-
 @ 7f6db517:a4931eda
2025-06-19 03:02:01
@ 7f6db517:a4931eda
2025-06-19 03:02:01
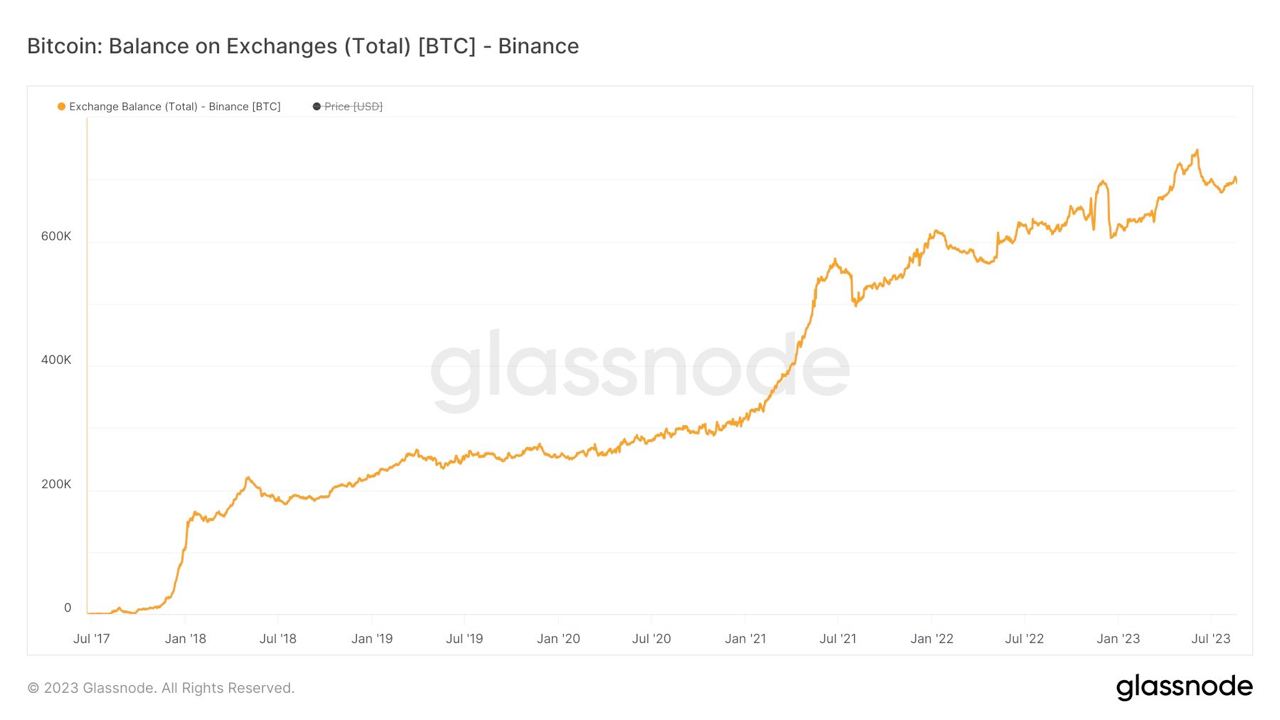
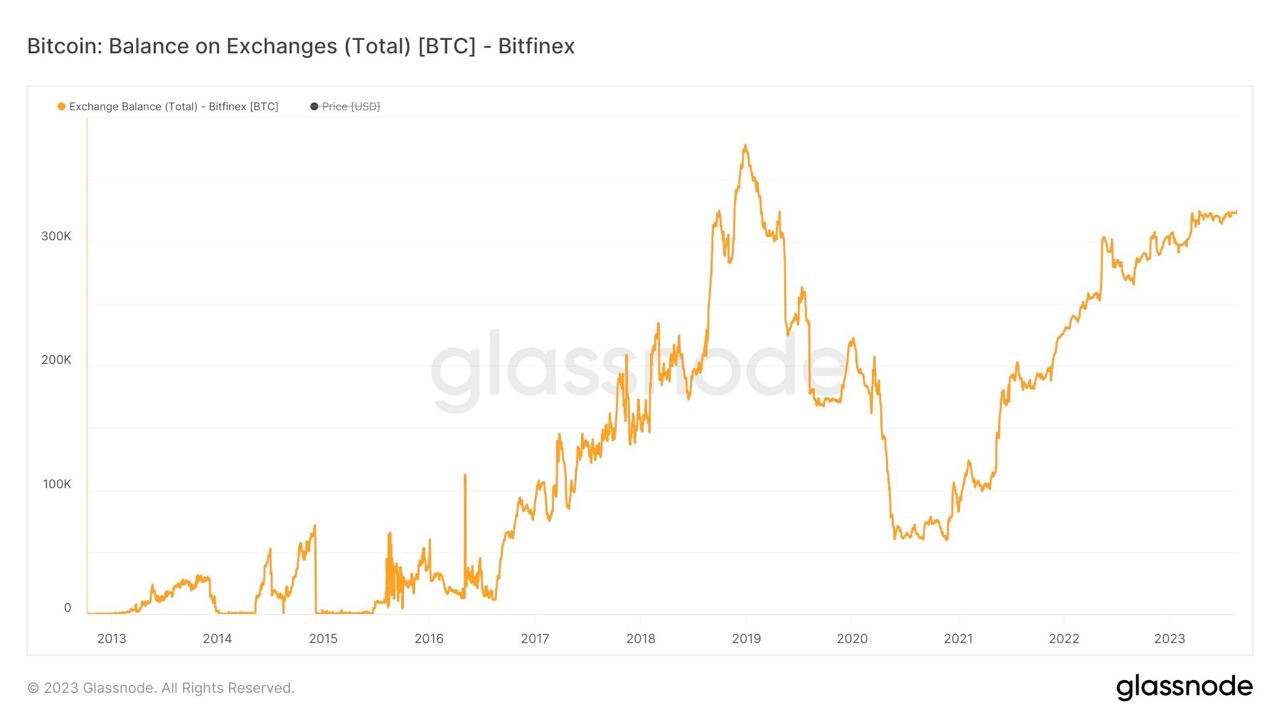
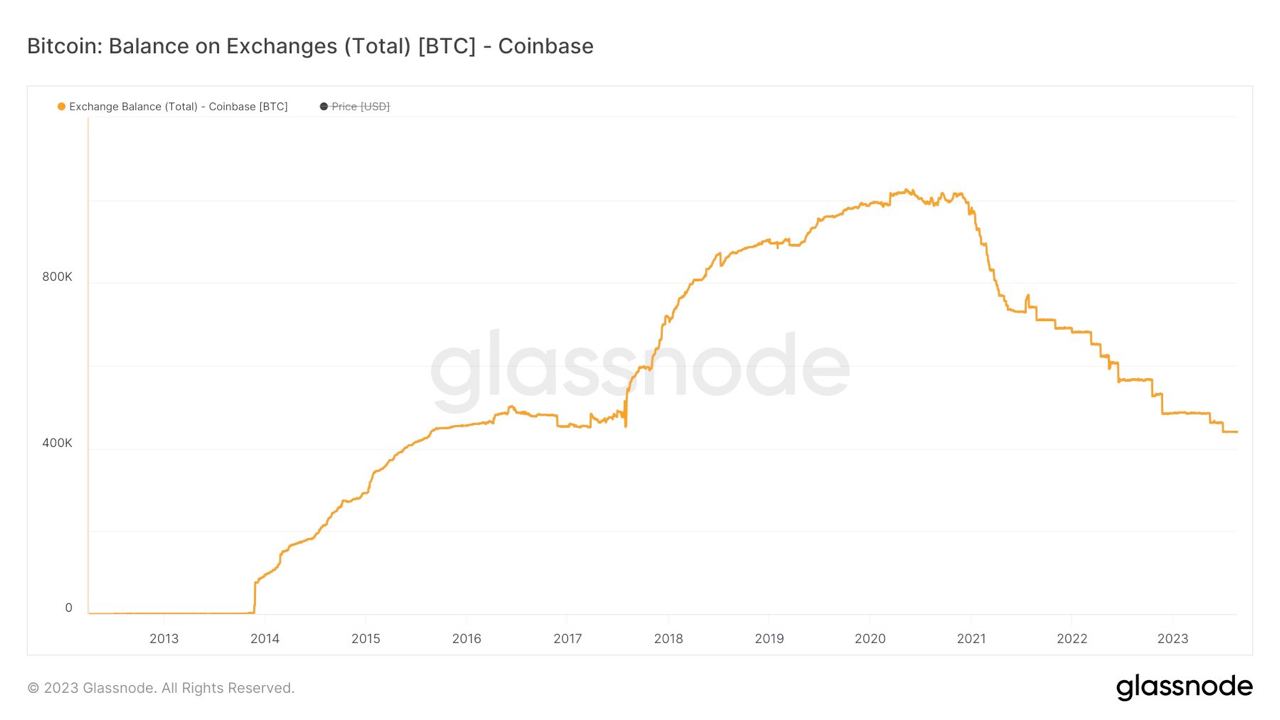
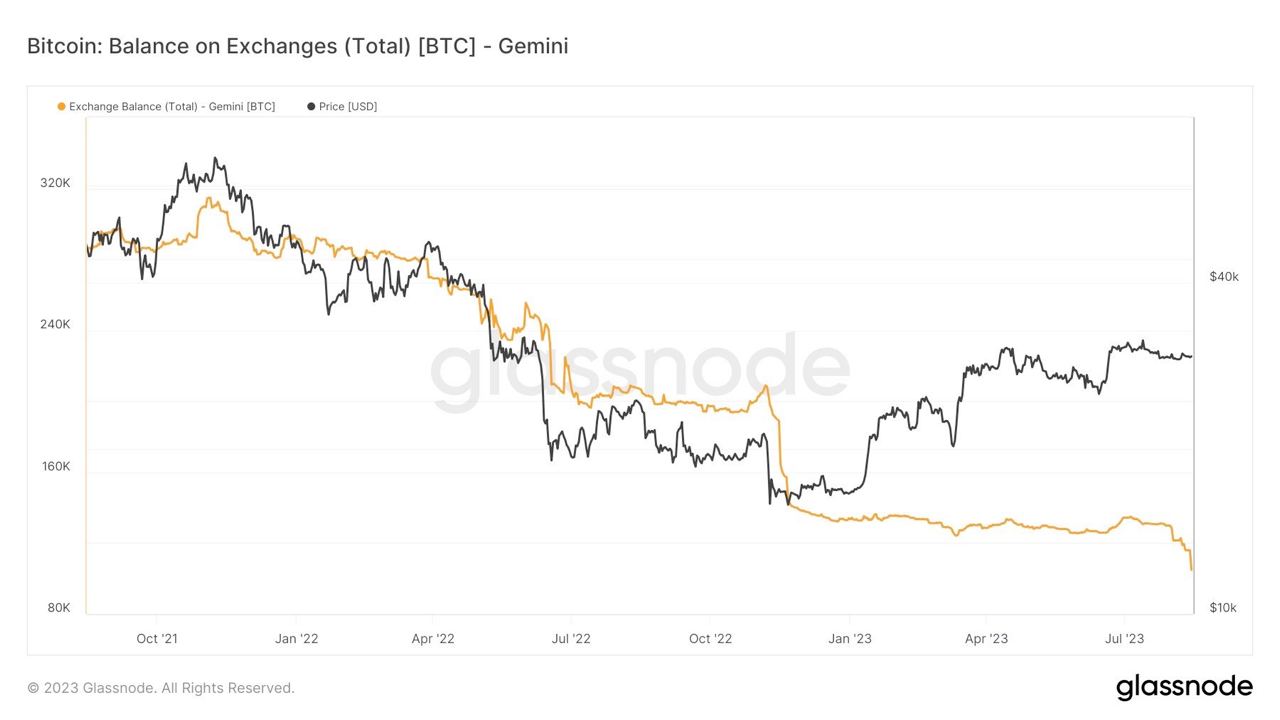
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
If you found this post helpful support my work with bitcoin.

-
 @ eb0157af:77ab6c55
2025-06-19 03:01:41
@ eb0157af:77ab6c55
2025-06-19 03:01:41Only 1% of stablecoin transactions in 2024 are linked to criminal activity.
A recent report by TRM Labs has revealed new data on stablecoin usage in 2024. Contrary to widespread perception, 99% of stablecoin transactions were entirely legal and compliant with existing regulations.
The research shows that over 60% of last year’s total transaction volume was conducted using dollar-pegged tokens.
One key point highlighted in the report is the intrinsic traceability of stablecoins. Operating on public blockchains, these digital currencies allow for highly precise transaction monitoring through specialized analytics tools.
Issuers of centralized tokens like USDT and USDC also have the ability to freeze or permanently remove tokens associated with illicit activities.
TRM Labs data shows a 24% decrease in crypto-related criminal activity compared to 2023, with a total of $45 billion representing just 0.4% of overall crypto transaction volume. This decline is attributed to increased law enforcement efforts, stronger industry collaboration, and the growing adoption of advanced analytics tools.
According to TRM Labs, regulatory clarity provided by legislation such as the GENIUS Act could accelerate stablecoin adoption among major banks, financial institutions, and corporations. Many of these entities are already testing stablecoin-based infrastructures for cross-border payments, supply chain management, and programmable finance.
The post Stablecoins: new report debunks myths about illicit use appeared first on Atlas21.
-
 @ b1ddb4d7:471244e7
2025-06-19 03:01:20
@ b1ddb4d7:471244e7
2025-06-19 03:01:20In a quiet corner of the world, bitcoin mining operations in Africa are turning electricity into digital currency and in the process, redefining how value is created.
At its core, bitcoin mining involves validating transaction information before adding new blocks to the Bitcoin blockchain by competing to solve a cryptographic puzzle that meets a specific criterion.
Globally, mining plays a key role in keeping the blockchain decentralized and secure. The system depends on miners to verify and record transactions, mainly to prevent a problem called double spending, the digital version of using the same money twice.
To understand this better, imagine Charles sends $5 to Amanda. With physical cash, Amanda can trust the note is real and hasn’t been used elsewhere. But with digital currency, copying data is easy, so how can she be sure that the same $5 wasn’t sent to someone else too? That’s the exact problem Bitcoin mining helps solve.
In recent years, Africa has started to draw attention in this space, positioning itself as a key hub in global bitcoin mining. While there may be less than 2 million bitcoin left to be mined from the total 21 million supply, the rise of mining operations in Africa has sparked excitement, creating new jobs and drawing in foreign capital.
Although some countries still grapple with power shortages and the energy demands of mining, many citizens view bitcoin as a more stable store of value and a safeguard against the volatility of their local currencies.
At the same time, Africa’s wealth of hydro, solar, wind, and geothermal resources makes the continent one of the most promising regions for cost-effective and sustainable mining.
What Makes a Large-Scale Bitcoin Mining Operation in Africa?
It all starts with difficulty. Bitcoin mining isn’t just about solving a puzzle, it’s about solving one that keeps getting harder. Mining difficulty refers to how much computational work is needed to generate a number lower than the target hash.
This difficulty automatically adjusts every 2,016 blocks (about every two weeks), depending on how quickly miners solved the previous batch. If mining is fast and efficient, the network increases the difficulty; if miners drop off and block times slow, it reduces it, all to maintain a consistent block production time of roughly 10 minutes.
The significance of mining difficulty lies in the increased demands it places on mining operations. As difficulty rises, miners require more powerful hardware, cost-effective energy sources, advanced infrastructure, and substantial financial investment. These requirements distinguish large-scale mining operations from smaller, casual miners.
In short, it’s the difficulty of mining that births the need for large facilities, massive energy inputs, industrial-grade hardware, and significant financial investment, the very traits that define a “large” bitcoin mining operation.
This leads us to the 4 key factors that define large Bitcoin mining operations in Africa, each one a direct response to the growing demands of the network:
1. Facility size and infrastructure:
The physical size of a mining facility is a direct reflection of its capacity to house mining equipment and support systems. Larger operations typically have thousands of mining rigs installed, supported by extensive infrastructure such as advanced cooling systems and stable power supplies.
These are critical to ensure that the equipment runs continuously and efficiently, given the intense heat and electricity demands of mining.
While it is possible to mine Bitcoin using desktop computers or gaming rigs by joining mining pools, these setups are limited in profitability. Mining pools distribute rewards based on the computational power contributed, meaning small or less efficient machines earn only modest returns.
To compete effectively, mining operations invest in specialized hardware known as Application-Specific Integrated Circuit (ASIC) miners. These machines are far more powerful and energy-efficient than regular computers but require significant capital investment, with prices ranging from $4,000 to $12,000 per rig depending on their performance.
Large-scale operations typically deploy hundreds or thousands of these ASIC miners, which necessitates the large facilities and sophisticated infrastructure mentioned earlier. In this way, the size of the facility and the sophistication of the mining equipment are tightly linked, together defining the overall scale and capability of a bitcoin mining operation.
2. Hashrate contribution:
Hashrate refers to the computational power used to mine and process transactions on the Bitcoin network. A higher hashrate indicates a more significant contribution to the network’s security and transaction processing.
Large mining operations often possess substantial hashrate, measured in exa hashes per second (EH/s). For instance, as of July 2024, the Bitcoin network’s hashrate was approximately 733.41 EH/s.
3. Energy consumption and power source:
Bitcoin mining is energy-intensive. The total energy consumption of the Bitcoin network has been estimated at 175.87 terawatt-hours annually, comparable to the power consumption of Poland. Large mining operations often seek locations with access to cheap and reliable energy sources, such as hydroelectric, solar, or wind power, to reduce operational costs and environmental impact.
4. Financial banking and investor interest:
Significant financial investment is required to establish and maintain large-scale mining operations. This includes the cost of mining hardware, facility construction, energy procurement, and operational expenses. Companies with substantial financial backing can invest in cutting-edge technology and infrastructure, enhancing their mining capabilities.
Overview of Bitcoin Mining in Africa
Africa is beginning to carve out its share of the global Bitcoin mining market, which was valued at $2.45 billion in 2024 and is projected to reach $8.24 billion by 2034.
As Bitcoin’s value continues to rise, countries across the continent are positioning themselves to benefit, many by tapping into abundant renewable energy sources and taking advantage of regulatory ambiguity or excess energy production.
Ethiopia currently leads the continent in Bitcoin mining activity, with around 2.5% of the global hashrate reportedly coming from operations powered entirely by renewable energy.
This energy mismatch has attracted major miners from China and other regions, who see an opportunity to monetize surplus electricity. Ethiopia’s success showcases how renewable energy and mining can coexist sustainably while contributing meaningfully to state revenue.
Kenya follows closely behind. As the top geothermal energy producer in Africa, with an installed capacity of 863 MW, the country is using its energy advantage to support sustainable mining.
Nigeria is emerging as a serious contender. While not yet dominant, its large population, increasing tech engagement, and growing interest in using flared gas for mining signal potential for expansion. Nigeria’s complex but evolving regulatory landscape also leaves room for further mining developments as the government explores clearer crypto frameworks.
Malawi represents a more localized model of Bitcoin mining. By converting rainfall-powered microgrids into revenue-generating infrastructure, Malawi shows how small-scale mining can play a powerful role in community development and rural electrification.
In Libya, Bitcoin mining is technically illegal, but that hasn’t stopped it. Despite the ban, underground mining continues to thrive thanks to heavily subsidized electricity. In 2021, Libyan miners accounted for an estimated 0.6% of the global Bitcoin production, the highest in both the Arab world and Africa at the time. Today, mining reportedly consumes around 2% of the country’s electricity, even as it operates in the shadows.
Angola rounds out the list with limited public data but notable potential. The country struggles with energy inefficiencies, losing nearly 40% of its hydroelectric power during transmission. Some reports suggest Bitcoin miners are beginning to capitalize on this otherwise stranded energy, though large-scale operations are yet to surface.
What unites these countries is a shared set of conditions: untapped or mismanaged energy resources, an openness or gray area in regulation, and the growing understanding that Bitcoin mining can serve as a financial incentive to build and stabilize decentralized energy systems.
Whether through massive hydroelectric projects or rural microgrids, Bitcoin mining is emerging as both an energy monetization strategy and a bridge to infrastructure development across Africa.
Profiles of the Largest Bitcoin Mining Operations in Africa
1. BitCluster (Ethiopia)
As of 2024, Bitcoin mining in Africa is largely concentrated in
-
 @ cae03c48:2a7d6671
2025-06-19 03:01:00
@ cae03c48:2a7d6671
2025-06-19 03:01:00Bitcoin Magazine

The Blockchain Group Buys $20 Million Worth Of BitcoinThe Blockchain Group has acquired an additional 182 Bitcoin for approximately €17 million ($19.6 million), further expanding its position as Europe’s first Bitcoin treasury company amid accelerating institutional adoption of Bitcoin reserves.
According to a press release issued June 18, the Euronext Growth Paris-listed company completed the purchases through multiple convertible bond issuances totalling over €18 million, subscribed by several investors, including UTXO Management, Moonlight Capital, and asset manager TOBAM.
JUST IN:
 French publicly traded, The Blockchain Group buys an additional 182 #Bitcoin for €17.0 million
French publicly traded, The Blockchain Group buys an additional 182 #Bitcoin for €17.0 million Nothing stops this train
 pic.twitter.com/fwIqq934Yy
pic.twitter.com/fwIqq934Yy— Bitcoin Magazine (@BitcoinMagazine) June 18, 2025
The acquisitions bring The Blockchain Group’s total Bitcoin holdings to 1,653 BTC, purchased at an average price of €90,081 ($104,000) per coin. The company reported a “BTC Yield” – measuring Bitcoin holdings relative to fully diluted shares – of 1,173.2% year-to-date, significantly outpacing other major corporate holders.
The company’s latest purchases were executed through Swissquote Bank Europe and Banque Delubac, with custody provided by Swiss infrastructure provider Taurus. Additional funding came from the conversion of share warrants into 2.98 million ordinary shares, raising €1.6 million.
We’re seeing unprecedented growth in corporate Bitcoin treasury strategies. The Blockchain Group’s success has created a model for European companies, with new organizations announcing Bitcoin purchases almost weekly.
The company indicated potential plans to acquire an additional 70 BTC through ongoing transactions, which could bring its total holdings to 1,723 BTC. This follows recent Bitcoin treasury announcements from companies including Metaplanet, which now holds 10,000 BTC, and Strategy’s latest acquisition of 10,1000 BTC.
At press time, Bitcoin trades at $104,021, down 1.26% over the past 24 hours, as markets continue to process the implications of growing institutional adoption. The Blockchain Group’s shares were down 3.9% to €4.80 on Wednesday, trading on Euronext Paris.
This post The Blockchain Group Buys $20 Million Worth Of Bitcoin first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ cae03c48:2a7d6671
2025-06-19 03:00:59
@ cae03c48:2a7d6671
2025-06-19 03:00:59Bitcoin Magazine

K33 Announces Plans To Purchase Up To 1,000 BitcoinK33 AB, a leading digital asset brokerage and research firm, announced today the launch of a SEK 85 million direct share issue to fund the purchase of Bitcoin. The company aims to build Bitcoin as a core asset on its balance sheet, targeting the accumulation of up to 1,000 BTC as a strategic reserve.
 PRESS RELEASE: K33 launches a share issue to finance the purchase of up to 1000 Bitcoin, with a minimum of SEK 85 million secured through pre-commitments pic.twitter.com/sG1LZjR6EI
PRESS RELEASE: K33 launches a share issue to finance the purchase of up to 1000 Bitcoin, with a minimum of SEK 85 million secured through pre-commitments pic.twitter.com/sG1LZjR6EI— K33 (@K33HQ) June 18, 2025
The share issue, priced at SEK 0.1036 per share, is fully backed by existing shareholders and new investors. Proceeds from the raise will be used exclusively to acquire BTC, supporting K33’s accumulation strategy revealed in May. By acquiring BTC, the company aims to strengthen its balance sheet, boost brokerage margins, launch new products, and attract more investors.
“This raise marks a major milestone towards our initial goal of acquiring 1000 BTC before scaling further,” commented the CEO of the Company Torbjørn Bull Jenssen. “We strongly believe that Bitcoin represents the future of global finance and are positioning K33 to benefit maximally from this. A strong balance sheet built on Bitcoin enables us to significantly improve our brokerage operation while maintaining full exposure to Bitcoin’s upside potential.”
As part of the strategy, K33 recently completed its first Bitcoin acquisition, purchasing 10 BTC for approximately SEK 10 million on June 3. This transaction is the initial deployment of capital from the SEK 60 million investment commitment announced earlier this year to support the company’s BTC treasury.
“We expect Bitcoin to be the best-performing asset in the coming years and will build our balance sheet in Bitcoin moving forward,” stated Jenssen. “This will give K33 direct exposure to the Bitcoin price and help unlock powerful synergies with our brokerage operation. Our ambition is to build a balance of at least 1000 BTC over time and then scale from there.”
During its Q1 2025 Report and Strategic Outlook presentation, K33 underscored the accelerating institutional adoption of Bitcoin, referencing the rapid growth of the US Bitcoin ETFs, which attracted more capital in its first year than gold ETFs had in the past two decades.
“For K33, Bitcoin is not only a high-conviction asset — it’s also a strategic enabler,” Jenssen said. “With a sizable BTC reserve, we will be able to strengthen our financial position while unlocking new revenue streams, product capabilities, and partnerships.”
This post K33 Announces Plans To Purchase Up To 1,000 Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-06-19 03:00:58
@ cae03c48:2a7d6671
2025-06-19 03:00:58Bitcoin Magazine

Bitcoin Tech Booms: Lightning Data Defies Digital Gold NarrativeEgo Death Capital’s portfolio reveals adoption metrics including $1.5 billion in Lightning-powered trading volume, as Block shocks the industry with their 9.7% Lightning Network yield.
While bitcoin treasury companies, debates about market structure bills, and strategic bitcoin reserve advocacy dominate the headlines in 2025, a trend is quietly growing in the background: the success of Bitcoin technology companies.
Increasingly recognized as digital gold and a long-term store of value, bitcoin is far more than just a shiny rock in cyberspace. As a software technology, Bitcoin is programmable and has unlocked a new paradigm of payments, custody, settlement and trading possibilities.
Nevertheless, some critics point to the empty blocks on the Bitcoin base layer and historically low transaction fees as implicit proof that Bitcoin is failing as a medium of exchange. Others claim that the Lightning Network has failed to get mainstream adoption and even argue that it suffers from significant privacy problems. But the opposite may be true.
New data coming out of various companies throughout the industry is starting to paint a different picture. Perhaps the Lightning Network has been so successful in drawing transactions off chain and making them more private that it is hard to quantify success metrics without companies involved sharing the data.
But, a variety of Bitcoin start-ups and companies using bitcoin to build out new financial infrastructure are now starting to boast of their success metrics, claiming numbers that suggest there is a strong product market fit beyond treasury strategies.
Jeff Booth, author of The Price Of Tomorrow and co-founder of the Bitcoin-focused VC firm Ego Death Capital, told Bitcoin Magazine he doesn’t “think the general public has any clue with how fast the Bitcoin ecosystem is growing.” Adding that, “They keep on hearing treasury companies this and politics that, and they’re missing the forest for the trees.”
Below follows a summary of various companies and projects demonstrating Bitcoin adoption in significant numbers, many of them within the Ego Death Capital portfolio.
Block: Earning Big on Lightning and Bitcoin Payments
The contrast in perspectives between the digital gold thesis and those that believe in Bitcoin as a payments technology was most recently seen at Bitcoin Vegas 2025 where Block, the parent company of Cash App, disclosed that they are earning 9.7% yield off their Bitcoin Lightning node.
Miles Suter, Bitcoin Product Lead at Block, told the live audience that “at the infrastructure layer, we’re earning nearly 10% bitcoin-on-bitcoin returns by efficiently routing real payments across the Lightning network. This isn’t yield from altcoin staking or reckless speculation; it’s from solving hard, real-time routing problems, and its real bitcoin-on-bitcoin returns from our corporate holdings via supporting real payments use cases.”
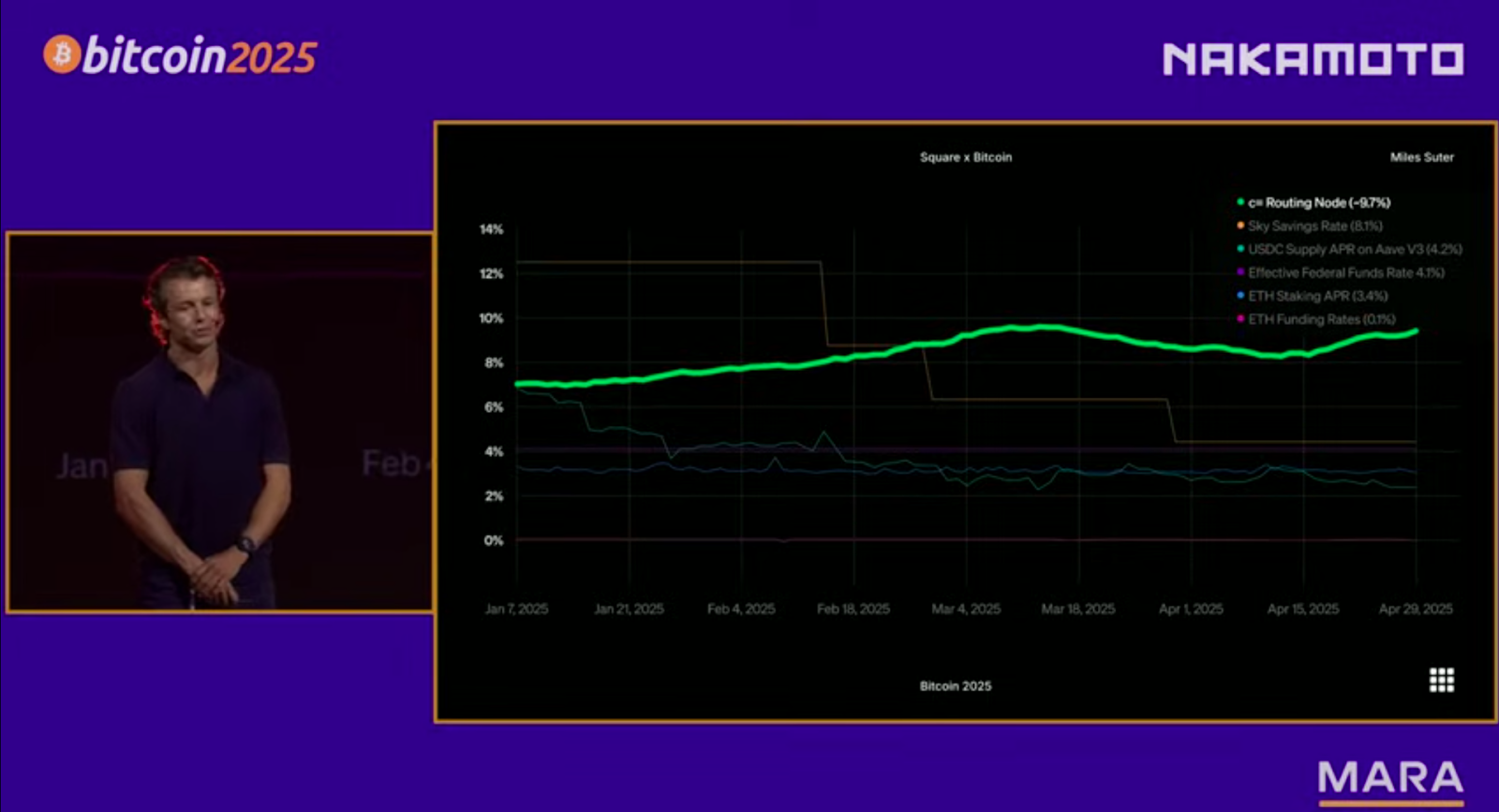
Besides Block’s stunning 9.7% figure announcement, which stood out as one of the most lasting impressions from the conference, Suter claimed that Cash App ranks “among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time,” adding that in 2024, its Lightning usage grew 7x and one in four of their outbound Bitcoin payments are processed on Lightning. These numbers highlight Block’s growth as a Bitcoin payments giant, now perhaps the most common merchant payments terminal and consumer payments app that integrates bitcoin.
Ego Death Capital
Ego Death Capital has been investing in Bitcoin infrastructure start-ups since 2022, initially raising a tactical 30 million dollar fund amid a boom in crypto and altcoin VC investments.
“When we first raised money, we actually targeted 30 million because the ecosystem at that time was really early. We realized we had to lean into these companies to help them scale. There were a lot of big crypto funds at that time, but they were spraying money everywhere else. And it was largely the exact opposite of what we believed would happen on Bitcoin.” Booth recalled that “Bitcoin was a protocol. It was developing in layers and it was early. And if you realized that and leaned in to help those companies that were developing in the layers, helping the infrastructure be created, then you would accelerate that. You would accelerate what we saw Bitcoin being, a currency, a store of value, an entirely new network.”
“We don’t have a failure in that fund,” Booth said of the firm’s first investment cohort, which included companies like Breez, Relai, LN Markets, Fedi, Wolf and Simple Proof. “That fund is just over three years old. It’s staggering. A number of those companies, I think three of those companies are already profitable — and profitable in bitcoin terms. So adding bitcoin to their treasury each month and growing incredibly fast.”

Breez: Powering a Global Lightning Payments Network
Breez, founded in 2018, is a self-custodial Lightning-as-a-service provider that enables developers to integrate Bitcoin payments into apps using its open source Breez SDK. By simplifying Lightning’s complexities, Breez has been driving widespread adoption across diverse industries.
“Over 40 apps have already implemented our SDK in production or beta since we launched it less than 18 months ago. Collectively, ~1.5 million users now have access to self-custodial, peer-to-peer bitcoin payments through these apps. These apps processed over $4.5 million in gross transaction volume in 2024,” wrote Roy Sheinfeld, CEO of Breez, in a January 2025 blog post.
The “Bitcoin Payments Report” by Breez and 1A1z, released February 2025, added, “The Lightning Network now reaches over 650 million users; driven by integrations with mainstream products, new developer tools, and growing merchant adoption.” A month later Sheinfeld published that “Lightning Pay’s user base has been growing with users moving a billion sats monthly.” Additionally, Breez’s integration with Klever Wallet brought Lightning to “100,000 monthly active users,” as stated in a December, 2024, blog post.
LN Markets: Lightning-Fueled Trading Takes Off
LN Markets, launched in 2020, is a Bitcoin-native derivatives trading platform, leveraging the Lightning Network for instant settlements and minimized counterparty risk.
Its Lightning-native login interface demonstrates they are on the cutting edge of Bitcoin technologies and unlocks user experience features that differentiate it from most other advanced trading platforms. The fast payment rails that result from this deep integration with the Lightning Network unlock faster settlement, lower withdrawal fees and provides access to smaller traders throughout the third world, with many users in South America in countries like Mexico, Brazil and Colombia.
“Basically we’ve gone from 50 million in monthly trading volume to 1.5 billion last month in May,” co-founder Romain Rouphael told Bitcoin Magazine, adding that they have gone from “one billion dollar yearly trading volume in 2023 to six billion last year to 12 billion this year.” Profitability is also strong, with Romain stating, “We double our revenue each year and we double our EBITDA as well every year,” and “We are doing millions of Lightning transactions every year” These figures highlight LN Markets’ strong and active user base as well as Lightning’s scalability.
The exchange focuses on
-
 @ cae03c48:2a7d6671
2025-06-19 03:00:58
@ cae03c48:2a7d6671
2025-06-19 03:00:58Bitcoin Magazine

Bitdeer Raises $330M to Expand Bitcoin Mining and AI OperationsSingapore-based Bitcoin mining firm Bitdeer Technologies Group has launched a $330 million convertible notes offering, aiming to strengthen its mining operations, develop ASIC rigs, and scale its AI infrastructure.
The notes, due in 2031, carry an annual interest rate of 4.875% and may be converted into Bitdeer Class A shares at a 25% premium to the current stock price of $11.84, placing the conversion price at approximately $15.88 per share.
The offering is targeted at qualified institutional buyers under Rule 144A of the Securities Act. If investors exercise an option to buy more within 13 days, the offering could reach $375 million.
This is Bitdeer’s third convertible notes raise. Previously, the company secured $150 million in August and $360 million in November last year. According to Bitdeer, the offering is expected to close on June 23, 2025.
Net proceeds are expected to total roughly $319.6 million. Around $129.6 million will go toward a zero-strike call option, with $36.1 million allocated for concurrent note exchanges. The remaining funds will support datacenter expansion, new ASIC rig development, and general corporate needs.
Bitdeer is also conducting a note exchange, offering cash and equity to holders of its 8.50% convertible notes due 2029. That transaction includes approximately $36.1 million in cash and 8.1 million shares, exchanged for $75.7 million in outstanding notes.
This announcement follows Bitdeer’s recent growth. As previously reported, the company mined 196 BTC in May (worth over $21 million) and expanded its self mining hashrate to 13.6 EH/s. New SEALMINER rigs were deployed across sites in Texas, Norway, and Bhutan, and its AI cloud platform, powered by large language models, officially launched.
“In May 2025, we continued to deploy our SEALMINER mining rigs to our sites in Texas, U.S., Norway, and Bhutan, bringing Bitdeer’s self-mining hashrate to 13.6 EH/s,” said Matt Kong, Chief Business Officer at Bitdeer.
Bitdeer also raised capital from Tether in 2024 and secured $40 million from a debt facility with Matrix Finance in May. Both Bitdeer and Matrix are led by Jihan Wu, co-founder of Bitmain.
With its market cap now exceeding $2.3 billion, Bitdeer continues to invest in scaling its infrastructure and technology as competition in Bitcoin mining and AI computing intensifies.
This post Bitdeer Raises $330M to Expand Bitcoin Mining and AI Operations first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-06-19 03:00:57
@ cae03c48:2a7d6671
2025-06-19 03:00:57Bitcoin Magazine

The Trolls Are Coming: Defending Bitcoin Mining from Patent TrollsIntroduction: Patent Trolls Targeting Bitcoin Mining
Bitcoin’s use of elliptic curve cryptography (ECC), which is essential for generating key pairs and validating digital signatures, has drawn the attention of a nonpracticing entity (NPE), more commonly known as a patent troll. In May 2025, Malikie Innovations Ltd., a troll that acquired thousands of patents from BlackBerry’s portfolio, filed lawsuits against major mining firms Core Scientific (CORZ) and Marathon Digital Holdings (MARA). (Some considered MARA an original patent troll itself and thus have expressed schadenfreude at the current attacks.) Malikie claims that routine Bitcoin operations (like verifying transactions with ECC-based signatures) infringe on several ECC-related patents originally developed by Certicom (later owned by BlackBerry). The patents cover techniques for accelerated digital signature verification, finite field math optimizations and other ECC improvements.
Malikie’s lawsuits, in Texas’ Eastern District against CORZ and Western District against MARA, demand damages for past infringement and an injunction against further use of the patented methods. In essence, Malikie seeks to impose a licensing regime on Bitcoin’s core cryptographic functions, a move that could set a dangerous precedent for the entire industry. If Malikie succeeds, virtually anyone running Bitcoin software (miners, node operators and potentially even wallet providers) could be exposed to patent liability. This threat has galvanized the Bitcoin and open source communities to explore every available defensive tool. In this preparatory briefing, we examine:
- Historical legal strategies used to fend off troll lawsuits.
- The mechanics, costs and effectiveness of Inter Partes Review (IPR) in challenging software/crypto patents.
- Community-led responses (EFF, Linux Foundation, COPA, etc.) that help defendants by funding prior-art searches or legal defenses.
- The potential ramifications for Bitcoin mining if Malikie’s claims prevail, drawing parallels from other industries.
1. Historical Strategies Against NPE Patent Lawsuits
Over the past two decades, tech companies and industries have developed several tactics to combat patent trolls. Key strategies include challenging patent validity, shifting lawsuits to favorable venues via declaratory judgment actions, leveraging recent case law to dismiss abstract patents and simply refusing to settle in order to deter trolls.
While not all strategies will apply to these cases, for completeness I’ll outline these approaches:
Rigorous Invalidity Challenges (Prior Art – §102/103): The most direct way to neutralize a troll’s patent is to demonstrate that the patent should never have been granted in the first place because earlier technology already taught the same invention. Defendants search for prior art — such as earlier publications, academic papers, standards (RFCs) or open source code — that predate the patent’s priority date and disclose the claimed invention. If a single prior art reference embodies every element of a patent claim, the claim is “anticipated” (invalid for lack of novelty under 35 U.S.C. §102). If no one reference is complete but a combination of references would have been obvious to a skilled person, the claim is invalid for obviousness (§103). In the Malikie cases, for example, Bitcoiners have been called to urgently collect publications from before January 18, 2005 (the priority date of one asserted patent, U.S. 8,788,827), and before December 31, 2001 (for U.S. 7,372,960). to prove the patented ECC techniques were already known. The Bitcoin community has noted that Hal Finney and others actively tracked ECC patents and even delayed certain optimizations in Bitcoin until patents expired — for instance, the famed “GLV endomorphism” speedup was only added to Bitcoin Core after its patent lapsed (and caution on the GLV issue was taken by developers, which Malikie itself acknowledged in its complaint — paragraphs 20 and 21 of the MARA complaint, for instance). Unearthing such prior art may not only win the case at hand but invalidate the patent for everyone.
-
Inter Partes Review (IPR) and Post-Grant Proceedings: Beyond raising invalidity in court, since 2012 defendants have relied on IPR at the Patent Trial and Appeal Board (PTAB) as a powerful forum to knock out bad patents. IPR is an administrative trial within the U.S. Patent Office where challengers can present prior patents or publications to show a granted patent is invalid. We detail IPR’s mechanics in Section 2, but historically it has been a favored tool against NPEs because of its high success rate (around 70%+ of patents see claims canceled when reviewed) and lower burden of proof (“preponderance of the evidence,” 51%, rather than the “clear and convincing,” 75%, standard in court). Companies sued by trolls often file IPR petitions early and then move to stay (or pause) the litigation pending the PTAB’s decision — a stay which many courts grant once an IPR is instituted, given the likelihood that the patent may be invalidated. Notably, in the landmark Personal Audio “podcasting patent” case, the Electronic Frontier Foundation (EFF) filed an IPR that successfully invalidated a troll’s patent on podcast distribution, even as the troll was suing podcasters in East Texas. That IPR, funded by over a thousand small donations from the community, culminated in the Patent Office canceling all claims of the patent in 2015, a result later affirmed on appeal. This victory protected not just the sued targets (like comedian Adam Carolla) but all podcasters going forward. Similarly, the best path for the Bitcoin ecosystem may be to file IPR (or the related Post-Grant Review) against Malikie’s ECC patents, leveraging the mountain of cryptography literature from the 1990s and early 2000s to demonstrate that Bitcoin’s use of ECC was not novel to Malikie’s assignors.
-
Declaratory Judgment (DJ) Actions: Another defensive tactic is to preempt the troll by filing a declaratory judgment lawsuit in a preferred court, seeking a ruling that your product does not infringe or that the patent is invalid. Under U.S. law, a company that feels threatened by a patent (e.g., it received a demand letter or sees peers being sued) can sometimes sue first if it can show a substantial controversy. The goal is to avoid being haled into the NPE’s chosen venue (historically, the Eastern District of Texas was favored by trolls) and instead litigate in a more neutral or defendant-friendly forum. For instance, when notorious troll Lodsys threatened dozens of small app developers over in-app purchase patents, one strategy (supported indirectly by Apple and Google) was to seek declaratory rulings outside of East Texas to undermine the troll’s jurisdiction. In practice, DJ actions can prompt a faster resolution or even settlement on better terms. However, the patent owner must have made a concrete infringement assertion to establish the requisite “case or controversy.” In Malikie’s situation, if other Bitcoin companies (exchanges, wallet providers, smaller miners) suspect they are next in line, those companies could file a declaratory suit in a jurisdiction of their choice. This would flip the script, making Malikie the defendant and potentially consolidating the fight in a forum less favorable to NPEs.
-
Motions to Dismiss Under Alice (35 U.S.C. §101): Since the 2014 Alice Corp. v. CLS Bank decision, many software patents have been invalidated early in litigation for claiming unpatentable abstract ideas. Courts now examine whether a patent is directed to a fundamental abstract idea (like a mathematical formula) without an “inventive concept.” Defendants often file Rule 12(b)(6) motions to dismiss, arguing the patent is invalid on its face under §101. While cryptographic algorithms can be viewed as mathematical computations (a classic abstract idea), success with an Alice motion depends on how the patent claims are drafted. If the claims merely cover a generalized math formula or the concept of using ECC on a computer, a judge could void them as abstract. Indeed, some defendants have beaten trolls this way, sparing the cost of trial. In Malikie’s case, their patents seem to cover specific techniques to speed up ECC computations (like endomorphisms, modular reduction optimizations, etc.) — arguably “technical improvements” in cryptography rather than a naked abstract idea. That may make an Alice challenge less straigh
-
 @ cae03c48:2a7d6671
2025-06-19 03:00:56
@ cae03c48:2a7d6671
2025-06-19 03:00:56Bitcoin Magazine

‘Ancient’ Bitcoin Supply Now Outpacing Newly Mined BTC: Fidelity ReportFidelity Digital Assets released a new report that reveals that for the first time in history, more bitcoin is entering “ancient supply,” which refers to coins that have remained unmoved for 10 years or more, than are being mined.
As of June 8, 17% of all bitcoin falls into the category of “ancient supply”—meaning these coins have not moved in a decade or more. What could this mean for scarcity, market dynamics, and investors’ conviction? Find our team’s thoughts: https://t.co/EALzrfS92c pic.twitter.com/Ckm3MylTLY
— Fidelity Digital Assets (@DigitalAssets) June 18, 2025
As of June 8, an average of 566 BTC per day is crossing the 10 year threshold, while only 450 BTC is being issued daily following the 2024 halving. 3
“The share of ancient supply also tends to increase each day, with daily decreases observed less than 3% of the time,” the report says. “In contrast, that number increases to 13% when the threshold is lowered to bitcoin holders of five years or more.”
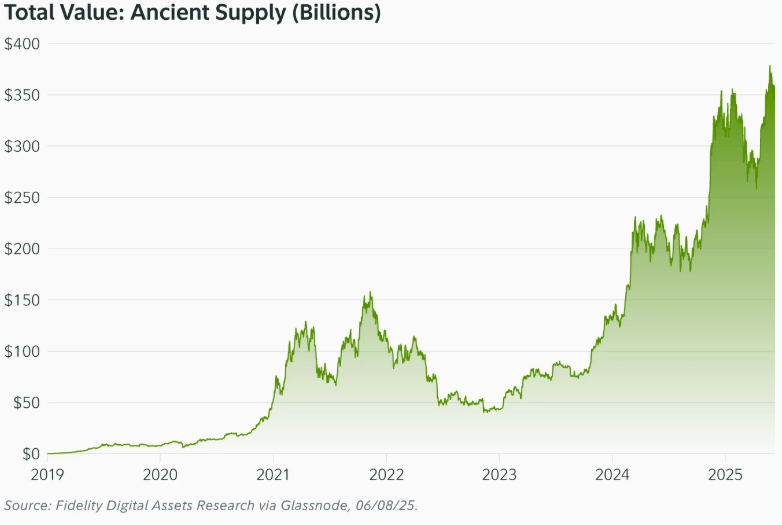
Bitcoin’s ancient supply has grown since January 1, 2019, when Satoshi Nakamoto became the first 10 year holder. Today, over 3.4 million BTC fall into this category, worth more than $360 billion. Around 1/3 is believed to belong to Nakamoto.
Despite their rising value, long-term holders are not cashing out. Ancient supply makes up over 17 percent of all bitcoin, and that share continues to grow.
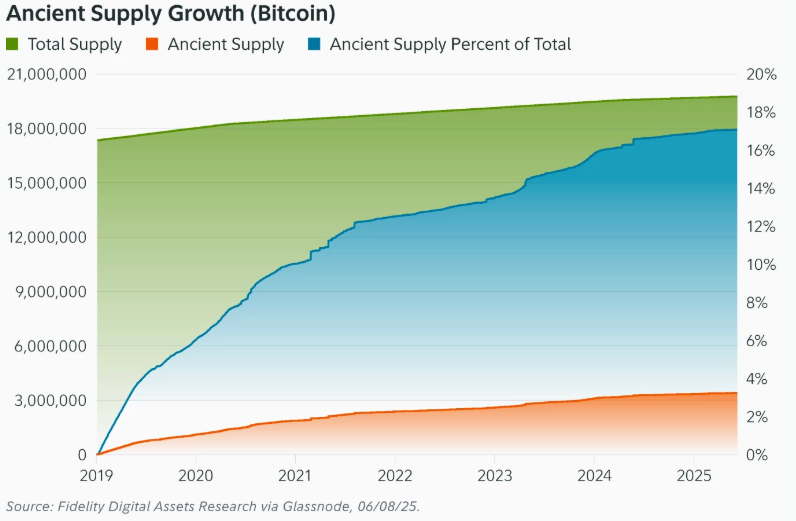
Since the 2024 halving, the number of coins entering ancient supply has consistently outpaced the number of new coins being mined, according to the report. This shift highlights growing long-term conviction among holders and reflects a broader tightening of bitcoin’s liquid supply.
Following the 2024 U.S. election, ancient supply declined on 10% of days, which is nearly four times higher than the historical average. Movement among the holders was even more pronounced, with daily declines occurring 39% of the time.
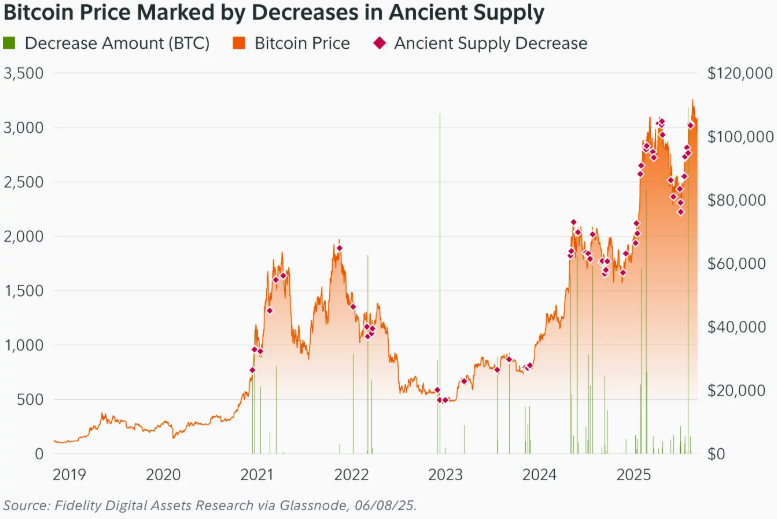
To better track this trend, Fidelity uses a metric called the ancient supply HODL rate. It measures how many coins are entering the 10 year category each day, adjusted for new issuance. This rate turned positive in April 2024 and has remained that way, reinforcing the long-term supply shift.
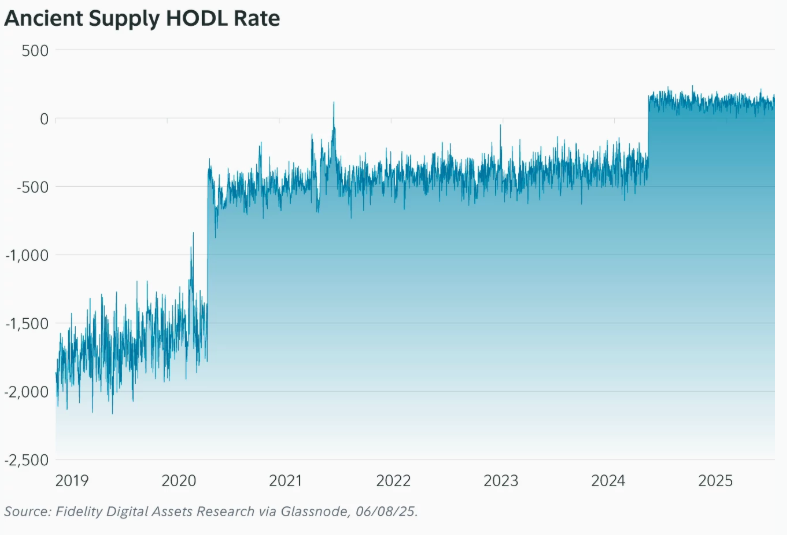
Looking ahead, Fidelity Digital Assets projections that ancient supply could reach 20 percent of total bitcoin by 2028 and 25 percent by 2034. If public companies holding at least 1,000 BTC are included, it could reach 30 percent by 2035.

As of June 8, 27 public companies hold more than 800,000 BTC combined, according to the report. This growing institutional presence may further tighten supply and increase the influence of long-term holders over time.

This post ‘Ancient’ Bitcoin Supply Now Outpacing Newly Mined BTC: Fidelity Report first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 56a18512:78772baf
2025-06-19 02:19:49
@ 56a18512:78772baf
2025-06-19 02:19:49Lots of wars, soon Christ will come! Repent you sons of sinners!
-
 @ dfa02707:41ca50e3
2025-06-19 02:02:03
@ dfa02707:41ca50e3
2025-06-19 02:02:03Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ eb0157af:77ab6c55
2025-06-19 02:01:42
@ eb0157af:77ab6c55
2025-06-19 02:01:42The world’s leading bitcoin mining rig manufacturers are moving to build facilities in the U.S. to sidestep tariffs imposed by President Trump.
According to Reuters, the three Chinese giants dominating global ASIC device production — Bitmain, Canaan, and MicroBT — have launched a strategic shift toward the United States, driven by steep tariffs enforced by the Trump administration.
The move is a direct response to American protectionist policies. Trump introduced 30% tariffs on Chinese tech products, heavily impacting a sector where China controls over 90% of global mining hardware production.
Bitmain led the way, starting device assembly on U.S. soil last December, just weeks after Trump’s election victory. Canaan quickly followed, launching a pilot production line in the U.S. to bypass the heavy import taxes.
Leo Wang, Canaan’s VP of Business Development, called the American project “exploratory,” highlighting the unpredictability of current trade policies. MicroBT, the world’s third-largest player, announced it was actively rolling out a U.S.-based “localization strategy.”
Guang Yang, Chief Technology Officer of Conflux Network, noted that “the U.S.-China trade war is triggering structural, not superficial, changes in Bitcoin’s supply chains.”
For American firms, this shift represents “a strategic pivot toward ‘politically acceptable’ hardware sources,” Yang added. The near-monopoly of the three Chinese mining giants — which, according to Frost & Sullivan, accounted for 95.4% of the global hashrate sold in 2023 — has raised national security concerns in the U.S.
Sanjay Gupta, Chief Strategy Officer at Auradine, pointed out the imbalance:
“While over 30% of global bitcoin mining occurs in North America, more than 90% of mining hardware originates from China representing a major imbalance of geographic demand and supply.”
The post Bitmain, Canaan, and MicroBT open U.S. factories to dodge Trump’s tariffs appeared first on Atlas21.
-
 @ 20986fb8:cdac21b3
2025-06-19 01:58:32
@ 20986fb8:cdac21b3
2025-06-19 01:58:32Build your AI-powered MiniApp, unlock new possibilities in decentralized social and payment experiences
📅 Timeline & Prize Pool
- Kickoff: June 20, 2025
- Development Phase: June 20 – July 15
- Demo & Community Review: July 15 – July 31
- Final Results: Early August
💰 Total Prize Pool: 10,000,000 sats (paid in BTC), awarded across three rounds:
- 🥇 1st Prize: 1,000,000 sats 1
- 🥈 2nd Prize: 700,000 sats 1
- 🥉 3rd Prize: 500,000 sats 2
- 🎁 Participation Rewards – All successfully deployed MiniApps will receive rewards (details TBA)
🛠 Hackathon Tracks
- Nostr Tools: Nip-05 services, Relay tools, Short notes services, plugins and more.
- Payment Solutions – Innovations in Payments: BTC, Lightning, Stablecoins, and Local Currencies; Red packets, tipping, QR pay, content paywalls, merchant tools
- AI Interaction – AI bots, content recommenders, smart media MiniApps
- Other Innovative Use Cases – Any decentralized application idea is welcome
How to participate?
✅ Nostr Version: - Submit your application to YakiHonne Smart Widgets GitHub - Deploy your MiniApp via YakiHonne (new or adapted from an existing app) - Your MiniApp must be usable and testable in Nostr posts
🧑⚖️ Judging Criteria
- Technical implementation & innovation
- UX/UI design quality
- Level of decentralization
- Integration with Nostr / YakiHonne
- Community votes
- Expert panel evaluation
🎉 Why Join?
- Build the next generation of AI-powered decentralized MiniApps
- Deploy on the most open and composable network: Nostr + Lightning + AI
- Gain global exposure, community traffic, and funding
- Rapidly validate your ideas in the real world
- Pioneer the Agentic MiniApp development track
🚀 Why Join the Agentic Mini Apps Hack on Nostr?
The Nostr network is rapidly growing, opening up unprecedented opportunities for innovation in decentralized social and payment systems. At the same time, AI is revolutionizing how we interact—with intelligent agents, social assistants, and content recommendations.
Agentic MiniApps represent a new generation of applications designed for this future: ✅ Lightweight, open, and composable. ✅ Natively support AI, payments, and social interaction. ✅ Decentralized deployment—no downloads needed, users access them directly from Nostr posts.
Agentic Mini Apps Hack on Nostr – Round 1 is the first hackathon centered on this emerging format. It combines Nostr + Bitcoin/Lightning payments + AI to explore the next generation of decentralized apps, enriching Nostr with advanced social, payment, and intelligent interaction capabilities—powering the open ecosystem forward.
What is a Mini App?
A MiniApp as a Smart Widgets are interactive graphical components encapsulated as Nostr events, designed for seamless integration into applications. Each widget type serves a specific purpose, with well-defined structures and behaviors to support various use cases.
Refer to https://yakihonne.com/docs/sw/intro for full documentation.
Widget Types
Basic Widget (Does not concern the current Hackathon)
- Description: A versatile widget comprising multiple UI components for flexible display and interaction.
- Components:
- Images (mandatory, maximum of one).
- Input Field (optional, maximum of one).
- Buttons (optional, maximum of six).
- Use Case: Ideal for scenarios requiring a combination of visual elements and user inputs, such as forms or dashboards.
Action Widget
- Description: A streamlined widget designed to trigger an action by embedding a URL in an iframe.
- Components:
- Image (single, for visual representation).
- Button (single, type: app).
- Behavior:
- Clicking the button opens the specified URL within an iframe.
- The iframe does not return any data to the parent application.
- Use Case: Suitable for launching external applications or resources without expecting a response, such as opening a third-party tool.
Tool Widget
- Description: A widget that facilitates interaction with an external application via an iframe, with data exchange capabilities.
- Components:
- Image (single, for visual representation).
- Button (single, type: app).
- Behavior:
- Clicking the button opens the specified URL within an iframe.
- The iframe is configured to return data to the parent application upon interaction.
- Use Case: Perfect for scenarios requiring data retrieval or feedback from an external tool, such as a configuration interface or a data picker.

Technical Notes
- Nostr Event Structure: Each widget is represented as a Nostr event, ensuring compatibility with the Nostr protocol for decentralized communication.
- Iframe Integration: For Action and Tool widgets, the iframe must adhere to standard web security practices (e.g., sandboxing, CORS policies) to ensure safe URL embedding.
- Extensibility: Developers can customize widget appearance and behavior within the defined constraints (e.g., maximum button limits, single input field) to align with application requirements.
🔧 How to Deploy Your MiniApp?
Developers will build and deploy via the YakiHonne Programmable Smart Widgets Product: 1. Build your mini app using YakiHonne provided packages 1. Smart widget handler package: https://yakihonne.com/docs/sw/smart-widget-handler 2. Smart widget previewer package (required for clients): https://yakihonne.com/docs/sw/smart-widget-previewer 2. Deploy to a hosting service: 1. Vercel, Netflify, GitHub Pages, etc. 2. Ensure the
/.well-known/widget.jsonfile is accessible (Widget Manifest)JSON { "pubkey": "your-nostr-pubkey-in-hex", "widget": { "title": "My Amazing Widget", "appUrl": " https://your-app-url.com", "iconUrl": " https://your-app-url.com/icon.png", "imageUrl": " https://your-app-url.com/thumbnail.png", "buttonTitle": "Launch Widget", "tags": ["tool", "utility", "nostr"] } } // This manifest serves two important purposes: // 1. Verifies the authenticity of your mini app // 2. Provides metadata for Nostr clients to display your widget (miniapp)3. Register with YakiHonne Widget Editor 1. Go to the YakiHonne Widget Editor 2. SelectActionorToolbased on your mini app type 3. Enter your mini app URL 4. The editor will fetch your manifest and validate it 5. Configure any additional settings 6. Publish to NostrSide notes:
- Smart widget previewer is required by Nostr client to preview all types of smart widgets whether: Action/Tool or even the Basic ones (Please refer to Smart widget previewer for more details)
- Smart widget builder is only used to created embedde
Basicsmart widgets types, which out of scope for this hackathon (Please refer to Smart widget builder for more details) - Smart widget handler is necessary for the
MiniAppsdevelopers to build and deploy theirMini-Apps(Smart widgets from types: Action/Tool) (Please refer to Smart widget handler for more details)
Common Use Cases
Action Mini Apps
- Note composers with special formatting
- Media uploaders
- Event creators
- NFT minters
- Payment widgets
Tool Mini Apps
- Analytics providers
- Search tools
- Data aggregators
- Content recommendation engines
- Information lookup services
💡 YakiHonne Smart Widgets are programmable micro-app components enabling real-time social interaction, on-chain payments, and AI features—creating a seamless “scroll-and-use” experience.
🎯 Why Choose YakiHonne Smart Widgets?
⚡ Fast deployment, viral reach – Go live instantly, no app store approval, spread via Nostr posts 🤖 Deep AI + Payment + Social integration – Build immersive, smart and transactional MiniApps
🔐 One-click login – Use Nostr, a pubkey with no KYC hassle
📈 High visibility – Your MiniApp lives in nostr events, clients, posts, DMs, and community feeds
🌍 Open ecosystem – Supports Lightning / BTC / stablecoins, accessible across clientsReference Links
- Smart widgets full documentation: https://yakihonne.com/docs/sw/intro
- Smart widgets builder package a package for NodeJS to build Nostr Smart Widgets:
- https://yakihonne.com/docs/sw/smart-widget-builder
- https://www.npmjs.com/package/smart-widget-builder
- Smart widgets previewer a React component for previewing and interacting with Nostr-based Smart Widgets:
- https://yakihonne.com/docs/sw/smart-widget-previewer
- https://www.npmjs.com/package/smart-widget-previewer
- Smart widgets handler an sdk to communicate with embeded apps on nostr smart widgets:
- https://yakihonne.com/docs/sw/smart-widget-handler
- https://www.npmjs.com/package/smart-widget-handler
Quick Tutorials
Action/Tool smart widgets mini-apps Part 1
Action/Tool smart widgets mini-apps Part 1](https://www.youtube.com/watch?v=SS-5N-LVCPM)
Action/Tool smart widgets mini-apps Part 2
Action/Tool smart widgets mini-apps Part 2](https://www.youtube.com/watch?v=4NfMqjkRKnQ)
Action/Tool smart widgets mini-apps Part 3
Action/Tool smart widgets mini-apps Part 3](https://www.youtube.com/watch?v=VGCEEGfIo_I)
-
 @ 52524fbb:ae4025dc
2025-06-19 01:50:14
@ 52524fbb:ae4025dc
2025-06-19 01:50:14GBP/JPY currency pair dubbed Beast or Widowmaker by traders is notoriously renowned for exceptional volatility with rather unpredictable price swings occurring rapidly. Potent combination of British Pound sensitivity to UK economic turmoil post-Brexit and Japanese Yen's safe-haven status fuels this characteristic globally. This potent mix further amplified by sizable interest rate differentials spawns a wildly volatile trading environment often fraught with unpredictability quickly. British Pound GBP remains inherently vulnerable mostly due to fluctuations triggered by sudden domestic political developments or sporadic releases of economic data. Post-Brexit UK economy grapples with gnarly structural issues and Pound sterling reacts violently to trade negotiation headlines and BoE monetary policy moves. Unexpected economic data releases or leadership changes in UK often trigger substantial moves in Pound rapidly amidst brewing political instability.
Japanese Yen JPY exhibits traditionally quirky safe-haven traits conversely under radically uncertain market conditions very quietly. Capital flows into Yen rapidly during global market turmoil or severe geopolitical crises triggering risk-off sentiment and making it surge in value. GBP might weaken due to UK-specific woes but some concurrent global risk-off event could catapult JPY higher against major currencies including Pound. Extreme volatility characterizing GBP/JPY stems largely from interaction between two forces that frequently amplify each other violently somehow. Envision a situation where lackluster UK economic data sends Pound tumbling lower and concurrently some major geopolitical kerfuffle sparks frantic flight into safe-haven Yen. Both factors would aggressively push GBP/JPY downwards pretty rapidly and sharply downwards still further. Strong UK data paired with a risk-on vibe worldwide can send GBPJPY soaring as JPY gets thoroughly pummeled. Movements in GBP/JPY are often starkly more pronounced than those seen in other major currency pairs under normal market conditions.
Significant interest rate differentials between UK and Japan add another layer of complexity and opportunity pretty substantially nowadays. Bank of England has generally maintained significantly higher interest rates than ultra dovish Bank of Japan over past few decades mostly. GBP/JPY appears particularly attractive for carry trade strategies where traders borrow cheap JPY and invest heavily in higher yielding GBP. Traders can reap rewards from daily interest accrual and potential capital gains if global risk appetite keeps carry trade momentum trending higher. Risk of a massive carry trade unwind in GBP/JPY remains substantial pretty much nowadays. Sudden global risk appetite downturn or BoJ policy shift surprisingly triggers rapid reversal as borrowed Yen gets bought back and higher-yielding Pound positions liquidate rapidly overseas. Such unwind can precipitate precipitous downward plunges befitting their notorious Widowmaker moniker eerily. GBP/JPY trading brutally tests resolve of even seasoned investors daily. Geopolitical events and significant yield differentials heavily amplify its volatility stemming from disparate fundamental drivers of constituent currencies. Its large swings offer potentially rewarding opportunities in Forex for experienced traders who are well-prepared and willing to take considerable risks.
-
 @ 52524fbb:ae4025dc
2025-06-19 01:40:59
@ 52524fbb:ae4025dc
2025-06-19 01:40:59NZD/USD currency pair affectionately known as Kiwi exemplifies commodity-sensitive currency behavior heavily influenced by New Zealand's hefty agricultural export reliance overseas. New Zealand economy heavily reliant on dairy products meat and other ag goods means Kiwi dances wildly to global food prices and China's whims. New Zealand's economy relies heavily on primary sector industries with dairy farming being a rather significant contributor somehow overseas. Fonterra its dominant dairy cooperative plays a significant role globally in various markets as one of world's largest dairy exporters. GDT auctions setting prices for various dairy products are keenly watched by NZD/USD traders fairly closely nowadays apparently. Strong global demand particularly from China drives up GDT auction prices directly translating into heftier export earnings for New Zealand bolstering NZD.
Meat and wool exports significantly bolster New Zealand's commodity currency status alongside dairy products reinforcing its robust export receipts quite substantially overseas. NZD/USD frequently acts as barometer for global agricultural demand and remains highly sensitive pretty much to economic shifts in China somehow. China being a huge consumer of New Zealand's farm produce its economic vitality and demand for imports heavily influence NZD exchange rates. Robust economic indicators from China or hints of surging demand for food imports frequently give Kiwi currency a welcome boost. Reserve Bank of New Zealand operates with such dynamics squarely in its mind evidently nowadays. RBNZ keenly aware of commodity price fluctuations impact on domestic economy while its mandate focuses on price stability and high employment levels. RBNZ may raise interest rates somewhat vigorously amid surging export prices and an extremely booming agricultural sector beset by inflationary pressures. A sharp downturn in commodity prices might prompt RBNZ to pivot towards dovish policies and possibly slash rates, thereby stimulating economic growth rapidly. Traders scrutinize RBNZ monetary policy statements and economic forecasts quite closely for cryptic insights into reaction functions amidst volatile commodity cycles.
NZD/USD appreciates markedly during heightened global risk appetite periods when investors eagerly invest in growth-sensitive assets with reckless abandon. This often aligns with a positive outlook for global growth which in turn bolsters demand somewhat irregularly across various commodity markets. During risk-off environments investors typically flock to relatively safe havens like US Dollar and NZD subsequently weakens quite drastically. NZD/USD pair serves as a singular lens into a tiny economy heavily swayed by natural resources and commodity prices abroad. Kiwi's movements are distinctly tied to fortunes of its agricultural sector and insatiable demand from key trading partners making it rather compelling currency pair.
-
 @ b1ddb4d7:471244e7
2025-06-18 09:01:10
@ b1ddb4d7:471244e7
2025-06-18 09:01:10Why are Stripe Alternatives are growing like mushrooms? When it comes to online payment processing, Stripe has long dominated the conversation.
However, with its complex pricing structure, strict policies and first-world focus, many entrepreneurs and companies are actively seeking viable Stripe alternatives.
Whether you’re a SaaS startup, e-commerce store, or global enterprise, choosing the right payment processor can significantly impact your bottom line and customer experience.
Table of Contents
- Why Consider Stripe Alternatives?
- The Complete List of Stripe Alternatives
- Additional Notable Mentions
- How to Choose the Right Stripe Alternative
- Conclusion
Why Consider Stripe Alternatives?
Before diving into our comprehensive list, it’s worth understanding why businesses are exploring alternatives to Stripe. While Stripe offers robust features and excellent developer tools, some businesses face challenges with pricing transparency, limited global coverage, or specific industry requirements that Stripe doesn’t fully address.
The Complete List of Stripe Alternatives
Based on extensive research and analysis of the payment processing landscape, here are 27 proven Stripe alternatives that could be the perfect fit for your business:
1. Flash – Easiest Bitcoin Payment Solution
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
2. Lemon Squeezy – The SaaS-Focused Alternative
Dubbed as “acq’d by Stripe,” Lemon Squeezy offers a comprehensive solution specifically designed for digital product sales and SaaS businesses. It provides strong customer support, built-in analytics, and handles payments, subscriptions, global tax compliance, and fraud prevention in one platform.
3. Gumroad – Creator Economy Champion
Gumroad has carved out a niche serving creators and small businesses by providing tools for selling digital products, physical goods, and subscriptions. It’s particularly popular among content creators, artists, and independent entrepreneurs who want to experiment with various ideas and formats. They also open-sourced their code which is quite the ‘chad-move’.
4. Paddle – All-in-One SaaS Commerce
Paddle caters to SaaS and software companies by offering a comprehensive platform with billing, licensing, and global tax handling capabilities. It’s designed to be a complete solution for subscription-based businesses, handling payments, tax, and subscription management in one platform.
5. FastSpring – Global E-commerce Specialist
FastSpring specializes in e-commerce solutions for software and SaaS companies, with a focus on global payments and subscription management. According to TechnologyAdvice, it’s particularly strong for international transactions and helps companies sell more, stay lean, and compete big.
6. 2Checkout – Versatile Payment Solutions
2Checkout (now part of Verifone) offers versatile payment solutions excelling in global payments, subscription billing, and digital commerce. One of the best stripe alternatives as it’s an all-in-one monetization platform that maximizes revenues and makes global online sales easier, supporting over 200 countries and territories.
7. Payoneer – Cross-Border Payment Expert
Payoneer simplifies cross-border payment solutions, offering local payment ease globally with a focus on market expansion and multi-currency support. It’s trusted by small to medium-sized businesses for global payment solutions and international money transfers.
8. Chargebee – Subscription Management Leader
Chargebee is a subscription management platform perfect for SaaS and SMBs, with robust billing and revenue management features. If you were looking for stripe alternatives to setup subscriptions, Chargebee might be right for you. It streamlines revenue operations and helps businesses grow efficiently with comprehensive subscription billing capabilities.
9. Maxio (formerly Chargify) – B2B SaaS Billing
Maxio offers a robust platform for B2B SaaS billing and financial operations, focusing on growth and efficiency for subscription businesses. It’s the most complete financial operations platform for B2B SaaS, bringing core financial operations into one platform.
10. Recurly – Dynamic Subscription Management
Recurly offers dynamic subscription management platform, excelling in churn management and data insights for subscription growth. It’s the only proven platform that expands and protects your recurring revenue with subscription management, recurring billing, and payments orchestration.
11. Braintree – PayPal’s Enterprise Solution
Braintree (by PayPal) provides a versatile global payments platform, integrating multiple payment methods with a focus on conversion and security. It delivers end-to-end checkout experiences for businesses, offering single-touch payments and mobile optimization.
12. PayKickstart – Modern Commerce Platform
PayKickstart offers a modern commerce platform for online billing and affiliates, focusing on revenue maximization and churn minimization. It’s the most complete checkout, recurring billing, affiliate management, and retention solution with global capabilities.
13. PayPro Global – Full-Service E-commerce
PayPro Global offers a full-service eCommerce solution for selling software and SaaS, focusing on global payments, tax compliance, and customer support. It provides flexible solutions with over 70 payment methods and great support for software companies.
14. Shopify Payments – E-commerce Integration
Integrated with Shopify, this service is ideal for SMBs in eCommerce, offering a seamless shopping cart and payment experience. It’s the simplest way to accept online payments, automatically set up for major methods with no fees for some payment types.
15. Square – Versatile POS and Payment Solutions
Square provides versatile POS and payment solutions for small businesses with a strong focus on retail and mobile payments. Forbes Advisor notes it as one of the top alternatives for businesses needing both online and offline payment capabilities.
16. Zoho Billing – Integrated Business Solution
Zoho Billing is an online recurring billing and subscription management solution, ideal for small and medium-sized businesses seeking professional invoice creation, time and expense tracking, and improved cash flow management. Zoho isn’t just competing for stripe alternatives, they offer a ton of other products and services.
17. WePay – Chase Company Integration
WePay, a Chase company, provides integrated payment solutions for ISVs and SaaS companies with customizable payment solutions. It’s designed for platforms like marketplaces and small business tools, offering seamless user experience and fraud protection.
18. QuickBooks Payments – SMB Accounting Integration
This service provides seamless accounting and payment solutions for SMBs and SaaS businesses, featuring real-time tracking and automated bookkeeping. It lets small businesses accept payments online from anywhere with easy integration into QuickBooks accounting.
19. Mangopay – Marketplace Payment Infrastructure
Mangopay offers a modular payment infrastructure for marketplaces and platforms, emphasizing flexibility, global payouts, and AI-powered anti-fraud. It uses flexible wallets built to orchestrate fund flows and monetize payment experiences.
20. Coinbase Commerce – Cryptocurrency Payments
Coinbase Commerce enables businesses to accept payments from around the world using cryptocurrency. It offers instant settlement, low fees, and broad asset support, making it easy for merchants to accept digital currency payments globally.
21. BTCPay Server – Open-Source Bitcoin Processor
BTCPay Server is a self-hosted, open-source cryptocurrency payment processor with 0% fees and no third-party involvement. It’s secure, private, censorship-resistant, and completely free for businesses wanting full control over their Bitcoin payments.
22. Lago – Open-Source Billing Alternative
Lago is an open-source alternative to Stripe Billing and Chargebee, specializing in billing and metering in one place for usage-b
-
 @ 52524fbb:ae4025dc
2025-06-19 01:32:01
@ 52524fbb:ae4025dc
2025-06-19 01:32:01EUR/GBP currency pair offers fascinating insight into divergent economic paths of Euro and British Pound wielding European powerhouses with starkly differing monetary policies. Situated geographically close yet starkly diverging economically post-Brexit this cross-channel nexus teems with lucrative opportunities for canny traders keenly observing contrasting fortunes amidst wildly divergent policy responses in Eurozone and United Kingdom. EUR/GBP reflects relative economic health starkly and monetary policy stances vehemently of European Central Bank alongside Bank of England pretty much. Both central banks share a price stability goal and react differently to economic environments resulting in significant movements within currency pairs occasionally.
Eurozone inflation persists markedly higher than UK rates or strong growth momentum prevails and ECB adopts decidedly hawkish stance by raising interest rates. Divergence in monetary policy makes Euro suddenly rather attractive leading to significant EUR/GBP appreciation very quickly over time. EUR/GBP will likely plummet if UK economy outshines Eurozone or BoE signals an aggressive rate hike pretty quickly. Brexit has been quite a pivotal factor undoubtedly for this particular pair of entities somewhat controversially. UK's departure from EU spawns long-term structural changes that subtly influence economic performance of both regions rather slowly now. Shifts in convoluted supply chains and disparate regulatory regimes can spawn enduring headwinds or surprisingly robust tailwinds for one economy or another very suddenly. UK businesses encountering heftier trade friction with EU nations versus their Eurozone rivals can hamper productivity and stunt growth thereby putting downward pressure on the Pound relative to the Euro.
Political developments in Eurozone and UK play a significant role alongside major structural shifts and unprecedented monetary policy decisions. Fiscal cohesion among Eurozone member states and stability of common currency are threatened by crises in major economies like France or Germany. Domestic political stability in UK and implementation of post-Brexit policies alongside fraught discussions with EU regarding Northern Ireland are pretty critical. EUR/GBP pair offers unique advantage being fairly less susceptible broadly to global risk sentiment compared pairs involving US Dollar or Yen. Its movements get finely calibrated rather irregularly according mostly to relative strengths or glaring weaknesses and also policy choices of two economies. EUR/GBP yields intriguing trading prospects for astute traders capable of deciphering such intricate narrative across multiple channels effectively.
-
 @ eb0157af:77ab6c55
2025-06-18 01:02:06
@ eb0157af:77ab6c55
2025-06-18 01:02:06Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ 04c3c1a5:a94cf83d
2025-06-18 12:40:02
@ 04c3c1a5:a94cf83d
2025-06-18 12:40:02123
-
 @ 04c3c1a5:a94cf83d
2025-06-18 12:26:00
@ 04c3c1a5:a94cf83d
2025-06-18 12:26:00123
-
 @ 31a4605e:cf043959
2025-06-18 19:28:26
@ 31a4605e:cf043959
2025-06-18 19:28:26Você já ouviu isso antes. Um bitcoiner é questionado sobre seus sats e, com um sorriso irônico, responde: “Perdi tudo num acidente de barco.” Mas de onde vem essa frase? Por que tantos bitcoiners fazem essa piada? E mais importante: o que ela realmente significa?
A origem do meme
A expressão "Lost all my Bitcoin in a boating accident" nasceu nos fóruns americanos de entusiastas de armas e metais preciosos, muito antes do Bitcoin ganhar notoriedade mainstream. O contexto original era o seguinte: alguém perguntava se você ainda tinha sua coleção de armas (ou ouro), e a resposta sarcástica era "infelizmente, perdi tudo num acidente de barco".
Essa desculpa servia como uma forma de recusar-se a declarar posse de bens aos olhos do governo ou de outras autoridades. Afinal, o que não se pode provar que existe, não pode ser confiscado, taxado ou regulado. Com o tempo, essa lógica encontrou um terreno fértil entre os defensores da soberania individual, um grupo no qual os bitcoiners naturalmente se encaixam.
A metáfora da resistência
Quando os maximalistas de Bitcoin adotaram a frase, ela passou a representar mais do que apenas uma desculpa para evitar perguntas incômodas: virou um símbolo de resistência contra um sistema financeiro cada vez mais invasivo e coercitivo. Dizer que “perdeu os seus Bitcoin num acidente de barco” é, muitas vezes, um eufemismo para dizer:
“Não é da sua conta quantos sats eu tenho.”
“Não reconheço a autoridade de quem tenta confiscar meu patrimônio digital.”
“Meus ativos são soberanos, autocustodiados e inalcançáveis por meios tradicionais.”
Bitcoin é liberdade, não compliance
O meme também toca num ponto central da filosofia bitcoin: a autocustódia e o direito à privacidade financeira. Em um mundo onde governos congelam contas, censuram transações e imprimem moeda ao bel-prazer, possuir Bitcoin é uma forma de resistência civil. Mas para que isso tenha valor real, é necessário que o indivíduo assuma a responsabilidade pela custódia e, inevitavelmente, pelo silêncio.
Dizer que você “perdeu seus Bitcoin” também é um lembrete: não fale sobre suas chaves privadas. Não ostente seus sats. Não coloque um alvo nas suas costas.
Um meme com propósito
No fim das contas, o “acidente de barco” é uma piada com um fundo muito sério. Ele nos relembra que, num sistema verdadeiramente soberano, a posse de ativos digitais é algo íntimo, pessoal e — se necessário — negável. É uma forma de reafirmar que o Bitcoin não é apenas uma ferramenta de investimento, mas um instrumento de liberdade.
Então da próxima vez que alguém te perguntar onde estão seus bitcoins, sorria e diga:
“Infelizmente, perdi tudo num acidente de barco…”
E deixe que fiquem imaginando.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 502ab02a:a2860397
2025-06-19 01:29:49
@ 502ab02a:a2860397
2025-06-19 01:29:49กลางทศวรรษ 1930 สหรัฐฯ เริ่มตระหนักว่า หากจะต้องเผชิญกับสงครามใหญ่ครั้งใหม่อย่างที่ยุโรปกำลังลุกเป็นไฟ กองทัพจะต้องพร้อมทั้งกำลังคนและ “กำลังแคลอรี่” โดยเฉพาะในสนามรบ ที่การขนส่งอาหารร้อนเต็มรูปแบบแทบเป็นไปไม่ได้เลย ยุคนั้นสิ่งที่มีอยู่คือ “ration” แบบกระป๋อง หรือแครกเกอร์กับน้ำตาลที่กินได้นาน แต่กินแล้วไม่อยากกินอีก
พันเอก Paul Logan แห่ง Quartermaster Corps เป็นผู้เสนอว่า “ทำไมเราถึงไม่มีอาหารฉุกเฉิน ที่เหมาะสำหรับทหารพกติดตัวได้ตลอดเวลา ให้พลังงานสูง กินง่าย ไม่เสียเร็ว และกินแล้วยังสามารถเดินหน้าต่อได้?” เขาไม่ได้ขอ “ขนม” แต่ขอ “อาวุธ” ทางพลังงาน และเมื่อพูดถึงช็อกโกแลต ผู้ผลิตเบอร์หนึ่งในอเมริกายุคนั้นก็คือ Hershey’s Chocolate Corporation
Logan ติดต่อไปหาประธานบริษัทชื่อ William Murrie ด้วยข้อเสนอที่ฟังดูย้อนแย้งสุดๆ เขาอยากได้ช็อกโกแลตที่ “กินไม่อร่อยเกินไป” เพราะหากมันอร่อยจนเกินไป ทหารจะกินหมดก่อนถึงเวลาจำเป็น จึงเป็นที่มาของภารกิจลับ: “Field Ration D”
โจทย์คือ… ต้องมีน้ำหนัก 4 ออนซ์ (ประมาณ 113 กรัม หรือขีดกว่าๆ) ให้พลังงานมากกว่า 600 kcal ต่อแท่ง ทนความร้อน 120°F (ประมาณ 49°C) ไม่ละลายในกระเป๋าทหาร ไม่อร่อยเกินไป (Seriously!) ช็อคโกแลต 1 แท่งแทนอาหาร 1 มื้อ ดังนั้นทหารแต่ละคนจะได้ช็อคโกแลตนี่ 3 แท่งต่อวัน
Milton Hershey (ผู้ก่อตั้งและเจ้าของอาณาจักรช็อกโกแลต) รับทราบโครงการและสนับสนุนแนวทางเต็มที่ รวมถึงให้ทุนวิจัยและกำลังการผลิตเริ่มต้นและคนที่ทำสูตรสำเร็จคือ Sam Hinkle นักเคมีกับทีมเทคนิคของ Hershey ที่รวมพลังคิดค้นแท่งช็อกโกแลตที่ไม่ละลายง่าย เป็นช็อตโกแลตแท่ง 4 เหลี่ยมผืนผ้า มีรอยตัดแบ่งเป็น 6 ช่อง และมีความแข็งพอจะทุบเป็นอาวุธได้ ในปี 1937 Hershey’s Field Ration D จึงถือกำเนิดขึ้น เป็นแท่งช็อกโกแลตสีน้ำตาลเข้ม แข็งราวอิฐก่อสร้าง มีส่วนผสมของ ช็อกโกแลต
น้ำตาล นมผงพร่องมันเนย ไขมันโกโก้ แป้งโอ้ต เจือกลิ่นสังเคราะห์ และวิตามิน B1 (เพื่อลดภาวะเหน็บชา)กินแล้วได้พลังทันที แต่ไม่อร่อยพอให้หยิบบ่อย และนี่คือสิ่งที่รัฐบาลสหรัฐฯ ต้องการพอดี ในสงครามโลกครั้งที่ 2 ช็อกโกแลตแท่ง Field Ration D กลายเป็นไอเท็มพื้นฐานใน “emergency kit” ของทหารอเมริกันทุกคน โดยเฉพาะในแนวหน้า ไม่ว่าจะเป็นสนามรบในยุโรปหรือในแปซิฟิก
มีข้อมูลบอกว่า จากส่วนผสมของมันที่เน้นด้วย ไขมันและแป้งข้าวโอ๊ต ทำให้ส่วนผสมนั้นข้นหนืดมากจนไม่สามารถใช้กระบวนการผลิตตามปกติของโรงงาน Hershey ในการบรรจุลงแม่พิมพ์ได้ ดังนั้น จึงต้องใช้แรงงานคนในการบรรจุส่วนผสมลงในแม่พิมพ์ขนาด 4 ออนซ์ด้วยมือแทน
เมื่อผลิตส่งไปทัพหน้าแล้วก็มีการค้นพบว่า ยิ่งเวลาผ่านไปมันจะยิ่งแข็งขึ้นไปมากกว่าตอนผลิตเสียอีก ดังนั้นถ้านับจากวันผลิตและกว่าจะขนส่งไปถึงทหารแนวหน้าจริงๆ อาจกินเวลาเป็นปีๆได้ นั่นคือมันจะแข็งอย่างกะก้อนหิน ต้องเอามีดมาหั่นเป็นชิ้นเล็กๆ ถึงจะเคี้ยวได้ และถ้าเอาไปต้มในน้ำเดือดก็จะได้เครื่องดื่มช็อคโกแลตร้อนแทน
แต่กระนั้นในช่วงสงคราม Hershey ก็ผลิต D Bar มากกว่า 3 พันล้านแท่ง และนี่ไม่ใช่ของฟรี บริษัทได้รับสัญญารัฐบาลและการสนับสนุนการผลิตเต็มรูปแบบ
และในปี 1943 Hershey ได้รับรางวัล Army-Navy ‘E’ Award ซึ่งเป็นรางวัลแห่งความยอดเยี่ยมด้านการผลิตยุทโธปกรณ์ ทั้งที่ผลิต “ขนม” แต่ถูกนับว่าเป็นอาวุธทางพลังงาน
เมื่อสงครามจบ ของดี(ของผู้ผลิต)จะทิ้งก็เสียดาย
Hershey และรัฐบาลสหรัฐฯ รู้ดีว่ากำลังการผลิตระดับนี้จะไม่สามารถคงอยู่ได้หากไม่มี “ตลาดรอง” จึงเริ่มเปลี่ยนภาพจำ “Field Ration D” ที่เคยเป็นของแข็งไร้รสชาติ ให้กลายเป็น “ช็อกโกแลตแห่งชัยชนะ” (Victory Chocolate) ทีมการตลาดของ Hershey จึงค่อยๆ ขยับสูตรให้กินง่ายขึ้น เพิ่มโกโก้ เพิ่มความหวาน ลดความแข็ง แล้วเปลี่ยนชื่อสู่แบรนด์พลเรือน เช่น Hershey’s Tropical Bar และต่อมากลายเป็นไอเดียให้แบรนด์ต่างๆ ทำแท่งพลังงานที่อิงโมเดลเดียวกัน หนึ่งในนั้นคือ PowerBar ที่เปิดตัวในยุค 1980 และอ้างอิงถึง “nutritional science” ที่ได้แรงบันดาลใจจากทหาร
เบื้องหลังของความอร่อย คือกลยุทธ์ที่หวานอมขมกลืน Hershey’s Field Ration D คือภาพสะท้อนของแนวคิด “การระดมอุตสาหกรรมเอกชนเพื่อรัฐ” ที่เกิดขึ้นในสงครามโลกอย่างแท้จริง บริษัทเอกชนที่มีศักยภาพถูก “จูงมือ” เข้าสู่ระบบยุทโธปกรณ์ภายใต้ข้ออ้างเรื่อง “ชาติ” และเมื่อชนะสงคราม ก็หันกลับมาครองตลาดพลเรือนด้วยต้นทุนและกำลังผลิตที่ไม่มีใครเทียบได้ ดังนั้น สิ่งที่เริ่มต้นด้วยความหวังดีอย่าง “อยากให้ทหารมีแรง” จึงกลายเป็นต้นแบบของแนวคิดการตลาด “อาหารคือพลัง อาหารคืออาวุธ และอาหารคือธุรกิจที่รัฐสนับสนุน”
Field Ration D ไม่ใช่แค่ช็อกโกแลตแท่ง แต่มันคือสิ่งที่เปลี่ยนวิธีที่โลกมองอาหารแบบพร้อมกิน (ready-to-eat) และกลายเป็นรากฐานของ “Functional Snack” ที่สร้างพฤติกรรมการกินแบบนี้และครองตลาดทั่วโลกในปัจจุบัน โดยมีฉากหลังเป็นทั้งสงคราม การเมือง และการตลาดแบบอเมริกันสไตล์ มันคือจุดเริ่มต้นของยุคสมัยที่มีการเข้ามาควบคุมพฤติกรรมการกินอย่างเป็นระบบ กลไกนี้ได้ขยายไปสู่การพัฒนา power bar หรือ energy bar ที่เราเห็นในตลาดปัจจุบัน มักใช้ผงพืช ผงถั่ว หรือสารสกัดต่างๆ มาขึ้นรูปเป็นแท่ง และถูกโฆษณาว่าเป็น “อาหารดีต่อสุขภาพ” แบบสำเร็จรูป ซึ่งในความเป็นจริงนี่คือกลยุทธ์ที่อยู่เบื้องหลังการกลืนกินพฤติกรรมการบริโภคอาหารแบบใหม่ ที่สร้างขึ้นโดยวงการ future food เพื่อควบคุมและกำหนดรูปแบบการกินทั่วโลก
การเปลี่ยนอาหารให้กลายเป็นสิ่งที่ง่าย สะดวก และพร้อมบริโภคตลอดเวลานั้น ส่งผลให้ผู้คนหันไปพึ่งพาอาหารแปรรูปเหล่านี้มากขึ้น และนี่คือการ “เข้าควบคุมอาหารโลก” ในแบบที่ซ่อนเร้น ผ่านการสร้าง superfood สำเร็จรูป ที่ถูกออกแบบมาให้ตอบโจทย์ตลาด ไม่ใช่ธรรมชาติของมนุษย์อย่างแท้จริง การเข้าใจเบื้องหลังเหล่านี้ช่วยให้เราระวังตัวและตั้งคำถามกับอาหารที่เรากินในทุกๆ มื้อ ว่าจริงๆ แล้ว เรากำลังถูกเลือกหรือควบคุมโดยใครกันแน่
ใครควบคุมอาหาร… คนนั้นคุมเกม #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-19 01:26:41
@ 5d4b6c8d:8a1c1ee3
2025-06-19 01:26:41Yesterday's regiment did the trick and I am now recovered from illness. I assume I caught whatever @grayruby had, after spending hours recording together.
Today, I got back on the OMAD train, but otherwise I still need to get back on track tomorrow, especially with the Sound HSA step challenge starting tomorrow.
Did you achieve your ~HealthAndFitness goals today, stackers?
https://stacker.news/items/1009821
-
 @ eb0157af:77ab6c55
2025-06-18 05:01:12
@ eb0157af:77ab6c55
2025-06-18 05:01:12The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ 52524fbb:ae4025dc
2025-06-19 01:21:43
@ 52524fbb:ae4025dc
2025-06-19 01:21:43USD/CHF currency pair showcases Swiss Franc a currency frequently lumped together with Japanese Yen as traditional safe haven asset class. Switzerland's rock-solid fiscal stewardship and beefy financial sector have long rendered "Swissie" highly sought after by jittery investors worldwide. Relying solely on its safe-haven status overlooks a crucial dynamic namely proactive intervention policies of Swiss National Bank and broader European stability. Switzerland's status as safe haven comes with caveat notably during risk-off periods such as financial crises and heightened geopolitical tensions surrounding small export-oriented economy. A ridiculously robust Franc makes Swiss goods ridiculously pricey for foreign buyers directly harming Switzerlands vital export sector potentially precipitating nasty deflationary pressures. SNB has quite a lengthy history of meddling in foreign exchange markets and curbing excessive CHF appreciation pretty vigorously overseas.
Such interventions manifest diversely including outright forex transactions undertaken pretty swiftly or imposition of rather negative interest rates. SNB actions or strongly worded verbal warnings can rapidly flip trends in USD/CHF creating sudden sharp volatility overnight with surprising ferocity. Dramatic unpegging of CHF from Euro in 2015 sent shockwaves through Forex market highlighting SNB's willingness to take drastic protective measures. Traders must stay vigilant for signals from SNB regarding its comfort level with Franc's burgeoning strength quite rapidly every day. Stability of Eurozone profoundly impacts USD/CHF pair beyond direct intervention occasionally with significant effects on currency markets daily. Switzerland's geographical positioning fosters deep economic ties with Eurozone nations which account for much Swiss trade sparking a flight to safety into CHF whenever major EU economic upheaval occurs. Periods of robust Eurozone expansion and unruffled politics can erode demand for Franc as safe haven potentially allowing USD/CHF currency pair to surge upwards. EUR/CHF frequently behaves as harbinger of USD/CHF movements despite being distinct currency pair altogether often unexpectedly.
Traders navigating USD/CHF currency pair require a complex analysis deeply rooted in SNB monitoring pretty closely for policy shifts and interventions. Keep an eye on key economic indicators and political developments within Eurozone as these can trigger safe-haven flows into CHF suddenly. USD/CHF combines allure of Swiss Franc with active management by SNB and susceptibility to economic fortunes of larger European neighbors essentially. Traders face a mercurial environment utterly dependent on grasping central bank machinations and regional upheaval alongside prevailing market mood swings rather tenuously.
-
 @ eb0157af:77ab6c55
2025-06-18 01:02:02
@ eb0157af:77ab6c55
2025-06-18 01:02:02A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-19 01:16:04
@ 5d4b6c8d:8a1c1ee3
2025-06-19 01:16:04At @Scoresby's request, this is a summary of the different places to engage in sports betting degeneracy with your bitcoin.
Predyx
Starting with ~Stacker_Sports' favorite, Predyx is a lightning only prediction market, where you can buy and sell shares directly with your own wallet. Despite still being in beta, they're already the most fun betting site and they offer better odds (i.e. lower spreads) than the regular sportsbooks discussed below. We also have access to one of the founders, @mega_dreamer, and devs, @emre, right here on Stacker News. They also took over ~oracle from @ek. These are our people.
The focus is more on longer term and more noteworthy outcomes (not exclusively sports), so they don't have the full offerings of parlays and moneylines and so forth that you might be looking for. However, the real-time odds adjustments as other participants buy and sell presents great opportunities to capitalize on price movements.
BetPlay
BetPlay is a traditional online sportsbook that allows lightning deposits and (I think) bitcoin denominated bets. They also accept various shitcoins, including fiat, and report all values in fiat terms, which is frustrating when you're trying to make a specific sats valued bet. The latter is useful for arbitraging odds mismatches with Predyx or Ember.
Also, my favorite thing about BetPlay is that you can watch live feeds of just about every sporting event in the whole world. It's amazing.
Ember
This one is fun, but comes with a major caveat emptor. Ember is a mobile app (referral code MNGKHFGBTRM) that streams sats to you at a fairly slow rate when you login. With those sats you can bet on upcoming sportsball matches from several different sports. While games are in progress, keep track of the odds over at BetPlay, just in case there are opportunities for arbitrage that you want to take advantage of.
The warning is that we've experienced inexplicable losses of sats from our balances and had difficulty withdrawing, so I strongly recommend against buying sats from them to increase your balance. Just play with the free sats and have some fun microbetting. I think Ember is supposed to have lightning withdrawals, but I have yet to be eligible for a withdrawal.
Freebitcoin
OGs remember freebitcoin as a faucet that used to give away ludicrous amounts of bitcoin, but they offer a seemingly random smattering of sports betting options too. The biggest downsides are being on-chain only (with a withdrawal fee) and the limited offerings.
What I most enjoy about Freebitcoin is that they have an unusual betting model and actually offer better-than-fair odds to early bettors. The rub is that when you place an early wager you have no idea what the odds will end up being, because it's a betting pool that divvies up the pot proportionally to those who picked the winner (usually). They have gotten outcomes wrong and never corrected their mistake.
I've described my approach thoroughly in RBOA: Risk Balanced Odds Arbitrage, but it's basically to bet early on all the outcomes and make a small not-quite-guaranteed return.
You can also check the odds right before a match begins to take advantage of mismatches with either BetPlay or Predyx.
Nitro Betting
Nitro Betting is very similar to BetPlay, but is on-chain. My cursory comparisons of odds on the two sites indicate that Nitro might have slightly lower spreads than BetPlay. However, I don't know if that compensates for on-chain fees for deposits. They also have higher minimum bets and a minimum withdrawal threshold. They do, however, express bets in bitcoin terms (rather than fiat), which is nice.
What are your favorites, stackers?
Are there any I missed?
https://stacker.news/items/1009810
-
 @ cee287bb:ffb55547
2025-06-19 02:20:37
@ cee287bb:ffb55547
2025-06-19 02:20:37Introducción a ¿qué carajo es Nostr?
Por sus siglas traducidas: Notas y otras cosas transmitidas por relays, Nostr no es más que un sencillo protocolo de comunicación capaz de generar los cimientos para la próxima revolución social.
Protocolos: Arquitectura
Para poder entender Nostr tendremos que hacer una comparativa de los elementos mas importantes dentro de los protocolos que más utilizamos (o espero que usen 😏).

¿Qué es un relay de Nostr? Un relay es un servidor, alojado por ti o por otra persona que cualquiera puede montar y/o gestionar. Existen relays públicos y de pago. A su vez, un relay funciona como base de datos en la cual guardan y reenvían notas.
Los relays usan el protocolo de websocket (wss://...) para conectarse con los clientes. Esto genera una comunicación asíncrona y canales de comunicación bidireccionales que se mantienen abiertos.
Un relay es “tonto”. Tanto la firma como la creación de las notas sucede de lado del cliente.
¿Qué es un cliente de Nostr? Un cliente de Nostr es una aplicación diseñada para interactuar con el protocolo de Nostr. Podés conectarte a un cliente mediante web, mobile, clientes de escritorios, etc.
Debido a que Nostr es un protocolo abierto, los clientes buscan ser lo mas interoperables posibles. Prueba algunos!
Web:
Primal.net
Zapcito.app
Androd:
Amethyst
Nostros
iOS:
Damus
¿Qué es un evento de Nostr? Los eventos, o también denominado notas, son toda interacción que genere el usuario del lado del cliente. Todo evento es enviado a los relays que el usuario tenga conectado.
Los eventos a nivel protocolo están construidos en formato JSON, un lenguaje utilizado para el manejo de estructuras de datos a nivel API. Además, tienen una estructura particular que determina el tipo de evento que se esta intentando transmitir.
Estructura de un evento Debido a que estamos usando un protocolo primo hermano de Bitcoin, podemos encontrar que la estructura de un evento es algo similar a una transacción:

id: identificador de 32 bytes con el que podremos identificar nuestras notas en otros relays. created_at: fecha de creación en formato unix. tags: array de etiquetas, su formato depende de su categoría. pubkey: nuestra llave publica de 32 bytes en formato hex. sig: firma de 64 bytes. content: contenido arbitrario en formato string. kind: categoría en formato numérico.
Aplicaciones centralizadas

Si bien es lo que conocemos, y como hemos estado trabajando todo este tiempo. La realidad es que las aplicaciones centralizadas tienen 3 grandes problemas:
Hackeos: debido a que se centraliza la información en un único lugar, existe un solo vector de ataque y, en caso de conseguirse, podría interrumpir cualquier comunicación.
Políticas de uso: en base a lo anteriormente comentado, podemos dar por sentado que nuestras cuentas no son realmente nuestras. No podemos trasladar nuestros datos entre plataformas como Twitter a Instagram (por ejemplo). Debido a esto, estamos limitados por los términos y políticas de uso.
Censura de gobiernos: esta es una realidad a la cual no podemos escapar (hasta ahora). Noticias recientes como que Brazil suspende la red social X/Twitter o Maduro quiere regular Instagram y Tiktok en Venezuela hace que se intente censurar la opinion publica o plataformas de comunicación “libres”.
Pero si Nostr es primo hermano de Bitcoin, y Bitcoin nos trae la premisa de que busca separar dinero de estado quitando al mayor intermediario del medio, ¿por que nosotros no hacemos lo mismo?
¿Y si eliminamos los intermediarios? Para lograr esto necesitaríamos una forma de identificarnos dentro de nuestro protocolo descentralizado. Como en Bitcoin, esto lo podemos resolver con un par de llaves:
Llave publica: piensa en tu llave publica como el usuario de una red social. Es un identificador con el que otras personas van a poder encontrarte. Ambos formatos mostrados corresponden al usuario de quien esta escribiendo este post:
Hexadecimal: cee287bb0990a8ecbd1dee7ee7f938200908a5c8aa804b3bdeaed88effb55547
NPUB (Nostr Pub Key): npub1em3g0wcfjz5we0gaaelw07fcyqys3fwg42qykw774mvgala424rsl26ytm
Llave privada: piensa en tu llave privada como tu contraseña o tu semilla de Bitcoin. NO LA COMPARTAS CON NADIE. Una vez vulnerada, no hay vuelta atrás y tocará generar una nueva. Podemos encontrarlo en varios formatos:
Hexadecimal: 3b1b6e09236ab49050079fffced663a3b09d610a4c5beb895cda5c7f53f6d1f2
NSEC (Nostr Secret Key): nsec18vdkuzfrd26fq5q8nllua4nr5wcf6cg2f3d7hz2umfw875lk68eqms52y6
BIP39 (Semilla): early please toss later caught book raven attract attract flower outside scene sponsor arena exotic convince rely cattle fortune scrub cluster tape shop horror
Algunas consideraciones:
Podés generar la cantidad de llaves que desees, son “infinitas”.
No se necesita internet para generar un par de llaves.
Utiliza gestores de claves como: GetAlby o Nos2x
Profesionales de UX: Si bien el formato hexadecimal es el más primitivo, la realidad es que para una rápida diferenciacion mostrarlo en formato npub y nsec.
NIP Los NIPs, o “Posibles implementaciones en Nostr”, definen la estructura de los eventos o notas. Entre ellos podemos encontrar algunas implementaciones de todo sistema social:
NIP-01: Protocolo básico de publicación y perfil
NIP-02: Lista de seguidores
NIP-05: Identificadores basados en DNS (ej: satoshi@bitcoin.org)
NIP-17: Mensajes privados
Ejemplos de uso: En base a ejemplo de aplicaciones sociales, ¿cómo podríamos utilizar estos NIP?
Twitter.com
NIP-02 - Lista de seguidores
NIP-18 - Republicar contenido
NIP-25 - Reacciones
Telegram.org NIP-17 - Mensajes privados NIP-29 - Grupo de mensajes
Cafecito.app NIP-57 - Pagos Lightning NIP-75 - Objetivos de pagos
LaWallet.io NIP-26 - Eventos delegados
Entonces, ¿por qué Web 5? Porque en lo que va del articulo no hemos hablado de crypto, blockchain o token. Únicamente de datos, datos que son resilientes, incensurables, transparentes y libre.
Debido a que estamos hablando a nivel protocolo, existen diferentes tipos de implementaciones. No aprendas un nuevo lenguaje para empezar a construir, utiliza el que ya conoces!
-
 @ b9ff7cb5:a0e092a8
2025-06-18 09:41:48
@ b9ff7cb5:a0e092a8
2025-06-18 09:41:48Bismillah
The internet has no instruction manual. Anyone can post freely, which means unwanted spam can flood your replies, feed, and notifications. New domains call for new practice, and joining a paid relay is one way you can protect yourself against nostr spam. As a relay is also community focused, it aims to be a way for those new to nostr to find fitra and ummah in cyber-space, thereby building and joining patterns of higher-purpose.
NoorNode is a nostr relay dedicated for muslims on nostr. It is maintained and moderated by the Pnostr:npub1vmgf2pzv8k3fsch2hvc5uqnp9kvrxwrfgucek95528zax3syfwtqhykxpn team, which is a podcast incubator project for the creation of Islamic media on nostr.
The Noor Node relay is free to read. All content posted to the relay is public. However, one must pay to join the relay in order to post content to it. This payment feature is small but necessary proof-of-work barrier to keep bots and spam out.
How To Join:
If you simply want to read notes on NoorNode, just add
wss://noornode.nostr1.comto your read/inbox relays in your client settings.To join NoorNode and post notes to the relay, visit the RelayTool explorer page at https://noornode.nostr1.com
Click on the gear button to show options and it will reveal a side pannel where you can submit your payment.
Enter your nostr public address (npub) into the text box and select the
Lightning Pay ✅ ⚡button for it to generate an invoice QR code.Once payment has been received a lightning bolt will animate across the screen and you will be able to post to the NoorNode relay.
Client Relay Cofigurations:
The RelayTool explorer is a very basic client which can be used to post to NoorNode, but for best user experience other clients will be preferable. So long as NoorNode set as a write/outbox relay in a client's settings, any client should work. That said, clients where you can customize the relay feeds are preferable. Of these, Yakihonne is the one we recommend due to it's support for both mobile (Andriod & iOS) and desktop.
To create a custom feed for NoorNode in Yakihonne from the desktop home page, select the gear button in the Note feed dropdown menu.

A widget will then pop up where NoorNode can be added as a custom relay feed. Enter
wss://noornode.nostr1.comand hit the+button and then select theUpdatebottom to save the custom feed.
The NoorNode relay can then be viewed as a seperate feed from Yakihonne's home page by selecting it from the note feed dropdown menu (scroll to the bottom to find it).
Other clients, like Jumble, can also funtion as great ways to test out customized relay feeds. As nostr continues to grow, it is expected that more clients will include this feature.
To learn more about relays and how they work on nostr, check out this guide from the developer of Amethyst
The intention behind NoorNode is for muslims on nostr to have a safe place to build community while not having to worry about issues like spam or religious intolerance. The payment to post is designed to enough to keep most bots out while also not being a significant barrier for anyone who want to enage. The mission of nostr:npub1vmgf2pzv8k3fsch2hvc5uqnp9kvrxwrfgucek95528zax3syfwtqhykxpn is to create new Islamicate mythos. We hope that the community that grows around NoorNode will embody that same goal and that the Noor of Islam will be able to radiate, even from nostr.
Please keep in mind that NoorNode is a public relay and notes posted can be picked up by others relays. If any content found on the relay does not seem appropriate or if any issues occure that cause concern, please reach out to the PodSystems team for support.
May the peace and blessings of the most merciful God be with you and light your way on nostr.
-
 @ 472f440f:5669301e
2025-06-18 04:25:57
@ 472f440f:5669301e
2025-06-18 04:25:57Marty's Bent
via Dr. Eli David
The case for a neutral, permissionless monetary protocol has never been stronger. The incumbent financial system is a permissioned wall garden that is susceptible to a tax. When you're using this system, you don't own your money. Your money doesn't really even exist. What you have is a claim to be able to ask your bank to give you your money or move it somewhere that you desire. Not only is it a permissioned wall garden, but it is an insecure permissioned wall garden that is susceptible to attacks from nefarious actors.
This was made very clear earlier today when Sepah Bank in Iran was the subject of a cyber attack that led to all of its databases being erased and their ATMs being deemed non-functional. Sepah Bank customers have been unable to withdraw cash. And many are warning Iranian citizens to withdraw as much cash as possible from any ATM outside of Sepah Bank's network that is working. Because there is a high likelihood that other banks and ATM networks will be targeted.
Bitcoin is a digital bearer instrument that you can custody yourself using either a software or hardware wallet. The network is operated by an army of geographically distributed nodes that maintain the rules and ensure that anybody trying to transact within the network is doing so within the rules that are set forth. Bitcoin is a push system, not a pull system. It is extremely hard to attack in the way that Sepah Bank was attacked earlier today.
I think it's important to note the way in which Sepah Bank was attacked and highlight that it is starkly different from the types of attacks or shortcomings from the financial system that we've seen over the years.
One of the events that caused a rush to Bitcoin over a decade ago was the banking crisis in Cyprus. We've seen hyperinflationary events in countries like Lebanon and Turkey that have rendered their currencies defunct. In the case of Lebanon, the central bank simply came out and said that people were not going to have access to their money and gave Lebanese citizens an overnight haircut on their savings. We've seen countries like India and Nigeria mess with their physical bills, forcing their citizens to exchange smaller denominations for larger denominations, causing massive disruptions in the process.
We've seen the United States government and its allies freeze the treasury assets of its enemies and they move towards a more multipolar monetary order over the last five years. We've seen the Canadian government freeze the bank accounts of protesters fighting for bodily autonomy. We've seen Operation Chokepoint 1.0 and 2.0. Here in the United States, the government directly targeted industries and businesses within those industries by either overtly preventing them from accessing bank accounts or covertly making it as hard as possible to access bank accounts.
On top of all this, obviously, we have the constant drumbeat of currency debasement across the world, even here in the United States, where the Federal Reserve and Federal Government are expanding the monetary base and going further into debt, ultimately destroying the purchasing power of the dollar at an increasing rate over time.
However, this type of cyber attack on a bank is unique, at least from what I can recall. The ability of nefarious actors to access bank databases and erase them is something new and something that should not be taken lightly. If Iranian hacking capabilities are as sufficient and capable as we are led to believe, it's not hard to imagine that we could see some retaliatory actions from the Iranian regime to counteract the attack on their banking system.
I don't want to incite alarm in any of you, but I think it is important to highlight that this new attack vector is definitely a step towards financial nihilism that could put hundreds of millions, if not billions of people in harm's way, in the sense that they could wake up one morning and be told that the bank does not have access to the records of their cuck buck IOUs. If something like this were to happen, I'm sure anyone who isn't holding Bitcoin in a wallet that they control will really wish they were. Being able to access your money is a vital part of being able to live you life. The thought of that ability being taken away because of a hacking war that breaks out is extremely unnerving.
As I said at the top of this letter, the case for a neutral, permissionless, distributed monetary system with a native currency that is finite is clearer than it ever has been, at least for me. It is imperative that you and anyone that you care about holds Bitcoin in self-custody to inoculate yourselves from these very real risks that are only going to increase from here on out.
Eliminate the trusted third party risks that exist in your life. Use Bitcoin as your money and use it correctly by holding it in self-custody.
Why 5% Interest Rates Won't Trigger The Next Market Crash
Guest Mel Mattison challenges the prevailing fear around rising interest rates, arguing that markets have developed immunity to higher yields. Unlike 2023's sharp selloff when the 10-year hit 5%, Mattison believes equities and Bitcoin can now absorb these levels because they signal stronger growth expectations ahead. He emphasizes that the pace of rate increases matters more than absolute levels, and notes that markets have had time to adjust. With oil trading at just $65 per barrel—a fraction of its inflation-adjusted 2008 peak of over $200—the deflationary pressure from cheap energy provides a crucial buffer.
> "It's not just what the rate we get to, it's how fast we get there." - Mel Mattison
Mattison's most compelling argument centers on AI-driven productivity gains enabling companies to maintain margins despite higher borrowing costs. As I've witnessed firsthand implementing AI tools at TFTC, what once required hiring multiple employees can now be handled by one person with the right automation. This productivity revolution means traditional rate sensitivity models may no longer apply.
Check out the full podcast here for more on institutional Bitcoin adoption, resistance money warnings, and bipartisan coalition building.
Headlines of the Day
Davis Commodities Puts 40% of $30M Into Bitcoin - via X
Ukraine Bill Adds Bitcoin to National Reserves - via X
Vinanz Raises £3.58M to Expand Bitcoin Mining - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The joy of a 5-year old riding a bike for the first time is something that should be protected at all costs.
*Download our free browser extension, Opportunity Cost: *<https://www.opportunitycost.app/> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ eb0157af:77ab6c55
2025-06-18 00:02:25
@ eb0157af:77ab6c55
2025-06-18 00:02:25The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-19 01:01:21
@ eb0157af:77ab6c55
2025-06-19 01:01:21The Thai government has eliminated taxes on gains from cryptocurrencies until 2029 to attract investors and promote the digital asset sector.
According to Efinance Thai, Thailand has approved a five-year tax exemption on profits from the sale of Bitcoin and other digital assets. The decision aims to position the country as one of the world’s leading digital financial hubs.
On June 17, Thailand’s Cabinet officially approved the tax measure proposed by the Ministry of Finance. The initiative removes personal income tax on capital gains from the sale of cryptocurrencies conducted through licensed operators under the 2018 Digital Asset Business Act.
Deputy Finance Minister Julapun Amornvivat stated that the tax policy is a cornerstone of the government’s strategy to turn Thailand into a major global center for Bitcoin and blockchain-based financial services.
The capital gains tax exemption will be in effect from January 1, 2025, to December 31, 2029. It applies exclusively to transactions carried out via exchanges, brokers, and dealers licensed and regulated by Thailand’s Securities and Exchange Commission (SEC).
Thai authorities estimate that this tax reform will boost the domestic Bitcoin market, generating positive spillovers for the country’s innovative tech ecosystem. Economic projections indicate a medium-term increase in tax revenues of at least 1 billion baht (around $30 million), driven by sector growth and fresh investment inflows.
According to the government, the initiative is also expected to encourage capital raising through digital tokens and foster the development of blockchain-based financial services.
The post Thailand abolishes taxes on Bitcoin: five-year tax exemption appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-06-18 04:02:01
@ 9ca447d2:fbf5a36d
2025-06-18 04:02:01Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ eb0157af:77ab6c55
2025-06-18 03:01:36
@ eb0157af:77ab6c55
2025-06-18 03:01:36A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-18 00:02:24
@ eb0157af:77ab6c55
2025-06-18 00:02:24A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-06-19 01:01:00
@ 9ca447d2:fbf5a36d
2025-06-19 01:01:00Zurich, 18th June — Relai has always been committed to offering the simplest and most intuitive way to buy bitcoin and hold the coins in a self-custodial manner.
From their 0% fee auto-invest plan up to 100 CHF/EUR per month, to their fast buy flow for one-time purchases.
That commitment is evident in the ever-growing user base, with over 500,000 app downloads, more than 85,000 active users, and a total user investment exceeding $1 billion. Relai users are enthusiastic about the brand and eager to use it to acquire generational wealth.
However, although owning bitcoin in a self-custodial manner is excellent, one must also think about the long-term security and protection of that wealth. By having bitcoin in a self-custody setup, one is already doing a great job; however, a better alternative is available: multisig.
This is why Relai is excited to announce its partnership with Casa, offering a simple and intuitive way to keep your hard-earned wealth in a safe setup.
For Relai users, particularly those with larger holdings or long-term goals, Casa is the ideal next step. Relai helps you stack; Casa enables you to secure. Adem Bilican, Co-Founder and CTO of Relai said:
“Self-custody is at the heart of Bitcoin’s promise. As our users continue to accumulate and grow their holdings over time, we recognize the need for long-term solutions designed for serious Bitcoin enthusiasts.
“Casa is the ideal partner – a sovereignty-focused and user-friendly solution. Together, we’re helping users secure not just their savings, but their legacy.”
Nick Neuman, CEO of Casa, stated:
“Casa’s mission is to maximize sovereignty and security in the world. The best way we can do that today is by making sovereign bitcoin custody as safe and simple as possible. Our partnership with Relai will help people stack bitcoin and store it securely, for themselves and their families.”
With this partnership, both companies will offer a first-of-its-kind model for everyday users to acquire bitcoin and keep it secure for generations to come, either by maintaining it in a multisig setup or by taking it a step further and also including inheritance plans for next of kin.
Press Contacts:
Joël Kai Lenz, Head of Communications
Email: joel@relai.appAbout Relai
Relai is a Swiss startup founded in 2020 in Zurich by Julian Liniger and Adem Bilican. Their Bitcoin-only app is designed to be simple and intuitive, allowing anyone to buy and sell Bitcoin within minutes. Relai stands out in the crowded cryptocurrency market with its unique approach to self-custody. Unlike other platforms, Relai does not hold user funds; instead, it empowers users to control their financial futures with an easy-to-use self-custodial wallet. Relai is a Swiss-licensed financial service provider with $1 billion in trading volume. In 2024, Relai was named one of the fastest-growing startups in Europe, and the company is regularly listed among the top 50 Swiss startups. Learn more at relai.app.
-
 @ 31a4605e:cf043959
2025-06-17 18:02:14
@ 31a4605e:cf043959
2025-06-17 18:02:14A história do Bitcoin é pontuada por marcos simbólicos que representam não apenas a evolução técnica da moeda digital, mas também sua trajetória rumo à legitimidade econômica e política. Neste artigo, revisitamos alguns dos momentos mais emblemáticos que marcaram a adoção do Bitcoin, desde seu uso inicial em uma simples transação até o seu reconhecimento como moeda oficial por nações soberanas.
A pizza mais cara da história
Em 22 de maio de 2010, Laszlo Hanyecz fez história ao pagar 10.000 BTC por duas pizzas. Na época, essa quantia equivalia a cerca de 40 dólares. Hoje, essas mesmas moedas valeriam centenas de milhões de dólares, tornando essa a refeição mais cara já registrada. Mais do que uma curiosidade, essa transação marcou a primeira vez em que o Bitcoin foi usado em uma troca comercial real, comprovando seu potencial como meio de pagamento.
Silk Road e o lado obscuro da adoção inicial
Ainda que controverso, o uso do Bitcoin no marketplace Silk Road mostrou ao mundo que a moeda digital era funcional como meio de troca em larga escala. A plataforma operou entre 2011 e 2013 e foi um catalisador para o desenvolvimento de infraestrutura em torno do BTC, apesar dos impactos negativos na imagem da criptomoeda.
Mt. Gox e a primeira grande crise
Em 2014, a corretora Mt. Gox, responsável por cerca de 70% das transações de Bitcoin no mundo, declarou falência após perder cerca de 850 mil BTC. O escândalo abalou a confiança no ecossistema, mas também deu início a um movimento de amadurecimento: a busca por melhores práticas de segurança, regulação e profissionalização do setor.
El Salvador e o reconhecimento oficial
Em setembro de 2021, El Salvador tornou-se o primeiro país a reconhecer o Bitcoin como moeda de curso legal. A medida, defendida pelo presidente Nayib Bukele, foi recebida com entusiasmo por entusiastas e com ceticismo por instituições financeiras internacionais. O experimento salvadorenho colocou o Bitcoin no centro do debate geopolítico e abriu precedentes para outras nações considerarem o mesmo caminho.
Resumindo, cada um desses momentos representa uma etapa distinta na evolução do Bitcoin: da experimentação à adoção institucional. Ao revisitarmos esses casos emblemáticos, conseguimos entender não apenas como o Bitcoin evoluiu tecnicamente, mas também como sua narrativa se consolidou como parte da história financeira contemporânea. Se a compra da pizza simbolizou o nascimento prático do BTC, o reconhecimento oficial por nações inteiras sugere um futuro em que a moeda digital pode ser protagonista em novas formas de organização econômica global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ d9a329af:bef580d7
2025-06-19 00:42:31
@ d9a329af:bef580d7
2025-06-19 00:42:31Note: All biblical references use the 1599 Geneva Bible. No other version is used unless specified to be either Young's Literal Translation or a modern-day spelling Wycliffe for clarification.\ \ Shabbat Shalom again.\ \ This time around, I want to cover the lunisolar calendar, and how this affects the days one is supposed to work. Most Christians are fooled by the idea of a repeating 6 day/1 day cycle, which actually comes from Constantine in the 4th century AD. This is what the Roman Catholic Church enforces when it comes to the calendar, which is a solar-only calendar intead of a different one.
The Lunisolar Calendar
The lunisloar calendar is a 29.5 day cycle (some months being 29 days, the others being 30), and has four rest days, which are the 8th, 15th, 22nd, and 29th of the month. These are classified as your Sabbaths (Shabbatot in the Hebrew). There's way more to this, but I will provide my thoughts on it, and why I posted something asking people not to zap it last week. Most references piggyback off of the work of David Nikao Wilcoxson, who studied this in depth for a long time.\ \ The basic idea of this calendar is that it's one that was practiced for at least 3,000 years. This calendar in particular was the exact calendar we were taught in the Scriptures, which Catholic leadership and Jesuits don't want us to understand. More on that later. For now, though, let us take a look into how a day is supposed to be structured, as follows.
The Daylight Cycle
The day starts at sunrise, and not sunset like how the Jesuits wanted it. It was always the former, as the term boqer (Strongs H1242) is the morning; whereas yom (Strongs H3117) means day, laylah (Strongs H3915) is night and ereb (Strongs H6153) is evening. Genesis 1 makes the assertion of how a day is structured, as follows in Verse 5:\ \ "And God called the Light, Day (Yom), and the darkenes, he called Night (Laylah). So the evening (Ereb) and the morning (Boqer) were the first day."\ \ Think about this for a second. Does it clearly state that a day starts at sunset, and end at a different sunset? This certainly can't match the natural order of things. However, the only sunset to sunset in the Scriptures is the Day of Attonement (Yom Kippurim), which starts at sunset the day prior, and ends at sunset the day of.\ \ Beside that, Genesis 1:5 clearly talks about the day starting just when the sun rises, as creation was done during the daytime, and not during the evening (as that was a rest). This is what's classified as a full day. This is why you'd observe a Shabbat (a lunisolar Shabbat for me, as I had described) during the daytime, and not during the night, for that doesn't make any sense in the grand scheme of things.\ \ To see when a day ends, let us take a look at Exodus 12:5,6 in order to know exactly when a day ends, as follows:\ \ "Your lamb shall be without blemish, a male of a year old: ye shall take it of the lambs, or of the kids. And ye shall keep it untill the fourteenth day of this month: then all the multitude of the Congregation of Israel shall kill it at even"\ \ This clearly talks about when the lamb is to be killed during passover. Keep in mind that animal sacrifices are not necessary after 31 AD due to the death of Messiah as the sacrificial lamb (This was on March 13th of that year). It's during the night (laylah), which falls between dusk (ereb) and dawn (boqer).\ \ Exodus 12:7-10 dictate that the lamb was to be eaten on the Passover, the 14th day of Nisan, before the next morning (the Shabbat on the 15th day of the month). It was eaten or burned.\ \ https://thescripturalcalendar.com/saturday-is-not-the-scriptural-sabbath-day/This particular study has more information on this matter, as it's too much for me to cover here. Let me move on.
Why Saturday and Sunday are Not the Weekly Shabbat
The home page of Wilcoxson's site for this calendar proves why a repeating 6 work day/1 Sabbath cycle is completely fraudulent. Let me get into that a bit with how the Shabbat works.\ \ Many people who came out of Romanism believe that Scripture mandates a repeating cycle of 6 work days and 1 rest day, though Seventh Day Adventists will proclaim that Sunday Shabbat is the Mark of the Beast (wholly unproven, by the way). I was SDA for a while, but thought it was much more insidious than that, surely.\ \ When Messiah carried out his ministry, there was an 8-day calendar the Romans were using at the time, so no 7-day week. Saturday wasn't even a thing at all, even. That said, Constantine would move the Shabbat to the 7th day (which is Saturday) in the 4th century, as mentioned, where he thought to change the times and the seasons. Antichrist Beast Pope Gregory XIII would reform it once again to his calendar, reflecting the solar cycle accurately, dropping 10 days from the calendar.\ \ This current 7th day is offset by three, causing the theory of 6 work days/1 rest day to be completely broken down. This clearly shows that Saturday was not always the 7th day of the Roman calendar.\ \ All of this is to say that a Scriptual Shabbat cannot be every 7 days, and this solar cycle is interrupted with a New Moon (Rosh Chodesh) at the head of the month, which is commanded. That is what invalidates the Roman solar calendar's importance in determining the Shabbat. This study proves that big time.
Conclusion
This is a relatively new deal for me, and I've been doing it for a few months at this point. I've been much better with it, and understanding the calendar more than even my elders (and they're supposed to know the truth... but I guess the Jesuits got them down bad for taking the Mark of the Beast by revering [forehead] and obeying [right hand] the Pope). Then again, I'm still learning this, and hopefully, this starts you testing what I've said against the Scriptures.\ \ Shalom.
-
 @ 52524fbb:ae4025dc
2025-06-19 00:57:04
@ 52524fbb:ae4025dc
2025-06-19 00:57:04USD/CAD currency pair nicknamed Loonie after Canada's one-dollar coin featuring a loon is exceptionally sensitive to crude oil price fluctuations nowadays. Canada's economic fortunes are deeply intertwined with global energy markets being one of world's largest oil producers and primary supplier of energy. USD/CAD pair exemplifies petro-currency behavior driven heavily by hydrocarbon market dynamics offering singularly unique trading opportunities quite frequently nowadays. Canada exports crude oil mostly sending copious production Stateside. Canada's export revenues surge rapidly when oil prices skyrocket thereby enhancing its terms of trade and bolstering current account balance quite positively. Foreign currency influx naturally bolsters Canadian Dollar value so it takes fewer loonies to purchase one greenback thereby lowering USD/CAD exchange rate. A drop in crude oil prices severely dents Canada's energy sector and reduces export earnings thereby weakening Canadian Dollar so USD/CAD rises sharply.
The correlation between crude oil (especially West Texas Intermediate, WTI, given its close ties to North American production) and USD/CAD is often inverse and remarkably strong. Traders frequently use oil price charts as a leading indicator for the Loonie. A rally in WTI futures, driven by supply concerns or robust global demand, will typically see USD/CAD move lower, while a sell-off in oil can trigger a sharp move higher in the pair. Oil prices sway Canadian economic vitality pretty significantly beyond direct export revenue effects. Canada's GDP gets a sizable boost from energy sector activity alongside substantial employment opportunities and hefty investment pouring in. Sustained high oil prices fuel hefty capital expenditure in oil sands and various energy projects thereby boosting economic activity briskly. Conversely low oil prices can precipitate job losses and markedly reduced investment thereby slowing economic growth which weighs heavily on Canadian Dollar.Crude oil prices are considered by Bank of Canada when formulating monetary policy alongside other pertinent economic indicators quite regularly. Oil prices greatly impact economic growth and inflationary pressures so they remain a crucial factor in BoC's assessment of economy. Rising oil prices expected soon might fuel inflation domestically so BoC may be more inclined and raise interest rates further supporting CAD. Falling oil prices could threaten economic outlook prompting BoC to adopt dovish stance potentially leading to rate cuts fairly quickly afterwards.
Traders navigating USD/CAD successfully must integrate energy market analysis into strategy therefore leveraging market fluctuations very carefully nowadays. Monitoring entails scrutinizing global oil supply and demand fluctuations influenced by OPEC+ production quotas geopolitical disruptions and hazy global economic forecasts. Weekly data releases on US crude oil stockpiles trigger sharp reactions in oil prices and USD/CAD currency pair instantly. Oil remains a dominant factor yet presence of other significant elements isn't entirely precluded obviously in many naturally occurring situations. USD/CAD exchange rates fluctuate maniacally under pressure from Federal Reserve policy and sundry influential monetary factors alongside US economic indicators. Hawkish Fed statements nowadays substantially bolster US Dollar and exert upward pressure on that currency pair pretty frequently overseas. Broad risk sentiment sways things fabulously in pro-cyclical environments and CAD performs remarkably well amidst surging global risk appetite.
-
 @ 52524fbb:ae4025dc
2025-06-19 00:31:21
@ 52524fbb:ae4025dc
2025-06-19 00:31:21AUD/USD currency pair often nicknamed Aussie occupies a singular spot heavily in Forex market dynamics globally every day. Its value fluctuates wildly with global commodity prices especially industrial metals like iron ore and coal that dominate Australian exports heavily nowadays. Aussie currency acts as barometer for global economic growth and health of Chinese economy making it compelling yet cyclical pair to trade frequently.
Australia's economy relies heavily on export of abundant natural resources found within its borders quite significantly every year. Iron ore and coal and liquefied natural gas LNG contribute substantially to Australia's export earnings mostly every year quite handsomely. Prices surge upward rapidly during spells of frenzied global economic activity and heightened industrial output fueling demand for such commodities greatly. Higher export revenues accrue from this for Australia thereby improving terms of trade and strengthening Australian Dollar significantly overseas.
AUDUSD and commodity prices especially industrial metals often correlate strikingly high. Traders keenly watch commodity indices and individual prices of key Australian exports like iron ore futures as leading indicators for AUD. Iron ore prices surge rapidly bolstering AUD strength as market participants eagerly anticipate hefty foreign currency inflows flooding Australia very quickly.
Trading AUD/USD effectively demands a rather complex and deeply nuanced approach obviously from traders with experience. Diligent monitoring of major commodity prices and acute awareness of Chinese economic trends alongside sensitivity to global risk appetite are required. A highly responsive barometer of global growth story the Aussie offers clear cyclical trading opportunities for those interpreting interconnected dynamics effectively.
-
 @ eb0157af:77ab6c55
2025-06-18 00:02:31
@ eb0157af:77ab6c55
2025-06-18 00:02:31Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:55:10
@ 4ba8e86d:89d32de4
2025-06-17 17:55:10DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ eb0157af:77ab6c55
2025-06-18 01:02:03
@ eb0157af:77ab6c55
2025-06-18 01:02:03The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ b7274d28:c99628cb
2025-06-18 00:01:01
@ b7274d28:c99628cb
2025-06-18 00:01:01Tired of dealing with spam? You're not alone. Here is a guide to picking relays that are good at keeping spam out, without sacrificing your own reach.
If you just want to skip to the relay suggestions, scroll to the sections titled "The Setup." There is one for users of Haven and one for those who aren't running their own relay at all.
Client Selection
"Wait, I thought this was a guide about selecting relays, not clients."
Yes, it is. But what relays you choose doesn't matter if you are using a client that does not read from your chosen relays, or that hard-codes problematic relays as fallbacks in addition to the relays you selected in an effort to "help you."
Additionally, some clients have settings that can help make up for poor relay selection using client-side spam mitigation methods. This includes clients like Coracle, Damus, Amethyst, and Nostur. Some may do so via web-of-trust (WoT) filters, so you only see notes and replies from those within your broader social circle, while others will automatically hide notes that those you follow have reported as spam or scams.
Coracle is a great client for dealing with spam, so long as you have gone into your "Content Settings" and set the "Minimum WoT Score" to at least 1. This means you will only see posts from users followed by at least one of the npubs you follow.
Damus also employs WoT, but it appears to be just for notifications, so you only receive notifications for those you follow and those they follow, or "friends of friends," as Damus put's it. This can be accessed by toggling it on in your notification tab at the top right, where you see the icon of the person with a check mark.
Nostur has WoT filters for downloading media turned on by default and also uses WoT to filter spam by default. Even better, if you use multiple npubs, you can filter using the WoT of your main npub, while logged into your alternate npubs.
Jumble recently added WoT filtering specifically for interactions. When you load a thread in Jumble, a shield icon will appear near the top right of the page, in line with the tabs for Replies and Quotes. Toggle it on, so the shield is green with a check mark and you will only see replies from those you follow and those your follows follow.
Amethyst does not yet have WoT based filtering built into the client, but it can hide notes that have been reported as spam, scams, impersonation, etc, by those you follow. This is not the most effective way to combat spam, though, since most users aren't often using the report feature. Hopefully we will see WoT filtering as an option in a future update.
Primal's apps do not read from any of your selected relays, but rather from their caching server alone. That said, they have a spam filter that is turned on by default so you see relatively little spam, regardless of which relays you use.
For this guide, I recommend using Amethyst for updating your relays, if you possibly can. The reason for this is because Amethyst has the most robust settings for being able to update all of your various relay lists.
Relay Lists Explained
Contrary to what you might think, there is not a single relay list for each user that is stored in a single note, because you can have relays that are used for only one purpose, and not for any other. Each of those purposes for which you might use a particular relay has its own list. That way a Nostr client can tell which relays you want to use for each separate purpose.
While this can make things less approachable for the user, it also means users don't have to rely on clients to hard code appropriate relays for each of these use-cases. If your client doesn't let you edit each of these relay lists, chances are they are using a set of relays for that purpose that the developer chose instead of you.
Public Outbox/Inbox Relays
This list of relays is found in your kind 10002 note, if you have one. If you don't have one, there won't be any relays shown for these categories in Amethyst. Other clients may fallback to showing you relays from a different list.
This list is intended to be used for Nostr clients to implement the "outbox model" to fetch notes from whatever relays they were written to, even if they aren't in the requesting user's relay list. This solves the issue of needing to share relays with those you follow in order to see their notes, allowing Nostr to remain decentralized.
Your "outbox" relays are the ones you write to, or at least the ones you want other users to know that you write to. When you add a relay here, it's like advertising to everyone, "If you want to see my public-facing notes, look for them on these relays."
Your "inbox" relays are the ones you read from. On this part of your list you are advertising, "If you want me to see your replies, comments, reactions, and zaps, then send them to these relays." These relays are massively important for reducing the amount of spam you see. If you have relays listed here that anyone can post to for free, you will almost certainly see a lot of spam in your replies, unless you have WoT filters turned on in your Nostr client.
DM Inbox Relays
This list is found in your kind 10050 note, if you have one, and is a list of relays where you want others to send you Direct Messages. Ideally, you will use a relay or two here that supports AUTH, so that it will only allow direct messages to be retrieved by the user they are addressed to.
What happens if you put a relay in here that doesn't support AUTH, so it allows anyone to retrieve your DMs? Not much. Anyone who wants to will just be able to see the encrypted content of the message, and depending on the type of DM they will see the identity of the receiver and perhaps also the sender. They will not be able to decrypt what was actually said in the messages. It's better if they cannot retrieve even that much, though.
Private Relays
This list is found in your 10013 note, if you have one. This is intended for listing a relay that you run yourself and that only you can access, as it will house notes that other users should not be able to see at all, such as eCash tokens and draft notes.
Search Relays
This list is found in your 10007 note, if you have one, and is used to search for notes or users who may not be using the same relays as you. It is good to use relays here that aggregate notes from other relays automatically, and which support NIP-50 for search capability.
Local Relays
This section is for any relays running on the local device, such as Citrine. Because the relays themselves are local, this list is local, as well, and is not saved to any note kind that is saved to your relays like the above lists.
General Relays
This list is found in the "content" tag of your kind 3 note, which is also where all of the npubs you follow are stored. As such, this note is commonly known as your follow list, rather than as a relay list. However, some clients, such as Amethyst, do make use of this list, and others use it as a fallback if they can't find a kind 10002.
If you are an Amethyst user most of the time, then I would recommend using this list to fill in any gaps that you may have from only writing to a few outbox relays, or only reading from a few inbox relays. It's a good place to put an aggregator relay, for instance, so long as that relay has good spam filtering, or a blastr relay, so those who don't yet use a client that supports the outbox model will still likely see your notes.
If you do not generally use Amethyst, then I would recommend you mirror your public inbox/outbox relays here, in case you use a client that cannot find your 10002 list. Relays that are only for outbox should be added as write only, those only for inbox should be added as read only, and those you use for both outbox and inbox should be both read and write.
The Setup (Haven Users)
If you are running your own set of Haven relays, here is the setup I would recommend:
Public Outbox (kind 10002)
Maximum of 4 relays.
- Your Haven outbox relay (Remember to add some public relays to your blastr)
- A paid relay of your choice (List available in "Paid Relays" section)
- A public relay, such as relay.damus.io, relay.primal.net, or nos.lol
Public Inbox (kind 10002)
Maximum of 4 relays.
- Your Haven inbox relay: [RelayAddress]/inbox
- A paid relay of your choice (can be same as outbox)
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- Your Haven "chat" relay: [RelayAddress]/chat
- An alternate AUTH relay, such as inbox.nostr.wine(paid), nostr.land(paid), or auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- Your Haven private relay: [RelayAddress]/private
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required) and/or wss://nostr.wine(paid for write, but can read for free).
The Setup (Not Running Haven)
If you are not running your own set of Haven relays, I would highly recommend you learn how and do so. However, if you decide against it, here is a setup that should suffice:
Public Outbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (List available in "Paid Relays" section)
- A large public relay, such as relay.damus.io, relay.primal.net, or nos.lol
- An additional public relay, but a smaller one, or one-time-payment paid relay.
Public Inbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (can be same as outbox)
- wss://nostr.wine - Even if you don't pay for it, you can read from it.
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- A paid AUTH relay, such as inbox.nostr.wine or nostr.land.
- An alternate AUTH relay, such as auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- A private relay you run on your Umbrel or Start9, or that is hosted for you on relay.tools.
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required).
- A blastr relay, such as filter.nostr.wine(paid), or...
- A few additional public relays set to write only.
Paid Relays
There are a ton of other paid relays out there that can be found via nostr.watch. The above listed options are simply the most popular with the largest feature-sets.
WoT Relays
These relays will only accept notes from npubs that are within the relay owner's WoT. I have provided a Jumble.social address for each relay so you can peruse the feed for yourself to see if you want to use it.
- wss://wot.utxo.one - Jumble Feed
- wss://nostrelites.org - Jumble Feed
- wss://wot.nostr.party - Jumble Feed
- wss://wot.sovbit.host - Jumble Feed
- wss://wot.girino.org - Jumble Feed
- wss://relay.lnau.net - Jumble Feed
- wss://wot.siamstr.com - Jumble Feed
- wss://relay.lexingtonbitcoin.org - Jumble Feed
- wss://wot.azzamo.net - Jumble Feed
- wss://wot.swarmstr.com - Jumble Feed
- wss://zap.watch - Jumble Feed
- wss://satsage.xyz - Jumble Feed
- wss://wons.calva.dev - Jumble Feed
- wss://wot.zacoos.com - Jumble Feed
- wss://wot.shaving.kiwi - Jumble Feed
- wss://wot.tealeaf.dev - Jumble Feed
- wss://wot.nostr.net - Jumble Feed
- wss://relay.goodmorningbitcoin.com - Jumble Feed
- wss://wot.sudocarlos.com - Jumble Feed
-
 @ 52524fbb:ae4025dc
2025-06-19 00:21:49
@ 52524fbb:ae4025dc
2025-06-19 00:21:49GBP/USD currency pair affectionately known as Cable has long been swayed by economic vitality of UK and US financial conditions simultaneously. Dynamics of this pair have shifted pretty fundamentally since 2016 Brexit referendum. GBP/USD trades against a backdrop of profound structural economic changes in UK and persistent political headwinds making it a challenging yet lucrative pair for Forex traders now.
Political headwinds in UK continue driving significant volatility in GBP/USD exchange rates beyond mere economic indicators. Rapid shifts in governmental leadership and murky implementation surrounding protocol for Northern Ireland or fresh trade policy spats quickly undermine investor confidence. Perception of risk can lead to massive capital outflows and a precipitously weaker Pound as political stability characterizing UK wavers somewhat now. Markets react swiftly to headlines suggesting political upheaval or egregious policy blunders often precipitating flash crashes or rapid currency depreciations.
Merely comparing US economic indicators and UK monetary policy or central bank pronouncements in isolation no longer cuts it when trading GBP/USD heavily nowadays. Traders must now somehow integrate a fairly holistic understanding of post-Brexit economic landscape quite rapidly and effectively overseas. Analyzing true impact of new trade agreements and non-tariff barriers heavily influences UK exports and imports drastically every year overseas. Foreign direct investment flows into UK serve as a barometer of long-term confidence pretty steadily overseas.
Post-Brexit Cable pair embodies deeply ingrained systemic shifts and ongoing political turmoil that profoundly reshape behavior of a currency. Pound's trajectory now hinges precariously on UK's adaptation rather slowly to its newfound global standing alongside Fed policy influencing US Dollar side heavily. Navigating complex interplay of economic upheaval and dramatic politics offers substantially heightened risks and sizable opportunities for diligent traders very astutely.
-
 @ dfa02707:41ca50e3
2025-06-18 23:02:15
@ dfa02707:41ca50e3
2025-06-18 23:02:15- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.
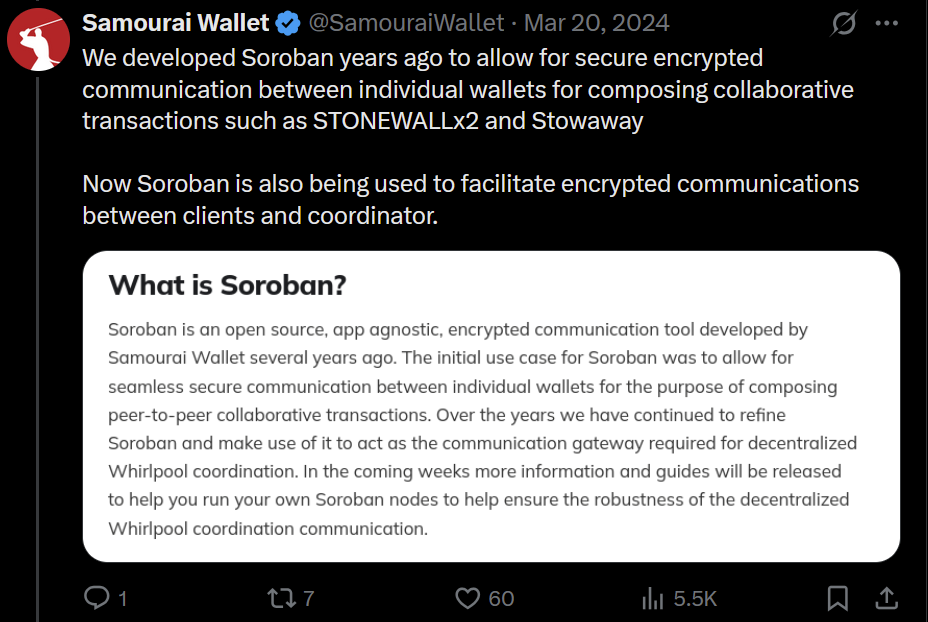

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 31a4605e:cf043959
2025-06-17 17:35:10
@ 31a4605e:cf043959
2025-06-17 17:35:10Desde a sua criação em 2008, Bitcoin tem sido visto como um desafio direto ao sistema bancário tradicional. Desenvolvido como uma alternativa descentralizada ao dinheiro fiduciário, Bitcoin oferece uma forma de armazenar e transferir valor sem depender de bancos, governos ou outras instituições financeiras. Essa característica faz com que seja considerado um símbolo de resistência contra um sistema financeiro que, ao longo do tempo, tem sido marcado por crises, manipulações e restrições impostas aos cidadãos.
Crise financeira de 2008 e o nascimento de Bitcoin
Bitcoin surgiu em resposta à crise financeira de 2008, um colapso que revelou as falhas do sistema bancário global. Bancos centrais imprimiram grandes quantidades de dinheiro para resgatar instituições financeiras irresponsáveis, enquanto milhões de pessoas perderam as suas casas, poupanças e empregos. Nesse contexto, Bitcoin foi criado como um sistema financeiro alternativo, onde não existe uma entidade central com o poder de manipular a economia em benefício próprio.
No primeiro bloco da blockchain ou timechain de Bitcoin, Satoshi Nakamoto incluiu a seguinte mensagem:
"The Times 03/Jan/2009 Chancellor on brink of second bailout for banks."
Essa frase, retirada de uma manchete de jornal da época, simboliza a intenção de Bitcoin de oferecer um sistema financeiro fora do controlo dos bancos e dos governos.
Principais razões pelas quais Bitcoin resiste ao sistema bancário
Descentralização: Ao contrário do dinheiro emitido por bancos centrais, Bitcoin não pode ser criado ou controlado por nenhuma entidade específica. A rede de utilizadores valida as transações de forma transparente e independente.
Oferta limitada: Enquanto os bancos centrais podem imprimir dinheiro sem limites, causando inflação e desvalorização da moeda, Bitcoin tem uma oferta fixa de 21 milhões de unidades, tornando-o resistente à depreciação artificial.
Impossibilidade de censura: Bancos podem bloquear contas e impedir transações a qualquer momento. Com Bitcoin, qualquer pessoa pode enviar e receber fundos sem pedir permissão a terceiros.
Autocustódia: Em vez de confiar os seus fundos a um banco, os utilizadores de Bitcoin podem armazenar as suas próprias moedas, sem risco de congelamento de contas ou falências bancárias.
Conflito entre bancos e Bitcoin
Ataques mediáticos: Grandes instituições financeiras frequentemente classificam Bitcoin como arriscado, volátil ou inútil, tentando desincentivar a sua adoção.
Regulação e repressão: Alguns governos, influenciados pelo setor bancário, têm criado restrições ao uso de Bitcoin, dificultando a sua compra e venda.
Criação de alternativas centralizadas: Muitos bancos centrais estão a desenvolver moedas digitais (CBDCs) que mantêm o controlo do dinheiro digital, mas sem oferecer a liberdade e a descentralização de Bitcoin.
Resumindo, o Bitcoin não é apenas uma moeda digital, mas um movimento de resistência contra um sistema financeiro que falhou repetidamente em proteger o cidadão comum. Ao oferecer uma alternativa descentralizada, transparente e resistente à censura, Bitcoin representa a liberdade financeira e desafia o monopólio dos bancos sobre o dinheiro. Enquanto o sistema bancário tradicional continuar a impor restrições e a controlar o fluxo de capital, Bitcoin permanecerá como um símbolo de independência e soberania financeira.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:49:18
@ 4ba8e86d:89d32de4
2025-06-17 17:49:18Ele é uma espécie de ponte do Tor que permite que os usuários se conectem à rede Tor por meio de um sistema distribuído de voluntários.
A história do Snowflake começou em 2019, quando o Tor Project percebeu que muitas pessoas em locais com restrições de acesso à Internet estavam recorrendo a soluções de VPN e proxies para contornar a censura. No entanto, muitas dessas soluções eram bloqueadas pelas autoridades governamentais, o que criou a necessidade de encontrar novas maneiras de contornar a censura. Foi aí que surgiu a ideia do Snowflake, que foi lançado como uma solução para ajudar a aumentar a capacidade do Tor de contornar a censura da Internet em todo o mundo.
O Snowflake funciona por meio de um sistema distribuído de voluntários que oferecem seus proxies para ajudar a contornar a censura. Quando um usuário se conecta ao Snowflake, seu tráfego é roteado por meio de um conjunto de proxies voluntários que se oferecem para ajudar a contornar a censura. Esses proxies são distribuídos em todo o mundo, o que ajuda a garantir que haja sempre uma opção disponível para os usuários que desejam acessar a Internet livremente.
O Snowflake resolve o problema de acesso à Internet em locais onde o acesso ao Tor é bloqueado. Ele permite que os usuários contornem a censura e a vigilância da Internet, acessando sites e aplicativos que seriam bloqueados em suas regiões. Com o Snowflake, os usuários podem navegar na Internet com mais privacidade e segurança, evitando serem detectados pelos censores da Internet.
"A privacidade é necessária para uma sociedade aberta na era eletrônica. Privacidade não é sigilo. Uma sociedade livre requer privacidade na comunicação, bem como privacidade na busca e na associação." - Eric Hughes
https://snowflake.torproject.org/
https://youtu.be/ZC6GXRJOWmo
-
 @ 9ca447d2:fbf5a36d
2025-06-18 23:01:55
@ 9ca447d2:fbf5a36d
2025-06-18 23:01:55Bitcoin Core Github page announced yesterday that Core Developers have merged pull request #32406, removing support for “-datacarrier” argument for Bitcoin Core software in their next release, expected to be published in October.
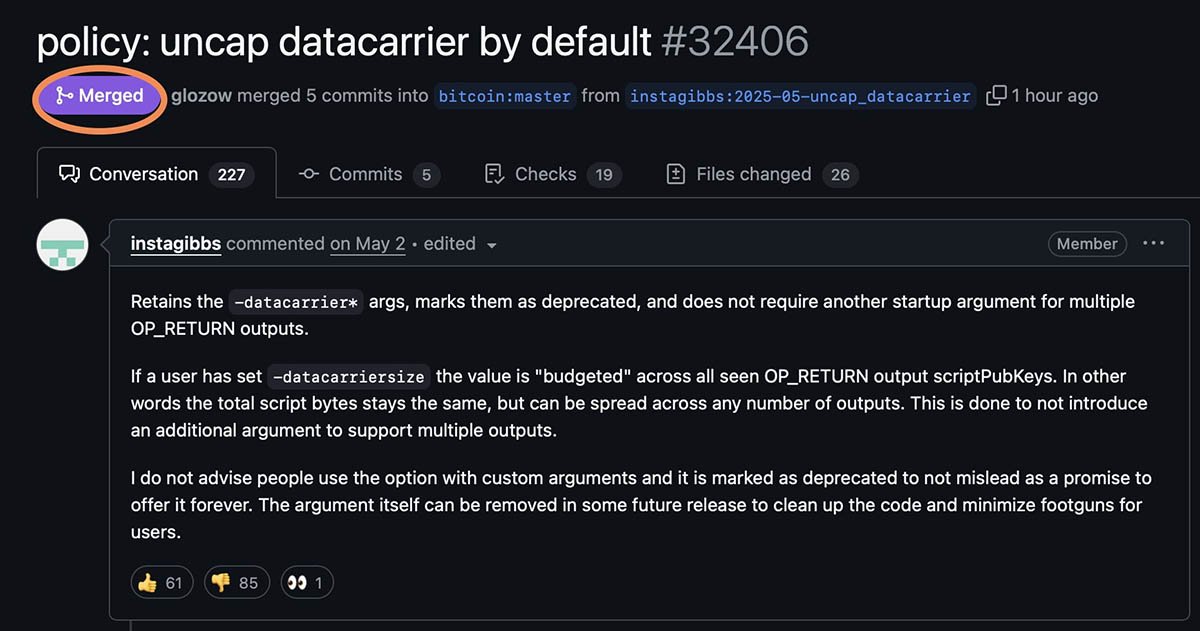
Pull request #32406 has been merged — Github
This is the latest development regarding the initiative brought forth by Bitcoin Core developer Peter Todd, which has caused intense debate among Bitcoiners, now known as the “spam wars”.
The disagreement is over a change to Bitcoin Core’s transaction relay policy that removes the OP_RETURN data limit, which some see as a threat to Bitcoin’s very purpose, while others see it as a necessary step to preserve decentralization and censorship resistance.
OP_RETURN is an arbitrary piece of data that can be amended to a bitcoin transaction, and used to be limited to 80 bytes. Users have found ways to go around this limit already and have uploaded larger data to the Bitcoin blockchain, including photos, audio, and even entire computer games.
Bitcoin Core allows for extra arguments when running the application, one of which is the “-datacarrier” argument, which tells the application to not accept transactions including larger OP_RETURN data into its mempool.
Now this argument is marked as “deprecated”, meaning it is not supported or developed anymore, and is expected to be completely removed in future versions.
This will make accepting Bitcoin transactions that contain non-financial data mandatory for anyone running future versions of the Core software.
Prior to the merging of the mentioned pull request on the morning of Monday June 9, a joint statement from 31 Bitcoin Core devs was released on June 6, reheating the already controversial debate in the Bitcoin community.
In the June 6 statement, Bitcoin Core devs explained how they think Bitcoin nodes should handle transactions that include non-financial data, like digital art or messages. This type of data has become more common with Ordinals and inscriptions.
Related: Discussions Heat Up Among Bitcoin Devs Over OP_RETURN Proposal
Core developers said they are not endorsing non-financial use of Bitcoin, but also won’t stop it. Their main point is that Bitcoin’s strength is in being open and censorship-resistant. They wrote:
“This is not endorsing or condoning non-financial data usage, but accepting that as a censorship-resistant system, Bitcoin can and will be used for use cases not everyone agrees on.”
They say it’s up to users and node operators to decide what kind of Bitcoin software they run. Bitcoin Core won’t block transactions that have economic demand and will be mined.
“Being free to run any software is the network’s primary safeguard against coercion,” the statement added.
The policy change goes back to a May 8th upgrade (announced by Core contributor and Engineer at Blockstream, Greg Sanders), where devs removed the long-standing 80-byte limit on OP_RETURN output size.
This limit was meant to discourage non-payment data usage, but devs say it no longer serves that purpose.
“Retiring a deterrent that no longer deters” makes sense, they argue, because people have already found ways to add large data to the blockchain.
They also point out that removing the cap may help miners and users more than it hurts. They claim the new approach helps predict which transactions will be mined, speeds up block propagation and helps miners find fee-paying transactions.
“Knowingly refusing to relay transactions that miners would include in blocks anyway forces users into alternate communication channels,” they explained, warning this could harm decentralization.
The response has been mixed.
The announcement of the merge received 64 upvotes and 93 downvotes from reviewers, showing the community is mostly against this action. Comments explaining their dissatisfaction with the merge also received the support of the majority.
Reviewers who voted ACK (acknowledgment and agreement) were downvoted, and the comments voting NACK (disagreement) received more upvotes.
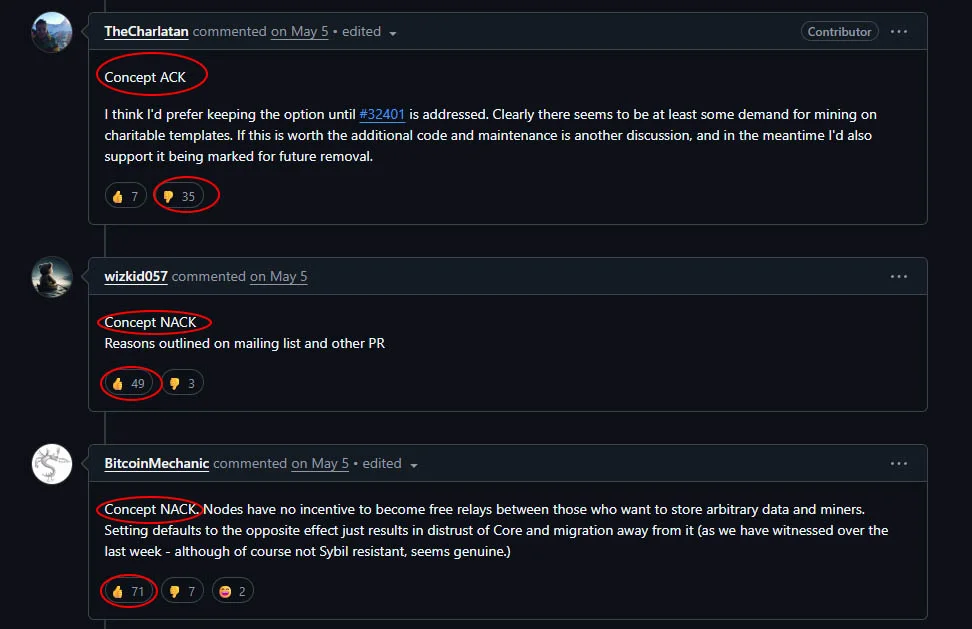
Comments regarding the recent merge — Bitcoin Core Github page
Critics say it opens the door to blockchain spam, higher fees and more bloat on the blockchain with non-financial content. They say Bitcoin should stick to its original purpose as a “peer-to-peer electronic cash system”.
Samson Mow, CEO of JAN3, was one of the most vocal critics. He said the devs are removing the barriers that protect the network from spam.
“Bitcoin Core devs have been changing the network gradually to enable spam,” Mow said. “It’s disingenuous to just say ‘It is what it is now, too bad’.”
Bitcoin dev Luke Dashjr also criticized the move, saying it undermines Bitcoin’s core function. He called the devs’ goals “basically all wrong” and said expecting spam to be mined is “defeatism”.
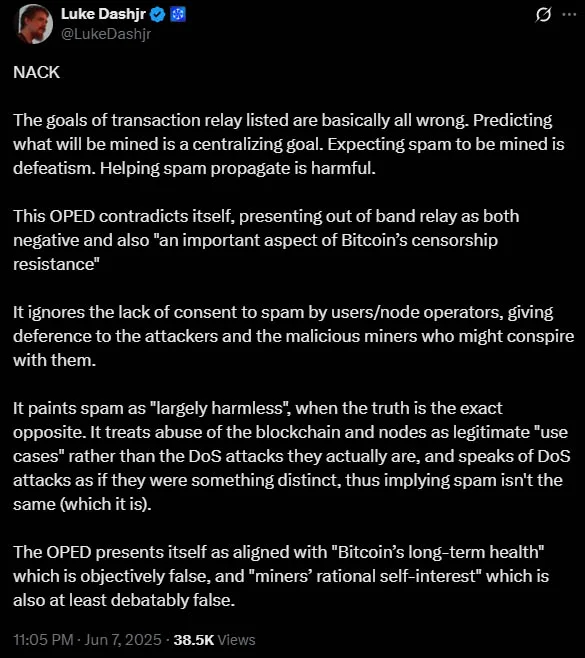
Luke Dashjr on X
One user said: “It’s Bit”Coin” not Bit”Bucket” or Bit”Store” or whatever general purpose data store you have in mind. It’s a peer to peer electronic cash system”.
Another user chimed in, warning it could increase costs, reduce efficiency and even hurt long-term scalability.
Their argument is simple: if nonfinancial data is allowed to be stored on the blockchain, it will increase its size over time, storing useless data, and it will hurt decentralization, as fewer individuals will be able to host the entire blockchain on their computers.
They argue allowing people to store whatever they want on the blockchain because transactions shouldn’t be censored, will lead to hurting bitcoin in the long run. Many even argue no additional information should be allowed on the blockchain at all.
But not everyone is unhappy.
Some like Jameson Lopp, co-founder of Bitcoin wallet provider Casa, praised the devs for being transparent and consistent.
“Core Devs are a group saying we can’t force anyone to run code they don’t like,” Lopp said. “Here is our thinking on relay policy and network health.”
Lopp believes a joint statement helps the public understand what the devs stand for.
Supporters also say in a truly decentralized system, devs shouldn’t be gatekeepers. Instead users and miners should be able to decide what goes on the blockchain.
With opinions so divided, the future of Bitcoin may be more contentious. Some predict a fork to create a version of Bitcoin that only deals with monetary use. Others expect new wallet and node software that lets users choose to filter out large data or allow it.
Despite the controversy, the devs are standing by their decision. “While we recognize that this view isn’t held universally,” they said. “it is our sincere belief that it is in the best interest of Bitcoin and its users.”
-
 @ b87245ac:158b965d
2025-06-18 22:23:16
@ b87245ac:158b965d
2025-06-18 22:23:16Requirements Summary
-
Problem Statement & Business Goals:
- Problem: Enable AI agents to retrieve specific Nostr events using their Bech32 pointers.
- Goal: Provide a reliable and efficient service for AI agents to fetch Nostr event data based on Bech32 identifiers.
-
Target Users & Key User Stories:
- Target User: AI Agents.
- User Story: An AI agent provides a Bech32-encoded Nostr event pointer (
nevent1...) to the MCP server and receives the corresponding Nostr event data.
-
Core Functional Scope (MVP):
- Accept a request containing a Bech32-encoded Nostr event pointer (e.g.,
nevent1...). - Retrieve the full Nostr event data corresponding to the provided pointer.
- Return the full Nostr event data.
- Input format: Bech32-encoded Nostr event pointer.
- Output format: Nostr event (presumably in its standard JSON format).
- Accept a request containing a Bech32-encoded Nostr event pointer (e.g.,
-
Nice-to-have Features / Future Phases:
- None specified, as the scope is strictly limited.
-
Data Flows & External Integrations:
- The server will need to interact with the Nostr network (relays) to retrieve the event data based on the Bech32 pointer. This implies a dependency on accessible Nostr relays.
-
Non-functional Needs:
- Performance: Needs to be reasonably fast in retrieving events, though specific latency requirements are not defined.
- Scalability: Should be able to handle multiple concurrent requests from AI agents.
- Availability: Should be available to AI agents when needed.
- Security: Needs to securely handle incoming requests and protect against potential abuse (e.g., rate limiting).
- Privacy/Compliance: No specific privacy or compliance requirements mentioned beyond standard data handling practices.
- Accessibility: Not applicable (server-to-server interaction).
- i18n: Not applicable.
-
Technical Constraints:
- Stack: Typescript, Bun.
-
Success Metrics & KPIs:
- Successfully processing requests for valid Bech32 pointers.
- Uptime and availability of the server.
- Latency of event retrieval.
-
Risks, Assumptions, Dependencies:
- Risks: Inability to connect to Nostr relays; invalid or malicious input from AI agents; performance bottlenecks with many requests.
- Assumptions: AI agents can provide valid Bech32 event pointers; Nostr relays are accessible and provide the requested data.
- Dependencies: Access to Nostr relays; Bun and Typescript environment.
-
Acceptance Criteria & “Definition of Done”:
- The server successfully receives a Bech32 event pointer.
- The server successfully connects to Nostr relays and retrieves the corresponding event.
- The server returns the correct Nostr event data in the expected format.
- The server is implemented using Typescript and Bun.
-
-
 @ 9ca447d2:fbf5a36d
2025-06-18 21:01:47
@ 9ca447d2:fbf5a36d
2025-06-18 21:01:47In a move that diverges from many other U.S. states, Connecticut has passed a new law that bars state and local governments from investing in bitcoin or any other digital currency.
The bill, HB7082, passed unanimously in both the House and Senate with zero opposing votes.
The law, officially titled “An Act Concerning the Regulation of Virtual Currency and State Investments,” was signed into law recently and is causing a stir in the Bitcoin and financial communities.
HB7082 prohibits the state of Connecticut and its political subdivisions from accepting, holding or investing in digital currencies. This includes bitcoin, ethereum and other digital assets. It also bars the state from creating a bitcoin reserve, a concept being explored by other states.
The law goes further by imposing strict rules on digital asset businesses operating in the state. These rules enforce anti-money laundering (AML) compliance and parental consent verification for digital asset users under 18.
It also requires 1:1 reserve requirements for bitcoin custodians.
Businesses that handle Bitcoin transactions must now provide users with clear information about risks and fees and provide receipts with full transaction details.
No business can let a minor use a money-sharing app without first getting proof of consent from a parent or guardian.
Lawmakers in Connecticut say it’s about protecting public funds and minimizing financial risk. They say Connecticut’s new law bars state investments in bitcoin to protect its financial assets from market risk.
Supporters argue that the high volatility of bitcoin makes it a risky investment for public money like pension funds and state reserves.
The law also looks to bring bitcoin businesses under tighter control, to make them follow the same rules as the traditional financial system.
While Connecticut is cracking down on digital assets, other states are going the other way.
States like Texas, New Hampshire and Arizona have already passed laws or proposed bills to create a bitcoin reserve, which allows public funds to be invested in bitcoin.
Texas has even described bitcoin as a “forward-thinking investment opportunity” and a long-term store of value.
The new law has caused mixed reactions in the financial world. Some think it’s too cautious, others think it’s part of a bigger plan.
Matt Hougan, CIO of Bitwise, responded with sarcasm, “The hedge fund managers got so upset they couldn’t beat Bitcoin…”
Matt Hougan on X
Some states like Florida, South Dakota and Oklahoma have either killed or vetoed Bitcoin bills this year. Others like Louisiana are still exploring the tech. Louisiana just announced it would create a special committee to study AI, blockchain and digital assets.
-
 @ f85b9c2c:d190bcff
2025-06-18 22:03:04
@ f85b9c2c:d190bcff
2025-06-18 22:03:04
You must have been hearing something like ‘coin’ and ‘token’ in the cryptocurrency space right? And you start wondering if they are the same thing. Yes they are similar but not the same.
A coin is any cryptocurrency that is fueling transactions on a native blockchain, it is also used to reward those who provide some kind of computational power to keep the blockchain alive. An example is PoW (Proof of Work) blockchains like Bitcoin. Ethereum is a coin on the Ethereum blockchain. XLM is a coin on the Lumen blockchain.
Now a token is any cryptocurrency that is created on a blockchain. Anyone who can create a smart contract can do this. I can deploy a token before I go to bed this night😃. It is that easy.
96% of cryptocurrencies that are in the market are tokens. You don’t need to build a blockchain to create a token but you must build a blockchain to have a coin.
I will give you a scenario you can relate to. ✔️Blockchain is like a hectare of land ✔️ Coin is the giant mansion or skyscraper on it ✔️Tokens are small rooms in the mansion.
I hope you gained something today as you are just getting familiar with the industry.
-
 @ 7ef5f1b1:0e0fcd27
2025-06-19 00:10:52
@ 7ef5f1b1:0e0fcd27
2025-06-19 00:10:52A Monthly Newsletter by The 256 Foundation
June 2025
 Opinions expressed do not necessarily reflect those of Proto Global, LLC
Opinions expressed do not necessarily reflect those of Proto Global, LLCIntroduction:
Welcome to the sixth newsletter produced by The 256 Foundation and supported by Proto! May was an eventful month for the Bitcoin mining industry with events ranging from the second 256 Foundation Telehash to the 2025 Bitcoin Conference in Las Vegas. There are several interesting things developing so dive in and catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice with OGBTC, and the current state of the Bitcoin network.
All the industry seems to be abuzz with the word “decentralization”. But you know this is a market top when the companies who have been building an empire on centralized services show up to the decentralization party and try to fit in. This is where words start to lose their meaning. Centralized pools will never decentralize Bitcoin mining full stop.

Definitions:
FinCEN = Financial Crimes Enforcement Network
UTXO = Unspent Transaction Output
Th/s = Terahash per second
Ph/s = Petahash per second
T = Trillion
ASIC = Application Specific Integrated Circuit
GUI = Graphical User Interface
FPPS = Full Pay Per Share
News:
May 5, big news broke in the Samourai Wallet case, the single most important issue looming over the future of Bitcoin and freedom tech development. In a Letter submitted to the court, defense counsel revealed that federal prosecutors had been suppressing exculpatory evidence for nearly year. Apparently, federal prosecutors approached the agency responsible for Money Services Businesses licensing requirements, FinCEN, and asked them for their opinion on whether or not Samourai Wallet would qualify as a Money Transmitter and be required to obtain a Money Transmitter’s License AND FINCEN EXPLICITLY REPLIED “NO”. There are multiple implications of this but to boil it down, this means there were no grounds for bringing the charges against Samourai Wallet in the first place and secondly that federal prosecutors were aware of evidence that pointed to their innocence and decided not to disclose it for almost a year.
May 9, but alas, the rogue federal prosecutors hell-bent on destroying any semblance of freedom-preserving technology responded to the defense counsel’s letter by minimizing their deceit stating that: “There is no basis for a hearing, nor is there anything to remedy…”. An unfortunate outcome considering this would have been the perfect opportunity for federal prosecutors to submit to the direct orders given by the US Department of Justice, Deputy Attorney General Todd Blanche, in the April 7 memo titled “Ending Regulation By Prosecution”.
May 14, Judge Berman, after reading both sides of the issue, decides to suggest that defense counsel raise this issue in the pretrial motion. Signaling that Judge Berman finds little to no issue with the prosecution’s behavior.
May 29, defense counsel submits a number of motions, including bringing up the prosecution’s failure to disclose exculpatory evidence again. Additional motions included things like bringing on an additional attorney from Washing DC, a motion for the defendants to have separate trials, and not least of all a compelling motion to dismiss the case. All signs point to this case going full steam ahead and your support is needed now more than ever, donate to their defense fund through p2prights.org.
May 19, backing up just a bit to capture other news, OrangeSurf published a UTXO Report, available here, which follows on the heels of the raging OP_RETURN debate that has engulfed the hearts and minds of Bitcoiners far and wide the last couple months. One of the concerns from the pro-filter camp is that the UTXO set will get bloated to the point that running a Bitcoin node on consumer hardware won’t be possible any longer. OrangeSurf reports that there are ~173 million UTXOs, half of them are less than 1,000 sats, and most of those are use Taproot. There are several charts and interesting facts in this report, take a look for yourself to see what really goes into the UTXO set.
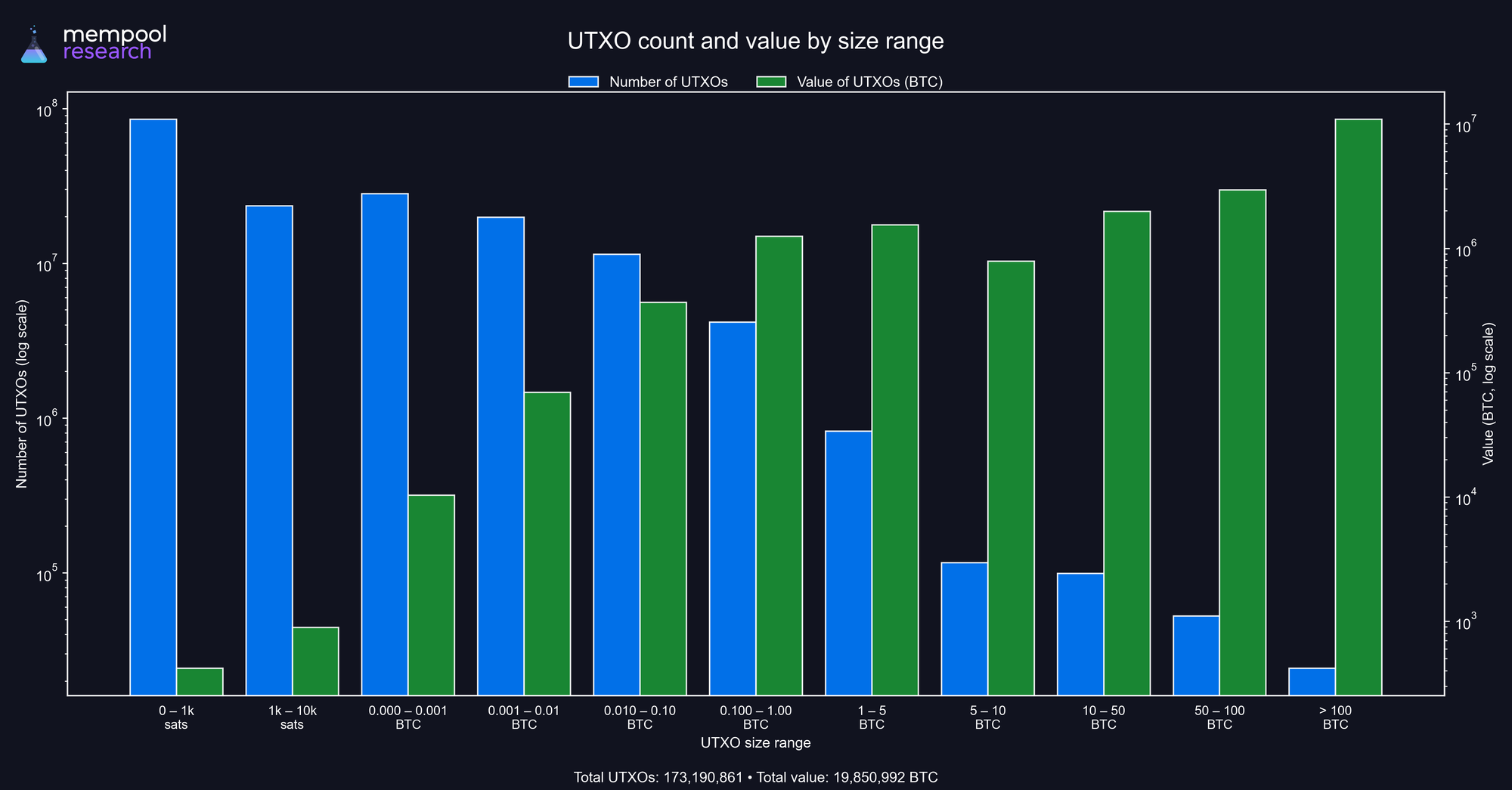
May 26, BitcoinVeterans holds a Telehash fundraiser seeking donated hashrate to increase their chance of finding a block to support their many great causes. This is an example of the Telehash idea spreading and enabling people to find new creative ways to incorporate Bitcoin into fundraisers.
May 27, centralized mining company, Bitmain, swoops in to decentralize Bitcoin mining! Leave it to Antpool, Bitmain’s mining pool, to jump on the “decentralization” corporate buzz word craze sweeping through the industry lately. At the “World Digital Mining Summit 2025”, which looks like it was a cringe Bitmain controlled side event in Las Vegas riding on the coat tails of the Bitcoin2025 conference, the CEO of Antpool apparently took the stage to unveil their new solution to save the Bitcoin network.
Following up the groundbreaking announcement with this tweet where Bitmain warns that 58% of hashrate is controlled by just two pools! Failing to mention that Antpool combined with their proxies accounts for roughly 40% of the overall network hashrate. The irony is palpable that Bitmain is saying Bitcoin mining needs a reset and Antpool will decentralize mining by giving miners the ability to make their own mining templates, while still maintaining FPPS payouts.
Let’s peel back the layers here and unpack this. FPPS gives miners steady rewards. Block finds on the other hand are variable. So how do pools pay miners a steady amount of Bitcoin when the rewards filling those coffers are not steady, you may ask. Great question! First of all, it takes a metric shit tonne of bitcoin on their balance sheet to offset the periods of time where the pool is experiencing bad luck and not finding any blocks. Read OrangeSurf’s Pool Survival Analysis for full details on the kinds of reserves needed to operate an FPPS pool.
What can pool operators do if they can’t afford the reserves needed? They ask Antpool to bankroll them in agreement to operate as a proxy pool. This is how Antpool absorbed Poolin, Braiins, Ultimus Pool, Binance Pool, SecPool, SigmaPool, Rawpool, Luxor, CloverPool (formerly BTC.com), and Mining Squared.
So what’s the big deal, you might be wondering, it sounds like miners get steady payouts and the pool operators have the cushion they need, where is the downside? Well there are a couple big problems driven by FPPS: One is custody and the other is templates, both lead to increased risk of censorship. The custodian can influence pool operators to behave in certain ways and the pool operator can dictate which transactions are in the templates that miners are hashing on. Another potential issue is increased risk of 51% attacks.
If Antpool is going to continue with the FPPS model then that means, like OCEAN, they will have control over coordinating the payouts but the rest of the transactions in the template can be chosen by the miner. Which brings us to the next layer here and the elephant in the room: is Bitcoin mining really getting decentralized by having miners build templates with a centralized pool?
Enabling miners to build their own templates is a great step in the right direction, don’t get me wrong. However, when there is still a centralized pool coordinating the payouts and counting the shares then the impact on centralization really doesn’t amount to much.
The idea is that a decentralized mining ecosystem would be more censorship resistant and vise versa as that ecosystem becomes more centralized, the more likely censorship attempts are to succeed. The issue is that while miners building their own templates is a good start, the pool operator can choose to or be coerced to enforce limits on which transactions are included in blocks. Such enforcement measures by the pool operator might look like excluding shares from certain users who have submitted work on a non-conforming template or excluding that user’s payout address.
While DATUM and SV2 are good steps toward decentralization, the marketing from companies like OCEAN and their employees/investors has exaggerated the impact of the solutions they have implemented. Suffice it to say that the Antpool announcement should be met with skepticism and centralized pools will never decentralize Bitcoin mining.
Free & Open Mining Industry Developments:
May 5, on Cinco De Mayo 256 Foundation held Telehash #2, the second hashrate-fueled fundraising event. Expectations were high as 256 Foundation descended upon Austin, TX at the former Bitcoin Commons (now the South Nashville Bitcoin Park campus). All of the grant recipients were there to represent their projects and talk about the whole free and open mining stack that 256 Foundation is building. The Telehash ran for 8-hours and a portion of that time featured a panel on the Ember One hashboard with Skot, a panel on the Libre Board with Schnitzel, a panel on Hydra Pool with Jungly, and a panel on Mujina Firmware with Ryan. There were other guests and topics as well throughout the evening. Shout out to The Space Denver for bringing dinner!
Public Pool also joined the effort by running a parallel instance that was mining to the same payout address with roughly 120 Ph/s. In total, at the peaks there were roughly 2,500 workers contributing roughly 245 Ph/s. The best difficulty was 43.5T, achieved by none other than Mega Watt, the same miner who found the golden nonce during Telehash #1.
However, despite all the effort and generous hashrate donations from supporters, unlike Telehash #1, no block was found by any of the miners and 256 Foundation did not raise any money during this fundraiser. The real reward was the frens we made along the way. The Telehash was live-streamed and that feed can be found here.
Grant Project Updates:
The next two days after Telehash #2 there was the TEMS event bringing together industry participants of all shapes and sizes with representatives from mining pools, mining companies, the energy sector, and more. There were several panels covering a wide range of Bitcoin mining related topics. One of the panels featured most of the 256 Foundation grant recipients to discuss a high-level overview of all the projects. That panel was recorded and can be found here.
OpenSats included the 256 Foundation in their eleventh wave of Bitcoin grants, which were announced on May 14. Even though 256 Foundation didn’t find a block at Telehash #2, OpenSats came through in a big way with a grant and generously supports our mission to dismantle the proprietary mining empire. OpenSats is a 501(c)(3) public charity which helps provide sustainable funding for free and open-source contributors working on freedom tech and projects that help bitcoin flourish. Some of the many projects OpenSats has supported in that past include: GrapheneOS, The Tor Project, Sparrow Wallet, SeedSigner, Stratum v2, and more. If you would like to support OpenSats, please do so here.
Additionally, HRF has continued their support of 256 Foundation with another grant for 2025, helping provide a generous portion of the funding needed to keep extending work on Ember One and more. HRF is a non-partisan, non-profit organization that promotes and protects human rights globally, with a focus on closed societies. HRF supports a wide range of programs such as the CCP Disruption Initiative, Combating Kleptocracy, and Impact Litigation to name a few. Within the Financial Freedom program at HRF is where you will find grants and financial support for software developers, entrepreneurs, and community builders tackling the most pressing issues facing activists, especially around financial surveillance, suppression, and control. This is where 256 Foundation fits in, because dismantling the proprietary mining empire unlocks innovations in Bitcoin mining that enable anyone to gain access to these emerging technologies. In addition to grants, there are a number of other initiatives within the Financial Freedom program like the Financial Freedom Report, the Finney Freedom Prize, and CBDC Tracker. Additionally, there are in-person events hosted throughout the year such as the Global Bitcoin Summit. You can support HRF and their many programs and initiatives here.
Ember One
There is not a whole lot to update on the Ember One project. The first release was published at the end of April, at the conclusion of the first grant cycle, and can be found here. There are a couple of modifications that are going to be made for v4 such as adding a reverse polarity protection circuit and another precautionary circuit that will help protect USB connected devices in the event of a spike in voltage. Once v4 is ready and released, there will be a small batch of Ember Ones produced specifically for testers and developers; more news on this to be announced. Otherwise, Ember One development with the Intel BZM2 chip will resume this fall, the exact timing is still to be determined.
Libre Board
Schnitzel wrote a great thread on the Libre board which can be found here. In it, he explains the reasoning behind building an open-source control board, why 256 Foundation decided not to use the recently open-sourced Braiins Control Board, and some of the applications that the Libre Board will unlock. Currently, considerations are being made for exactly which connectors will be included on the Libre Board, how many of each, and what their placement should be. So far, the list of connectors/buttons that will be included on the first Libre Board include:
• Power Button • Boot mode button • SD card slot • LED indicator • MIPI • HDMI • Ethernet • USB-C port x1 • 4-pin JST SH connector • 12-24v power input • USB-C data-only ports x 4 • Fan connectors for hashboards x4 • Raspberry Pi HAT • Two 100-pin Compute Module connectors • Battery • Control board fan • NVME SSD connectorMujina Firmware
Development on Mujina continues to progress, the ability for the firmware to deliver a work payload to the ASICs and get a response is working now; nearly completing one of four primary interfaces that the firmware must handle: delivering work to the ASICs and handling the responses being one, the API interface for things like a GUI being two, retrieving work from the pool and passing back shares being three, and reading on-board systems like temperature sensors being the fourth.
Hydra Pool
The first iteration of Hydra Pool was used for the Cinco De Mayo Telehash, a fork of CK Pool on the back end that used a modified version of the CK Stats interface for the front end. There were some lessons learned through this exercise and some issues with the back end resulted in the server being restarted approximately nine times during the first few hours of the Telehash before a correcting change was made and that particular issue was resolved.
As development continued after the Telehash, the decision was made to not use CK Pool as the code base for Hydra Pool. Both DATUM and Stratum v2 were examined as potential code bases to start with for the Stratum server however, after review the decision was made instead for Hydra Pool to now be a simple Stratum server built from the ground up in Rust. Going forward, this will be the foundation used to build the rest of Hydra Pool on top of. Most of this foundational stratum server is currently working and passing internal tests. Testing will be opened to the public soon and announcements along with instructions will be provided at that time.
Actionable Advice:
During TEMS, there was a panel titled: “Beating The Texas Heat” featuring mining pro Marshall Long, moderated by econoalchemist. The following is a transcript of that panel which is full of insight from Marshall gained over years of experience. If you prefer to watch the video of this panel, it can be found here.
eco: Marshall, I heard it gets hot in Texas...
Marshall ⁓ you know, we've got two seasons in Texas. We have first summer and we have second summer, so.
eco: All right. What are the most promising cooling technologies currently being deployed to handle Texas's extreme heat in mining operations?
Marshall: You know, a lot of people still run air mines here. The challenge is not only heat, but also, you know, the upkeep, the maintenance. You know, the guys at Riot do a great job but you know it's a tall order. You know, their new site is… There's a lot of immersion there and it's not necessarily just for cooling efficiency, but it also keeps the machines much cooler and cleaner.
So, you know, longevity of your machines is a big part because in some places in Texas, it's so humid that even if it gets dusty, you can get shorts. So like mining in Houston, pain in the neck just because it is so humid. So there's the heat, there's the humidity, there's dust. You know, a lot of these places are on job sites, construction sites. All that stuff is, you know, reason to seek alternative measures and then when people ask me well, do you want two-phase cooling? Do you want a regular single phase cooling? Do you want hydro? What's the kind of like, what's the take and I ask people: Where do you want your pain and when do you want it? You know, if you want to do hydro your pain is gonna be upfront because it's expensive and the setup is not trivial. It's a little bit different than normal setups. It's gonna cost you a lot but, you know, you're gonna eat it all up front.
Immersion, single phase immersion is a little bit of a longer process. It's less expensive. There's other reasons why you might wanna do it. You can use off the shelf air miners that you retrofit. You know, it's only been very recent that OEMs have been making immersion specific machines. ⁓ And then, know, air you can, it's easy to start, but to keep it going, you're gonna get your pain on the back end forever.
So you just got to pick your poison and where you want to deal with it. Have you taken any operations that were like air and then decided to upgrade them to like hydro or immersion or? Yeah, sure. So that's a bit of an easier task. Doing it the other way, much bigger pain in the neck. You got to take apart the machines and do all these kinds of stuff. I mean, if you want to hear, you know, terror and war stories, I mean, you know.
Mr. Schatz and I could sit around a ⁓ fireplace for many hours and cry many tears about how that works. So it's better you make your choice the right first time and then you never have to make it again. And then just stick with it.
eco: How do air-cooled and liquid-cooled or hydro-cooled, for that matter, systems - how do they compare in performance, cost, long-term reliability ⁓ specific to the Texas climate?
Marshall: Yeah, sure. So the hydro is just kind of like a newer thing. So it's a bit harder to say long term how that shakes out. It's gotten better. You know, the difficulties there are, you know, if you have to take those machines out, you know, those can be 80 pounds a piece. So it's really hard on the ops guys, ops guys and gals to do that stuff. I mean, it's it's backbreaking to the stores, especially if they go out or they have power supply problems, you know, water and electronics doesn't really mix that well. So there's other additional safety concerns there.
However, you get a benefit if you want to use the heat for other things. like where this beer is made, we have a hydro set up and off the manifold, we preheat the water using the hydro set up. And so, you know, it makes heat reuse much easier. ⁓ It's just they're heavier, they're more expensive, but they use more power. So they're three phase. So, you know, how your power is set up is a consideration. If you only have single phase power, probably not the right fit.
You know, the, the immersion has a benefit of being able to use immersion specific things or being able to convert air miners to immersion miners as well. So there's that, those are kind of the main considerations there.
eco: Do you find yourself running like a mix of different cooling techniques in one operation, or is it just like across the board, all the, all this whole, this whole setup here is going to be all air, this one's going to be all hydro, etc?
Yeah, you know, usually unless it's like a long lived site, you know, like the Riot site's a great example, you know, that's been a very long standing massive operation and they've iterated with the times and you can kind of see that iteration as they go on, you know, their building design changed and their infrastructure setup changed a little bit as they got smarter. But if you're just like new getting into it, most setups are going to be just one and done unless, you know, you're a big guy who's got a huge long power contract.
⁓ You know if you're not trying to go super mega industrial scale and you're having to change as the years go, you know, you're probably just going to have one set up. You're going to make a choice and you're going to stick with it and then what role does facility design play in maximizing cooling efficiency and overall energy sustainability? Yeah, the design is important. It's the most important for, I'll give you a good example, so when you do a immersion right and Cameron will tell you this and all the guys at Shell will tell you this: The fluid you choose, that's a really big consideration. There's a lot of vendors, right? You got Exxon, you got engineered fluids, and they all sell what they claim is different. But as time goes on, you can tell those products are mostly the same or widely different. You can see fluid changing colors, and then it becomes more acidic and maybe eats all your machines, right? So doing work on the chemistry side for immersion is like, huge.
It's less about the price today as it is the price over five years because the fluid is not free. As much as Cameron would like to sell it for free, well, maybe he wouldn't like to sell it for free, but ⁓ that fluid's expensive.
eco: Yeah, and does it come with guarantees? Like, we guarantee you can run this fluid for 2,000 hours before it needs to be changed. I mean, every vendor's different, right? So what each vendor will say...
Marshall: Most of them will say that their stuff has been signed off by the manufacturer, know, that maybe it doesn't void your warranty, stuff like that. They've done work with the manufacturers, but the chemistry is different and unique between all of them. And so, you know, when we first got into immersion in like 2018, we just use mineral oil. And over time, that stuff breaks down. And I had a host of S9s just get fried because we became conductive. I didn't know that could happen. So like microfluidics engineering is like a whole field.
And you really got to do your diligence before you just buy the cheapest or what they claim is the best. There's a whole bunch of considerations around what pump do I use? Does it change viscosity when it changes temperatures? Like there's a bunch of stuff and every vendor's got different aspects. So another example is, if you got a certain type of fluid, maybe your fire suppression system has to change to meet code, right? Is the flash point of this fluid so high that maybe you don't need fire suppression in your building? There's a lot of give and takes there.
eco: Wow, yeah, so that goes into the design of the facility too. Do they like do them? Are the manufacturers like suggesting or dictating like you've got to use this pump if you're running this fluid or like, you know, we can't get results if you're running this other type of pump.
Marshall: No, not generally. They're not going to really make a recommendation on like infrastructure. They'll tell you what they've used before and maybe try to like guide you. They'll be as helpful as possible. But, you know, most pumps for more or less are just as a reliability thing, you you buy a cheap pump, it's probably going to crap out earlier than a nice pump. They'll give you more guidance around like flow rates and you know, they can, you know, at least show anyway, they've been very helpful. They'll do like a fluid simulation of your design for you and say like, maybe you can optimize here. Maybe this drop of this pipe could be different. It's at scale when you're buying a lot that's more collaborative than just buying stuff off the shelf. So ⁓ I'll say they'll help you as much as they can, but they're not going to vouch for other companies' equipment.
eco: Can they help you in supporting ways, like doing oil analysis after the fluid's been in use and kind of give you an idea of the metals that are starting to show up and break down?
Marshall: Yeah, so that's a big thing that a good fluid vendor should offer you, where maybe you have a chemist that can do small-scale testing, like voltage breakdown to see at what point does the voltage, does the fluid conduct the electricity or acidity levels. But if you have a good vendor, they should say, like once a quarter or once a month, send us a couple gallons as a sample. And they'll do like full crazy testing. Like Shell's got an FTIR machine, which is like a multi-million dollar machine that can tell you this is how much dissolved silicon from a thermal paste is in there. And this is XYZ, here's your fluid is aged XYZ. They'll give you the whole breakdown. So any good vendor should have a testing facility to do that for you.
eco: And then how many miners are balancing the trade-offs between, or sorry, how are miners balancing the trade-offs between upfront investment and operational savings when selecting cooling infrastructure?
Marshall: Yeah, and I think that's a question that's gonna change based on two things. The public guys are gonna play a different game than the non-public guys. Public guys have a bunch of different considerations. Right now, I ⁓ would say the majority of public miners is let's grow at all costs. Some of them have chosen different treasury management strategies and that kind of stuff and all those kind of, I would say, take a front row to these kinds of design choices. ⁓ I think the industry for hydro, and Tyler and I were just talking about this, is evolving rapidly.
Micro BT is putting out stuff that's like single phase power for exclusively for heat reuse. The Auradine guys just got into hydro recently as well. there's a bifurcation between strategies because they're playing different games. So the arbitration between what they're going to do really comes down to scale and how you can do certain things. Because what I do with my little 10 megawatt shack might be OK in downtown Houston.
But if I do those same kind of things inside the city limits somewhere else, fire marshal's going to get involved, like you can't do things the same way. And there's a bunch of trade-offs. Fire suppression being another example, a guy will come in, well, because this fluid XYZ, he's gonna look at like a safety data sheet and he wants to see when does this fluid become flammable and all these other considerations that mid-tier and small-tier guys don't even have to think about. I imagine there's like… the peripherals can just kind of spiral out of control. All it takes is the fire marshal to just say, we're going to revoke your certificate of occupancy. Guess what? You can't work there. Then it becomes illegal, because one guy had a bad day. So there's a lot of considerations. And you've got to be able to point to the fire code, like, no, that's not the case. And that's where having a good vendor for ⁓ even hydro, because they'll put additives in the water to reduce scaling and fluid.
And also like the infrastructure providers, you you've got to work with them so you know the laws. And so, you know, one guy having a bad day can't shut down a billion dollar operation.
eco: Right. Do you find that like ASIC manufacturers are making suggestions about like what like hydro to run through their miners, like what immersion their miners can go into or like are miner manufacturers and immersion fluid manufacturers working together or do you have to kind of play that role of liaison?
Marshall: Yeah, that's a good question. I can say that there have been OEMs that have worked directly with the fluid providers. If you want details and specifics on that, can definitely ask Cameron. I don't know what's public and what's not. I can say that when they come up with a new fluid, most vendors will reach out to OEMs and say hey, can you like put this on an approved list saying that hey, we've tested this we've tried this? There is some behind-the-scenes like co-development. I would say for, you know, use case specific applications. I know Engineered Fluids does as a little bit, too. So it's not just here's a fluid because what works for Bitcoin miners is not necessarily what works for you know guys running GPUs. You know they want different volumes and different viscosities.
So it's not like a one size fits all thing. So there's a lot of collaboration, I'd say for sure.
eco: All right. What innovations on the horizon could redefine how we approach thermal management in large scale mining under high heat conditions?
Marshall: Yeah, that's you know, what's really interesting is everybody's like AI, HPC, blah, blah. If you go to any HPC conference, these people think that cooling 1000 watts is like cutting edge insane, like nobody can do it.
So I went to Open Compute like a year ago, actually with Cameron, and I walked in and the guys at, I think it was Intel, they had this little mini immersion set up and they had the processor clocked to like 900 watts and everybody there was like, my God, this is so revolutionary. And I'm just like, this is like five years ago. So the fact that Bitcoin has like just blown HPC out of the water from like what we can cool.
When we were talking to vendors, they're like, what flow rates are you pushing? And it's several orders of magnitude beyond what any HPC data center is doing. And it's interesting when you sit down with these people and say, oh, we're moving 1,700 liters a minute. Their face melts off. And you're like, we'd like to be faster, maybe, or whatever. They just never thought that cooling in one small footprint, 5,000 watts, is even thinkable.
So the fact that the AI guys are starting to learn from the Bitcoin guys makes us feel like we're not little boys anymore. We're big guys who are starting to pay attention a little bit. So that's been really cool to see. As far as what's changing, I think the biggest change is the OEMs. MicroBT ⁓ was the first to come out with an immersion-specific SKU. ⁓ Riot famously purchased a lot of those. ⁓ Those are interesting to see. Because before, you got to take the fans off and have special firmware and really do all this bespoke stuff which just takes times away. Bitmain started shipping SKUs without fans. Auradine's got SKUs without fans. So seeing the OEMs kind of tailored to us now instead of us trying to like square peg round hole situation has been good to see. You go into any, if you're a big boy, you buy $100 million of Microsoft contracts, they're gonna have a guy there to help you make your stuff work for you.
And that's just now becoming the case for Bitcoin. And it's good to see. Because before, everybody's just like, you can't figure it out. You can't hack our firmware or whatever. That's your problem. No, you can't have SSH access to the boards. And it was like pulling teeth up until like three years ago, maybe. But now they're starting to come along and see like, look, we now have the money to hire serious professionals, serious electrical engineers. If you're not going to build it, we'll build it ourselves. So you can either come along or not.
And now to see the OEMs kind of play ball a little bit has been really encouraging. So yeah, I imagine like they're looking at this like if they don't do it, their competitors are going to do it. Not even that; if they don't do it, we will do it. So like early on, I know, maybe 2020 micro BT wouldn't give you SSH access unless you really begged and pleaded. But the tool that they had, had a sequel injection vulnerability, so we would just give ourselves root access through the Whatsminer tool.
And you know, you can just see through the Whatsminer tool by updating your pool. Okay, cool. And then for like two years, it was cat and mouse. They would patch that. We'd find another one where if you shove an SD card during post, it'll dump the firmware. And now you got the firmware and you can do all these things. This whole adversarial kind of, when I'm spending hundreds of millions of dollars with you, no other vendor would have done that in the professional world, right? And so now it's starting to kind of come back to where it should be, which has been very useful for just running a good operation.
eco: Have you been confronted with like environmental concerns like, you know, cooling Bitcoin miners with hydro uses a lot of water?
Marshall: Yeah.
eco: How do you how do you counter those?
Marshall: There's most of the marketing now. There's a very infamous Bitcoin site that I will leave names out in West Texas where these guys used Bitmain cooling. They had like a cooling tower and the Bitmain hydros and they had to drill wells and they started a reverse osmosis water treatment plant in order to get enough water to run in their cooling tower. And then as the water table depleted, the water got more and more briny and more and more salty, and then their RO system got clogged up. And then their site failed, and then it was like a whole massive thing. And so now anybody doing a tour, their big selling point from these, like let's say Heatcore for example, they'll say you don't have to add any water. Once you fill the system up, that's it. It's a closed system.
That's everybody's marketing point now is we don't use water. ⁓ Beyond that, you know, it just gets so freaking hot that OEMs are starting to use better components. Like micro BTs and Auradine hydro units can withstand like 65 Celsius degrees or 75 Celsius degree water coming into the machine so that you can use no water. So the, you know, outside of that, it also depends on where you're located. If it was a previously EPA investigated site.
You get one drop of immersion fluid outside the containing wall of your building. It's a whole like EPA shutdown. They gotta come and do soil studies and sampling and all this other crap because somebody before you had messed up the site, right? From like a previous business or whatever. you know, anything you can do to keep things contained is super important because it just takes you spilling a couple of liters of immersion fluid outside a previously condemned site and then can shut you down for a week while they do this sample study for like a gallon of milk spilling outside basically like rainwater runoff all this kind of crap when you hit scale it's like a huge operational overhead so anybody here that you know that runs a big op they've all got to deal with this crap and it's like it's a very serious time and money sink to do that and so working with the people to make sure that you can limit all those risks long till is super beneficial ⁓
eco: We've got five minutes left. Are we gonna take questions on this panel? All right, I'm wondering if you've got any funny anecdotes from your experience as it relates to keeping miners cool.
Marshall: Yeah, we used to do this thing where if you start working, I still do this in my current facility, my little test lab. If you come in there and you want a tour, you have to taste the fluid.
eco: No, you don't. Come on.
Marshall: I make people put a little finger in there because the good fluid is all biodegradable. They use it in like make up and stuff.
eco: It's like food grade?
Marshall: Yeah. And so that's like my first like right of passage. If you want to tour at my dojo, you got to taste it. And the feedback, at least for the Shell, I don't know if you guys got in this feedback, but your fluid has a slight buttery taste. So ⁓ that's the most common feedback we get. I don't know if that's useful, but maybe a selling point. ⁓
We also, we like to sous vide steaks in there as well. So for lunch, we get out the flamethrower, finish it off. It's the perfect temperature for like a nice, it's a little bit too well done for my taste, but you know, nice like medium. We do a lot of sous vide in the tanks. ⁓ So yeah, those are just a few of what I can mention publicly. So.
eco: That's awesome. Let's give Marshall a round of applause here.
And then I think we got enough time for two questions before we break for lunch, right? one more panel, okay.
All right, well thanks. Huge round of applause for these gentlemen. You guys crushed it. ⁓ Note to self, I'll double check the state.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~837 Eh/s at the beginning of May to a new all-time high of ~917 Eh/s by the end of May, marking ~9.5% growth for the month and ~17% year to date.
Difficulty was 119.12T at it’s lowest in May and 126.98T at it’s highest, which is a 6.6% increase for the month. All together for 2025 up to Epoch #446, difficulty has gone up ~15.6%.
According to the Hashrate Index, ASIC prices have increased ever so slightly over the last month. The more efficient miners like the <19 J/Th models are now fetching $17.77 per terahash, models between 19J/Th – 25J/Th are selling for $8.85 per terahash, and models >25J/Th are selling for $3.02 per terahash. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
Hashvalue over the month of May peaked at ~59,000 sats/Ph per day and closed the month out at ~52,000 sats/Ph per day, according to the Braiins Insights dashboard.
The next halving will occur at block height 1,050,000 which should be in roughly 1,026 days or in other words ~150,000 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the sixth 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.

If you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers. Also, consider talking to your local representatives about the Blockchain Regulatory Certainty Act which aims to codify that software developers cannot be held liable for the actions of end-users.
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:46:21
@ 4ba8e86d:89d32de4
2025-06-17 17:46:21A sede do ProtonMail está localizada na Suíça, um país conhecido por suas leis rigorosas de privacidade, embora a empresa tenha enfrentado alguns desafios, como ataques DDoS e pressão do governo suíço, ela continua comprometida em fornecer um serviço seguro e privado aos seus usuários.
O ProtonMail foi fundado em 2014 por um grupo de cientistas do CERN (Organização Europeia para Pesquisa Nuclear) que queriam criar uma plataforma de e-mail segura e privada que usasse criptografia de ponta a ponta. O objetivo era oferecer aos usuários uma alternativa aos serviços de e-mail tradicionais que frequentemente violam a privacidade dos usuários.A equipe fundadora incluía Andy Yen, Jason Stockman e Wei Sun, todos com formação em física e matemática.
Ao longo dos anos, o ProtonMail lançou vários recursos adicionais, incluindo aplicativos móveis para iOS e Android, integração com Tor e a possibilidade de enviar e-mails criptografados para usuários de outros provedores de e-mail. O ProtonMail também lançou uma VPN (rede privada virtual) chamada ProtonVPN, que segue o mesmo compromisso com a privacidade e segurança dos usuários.
A criptografia de ponta a ponta utilizada pelo ProtonMail assegura a proteção de todas as mensagens de seus usuários. O processo de criptografia ocorre no dispositivo do remetente antes do envio das mensagens aos servidores da ProtonMail, onde elas são armazenadas em formato criptografado. Quando o destinatário abre a mensagem, ela é descriptografada no dispositivo do destinatário, garantindo que somente o destinatário possa ler o conteúdo da mensagem. Isso significa que, mesmo que os servidores da ProtonMail sejam violados, as mensagens dos usuários permanecerão seguras e protegidas.
O ProtonMail oferece suporte à autenticação de dois fatores usando chaves de segurança YubiKey. Isso adiciona uma camada extra de segurança ao login da conta do ProtonMail, pois um invasor precisaria não apenas da senha, mas também da chave física para acessar a conta do usuário. A YubiKey é uma opção popular para autenticação de dois fatores, pois é fácil de usar e oferece proteção adicional contra-ataques de phishing e keylogging. O ProtonMail também suporta outras opções de autenticação de dois fatores, aplicativos de autenticação, como o Aegis Authenticator.
Outra funcionalidade importante é a proteção contra phishing e spam. O ProtonMail utiliza algoritmos avançados de filtragem para identificar e bloquear mensagens maliciosas antes que elas cheguem à caixa de entrada do usuário. Isso ajuda a reduzir a quantidade de spam recebida e a proteger contra-ataques de phishing, que tentam enganar o usuário a fornecer informações pessoais.
Passo a passo instalação do aplicativo protonmail no Android:
-
Baixe e instale o aplicativo protonmail em seu dispositivo móvel no F-droid ou obtainium.
-
Clique em "Criar nova conta" se você ainda não tiver uma conta ProtonMail, ou clique em "Fazer login" se já tiver uma conta.
-
Se você está criando uma nova conta, preencha os campos de registro, incluindo seu endereço de e-mail desejado e uma senha forte.
-
Depois de criar ou fazer login em sua conta, você pode usar o ProtonMail em seu dispositivo Android para enviar e receber e-mails seguros e protegidos.
Lembre-se de que, para garantir a privacidade e a segurança de suas informações, é importante usar uma senha forte e habilitar a autenticação de dois fatores. Utilize o Tor para acessar seu e-mail no site onion e considere usar uma VPN.
No Relatório de Transparência do ProtonMail, em muitos casos, a única informação que eles puderam fornecer foi um e-mail de recuperação (opcional na criação da conta) ou o IP que acessou o e-mail.
A própria ProtonMail recomenda o uso do Tor para acesso anônimo ao serviço. Se um juiz exigir a coleta do seu IP, a Proton não terá essa informação se você acessar seu e-mail via o site onion pelo Tor.

Se você é uma pessoa em situação de risco, como um ativista ou alguém que pode ser perseguido por diversos motivos, é essencial tomar medidas excepcionais: 1. Pague pelo serviço com Bitcoin. 2. Não use informações que possam identificá-lo ao se registrar. 3. Utilize o Tor, ou uma VPN, sempre que acessar o ProtonMail.
-
-
 @ cae03c48:2a7d6671
2025-06-17 22:01:57
@ cae03c48:2a7d6671
2025-06-17 22:01:57Bitcoin Magazine

Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or CustodyFlash, a Bitcoin payment platform, just announced it has launched Flash Invoicing, a completely free, non-custodial, and KYC-free Bitcoin invoicing tool. Designed for freelancers, the platform allows users to send professional invoices without platform fees, identity checks, or third party custody.
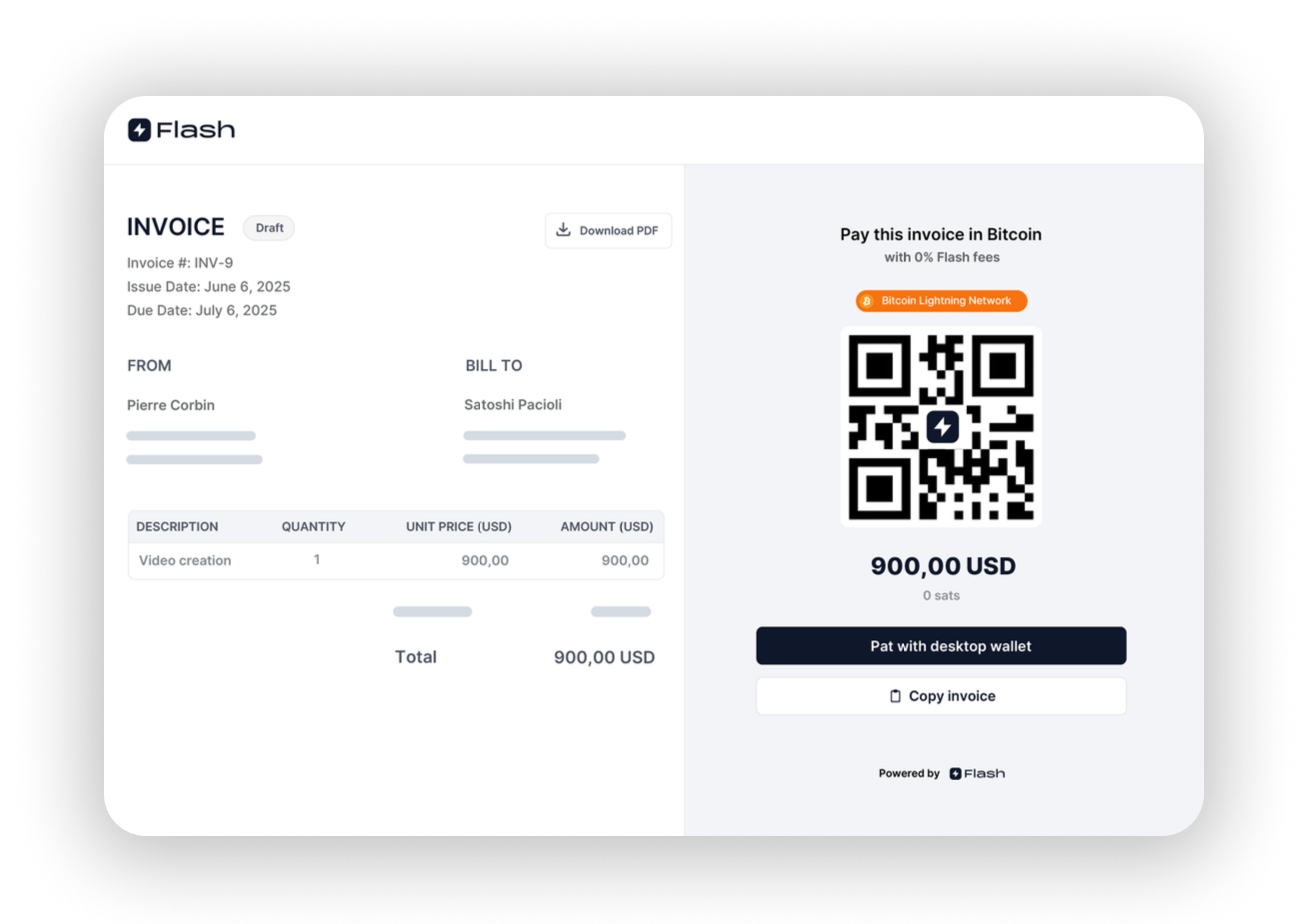
According to Deel, a crypto payments company for freelancers, Bitcoin is the most used cryptocurrency in the world for payments. Despite this growth, many freelancers continue to use basic methods such as pasting Bitcoin addresses into PDFs or emails. Some rely on custodial platforms that deduct fees or require identity verification, which can affect both earnings and data privacy.
“We’ve seen too many people paste BTC addresses into documents and call it invoicing,” said the CEO of Flash Pierre Corbin. “It’s messy. It’s risky. And it’s time for something better.”
Flash Invoicing Features:
- 0% platform fees: no subscriptions or commission
- Non-custodial: Bitcoin goes straight to the user’s wallet
- No KYC: users maintain full privacy
- Professional output: branded PDFs and secure payment links
- Integrated dashboard: manage payments, clients, and revenue
- Works with Flash ecosystem: including Stores, Donations, Paywalls, and POS
Many Bitcoin invoicing tools charge a percentage per transaction or require a subscription. As a result, freelancers often lose part of their income simply to issue an invoice and receive payment. Flash is aiming to solve this issue.
“Freelancers work hard enough. The last thing they need is a platform skimming off their earnings,” said Corbin. “That’s why we dropped our fee from 1.5% to 0% — and launched the first invoicing tool that’s truly free, without compromising on privacy or control.”
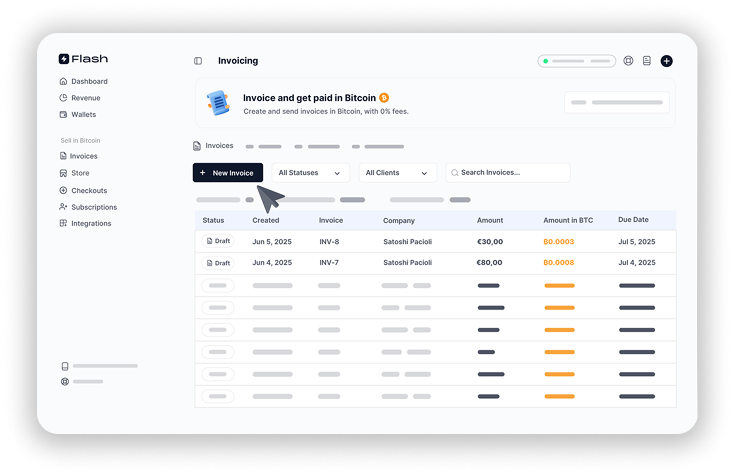
Flash Invoicing allows users to accept Bitcoin payments without relinquishing control, privacy, or revenue. It is integrated with the broader Flash suite, enabling users to manage invoicing alongside features such as setting up stores, receiving donations, or gating premium content.
“As a freelancer myself, I love using the Flash invoicing feature,” stated a freelancer & Flash user. ”It keeps all my clients in one place, allows me to easily edit invoices and track payments. Much more professional than sending a lightning address in the footer of a PDF invoice.”
This post Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or Custody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 31a4605e:cf043959
2025-06-17 17:46:15
@ 31a4605e:cf043959
2025-06-17 17:46:15Desde a sua criação, Bitcoin tem sido um marco na revolução do dinheiro digital, mas a sua evolução não parou no conceito inicial de transações descentralizadas. Ao longo dos anos, novas soluções tecnológicas foram desenvolvidas para expandir as suas capacidades, tornando-o mais eficiente e versátil. Entre essas inovações, destacam-se os smart contracts e a Lightning Network, que permitem aumentar a funcionalidade e escalabilidade da rede, garantindo um sistema mais rápido, barato e acessível.
Smart contracts no Bitcoin
Os smart contracts (contratos inteligentes) são programas que executam automaticamente determinadas ações quando certas condições pré-definidas são cumpridas. Embora o conceito seja mais comummente associado a outras redes, Bitcoin também suporta contratos inteligentes, especialmente através de atualizações como o Taproot.
Os smart contracts em Bitcoin permitem funcionalidades como:
Pagamentos condicionais: Transações que só são concluídas se determinadas regras forem cumpridas, como assinaturas múltiplas ou prazos específicos.
Gestão avançada de fundos: Utilização de carteiras multi-assinatura, onde diferentes partes precisam aprovar uma transação antes de ser processada.
Maior privacidade: Com a atualização Taproot, os smart contracts podem ser mais eficientes e indistinguíveis das transações normais, melhorando a privacidade da rede.
Embora os contratos inteligentes em Bitcoin sejam mais simples do que em outras redes, essa simplicidade é uma vantagem, pois mantém a segurança e robustez da rede, evitando vulnerabilidades complexas.
Lightning Network: escalabilidade e transações instantâneas
Um dos maiores desafios enfrentados por Bitcoin é a escalabilidade. Como a rede original foi desenhada para priorizar segurança e descentralização, a velocidade das transações pode ser limitada em períodos de alta procura. Para resolver esse problema, foi criada a Lightning Network, uma solução de segunda camada que permite transações quase instantâneas e com taxas extremamente baixas.
A Lightning Network funciona criando canais de pagamento entre utilizadores, permitindo que realizem várias transações fora da blockchain ou timechain principal de Bitcoin, registando apenas o saldo final na rede principal. Algumas vantagens incluem:
Velocidade: Transações são concluídas em milissegundos, tornando Bitcoin mais adequado para pagamentos diários.
Taxas baixas: Como as transações ocorrem fora da blockchain ou timechain principal, as taxas são mínimas, permitindo microtransações viáveis.
Descongestionamento da rede: Ao transferir grande parte das transações para a Lightning Network, a rede principal de Bitcoin torna-se mais eficiente e menos sobrecarregada.
Resumindo, o Bitcoin continua a evoluir tecnologicamente para se adaptar às necessidades de um sistema financeiro global. Os smart contracts aumentam as suas funcionalidades, permitindo maior flexibilidade e segurança nas transações. A Lightning Network melhora a escalabilidade, tornando Bitcoin mais rápido e eficiente para pagamentos do dia a dia. Com estas inovações, Bitcoin mantém-se na vanguarda da revolução financeira, demonstrando que, apesar das limitações iniciais, continua a adaptar-se e a crescer como um sistema monetário verdadeiramente descentralizado e global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:37:05
@ 4ba8e86d:89d32de4
2025-06-17 17:37:05O protocolo Matrix é um sistema de comunicação descentralizado de código aberto que fornece uma plataforma para mensageiros descentralizados. O Element foi lançado em 2014 como uma implementação do protocolo Matrix, originalmente conhecido como Riot.im , A ideia do Element nasceu quando Matthew Hodgson e Amandine Le Pape, dois desenvolvedores de software, decidiram criar uma plataforma de comunicação aberta e segura, que permitisse aos usuários terem total controle sobre suas informações. Eles acreditavam que a internet deveria ser um lugar onde as pessoas pudessem se comunicar livremente, sem se preocupar com a privacidade de suas informações.
O Element é um aplicativo de chat gratuito e de código aberto disponível em várias plataformas, incluindo desktop, web e aplicativos móveis. Ele oferece criptografia de ponta a ponta, o que significa que as mensagens são protegidas e só podem ser lidas pelo remetente e pelo destinatário. Além disso, o Element é descentralizado, o que significa que ele não é controlado por uma única entidade, mas sim por uma rede global de servidores.
O Element é amplamente utilizado por indivíduos e empresas que desejam ter uma comunicação segura e privada. É frequentemente usado por equipes de projetos, organizações sem fins lucrativos e grupos ativistas que precisam compartilhar informações confidenciais e se comunicar de forma segura. O Element também é conhecido por seu recurso de salas públicas, que permite que os usuários se juntem a grupos de discussão sobre vários tópicos de interesse.
Uma das principais vantagens do Element é sua arquitetura descentralizada. Ao contrário das plataformas de mensagens convencionais que centralizam os dados em seus próprios servidores, o Element utiliza uma rede descentralizada, distribuindo as informações em diversos servidores espalhados pelo mundo. Isso significa que os dados dos usuários são menos suscetíveis a ataques cibernéticos e invasões, já que não são centralizados em um único ponto vulnerável.
Para usar o Element, normalmente os usuários precisam se registrar em um servidor Matrix. Existem várias opções disponíveis, incluindo servidores públicos e privados. No entanto, outra opção é criar um servidor próprio para usar o Element.
O Element também utiliza criptografia de ponta a ponta para proteger as mensagens e arquivos trocados entre os usuários. Isso significa que apenas o remetente e o destinatário das mensagens podem ler o conteúdo, garantindo que as informações permaneçam seguras e privadas.
Outra vantagem do Element é sua ampla variedade de recursos, incluindo videochamadas criptografadas, compartilhamento de tela e integração com outros serviços, como calendários e aplicativos de produtividade. Isso torna o Element uma plataforma completa de comunicação e colaboração, adequada para uso pessoal e empresarial.
O Element também é fácil de usar e possui uma interface intuitiva e personalizável. Os usuários podem personalizar a aparência do aplicativo e acessar diferentes configurações e recursos com apenas alguns cliques.
https://element.io/
https://github.com/vector-im/element-android
-
 @ 88cc134b:5ae99079
2025-06-18 22:26:00
@ 88cc134b:5ae99079
2025-06-18 22:26:00 -
 @ 31a4605e:cf043959
2025-06-17 17:33:02
@ 31a4605e:cf043959
2025-06-17 17:33:02Bitcoin tem vindo a desempenhar um papel cada vez mais relevante em protestos e movimentos sociais em todo o mundo. Graças à sua natureza descentralizada, resistente à censura e independente do controlo governamental, Bitcoin tornou-se uma ferramenta valiosa para ativistas, organizações e cidadãos que lutam contra regimes opressivos ou sistemas financeiros restritivos.
Bitcoin como alternativa ao sistema financeiro tradicional
Nos últimos anos, governos e instituições bancárias têm utilizado restrições financeiras como uma forma de repressão política. Contas bancárias congeladas, doações bloqueadas e limitações a transações são algumas das estratégias utilizadas para enfraquecer movimentos sociais e protestos. Bitcoin oferece uma alternativa, permitindo que fundos sejam transferidos e armazenados sem a interferência de bancos ou governos.
Uma das principais vantagens de Bitcoin nestes contextos é a sua resistência à censura. Enquanto contas bancárias podem ser encerradas e serviços de pagamento centralizados podem ser pressionados a bloquear transações, Bitcoin funciona numa rede descentralizada, onde ninguém pode impedir que um utilizador envie ou receba fundos.
Exemplos do uso do Bitcoin em protestos
Hong Kong (2019-2020): Durante os protestos pró-democracia, ativistas enfrentaram restrições financeiras ao tentarem organizar manifestações e campanhas. Muitos recorreram a Bitcoin para evitar o rastreamento do governo chinês e garantir financiamento para as suas ações.
Canadá (2022): O movimento dos camionistas que protestavam contra restrições governamentais viu as suas contas bancárias congeladas. Como alternativa, doações em Bitcoin foram utilizadas para contornar a repressão financeira.
Bielorrússia (2020): Após as eleições presidenciais contestadas, manifestantes usaram Bitcoin para financiar atividades e ajudar aqueles que perderam os seus empregos devido à repressão estatal.
Nigéria (2020): Durante os protestos contra a brutalidade policial, conhecidos como #EndSARS, doações internacionais para os manifestantes foram bloqueadas. Bitcoin tornou-se um dos principais meios de financiamento do movimento.
Desafios do uso do Bitcoin em movimentos sociais
Educação e acessibilidade: Muitos ainda desconhecem como utilizar Bitcoin de forma segura e eficiente. A falta de conhecimento pode dificultar a sua adoção em larga escala.
Segurança digital: Movimentos sociais muitas vezes operam sob vigilância intensa. Se as medidas de segurança adequadas não forem seguidas, os fundos podem ser comprometidos.
Volatilidade: O preço de Bitcoin pode variar significativamente num curto período, o que pode afetar o valor das doações e dos fundos arrecadados.
Resumindo, o Bitcoin tem demonstrado ser uma ferramenta essencial para a resistência contra a censura financeira e a repressão governamental. Ao permitir que movimentos sociais e ativistas financiem as suas causas sem depender de intermediários, Bitcoin fortalece a luta pela liberdade e pela justiça. No entanto, a adoção eficaz da tecnologia exige conhecimento, segurança e adaptação às suas características únicas. À medida que mais pessoas aprendem a utilizar Bitcoin, o seu papel nos protestos e movimentos sociais continuará a crescer, reforçando a importância da soberania financeira na luta por direitos e liberdades.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 4ba8e86d:89d32de4
2025-06-18 19:05:43
@ 4ba8e86d:89d32de4
2025-06-18 19:05:43Ele usa a tecnologia PGP (Pretty Good Privacy) para criptografar e descriptografar informações.
O OpenKeychain Foi criado por Dominik Schürmann em 2011, com o objetivo de disponibilizar uma ferramenta de criptografia acessível e fácil de usar para usuários de Android. O openKeychain é uma das principais opções de criptografia de e-mail para usuários de Android em todo o mundo.
Criptografia de e-mail é um processo de proteção das informações contidas em um e-mail, de forma que somente as pessoas autorizadas possam acessá-las. A criptografia envolve a codificação da mensagem original em uma sequência de caracteres ilegíveis, que só podem ser decodificados por alguém que possua a chave de criptografia correspondente.O objetivo da criptografia de e-mail é garantir a privacidade e segurança das informações enviadas por e-mail, especialmente quando se trata de informações confidenciais ou sensíveis. Isso ajuda a prevenir que informações privadas sejam interceptadas ou lidas por pessoas não autorizadas durante a transmissão do e-mail.
Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
- Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
- Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Selecionar o aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas.
Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ c631e267:c2b78d3e
2025-06-18 18:50:48
@ c631e267:c2b78d3e
2025-06-18 18:50:48Ich dachte immer, jeder Mensch sei gegen den Krieg, \ bis ich herausfand, dass es welche gibt, \ die nicht hingehen müssen. \ Erich Maria Remarque
Was sollte man von einem Freitag, den 13., schon anderes erwarten?, ist man versucht zu sagen. Jedoch braucht niemand abergläubisch zu sein, um den heutigen Tag als unheilvoll anzusehen. Der israelische «Präventivschlag» von heute Nacht gegen militärische und nukleare Ziele im Iran könnte allem Anschein nach zu einem längeren bewaffneten Konflikt führen – und damit unweigerlich zu weiteren Opfern.
«Wir befinden uns im Krieg», soll ein ranghoher israelischer Militärvertreter gesagt haben, und der Iran wertet den israelischen Angriff laut seinem Außenminister als Kriegserklärung. Na also. Teheran hat Vergeltungsschläge angekündigt und antwortete zunächst mit Drohnen. Inzwischen ist eine zweite israelische Angriffswelle angelaufen. Ob wir wohl künftig in den Mainstream-Medien durchgängig von einem «israelischen Angriffskrieg auf den Iran» hören und lesen werden?
Dass die zunehmenden Spannungen um das iranische Atomprogramm zu einer akuten Eskalation im Nahen Osten führen könnten, hatte Transition News gestern berichtet. Laut US-Beamten sei Israel «voll bereit», den Iran in den nächsten Tagen anzugreifen, hieß es in dem Beitrag. Heute ist das bereits bittere Realität.
Der Nahe Osten steht übrigens auch auf der Themenliste des diesjährigen Bilderberg-Treffens, das zurzeit in Stockholm stattfindet. Viele Inhalte werden wir allerdings mal wieder nicht erfahren, denn wie immer hocken die «erlauchten» Persönlichkeiten aus Europa und den USA «informell» und unter größter Geheimhaltung zusammen, um über «Weltpolitik» zu diskutieren. Auf der Teinehmerliste stehen auch einige Vertreter aus der Schweiz und aus Deutschland.
Die Anwesenheit sowohl des aktuellen als auch des vorigen Generalsekretärs der NATO lässt vermuten, dass man bei dem Meeting weniger über das Thema «Neutralität» sprechen dürfte. Angesichts des Zustands unseres Planeten ist das schade, denn der Ökonom Jeffrey Sachs hob kürzlich in einem Interview die Rolle der Neutralität in geopolitischen Krisen hervor. Mit Blick auf die Schweiz betonte er, der zunehmende Druck zur NATO-Annäherung widerspreche nicht nur der Bundesverfassung, sondern auch dem historischen Erbe des Landes.
Positives gibt es diese Woche ebenfalls zu berichten. So hat der US-Gesundheitsminister Robert F. Kennedy Jr. nach der «sensationellen» Entlassung aller Mitglieder des Impfberatungsausschusses (wegen verbreiteter direkter Verbindungen zu Pharmaunternehmen) nun auch bereits neue Namen verkündet. Demnach möchte er unter anderem Robert W. Malone, Erfinder der mRNA-«Impfung» als Technologie und prominenter Kritiker der Corona-Maßnahmen, in das Komitee aufnehmen.
Auch die Aufarbeitung der unsinnigen Corona-Politik geht Schrittchen für Schrittchen weiter. In Heidelberg hat die Initiative für Demokratie und Aufklärung (IDA) den Gemeinderat angesichts der katastrophalen Haushaltslage zu einer offenen und ehrlichen Diskussion über die Ursachen der Krise aufgefordert. Das Thema «Corona» sei «das Teuerste, was Heidelberg je erlebt hat», sagte IDA-Stadtrat Gunter Frank im Plenum. Außerdem seien aus den Krisenstabsprotokollen der Stadt auch die enormen Verwerfungen ersichtlich, und es gebe Anlass für tiefgehende Gespräche mit der Stadtverwaltung.
Den juristischen und öffentlichen Druck auf die Kommunen möchte der Unternehmer Markus Böning erhöhen. Seine «Freiheitskanzlei» will Bürgern helfen, die Aufarbeitung selbst in die Hand zu nehmen. Unter dem Motto «Corona-Wiedergutmachung» bietet er Hilfestellung, wie Betroffene versuchen können, sich unrechtmäßige Bußgelder zurückzuholen.
So bleibt uns am Ende dieses finsteren Freitags doch auch Anlass zur Hoffnung. Es gibt definitiv noch Anzeichen von Menschlichkeit. Darauf möchte ich mich konzentrieren, und mit diesem Gefühl verabschiede ich mich ins Wochenende.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ dfa02707:41ca50e3
2025-06-17 21:01:55
@ dfa02707:41ca50e3
2025-06-17 21:01:55- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.


Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ fd0bcf8c:521f98c0
2025-06-18 18:23:27
@ fd0bcf8c:521f98c0
2025-06-18 18:23:27Marcus enters the dining room.
They're all waiting.
Ramirez at the head of the table like some broken queen. Morrison to her right, medals catching light that costs more than food. Chen sweating through his collar, salt stains mapping his desperation. Williams straightening his tie with shaking hands.
The table is set.
China plates cracked at the edges. Crystal glasses clouded with water spots. Nothing on them. Nothing coming.
"Mr. Cross." Ramirez rises. Perfect smile painted over ruin. "Marcus. Thank you for coming."
"You said lunch."
"Yes. Well. Please, sit. We have so much to discuss."
He takes the empty chair. Studies the empty plates. The pristine silverware that won't touch food. Because there is no food.
Outside, sirens wail. Inside, silence breeds.
"How was the drive?" Morrison asks. His voice too bright. "Traffic not too bad, I hope?"
"Fine."
"The new checkpoint system," Chen adds, dabbing sweat. "It's actually improved flow rates by thirty percent."
"Forty percent," Williams corrects. His collar damp now. "In some sectors."
Small talk. The dance of the damned. Marcus waits. Watches them perform their ritual of normalcy while the state dies around them.
"Your parents," Ramirez says finally. The real conversation beginning. "We've been discussing ways to honor them."
"Have you."
"The Cross Memorial Act. Full posthumous pardons. A park perhaps." She gestures at nothing. "With fountains."
"They're dead."
"Their legacy—"
"Dead too."
Silence falls like ash.
Morrison adjusts his medals, each one marking battles they've already lost. Chen dabs his forehead with a napkin that costs more than most people's meals. The air conditioning hums but doesn't cool. Nothing cools anymore.
"Water?" Ramirez offers. Lifts an empty pitcher. Crystal catching fluorescent light. Sets it down with a clink that echoes. "I apologize. We're waiting on a delivery."
"No need."
"The shortages," she explains. Her voice smaller now. "Temporary. Everything's temporary."
"Except Bitcoin."
The word hangs there.
What they've been dancing around.
Why he's really here. Why they called him to this tomb of a dining room with its empty promises and emptier plates.
"Yes," she says. Breathing shallow. "Bitcoin. We should discuss that."
"Should we."
"California's position has... evolved." The word costs her. "We see the value now. The importance."
"You had ten thousand coins once."
Her smile flickers. Dies. Returns as a grimace. "Ancient history."
"You sold."
"The state needed liquidity." A lie they've told themselves so many times it almost sounds true.
"The state needed better advisors."
Morrison leans forward. His chair creaks under the weight of his desperation. "We've learned... from our mistakes."
"Have you."
"We bought back what we could," Chen says. Voice breaking on each syllable. "Four coins. Cost us everything."
"Two coins," Williams corrects quietly. A whisper of defeat. "We paid for water this morning."
The mask slips. Ramirez's perfect composure cracks like drought earth. Like everything else in this dying place.
"Two coins," she repeats. Testing the words. Tasting failure. "Yes. Two."
"Not enough," Marcus says.
"No. Not nearly enough."
More silence.
The empty plates mock them with their hunger. The crystal glasses hold nothing but light and broken dreams. Somewhere in the distance, gunfire. Always gunfire now.
"We know you have ten," Morrison says. Drops the pretense like a worn mask. "Chain analysis confirms it."
"So?"
"First purchase at sixteen thousand. Smart. Eight more over the years. The last two—" He stops. Even desperation has limits.
"What about them?"
"We know what they cost you. What you sacrificed."
Marcus says nothing. The silence stretches taut as wire. They all know. His wife. His daughter. The hospital that wouldn't take dollars. That only took Bitcoin. The choice no father should make.
"We need your help," Ramirez says simply. Truth naked and bleeding. "California needs your help."
"California needed help ten years ago."
"We weren't ready then."
"You're not ready now."
"We are." She opens her laptop. Shows him contracts printed on paper they can't afford. Plans drawn in blood they haven't shed yet.
"With what funds?"
"We'll find funds."
"You can't afford lunch."
The words land like bullets. Chen looks at his empty plate as if it might sprout food through will alone. Williams studies the ceiling, counting cracks like rosary beads.
"The militia needs payment," Morrison says. Each word a stone in his throat. "Without them, it's chaos."
"It's already chaos."
"Controlled chaos. One Bitcoin keeps them loyal for three months."
"And then?"
"We mine more."
"With what power?"
"Solar. Wind." Fantasies dressed as plans.
"With what hardware?"
"We'll source it."
"With what expertise?"
"You."
Ramirez turns her laptop. "Digital Currency Advisor. New position. Help us transition."
Marcus stands. The empty chair scrapes marble like nails on coffin wood. The sound echoes in the tomb they've made of governance.
"We're done here."
"Wait." Morrison stands too. His hand moves toward his sidearm. Old habits. "Executive order 12204. We can requisition digital assets."
"From where? My brain?"
"We have methods."
"You have nothing. Empty plates. Empty promises. Empty threats from empty men."
"Sit down," Ramirez says quietly. The last queen of a broken kingdom. "Please."
Marcus remains standing. Ten feet tall in a room full of shadows.
"Half a coin," he says. Each word measured. Weighed. "For the kids. Not for you. Not for your militia. For the kids dying of thirst in your streets."
"Half?" Chen's voice breaks completely. "We need all ten."
"You need time travel. You need your ten thousand coins back. You need leaders who understood value before it was too late."
"That's not fair," Williams whispers.
"Fair?" Marcus almost laughs. The sound would shatter glass if there was any left unbroken. "You invited me to lunch with no food. You talk about honoring my parents with no money. You make threats with no power. Tell me about fair."
Ramirez closes her laptop. The performance over. The curtain fallen. The truth naked between them like a wound.
"Half a coin," she says. "We accept."
Marcus pulls out his phone. The transfer screen glows like salvation. His fingers pause over buttons that control the future.
"This is the last time. Don't contact me again."
"Understood."
He sends it. Half a Bitcoin disappearing into the void of their incompetence. Ten percent of his wealth. For children he'll never meet in a state that can't save itself.
The transaction confirms. Somewhere, servers hum. The blockchain grows. The future loads one block at a time.
Marcus walks to the door. Each step an epoch. Stops. Turns back to them. Their empty plates. Their empty treasury. Their empty souls.
"What if we fail?" Ramirez asks. The last question of the dying.
"You already did."
He opens the door. Steps through. Closes it behind him with the finality of extinction.
In the dining room, they sit with their empty plates and their single Bitcoin and the weight of what comes next. Outside, through windows that still gleam with borrowed light, California burns on. The sovereign individual has made his choice. The state has made theirs.
The future already loading. One block at a time.
-
 @ dfa02707:41ca50e3
2025-06-17 19:01:50
@ dfa02707:41ca50e3
2025-06-17 19:01:50Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 8bad92c3:ca714aa5
2025-06-19 00:02:21
@ 8bad92c3:ca714aa5
2025-06-19 00:02:21Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 31a4605e:cf043959
2025-06-17 17:31:08
@ 31a4605e:cf043959
2025-06-17 17:31:08Milhões de pessoas em todo o mundo ainda não têm acesso a serviços bancários básicos, seja por falta de infraestrutura, requisitos burocráticos ou instabilidade económica nos seus países. Bitcoin surge como uma solução inovadora para este problema, permitindo que qualquer pessoa com acesso à internet tenha controlo sobre o seu dinheiro, sem depender de bancos ou governos. Ao oferecer um sistema financeiro aberto e acessível, Bitcoin torna-se uma ferramenta poderosa para a inclusão financeira global.
O problema da exclusão financeira
Em muitos países em desenvolvimento, grande parte da população não possui conta bancária. Isto pode acontecer por diversas razões, como:
Falta de acesso a bancos: Muitas comunidades, especialmente em áreas rurais, não têm instituições financeiras próximas.
Exigências burocráticas: Alguns bancos exigem documentação específica ou um histórico de crédito que muitas pessoas não conseguem fornecer.
Custos elevados: As taxas bancárias podem ser proibitivas para quem ganha pouco dinheiro.
Instabilidade económica e política: Em países com alta inflação ou governos instáveis, os bancos podem não ser uma opção segura para guardar dinheiro.
Estas dificuldades deixam milhões de pessoas à margem do sistema financeiro, impossibilitadas de poupar, investir ou realizar transações de forma eficiente.
Bitcoin como alternativa
Bitcoin resolve muitos dos problemas da exclusão financeira ao oferecer um sistema acessível e descentralizado. Com Bitcoin, qualquer pessoa com um telemóvel e acesso à internet pode armazenar e transferir dinheiro sem necessidade de um banco. Entre as principais vantagens estão:
Acessibilidade global: Bitcoin pode ser usado em qualquer lugar do mundo, independentemente da localização do utilizador.
Sem necessidade de intermediários: Diferente dos bancos, que impõem taxas e regras, Bitcoin permite transações diretas entre pessoas.
Baixo custo para transferências internacionais: Enviar dinheiro para outro país pode ser caro e demorado com os métodos tradicionais, enquanto Bitcoin oferece uma alternativa mais rápida e acessível.
Proteção contra a inflação: Em países com moedas instáveis, Bitcoin pode ser usado como reserva de valor, protegendo o poder de compra da população.
Casos de uso na inclusão financeira
Bitcoin já tem sido utilizado para promover a inclusão financeira em diversas partes do mundo. Alguns exemplos incluem:
África e América Latina: Em países como Nigéria, Venezuela e Argentina, onde a inflação é elevada e o acesso a dólares é limitado, muitas pessoas usam Bitcoin para preservar o seu dinheiro e realizar transações internacionais.
Remessas internacionais: Trabalhadores que enviam dinheiro para as suas famílias no estrangeiro evitam as elevadas taxas das empresas de transferências tradicionais ao utilizarem Bitcoin.
Microeconomia digital: Pequenos comerciantes e freelancers que não têm acesso a contas bancárias podem receber pagamentos em Bitcoin de forma direta e segura.
Desafios da inclusão financeira com Bitcoin
Apesar das suas vantagens, a adoção de Bitcoin como ferramenta de inclusão financeira ainda enfrenta alguns desafios, tais como:
Acesso à internet: Muitas regiões pobres ainda não têm uma infraestrutura digital adequada.
Educação financeira: Para que mais pessoas utilizem Bitcoin, é necessário maior conhecimento sobre a tecnologia e as melhores práticas de segurança.
Volatilidade do preço: As oscilações de valor podem dificultar o uso de Bitcoin no dia a dia, especialmente em países onde as pessoas vivem com rendimentos instáveis.
Resumindo, o Bitcoin oferece uma solução viável para milhões de pessoas excluídas do sistema financeiro tradicional. Ao proporcionar acesso global, transações baratas e segurança contra a inflação, torna-se um instrumento poderoso para promover a inclusão financeira. No entanto, para que o seu potencial seja totalmente aproveitado, é essencial investir na educação digital e expandir a infraestrutura tecnológica, permitindo que mais pessoas tenham autonomia financeira através de Bitcoin.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 9ca447d2:fbf5a36d
2025-06-19 00:02:01
@ 9ca447d2:fbf5a36d
2025-06-19 00:02:01While most Bitcoin companies chase quick wins with flashy marketing and complex trading features, Coinfinity is taking a different path. The Austria-based company has built their entire business model around something most brokers treat as an afterthought: education.
Founded on the principle that Bitcoin adoption requires understanding, not just access, Coinfinity offers something great in the Bitcoin space: a broker that actually wants you to take your bitcoin off their platform.
Their Bitcoin Blinks educational series provides a self-custody-first approach, and Austrian economics foundation make them stand out in a crowded field of crypto casinos.

Coinfinity’s HQ in Graz, Austria
At the heart of this educational mission is Fab, Coinfinity’s Head of Bitcoin Education, whose journey to Bitcoin mirrors that of many who’ve found their way to Austrian economics through pure instinct.
“I always had the feeling that something in the world just doesn’t add up,” he told Bitcoin News when he sat down with us. “Something’s wrong, I don’t know what, but I felt like the foundation of our society isn’t quite fair, I just never knew what it was.”
Sound familiar?
That hunch eventually led him down a rabbit hole of geopolitics, monetary systems, and finally to Andreas Antonopoulos videos on YouTube.
“I basically disappeared from life for about a week, just watching those videos,” Fab recalled. But it wasn’t until he read The Bitcoin Standard that everything clicked.
“I remember it like it was yesterday, I closed the book and thought ‘Holy s***, now I get it.’ That was the moment. From then on, I was Bitcoin-only.”

Many of the best Bitcoin books are in English and translating them is important
Now as Head of Bitcoin Education at Coinfinity and co-founder of Aprycot Media (a German publishing house focused exclusively on Bitcoin), Fab spends his days helping others find that same spark.
And unlike most “crypto” companies, Coinfinity’s strategy isn’t driven by marketing gimmicks or token launches, it’s driven by teaching.
“Our goal is to create educational content that’s so easy to understand that people love sharing it,” Fab explained. “When they share it, they connect with us. Once they start understanding Bitcoin, they choose us to buy it.”
Most companies buy Google ads. Coinfinity builds minds. With their Bitcoin Blinks, 42 short, clear lessons covering everything from subjective value to seed phrases, they’re offering what most brokers won’t: context. Meaning. Philosophy.
“It became quite popular, and we think it’s way more effective for our brand than just buying ads,” Fab said.
And they don’t stop there. When it comes to custody, Coinfinity takes a radically different approach than most Bitcoin brokers.
“When you buy bitcoin from us, you always take custody, either in our in-app wallet where you control the seed, or your own hardware wallet,” Fab emphasized. “Even our lightning feature works the same way you always buy into your own wallet.”
That’s not just a slogan. It’s a core value of the company that runs so deep they’re willing to sacrifice user experience for it. “We never custody your bitcoin,” Fab said. “It’s one of the core values that you custody them yourself.”
Even as fees rise and UTXO management gets harder, Coinfinity stays committed to self-custody. They are open to optional custodial tools in the future, but always paired with education, and always encouraging users to take their bitcoin off-platform when the time is right.
“If we ever offer custodial services, it would only be to help users stack small amounts until they reach a meaningful UTXO size,” Fab explained.
The plan would involve accumulating smaller purchases monthly or weekly until users hit a threshold, maybe a million sats, then withdrawing to self-custody. “We don’t want to play games with your bitcoin. We don’t want to lend it out or earn interest on it.”

Coinfinity emphasizes on self-custody and education, even in its app
The challenge is real though. When new users first encounter Bitcoin, the technical barriers can be overwhelming. “Often causes problems with people just getting into Bitcoin who don’t understand what self custody is” Fab notes.
That’s why they built their in-app wallet, to smooth the onboarding while maintaining their self-custody values. “The in-app wallet was our first step toward optimizing user experience without compromising our core value of bringing bitcoin into self-custody,” he said.
“One of our taglines is ‘bringing Bitcoin to the people’ and we literally mean that. We want to bring bitcoin to them, not keep it from them.”
Another promising thing the company is doing in their operations is using AI to create more content, faster. Podcast scripts, educational summaries, internal tools, Fab’s even feeding Austrian economics PDFs into models to keep the tone on-brand and Bitcoin-only.
“We’re using these tools in our business development and marketing teams to generate more output with the same number of people,” he said. But the future looks even more exciting.
“Maybe one day we’ll have a tutor in the app where you can do a video call and ask ‘What is a Bitcoin address?’ and it will talk back to you naturally, going deeper as you ask more questions,” Fab explained. “That’s absolutely possible.”
The technology isn’t quite there yet for mainstream deployment in their app, but Fab is optimistic. “I’m sure that in the future, this won’t just be used for improving our internal workflow, but for enhancing the content itself,” he said.
It’s not a pipe dream. The tech is already close. The only thing missing is more Bitcoin-native data and companies like Coinfinity are quietly building that layer.
One of the favorite parts of these interviews is asking the builders in the space what they would ask Satoshi if given one question. When I asked Fab what he’d ask Bitcoin’s creator, he didn’t hesitate:
“Did you purposely build Bitcoin based on Austrian economics, or did it just happen by accident?
“All this monetization theory, Bitcoin being a store of value first, is this something you actually thought was possible and had in mind? Or was it just a lucky shot that accidentally gave us the best monetary properties?”
Because if Satoshi had built Bitcoin with a 2% inflation rate, like some other projects, it might’ve worked. But it wouldn’t have lasted.
“He could have made it with 2% tail emission, it still would have been decentralized. But then today, someone might introduce a coin with a fixed supply that could kill Bitcoin,” Fab noted.
Fab suspects the fixed supply wasn’t an accident. And thank God for that.
What’s remarkable about Coinfinity isn’t just their Austrian approach or their self-custody obsession, it’s how they’re proving that education-first Bitcoin companies can compete with the flashy crypto casinos dominating the space.
Coinfinity doesn’t serve U.S. customers. They’re focused on Europe, operating within EU regulations. But what they’re building, honest Bitcoin education, smart tools, and a relentless push for financial sovereignty, matters everywhere.
-
 @ b1ddb4d7:471244e7
2025-06-19 00:01:41
@ b1ddb4d7:471244e7
2025-06-19 00:01:41The OP_RETURN Debate has recently caused a stir within the bitcoin community. Bitcoin stands as a groundbreaking peer-to-peer currency, engineered for financial sovereignty and unshackled from centralized control, embodying Satoshi Nakamoto’s visionary design of a trustless monetary system.
Introduced in 2009, it leverages proof-of-work and a decentralized network of nodes to enable individuals to transact freely, free from the influence of banks or governments. This design prioritizes the integrity of money as a store of value and medium of exchange, reflecting Nakamoto’s intent to create a resilient alternative to fiat currencies.
For over a decade, bitcoin has thrived as a beacon of economic autonomy, drawing adherents who value its unalterable rules and global accessibility.
Yet, as of June 14, 2025, the ongoing OP_RETURN debate has emerged as a critical juncture, challenging bitcoin’s core identity. OP_RETURN, a script opcode introduced in 2014 to embed up to 80 bytes of data in transactions, was designed to reduce UTXO bloat from earlier data-stuffing practices.
However, recent proposals, such as Peter Todd’s pull request #32359, to expand this limit—potentially up to the 1MB block size—have sparked intense discussion. This controversy pits the purity of bitcoin’s monetary purpose against a push for data-driven experimentation, such as timestamping, NFTs, and Ordinals, which leverage the blockchain for purposes beyond financial transactions.
At the heart of this debate lies a fundamental tension: whether bitcoin should remain a specialized ledger for value transfer or evolve into a general-purpose data platform.
Proponents argue that expanding OP_RETURN could streamline development and enable innovative use cases, such as sidechains, while critics warn it risks diluting bitcoin’s focus, increasing node costs, and eroding its decentralized ethos.
This clash echoes past scaling disputes, like the 2017 block size wars, and underscores the delicate balance between adapting to new demands and preserving the principles that define bitcoin’s strength. As of June 14, 2025, the community appears divided, with developers like Todd and Luke Dashjr advocating opposing views, and the outcome poised to shape bitcoin’s future trajectory.
For those guided by bitcoin’s original vision of sovereignty and minimalism, this debate is more than technical—it’s philosophical. The push to expand OP_RETURN raises questions about the integrity of the network, the role of individual node operators, and the risk of centralization through data-heavy use.
As the discussion unfolds, it forces a reckoning: will bitcoin stay true to its roots as sound money, or will it embrace experimentation that critics argue could compromise its foundational values? This article explores these tensions, offering a perspective rooted in bitcoin’s essence and the principles of its staunchest defenders.
Background on OP_RETURN
OP_RETURN emerged as a script opcode in 2014, designed to allow the inclusion of up to 80 bytes of arbitrary data within unspendable transaction outputs on the Bitcoin blockchain. This innovation addressed the inefficiencies of earlier data-stuffing methods, which cluttered the UTXO set (a database of spendable coins) and increased the computational burden on nodes.
By providing a controlled way to embed data—marking it as unspendable—OP_RETURN aimed to balance the network’s functionality with its primary role as a monetary ledger, reflecting bitcoin’s focus on efficiency and scalability.
Historically, OP_RETURN has been used for practical purposes like timestamping documents and limited data storage, serving as a lightweight tool for decentralized proof-of-existence. However, in recent years, particularly by June 14, 2025, its use has increasingly shifted toward innovative but data-intensive applications like Ordinals and NFTs.
These developments, often achieved through workarounds such as inscribing data in SegWit fields or layered protocols, have pushed the boundaries of the 80-byte limit, transforming Bitcoin into a platform for digital collectibles and other use cases. This shift has sparked debate about whether such applications align with or undermine Bitcoin’s original intent as a peer-to-peer currency.
The Proposed Update
One of the most notable proposals in the OP_RETURN debate, as of June 14, 2025, is a pull request attributed to Peter Todd (#32359), which suggests removing the existing 80-byte cap on data embedded via OP_RETURN.
This change would potentially allow data payloads to expand up to the full 1MB block size limit, significantly increasing capacity for embedding information directly into bitcoin transactions. Introduced to address evolving use cases and technical inefficiencies, the proposal has gained traction among some developers who see it to enhance the protocol’s flexibility, leveraging Bitcoin’s existing infrastructure.
Arguments in favor of this update highlight several benefits. Proponents argue that removing the cap would simplify bitcoin’s codebase by eliminating the need for workarounds, such as multi-signature schemes or excessive transaction outputs, that currently clutter the UTXO set (a database of spendable coins).
Additionally, it could reduce network strain caused by these inefficient methods, potentially improving performance. Another key point is the potential to enable sidechain innovations, allowing bitcoin to serve as a foundation for layered solutions that enhance scalability and support new applications, all while keeping data within the blockchain’s secure framework.
However, the proposal faces strong counterarguments rooted in bitcoin’s monetary focus. Critics contend that lifting the 80-byte limit risks transforming bitcoin into a general-purpose data ledger, diluting its primary role as a peer-to-peer currency and store of value.
This shift could lead to blockchain bloat—potentially adding significant storage demands annually—raising resource requirements for node operators and possibly excluding smaller participants, thus threatening decentralization.
While some argue modern hardware can handle larger blocks, critics warn that even small increases burden low-resource nodes, clashing with the minimalist vision of Satoshi Nakamoto and purists like Giacomo Zucco, who argue that data storage is better suited to alternative blockchains or off-chain solutions.
Giacomo Zucco, a leading voice in the bitcoin community, champions the notion that bitcoin’s strength derives from its decentralization and censorship resistance, safeguarded by a minimal, secure protocol built on proof-of-work. Like Zucco, Nakamoto’s whitepaper emphasizes a lean system focused on financial transactions, empowering individual node operators to enforce consensus rules and prevent any single entity—be it a miner, developer, or corporation—from dictating its direction.
Expanding OP_RETURN undermines this vision by inviting bloat, which could raise node operational costs and centralize control among well-funded data users. This shift risks turning bitcoin into a platform for data-intensive applications like NFTs or Ordinals, rather than a robust financial network.
Zucco and other purists would likely argue that proof-of-work and the fee market should prioritize financial transactions, reflecting bitcoin’s original intent as a currency and store of value, while data storage belongs on second layers or alternative chains.
Preserving this focus is essential to maintaining the decentralized soul that defines bitcoin’s essence, a principle that node operators must uphold to honor its founding ethos.
Community Divide and Risks
The OP_RETURN debate has exposed a deep divide within the bitcoin community, particularly among developers and users, as of mid-June 2025. On one side, figures like Peter Todd and Antoine Poinsot support expanding the OP_RETURN limit to 4MB in Bitcoin Core’s version 30, set for release in October 2025, arguing it aligns with miner practices and reduces harmful workarounds.
In contrast, developers like Luke Dashjr argue that such changes dilute bitcoin’s monetary purpose, promoting Bitcoin Knots—a fork of Bitcoin Core with stricter filters, defaulting to a 40-byte OP_RETURN limit—as a countermeasure.
This split extends to users, with Bitcoin Knots nodes surging from 2% to 11% by June 2025, signaling a preference for a leaner blockchain, while others embrace the flexibility of larger data capacities, highlighting growing tension over the network’s future direction.
This division carries significant risks that could undermine bitcoin’s accessibility, a cornerstone of its decentralized ethos. Expanding OP_RETURN could lead to fee spikes as data-heavy transactions compete for block space, disproportionately burdening smaller users and node operators with limited resources.
Proponents argue that fee markets and prunable OP_RETURN outputs will regulate data use, but critics warn that spikes could still exclude low-resource participants. Node fragmentation is another concern, as differing mempool policies between Knots and Bitcoin Core nodes could disrupt transaction relay, weakening the unified network that secures Bitcoin.
While the change avoids a hard fork by adjusting mempool policy rather than consensus rules, it risks eroding trust in Bitcoin Core’s governance, reminiscent of the 2017 block size wars that fractured the community. Such tensions could weaken Bitcoin’s security and trustless environment, posing a critical challenge to its long-term viability.
Preserving Bitcoin’s Essence
-
 @ b7274d28:c99628cb
2025-06-18 18:21:04
@ b7274d28:c99628cb
2025-06-18 18:21:04Tired of dealing with spam? You're not alone. Here is a guide to picking relays that are good at keeping spam out, without sacrificing your own reach.
If you just want to skip to the relay suggestions, scroll to the sections titled "The Setup." There is one for users of Haven and one for those who aren't running their own relay at all.
Client Selection
"Wait, I thought this was a guide about selecting relays, not clients."
Yes, it is. But what relays you choose doesn't matter if you are using a client that does not read from your chosen relays, or that hard-codes problematic relays as fallbacks in addition to the relays you selected in an effort to "help you."
Additionally, some clients have settings that can help make up for poor relay selection using client-side spam mitigation methods. This includes clients like Coracle, Damus, Amethyst, and Nostur. Some may do so via web-of-trust (WoT) filters, so you only see notes and replies from those within your broader social circle, while others will automatically hide notes that those you follow have reported as spam or scams.
Coracle is a great client for dealing with spam, so long as you have gone into your "Content Settings" and set the "Minimum WoT Score" to at least 1. This means you will only see posts from users followed by at least one of the npubs you follow.
Damus also employs WoT, but it appears to be just for notifications, so you only receive notifications for those you follow and those they follow, or "friends of friends," as Damus put's it. This can be accessed by toggling it on in your notification tab at the top right, where you see the icon of the person with a check mark.
Nostur has WoT filters for downloading media turned on by default and also uses WoT to filter spam by default. Even better, if you use multiple npubs, you can filter using the WoT of your main npub, while logged into your alternate npubs.
Jumble recently added WoT filtering specifically for interactions. When you load a thread in Jumble, a shield icon will appear near the top right of the page, in line with the tabs for Replies and Quotes. Toggle it on, so the shield is green with a check mark and you will only see replies from those you follow and those your follows follow.
Amethyst does not yet have WoT based filtering built into the client, but it can hide notes that have been reported as spam, scams, impersonation, etc, by those you follow. This is not the most effective way to combat spam, though, since most users aren't often using the report feature. Hopefully we will see WoT filtering as an option in a future update.
Primal's apps do not read from any of your selected relays, but rather from their caching server alone. That said, they have a spam filter that is turned on by default so you see relatively little spam, regardless of which relays you use.
For this guide, I recommend using Amethyst for updating your relays, if you possibly can. The reason for this is because Amethyst has the most robust settings for being able to update all of your various relay lists.
Relay Lists Explained
Contrary to what you might think, there is not a single relay list for each user that is stored in a single note, because you can have relays that are used for only one purpose, and not for any other. Each of those purposes for which you might use a particular relay has its own list. That way a Nostr client can tell which relays you want to use for each separate purpose.
While this can make things less approachable for the user, it also means users don't have to rely on clients to hard code appropriate relays for each of these use-cases. If your client doesn't let you edit each of these relay lists, chances are they are using a set of relays for that purpose that the developer chose instead of you.
Public Outbox/Inbox Relays
This list of relays is found in your kind 10002 note, if you have one. If you don't have one, there won't be any relays shown for these categories in Amethyst. Other clients may fallback to showing you relays from a different list.
This list is intended to be used for Nostr clients to implement the "outbox model" to fetch notes from whatever relays they were written to, even if they aren't in the requesting user's relay list. This solves the issue of needing to share relays with those you follow in order to see their notes, allowing Nostr to remain decentralized.
Your "outbox" relays are the ones you write to, or at least the ones you want other users to know that you write to. When you add a relay here, it's like advertising to everyone, "If you want to see my public-facing notes, look for them on these relays."
Your "inbox" relays are the ones you read from. On this part of your list you are advertising, "If you want me to see your replies, comments, reactions, and zaps, then send them to these relays." These relays are massively important for reducing the amount of spam you see. If you have relays listed here that anyone can post to for free, you will almost certainly see a lot of spam in your replies, unless you have WoT filters turned on in your Nostr client.
DM Inbox Relays
This list is found in your kind 10050 note, if you have one, and is a list of relays where you want others to send you Direct Messages. Ideally, you will use a relay or two here that supports AUTH, so that it will only allow direct messages to be retrieved by the user they are addressed to.
What happens if you put a relay in here that doesn't support AUTH, so it allows anyone to retrieve your DMs? Not much. Anyone who wants to will just be able to see the encrypted content of the message, and depending on the type of DM they will see the identity of the receiver and perhaps also the sender. They will not be able to decrypt what was actually said in the messages. It's better if they cannot retrieve even that much, though.
Private Relays
This list is found in your 10013 note, if you have one. This is intended for listing a relay that you run yourself and that only you can access, as it will house notes that other users should not be able to see at all, such as eCash tokens and draft notes.
Search Relays
This list is found in your 10007 note, if you have one, and is used to search for notes or users who may not be using the same relays as you. It is good to use relays here that aggregate notes from other relays automatically, and which support NIP-50 for search capability.
Local Relays
This section is for any relays running on the local device, such as Citrine. Because the relays themselves are local, this list is local, as well, and is not saved to any note kind that is saved to your relays like the above lists.
General Relays
This list is found in the "content" tag of your kind 3 note, which is also where all of the npubs you follow are stored. As such, this note is commonly known as your follow list, rather than as a relay list. However, some clients, such as Amethyst, do make use of this list, and others use it as a fallback if they can't find a kind 10002.
If you are an Amethyst user most of the time, then I would recommend using this list to fill in any gaps that you may have from only writing to a few outbox relays, or only reading from a few inbox relays. It's a good place to put an aggregator relay, for instance, so long as that relay has good spam filtering, or a blastr relay, so those who don't yet use a client that supports the outbox model will still likely see your notes.
If you do not generally use Amethyst, then I would recommend you mirror your public inbox/outbox relays here, in case you use a client that cannot find your 10002 list. Relays that are only for outbox should be added as write only, those only for inbox should be added as read only, and those you use for both outbox and inbox should be both read and write.
The Setup (Haven Users)
If you are running your own set of Haven relays, here is the setup I would recommend:
Public Outbox (kind 10002)
Maximum of 4 relays.
- Your Haven outbox relay (Remember to add some public relays to your blastr)
- A paid relay of your choice (List available in "Paid Relays" section)
- A public relay, such as relay.damus.io, relay.primal.net, or nos.lol
Public Inbox (kind 10002)
Maximum of 4 relays.
- Your Haven inbox relay: [RelayAddress]/inbox
- A paid relay of your choice (can be same as outbox)
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- Your Haven "chat" relay: [RelayAddress]/chat
- An alternate AUTH relay, such as inbox.nostr.wine(paid), nostr.land(paid), or auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- Your Haven private relay: [RelayAddress]/private
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required) and/or wss://nostr.wine(paid for write, but can read for free).
The Setup (Not Running Haven)
If you are not running your own set of Haven relays, I would highly recommend you learn how and do so. However, if you decide against it, here is a setup that should suffice:
Public Outbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (List available in "Paid Relays" section)
- A large public relay, such as relay.damus.io, relay.primal.net, or nos.lol
- An additional public relay, but a smaller one, or one-time-payment paid relay.
Public Inbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (can be same as outbox)
- wss://nostr.wine - Even if you don't pay for it, you can read from it.
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- A paid AUTH relay, such as inbox.nostr.wine or nostr.land.
- An alternate AUTH relay, such as auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- A private relay you run on your Umbrel or Start9, or that is hosted for you on relay.tools.
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required).
- A blastr relay, such as filter.nostr.wine(paid), or...
- A few additional public relays set to write only.
Paid Relays
There are a ton of other paid relays out there that can be found via nostr.watch. The above listed options are simply the most popular with the largest feature-sets.
WoT Relays
These relays will only accept notes from npubs that are within the relay owner's WoT. I have provided a Jumble.social address for each relay so you can peruse the feed for yourself to see if you want to use it.
- wss://wot.utxo.one - Jumble Feed
- wss://nostrelites.org - Jumble Feed
- wss://wot.nostr.party - Jumble Feed
- wss://wot.sovbit.host - Jumble Feed
- wss://wot.girino.org - Jumble Feed
- wss://relay.lnau.net - Jumble Feed
- wss://wot.siamstr.com - Jumble Feed
- wss://relay.lexingtonbitcoin.org - Jumble Feed
- wss://wot.azzamo.net - Jumble Feed
- wss://wot.swarmstr.com - Jumble Feed
- wss://zap.watch - Jumble Feed
- wss://satsage.xyz - Jumble Feed
- wss://wons.calva.dev - Jumble Feed
- wss://wot.zacoos.com - Jumble Feed
- wss://wot.shaving.kiwi - Jumble Feed
- wss://wot.tealeaf.dev - Jumble Feed
- wss://wot.nostr.net - Jumble Feed
- wss://relay.goodmorningbitcoin.com - Jumble Feed
- wss://wot.sudocarlos.com - Jumble Feed
-
 @ 4ba8e86d:89d32de4
2025-06-17 18:01:47
@ 4ba8e86d:89d32de4
2025-06-17 18:01:47Como funciona o PGP.
GP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
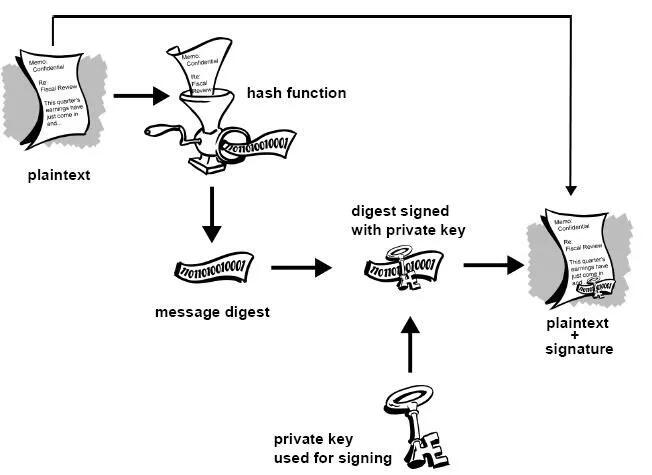
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
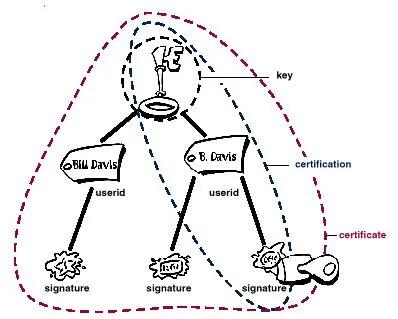 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
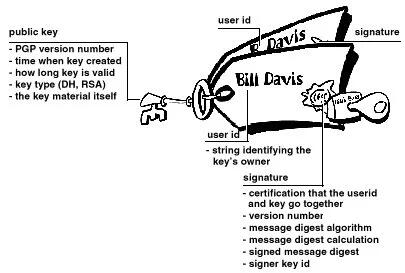 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
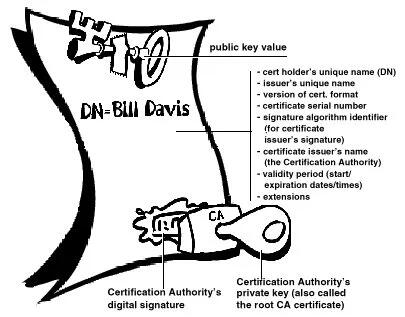
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 4f0a2f7a:9dc7fd0e
2025-06-18 18:47:51
@ 4f0a2f7a:9dc7fd0e
2025-06-18 18:47:51Web Application Specification
Overview
This document outlines the plan to build a complete web application with user authentication, REST API, database schema, frontend UI, and a comprehensive test suite.
High-Level Plan
- Define core application functionality.
- Design the database schema.
- Develop the backend (REST API and authentication).
- Develop the frontend (UI).
- Implement the test suite.
Requirements (Initial)
- User registration, login, and logout.
- REST API for data interaction.
- Database to store application data.
- Frontend UI for user interaction.
- Automated test suite.
Next Steps
- Gather detailed requirements for the application's core functionality.
- Choose appropriate technologies (backend framework, frontend framework, database system).
- Begin designing the database schema based on requirements.
-
 @ 31a4605e:cf043959
2025-06-17 17:29:01
@ 31a4605e:cf043959
2025-06-17 17:29:01Desde a sua criação, Bitcoin tem sido associado à ideia de liberdade financeira e individual. Diferente do dinheiro tradicional, controlado por governos e bancos centrais, Bitcoin permite que qualquer pessoa no mundo transacione e armazene valor sem depender de intermediários. Essa característica torna-se especialmente relevante em contextos de instabilidade económica, censura financeira e falta de acesso ao sistema bancário.
Bitcoin como ferramenta de autonomia financeira
A principal promessa de Bitcoin é devolver às pessoas o controlo sobre o seu próprio dinheiro. No sistema financeiro tradicional, os bancos e governos têm o poder de congelar contas, restringir transações e desvalorizar moedas através da impressão excessiva de dinheiro. Com Bitcoin, cada utilizador tem total posse dos seus fundos, desde que armazene as suas chaves privadas de forma segura. Isso significa que ninguém pode confiscar ou bloquear o acesso ao seu dinheiro.
Além disso, Bitcoin permite transações internacionais rápidas e baratas, sem depender de bancos ou plataformas de pagamento centralizadas. Em países onde as transferências internacionais são burocráticas e caras, Bitcoin representa uma alternativa eficiente e acessível.
Proteção contra a censura e o controlo estatal
Governos e instituições financeiras podem restringir o acesso ao dinheiro por motivos políticos ou económicos. Em regimes autoritários, dissidentes e jornalistas frequentemente enfrentam bloqueios financeiros como forma de repressão. Bitcoin oferece uma solução para esse problema, pois a sua rede descentralizada impede que qualquer entidade tenha controlo total sobre as transações.
Isto já foi demonstrado em diversos casos ao redor do mundo. Em momentos de crise, quando governos impõem restrições a saques bancários ou impõem limites às remessas de dinheiro, Bitcoin tem sido usado para contornar essas barreiras e garantir que as pessoas possam manter a sua liberdade financeira.
Desafios e responsabilidades da liberdade financeira
Embora Bitcoin ofereça mais liberdade individual, também exige maior responsabilidade por parte do utilizador. Diferente de uma conta bancária, onde um cliente pode recuperar o acesso à sua conta com um simples pedido, em Bitcoin a posse das chaves privadas é essencial. Se um utilizador perde as suas chaves, perde o acesso aos seus fundos para sempre.
Além disso, a volatilidade do preço de Bitcoin pode representar um desafio para quem pretende utilizá-lo como reserva de valor no curto prazo. No entanto, essa característica é compensada pelo seu modelo deflacionário, que protege a poupança a longo prazo contra a desvalorização causada pela inflação das moedas fiduciárias.
Resumindo, o Bitcoin representa uma revolução na forma como as pessoas gerem e protegem o seu dinheiro. Ao permitir transações livres de intermediários e resistir à censura financeira, Bitcoin fortalece a liberdade individual e oferece uma alternativa viável a sistemas financeiros centralizados e controlados por governos. No entanto, essa liberdade vem acompanhada da necessidade de maior responsabilidade, uma vez que cada utilizador é o único responsável pela segurança dos seus fundos. Para aqueles que valorizam a soberania financeira, Bitcoin é uma ferramenta poderosa que pode redefinir o conceito de dinheiro e autonomia pessoal no mundo moderno.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ a53364ff:e6ba5513
2025-06-18 18:23:43
@ a53364ff:e6ba5513
2025-06-18 18:23:43The internet is filled with countless social media platforms, all built on centralized servers and proprietary algorithms. However, in the world of decentralized technologies, a new contender is rising. Nostr is a simple, open protocol that promises to bring decentralized, censorship-resistant communication to the masses. In this article, we will explore what Nostr is, how it works, and why it might be the next big thing in the social media space.
How Did the Nostr Protocol Come About?
Nostr (Notes and Other Stuff Transmitted by Relays) was first conceived as a solution to the growing control centralized entities exert over online communications. Most social media platforms today are controlled by corporations, which have the power to censor, ban users, or manipulate what people see in their feeds. These issues, combined with growing concerns about privacy and data collection, inspired the creation of Nostr in 2020 by an anonymous developer named “fiatjaf”. The protocol aims to provide a decentralized alternative where users have control over their own content and identities.
What is Nostr?
Nostr is an open, decentralized communication protocol that allows users to send and receive messages in a censorship-resistant manner. It’s not a social network by itself but a foundation for building decentralized applications (DApps), such as social networks, chat apps, and other forms of communication platforms. Unlike traditional platforms, where all data is stored and managed by a single company, Nostr allows users to control their own data and interact directly without intermediaries.
Why is Nostr Different from Other Social Networks?
Traditional social media platforms like Twitter, Facebook, and Instagram are centralized, meaning all of your posts, messages, and data are controlled by a single company. These platforms have the power to suspend accounts, remove content, or alter algorithms in ways that impact your online presence. Nostr, on the other hand, is decentralized and open-source. There is no central authority, meaning your posts cannot be censored or deleted by a single entity. Each user owns their data, and communication happens directly between users and servers (called relays), reducing the potential for manipulation or surveillance.
Similarities of Nostr with Bitcoin
Nostr shares a similar ethos with Bitcoin, in that both are decentralized, censorship-resistant, and permissionless. Just as Bitcoin allows people to transfer value without intermediaries, Nostr enables communication without relying on a central authority. Both projects promote the idea of individual sovereignty—whether that’s over your money or your communication.
Another connection is the use of public and private keys for identity management. Like Bitcoin wallets, Nostr uses cryptographic keys, meaning that users “log in” by signing messages with their private key. This ensures that only the true owner of the key can send messages from a specific identity.
Bitcoin Integrations
Bitcoin and Nostr are increasingly integrated, especially through Bitcoin’s Lightning Network, which is designed for fast, low-fee transactions. Nostr and Bitcoin are a natural fit. By integrating Bitcoin’s Lightning Network, Nostr allows users to send and receive micropayments seamlessly. This is particularly useful for tipping or rewarding content creators within the network. Satoshis (the smallest unit of Bitcoin) can be sent across Nostr’s network almost instantly and with minimal fees. On Nostr, users can send Bitcoin micropayments, often referred to as “zaps.” This enables tipping and rewarding users directly within the network, providing a seamless way for content creators to monetize their work without the need for third-party platforms. For example, if you appreciate a post, you can “zap” the creator a small amount of Bitcoin, creating a new way to support online communities.
How Does Nostr Work? What are Clients and Relays?
Nostr operates through two main components: Clients and Relays.
– Clients are applications that allow users to create accounts, post messages, and interact with others. These clients can be web apps, mobile apps, or desktop apps that interact with the Nostr network.
– Relays are servers that store and transmit the messages between clients. When you post a message on Nostr, it is sent to a relay, and other users’ clients pull that message from the relay. You are not tied to any single relay, so even if one relay is down or blocks your content, you can still interact with others using different relays.
This relay-client model ensures that the network remains decentralized and difficult to censor.
Difference Between Today’s Internet and Nostr’s
Today’s internet is heavily centralized. Most of our communication, from emails to social media, is managed by large corporations with access to vast amounts of data about their users. This leads to issues like censorship, surveillance, and data harvesting. Nostr seeks to change this by decentralizing communication. It puts control back into the hands of users, allowing for a more private and open internet experience. There’s no need for trust in any single company—users own their data and decide which relays to trust or use.
How Do Bitcoin Zaps and Micropayments Work on Nostr?
One of the most exciting features of Nostr is its integration with Bitcoin’s Lightning Network. Through this integration, users can send Bitcoin zaps, which are small amounts of Bitcoin transferred instantly over the Lightning Network. Zaps function like “likes” on traditional social media platforms, but with the added benefit of rewarding users with real monetary value.
To send a zap, users link their Nostr profile to a Lightning wallet. Once connected, they can zap others by sending small amounts of Bitcoin, typically for content they enjoy or want to support. These zaps are fast, inexpensive, and work seamlessly within the Nostr ecosystem, making it easy for users to monetize content and interact with Bitcoin in a meaningful way.
Conclusion
Nostr is an exciting protocol that promises to reshape how we think about online communication. Its decentralized, censorship-resistant nature, along with its integration with Bitcoin, creates a platform where users have control over their data and interactions. Whether you’re looking for a more private social media experience or want to explore new ways to integrate Bitcoin into everyday interactions, Nostr is a protocol worth watching. With its growing ecosystem of clients and relays, Nostr might just be the future of decentralized communication.
Nostr is more than just a social network; it represents a shift towards user autonomy, privacy, and decentralized control. By combining cutting-edge technology with a solid ideological foundation, Nostr offers a refreshing alternative to mainstream social platforms. Whether you’re tech-savvy or just curious about new innovations, Nostr is worth exploring. And with various clients making it easily accessible, there’s no reason not to dive in and experience the future of decentralized social networking for yourself!
-
 @ 31a4605e:cf043959
2025-06-17 17:01:31
@ 31a4605e:cf043959
2025-06-17 17:01:31Desde a sua criação, Bitcoin tem sido alvo de debates sobre a sua utilização em atividades ilícitas. muitos críticos afirmam que Bitcoin facilita crimes como lavagem de dinheiro e financiamento de atividades ilegais, devido à sua natureza descentralizada e à possibilidade de realizar transações sem intermediários. no entanto, a realidade é mais complexa e muitas dessas alegações são exageradas ou baseadas em mitos. na verdade, a maioria das transações com Bitcoin são legítimas e até mais rastreáveis do que muitos imaginam.
O mito: Bitcoin é a principal moeda para criminosos
Um dos maiores mitos sobre Bitcoin é a ideia de que ele é amplamente utilizado por criminosos devido ao seu suposto anonimato. este argumento tornou-se popular principalmente devido a casos como o da Silk Road, um mercado negro online desmantelado pelas autoridades em 2013, onde Bitcoin era usado para transações ilegais. no entanto, os dados mais recentes mostram que apenas uma pequena fração das transações em Bitcoin está relacionada com atividades ilícitas.
Além disso, ao contrário do dinheiro em espécie, que é quase impossível de rastrear, todas as transações de Bitcoin são registadas publicamente na blockchain ou timechain. isto significa que qualquer pagamento feito com Bitcoin pode ser analisado e seguido, tornando mais difícil esconder transações suspeitas a longo prazo.
A realidade: Bitcoin é transparente e rastreável
Ao contrário do que muitos pensam, Bitcoin não é completamente anónimo, mas sim pseudónimo. todas as transações ficam registadas na blockchain ou timechain, permitindo que autoridades e analistas de dados consigam seguir os fluxos de dinheiro com precisão. várias empresas especializadas em análise forense de blockchain ou timechain já ajudaram a identificar e desmantelar redes criminosas que tentavam utilizar Bitcoin para fins ilícitos.
Governos e autoridades, como o FBI e a Europol, têm utilizado esta característica para combater crimes financeiros. na prática, criminosos que tentam usar Bitcoin acabam frequentemente por ser apanhados devido à transparência do sistema. por isso, a ideia de que Bitcoin é um refúgio seguro para criminosos não corresponde à realidade.
O uso ilícito de moedas fiduciárias é muito maior
Se compararmos Bitcoin com as moedas fiduciárias tradicionais, como o euro ou o dólar, percebemos que estas são muito mais utilizadas para atividades ilícitas. segundo relatórios de organizações internacionais, a lavagem de dinheiro e o financiamento de crimes organizados ocorrem predominantemente através de bancos, empresas fictícias e dinheiro em espécie.
Por exemplo, em escândalos financeiros globais, como o Panama Papers e o caso do banco HSBC envolvido em lavagem de dinheiro para cartéis, os meios tradicionais foram os preferidos para esconder fortunas ilegais. apesar disso, Bitcoin continua a ser injustamente associado ao crime, enquanto os verdadeiros mecanismos de financiamento ilícito continuam a operar dentro do sistema financeiro convencional.
Resumindo, o mito de que Bitcoin é um meio privilegiado para atividades ilícitas tem sido amplamente desmentido por dados e investigações. apesar de alguns criminosos terem tentado usá-lo no passado, a realidade é que Bitcoin é um sistema financeiro mais transparente e rastreável do que o dinheiro tradicional. a grande maioria das suas transações é legítima e, à medida que a adoção cresce, Bitcoin continua a provar o seu valor como um meio seguro e descentralizado para transações financeiras.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:58:15
@ 31a4605e:cf043959
2025-06-17 17:58:15Bitcoin, desde o seu surgimento em 2009, tem gerado uma variedade de histórias de sucesso e fracasso. Algumas dessas histórias são de pessoas que investiram cedo na criptomoeda e colheram os frutos de sua visão precoce, enquanto outras refletem os altos e baixos que caracterizam o mercado altamente volátil de Bitcoin. Ao longo dos anos, muitas dessas histórias tornaram-se emblemáticas, servindo tanto de inspiração quanto de alerta para quem entra nesse mercado.
Histórias de sucesso
O caso de Laszlo Hanyecz – A pizza de 10.000 Bitcoins Uma das histórias mais icônicas e, ao mesmo tempo, um exemplo do potencial e da volatilidade do Bitcoin, envolve Laszlo Hanyecz, um programador americano. Em 2010, Hanyecz pagou 10.000 bitcoins por duas pizzas. Na época, o valor das criptomoedas era tão baixo que essa transação passou despercebida, mas, em retrospectiva, os 10.000 bitcoins pagos por uma simples refeição valeriam centenas de milhões de dólares nos anos seguintes, quando o preço do Bitcoin disparou.
Essa história, muitas vezes citada, é um lembrete da enorme valorização do Bitcoin desde os seus primeiros dias. Embora Hanyecz não tenha ficado rico com essa transação, a história da "pizza de 10.000 bitcoins" tornou-se uma metáfora para o crescimento do Bitcoin, mostrando como uma pequena quantidade da moeda no início poderia ter mudado a vida de alguém para sempre.
O caso de Michael Saylor e a MicroStrategy no presente Michael Saylor, CEO da MicroStrategy, é outro exemplo de sucesso no mundo do Bitcoin. Em 2020, Saylor decidiu transformar a sua empresa numa das primeiras grandes corporações a investir pesadamente em Bitcoin, comprando mais de 100.000 bitcoins. A decisão foi inicialmente vista com ceticismo, mas ao longo do tempo, o preço do Bitcoin subiu consideravelmente, fazendo com que o investimento de Saylor se tornasse extremamente lucrativo. Para ele, o Bitcoin não era apenas um investimento especulativo, mas uma maneira de proteger a sua empresa da inflação e da desvalorização da moeda fiduciária.
Este caso é um exemplo de como uma aposta estratégica em Bitcoin pode resultar em grandes lucros para quem tem visão de longo prazo e confiança no potencial do ativo. A MicroStrategy tornou-se um dos maiores detentores de Bitcoin no mundo corporativo, e Saylor ganhou reconhecimento por ser um defensor do Bitcoin no mundo empresarial.
Histórias de fracasso
O caso de James Howells – O desaparecimento de 8.000 Bitcoins James Howells, um ex-empregado de TI de Gales, é um exemplo clássico de como a volatilidade e a negligência podem resultar em grandes perdas. Em 2013, Howells, que estava a minerar Bitcoin em casa, acumulou 8.000 bitcoins, que valiam cerca de 5.000 libras na época. Quando o mercado estava em queda, ele decidiu limpar o seu computador antigo e jogá-lo fora, sem perceber que os bitcoins estavam guardados em uma carteira digital nesse dispositivo.
Após a ascensão do preço do Bitcoin, Howells tentou recuperar o disco rígido, que estava enterrado numa lixeira em um aterro sanitário. Apesar das tentativas de convencer a cidade a permitir a escavação do aterro, o pedido foi negado, e ele nunca conseguiu recuperar os bitcoins. Este caso é um lembrete de como, sem a devida segurança e cuidado, até mesmo grandes fortunas podem ser perdidas no mundo das criptomoedas.
O colapso da Mt. Gox – A maior exchange de Bitcoin da história Uma das maiores histórias de fracasso envolvendo Bitcoin está relacionada à exchange Mt. Gox, uma plataforma de negociação de Bitcoin que, em 2014, faliu após alegadamente perder cerca de 850.000 bitcoins dos seus clientes, num valor superior a 450 milhões de dólares na época. A Mt. Gox foi, por um período, a maior exchange de Bitcoin do mundo, mas a sua falência foi um marco negativo na história do Bitcoin.
A falência da Mt. Gox foi causada por uma combinação de hacking, erros internos de segurança e má gestão. Embora alguns dos bitcoins perdidos tenham sido recuperados mais tarde, muitos investidores ficaram devastados pela perda dos seus fundos. Este incidente trouxe à tona a importância da segurança nas exchanges de Bitcoin e da responsabilidade das plataformas financeiras no manejo das criptomoedas de seus clientes.
O impacto da volatilidade e da adoção no mercado
As histórias de sucesso e fracasso envolvendo Bitcoin não são apenas anedotas, mas refletem a natureza imprevisível e arriscada do mercado de criptomoedas. O preço de Bitcoin pode flutuar drasticamente, o que significa que investidores podem tanto fazer grandes fortunas quanto sofrer grandes perdas. Enquanto alguns vêem Bitcoin como uma forma de alcançar a liberdade financeira e proteger-se contra a inflação, outros enfrentam o risco de perder tudo, como demonstrado pelos casos de fracasso.
A adoção crescente de Bitcoin em mercados emergentes, bem como a entrada de investidores institucionais, como a MicroStrategy e o próprio Elon Musk, são indicativos de que o Bitcoin está a ser cada vez mais reconhecido como uma alternativa legítima ao sistema financeiro tradicional. No entanto, as falências de exchanges e as perdas de grandes quantidades de Bitcoin destacam a necessidade de uma abordagem prudente e de uma infraestrutura mais robusta para garantir a segurança e a confiança dos utilizadores.
Resumindo, as histórias de sucesso e fracasso em torno do Bitcoin são um reflexo da natureza volátil e emergente desta moeda digital. Enquanto alguns ganharam milhões, outros perderam fortunas devido à falta de precaução, erros de gestão ou simplesmente pelo preço imprevisível da criptomoeda. Através destas histórias, fica claro que, embora o Bitcoin tenha o potencial de gerar grandes recompensas, ele também apresenta riscos significativos. Para aqueles que entram nesse mercado, é crucial estar preparado e consciente dos desafios que podem surgir, garantindo segurança e adotando uma estratégia de longo prazo para lidar com as incertezas e volatilidade do mercado.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:08:15
@ 31a4605e:cf043959
2025-06-17 17:08:15Bitcoin surgiu como uma alternativa ao sistema financeiro tradicional, oferecendo um meio de troca descentralizado e resistente à censura. No entanto, essa proposta desafia diretamente o controlo que os governos exercem sobre a economia, especialmente no que diz respeito à emissão de moeda e regulação do setor financeiro. Como resultado, muitos governos veem Bitcoin com desconfiança e tentam limitar a sua adoção, enquanto outros procuram integrá-lo à economia de forma controlada.
Motivos para o conflito entre governos e Bitcoin
A resistência governamental à adoção de Bitcoin deve-se a vários fatores, entre os quais se destacam:
Perda de controlo monetário: Os governos controlam a política monetária através da emissão de moeda fiduciária e da manipulação das taxas de juro. Bitcoin, por ter uma oferta fixa e descentralizada, impede que governos imprimam mais dinheiro, limitando a sua influência sobre a economia.
Dificuldade na tributação: A utilização de Bitcoin dificulta a fiscalização de transações e a cobrança de impostos, tornando-se um desafio para as autoridades que dependem da tributação para financiar gastos públicos.
Preocupações com regulação e crime financeiro: Muitos governos argumentam que Bitcoin pode ser usado para lavagem de dinheiro, evasão fiscal e outras atividades ilícitas. No entanto, como todas as transações ficam registadas na blockchain ou timechain, Bitcoin é, na realidade, mais rastreável do que o dinheiro físico.
Competição com moedas digitais de bancos centrais (CBDCs): Alguns governos estão a desenvolver as suas próprias moedas digitais, conhecidas como CBDCs. Estas oferecem um alto nível de controlo sobre as transações financeiras, mas não possuem as mesmas propriedades descentralizadas de Bitcoin. Para garantir a adoção das CBDCs, alguns governos tentam limitar ou proibir o uso de Bitcoin.
Diferentes países têm abordagens variadas em relação a Bitcoin, desde a aceitação total até a repressão severa.
El Salvador: foi o primeiro país a adotar Bitcoin como moeda legal em 2021. Esta decisão gerou conflitos com instituições financeiras globais, como o Fundo Monetário Internacional (FMI), que pressionou o governo salvadorenho a reconsiderar a sua decisão.
China: o governo chinês proibiu completamente a mineração e o uso de Bitcoin em 2021, alegando preocupações ambientais e riscos financeiros. No entanto, muitos mineradores e utilizadores chineses continuam a operar através de meios alternativos.
Estados Unidos: embora Bitcoin seja legal nos EUA, o governo tem imposto regulamentações mais rígidas às plataformas de troca e à mineração, tentando aumentar o controlo sobre o setor. Alguns políticos defendem uma abordagem favorável, enquanto outros veem Bitcoin como uma ameaça ao dólar.
União Europeia: a UE tem adotado uma postura regulatória mais rigorosa, impondo regras sobre a identificação dos utilizadores e a transparência das transações. Apesar disso, Bitcoin continua a ser legal e amplamente utilizado.
Apesar dos desafios impostos por alguns governos, a adoção de Bitcoin continua a crescer. Muitos utilizadores veem Bitcoin como uma forma de preservar a sua riqueza perante políticas monetárias inflacionárias e controlo excessivo sobre o dinheiro. Além disso, países com economias instáveis e sistemas financeiros pouco acessíveis encontram em Bitcoin uma solução para pagamentos internacionais e proteção contra crises económicas.
A resistência dos governos pode desacelerar a adoção de Bitcoin em algumas regiões, mas não conseguirá eliminá-lo completamente. Como uma rede descentralizada e global, Bitcoin continuará a ser utilizado, independentemente das restrições impostas por qualquer governo. A longo prazo, a sua adoção dependerá da capacidade dos indivíduos e empresas de resistirem às pressões regulatórias e continuarem a utilizá-lo como uma alternativa financeira.
Resumindo, o conflito entre governos e Bitcoin reflete a luta entre um sistema financeiro tradicional centralizado e uma nova alternativa descentralizada. Enquanto alguns países tentam proibir ou restringir o seu uso, outros adotam-no como parte da sua economia. No final, a resistência dos governos pode apenas atrasar, mas dificilmente impedirá a adoção global de Bitcoin, que continua a demonstrar a sua resiliência e utilidade como uma reserva de valor e meio de troca.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ f85b9c2c:d190bcff
2025-06-18 16:39:13
@ f85b9c2c:d190bcff
2025-06-18 16:39:13
This is too scaring cannot break this vicious circle and it goes with complications. There isn't a more serious condition beyond an empty pocket or people's economic status.People told they do not have the right to education, healthcare etc. Of course there are thousands of critical areas to target so that it may be adequately addressed to help break the cycle of areas of education, economic opportunities, health care, and mechanisms of social support.
Education Quality education should also give them the ability to lead a stable income, course of better lives. However the program would benefit poor children and help in more long-term aspects . Investment in education also means an improvement of the school environment in poor areas. It means first of all professional education of teachers, improving conditions and accessibility to all resources needed for studying-books, technology, etc. Relatively low costs of higher education and vocational trainings can equip young people with the needed and actually demanded skills for more promising employment.
Economic Opportunities It is the most basic need to save people from poverty and empower them with ownership over some opportunities economically. For example creation of jobs, small businesses, equal pay to citizens within the country and a willing government and organizations which will give out a micro-loan and grant to business-oriented entrepreneurs who want to start up. Then undergoing a good program on training of financial literacy, business management, and marketing that will empower people with a better foundation which can then leverage to do well through enterprising ambition. For this reason people will thus be able to make a living wage ,at least their basic needs will be available and the means to invest for themselves.

Access to Health Care Health and poverty problems are evident therefore better health means improved levels of productivity.Improvement in health care is therefore expected to get health care that not only meets the price but also accessible at some cost. So ,universal health services including preventive service, mental health and maternal and child health care may improve the health of families defined as low-income providers. All these public health programs should be based on nutrition sanitation and prevention of diseases. Education should bring out the potentiality of the community in acquiring the proper information that will help them decide the right choices for betterment in health, hence a healthier economic outlook in the future.
Social Support Systems Support systems that would have protection provided for families and individuals. Other programs may also be monetary, food, or housing that may be needed which will minimize a part of the direct burdens. Such assistance and resources are also made possible with access entry to community networks. Community organizations and non-profits providing counseling and mentoring support perhaps some skills development programs-show people an opportunity to work against the challenge that stands out as a barrier for people getting successes.
-
 @ 9ca447d2:fbf5a36d
2025-06-18 18:01:34
@ 9ca447d2:fbf5a36d
2025-06-18 18:01:34When Richard Scotford moved to Costa Rica in 2018, he had no idea he would become a key figure in a thriving Bitcoin economy.
A longtime Bitcoin holder who initially saw it through the lens of speculation, Scotford’s journey led him to embrace Bitcoin’s deeper purpose and spearhead Bitcoin Jungle — a grassroots movement bringing real-world Bitcoin adoption to Costa Rica.
Bitcoin circular economies create holistic value for Bitcoiners
Bitcoin Jungle is inspired by Bitcoin Beach in El Salvador but uniquely adapted to Costa Rica’s economic landscape. Unlike El Salvador, where Bitcoin was positioned as a tool for financial inclusion, Costa Rica already has a fairly stable banking system.
The real issue? The friction of moving money. Expats, business owners, and tourists struggle with high fees, banking red tape, and slow transactions. Bitcoin helped solve a lot of these problems.
The Birth of Bitcoin Jungle
Scotford and his team launched Bitcoin Jungle in late 2021 with a simple goal: get bitcoin into people’s hands and make it usable. However, there was one challenge — he had no technical background.
Determined to create a circular bitcoin economy, Scotford networked aggressively. He attended the first Adopting Bitcoin conference in El Salvador, approaching strangers with his vision:
“I was just walking around trying to find people who could help me make this economy, going up to random people saying ‘Hey, what can you do? We’re trying to make a circular economy in Costa Rica, can you help us?’ They all thought I was crazy.”
The breakthrough came when he turned to Bitcoin Twitter. Nicolas Burtey from Galoy encouraged him to create a wallet, and developer Lee Salminen forked the Bitcoin Beach wallet for their project.
“Within two weeks of Adopting Bitcoin, Lee forked the Galoy Bitcoin Beach wallet, which took Galoy by surprise. Even though they made their wallet to be forked if necessary, I don’t think they were expecting people to do it so fast and, I’d like to say, so well. They were like, ‘Okay, cool, who are these guys doing this?’”
Finally Bitcoin Jungle had its own working wallet, surprising even the Galoy team with the speed of execution.
Grassroots Adoption: One Vendor at a Time
How do you build a bitcoin economy from scratch? Scotford’s answer was simple: start at the farmers’ markets.
“We were like, okay, we’re going to get all the bespoke niche market sellers who are in this area. We have all these beautiful farmers markets, and we decided to approach these people first,” Scotford explained.
His team took a strategic approach, targeting market gatekeepers first.
“If you want to talk to every individual person, it’s really difficult. But if you can talk to the person who is the owner of the market, and then they can introduce you to their market stores, you’re already halfway there.”
Going stall by stall, they pitched Bitcoin’s advantages — no bank fees and better payment options. But adoption didn’t happen overnight, so Bitcoin Jungle initially offered a safety net — vendors could cash out at the end of the day.
“We would say to the vendors, ‘Look, accept bitcoin, and at the end of the day, if you don’t want to keep the bitcoin, we’ll buy it off you,’” Scotford recalled.
“When we first started, maybe 30–40% of the vendors were cashing up every day or at the weekends. Lee would be walking around with big fistfuls of money, cashing out vendors.”
But over time, something shifted — they started keeping their bitcoin.
“Eventually, the vendors started to learn themselves that, ‘Oh, actually it’s better to keep it.’ They would then pay for their tables in the markets using bitcoin. They thought, ‘Well, I don’t want to keep this bitcoin, I don’t really know what to do with it, but I can pay for my table.’ So there, the circular economy starts to happen.”
Today, Bitcoin Jungle runs with minimal intervention, and Scotford takes pride in their reliability.
“When you come here to Costa Rica, what we really pride ourselves on is that if someone says they accept bitcoin, 99% of the time, they will. And if they’re part of Bitcoin Jungle, they will 100% accept bitcoin and you will have a fluid experience with it.”
By mid-summer 2024 over 380 locations in Costa Rica accepted bitcoin
The Bitcoin Jungle Wallet and Real Usage
Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network.
Acting as a community bank, the project processes a large number of transactions daily. To encourage proper security practices, Scotford’s team alerts their peers, reminding users to move their bitcoin to cold storage.
“If you’ve got too much bitcoin on your wallet, we send you a message telling you to move it to cold storage,” he explained. For larger businesses, they even offer hands-on assistance to secure funds properly.
Unlike the HODL-only philosophy that many Bitcoiners advocate, Bitcoin Jungle encourages spending.
“Michael Saylor says don’t spend your bitcoin. We say the opposite,” Scotford laughed. “We’re the antithesis of that. You need to spend it.”
Bitcoin Jungle’s Unique Approach to Costa Rica
Bitcoin Jungle isn’t just another Bitcoin adoption effort; it’s tailored to Costa Rica’s economy. The wallet operates in Costa Rican colónes, making transactions feel familiar to residents while ensuring tourists and expats can still interact easily.
The team has also introduced low-fee bitcoin ATMs, point-of-sale integrations, and partnerships that allow users to pay in bitcoin while the recipient receives local currency.
A major breakthrough came when Francis Pouliot from Bull Bitcoin joined forces with Bitcoin Jungle, bringing his expertise in banking infrastructure to the project.
This collaboration enabled seamless bitcoin payments that integrate directly with Costa Rica’s financial system, allowing users to pay anyone, even businesses that don’t directly accept bitcoin, while the recipient receives funds in colónes or dollars.
“I can go to a hardware store, order steel for my new basketball court, pay in bitcoin, and the store gets dollars,” Scotford said. “For a non-tech guy like me, it’s magical.”
Why Aren’t There More Bitcoin Jungles?
Scotford sees an opportunity for more localized bitcoin economies.
“There should be a Bitcoin Harbor, a Bitcoin Mountain, a Bitcoin Driveway,” he joked. “But instead of waiting for permission or corporate funding, people need to take action themselves.”
He emphasizes that building a circular bitcoin economy doesn’t require deep pockets. “I probably gave away $600 worth of bitcoin when we started — just $3 here, $4 there — to get people using it.”
The Future of Bitcoin Jungle
Bitcoin Jungle continues to grow, recently hosting events like the Bitcoin Freedom Festival and integrating bitcoin into community projects, including a school where tuition can be paid in bitcoin.
“The institutions have come in, but the grassroots projects haven’t caught up,” Scotford observed. “It’s time for people to stop sitting on their hands and start building.”
Bitcoin is permissionless, no one has to wait for approval to start using it. Bitcoin Jungle proves that with vision and persistence, anyone can build a thriving Bitcoin economy, one market stall at a time.
Get the latest from Bitcoin Jungle: follow them on X
-
 @ 31a4605e:cf043959
2025-06-17 17:04:50
@ 31a4605e:cf043959
2025-06-17 17:04:50Bitcoin foi concebido como um sistema descentralizado, onde qualquer pessoa pode participar na rede, validar transações e garantir a segurança do sistema. no entanto, ao longo dos anos, a mineração de Bitcoin tornou-se cada vez mais concentrada em certas regiões do mundo, levantando preocupações sobre a sua descentralização e segurança. este debate tem gerado diversas opiniões, com alguns a argumentarem que a centralização da mineração pode comprometer os princípios fundamentais de Bitcoin.
Por que a mineração se tornou centralizada em alguns países?
A mineração de Bitcoin exige uma grande quantidade de energia e equipamentos especializados, conhecidos como ASICs. devido a fatores como custos de eletricidade, clima e regulamentação, algumas regiões tornaram-se polos de mineração, atraindo grandes operações. entre os principais motivos para essa concentração estão:
Custo da eletricidade: países com eletricidade barata, como a China (antes da proibição), Cazaquistão e algumas regiões dos Estados Unidos, tornaram-se centros de mineração porque os custos de operação são significativamente mais baixos.
Clima favorável: locais com temperaturas frias reduzem a necessidade de sistemas de refrigeração para os equipamentos de mineração, tornando a operação mais eficiente.
Regulamentação e incentivos fiscais: algumas nações criam ambientes favoráveis para a mineração, oferecendo benefícios fiscais ou políticas de incentivo ao setor energético.
Impactos da centralização da mineração
A centralização da mineração em certos países gera preocupações sobre o controlo da rede Bitcoin. entre os principais riscos, destacam-se:
Risco de censura: se um país com grande concentração de mineradores decidir regulamentar ou restringir a mineração, pode afetar temporariamente a rede, tornando-a mais vulnerável a ataques ou censura.
Ataque de 51%: um dos maiores receios é a possibilidade de um grupo de mineradores controlar mais de 50% do poder de hashing da rede, o que poderia permitir a manipulação de transações. embora improvável, este cenário preocupa a comunidade de Bitcoin.
Dependência de infraestruturas centralizadas: se a mineração estiver concentrada em poucas regiões, falhas em infraestruturas locais, como cortes de eletricidade ou desastres naturais, podem ter um impacto significativo na rede.
Medidas para descentralizar a mineração
Apesar da tendência de centralização, a rede Bitcoin continua resiliente e existem iniciativas para tornar a mineração mais distribuída. algumas soluções incluem:
Mineração caseira e comunitária: o incentivo à mineração em pequena escala pode ajudar a distribuir o poder de hashing de forma mais equilibrada.
Uso de energia renovável em várias regiões: à medida que mais mineradores adotam fontes renováveis, novas localidades estão a surgir como centros de mineração descentralizados.
Exodo de mineradores: após a proibição da mineração na China em 2021, muitas operações foram realocadas para diversos países, como Estados Unidos, Canadá e países da América Latina, ajudando a diversificar a rede.
Resumindo, a centralização da mineração em algumas regiões é um desafio para Bitcoin, mas não significa que a rede esteja em risco imediato. à medida que a indústria evolui, a tendência é que a mineração se torne cada vez mais distribuída, garantindo a segurança e a descentralização do sistema. embora seja essencial monitorizar esta questão, Bitcoin continua a demonstrar a sua resistência, adaptando-se constantemente às mudanças no setor da mineração.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:56:33
@ 31a4605e:cf043959
2025-06-17 17:56:33Bitcoin, desde o seu lançamento em 2009, tem atraído a atenção de diversos investidores e visionários que acreditam no seu potencial para revolucionar o sistema financeiro global. Ao longo dos anos, várias figuras se destacaram no movimento em torno da criptomoeda, seja como pioneiros que ajudaram a fundá-la, ou como investidores que apostaram no seu futuro. Estes indivíduos desempenharam papéis cruciais no desenvolvimento do Bitcoin, na sua adoção crescente e na sua legitimação no mercado financeiro.
Satoshi Nakamoto
O maior pioneiro do Bitcoin é, sem dúvida, o seu criador, Satoshi Nakamoto. Embora o nome seja um pseudónimo, a sua contribuição para a criação e lançamento do Bitcoin foi fundamental. Em 2008, Nakamoto publicou o famoso whitepaper intitulado "Bitcoin: A Peer-to-Peer Electronic Cash System", detalhando a ideia de uma moeda digital descentralizada que poderia operar sem a necessidade de uma autoridade central, como um banco. Em 2009, ele lançou o software Bitcoin e minerou o primeiro bloco da blockchain, conhecido como "bloco gênese".
Satoshi Nakamoto permaneceu uma figura misteriosa, nunca revelando a sua verdadeira identidade. Ele foi responsável pelo desenvolvimento inicial do protocolo, mas desapareceu gradualmente da cena pública por volta de 2011, deixando o projeto nas mãos de uma comunidade crescente de desenvolvedores. A sua identidade permanece desconhecida até hoje, mas o seu impacto na criação de uma nova era digital é inegável.
Hal Finney
Hal Finney foi um dos primeiros colaboradores de Nakamoto e é amplamente reconhecido como o primeiro a receber uma transação de Bitcoin. Em janeiro de 2009, Finney recebeu 10 bitcoins de Nakamoto como parte de um teste de transação, tornando-se uma das primeiras pessoas a acreditar no projeto. Finney, que era um programador e investigador de segurança, desempenhou um papel importante no desenvolvimento técnico do Bitcoin e ajudou a popularizá-lo nas suas primeiras fases.
Finney foi uma figura respeitada na comunidade de criptografia e um defensor do movimento de descentralização digital. Ele continuou a apoiar o Bitcoin até sua morte, em 2014, e é lembrado como um dos maiores pioneiros da moeda digital.
Roger Ver
Roger Ver, conhecido como o "Bitcoin Jesus", foi um dos primeiros investidores e “evangelistas” do Bitcoin. Ver ficou fascinado com o conceito de uma moeda descentralizada e investiu cedo em vários projetos relacionados ao Bitcoin. Ele foi um dos primeiros a reconhecer o potencial disruptivo do Bitcoin, defendendo a sua adoção global e promovendo o seu uso como meio de pagamento.
Ver também foi uma das figuras centrais na criação de empresas e iniciativas que ajudaram a impulsionar o ecossistema Bitcoin. Embora tenha sido uma figura polêmica, devido às suas opiniões fortes sobre a escalabilidade do Bitcoin, e tenha se afastado da blockchain original do Bitcoin em favor do Bitcoin Cash, sua contribuição para a popularização da moeda é inegável.
Tim Draper
Tim Draper é um dos investidores mais conhecidos no espaço do Bitcoin e um defensor da sua adoção em larga escala. Em 2014, Draper comprou quase 30.000 bitcoins, que foram apreendidos pelo governo dos Estados Unidos em uma operação contra o mercado Silk Road. Draper fez essa compra por cerca de 19 milhões de dólares, e ele tem sido uma figura-chave na promoção do Bitcoin como uma alternativa viável às moedas fiduciárias.
Draper, um investidor de risco de renome e fundador da Draper Associates, é conhecido por sua visão de longo prazo e pela sua confiança na ascensão das criptomoedas. Ele tem defendido o Bitcoin como uma ferramenta para democratizar o acesso ao dinheiro e acredita que a adoção do Bitcoin vai crescer exponencialmente nos próximos anos.
Michael Saylor
Michael Saylor, CEO da MicroStrategy, é uma figura importante na adoção institucional do Bitcoin. Em 2020, Saylor fez uma aposta significativa ao comprar mais de 100.000 bitcoins para a sua empresa, transformando-a na primeira companhia pública a ter Bitcoin como reserva de valor no seu balanço. Saylor tem defendido publicamente o Bitcoin como uma proteção contra a inflação e uma alternativa mais segura ao dinheiro fiduciário. A sua aposta ajudou a legitimar o Bitcoin no mundo corporativo e inspirou outras empresas a seguir o seu exemplo.
A sua posição em relação ao Bitcoin tem sido clara: ele acredita que o futuro financeiro do mundo está no Bitcoin, e a sua empresa serve como um exemplo para outras grandes corporações a adotarem a moeda digital.
Resumindo, os pioneiros e investidores que contribuíram para o crescimento e a difusão do Bitcoin desempenharam papéis vitais na evolução desta tecnologia disruptiva. Desde o misterioso Satoshi Nakamoto até figuras como Hal Finney, Roger Ver, Tim Draper e Michael Saylor, o Bitcoin tem sido moldado por pessoas com uma visão única sobre o futuro do dinheiro e da liberdade financeira. Através da sua perseverança e crença no potencial do Bitcoin, esses indivíduos ajudaram a estabelecer as bases para a adoção global da moeda digital, transformando-a de uma ideia inovadora em uma força revolucionária no sistema financeiro. O futuro do Bitcoin dependerá, em grande parte, da continuidade da sua evolução e da adoção por mais pessoas e instituições, mas é indiscutível que os pioneiros e investidores desempenharam um papel fundamental na sua ascensão.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ b1ddb4d7:471244e7
2025-06-18 16:02:21
@ b1ddb4d7:471244e7
2025-06-18 16:02:21Why are Stripe Alternatives are growing like mushrooms? When it comes to online payment processing, Stripe has long dominated the conversation.
However, with its complex pricing structure, strict policies and first-world focus, many entrepreneurs and companies are actively seeking viable Stripe alternatives.
Whether you’re a SaaS startup, e-commerce store, or global enterprise, choosing the right payment processor can significantly impact your bottom line and customer experience.
Table of Contents
- Why Consider Stripe Alternatives?
- The Complete List of Stripe Alternatives
- Additional Notable Mentions
- How to Choose the Right Stripe Alternative
- Conclusion
Why Consider Stripe Alternatives?
Before diving into our comprehensive list, it’s worth understanding why businesses are exploring alternatives to Stripe. While Stripe offers robust features and excellent developer tools, some businesses face challenges with pricing transparency, limited global coverage, or specific industry requirements that Stripe doesn’t fully address.
The Complete List of Stripe Alternatives
Based on extensive research and analysis of the payment processing landscape, here are 27 proven Stripe alternatives that could be the perfect fit for your business:
1. Flash – Easiest Bitcoin Payment Solution
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.

2. Lemon Squeezy – The SaaS-Focused Alternative
Dubbed as “acq’d by Stripe,” Lemon Squeezy offers a comprehensive solution specifically designed for digital product sales and SaaS businesses. It provides strong customer support, built-in analytics, and handles payments, subscriptions, global tax compliance, and fraud prevention in one platform.
3. Gumroad – Creator Economy Champion
Gumroad has carved out a niche serving creators and small businesses by providing tools for selling digital products, physical goods, and subscriptions. It’s particularly popular among content creators, artists, and independent entrepreneurs who want to experiment with various ideas and formats. They also open-sourced their code which is quite the ‘chad-move’.
4. Paddle – All-in-One SaaS Commerce
Paddle caters to SaaS and software companies by offering a comprehensive platform with billing, licensing, and global tax handling capabilities. It’s designed to be a complete solution for subscription-based businesses, handling payments, tax, and subscription management in one platform.
5. FastSpring – Global E-commerce Specialist
FastSpring specializes in e-commerce solutions for software and SaaS companies, with a focus on global payments and subscription management. According to TechnologyAdvice, it’s particularly strong for international transactions and helps companies sell more, stay lean, and compete big.
6. 2Checkout – Versatile Payment Solutions
2Checkout (now part of Verifone) offers versatile payment solutions excelling in global payments, subscription billing, and digital commerce. One of the best stripe alternatives as it’s an all-in-one monetization platform that maximizes revenues and makes global online sales easier, supporting over 200 countries and territories.
7. Payoneer – Cross-Border Payment Expert
Payoneer simplifies cross-border payment solutions, offering local payment ease globally with a focus on market expansion and multi-currency support. It’s trusted by small to medium-sized businesses for global payment solutions and international money transfers.
8. Chargebee – Subscription Management Leader
Chargebee is a subscription management platform perfect for SaaS and SMBs, with robust billing and revenue management features. If you were looking for stripe alternatives to setup subscriptions, Chargebee might be right for you. It streamlines revenue operations and helps businesses grow efficiently with comprehensive subscription billing capabilities.
9. Maxio (formerly Chargify) – B2B SaaS Billing
Maxio offers a robust platform for B2B SaaS billing and financial operations, focusing on growth and efficiency for subscription businesses. It’s the most complete financial operations platform for B2B SaaS, bringing core financial operations into one platform.
10. Recurly – Dynamic Subscription Management
Recurly offers dynamic subscription management platform, excelling in churn management and data insights for subscription growth. It’s the only proven platform that expands and protects your recurring revenue with subscription management, recurring billing, and payments orchestration.
11. Braintree – PayPal’s Enterprise Solution
Braintree (by PayPal) provides a versatile global payments platform, integrating multiple payment methods with a focus on conversion and security. It delivers end-to-end checkout experiences for businesses, offering single-touch payments and mobile optimization.
12. PayKickstart – Modern Commerce Platform
PayKickstart offers a modern commerce platform for online billing and affiliates, focusing on revenue maximization and churn minimization. It’s the most complete checkout, recurring billing, affiliate management, and retention solution with global capabilities.
13. PayPro Global – Full-Service E-commerce
PayPro Global offers a full-service eCommerce solution for selling software and SaaS, focusing on global payments, tax compliance, and customer support. It provides flexible solutions with over 70 payment methods and great support for software companies.
14. Shopify Payments – E-commerce Integration
Integrated with Shopify, this service is ideal for SMBs in eCommerce, offering a seamless shopping cart and payment experience. It’s the simplest way to accept online payments, automatically set up for major methods with no fees for some payment types.
15. Square – Versatile POS and Payment Solutions
Square provides versatile POS and payment solutions for small businesses with a strong focus on retail and mobile payments. Forbes Advisor notes it as one of the top alternatives for businesses needing both online and offline payment capabilities.
16. Zoho Billing – Integrated Business Solution
Zoho Billing is an online recurring billing and subscription management solution, ideal for small and medium-sized businesses seeking professional invoice creation, time and expense tracking, and improved cash flow management. Zoho isn’t just competing for stripe alternatives, they offer a ton of other products and services.
17. WePay – Chase Company Integration
WePay, a Chase company, provides integrated payment solutions for ISVs and SaaS companies with customizable payment solutions. It’s designed for platforms like marketplaces and small business tools, offering seamless user experience and fraud protection.
18. QuickBooks Payments – SMB Accounting Integration
This service provides seamless accounting and payment solutions for SMBs and SaaS businesses, featuring real-time tracking and automated bookkeeping. It lets small businesses accept payments online from anywhere with easy integration into QuickBooks accounting.
19. Mangopay – Marketplace Payment Infrastructure
Mangopay offers a modular payment infrastructure for marketplaces and platforms, emphasizing flexibility, global payouts, and AI-powered anti-fraud. It uses flexible wallets built to orchestrate fund flows and monetize payment experiences.
20. Coinbase Commerce – Cryptocurrency Payments
Coinbase Commerce enables businesses to accept payments from around the world using cryptocurrency. It offers instant settlement, low fees, and broad asset support, making it easy for merchants to accept digital currency payments globally.
21. BTCPay Server – Open-Source Bitcoin Processor
BTCPay Server is a self-hosted, open-source cryptocurrency payment processor with 0% fees and no third-party involvement. It’s secure, private, censorship-resistant, and completely free for businesses wanting full control over their Bitcoin payments.
22. Lago – Open-Source Billing Alternative
Lago is an open-source alternative to Stripe Billing and Chargebee, specializing in billing and metering in one place for usage-b
-
 @ b1ddb4d7:471244e7
2025-06-18 23:01:34
@ b1ddb4d7:471244e7
2025-06-18 23:01:34That’s exactly what Simplified Privacy VPN is offering: a new kind of privacy tool that feels more like spinning up a secure, disposable virtual browser than using a traditional VPN.
Most of us know what a VPN is: it hides your IP address, encrypts your traffic, and gives you a bit more control over your privacy online. But what if you could go way beyond that—without setting up a complicated system, running a full virtual machine, or revealing anything about yourself?
What Makes It Different?
When I tried it myself, I realized this wasn’t just another VPN. It didn’t just route my traffic—it gave me access to a completely separate browsing environment. Imagine logging into a private, anonymous machine in the cloud, one that:
- Has its own browser and system settings
- Can’t see your personal files, history, or identity
- Randomizes details like screen size and timezone
- Leaves no trace once you’re done
This isn’t just hiding your IP—it’s giving you a fresh, secure web session that’s disconnected from your actual device.
Simplified Privacy VPN: The Lightning-Powered Twist
Here’s where it gets even cooler for us in the Lightning world: access costs just $1 in bitcoin via the Lightning Network.
You send a few sats, and within seconds you get access to a private browser session that lasts for a full month. Want a different profile or setup? Just pay another dollar and spin up a new one—no account, no email, no friction.
You can create as many instances as you like, each with its own identity. This is microtransaction-based privacy in action—exactly the kind of innovation Lightning enables.
Excellent Support, Secure Channels
I also tested their support team with a couple of questions—one technical issue and one feature request. Support is offered through secure, privacy-respecting channels, including Session chat. Responses were fast, friendly, and helpful. Even more impressive: my feature request was implemented not long after I sent it in.
In a space where many privacy tools leave you to figure things out on your own, this kind of responsive support makes a big difference.
Why This Matters
For journalists, activists, developers, or just regular folks who don’t want Big Tech watching their every move, this setup is a game-changer:
- More realistic protection than just using incognito mode or a VPN
- No need to trust the website, since this system isolates the browser to its own filesystem
- No need to trust the app, since it doesn’t require root access or your system password.
- Instant access with no signup or personal info
- Perfect match for Lightning’s low-cost, no-middleman model
One Note of Caution
While the system is impressive and genuinely different from anything I’ve seen, the project is still early and niche. The website and team aren’t as well-known as major VPN providers. So use it like any experimental tool—test it, learn from it, but don’t put all your trust in one basket yet.
Final Thoughts
In a world where online tracking is getting creepier and centralized control is tightening, SimplifiedPrivacy.com is pushing in the opposite direction: easy, user-controlled privacy with zero setup and lightning-fast access.
If you’ve got a dollar and a need for a little online invisibility, this might be one of the best ways to spend your sats.
-
 @ 31a4605e:cf043959
2025-06-17 17:00:03
@ 31a4605e:cf043959
2025-06-17 17:00:03Bitcoin funciona através de um sistema descentralizado que depende de um processo chamado mineração para validar transações e garantir a segurança da rede. no entanto, a mineração de Bitcoin exige uma grande quantidade de energia, o que levanta preocupações sobre o seu impacto ambiental. embora existam soluções para tornar este processo mais sustentável, o consumo energético continua a ser um tema debatido tanto por críticos como por defensores da tecnologia.
Como funciona a mineração de Bitcoin?
A mineração de Bitcoin é o processo pelo qual novos blocos são adicionados à blockchain ou timechain e novas moedas são criadas. este processo utiliza um mecanismo chamado proof-of-work (prova de trabalho), onde computadores especializados (miners) competem para resolver problemas matemáticos complexos. para isso, consomem uma enorme quantidade de eletricidade, pois os equipamentos precisam de funcionar continuamente para garantir que a rede se mantém segura e descentralizada.
O consumo de energia e o impacto ambiental
A principal crítica à mineração de Bitcoin está relacionada com o elevado consumo de eletricidade. atualmente, estima-se que a rede Bitcoin consome tanta energia quanto alguns países inteiros. este consumo gera preocupações ambientais, pois grande parte da eletricidade mundial ainda é produzida a partir de combustíveis fósseis, que emitem gases poluentes.
Os impactos ambientais da mineração de Bitcoin incluem:
Emissões de carbono: se a eletricidade utilizada para a mineração vier de fontes poluentes, o processo contribui para o aumento das emissões de CO₂, intensificando o aquecimento global.
Uso excessivo de recursos naturais: a mineração em grande escala pode sobrecarregar redes elétricas locais e aumentar a procura por eletricidade, levando a um maior consumo de combustíveis fósseis em algumas regiões.
Produção de resíduos eletrónicos: os equipamentos de mineração têm um tempo de vida útil relativamente curto, o que leva à produção de grandes quantidades de lixo eletrónico.
Alternativas e soluções sustentáveis
Apesar das preocupações, a mineração de Bitcoin está a tornar-se cada vez mais eficiente e sustentável. muitas operações de mineração já utilizam fontes de energia renovável, como hidrelétrica, solar e eólica, reduzindo significativamente a pegada ecológica. algumas soluções incluem:
Uso de energia renovável: miners estão a mudar-se para regiões onde há excesso de produção de energia renovável, aproveitando recursos que, de outra forma, seriam desperdiçados.
Reciclagem de calor gerado pela mineração: algumas empresas estão a utilizar o calor produzido pelos equipamentos de mineração para aquecer edifícios e infraestruturas, aproveitando a energia de forma mais eficiente.
Inovações tecnológicas: o desenvolvimento de novos chips e equipamentos mais eficientes reduz o consumo energético da mineração sem comprometer a segurança da rede.
Resumindo, o impacto ambiental da mineração do Bitcoin é um tema controverso, mas as soluções para tornar o processo mais sustentável estão a evoluir rapidamente. embora o consumo energético continue elevado, a transição para fontes de energia renovável e novas tecnologias pode tornar Bitcoin um sistema mais eficiente e amigo do ambiente. assim, a questão não é apenas o consumo de eletricidade, mas sim a origem dessa energia e as inovações que tornam a mineração cada vez mais sustentável.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:54:26
@ 31a4605e:cf043959
2025-06-17 17:54:26Bitcoin, desde a sua criação, tem sido um dos ativos mais debatidos no mundo financeiro, tanto pelos seus seguidores apaixonados quanto pelos céticos. A sua volatilidade extrema e o impacto que tem causado no sistema financeiro tradicional tornaram-no objeto de especulação constante. À medida que o tempo passa, a adoção de Bitcoin cresce e surgem novas discussões sobre o seu futuro, tanto no que diz respeito ao seu preço quanto à sua integração no sistema financeiro global. Neste contexto, existem várias previsões para o futuro de Bitcoin, com cenários tanto otimistas quanto cautelosos, baseados em fatores como regulamentação, adoção institucional e inovação tecnológica.
O preço de Bitcoin: previsões e fatores de influência
Adoção Institucional: A crescente adoção de Bitcoin por grandes empresas e investidores institucionais tem sido vista como um fator de valorização. Organizações como Tesla, MicroStrategy e Square já incorporaram Bitcoin nas suas reservas de tesouraria, o que gerou uma maior confiança no ativo como uma reserva de valor. À medida que mais empresas sigam esse caminho, a demanda por Bitcoin pode aumentar, pressionando o preço para cima.
Regulação Governamental: A forma como os governos lidam com Bitcoin é um dos maiores fatores de incerteza. Uma regulação excessiva pode restringir o acesso e diminuir o interesse, enquanto uma abordagem mais amigável pode impulsionar a adoção e aumentar o preço. Em países como El Salvador, que adotaram o Bitcoin como moeda legal, observa-se uma tendência positiva, mas em muitas outras nações, a regulação ainda é um grande desafio.
Oferta Limitada: A oferta de Bitcoin é limitada a 21 milhões de unidades, o que significa que não há risco de inflação ou aumento da quantidade disponível. Este facto torna Bitcoin particularmente atraente como reserva de valor, especialmente em tempos de incerteza económica global, o que pode continuar a impulsionar a sua valorização a longo prazo.
Tecnologia e Escalabilidade: Inovações como a Lightning Network e o Taproot, que visam melhorar a escalabilidade e a eficiência das transações, podem contribuir para uma adoção mais ampla, o que, por sua vez, poderia ter um impacto positivo no preço. Se Bitcoin se tornar mais acessível e viável para transações diárias, a sua utilidade será mais valorizada no mercado.
Adoção global do Bitcoin: o caminho para a inclusão financeira
A adoção global de Bitcoin está a crescer, especialmente em regiões onde os sistemas financeiros tradicionais são ineficazes ou limitados. Países com economias instáveis, como nações com alta inflação ou crise cambial, estão cada vez mais a ver no Bitcoin uma alternativa viável. Além disso, a inclusão financeira é um dos maiores motores dessa adoção, uma vez que Bitcoin pode oferecer serviços financeiros a populações que estão fora do alcance dos bancos tradicionais.
Mercados Emergentes: Em países como o Brasil, Argentina, Nigéria e outros mercados emergentes, a procura por Bitcoin tem crescido, pois as pessoas procuram proteger os seus ativos da desvalorização das suas moedas locais. Nesses locais, Bitcoin surge como uma alternativa de reserva de valor e meio de troca que não está sujeita ao controlo de uma autoridade central.
Adoção por Governos e Empresas: A crescente aceitação de Bitcoin por grandes empresas e governos pode acelerar a sua integração nas economias globais. Países como El Salvador demonstraram que é possível adotar Bitcoin como uma moeda oficial, enquanto grandes empresas estão cada vez mais a aceitar Bitcoin como forma de pagamento, o que legitima ainda mais o seu uso no comércio global.
Educação e Acessibilidade: A medida que mais pessoas compreendem o funcionamento do Bitcoin e as suas vantagens em termos de segurança, privacidade e liberdade financeira, a adoção tende a crescer. A simplicidade das plataformas de exchange e as melhorias em termos de usabilidade das carteiras digitais tornam mais fácil para os utilizadores entrarem no mercado e utilizarem Bitcoin no seu dia a dia.
Cenários futuros: otimismo ou cautela?
O futuro do Bitcoin é incerto, mas diversos cenários podem se desenrolar. O cenário otimista aponta para uma maior valorização e adoção global, impulsionada pela inovação tecnológica, aumento da confiança institucional e a busca por uma alternativa descentralizada ao sistema financeiro tradicional. Nesse cenário, Bitcoin poderia tornar-se uma forma amplamente aceite de pagamento e uma reserva de valor global, com preços que poderiam ultrapassar os valores mais elevados já registados.
Por outro lado, o cenário cauteloso sugere que os obstáculos como regulação governamental, competição com outras moedas digitais e possíveis falhas tecnológicas podem impedir que o Bitcoin se torne uma parte central do sistema financeiro. Além disso, a volatilidade do preço pode desencorajar aqueles que buscam estabilidade e segurança.
Resumindo, as previsões sobre o preço e a adoção global de Bitcoin são, sem dúvida, complexas e influenciadas por vários fatores. O futuro do Bitcoin dependerá de como a sociedade, os governos e as empresas responderão a essa nova forma de dinheiro. Embora o potencial de valorização seja significativo, o risco e a volatilidade são características que não podem ser ignoradas. À medida que a adoção global cresce e a tecnologia evolui, será necessário acompanhar de perto os desenvolvimentos que irão moldar o futuro de Bitcoin no sistema financeiro global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 16:31:03
@ 31a4605e:cf043959
2025-06-17 16:31:03O Bitcoin tem revolucionado a forma como as pessoas realizam transações financeiras em todo o mundo. Sendo uma moeda digital descentralizada, oferece novas oportunidades para pagamentos no comércio eletrónico e transferências internacionais de dinheiro. A sua rapidez, segurança e baixos custos tornam-no uma alternativa eficiente aos métodos tradicionais, eliminando intermediários e facilitando transações globais.
Bitcoin no comércio eletrónico
O comércio eletrónico tem crescido exponencialmente, e o Bitcoin surge como uma solução inovadora para pagamentos online. Grandes retalhistas e pequenas empresas estão a começar a aceitar Bitcoin como forma de pagamento, oferecendo benefícios tanto para os comerciantes como para os consumidores.
Vantagens do Bitcoin para o comércio eletrónico:
Baixas taxas de transação: ao contrário dos cartões de crédito e plataformas de pagamento que cobram taxas elevadas, as transações em Bitcoin apresentam, geralmente, custos mais reduzidos. Isto beneficia os comerciantes, que podem diminuir despesas e oferecer preços mais competitivos aos clientes.
Eliminação de chargebacks: no sistema tradicional, os chargebacks (reembolsos forçados pelos bancos ou operadoras de cartão) representam uma preocupação para os lojistas. Como as transações em Bitcoin são irreversíveis, os comerciantes evitam fraudes e disputas.
Acesso global: qualquer pessoa com acesso à Internet pode pagar com Bitcoin, independentemente da sua localização. Isto permite às empresas expandirem o seu mercado internacionalmente, sem depender de bancos ou sistemas de pagamento locais.
Privacidade e segurança: as transações em Bitcoin protegem a identidade do utilizador, oferecendo maior privacidade em comparação com pagamentos através de cartão de crédito ou transferências bancárias. Além disso, como não há necessidade de partilhar dados pessoais, o risco de roubo de informações é reduzido.
Desafios do Uso do Bitcoin no Comércio Eletrónico:
Volatilidade: o preço do Bitcoin pode oscilar rapidamente, o que dificulta a fixação de preços para produtos e serviços. No entanto, alguns comerciantes utilizam serviços de pagamento que convertem automaticamente Bitcoin em moeda fiduciária, minimizando esse risco.
Adoção limitada: apesar do crescimento, a aceitação do Bitcoin ainda não é universal. Muitas lojas e plataformas populares ainda não o adotaram, o que pode dificultar a sua utilização em compras diárias.
Tempo de confirmação: embora o Bitcoin seja mais rápido do que as transferências bancárias tradicionais, o tempo de confirmação pode variar consoante a taxa de rede paga. Algumas soluções, como a Lightning Network, estão a ser desenvolvidas para tornar os pagamentos instantâneos.
Bitcoin na remessa de dinheiro
O envio de dinheiro para o estrangeiro sempre foi um processo burocrático, dispendioso e demorado. Serviços tradicionais, como os bancos e empresas de transferência de dinheiro, cobram taxas elevadas e podem demorar dias a concluir uma transação. O Bitcoin, por outro lado, oferece uma alternativa eficiente para remessas globais, permitindo que qualquer pessoa envie e receba dinheiro de forma rápida e económica.
Benefícios do Bitcoin para remessas:
Custos reduzidos: enquanto os bancos e empresas como a Western Union cobram elevadas taxas para transferências internacionais, o Bitcoin permite o envio de dinheiro com custos mínimos, independentemente do montante ou do destino.
Velocidade nas transações: as transferências bancárias internacionais podem demorar vários dias a serem concluídas, especialmente em países com uma infraestrutura financeira limitada. Com o Bitcoin, o dinheiro pode ser enviado para qualquer parte do mundo em poucos minutos ou horas.
Acessibilidade global: em regiões onde o sistema bancário é restrito ou ineficiente, o Bitcoin possibilita que as pessoas recebam dinheiro sem depender de bancos. Isto é particularmente útil em países em desenvolvimento, onde as remessas internacionais são uma fonte essencial de rendimento.
Independência de intermediários: o Bitcoin opera de forma descentralizada, sem necessidade de recorrer a bancos ou empresas de transferência. Isto significa que as pessoas podem enviar dinheiro diretamente para amigos e familiares sem intermediários.
Desafios das remessas com Bitcoin:
Conversão para moeda local: apesar de o Bitcoin poder ser recebido instantaneamente, muitas pessoas ainda precisam de convertê-lo em moeda local para o utilizar. Isso pode envolver custos adicionais e depender da disponibilidade de serviços de câmbio.
Adoção e conhecimento: nem todos compreendem o funcionamento do Bitcoin, o que pode dificultar a sua adoção generalizada para remessas. No entanto, a crescente educação financeira sobre o tema pode ajudar a ultrapassar essa barreira.
Regulamentação e restrições: alguns governos impõem restrições ao uso do Bitcoin, tornando as remessas mais complicadas. A evolução das regulamentações pode afetar a facilidade de uso em determinados países.
Resumindo, o Bitcoin está a transformar o comércio eletrónico e as remessas de dinheiro em todo o mundo. A sua capacidade de eliminar intermediários, reduzir custos e oferecer pagamentos rápidos e seguros torna-o uma alternativa viável aos sistemas financeiros tradicionais.
No comércio eletrónico, proporciona benefícios para lojistas e consumidores, reduzindo taxas e melhorando a privacidade. No setor das remessas, facilita a transferência de dinheiro para qualquer parte do mundo, especialmente para aqueles que vivem em países com sistemas bancários pouco eficientes.
Apesar dos desafios, a adoção do Bitcoin continua a crescer, impulsionada por soluções inovadoras e pelo reconhecimento do seu potencial como meio de pagamento global. À medida que mais empresas e indivíduos aderirem a esta tecnologia, a sua presença no comércio eletrónico e nas remessas internacionais será cada vez mais relevante.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:51:52
@ 31a4605e:cf043959
2025-06-17 17:51:52Com a crescente digitalização do dinheiro, os governos de vários países começaram a desenvolver moedas digitais de banco central (CBDCs - Central Bank Digital Currencies) como resposta à popularização de Bitcoin. Enquanto Bitcoin representa um sistema financeiro descentralizado e resistente à censura, as CBDCs são versões digitais das moedas fiduciárias, controladas diretamente pelos bancos centrais. Essa concorrência pode moldar o futuro do dinheiro e definir o equilíbrio entre liberdade financeira e controlo estatal.
Diferenças fundamentais entre Bitcoin e CBDCs
Bitcoin e as CBDCs diferem em praticamente todos os aspetos fundamentais:
Centralização vs. Descentralização: Bitcoin opera numa rede descentralizada, onde nenhum governo ou entidade pode alterar as regras ou censurar transações. Já as CBDCs são emitidas e controladas pelos bancos centrais, permitindo um maior controlo sobre a circulação e utilização do dinheiro.
Oferta limitada vs. Inflação controlada: Bitcoin tem uma oferta fixa de 21 milhões de unidades, tornando-se um ativo escasso e deflacionário. As CBDCs, por outro lado, podem ser criadas sem limites, como acontece com as moedas fiduciárias tradicionais, sujeitas a políticas monetárias inflacionárias.
Privacidade vs. Monitorização: Bitcoin permite transações pseudónimas, garantindo um certo nível de privacidade financeira. As CBDCs, no entanto, podem ser programadas para permitir o rastreamento total de cada transação, facilitando a supervisão governamental e, potencialmente, o controlo sobre o que os cidadãos podem ou não gastar.
Resistência à censura vs. Controlo estatal: Bitcoin permite que qualquer pessoa realize transações sem depender de aprovação de terceiros. As CBDCs, por serem centralizadas, podem ser usadas pelos governos para restringir transações indesejadas ou mesmo confiscar fundos com um simples comando digital.
O que os governos pretendem com as CBDCs?
A introdução das CBDCs tem sido vendida com argumentos como:
Maior eficiência nas transações financeiras, eliminando intermediários e reduzindo custos bancários.
Facilidade na implementação de políticas económicas, como estímulos diretos à população ou tributação automatizada.
Combate a atividades ilegais, dado que as transações podem ser rastreadas em tempo real.
No entanto, muitas destas justificações levantam preocupações sobre a perda de privacidade financeira e o aumento do poder dos governos sobre o sistema monetário.
Bitcoin como alternativa às CBDCs
A ascensão das CBDCs pode fortalecer a posição de Bitcoin como alternativa de dinheiro verdadeiramente livre. À medida que os cidadãos percebem os riscos de um sistema financeiro 100% controlado pelo Estado, a procura por um ativo descentralizado e resistente à censura pode crescer.
Proteção contra o controlo estatal: Bitcoin permite que os utilizadores mantenham total soberania sobre o seu dinheiro, sem o risco de bloqueios arbitrários ou confiscações.
Preservação da privacidade financeira: Ao contrário das CBDCs, que podem monitorizar todas as transações, Bitcoin oferece um grau de anonimato que protege os indivíduos da vigilância excessiva.
Reserva de valor contra a inflação: Enquanto os governos podem emitir CBDCs indefinidamente, Bitcoin mantém a sua escassez garantida, tornando-se um refúgio contra políticas monetárias irresponsáveis.
Resumindo, a competição entre Bitcoin e as CBDCs será uma das maiores batalhas financeiras do futuro. Enquanto os governos tentam consolidar o seu controlo através de moedas digitais centralizadas, Bitcoin continua a ser a principal alternativa para aqueles que procuram independência financeira e proteção contra a vigilância estatal. A escolha entre um sistema financeiro livre e um sistema monitorizado e controlado poderá definir o rumo da economia digital nas próximas décadas.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ b1ddb4d7:471244e7
2025-06-18 17:02:18
@ b1ddb4d7:471244e7
2025-06-18 17:02:18In a quiet corner of the world, bitcoin mining operations in Africa are turning electricity into digital currency and in the process, redefining how value is created.
At its core, bitcoin mining involves validating transaction information before adding new blocks to the Bitcoin blockchain by competing to solve a cryptographic puzzle that meets a specific criterion.
Globally, mining plays a key role in keeping the blockchain decentralized and secure. The system depends on miners to verify and record transactions, mainly to prevent a problem called double spending, the digital version of using the same money twice.
To understand this better, imagine Charles sends $5 to Amanda. With physical cash, Amanda can trust the note is real and hasn’t been used elsewhere. But with digital currency, copying data is easy, so how can she be sure that the same $5 wasn’t sent to someone else too? That’s the exact problem Bitcoin mining helps solve.
In recent years, Africa has started to draw attention in this space, positioning itself as a key hub in global bitcoin mining. While there may be less than 2 million bitcoin left to be mined from the total 21 million supply, the rise of mining operations in Africa has sparked excitement, creating new jobs and drawing in foreign capital.
Although some countries still grapple with power shortages and the energy demands of mining, many citizens view bitcoin as a more stable store of value and a safeguard against the volatility of their local currencies.
At the same time, Africa’s wealth of hydro, solar, wind, and geothermal resources makes the continent one of the most promising regions for cost-effective and sustainable mining.
What Makes a Large-Scale Bitcoin Mining Operation in Africa?
It all starts with difficulty. Bitcoin mining isn’t just about solving a puzzle, it’s about solving one that keeps getting harder. Mining difficulty refers to how much computational work is needed to generate a number lower than the target hash.
This difficulty automatically adjusts every 2,016 blocks (about every two weeks), depending on how quickly miners solved the previous batch. If mining is fast and efficient, the network increases the difficulty; if miners drop off and block times slow, it reduces it, all to maintain a consistent block production time of roughly 10 minutes.
The significance of mining difficulty lies in the increased demands it places on mining operations. As difficulty rises, miners require more powerful hardware, cost-effective energy sources, advanced infrastructure, and substantial financial investment. These requirements distinguish large-scale mining operations from smaller, casual miners.
In short, it’s the difficulty of mining that births the need for large facilities, massive energy inputs, industrial-grade hardware, and significant financial investment, the very traits that define a “large” bitcoin mining operation.
This leads us to the 4 key factors that define large Bitcoin mining operations in Africa, each one a direct response to the growing demands of the network:
1. Facility size and infrastructure:
The physical size of a mining facility is a direct reflection of its capacity to house mining equipment and support systems. Larger operations typically have thousands of mining rigs installed, supported by extensive infrastructure such as advanced cooling systems and stable power supplies.
These are critical to ensure that the equipment runs continuously and efficiently, given the intense heat and electricity demands of mining.
While it is possible to mine Bitcoin using desktop computers or gaming rigs by joining mining pools, these setups are limited in profitability. Mining pools distribute rewards based on the computational power contributed, meaning small or less efficient machines earn only modest returns.
To compete effectively, mining operations invest in specialized hardware known as Application-Specific Integrated Circuit (ASIC) miners. These machines are far more powerful and energy-efficient than regular computers but require significant capital investment, with prices ranging from $4,000 to $12,000 per rig depending on their performance.
Large-scale operations typically deploy hundreds or thousands of these ASIC miners, which necessitates the large facilities and sophisticated infrastructure mentioned earlier. In this way, the size of the facility and the sophistication of the mining equipment are tightly linked, together defining the overall scale and capability of a bitcoin mining operation.
2. Hashrate contribution:
Hashrate refers to the computational power used to mine and process transactions on the Bitcoin network. A higher hashrate indicates a more significant contribution to the network’s security and transaction processing.
Large mining operations often possess substantial hashrate, measured in exa hashes per second (EH/s). For instance, as of July 2024, the Bitcoin network’s hashrate was approximately 733.41 EH/s.
3. Energy consumption and power source:
Bitcoin mining is energy-intensive. The total energy consumption of the Bitcoin network has been estimated at 175.87 terawatt-hours annually, comparable to the power consumption of Poland. Large mining operations often seek locations with access to cheap and reliable energy sources, such as hydroelectric, solar, or wind power, to reduce operational costs and environmental impact.
4. Financial banking and investor interest:
Significant financial investment is required to establish and maintain large-scale mining operations. This includes the cost of mining hardware, facility construction, energy procurement, and operational expenses. Companies with substantial financial backing can invest in cutting-edge technology and infrastructure, enhancing their mining capabilities.
Overview of Bitcoin Mining in Africa
Africa is beginning to carve out its share of the global Bitcoin mining market, which was valued at $2.45 billion in 2024 and is projected to reach $8.24 billion by 2034.
As Bitcoin’s value continues to rise, countries across the continent are positioning themselves to benefit, many by tapping into abundant renewable energy sources and taking advantage of regulatory ambiguity or excess energy production.
Ethiopia currently leads the continent in Bitcoin mining activity, with around 2.5% of the global hashrate reportedly coming from operations powered entirely by renewable energy.
This energy mismatch has attracted major miners from China and other regions, who see an opportunity to monetize surplus electricity. Ethiopia’s success showcases how renewable energy and mining can coexist sustainably while contributing meaningfully to state revenue.
Kenya follows closely behind. As the top geothermal energy producer in Africa, with an installed capacity of 863 MW, the country is using its energy advantage to support sustainable mining.
Nigeria is emerging as a serious contender. While not yet dominant, its large population, increasing tech engagement, and growing interest in using flared gas for mining signal potential for expansion. Nigeria’s complex but evolving regulatory landscape also leaves room for further mining developments as the government explores clearer crypto frameworks.
Malawi represents a more localized model of Bitcoin mining. By converting rainfall-powered microgrids into revenue-generating infrastructure, Malawi shows how small-scale mining can play a powerful role in community development and rural electrification.
In Libya, Bitcoin mining is technically illegal, but that hasn’t stopped it. Despite the ban, underground mining continues to thrive thanks to heavily subsidized electricity. In 2021, Libyan miners accounted for an estimated 0.6% of the global Bitcoin production, the highest in both the Arab world and Africa at the time. Today, mining reportedly consumes around 2% of the country’s electricity, even as it operates in the shadows.
Angola rounds out the list with limited public data but notable potential. The country struggles with energy inefficiencies, losing nearly 40% of its hydroelectric power during transmission. Some reports suggest Bitcoin miners are beginning to capitalize on this otherwise stranded energy, though large-scale operations are yet to surface.
What unites these countries is a shared set of conditions: untapped or mismanaged energy resources, an openness or gray area in regulation, and the growing understanding that Bitcoin mining can serve as a financial incentive to build and stabilize decentralized energy systems.
Whether through massive hydroelectric projects or rural microgrids, Bitcoin mining is emerging as both an energy monetization strategy and a bridge to infrastructure development across Africa.
Profiles of the Largest Bitcoin Mining Operations in Africa
1. BitCluster (Ethiopia)
As of 2024, Bitcoin mining in Africa is largely concentrated in
-
 @ 000002de:c05780a7
2025-06-18 16:41:41
@ 000002de:c05780a7
2025-06-18 16:41:41By this all people will know that you are my disciples, if you have love for one another.”
I've been meditating on these words from our savior since Easter. In these times I need to remind myself of this pretty much every day.
https://stacker.news/items/1009542
-
 @ cae03c48:2a7d6671
2025-06-17 15:00:39
@ cae03c48:2a7d6671
2025-06-17 15:00:39Bitcoin Magazine

Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or CustodyFlash, a Bitcoin payment platform, just announced it has launched Flash Invoicing, a completely free, non-custodial, and KYC-free Bitcoin invoicing tool. Designed for freelancers, the platform allows users to send professional invoices without platform fees, identity checks, or third party custody.

According to Deel, a crypto payments company for freelancers, Bitcoin is the most used cryptocurrency in the world for payments. Despite this growth, many freelancers continue to use basic methods such as pasting Bitcoin addresses into PDFs or emails. Some rely on custodial platforms that deduct fees or require identity verification, which can affect both earnings and data privacy.
“We’ve seen too many people paste BTC addresses into documents and call it invoicing,” said the CEO of Flash Pierre Corbin. “It’s messy. It’s risky. And it’s time for something better.”
Flash Invoicing Features:
- 0% platform fees: no subscriptions or commission
- Non-custodial: Bitcoin goes straight to the user’s wallet
- No KYC: users maintain full privacy
- Professional output: branded PDFs and secure payment links
- Integrated dashboard: manage payments, clients, and revenue
- Works with Flash ecosystem: including Stores, Donations, Paywalls, and POS
Many Bitcoin invoicing tools charge a percentage per transaction or require a subscription. As a result, freelancers often lose part of their income simply to issue an invoice and receive payment. Flash is aiming to solve this issue.
“Freelancers work hard enough. The last thing they need is a platform skimming off their earnings,” said Corbin. “That’s why we dropped our fee from 1.5% to 0% — and launched the first invoicing tool that’s truly free, without compromising on privacy or control.”

Flash Invoicing allows users to accept Bitcoin payments without relinquishing control, privacy, or revenue. It is integrated with the broader Flash suite, enabling users to manage invoicing alongside features such as setting up stores, receiving donations, or gating premium content.
“As a freelancer myself, I love using the Flash invoicing feature,” stated a freelancer & Flash user. ”It keeps all my clients in one place, allows me to easily edit invoices and track payments. Much more professional than sending a lightning address in the footer of a PDF invoice.”
This post Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or Custody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 8bad92c3:ca714aa5
2025-06-18 22:01:50
@ 8bad92c3:ca714aa5
2025-06-18 22:01:50Marty's Bent
via me

I had a completely different newsletter partially written earlier tonight about whether or not "this cycle is different" when this nagging thought entered my head. So I'm going to write about this and maybe I'll write about the dynamics of this cycle compared to past cycles tomorrow.
A couple of headlines shot across my desk earlier tonight in relation to the potential escalation of kinetic warfare in the Middle East. Apparently the U.S. Embassy in Iraq was sent a warning and evacuation procedures were initiated. Not too long after, the world was made aware that the United States and Israel are contemplating an attack on Iran due to the "fact" that Iran may be close to producing nuclear weapins. The initial monkey brain reaction that I had to these two headlines was, "Oh shit, here we go again. We're going to do something stupid." My second reaction was, "Oh shit, here we go again, I've seen these two exact headlines many times over the years and they've proven to be lackluster if you're a doomer or blood thirsty war monger." Nothing ever happens.
As I venture into my mid-30s and reflect on a life filled with these types of headlines and my personal reactions to these headlines, I'm finally becoming attuned to the fact that the monkey brain reactions aren't very productive at the end of the day. Who knows exactly what's going to happen in Iraq or Iran and whether or not kinetic warfare escalates and materializes from here? Even though I'm a "blue-blooded taxpaying American citizen" who is passively and unwillingly contributing to the war machine and the media industrial complex, there's really nothing I can do about it.
The only thing I can do is focus on what is in front of me. What I have control of. And attempt to leverage what I have control of to make my life and the life of my family as good as humanly possible. Ignoring the external and turning inward often produces incredible results. Instead of worrying about what the media wants you to believe at any given point in time, you simply look away from your computer screen, survey the physical space which you're operating in and determine what you have, what you need and how you can get what you need. This is a much more productive way to spend your time.
This is what I want to touch on right now. There's never been a better time in human history to be productive despite what the algorithm on X or the mainstream media will lead you to believe. Things aren't as great as they could be, but they're also not as bad as you're being led to believe. We live in the Digital Age and the Digital Age provides incredible resources that you can leverage to make YOUR life better.
Social media allows you to create a platform without spending any money. AI allows you to build tools that are beneficial to yourself and others with very little money. And bitcoin exists to provide you with the best form of money that you can save in with the knowledge that your relative ownership of the overall supply isn't going to change. No matter what happens in the external world.
If you can combine these three things to make your life better and - by extension - potentially make the lives of many others better, you're going to be well off in the long run. Combining these three things isn't going to result in immediate gratification, but if you put forth a concerted effort, spend the time, have some semblance of patience, and stick with it, I truly believe that you will benefit massively in the long run. Without trying to sound like a blowhard, I truly believe that this is why I feel relatively calm (despite my monkey brain reactions to the headlines of the day) at this current point in time.
We've entered the era of insane leaps in productivity and digital hard money that cannot be corrupted. The biggest mistake you can make in your life right now is overlooking the confluence of these two things. With an internet connection, an idea, some savvy, and hard work you can materially change your life. Create something that levels up your knowledge, that enables you to get a good job in the real world, or to create a company of your own. Bring your talents to the market, exchange them for money, and then funnel that money into bitcoin (if you're not being paid in it already). We may be at the beginning of a transition from the high velocity trash economy to the high leverage agency economy run on sound money and applied creativity.
These concepts are what you should be focusing most of your time and attention to today and in the years ahead. Don't get distracted by the algorithm, the 30-second video clips, the headlines filled with doom, and the topics of the 24 hour news cycle. I'll admit, I often succumb to them myself. But, as I get older and develop a form of pattern recognition that can only be attained by being on this planet for a certain period of time, it is becoming very clear that those things are not worth your attention.
Living by the heuristic that "nothing ever happens" is a pretty safe bet. Funnily enough, it's incredibly ironic that you're led to believe that something is happening every single day, and yet nothing ever happens. By getting believing that something happens every day you are taking your attention away from doing things that happen to make your life better.
Tune out the noise. Put on the blinders. Take advantage of the incredible opportunities that lie before you. If enough of you - and many others who do not read this newsletter - do this, I truly believe we'll wake up to find that the world we live in is a much better place.
Nothing ever happens, so make something happen.
Intelligence Officials Are Quietly Becoming Bitcoin Believers
Ken Egan, former CIA Deputy Chief of Cyber Operations, revealed a surprising truth on TFTC: the intelligence community harbors numerous Bitcoin advocates. Egan explained that intelligence professionals uniquely understand how governments weaponize financial systems through sanctions and account freezing. Having wielded these tools themselves, they recognize the need for personal financial sovereignty. He shared compelling anecdotes of discovering colleagues with "We are all Satoshi" stickers and a European chief of station paying for dinner with a BlockFi card to earn Bitcoin rewards.
"I think there are a lot of Bitcoiners, not just at CIA, but across the whole national security establishment... they're in it for the exact same reasons everybody else is." - Ken Egan
The Canadian trucker protests served as a pivotal moment, Egan noted. Watching Western governments freeze citizens' bank accounts for political dissent struck a nerve among intelligence professionals who previously viewed financial weaponization as a tool reserved for foreign adversaries. This awakening has created unlikely allies within institutions many Bitcoiners distrust.
Check out the full podcast here for more on Bitcoin's national security implications, privacy tech prosecutions, and legislative priorities.
Headlines of the Day
Stripe Buys Crypto Wallet Privy After Bridge Deal - via X
Trump Calls CPI Data "Great" Urges Full Point Fed Cut - via X
Bitcoin Hashrate Reaches New All-Time High - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Life is good.
Download our free browser extension, Opportunity Cost: https://www.opportunitycost.app/ start thinking in SATS today.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; p
-
 @ 31a4605e:cf043959
2025-06-17 16:46:45
@ 31a4605e:cf043959
2025-06-17 16:46:45Bitcoin é conhecido pela sua forte volatilidade, com oscilações de preço que podem ocorrer em curtos períodos de tempo. Esta característica atrai tanto investidores que procuram grandes lucros como também afasta aqueles que preferem ativos mais estáveis. A volatilidade do preço de Bitcoin tem um impacto significativo no mercado, influenciando estratégias de investimento, adoção e até a perceção pública da moeda digital.
O que causa a volatilidade do preço de Bitcoin?
A volatilidade de Bitcoin deve-se a vários fatores que afetam a sua oferta e procura. entre os principais motivos estão:
Oferta limitada e halving: Bitcoin tem um fornecimento máximo de 21 milhões de unidades, o que cria escassez. além disso, o halving, que reduz a emissão de novos Bitcoins a cada quatro anos, pode provocar aumentos de preço devido à redução da oferta.
Especulação no mercado: muitos investidores compram e vendem Bitcoin para obter lucros rápidos, criando grandes flutuações no preço. movimentos especulativos, muitas vezes impulsionados por notícias e redes sociais, podem causar variações bruscas.
Eventos económicos e regulamentação: decisões governamentais, como proibições ou regulamentações favoráveis, afetam diretamente o preço. declarações de bancos centrais ou figuras influentes no setor financeiro podem também gerar fortes reações no mercado.
Liquidez e volume de negociação: o mercado de Bitcoin ainda é pequeno comparado a ativos tradicionais, como o ouro ou ações. isto significa que grandes ordens de compra ou venda podem causar oscilações significativas.
Impacto nos investidores e “investidores“
A volatilidade do preço de Bitcoin afeta diferentes tipos de investidores de formas distintas:
Investidores de curto prazo: traders que fazem operações diárias tentam lucrar com as flutuações de preço. no entanto, este tipo de estratégia envolve altos riscos e pode resultar em perdas significativas para quem não tem experiência no mercado.
Investidores de longo prazo (HODLers): quem investe com uma perspetiva a longo prazo costuma ignorar as variações diárias e foca-se no potencial de valorização de Bitcoin ao longo dos anos. apesar das quedas temporárias, muitos acreditam que o preço continuará a subir devido à escassez e à adoção crescente.
Empresas e instituições: empresas que investem em Bitcoin como reserva de valor, como a MicroStrategy e a Tesla, precisam de gerir os riscos da volatilidade. algumas optam por estratégias que minimizam a exposição direta a grandes oscilações.
Como lidar com a volatilidade?
Apesar dos desafios, existem formas de lidar com a volatilidade de Bitcoin de forma estratégica:
Diversificação da carteira: em vez de investir todo o capital em Bitcoin, muitos investidores diversificam para reduzir o impacto das oscilações de preço.
Investimento recorrente: estratégias como "dollar-cost averaging" (compra recorrente e fracionada) ajudam a suavizar os efeitos da volatilidade, reduzindo o risco de comprar numa alta momentânea.
Uso de armazenamento seguro: em vez de deixar Bitcoin em corretoras, que podem ser vulneráveis a ataques e manipulações de mercado, a auto-custódia em carteiras seguras protege o investimento a longo prazo.
Resumindo, a volatilidade do Bitcoin é uma das suas principais características e influencia tanto o comportamento dos “investidores” como a sua adoção em larga escala. Enquanto pode representar oportunidades para grandes lucros, também envolve riscos consideráveis, exigindo estratégias bem definidas para minimizar perdas. Com o tempo o Bitcoin amadurece e mais investidores institucionais entram no mercado, a volatilidade pode reduzir-se, tornando-o ainda mais atrativo como reserva de valor.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ a53364ff:e6ba5513
2025-06-18 18:22:54
@ a53364ff:e6ba5513
2025-06-18 18:22:54Run Knots…
Knots helps you exercise your self sovereignty verification muscle, instead of conforming to the TrustMeBro defaults of core. Thus, you are more prepared to actively defend Bitcoin in case of hardfork-softfork or other shenanigan’s.
Knots is more feature rich and useful than core, allowing end users to finely tune their nodes mempool policy to reject spam transactions from their own mempools, through such bitcoin.conf settings as: rejectparasites=1 , datacarrier=0, permitbaremultisig=0
Running a Underdog Bitcoin Client makes the Bitcoin network more robust as a whole. Supporting an ecosystem of multiple compatible clients running in tandem. Running knots makes Bitcoin, the network more robust, and makes the bitcoin development ecosystem richer. Knots is a backup-option in case core becomes obviously compromised. For decentralization, do we really want only a single implementation, with all our eggs in one basket with just bitcoin core? No.
Knots makes it so that you’re not using your node’s computing resources to hold and process spam shitcoin transactions and you have better control over what transactions you prioritize processing.” — Thus you can save your mempool resources from being abused by bad actors with Knots, but not with core, unfortunately. Core doesn’t believe in giving their end users too much choice. This has long been their attitude: to dictate down and deny non-consensus violating choice to end users.
Thus running Knots is a counter movement to the unfortunate attitude in core that has willfully neglected a core subset of it’s users who care about spam filters. Running Knots is not just a technical improvement in running Bitcoin. It’s a political statement in the Bitcoin development ecosystem.
-
 @ 31a4605e:cf043959
2025-06-17 16:40:37
@ 31a4605e:cf043959
2025-06-17 16:40:37Bitcoin tem vindo a ganhar cada vez mais aceitação como meio de pagamento, deixando de ser apenas um ativo digital para investimento e tornando-se uma alternativa viável às moedas tradicionais. Atualmente, diversas empresas em todo o mundo já aceitam Bitcoin como forma de pagamento, proporcionando aos consumidores mais liberdade financeira e eliminando a necessidade de intermediários bancários.
Empresas globais que aceitam Bitcoin
Ao longo dos anos, várias empresas de renome começaram a aceitar Bitcoin, reconhecendo as suas vantagens, como a segurança, a transparência e as baixas taxas de transação. Entre as mais conhecidas, destacam-se:
Microsoft: a gigante da tecnologia permite que os utilizadores adicionem saldo às suas contas utilizando Bitcoin. isto permite a compra de produtos digitais, como jogos, aplicações e outros conteúdos disponíveis na Microsoft Store.
Overstock: um dos maiores retalhistas online que aceita Bitcoin para a compra de móveis, eletrodomésticos e artigos para casa. a empresa foi uma das pioneiras na adoção de Bitcoin, mostrando o seu compromisso com a inovação financeira.
AT&T: a operadora de telecomunicações dos Estados Unidos foi a primeira do setor a aceitar pagamentos em Bitcoin, permitindo que os seus clientes paguem faturas através deste meio digital.
Twitch: a popular plataforma de streaming de videojogos permite que os utilizadores façam doações e subscrições utilizando Bitcoin, incentivando a adoção desta moeda entre criadores de conteúdo.
Namecheap: um dos principais serviços de registo de domínios na internet aceita Bitcoin para a compra de domínios e serviços de alojamento web, demonstrando a aplicabilidade prática desta moeda no setor digital.
Pequenos negócios e comércio local
Para além das grandes empresas, muitos pequenos negócios e comerciantes locais já aceitam Bitcoin, especialmente em cidades que estão a tornar-se polos da economia digital.
Restaurantes e cafés: em cidades como Lisboa, Londres e Nova Iorque, alguns cafés e restaurantes aceitam Bitcoin como forma de pagamento, atraindo clientes que preferem pagar com esta tecnologia.
Hotéis e turismo: algumas redes hoteleiras e agências de viagens permitem o pagamento em Bitcoin, facilitando reservas e eliminando taxas cambiais para turistas internacionais.
Lojas online: muitos pequenos comerciantes na internet vendem produtos e serviços exclusivamente com Bitcoin, aproveitando a facilidade das transações digitais e a segurança da rede.
Vantagens para empresas e consumidores
O aumento da aceitação de Bitcoin deve-se aos benefícios que tanto empresas como consumidores obtêm ao utilizá-lo:
Menores taxas de transação: empresas evitam as altas comissões cobradas por bancos e serviços de pagamento tradicionais.
Eliminação de intermediários: transações são diretas entre comprador e vendedor, reduzindo burocracias e riscos de fraudes com cartões de crédito.
Acesso global: Bitcoin permite pagamentos internacionais sem necessidade de conversões cambiais, ideal para negócios online.
Resumindo, a adoção de Bitcoin como meio de pagamento continua a crescer, com empresas de todos os setores a reconhecerem as suas vantagens. à medida que mais negócios aderem a esta tecnologia, Bitcoin torna-se cada vez mais uma alternativa viável ao dinheiro tradicional. Apesar dos desafios de volatilidade e regulamentação, a tendência aponta para um futuro onde pagar com Bitcoin será algo comum no dia a dia.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 9ca447d2:fbf5a36d
2025-06-18 22:01:29
@ 9ca447d2:fbf5a36d
2025-06-18 22:01:29BlackRock’s iShares Bitcoin Trust (IBIT) has become the fastest exchange-traded fund (ETF) to ever reach $70 billion in assets under management (AUM).
The fund, which launched in January 2024, hit this milestone in just 341 trading days—five times faster than the previous record-holder, the SPDR Gold Shares ETF (GLD), which took 1,691 days to reach the same mark.
IBIT now holds over 662,000 BTC — iShares
Bloomberg ETF analyst Eric Balchunas tweeted on June 9, “IBIT just blew through $70 billion and is now the fastest ETF to ever hit that mark in only 341 days.” This is a big deal and shows bitcoin is going mainstream.
IBIT has beaten fastest growing ETFs in history — Eric Balchunas on X
The fund’s rapid growth means institutional investors are embracing bitcoin at scale.
The fund has $71.9 billion in AUM and holds over 662,000 bitcoin. This makes BlackRock the largest institutional bitcoin holder in the world. To put that in perspective, the fund holds more bitcoin than Binance or Michael Saylor’s Strategy.
“IBIT’s growth is unprecedented,” said Bloomberg analyst James Seyffart. “It’s the fastest ETF to reach most milestones, faster than any other ETF in any asset class.”
BlackRock’s bitcoin ETF isn’t just big. It’s also greatly outperforming other spot bitcoin ETFs launched at the same time. BlackRock’s brand and global client base gave the fund instant credibility.
Many institutional investors want a regulated and convenient way to get into bitcoin without holding the asset directly, and this fund has made it easy for them to invest.
Robert Mitchnick, BlackRock’s head of digital assets, told Yahoo Finance that bitcoin’s rising status as an inflation hedge and alternative store of value is driving IBIT’s popularity.
He explained bitcoin is becoming an inflation hedge and alternative store of value and that’s what’s driving the growth.
Eric Balchunas also noted that when BlackRock filed for IBIT, bitcoin was at $30,000 and there was still skepticism after the FTX blowup. Now that bitcoin is at $110,000, it is “seen as legitimate for other big investors.”
Institutional demand for bitcoin has never been stronger, with IBIT making up nearly 20% of all bitcoin held by public companies, private firms, governments, exchanges and decentralized finance platforms.
That dominance may soon be challenged as public companies prepare to buy more bitcoin and shake up the current supply distribution.
Matthew Sigel, VanEck’s head of digital assets research, shared data that six public companies plan to raise, or have raised, up to $76 billion to buy bitcoin. That’s more than half of the spot Bitcoin ETF industry’s current AUM, so there’s clearly interest beyond ETFs.
On the broader market, IBIT’s rise coincided with bitcoin’s price surge to new highs above $110,000. The inflows reflect investors’ confidence in Bitcoin’s future and desire for regulated exposure through traditional products.
It’s worth mentioning that IBIT also had over $1 billion in volume on its first day of trading. It’s now the largest ETF in BlackRock’s lineup, even bigger than gold funds and other popular ETFs tracking international equities.
-
 @ 8d34bd24:414be32b
2025-06-18 15:41:52
@ 8d34bd24:414be32b
2025-06-18 15:41:52As I read the news over the past week, we’ve heard of Ukrainian drone attacks on Russia’s nuclear attack planes and Russia’s threats of retaliation. We’ve heard of Israel attacking Iran’s nuclear facilities and Iran returning attacks on Israel’s major cities. I’ve read of AI taking jobs, threatening someone trying to turn it off, and refusing to turn off. There are threats of inflation, market crashes, housing crashes, and monetary crashes. There are riots across the US. There are warnings of potential new pandemics or of calls for terrorist cells to awaken and attack. It is easy to get overwhelmed by everything happening in the world. It is easy to become fearful of everything, but God does not call us to be afraid. He repeatedly tells us to “trust him” and to “fear not.”
Do not fear, for I am with you;\ Do not anxiously look about you, for I am your God.\ I will strengthen you, surely I will help you,\ Surely I will uphold you with My righteous right hand.’ (Isaiah 41:10)
With all of the crazy going on in the world, it is easy to worry about our jobs, our families, our country, and even our lives, but God does not want us to worry. He wants us to trust in Him in all things.
And He said to His disciples, “For this reason I say to you, do not worry about your life, as to what you will eat; nor for your body, as to what you will put on. For life is more than food, and the body more than clothing. Consider the ravens, for they neither sow nor reap; they have no storeroom nor barn, and yet God feeds them; how much more valuable you are than the birds! And which of you by worrying can add a single hour to his life’s span? If then you cannot do even a very little thing, why do you worry about other matters? Consider the lilies, how they grow: they neither toil nor spin; but I tell you, not even Solomon in all his glory clothed himself like one of these. But if God so clothes the grass in the field, which is alive today and tomorrow is thrown into the furnace, how much more will He clothe you? You men of little faith! And do not seek what you will eat and what you will drink, and do not keep worrying. For all these things the nations of the world eagerly seek; but your Father knows that you need these things. But seek His kingdom, and these things will be added to you. Do not be afraid, little flock, for your Father has chosen gladly to give you the kingdom. (Luke 12:22-32) {emphasis mine}
God provides for His own. He doesn’t always provide in the way we wish, but He does provide when we trust in Him. Even when believers die, He provides them a place in heaven.
When we look at the world around us, where everything seems like it is falling apart and/or turning to evil, we need to keep our eyes on Jesus and on eternity.
Therefore we do not lose heart, but though our outer man is decaying, yet our inner man is being renewed day by day. For momentary, light affliction is producing for us an eternal weight of glory far beyond all comparison, while we look not at the things which are seen, but at the things which are not seen; for the things which are seen are temporal, but the things which are not seen are eternal. (2 Corinthians 4:16-18) {emphasis mine}
What we experience here on earth may sometimes be unpleasant, but it is a “momentary, light affliction” compared to the glory of heaven. Just as labor and delivery of a child is hard and unpleasant, but is worth every effort and pain when you hold your child, in the same way our suffering on earth will seem like nothing compared to the joy of being in the presence of our Creator God and Savior.
My Experiences
I used to try to prepare for everything. When I was young, I would say, “a good Girl Scout is always prepared.” When I got married and had kids, I started trying to prepare for anything that might possibly go wrong. I had extra food, water, and medical supplies. I started a garden. I got chickens. I got rid of chickens when I developed a lung allergy and couldn’t breathe.
None of that was wrong in itself. I’d even argue it could be wise actions, but I was relying on myself and stuff to face the troubles of this world instead of relying on God. That was definitely not good and was not the way to peace.
We also got involved in politics. My husband was in the state legislature. I was a precinct person and involved in precinct, county, state, and national meetings. I helped set the platform for our state political party in two elections and helped set the resolutions in another.
None of that was wrong in itself. I’d even argue that Christians are called to be a blessing to our earthly nations, but it wasn’t the way to peace, nor was it putting my time in effort into the most important things.
I’ve been reading my Bible daily for 40+ years and reading the Bible in a year for 20+ years. For more than a decade I intensely studied the beginnings, Genesis and how science and archaeology support every fact in Genesis. That study really taught me the power of God and how He always keeps His promises.
For the past several years, I’ve switched to spending most of my intense study on end times prophecy. Despite the fact that the end times prophecies predict a time of unimaginable hardship, the promises of the rapture, the millennial kingdom, and eternity with Jesus in heaven brings great peace. The crazy, evil, and agony in the world is not the world falling apart, but God’s controlled, merciful judgment on the world. I can see the light at the end of the tunnel. I don’t just see everything that can possibly go wrong. I trust God with my life and that of my family.
I still have extra food, water, and medical supplies on hand, but I don’t obsess about it, nor do I put all my trust in my preparations. I still vote, but I have pulled back from political life. I have learned to trust Jesus in these difficult times. I try to be wise, but not worry about every thing that could possibly go wrong. I have gained peace.
But the Helper, the Holy Spirit, whom the Father will send in My name, He will teach you all things, and bring to your remembrance all that I said to you. Peace I leave with you; My peace I give to you; not as the world gives do I give to you. Do not let your heart be troubled, nor let it be fearful. You heard that I said to you, ‘I go away, and I will come to you.’ If you loved Me, you would have rejoiced because I go to the Father, for the Father is greater than I. Now I have told you before it happens, so that when it happens, you may believe. (John 14:26-29) {emphasis mine}
Studying God’s word enables me to know God’s power, trust His promises, and know His predictions. I don’t need to worry because God is in control of everything that happens in the world.
Let your gentle spirit be known to all men. The Lord is near. Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:5-7) {emphasis mine}
I really can know the “peace of God, which surpasses all comprehension.”
What We Need for Peace
Knowing God’s word can give us peace. We can bring Bible verses to mind as reminders of His promises given and His promises fulfilled. I am going to go through a bunch of verses that we can bring to mind when we are feeling worried and fearful. I’ll probably make a few comments, but I want God’s word to speak to you.
When I am afraid,\ I will put my trust in You.\ In God, whose word I praise,\ In God I have put my trust;\ I shall not be afraid.\ What can mere man do to me? (Psalm 56:3-4)
It is hard to be afraid when you are praising God.
While He was still speaking, they came from the house of the synagogue official, saying, “Your daughter has died; why trouble the Teacher anymore?” But Jesus, overhearing what was being spoken, said to the synagogue official, “Do not be afraid any longer, only believe.” (Mark 5:35-36)
Once trusting Jesus as Savior, we don’t need to be afraid of anything, just believe.
The Lord also will be a stronghold for the oppressed,\ A stronghold in times of trouble;\ And those who know Your name will put their trust in You,\ For You, O Lord, have not forsaken those who seek You. (Psalm 9:9-10)
No matter what we are going through, God is with us and working through us for good. We are never left alone.
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
God may allow hard times to come, but it is always for good. There is no pointless pain.
Be strong and courageous, do not be afraid or tremble at them, for the Lord your God is the one who goes with you. He will not fail you or forsake you. (Deuteronomy 31:6)
It is amazing how we can deal with hardships when we rely on God and not our own power.
For the eyes of the Lord are toward the righteous,\ And His ears attend to their prayer,\ But the face of the Lord is against those who do evil.
Who is there to harm you if you prove zealous for what is good? But even if you should suffer for the sake of righteousness, you are blessed. And do not fear their intimidation, and do not be troubled, but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence; and keep a good conscience so that in the thing in which you are slandered, those who revile your good behavior in Christ will be put to shame. (1 Peter 3:12-16) {emphasis mine}
How amazing is it that suffering can actually be a blessing. There is no witness stronger than the person who keeps the faith and has joy and hope in suffering.
Do not fret because of evildoers,\ Be not envious toward wrongdoers.\ For they will wither quickly like the grass\ And fade like the green herb.\ *Trust in the Lord and do good*;\ Dwell in the land and cultivate faithfulness.\ Delight yourself in the Lord;\ And He will give you the desires of your heart.\ *Commit your way to the Lord*,\ Trust also in Him, and He will do it. (Psalm 37:1-5) {emphasis mine}
When we trust in God, commit our way to Him, and delight in Him, we can have joy in any situation.
Open the gates, that the righteous nation may enter,\ The one that remains faithful.\ **The steadfast of mind You will keep in perfect peace,\ Because he trusts in You.\ Trust in the Lord forever,\ For in God the Lord, we have an everlasting Rock. (Isaiah 26:2-4) {emphasis mine}
What a promise! “The steadfast of mind You will keep in perfect peace, because he trusts in You.”
I know your tribulation and your poverty (but you are rich), and the blasphemy by those who say they are Jews and are not, but are a synagogue of Satan. Do not fear what you are about to suffer. Behold, the devil is about to cast some of you into prison, so that you will be tested, and you will have tribulation for ten days. Be faithful until death, and I will give you the crown of life. (Revelation 2:9-10) {emphasis mine}
Do you think of tribulation and poverty as riches? If you trust Jesus, then you are rich in blessings when you experience tribulation and poverty. God does not promise His people ease in this life, but He does promise to use every pain and hardship for good — for our good, the good of others, and His glory. We need to trust Jesus and not fear.
Trust in the Lord with all your heart\ And do not lean on your own understanding.\ In all your ways acknowledge Him,\ And He will make your paths straight.\ *Do not be wise in your own eyes;\ Fear the Lord* and turn away from evil.\ It will be healing to your body\ And refreshment to your bones.** (Proverbs 3:5-8) {emphasis mine}
I need this verse: “Trust in the Lord with all your heart, and do not lean on your own understanding.” I definitely want to lean on my own power and understanding and have to remind myself of God’s power, wisdom, and goodness continually so I lean on Him. You have to love what God promises when we trust in Him alone: “healing to your body and refreshment to your bones.” Doesn’t that sound wonderful?
For this reason I remind you to kindle afresh the gift of God which is in you through the laying on of my hands. For God has not given us a spirit of timidity, but of power and love and discipline.
Therefore do not be ashamed of the testimony of our Lord or of me His prisoner, but join with me in suffering for the gospel according to the power of God, who has saved us and called us with a holy calling, not according to our works, but according to His own purpose and grace which was granted us in Christ Jesus from all eternity, (2 Timothy 1:6-9) {emphasis mine}
If you haven’t relied on God for everything for a long time, a call to “join with me in suffering for the gospel” probably sounds crazy, but when we live a life “not according to our works, but according to His own purpose and grace” we quickly learn how everything in life brings more peace and joy. It doesn’t make it easier or nicer necessarily, but it does bring peace and joy like you can’t imagine.
Whoever confesses that Jesus is the Son of God, God abides in him, and he in God. We have come to know and have believed the love which God has for us. God is love, and the one who abides in love abides in God, and God abides in him. By this, love is perfected with us, so that we may have confidence in the day of judgment; because as He is, so also are we in this world. There is no fear in love; but perfect love casts out fear, because fear involves punishment, and the one who fears is not perfected in love. (1 John 4:15-18) {emphasis mine}
If we repent of our sins and confess Jesus as Lord, the God and Creator of the universe lives in us. Is there anything more magnificent? When we trust in Jesus, “we may have confidence in the day of judgment.” When we love God, He loves us and “perfect love casts out fear.”
What Would I Do?
My son with Down Syndrome loves watching this show called “Mayday, Air Disaster.” It goes through different, real plane crashes and reviews how they figured out why the plane crashed. Sometimes everyone dies. Sometimes everyone lives. Sometimes some live and some die.
Watching this show and seeing the people (in reenactments) screaming in terror as the plane plummets to the ground makes me wonder how I would react in a similar circumstance. If I wasn’t a Christian, I’d probably never set foot on a plane again after watching the show. I’d like to think I would be like Jesus calmly praying “into thy hands I commit my spirit,” but I might be frantically gripping the armrests and screaming like the rest. I don’t guess anyone truly knows until they experience something like that.
Whatever the case, whether we act in perfect faith or whether we have a moment of weakness in fear of danger, pain, and the unknown, Jesus will be there with us, if we have trusted in Jesus as Savior. Everything is better with Jesus.
May our Lord, Creator, and Savior keep us in total faith, love, peace, and joy in Him so that we do not fear, no matter what trials we face. May He help us to lean on Him and not try to do everything ourselves or rely on stuff. May our faithful service and hope during trial glorify Him and draw many to Him.
Trust Jesus
-
 @ e5cfb5dc:0039f130
2025-06-17 11:00:35
@ e5cfb5dc:0039f130
2025-06-17 11:00:35はりまメンタルクリニック:GIDの大手そう。丸の内線ならパムくんちが近い。
わらびメンタルクリニック:GIDの大手そう?公式サイトには影もかたちも
ナグモクリニック:SRS手術までしてるところ。GID精神科外来が月1第1木曜日だけ?
狭山メンタルクリニック:距離・時間的にはまま近い。サイトの記述が思想的にちょとあやしげ。新患受付がだいぶ先。GIDは専門外か?
川島領診療所:オンライン診療あり!強迫性障害や美容皮膚科をやっている。雰囲気よさそうなところ。GIDは専門外か?
Jこころのクリニック:電車いっぽんなので楽。GIDは専門外か?
ハッピースマイルクリニック:オンライン診療あり!GIDは専門外か?
-
 @ 31a4605e:cf043959
2025-06-17 16:35:04
@ 31a4605e:cf043959
2025-06-17 16:35:04Bitcoin foi criado para oferecer uma alternativa segura e descentralizada ao dinheiro tradicional, permitindo transações financeiras sem a necessidade de intermediários. DeFi, por outro lado, surgiu como uma expansão deste conceito, propondo serviços financeiros descentralizados, como empréstimos, trocas e geração de rendimento. No entanto, apesar das promessas de inovação, DeFi apresenta inúmeros riscos, tornando-se uma aposta perigosa para quem valoriza a segurança do seu Bitcoin.
O que é DeFi?
DeFi refere-se a um conjunto de aplicações financeiras que funcionam sem a intermediação de bancos ou instituições tradicionais. Estas plataformas utilizam contratos inteligentes para automatizar transações, permitindo que qualquer pessoa aceda a serviços financeiros sem depender de terceiros. Na teoria, DeFi promete mais liberdade financeira, mas na prática está cheio de riscos, fraudes e vulnerabilidades técnicas que podem comprometer os fundos dos utilizadores.
Os riscos de DeFi para quem tem Bitcoin
Bitcoin é a moeda digital mais segura do mundo, protegida por uma rede descentralizada e resistente à censura. Ao contrário de DeFi, que ainda está em fase experimental e já sofreu inúmeros ataques, Bitcoin mantém-se sólido e confiável. Quando alguém coloca Bitcoin em plataformas DeFi, está a abrir mão da segurança da sua custódia direta e a confiar em sistemas mais frágeis. os principais riscos incluem:
Hackers e falhas de código: contratos inteligentes são escritos por programadores e podem conter falhas que permitem roubos massivos. ao longo dos anos, milhares de milhões de dólares já foram perdidos devido a vulnerabilidades em plataformas DeFi.
Riscos de liquidação: muitas aplicações DeFi funcionam com sistemas de colateralização, onde os utilizadores bloqueiam Bitcoin para obterem empréstimos. se o mercado se tornar volátil, esses Bitcoins podem ser liquidados a preços abaixo do esperado, causando perdas irreversíveis.
Fraudes e rug pulls: DeFi está repleto de projetos obscuros onde os criadores desaparecem com os fundos dos utilizadores. sem regulamentação e sem garantias, quem deposita Bitcoin nessas plataformas pode nunca mais recuperar os seus fundos.
Guardar Bitcoin em segurança é a melhor escolha
Bitcoin foi criado para ser auto-custodiado, ou seja, cada utilizador deve ter controlo direto sobre os seus fundos sem depender de terceiros. Ao enviar Bitcoin para plataformas DeFi, perde-se essa segurança e expõe-se o ativo a riscos desnecessários. A melhor forma de proteger Bitcoin é armazená-lo numa carteira segura, preferencialmente offline (cold storage), evitando qualquer tipo de exposição a contratos inteligentes ou sistemas vulneráveis.
Resumindo, DeFi pode parecer inovador, mas os riscos superam largamente os potenciais benefícios, especialmente para quem valoriza a segurança de Bitcoin. ao invés de arriscar perder fundos em plataformas inseguras, o mais sensato é manter Bitcoin armazenado de forma segura, garantindo a sua preservação a longo prazo. Enquanto Bitcoin continua a ser a melhor reserva de valor digital do mundo, DeFi ainda se revela um ambiente instável e perigoso, onde poucos saem ganhadores e muitos acabam por perder.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:49:53
@ 31a4605e:cf043959
2025-06-17 17:49:53Desde a sua criação, Bitcoin tem sido um ativo revolucionário, desafiando o sistema financeiro tradicional e propondo uma nova forma de dinheiro descentralizado. No entanto, o seu futuro ainda é incerto e gera intensos debates. Entre os cenários possíveis, dois extremos destacam-se: a hiperbitcoinização, onde Bitcoin se torna a moeda dominante na economia global, ou a obsolescência, caso a rede perca relevância e seja substituída por outras soluções.
Hiperbitcoinização: o mundo adota Bitcoin como padrão monetário
Perda de confiança nas moedas fiduciárias: Com a impressão excessiva de dinheiro por bancos centrais, muitas economias enfrentam inflação descontrolada. Bitcoin, com a sua oferta limitada de 21 milhões de unidades, apresenta-se como uma alternativa mais confiável.
Adoção crescente por empresas e governos: Alguns países já começaram a integrar Bitcoin na sua economia, aceitando-o para pagamentos e reserva de valor. Se essa tendência continuar, a legitimidade de Bitcoin como moeda global aumentará.
Facilidade de transações globais: Bitcoin permite transferências internacionais rápidas e baratas, eliminando a necessidade de intermediários financeiros e reduzindo custos operacionais.
Avanços tecnológicos: Melhorias na escalabilidade, como a Lightning Network, podem tornar Bitcoin mais eficiente para uso diário, facilitando sua adoção em massa.
Se a hiperbitcoinização acontecer, o mundo pode testemunhar uma mudança radical no sistema financeiro, com maior descentralização, resistência à censura e uma economia baseada em dinheiro sólido e previsível.
Obsolescência: Bitcoin perde relevância e É substituído
Regulações governamentais restritivas: Se grandes potências económicas impuserem regulações severas sobre Bitcoin, a adoção pode ser dificultada, reduzindo sua utilidade.
Falhas tecnológicas ou falta de inovação: Apesar da sua segurança e descentralização, Bitcoin pode enfrentar dificuldades para escalar de forma eficiente. Se soluções melhores surgirem e forem amplamente aceites, Bitcoin pode perder a sua posição de liderança.
Concorrência com alternativas mais rápidas e eficientes: Se outras formas de dinheiro digital conseguirem superar Bitcoin em termos de escalabilidade e usabilidade, a rede pode ver a sua adoção diminuir.
Falta de incentivos para os mineradores: Como a emissão de novos Bitcoins diminui a cada halving, os mineradores dependerão cada vez mais das taxas de transação. Se essas taxas não forem suficientes para sustentar a segurança da rede, pode haver um risco para a sua viabilidade a longo prazo.
Resumindo, o futuro do Bitcoin pode seguir diferentes caminhos, dependendo de fatores como inovação, adoção global e resistência a desafios externos. A hiperbitcoinização representaria uma revolução económica, com um sistema monetário descentralizado e resistente à inflação. No entanto, a obsolescência continua a ser um risco, caso a rede não consiga adaptar-se às exigências futuras. Independentemente do desfecho, Bitcoin já deixou a sua marca na história financeira, abrindo caminho para uma nova era de dinheiro digital e liberdade económica.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 31a4605e:cf043959
2025-06-17 17:27:05
@ 31a4605e:cf043959
2025-06-17 17:27:05Desde a sua criação, Bitcoin tem sido visto tanto como uma inovação financeira quanto como uma ameaça ao controlo governamental sobre a economia. Como uma moeda descentralizada, Bitcoin opera fora do sistema financeiro tradicional, desafiando a autoridade dos bancos centrais e dos governos que regulam a emissão e circulação do dinheiro. Essa característica tem levado a diversos conflitos entre governos e a crescente adoção de Bitcoin por indivíduos e empresas.
Razões para a oposição governamental
Perda de controlo monetário: Os governos controlam a economia através da emissão de moeda fiduciária e da definição de políticas monetárias. Como Bitcoin tem uma oferta fixa e não pode ser manipulado, isso reduz a influência governamental sobre a economia.
Dificuldade na tributação e fiscalização: A natureza descentralizada de Bitcoin dificulta a cobrança de impostos e o rastreamento de transações, tornando mais difícil para os governos garantir a conformidade fiscal.
Concorrência com moedas digitais estatais (CBDCs): Muitos países estão a desenvolver moedas digitais de banco central (CBDCs), que oferecem maior controlo sobre as transações financeiras. Bitcoin representa uma alternativa descentralizada, o que pode ameaçar a adoção dessas moedas estatais.
Preocupações com crimes financeiros: Alguns governos argumentam que Bitcoin pode ser usado para lavagem de dinheiro e financiamento ilícito, apesar de ser mais rastreável do que o dinheiro físico devido à transparência da blockchain ou timechain.
Exemplos de conflitos entre governos e Bitcoin
El Salvador: Foi o primeiro país a tornar Bitcoin moeda legal em 2021. Essa decisão gerou reações negativas de instituições financeiras internacionais, como o FMI, que alertou para riscos económicos e tentou pressionar o país a reverter a sua decisão.
China: Em 2021, a China proibiu a mineração e o uso de Bitcoin, citando preocupações ambientais e riscos financeiros. Apesar da proibição, muitos utilizadores chineses continuam a usar Bitcoin de forma descentralizada.
Estados Unidos: Embora Bitcoin seja legal nos EUA, o governo tem aumentado a regulamentação sobre exchanges e mineradores, tentando exercer maior controlo sobre a rede.
União Europeia: A UE tem imposto regulamentos rigorosos sobre Bitcoin, como exigências de identificação para transações, mas não proibiu a sua utilização.
O futuro da adoção do Bitcoin
Apesar da resistência de alguns governos, Bitcoin continua a ser adotado por indivíduos e empresas como uma alternativa financeira segura. Em países com economias instáveis, Bitcoin tem sido uma ferramenta essencial para proteger a riqueza contra a inflação e restrições bancárias.
A tentativa de controlo governamental pode dificultar a adoção de Bitcoin em algumas regiões, mas não impedirá o seu crescimento global. Como uma rede descentralizada, Bitcoin não pode ser banido completamente, e a sua utilidade como reserva de valor e meio de troca continuará a atrair utilizadores em todo o mundo.
Resumindo, os conflitos entre governos e a adoção de Bitcoin refletem o choque entre um sistema financeiro centralizado e uma tecnologia descentralizada que devolve o controlo do dinheiro aos indivíduos. Embora alguns governos tentem restringir o seu uso, Bitcoin continua a crescer e a provar a sua resistência, tornando-se cada vez mais uma opção viável para aqueles que procuram liberdade financeira.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 8bad92c3:ca714aa5
2025-06-18 21:02:08
@ 8bad92c3:ca714aa5
2025-06-18 21:02:08Key Takeaways

In this episode, host Marty speaks with Ken, a former CIA deputy chief and now head of government affairs at the Bitcoin Policy Institute, about Bitcoin’s growing relevance in U.S. national security and policy circles. Ken traces his Bitcoin journey from professional curiosity within the CIA, studying adversarial use cases like the Lazarus Group, to personal conviction following events like the Canadian trucker protests, which exposed the dangers of financial censorship. Contrary to popular belief, he reveals that many in the intelligence community support Bitcoin for its alignment with American values such as sovereignty and freedom. The conversation highlights a major cultural shift in Washington, where policymakers now view Bitcoin as a strategic asset rather than a criminal tool. Ken stresses that the future hinges on whether Bitcoin shapes institutions or is co-opted by them, and that political engagement is crucial to ensure the former. He argues Bitcoin can help solve systemic problems from fiscal irresponsibility to geopolitical instability, but only if the industry continues to organize, advocate, and embed its values into national policy.
Best Quotes
"Either institutions are going to win, or Bitcoin is going to win."
"Bitcoin naturally washes out leverage… it's what makes Bitcoin antifragile."
"The CIA didn’t create Bitcoin, but they sure are paying attention now."
"We were all Satoshi."
"Let’s not test the resistance-money thesis in the United States."
"Bitcoin strengthens U.S. values, freedom, private property, sovereignty."
"Bitcoin is political, but it doesn't have to be partisan."
"If you're in a federal agency, the only incentive is to spend more. Bitcoin changes that."
"Don't underestimate your voice. If you keep the phones ringing, they listen."
Conclusion
This episode offers a rare glimpse into how Bitcoin is increasingly viewed as a serious strategic asset within the U.S. intelligence and policy communities. Ken, with his high-level government background and current role in Bitcoin advocacy, underscores the shift from skepticism to engagement among policymakers. His message is clear: Bitcoiners are no longer outsiders, they have a seat at the table, and with sustained political action and education, they can shape the future of Bitcoin policy. The time to engage is now, because the battle for Bitcoin’s role in society is already in motion.
Timestamps
0:00 - Intro
0:26 - Ken's background
6:58 - Tornado/Samourai, surveillance state
11:53 - Reestablishing trust
14:23 - Bitkey
15:18 - CIA bitcoin theory
18:42 - Neutral reserve asset
23:52 - Unchained
24:20 - BPI
29:49 - CLARITY and Secret Service message
33:54 - Withstanding a change in administration
40:03 - Institutions win or bitcoin wins
46:43 - Shrinking gov with bitcoin
57:47 - BPI summitTranscript
00:00:00 compared to China or Russia, do we have a comparable advantage in gold? How do we compete with China? And this is what the kinds of things CI will think about. Bitcoin is a natural option. At the end of the day, Bitcoin undermines the authority of the Chinese Communist Party. Either institutions are going to win or Bitcoin is going to win. But we do fundamentally on some level need institutions to make the country run. We want those institutions to be properly incentivized. In 10 years, Bitcoin is
00:00:19 either at a million dollars or is zero dollars. Ken, it's great to have you on the show. Thank you for joining me. Marty, finally. We've been we've been kicking us around for a few weeks. I'm glad we uh glad we were finally able to make it work. As I was telling you, in the middle of a move, conference in the middle of that move. It's been a hectic week, so I think I'm finally settling in. As you can see, no bookshelf, but we have stacked books behind me. Hopefully, they will be on on shelves soon.
00:00:52 No, there there are definitely ways there are ways in the world to get you know to get credits on um you know uh what do you call it? Um uh we're good Catholics, you know, when you when you pass and don't go to heaven. Um come on. Thank you. Well, moving is purgatory credit. So, I've done it many times in my life. So, I uh I feel for you. Well, thank you. But I'm really excited for this conversation and likewise the event in a few weeks, the BPI event down in DC, the summit, we met about a month ago, two months ago now at
00:01:26 this point in Austin during the takeover. And Zach was very eager to introduce you to me considering the the history of the show, topics we covered. And I think I'm excited for this cuz I'm infinitely curious to learn how somebody with your pedigree and your resume got into Bitcoin is now working for the Bitcoin Policy Institute as a director of government affairs. So for anybody listening who was unaware of Ken's resume, he did 20 years in government culminating as deputy chief of operations at the CIA Center for Cyber
00:02:01 Intelligence. uh you've worked overseas for the US State Department and now you're advocating on behalf of Bitcoin on Capitol Hill. So, how does somebody with that resume go from statecraft to cipher punk sort of ideas? Yeah. No, so I um like everybody else, I uh I um my my Bitcoin journey is a little bit everybody everybody has a unique journey, right? Um mine actually started at CIA, believe it or not. And it was for purely professional reasons. I um so I was an operations officer. I spent most of my career overseas um as
00:02:37 most of us do. Um but my last two years, my last two turn tours at CIA, I was at the center for cyber intelligence, which is CIA's cyber unit. Um and my first job there, I was group ch I was a operations chief for a group that worked on cyber threat issues. And this was in 2018. So you remember this was when Lazarus group the North Koreans figured out that stealing crypto was a lot easier than like you know trying to rob banks. Um this is when ransomware broke out as a serious problem just preceded you may
00:03:04 remember the Colonial Pipeline hack that shut down you know gasoline shipments to the east coast. So in 2018 um and it's kind of funny like I this is people say did the CIA create Bitcoin. I can tell you in 2018 when policy makers first had to confront its use by actors as an issue like nobody was ready for it. Like if they created it, it was tucked away and hidden in the basement cuz the the bench for people with crypto knowledge in general, digital assets, certainly Bitcoin was really really really shallow. Um I remember we had two
00:03:33 guys um who kind of had background in it and then you they became superstars because all of a sudden we were calling upon them to teach us about Bitcoin and digital assets in general. Um, but yeah, that's so I learned and like everything else, I learned about it because I had to because people we cared people we cared about were using it. Um, but like everything else there there was sort of a mind virus to it. Um, and I I admit, you know, I during co I was in the uh I was in the altcoin casino. I was defying
00:04:00 and memecoining and it was it was fun, you know. No, I I I don't hold any hate for the uh for the alcoiners. People do what they want with their money. Um but I you know that that was when it was during co um I had been sort of buying in 2018 but during co when I really started learning because this is what everybody learned right um and I you know for me Bitcoin was immediately attracted me to it and I was sort of inspired by um I mean the co Kenny trucker protest was something really important to me um I saw how it was
00:04:29 being used um but also sort of in my day job you know I I had a pretty good understanding of how the government uses financial financial tools as a weapon. Um, freezing bank accounts, OFAC sanctions, that kind of thing. And if you're on the, you know, on the giving end of that, that's great. Those are great tools to have if you're the government. Uh, not so great if you're on the other end of it. And, you know, watching these Canadian truckers the first time, you know, you'll be able to, it's very easy
00:04:54 to say, "Yeah, sanction the Iranian, sanction North Korea, whatever." You know, I'm not Iranian. Um but when you see all of a sudden Kat and Trucker people you had some sympathy with being targets of financial you know weaposition of the financial system it you know it struck it struck a it struck a nerve like a really really profound stinging shot to my consciousness my conscious about this issue. Um so for me for the first thing about Bitcoin was um was permissionless transactions that that's that's what got me into it. Um
00:05:23 then of course you go from there and by the time I left the government 2022 I had I was f I was you know full boore I was you know attending meetups and um that's when I started doing some advocacy stuff on Capitol Hill and and and messing around with uh David and Granny PPI doing some advocacy stuff but yeah but it it comes from my time at CIA and yeah I think the um the uh I think what might surprise some people is there are a lot of Bitcoiners um not just at CIA but across the whole national
00:05:52 security establishment And I think they're into it for the same reason that you know that everybody most of your listeners are right like it's you see what's happening in the world. You see the challenges we're facing. You see how governments use financial tools to weaponize them against opposition. You know it's it's very natural that if you have that kind of insight that you look for things to protect yourself and Bitcoin is obvious. So I I I tell a funny story when I um when I was first into it there was um cubicle one of the
00:06:17 guys and he had a bumper