-
 @ ac8bb9b0:70278acc
2025-06-05 18:12:29
@ ac8bb9b0:70278acc
2025-06-05 18:12:29Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 12
Ingredients
- 1 and 1/2 cups (345g) mashed bananas (about 4 medium or 3 large ripe bananas)
- 1/3 cup (113g) honey
- 1 large egg
- 1/4 cup (56g) coconut oil, melted
- 1 teaspoon pure vanilla extract
- 1 cup (130g) whole wheat flour
- 1/2 cup (41g) natural unsweetened cocoa powder
- 1 teaspoon baking powder
- 1 teaspoon baking soda
- 1/2 teaspoon salt
- 1 cup (180g) semi-sweet or dark chocolate chips
Directions
- Preheat oven to 425°F (218°C). Spray a 12-count muffin pan with nonstick spray or line with cupcake liners. Set aside.
- In a medium bowl, mash the bananas up using a fork.* Try to mash up any large lumps. Once mashed, whisk in the honey, egg, coconut oil, and vanilla extract until combined. Set aside.
- In a large bowl, whisk the flour, cocoa powder, baking powder, baking soda, and salt together. Pour the wet ingredients into the dry ingredients and whisk until everything is combined. Fold in the chocolate chips, reserving some for the tops of the warm muffins.
- Spoon the batter evenly into each cup or liner, filling each all the way to the top.
- Bake for 5 minutes at 425°F (218°C); then, keeping the muffins in the oven, reduce heat to 350°F (177°C) and continue baking for another 15–17 minutes or until a toothpick inserted in the center comes out clean. The total time these muffins take in the oven is about 20–21 minutes, give or take. (For mini muffins, bake 11–13 minutes at 350°F (177°C) the whole time.)
- Press any remaining chocolate chips into the tops of the warm muffins. Allow the muffins to cool for 5 minutes in the muffin pan, and then transfer to a wire rack to continue cooling, or enjoy warm.
- Muffins stay fresh covered at room temperature for a few days, then transfer to the refrigerator for up to 1 week.
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:37
@ dfa02707:41ca50e3
2025-06-05 18:02:37News
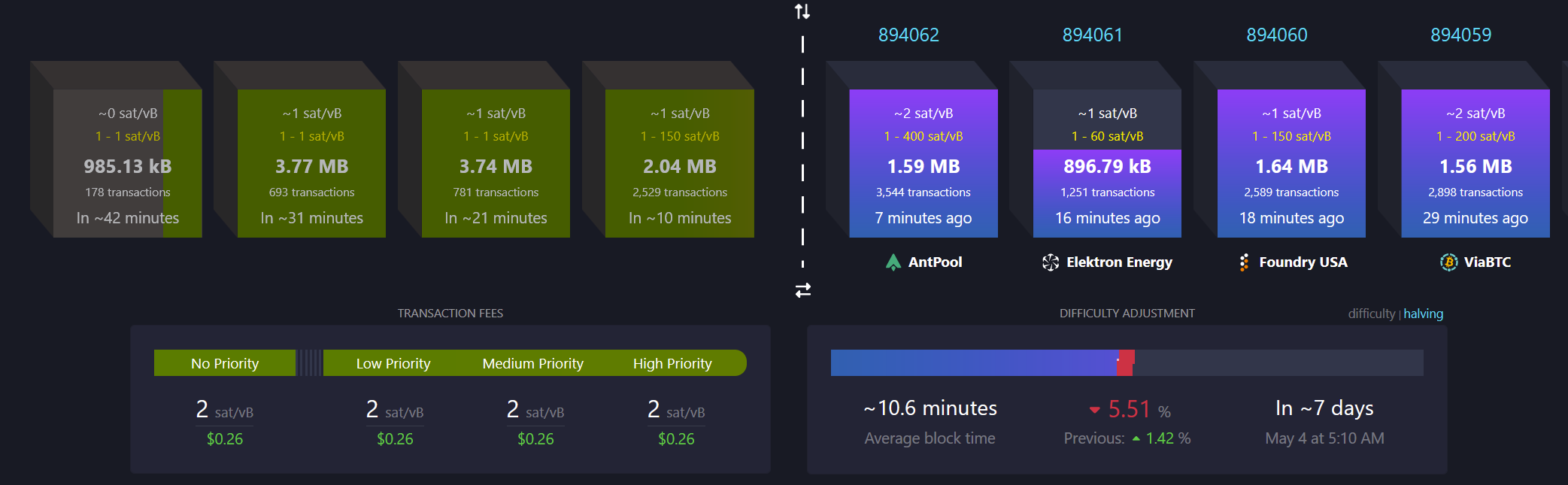
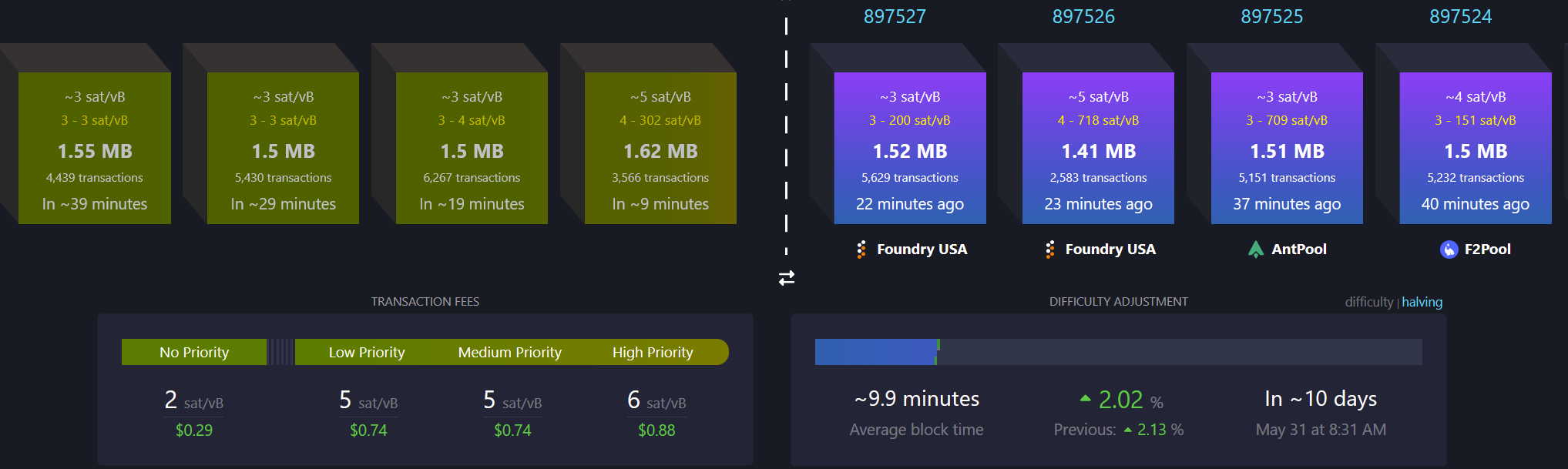
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
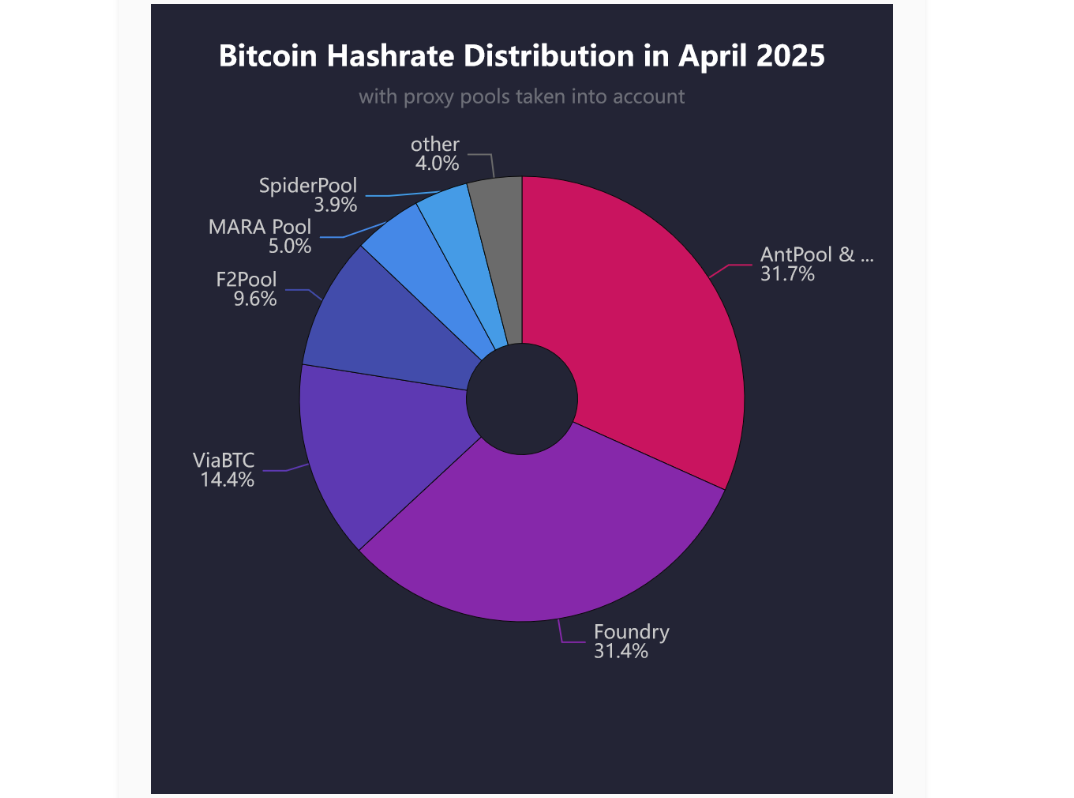
Source: b10c's blog.
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
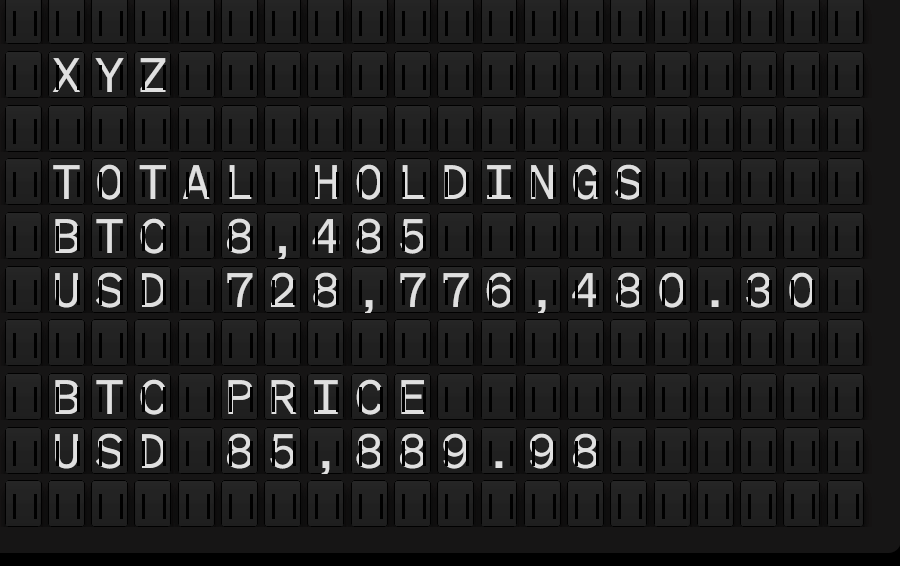
- Block launched open-source tools for Bitcoin treasury management. These include a dashboard for managing corporate bitcoin holdings and provides a real-time BTC-to-USD price quote API, released as part of the Block Open Source initiative. The company’s own instance of the bitcoin holdings dashboard is available here.
Source: block.xyz
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Corporate bitcoin holdings hit a record high in Q1 2025. According to Bitwise, public companies' adoption of Bitcoin has hit an all-time high. In Q1 2025, these firms collectively hold over 688,000 BTC, marking a 16.11% increase from the previous quarter. This amount represents 3.28% of Bitcoin's fixed 21 million supply.
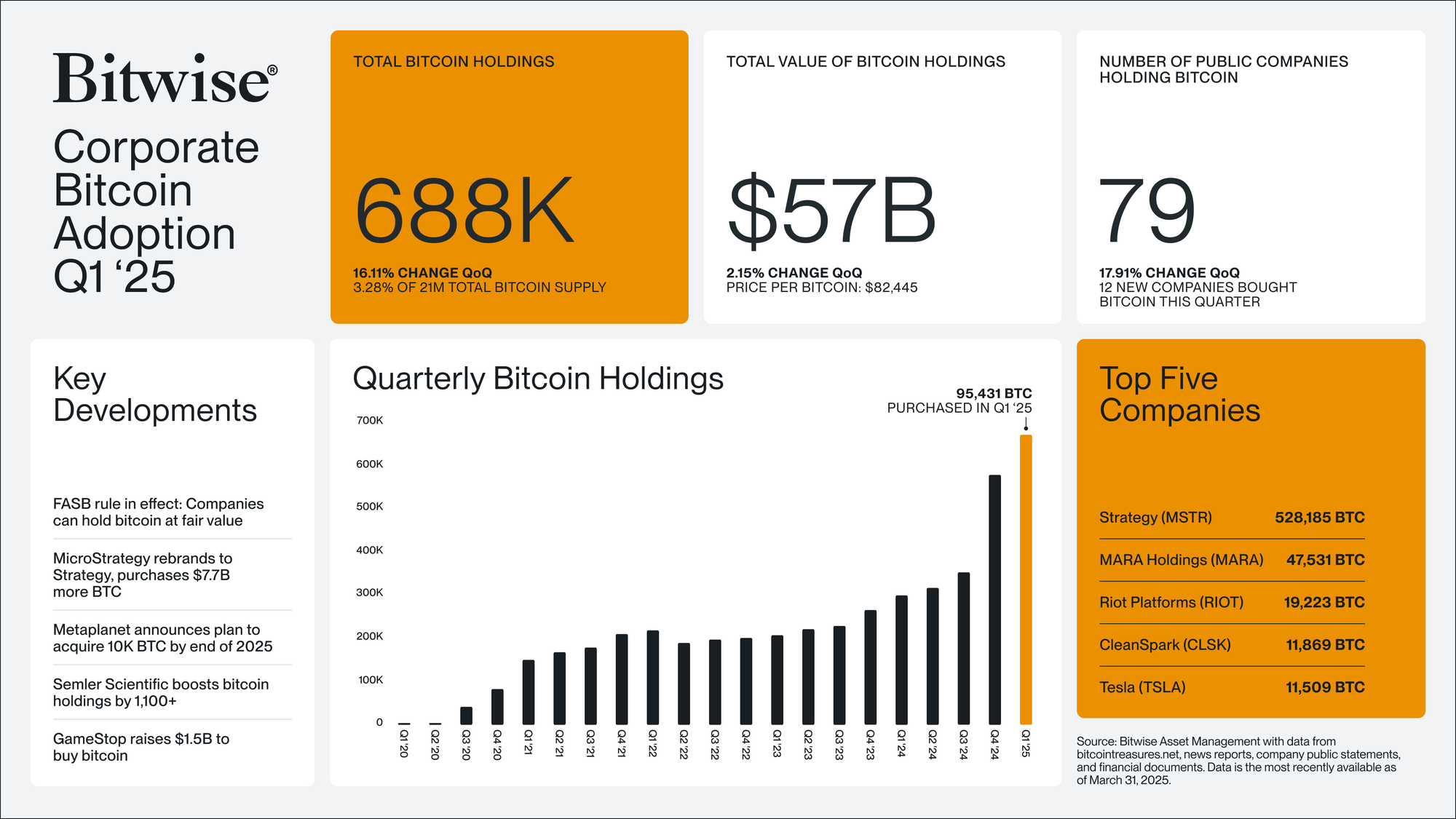
Source: Bitwise.
- The Bitcoin Bond Company for institutions has launched with the aim of acquiring $1 trillion in Bitcoin over 21 years. It utilizes secure, transparent, and compliant bond-like products backed by Bitcoin.
- The U.S. Senate confirmed Paul Atkins as Chair of the Securities and Exchange Commission (SEC). At his confirmation hearing, Atkins emphasized the need for a clear framework for digital assets. He aims to collaborate with the CFTC and Congress to address jurisdiction and rulemaking gaps, aligning with the Trump administration's goal to position the U.S. as a leader in Bitcoin and blockchain finance.
- Ethereum developer Virgil Griffith has been released from custody. Griffith, whose sentence was reduced to 56 months, is now seeking a pardon. He was initially sentenced to 63 months for allegedly violating international sanctions laws by providing technical advice on using cryptocurrencies and blockchain technology to evade sanctions during a presentation titled 'Blockchains for Peace' in North Korea.
- No-KYC exchange eXch to close down under money laundering scrutiny. The privacy-focused cryptocurrency trading platform said it will cease operations on May 1. This decision follows allegations that the platform was used by North Korea's Lazarus Group for money laundering. eXch revealed it is the subject of an active "transatlantic operation" aimed at shutting down the platform and prosecuting its team for "money laundering and terrorism."
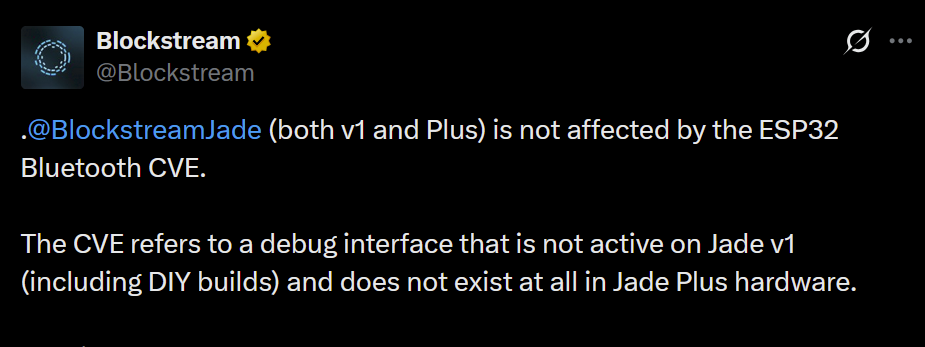
- Blockstream combats ESP32 FUD concerning Jade signers. The company stated that after reviewing the vulnerability disclosed in early March, Jade was found to be secure. Espressif Systems, the designer of the ESP32, has since clarified that the "undocumented commands" do not constitute a "backdoor."
- Bank of America is lobbying for regulations that favor banks over tech firms in stablecoin issuance. The bank's CEO Brian Moynihan is working with groups such as the American Bankers Association to advance the issuance of a fully reserved, 1:1 backed "Bank of America coin." If successful, this could limit stablecoin efforts by non-banks like Tether, Circle, and others, reports The Block.
- Tether to back OCEAN Pool with its hashrate. "As a company committed to financial freedom and open access, we see supporting decentralization in Bitcoin mining as essential to the network’s long-term integrity," said Tether CEO Paolo Ardoino.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Tether acquires $32M in Bitdeer shares. The firm has boosted its investment in Bitdeer during a wider market sell-off, with purchases in early to mid-April amounting to about $32 million, regulatory filings reveal.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Voltage has partnered with BitGo to [enable](https://www.voltage.cloud/blog/bitgo-and-voltage-team-up-to-deliver-instant-bitcoin-and-stabl
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:36
@ dfa02707:41ca50e3
2025-06-05 18:02:36Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
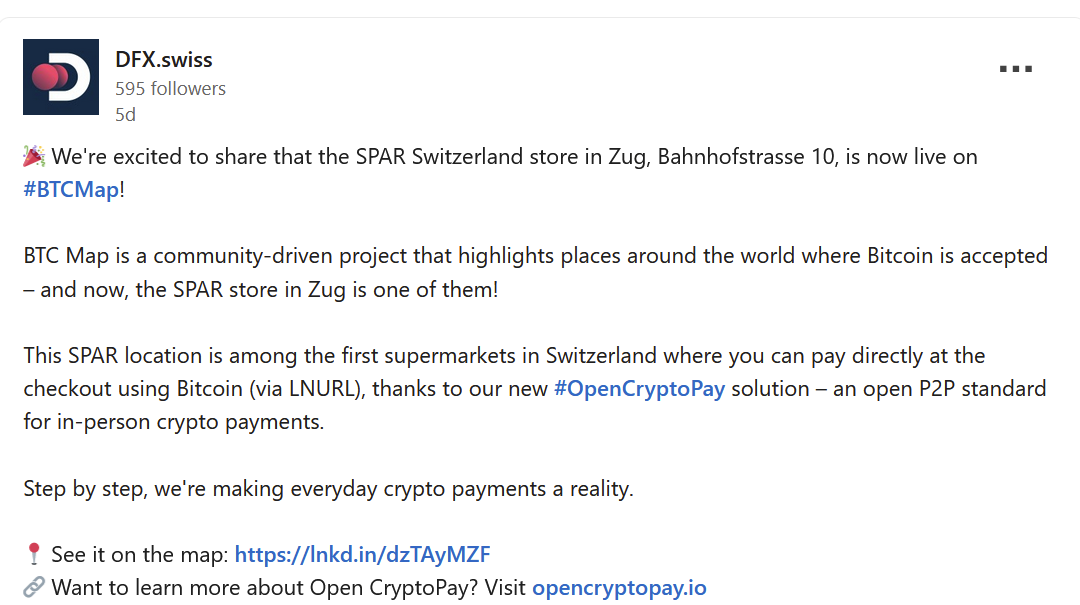
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:36
@ dfa02707:41ca50e3
2025-06-05 18:02:36Headlines
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Florida's SB 868 proposes a backdoor into encrypted platforms. The bill and its House companion have both passed through their respective committees and are headed to a full vote. If enacted, SB 868 would require social media companies to decrypt teens' private messages, ban disappearing messages, allow unrestricted parental access to private messages, and likely eliminate encryption for all minors altogether.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable for miners on OCEAN but also one of the best things for Bitcoin," stated the mining pool.
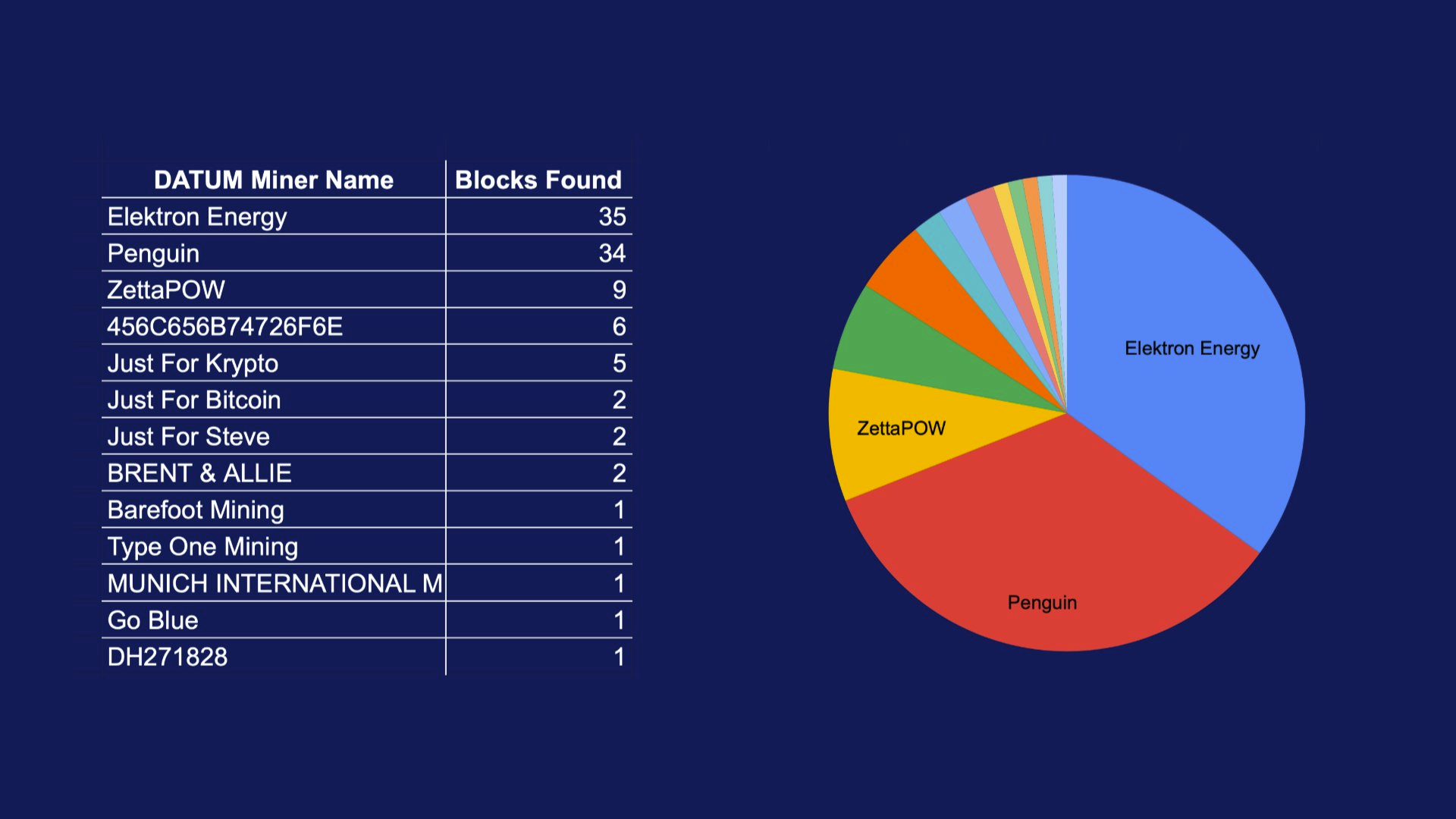
Source: orangesurf
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- TABConf 2025 is scheduled to take place from October 13-16, 2025. This prominent technical Bitcoin conference is dedicated to community building, education, and developer support, and it is set to return in October. Get your tickets here.
- Kaduna Lightning Development Bootcamp. From May 14th to 17th, the Bitcoin Lightning Developer Bootcamp will take place in Kaduna, Nigeria. Thisevent offers four dynamic days of coding, learning, and networking. Organized by Africa Free Routing and supported by Btrust, Tether, and African Bitcoiners, this bootcamp is designed as a gateway for African developers eager to advance their skills in Bitcoin and Lightning development. Apply here.

Source: African Bitcoiners.
Use the tools
- Core Lightning (CLN) v25.02.2 as been released to fix a broken Docker image. The issue was caused by an SQLite version that did not support an advanced query.
- Blitz wallet v0.4.4-beta introduces several updates and improvements, including the prevention of duplicate ecash payments, fixes for background ecash invoice handling, the ability for users to send payments to BOLT12 invoices from their Liquid balance, support for Blink QR codes, a lowered minimum amount for Lightning-to-Liquid payments to 100 sats, the option to initiate a node sync via a swipe gesture on the wallet's home screen, and the introduction of opt-in or opt-out functionality for newly implemented crash analytics via settings.
- Utreexo v0.5.0, a hash-based dynamic accumulator, is now available.
- Specter v2.1.1 is now available on StartOS. "This update brings compatibility with Bitcoin Core v28 and incorporates several upstream improvements," said developer Alex71btc.
- ESP-Miner (AxeOS) v2.7.0b1 is now available for testing.
- NodeGuard v0.16.1, a treasury management solution for Lightning nodes, has been released.
- The latest stacker.news updates include prompts to add a receiving wallet when posting or making comments (for new users), an option to randomize poll choices, improved URL search, and a few other enhancements. A bug fix for territories created after 9/19/24 has been implemented to reward 70% of their revenue to owners instead of 50%.
Other stuff
- The April edition of the 256 Foundation's newsletter is now available. It includes the latest mining news, Bitcoin network health updates, project developments, and a tutorial on how to update FutureBit's Apollo 1 to the Apollo 2 software.
- Siggy47 has posted a comprehensive RoboSats guide on stacker.news.
- Learn how to run your own Nostr relay using Citrine and Cloudflare Tunnels by following this step-by-step guide by Dhalism.
- Max Guise has written a Bitkey roadmap update for April 2025.
-
PlebLab has uploaded a video on how to build a Rust wallet with LDK Node by Ben Carman.
-
Do you want more? Subscribe and get No Bullshit GM report straight to your mailbox and No Bullshit Bitcoin on Nostr.
- Feedback or tips? Drop it here.
- #FREESAMOURAI
Sign up for No Bullshit Bitcoin

No Bullshit Bitcoin Is a Bitcoin News Desk Without Ads, Paywalls, or Clickbait.
Subscribe .nc-loop-dots-4-24-icon-o{--animation-duration:0.8s} .nc-loop-dots-4-24-icon-o *{opacity:.4;transform:scale(.75);animation:nc-loop-dots-4-anim var(--animation-duration) infinite} .nc-loop-dots-4-24-icon-o :nth-child(1){transform-origin:4px 12px;animation-delay:-.3s;animation-delay:calc(var(--animation-duration)/-2.666)} .nc-loop-dots-4-24-icon-o :nth-child(2){transform-origin:12px 12px;animation-delay:-.15s;animation-delay:calc(var(--animation-duration)/-5.333)} .nc-loop-dots-4-24-icon-o :nth-child(3){transform-origin:20px 12px} @keyframes nc-loop-dots-4-anim{0%,100%{opacity:.4;transform:scale(.75)}50%{opacity:1;transform:scale(1)}}
Email sent! Check your inbox to complete your signup.
No spam. Unsubscribe anytime.
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:36
@ dfa02707:41ca50e3
2025-06-05 18:02:36Headlines
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- All virtual asset service providers expect to be fully compliant with the Travel Rule by the end of 2025. A survey by financial surveillance specialist Notabene reveals that 90% of virtual asset service providers (VASPs) expect full Travel Rule compliance by mid-2025, with all aiming for compliance by year-end. The survey also shows a significant rise in VASPs blocking withdrawals until beneficiary information is confirmed, increasing from 2.9% in 2024 to 15.4% now. Additionally, about 20% of VASPs return deposits if originator data is missing.
- UN claims Bitcoin mining is a "powerful tool" for money laundering. The Rage's analysis suggests that the recent United Nations Office on Drugs and Crime report on crime in South-East Asia makes little sense and hints at the potential introduction of Anti-Money Laundering (AML) measures at the mining level.
- Riot Platforms has obtained a $100 million credit facility from Coinbase Credit, using bitcoin as collateral for short-term funding to support its expansion. The firm's CEO, Jason Les, stated that this facility is crucial for diversifying financing sources and driving long-term stockholder value through strategic growth initiatives.
- Bitdeer raises $179M in loans and equity amid Bitcoin chip push. The Miner Mag reports that Bitdeer entered into a loan agreement with its affiliate Matrixport for up to $200 million in April, as disclosed in its annual report filed on Monday.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- U.S. 'crypto' scam losses amounted to $9.3B in 2024. The US The Federal Bureau of Investigation (FBI) has reported $9.3 billion losses in cryptocurrency-related scams in 2024, noting a troubling trend of scams targeting older Americans, which accounted for over $2.8 billion of those losses.
Source: FBI.
- North Korean hackers establish fake companies to target 'crypto' developers. Silent Push researchers reported that hackers linked to the Lazarus Group created three shell companies, two of which are based in the U.S., with the objective of spreading malware through deceptive job interview scams aimed at individuals seeking jobs in cryptocurrency companies.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- Hesperides University offers a Master’s degree in Bitcoin. Bitcoin Magazine reports the launch of the first-ever Spanish-language Master’s program dedicated exclusively to Bitcoin. Starting April 28, 2025, this fully online program will equip professionals with technical, economic, legal, and philosophical skills to excel in the Bitcoin era.
- BTC in D.C. event is set to take place on September 30 - October 1 in Washington, D.C. Learn more about this initiative here.
Use the tools
- Bitcoin Keeper just got a new look. Version 2.2.0 of the mobile multisig app brought a new branding design, along with a Keeper Private tier, testnet support, ability to import and export BIP-329 labels, and the option to use a Server Key with multiple users.
- Earlier this month the project also announced Keeper Learn service, offering clear and guided Bitcoin learning sessions for both groups and individuals.
- Keeper Desktop v0.2.2, a companion desktop app for Bitcoin Keeper mobile app, received a renewed branding update, too.

The evolution of Bitcoin Keeper logo. Source: BitHyve blog.
- Blockstream Green Desktop v2.0.25 updates GDK to v0.75.1 and fixes amount parsing issues when switching from fiat denomination to Liquid asset.
- Lightning Loop v0.31.0-beta enhances the
loop listswapscommand by improving the ability to filter the response. - Lightning-kmp v1.10.0, an implementation of the Lightning Network in Kotlin, is now available.
- LND v0.19.0-beta.rc3, the latest beta release candidate of LND is now ready for testing.
- ZEUS v0.11.0-alpha2 is now available for testing, too. It's nuts.
- JoinMarket Fidelity Bond Simulator helps potential JoinMarket makers evaluate their competitive position in the market based on fidelity bonds.
- UTXOscope is a text-only Bitcoin blockchain analysis tool that visualizes price dynamics using only on-chain data. The
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:35
@ dfa02707:41ca50e3
2025-06-05 18:02:35Contribute to keep No Bullshit Bitcoin news going.
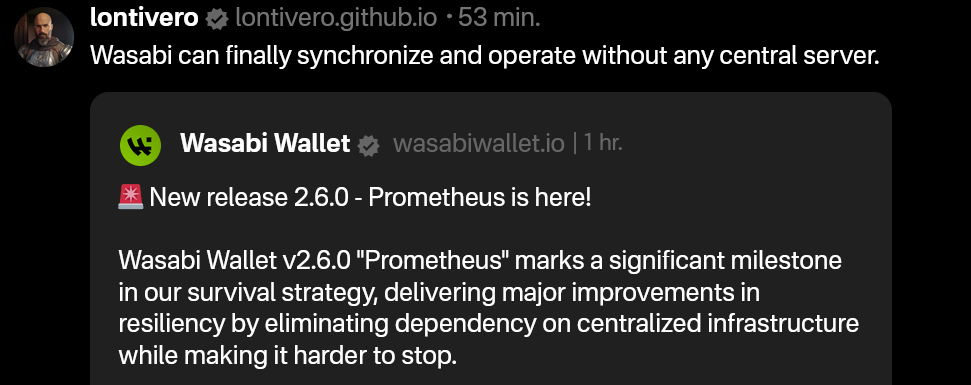
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:35
@ dfa02707:41ca50e3
2025-06-05 18:02:35Contribute to keep No Bullshit Bitcoin news going.
- "Today we're launching the beta version of our multiplatform Nostr browser! Think Google Chrome but for Nostr apps. The beta is our big first step toward this vision," announced Damus.
- This version comes with the Dave Nostr AI assistant, support for zaps and the Nostr Wallet Connect (NWC) wallet interface, full-text note search, GIFs and fullscreen images, multiple media uploads, user tagging, relay list and mute list support, along with a number of other improvements."
"Included in the beta is the Dave, the Nostr AI assistant (its Grok for Nostr). Dave is a new Notedeck browser app that can search and summarize notes from the network. For a full breakdown of everything new, check out our beta launch video."
What's new
- Dave Nostr AI assistant app.
- GIFs.
- Fulltext note search.
- Add full screen images, add zoom, and pan.
- Zaps! NWC/ Wallet UI.
- Introduce last note per pubkey feed (experimental).
- Allow multiple media uploads per selection.
- Major Android improvements (still WIP).
- Added notedeck app sidebar.
- User Tagging.
- Note truncation.
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline.
- Mute list support (reading).
- Relay list support.
- Ctrl-enter to send notes.
- Added relay indexing (relay columns soon).
- Click hashtags to open hashtag timeline.
- Fixed timelines sometimes not updating (stale feeds).
- Fixed UI bounciness when loading profile pictures
- Fixed unselectable post replies.
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:33
@ dfa02707:41ca50e3
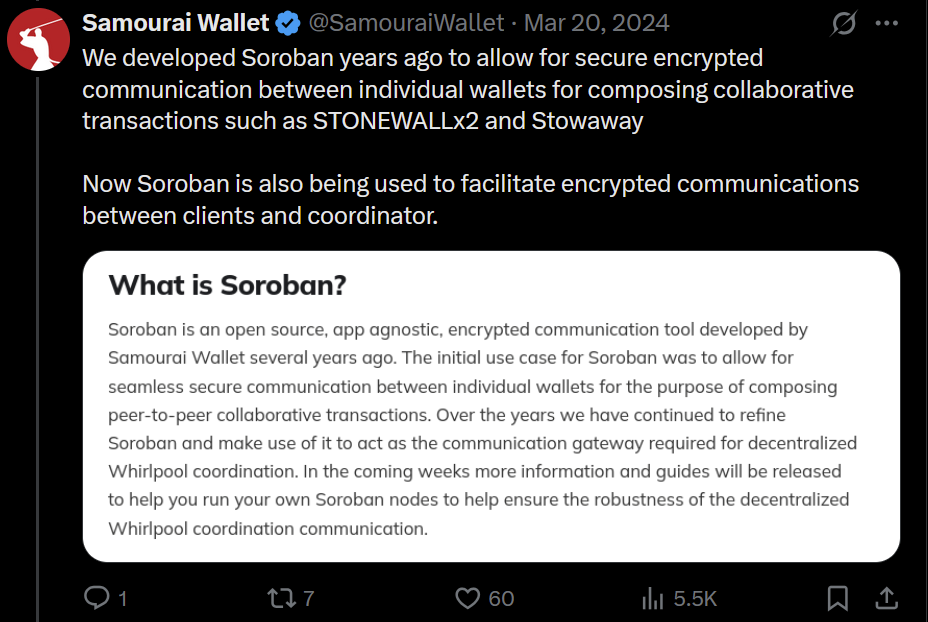
2025-06-05 18:02:33- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ eb0157af:77ab6c55
2025-06-05 18:02:22
@ eb0157af:77ab6c55
2025-06-05 18:02:22The Spanish coffee chain follows in Strategy’s footsteps, aiming for a Bitcoin-first strategy.
Vanadi Coffee SA, a well-known Spanish coffee shop chain, is preparing for a major shift in its business model through a bitcoin investment worth over $1.1 billion. The company plans to transform itself from a simple coffee distributor into an entity centered around the leading cryptocurrency.
Salvador Martí, chairman of the board of directors, has outlined a clear vision for the company’s future, seeking authorization to implement a bitcoin accumulation strategy with a maximum budget of €1 billion, according to documentation submitted to BME Growth.
The strategy involves using convertible financing lines to support the bitcoin acquisition, following the model successfully pioneered by Strategy. Martí has already demonstrated his conviction by purchasing 5 BTC for approximately $500,000 two weeks ago.
Vanadi Coffee’s decision comes at a critical moment for the company, which reported losses of $3.7 million in 2024 — exceeding its annual revenues by nearly $600,000. The GameStop episode offers a relevant case study: the American company, facing similar difficulties, opted to purchase bitcoin through a debt securities issuance, acquiring a total of 4,710 bitcoins.
The corporate bitcoin trend
Vanadi Coffee’s initiative is part of a broader global movement, with companies from various industries embracing bitcoin as a strategic reserve asset. From Chinese logistics firms to football clubs, the phenomenon of corporate adoption is crossing both geographic and sectoral boundaries.
Strategy remains the pioneer of this approach, having demonstrated how a company can completely reinvent itself through bitcoin accumulation. Michael Saylor’s success story has inspired numerous other businesses to consider cryptocurrency not merely as an investment, but as a central pillar of their business strategy.
The next Vanadi Coffee board meeting, scheduled for June 29, will mark a pivotal moment for the Spanish company. Approval of the $1.1 billion strategy could trigger further investments from other corporations.
The post Spanish company Vanadi Coffee bets on Bitcoin: $1.1 billion investment appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-06-05 18:02:02
@ 9ca447d2:fbf5a36d
2025-06-05 18:02:02El Salvador – June 3, 2025 — The grassroots Bitcoin community of El Salvador is proud to announce the return of Bitcoin Week, taking place this November with five dynamic events celebrating Bitcoin adoption, education, and community-led innovation.
Join us for a week of inspiration, collaboration, and impact.

Bitcoin Week 2025 calendar
📍 November 12 – Bitcoin Education Celebration Gala: Kick off the week in style with a luxurious and intimate evening at a high-class dinner, celebrating “proof of work” and the achievements of the Bitcoin education movement.
Expect major plans for the year(s) ahead but also a reflection to past proof-of-work—and don’t miss out on the Great Grassroots Giveaway, included with every ticket.📍 November 13 – Bitcoin Educators Unconference: Hosted for the third time in San Salvador at Cadejo Montaña, this sixth edition of the Educators Unconference embodies our commitment to provide a space for decentralized, community-led conversations.
Join educators and leaders shaping the global Bitcoin conversation!📍 November 14–15 – Adopting Bitcoin: The Network Effect: Now in its fifth year, Adopting Bitcoin returns with a powerful focus on real-world Bitcoin usage across global communities.
This year’s theme—The Network Effect—explores how interconnected local initiatives can spark exponential growth in adoption.📍 November 16 – Visit Bitcoin Beach, El Zonte: Make your way to Bitcoin Beach, the heart of El Salvador’s Bitcoin story. Enjoy a day of connection and discovery in this iconic beachside town. Full details coming soon.
📍 November 22–23 – Economía Bitcoin, Berlín: Head to the town of Berlín, El Salvador for the second edition of Economía Bitcoin, a powerful, small-scale conference and festival focused on circular economies and practical Bitcoin use.
Spend sats freely in town and see how local action drives global impact.With five unique events across three regions in Bitcoin Country, this edition of Bitcoin Week is your chance to experience El Salvador’s Bitcoin journey up close. Whether you’re an educator, builder, Bitcoiner, or simply curious—you’re invited.
Join us this November. Be part of the movement.
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:34
@ dfa02707:41ca50e3
2025-06-05 18:02:34Contribute to keep No Bullshit Bitcoin news going.
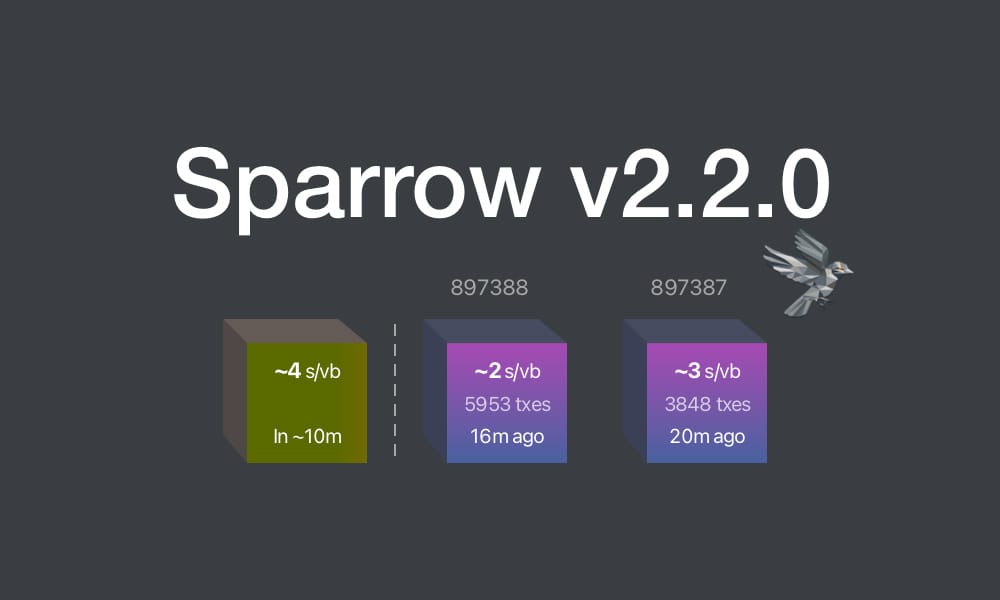
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:41
@ 7f6db517:a4931eda
2025-06-05 18:02:41
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ da8b7de1:c0164aee
2025-06-05 17:39:41
@ da8b7de1:c0164aee
2025-06-05 17:39:41| Régió/Ország | Fő esemény/politika | Forrás | |------------------|--------------------------------------------------------------------------------------------------|-------------| | Egyesült Államok | Végrehajtási rendeletek a nukleáris termelés négyszeresére növeléséről; a nem létfontosságú K+F költségvetésének csökkentése; SMR és mikroreaktor kezdeményezések | world-nuclear-news, nucnet, aoshearman, ans | | Kanada | Engedélyezés új BWRX-300 SMR reaktor építésére Darlingtonban | world-nuclear-news, ans | | Európa | EU tervek az orosz nukleáris importok korlátozására; Westinghouse–Bulgária beszállítói megállapodások | nucnet, world-nuclear-news | | Globális/Világbank | A nukleáris finanszírozási tilalom esetleges feloldása a fejlődő országok számára | globalissues | | Egyesült Királyság| Új kiberbiztonsági jogszabályok a nukleáris szektorban | aoshearman | | Katonaság/Védelem| A védelmi minisztérium cégeket választott ki mikroreaktorok telepítésére | ans |
Források:
world-nuclear-news
nucnet
aoshearman
globalissues
ans -
 @ cae03c48:2a7d6671
2025-06-05 18:01:41
@ cae03c48:2a7d6671
2025-06-05 18:01:41Bitcoin Magazine

Moscow Exchange Launches Bitcoin Futures For Qualified InvestorsThe Moscow Exchange, Russia’s largest exchange group, announced the launch of Bitcoin futures contracts on June 4th, 2025. The new derivatives will allow qualified investors in Russia to gain exposure to bitcoin prices without directly owning it.
The bitcoin futures contracts are cash-settled in Russian rubles and will be tied to the iShares Bitcoin Trust ETF (IBIT) that trades on U.S. exchanges. The IBIT ETF tracks the price of bitcoin, with each share representing 0.00068 bitcoin.
BREAKING:
 Russia’s largest exchange, Moscow Exchange launches #Bitcoin futures trading for qualified investors. pic.twitter.com/J9htJUWpLw
Russia’s largest exchange, Moscow Exchange launches #Bitcoin futures trading for qualified investors. pic.twitter.com/J9htJUWpLw— Bitcoin Magazine (@BitcoinMagazine) June 4, 2025
Trading for the new bitcoin futures kicked off on Wednesday, with the first contracts expiring in September 2025. Each futures contract will be denominated in U.S. dollars per bitcoin but settled in rubles.
The launch of bitcoin futures on the Moscow Exchange comes after increased interest in Bitcoin exposure from Russian financial institutions. In May, Russia’s central bank formally permitted the offering of crypto-linked securities and derivatives to qualified investors. Prior to this, direct investment in Bitcoin was discouraged.
Sberbank, Russia’s largest bank, also announced plans to unveil its own bitcoin futures product in addition to the Moscow Exchange’s offering. The bank is launching exchange-traded notes that track Bitcoin’s price without direct ownership.
Bitcoin futures and other crypto-derivatives have seen surging interest recently as the Bitcoin and crypto industry matures. The move comes as an increasing number of countries have started adding Bitcoin to their reserves.
As Bitcoin adoption increases, investors and financial institutions are seeking more routes to gain exposure to Bitcoin. The launch of futures on the Moscow Exchange provides regulated bitcoin exposure to qualified Russian investors. But direct ownership of “physical” bitcoin remains off limits for most in Russia’s traditional finance sector.
This post Moscow Exchange Launches Bitcoin Futures For Qualified Investors first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ cae03c48:2a7d6671
2025-06-05 18:01:36
@ cae03c48:2a7d6671
2025-06-05 18:01:36Bitcoin Magazine

Semler Scientific Acquires 185 Bitcoin, Increasing Total Holdings to 4,449 BTCToday, Semler Scientific announced it has increased its Bitcoin holdings. The company acquired 185 Bitcoin between May 23 and June 3 for $20 million with an average purchase price of $107,974 per Bitcoin, using proceeds from its at-the-market (ATM) offering program.
JUST IN:
 Public company Semler Scientific purchases an additional 185 #bitcoin for $20 million. pic.twitter.com/Iir6NiNzc8
Public company Semler Scientific purchases an additional 185 #bitcoin for $20 million. pic.twitter.com/Iir6NiNzc8— Bitcoin Magazine (@BitcoinMagazine) June 4, 2025
“We continue to accretively grow our bitcoin arsenal using operating cash flow and proceeds from debt and equity financings,” said the chairman of Semler Scientific Eric Semler. “And we are excited to launch the Semler Scientific dashboard today on our website to provide the public with regularly updated information on our bitcoin holdings and other key metrics.”
Since launching the ATM program in April 2025, Semler has raised approximately $136.2 million under the sales agreement of over 3.6 million shares of its common stock.
As of June 3, 2025, Semler holds 4,449 Bitcoin which were acquired for an amount of $410.0 million, with an average purchase price of $92,158 per Bitcoin. At the time of writing, the market value of these holdings is around $446.2 million.
Eric Semler on X posted, “SMLR acquires 185 Bitcoins for $20 million and has generated BTC Yield of 26.7% YTD. Now holding 4,449 $BTC.”
$SMLR acquires 185 #Bitcoins for $20 million and has generated BTC Yield of 26.7% YTD. Now holding 4,449 $BTC.

— Eric Semler (@SemlerEric) June 4, 2025
Semler Scientific uses the BTC Yield as a key performance indicator (KPI) to help assess the performance of its strategy of acquiring Bitcoin. As of year-to-date, the company has achieved a BTC Yield of 26.7%.
“Semler Scientific believes this KPI can be used to supplement an investor’s understanding of Semler Scientific’s decision to fund the purchase of Bitcoin by issuing additional shares of its common stock or instruments convertible to common stock,” stated the 8-K form.
In Q1 FY2025, Semler Scientific reported a difficult quarter. Revenue came in at $8.8 million, a 44% decrease year-over-year. Operating expenses jumped to $39.9 million from $8.9 million last year, mainly due to a $29.8 million contingent liability tied to the potential settlement with the DOJ. This led to a $31.1 million operating loss, compared to a $7.0 million profit in Q1 2024.
“Our healthcare business is seeing green shoots from the cardiovascular product line that we introduced to our large enterprise customer base this year,” said the CEO of Semler Scientific Doug Murphy-Chutorian. “We are expecting growth and cash generation from these FDA-cleared products and services, which will add to our bitcoin treasury strategy.”
This post Semler Scientific Acquires 185 Bitcoin, Increasing Total Holdings to 4,449 BTC first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 2f5de000:2f9bcef1
2025-06-05 17:33:37
@ 2f5de000:2f9bcef1
2025-06-05 17:33:37I've wanted to write this piece for months. Not because I have anything against Jack Mallers personally - quite the opposite. But because I've watched a pattern emerge in Bitcoin that mirrors one of the most chilling dynamics in Atlas Shrugged: the systematic destruction of our most productive builders by the very people who should be celebrating them.
We are the looters. And Jack might just be our Hank Rearden.
The Underdog's Dilemma
There's a cruel irony in how we treat success in Bitcoin. We champion the underdog, root for the builder in the garage, celebrate the cypherpunk taking on the establishment. But the moment that underdog succeeds - the moment they scale, grow, and inevitably have to navigate the messy realities of the existing system - we turn on them with the ferocity of the same establishment we claim to oppose.\ \ Jack began building Zap (which evolved into Strike) from his parents home in Chicago. Strike has grown into one of the most seamless fiat-to-bitcoin on-ramps for everyday users. No complexity, just pure utility. From day one, he's operated at a level of transparency that would make most CEO's uncomfortable. He's been building in public, taking feedback, admitting mistakes, and iterating - sometimes within hours of criticism.
The Rearden Parallel
In Atlas Shrugged, Hank Rearden creates Rearden Metal - a revolutionary alloy that's stronger, lighter, and more efficient than anything that came before. Instead of celebration, he faces endless scrutiny, regulation, and demands to prove is worthiness. The people who benefit from his innovation spend their time questioning his motives, dissecting his business practices, and demanding he justify his success.
Sound familiar?
Jack comes from a finance background - his father and grandfather were in the industry. This isn't a liability; it's an asset. He understands the beast we're fighting. He's been a Bitcoiner since 2013 with a spotless track record in a space littered with exit scams and broken promises. His values align with proof of work, individualism, and the radical idea that bitcoin is for everyone.
Yet when he helps launch 21 Capital, we don't see innovation - we see betrayal. When he navigates regulatory requirements to build products that can actually reach mainstream adoption, we don't see pragmatism - we see capitulation.
The Scarred Perspective
Our skepticism isn't entirely unfounded. We've been burned before. Mt. Gox, FTX, Three Arrows Capital, Celcius, Terra/ LUNA, BlockFi, Bitconnect, Voyager, QuadrigaCX - the graveyard of Bitcoin is littered with the corpses of trusted institutions. We've learned, painfully, that trust must be earned and verified.
But somewhere along the way, our healthy skepticism has metastasized into destructive paranoia. We've become so focused on protecting ourselves from the next SBF that we're attacking the people building the future we claim to want.
I'm guilty of this myself. I've made scathing attacks on my Nostr feed, comparing Jack to SBF, scrutinising contract clauses about re-hypothecation, and questioning his every move privately. I was viewing his actions through the lens of collective trauma rather than the reality of his long track record.
The Looters Paradox
Here's the uncomfortable truth: we're not just passive observers in this drama. We're active participants. We're the looters.
In Atlas Shrugged, the looters don't necessarily steal directly. They steal time, energy, and focus. They create bureaucracy, demnd endless justification, and burden the productive with the weight of constant explanation. They don't build competing products - they just tear down what others have built.
Everytime we demand Jack explain his business model for the hundredth time, we're stealing his time. Every time we scrutinize his partnerships without offering alternatives, we're creating bureaucracy . Everytime we attack his character rather than his arguments, we're furthering the system we claim to oppose.
The free market will create products whether we like them or not. People will build services that use bitcoin as collateral, create lending products, and navigate regulatory frameworks. The question isn't whether these products will exist - it's whether they'll be built by people who share our values or by those who don't.
The Atlantis Risk
The producers eventually withdraw from society in Atlas Shrugged, retreating to Galt's Gulch (Atlantis) and leaving the looters to face the consequences of their destructive behaviour. The economy collapses because the people who actually build things decided it wasn't worth the hassle anymore.
We're walking dangerously close to this precipice in Bitcoin. We're creating an environment where our most capable builders might just decide it's not worth it. Where the hassle of dealing with our constant scrutiny and bad-faith attacks outweighs the mission of building the future.
Jack has been more patient with our criticism than we deserve. He's addressed concerns publicly, changed the course when necessary, and continued building despite the noise. But patience has limits. At some point, even the most mission-driven builders will ask themselves: "Why am I doing this?"
The Path Forward
I don't know enough about finance to fully understand everything Jack is building with 21 Capital. Neither do most of his critics. But I know enough about Bitcoin to recognise someone who's been fighting the good fight for over a decade.
This doesn't mean we should trust blindly. It doesn't mean we should stop asking questions or demanding transparency. But it does mean we should approach our builders with the same benefit of the doubt we'd want for ourselves.
We need to distinguish between healthy skepticism and destructive paranoia. Between holding people accountable and tearing them down. Between being vigilant and being looters.
The fiat system is the real enemy here. It's massive, entrenched, and infinitely resourcesful. It will adapt, co-opt, and corrupt everything it touches. Fighting it requires builders who are willing to get their hands dirty, navigate imperfect systems, and make pragmatic compromises while holding onto their core values.
We can continue to be looters, tearing down what we don't understand and driving our best builders toward their own version of Atlantis. Or we can be what we claim to be: supporters of the free market, believers of proof of work, and champions of those building the future.
Don't trust. Verify. But remember: verification works both ways.
-
 @ cae03c48:2a7d6671
2025-06-05 18:01:28
@ cae03c48:2a7d6671
2025-06-05 18:01:28Bitcoin Magazine

BTCPay Server: The Backbone of Bitcoin Commerce, 2025The genesis story of BTCPay Server is without a doubt one of the most iconic moments in Bitcoin history. A single developer, feeling betrayed by Bitpay, a bitcoin payments processing giant and its attempt at co-opting Bitcoin, declared economic war on the company in a tweet that will never be forgotten by the Bitcoin industry; “This is lies, my trust in you is broken, I will make you obsolete.”
Nicolas Dorier went on to create one of the most widely distributed open source projects in the Bitcoin industry and perhaps the invoicing and payments industry as a whole: BTCPay Server. Much has been written about the context and motivation behind Dorier’s founding of the project — there’s even a documentary about it.
What’s seldom highlighted is how ambitious a project BTCPay Server is, how feature-rich it has become and how deeply integrated it is with the industry. In fact, it is easy to forget that as an open source project with no centralized database of users, BTCPay Server is both a massive privacy upgrade for its users and represents the removal of a fundamental middleman processing payments. As a result, Dorier and the BTCPay Server community have created a public goods infrastructure — a kind of commons of payment processing — that provides users real value by saving them fees, and providing them a much smoother user experience given that no personal information is required for the payments to flow.
Humbly described on their website as “a self-hosted, open-source cryptocurrency payment processor,” BTCPay Server is an invoicing and accounting system for merchants, a fully featured Bitcoin wallet with full node capabilities; on-chain, Lightning Network and Liquid Network support; hardware wallet support; and a modular plugin system. The plugins in particular extend the core of BTCPay Server into a wide range of niches. They also integrate into e-commerce giants such as WooCommerce and Shopify.
It is somewhat difficult to gauge the success and scope of BTCPay Server. Because it is a self-hosted platform that does not capture customer data of any kind — it has no central cloud service as other payment processors do — our view into its success is somewhat limited.
However, we can get a sense of their reach by proxy of other metrics, for example, their primary software repository has had over 170 open source contributors, with 8,393 commits at the time of writing.
As of 2025, BTCPay Server has had one million downloads directly from its GitHub repository, which does not account for cloud providers of the software as hosted by companies like Voltage or Lunanode. It is also often the case that one instance of BTCPay Server serves multiple merchants and hosts multiple stores simultaneously.
R0ckstardev, one of the top contributors to the project, told Bitcoin Magazine that there could be hundreds of thousands of instances of BTCPay Server running throughout the world. Tobe Chileta, a contributor to the project, also told Bitcoin Magazine that “of the seven continents of the world, I think it is only Antarctica that I haven’t seen someone run BTCPay server.” He added, “I’m certain we have merchants running in Asia, Africa, North America, South America, Europe and Australia.”
Companies
BTCPay Server’s website business directory, while far from exhaustive, covers hundreds of merchants onboarded. The BTCPay Server community also does regular case studies of user cohorts or major merchants that use the software, documenting their integration and story in their case studies page. It gives fantastic insights into a variety of Bitcoin communities throughout the world and includes useful guides on how to replicate various results and implementations.
Namecheap, for example, boasted over 70 million dollars’ of bitcoin volume since their integration of BTCPay Server. From May 18, 2020, to October 2024 they clocked in 1.1m transactions in total with over 500,000 users paying in bitcoin, resulting in over $73 million in revenue through payments made from over 200 countries.
BTC Inc, the parent company of the biggest Bitcoin conference in the world, has for years been setting up BTCPay Server for its merchants, and even has a one-hour behind-the-scenes documentary on the complexities of setting up dozens of merchants at a conference (filmed during the Nashville 2024 Bitcoin conference). The event saw over 25,000 attendees, including the 47th president of the U.S., Donald J. Trump.
In this most recent Bitcoin 2025 conference in Las Vegas, BTCPay Server was used to process a new world record of Bitcoin transactions within an eight-hour period, with 4,187 transactions in total. The initial target was 4,000 transactions and was set by the Guinness World Records organization.
Integrations and Plugins
One of the most important dimensions of BTCPay Server is its plugin system. Given the wide variety of ways companies can interact with Bitcoin, the developer community has optimized the BTCPay Server code toward a plugin model that developers can build for with a well-documented set of GitHub repos and an API. Today there are over 30 plugins available on BTCPay Server. Here are some of the greatest hits:
Boltz Swap Exchange Plugin
Boltz is an atomic swap exchange focused on the various Bitcoin layers such as Liquid, Lightning, Rootstock and of course Bitcoin on-chain. It has gained prominence of late as a very simple solution to the channel rebalancing challenges Lightning wallets face. R0ckstardev told Bitcoin Magazine that he is particularly impressed with the Boltz integration, and even tweeted as much earlier this year.
I've recently been going through the code of @Boltzhq plugin for @BtcpayServer, what jackstar12 & @kilrau have done there is an absolutely l33t engineering.
It's a literal crime against humanity that what they've done was not featured more in Bitcoin media.
— Uncle Rockstar Developer (@r0ckstardev) April 24, 2025
Branded as a noncustodial Bitcoin Bridge, Boltz allows users to swap between different Bitcoin layers while retaining maximum control of their funds, using atomic swap technology that eliminates third-party trust across crypto-native payments. For example, you can use Boltz via BTCPay Server to make a Lightning payment, where the sats are initially held at rest in a Liquid network wallet and are pulled from that balance by the Boltz plugin. The L-BTC is atomically swapped for sats on the Lightning Network via the Boltz exchange and the satoshis flow to the end recipient. This whole process is effectively noncustodial.
This is the same type of “lightning service provider” style infrastructure with which Breez wallet recently announced integration. While it is not quite as cheap as a user-operated Lightning node can be in the best of cases, it is far easier to set up and run — only demanding a few clicks on the BTCPay Server interface. As far as BTCPay Server is concerned, this Boltz plugin represents a full Lightning node, integrating natively with the invoicing and accounting layers.
This tech also scales quite well: One BTCPay Server admin can support many different merchants and not even have to run or manage a standard Lightning node, since the plugin supports automated liquidity management.
The Bolt Cards Plugin
The Bolt card, a company and product created by the Coincenter exchange, has come into prominence recently thanks to its unique graphics and the laser-eyes that light up on tap-to-pay. They, too, have a BTCPay Server plugin that lets users manage and connect these cool NFC cards to their wallets via the plugin.
BITCOIN IS MONEY.
AND AT @THEBITCOINCONF WE WILL PAY IN STYLE, WITH @JACK LASER-EYES BOLT CARDS.
ONLY 1,000 AVAILABLE, GET YOURS ON MAY 28TH. [pic.twitter.com/fDrZW5TGCv](https:
-
 @ cae03c48:2a7d6671
2025-06-05 18:01:22
@ cae03c48:2a7d6671
2025-06-05 18:01:22Bitcoin Magazine

JPMorgan to Offer Clients Financing Against Bitcoin & Crypto ETFsJPMorgan Chase & Co. plans to allow its trading and wealth-management clients to use cryptocurrency-linked assets, including spot Bitcoin exchange-traded funds (ETFs), as collateral for loans, according to Bloomberg.
 JPMorgan Plans to Offer Clients Financing Against Crypto ETFs pic.twitter.com/QpausRiHxM
JPMorgan Plans to Offer Clients Financing Against Crypto ETFs pic.twitter.com/QpausRiHxM— matthew sigel, recovering CFA (@matthew_sigel) June 4, 2025
The bank will begin with BlackRock’s iShares Bitcoin Trust (IBIT), and additional ETFs are expected to be added over time. The policy will apply globally, spanning all client segments—from individual retail accounts to investors.
In addition to the lending change, JPMorgan will begin factoring crypto holdings into overall net worth and liquid asset evaluations, placing them on par with stocks, vehicles, or fine art when determining loan eligibility, according to those familiar with the matter.
This development marks a formal expansion of what had previously been permitted on a limited, case-by-case basis. The bank’s new approach comes as other major financial institutions, including Morgan Stanley, explore ways to integrate crypto offerings more broadly. Last month, Bloomberg also reported that Morgan Stanley plans to bring crypto trading to its E*Trade platform.
The shift also reflects changes in the U.S. regulatory environment. Since returning to office, President Donald Trump’s administration has taken a more favorable stance toward digital assets. Spot Bitcoin ETFs, first introduced in January 2024, have seen rapid growth and now manage a combined $128 billion in assets, making them among the most successful ETF launches to date.

Bitcoin’s price has also risen significantly in recent months, reaching a record $111,980 in May 2025.
JPMorgan was among the first large U.S. banks to experiment with blockchain technology and maintains relationships with firms such as Coinbase. This latest decision allows more digital assets into the bank’s lending framework.
While JPMorgan CEO Jamie Dimon has remained publicly skeptical of Bitcoin, he has consistently emphasized clients’ right to access the asset. Speaking at the firm’s investor day in May, Dimon stated, “I’m not a fan of Bitcoin.” He went on to say, “I don’t think we should smoke, but I defend your right to smoke. I defend your right to buy Bitcoin, go at it.”
This post JPMorgan to Offer Clients Financing Against Bitcoin & Crypto ETFs first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:40
@ 7f6db517:a4931eda
2025-06-05 18:02:40

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-05 18:01:15
@ cae03c48:2a7d6671
2025-06-05 18:01:15Bitcoin Magazine

Bitcoin Layer 2: The Key To Scaling BitcoinBitcoin, and for that matter all blockchains, do not scale. It is a fundamental limitation of blockchain based systems that they are incapable of facilitating transactional use at a truly global scale without completely sacrificing the decentralization and verifiability that make them valuable in the first place.
This has been an existential issue that Bitcoiners have grappled with from the very beginning of Bitcoin. This is a comment from James A. Donald, a Canadian cypherpunk who was the first person to reply to Satoshi’s original post on the cryptography mailing list:
Satoshi Nakamoto wrote:
“The bandwidth might not be as prohibitive as you
think. A typical transaction would be about 400 bytes
(ECC is nicely compact). Each transaction has to be
broadcast twice, so lets say 1KB per transaction.
Visa processed 37 billion transactions in FY2008, or
an average of 100 million transactions per day. That
many transactions would take 100GB of bandwidth, or
the size of 12 DVD or 2 HD quality movies, or about
$18 worth of bandwidth at current prices.”The trouble is, you are comparing with the Bankcard
network.But a new currency cannot compete directly with an old,
because network effects favor the old.You have to go where Bankcard does not go.
At present, file sharing works by barter for bits. This,
however requires the double coincidence of wants. People
only upload files they are downloading, and once the
download is complete, stop seeding. So only active
files, files that quite a lot of people want at the same
time, are available.File sharing requires extremely cheap transactions,
several transactions per second per client, day in and
day out, with monthly transaction costs being very small
per client, so to support file sharing on bitcoins, we
will need a layer of account money on top of the
bitcoins, supporting transactions of a hundred
thousandth the size of the smallest coin, and to support
anonymity, chaumian money on top of the account money.Let us call a bitcoin bank a bink. The bitcoins stand
in the same relation to account money as gold stood in
the days of the gold standard. The binks, not trusting
each other to be liquid when liquidity is most needed,
settle out any net discrepancies with each other by
moving bit coins around once every hundred thousand
seconds or so, so bitcoins do not change owners that
often, Most transactions cancel out at the account
level. The binks demand bitcoins of each other only
because they don’t want to hold account money for too
long. So a relatively small amount of bitcoins
infrequently transacted can support a somewhat larger
amount of account money frequently transacted.Despite the era of the Blocksize Wars, the big blockers, and the naive assumptions by many early Bitcoiners that simply raising the blocksize was a viable solution to scale the system, it has been understood by competent observers and engineers from the very beginning that this would undermine the core value proposition of that made it useful in the first place. Hal Finney also spoke of the need for such a settlement layer on top.
Scaling in layers has always been the only rational plan to make Bitcoin work in the long term, but for a long period of Bitcoin’s early history how to do so without relying on trusted third parties was an elusive problem.
One of the first ideas on how to do this was sidechains, independent blockchains with a peg to facilitate locking bitcoin on the mainchain to utilize on the sidechain, and at any point unlocking funds on the mainchain to move them back by proving legitimate control of bitcoin on the sidechain. These systems however have yet to achieve a way to operate a peg without either 1) introducing some form of trusted third party, no matter how well mitigated, or 2) creating centralization pressure for the primary Bitcoin network.
Since those early days there have been many more ideas developed that have found better ways to peg into second layer systems, specifically schemes like the Lightning Network and Ark which allow end users to unilaterally exit back to the mainchain without needing the permission or approval of some operator.
Scaling Bitcoin in a way that facilitates higher transactional volumes without degrading the security properties of Bitcoin to the point of being indistinguishable from third party operated custodians is one of the most critical problems to solve in order for Bitcoin to truly succeed in the long term.
This article series will explore the architectures of different Layer 2 systems for Bitcoin, both those deployed live on the network right now and those that are simply design proposals at this point.
Listed below are the systems I will be covering. The design space of Layer 2s is much more expansive than many people are familiar with, so this list should not be taken as comprehensive and complete, and will be updated over time to reflect additional Layer 2s that are covered.
- Ark
- Statechains
- Lightning Network
- Sidechains
- Clique
- Rollups
- Client Side Validated Systems
- Ecash
- Custodial Systems
- Physical Bearer Instruments
This post Bitcoin Layer 2: The Key To Scaling Bitcoin first appeared on Bitcoin Magazine and is written by Shinobi.
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:40
@ 7f6db517:a4931eda
2025-06-05 18:02:40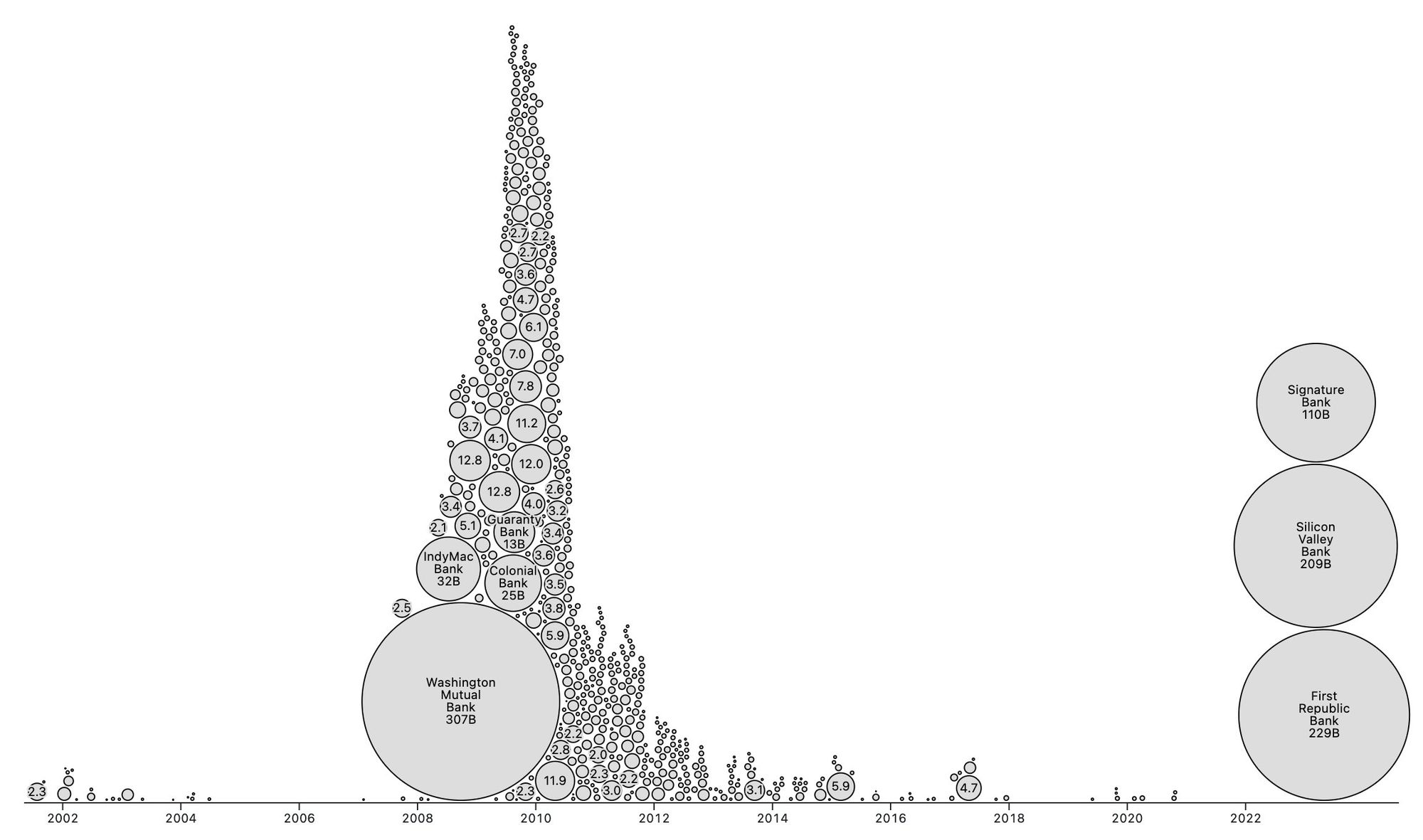
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-05 18:01:05
@ cae03c48:2a7d6671
2025-06-05 18:01:05Bitcoin Magazine

Support The Blockchain Regulatory Certainty Act (BRCA) To Protect Noncustodial ServicesWith a lot of regulatory talk centered around The GENIUS Act and The CLARITY Act (the market structure bill) right now, it’s important that Bitcoin enthusiasts also pay attention to and support The Blockchain Regulatory Certainty Act (BRCA) — H.R. 1747.
The act, which was reintroduced to Congress on May 21, 2025 by Rep. Tom Emmer (R-MN) and Rep. Ritchie Torres (D-NY), provides “safe harbor from licensing and registration for certain non-controlling blockchain developers and providers of blockchain services.”
Critical Bitcoin legislation was introduced last week & it needs our support

The Blockchain Regulatory Certainty Act (BRCA) by @GOPMajorityWhip and @RitchieTorres protects self-custody developers, miners, and nodes from being classified as money transmitters.
Thread
 pic.twitter.com/cJ8Ogno3h5
pic.twitter.com/cJ8Ogno3h5— Nick Neuman (@Nneuman) May 30, 2025
It also stipulates that no blockchain developer or provider of a blockchain service shall be treated as a money transmitter unless the developers or providers behind the project have control over user funds.
This bill is relevant because the developers for both Samourai Wallet and Tornado Cash are currently facing charges for operating unlicensed money transmitter businesses, despite the fact that the developers for neither of these technologies ever had control over user funds.
It’s also important because, under the Biden administration, the U.S. Department of Justice (DoJ) didn’t just classify privacy services as money transmitters, but ancillary services such as Lightning nodes, rollup sequencers, and other Bitcoin and blockchain technology, as well.
If the BRCA isn’t enacted into law, there is a risk that all Bitcoin and crypto wallets as well as other noncustodial services and technologies will be made illegal and/or subject to KYC/AML laws.
While Rep. Emmer and Rep. Torres’ reintroducing this bill is a positive step, the congressmen need our help in making the BRCA a priority for this current Congress.
To help, go to SaveOurWallets.org and follow the directions on the website to contact the elected officials that represent your district and state in the federal government and tell them that you would like to see them support the BRCA.
But they need our help, we need to make clear that the Blockchain Regulatory Certainty Act is *the* priority this Congress for our space. Go to https://t.co/fXVqSQ2nUv, put in your ZIP code, and make a quick call. It works.
— saveourwallets (@saveourwalets) June 3, 2025
If this act doesn’t pass, we will face significant hurdles regarding the scaling of Bitcoin and other blockchains as well as around privacy.
Yes, yes, I know some of you are saying to yourselves Bitcoin will win regardless of our actions (or that it’s already won) and that we don’t need to engage with politicians in the process.
I’m here to say 1.) this isn’t necessarily true, 2.) there are four developers currently facing trial (the Samourai and Tornado Cash developers) and pushing to get this bill passed may help them, 3.) if this bill doesn’t pass, scaling Bitcoin may be much more difficult, and 4.) there’s a reality in which we give up a lot of our legal right to privacy when using Bitcoin if the bill doesn’t pass.
So, with these points in mind, pick up the phone and/or send an email to your elected representatives and tell them you’d like to see them support the BRCA.
This article is a Take. Opinions expressed are entirely the author’s and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
This post Support The Blockchain Regulatory Certainty Act (BRCA) To Protect Noncustodial Services first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ cae03c48:2a7d6671
2025-06-05 18:00:54
@ cae03c48:2a7d6671
2025-06-05 18:00:54Bitcoin Magazine

Matador Technologies Raises C$1.64M To Invest in Their Bitcoin ReserveMatador Technologies Inc. (TSXV: MATA, OTCQB: MATAF), a Bitcoin-focused tech company, announced that it has closed the second tranche of its non-brokered private placement, raising C$1,644,300 through the issuance of 2,652,097 units at a price of $0.62 per unit, with the proceeds going towards investing in their Bitcoin reserve.
 Matador (TSXV: MATA | OTCQB: MATAF | FSE: IU3) closes $1.64M second tranche at $0.62/unit
Matador (TSXV: MATA | OTCQB: MATAF | FSE: IU3) closes $1.64M second tranche at $0.62/unit
 Each unit: 1 share + ½ warrant @ $0.77
Each unit: 1 share + ½ warrant @ $0.77
Proceeds:
 Buy more Bitcoin
Buy more Bitcoin
 Expand gold & Grammies
Expand gold & Grammies
 General corporate growth
General corporate growth  https://t.co/nUm0bFWtO0#Bitcoin #TreasuryStrategy…
https://t.co/nUm0bFWtO0#Bitcoin #TreasuryStrategy…— Matador Technologies (@buymatador) June 4, 2025
“Each Unit consists of one common share and one-half of one common share purchase warrant,” stated in the press release. “Each Warrant entitles the holder to acquire one additional common share of the Company at a price of $0.77 for a period of twelve months from the date of issuance.”
The warrants are subject to acceleration if Matador’s shares trade at or above $1.15 for five consecutive trading days at any time following the date which is four months and one day after the closing date.
The securities from the second tranche are under a hold period that lasts until October 5, 2025. As part of the deal, the company also paid finder’s fees totaling $95,582 and issued 152,165 broker warrants on the same terms.
This follows the first tranche of the offering, announced on May 30, 2025, which included a CAD$1.5 million investment from Arrington Capital, a digital asset management firm co-founded by Michael Arrington.
“We’re thrilled to welcome Arrington Capital as a strategic investor,” said the CEO of Matador Technologies Inc. Deven Soni. “Their deep conviction in the Bitcoin ecosystem and global perspective on digital assets align perfectly with Matador’s vision. This investment enhances our ability to accelerate development of Bitcoin-native financial products and scale our platform globally.”
In that tranche, Matador issued 2,419,354 units under the same terms. Each including one common share and one-half warrant, with full warrants exercisable at $0.77 for one year. Like the second tranche, those warrants are also subject to acceleration if the share price hits $1.15 for five consecutive trading days following the initial four-month period.
“This is more than just a capital raise—it’s a signal that the world’s top digital asset investors see the same future we do,” said the Chief Visionary Officer of Matador Mark Moss.
“At Matador, we believe the next wave of global financial infrastructure will be built on digital assets,” commented Moss. “By aligning with HODL, we’re not just expanding geographically—we’re expanding the reach of the digital assets’ ecosystem into a key innovation hub.”
This post Matador Technologies Raises C$1.64M To Invest in Their Bitcoin Reserve first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-06-05 18:00:44
@ cae03c48:2a7d6671
2025-06-05 18:00:44Bitcoin Magazine

Botanix Launches Federated Sidechain with 16 Members On TestnetBotanix Labs has launched Botanix on testnet as a federated sidechain built on Bitcoin with a 16-node founding federation that includes XBTO, Fireblocks, Antpool, UTXO Management, and other entities (full list below).
The federation ensures that no single entity — including Botanix Labs — controls the network. Botanix Labs has relinquished operational responsibilities, transferring governance and consensus to the node operators. The network plans to evolve into a dynamic federation that supports hundreds of nodes, with the long-term goal of enabling anyone to run a Botanix node. The network’s mainnet is scheduled to launch later this quarter.
Willem Schroé, CEO and co-founder of Botanix Labs, stated in a press release that, “The Bitcoin economy cannot be built on centralized rails. With this 16-node founding federation, we’ve stripped out centralized control and laid the groundwork for a fully permissionless future.”
Botanix’s design emphasizes resilience, with geographically distributed nodes and different kinds of security hardware to minimize single points of failure. The goal is to support consistent availability and uncensorable transaction processing, aligning with Bitcoin’s principles of security and open access. Their use of what they call the “Spiderchain” protocol enables Ethereum Virtual Machine compatibility, allowing applications like lending and staking directly on the network without wrapped assets or bridges.
Philippe Bekhazi, co-founder and CEO of XBTO, commented, “Institutional interest in Bitcoin continues to grow, but that growth depends on secure, decentralized infrastructure that can meet the standards of professional markets.”
Bekhazi also noted XBTO’s commitment to supporting Botanix.
Founded in 2023, Botanix Labs developed the Spiderchain protocol and initiated Botanix. With the network now independently operated, the lab focuses on research, developer tools, and ecosystem support. Botanix enables developers to build financial applications while maintaining Bitcoin’s base layer integrity.
The network’s decentralized structure supports scalability and security for Bitcoin-related applications. As Botanix prepares for its mainnet launch, it aims to expand its federation and move toward further decentralization.
The full founding Botanix federation includes Botanix, Galaxy, Fireblocks, Alchemy, XBTO, Antpool, UTXO Management, Kiln, Chorus One, UndefinedXBlockPI, DAIC, Pier Two, Stakin, Vertex, Stake.fish, and Hashkey Cloud.
Bitcoin Magazine is wholly owned by BTC Inc., which operates UTXO Management, a regulated capital allocator focused on the digital assets industry. UTXO invests in a variety of Bitcoin businesses, and maintains significant holdings in digital assets.
This post Botanix Launches Federated Sidechain with 16 Members On Testnet first appeared on Bitcoin Magazine and is written by Juan Galt.
-
 @ cae03c48:2a7d6671
2025-06-05 18:00:34
@ cae03c48:2a7d6671
2025-06-05 18:00:34Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:14:50
@ e2c72a5a:bfacb2ee
2025-06-05 17:14:50The silent revolution: Ethereum's pivot to 'digital oil' could redefine crypto's future. While Bitcoin grabs headlines as digital gold, Ethereum is quietly transforming into something potentially more valuable—the essential infrastructure powering our digital economy. Ryan Berckmans reveals Ethereum's strategic shift from being just another cryptocurrency to becoming the foundation for stablecoins, tokenized assets, and global financial systems. With $480 billion in stablecoin volume and institutional players entering the space, Ethereum isn't just competing with Bitcoin—it's creating an entirely different value proposition. The question isn't whether ETH will hit $3K, but whether we're underestimating its long-term potential as the backbone of digital finance. Are you positioning yourself for the real crypto revolution happening right under our noses?
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:39
@ 7f6db517:a4931eda
2025-06-05 18:02:39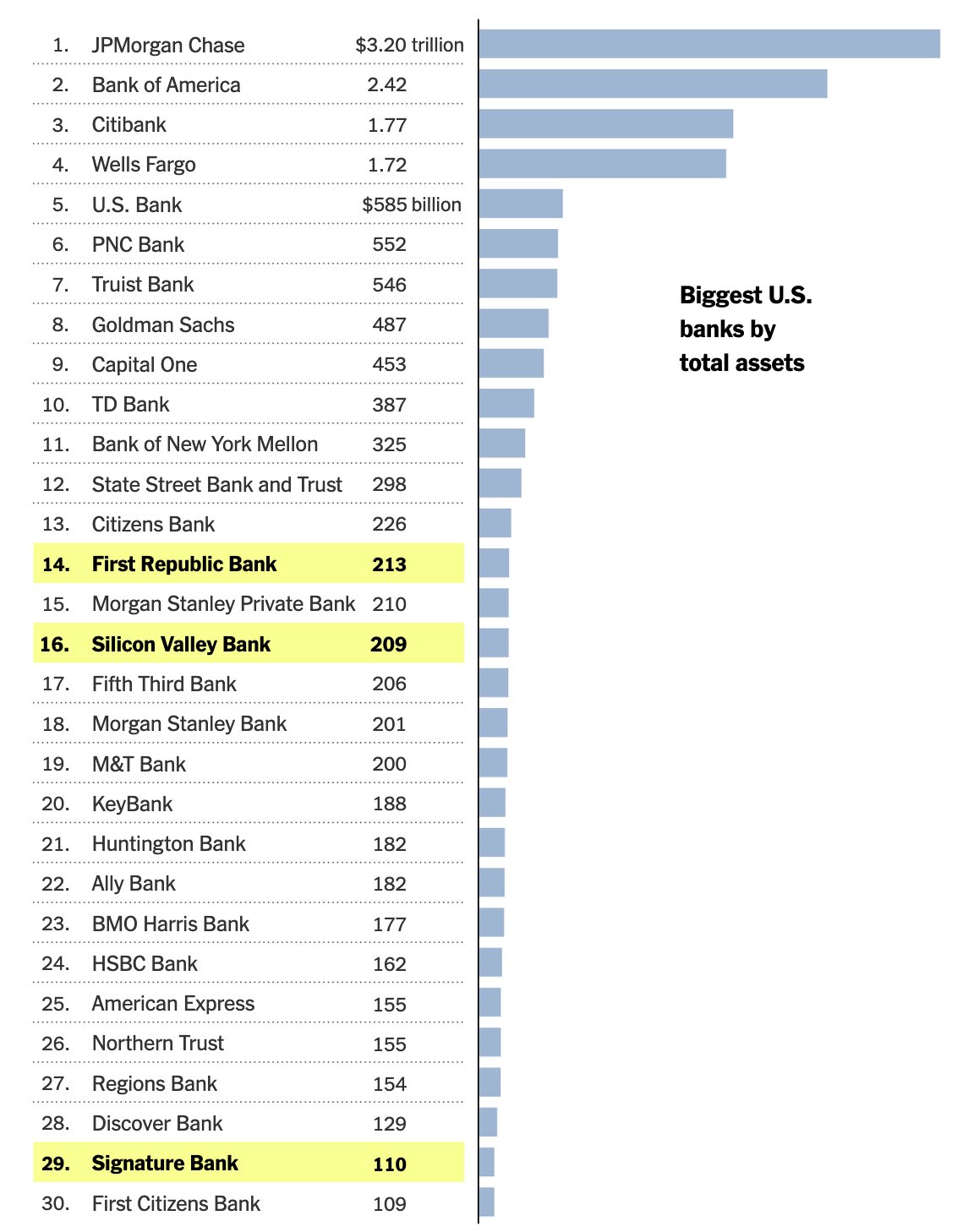
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-05 18:00:23
@ cae03c48:2a7d6671
2025-06-05 18:00:23Bitcoin Magazine

Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in BitcoinMeanwhile Insurance Bitcoin (Bermuda) Limited (“Meanwhile”) announced it has become the first company in the world to release externally audited financial statements denominated entirely in Bitcoin. According to the announcement, the company reported 220.4 BTC in assets and 25.29 BTC in net income for 2024, a 300% year over year increase.
Today marks a global first & historic event for us, along with the public release of our 2024 audited financial statements, covering our 1st year of sales.
As the 1st company in the world to have Bitcoin-denominated financial statements externally audited, we are excited to…
— meanwhile | Bitcoin Life Insurance (@meanwhilelife) June 5, 2025
“We’ve just made history as the first company in the world to have Bitcoin-denominated financial statements externally audited,” said Zac Townsend, CEO of Meanwhile. “This is an important, foundational step in reimagining the financial system based on a single, global, decentralized standard outside the control of any one government.”
The financial statements were audited by Harris & Trotter LLP and its digital asset division ht.digital. Meanwhile’s financials also comply with Bermuda’s Insurance Act 1978, noting that their BTC denominated financials were approved and comply with official guidelines. The firm, fully licensed by the Bermuda Monetary Authority (BMA), operates entirely in BTC and is prohibited from liquidating Bitcoin assets except through policyholder claims, positioning it as a long term holder.
“As the first regulated Bitcoin life insurance company, we view the BTC held by Meanwhile as inherently long-term in nature—primarily held to support the Company’s insurance liabilities over decades,” Townsend added. “This makes it significantly ‘stickier’ and resistant to market pressures compared to the BTC held by other companies as part of their treasury management strategies.”
Meanwhile’s 2024 financials also revealed 23.02 BTC in net premiums and 4.35 BTC in investment income, showing that its model not only preserves Bitcoin, but earns it. The company’s reserves (also held in BTC) were reviewed and approved by Willis Towers Watson (WTW).
Meanwhile also offers a Bitcoin Whole Life insurance product that allows policyholders to save, borrow, and build legacy wealth—entirely in BTC, and has plans to expand globally in 2025.
“We are incredibly proud of today’s news as it underscores how Meanwhile is at the forefront of the next phase of the convergence between Bitcoin and institutional financial markets,” said Tia Beckmann, CFO of Meanwhile. “Now having generated net income in BTC, we have demonstrated that we are earning it through a sustainable insurance business model designed for the long term.”
This post Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:11:03
@ e2c72a5a:bfacb2ee
2025-06-05 17:11:03The $220 million crypto heist that took just minutes reveals a fatal flaw in DeFi security. While blockchain tech promises trustless transactions, the Cetus DEX exploit on Sui exposed how a single undetected bug in a math library became catastrophic. What's truly alarming isn't the hack itself but the revelation from Curve's founder that professional hackers-for-hire are now coordinating sophisticated cross-platform attacks. This signals a dangerous evolution in crypto threats where vulnerabilities aren't just discovered—they're hunted by organized teams with specialized skills. The industry faces a stark choice: invest aggressively in preventative security or watch as billions more vanish in seconds. Is your crypto truly safe, or just waiting for the right hacker to find its weakness?
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:38
@ 7f6db517:a4931eda
2025-06-05 18:02:38
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-05 18:01:56
@ b1ddb4d7:471244e7
2025-06-05 18:01:56When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:37
@ dfa02707:41ca50e3
2025-06-05 18:02:37Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 7f6db517:a4931eda
2025-06-05 18:02:41
@ 7f6db517:a4931eda
2025-06-05 18:02:41
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-05 17:01:42
@ 7f6db517:a4931eda
2025-06-05 17:01:42
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-05 17:01:41
@ 7f6db517:a4931eda
2025-06-05 17:01:41
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:00:01
@ e2c72a5a:bfacb2ee
2025-06-05 17:00:01Forget Lambos, think real estate tokens.
A European fund just dropped $3.4 million on tokenized real estate, marking the first time big money directly bought retail available tokens. This isn't just about crypto hype; it's about institutions embracing regulated crypto assets. Real World Assets (RWAs) are booming, up 260% this year, fueled by clearer US crypto rules. This surge pushes the tokenization sector past $23 billion.
Is this the start of crypto's mainstream moment?
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:40
@ 7f6db517:a4931eda
2025-06-05 18:02:40
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-05 18:02:40
@ 7f6db517:a4931eda
2025-06-05 18:02:40
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:54:43
@ e2c72a5a:bfacb2ee
2025-06-05 16:54:43Think your crypto is FDIC insured like your bank account? Big mistake. Crypto's wild west demands you be your own bank and security guard.
Crypto trading involves buying, selling, and exchanging digital currencies like Bitcoin or Ethereum, aiming to profit from price fluctuations. Security is paramount. Understand basic concepts like wallets (digital storage for your crypto), private keys (passwords to access your crypto), and blockchain (the technology that records all transactions).
Real world applications include using crypto for online purchases, international money transfers, and decentralized finance (DeFi) services like lending and borrowing. Current trends include the rise of DeFi, NFTs (non-fungible tokens), and increasing institutional investment.
Best practices? Use strong, unique passwords, enable two factor authentication (2FA) on all accounts, and store most of your crypto in cold wallets (offline storage) to protect against hacking. Be wary of phishing scams and fake websites. Never share your private keys or seed phrases.
Misconceptions? Crypto is not anonymous, transactions are not easily reversible, and past performance is not indicative of future results. Also, remember that regulations are evolving, so stay informed.
With crypto hacks on the rise, are you truly ready to secure your digital fortune, or are you leaving the door open for the next billion dollar heist?
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:37
@ dfa02707:41ca50e3
2025-06-05 18:02:37
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ dfa02707:41ca50e3
2025-06-05 18:02:35
@ dfa02707:41ca50e3
2025-06-05 18:02:35Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 7f6db517:a4931eda
2025-06-05 17:01:41
@ 7f6db517:a4931eda
2025-06-05 17:01:41

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:50:08
@ e2c72a5a:bfacb2ee
2025-06-05 16:50:08Think crypto is just magic internet money? Think again.
Tokenomics is the secret sauce that makes or breaks a crypto project. It is the study of how tokens are created, distributed, and used within a blockchain ecosystem. Imagine it as the economic policy of a digital nation, dictating everything from supply and demand to user incentives.
Key features include supply caps, distribution models, utility, and burn mechanisms. A well designed token economy incentivizes user behavior, secures the network, and fosters long term growth. Poor tokenomics? It can lead to manipulation and project failure.
Zero Knowledge Proofs are like showing you know a password without revealing the password itself. This tech allows for private and secure transactions, verifying data without exposing the data itself. Think of voting systems where your vote stays secret, or supply chains where product details are confirmed without revealing the supplier.
Want to dive deeper into the economics of crypto? What project has the most interesting tokenomics you have seen?
-
 @ 7f6db517:a4931eda
2025-06-05 17:01:40
@ 7f6db517:a4931eda
2025-06-05 17:01:40
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:46:19
@ e2c72a5a:bfacb2ee
2025-06-05 16:46:19Think proving you're over 21 without showing your ID is impossible? Zero Knowledge Proofs make it real.
Zero Knowledge Proofs let you prove something is true without revealing the information itself. Imagine proving you know a password without saying it. It's like magic, but it's math.
They're used in crypto for private transactions, secure voting, and faster blockchains. Zcash and Aztec use them to hide transaction details. StarkWare uses them to make Ethereum faster.
But here's the twist: zk STARKs don't need a trusted setup, unlike zk SNARKs. This makes them more secure and decentralized.
Misconception alert: ZKPs aren't just for privacy. They also boost scalability and interoperability.
Want to dive deeper into this mind bending tech? What other secrets can ZKPs unlock?
-
 @ 7f6db517:a4931eda
2025-06-05 17:01:39
@ 7f6db517:a4931eda
2025-06-05 17:01:39
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-06-05 17:01:35
@ dfa02707:41ca50e3
2025-06-05 17:01:35News
- Wallet of Satoshi teases a comeback in the US market with a non-custodial product. According to an announcement on X, the widely popular custodial Lightning wallet is preparing to re-enter the United States market with a non-custodial wallet. It is unclear whether the product will be open-source, but the project has clarified that "there will be no KYC on any Wallet of Satoshi, ever!" Wallet of Satoshi ceased serving customers in the United States in November 2023.
- Vulnerability disclosure: Remote crash due to addr message spam in Bitcoin Core versions before v29. Bitcoin Core developer Antoine Poinsot disclosed an integer overflow bug that crashes a node if spammed with addr messages over an extended period. A fix was released on April 14, 2025, in Bitcoin Core v29.0. The issue is rated Low severity.
- Coinbase Know Your Customer (KYC) data leak. The U.S. Department of Justice, including its Criminal Division in Washington, is investigating a cyberattack on Coinbase. The incident involved cybercriminals attempting to extort $20 million from Coinbase to prevent stolen customer data from being leaked online. Although the data breach affected less than 1% of the exchange's users, Coinbase now faces at least six lawsuits following the revelation that some customer support agents were bribed as part of the extortion scheme.
- Fold has launched Bitcoin Gift Cards, enabling users to purchase bitcoin for personal use or as gifts, redeemable via the Fold app. These cards are currently available on Fold’s website and are planned to expand to major retailers nationwide later this year.
"Our mission is to make bitcoin simple and approachable for everyone. The Bitcoin Gift Card brings bitcoin to millions of Americans in a familiar way. Available at the places people already shop, the Bitcoin Gift Card is the best way to gift bitcoin to others," said Will Reeves, Chairman and CEO of Fold.
- Corporate treasuries hold nearly 1.1 million BTC, representing about 5.5% of the total circulating supply (1,082,164 BTC), per BitcoinTreasuries.net data. Recent purchases include Strategy adding 7,390 BTC (total: 576,230 BTC), Metplanet acquiring 1,004 BTC (total: 7,800 BTC), Tether holding over 100,521 BTC, and XXI Capital, led by Jack Mallers, starting with 31,500 BTC.
- Meanwhile, a group of investors has filed a class action lawsuit against Strategy and its executive Michael Saylor. The lawsuit alleges that Strategy made overly optimistic projections using fair value accounting under new FASB rules while downplaying potential losses.
- The U.S. Senate voted to advance the GENIUS stablecoin bill for further debate before a final vote to pass it. Meanwhile, the House is crafting its own stablecoin legislation to establish a regulatory framework for stablecoins and their issuers in the U.S, reports CoinDesk.
- French 'crypto' entrepreneurs get priority access to emergency police services. French Minister of the Interior, Bruno Retailleau, agreed on measures to enhance security for 'crypto' professionals during a meeting on Friday. This follows a failed kidnapping attempt on Tuesday targeting the family of a cryptocurrency exchange CEO, and two other kidnappings earlier this year.
- Brussels Court declares tracking-based ads illegal in EU. The Brussels Court of Appeal ruled tracking-based online ads illegal in the EU due to an inadequate consent model. Major tech firms like Microsoft, Amazon, Google, and X are affected by the decision, as their consent pop-ups fail to protect privacy in real-time bidding, writes The Record.
- Telegram shares data on 22,777 users in Q1 2025, a significant increase from the 5,826 users' data shared during the same period in 2024. This significant increase follows the arrest of CEO and founder Pavel Durov last year.
- An Australian judge has ruled that Bitcoin is money, potentially exempting it from capital gains tax in the country. If upheld on appeal, this interim decision could lead to taxpayer refunds worth up to $1 billion, per tax lawyer Adrian Cartland.
Use the tools
- Bitcoin Safe v1.3.0 a secure and user-friendly Bitcoin savings wallet for beginners and advanced users, introduces an interactive chart, Child Pays For Parent (CPFP) support, testnet4 compatibility, preconfigured testnet demo wallets, various bug fixes, and other improvements.
- BlueWallet v7.1.8 brings numerous bug fixes, dependency updates, and a new search feature for addresses and transactions.
- Aqua Wallet v0.3.0 is out, offering beta testing for the reloadable Dolphin card (in partnership with Visa) for spending bitcoin and Liquid BTC. It also includes a new Optical Character Recognition (OCR) text scanner to read text addresses like QR codes, colored numbers on addresses for better readability, a reduced minimum for spending and swapping Liquid Bitcoin to 100 sats, plus other fixes and enhancements.

Source: Aqua wallet.
- The latest firmware updates for COLDCARD Mk4 v5.4.3 and Q v1.3.3 are now available, featuring the latest enhancements and bug fixes.
- Nunchuk Android v1.9.68.1 and iOS v1.9.79 introduce support for custom blockchain explorers, wallet archiving, re-ordering wallets on the home screen via long-press, and an anti-fee sniping setting.
- BDK-cli v1.0.0, a CLI wallet library and REPL tool to demo and test the BDK library, now uses bdk_wallet 1.0.0 and integrates Kyoto, utilizing the Kyoto protocol for compact block filters. It sets SQLite as the default database and discontinues support for sled.
- publsp is a new command-line tool designed for Lightning node runners or Lightning Service Providers (LSPs) to advertise liquidity offers over Nostr.
"LSPs advertise liquidity as addressable Kind 39735 events. Clients just pull and evaluate all those structured events, then NIP-17 DM an LSP of their choice to coordinate a liquidity purchase," writes developer smallworlnd.
-
Lightning Blinder by Super Testnet is a proof-of-concept privacy tool for the Lightning Network. It enables users to mislead Lightning Service Providers (LSPs) by making it appear as though one wallet is the sender or recipient, masking the original wallet. Explore and try it out here.
-
Mempal v1.5.3, a Bitcoin mempool monitoring and notification app for Android, now includes a swipe-down feature to refresh the dashboard, a custom time option for widget auto-update frequency, and a
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:40
@ 7f6db517:a4931eda
2025-06-05 18:02:40
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-06-05 18:02:34
@ dfa02707:41ca50e3
2025-06-05 18:02:34Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ dfa02707:41ca50e3
2025-06-05 17:01:35
@ dfa02707:41ca50e3
2025-06-05 17:01:35Contribute to keep No Bullshit Bitcoin news going.
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ 7f6db517:a4931eda
2025-06-05 18:02:39
@ 7f6db517:a4931eda
2025-06-05 18:02:39
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 2e8970de:63345c7a
2025-06-05 16:07:04
@ 2e8970de:63345c7a
2025-06-05 16:07:04https://x.com/jburnmurdoch/status/1930203297396249067
https://www.dropbox.com/scl/fi/1lp1dwzx608xdu8jfpkqk/FT_GENDER_DIVIDE_SXSW.pptx?rlkey=9gcwvn77zss3k5l5vgiquennl&e=1&st=apgyr3ug&dl=0
https://stacker.news/items/998014
-
 @ 58537364:705b4b85
2025-06-05 15:55:12
@ 58537364:705b4b85
2025-06-05 15:55:12อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก
…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ 8bad92c3:ca714aa5
2025-06-05 17:01:32
@ 8bad92c3:ca714aa5
2025-06-05 17:01:32Key Takeaways

In this episode of TFTC, energy economist Anas Alhajji outlines a profound shift in U.S. foreign policy under Trump—away from military intervention and toward transactional diplomacy focused on trade, reconstruction, and curbing Chinese and Russian influence in the Middle East. He highlights Trump’s quiet outreach to Syria as emblematic of the U.S.'s strategic flexibility in legitimizing former adversaries when economically beneficial. Alhajji dismisses BRICS as a fractured bloc incapable of rivaling the U.S.-led order and insists the dollar and petrodollar remain dominant. On energy, he warns that despite favorable fundamentals, prices are suppressed by political confusion, underinvestment, and an aging power grid ill-prepared for the AI and urbanization boom. He also contends that Iran is stalling negotiations to buy time for nuclear advancement and that any deal will be superficial. Finally, Alhajji debunks the myth of Trump being pro-oil, noting his long-standing hostility toward the industry and explaining why a repeat of his past energy boom is implausible given today’s financial and structural constraints.
Best Quotes
- “BRICS is a paper tiger. Everything about BRICS is what China does—and that’s it.”
- “The dollar is here to stay. The petrodollar is here to stay. End of story.”
- “Trump hates the oil industry. He always classified it as an enemy.”
- “Energy projects are 30- to 40-year investments, but politicians think in 4-year cycles. That’s where the disconnect lies.”
- “People think shale will boom again. It won’t. The model changed from ‘drill baby drill’ to ‘control baby control.’”
- “The real story of Trump’s trip wasn’t about politics—it was investment, investment, investment.”
- “Without massive investment in the grid and gas turbines, blackouts will become the norm—even in rich countries like Kuwait.”
- “Iran and China have perfected the game of oil exports. Sanctions are just theater at this point.”
Conclusion
Anas Alhajji’s conclusion challenges conventional narratives, arguing that global power is shifting from military dominance to economic leverage, infrastructure investment, and energy control. He presents a nuanced view of U.S. foreign policy under Trump, emphasizing the strategic importance of trade and reconstruction over regime change. As energy demand soars and geopolitical risks mount, Alhajji warns that the real dangers lie not in foreign adversaries, but in policy confusion, infrastructural lag, and complacency—making this episode a crucial listen for anyone seeking to understand the high-stakes intersection of energy, economics, and diplomacy.
Timestamps
0:00 - Intro
0:48 - Syria and US diplomacy in Middle East
12:50 - Trump in the Middle East
18:12 - Fold & Bitkey
19:48 - Iran - Nuclear program and PR
33:53 - Unchained
34:22 - Crude markets, trade war and US debt
54:28 - Trump's energy stance
1:05:46 - Energy sector challanges
1:14:44 - Policy recommendations
1:21:18 - AI and bitcoinTranscript
(00:00) oil prices market fundamentals support higher price than where we are today. But because of this confusion, everyone is scared of low economic growth and that is a serious problem. The US media ignored part of Trump's speech when he said we are not about nation building and they refer to Afghanistan and Iraq.
(00:15) Look at them. This is a criticism of George W. Bush. We have groups that are talking about the demise of the dollar, the rise of bricks. Bricks is a paper tiger. Everything about bricks is what China does and that's it. The dollar is here to stay and the petro dollar is here to stay.
(00:31) The perception is that the Trump administration is cold but the reality Trump hates the oil [Music] indust. How are you? Very good. Very good. Thank you. As you were telling me, you've been a bit sleepd deprived this week trying to keep up with what's going on. Oh, absolutely. I mean, Trump keeps us on our toes uh all the time.
(01:06) In fact, I plan certain things for the weekend and Trump will say something or he will do something and all of a sudden we get busy again. Uh so clients are not going to wait for you until you finish your work. Basically, they want to know what's going on. So what is going on? What what how profound were the events in the Middle East? These are very uh very profound changes basically because it is very clear that if you look at the last 15 years uh and you look at the growth uh in the Middle East, you look at the growth of Saudi Arabia and uh the
(01:41) role of Turkey for example in the region uh it just just amazing be beyond any uh any thoughts. Uh in fact both of them Turkey and Saudi Arabia are part of the G20. Uh so they have economic influence and they have political influence. And of course the icing on the cake for those who are familiar with the region is to recognize the Syrian government and meet with the Syrian uh president.
(02:11) Uh this is a major a major change in economics and politics uh of the Middle East. Let's touch on that Syria uh topic for a while because I think a lot of people here in the United States were a bit shocked at how sort of welcoming President Trump was towards the new Syrian president considering the fact that uh he was considered an enemy not too long ago here in the United States.
(02:42) What first of all it's a fact of life for those who would like to check the history of politics. There were many people around the world who were classified or they were on the terrorism list and then they became friends of the United States or they were became heroes. I mean Nelson Mandela is one of them. You look at Latin America, there are presidents in Latin America who were uh the enemy of the United States and then they became uh uh cooperative with the United States and the United States recognized their governments and the result of their uh elections. Uh so
(03:15) we've seen this historically uh several uh several times around the world and as they say freedom fighters for some basically are the enemies and the terrorists for for others etc. So uh what we've seen that's why the the visit is very important that the recognition of this government is very important. uh the fact on the ground that uh the president of Syria had the power on the ground uh he had the the the people on the ground and he had the control on the ground and whatever he's been he's been doing since he came into power until now
(03:52) he done all the right steps u and people loved him I mean everyone who went to Syria whether the Syrians who left Syria 40 years ago or uh the visitors who are coming to Syria, they will tell you, "We have never seen the Syrian people as happy as we've seen them today, despite the fact that they they live in misery.
(04:17) They don't have um 8 million people without housing. Uh there is barely any electricity in most of the country. There is no internet. There is barely any food. The uh inflation is rampant, etc. But people are happy because they lived in fear for a very long time. And uh the steps they have taken. For example, the uh ministers in the previous government uh are still there and they are still in the housing of the government.
(04:49) They still have the drivers. They still have the cars from the previous government. They still have it until today. So uh they they were classified as enemies before. But all of a sudden now you have a new government that is uh accepting them. Uh so we we see some changes on the ground that are positive and we'll see how these things will go given that the area around them basically has been unstable for a very long time.
(05:17) how because I don't the the news when I was actually it was surreal for me because my first trip to the Middle East was last December when it was literally f flying over Syria to Abu Dhabi when uh um Assad was getting thrown out and it was pretty surreal to be in that region of the world.
(05:43) How as it pertains to like religious minorities within Syria moving forward is there protractions protections there? Um well let me just uh I want to emphasize one point that is very important. What did the interest of Turkey, Saudi Arabia and the United States in Syria if remember Syria was controlled by Iran and was controlled by the Russians.
(06:09) So in a sense it becomes uh kind of an imperative that taking it away from Iran and Russia and not bringing Iran or Russia back is extremely important. Now the Russians are still there and they have their own base but at least they are not bombing the Syrians and not killing them anymore. But the idea here is taking Syria out of Iran and Russia and probably later on if they kick the Russians out, Russians will not have access to the Mediterranean.
(06:37) Uh so there is an interest uh of all parties basically to take Russia out of Iran and um out of uh Syria regardless the country is uh devastated and it creates massive opportunities for US companies on all levels and uh we've seen a contract uh done recently with you mentioned Abu Dhabi uh uh a contract uh uh with the UA a basically to revamp all the Syrian ports and work on the Syrian ports.
(07:13) Uh so such contracts basically uh when you have a country that has nothing and it's completely devastated the whole infrastructure is devastated. Who is going to build it? If the uh what the Chinese, the Russians, so who who are going to build it? So, uh I think there is a a big room for US companies and others basically to come in and uh literally help on one side and make money on the other.
(07:38) Yeah, I think that that's what I'm trying to discern. What was this convoy from the United States to the Middle East this week signali -
 @ 7f6db517:a4931eda
2025-06-05 18:02:39
@ 7f6db517:a4931eda
2025-06-05 18:02:39Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-05 17:00:50
@ b1ddb4d7:471244e7
2025-06-05 17:00:50“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:39
@ 7f6db517:a4931eda
2025-06-05 18:02:39
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 9ca447d2:fbf5a36d
2025-06-05 17:01:11
@ 9ca447d2:fbf5a36d
2025-06-05 17:01:11Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:38
@ 7f6db517:a4931eda
2025-06-05 18:02:38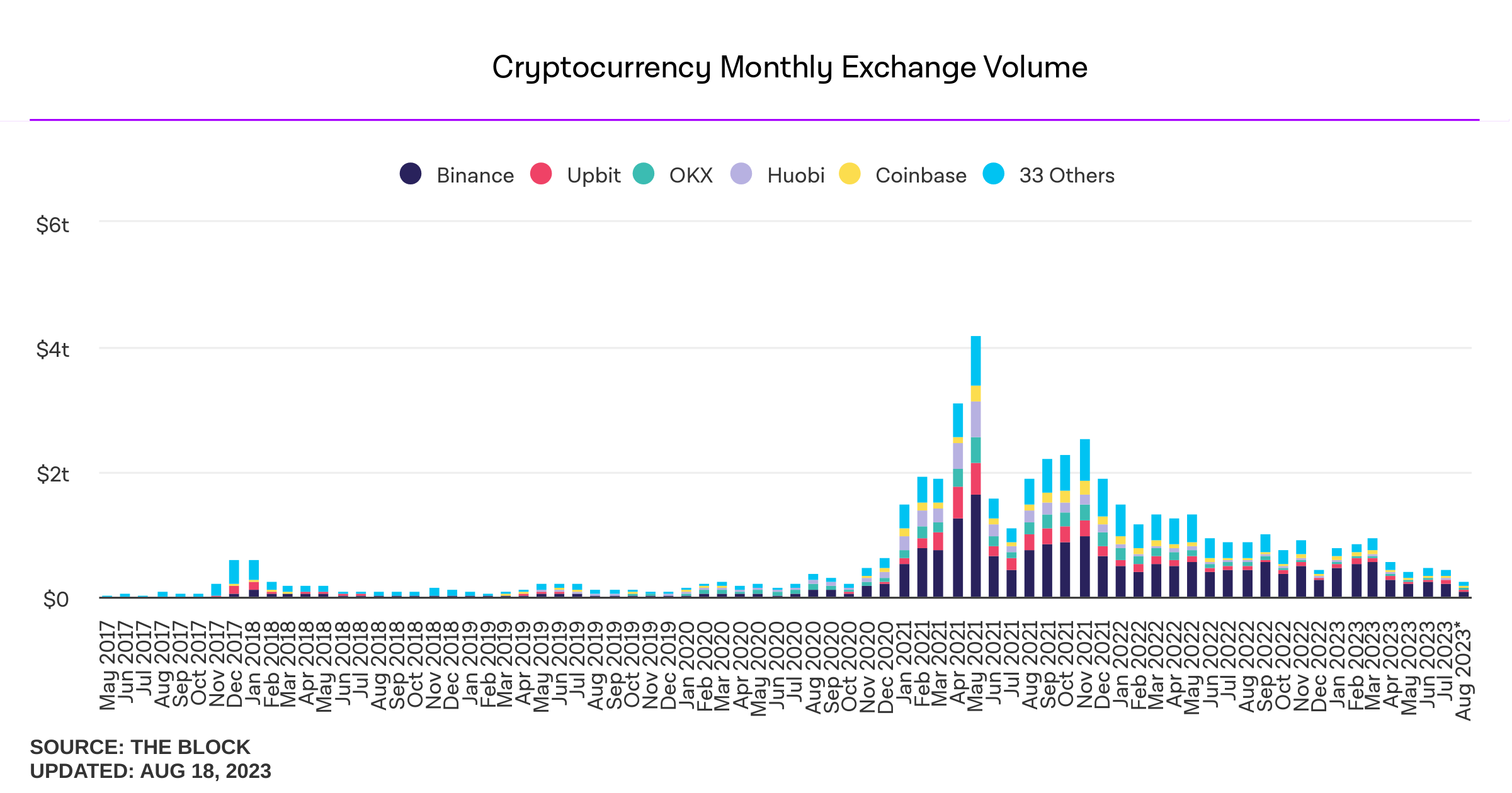
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
If you found this post helpful support my work with bitcoin.

-
 @ 7460b7fd:4fc4e74b
2025-06-05 15:54:42
@ 7460b7fd:4fc4e74b
2025-06-05 15:54:42比特币正在主动引诱量子计算“破解自己”
引言:危机还是契机?
比特币和量子计算,这两个看似对立的存在,正在酝酿一场耐人寻味的博弈。许多人担心未来强大的量子计算机将秒破比特币的密码学基石,从而令区块链安全灰飞烟灭。然而,本文想传达的核心观点却截然相反:比特币不仅不会被量子破解打败,反而正在通过协议层的巧妙设计来“引诱”量子计算进入自己的游戏规则之中。通过诸如BIP-360等提案,比特币有望将量子计算的威胁转化为动力,开启一个“后挖矿时代”的全新正反馈经济体系,让“破解”本身成为新的挖矿机制。
这样的观点听起来近乎狂想,但背后有着深厚的技术逻辑支撑。我们将从基本的密码学原理谈起,逐步剖析量子计算的能力与局限,以及比特币协议在抗量子方向做出的结构性准备。最后,我们探讨一种大胆的经济模型:当量子计算被诱导去参与“破解竞赛”时,或许正是比特币凤凰涅槃、新经济形态崛起之机。
非对称加密的数学本质:“上帝视角”的陷门答案
非对称加密(如RSA、椭圆曲线加密ECC等)的核心在于存在一种单向函数:正向计算容易,反向推导极难。公钥可以视作某个难题的题目,私钥则相当于“上帝视角”提前知道的答案。一旦掌握私钥,就能轻松完成从答案到题目的逆推;而只有公钥时,想要逆推出私钥则被设计为在现实中不可行。这类单向难题通常通过陷门函数来实现——对合法持有者(私钥)来说,存在隐藏的捷径(陷门)可以快速解题;而对局外人来说,题目看似无解。
举例来说,比特币当前采用的ECC加密:私钥与公钥的关系就像“一次难以逆推的乘法”。给定私钥x,乘以基点G可轻易得到公钥点P = x·G,但已知P却无法高效求出x。这种不对称确保了签名者可以用私钥生成签名,而验证者只能用公钥验证签名而无法伪造。私钥掌握了解题的“上帝答案”,公钥则只能用于验证答案是否正确。
这一点在新型的抗量子算法中同样体现。以格密码(lattice cryptography)为例:Falcon等基于NTRU格的签名算法,其公钥可以被视为一个高维长基,私钥是对应的短基。pqshield.com在二维格子上的示意说明了这种不对称性:拥有短基(私钥)时,我们可以高效地找到距离某个目标点很近的格点解;但只有长基(公钥)时,我们顶多能验证某个给定解是否有效,却很难自行找到足够优质的解pqshield.com。换言之,私钥提供了一个陷门,允许持有者快速逆推答案,而公钥持有者只能望“题”兴叹。
图:在二维格子中,签名者持有的短基(私钥)可以高效求解出距离目标点(黑色方块)极近的格点解(绿色圆点)。绿色平行四边形表示短基下求解空间很小,因而容易找到最优解。这直观展示了陷门函数的威力:私钥掌握短基就如同拿到了解题捷径。
图:仅持有长基(公钥)时,使用相同算法得到的格点解(红色圆点)可能距离目标(黑色方块)很远。红色平行四边形代表在无陷门情况下求解范围巨大,找到最佳解极其困难。但验证者仍可用长基检查出某个解(如绿色点)确实是有效解pqshield.com。这体现了公私钥在计算能力上的不对称:私钥可求解,公钥仅可验证。
总而言之,非对称加密的安全性源自数学难题的单向性质和陷门结构。私钥就是那个隐藏的逆向通道,“上帝视角”的答案;公钥则是不具备捷径的信息,只够验证而无法逆推。从RSA的整数分解、ECC的离散对数,到Falcon的近似最近矢量问题,每一种公钥体制都是在构造“题目易出答案难逆”的格局,让持有陷门者轻松,旁观破解者绝望。
量子计算的原理与极限:并行穷举的神话与现实
量子计算机令人畏惧之处,在于其并行计算能力。通过量子叠加态,n个量子比特(qubit)可同时表示2^n种状态——仿佛能把指数级的可能性同时考虑。配合量子干涉与算法设计,量子计算机能够以远胜传统计算机的效率解决某些特定问题。其中最著名的就是Shor算法,它能在多项式时间内完成对大整数的质因数分解和离散对数求解。这正是传统公钥加密(RSA、ECC)的命门:一旦有足够强大的量子计算机,基于这些数学问题的公钥体制将不再困难,私钥可以由公钥“解密”而出coindesk.com。
然而,“并行穷举”的神话背后有严格的物理和工程学限制。首先是量子比特数量和质量的限制:当前的量子芯片规模远未达到破解现代加密所需的级别。据风险研究机构与专家调查,目前我们只有几十到几百个物理qubit,而要威胁256位ECC或2048位RSA,需要数百万高质量qubitdeloitte.com。不仅数量上相差几个数量级,现有量子芯片的纠错和降噪技术也远不成熟。量子比特极其敏感,微小噪声都会引入错误,真正实用的量子计算机需要对成千上万的物理比特进行纠错编码,形成稳定的逻辑比特。这个工程挑战之巨大,使得可攻破密码的量子计算机仍是多年之后的前景——多数专家预测大概还需十几年时间才可能出现实质威胁deloitte.com。
其次,量子计算并非万能破解,仅对特定问题有指数级加速。Shor算法擅长因数分解和离散对数,Grover算法可以对无结构的穷举搜索加速(将时间复杂度平方根降低)。但许多新兴的抗量子算法依赖的问题(如格上的最短向量问题SVP、最近向量问题CVP,或多变量方程、哈希预像等)目前并无高效量子算法。这些问题大多属于NP难类,甚至找近似解也极为困难emerginginvestigators.org。尽管量子计算提供并行试探能力,但对这类高度复杂的问题也爱莫能助。正如一项研究指出:SVP和CVP问题即便在量子计算机上依然“极端困难”,在可预见的将来仍足以保证安全性emerginginvestigators.org。Falcon所使用的NTRU格就是这样的难题代表——没有已知算法可以像Shor之于RSA那样,高效攻破NTRU问题。
最后,我们还需注意量子攻击的实际条件。量子破解比特币主要有两种情景:存储攻击和传输攻击deloitte.com。存储攻击指利用量子计算找出已公开公钥对应的私钥,从而盗取静态存放于链上某地址的币;传输攻击则是当交易广播(公钥暴露)后,在被矿工打包上链前的短暂窗口内,量子计算抢先推导私钥并盗转。这两种攻击对量子能力要求不同:存储攻击允许耗时几周甚至数月破解一个密钥,只要在币移动前完成即可;而传输攻击要求在区块确认之前(比特币约10分钟内,以太坊更短)秒破私钥deloitte.com。显然,目前和可预见的中期内,量子计算都远达不到传输攻击所需的即时破解水平;即便存储攻击,由于比特币区块链的UTXO模型(稍后详述),真正高价值、长时间暴露公钥的币也相对有限deloitte.com。因此,量子威胁虽然现实存在,但并非一夜之间让比特币崩溃的魔法。这反倒给予我们部署抗量子方案、引导量子力量“为我所用”的时间窗口。
抗量子密码学的三大结构前提
要让比特币真正抵御量子威胁,并把量子计算纳入自身生态,需要满足几个结构性前提。经过多年社区讨论和研究,以下三点被认为是比特币走向抗量子的关键设计要素:
-
UTXO模型:隐藏公钥缩短攻击窗口 – 比特币采用UTXO模型,每次交易都会生成新地址,公钥通常以哈希形式隐藏在地址中,直到你花费时才公布。这意味着量子计算只有在你发起交易后的很短时间内(交易确认前)才能获得公钥并尝试破解,大大压缩了攻击窗口anduro.iodeloitte.com。相较之下,账户模型(如以太坊)重复使用固定地址,公钥一旦被提取或首次使用后就长久暴露,使得65%以上的以太币当前都处于量子暴露风险中,而比特币约只有25%处于类似风险deloitte.com。UTXO模型通过“一次性地址”和“不用则公钥不出”的原则,天然提供了对抗量子存储攻击的第一道屏障。
-
“见证隔离”(SegWit):模块化升级签名算法 – 抗量子方案的发展日新月异,比特币必须保持签名算法的可插拔升级能力。2017年的见证隔离升级正是为此奠定基础:SegWit将签名等见证数据与交易本体分离,并引入版本化的见证脚本格式。这使得添加新签名类型成为可能——通过软分叉引入新的输出类型和见证版本,就能兼容地支持不同算法delvingbitcoin.org。正如BIP-341利用SegWit扩展出了Taproot的Schnorr签名,比特币也可以扩展出抗量子签名的新地址类型而无需硬分叉或显著增加区块体积delvingbitcoin.org。这一模块化特性对于迎接未来各类抗量子算法至关重要,没有SegWit的铺垫,抗量子改造将困难重重。
-
分级安全机制:根据价值和时效选择算法强度 – 由于UTXO的性质,每笔交易在花费时都会暴露其公钥。因此,安全策略不能“一刀切”,应允许根据币值大小或持有时长采用不同强度的抗量子算法。高价值的UTXO、长期未移动的“老币”,应使用更高安全级别但可能更重型的签名方案;反之,小额频繁交易可用较轻量的方案以兼顾效率和区块容量。好比Falcon提供了512和1024两种参数版本:Falcon-1024安全级别更高但签名稍大,而Falcon-512签名更小速度更快,适合资源受限场景emerginginvestigators.org。未来比特币或可同时支持多种抗量子算法或参数,用户按需选用,让“安全性”成为一种可以权衡和市场定价的链上资源。每一次支付都在安全与成本之间找到平衡,这将促使一个分层的安全市场形成——进一步论述见后文经济模型部分。
上述三大前提缺一不可:UTXO模型提供了基础的_安全缓冲_,SegWit机制给予_升级弹性_,分级算法让_经济可行性_落地。在这方面,比特币的体系结构远优于某些后来的公链。例如,以太坊的账户模型天生缺乏隐藏公钥的机制,地址就是固定的公钥哈希,一旦使用过私钥签名就永久暴露公钥,同时其交易脚本(EVM)对签名算法固定死,没有灵活插拔空间。这意味着以太坊想转向抗量子算法,必须经过极其痛苦的整体迁移或硬分叉——开发者需要为每个账户引入新密钥,新老算法并行过渡,智能合约地址、签名验证逻辑全部推倒重来。这种难度令人生畏,以至于有人嘲讽以太坊“几乎不可能”实现真正的抗量子迁移。反观比特币,得益于其简单而弹性的UTXO+Script设计,只需通过新的输出类型软分叉,就可以逐步引入抗量子地址,让用户自愿迁移过渡,避免一次性硬分叉的系统性风险。
BIP-360:可选抗量子签名,引入量子博弈
面对量子威胁,比特币开发社区并未坐以待毙。2024年,由开发者Hunter Beast提出的BIP-360提案(又称P2QRH,意为“支付到抗量子哈希”)正式将抗量子签名引入了议事日程anduro.io。BIP-360核心思路是在比特币中增加新的地址类型,这些地址采用后量子密码学的签名算法(当前优先考虑Falcon,并备选CRYSTALS-Dilithium和SPHINCS+等)来取代易受量子攻击的ECDSA/Schnorr签名anduro.iogroups.google.com。换句话说,用户可以自愿选择生成一种“抗量子地址”,对应的UTXO需使用抗量子算法签名才能解锁。
为什么说BIP-360让比特币“引诱”量子计算加入博弈?这里有几层含义:
首先,BIP-360采用软分叉方式部署,可选而非强制。这意味着在量子计算真正成熟之前,绝大多数交易仍可继续使用原有签名算法,不平添负担;而有安全偏好的用户或机构可以提前迁移一部分资金到抗量子地址以高枕无忧。随着量子技术进展,逐步会有更多人选择这个选项,形成一个与量子威胁赛跑的过程。这种自愿迁移机制本身就是一种对量子黑客的诱导:网络主动暴露出一个“堡垒更坚固”的区域,鼓励守法用户往那里走,同时意味着留下的旧区域反而成为显眼的攻击目标和“诱饵”。
其次,BIP-360在算法选择和参数上充分考虑了区块链经济的承受力。起初提案曾讨论过一些前沿算法如SQIsign,但发现其验证开销高达ECDSA的15,000倍,若全网采用将使验证一块新区块从1秒暴涨到4小时,带来难以接受的性能瓶颈groups.google.com。最终的方案优选Falcon等NIST标准算法,它们签名体积较小、验证高效,可与当前区块大小和验证速度相容groups.google.com。例如Falcon-1024的签名约1.3KB、公钥1.7KB左右,这虽然比当前64字节的Schnorr签名大得多,但并非无法承受。通过配置灵活的安全级别(如重要交易才用Falcon-1024,一般小额用Falcon-512或普通Schnorr),比特币区块空间将被合理分配在安全性和费用之间。BIP-360精心设计了新的地址格式和见证结构,确保即便引入抗量子签名,区块验证和存储开销也在经济范围内,不会动摇挖矿和节点运行的成本平衡anduro.io。
最后也是最具前瞻性的一点,BIP-360为量子计算参与链上博弈打开了一扇门。通过提供抗量子和非抗量子地址并存的环境,比特币网络其实设置了一个对量子计算的挑战擂台:量子计算可以选择去攻击那些仍使用旧签名算法且价值巨大的UTXO,但同一时间,网络里的用户也在不断提升关键UTXO的签名强度来应对。量子计算不再是一个纯粹的外部敌人,而被巧妙地“请”进了系统,在规则内与用户和矿工互动。这为下一节将讨论的新经济模型奠定了基础——破解即挖矿的雏形由此孕育。
值得一提的是,BIP-360还提出了一个Taproot的量子安全补丁方案P2TRH,用哈希隐藏Taproot的公钥以弥补其“公钥长曝”缺陷groups.google.comgroups.google.com。因为现有的Taproot地址(见证v1)是直接以公钥生成地址,失去了UTXO模型隐藏公钥的优势,量子攻击者可以随时尝试破解Taproot资金。P2TRH通过将Taproot公钥再哈希一层,恢复“见证前隐藏公钥”的特性,代价是每笔此类输入增加8.25字节开销groups.google.com。这显示出比特币开发者未雨绸缪,连新升级的Taproot漏洞也在想办法弥补,使全局达到抗量子的结构性统一。
综上,BIP-360及相关提案不仅提供了技术方案,更释放出一种积极的信号:比特币正主动拥抱量子挑战,将其纳入规则之内。正如Anduro团队支持BIP-360时所言:“量子攻击的威胁严肃而迫近,我们不能坐等紧急关头才手忙脚乱。”anduro.ioanduro.io比特币社区选择了在危机到来前主动布局,以最小的代价换取最大的安全冗余和发展新契机。
“破解竞赛”经济模型:当量子成为新矿工
设想未来5-15年内,量子计算技术逐步成熟。在比特币网络中,可能会上演这样一幕令人惊叹的图景:量子计算矿工和抗量子验证者同时在线,围绕着尚未升级的老式UTXO展开一场你追我赶的“破解竞赛”。这将引发怎样的经济动力?我们大胆描绘一个后PoW时代的可能场景:
一方面,强大的量子计算机不再浪费算力去挖掘哈希谜题(传统PoW),而是直接瞄准那些“量子易攻”的UTXO,即尚使用老式ECDSA/Schnorr签名且公钥已暴露的地址。这些地址里的币对合法持有人来说如果迟迟未迁移到抗量子地址,实际上就变成了躺在链上的“悬赏”:谁能先算出私钥,谁就能转走这些币。在量子计算参与者眼中,这些币和早期比特币矿工眼中的区块奖励无异,都是凭借算力可竞争获取的收益。值得注意的是,根据分析,目前约有25%的比特币(按币量)处于公钥已暴露状态deloitte.com。随着时间推移,这个比例可能上升——除非持有人主动升级安全。这就像网络故意留出了一片“牧场”,让量子计算在其中竞相捕猎,以获得收益。量子攻击者之间形成竞争:更快的量子芯片、更好的算法意味着可以更早破解特定私钥,拿下那笔币。这几乎就是PoW的变体——过去矿工拼SHA-256算力抢区块奖励,未来量子矿工拼质因数分解/离散对数能力抢遗留UTXO。
另一方面,守护这片“牧场”的则是抗量子验证者和普通用户自身的防范行为。所谓抗量子验证者,可能是运行完整后量子节点或提供安全服务的专业机构。他们一方面帮助用户升级UTXO(例如提供一键迁移服务,把旧地址币转移到新PQ地址上,收取服务费),另一方面监测全网可疑交易。当量子攻击者尝试盗取某UTXO时,如果该UTXO持有者事先购买了“安全服务”,验证者可以抢先代为花费将币转移到更安全的地址(类似白帽黑客行为),或者提供更高级别签名升级以挫败攻击。总之,抗量子能力本身也成为一种商品,在市场上明码标价。你想让自己的币绝对安全?可以付费请量子安全服务团队定期轮换密钥、使用最高强度签名、监控链上异常。你的交易想确保不中途被截胡?可以支付更高矿工费甚至指定量子保险节点护送。在链上,一个根据签名难度和安全级别定价的市场逐渐形成:越高难度的签名(比如超长位的Falcon变种、多重签名方案结合等)需要支付越高的费用来存储和验证;反过来,这些费用补贴给保障网络安全的矿工/节点,激励他们投入更多资源提升抗量子能力。这种正反馈循环下,“安全”本身成为了新的经济激励。
如此一来,比特币生态迎来了“后挖矿时代”的转型:当区块补贴逐渐趋零,原本空缺的矿工激励由量子破解竞赛和安全服务市场所填补。量子计算加入竞争并非摧毁网络,反而扮演起类似矿工的角色,通过攻破薄弱环节来获得收益;而诚实的参与者则通过不断升级安全措施和支付安全费用来保护资产。这看似矛盾,却形成了动态平衡:正如生物进化中的“红后效应”,猎豹越快,羚羊也进化得更快,两者共同提升了系统的活力。
当然,这一模型中也充满戏剧性和讽刺意味——尤其当我们把眼光投向其他缺乏这种机制的公链。以太坊等账户制链若在量子时代陷入危机,很可能只能选择停机硬分叉、或者由中心化机构出面更换用户密钥,几乎无自动博弈的空间可言。而比特币网络则通过精妙的协议调整,把外部威胁内化为内部博弈,让市场机制去调节和应对。这种弹性与活力,正是比特币经久不衰的原因。
结语:危机催生新生,量子力量为我所用
当年互联网面对计算机病毒肆虐时,人们最终没有被动防守,而是发展出杀毒产业、安全协议,将病毒的威胁转化为推动网络更加健壮的动力。同样道理,比特币面对量子计算的冲击,并非只能筑高墙固步自封,而是选择了更具前瞻性的道路:拥抱威胁、化敌为友。通过提前布局抗量子基础设施(UTXO模型、SegWit扩展、PQ签名算法)、逐步推行BIP-360等方案,比特币正悄然改变游戏规则。在这个新规则中,量量对决、攻守博弈将上演全新篇章,网络安全不再是一成不变的盾牌,而是一套动态进化的生态系统。
或许若干年后回望,我们会发现量子计算并没有摧毁比特币,反而成就了比特币历史上的一次重大飞跃——开启了一个后工作量证明时代的新纪元。在这个纪元里,“破解就是新挖矿”不再只是戏谑之语,而成为链上真实上演的经济现象;“出售安全”也从附属服务变成每个节点和用户的日常考量。比特币将继续履行其角色:作为一个去中心化的、自我强化的金融体系,它有能力将任何挑战转化为自身进化的燃料。
正如BIP-360提案作者所言,这是一个“when 而非 if”的议题anduro.io。量子计算终将到来,而比特币已在主动邀请它参与一场精心设计的游戏。当量子计算机真的站上擂台,比特币早已不再是那个任人宰割的靶子,而更像是一位早已摆好阵势的棋手,静候对手入局。在这盘大棋中,没有永远的猎物,只有不断进化的猎人。比特币,会是那个始终笑到最后的“猎人”吗?让我们拭目以待。
参考文献:
-
【18】PQShield博客:《Falcon – A Post-Quantum Signature Scheme》 – 阐释格密码中长基(公钥)与短基(私钥)的不对称性pqshield.com。
-
【28】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 比较了比特币UTXO模型与以太坊账户模型在量子攻击下的差异,指出以太坊65%资产易受量子威胁,而比特币约25%deloitte.comdeloitte.com。
-
【23】Bitcoin开发者论坛:《Proposing a P2QRH BIP towards a quantum resistant soft fork》 – 描述了通过SegWit扩展新签名算法的思路,无需硬分叉且不增加区块大小delvingbitcoin.org。
-
【22】Emerging Investigators论文:《A meta-analysis on NIST post-quantum cryptographic primitive finalists》 – 说明Falcon-512与Falcon-1024在安全性和性能上的差异,并强调SVP/CVP等问题对量子计算依然极为困难emerginginvestigators.orgemerginginvestigators.org。
-
【36】Anduro博客:《Bitcoin Needs Quantum Resistant Addresses – We Support BIP360》 – 介绍了BIP-360提案内容,引入抗量子地址类型P2QRH,采用Falcon和Dilithium签名,软分叉兼容anduro.io。同时强调量子威胁需提早应对的紧迫性anduro.ioanduro.io。
-
【32】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 提供了BIP-360提案的最新动态,算法选型从SQIsign转向Falcon、Dilithium、SPHINCS+,原因是前者验证开销过大(15,000倍)而不切实际groups.google.comgroups.google.com。
-
【30】CoinDesk报道:《Quantum Computing Could Break Bitcoin-Like Encryption Far Easier…》 – 提及比特币所用ECC也可被Shor算法破解,只要有足够强大的量子计算机coindesk.com。
-
【33】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 阐述当前量子计算的物理局限:需要上百万qubit且降低噪声量级,目前技术远不能攻击密码算法deloitte.com。
-
【38】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 描述了针对Taproot的P2TRH抗量子方案,用哈希隐藏公钥以减小长时间暴露,并分析其开销和局限groups.google.comgroups.google.com。
-
-
 @ 7f6db517:a4931eda
2025-06-05 15:02:24
@ 7f6db517:a4931eda
2025-06-05 15:02:24
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 8bad92c3:ca714aa5
2025-06-05 18:02:28
@ 8bad92c3:ca714aa5
2025-06-05 18:02:28Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ b1ddb4d7:471244e7
2025-06-05 17:00:56
@ b1ddb4d7:471244e7
2025-06-05 17:00:56When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:38
@ 7f6db517:a4931eda
2025-06-05 18:02:38
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-05 17:00:51
@ b1ddb4d7:471244e7
2025-06-05 17:00:51It’s 3 AM, and you’re staring at your phone screen, watching bitcoin’s price fluctuate by thousands of dollars in real-time. Your heart races as you see green candles shooting upward, and suddenly you’re questioning every financial decision you’ve ever made. Should you buy? Should you sell? Are you already too late to the party?
Welcome to the wild psychological rollercoaster that is bitcoin investing, where emotions often override logic, and where the ancient human drives of fear and greed play out on digital exchanges 24/7.
Community Driven by Emotion
Recent research reveals just how deeply psychology permeates the bitcoin ecosystem. According to a comprehensive 2024 survey by Kraken, 84% of digital currency holders have made investment decisions based on FOMO (Fear of Missing Out), while 81% admitted to making choices driven by FUD (Fear, Uncertainty, and Doubt). Perhaps most telling of all: 63% of holders acknowledged that emotional decisions have significantly damaged their portfolios.
With over 560 million digital currency users worldwide as of 2024, and bitcoin maintaining its position as the flagship digital asset, these psychological patterns affect hundreds of millions of investors globally. In the United States alone, approximately 36 million adults own bitcoin, making this psychological phenomenon a mainstream financial reality.
The FOMO Factor: When Missing Out Becomes an Obsession
FOMO in bitcoin isn’t just about missing a quick profit—it’s about missing what many believers see as a once-in-a-generation wealth transfer. The Kraken study found that 60% of bitcoin holders fear missing a significant price surge more than they fear missing a buying opportunity during dips. This reveals a fascinating bias: investors are more concerned with unrealized gains from assets they already own than with strategic accumulation during downturns.
This psychological quirk explains why bitcoin often experiences explosive rallies followed by sharp corrections. When FOMO kicks in, rational decision-making goes out the window. Investors chase green candles, buying at peaks instead of strategically accumulating during valleys. The irony? This behavior often ensures they miss the very opportunities they’re trying to catch.
Consider bitcoin’s journey past $100,000 in late 2024. As the price breached this psychological barrier, social media exploded with FOMO-driven content, creating a feedback loop where seeing others’ gains intensified the fear of being left behind. Yet historically, many of these late-stage buyers found themselves underwater when inevitable corrections followed.
The Fear and Greed Index
Bitcoin’s psychological state is so influential that it has its own emotional barometer: the Crypto Fear and Greed Index. This fascinating tool measures market sentiment on a scale from 0 (Extreme Fear) to 100 (Extreme Greed), incorporating factors like volatility, trading volume, social media sentiment, market dominance, and Google search trends.
The index reveals a counterintuitive truth: the best buying opportunities often occur during periods of “Extreme Fear,” while “Extreme Greed” frequently signals market tops. Yet human psychology drives us to do the opposite—buying when everyone’s greedy and selling when fear dominates.
This emotional inversion creates what researchers call “behavioral arbitrage”—opportunities for those who can master their psychology to profit from others’ emotional mistakes. The index serves as a mirror, reflecting our collective psychological state and often predicting market movements with surprising accuracy.
The HODL Culture
Perhaps nowhere is bitcoin’s unique psychology more evident than in its “HODL” culture. What began as a misspelled “hold” has evolved into a sophisticated psychological framework that shapes market dynamics in ways traditional finance has never seen.
Research into Bitcoin’s HODL phenomenon reveals that volatility actually strengthens conviction rather than weakening it. Unlike traditional investors who might panic-sell during 30-50% corrections, bitcoin holders often view these drops as validation of their long-term thesis rather than reasons to exit.
This creates a unique market structure where the supply of available bitcoin for trading continuously shrinks. Long-term holders remove coins from circulation, creating artificial scarcity that amplifies price movements in both directions. It’s not just code that makes bitcoin scarce—it’s psychology.
The HODL mentality represents a form of collective resistance to short-term market dynamics. Holders refuse to participate in what they see as irrational price discovery, instead betting on long-term adoption and monetary debasement. This isn’t passive investing; it’s active rebellion against traditional financial thinking.
Social Media: The Amplifier of Emotions
The role of social media in bitcoin psychology cannot be overstated. The Kraken study found a strong correlation between social media usage and FOMO-driven decisions: 85% of investors who rely on social media for investment information reported that emotional decisions had negatively impacted their portfolios.
Platforms like Twitter (now X), Reddit, and Discord function as emotional echo chambers where bullish sentiment gets amplified during rallies and bearish fears spread like wildfire during corrections. Memes become market-moving forces, and influential personalities can trigger massive buying or selling waves with single tweets.
This creates a fascinating paradox: the democratization of financial information through social media empowers individual investors, but it also makes them more susceptible to emotional manipulation and herd mentality. The speed and scale of information flow intensify psychological responses, compressing emotional cycles that might have taken weeks in traditional markets into mere hours or minutes.
The Gender and Age Divide in Bitcoin Psychology
Fascinating demographic patterns emerge when examining bitcoin’s psychological landscape. The Kraken research revealed significant gender differences in emotional investing: 66% of male bitcoin holders frequently made FOMO-driven decisions, compared to only 42% of female holders. Similarly, 83% of men reported FUD-influenced decisions versus 75% of women.
Age also plays a crucial role. Investors aged 45-60 showed the most extreme psychological patterns: 78% felt they had missed bitcoin’s biggest gains, yet 75% remained optimistic about future opportunities. This suggests that FOMO and hope can coexist, creating a complex emotional state that drives continued participation despite feelings of regret.
These demographic differences highlight how personal psychology intersects with market dynamics. Understanding these patterns can help investors recognize their own biases and develop more rational strategies.
The Neuroscience of Bitcoin Volatility
Recent academic research reveals the neurological basis of bitcoin’s psychological appeal. Studies on digital currency trading psychology show that bitcoin’s extreme volatility triggers the same reward pathways associated with gambling, creating potentially addictive patterns of behavior.
The unpredictability of bitcoin’s price movements creates what psychologists call “intermittent reinforcement”—the most powerful form of behavioral conditioning. Like slot machines, bitcoin provides irregular rewards that keep investors engaged far longer than consistent returns would.
This neurological response explains why many bitcoin investors check prices obsessively. The survey found that 55% of digital asset holders check markets significantly more frequently than traditional markets, suggesting an almost compulsive relationship with price monitoring.
Breaking Free from Emotional Cycles
Understanding bitcoin’s psychology isn’t just academic—it’s practical. Successful bitcoin investors develop strategies to counteract their emotional biases:
Dollar-Cost Averaging (DCA) has emerged as the most popular emotion-neutral strategy, with 59% of U.S. digital currency users employing this approach. By making regular purchases regardless of price, DCA removes the emotional burden of timing the market.
Automated trading tools and scheduled purchases help investors stick to predetermined strategies without succumbing to FOMO or FUD. These tools essentially outsource emotional decision-making to algorithms, reducing the psychological burden of active trading.
Education and community engagement in healthy bitcoin communities can provide emotional anchoring during volatile periods. Understanding bitcoin’s long-term value proposition helps investors maintain perspective during short-term chaos.
Bitcoin investing isn’t just about understanding technology, economics, or market analysis—it’s about understanding yourself. The statistics are clear: emotional decision-making significantly damages portfolio performance, yet the vast majority of investors continue making emotion-driven choices.
The key insight? Bitcoin’s psychology isn’t a bug—it’s a feature. The emotional volatility that terrifies traditional investors creates opportunities for th
-
 @ 7f6db517:a4931eda
2025-06-05 15:02:23
@ 7f6db517:a4931eda
2025-06-05 15:02:23
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 9ca447d2:fbf5a36d
2025-06-05 18:02:11
@ 9ca447d2:fbf5a36d
2025-06-05 18:02:11Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ dfa02707:41ca50e3
2025-06-05 15:02:22
@ dfa02707:41ca50e3
2025-06-05 15:02:22Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ fbf0e434:e1be6a39
2025-06-05 14:08:24
@ fbf0e434:e1be6a39
2025-06-05 14:08:24Hackathon 概要
ETHBratislava Hackathon Vol.2 汇聚 54 名开发者并审核通过 11 个项目,成为以太坊社区的重要盛事。此次黑客马拉松在斯洛伐克技术大学举办,参与者可免费参与 ETHBratislava 大会,这一安排助力开发者探索区块链技术的前沿进展。
项目在解决以太坊可扩展性与互操作性问题上成果显著,尤其在 “World Computer” 赛道表现突出。“Zircuit Restaking Track” 赛道也带来重要创新,聚焦通过 AI 驱动的 zk rollups 技术提升安全性与扩展性。“European Stablecoin EURØP Challenge” 则致力于开发欧元背书的稳定币,推动欧洲监管数字货币概念落地。
参与者不仅获得资深导师指导、与行业领袖建立连接的机会,现场更有招聘方挖掘技术人才。活动在兼具庆祝与社交属性的派对中落幕。总计 4,000 欧元奖金的设置,营造了开发者之间竞争与合作并存的创新氛围。ETHBratislava Vol.2 成功孵化出影响以太坊未来的创新构想,同时强化了社区联结。
Hackathon 获奖者
World Computer 奖项获奖者
此类别着重于利用以太坊能力的面向消费者的应用程序。开发者创建了解决方案,旨在增强包容性、金融工具和教育平台。获奖者包括:
- Zhar: 该去中心化平台使用AI和以太坊区块链来管理、执行和激励使用智能合约和代币的链上挑战。
- Ledger Lens: 一个Web应用程序,促进对以太坊多层生态系统的可视化和分析,强调代币流动和跨链桥使用等指标。
现实世界代币化奖项获奖者
此类别集中于在欧洲利用EUR锚定的稳定币EURØP构建效用。项目目标是在此数字货币之上部署初步技术增强。
- dEST: 一个去中心化平台,利用NFTs和智能合约来促进无中介的代币化房地产交易。
- EnergyHub: 一个提供去中心化平台以货币化多余绿色能源并通过智能合约和用户友好的仪表板实现能源捐赠的应用程序。
Restaking 奖项获奖者
此类别鼓励团队在Zircuit生态系统内的AI驱动zkEVM上进行构建,着重于支持AI增强安全性和创新zk rollup技术的项目。
- RestakerX: 一个仪表板应用程序,设计用于跟踪Zircuit网络上的数字资产,提供算法建议以最大化收益。
有关所有项目的更多详细信息和此次黑客马拉松中展示的创新理念的进一步见解,请访问 ETHBratislava Hackathon页面。
关于组织者
Ethereum Bratislava
Ethereum Bratislava 是中欧和东欧地区区块链和技术领域的一个重要社区,致力于推进以太坊的开发和整合。由一支专家团队支持,该组织在增强以太坊在中欧和东欧地区的可扩展性和安全性的项目中作出了重大贡献。积极参与社区活动和教育活动强调了他们在区块链领域促进技术创新和知识共享的承诺。Ethereum Bratislava 继续支持技术改进和生态系统增长,旨在增强以太坊的能力和跨各行业的采用。
-
 @ 7f6db517:a4931eda
2025-06-05 18:02:38
@ 7f6db517:a4931eda
2025-06-05 18:02:38
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ 975e4ad5:8d4847ce
2025-06-05 13:14:46
@ 975e4ad5:8d4847ce
2025-06-05 13:14:46What is the Fiat System and How Do Central Banks Set Interest Rates?
When central banks expand credit, they often increase the money supply by creating new money through mechanisms like quantitative easing (QE). For instance, a central bank may purchase government bonds, injecting money into the economy. This boosts liquidity but can lead to inflation when too much money chases limited goods and services.
Low interest rates make borrowing cheaper, encouraging spending and investment. However, this can overheat the economy, create speculative bubbles (e.g., in real estate), and drive inflation. Conversely, high interest rates restrict borrowing, slow the economy, and curb inflation but may trigger recessions.
How Would Interest Rates Work Under a Bitcoin Standard?
Under a Bitcoin standard, the money supply is fixed—only 21 million bitcoins will ever exist, with the last one mined around 2140. Unlike the fiat system, no central authority can manipulate the money supply or set interest rates. Instead, interest rates would be determined entirely by the market—by the supply and demand for capital.
If someone wants to borrow bitcoins, the interest rate would depend on negotiations between the lender and borrower. For example, if demand for loans is high and available bitcoins are scarce, interest rates would rise. Conversely, if there are ample bitcoin savings, rates might fall. This process would be fully decentralized and reflect real market conditions, not central bank decisions.
Since new bitcoins cannot be “printed,” there would be no inflation caused by an expanding money supply. Instead, bitcoin’s value would likely rise over time (deflation) as its fixed supply competes with growing demand. This could encourage saving over reckless spending, reshaping economic behavior.
Advantages of a Bitcoin Standard
-
Protection Against Inflation: Bitcoin’s fixed supply prevents currency devaluation, a common issue with fiat money. This safeguards savings and promotes long-term planning.
-
Decentralization: Without a central bank manipulating the market, economic decisions are made by individuals, not bureaucrats. This aligns with free-market principles where competition and innovation thrive.
-
Transparency and Security: The Bitcoin blockchain is public and immutable, ensuring transactions are transparent and secure from tampering.
-
Financial Freedom: Under a Bitcoin standard, individuals have full control over their money without government or bank interference, which is especially crucial in countries with unstable regimes or currencies.
-
Discipline in Lending: Without the ability to print money, lenders would be more cautious, reducing risky investments and speculative bubbles.
Potential Drawbacks and Why a Bitcoin Standard is Superior
One major argument against a Bitcoin standard is that it could slow economic growth. Low interest rates in the fiat system encourage borrowing and spending, driving economic activity. Under a Bitcoin standard, where interest rates are market-driven and likely higher, borrowing would be costlier, potentially limiting investments in new projects.
However, this critique misses a key point: economic growth fueled by artificially low interest rates and money printing is often unsustainable. It leads to debt crises, inflation, and bubbles that eventually burst, as seen in 2008. A Bitcoin standard promotes healthy economic discipline, where investments are based on real value, not artificial capital.
Moreover, bitcoin’s deflationary nature could shift how people view money. Instead of chasing endless growth, societies might prioritize sustainability, innovation, and efficiency. This could lead to a more stable and equitable economy in the long run.
Additional Considerations
A Bitcoin standard could transform global trade. Today, countries with fiat currencies often manipulate exchange rates to gain trade advantages. With bitcoin as a universal currency, such manipulations would vanish, fostering fairer competition.
Another aspect is energy efficiency. While bitcoin mining consumes energy, it incentivizes the development of renewable sources as miners seek cheap, sustainable energy. This could accelerate the transition to a green economy.
Conclusion
The Bitcoin standard offers a vision of an economy rooted in sound money, free markets, and financial freedom. While it may slow certain aspects of economic growth, it creates a more stable and sustainable system that protects individuals from inflation and centralized control. In a world where trust in institutions is waning, the Bitcoin standard is a step toward a fairer and more transparent future.
-
-
 @ 9ca447d2:fbf5a36d
2025-06-05 16:01:41
@ 9ca447d2:fbf5a36d
2025-06-05 16:01:41President Donald Trump’s media company, Trump Media & Technology Group (TMTG), is doubling down on its Bitcoin bet, partnering with Crypto.com and Yorkville America Digital to launch its own bitcoin exchange-traded fund (ETF), called the Truth Social Bitcoin ETF.
On June 3, a division of the New York Stock Exchange, NYSE Arca, filed a 19b-4 form with the Securities and Exchange Commission (SEC).
This is the final regulatory hurdle before an ETF can be launched. If approved, this new fund will allow everyday investors to buy shares tied to the price of bitcoin, without having to hold the asset themselves.
The Truth Social Bitcoin ETF will track the price of bitcoin and give investors a simple, regulated way to invest in the digital money.
It will be listed and traded on NYSE Arca, and Foris DAX Trust Company (the custodian for Crypto.com’s assets) has been named as the proposed custodian for this new fund.
According to the filings, the ETF is “designed to remove the obstacles represented by the complexities and operational burdens involved in a direct investment in bitcoin.”
This is part of a bigger plan by Trump Media to offer a full suite of digital-asset-based financial products.
The company has also applied to trademark six investment products and has plans for additional ETFs under its Truth.Fi fintech platform, which will focus on digital assets and energy sectors.
Trump Media also recently announced a $2.5 billion bitcoin treasury plan and raised $2.4 billion in stock and debt to support its bitcoin initiatives.
Related: Trump Media Will Raise $2.5 Billion to Build Bitcoin Treasury
Now that the 19b-4 has been filed, the SEC has 45 days to approve, reject or delay the application. This can be extended several times, but a final decision must be made by January 29, 2026.
In addition to the 19b-4, Yorkville America Digital must also file an S-1 registration statement. This will outline exactly how the ETF will work, what it offers to investors, how funds will be used, and the risks involved.
Since January 2024, bitcoin ETFs have been all the rage, with over $130 billion in assets. Big players like BlackRock’s iShares Bitcoin Trust (IBIT) and Fidelity’s FBTC dominate the space. BlackRock alone has $69 billion in assets through its bitcoin ETF.
Even though Trump’s ETF is entering a crowded field, its name will get attention. The Truth Social bitcoin ETF is expected to generate media buzz, political controversy and divided investor opinions, making it a cultural and financial statement.
Donald Trump is the majority owner of Trump Media, although his shares are in a trust controlled by his son, Donald Trump Jr. The ETF filing doesn’t mention Trump by name, but most people see it as a Trump product.
The President is getting more and more involved in the digital asset space. He has NFT collections, meme coins, a bitcoin mining company, a digital asset wallet, and now a potential bitcoin ETF.
But not everyone is happy. Some argue that a sitting president’s involvement in regulated financial products, especially one that could benefit from political influence, is unethical.
An SEC-approved digital asset product from Trump could blur the lines between politics, personal gain and digital assets.
Others, however, see this as a calculated move to boost Trump’s image and position him as a leader in the digital asset and tech space.
-
 @ cae03c48:2a7d6671
2025-06-05 16:01:20
@ cae03c48:2a7d6671
2025-06-05 16:01:20Bitcoin Magazine

Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury StrategyToday, H100 Group AB announced it has entered a SEK 21 million convertible loan from an investment agreement with Adam Back, with the option to expand his investment to SEK 277 million through a five-tranche convertible loan deal. The proceeds will be used to buy Bitcoin in alignment with H100 Group’s long-term Bitcoin treasury strategy.
H100 Group AB (Ticker: H100) secures a SEK 21M ($2.1M) commitment from @adam3us , with rights to invest an additional SEK 128M ($12.8M) in tranches—bringing the total contemplated raise to SEK 277M (~$27.7M). pic.twitter.com/c0HgMSRxut
— H100 (@H100Group) June 3, 2025
Under the agreement, Back may invest up to SEK 128 million across four additional tranches, with guaranteed participation of at least 50%. Each tranche is twice his committed amount, demonstrating his support for H100’s long-term growth.
The press release said, “Adam Back may request the Second Tranche within 90 days from signing of the Initial Tranche, the Third Tranche within 90 days from signing of the Second Tranche, the Fourth Tranche within 90 days from signing of the Third Tranche and the Fifth Tranche within ninety 90 days from signing of the Fourth Tranche. In the event Adam Back does not request a Future Tranche within the deadline, the right to request subsequent Future Tranches lapses.”
The convertible loans have no interest and have a five year maturity. At any time, Back may convert the loans into shares of the Company. Conversion prices are fixed per tranche: SEK 1.75 per share for the initial tranche, rising to SEK 5.00 by the fifth tranche. H100 retains the right to force conversion if the stock price exceeds the conversion rate by 33% over a 20 day period. Full conversion of the initial tranche would result in 12 million new shares and a 9.3% dilution.
“Upon request of a tranche Adam Back is obliged to invest in the relevant Tranche with SEK 15,750,000 in the second tranche, SEK 23,625,000 in the third tranche, SEK 35,437,500 in the fourth tranche, and SEK 53,156,250 in the fifth tranche,” stated the press release. “The contemplated size for each tranche is twice the entitled amount of Adam Back.”
Blockstream has “been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then,” said Adam Back at the 2025 Bitcoin Conference. “I think the way to look at the treasury companies is that Bitcoin is effectively the hurdle rate; it’s very hard to outperform bitcoin. Most people that have invested in things since bitcoin has been around have thought, ‘oh, I should have put that in bitcoin and not in the other thing.”
This post Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury Strategy first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ dfa02707:41ca50e3
2025-06-05 15:02:20
@ dfa02707:41ca50e3
2025-06-05 15:02:20Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 31a4605e:cf043959
2025-06-05 13:03:59
@ 31a4605e:cf043959
2025-06-05 13:03:59Nos últimos anos, o Bitcoin tem sido frequentemente comparado ao ouro, ganhando o nome de "ouro digital". Essa comparação ocorre porque ambas as formas de valor têm características em comum, como escassez, durabilidade e aceitação mundial. Contudo, o Bitcoin também representa uma novidade tecnológica que muda a ideia de dinheiro e investimento, se destacando como uma alternativa moderna e eficaz ao ouro físico.
Uma das razões pelas quais o Bitcoin é comparado ao ouro é a sua escassez programada. Enquanto o ouro é um recurso natural limitado, cuja oferta depende da mineração, o Bitcoin tem um teto máximo de 21 milhões de unidades, definido em seu código. Esse teto faz com que o Bitcoin seja protegido contra a inflação, ao contrário das moedas tradicionais, que podem ser criadas sem limites pelos bancos centrais.
Essa característica traz um valor duradouro, parecido com o ouro, já que a oferta limitada ajuda a manter o poder de compra ao longo do tempo. Com o aumento da procura por Bitcoin, sua quantidade reduzida reforça seu papel como reserva de valor.
Outro aspecto que aproxima o Bitcoin do ouro é a durabilidade. Enquanto o ouro resiste à corrosão e pode ser guardado por séculos, o Bitcoin é um ativo digital protegido por criptografia avançada e armazenado na blockchain — um livro-razão imutável e descentralizado.
Além disso, o Bitcoin é mais fácil de transportar do que o ouro. Mover ouro físico envolve custos e segurança, tornando o transporte complicado, principalmente em transações internacionais. Por outro lado, o Bitcoin pode ser enviado digitalmente para qualquer parte do mundo em minutos, com taxas baixas e sem intermediários. Essa vantagem tecnológica torna o Bitcoin mais eficaz para um mundo globalizado e digital.
A segurança é outra característica que o Bitcoin e o ouro têm em comum. O ouro é difícil de falsificar, fazendo dele uma reserva de valor confiável. Da mesma forma, o Bitcoin usa protocolos de criptografia que asseguram transações seguras e protegidas contra fraudes.
Além disso, todas as transações feitas com Bitcoin são registradas na blockchain, fornecendo um nível de transparência que o ouro físico não oferece. Qualquer pessoa pode revisar as transações na rede, aumentando a confiança e a rastreabilidade.
EconômicaHistoricamente, o ouro tem sido utilizado como proteção contra a inflação e crises econômicas. Durante momentos de instabilidade, os investidores buscam o ouro como uma maneira de preservar seu patrimônio. O Bitcoin, por sua vez, está surgindo como uma alternativa digital com o mesmo propósito.
Em países com alta inflação ou instabilidade política, o Bitcoin tem sido usado como uma proteção contra a desvalorização das moedas locais. Sua natureza descentralizada impede que governos confisquem ou controlem diretamente o ativo, garantindo maior liberdade financeira para os usuários.
Apesar de suas semelhanças com o ouro, o Bitcoin ainda enfrenta desafios. Sua volatilidade é muito maior, o que pode causar incertezas a curto prazo. No entanto, muitos especialistas afirmam que essa volatilidade é uma característica comum em ativos novos e tende a diminuir com o tempo, à medida que a aceitação cresce e o mercado se desenvolve.
Outro desafio é a regulamentação. Enquanto o ouro já é reconhecido globalmente como um ativo financeiro, o Bitcoin ainda enfrenta resistência de governos e instituições financeiras, que procuram formas de controlá-lo e regulá-lo.
Resumindo, o Bitcoin, muitas vezes chamado de "ouro digital", oferece uma nova forma de valor que combina as melhores características do ouro com a eficiência e a inovação da tecnologia digital. Sua escassez planejada, segurança criptográfica, portabilidade e resistência à censura fazem dele uma alternativa viável para preservar riqueza e realizar transações no mundo moderno.
Mesmo com muita volatilidade, o Bitcoin está se firmando como uma reserva de valor e como um ativo de proteção contra crises econômicas. Assim, ele representa não apenas uma evolução do sistema financeiro, mas também um símbolo da mudança para uma economia digital descentralizada e global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ dfa02707:41ca50e3
2025-06-05 15:02:19
@ dfa02707:41ca50e3
2025-06-05 15:02:19Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 812cff5a:5c40aeeb
2025-06-05 12:55:10
@ 812cff5a:5c40aeeb
2025-06-05 12:55:10Chorus: تجربة في البرمجة الانسداحية
كيفية بناء تطبيق Nostr بسرعة البرق باستخدام الذكاء الاصطناعي.
في 26 مايو، تم إطلاق تطبيق Chorus في منتدى أوسلو للحرية. صُمم هذا التطبيق للناشطين والمعارضين ومنظمي المجتمع، ويتميز بمجموعات تشبه تلك الموجودة في فيسبوك مع محفظة eCash مدمجة لجمع التبرعات.
Chorus مبني على Nostr، وهو بروتوكول لامركزي ومفتوح مصمم ليكون مقاومًا للرقابة. يمكن لأي شخص في العالم إنشاء حساب Nostr والنشر إلى خوادم Nostr، أو حتى بناء تطبيق Nostr خاص به — ولا يمكن لأحد إيقافه. هذا ما يجعل Nostr المكان المثالي للمقاتلين من أجل الحرية، الذين غالبًا ما يواجهون الرقابة من الحكومات الاستبدادية أو الشركات التي تتحكم في المنصات الاجتماعية الرئيسية.
يمكن للمستخدمين إنشاء حساب Chorus (أو تسجيل الدخول باستخدام حساب Nostr موجود) في ثوانٍ والبدء فورًا في استلام eCash، وإنشاء مجموعات، ومشاركة المحتوى. يتضمن التطبيق ميزات قوية لإدارة المجتمع، بحيث يمكن للمجموعات اختيار أنواع المحتوى التي تسمح بها وفقًا لشروطها الخاصة. يمكن للمستخدمين إرسال eCash على الفور إلى المجموعات التي يرغبون في دعمها، مما يوفر أداة لجمع التبرعات عبر الحدود لا يمكن لأي حكومة إيقافها.
قبل عام فقط، ربما استغرق بناء النسخة التي تم إطلاقها الأسبوع الماضي من Chorus أسابيع. ولكن بفضل أدوات الذكاء الاصطناعي الحالية، قمنا بذلك في خمسة أيام فقط.
⸻
كيفية القيام بذلك: بناء تطبيق في أيام باستخدام وكلاء الذكاء الاصطناعي
الخطوة 1: تجميع الفريق
تم بناء Chorus بواسطة And Other Stuff، وهي مجموعة جديدة مكرسة لتعزيز Nostr في خمسة مجالات رئيسية: تجربة المستخدم والتسجيل، المجتمعات، الاتصالات الخاصة، التجارة، والذكاء الاصطناعي. شمل فريق هذا المشروع: • Calle، منشئ Cashu (eCash) • JeffG، منشئ White Noise (الاتصالات الخاصة) • Rabble و Liz Swiegart من Nos (تجربة المستخدم والتسجيل) • Alex Gleason و MK Fain، منشئو Soapbox (المجتمعات) • و Jack Dorsey (مستشار)
الخطوة 2: البدء بقالب قوي
عند البرمجة بالانسداح، السياق هو الملك. إذا بدأت بمجلد فارغ وطلبت من وكيل ذكاء اصطناعي “بناء تطبيق مجموعات Nostr”، فلا يزال أمامك الكثير من العمل للحصول على شيء وظيفي حتى بشكل بسيط. من المحتمل أن تكون تنفيذات Nostr محاكاة، لا تتصل بخوادم حقيقية، أو تم تنفيذها بشكل غير صحيح. قد تكون أنواع الأحداث خاطئة، وقد لا يتم تحميل واجهة المستخدم، وحظًا سعيدًا في محاولة معرفة الخطوة التالية لإصلاح الفوضى.
هذا لأن الذكاء الاصطناعي يفتقر إلى بعض السياقات الرئيسية للبدء: • وثائق صديقة للذكاء الاصطناعي حول بروتوكول Nostr • أمثلة عالية الجودة على تنفيذ Nostr • أساسيات حول تكديس التكنولوجيا المفضل • سياق حول كيفية بناء المشروع وتشغيله وتصحيحه
الحل هو توفير المزيد من السياق، وسيكون العديد من مبرمجي الانسداح المخضرمين على دراية بالصراع في محاولة جعل الوكيل يقرأ روابط مختلفة للوثائق ويتبع 500 كلمة من السياق المصاغ بعناية في مطالبتهم الافتتاحية. ومع ذلك، غالبًا ما يربك هذا الوكلاء الذين يعملون بشكل أفضل مع مطالبات بسيطة. الحل لهذه المشكلة هو Stacks.
Stacks: بدء البرمجة الانسداحية بسرعة
Stacks تحل مشكلة نقص السياق الأولي من خلال إنشاء قوالب جاهزة مصممة خصيصًا لاستخدام وكلاء الذكاء الاصطناعي. يمكن استخدام “stack” لبناء أي نوع من المشاريع بأي لغة برمجة مع أي هدف نهائي في الاعتبار. بالنسبة لـ Chorus، استخدمنا MKStack، وهو قالب مصمم خصيصًا لبناء تطبيقات Nostr.
يتميز MKStack بعدة حلول للمشاكل الشائعة في الذكاء الاصطناعي: • Nostrbook MCP للاستعلام عن وثائق Nostr • مكونات بداية لميزات Nostr الشائعة مثل تسجيل الدخول • دعم Blossom لتحميل الوسائط • ملفات سياقية لتوجيه الوكيل خلال العقبات الشائعة وسير عمل التصحيح • نشر موقعك على الفور باستخدام Surge
النتيجة هي موقع جميل يعمل مباشرة مع Nostr في مطالبة واحدة:
“بناء تطبيق مجموعات على غرار فيسبوك على Nostr باستخدام NIP 72.”
كان هذا هو نتيجة تلك المطالبة الواحدة: http://groups72.surge.sh
الخطوة 3: إضافة الميزات باستخدام وكلاء الذكاء الاصطناعي
Stacks بدأت تطوير Chorus بسرعة. بعد ذلك، استخدمنا وكلاء الذكاء الاصطناعي لإضافة ميزات إضافية مثل: • محفظة eCash مدمجة • ميزات إدارة المجتمع • دعم الوسائط المتعددة
كل ذلك تم باستخدام مطالبات بسيطة وتوجيهات للذكاء الاصطناعي، مما سمح لنا ببناء تطبيق كامل الوظائف في أيام قليلة فقط.
⸻
ملاحظة:تم استخدام مصطلح برمجة الانسداحية بهدف الطرفة كترجمة لمصطلح Vibe coding تم كتابة هذه المقال من قبل المبدعة nostr: npub1jvnpg4c6ljadf5t6ry0w9q0rnm4mksde87kglkrc993z46c39axsgq89sc
-
 @ b1ddb4d7:471244e7
2025-06-05 18:01:51
@ b1ddb4d7:471244e7
2025-06-05 18:01:51“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ 9ca447d2:fbf5a36d
2025-06-05 15:01:55
@ 9ca447d2:fbf5a36d
2025-06-05 15:01:55Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ 31a4605e:cf043959
2025-06-05 12:49:36
@ 31a4605e:cf043959
2025-06-05 12:49:36O surgimento do Bitcoin trouxe uma nova visão para o conceito de dinheiro, desafiando o sistema financeiro convencional baseado em moedas fiduciárias. Enquanto as moedas fiduciárias, como o real, o dólar e o euro, são amplamente usadas e reconhecidas como métodos de troca, o Bitcoin representa uma inovação digital que propõe descentralização e autonomia financeira. Embora ambos desempenhem funções básicas como meio de troca e reserva de valor, suas diferenças principais estão na maneira como são emitidos, geridos e transacionados.
Uma das principais distinções entre o Bitcoin e as moedas fiduciárias é a maneira como são emitidos e administrados. As moedas fiduciárias são emitidas por bancos centrais, que têm o poder de regular sua quantidade em circulação. Esse modelo permite a aplicação de políticas monetárias, como o aumento da oferta de dinheiro para estimular a economia ou a diminuição para controlar a inflação. No entanto, essa capacidade também pode resultar na desvalorização da moeda, se for emitida em excesso.
O Bitcoin, por outro lado, tem um sistema de emissão totalmente descentralizado. Ele é criado por meio de um processo chamado mineração, no qual computadores resolvem problemas matemáticos complexos para validar transações na rede. Além disso, a oferta total de bitcoins é limitada a 21 milhões de unidades, tornando-o um ativo deflacionário, ou seja, sua escassez pode aumentar seu valor ao longo do tempo. Essa limitação contrasta fortemente com a natureza ilimitada da impressão de moedas fiduciárias.
Moedas fiduciárias são centralizadas, o que significa que sua emissão e controle são decididos por autoridades governamentais. Isso também implica que transações feitas com essas moedas passam por intermediários, como bancos, que podem aplicar taxas e limites, além de estarem sujeitos a regulamentações e auditorias.
O Bitcoin, por sua vez, é descentralizado. Ele opera em uma rede peer-to-peer, onde as transações são verificadas por participantes chamados mineradores e registradas em um livro público conhecido como blockchain. Essa descentralização elimina a necessidade de intermediários, tornando o Bitcoin mais resistente à censura e ao controle governamental. Isso também proporciona maior transparência, já que qualquer pessoa pode verificar as transações na rede.
Outra diferença importante está na maneira como as transações são feitas. Com moedas fiduciárias, as transações geralmente dependem de bancos ou sistemas de pagamento, que podem impor restrições de horários e taxas altas, especialmente para transferências internacionais.
O Bitcoin, por outro lado, permite transferências diretas entre pessoas, em qualquer lugar do mundo e a qualquer momento, sem a necessidade de intermediários. Isso torna o sistema mais acessível, especialmente para aqueles que não possuem contas bancárias ou vivem em países com sistemas financeiros restritivos. Além disso, as taxas de transação do Bitcoin podem ser menores do que as taxas cobradas por bancos tradicionais.
As moedas fiduciárias proporcionam segurança baseada em leis governamentais e no sistema bancário, mas os usuários precisam confiar nesses intermediários. O Bitcoin, em contrapartida, oferece um alto nível de segurança através de criptografia avançada. As carteiras digitais, que guardam bitcoins, são protegidas por chaves privadas, assegurando que somente o dono possa acessá-las.
No entanto, a privacidade funciona de maneira diferente. Transações em moedas fiduciárias normalmente estão ligadas à identidade do usuário, enquanto o Bitcoin oferece um certo nível de anonimato, já que os endereços das carteiras não requerem identificação pessoal. Ainda assim, todas as transações são públicas e registradas no blockchain, o que pode ser um ponto de monitoramento para autoridades.
O valor das moedas fiduciárias é sustentado pela confiança no governo que as emite e na economia do país. Por outro lado, o Bitcoin não é apoiado por nenhum governo ou ativo físico. Seu valor é definido pela oferta e demanda no mercado, fazendo com que seja altamente volátil. Embora essa volatilidade apresente um risco, também atrai pessoas que veem o Bitcoin como uma possibilidade de valorização a longo prazo.
Resumindo, o Bitcoin e as moedas fiduciárias diferem significativamente em sua estrutura, controle e funcionalidade. Enquanto as moedas fiduciárias são controladas por governos e dependem de intermediários, o Bitcoin oferece descentralização, transparência e liberdade financeira. Apesar de sua volatilidade e alguns desafios relacionados à regulamentação, o Bitcoin representa uma alternativa nova ao sistema financeiro tradicional.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 2cde0e02:180a96b9
2025-06-05 15:13:03
@ 2cde0e02:180a96b9
2025-06-05 15:13:03pen & ink; monochromized
Magdalena Carmen Frida Kahlo y Calderón[a] (Spanish pronunciation: [ˈfɾiða ˈkalo]; 6 July 1907 – 13 July 1954[1]) was a Mexican painter known for her many portraits, self-portraits, and works inspired by the nature and artifacts of Mexico. Inspired by the country's popular culture, she employed a naïve folk art style to explore questions of identity, postcolonialism, gender, class, and race in Mexican society.[2] Her paintings often had strong autobiographical elements and mixed realism with fantasy. In addition to belonging to the post-revolutionary Mexicayotl movement, which sought to define a Mexican identity, Kahlo has been described as a surrealist or magical realist.[3] She is also known for painting about her experience of chronic pain.[4]
https://stacker.news/items/997980
-
 @ 8bad92c3:ca714aa5
2025-06-05 13:01:29
@ 8bad92c3:ca714aa5
2025-06-05 13:01:29Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 90c656ff:9383fd4e
2025-06-05 12:27:43
@ 90c656ff:9383fd4e
2025-06-05 12:27:43When people talk about Bitcoin, it’s often described as a digital currency or a “speculative investment.” However, one of Bitcoin’s most fundamental and least understood roles is its function as a settlement network. To understand this, it’s worth comparing it with traditional settlement systems like SWIFT and exploring how Bitcoin offers a foundational layer for global value transfer decentralized and censorship-resistant.
First, let’s explain the difference between liquidity and settlement:
-
Liquidity refers to the ease with which an asset can be converted into “money” without losing value.
-
Settlement is the process of completing a transaction (actual transfer of value between parties).
SWIFT: The communication layer of the traditional financial system
The SWIFT system (Society for Worldwide Interbank Financial Telecommunication) is a network for communication between banks. It doesn’t move money directly but sends standardized messages that instruct financial institutions to perform transfers. The process involves multiple intermediaries, is costly, slow (can take days), and depends on trust between parties and local regulations.
Unlike SWIFT, Bitcoin is a self-sufficient network that enables the direct settlement of value between two parties, without the need for intermediaries. With each block mined, transactions are validated and recorded immutably in a global, transparent, and secure database: the timechain or "blockchain".
01 - Final settlement: Once a transaction is confirmed by a sufficient number of blocks, it is considered final and irreversible.
02 - Censorship resistance: There is no central entity that can block or reverse a valid transaction.
03 - Global availability: The network is accessible 24/7 anywhere in the world with internet access.
Just as gold once served as the foundation of monetary systems, Bitcoin is establishing itself as a base layer of digital value. This layer can support others, such as:
01 - The Lightning Network, which enables near-instant transactions with extremely low fees;
02 - Tokenized financial services, which can use Bitcoin as collateral or for inter-institutional settlement.
By functioning as a public and neutral settlement network, Bitcoin offers an alternative to the traditional system, which is fragmented, closed, and reliant on trust between institutions.
In summary, more than just a speculative asset, Bitcoin is emerging as a global financial infrastructure. As a settlement network, it removes intermediaries, reduces costs, increases security, and democratizes access to value transfer. In an increasingly interconnected and digital world, understanding Bitcoin’s role as a base layer may be key to understanding the future of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
-
 @ dfa02707:41ca50e3
2025-06-05 15:02:22
@ dfa02707:41ca50e3
2025-06-05 15:02:22
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.

- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 87fedb9f:0da83419
2025-06-05 12:15:33
@ 87fedb9f:0da83419
2025-06-05 12:15:33So Much… and Still, Not Feeling It
So much abundance. It’s everywhere—overflowing around me. My six-year-old car would be a magical carriage to kings and queens of old. And yet, I get in, turn the key, and don’t often Feel The Magic.
Do I let myself feel how abundant life is? Eh. That does not come by default for me.
Adapting Is Normal. Savoring Is Not.
I adapt. I’m good at it. Weather shifts 40 degrees? No problem. A new location? I’ll adjust. And that’s useful—it keeps me moving. But it also numbs me. If I only adapt, life flattens out. That’s not thriving. That’s functioning.
Thriving, I’ve come to feel, asks for something more.
Our ancestors had rituals. They didn’t just adapt… they paused to feel the blessings, to name them. That created richness—not just survival. And today? I can have food delivered to my door. Are you a king? No—just have Amazon Prime.
Still, I want more than convenience. I want connection. To the food I eat. The flowers that bloom. The people I love. I want to feel that connection in my bones.
My Engineer Brain Doesn’t Celebrate
And yet, my mind often slips into improvement mode. I see what could be better. Smoother. More efficient. Useful? Sure. Celebratory? Not so much.
So I’ve started something: at the end of each day, when I look at my to-do list, I take a breath. I ask: what were the blessings today? Not just the big ones—because we adapt to those too. A new car? A new house? We get used to it. Quickly. But the micro-blessings… those are different.
My daughter’s laugh at a silly face I made yesterday. That memory settles deeper when I notice it and write it down. That’s a micro-blessing. I want to feel more of those.
A New Practice, A Shift in Dreams
And after about 75 days of doing this nightly pause, I’m noticing something surprising: my dreams are changing. They’re weaving in those sweet, ordinary moments. They say, “Yes. Adapt. And also savor.”
The Confusion Between Privilege and Blessing
But here’s something raw. Something I’ve hesitated to share.
I’m a white man. An older one. And I’ve been in spaces where “white male privilege” is spoken as a curse. I absorbed that. My body did. And it twisted something deep inside me. Because in my system, “privileged” and “blessing” are linked.
So I started feeling that feeling blessed was wrong. Like I should shrink from it. That it was unfair, maybe even immoral.
I’ve had to tap through that.
Is it okay to feel blessed? Not above anyone—but blessed to have food. Skill. Mobility. A car that works. Is it okay?
Yes.
I Don’t Want to Shrink or Perform
Scarcity and guilt are real energies, but I don’t want them steering my experience of life. I want to choose presence. Connection. I want to know in my body: I am blessed. And I can feel that without disconnecting from those who are struggling.
I don’t want to perform gratitude out of duty. But I also don’t want to avoid it out of shame.
Practicing Our Birthright
Abundance is our birthright. Many of us are born with protections our ancestors could barely dream of—shelter, clean water, safety from predators. And if we want to truly be thriving, not just surviving, it feels essential to practice remembering that.
Because adaptation will keep us alive.
But only conscious attention to blessings—only savoring—will let us thrive.
Useful Concepts for Thriving in This Story
-
Abundance\ Abundance is the felt experience of more-than-enoughness, when we pause to really receive what surrounds and sustains us.
-
Adapting\ Adapting keeps us functional, but thriving asks us to adapt and engage with what truly nourishes us.
-
Awareness\ Awareness brings the blessings into view—even the ones so small they almost disappear without it.
-
Allowing\ Allowing lets us stay open to blessings, even when shame or guilt try to close the door.
-
Thriving\ Thriving means more than surviving—it’s about feeling, savoring, and aligning with life’s richness.
-
-
 @ e4950c93:1b99eccd
2025-06-05 10:23:39
@ e4950c93:1b99eccd
2025-06-05 10:23:39Marques
Nordkidz est une marque allemande qui crée à la demande des vêtements et linges pour les bébés, les enfants, et un peu pour leurs parents.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements : bébés, enfants, unisexe
- Hauts : pulls, t-shirts
- Bas : pantalons, pantalons de survêtement, shorts
- Tête et mains : bonnets, écharpes
Maison
- Linge : housses de pouf, langes, ponchos de bain
Autres informations
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Nordkidz (en allemand, zone de livraison : Allemagne et Union Européenne) 💚 Via ce lien vous soutenez directement la marque.
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:46:07
@ 20e7c953:3b8bcb21
2025-06-05 10:46:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bircoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
Skatestr
-
 @ b1ddb4d7:471244e7
2025-06-05 10:00:43
@ b1ddb4d7:471244e7
2025-06-05 10:00:43Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ dfa02707:41ca50e3
2025-06-05 15:02:18
@ dfa02707:41ca50e3
2025-06-05 15:02:18Contribute to keep No Bullshit Bitcoin news going.

This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:17
@ 8bad92c3:ca714aa5
2025-06-05 15:02:17Key Takeaways

In this episode, Bitcoin Core veteran James O’Beirne delivers a sharp critique of Bitcoin’s developmental stagnation, attributing it to political dysfunction, post-fork trauma, and resistance within Bitcoin Core to critical upgrades like CheckTemplateVerify (CTV). He argues that while institutional adoption accelerates, internal innovation is being stifled by misplaced controversies—such as the OP_RETURN policy debate—and a bottlenecked governance model. O’Beirne warns that without urgent progress on scaling solutions like CTV, congestion control, and vaulting systems, Bitcoin risks ossifying and becoming vulnerable to institutional capture. Advocating a more adversarial posture, he suggests forking or building alternative clients to pressure progress but remains hopeful, seeing rising momentum for protocol upgrades from developers outside the Core elite.
Best Quotes
“Everybody has mempool derangement syndrome… it’s such a small issue in the grand scheme of challenges Bitcoin is facing.”
“Bitcoin is as much an experiment in technical human organization as it is a pure technology.”
“If we don’t figure out how to scale trustless Bitcoin self-custody, we’re toast. Right now, only about 2.5% of Americans could actually use Bitcoin monthly in a meaningful way.”
“CTV isn’t sexy—it just works. It keeps getting reinvented because it's so useful. At this point, it’s essential.”
“If Core isn’t going to evaluate these proposals, someone has to. Otherwise, we need to build the social justification for forking.”
“Lightning didn’t scale Bitcoin the way we expected. Let’s stop assuming a silver bullet is coming and start building the bridges ourselves.”
“You could onboard someone with just a phone and a vault… and give them more security than most hardware wallets.”
Conclusion
While Bitcoin gains traction with institutions and governments, its internal development is stalling under political inertia and misplaced focus. James O’Beirne urges the community to prioritize impactful upgrades like CTV and CCV, challenge the bottleneck of Bitcoin Core if needed, and recommit to Bitcoin’s foundational principles. This episode underscores the urgent need to bridge technical and social divides to ensure Bitcoin remains a decentralized, censorship-resistant tool for global value transfer.
Timestamps
0:00 - Intro
0:41 - Multi axis issue
5:12 - Core governance
9:41 - Derailing productive discussions
17:05 - Fold & Bitkey
18:32 - CTV
29:24 - Unchained
29:53 - Magnitude of change
41:45 - Covenant proposals
50:16 - CTV benefits
57:56 - Institutional ownership
1:05:26 - Moving forwardTranscript
(00:00) I think I have a somewhat different take than 99% of the people in the discussion. What freaks me out is if you've got Sailor owning half million coins or whatever and Black Rockck owning however many, people forget that Bitcoin is as much an experiment in technical human organization as it is, you know, as a sort of pure technology.
(00:17) The undernowledged reality is I'm actually interested to see if we have like a black swan adoption event from the machines. the risk given the increased scrutiny that things like the strategic Bitcoin reserve introduce there's a shot clock on getting to trustless decentralized value storage technology and I think we really have to be thinking about that combination of physically tired and mentally tired it's also tiresome James it's it's I was looking at that picture today and I was actually going to tweet it absent any caption just because it's
(00:52) a really good Uh yeah, it's a really good epitome of uh of a lot of stuff. But I'm with you, man. I'm tired. It's Friday. Who is it? Is that a just some random Japanese guy? I think it's it's I actually think it's from a documentary about I don't know if it's Africa, but Oh, yes. Yes.
(01:13) It's there's a little bit of a kind of like racy connotation there. Um yeah, the uh it's been long. It was interesting for me. We had Texas Energy Mining Summit here in Austin the beginning of the week. It sort of blended with Bitcoin plus I was over at Bitcoin++ Wednesday and yesterday doing the live desk and obviously topic of conversation is OP return this policy decision and this policy change that that core wants to make and many people are uh angry about and it's just again it's also tiresome.
(01:52) spoke with people on both sides over the two days and I I think I came away more confused than than I entered entered the week like what is the optimal path and somebody who's worked on Bitcoin core worked on Bitcoin core for for many years I've seen you tweeting about it seems like I won't put words in your mouth I'll let you say like what is your perspective on this whole policy debate around op return yeah so in general I think I have a somewhat different take than um 99% of the people in in the discussion which is basically that this
(02:25) is a really stupid discussion um everybody has mempool derangement syndrome like at every layer um and uh what what frustrates me a little bit about the conversation not not to not to uh get like um grumpy right off the bat but it's just it's it's such a small issue in the in the grand scheme of challenges that are being presented to Bitcoin that like spending all this drama on it um is is really a silly use of time and uh kind of emotion, but I can break it down for you.
(03:02) I mean, I think I think like largely the argument is happening on a few layers. Um the change itself technically I'm totally in favor of it. It makes sense. you know, basically the rationale is like, well, you know, um, people want to include exogenous data into the chain. Um, you can't really stop them from doing that.
(03:23) Um and so let's basically minimize the damage by saying hey you know we're going to make it easier for people to actually make use of op return as a data carrier which uh lets us avoid bloat in the UTXO set which is like one of the precious resources we have to take care of for the node.
(03:44) Um, so that's all good and the and the other thing too is that as we've seen with the ordinal stuff is um, you know, data is going to wait make its way into the chain and actually it hurts the whole network when um, there are transactions that most nodes haven't seen yet but they come through a block. Basically that slows down block propagation time.
(04:06) And so the whole idea is if you bring policy closer to the actual consensus rules, closer to the actual transactions that are going to come through and be mined, then you're going to have better network performance. You're going to have lower latency when it comes to actually broadcasting a new block around. So that's like the the sort of technical layer of the discussion.
(04:25) It's it's really a minute non-controversial change if you kind of have fluency with the the technical end of the mempool. Um, but I think there's this this higher layer to the conversation which is sort of a readjudication of spam in Bitcoin. And it's, you know, I think a lot of the the old animal spirits and sentiments are emerging about like, well, we don't like spam.
(04:49) And I think for a lot of people who kind of get lost in the technical details, it's very easy to latch on to the sentiment of I don't like spam. Um and so uh so that makes the sort of ocean knots camp maybe more appealing. Uh so that's yeah that's I guess a summary if you want to jump in anything in particular we can that's what I was saying I came out more confused than I went in.
(05:20) So last week on RHR, hey, I agree. You want policy to be aligned with consensus. Like whether we like it or not, these transactions are getting into blocks. They're non-standard, but they are valid within consensus rules and policy just isn't aligning with that. And like you said, this is disrupting the P2P layer and potentially the fee uh estimation process that that many nodes use, many applications use.
(05:49) And it makes sense to me to align policy with consensus. These things are happening. And if you can make it so Bitcoin full nodes are operating as efficiently and optimally as possible by changing this, it makes sense to me. I think my one like push back was like makes sense to me. However, I think how it was communicated to people and the whole mess with the PR.
(06:12) I think it's I think it's it was it's it's just a tactical error. Like even if this change gets in the the the real benefit of is is not material. You know, nobody was really clamoring for it. um this stuff always, you know, gets the hackles up of everybody who cares at all about, you know, spamming Bitcoin. So, it was a real tactical error.
(06:36) And I think that's that's one place where I mean it's kind of I had a little bit of shot in Freud seeing it because I'm fairly critical of core as a project along you know a variety of axes at this point and it was just kind of a demonstration of the the disconnection and kind of ineptitude of um publicity management kind of on on their end.
(06:58) Um, and so like there's part of me that enjoys seeing that because I I'm kind of convinced that that group has a lot less efficacy than they have credibility. And so to to see that kind of catch up was was interesting. The uh let's dive into that like what you said multiple axes you have a problem. I think we've throughout the years like we've been discussing the issues that Bitcoin like yourself particularly as a Bitcoin core developer for many years trying to get things through not only in the context of the way core works from a governance
(07:35) structure but just the way Bitcoin works as a distributed open source protocol like trying to get changes in and I will say like -
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:17
@ 8bad92c3:ca714aa5
2025-06-05 15:02:17Marty's Bent

If you do one thing today, take the time to spend an hour to watch this YouTube video. As someone creating content who has become very cognizant of the effects of the algorithm and the pressures to cater to it, this video was unexpectedly and incredibly satisfying. We're coming up on the eight year anniversary of this newsletter and the podcast that accompanies it and over that eight year period, the pressures to compete in the world of ever increasing digital soy slop grow at an accelerating rate.
If you've seen our YouTube channel recently, you'll probably notice that we've bent the knee to the thumbnail and title clickbait game in an attempt to get our content out to a wider audience. This is something I've held out on for many years now at this point, but recently became convinced that it's something we simply have to do if we want to get our message out to a wider audience. As I write this, I'm thinking that maybe the fact that we have to do that in the first place says something about the content we're putting out there and whether or not it is actually valuable. But I do think the high velocity trash economy becoming completely saturated with digital soy slop has made it so people who truly want to get their message out have to play that game.
I want to make one thing clear. I certainly do not think I'm an artist, but I do like to think that over the last eight years we've been putting out information via content mediums that is valuable to you, dear reader. However, the informational content we put out there, particularly the audio and video content, is put on platforms where it is forced to compete with others who cater to the lowest common denominators of dopamine hijacking and in-group signaling that draws the masses like moths to a flame.
If you haven't watched the YouTube video yet, which I'm assuming 99.9% of you haven't, this may seem like a nonsensical ramble. So, I'll keep this one short and urge you to go watch the social commentary from comedian Jarrett Moore about the state of art, "content" and its effect on culture as it stands today. I'm assuming this isn't too much of a spoiler alert, but the situation is pretty dire. The world needs better art and people who are willing to support artists who are truly creative and take risks. This has nothing to do with bitcoin. But I think it highlights an interesting part of our society that is deteriorating at a rapid clip. And it's something that all of us should feel compelled to attend to lest we speed run into Idiocracy.
It made me feel uneasy about parts of my approach to this business, and that's a good thing.
Don't forget to buy a Bitkey!
Iran's Nuclear Ambitions Create a "Never-Ending Crisis"
In our latest discussion, energy expert Dr. Anas Alhajji described what he called Iran's "never-ending crisis" – a thesis he first published over 20 years ago that has proven remarkably accurate. As Alhajji explained, this crisis persists because of a fundamental contradiction: the U.S. sees any Iranian nuclear program (even peaceful) as strengthening a hostile regime, while Iran views nuclear energy as essential for domestic stability and economic survival.
"Iran is not going to negotiate over the bomb. They want to drag everything for the longest period until they get the bomb." - Dr. Anas Alhajji
What's particularly concerning is Iran's resilience against sanctions. Alhajji detailed how Iran has masterfully circumvented oil export restrictions through China, using a dedicated Chinese bank to process payments outside the international system. Iran's leadership appears willing to endure temporary geopolitical losses in Syria, Lebanon, and potentially Yemen, calculating that obtaining nuclear weapons will fundamentally transform regional politics and their treatment by the United States.
Check out the full podcast here for more on Trump's Middle East strategy, the future of BRICS, and critical challenges facing global energy infrastructure.
Headlines of the Day
Standard Chartered Predicts Bitcoin Will Reach $500K by 2028 - via X
Lummis: Genius Act Makes US Leader in Digital Asset Policy - via X
Get our new STACK SATS hat - via tftcmerch.io
Jake Tapper's Admission on Biden's Decline Sparks Media Ethics Debate - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
My oldest is already at the "faking sick to get out of school" stage and I'm extremely proud.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:16
@ 8bad92c3:ca714aa5
2025-06-05 15:02:16
Another week of conversations with sharp minds thinking about Bitcoin's future and the broader economic landscape. Here are the three most compelling predictions from recent episodes.
Bitcoin Core Will Face a Major Governance Crisis Over Covenant Proposals in 2025 - James O'Beirne
James made a prediction that sent chills through the Bitcoin development community - he believes Bitcoin Core's current governance structure will reach a breaking point this year over covenant proposals like CTV. After working as a Core developer for nearly a decade, he's convinced that the organization's inability to make progress on scaling solutions will force alternative implementations.
His timeline is specific and urgent. James believes that if Core doesn't show "substantive review discussion about how we get this stuff in" within six months, credible developers will start building alternate activation clients. The technical argument is compelling: covenants like CheckTemplateVerify have been thoroughly reviewed for seven years, with a 5 BTC bounty (worth over $500,000) still unclaimed for finding material bugs.
The stakes couldn't be higher for Bitcoin's future. James noted that currently "just over two and a half percent of Americans would be able to, on a monthly basis, buy Bitcoin on an exchange, withdraw it to self-custody, and then maybe make a spend." Without scaling solutions, this number won't improve meaningfully. His prediction reflects growing frustration with Core's de facto monopoly over protocol development. "You simply can't ignore that there is a social reality to being in that world," he said, referring to the concentrated funding and decision-making power that has created what he sees as an unsustainable bottleneck for Bitcoin's evolution.
The U.S. Will See Widespread Energy Blackouts as AI Data Centers Strain the Grid - Anas Alhajji
Dr. Anas delivered a sobering prediction about America's energy infrastructure failing to keep pace with exploding AI demand. He expects we'll see significant blackouts in major cities within the next few years, with a particularly concerning scenario where AI facilities maintain power while residential areas go dark. "I will not be surprised if we end up with a situation like this in some states and some cities," he warned.
The mathematics behind his prediction are stark. Energy consumption is skyrocketing due to multiple factors: urbanization, AI data centers, and simple population growth. When migrants move from rural areas to U.S. cities, their energy consumption increases by 30-70 times. Meanwhile, AI facilities require massive baseload power that renewable sources simply cannot provide reliably.
The infrastructure problems run deeper than just generation capacity. Anas explained that America's electrical grid is aging and wasn't designed for this level of demand. Even worse, we lack the manufacturing capacity to produce enough natural gas turbines - the only realistic solution for reliable baseload power at scale. He predicts this will create a dangerous political dynamic where tech companies with guaranteed power contracts maintain operations during blackouts while regular citizens lose electricity. "We might see a backlash from the population, and we will see politicians basically being forced to fight them because of that."
AI Will Force Millennials Into Career Reinvention Within the Next Decade - Bram Kanstein
Bram made a stark prediction about the collision between artificial intelligence and millennial career paths. He believes that traditional knowledge-based jobs will become obsolete much faster than people expect, forcing an entire generation to completely rethink their working lives. "If you think you're going to work for the next 30 years of your life, think again," he warned during our conversation.
His argument centers on the rapid advancement of AI capabilities that he's witnessed firsthand. After spending just 12 hours working with AI tools, Bram claims he developed what could be "a top 10 cybersecurity invention" - despite having no cybersecurity background. This experience convinced him that jobs requiring strict knowledge and logic are already dead. The implications are massive for millennials who built their careers around expertise that AI can now replicate instantly.
The timing couldn't be worse, as Bram notes that this technological disruption is happening precisely when millennials need stable income to support families and prepare for retirement. His solution? Use Bitcoin to create the time and space needed to figure out how to function in an AI-dominated world. "You need to be aware of that. This is where it's going. So how do you protect yourself in an age of AI? Bitcoin is the perfect way to do that."
Blockspace conducts cutting-edge proprietary research for investors.
New Bitcoin Mining Pool Flips Industry Model: "Plebs Eat First" Could Threaten Corporate Dominance
Parasite Pool's radical zero-fee structure challenges mining giants by guaranteeing payouts to small miners while rewarding block finders with instant Bitcoin. It disrupts traditional mining with a hybrid payout model that gives block discoverers 1 BTC immediately, while distributing remaining rewards (~2.125 BTC plus fees) among all pool participants. This "plebs eat first" approach targets the 22% discount miners typically accept in exchange for guaranteed income.
Key innovations that matter:
- Lightning Network integration bypasses Bitcoin's 100-block maturity rule, delivering instant payouts to Lightning wallets
- 10-sat minimum withdrawal eliminates traditional barriers for small miners
- Block withholding protection through substantial honest-miner rewards reduces pool attacks
The pool currently commands just 5 PH/s (0.000006% of Bitcoin's network), meaning an expected 3+ years before hitting a block. But this represents a growing counterculture against Full Pay Per Share (FPPS) pools that dominate corporate mining.
Industry impact: If successful, Parasite Pool could attract commercial miners seeking downside protection while maintaining the lottery appeal that drives pleb participation. The model challenges the structural advantages of corporate mining pools.
What's next: ZK Shark plans to open-source components over time, with the current beta suggesting this is just "V1" of a broader disruption strategy.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
STACK SATS hat: https://tftcmerch.io/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ d5c440ce:04726d89
2025-06-05 06:19:49
@ d5c440ce:04726d89
2025-06-05 06:19:49Effektiv behandling af blodsprængninger kræver en professionel tilgang og de rette metoder. Hos Klinik Zenit tilbyder vi skånsomme og dokumenterede teknikker til at reducere synligheden af blodsprængninger i ansigt og på krop. Vores behandlinger tilpasses individuelt og udføres af erfarne specialister med fokus på sikkerhed og langvarige resultater. Få vejledning om hudpleje før og efter behandlingen for at opnå det bedste resultat. Kontakt Klinik Zenit for en professionel vurdering og behandlingsplan.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 11:54:19
@ e2c72a5a:bfacb2ee
2025-06-05 11:54:19Think crypto analytics is just charts and graphs? Wrong. It's a crystal ball for savvy investors.
Analytics in crypto decodes blockchain data revealing hidden trends. It transforms complex data into actionable insights. Basic concepts include on chain metrics, sentiment analysis, and trading volume. Real world applications range from fraud detection to predicting price movements.
Current trends emphasize DeFi analytics and cross chain data aggregation. Best practices involve using multiple data sources and verifying information. A common misconception is that analytics guarantees profits. It only enhances decision making.
Institutional investors are diving deep into on chain analytics. Stablecoins are disrupting payments. Layer 2 solutions are leading the way.
Ready to see the future? What hidden patterns will you uncover?
-
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:16
@ 8bad92c3:ca714aa5
2025-06-05 15:02:16Key Takeaways

In this episode, Bram Kanstein delivers a powerful exploration of how studying money for thousands of hours led him to a single, life-changing conclusion: Bitcoin is the key to preserving value and reclaiming personal agency in an increasingly unstable world. Through the lens of a disillusioned millennial generation—raised with technological optimism but betrayed by economic reality—Bram exposes the fiat system as one built on illusion, debt, and diminishing returns. He explains how Bitcoin’s transparent, rule-based design offers a principled alternative, especially for those wired to question systems and seek truth. Describing the fiat economy as a “high-velocity trash system” that undermines innovation and long-term planning, he argues Bitcoin creates the time and space to think, build, and live freely. As AI reshapes the labor market, Bram sees Bitcoin as a vital foundation for individuals to adapt, maintain sovereignty, and thrive in a future defined by rapid technological disruption.
Best Quotes
“Anything that you would want to fix in the world is broken because the money is broken.”
“You’re stacking nothing. Literal paper.”
“You have to red pill before you orange pill.”
“The only thing you need to do is move to the other money that they cannot mess with.”
“One Bitcoin is one Bitcoin. That’s the whole point.”
“Millennials are primed to understand Bitcoin.”
“Bitcoin lets you get out of the rat race and start walking your own path.”
“The fiat mindset is a zero-sum game. In Bitcoin, value is created.”
“We should stop asking how to value Bitcoin—and start asking how to value everything else in Bitcoin.”
“Even with a master’s in economics, people still don’t understand what money is.”
Conclusion
This episode delivers a powerful call to rethink everything we assume about money, arguing that understanding Bitcoin is less about profit and more about reclaiming personal agency in a world defined by uncertainty. Bram Kanstein shows how asking fundamental questions—like “What is money?”—can lead to a deeper sense of purpose and autonomy. As AI and systemic instability accelerate, Bitcoin emerges not just as sound money, but as a life tool for intentional living, long-term thinking, and individual sovereignty.
Timestamps
0:00 - Intro
0:36 - INTJ bitcoiners
4:58 - The millennial headspace is primed for bitcoin
7:25 - Bitcoin gives time and space to build
15:29 - Fold & Bitkey
17:05 - Seeing systemic problems
26:25 - Bitcoin’s positive feedback loop
33:55 - Recognize your agency
37:58 - Unchained
38:27 - Fiat money creates uncertainty
44:41 - What is money?
54:04 - Money and energy
1:03:43 - Bitcoin allows growth
1:09:02 - Bitcoin/AI
1:31:34 - Optimistic noteTranscript
(00:00) Let's say you're a millennial and mid-30s and you want to retire in 30 years. If you calculate the amount of dollar, pound the euro, yen units. You need way more units of that money than you think right now. They are funding pension funds, but the pension funds are using that money for the people that are actually retiring.
(00:17) No one knows about money. They don't know how debt works, how finance works. But that's kind of how it's designed, right? Like that's what eventually keeps the Ponzi alive. And I just started with the question, what do you think happens if you call the bank and say like, hey, can I get 100 or 200k in cash? Man, you got an editor like in house.
(00:39) That's That's pro. That's uh it's because this setup I'm so far away from the computer. I just need somebody to hit the button. Okay. Okay. the extent the extent of of Logan's job extends far beyond just hitting the button. But yeah, INTJ I think uh I think it was as we rear into what looks to be another bull market.
(01:05) I think getting back to first principles and discussing the challenges of studying and understanding Bitcoin, it's important to to highlight the archetype of individuals who have studied fallen down the rabbit hole and really dedicated their lives to Bitcoin. And this INTJ cohort that exists within Bitcoin seems pretty material apparently. Yeah.
(01:35) I mean, I have many moments where I just realize that I'm lucky that my brain is wired in a certain way, you know. I feel like crazy blessed that I figured out this Bitcoin thing, you know, and that when I ran into certain realizations along the way in my Bitcoin journey that I was like, hm, you know, how does this actually work? you know, do I actually understand the systems I'm participating in, the things that I believe, you know, the the the the people that I abstracted um or or outsourced certain responsibilities to to take care of, for example, my money
(02:10) in the bank. You know, I I think um being wired in a certain way definitely helps in grasping Bitcoin to a degree where you're like, okay, this is the only thing I need to pay attention to, you know, in my life. And yeah, we we jokingly started talking about this because I have the hat here, but there was this um I think it was like like a Twitter poll actually or someone shared it on Twitter and this is already like two or three years old where where someone investigated these MyersBriggs um personality types and I think there's
(02:42) only like 2% of people that have INTJ but like 20% of Bitcoiners have that personality type. So it um it apparently helps. So yeah, I just I just quickly Googled it actually. It says uh the INTJ is the architect. It's a personality type with the introverted intuitive thinking and judging traits. These thoughtful tacticians love perfecting the details of life, applying creativity and rationality to everything they do.
(03:09) I think the rationality part here is what um what uh I think helps you to to gro Bitcoin eventually. Yeah, it reminds me of I forget what the study was, but postco it was a similar distribution of just like 2% of people were highly skeptical of what was going on with the lockdowns and the attack on bodily autonomy.
(03:38) And there was a study that was done about I forget it was bees or some type of fly that they they have like the horde of um the horde of the particular fly I think it was bees has like 2% act as these sort of alarm bells that are on the outside the outskirts of the community and they'll start communicating like hey something's wrong here and people the other flies or bees will be skeptical at first but then eventually uh the alarm bells will be proven to be right that there was some sort of danger around the corner. That's fascinating.
(04:09) Yeah. Yeah, that's fascinating. I I think we're not that special eventually, you know, like we think we have all this autonomy, but but um yeah, we're we're just wired in a certain way. And I think I don't know where you want to take this conversation, but I think, you know, part of growing up and being an adult is figuring out, you know, how do I actually work and how do I work with how I work, you know? Yeah. No, it is.
(04:36) And as I get older, creep into my mid-30s, which is hard hard to come to grips with, it is uh really falling back on like, all right, I I feel like I have a good perspective on the world and my place in it, and how do I just optimize to make sure I'm aligning my my work and my career, I guess, if you call it that, with what I'm passionate about. Yeah.
(05:00) Well, I also think that is actually why our generation, you know, my my podcast is Bitcoin for millennials. I think uh the millennials are primed to understand Bitcoin. You know, we are in this life phase where big things happen, you know, starting a family or settling somewhere or or making big career moves or decide Yeah.
(05:25) like deciding what am I going to spend like the next 10 20 years on and uh I think it's an interesting phase actually I I don't know how that was for you but but for me like the the 30s were really where I dove more and more into Bitcoin like got got that stronger conviction and also yeah kind of was invited to go further down that that rabbit hole you know and like how I see it now is that that Bitcoin is really the foundation for the rest of my life, you know, like it it gives me time and space to look forward and enthusiasm, you know, like I sometimes lurk on the
(06:01) millennial subreddit, you know, or the finance sub subreddit. And many people in our generation are very nihilistic, you know, they're very unsure about the future. Like some people aren't even having kids because they think they cannot afford it, you know. And uh whenever I read that, I just think like, yeah, I I don't really have those things.
(06:22) But I know it's because of Bitcoin, you know. I I know that Bitcoin gives me, yeah, like I said, the time and space to figure out what's next, like what should I focus on? Like it gives time and space to to try out stuff, to build something, you know, to to to really attempt at at doing something. Where I see many people that don't see that, they are more in the consumer type, you know, like they they just spend the money that's worth the most today, you know, like that's what they're incentivized to do. Yeah.
(06:49) And is is that why you started Bitcoin for millennials is to number one put the put the message out there. Millennials come listen to this. One of you Yes. that is trying to educate you about this. But because this is something I think about a lot is somebody's like dead smack in the middle of the millennial generation and has observed many of the things you just described in my own life, my own network.
(07:13) And that's part of the reason why this podcast exists. And um what I'm trying to do at TFTC is just try to figure out a way to reach into the minds of millennials, hopefully c -
 @ 0b118e40:4edc09cb
2025-06-05 05:52:28
@ 0b118e40:4edc09cb
2025-06-05 05:52:28The idea of Bitcoin as an internet native currency, and eventually a global one, is coming to life slowly. But historically, the idea of global currency has haunted the world’s financial imagination for nearly a century.
From Keynes’s Bancor in 1944 to Zhou Xiaochuan’s post-crisis proposal in 2009 to today’s renewed debates, the idea resurfaces every time the global economy fractures.
Could this time be different with Bitcoin?
I decided to trace the idea of global currency through several decades and books. I may have missed some parts, so feel free to add. I’ll keep this brief and leave the books I’ve read below.
In the beginning
It all started on July 1, 1944. 730 delegates from 44 Allied nations, including major powers like the US, UK, Soviet Union, China, and France, gathered at the Mount Washington Hotel in Bretton Woods, New Hampshire. They spent 2 weeks figuring out how the new international monetary and financial system would be, post WW2
After WW1, the treaty of Versailles was needed, but imposed harsh reparations that devastated economies and contributed to the rise of fascism, such as Hitler, Mussolini and gang.
So when folks met up in 1944 (WW2 was almost ending), the goal was to prevent another Great Depression, another global conflict and build a stable global economic order.
2 main proposals were discussed in Bretton Woods.
-
John Maynard Keynes, representing the UK, proposed the creation of a global currency called Bancor. It will be issued through a global central bank known as the International Clearing Union (ICU).
-
Harry Dexter White, representing the US, promoted a dollar-based system. Countries would peg their currencies to the US. dollar backed by gold. He also led the creation of the IMF and the World Bank.

To understand how both of these proposals work, let's look at an example.
-
Country A (Germany): Massive exporter
-
Country B (USA): Massive importer
-
Country C (Brazil): Balanced trade (imports = exports)
***Based on Dexter’s model and the current USD-based system, ***
Say Germany sells $1B worth of cars to the US. The US pays in dollars, increasing its trade deficit. Germany accumulates dollars as reserves or buys the US Treasury bonds. Over time, the US continues running trade deficits, while Germany keeps hoarding dollars. Hence the unsustainable debt of the US.
***In Keynes’s Bancor system, ***
If Germany sells $1B worth of cars to the US, then the US does not pay in dollars. Instead, the ICU credits Germany with 1B Bancors and debits the US with -1B Bancors.
The ICU police this. If Germany exceeds the surplus threshold, it pays interest or penalties to discourage hoarding. If the US exceeds its deficit threshold, it is warned to rebalance trade or face restrictions.
Here, Germany is incentivized to import more (e.g., from Brazil) or invest in global development. The US is encouraged to export more or reduce consumption. Brazil, with balanced trade, enjoys stability in Bancor flows and avoids pressure.
The idea behind Bancor was a zero-sum balancing act. No country could become “too big to fail” due to excessive deficits. But it was too complicated and idealistic in assuming every country could maintain balanced trade.
Dexter on the other hand had a few tricks up his sleeve. In the end, Dexter’s USD dominance proposal was adopted.
The Bretton Woods system established the US dollar as the central global currency
Why did dollar dominance win over Bancor?
Simplicity often wins over complexity. But more so ICU felt too centralized, asking nations to surrender economic autonomy to a global body. That didn’t sit well in a post-war world where sovereignty was non-negotiable. That and idealist economic trade balance views.
Dexter’s dollar-based system on the other hand wasn’t fair play at all. It was centralized and authoritarian in its design.
So how did Dexter pull it off?
They had gold. They were ahead in economic recovery.
And they had nuclear weapons.
At the time, the US held nearly 2/3 of the world’s gold reserves. It was a significant advantage in advocating for a gold-backed dollar as the bedrock of global trade.
The US proposed a fixed gold peg at $35 per ounce.
From a broader geopolitical backdrop, the global population in 1944 was about 2.3 billion, a fraction of today’s 8 billion. The world was far less interconnected. The war had devastated Europe, Russia, and much of Asia. Infrastructure, economies, and entire cities were in ruins. The US, by contrast, had faced far fewer casualties and damages. Being geographically isolated, it had minimal domestic losses, around a tenth of what Europe suffered, and its economy was poised to rebuild faster.
But gold dominance and economic recovery alone didn’t secure US financial dominance.
American scientific breakthroughs had already signaled global power. Physicists like Leo Szilard and Albert Einstein, who had fled Europe, helped develop nuclear weapons. Their intent was deterrence, not destruction. But once the bomb existed, it changed geopolitics overnight. The US had military dominance. And after Hiroshima and Nagasaki in 1945, it became the undisputed superpower.
In the end, the USD won and the vision for neutral global currency faded.
And 20 years passed on…
France sends its warship to the US
Under Bretton Woods, countries could exchange dollars for gold, but the US had been printing more dollars than it had gold to back it. And it used it to fund the costly Vietnam War and domestic programs like the Great Society under LBJ.
Belgian-American economist Robert Triffin pointed out a fatal flaw in the Bretton Woods system that came to be known as the Triffin dilemma.
-
The world needed US dollars for liquidity and trade.
-
But the more dollars the US pumped out, the less credible its gold promise became.
Yet the US kept promising that every dollar was still convertible to gold at $35 per ounce.
French President Charles de Gaulle saw this as financial imperialism. He called it the “exorbitant privileged position”. The world had to pay for what they bought with the money they have, but not the US.
So in 1965, France did something unexpected. It sent a warship to New York Harbor to physically retrieve French gold reserves held by the Federal Reserve.

Would it have escalated to war? Maybe. But likely not. It was perhaps more of a diplomatic theatre and a sovereign flex. France was exercising its right under the Bretton Woods agreement to convert dollars into gold. But doing it with military formality was to send a signal to the world that they don’t trust the US system anymore.
It was one of the first major public blows to the dollar’s credibility. And France wasn’t alone. Other countries like West Germany and Switzerland followed suit, redeeming dollars for gold and draining US reserves.
The Nixon shock
Given they did not have enough gold, the IMF introduced Special Drawing Rights (SDRs) in 1969. SDRs were an international reserve asset, created to supplement gold and dollar reserves. Instead of relying solely on the US dollar, SDRs were based on a basket of major currencies (originally gold-backed but later diversified).
The idea was to reduce the world’s dependence on the dollar and avoid a liquidity crisis. But SDRs were a little too late and a little too weak to solve the underlying problem.
By 1971, the US could no longer sustain the illusion. President Nixon “closed the gold window,” suspending dollar convertibility to gold.
The Bretton Woods collapsed and this marked the beginning of fiat money dominance.
The French pursuit
While France demanded justice in one corner of the world, the French franc, specifically the CFA franc, has been dominant in parts of Africa since 1945, long before 1971.
After WWII, France created two CFA franc zones:
-
West Africa: Communauté Financière Africaine (XOF)
-
Central Africa: Coopération Financière en Afrique Centrale (XAF)
These zones included 14 African countries, many of which were former French colonies. France maintained monetary control via currency convertibility guarantees and representation in African central banks. Till today it has influence over these country’s monetary policy.
Colonisation hasn't ended in some parts of the world.
Did countries stop using the USD after the Nixon shock 1971?
Nope. The US dollar was no longer convertible to gold and it dismantled the fixed exchange rate system. But most countries did not stop using the USD as their dominant reserve or trade currency. There were no decent alternatives. Instead, they floated their currencies or maintained a soft peg to the dollar or a basket of currencies.
The USD remained dominant in oil trade (OPEC priced oil in USD) - petrodollar deal, global debt markets and FX reserves (central banks kept holding USD).
In 1997, when many Southeast Asian countries were still pegged to the USD, Soros claimed that SEA will tank. The US further increased its credit rates leading to capital flight and eventual tanking of these countries leading to Asian Financial Crisis '97. Many financial crisis has similar vibe.
The 1999 Euro launch
The idea of a shared currency appeared again, this time through the forms of Euro. It was a mandatory system for member states of the Eurozone, and came with centralized authority, the European Central Bank (ECB), which controlled monetary policy for all participating nations.

At first glance, the euro seemed like a win. It eliminated exchange rate fluctuations, making trade within the Eurozone smoother. It gave weaker economies access to lower borrowing costs and helped Europe establish itself as a financial heavyweight. Today, the euro is the second most-used reserve currency after the US dollar.
But it came at a cost. Countries that adopted the euro lost monetary sovereignty and could no longer print their own money or adjust interest rates to respond to local crises. This became painfully clear during Greece’s debt crisis, where strict monetary policies prevented the country from devaluing its currency to recover. The one-size-fits-all approach meant that economies as different as Germany and Greece had to follow the same rules, often to the detriment of weaker nations. Debt-ridden countries like Italy and Spain were forced into harsh austerity measures because they could not manipulate their currency to ease financial strain. Meanwhile, richer nations like Germany and the Netherlands felt they were unfairly propping up struggling economies, creating political tension across the EU.
In recent years, the euro has faced pressure from global trade tensions, monetary tightening, and geopolitical instability contributing to market volatility and periodic depreciation against other major currencies.
The Bretton Woods 2.0
Believe it or not, after all that, there was a call for Bretton Woods 2.0. Yet another global currency dream.
When the housing market collapsed in 2008 followed by a series of domino effects, global banks froze lending, economies contracted, and panic set in. The crisis exposed how fragile the international financial system had become as it was overly reliant on debt, under-regulated, and centered around the US dollar.
Many countries, especially in the Global South and emerging markets, started to question whether a system built around a single national currency was sustainable.
China, for instance, had been holding huge amounts of US debt while the US printed more dollars through bailouts and quantitative easing. This created global imbalances as exporting nations were lending money to the US to keep the system running, while taking on the risk of dollar depreciation.
In 2009, China’s central bank openly proposed replacing the US dollar with a neutral global reserve currency suggesting SDRs (Special Drawing Rights) issued by the IMF instead.
These concerns led to a wave of calls from world leaders for a “Bretton Woods 2.0” , a modern rethinking of the post-WWII economic order. At G20 summits in London in 2009, countries like France, China, and Russia pushed for reforms in global financial institutions and more balanced power sharing.
In the end, the IMF received more funding, and some banking regulations were tightened in the years after. But no real overhaul happened. No surprise there? The dollar remained dominant.
The foundation of the global economy didn’t change, even though trust in it had been deeply shaken.
The growth of BRICS
In 2023, Brazil, Russia, India, China, and South Africa began discussing the idea of a shared currency or alternative mechanism to reduce the dependence on USD ie de-dollarisation. The sanctions on Russia didn't help. After Russia’s invasion of Ukraine, the US and its allies froze Russia’s dollar reserves and cut it off from SWIFT, the “backbone of global banking communication”. This made one thing clear. If you fall out with Washington, your access to the global economy can vanish overnight.
China’s growing economic power also gave it more leverage to process alternative options. It would trade in Yuan with Russia and Iran.
I know many still say it's at its early stage, but I see many countries hedging their bets quietly and aligning with Putin and Xi. It became more obvious after US imposed tariffs on multiple nations, signaling that economic tools can double as political weapons. The world’s second financial system is slowly forming.
What is the world looking for, for the last century ?
A global currency that is
-
Simple
-
Free from dominant power
-
Decentralised
-
Borderless
-
Scarce
-
Transparent
-
Inclusive, with self custody
-
Resilient in crisis
-
Built for individual financial sovereignty
-
A new backbone for global finance, owned by no one
It doesn’t matter where you’re from, what politics you believe in, or how your economy leans. The answer keeps pointing in the same direction:
Bitcoin
This is the first true global currency.
And it’s just there
Waiting...
.
.
.
Some books that might interest you :
-
The Battle of Bretton Woods by Benn Steil
-
Goodbye, Great Britain by Kathleen Burk and Alec Cairncross
-
The Ghost of Bancor by Tommaso Padoa-Schioppa
-
Confessions of an Economic Hitman by John Perkins
-
The Blood Bankers by James S. Henry
-
-
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:13
@ 8bad92c3:ca714aa5
2025-06-05 15:02:13Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 8bad92c3:ca714aa5
2025-06-05 15:02:13
@ 8bad92c3:ca714aa5
2025-06-05 15:02:13Marty's Bent
via me

I think we'll look back at last weekend as one of the most pivotal points in human history. Ukraine's Operation Spider Web is one of the more shocking things I've seen in terms of military operations in my life. It validates something that many bitcoiners, many cypherpunks, and many prescient individuals have been talking about for decades now at this point, which is asymmetric drone warfare.
The Sovereign Individual is a book that many bitcoiners have talked about throughout the years due to how prescient it was in terms of the inevitable emergence of a digital currency outside the control of central banks and governments. The book was written in the mid-90s, so the fact that the two authors were able to predict that something like bitcoin would emerge less than 20 years after writing the book is pretty incredible. However, digital currencies leveraging cryptography were not the sole focus of the book. Another portion of the book was dedicated to the idea of asymmetric drone warfare and its effects on society overall.
It seems pretty clear today that this is another call from The Sovereign Individual that is coming true. Obviously, unless you've been living under a rock, you've noticed that Ukraine has been using drones in the battlefield to target strategic Russian assets and individual soldiers over the last year. The amount of battlefield videos I've seen of Russian soldiers running from autonomous drones that are hunting them down has been increasing significantly over the last six months. The footage is truly harrowing. It is a death that I wouldn't wish on anybody. With Operation Spider Web Ukraine has increased the stakes of this type of drone warfare by going deep into Russian territory and targeting strategic long-range bombers, some of which had the ability to deploy nuclear warheads. This is sure to incite a reaction from Russia. No one will be surprised if, by the end of the week, Russia has started a shock and awe campaign that goes deep into Ukrainian territory in retaliation for the kamikaze drone strikes on their long-range aircraft. I pray for peace and a quick resolution to this war, and every other war for that matter.
I didn't come here to pontificate and give my thoughts on this particular war, but I would like to focus on this new tactic of war and what it means for military budgets moving forward. The Sovereign Individual laid it out clearly when they wrote in the 1990s that at some point in the future autonomous drones would be leveraged in the battlefield and prove to be asymmetric because of the fact that they are extremely cheap to produce. When you compare the price it cost to produce one of these drones to the price of the equipment they are destroying, things get pretty crazy. With tens of thousands of dollars of drone equipment the Ukrainian army destroyed tens if not hundreds of millions of dollars worth of long-range missile aircraft. And it did so without putting any Ukrainian military personnel in harm's way. Directly, at least.
When you consider the return on investment of deploying these drones compared to sending in soldiers, tanks, and your own aircraft, it becomes pretty obvious that this is going to quickly become the most logical way to fight a war moving forward. The question that remains is how quickly do other governments recognize this and implement it into their own defense strategies? As an American looking at our military budget, which is quickly approaching $1 trillion in annual spend, I'm forced to question whether or not most of that money is simply being wasted, considering the fact that we live in a time where these asymmetric battlefield strategies now exist. Why build new fighter jets when a Somali pirate, or nefarious individual for that matter, could use a $200 drone to destroy it in a matter of seconds with no threat of direct physical harm?
I'm no military expert, but if I were at the helm of the Defense Department, I would seriously be forcing those below me to focus a ton of effort on this problem and create plans to make sure that we are sufficiently protected from these risks. The only way to protect from these risks is to build the capabilities yourself. When it comes to the risk reward from a defense tech investment perspective I think a majority of the effort should be focused on defensive drone technologies and capabilities.
With that being said, it does seem like the US military is privy to this asymmetric reality that we currently live in. Defense contracts with Andruil make this pretty clear. Andruil is certainly ahead of the curve when it comes to autonomous drone warfare and defense against it. As an American, even though I don't like war, or the military industrial complex, knowing that the military is working with companies like Andruil does give me some comfort. However, the other side of that coin is that it is very unnerving when you consider that the government creating these public-private partnerships could lead to some Orwellian outcomes here at home. It may make some of you feel uncomfortable, but I believe the ideal scenario is that any individual has access to these types of defensive drone technologies in the future. The end goal being to create a nuclear game theoretical outcome where violence is reduced because one always has to assume that anyone they intend to attack has access to sufficient and formidable defensive technologies.
It's truly scary times we're living in as we transition further into the Digital Age. Part of the reason that I've dedicated my whole life to bitcoin is because I truly do believe that if you fix the money, you can fix the world. That is not to say that kinetic wars or physical violence will not exist in the future. It certainly will. But I believe sound money and open access to these systems and tools creates conditions which are much more suitable for cooperation and less so for conflict.
Multi-Signature Bitcoin Custody Is Replacing Single-Point Solutions
Jesse Gilger made a compelling case for why multi-signature Bitcoin custody represents the future of secure storage. He explained how Gannett Trust's approach ensures "not all of the keys are going to be at any one entity," fundamentally reducing the honeypot risk that plagues centralized custodians. This distributed model means no single point of failure can compromise your Bitcoin, whether through hacking, internal fraud, or regulatory seizure.
"I was on the list. I got the email. 'You were affected.'" - Jesse Gilger
Jesse's firsthand experience with the Coinbase data breach drives home why centralized custody is fundamentally flawed. While Coinbase holds keys for 10 of 12 Bitcoin ETFs, smart money is moving toward multi-institutional setups where Gannett holds a key, Unchained holds a key, and a third party holds a key. This alignment with Bitcoin's decentralized ethos isn't just philosophically pure—it's pragmatically superior for protecting generational wealth.
Check out the full podcast here for more on MSTY risks, Bitcoin retirement strategies and nation-state adoption dynamics.
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Trying to imagine the future my children are going to live in gets harder by the day.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients