶级将显着增加。随着将创意追求货币化变得更加容易(基于支持工具增加和个人支付意愿的双重假设),更多的创作者群体将能够从他们的创意作品中获得可持续的收入。
影响者/内容创作者孵化器的兴起。中国的影响力孵化器已经扩大规模,例如 Jake Paul 的 Team 10。虽然这是一个潜力巨大的领域,但获得少数比例的创作者收入是一个棘手的问题。
额外的货币化工具可以解锁创作者中产阶级,使创作追求更容易获得。观众限制在 1,000 或 100 个真正的粉丝可以让创作者获得稳定的收入,并增加能够通过追求创造性的努力谋生的人数。
总而言之,前路漫漫。创作者增长潜力很高,尽管存在许多不利因素,但并非无法克服。如果 Web3 的 UI/UX 和教育挑战能够长期解决,那么创作者和所有权经济很有可能达到其潜力的顶峰。
-
 @ 05e6367c:6ba9be85
2023-04-03 11:27:19
@ 05e6367c:6ba9be85
2023-04-03 11:27:19集中流动性:基础知识
TL;DR — 集中流动性做市商 (CLMM) 允许流动性提供者决定他们的资产可以在市场上以什么价格被交易者使用,这与恒定乘积 AMM 不同,后者的流动性在资产的所有潜在价格中均匀分布。集中流动性可以将资本效率提高 4000 倍,但需要流动性提供者进行积极的流动性管理。
流动性提供者不是向资产的每一个可能的价格提供流动性(如x*y=k风格的AMM),他们可以选择只在一个有限的范围内提供流动性,通常是当前交易活动正在发生的范围。
原因
-
更少的滑点和更好的交易,因为大多数交易活动的价格范围受益于更深的流动性。
-
流动性提供者的年利率更高。仅提供进行交易的区域,意味着交易者会使用更多的流动性,从而获得更多的交易费用。
-
您可以达到相同的深度,但流动性更少。根据人们更新集中头寸的积极程度,CLMM 可以实现与普通 AMM 相同的滑点和深度,而流动性仅为普通 AMM 所需的 10% 到 25%。
知识点备注
流动性有三种衡量的方式,分别是即时性、宽度和深度。
● 即时性(immediacy)是指给定数量和价格,能多快成交。
● 宽度(width)是指给定时限和数量,能以多低的价格成交。
● 深度(Depth)是指给定时限和价格,能成交多大的数量。
什么是 NFT AMM?
NFT AMM 有两种,一种是基于恒定乘积曲线的,一种是基于集中流动性头寸的。
恒定乘积NFT AMM 通常会使用现有的 DEX,如 Serum 或 UniSwap,并在 NFT 和 DEX 之间添加一个中间层。这个中间层通过锁定 NFT 并铸造一个可替代的地板代币,使 NFT 具有可替代性。然后可以在 DEX 上针对 USDC、SOL 或 ETH 交易这种可替代的底价代币,其价值应该与NFT集合的当前底价大致相当。
如果有人想从池子里购买整个NFT,他们必须从DEX购买一个可替换的地板代币,然后烧掉代币以换取NFT。
可替换地板代币的复杂性在于其造币/燃烧机制,这可以很容易地从用户那里抽象出来。外包的 DEX 和 AMM 基础设施也是如此。
例子。NFTX, NFT20, Solvent, Frakt, Elixir.
集中流动性NFT AMMs(NFT CLMMs)允许流动性提供者(存入NFTs/代币)创建他们自己的NFTs池,卖出池,买入池,或交易池。
卖出池实际上是 NFT 所有者要价的总和。卖家说他们想卖出 X 个 NFT,每次有人从他们那里购买,他们想增加要价。
购买池则相反,它们是来自 NFT 买家的购买订单的总和。买家决定购买 X 个 NFT,并且每次有人向他们出售 NFT,他们都希望降低出价。出售给矿池的 NFT 越多,卖家的价格就越差。这意味着更多的需求会提高价格,而更多的供应会降低价格。
交易池允许流动性提供者将 NFT 和可替代代币供应到一个微型池中,设置他们自己的交易费用和他们自己的定价曲线(每次销售后 NFT 的价格如何变化)。流动性并没有被隔离到这些微池中,而是一个聚合器合约在任何给定时刻引导交易者通过最好的池。这使得 CLMM 高度灵活、高效,但也更加复杂。
例子:Sudoswap、TensorSwap、GoatSwap、HadeSwap。
我们需要NFT AMMs吗?
NFTs很难交易,抛开版税问题不谈,相对于可替代的代币来说,其供应量小,使得它的流动性和波动性非常低。人们对围绕这些资产的更多金融基础设施有明确的需求,但如果没有一个流动性层作为基础,这种需求就无法存在。
NFT AMMs的目标是成为NFTs的流动性层,并取代市场,为一系列DeFi应用的建立释放潜力。
然而,在NFT流动性不足的核心问题上,存在着AMMs尚未克服的基本挑战。
1. 没有人关心碎片化的问题
当NFTs被转换为可替代的地板代币时,对可替代的地板代币及其分数没有购买压力。人们对购买NFT的零碎部分感兴趣的说法,从他们可能被定价的集合中并没有得到证实。如果这是真的,你会期望NFT的小数点以溢价交易,因为会被更多的投资者获得,并且有较低的准入门槛。然而,由于NFT AMM套利的性质,这些代币最常以折扣价交易。
由于不对称套利,在可替代的地板代币的价格和NFT地板价格之间保持挂钩是很困难的。以下是它的工作原理。
如果可替代的地板代币的价格高于NFT市场的底价,套利者应该从市场上购买NFT,然后在AMM交易,以换取可替代的地板代币。然后他们以高于他们购买NFT的价格出售该代币。在这个方向上,套利是即时的。
如果可替换的地板代币低于NFT市场,他们应该用更便宜的代币换取池中的NFT,从而以折扣价获得NFT,然后在市场上列出NFT。结果是:你现在在等待有人购买它,并在有人购买之前坚持风险。在这个方向上,套利是有风险的,而且不是即时的。
有了可替换的地板代币,套利只在一个方向上起作用,导致这些代币的价格有偏差,几乎总是比地板价格有折扣。
**2. 相对于可替换代币而言,供应量较低 ** 一个NFT藏品通常只有1万个代币,这对NFT AMM来说是个问题。AMM中究竟能有多少代币?
收藏品通常以在二级市场上市的代币数量少而自豪,然而这种看涨的非流动性削弱了NFT AMM的实用性。
但是为什么不在平台上提供你的 NFT 作为流动性呢?你仍然可以看涨并将你的 NFT 放在一个池子里吗?是的,但您必须接受您提取的 NFT 可能与您存入的 NFT 不同。由于您的 NFT 正在交易,您可能会留下买方不想要的 NFT。这场谁最终得到不需要的 NFT 的游戏将我们引向另一个问题。
烫手山芋问题
NFTs的不可伪造性与AMM的核心假设之一相悖。
AMM使用数学表达式x*y=k来反映资产X的价格变化,如果人们出售它以获得资产Y。我们没有任何价值可以赋予X,使它在这个池子里有所区别,并使这个公式无效。
然而,如果X是一组NFT资产,那么它们的特性、稀有性、潜在收益和其他特征使X的价值严重依赖于组成它的代币。因此,该公式假设所有提供的NFT是平等的,使得该池子只与具有同等价值的地板NFT有关。这意味着NFT AMM是整个集合的一个不完美样本。
NFT是可互换的假设适用于NFT CLMMs和恒定乘积AMMs,但是CLMMs可以更容易地摆脱制作特定性状的微池。
NFT AMMs需要有机制来防止他们的池子因交易而变质,因为交易员会抢走最好的NFT,并用相同系列的劣质NFT取代它们。随着时间的推移,资金池将是一个集合中最不需要的NFT的结果。
Solana NFT AMMs中提供的Degen Apes最能说明这一点,剩余流动性的一半是由臭名昭著的粉红色礼服Degen Apes组成。
Frakt很早就解决了这个问题,在他们的资金池中加入随机交易。虽然这使资金池更健康,可以非常游戏化,但它的代价是交易经验和更难套利。
不是所有的NFT AMM都是一样的
恒积 AMM 的另一个副产品是它们永远不会耗尽池中任何资产的储备。这是通过滑点强制执行的。如果对池中的一种资产的需求过多,池中资产 X 和 Y 的比例开始发生变化,使得需求最多的资产的价格变得越来越不利。这种平衡行为在 AMM 中不断发生。
价格成为指数级的不利因素,意味着购买的资产X越多,其价格就越快地趋向于无穷大,所以我们永远不会耗尽池中的资产X。对于NFTs,由于其供应量非常有限,所以非常容易耗尽储备,因此,同样容易出现非常高的滑点。
在流动性低的情况下,增加1个ETH来购买NFT,沿着恒定乘积曲线急剧改变其价格。
由于收藏量太小,而且总是以整数单位进行交易,NFT加剧了AMM的滑点问题。
NFTs中的流动性太稀缺了,不可能像恒定乘积AMM那样在0和无穷之间均匀分布。
当使用恒定乘积函数提供流动性时,在当前价格的 -50% 和 +50% 的价格范围内,只有大约 25% 的流动性被使用。
示例:Solana Monkey Business 的交易价格为 200 SOL。您在 AMM 中为 SMB 提供 500 SOL 的流动性。使用恒定乘积曲线,在每个 SMB 100 SOL 和 300 SOL 的价格之间,交易者只能使用 25% 的流动性。这意味着 SMB 池在 200 SOL 价格附近的价格范围内的深度等于 125 SOL。在流动性有限的情况下进行 1 个 SMB 的交易所需的价格差异通过滑点解决。
根据 0xmons 的示例:一个拥有 20 个 NFT 的池的最小滑点约为 5%。
我们可以添加更多的 NFT 和更多的 SOL 以获得更深的流动性,但这非常有限。由于 NFT 的稀缺性,它们需要在更窄的价格范围内供应,以免在无限的潜在价格中低效稀释流动性。
在我们之前的示例中,流动性提供者在池中提供了价值 500 SOL 的流动性,从而在当前下限 +/- 50% 的价格范围内产生了 125 SOL 的深度。使用 CLMM 模型,流动性提供者只需提供 125 SOL 即可达到相同的深度,并将范围设置为当前下限的 +/- 50%。
如果池中的交易活动通常被限制在这个价格范围内,那么流动性提供者赚取相同数量的费用,但只提供 125 SOL 而不是 500 SOL。这实际上意味着使用具有广泛范围的 CLMM,而不是恒定乘积 AMM,他们的 APR 提高了 4 倍。
如果流动性提供者决定在比 +/- 50% 更窄的范围内提供流动性,这个 APR 可能会更高,但他们将不得不随着价格的变化更频繁地调整它。
NFT CLMM 为买卖双方提供更好的价格
在流动性集中的世界中,滑点是由微池中选择的曲线设置的,并且在限制上更合理。
在恒定乘积 (x*y=k) AMM 中,其中 X 是 NFT 集合,Y 是类似 SOL 的可替代代币,购买池中多个 NFT 的价格和滑点呈指数增长,购买的 NFT 越多。
这导致在 AMM 中购买多个 NFT 的平均价格非常高。
最好用 SudoSwap 的修改示例来说明:
假设 1 SMB = 200 SOL。我们使用具有 10 个 SMB 和 2000 SOL 流动性的恒定乘积函数创建一个流动性池。
有人想从这个池中购买 5 个 SMB。
购买第一个SMB,产生了大约11%的滑点,必须支付222 SOL来获得SMB。购买第二个SMB,这个池子现在的报价是每个SMB 278 SOL,第三个将花费357 SOL,第四个476 SOL,第五个667 SOL。如果买方想买5个SMB,平均价格将是每个SMB400 SOL。
现在假设流动性提供者在 CLMM 中创建了一个微型池,并在每次销售后将价格设置为上涨 10%。
同一买家想从该池中购买 5 个 SMB。第一个将花费 200 SOL,第二个 220 SOL,第三个 242 SOL,第四个 266 SOL,第五个 292 SOL。如果买家想用这个 CLMM 购买 5 台 SMB,平均价格将为每台 SMB 244 SOL。
请注意,在上面的示例中,滑点不会随着每笔交易而增加,而是保持在 10% 不变。这意味着价格不会趋向于无穷大,池中的最后一个(第 10 个)NFT 价值 471 SOL 而不是∞ SOL。
结论
这就是 CLMM 的力量,如果我们想创造深度流动性来支持清算、期权、衍生品、杠杆等金融基础设施,为什么 NFT 如此迫切地需要它们。
恒积 AMM 旨在忽略许多 NFT 收藏家最看重的东西,即他们资产的独特性。将 DeFi AMM 的概念成功应用到 NFT 是很困难的,需要项目来反思 NFT 的特殊性。忽略这些特征将导致糟糕的用户体验和不利的交易,最终将限制 NFT AMM 的扩展能力。
集中流动性 AMM 有可能解决这些痛点,但现在面临着复杂用户体验的挑战。
-